Patents
Literature
78results about How to "Easy to deploy and implement" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
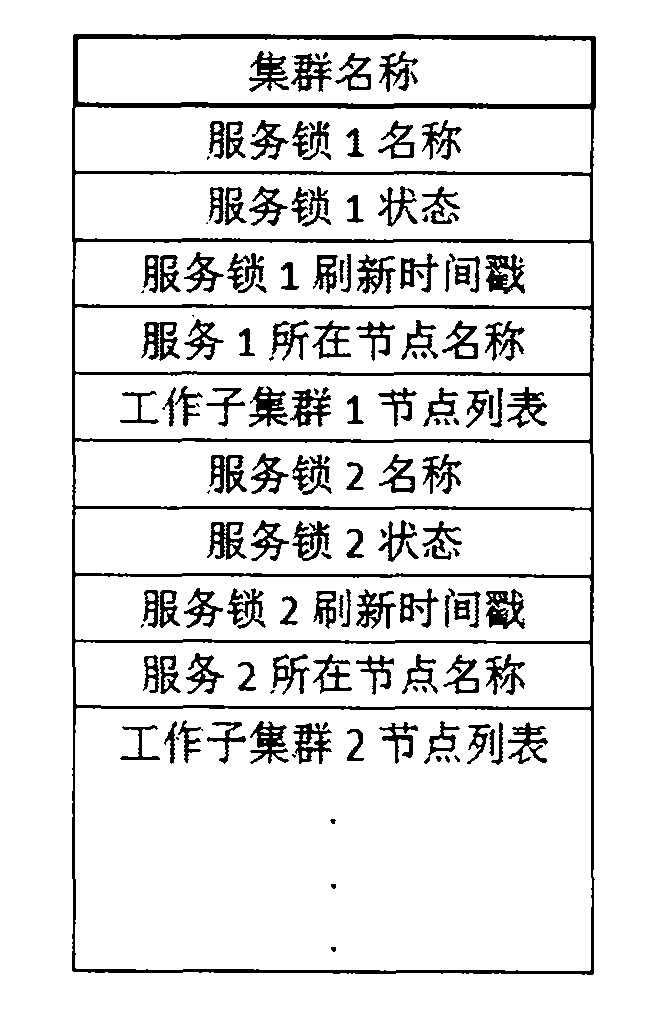
Arbitration server based cluster split-brain prevent method and device
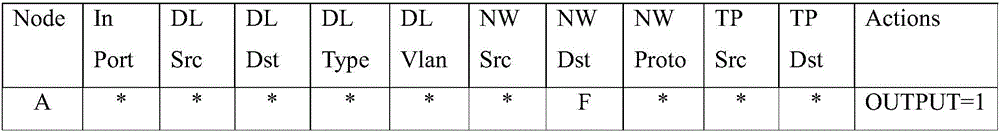
ActiveCN103684941AAvoid the risk of simultaneous launchesImprove resource usage efficiencyNetworks interconnectionSplit-brainCluster Node
The invention discloses an arbitration server based cluster split-brain prevent method and device, and belongs to high-availability cluster split-brain prevention technology in the field of computer cluster technology, in order to solve the problem that services cannot be taken over or the services run on two nodes at the same time due to the fact that states of other nodes and running services thereof cannot be accurately distinguished when a cluster heartbeat network is interrupted. The scheme includes that when the heartbeat network is interrupted, cluster nodes not running services can take over the services only by acquiring corresponding service locks through an arbitration server so as to avoid the problem of split-brain; after the services cease, the arbitration server recovers the service locks and allows other cluster nodes to preempt the same again; in the process that multiple nodes preempt one service lock, only one node succeeds in preemption and the services can be started to prevent occurrence of the split-brain.
Owner:GUANGDONG ZHONGXING NEWSTART TECH CO LTD
Public information intelligent analysis platform based on big data analysis and mining
InactiveCN104915793AImprove management efficiencyEasy to handleResourcesSpecial data processing applicationsData pre-processingCause and effect analysis
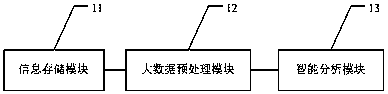
The invention provides a public information intelligent analysis platform based on big data analysis and mining. The public information intelligent analysis platform comprises a big data preprocessing module, an intelligent analysis module and an information presentation module. The big data preprocessing module is used for storing and preprocessing enterprise information via a clouded mode. The intelligent analysis module is used for performing event cause and effect analysis, assessment of the overall situation of the company and future trend prediction and returning analysis results to an upper layer by comprehensively utilizing the preprocessed data according to data analysis tasks transmitted by the upper layer. The information presentation module is used for generating the data analysis tasks to the intelligent business analysis module and receiving the returned results, presenting the analysis results of the intelligent analysis module and providing an operation interface to a user. Intelligent analysis is performed on mass data in enterprise operation by adopting a clustered computing method via flexibly establishing and configuring analysis models so that problems of poor real-time performance, high effectiveness and interactivity of a conventional data processing method are solved, the user is assisted to perceive the enterprise situation in real time and thus enterprise management efficiency and business processing level are enhanced.
Owner:北京航天数据股份有限公司
Intelligent early-stage training system for cognitive and communicating behaviors of autism children
ActiveCN103794110ALow costImproved cognitive communication skillsSpecial data processing applicationsTeaching apparatusPhysical medicine and rehabilitationSimulation
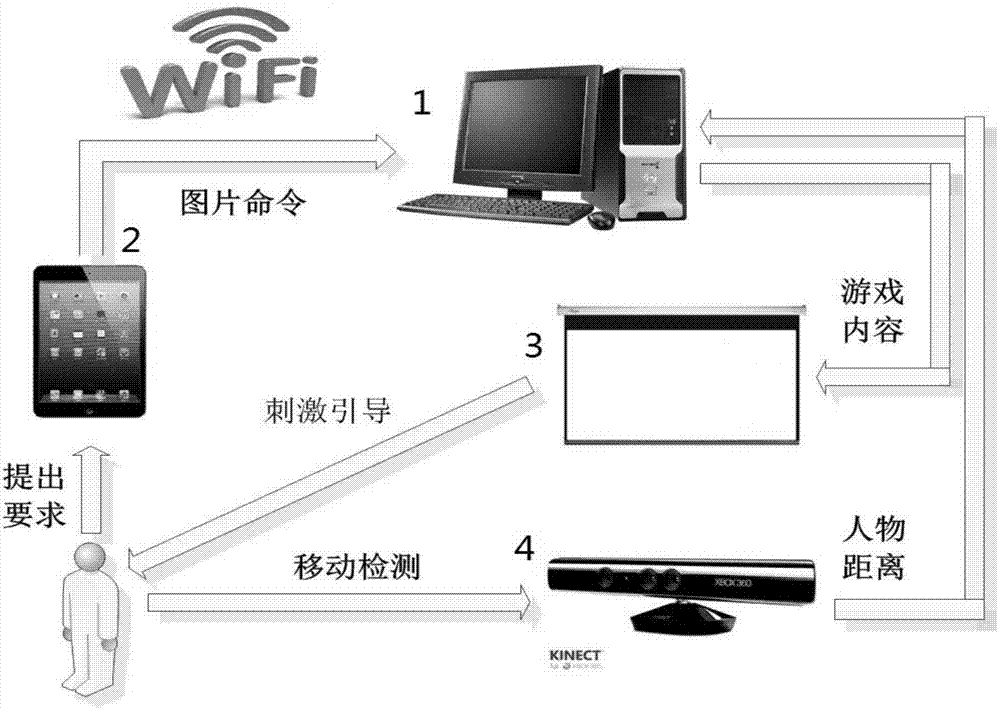
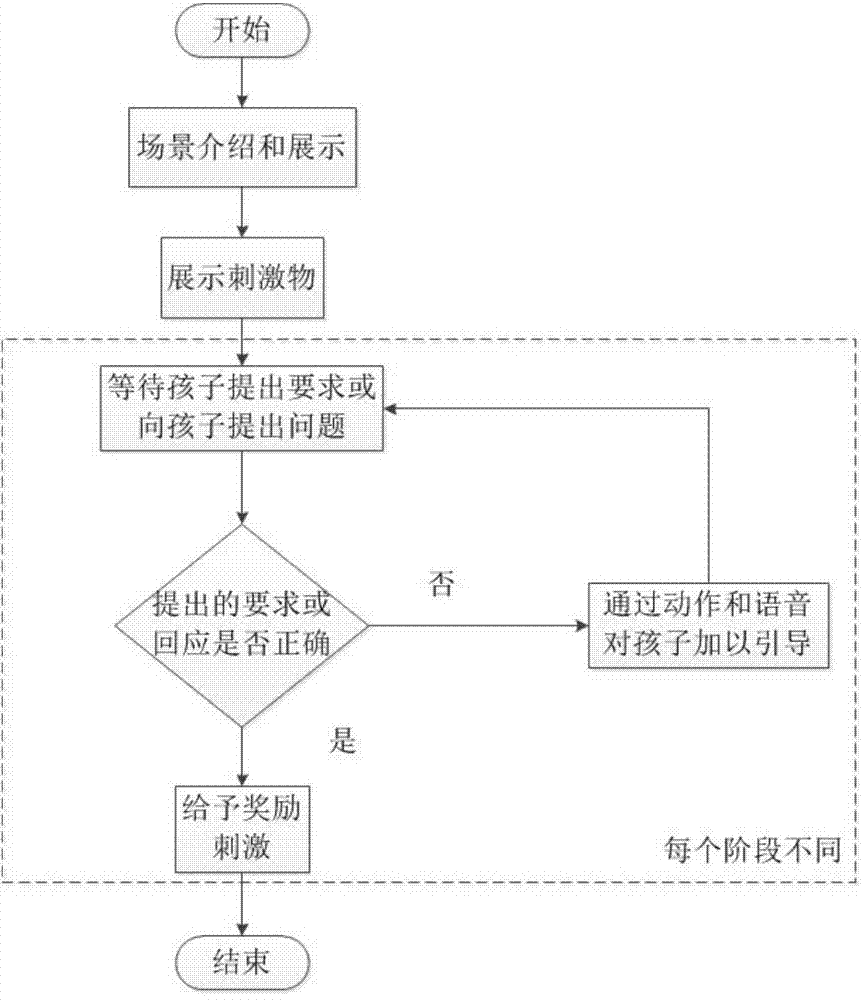
Disclosed is an intelligent early-stage training system for cognitive and communicating behaviors of autism children. A computer terminal is in data transmission with a hand-held terminal, and is further connected with an output terminal, a Kinect sensor is connected with the computer terminal, related information of behavior training games and treatment software is carried out on the computer terminal, the computer terminal 1 projects game pictures on a large screen, the trained autism children utilize a hand-held terminal device and software running on the device to send a command to the computer terminal, intersection between the hand-held terminal device and the computer terminal is achieved, the interactive process of the children and three-dimensional figures is completed, the Kinect sensor can detect position information of the trained children, and send the information to computer software of the computer terminal, the computer software can judge the next game process through the position information, and the whole game treatment process is completed. The system is beneficial to rehabilitation training and treatment of cognitive and communicating capability of the autism children.
Owner:XI AN JIAOTONG UNIV
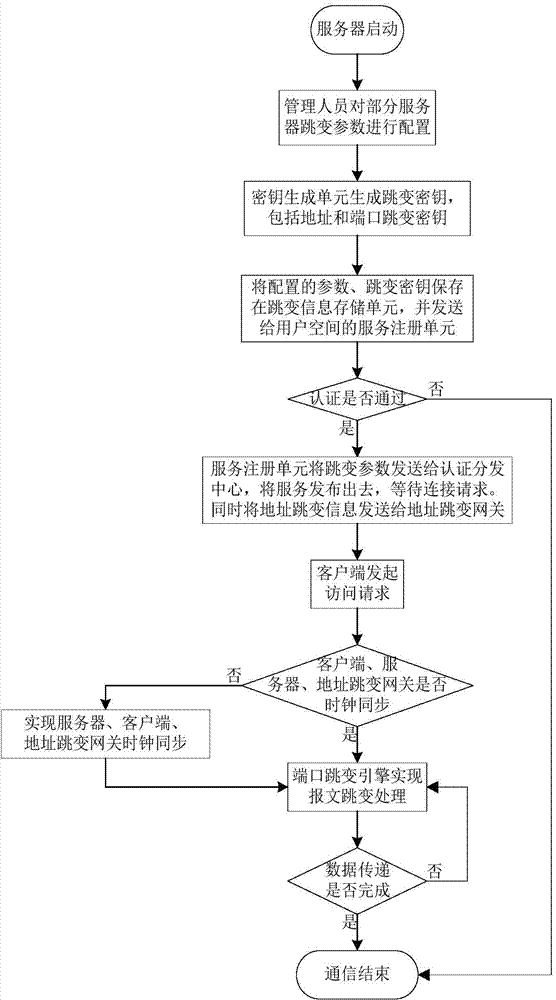
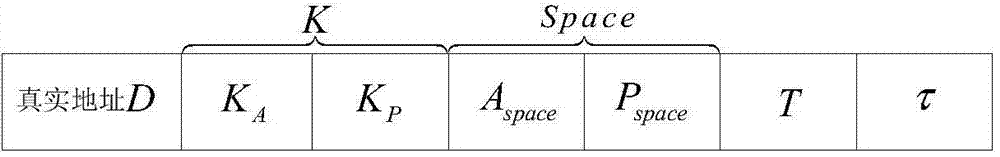
Netfilter-based address and port hopping communication implementation method
ActiveCN104853003AAvoid multiple copiesImprove processing efficiencyTransmissionComputer scienceClock synchronization
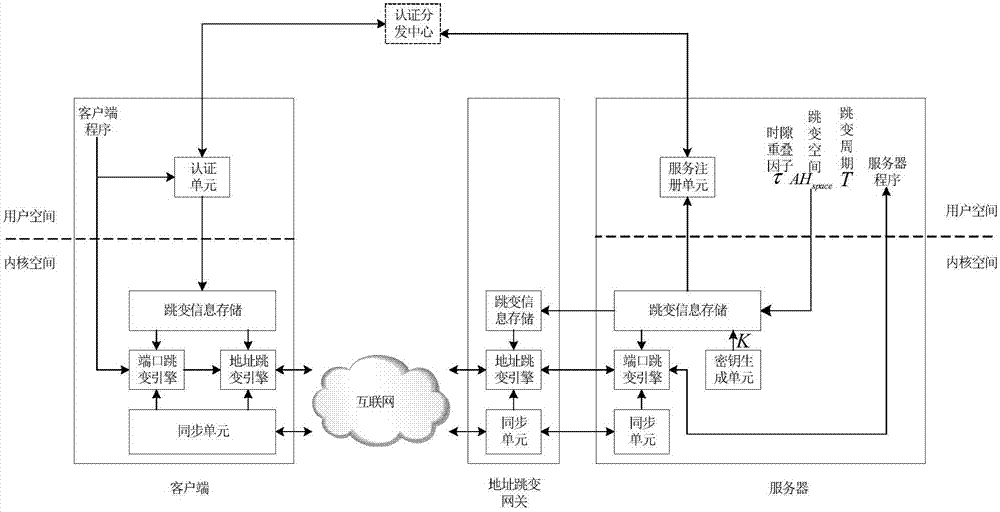
The invention provides a netfilter-based address and port hopping communication implementation method, which comprises the steps of 1) initially deploying; 2) configuring the hopping parameters of a server, generating a hopping key, storing the hopping key, and distributing the hopping parameters to an authentication and distribution agent by means of the server; 3) acquiring the hopping parameters of the server by means of a client after the authentication process of the client by an authentication and distribution center; 4) synchronizing the clocks of the client, the server and an address hopping gateway, calculating the current hopping address and the current hopping port of the server, and modifying addresses and ports corresponding to data messages sent and received by a local computer so as to realize the communication; 5) receiving communication messages received by the address hopping gateway from the client and the server, and acquiring the hopping address of the server by an address hopping engine according to the above address hopping parameters, and modifying addresses corresponding to the above messages to complete the message forwarding process; 6) realizing the port hopping function through a port hopping engine by the server, modifying ports corresponding to the messages of an importer / exporter to complete the communication. The method is simple in principle, easy to realize and popularize, and good in safety.
Owner:NAT UNIV OF DEFENSE TECH
Method for avoiding loop for routers adopting LFA mode in multilink fault environment
ActiveCN101599898AAvoid it happening againImprove performanceData switching networksComputer scienceRouting protocol
The invention relates to a method for avoiding loops for routers adopting LFA mode in multilink fault environment. As the traditional LFA rapid rerouting mode is mainly used to deal with single link fault, namely that the routers adopting LFA mode respectively calculate backup route entry of the route entry of the routers; with regards to the same target address, adjacent routers take each other as the next hop for backup thereof; so that when multilink faults occur, adjacent routers perhaps take each other as the next hop thereof to create loops. The method of the invention better deals with the restriction that the LFA mode can only handle single link faults; in addition, in the method, communication process is established between adjacent routers using LFA mode, so that when multilink faults occur in succession, loops can be avoided between adjacent routers adopting the LFA mode for rapidly rerouting; moreover, the method features simple and easy operation sequences, no need of greatly modifying the traditional router protocols and convenient deployment and implementation in terms of engineering.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Large-sized data centre IT system basic software and firmware platform deep cruising check system
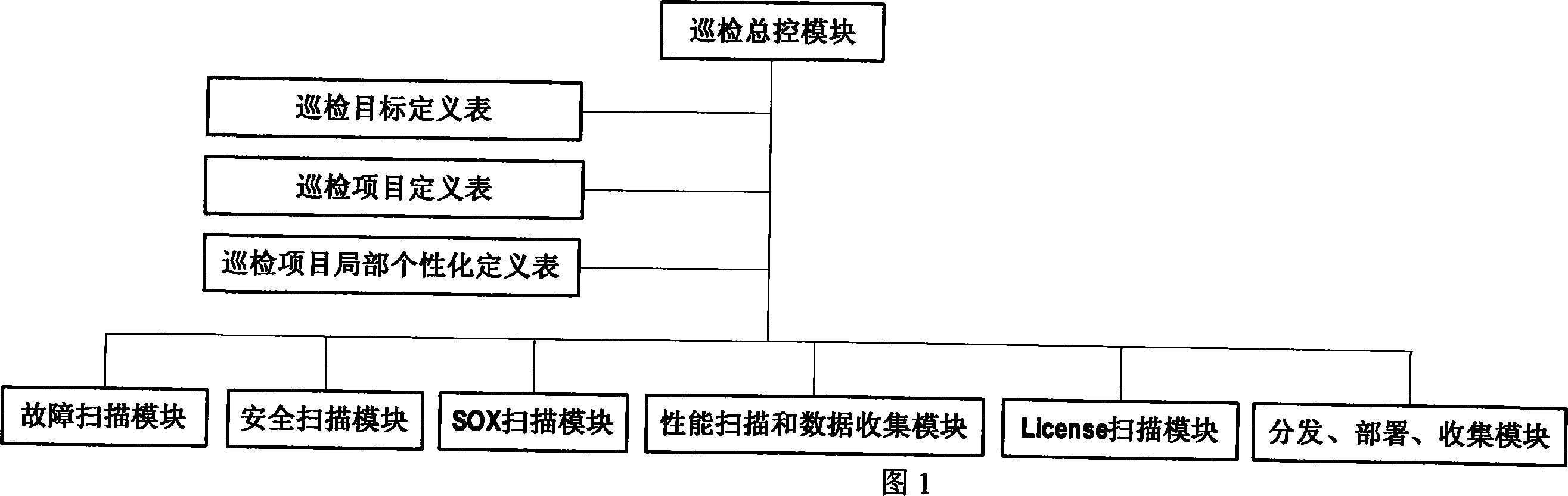
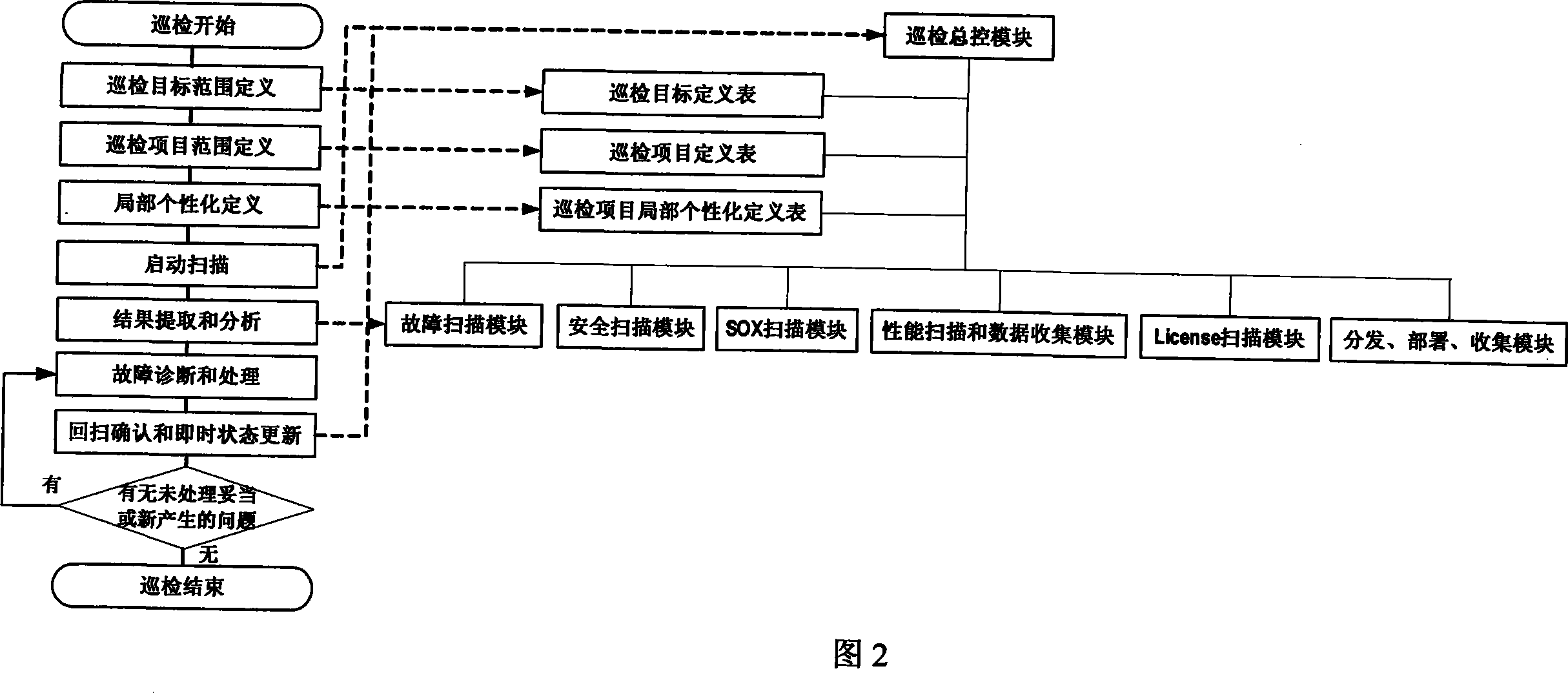
ActiveCN101216797AQuick extractionInspector generalHardware monitoringData switching networksPersonalizationData center
The invention discloses a deep inspection system and a method used on a basic software and hardware platform of a large data center IT system. The invention is characterized in that: the deep inspection system comprises an inspection main control module, an inspection object definition table, an inspection item definition table, an inspection item local personalization definition table, a fault scanning module, a security scanning module, a SOX scanning module, a performance scanning module and a data collection module, a License scanning module, and a distribution / deployment / collection module; during the inspection process, a destination range, an inspection item and an inspection item local of the inspection are respectively customized to ensure the destination range, the inspection item and the inspection item local of the inspection first, through the inspection object definition table, the inspection item definition table and the inspection item local personalization definition table; then the scanning is acted, namely, an inspection general control module starts up to control and select one module or a plurality of modules from the fault scanning module, the security scanning module, the SOX scanning module, the performance scanning module and the data collection module, the License scanning module and the distribution / deployment / collection module for inspection; at the same time, the inspection general control module adopts a nesting double-layer cycle to call each function module subroutine to inspect initially, to obtain an initial inspection result; after the double-layer cycle scanning, an initial inspection result file is collected by the inspection general control module and then is processed, filtered and analyzed for a second time, and is output to a result file.
Owner:CHINA MOBILE GROUP SICHUAN
System and method for realizing mobile service via broadband wireless access
ActiveCN101188856AIncrease speedReduce loadConnection managementData switching by path configurationAccess networkMobile business
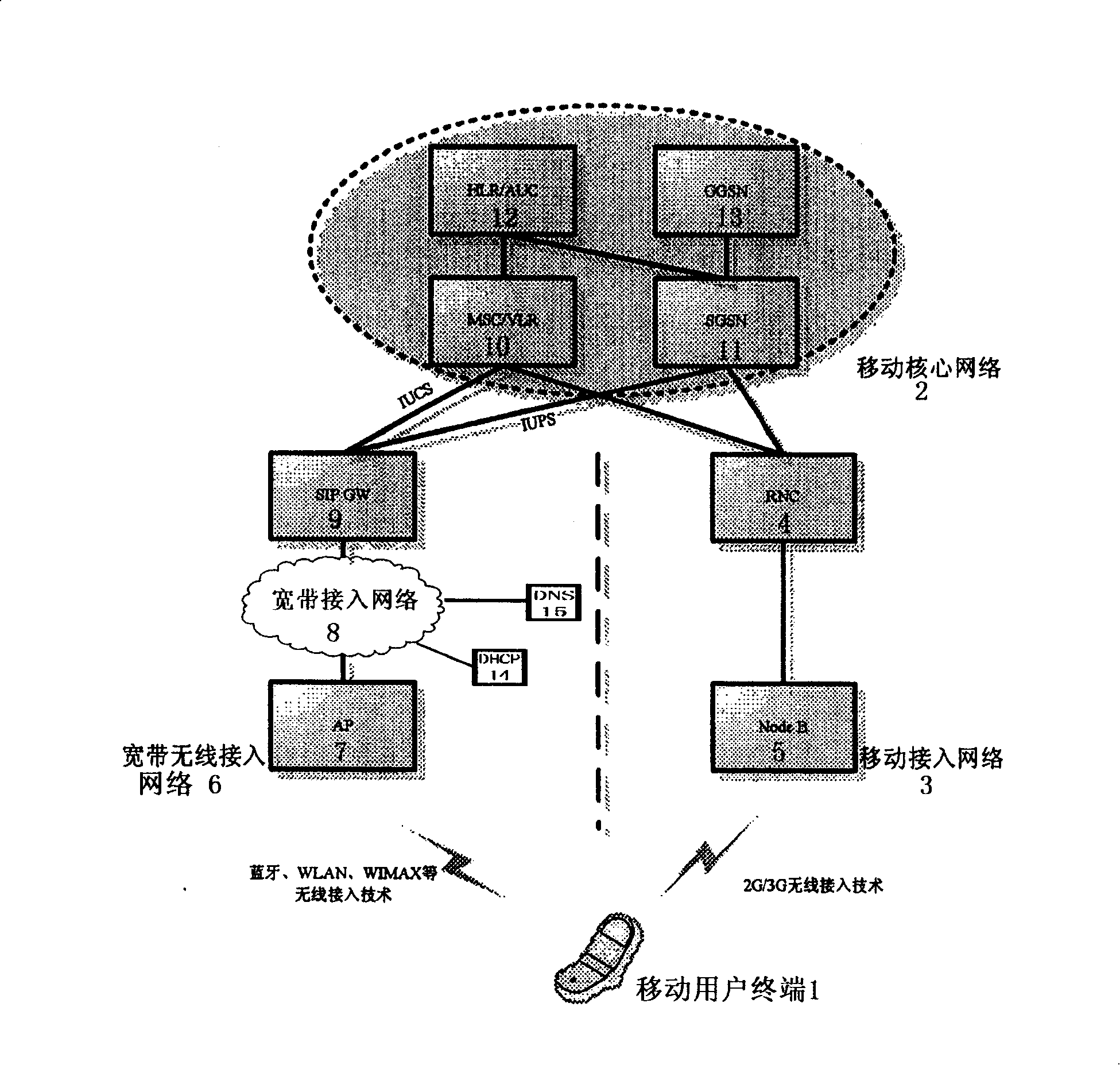
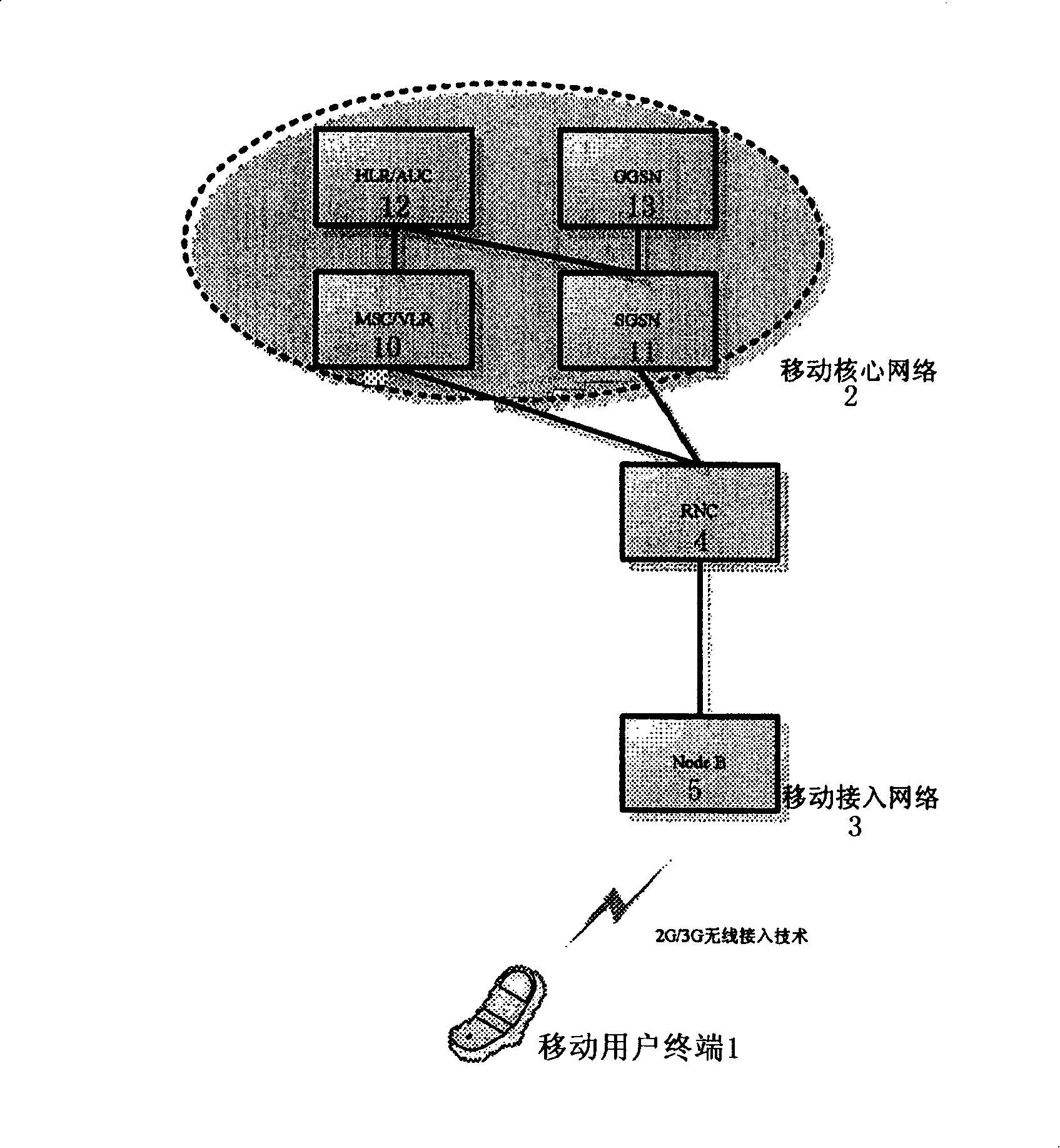
The invention provides a system which can realize mobile service through Broad Band wireless access, and the system comprises a mobile user terminal, a mobile core network and a mobile access network. The mobile user terminal has the capability of carrying out network access by a mobile wireless access technology and the capability of carrying out the network access by a wireless Broad Band technology; the mobile access network is arranged between the mobile user terminal and the mobile core network. The invention is characterized in that a Broad Band access network is also arranged between the mobile user terminal and the mobile core network, the Broad Band access network is coupled to the mobile core network through the session initial protocol network gateway SIP GW. The invention overcomes the limitation on the high speed rate service provided by the network with the prior art.
Owner:CHINA TELECOM CORP LTD
Abnormal flow monitoring method, device and equipment based on statistics and storage medium
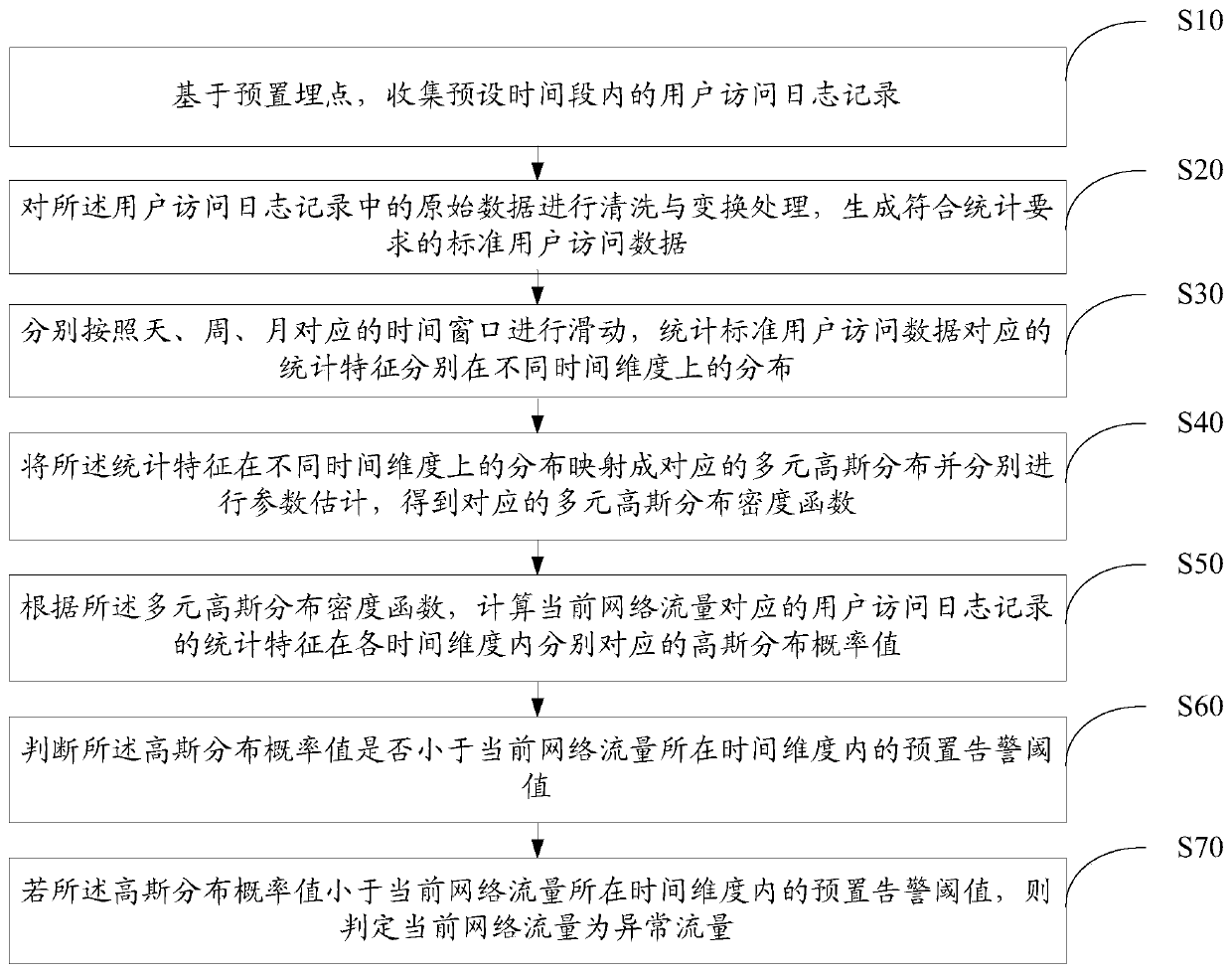
InactiveCN110830450AGood warningImprove the problem of high implementation costTransmissionInternet trafficTime segment
The invention discloses an abnormal traffic monitoring method based on statistics, which comprises the following steps: collecting user access log records in a preset time period, and carrying out cleaning and transformation processing to generate standard user access data; counting the distribution of statistical characteristics corresponding to the standard user access data in different time dimensions; mapping the distribution of the statistical characteristics on different time dimensions into corresponding multivariate Gaussian distribution and respectively performing parameter estimation; calculating Gaussian distribution probability values respectively corresponding to the statistical characteristics corresponding to the current network flow in each time dimension; judging whether the Gaussian distribution probability value is smaller than a preset alarm threshold value of the current network flow in the time dimension or not; If so, judging that the current network traffic is abnormal traffic. The invention further discloses an abnormal flow monitoring device and equipment based on statistics and a storage medium. The method is easy to deploy and low in implementation cost,and can flexibly respond to abnormal flow real-time alarms of different service scenes in different time periods.
Owner:PING AN TECH (SHENZHEN) CO LTD
Storm task deployment and configuration platform with cluster adaptability
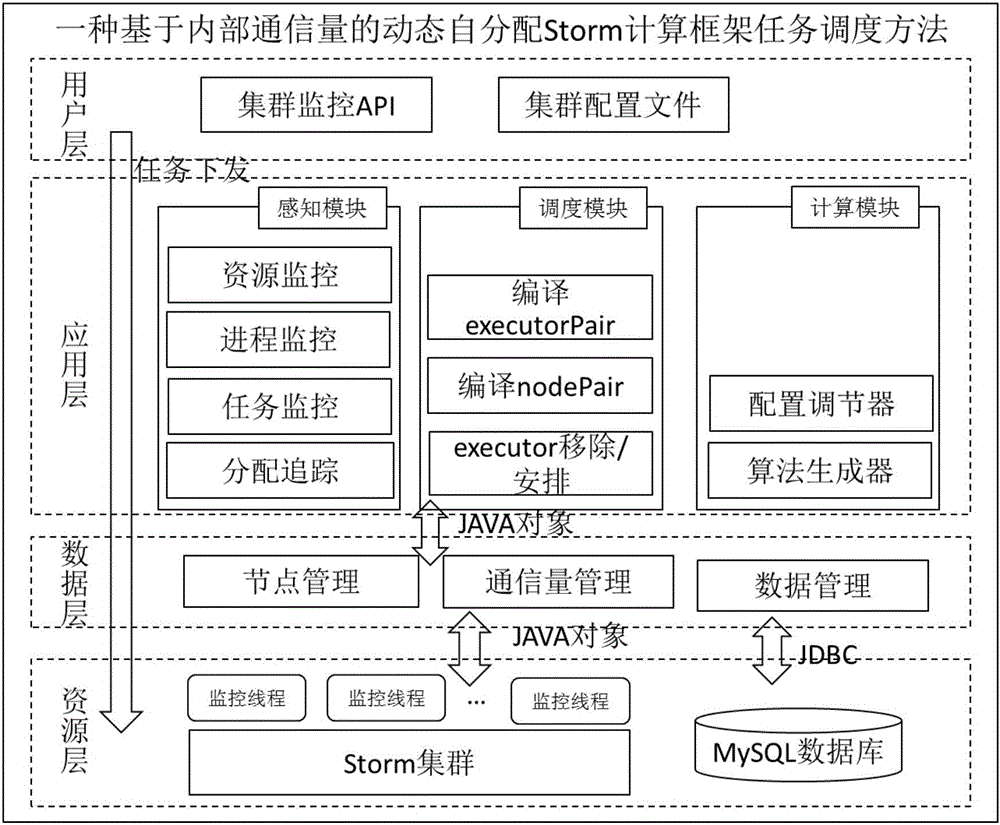
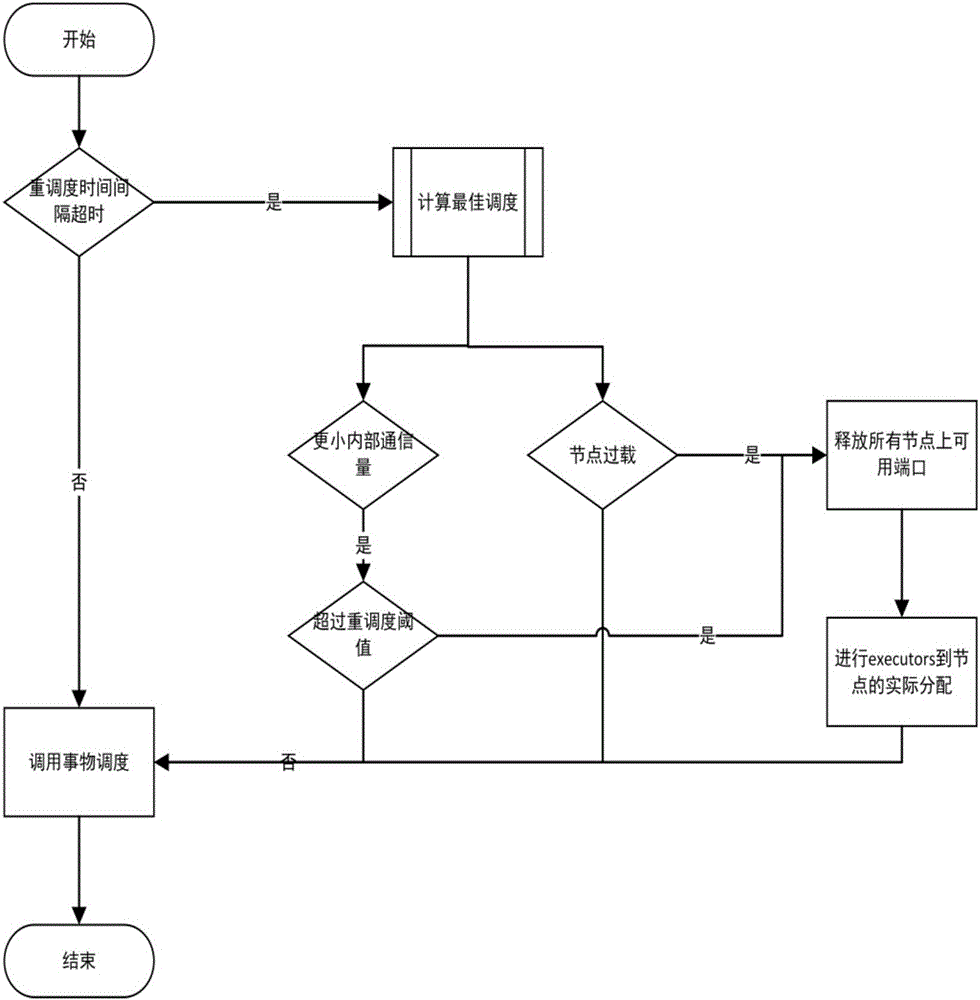
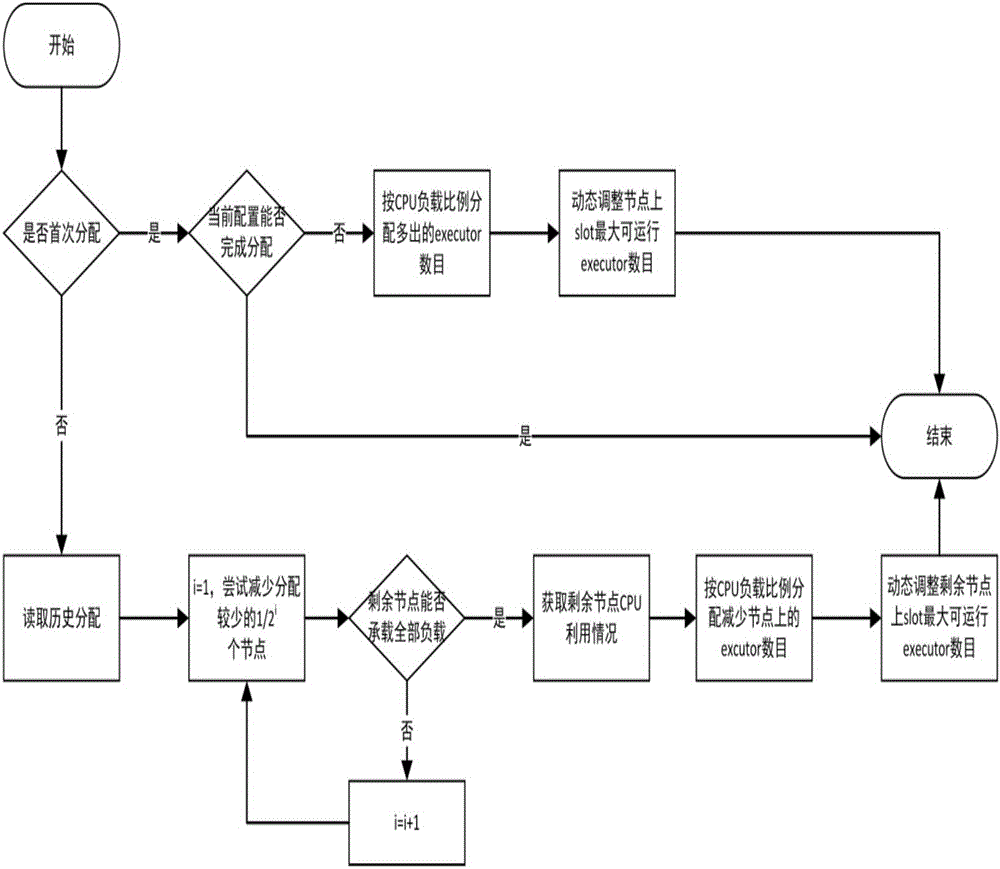
ActiveCN106021411ARealize monitoringImprove portabilityDatabase distribution/replicationSpecial data processing applicationsStreaming dataTask demand
The invention discloses a Storm task deployment and configuration platform with cluster adaptability, and belongs to the field of real-time streaming data computing and processing. Through the platform, a Storm cluster can sense internal communication traffic among nodes and remaining resources, and perform running process number configuration self-adjustment according to a topology task demand published by a user and the cluster remaining resources, so that the limitation of the need of artificially specifying a process number in a conventional Storm scheduling method is broken through. A friendly centralized communication traffic monitoring interface is provided for the user by the platform, and is convenient for the user to call in a task program, so that load and resource awareness is realized. Moreover, a one-phase commitment scheduling method which is different from a conventional Storm two-phase commitment scheduling method is implemented on the platform in an embedding way, and communication traffic optimization among different processes at the same node is realized. Through adoption of the Storm task deployment and configuration platform, optimal scheduling can be realized by setting of basic optimization threshold parameters, and great convenience is brought to a cluster user and a manager.
Owner:DALIAN UNIV OF TECH
IBeacon indoor positioning system and method
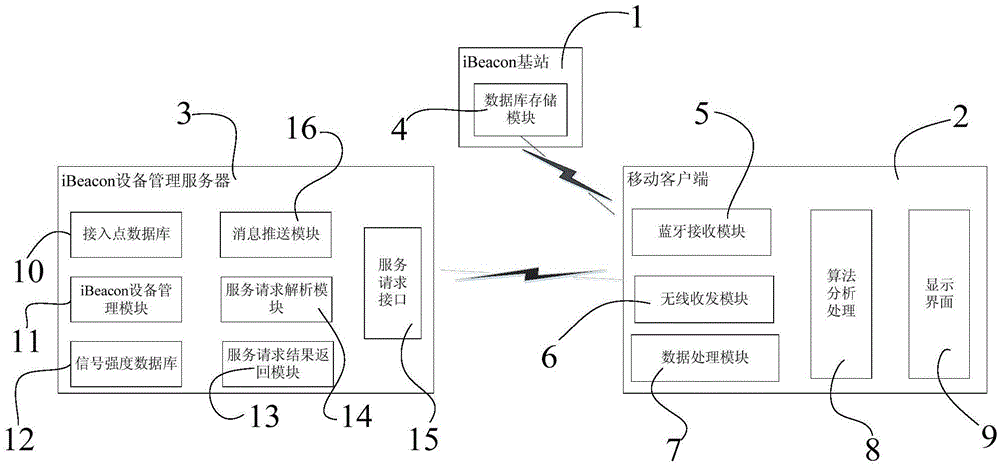
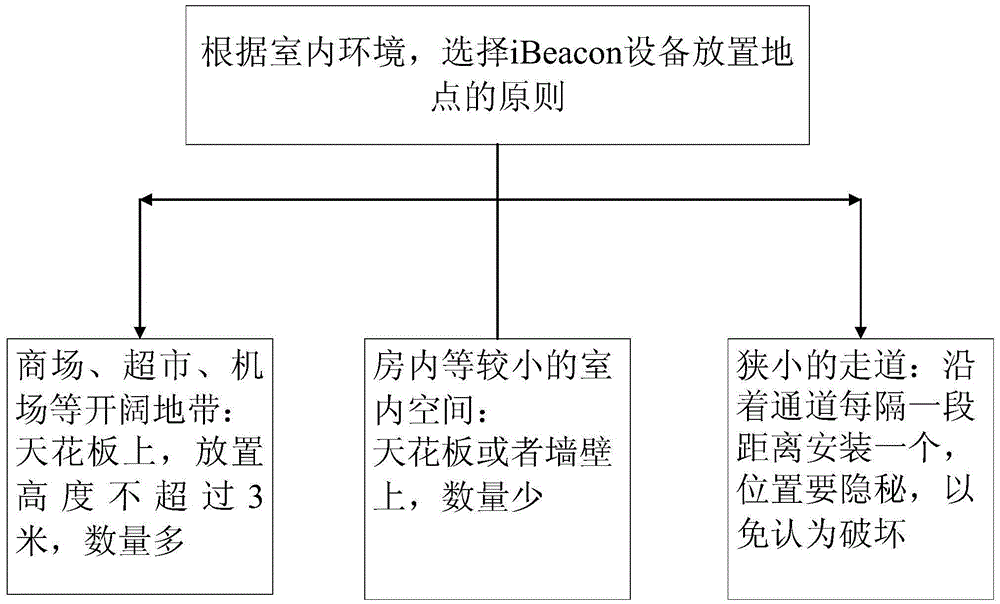
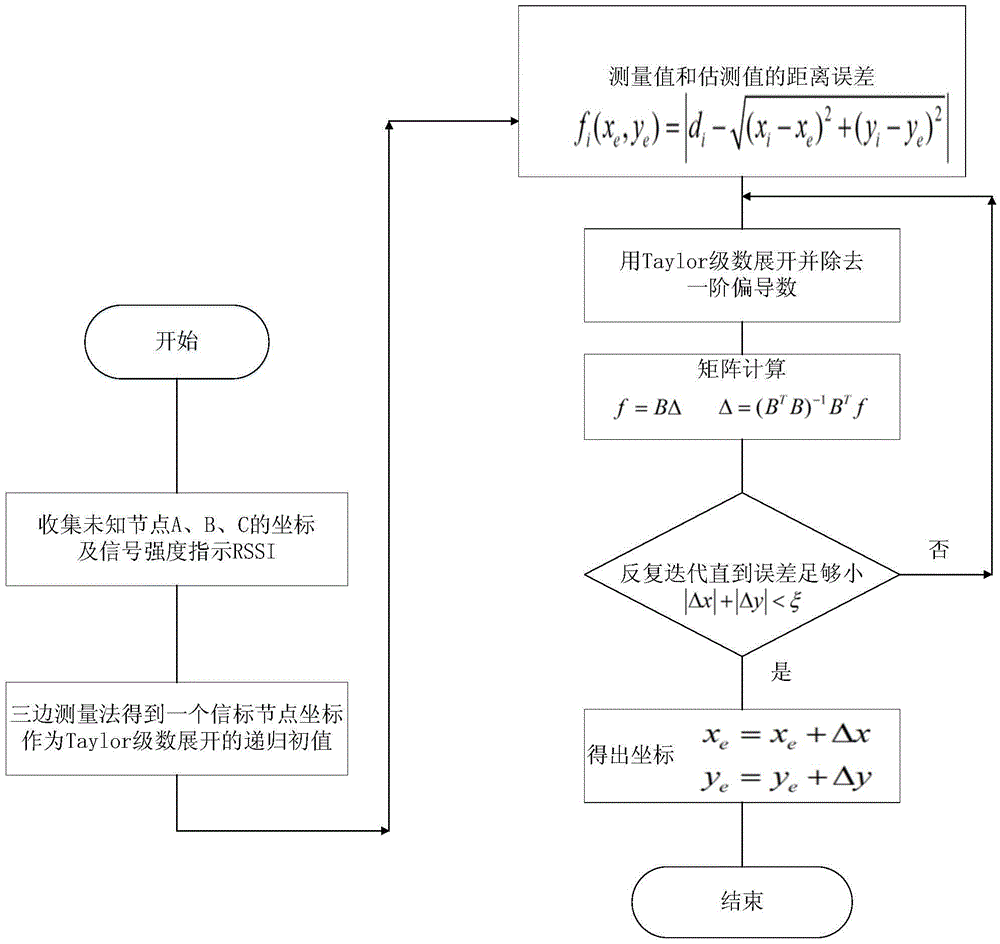
InactiveCN105636199APrecise positioningCompact structureNavigational calculation instrumentsWireless communicationClient-sideIBeacon
The invention relates to an iBeacon indoor positioning system and method. The system comprises an iBeacon base station, a mobile client and an iBeacon equipment management server; the mobile client sends a positioning service request to the iBeacon equipment management server, and the iBeacon equipment management server verifies the mobile client and the iBeacon base station; after the iBeacon equipment management server verifies and confirms the identify information of the mobile client and the iBeacon base station, the iBeacon equipment management server transmits position information of the corresponding iBeacon base station and distance information between the iBeacon base station and the mobile client to the mobile client; and the mobile client determines the position information thereof by using trilateration and a Taylor series expansion method according to the position information of the iBeacon base station and distance the information between the iBeacon base station and the mobile client returned by the iBeacon equipment management server. The system is compact in structure, can realize high-precision positioning of different indoor environments, is easy to deploy and implement, and is secure and reliable.
Owner:WUXI WUXIN INTERNET TECH CO LTD
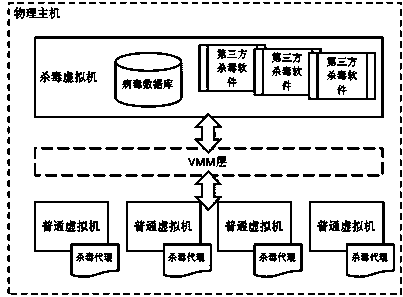
Computer virus searching and killing method based on desktop cloud virtualization technology
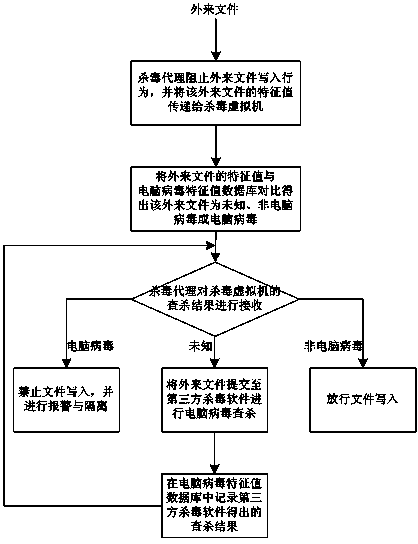
InactiveCN103810429AReduce consumptionReduce attack surfacePlatform integrity maintainanceSoftware simulation/interpretation/emulationVirtualizationThird party
The invention discloses a computer virus searching and killing method based on the desktop cloud virtualization technology. The method mainly solves the problems that in the prior art, when virus killing is carried out on a virtualization platform, resources of a server are occupied, a virus storm and a virus killing storm are easily formed and management is inconvenient to achieve. When more than two independent virtual hosts are allocated for each physical host, one of the virtual hosts serves as an antivirus virtual machine, the rest of the virtual hosts serve as common virtual machines, a third-party antivirus software is integrated in the antivirus virtual machine so that the antivirus virtual machine can have capacity for searching and killing viruses and recording searching and killing results, antivirus agents are installed in the common virtual machines, and a computer virus characteristic value database is installed in the antivirus virtual machine. By the adoption of the scheme, the method is convenient to use and high in extendibility and has high practical value and promotional value.
Owner:CHENGDU CHANGTIAN INFORMATION TECH CO LTD
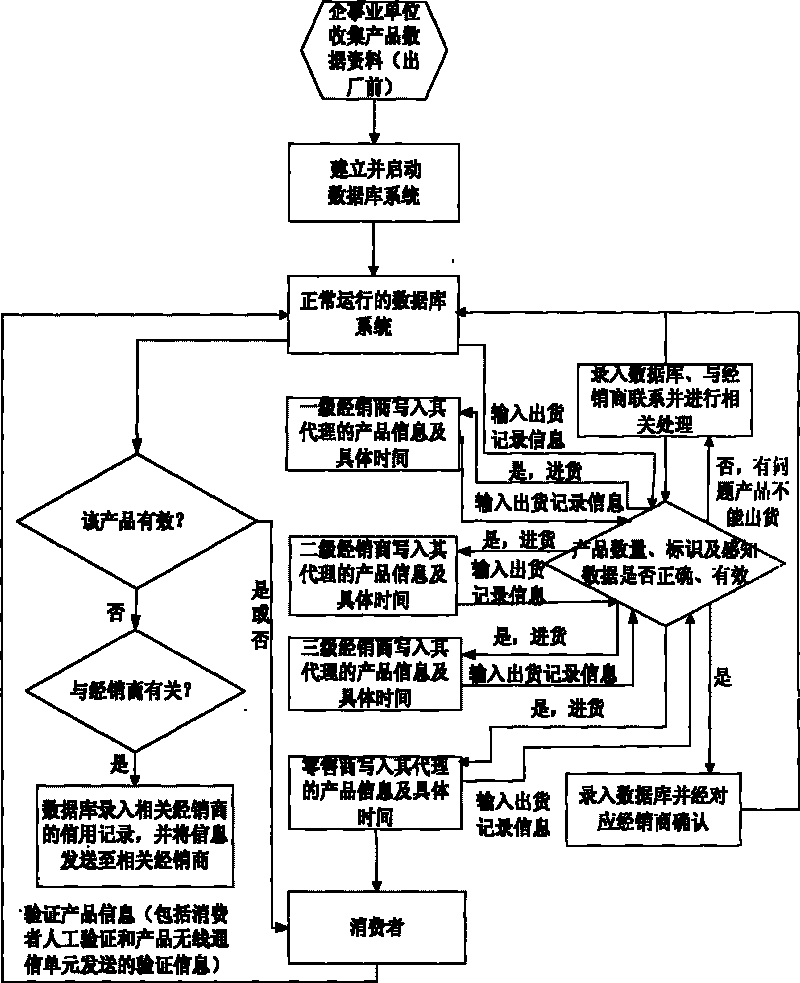
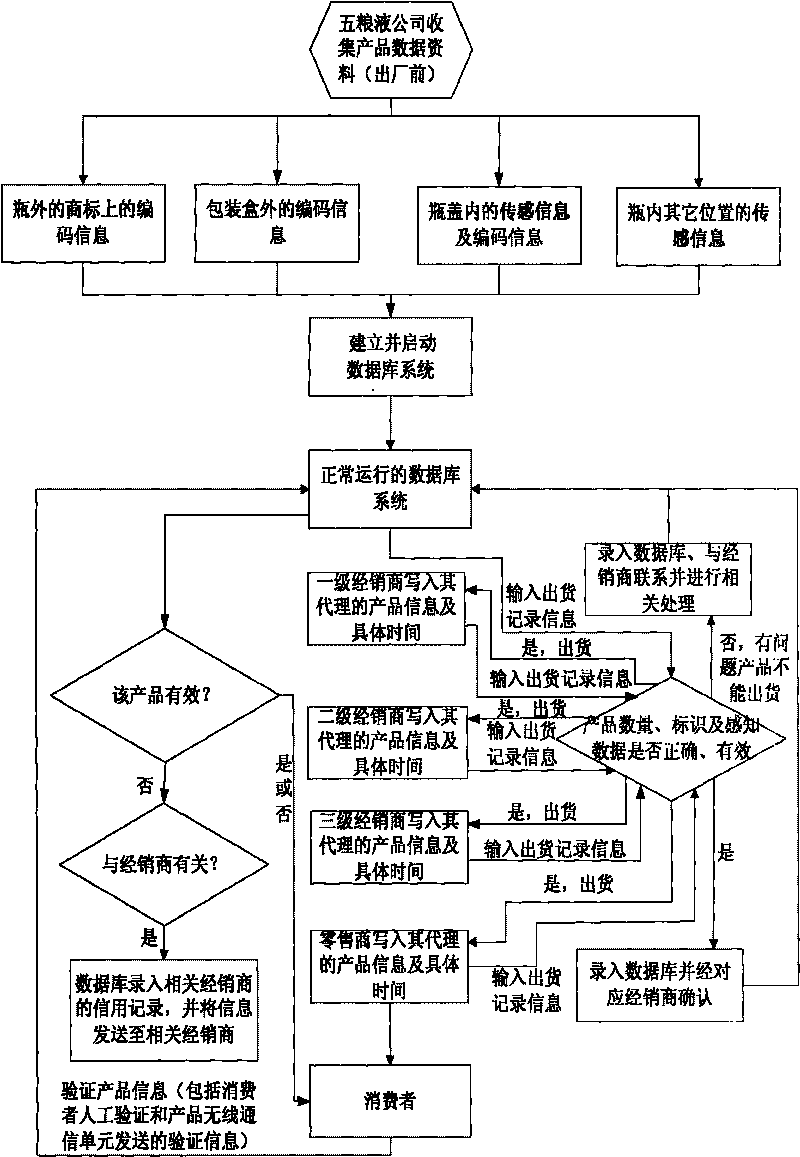
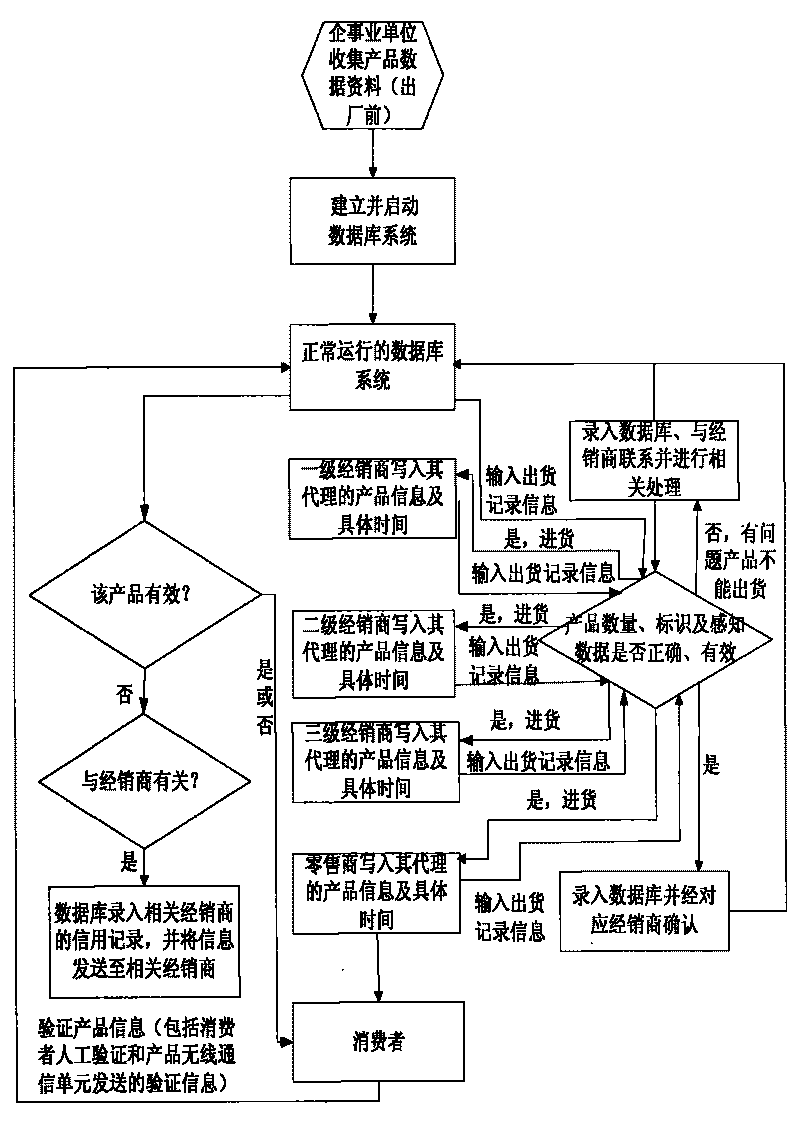
Mutually unique mark implementation method for terminal of Internet of Things
InactiveCN101765224AFlexible implementationFlexible implementation methodNetwork topologiesSpecial data processing applicationsData informationSpecific time
The invention relates to a mutually unique mark implementation method for a terminal product of Internet of Things. The method comprises the following steps: enabling the mark of a terminal of Internet of Things to correspond to the marked product one by one; establishing and enabling a real-time database according to effective data information such as plant quantity and specific time of leaving the factory of the product, corresponding numbers and EPC information, and different statuses corresponding to different perception data; transmitting the identifying information into the database, and confirming the trueness of the terminal product by the database through the mark information and the identifying information. The method has the advantages of flexible application, convenient deployment and implementation, wide application range, easy networking, low cost and very high use value and market value.
Owner:彭保
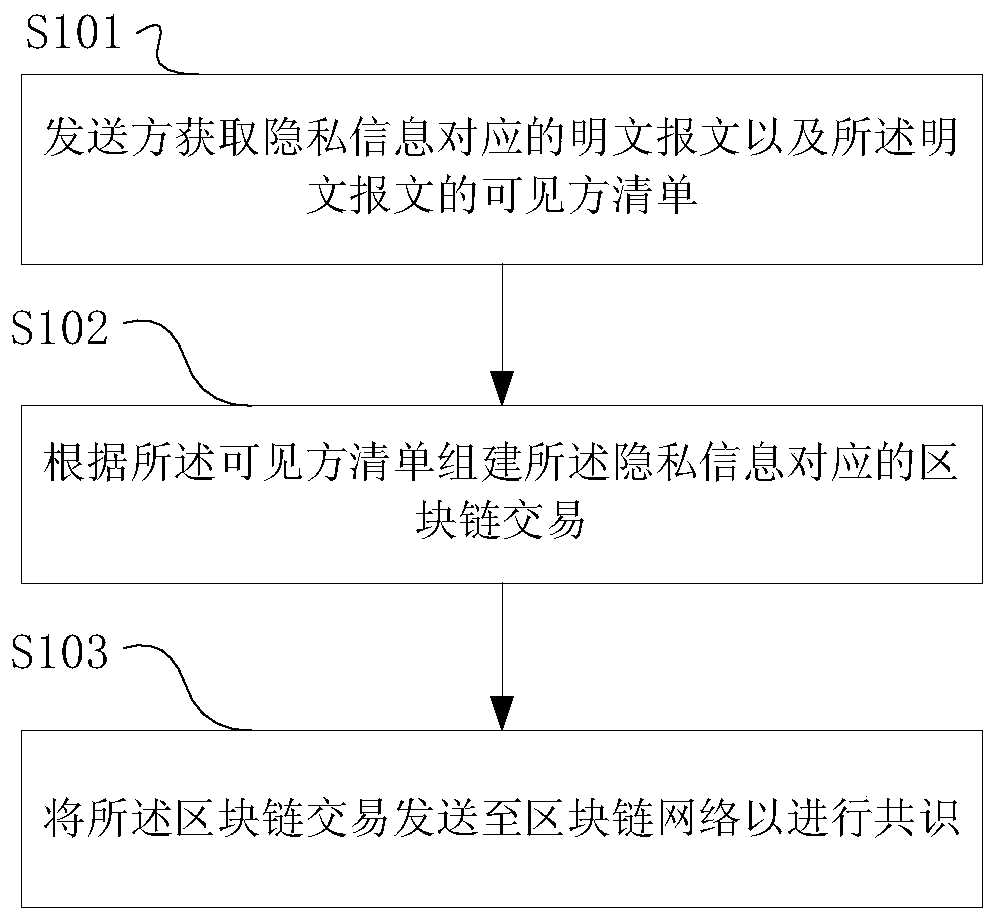
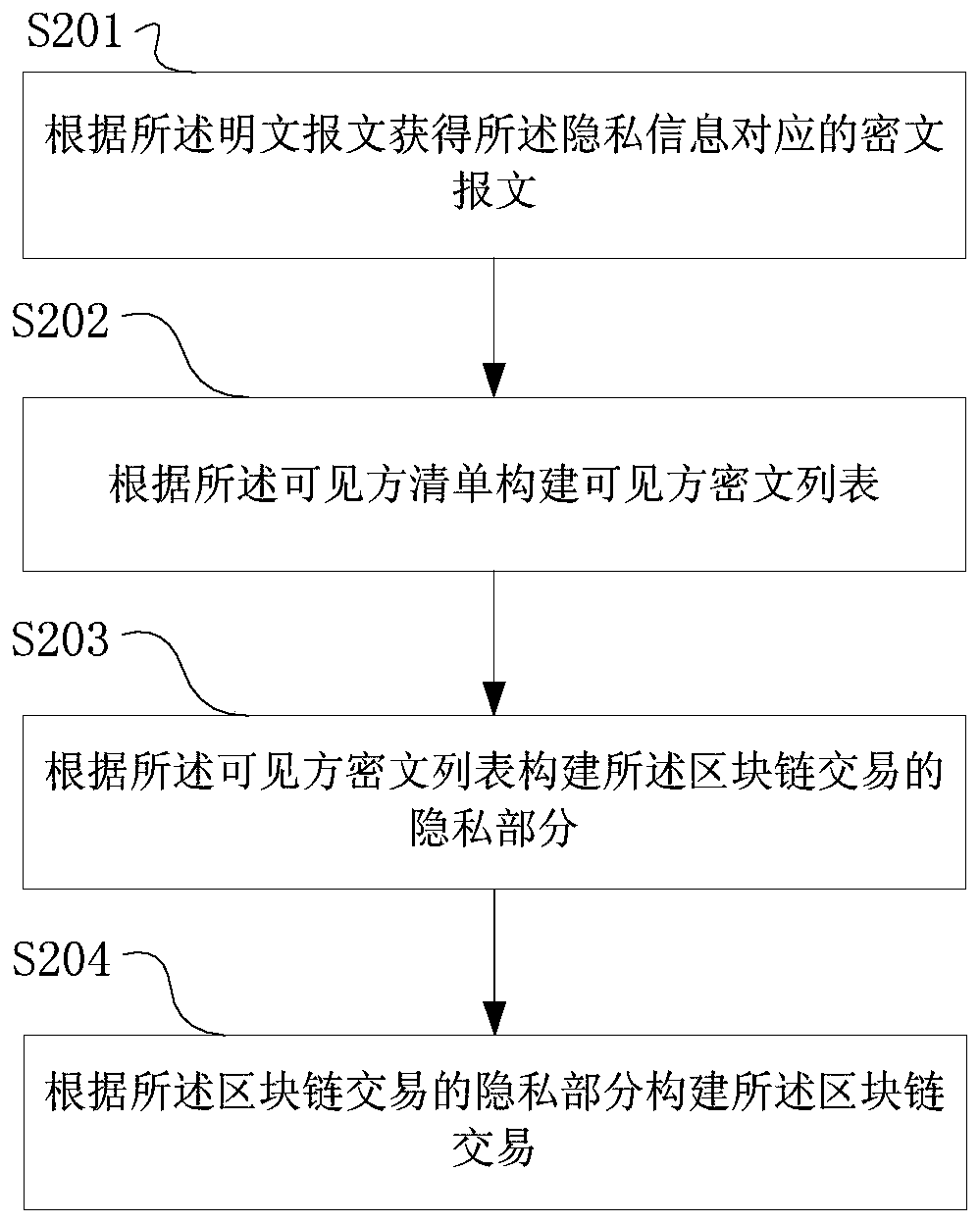
Transaction privacy protection method, device and system based on block chain system
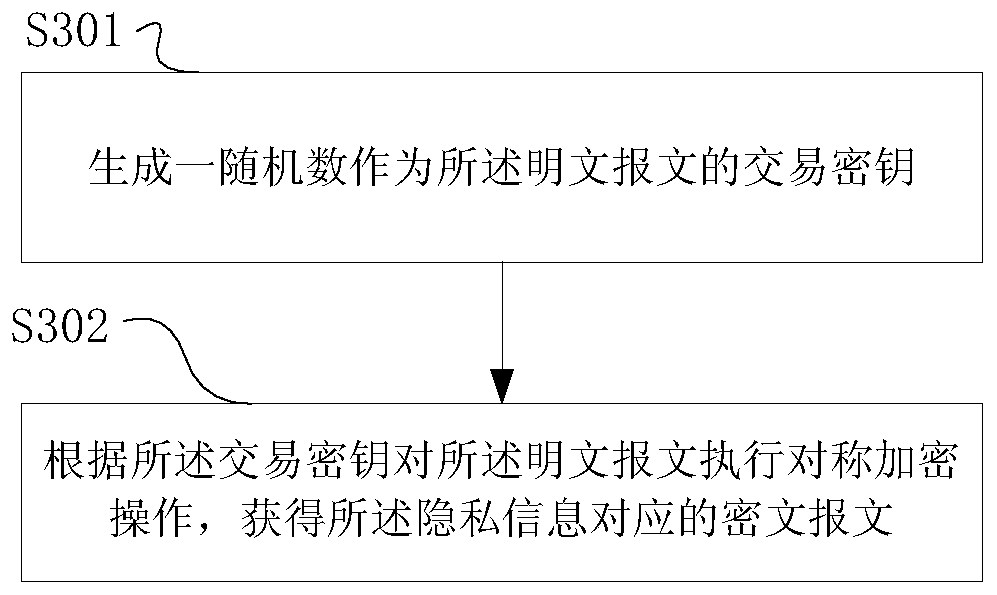
ActiveCN110335043AReduce generationReduce distributionDatabase distribution/replicationPayment protocolsPlaintextCiphertext
The invention provides a transaction privacy protection method based on a block chain system, a sender, a viewer, a system, computer equipment and a computer readable storage medium, and relates to the technical field of data processing. The method comprises the steps that a sender obtains a plaintext message corresponding to privacy information and a visible party list of the plaintext message, builds a block chain transaction corresponding to the privacy information according to the visible party list, and sends the block chain transaction to a block chain network for consensus; and the visible party acquires the block containing the private information, analyzes the block, acquires the ciphertext message of the private information and the ciphertext list of the visible party, and acquires the plaintext message of the private information according to the ciphertext list of the visible party and the ciphertext message. According to the method, the purpose that the privacy field is only readable to the designated participant is achieved by encrypting the key data needing privacy protection in the transaction, and efficient privacy encryption is achieved through a method of matchingsymmetric encryption and asymmetric encryption.
Owner:BANK OF CHINA
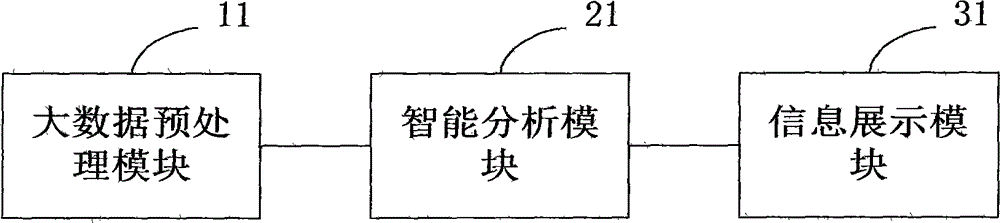
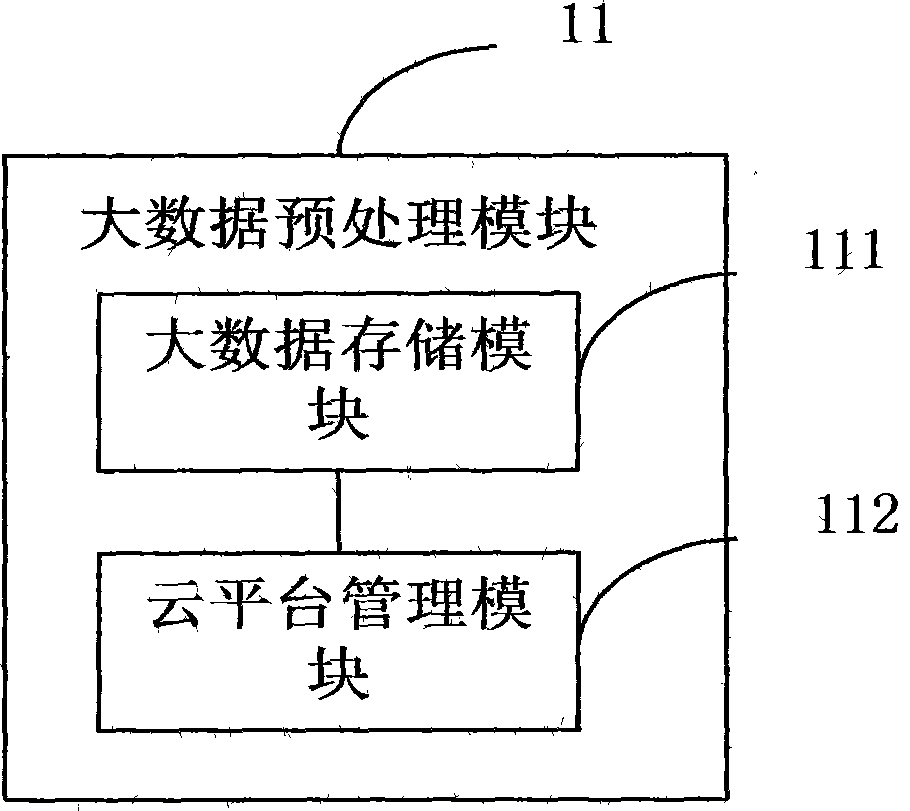
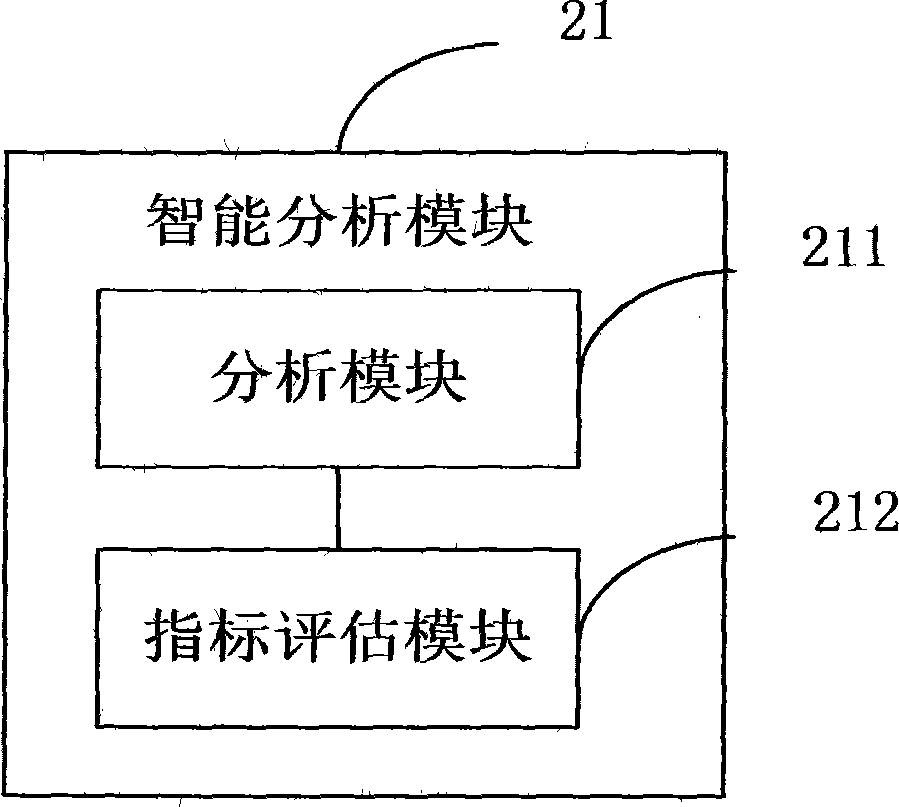
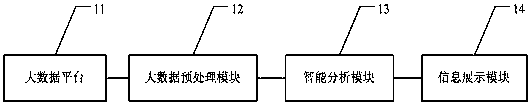
Big data intelligent analysis system
InactiveCN107590181AGive full play to computing powerProcessing speedSpecial data processing applicationsData platformResource virtualization
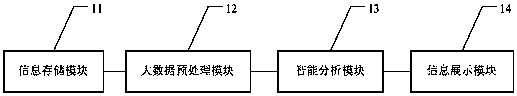
An embodiment of the invention provides a big data intelligent analysis system. The system comprises a big data platform used for storing and receiving collected big data, a big data preprocessing module used for preprocessing the collected big data, an intelligent analysis module used for performing big data analysis according to a received instruction and performing event causal analysis by comprehensively utilizing the data provided by the big data preprocessing module, and an information display module used for generating a data analysis task, transmitting the data analysis task to the intelligent business analysis module and receiving a result returned by the intelligent analysis module, wherein the preprocessing is used for realizing load balancing, resource virtualization and distributed data storage management. Through an interactive visualization technology, analysis and evaluation results of enterprise information and various detail data are hierarchically subjected to comprehensive and real-time display. By applying the system, the problems of relatively poor timeliness, efficiency and interactivity of a conventional data processing method are solved.
Owner:FOSHAN SHENYAN INFORMATION TECH CO LTD
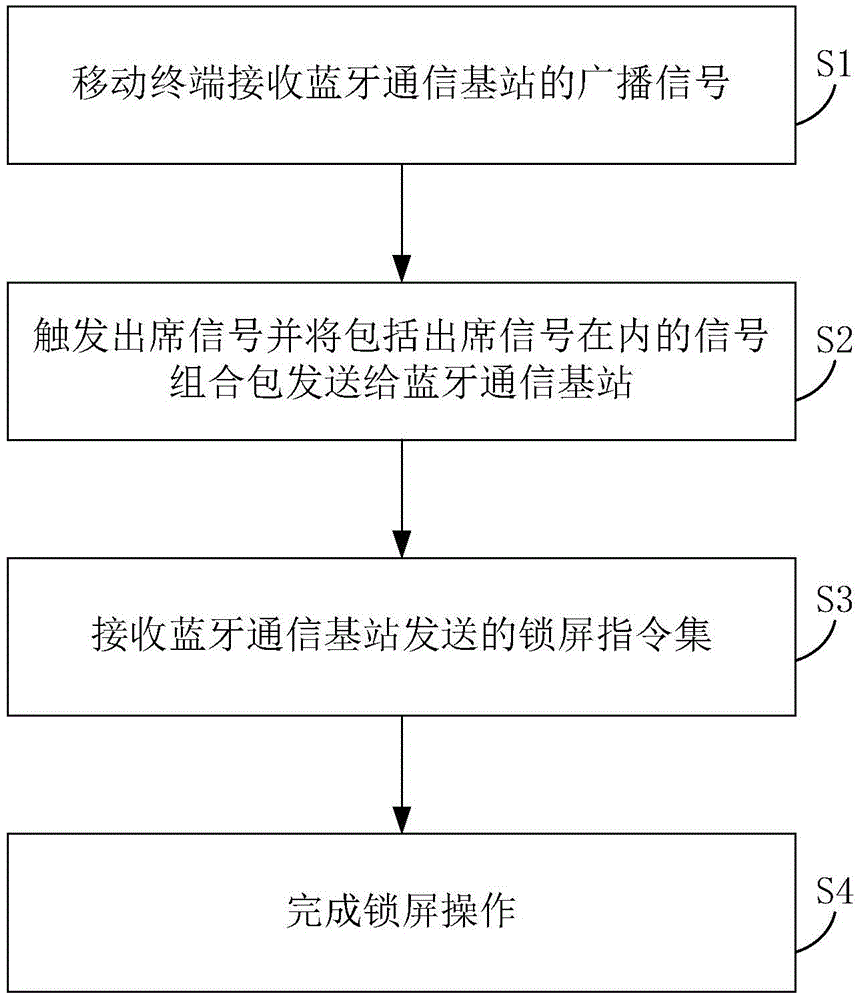
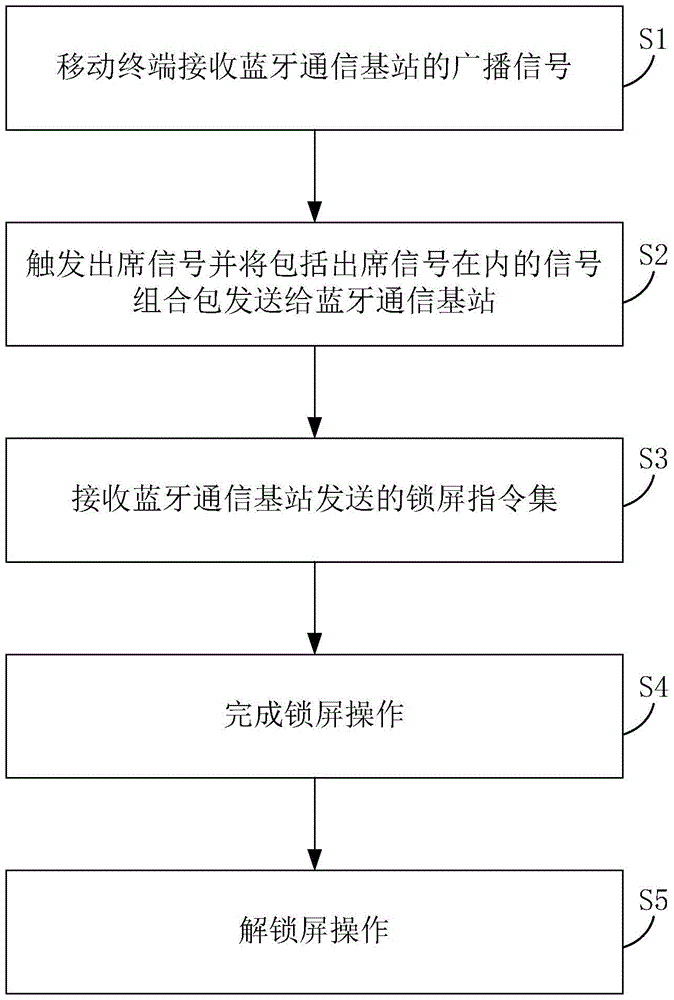
Attendance monitoring method and system based on Bluetooth communication technology
InactiveCN105744468ALow costEasy to operateUnauthorised/fraudulent call preventionResourcesMonitoring systemComputer terminal
The invention relates to the technical field of Bluetooth communication, and in particular relates to an attendance monitoring method and an attendance monitoring system based on a Bluetooth communication technology. The method comprises the steps that a mobile terminal receives a broadcast signal from a Bluetooth communication base station, triggers an attendance signal and sends a combined packet of signals including the attendance signal to the Bluetooth communication base station, receives a screen locking command set sent by the Bluetooth communication base station, and completes the screen locking operation. According to the method, besides the check on attendance can be achieved, the monitoring on the locked screens of the mobile terminals entering the attendance checking area is achieved through triggering the attendance signal and the received screen locking command set, further detection is performed after locking the screens to unlock the locked screens, and thereby the mobile terminals can return to normal use; the attendance monitoring method is simple to implement, low in device cost and operation price, convenient to operate, capable of not relying on the existing network, and easy to deploy and implement.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
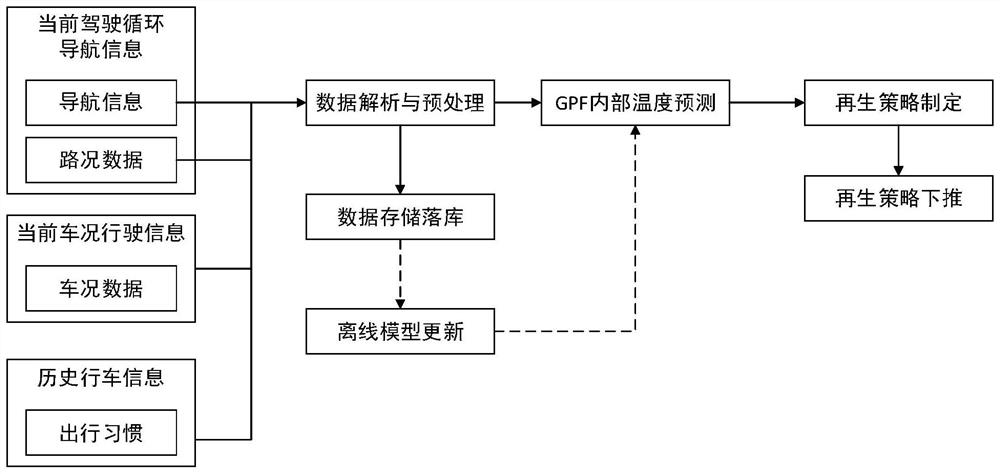
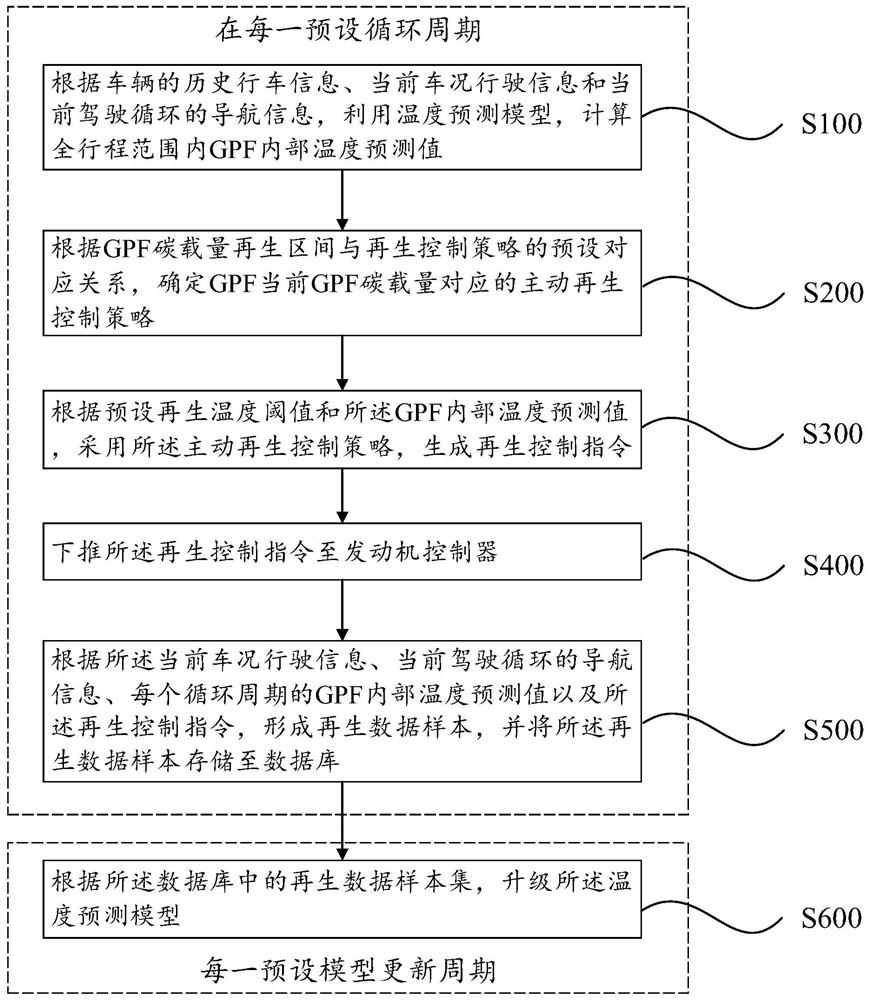
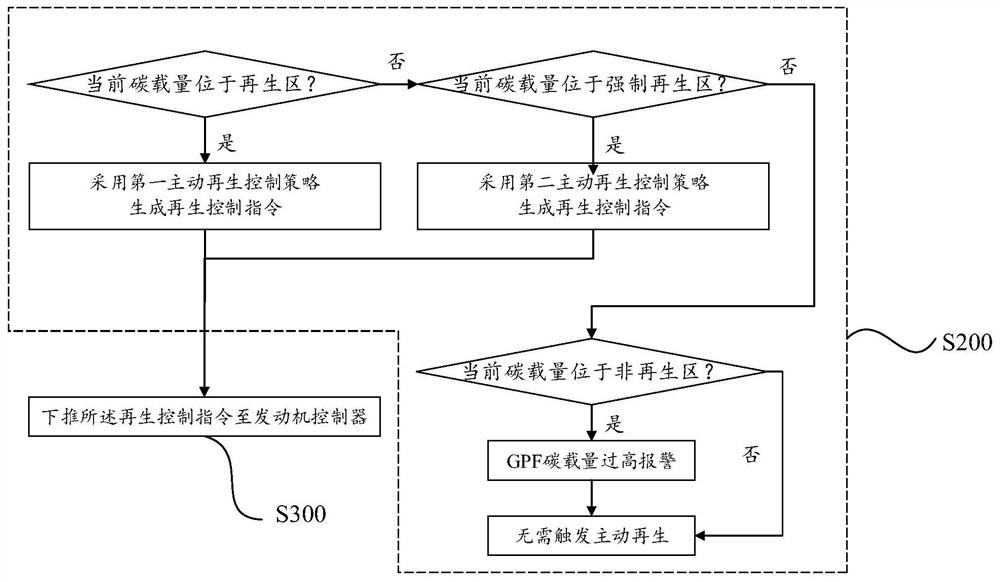
Regeneration control method and system for vehicle particulate matter trap and storage medium
ActiveCN113202607AGood flexibilityThe regeneration process is stableInternal combustion piston enginesExhaust apparatusProcess engineeringDriving cycle
The invention provides a regeneration control method and system for a vehicle particulate matter trap and a storage medium. The regeneration control method comprises the following steps of in each preset cycle period, executing the following steps of according to historical driving information of a vehicle, current vehicle condition driving information and navigation information of a current driving cycle, utilizing a temperature prediction model to calculate a GPF internal temperature prediction value in a whole travel range; determining an active regeneration control strategy, corresponding to current GPF carbon loading capacity, of the GPF according to a preset corresponding relation between a GPF carbon loading capacity regeneration interval and a regeneration control strategy; according to a preset regeneration temperature threshold value and the GPF internal temperature predicted value, adopting the active regeneration control strategy to generate a regeneration control instruction; and pushing down the regeneration control instruction to an engine controller. According to the regeneration control method and system and the storage medium, no hardware cost needs to be increased, a GPF regeneration process can be accurately controlled, the regeneration accuracy and rationality can be remarkably improved, and the regeneration efficiency is improved.
Owner:UNITED AUTOMOTIVE ELECTRONICS SYST
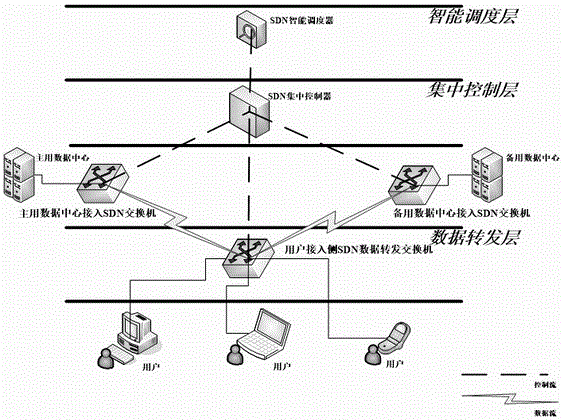
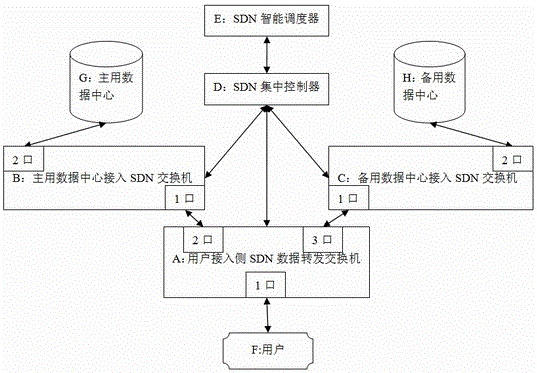
SDN-based disaster recovery system and data disaster recovery method thereof
InactiveCN106027311ARealize switchingAchieve rewindData switching networksState variationData center
The invention discloses an SDN-based disaster recovery system and a data disaster recovery method thereof. The system comprises an intelligent scheduling module, a centralized controlling module and a data forwarding module, wherein the intelligent scheduling module is arranged in an intelligent scheduling layer, and is used for monitoring link state changes when a main data center stored in an SDN centralized controller is accessed to an SDN switch and issuing an instruction to the SDN centralized controller when the main data center is abnormal or recovery is abnormal to complete a flow table operation of the SDN switch by the SDN centralized controller; the centralized controlling module is arranged in a centralized controlling layer, and is used for storing a link state of the controlled SDN switch and completing the flow table management of the controlled SDN switch according to an instruction issued by an SDN intelligent scheduler; and the data forwarding module is arranged on an SDN data forwarding switch at a user access side, and is used for forwarding data according to a flow table issued by the controller.
Owner:JIANGSU FUTURE NETWORKS INNOVATION
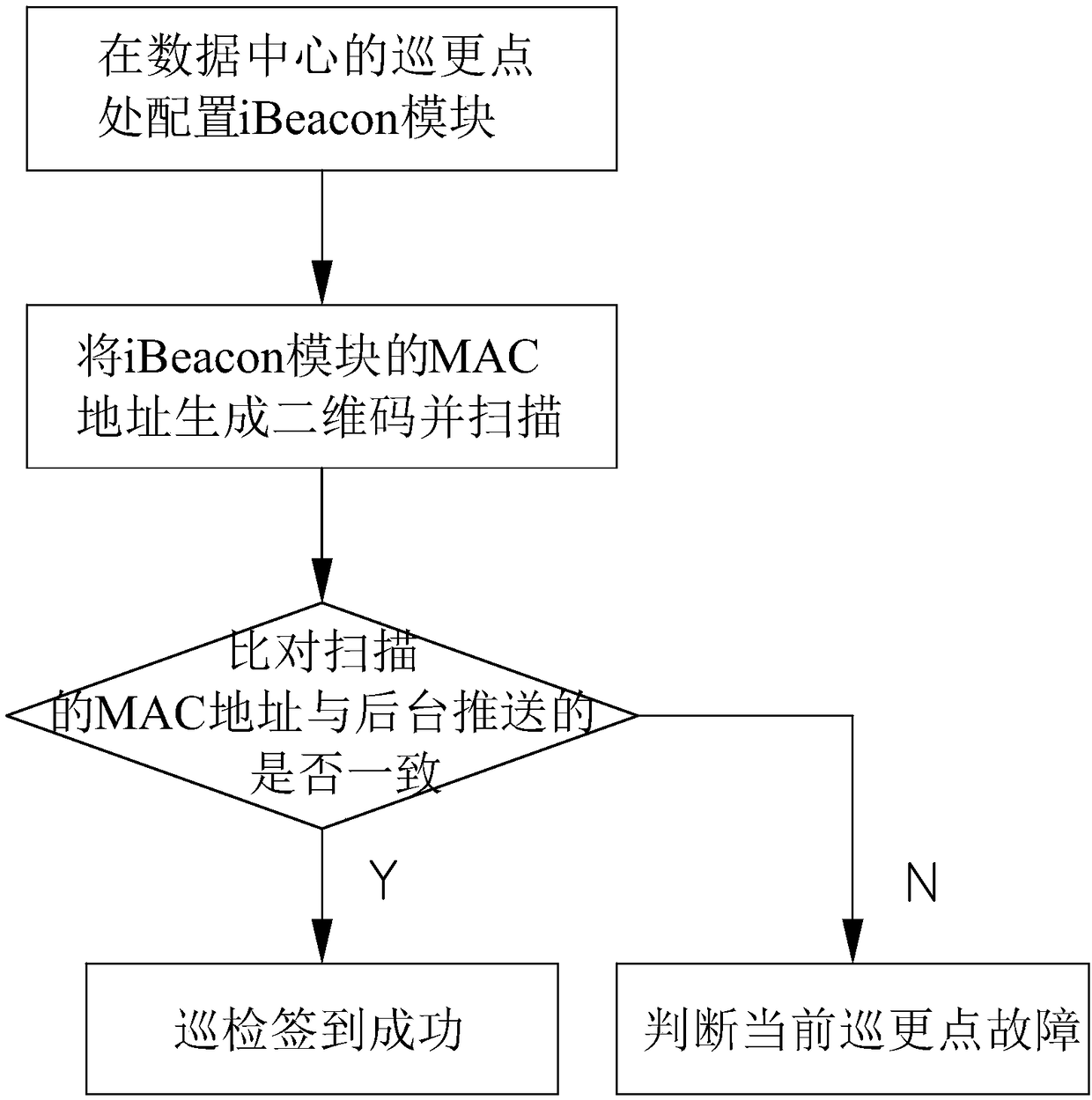
Electronic patrol method and system for comprehensive management system of data center
InactiveCN108650665AEasy to deploy and implementReduce maintenance workloadChecking time patrolsTransmissionBluetooth Low EnergyCombined method
The embodiment of the invention discloses an electronic patrol method and system for a comprehensive management system of a data center. The patrol method comprises the steps of configuring iBeacon modules at patrol points of the data center, and generating two-dimensional bar codes based on MAC addresses of the iBeacon modules, scanning the two-dimensional bar codes, comparing whether the obtained MAC addresses are consistent with the MAC addresses pushed by a background or not; judging that the patrol checkin is successful if the obtained MAC addresses are consistent with the MAC addresses pushed by the background; and judging that faults occur in the current patrol points if the obtained MAC addresses are inconsistent with the MAC addresses pushed by the background. According to the electronic patrol method provided by the embodiment of the invention, a Bluetooth low energy technology and the two-dimensional bar codes are combined, so the problem that the patrol points are difficultto position precisely is solved. According to the method, through adoption of a technology and management combined method, the management work of the data center is relatively normal and scientific,and the operation risk of a power environment and information system of the data center is effectively reduced.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
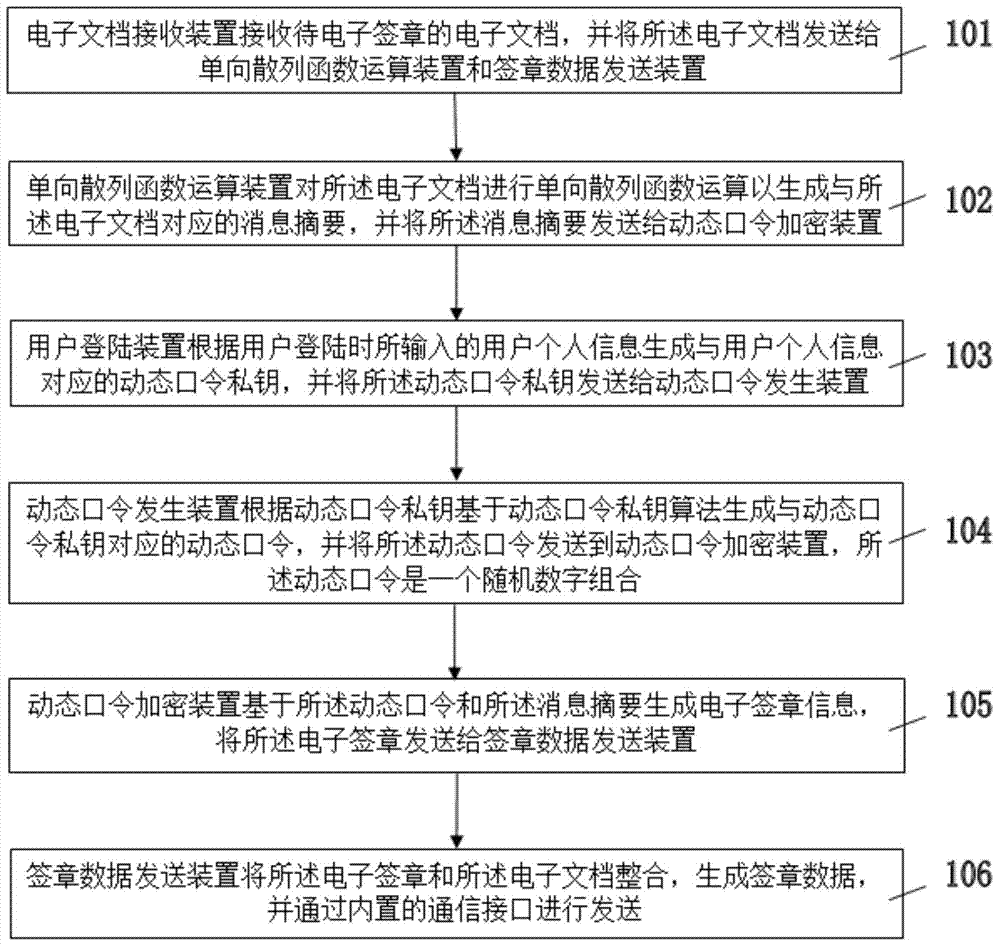
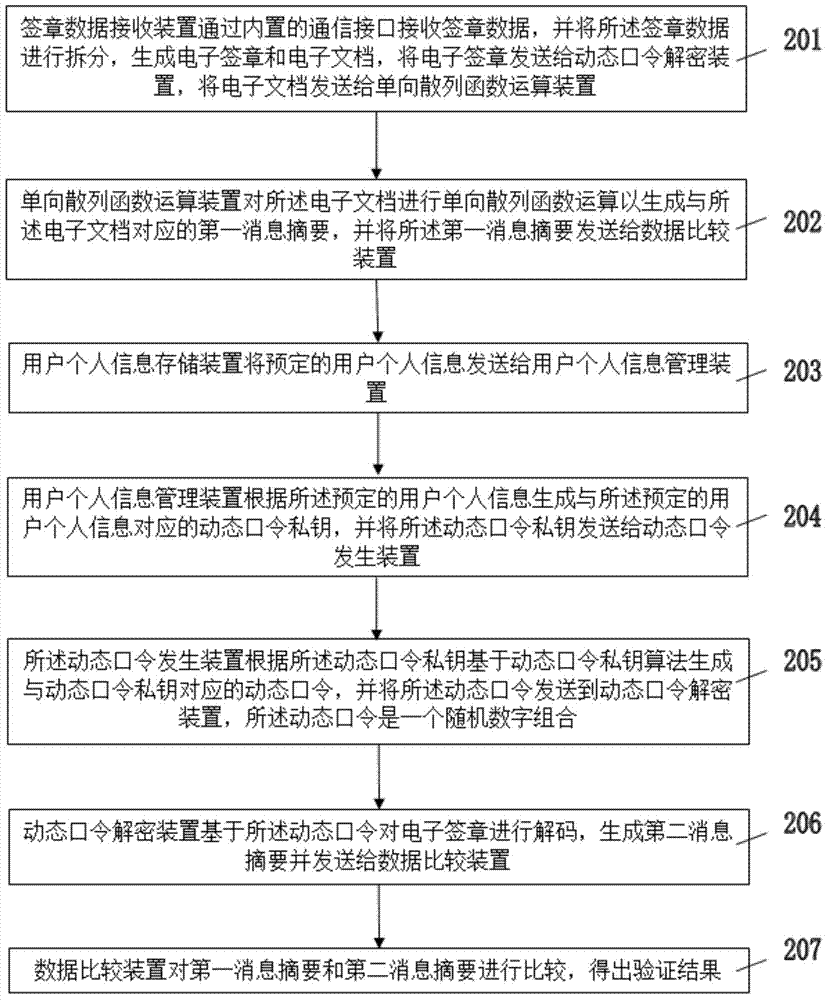
Electronically signing method and electronic signature verification method based on dynamic passwords
ActiveCN103581195AEasy to useEasy to deploy and implementUser identity/authority verificationElectronic documentDigital document
The invention discloses an electronically signing method and an electronic signature verification method based on dynamic passwords. According to the electronically signing method, electronic documents to be signed electronically are signed electronically on the basis of dynamic password private keys generated by personal information of a user, and according to the electronic signature verification method, electronic signature verification is performed on received signature data on the basis of the reserved personal information of the user. The electronically signing method and the electronic signature verification method based on the dynamic passwords are easy to manage, convenient to operate, low in manufacturing cost and convenient for the user to use.
Owner:SHANGHAI PEOPLENET SECURITY TECH
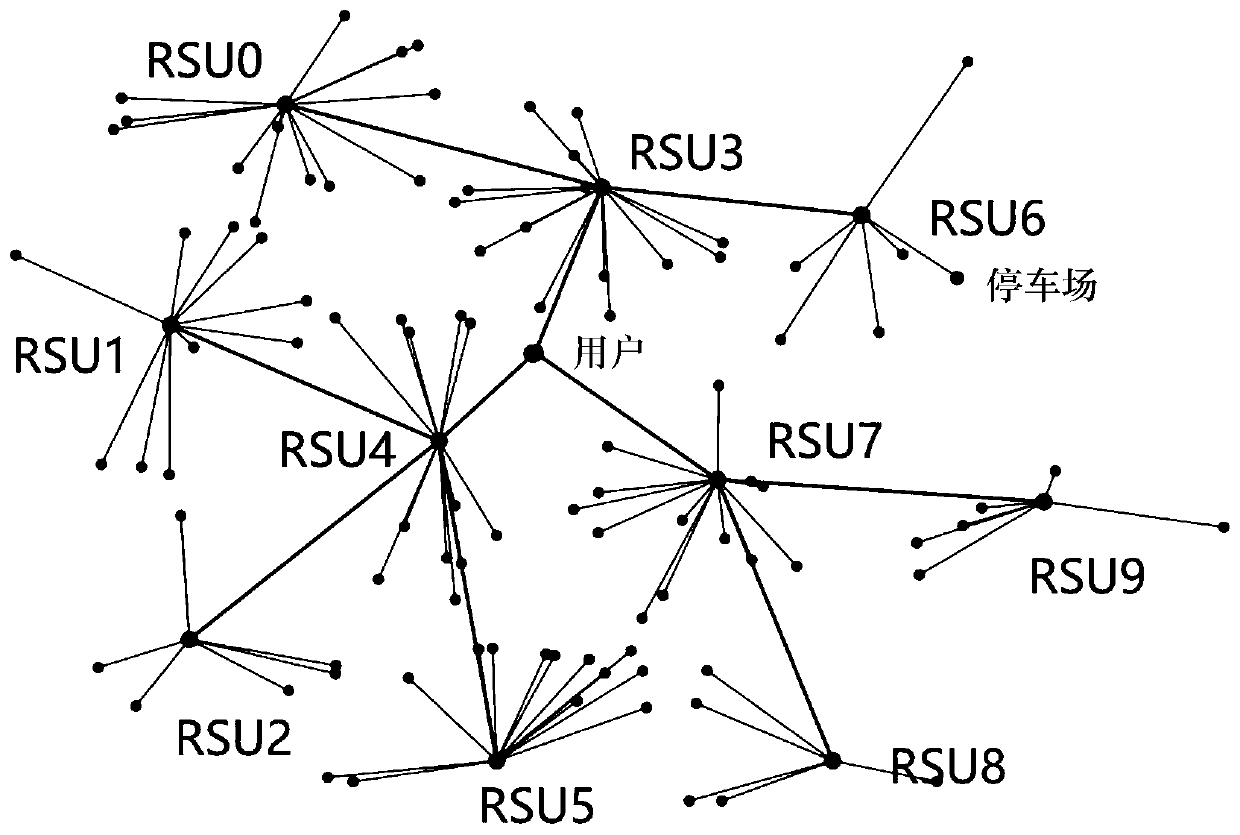
Fuzzy Skyline real-time parking recommendation method with privacy protection function
ActiveCN111063212AReduce overheadImprove real-time performanceTicket-issuing apparatusIndication of parksing free spacesPrivacy protectionParking space
The invention discloses a fuzzy Skyline real-time parking recommendation method with a privacy protection function. The method comprises the following steps: 1, a roadside traffic facility RSU collects fuzzy parking lot and traffic information of the surrounding in real time; 2, a user sends a parking query request to the RSU, the query request comprises three default requirements, namely, the parking stall obtaining possibility, the parking lot reaching time and the charging standard, and a recommendation result return path based on the user is established according to a query message and theRSU; and 3, a fuzzy language variable comparison operation operator based on s-norm operation in the fuzzy method is defined, the RSU performs skyline information fusion by utilizing the fuzzy language variable comparison operator, and a result is returned to the user. The method is good in privacy protection effect, high in real-time performance and easy to implement and apply.
Owner:ZHEJIANG UNIV OF TECH
Information display system of big data
InactiveCN108399208AGive full play to computing powerProcessing speedExecution for user interfacesSpecial data processing applicationsInformation display systemsData profiling
The embodiment of the invention provides an information display system of big data. The system includes: an information storage module, which is used for storing and receiving the already-collected big data; a big-data preprocessing module, which is used for preprocessing the already-collected big data, wherein preprocessing includes normalization, filtering and clustering; an intelligent analysismodule, which is used for carrying out analysis of the big data according to a received instruction, and comprehensively utilizing the data, which are provided by the big-data preprocessing module, for event causality analysis; and an information display module, which is used for generating a data analysis task, passing the same to the intelligent service analysis module, and receiving a result returned by the intelligent analysis module. The analysis and evaluation result of enterprise information and various types of detailed data are hierarchically and comprehensively presented in real time through visualization technology which is capable of interaction. By applying the embodiment of the invention, the problem that real-time performance, high effectiveness and interactivity of traditional data processing methods are poorer is solved.
Owner:广东聚晨知识产权代理有限公司
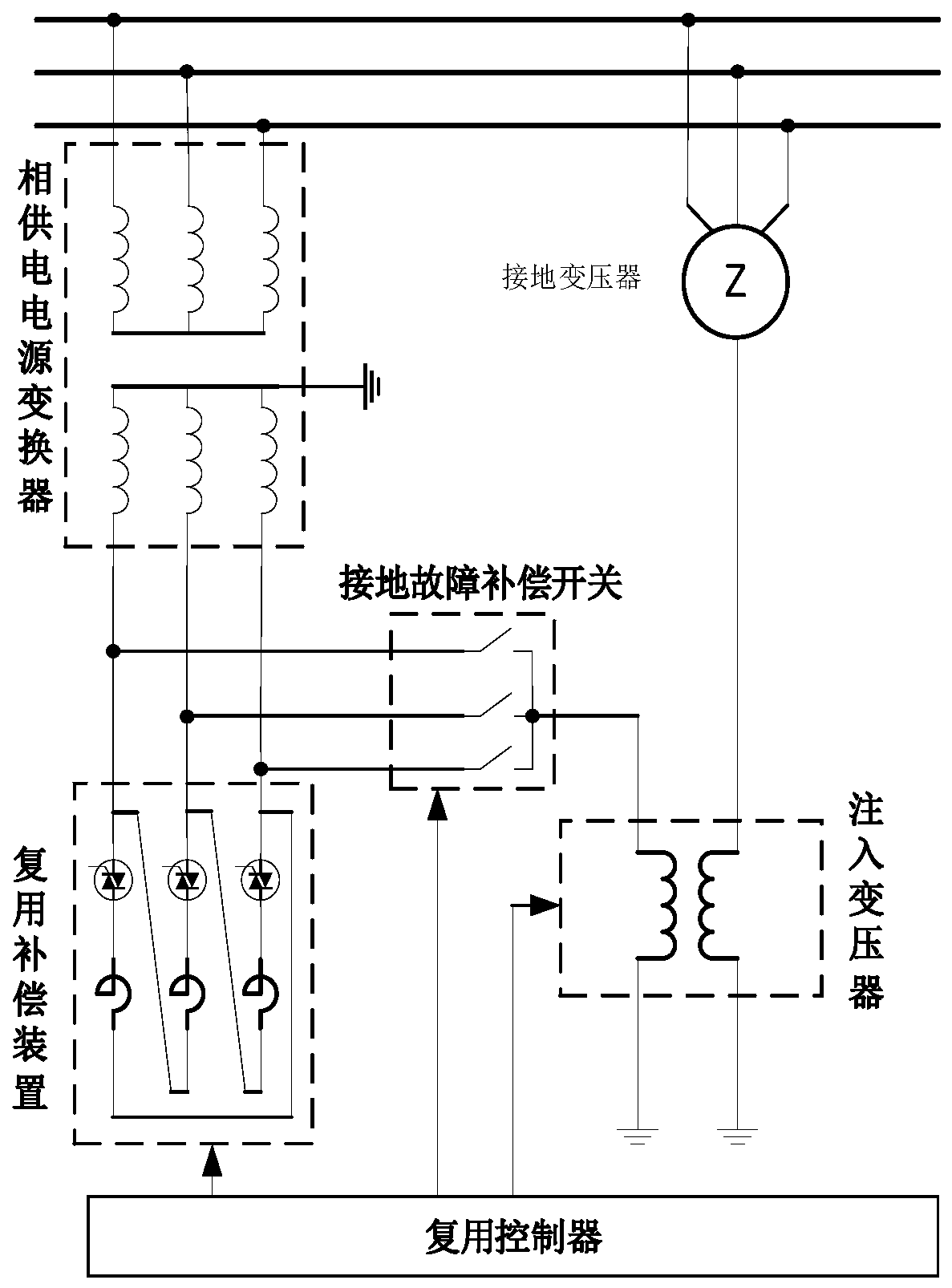
Ground fault full-compensation system and method for multiplexing parallel reactive power compensation
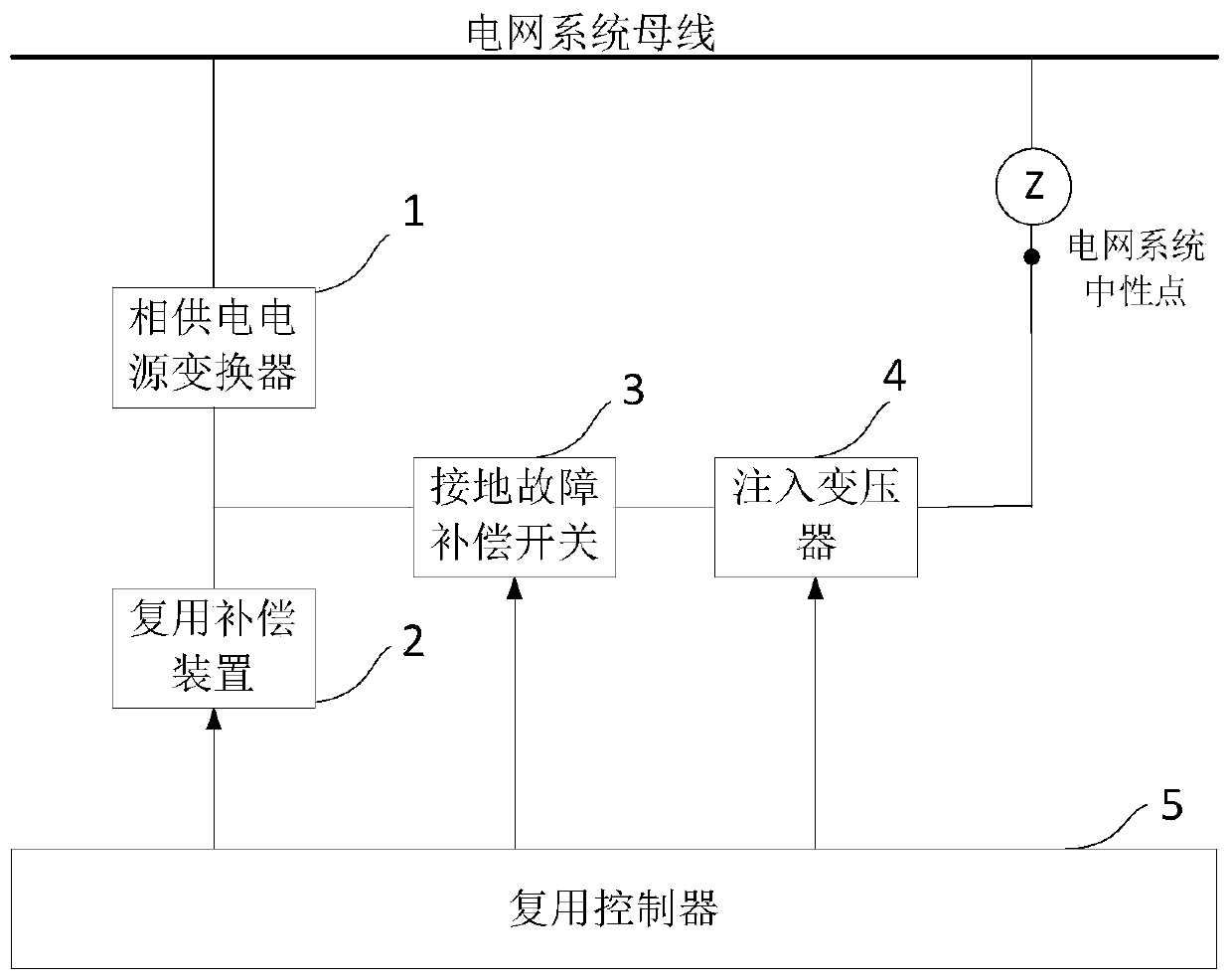
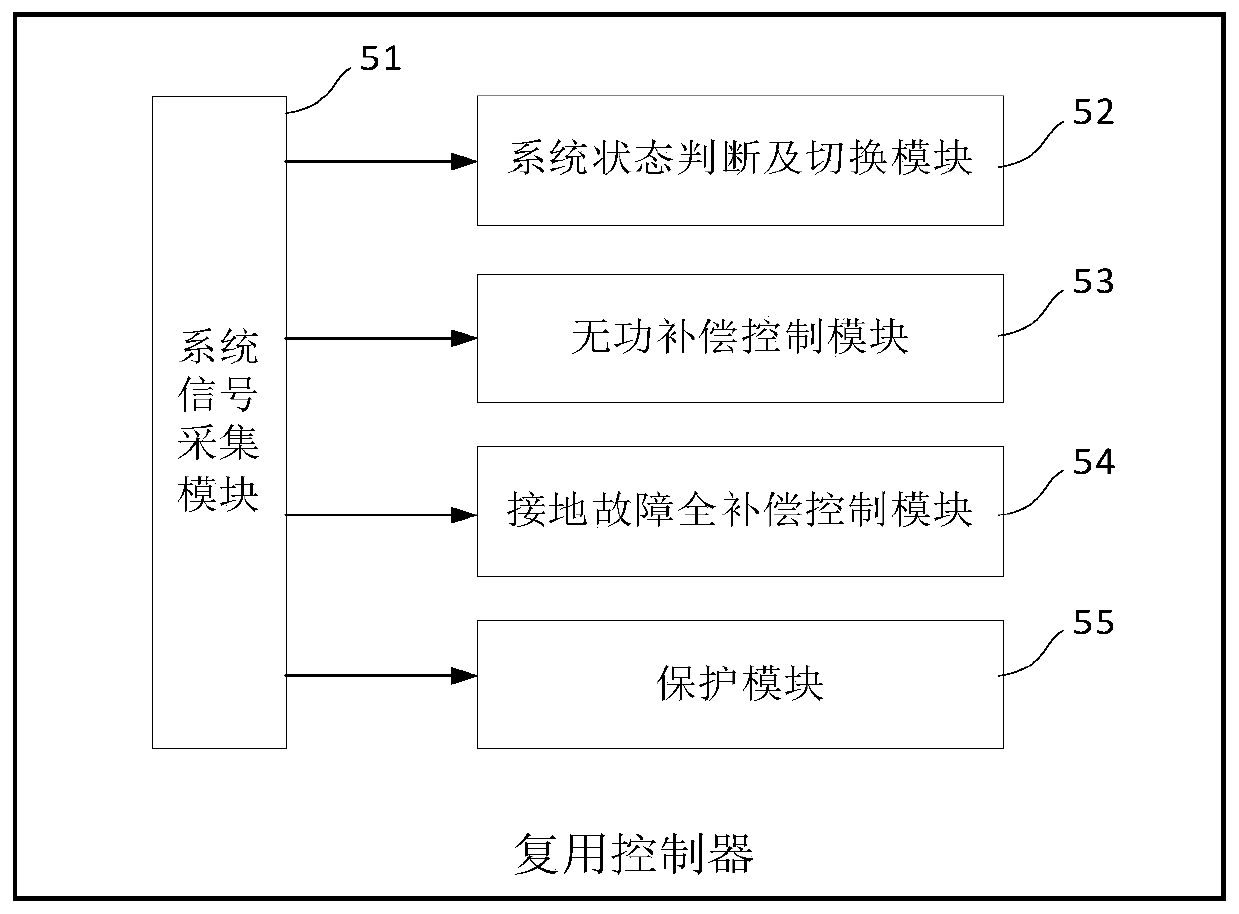
PendingCN111509692AIncrease profitRealize full life cycle applicationReactive power adjustment/elimination/compensationEmergency protective arrangements for limiting excess voltage/currentMultiplexingPower compensation
The invention provides a ground fault full-compensation system and method for multiplexing parallel reactive power compensation. The system is composed of a phase power supply converter, a multiplexing compensation device, a grounding fault compensation switch, an injection transformer and a multiplexing controller. The multiplexing controller judges whether the system is in a normal operation state or a single-phase ground fault state according to acquired signals; when the power system is in the normal operation state, the ground fault compensation switch is switched off, and the multiplexing compensation device performs reactive power compensation on the power system; and when a single-phase ground fault occurs in the power system, a grounding phase is determined, a corresponding groundphase switch of the ground phase is closed, and the transformation ratio of the injection transformer is adjusted to carry out single-phase ground fault full compensation. The system carries out reactive power compensation when the power system normally operates, carries out grounding fault current full compensation when the single-phase grounding fault occurs in the system, works in a full lifecycle, and improves the utilization rate of a single-phase grounding compensation device.
Owner:YUNNAN POWER GRID CO LTD ELECTRIC POWER RES INST
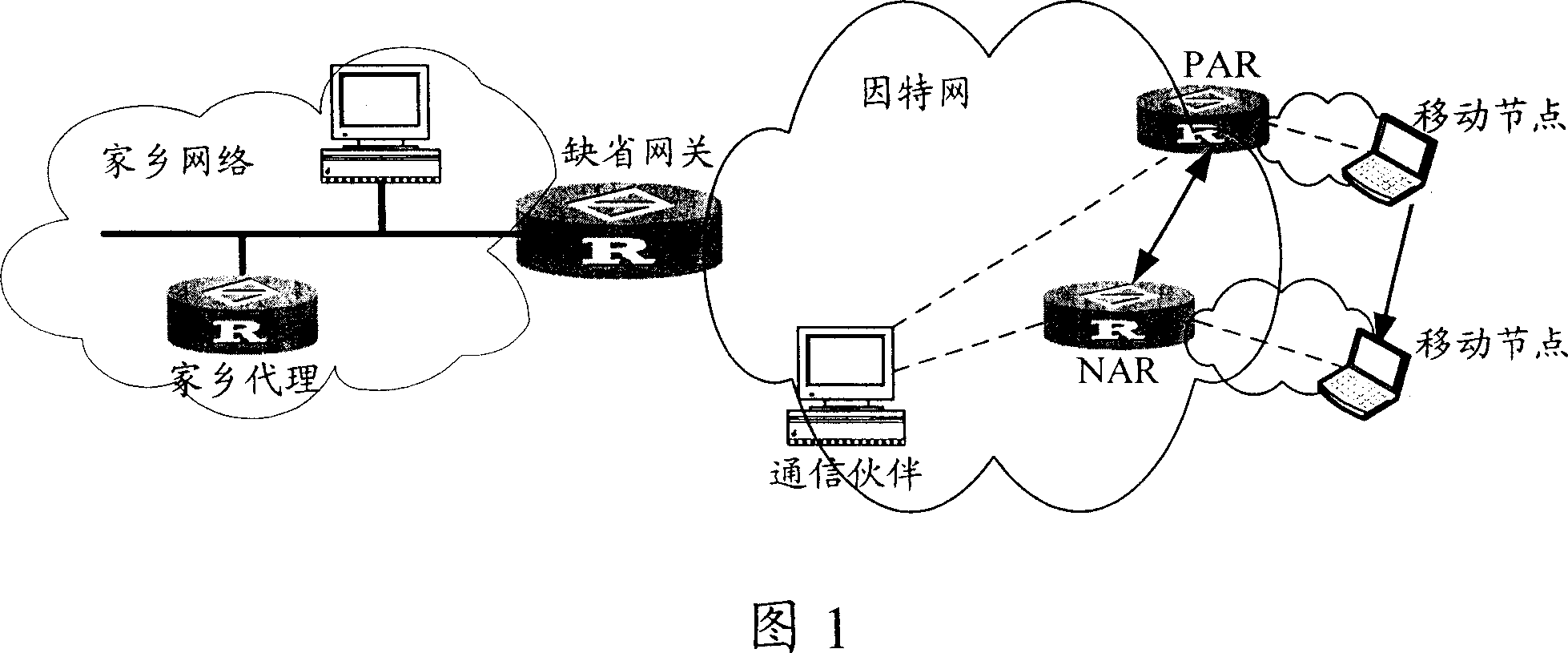
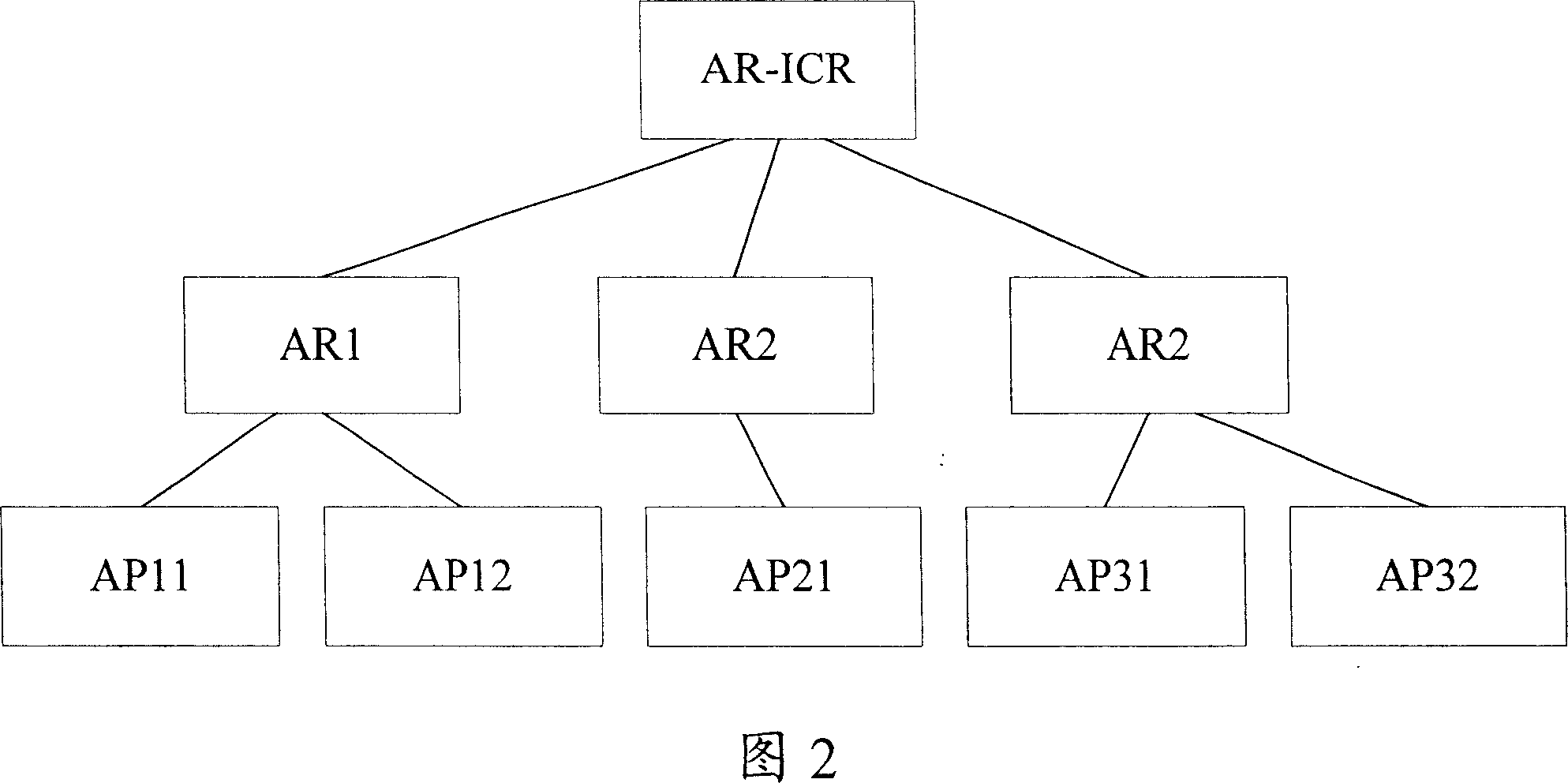
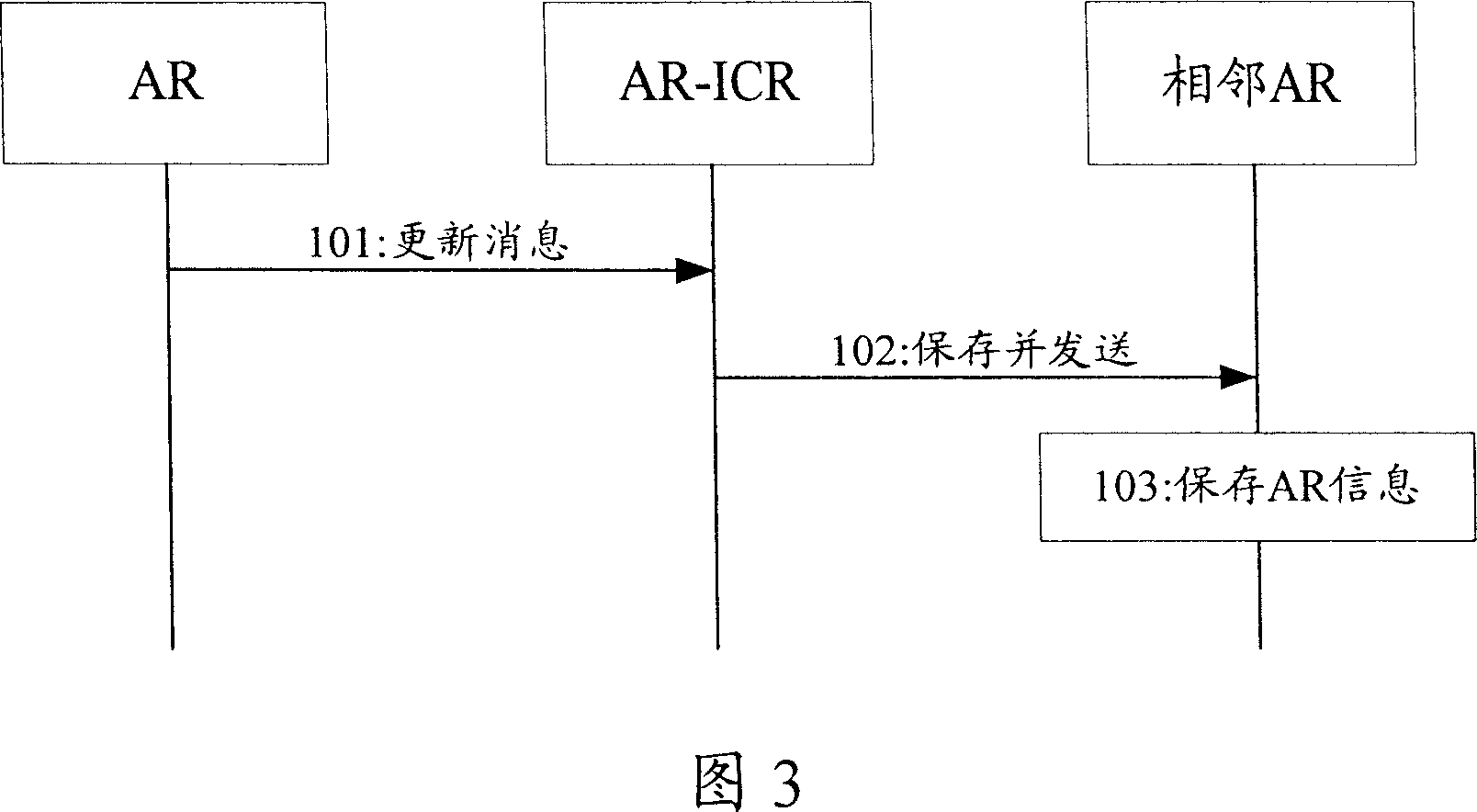
Method for collecting information of access route and its system
InactiveCN101047674AAvoid poor scalabilityPrevent malicious attacksStore-and-forward switching systemsNetwork connectionsAccess routeAccess network
This invention discloses a method for collecting AR information by setting AR-ICR in an access network including the following steps: A, AR transmits one or more than one update messages of AR information to AR-ICR, B, AR-ICR sends said AR information to adjacent AR at a same position. This invention also discloses a system for collecting AR information including AR-ICR and at least two AR, which can collect AR information automatically without triggering mobile nodes or artificial configuration.
Owner:HUAWEI TECH CO LTD
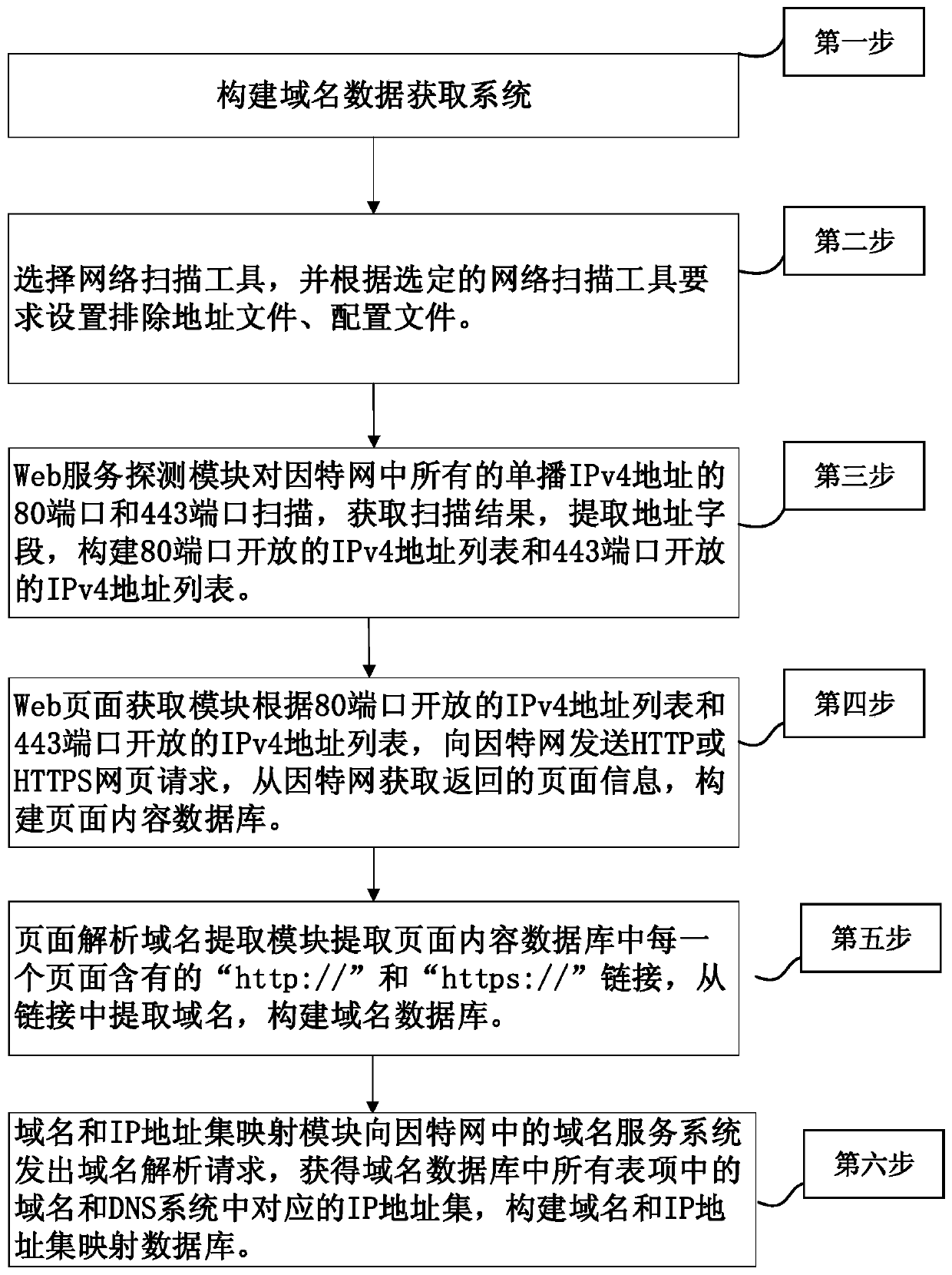
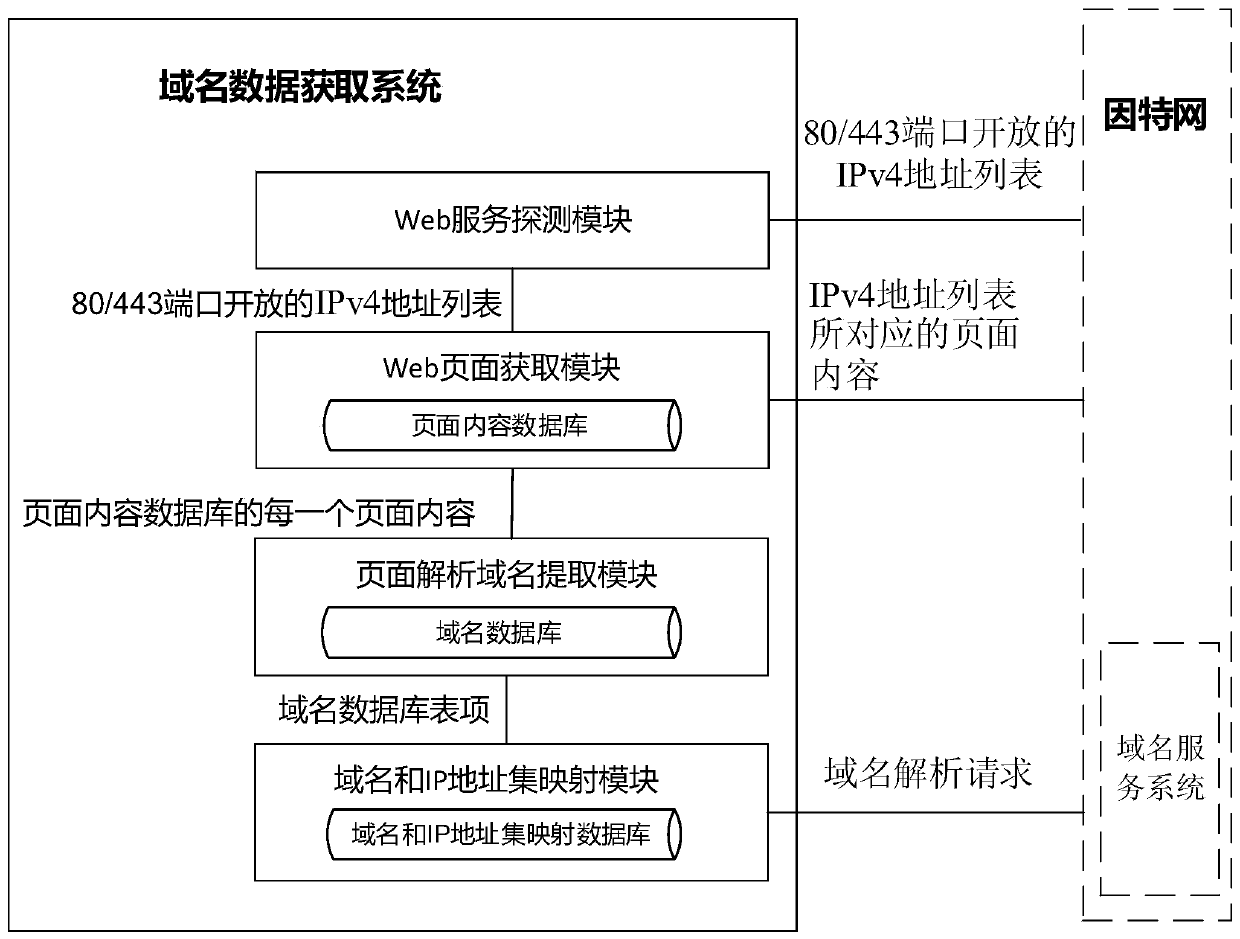
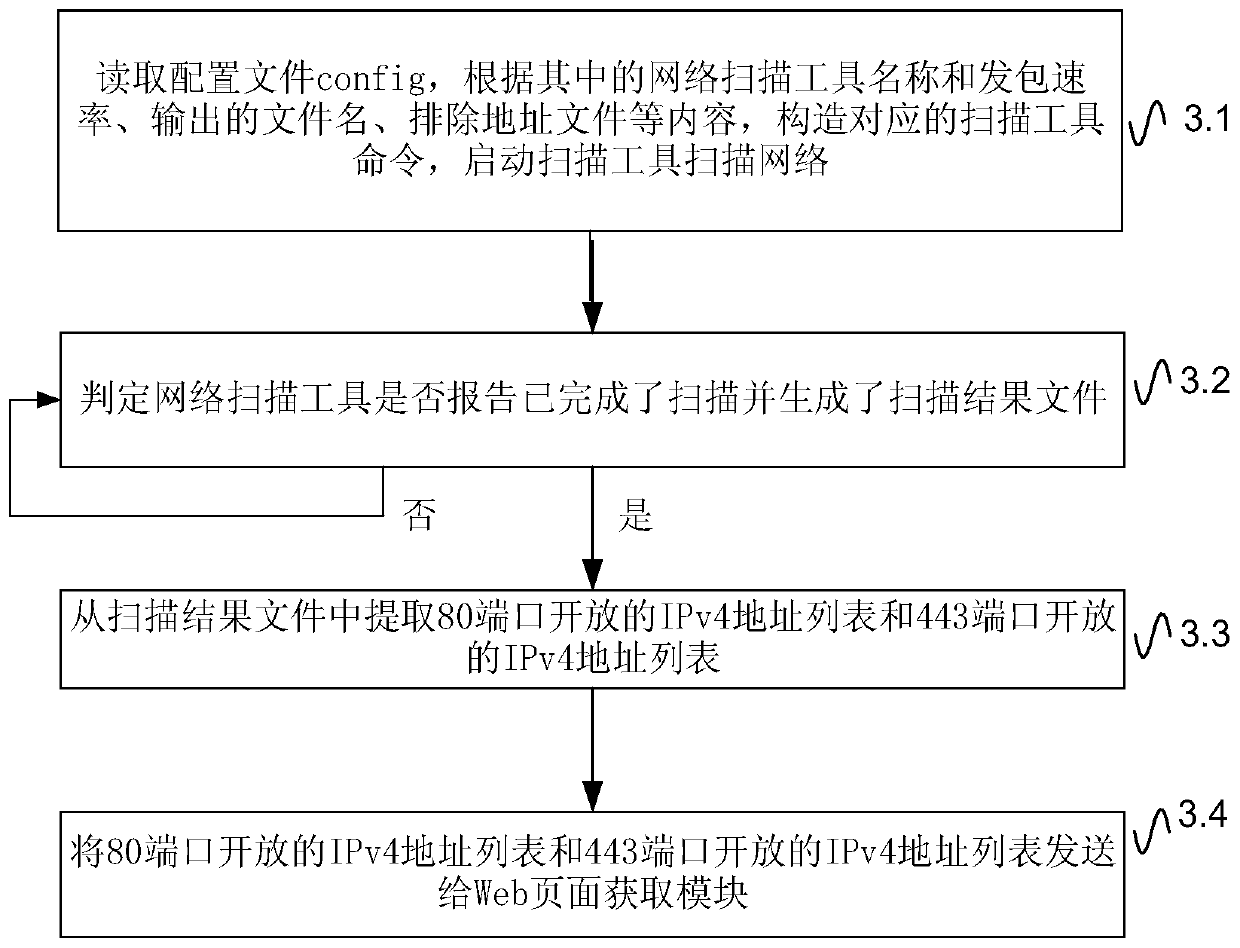
Domain name data acquisition method based on Web
The invention discloses a domain name data acquisition method based on Web. According to the scheme, a domain name data acquisition system composed of a Web service detection module, a Web page acquisition module, a page resolution domain name extraction module and a domain name and IP address set mapping module is constructed; the Web service detection module scans the IPv4 unicast address spacethrough 80 and 443 ports by adopting a network scanning tool, and establishes an IPv4 address list with open 80 and 443 ports; the Web page acquisition module sends a webpage request according to theport number and the IPv4 address list, acquires page information and establishes a page content database; the page resolution domain name extraction module extracts each link of each page in the pagecontent database, extracts a domain name and establishes a domain name database; the domain name and IP address set mapping module sends a domain name resolution request to a domain name service system to obtain each domain name and a corresponding IP address set in a domain name database. According to the invention, efficient acquisition of global website domain names can be realized, the flow overhead is reduced, and the domain name data acquisition breadth and efficiency are improved.
Owner:NAT UNIV OF DEFENSE TECH
Big data intellectualized processing system
InactiveCN108304549AGive full play to computing powerProcessing speedDatabase management systemsSpecial data processing applicationsData platformComputer module
The invention provides a big data intellectualized processing system. The big data intellectualized processing system comprises a big data platform, a big data preprocessing module and an intelligentanalysis module, wherein the big data platform is used for storing already-collected big data, the big data preprocessing module is used for preprocessing the already-collected big data, preprocessingis used for achieving load balance, resource virtualization and distributed data storage management, the intelligent analysis module is used for analyzing big data according to a received instruction, comprehensively utilizing the data provided by the big data preprocessing module to analyze the cause and effect of events, obtaining an application service request of a user, determining a processing algorithm corresponding to the application service request, using the processing algorithm corresponding to the application service request and a representing learning module to obtain high-dimension vectors of the analysis of the cause and effect of the events, and adopting a neural network to process the high-dimension vectors. By means of the big data intellectualized processing system, theproblems that a traditional data processing method is poor in real-time performance, efficiency and interactivity are solved.
Owner:广东聚晨知识产权代理有限公司
Laser dust particle counting and monitoring system based on Zigbee
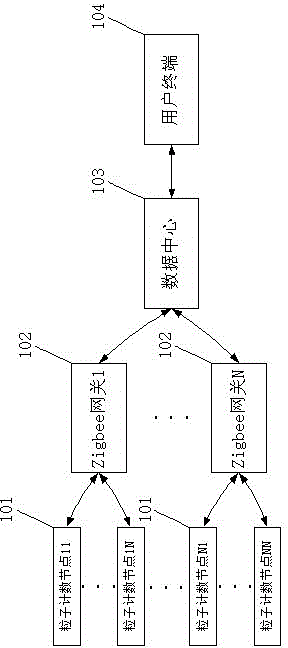
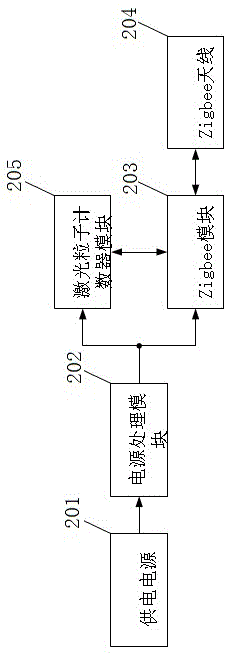
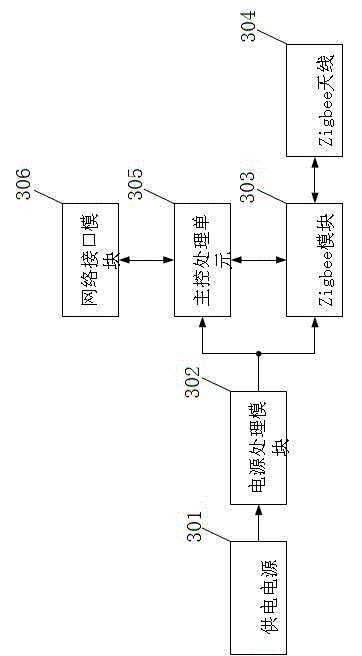
InactiveCN104157124ALarge storage capacityImprove efficiencyTransmission systemsIndividual particle analysisNon real timeData center
The invention discloses a laser dust particle counting and monitoring system based on Zigbee. The system includes a particle counting node, a Zigbee gateway, a data center and a user terminal. The particle counting node is wirelessly connected to the Zigbee gateway through a Zigbee technology. The Zigbee gateway is connected to the data center through Ethernet. The data center is connected to the user terminal in a manner of one of Ethernet, WiFi, GSM, 3G and 4G. The laser dust particle counting and monitoring system is advantaged in that compared with conventional artificial on-site non-real-time detection, the system can significantly increase efficiency and reduce labor cost. The wireless connection is employed in the node so that deployment is easy to carry out. The data center is large in storage capacity and can allow data to be saved for several weeks, several months even a longer time. Data can be browsed on an intelligent terminal so that the system is very convenient to use.
Owner:无锡硅奥科技有限公司
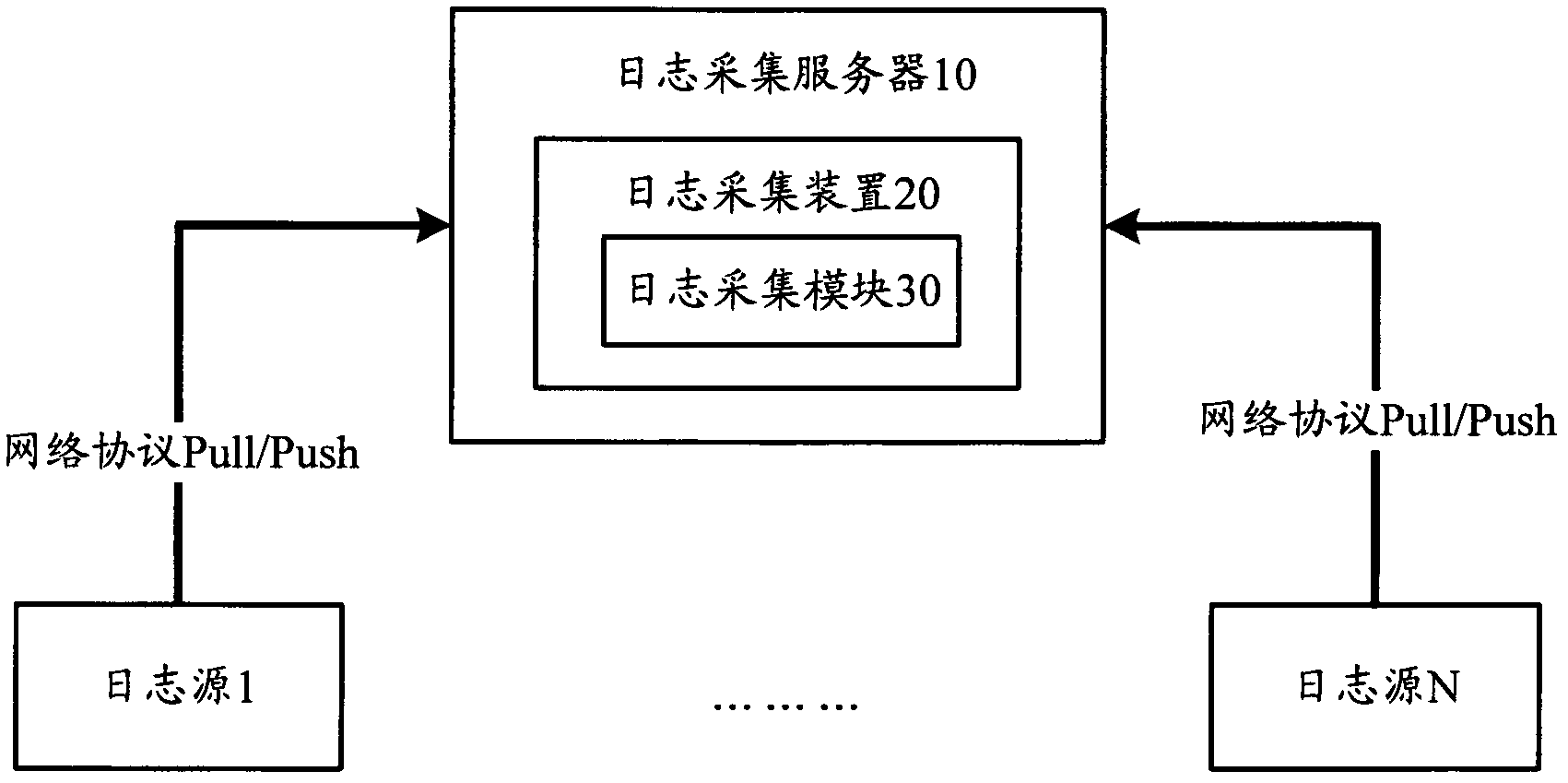
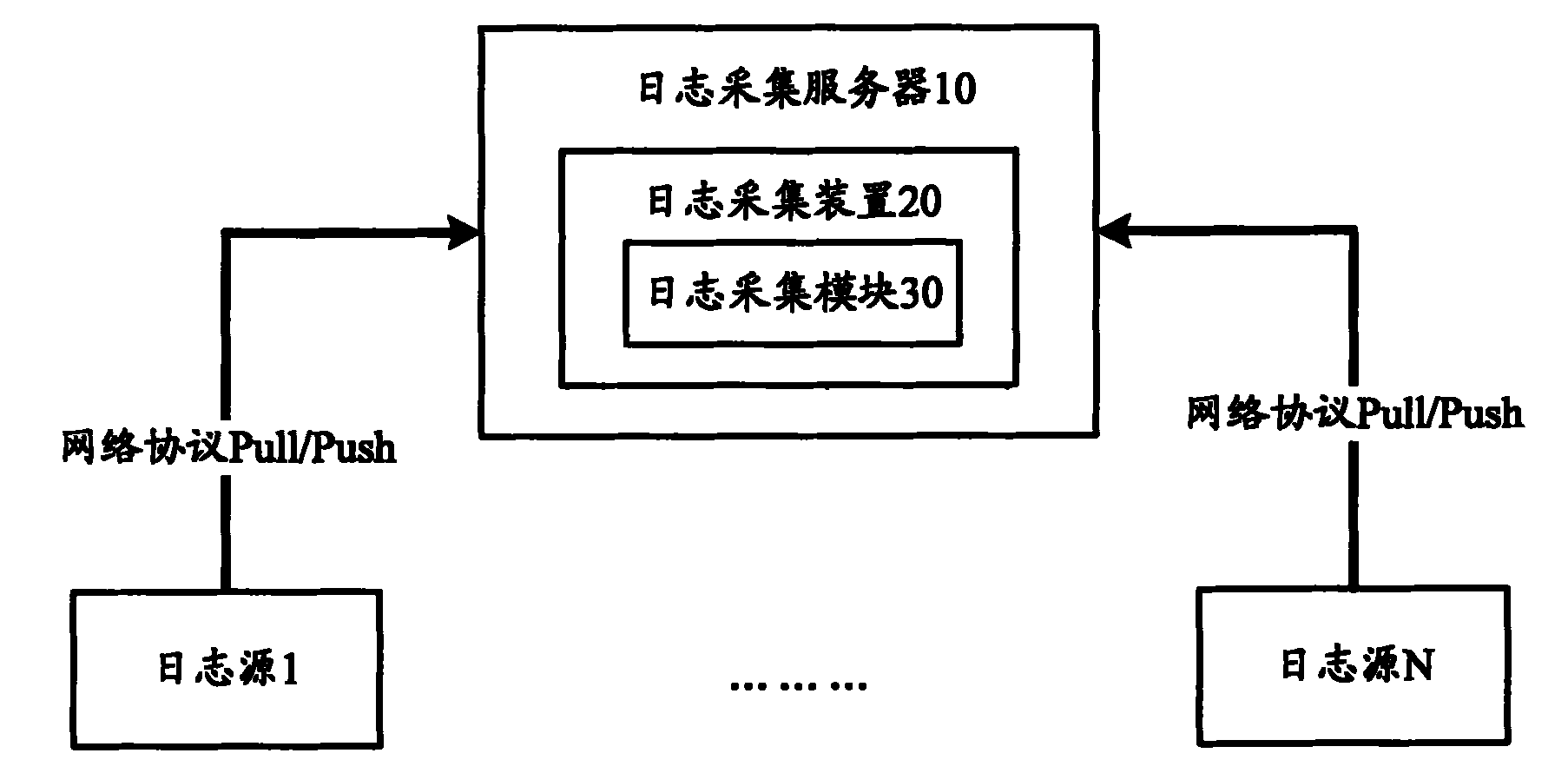
Log acquisition method and apparatus thereof
InactiveCN102368709AImprove collection effectImprove securityData switching networksAcquisition apparatusComputer module
The invention provides a log acquisition method which comprises the following steps: without installing a plug-in at a log source, a log acquisition server remotely acquires a log of the log source through a network protocol. The invention also provides a log acquisition apparatus which comprises a log acquisition module used for remotely acquiring the log of the log source through the network protocol without installing any plug-in at the log source. According to the log acquisition method and the apparatus thereof in the invention, log acquisition without the plug-in is realized, influence on the log source is reduced, simultaneously engineering personnel disposition enforcement is facilitated, and abundant enforcement cost and communication cost are reduced.
Owner:ZICT TECH CO LTD
Wireless downlink communication method with low power consumption and high real-time performance
ActiveCN111132303AImprove real-time performanceImprove reliabilitySynchronisation arrangementHigh level techniquesEngineeringTimestamping
The invention discloses a wireless downlink communication method with low power consumption and high real-time performance, which comprises terminals and at least two base stations for broadcasting guide broadcast to each terminal and executing wireless communication with the terminals, wherein the terminal searches for the guide broadcast in a range, and determines the base station communicatingwith the terminal according to the guide broadcast; and the sending time point of the next time synchronization broadcast is obtained from the guide broadcast; at the arrival of the sending time point, a receiving window is opened, the time synchronization broadcast is searched, if a response is received, a base station timestamp in the time synchronization broadcast is extracted and set to be a timestamp of the terminal, the synchronization with the base station is achieved, a downlink data communication window is negotiated, and downlink communication with high real-time performance can be achieved. The method is high in reliability, and the stability is higher than that of a whole-network synchronization scheme.
Owner:SUZHOU XUNXI ELECTRONICS SCI & TECH CO LTD
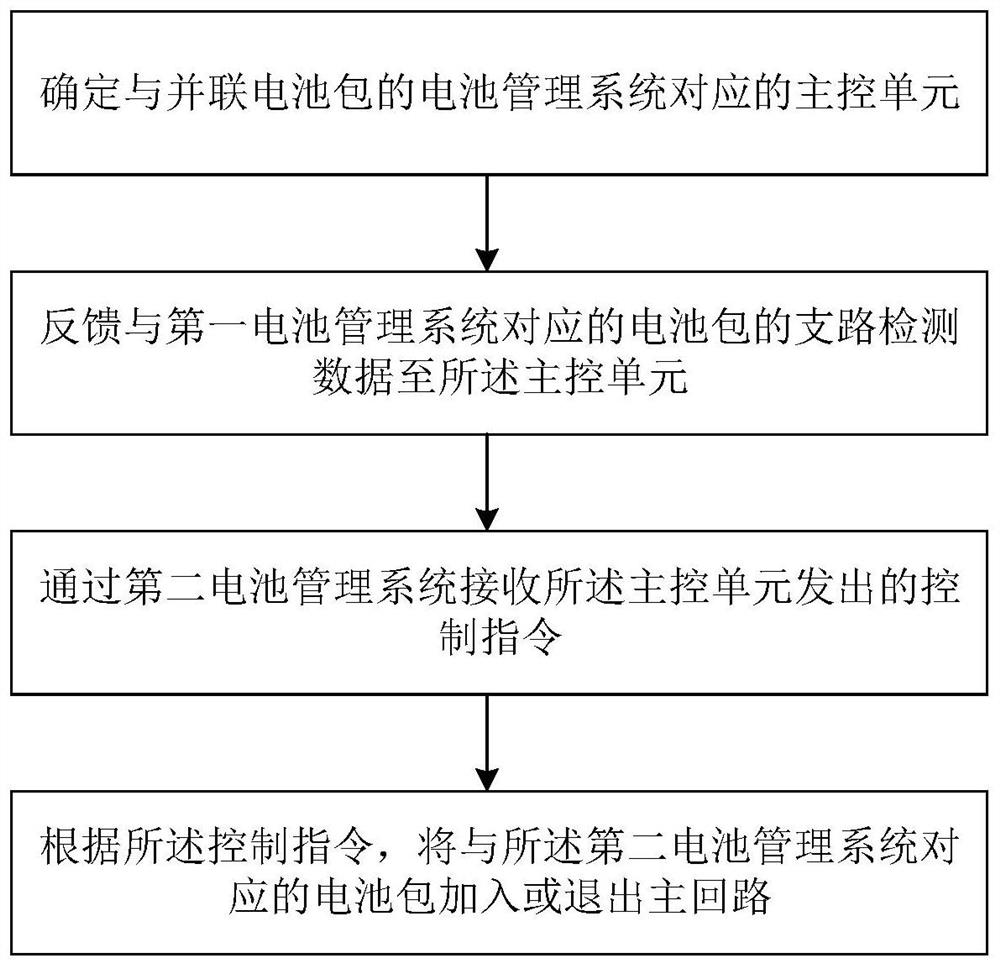
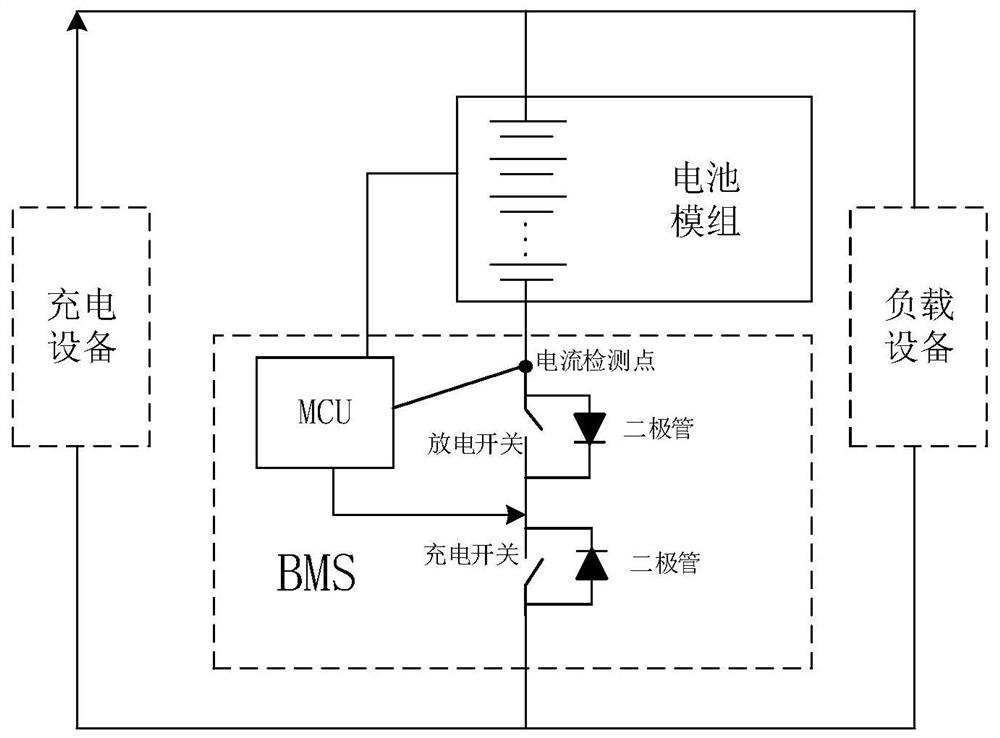
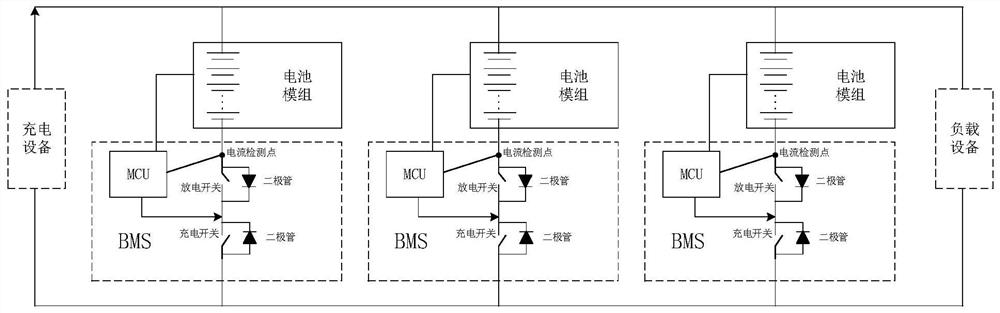
Parallel battery pack control method and system, electronic equipment and vehicle
ActiveCN112600264AEasy to deploy and implementBalanced chargingCharge equalisation circuitElectric powerAutomotive engineeringElectrical battery
The invention provides a parallel battery pack control method and system, electronic equipment and a vehicle, and belongs to the technical field of batteries. The method comprises the following steps:determining a main control unit corresponding to a battery management system of a parallel battery pack; feeding back the branch detection data of the battery pack corresponding to a first battery management system to the main control unit; receiving a control instruction sent by the main control unit through a second battery management system, wherein the control instruction is determined by themain control unit through the branch detection data, and both the first battery management system and the second battery management system are determined as slave units; and according to the controlinstruction, making a battery pack corresponding to the second battery management system be added into or withdrawn from a main loop, wherein the main loop comprises the parallel battery pack and loadequipment, or the main loop comprises the parallel battery pack and charging equipment. The method can be used for parallel connection of the lithium battery packs.
Owner:SVOLT ENERGY TECHNOLOGY CO LTD
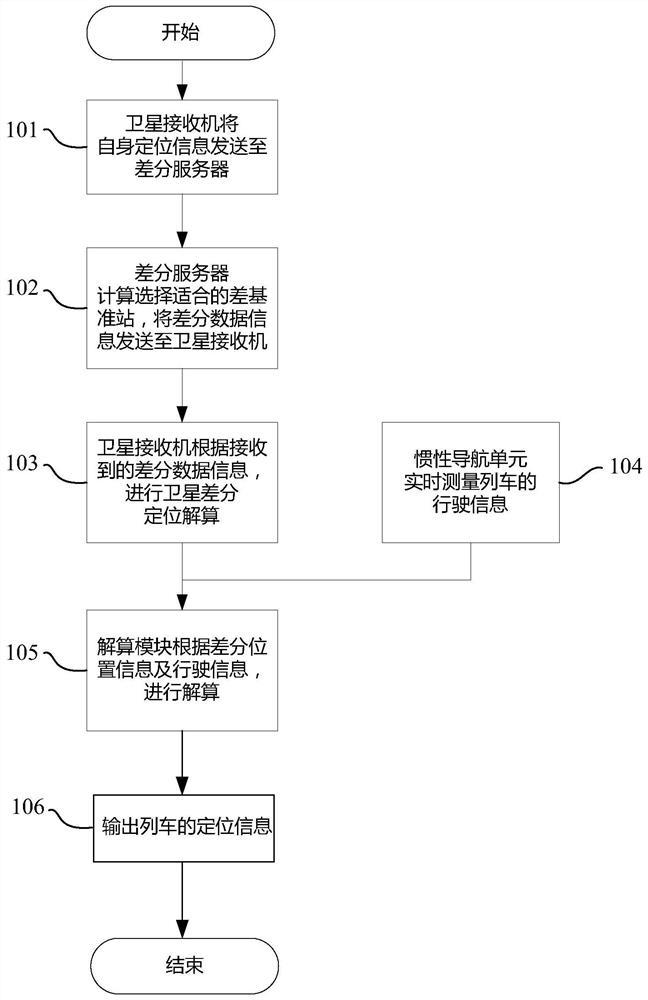
Train positioning method and device
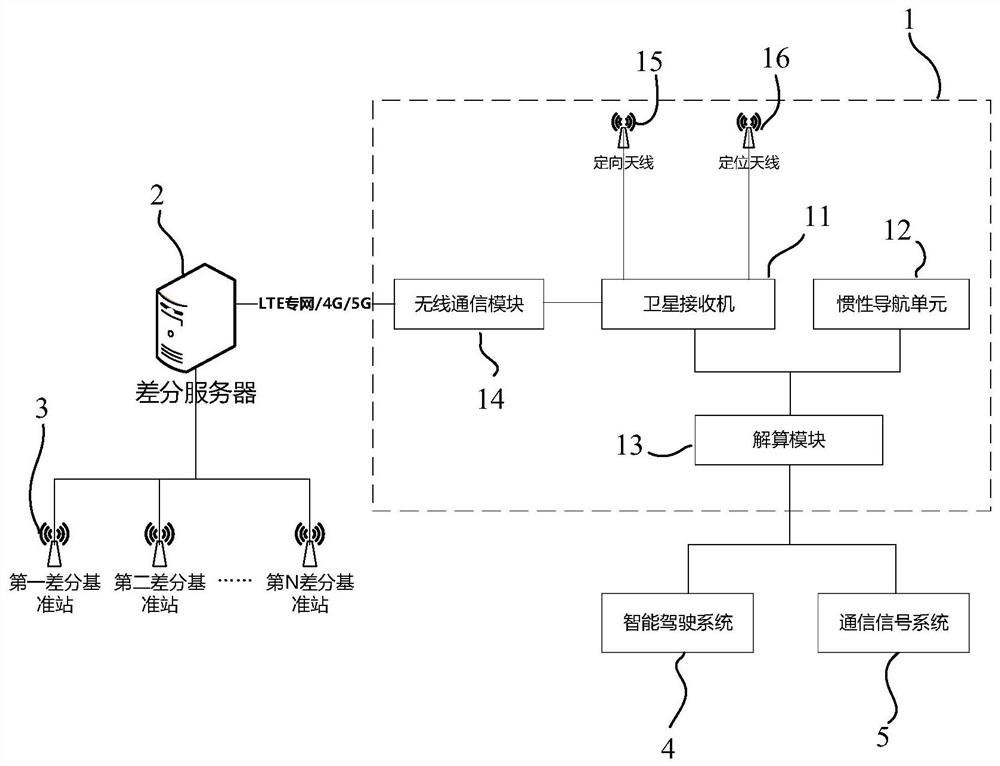
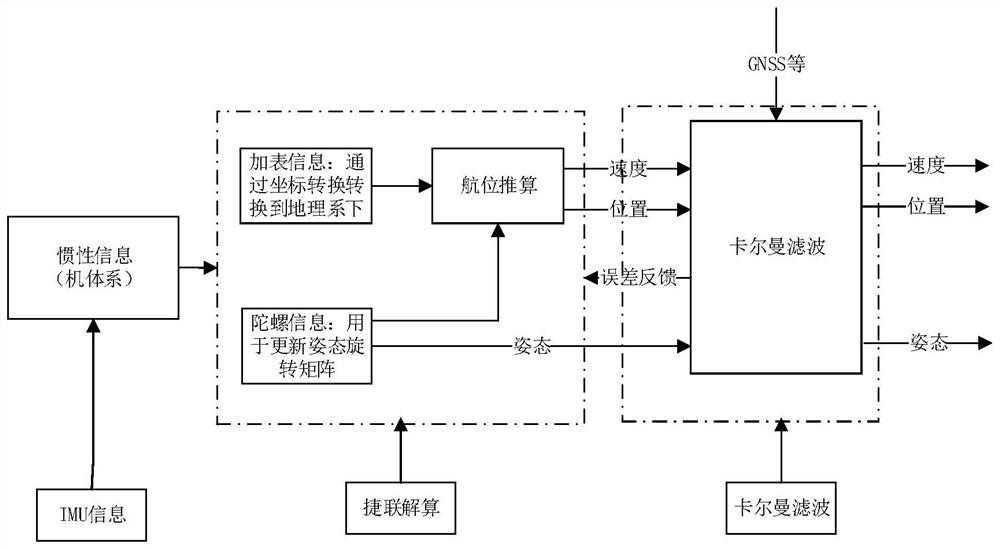
PendingCN112526570AHigh positioning accuracyReduce mistakesSatellite radio beaconingTrainReal-time computing
The invention discloses a train positioning method and device. The method comprises steps of obtaining the differential position information of a train from a satellite receiver, and obtaining the driving information of the train from an inertial navigation unit; and carrying out positioning calculation according to the differential position information and the driving information so as to outputthe positioning information of the train. According to the method, positioning precision is improved, the error is reduced, implementation and deployment are convenient, and construction cost is low.
Owner:CSR ZHUZHOU ELECTRIC LOCOMOTIVE RES INST
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com