Patents
Literature
605 results about "Records management" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Records management, also known as records and information management, is an organizational function devoted to the management of information in an organization throughout its life cycle, from the time of creation or inscription to its eventual disposition.This includes identifying, classifying, storing, securing, retrieving, tracking and destroying or permanently preserving records.
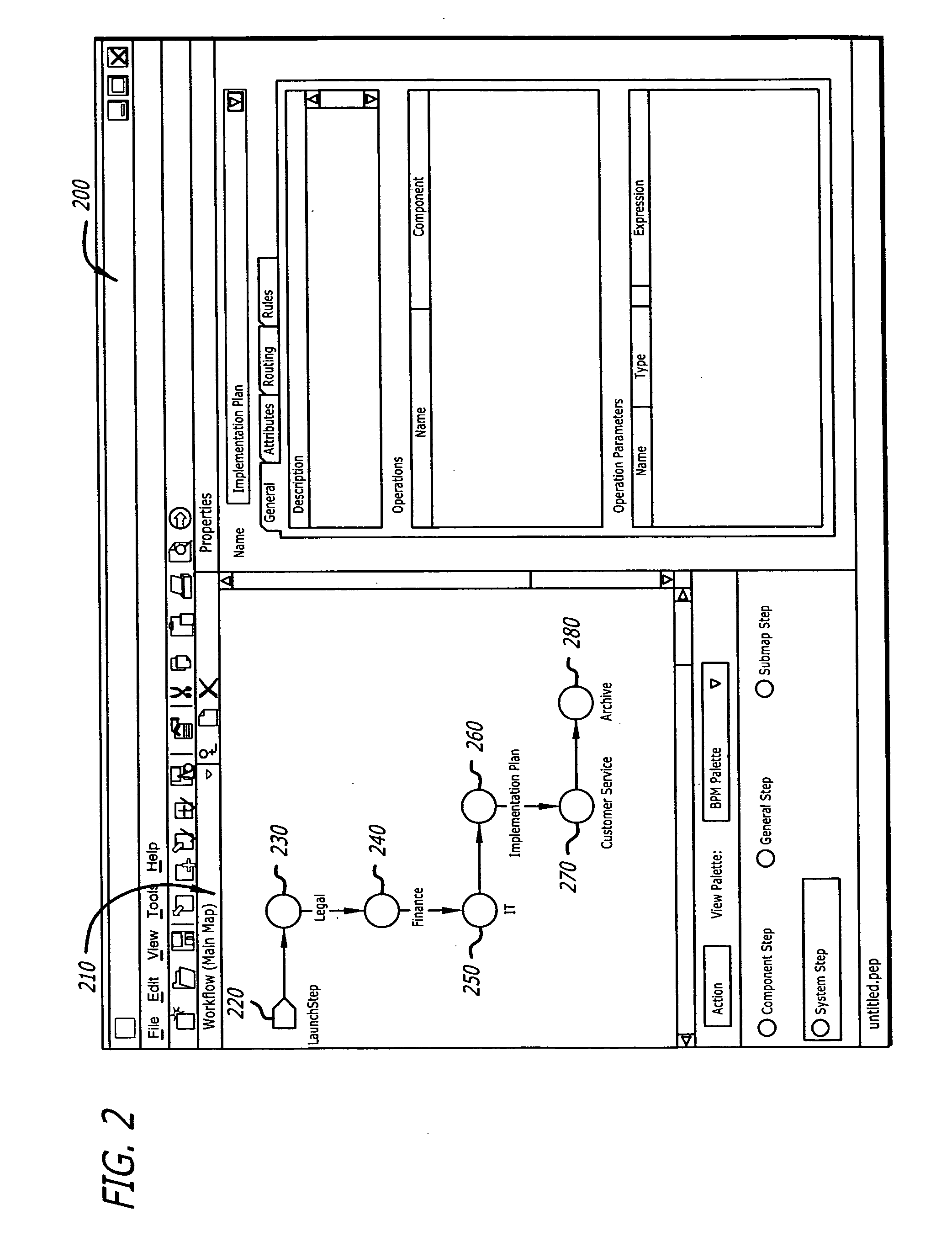
Recording apparatus, recording method, program for recording method, and storage medium that stores program for recording method
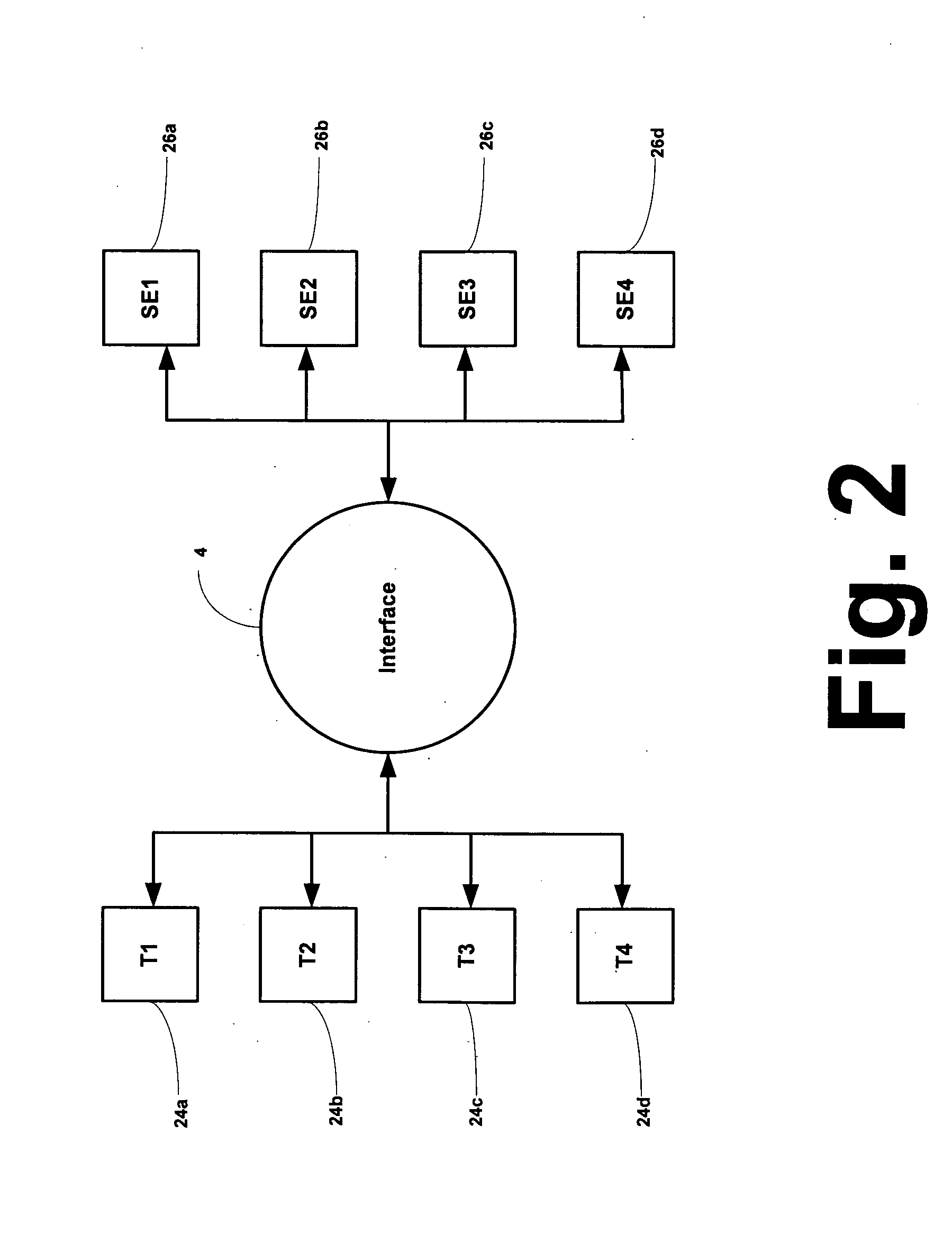
InactiveUS20090198889A1Suppress significant in serviceable lifeIncrease in sizeRecording carrier detailsInput/output to record carriersData recordingRecords management
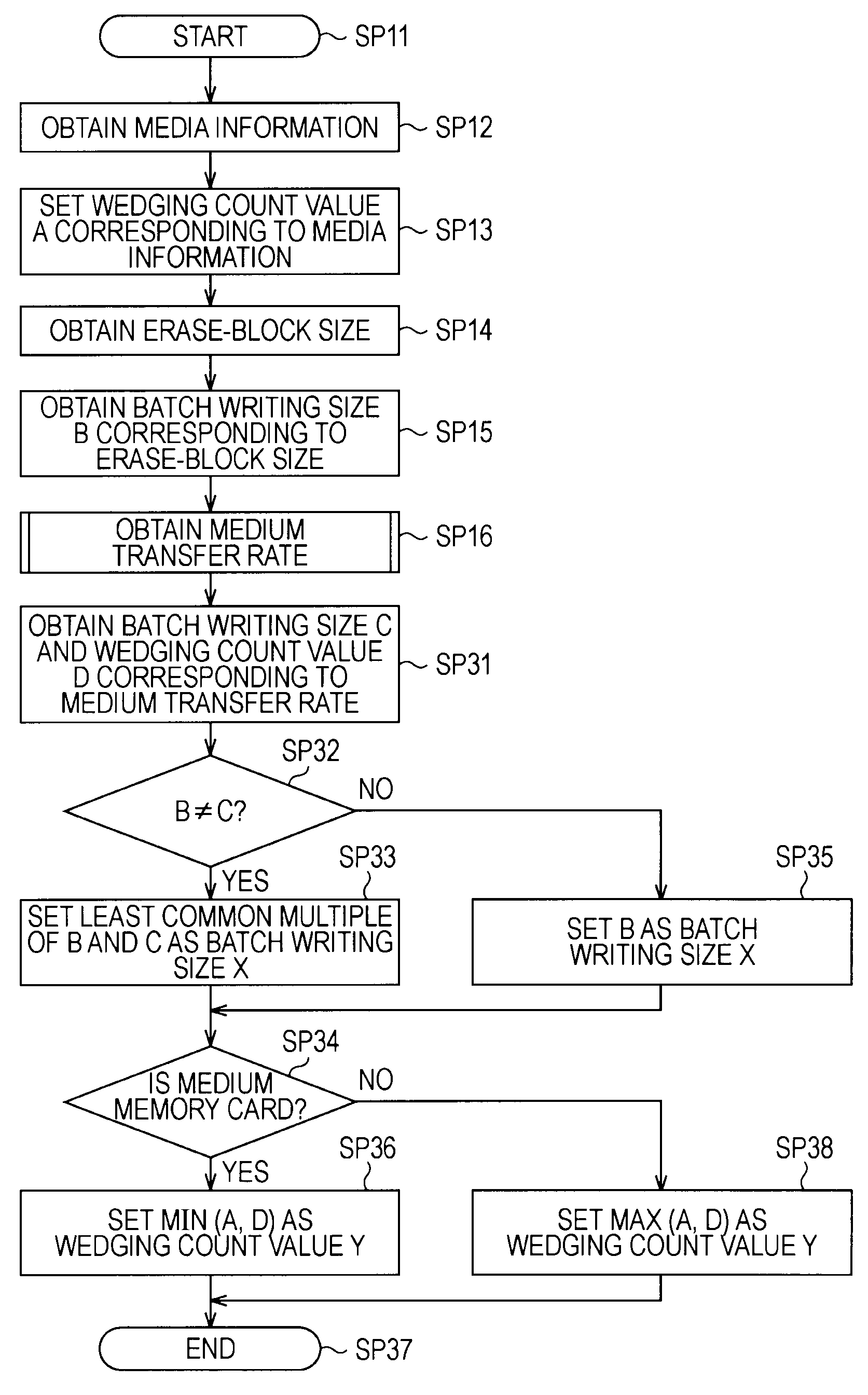
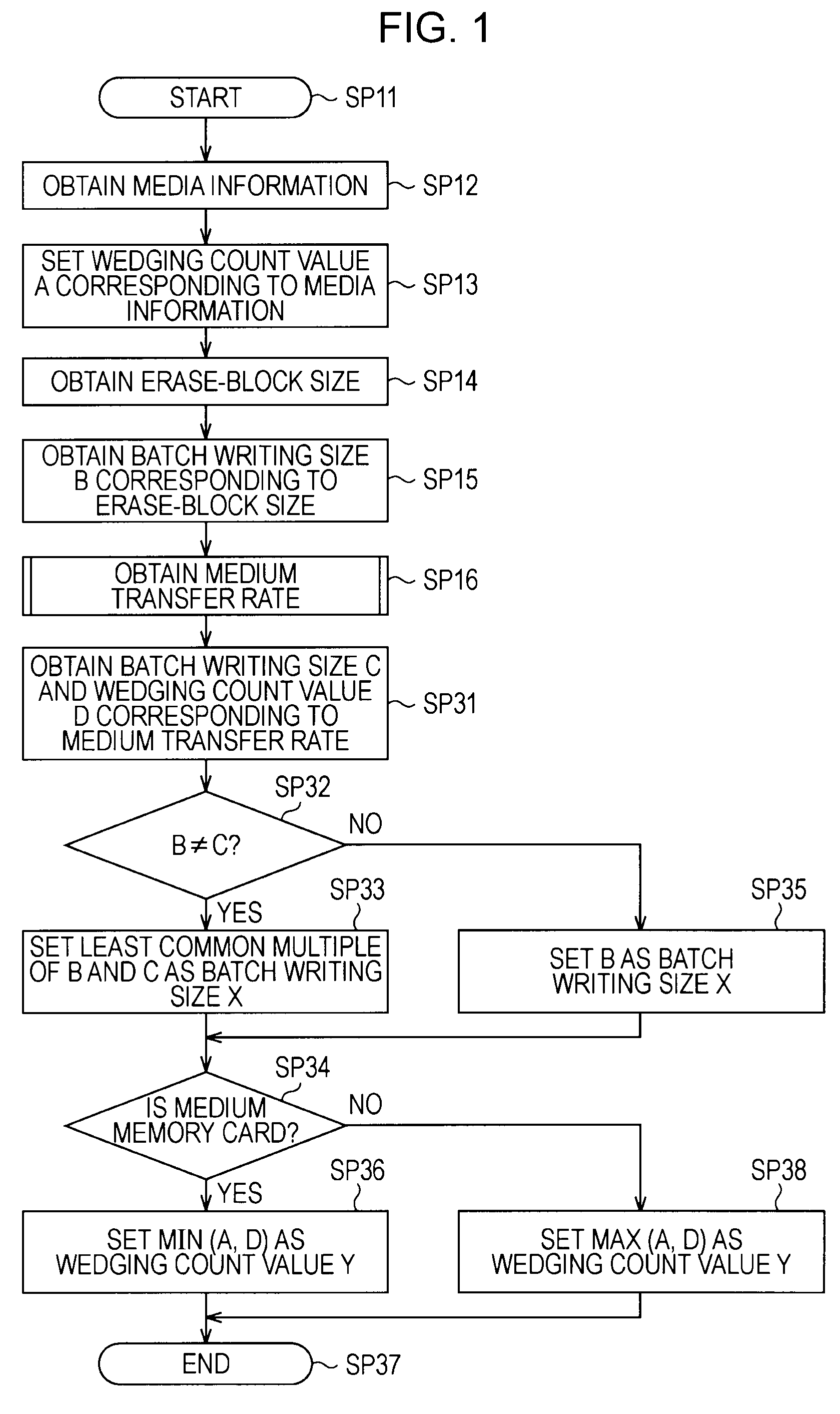
A recording apparatus includes: a type detecting section that detects a type of storage medium; an erase-block size detecting section that detects an erase-block size of the storage medium; a recording section that records desired data to a data area in the storage medium and records management information of the data area to a management area in the storage medium; and a control section that controls the recording section by issuing a command to the recording section, on the basis of results of the detection. Each time a certain amount of data is recorded to the data area, the control section updates the management information in accordance with the recording, and when the storage medium is a storage medium in which recorded data is updated for each erase-block size, the control section increases the certain amount of data according to an increase in the erase-block size.
Owner:SONY CORP
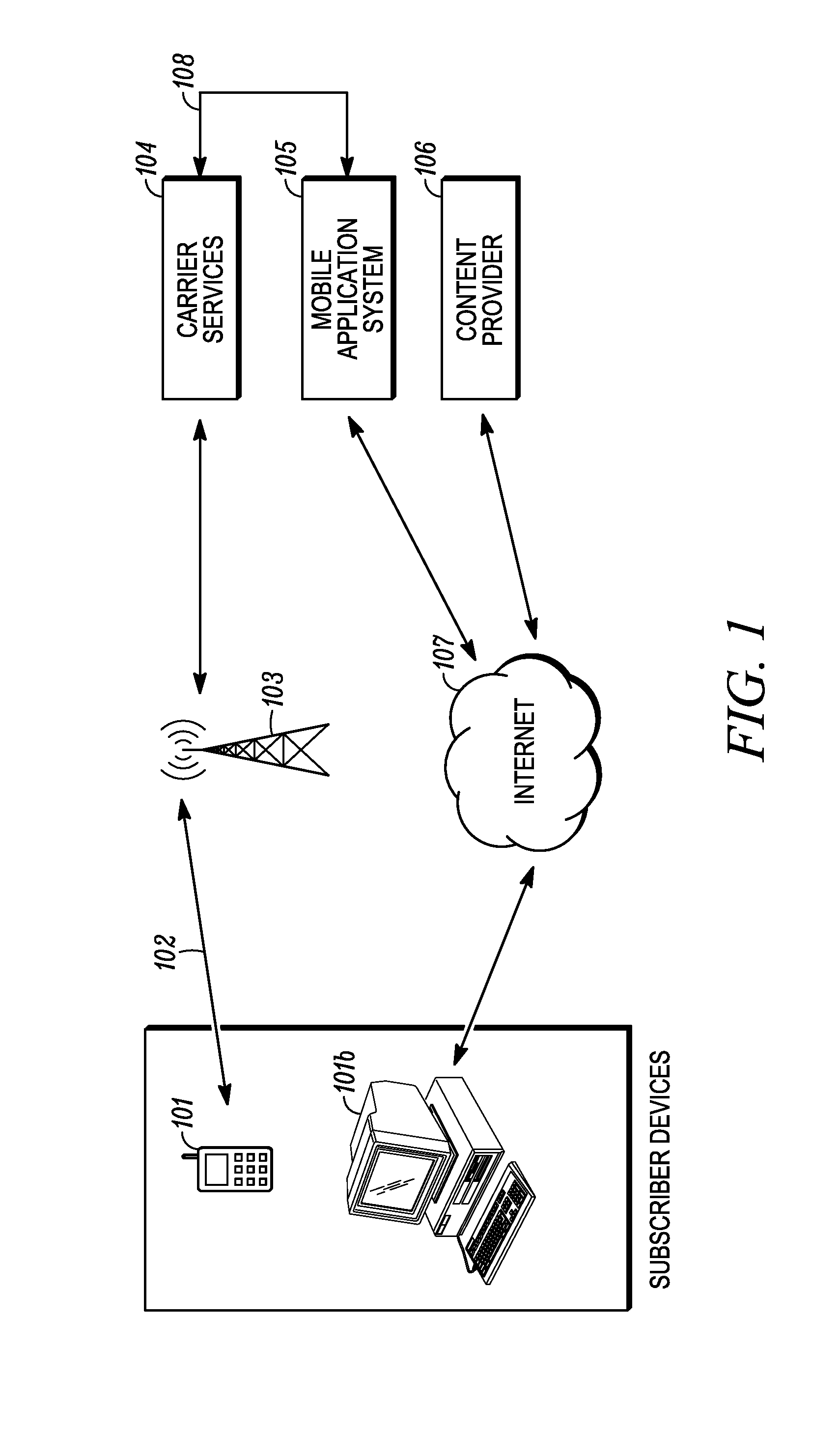
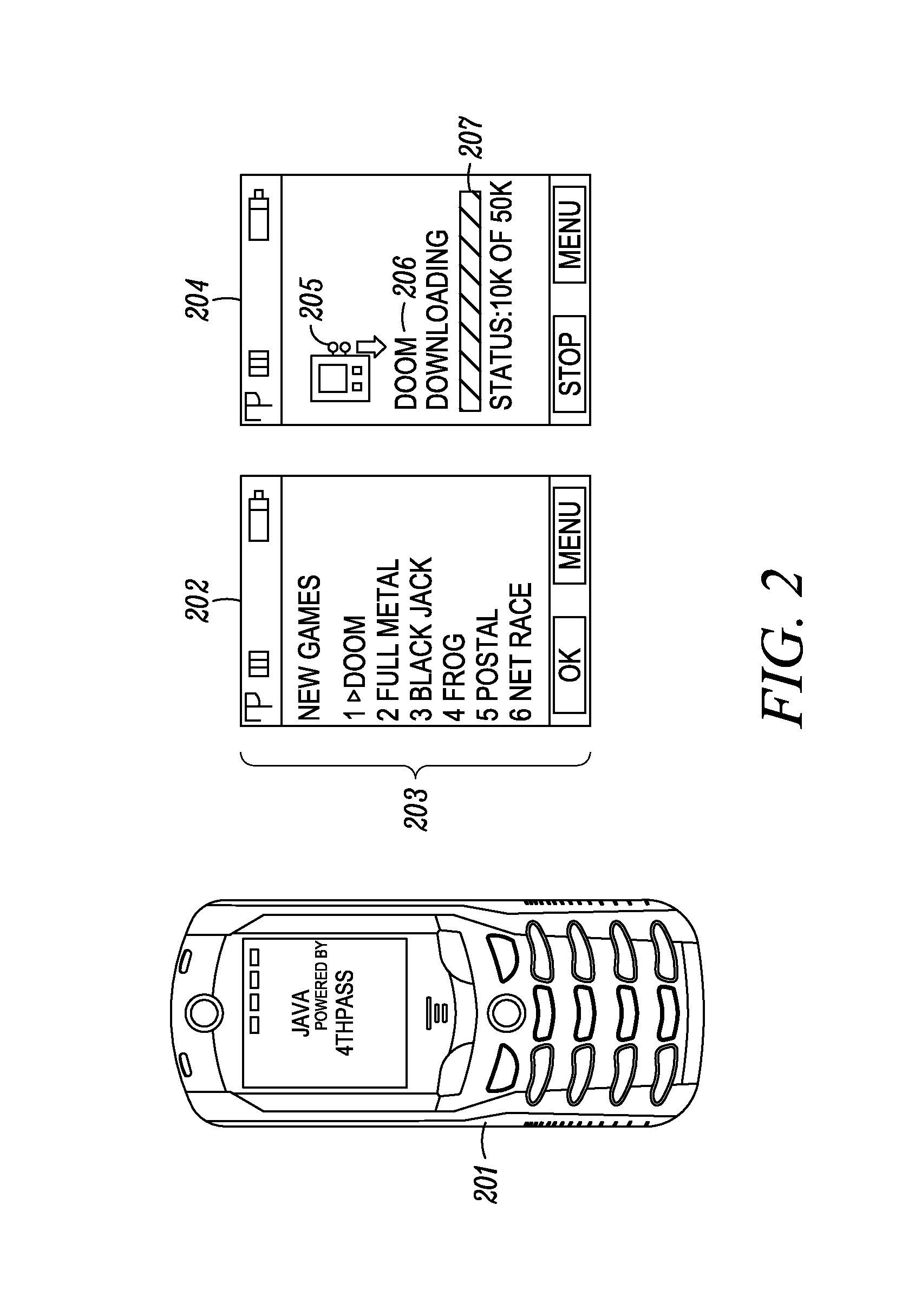
Method and System for Maintaining and Distributing Wireless Applications
InactiveUS20080301231A1Greater assurance of their ability to successfully executeRaise the possibilityAccounting/billing servicesNetwork traffic/resource managementSupply managementApplication computers
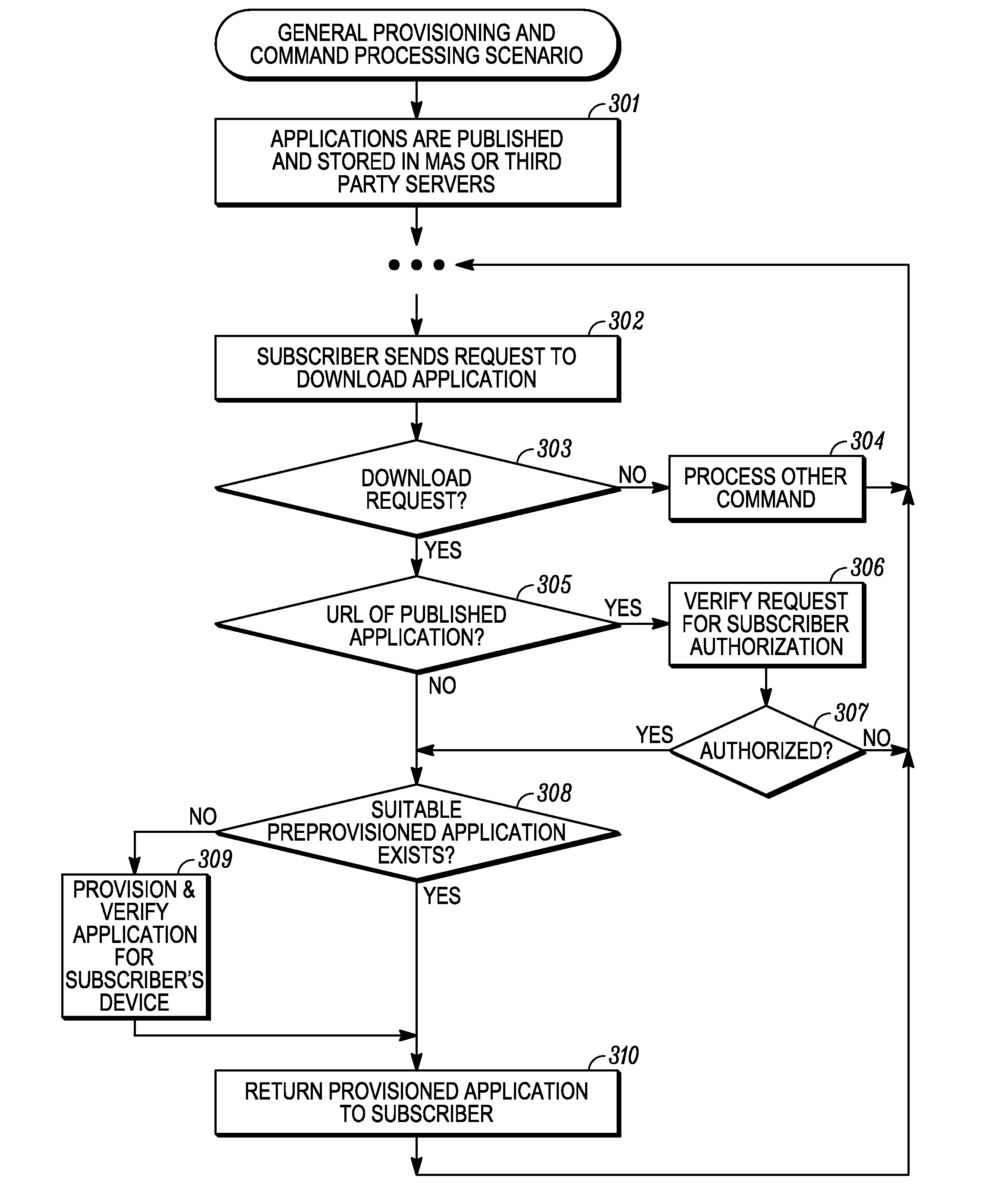
Computer- and network-based methods and systems for maintaining and provisioning wireless applications are provided. Example embodiments provide a Mobile Application System (MAS), which is a collection of interoperating server components that work individually and together in a secure fashion to provide applications and resources to mobile subscriber devices, such as wireless devices. Embodiments of the present invention can also be used to deploy applications and resources for wired subscriber devices. Application, resources, and other content is provisioned and verified by the MAS for authorized access by the subscriber, compatibility with a requesting subscriber device, and the security and billing policies of the carrier and system administrators of the MAS. In this manner, applications, resources, and other content can be downloaded to devices, such as wireless devices, with greater assurance of their ability to successfully execute. In one embodiment, content is provisioned by one or more of the steps of inspecting the content for malicious or banned code, optimizing the content for smaller size and greater speed, instrumentation of code that implements security, billing, and other carrier policies, and packaging of code for the intended subscriber device. Additional security is provided through application filters that are used to prevent applications that contain designated API from being downloaded to a subscriber's device. In one embodiment, the MAS includes a Protocol Manager, Provisioning Manager, Cache, Deployment Manager, Billing Manager, Logging Manager, Administrator, and Heartbeat Monitor, which interoperate to provide the provisioning functions.
Owner:MEHTA SAMIR NARENDRA +2
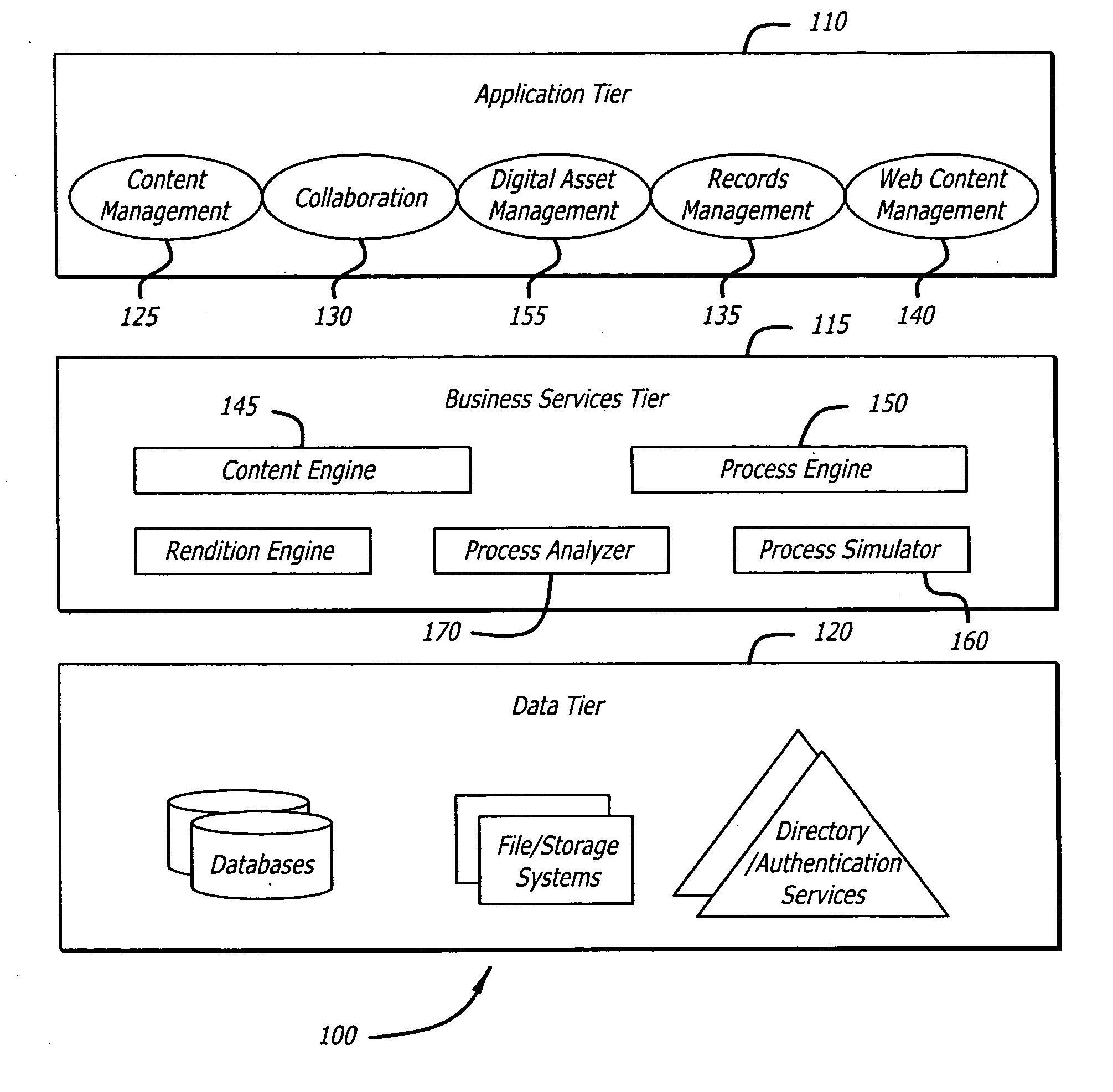
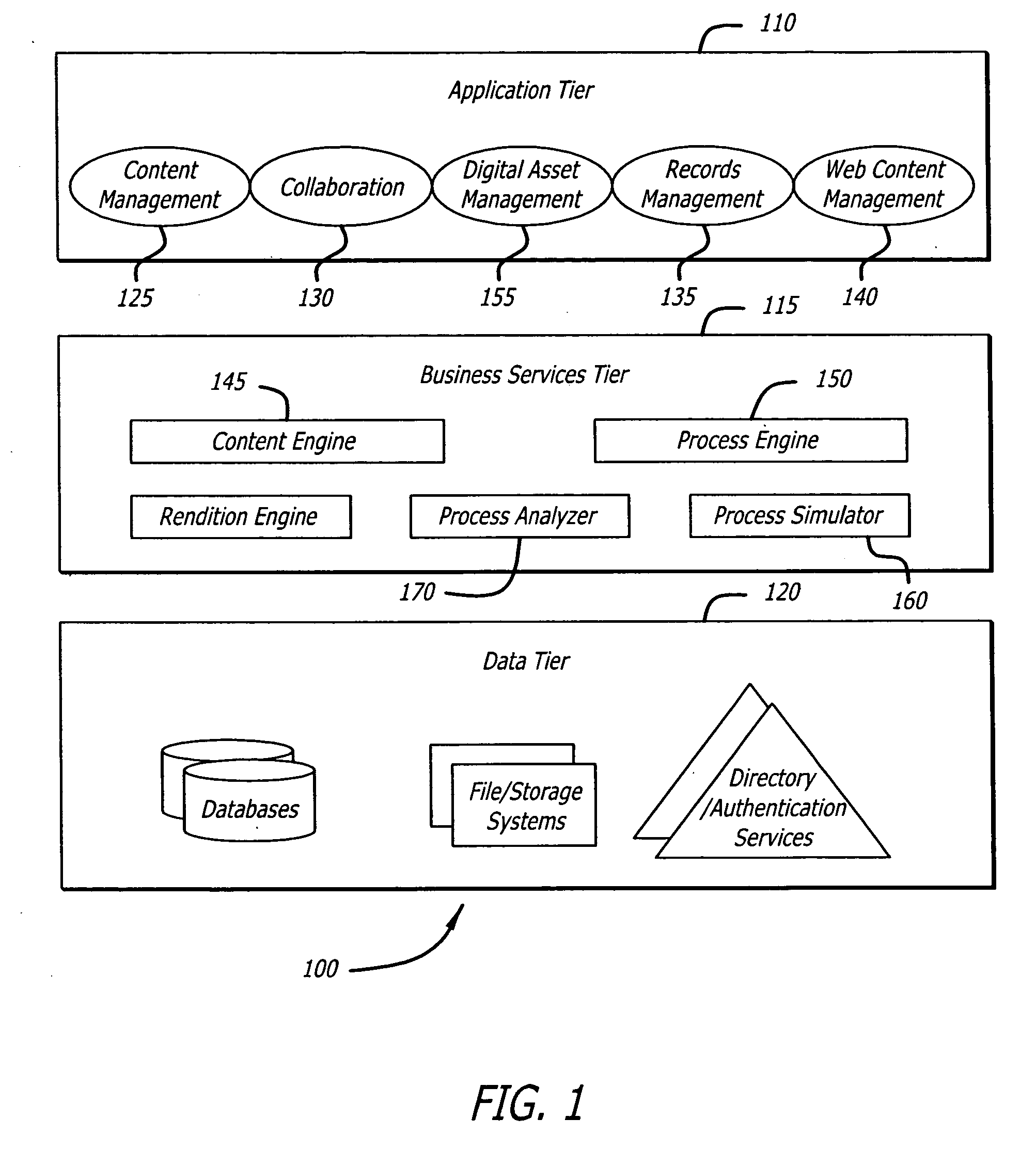
Team collaboration system with business process management and records management
A user-friendly web-based team collaboration solution that provides diverse team members the opportunity to participate in synchronous and asynchronous activities through a teamspace. Using a single platform that integrates team collaboration with business process management, team activities may be implemented through ad-hoc tasks and business process management driven steps to accomplish specific business objectives. Using this single platform, collaboration artifacts may also be managed through a records management system, thus making team collaboration efforts available as records. Numerous method variations, as well as related systems and computer-readable media are also disclosed.
Owner:IBM CORP
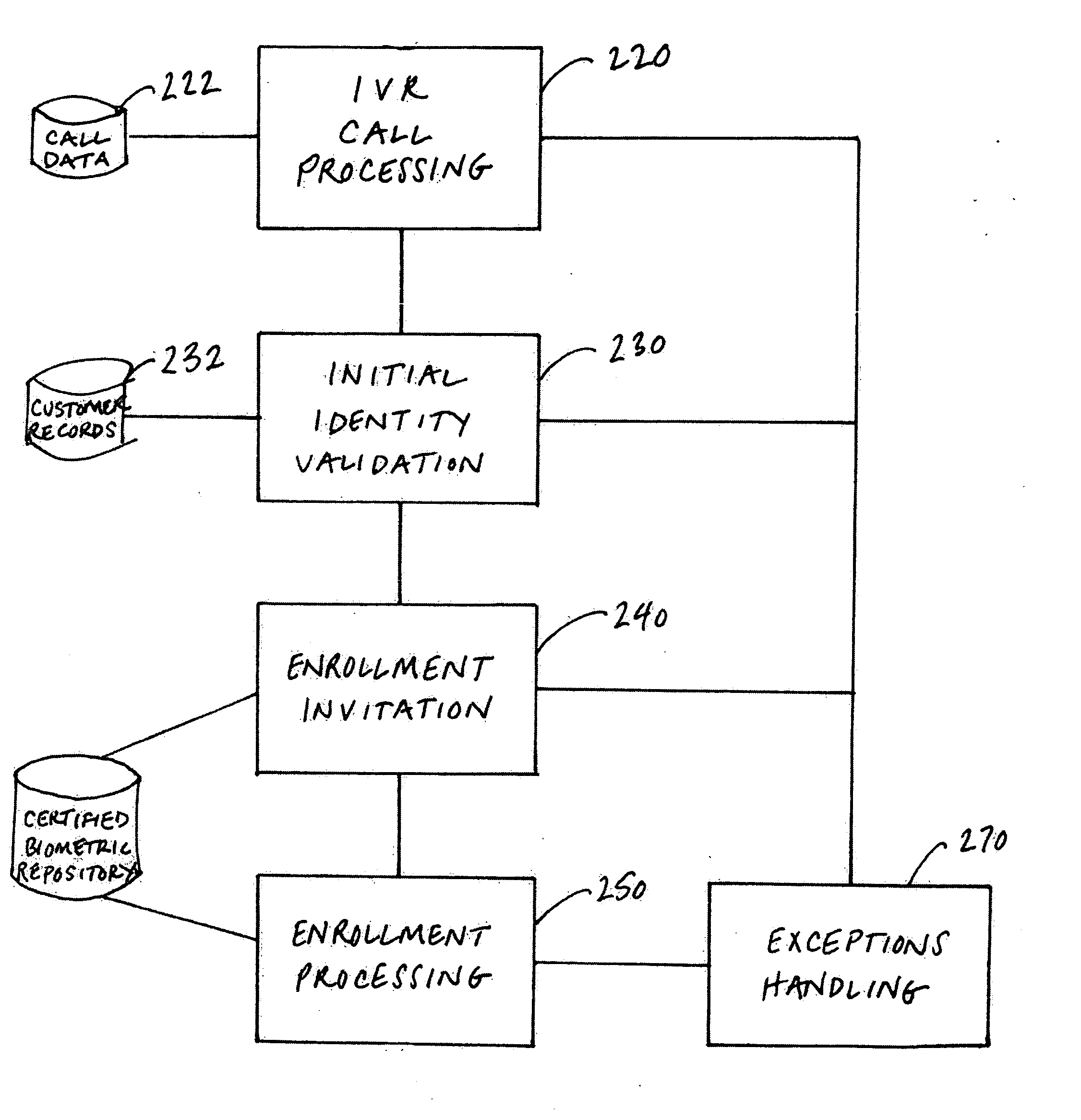
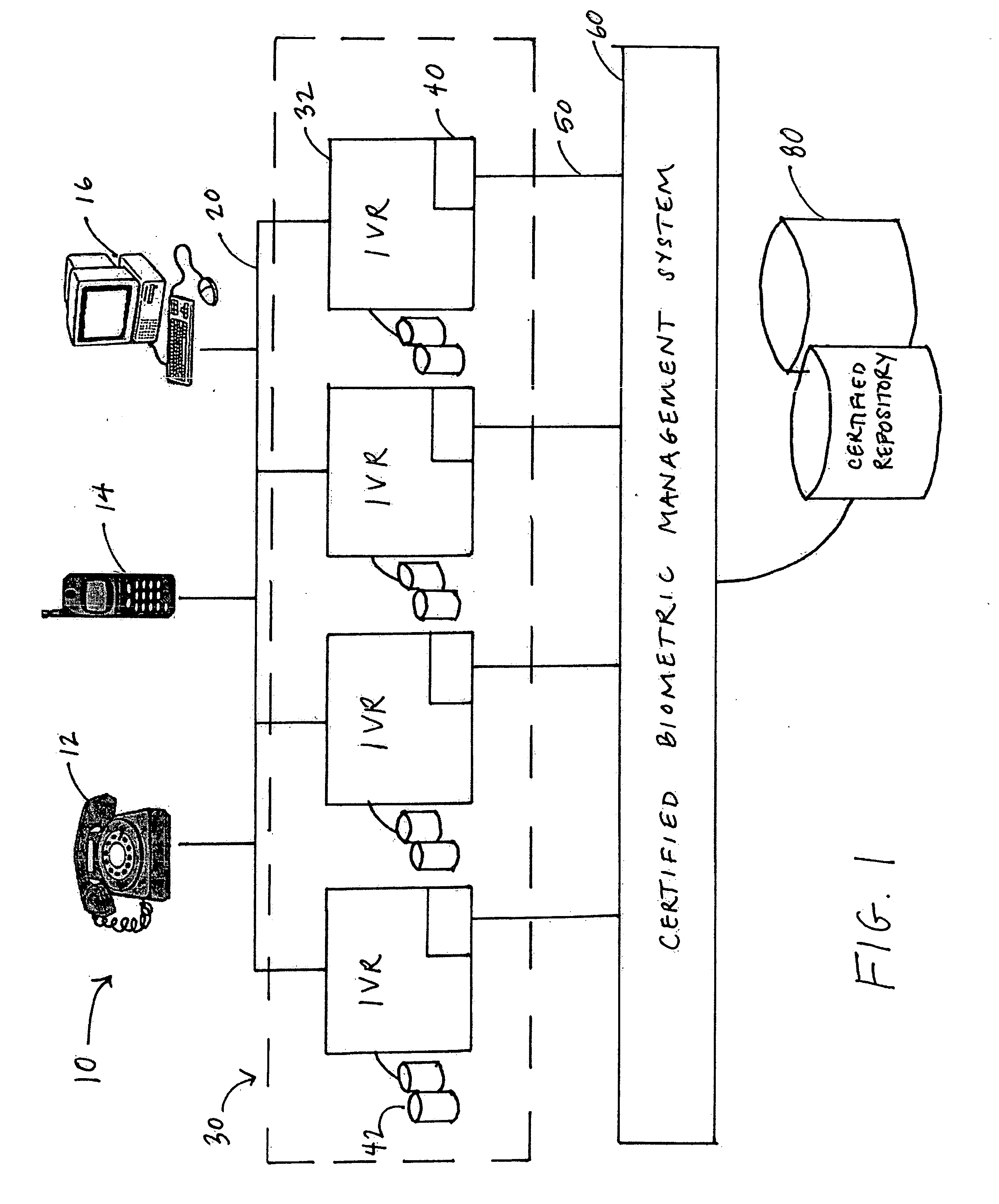
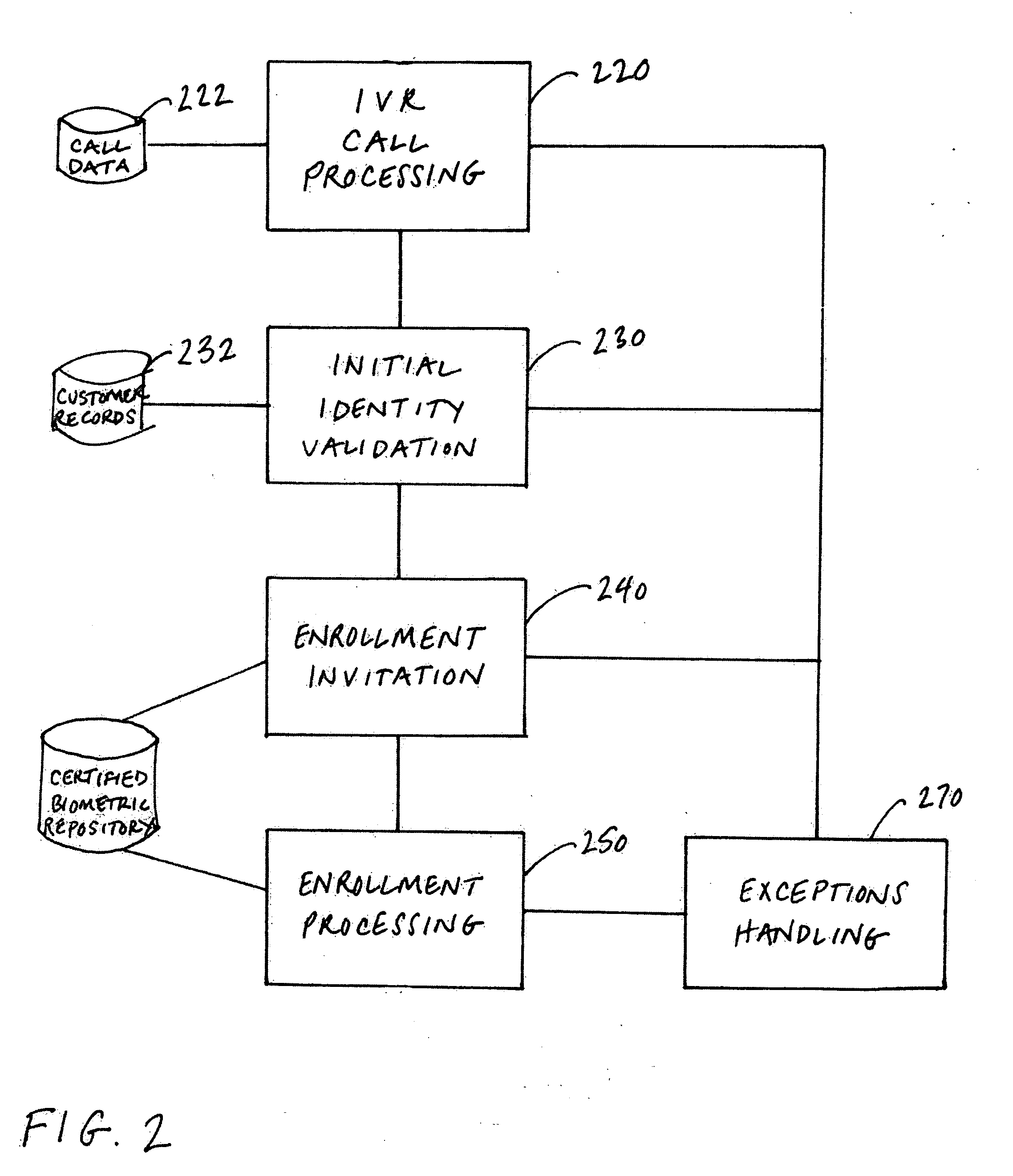
Biometric record management
InactiveUS20060106605A1Easy to implementImprove availabilitySpeech recognitionMultiple formsNetwork communication
A method of enrolling voice information of an individual in a repository is disclosed. The individual may be associated with a contributing entity and the repository may be used by multiple entities within a consortium for creating, accessing or enhancing one or more forms of utterances associated with an individual. The method comprises establishing a predefined certification process for enrollment by multiple contributing entities of individual voice information in a repository, capturing one or more utterances from an individual associated with a contributing entity while the individual communicates over a network and storing one or more forms of the captured utterance associated with the individual along with information identifying the contributing entity associated with the individual in the repository.
Owner:TARGUS INFORMATION CORP
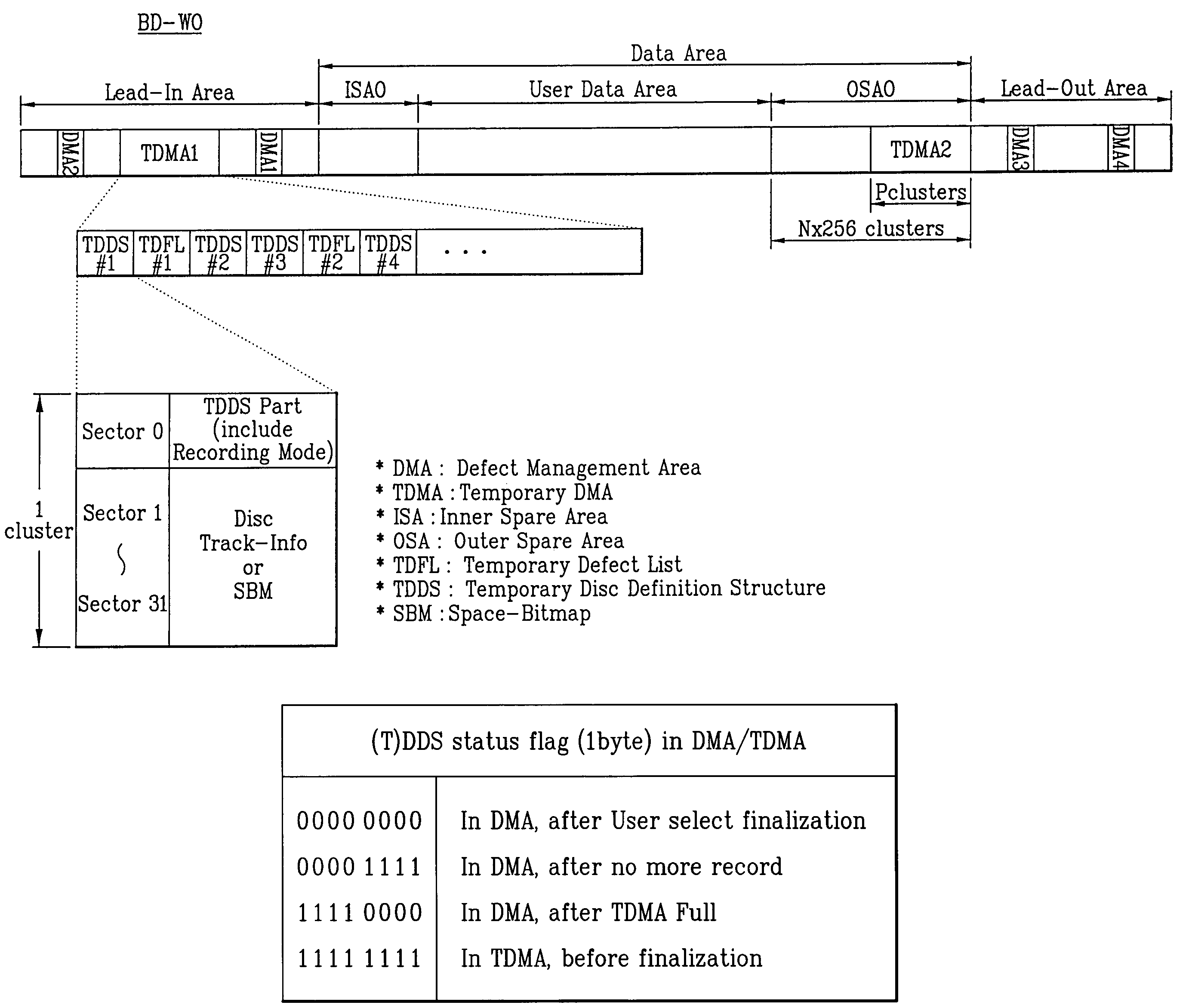
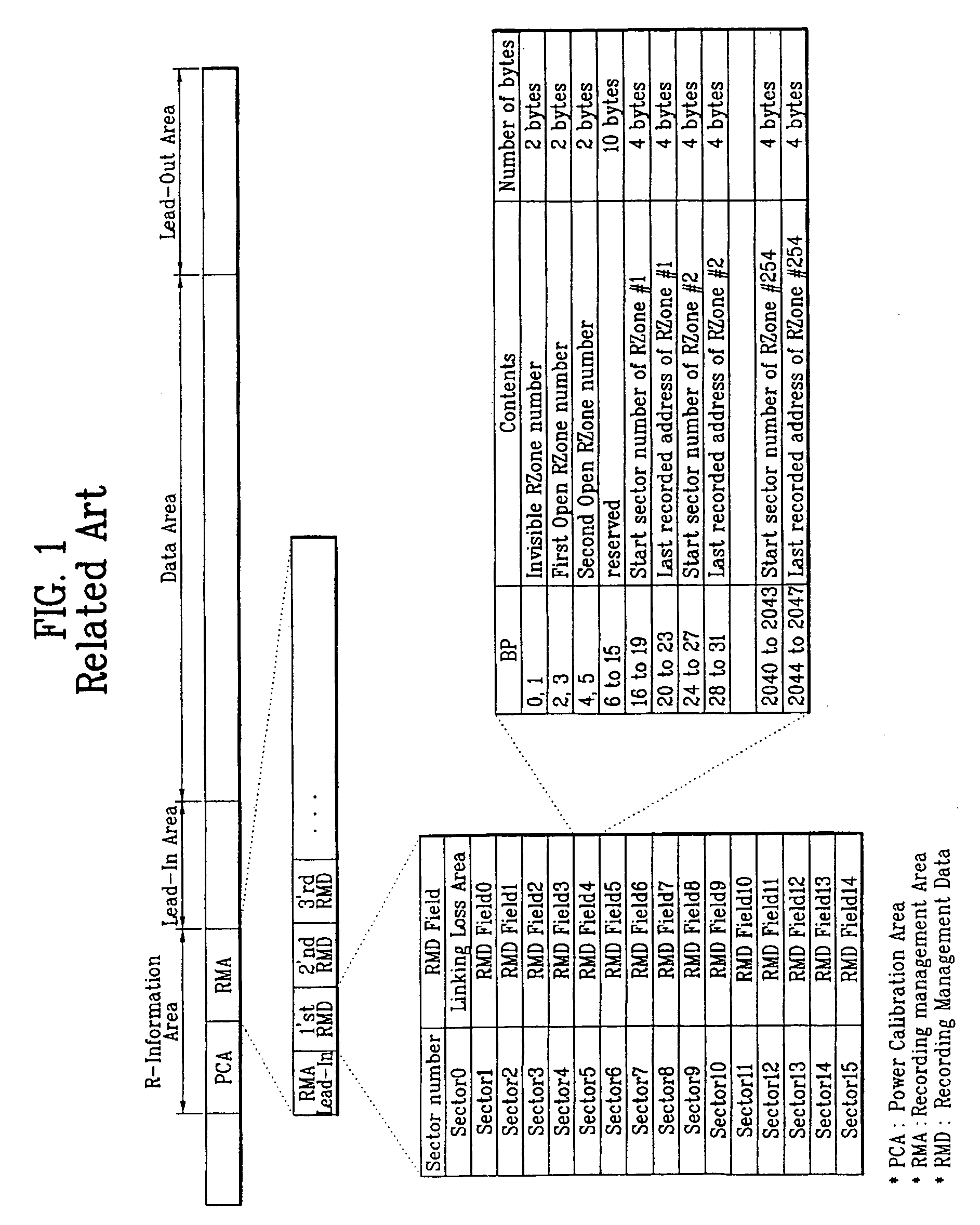
Write-once optical disc, and method and apparatus for recording management information on write-once optical disc
ActiveUS7233550B2Disc-shaped record carriersFilamentary/web record carriersComputer hardwareOptical recording
A write-once optical recording medium, and a method and apparatus for recording management information on the recording medium are provided. The method includes recording, in a temporary defect management area (TDMA), management information produced while the recording medium is in use, and transferring and recording the latest management information of the TDMA in a final defect management area (DMA) of the recording medium at a DMA fill-in stage of the recording medium.
Owner:LG ELECTRONICS INC
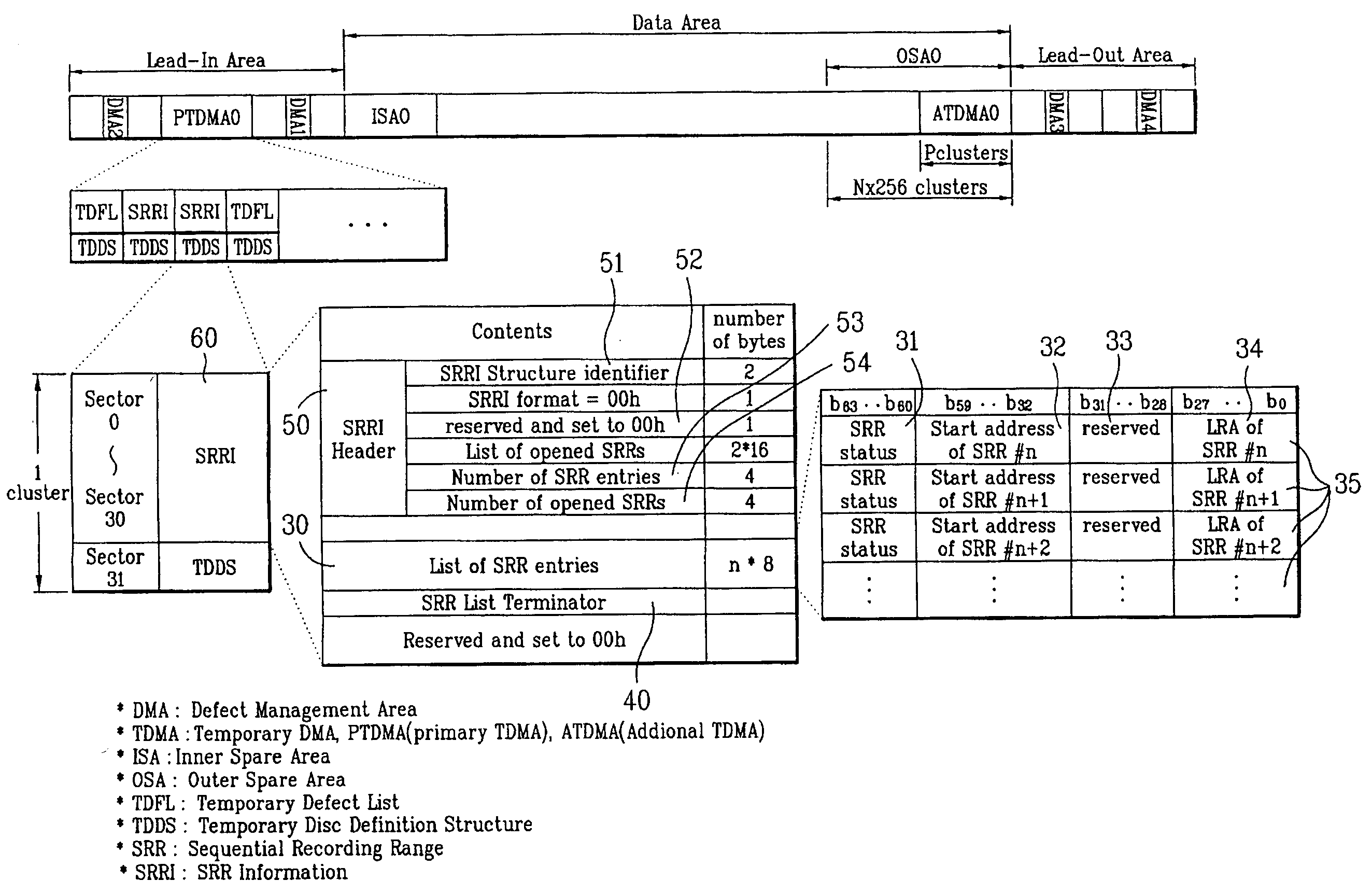
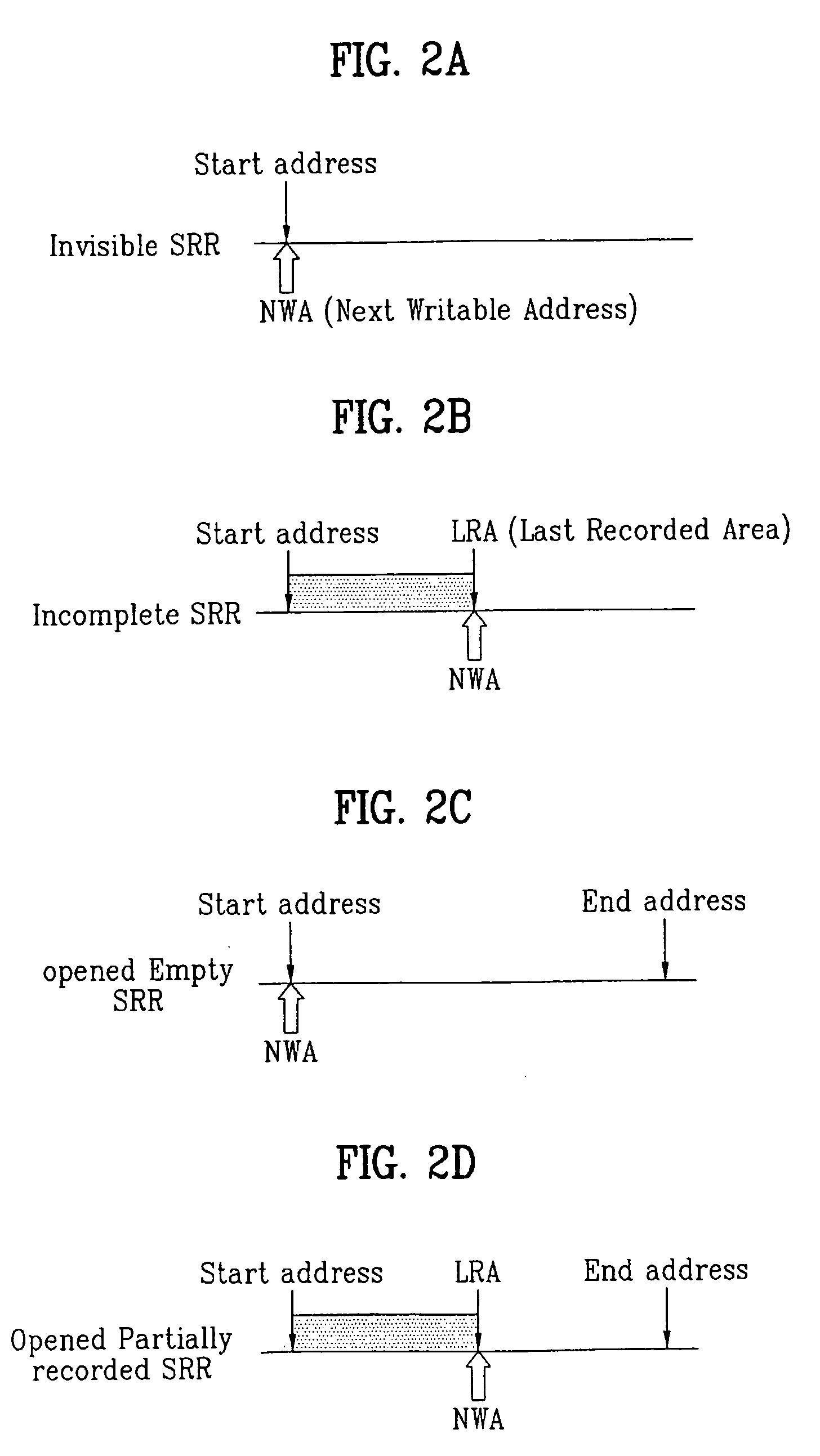
Write-once optical disc, method and apparatus for recording management information on write-once optical disc
InactiveUS20050060489A1Efficiently recording and managing this recording status informationFilamentary/web record carriersRecord information storageRecord statusRecording layer
A write-once optical disc, and a method and apparatus for recording management information on the write-once optical disc, are provided. The optical disc includes at least one recording layer, and at least one SRR entry. Each SRR entry corresponds to an SRR and includes at least one status field for indicating a recording status of the corresponding SRR. The status field includes a session start flag for indicating whether the corresponding SRR is a start of a session, the session being formed by a group of the SRRs. Each SRR entry further includes a start address field indicating where the corresponding SRR starts, and a last address field indicating the last recorded address of the corresponding SRR.
Owner:LG ELECTRONICS INC
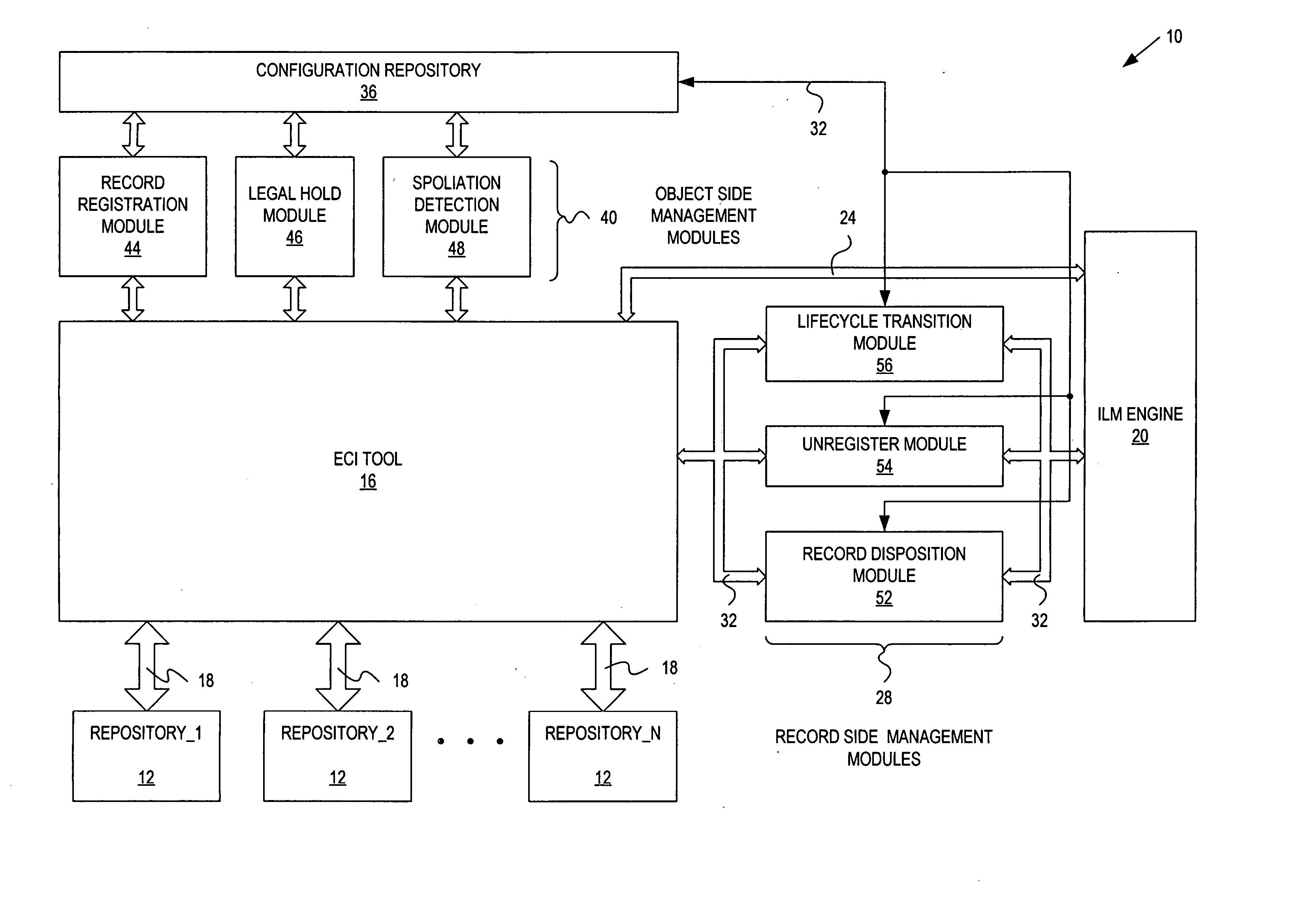
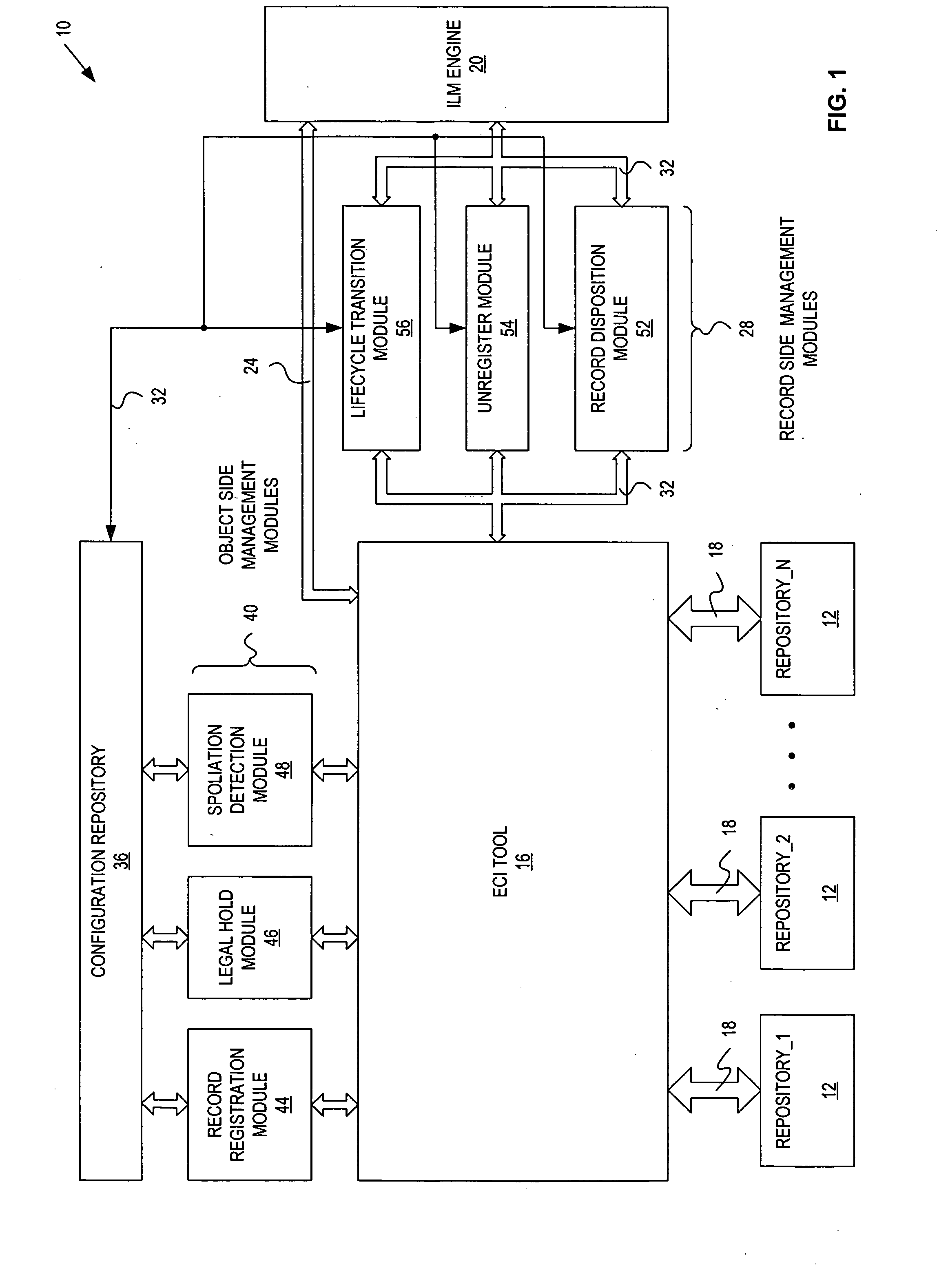
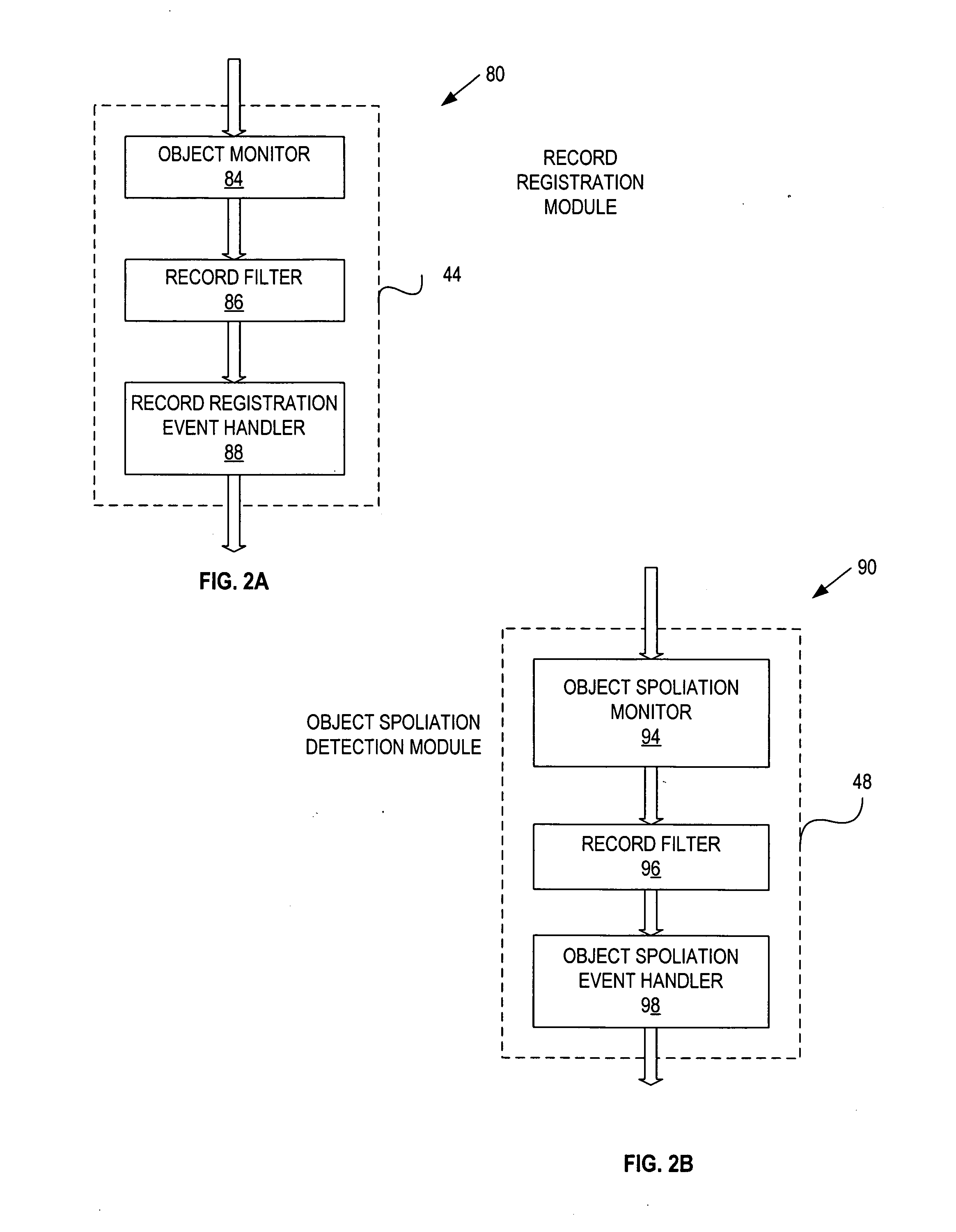
Records management federation
InactiveUS20060230044A1Database updatingDatabase management systemsInformation repositoryRecords management
A record management system includes: a configuration repository providing a mapping between object information and record management information for each of a plurality of record management actions; at least one object side record management module communicatively coupled with an ECI tool, an ILM engine and the configuration repository, and being responsive to object events, and operative to initiate and control at least one of the record management actions based on the mapping provided by the configuration repository; and at least one record side record management module communicatively coupled with the ILM engine and the configuration repository, and being responsive to record events, and operative to initiate and control at least one of the record management actions based on the mapping provided by the configuration repository.
Owner:DATA EMPOWERMENT GRP
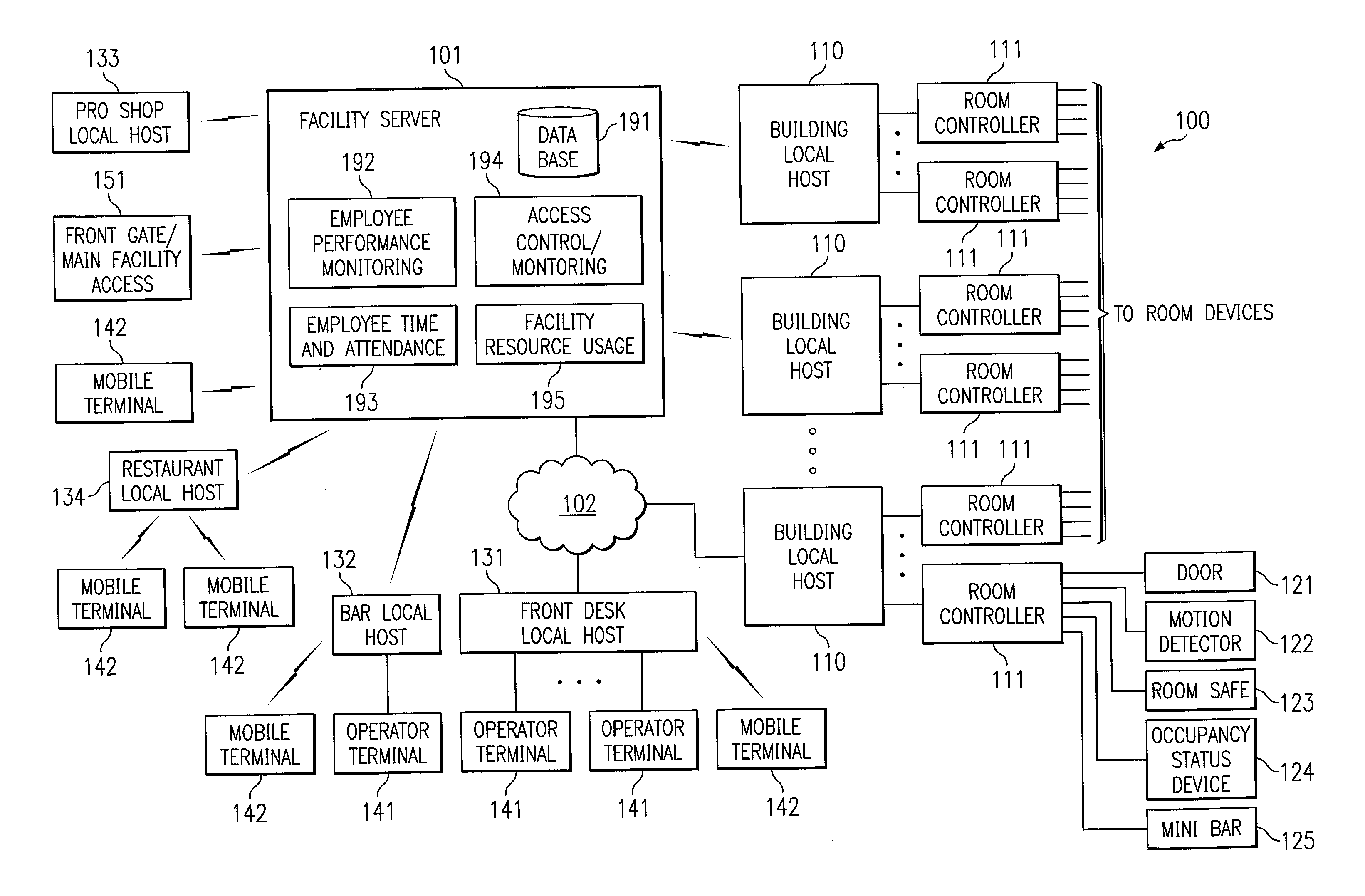
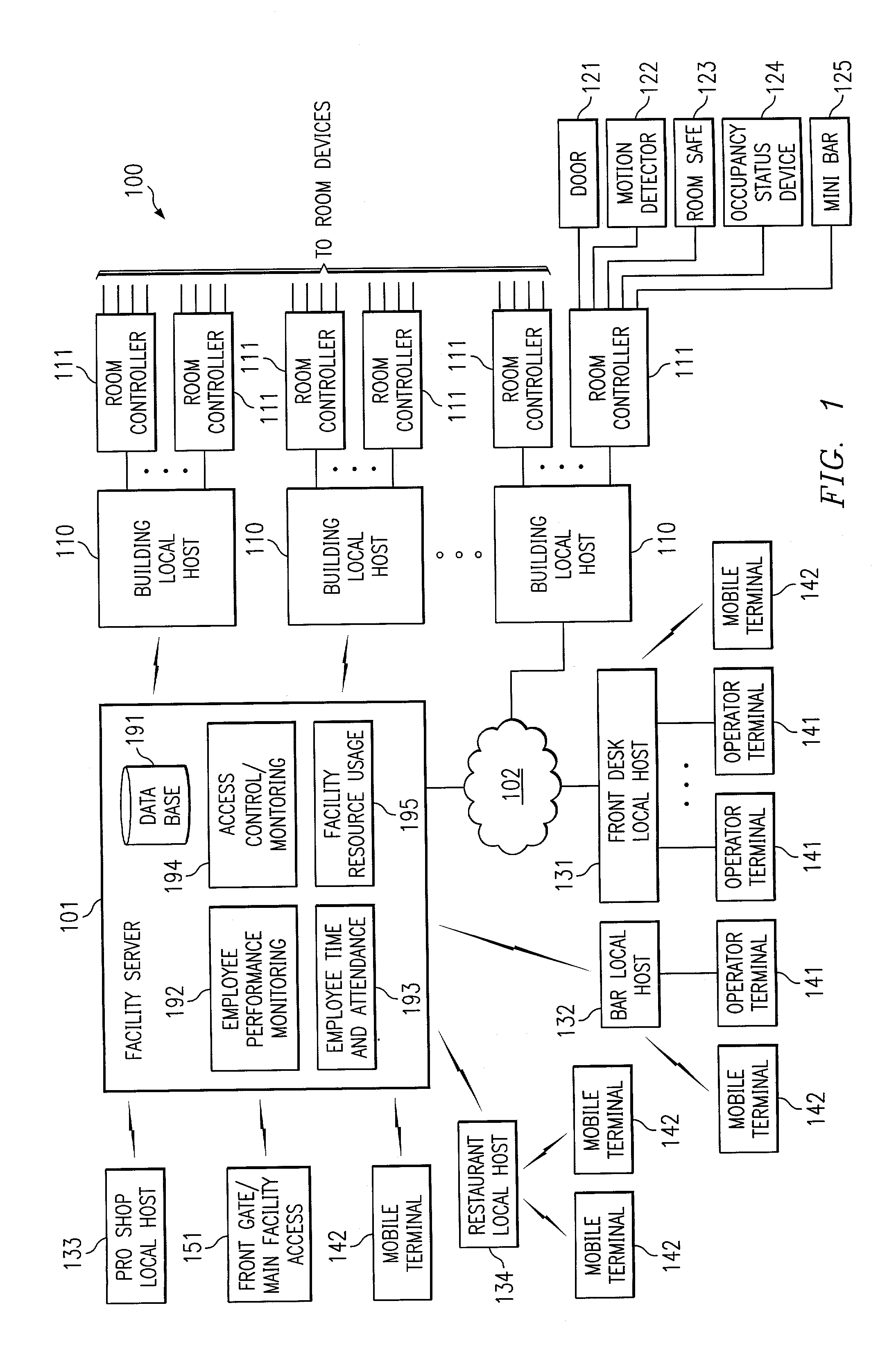
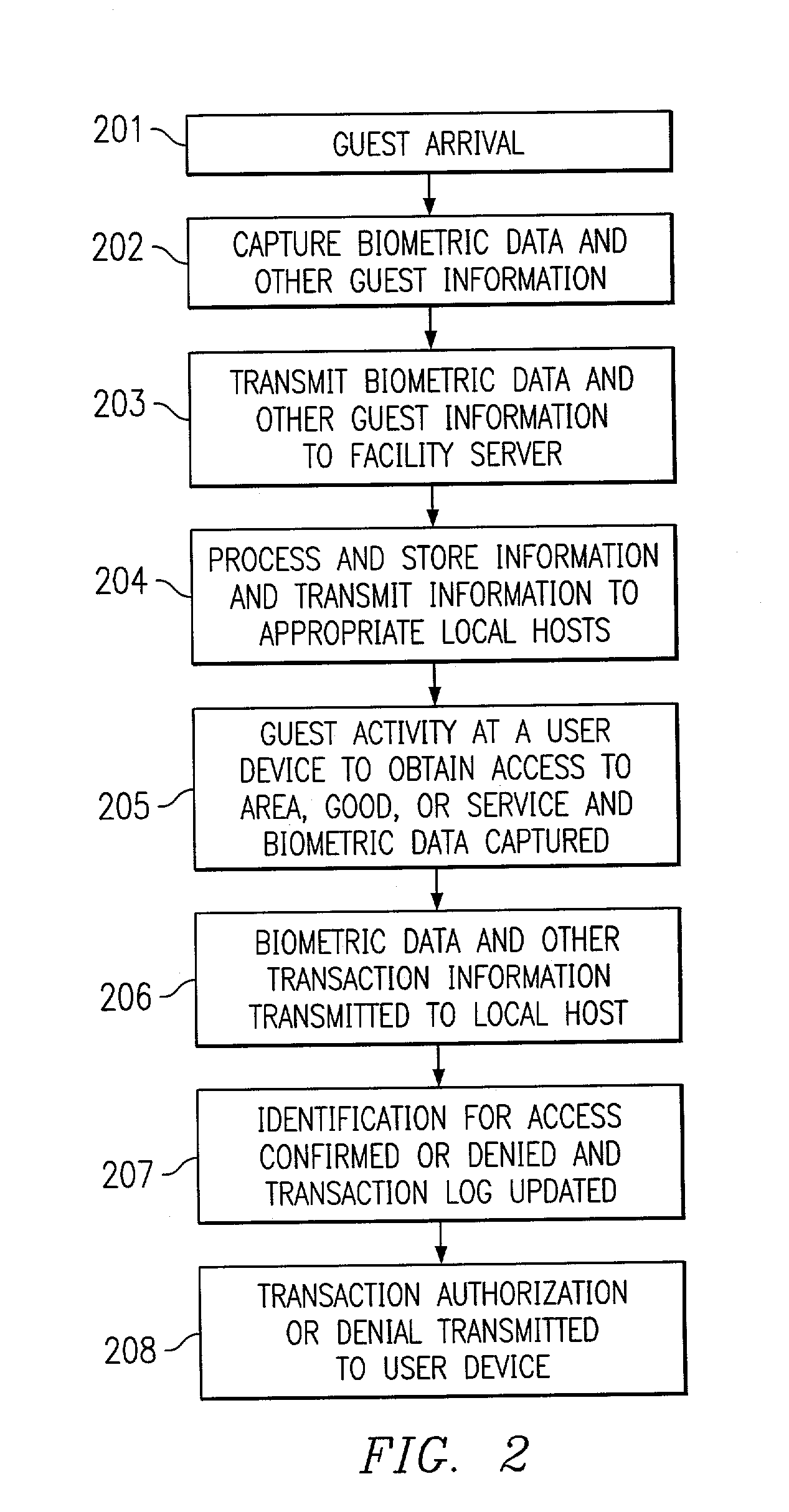
System and method for using biometric data for providing identification, security, access and access records
InactiveUS6972660B1Avoid accessElectric signal transmission systemsDigital data processing detailsWired communicationBiometric data
Disclosed are systems and methods which determine, to a desired level of certainty, the identities of each individual granted access to an area, room, container, and / or good or service using biometric data. A plurality of access points may be networked to provide access control and / or access record generation on a real time basis. Biometric scanners, electronic locks, and control devices are preferably disposed throughout a hierarchical access facility, such as a hotel, to provide access to areas, rooms, and containers, to acquire information with respect individuals' access thereto, and / or to identify individuals for providing access to goods and services. Such devices may be in communication with one another and / or host systems, such as local hosts and facility servers, via wireline communication, wireless communication, and combinations thereof to thereby provide a pervasive access and access record management system.
Owner:PINON HLDG
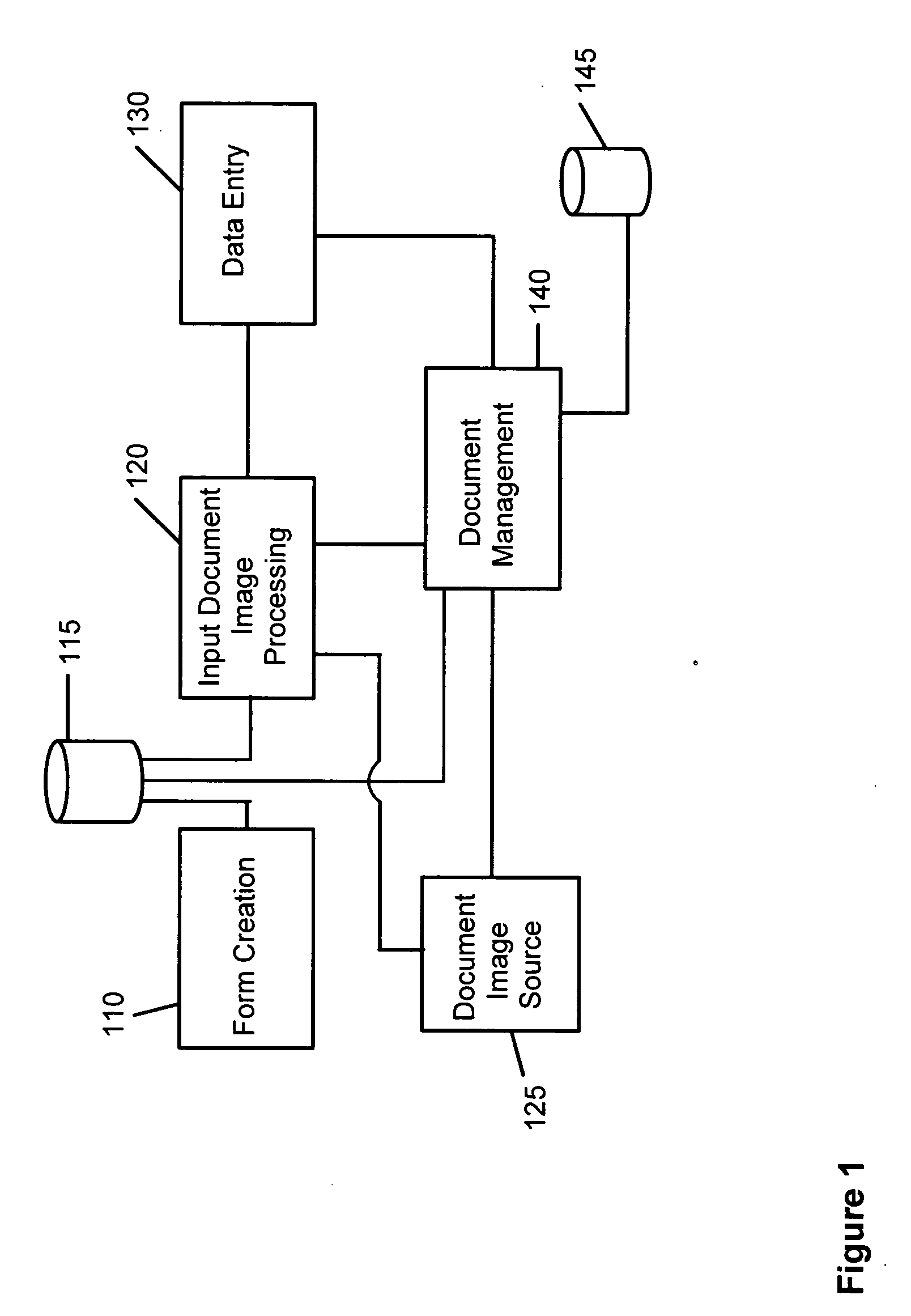
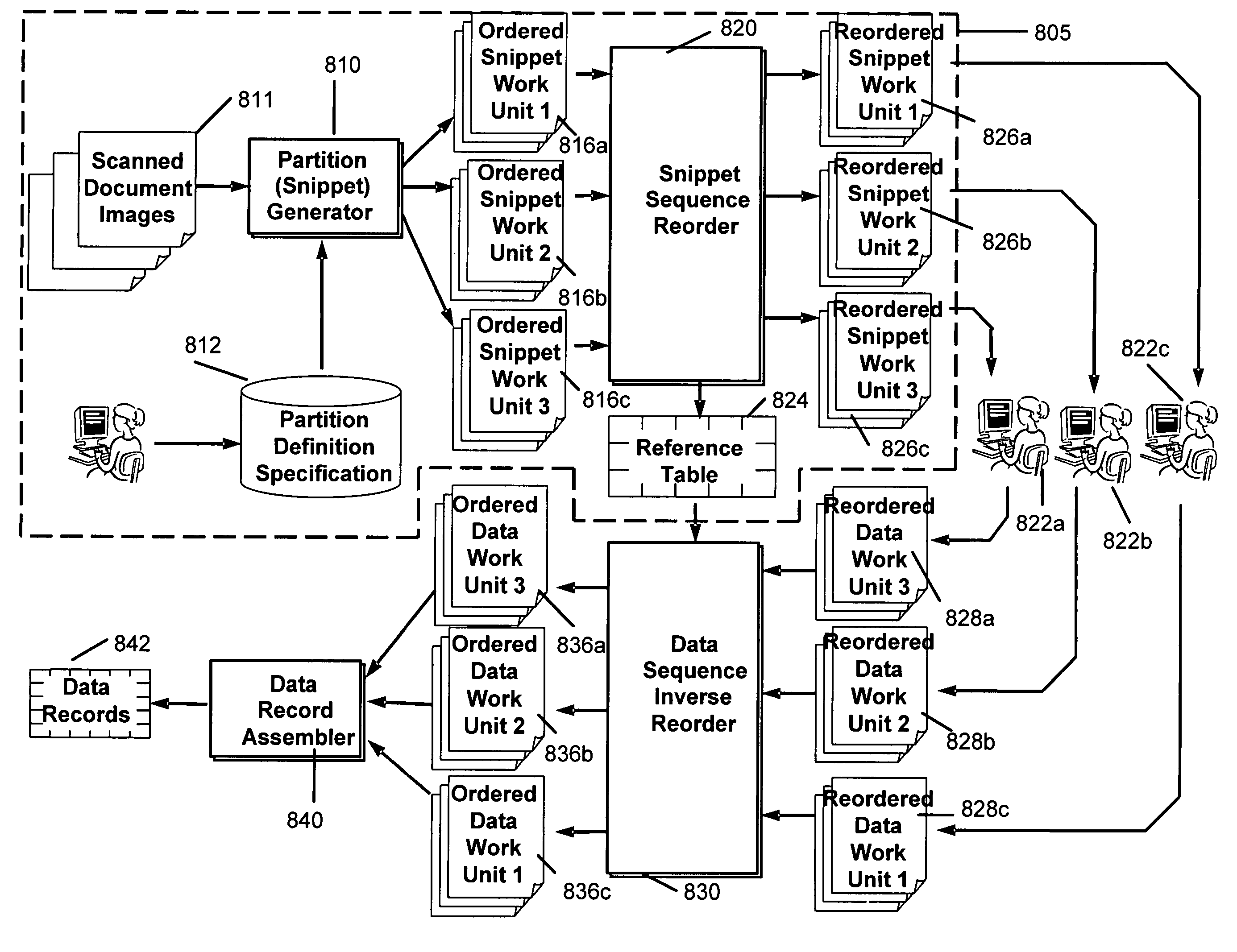
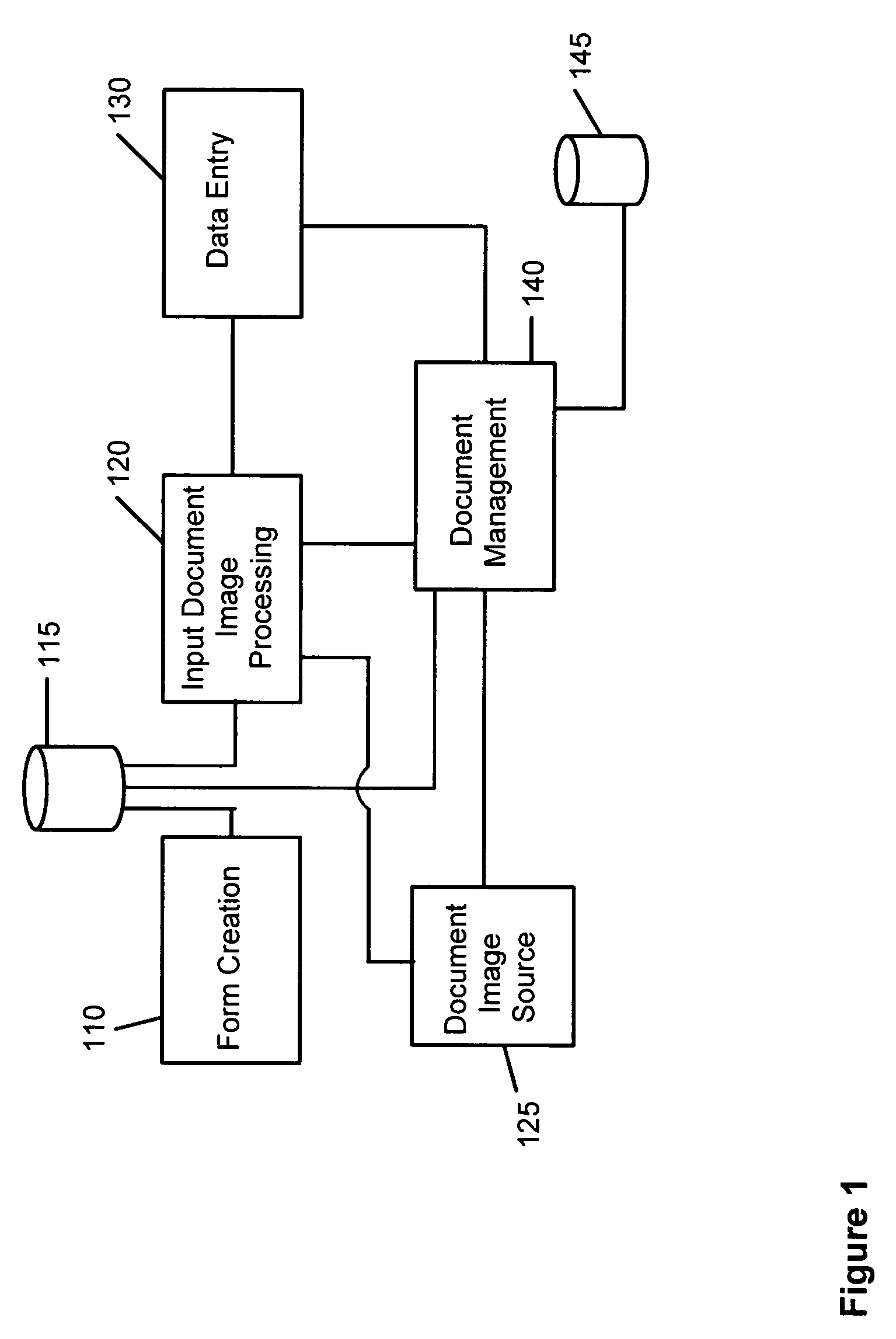
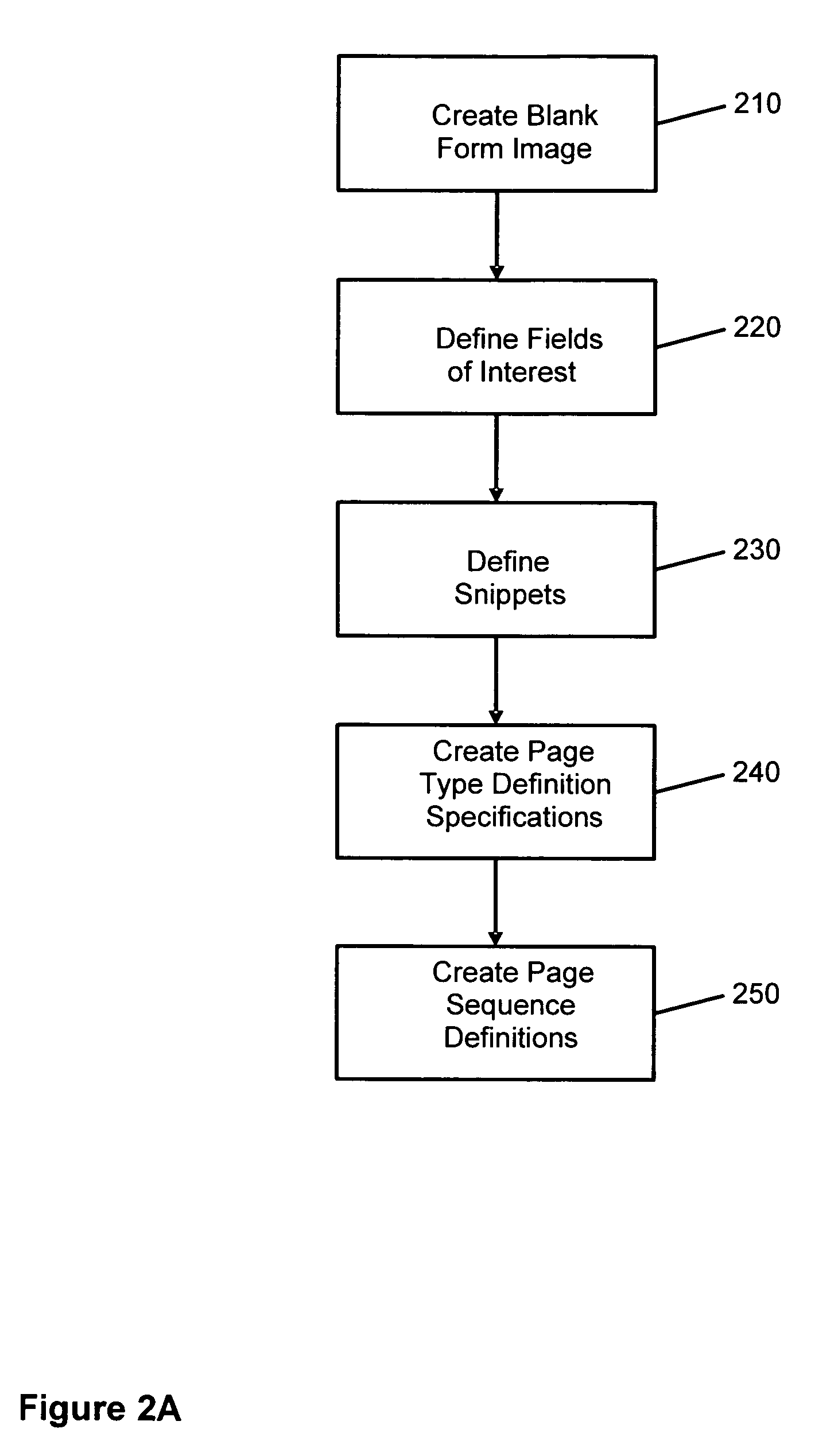
System and method for electronically processing document images
InactiveUS20060190489A1Easy to controlEasy to manageDigital data processing detailsCharacter and pattern recognitionElectronic documentPaper document
The system and method facilitate the control and management of information and actions related to the computerized scanning, categorization, processing, storage, and retrieval of paper documents and electronic document images for the purposes of creating electronic data; data entry; data capture; data classification and categorization; and document-, file-, and records-management. The systems and methods facilitate the conversion of paper documents into electronic images and into more useful forms.
Owner:ICHANNEX CORP
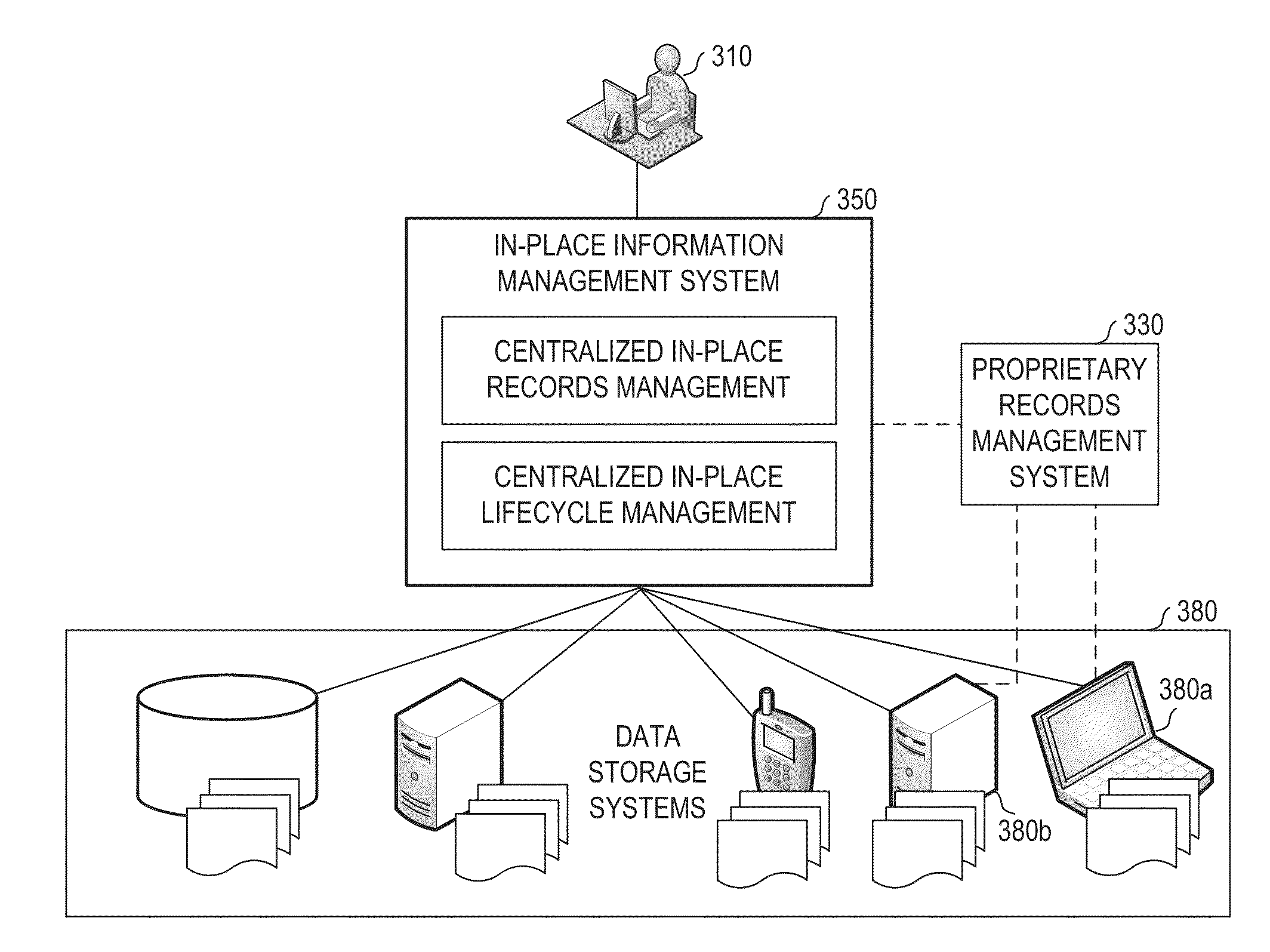
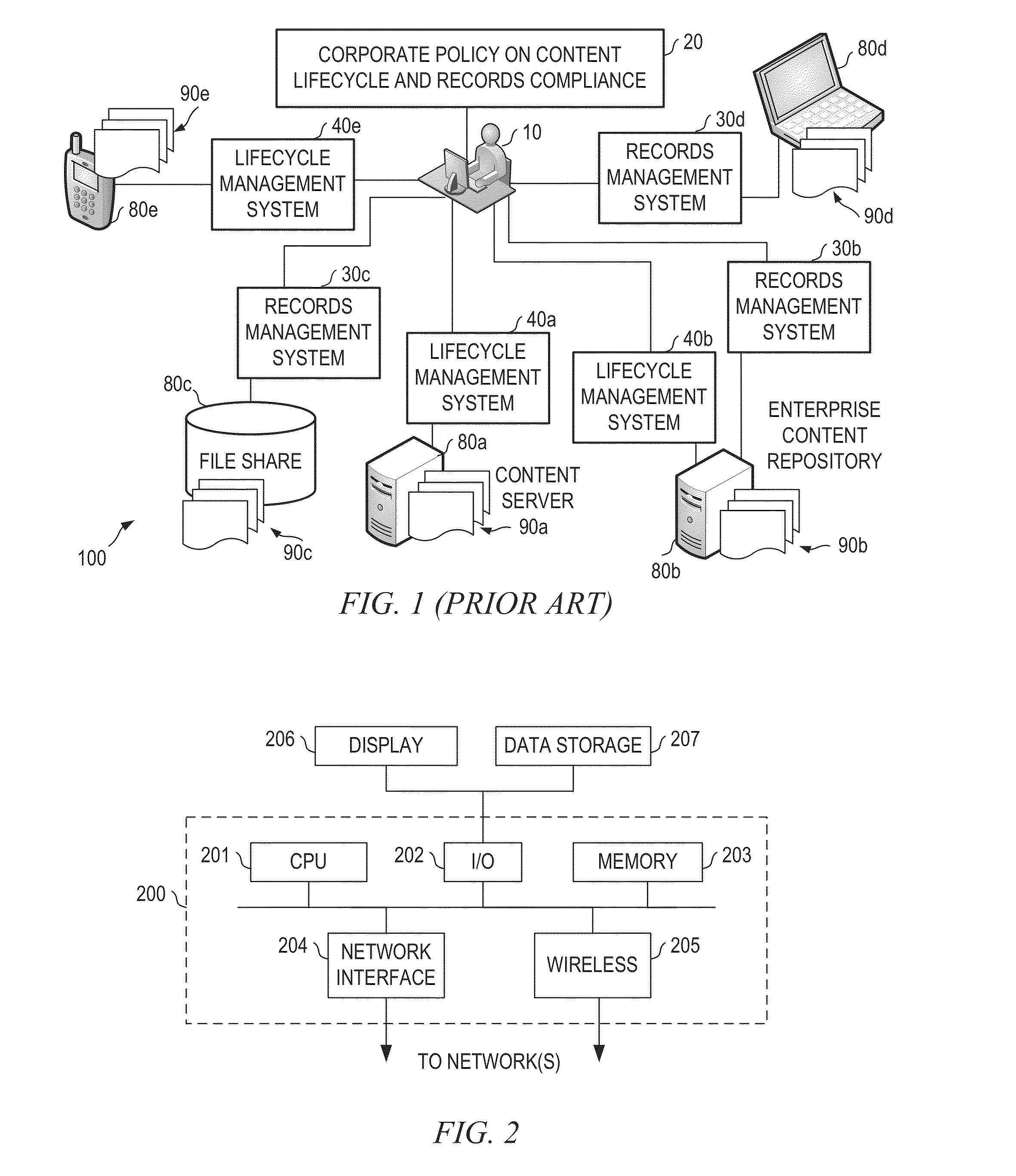
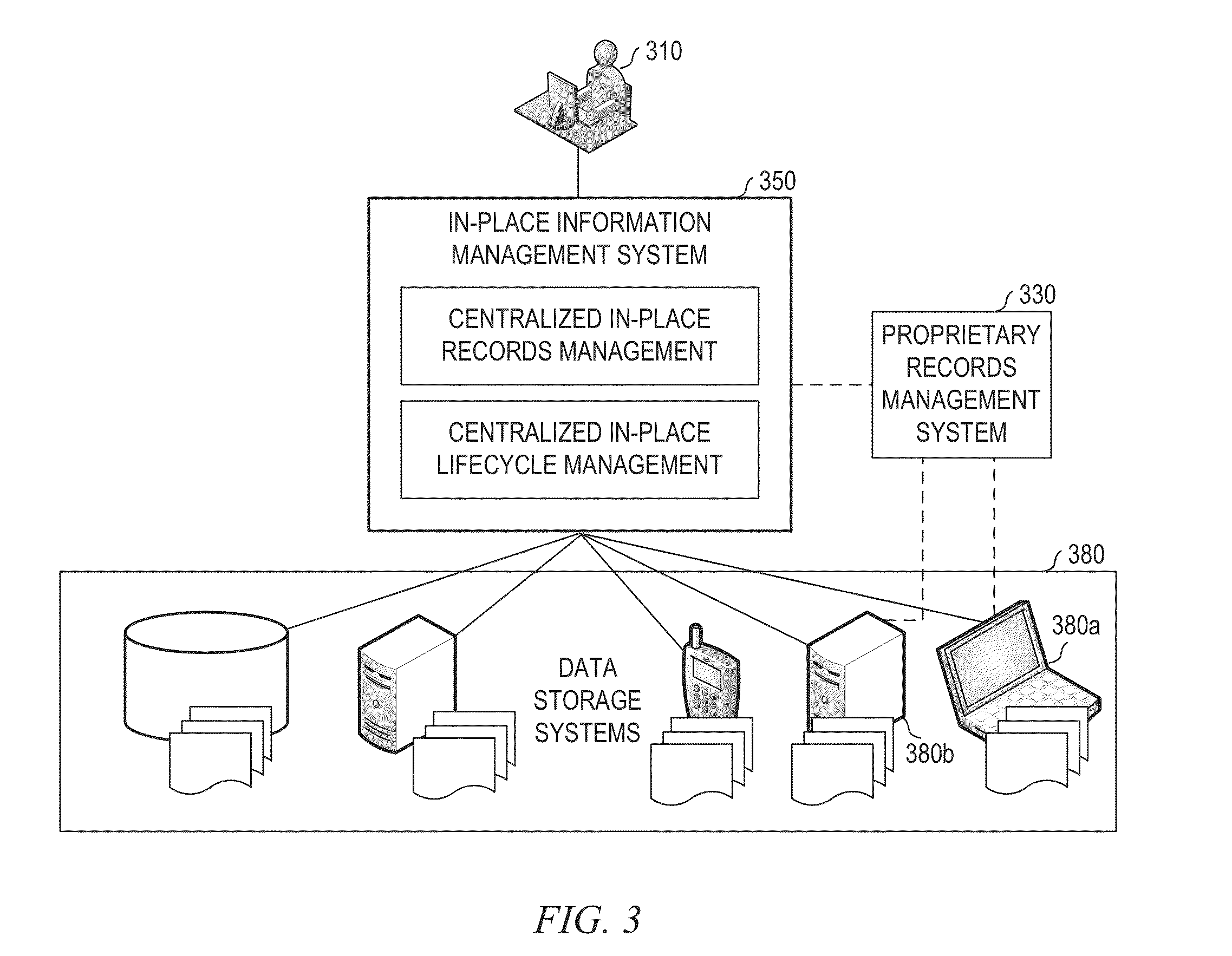
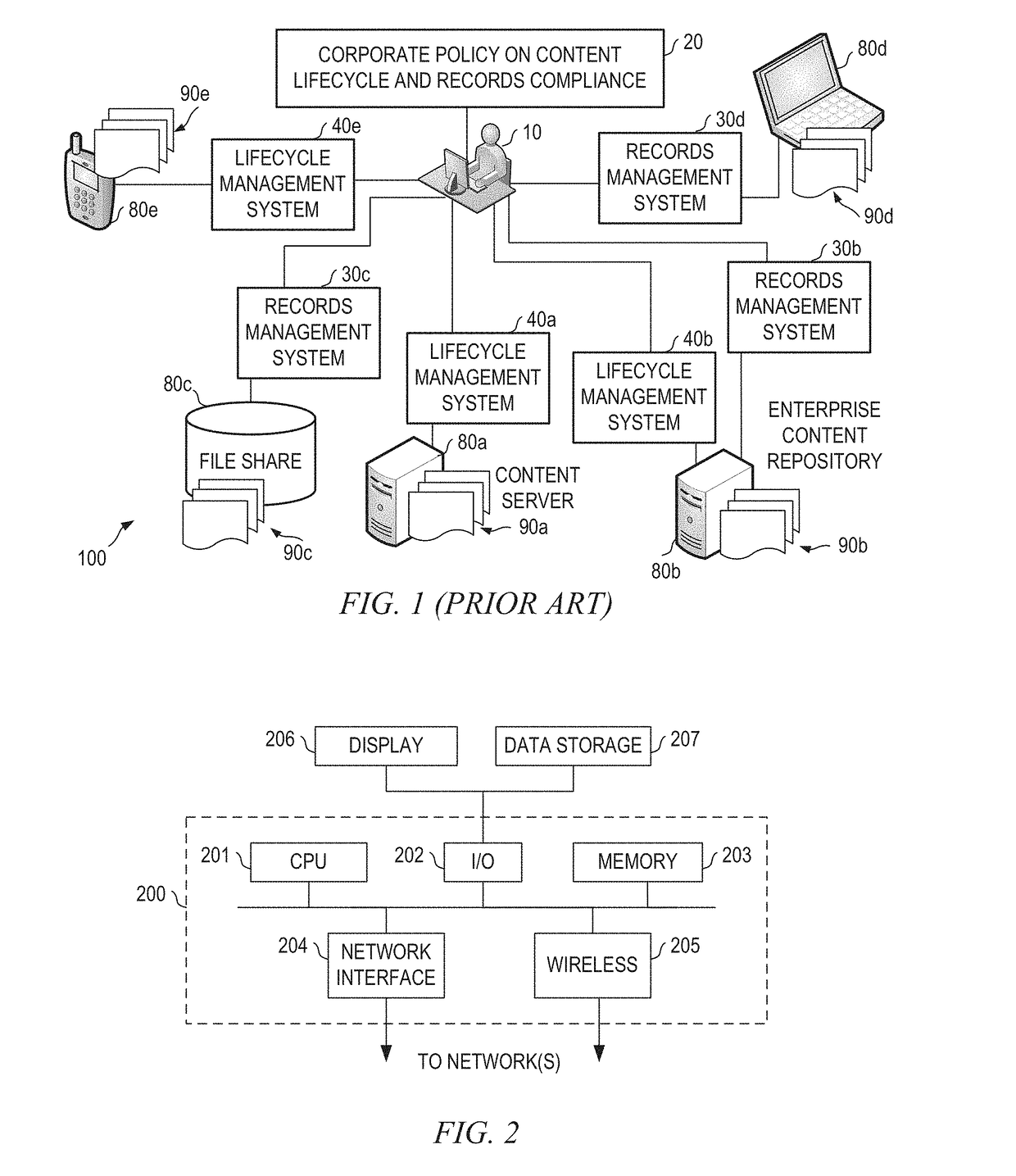
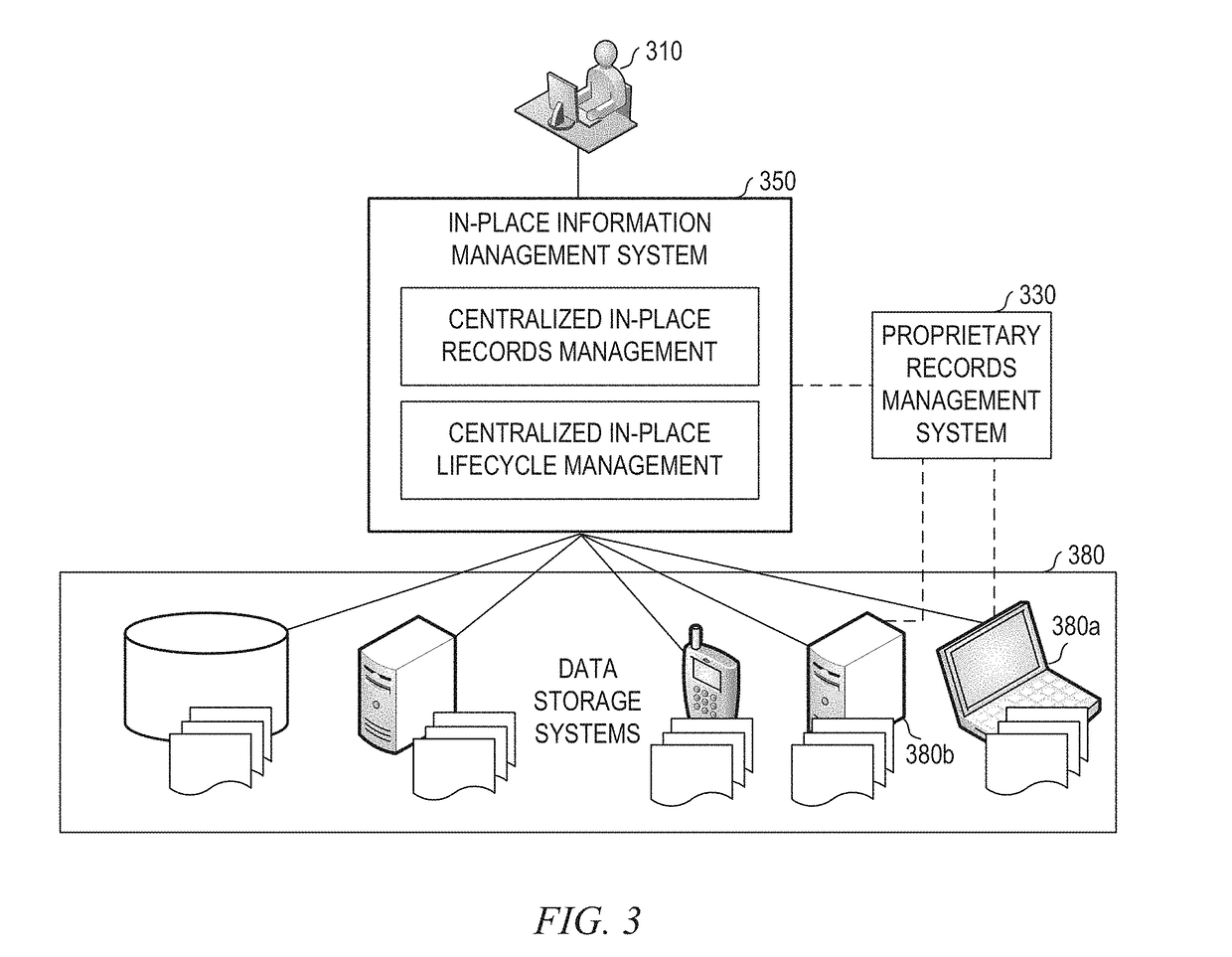
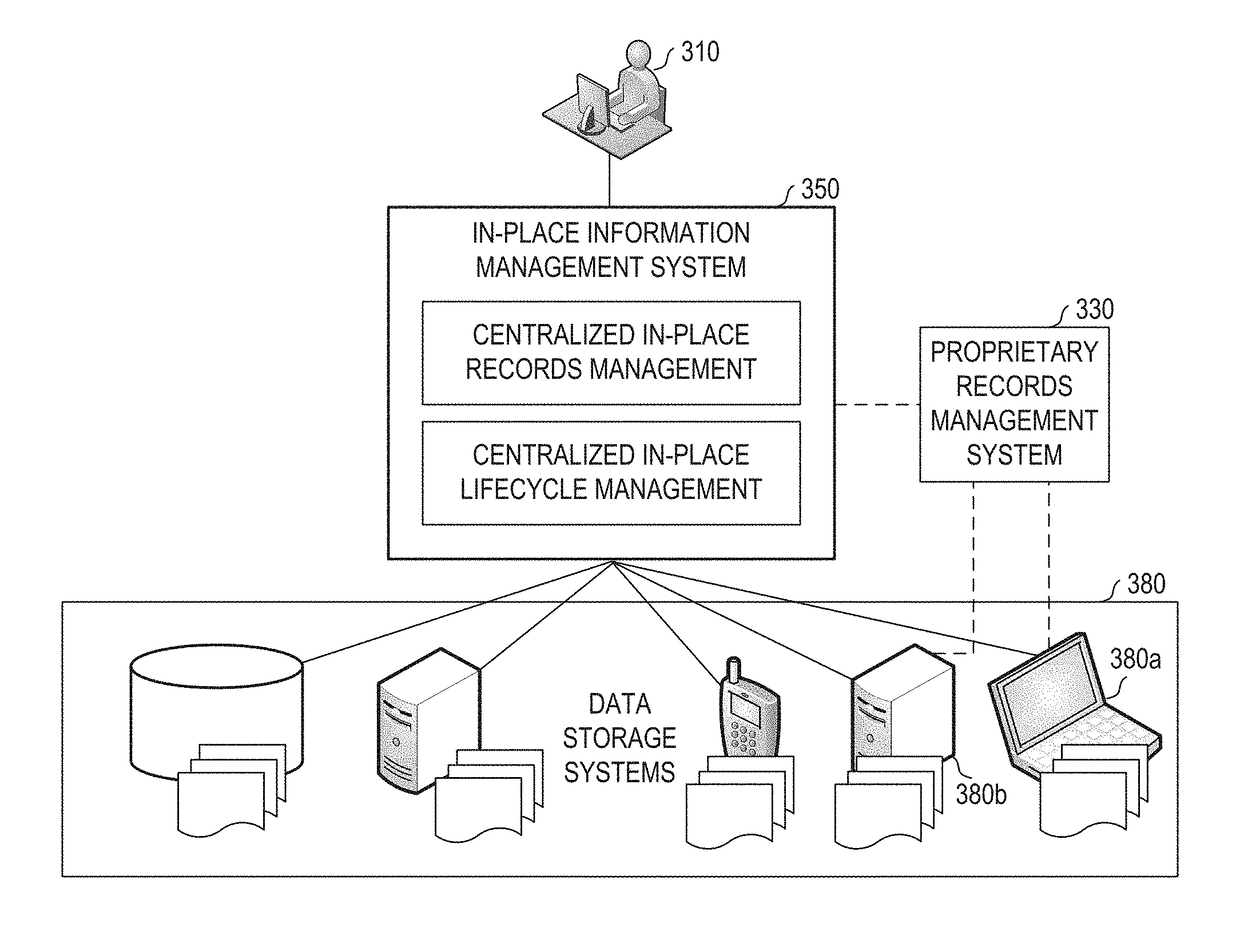
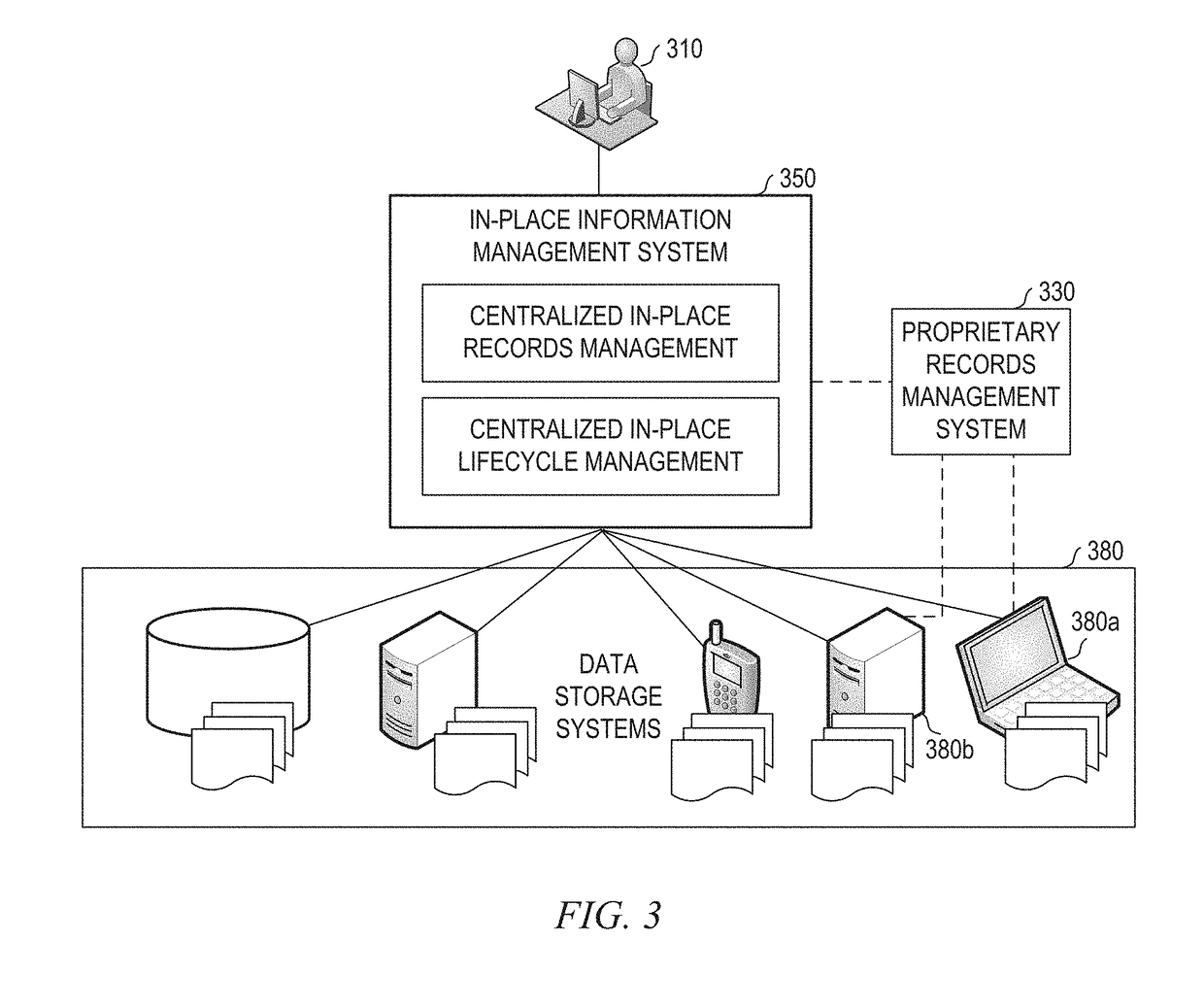
Systems and methods for in-place records management and content lifecycle management
ActiveUS20140019426A1Reduced and minimized and more manageable numberDatabase management systemsDigital data processing detailsApplication lifecycle managementCorporate policy
An in-place information management system having a management application built on a common data model and configured for asynchronous query-based application of policies on content stored in the disparate data storage systems through a query interface which may be part of a set of integration services. The common data model may be configured based on common architectures of the disparate data storage systems. The query interface may be configured for running a query on a data storage system in response to a search request received by the management application from a records manager and for mapping semantically equalivant keys from disparate data storage systems to a key in the common data model. The query may define a set of records to be treated similarly according to corporate policy on content lifecycle and records compliance.
Owner:OPEN TEXT SA ULC
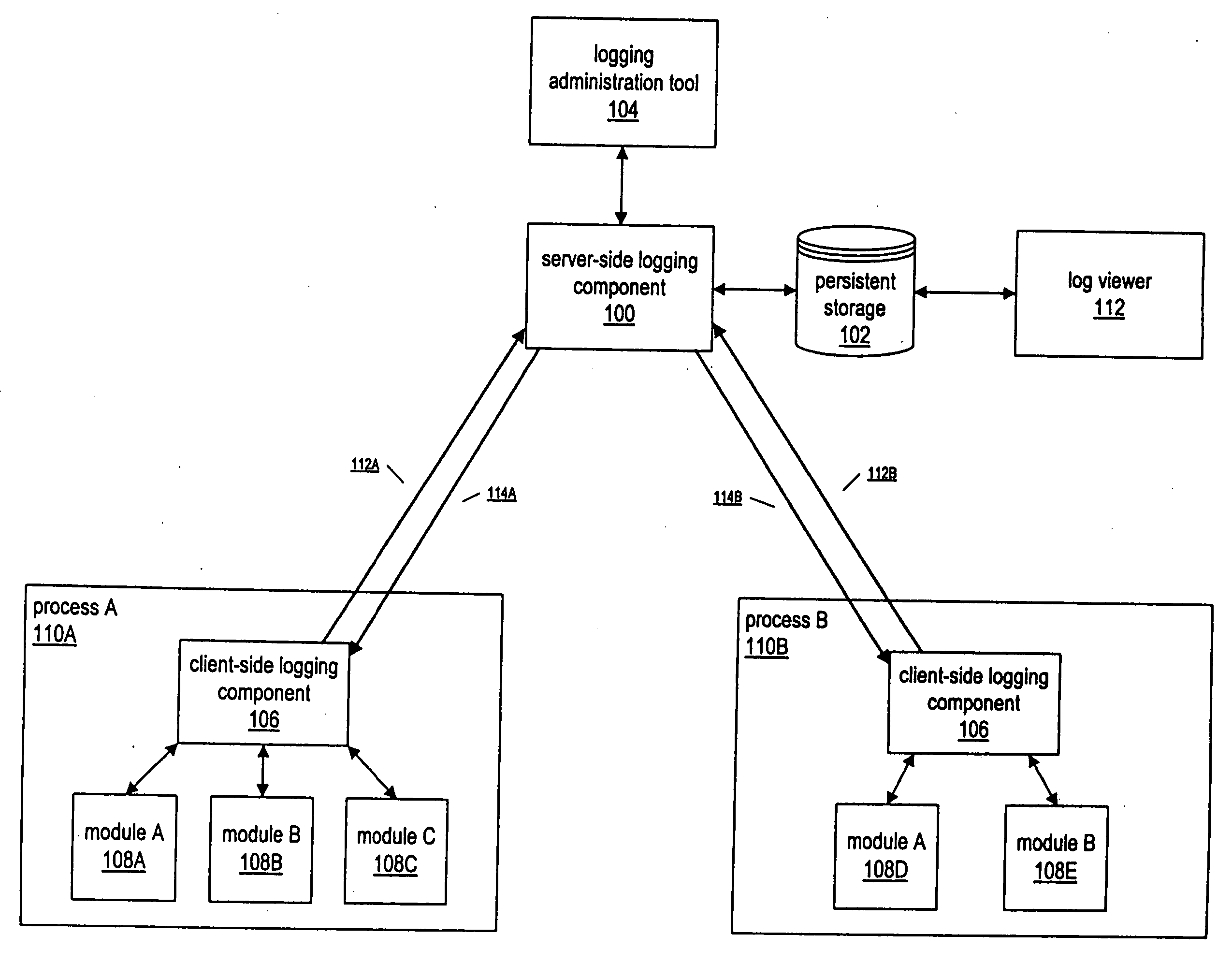
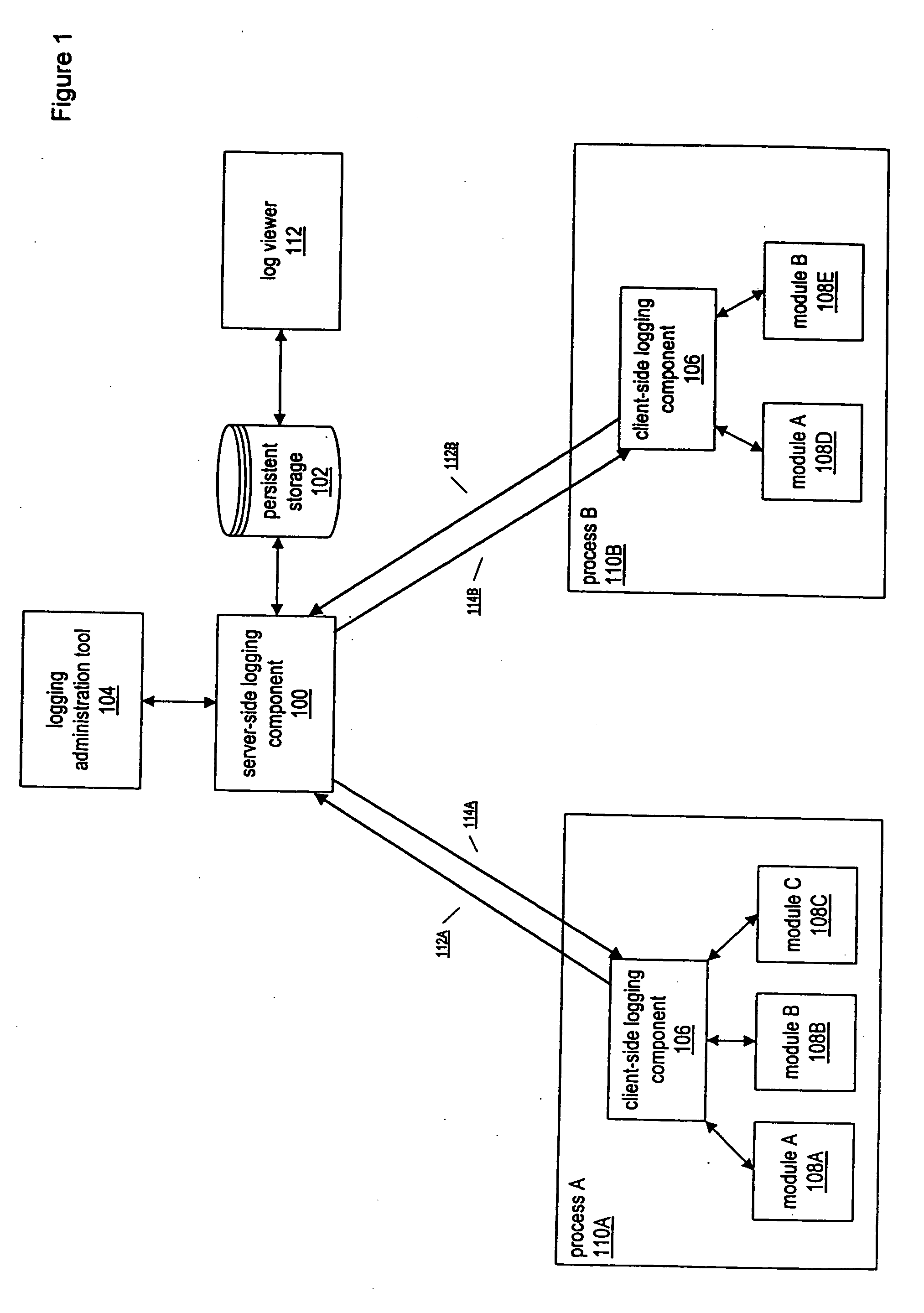
System and method enabling multiple processes to efficiently log events
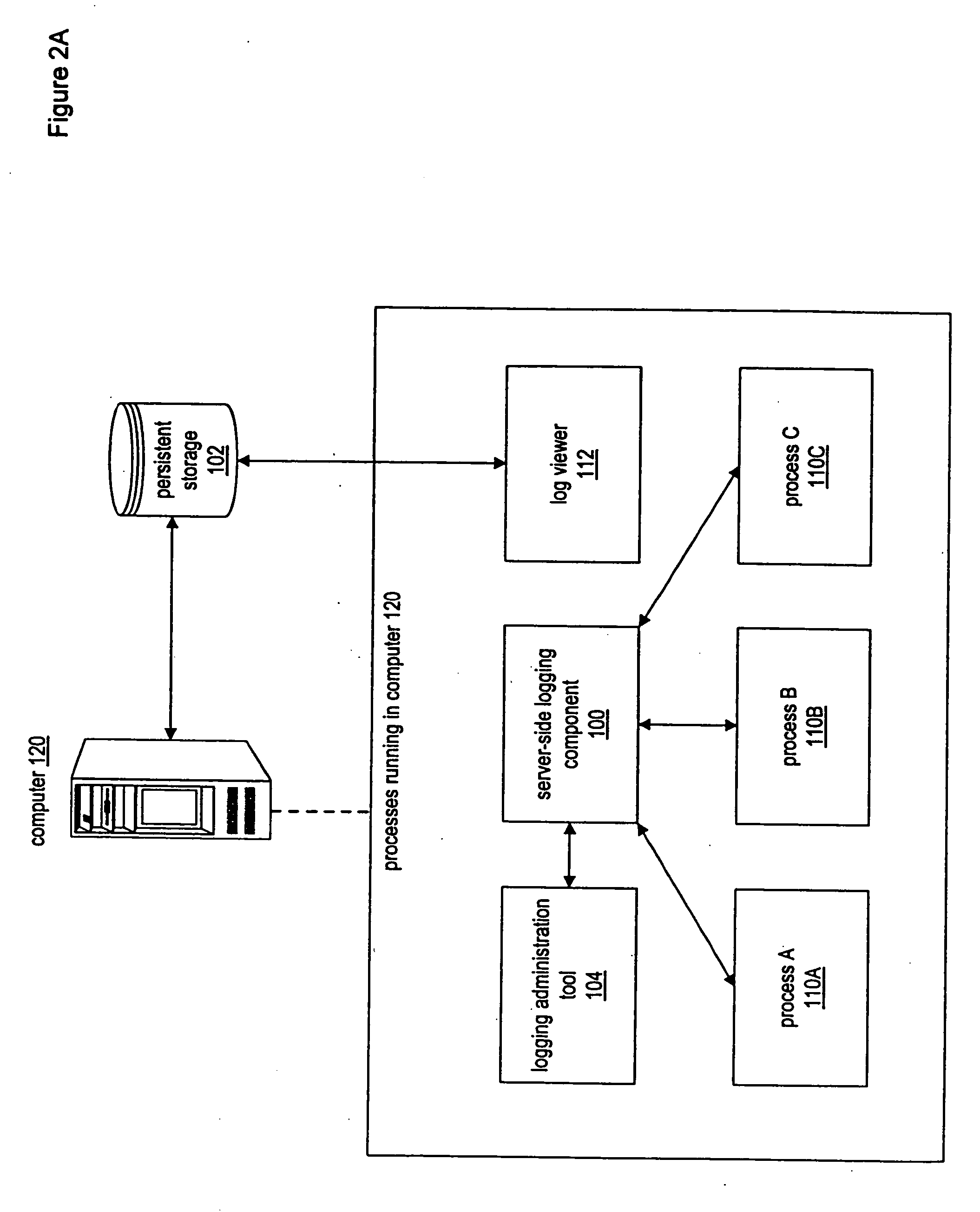
InactiveUS20050028171A1Efficiently log eventError detection/correctionProgram controlInformation dispersalEvent level
A system and method for enabling multiple processes to efficiently log events is described. A client executable module that needs to log an event may interface with a module or component referred to as a “client-side logging component”, passing various types of information regarding the event, such as an associated event level, one or more event associated event categories, an informational message, etc. The client-side logging component may maintain event logging criteria specifying which types of events should be logged. If the event should be logged, the client-side logging component may queue the event information and return execution control the client module. The event information may then be asynchronously retrieved from the event queue and sent to a server-side logging component. The server-side logging component may persistently log the event information in any of various ways, e.g., by storing it in a file, a database, etc. Processes running on multiple computers may call the server-side logging component to log events, via a client-side logging component instance associated with the process. A logging administration tool may be utilized in order to set event logging criteria. In response to being configured with new event logging criteria information, the server-side logging component may automatically propagate the logging criteria information to each of the client-side logging components. The client-side logging components may then being using the new logging criteria, dynamically changing the filtering of events that are sent to the server-side logging component.
Owner:KOUGIOURIS PANAGIOTIS +1
Transformer station three-dimensional real scene simulation system and implementation method
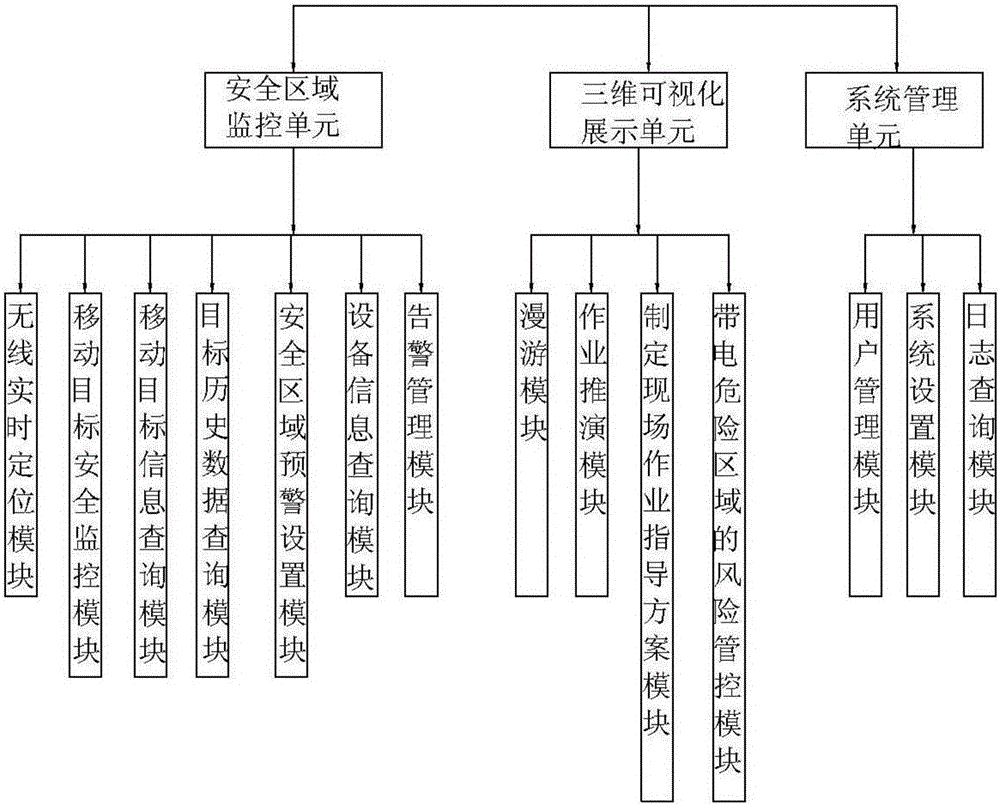
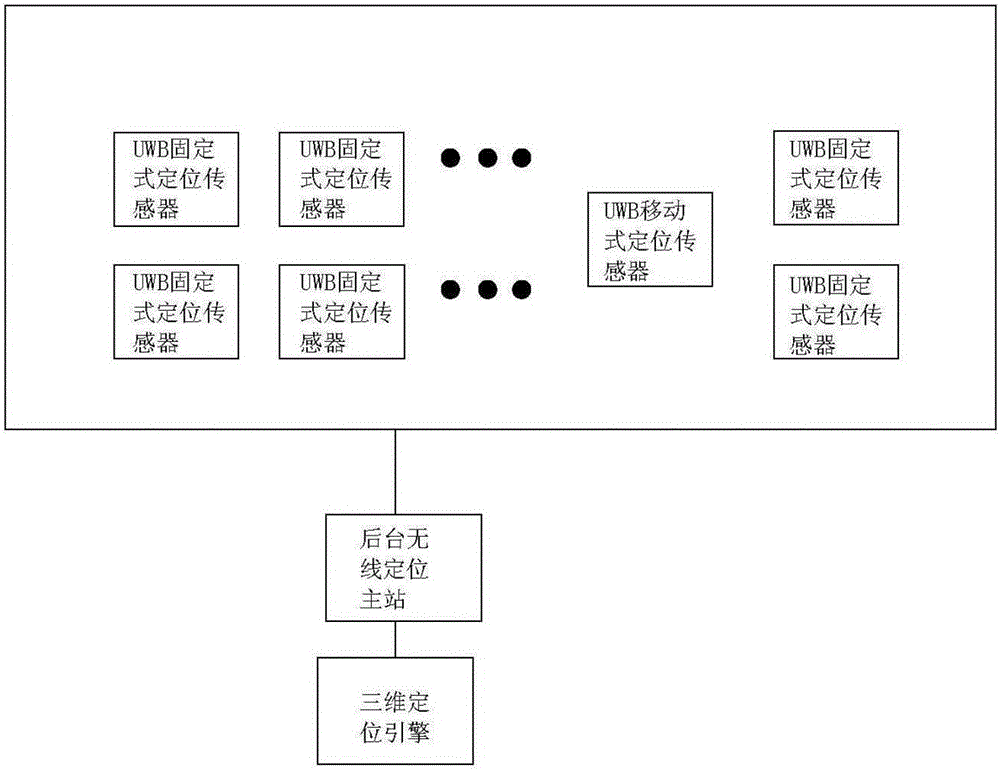
ActiveCN105956232ARealize 3D dynamic displayAvoid missingData processing applicationsDesign optimisation/simulationSystems managementTransformer
The invention relates to a transformer station three-dimensional real scene simulation system and an implementation method. The system comprises a safety region monitoring unit, a three-dimensional visualization display unit, and a system management unit. The safety region monitoring unit comprises a wireless real-time positioning module using a UWB positioning technology, a moving target security monitoring module, a moving target information query module, a target historical data query module, a safety region early warning setting module, an equipment information query module, and an alarm management module. The three-dimensional visualization display unit comprises a roaming module, an operation deduction module, a field operation instruction scheme making module, and a risk management and control module of an electrified dangerous region. The system management unit comprises a user management module, a system setting module, and a log query module. The system realizes functions of daily inspection and maintenance visual management of a transformer station, operating personnel daily inspection and maintenance process real-time tracking and monitoring, security alert alarm and intelligent recording management.
Owner:WUHAN NARI LIABILITY OF STATE GRID ELECTRIC POWER RES INST +1
Systems and methods for in-place records management and content lifecycle management
ActiveUS9798737B2Reduced and minimized and more manageable numberDatabase management systemsSpecial data processing applicationsApplication softwareRecords management
An in-place information management system having a management application built on a common data model and configured for asynchronous query-based application of policies on content stored in the disparate data storage systems through a query interface which may be part of a set of integration services. The common data model may be configured based on common architectures of the disparate data storage systems. The query interface may be configured for running a query on a data storage system in response to a search request received by the management application from a records manager and for mapping semantically equalivant keys from disparate data storage systems to a key in the common data model. The query may define a set of records to be treated similarly according to corporate policy on content lifecycle and records compliance.
Owner:OPEN TEXT SA ULC
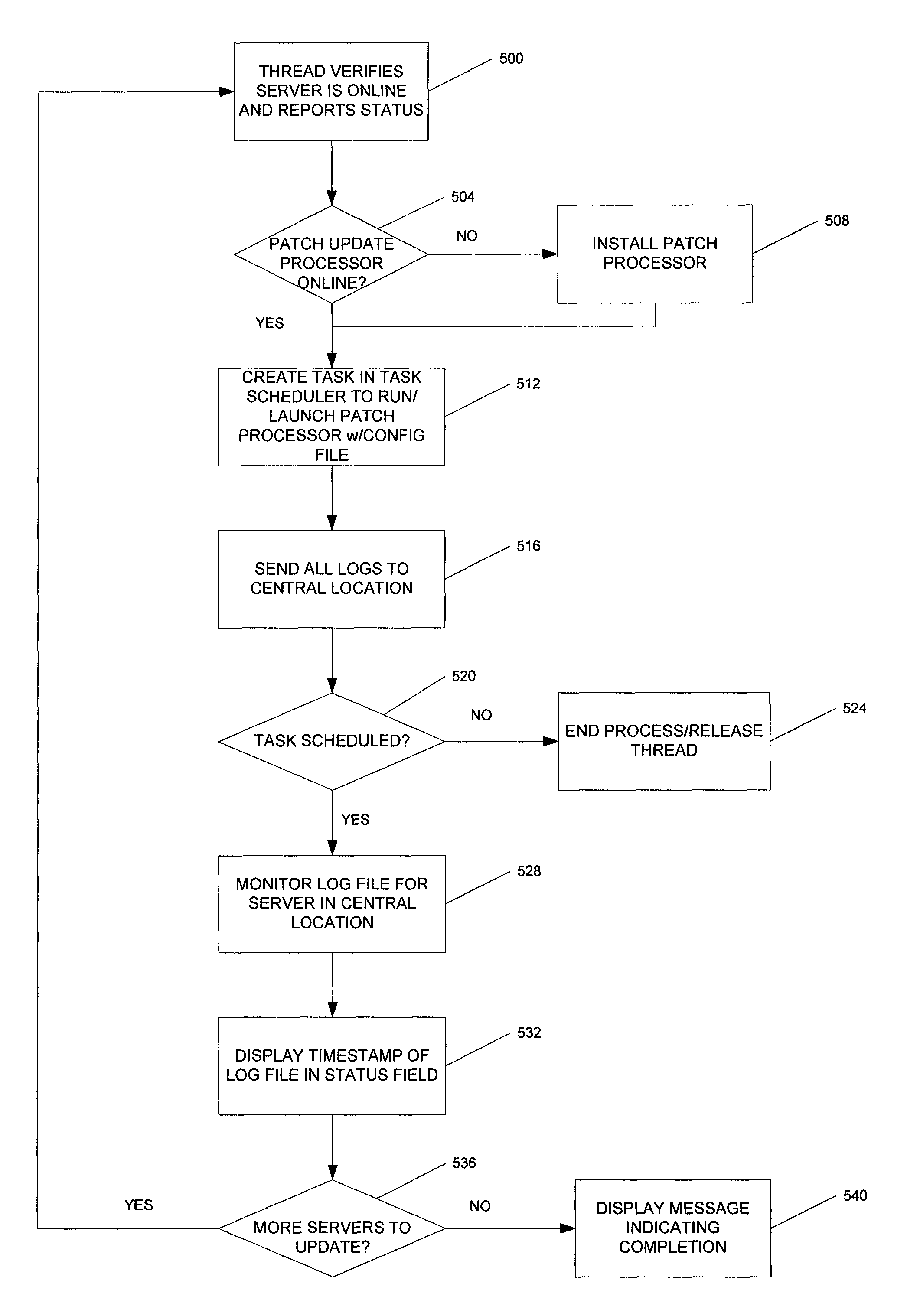
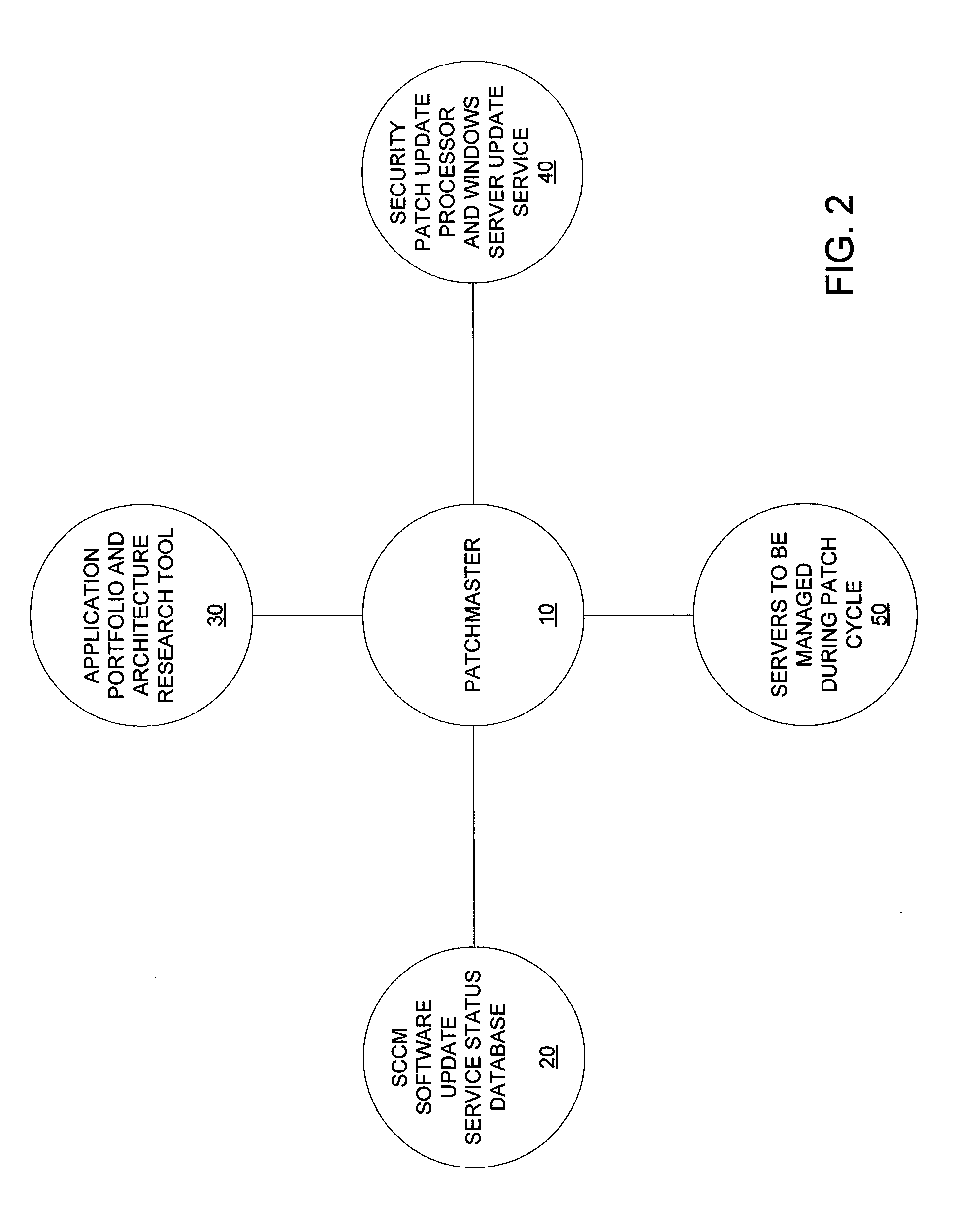
Patch cycle master records management and server maintenance system
ActiveUS8296756B1Reduce gapSoftware engineeringSpecific program execution arrangementsBusiness enterpriseEnterprise computing
A method, system, and computer readable storage medium for managing the deployment of software patch updates on a plurality of computers in an enterprise computer network during a patch cycle wherein each computer receives and installs periodic software patch updates automatically. An inventory is maintained of the computers in a central database that stores a status of each computer for each patch during the patch cycle. The computers are filtered into at least one filter group and a list of computers in the filter group is displayed along with the status for each patch. The status of each patch is verified and displayed for each computer in the filter group. A controlled software patch update is performed for each non-compliant computer in the filter group. A controlled reboot of each computer in the filter group is performed following the completion of the software patch updates for the patch cycle.
Owner:SOUTHERN COMPANY SERVICES
Systems and methods for in-place records management and content lifecycle management
ActiveUS20180025027A1Reduced and minimized and more manageable numberDatabase management systemsSpecial data processing applicationsCorporate policyIntegration service
An in-place information management system having a management application built on a common data model and configured for asynchronous query-based application of policies on content stored in the disparate data storage systems through a query interface which may be part of a set of integration services. The common data model may be configured based on common architectures of the disparate data storage systems. The query interface may be configured for running a query on a data storage system in response to a search request received by the management application from a records manager and for mapping semantically equalivant keys from disparate data storage systems to a key in the common data model. The query may define a set of records to be treated similarly according to corporate policy on content lifecycle and records compliance.
Owner:OPEN TEXT SA ULC
Method and apparatus for utilizing dynamic bandwidth allocation for recording content
InactiveUS20110083154A1Two-way working systemsSelective content distributionDynamic bandwidth allocationRecords management
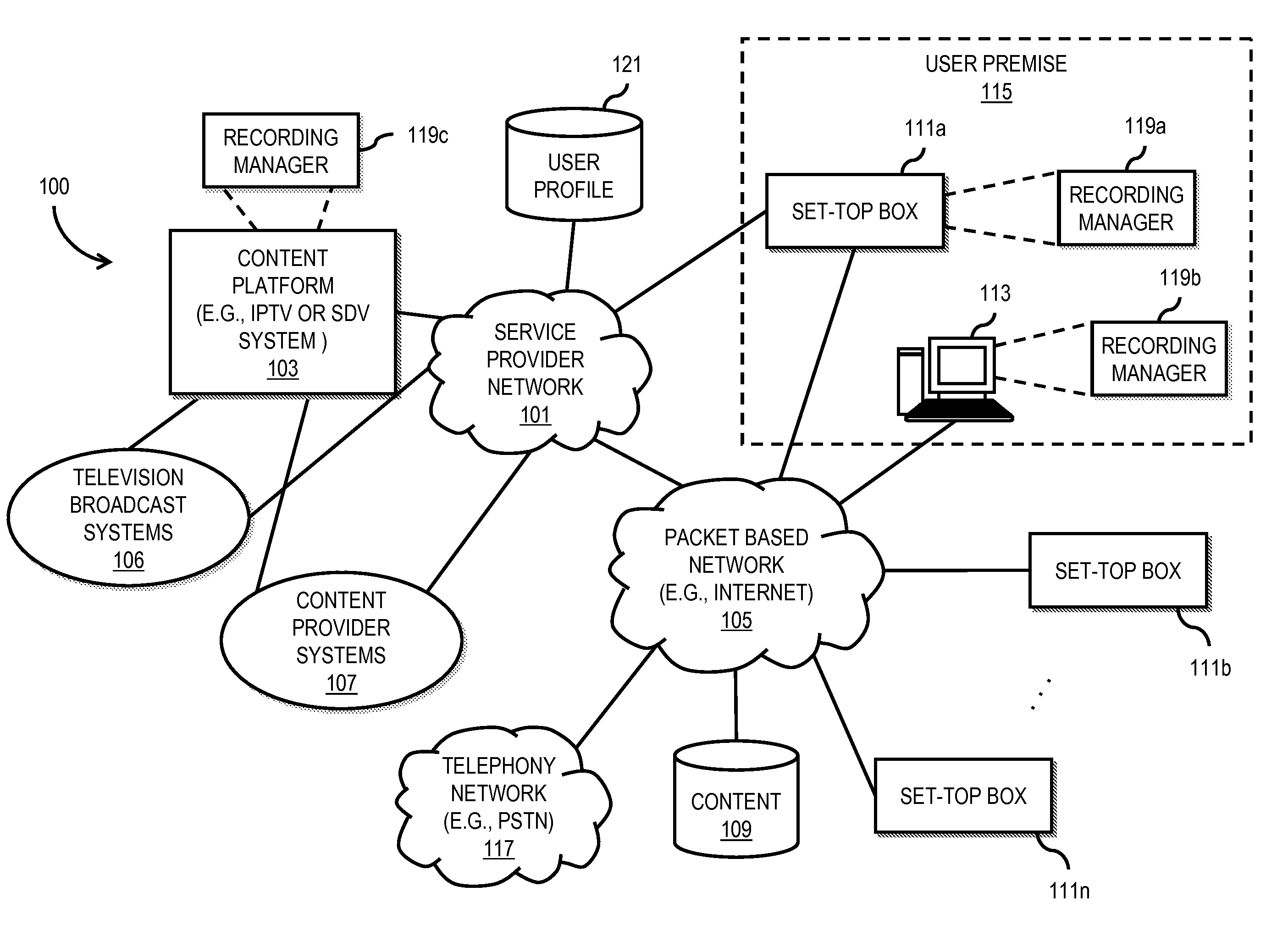
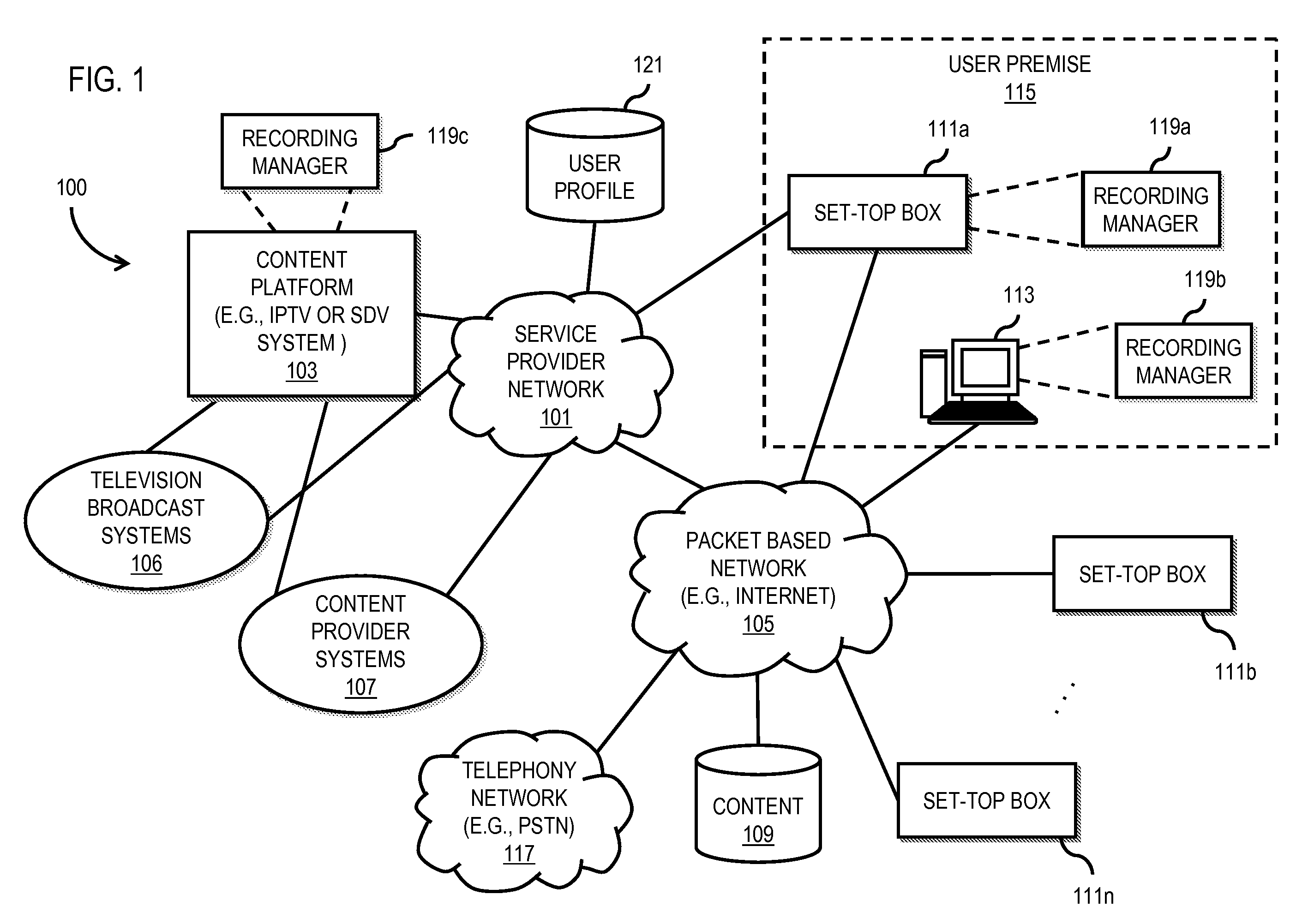
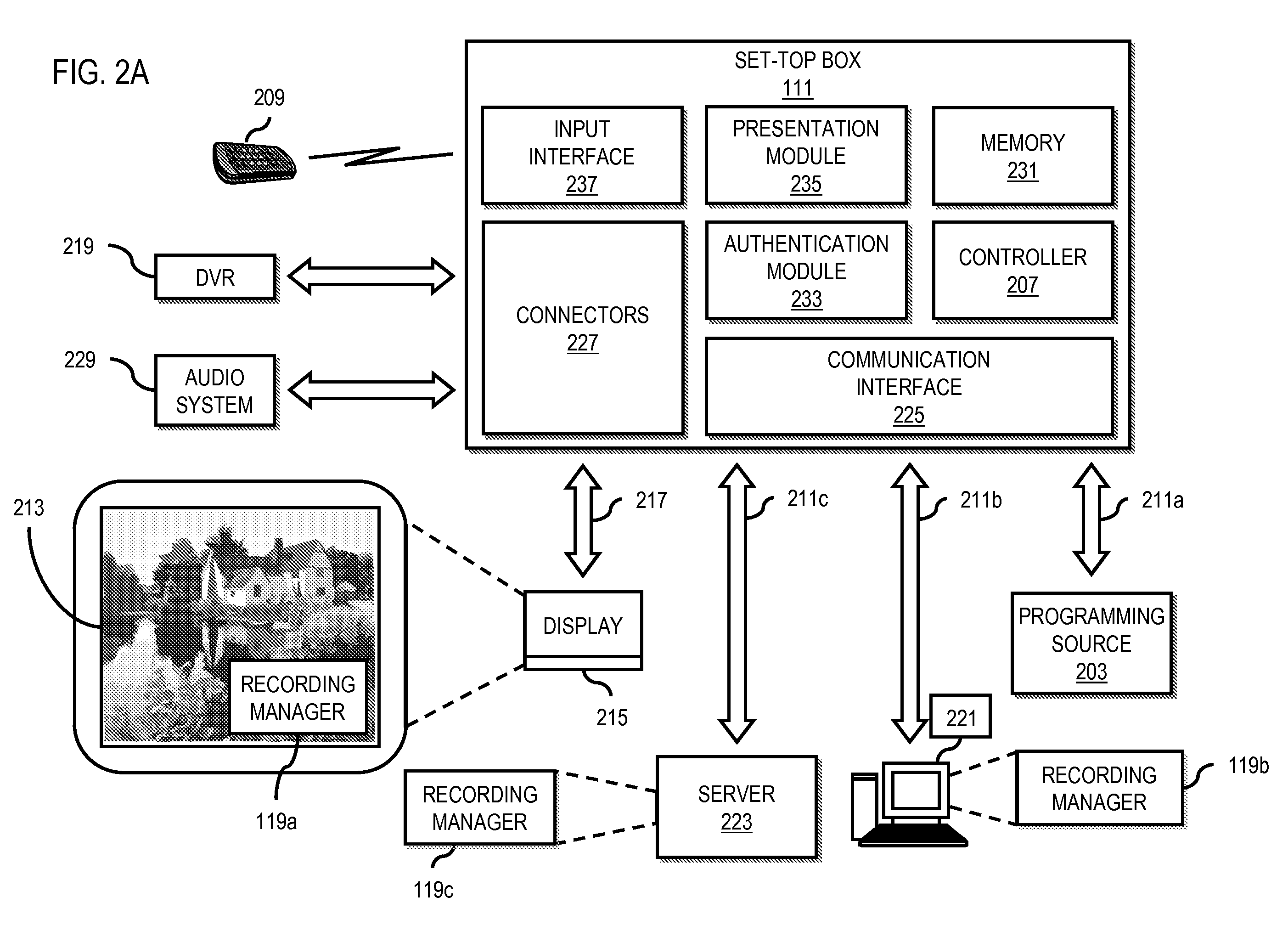
An approach is provided for utilizing dynamic bandwidth allocation for recording content. A recording manager generates a request for bandwidth for a future recording of a programming content to be delivered to a set-top box. The recording manager then receives a response indicating a dynamic bandwidth allocation for the future recording and schedules the future recording of the programming content based on the dynamic bandwidth allocation.
Owner:VERIZON PATENT & LICENSING INC
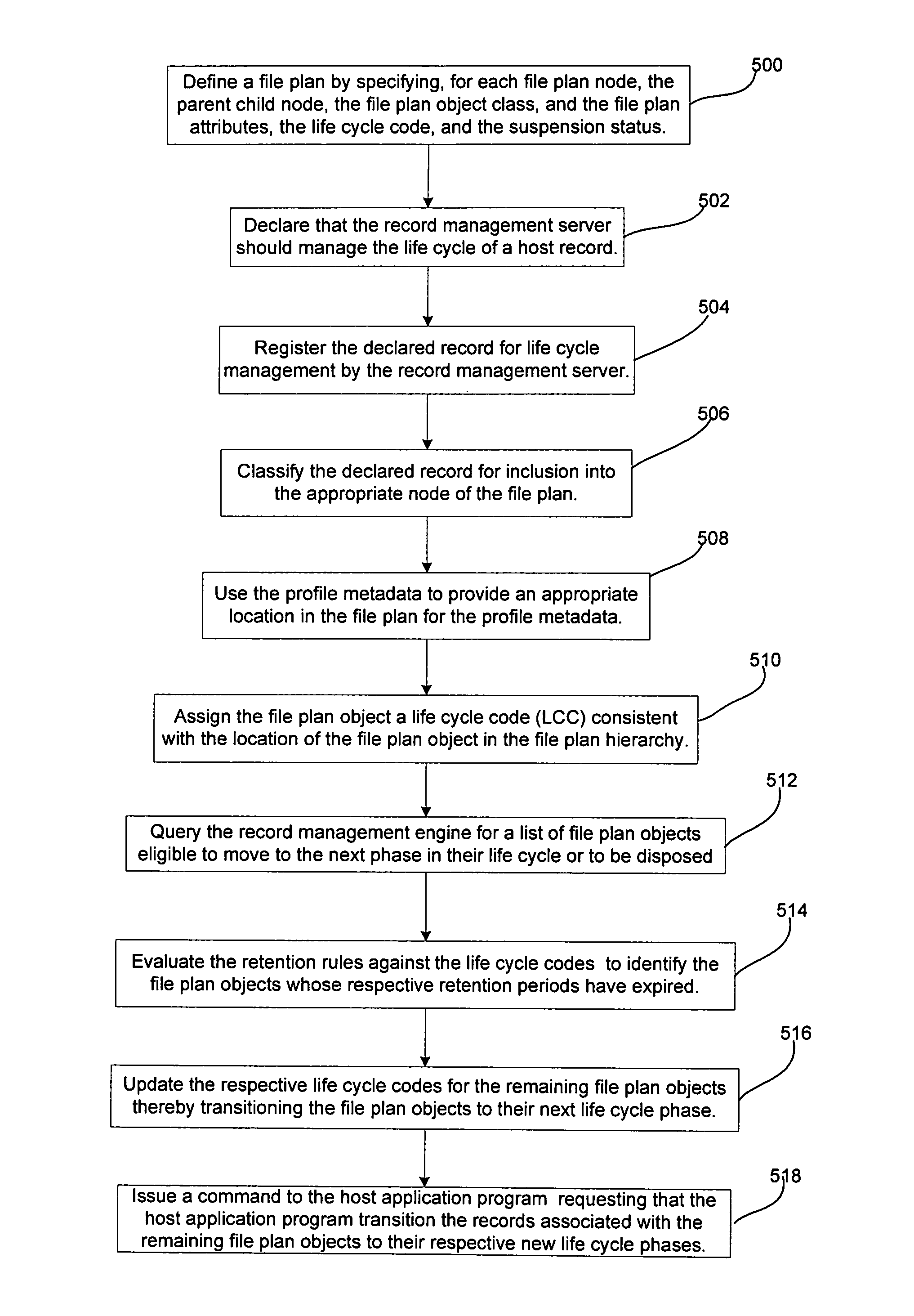
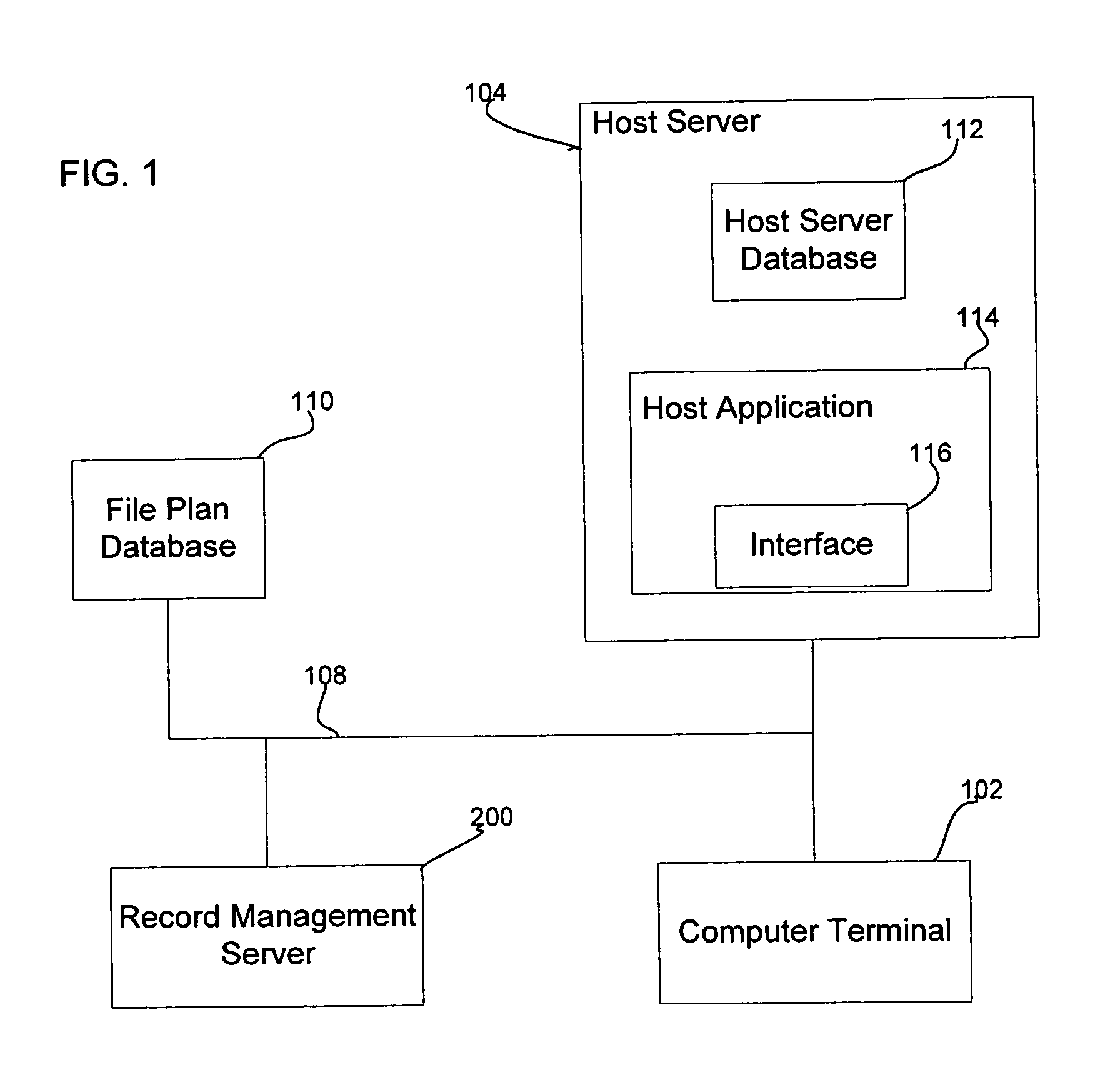
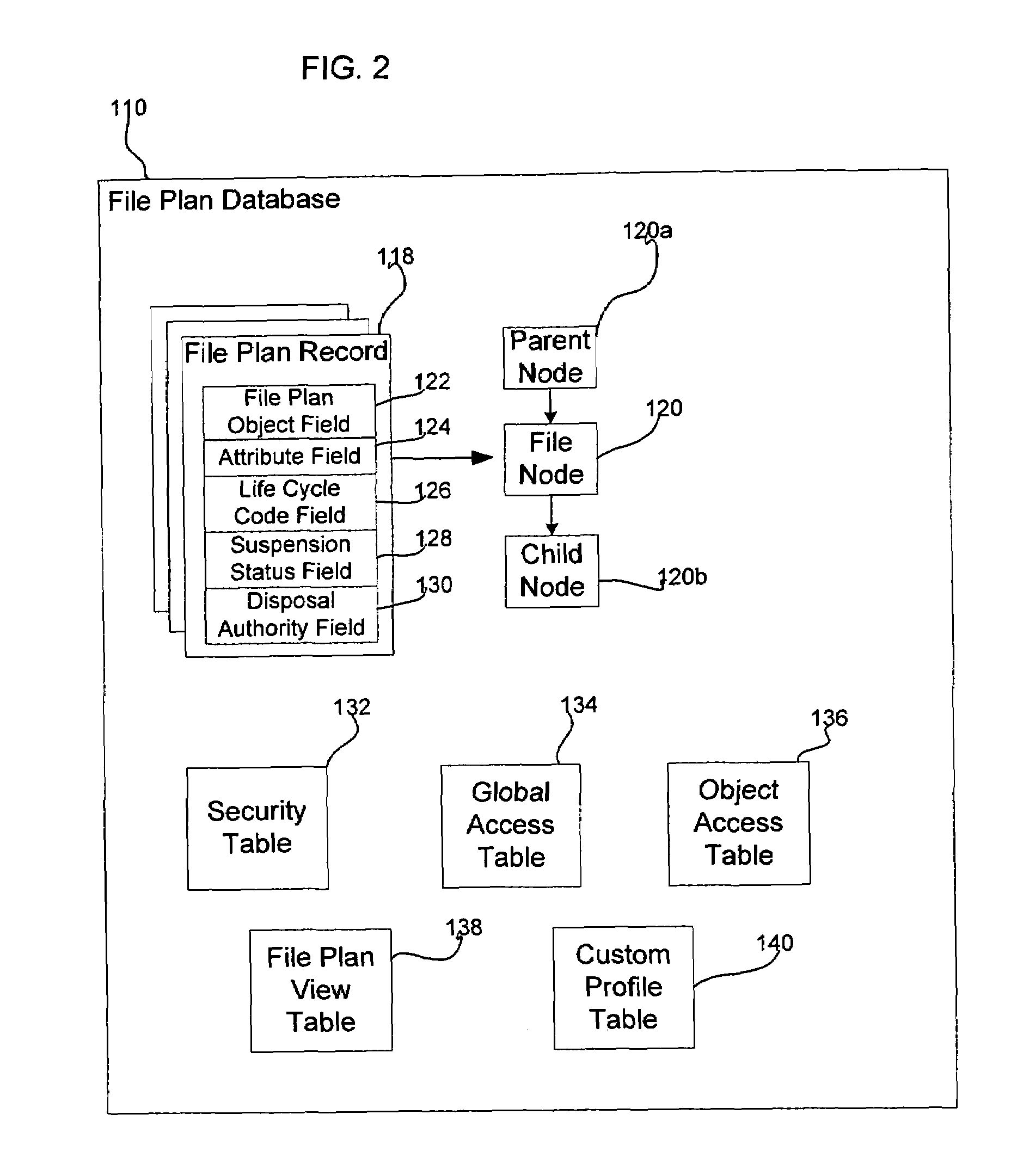
Life-cycle management engine
ActiveUS7233959B2Data processing applicationsStructured data retrievalProgram managementApplication software
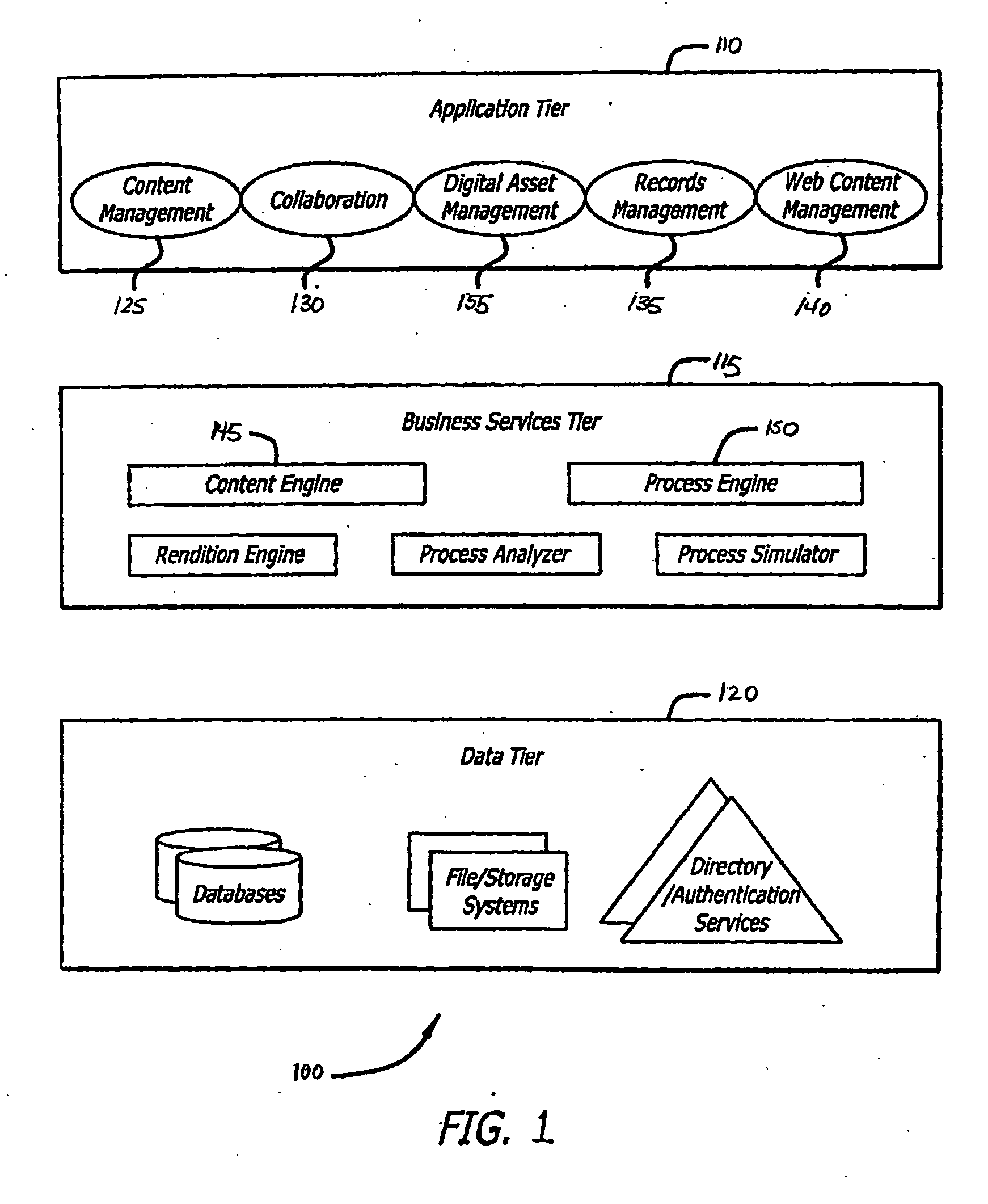
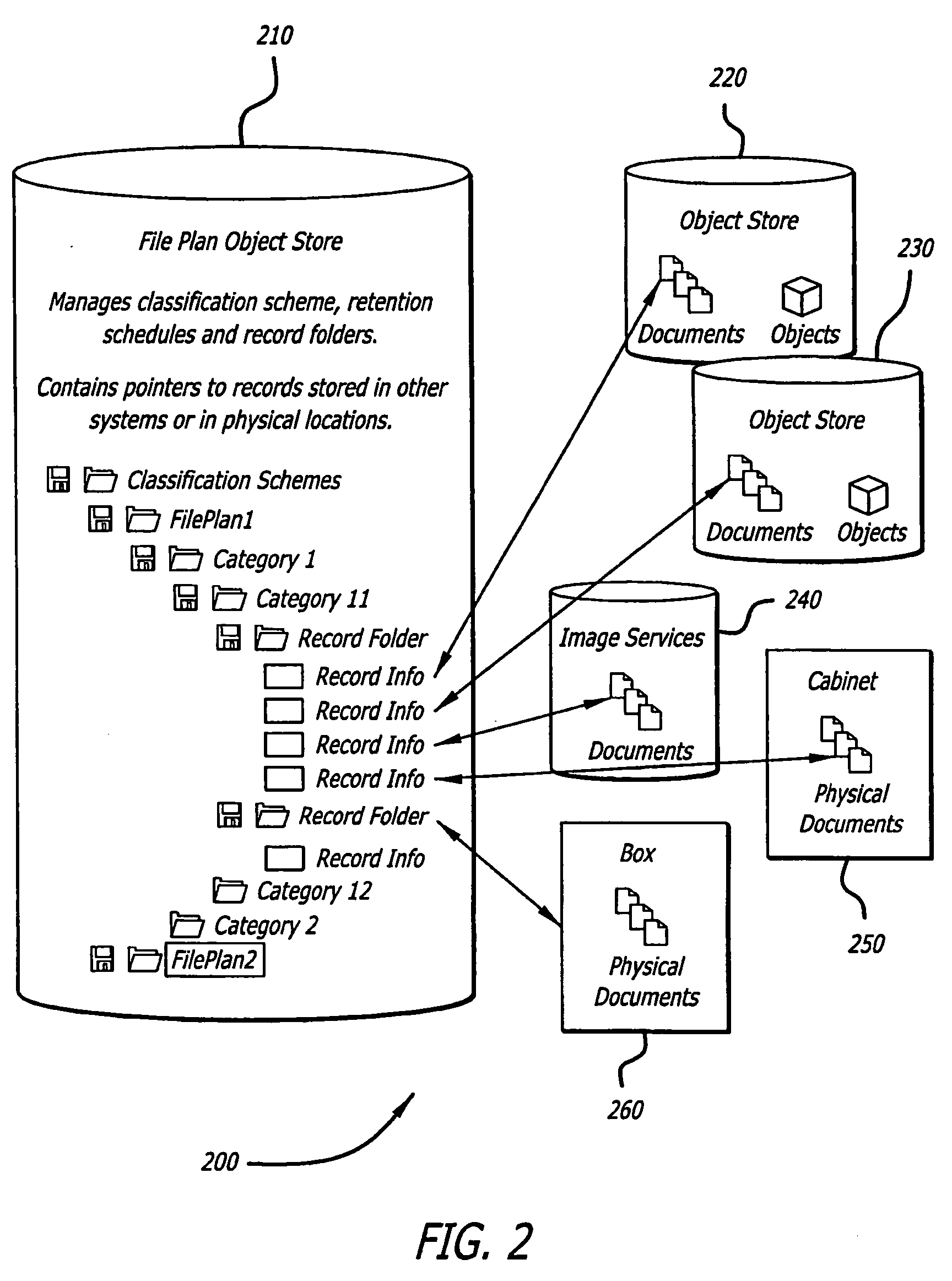
A records manager manages life cycle phases of records managed by a host application program. The records manager is in communication with the host application program over a network and includes a file plan database, a record management engine and an application program interface. The file plan database includes at least one file plan object, with each file plan object having a life cycle rule. The record management engine is configured to manage life cycle states of the record. The application program interface is in communication with the record management engine and is configured to transmit to the host application program over the network indications of changes in the life cycle phases.
Owner:IBM CANADA LTD
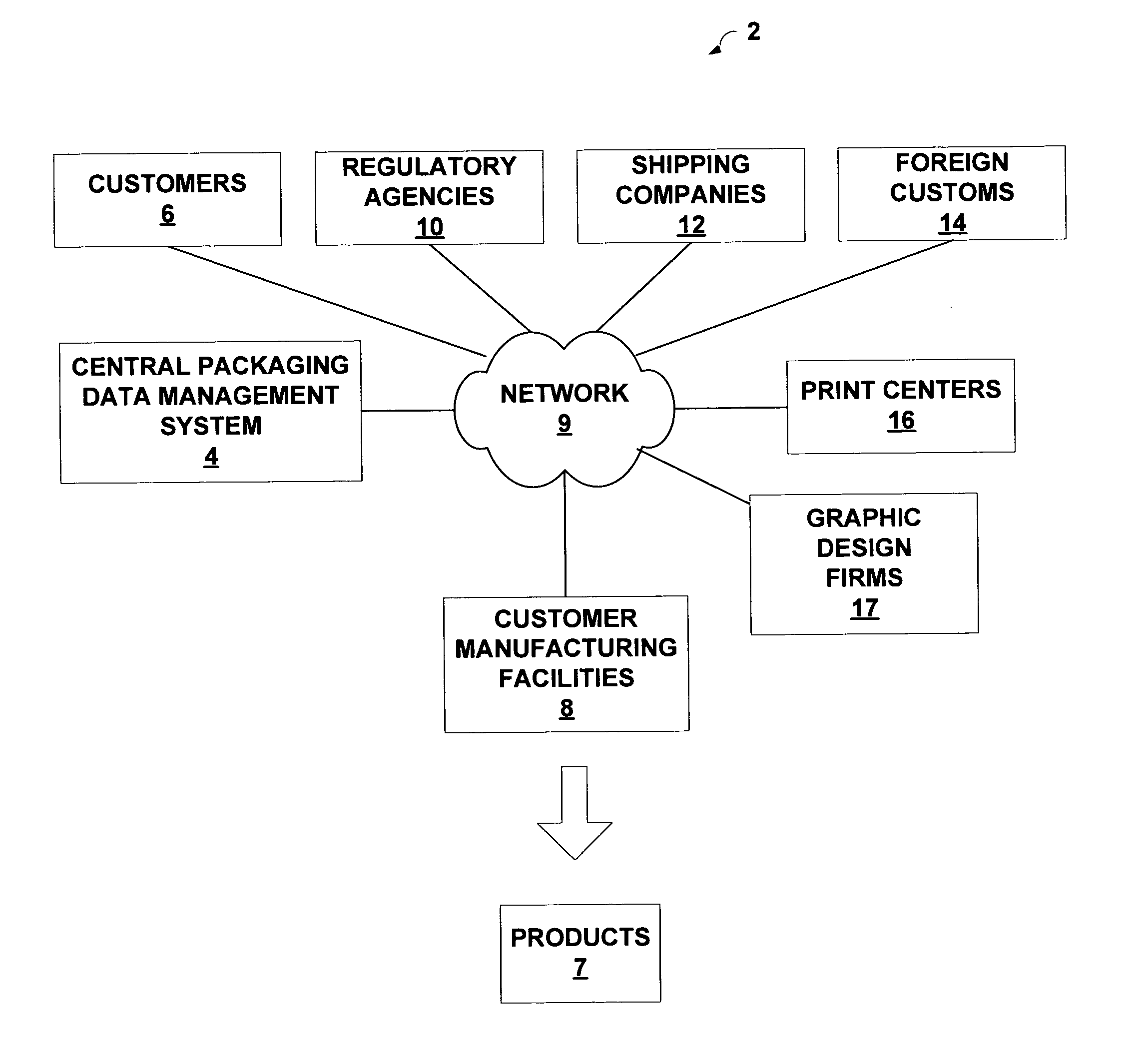
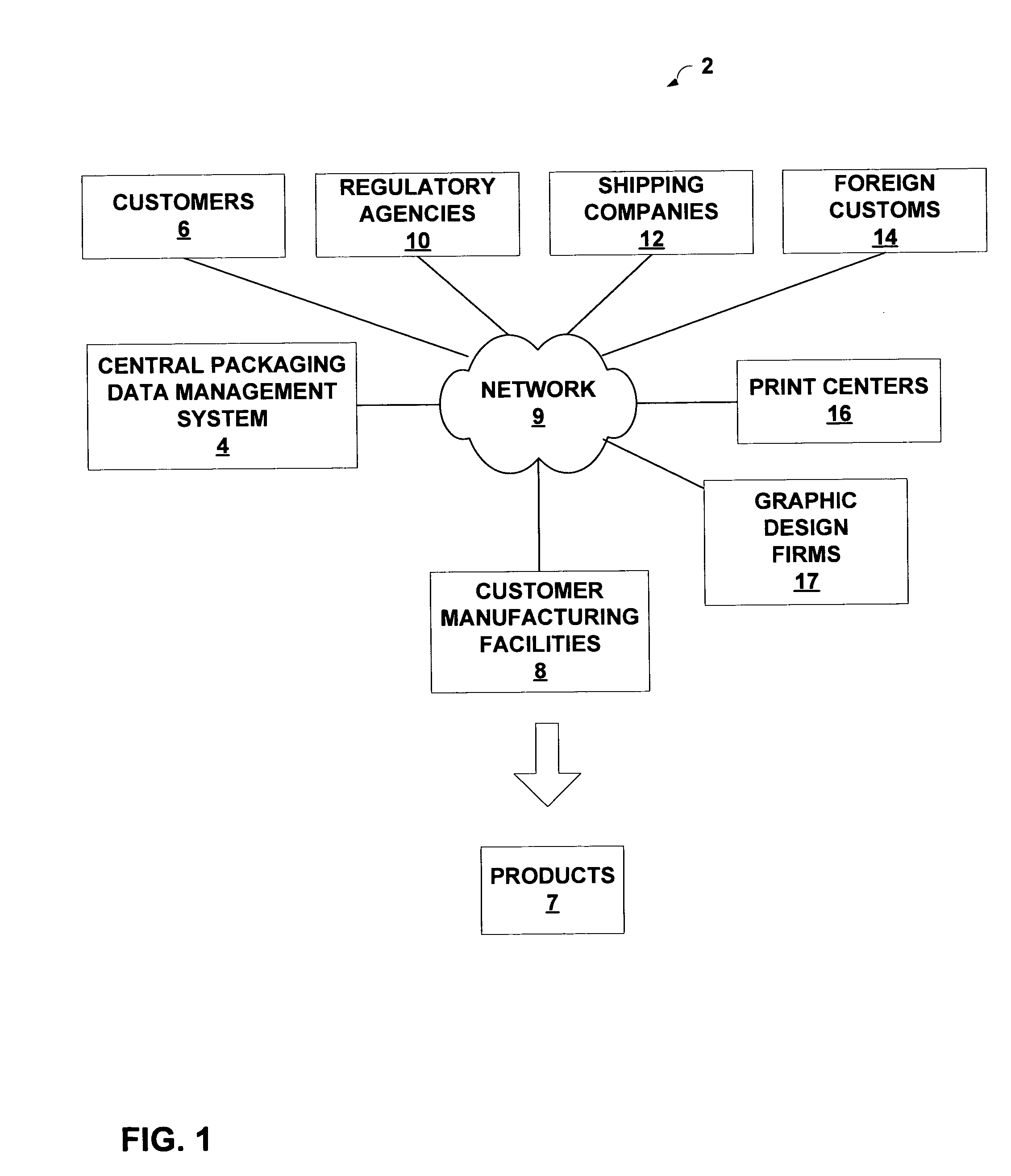
Centralized management of packaging data with artwork importation module
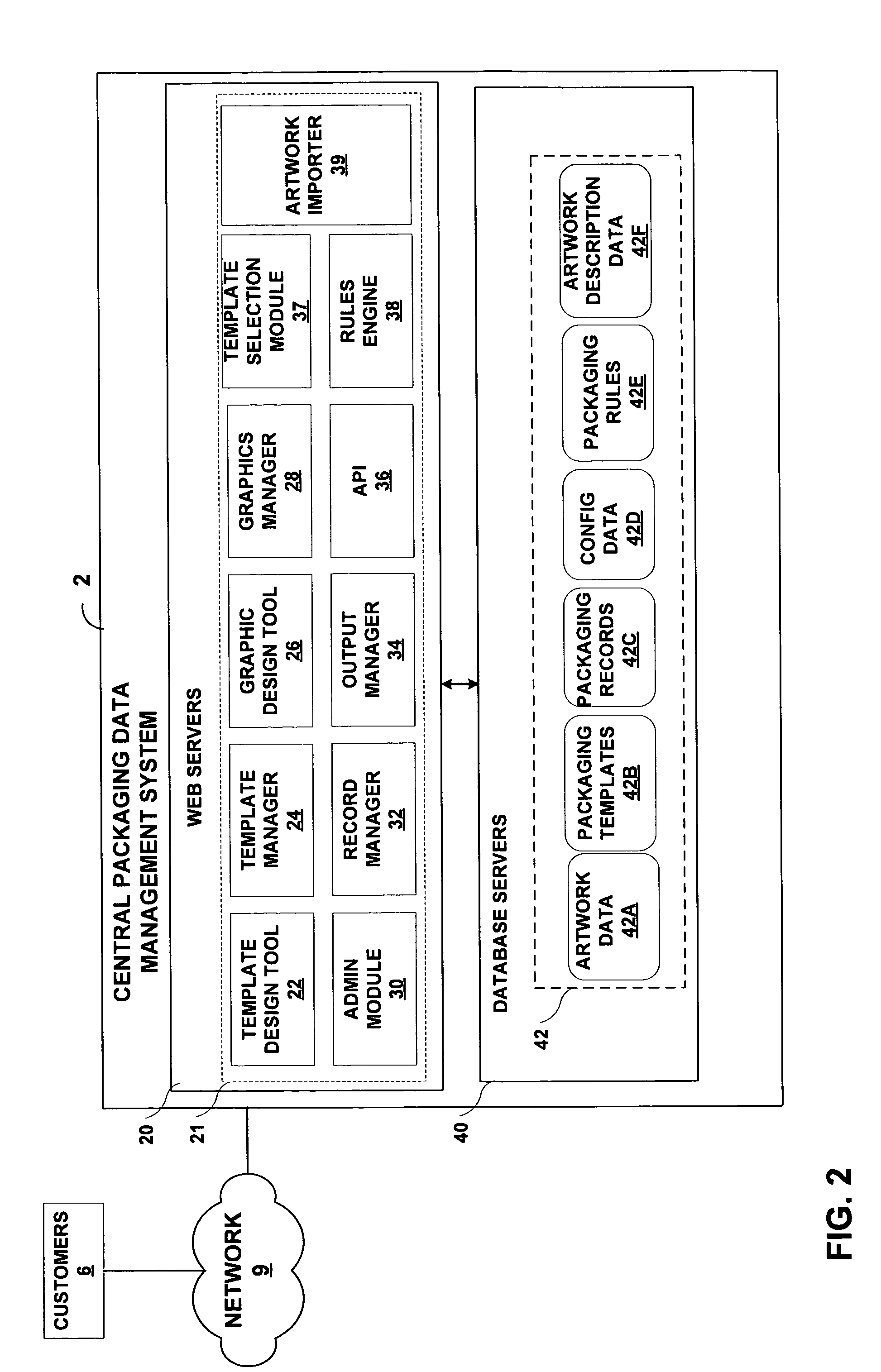
InactiveUS20050050052A1Easy to controlSecure distributionDigital data processing detailsExecution for user interfacesGraphicsData field
A central packaging data (CPD) management system provides an online environment in which customers manage packaging data for their respective products. The CPD management system securely distributes the packaging data to manufacturing sites or other output locations, and allows the customers to control the printed output material applied to their packaging and manufactured products. The CPD management system includes a set of packaging templates having data fields selected from a set of data field types, and an artwork importation module that processes a graphic file to identify elements of a packaging layout. The artwork importer generates metadata that associates each of the elements with a respective one of the data field types of the packaging templates. A record manager presents an interface by which a user forms packaging records based on the metadata. An output manager communicates the packaging record to an output location to control printing of packaging material.
Owner:3M INNOVATIVE PROPERTIES CO
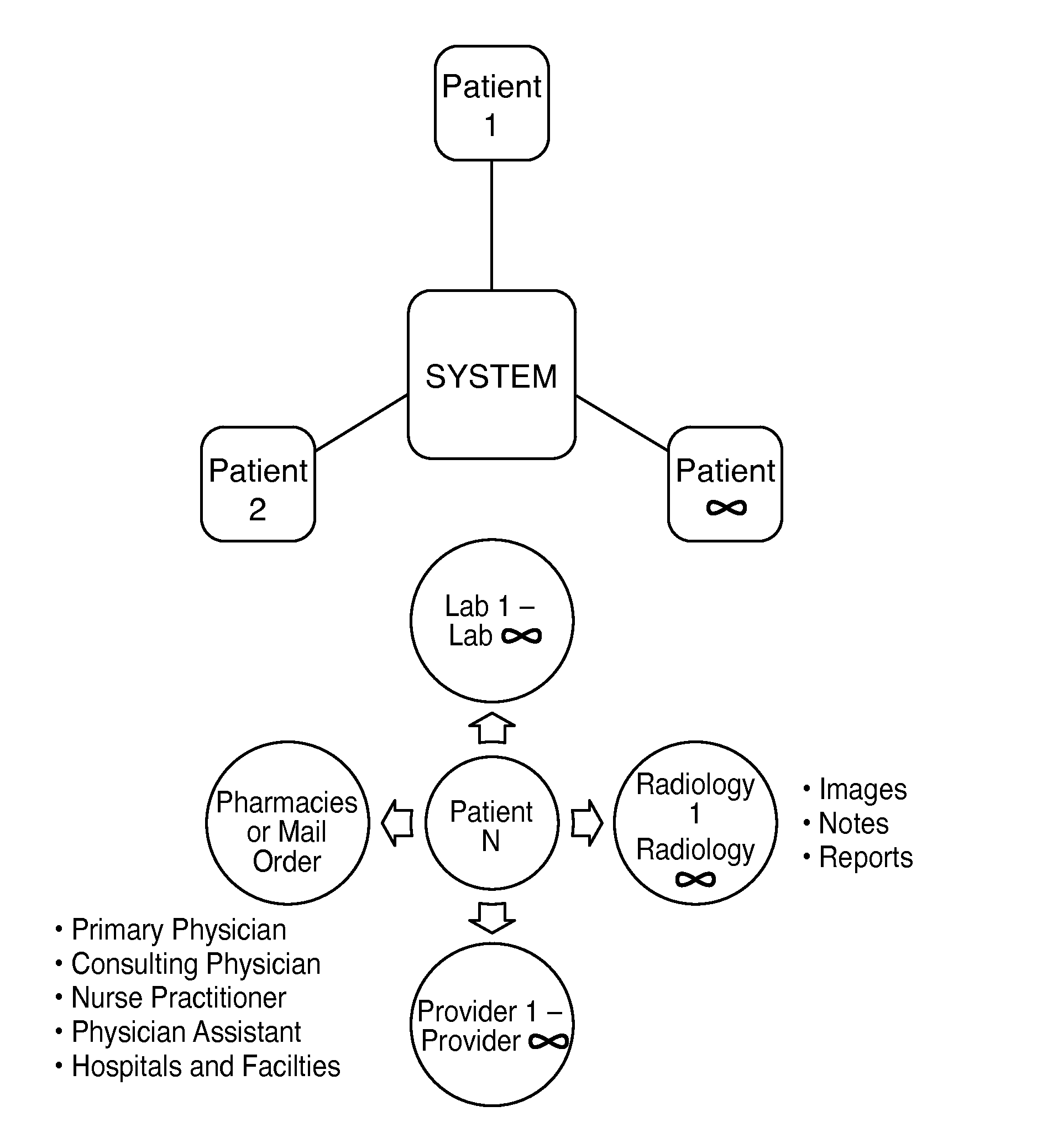
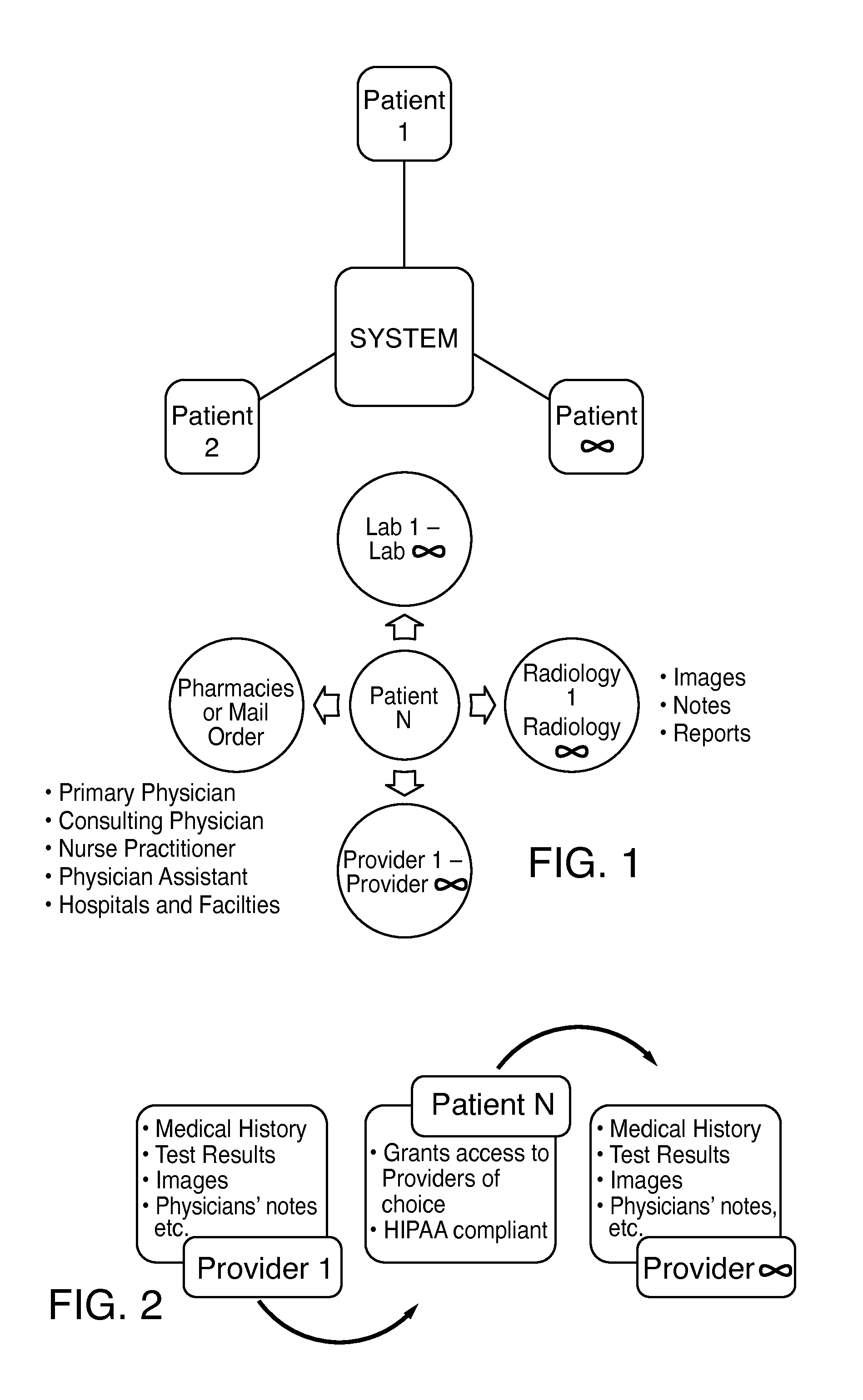
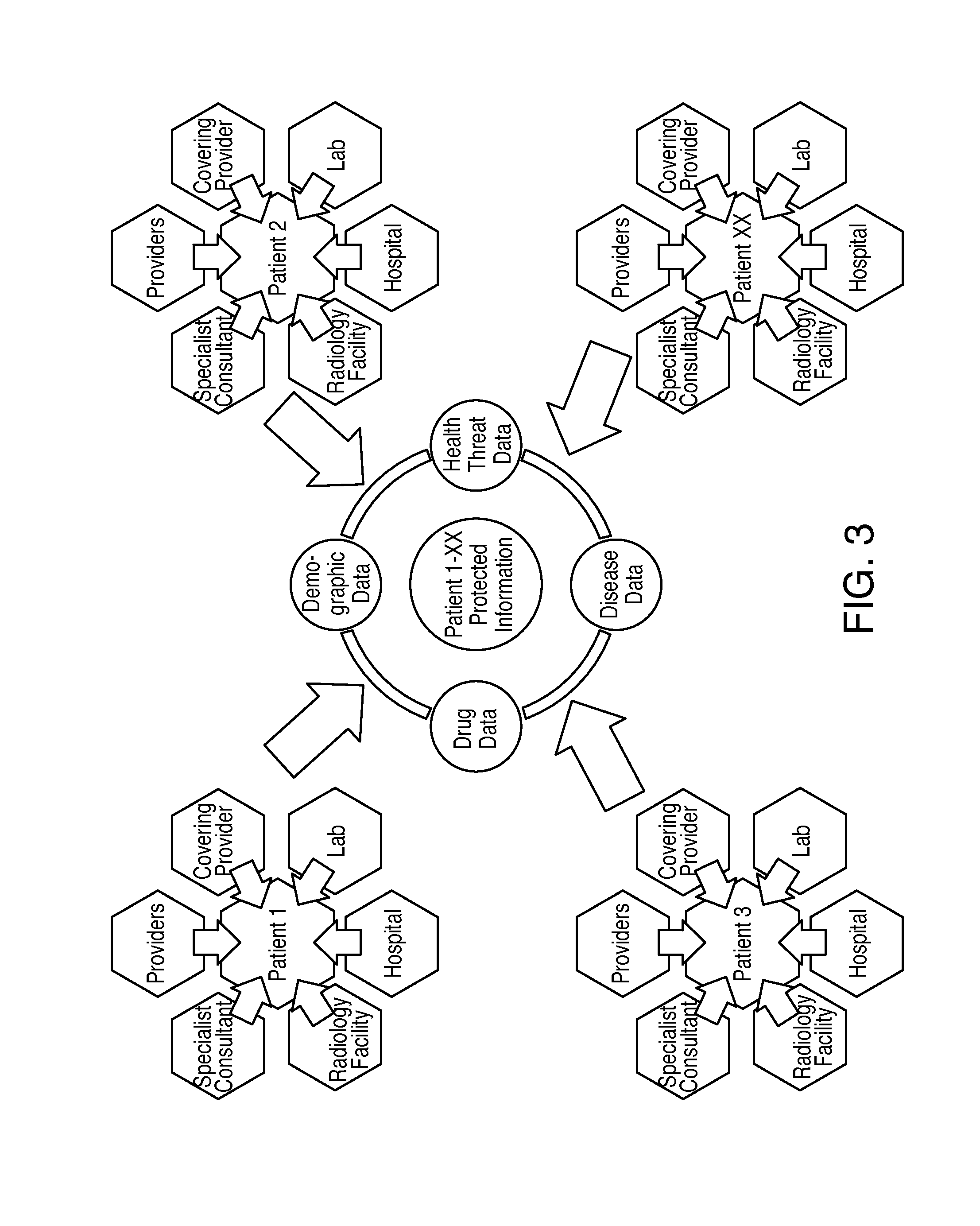
Method for an Interactive, Patient Controlled Medical Information System in a Digital, Real Time Manner which Features a Single Point of Entry for Patients, Physicians, all other Health Care Providers, Health Care Payers, Researchers and Pharmaceutical Companies
InactiveUS20150356250A1Easy accessData processing applicationsLocal control/monitoringMedical recordRecords management
A system and method of managing and maintaining electronic health care records on a web based database controlled by the patient where the electronic health care records are updated on the web based database immediately at the point of service. A user patient logs into the system and authorizes health care providers to have access to that user patient's medical records database. These health care providers generate electronic medical records pertaining to the user patient. These electronic medical records are uploaded onto the user patient's database and sorted by HL7 / FHIR resource code in that database. The electronic medical records are immediately available to the patient and authorized health care providers through the patient's medical records management system database. Additionally, the electronic medical records of all patients on the medical records management system database are available to be searched as a function of medically relevant data stored on the database.
Owner:POLIMENI MEDICAL INFROMATION TECH
Smart quality setting for personal TV recording
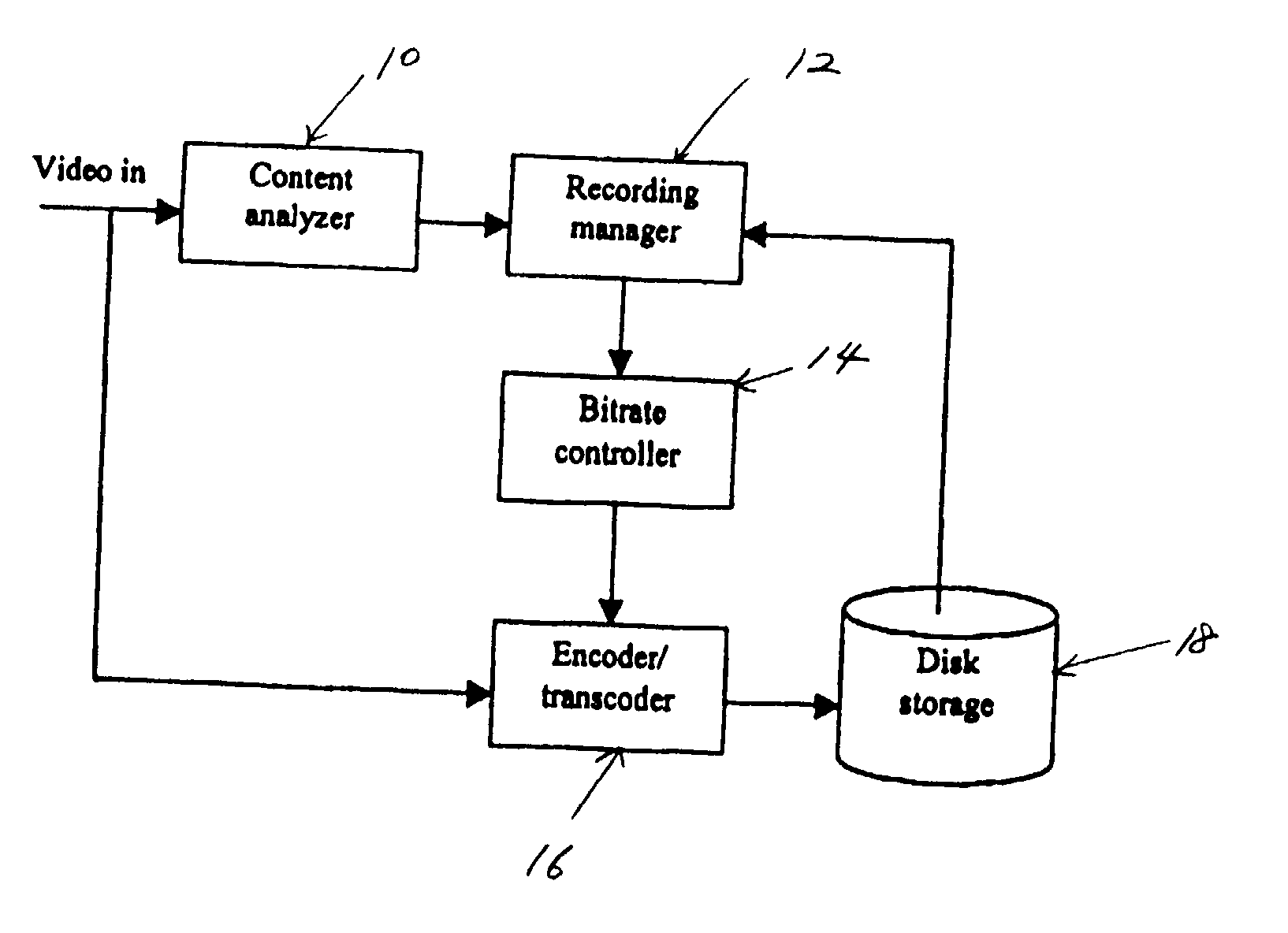
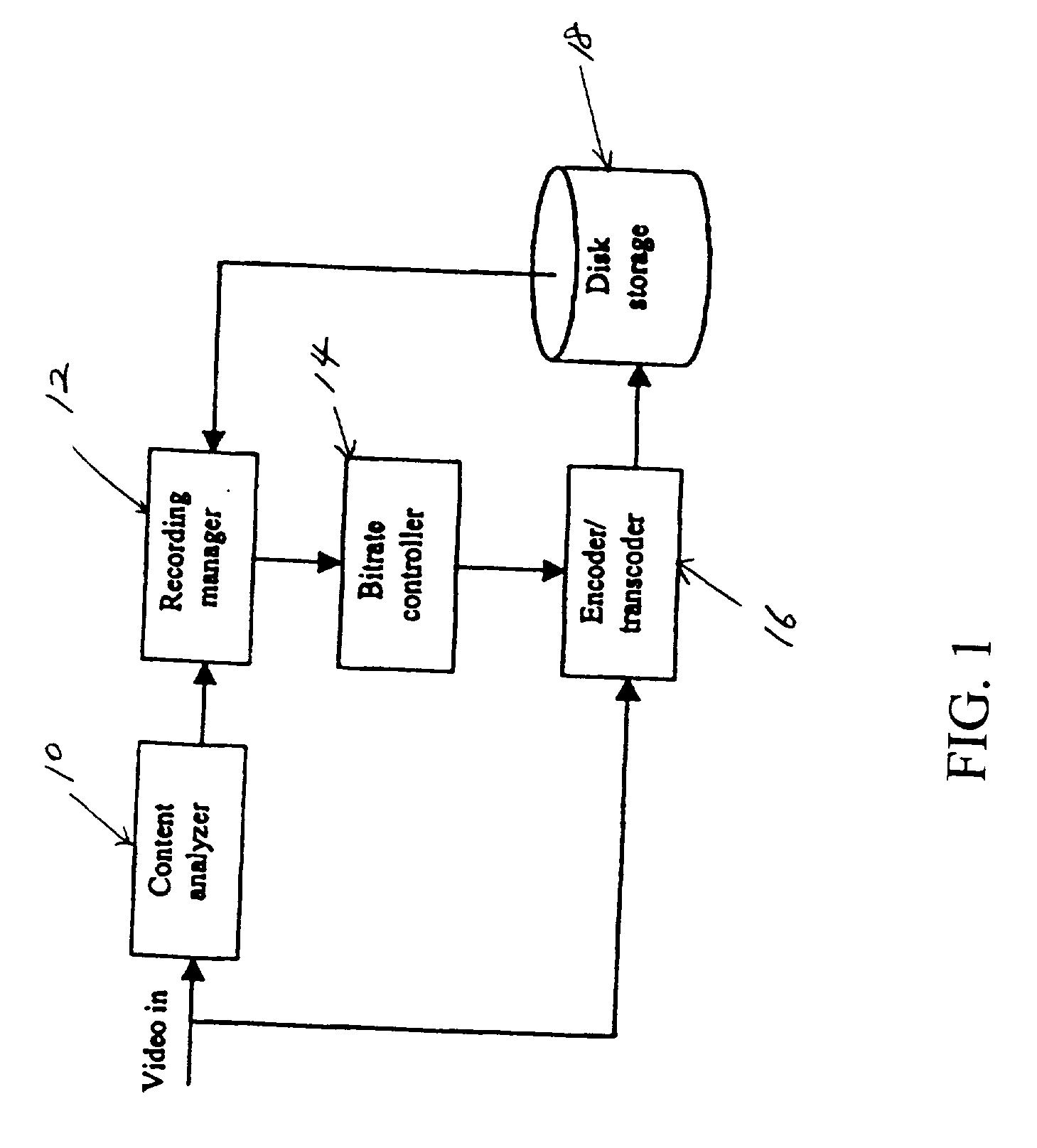
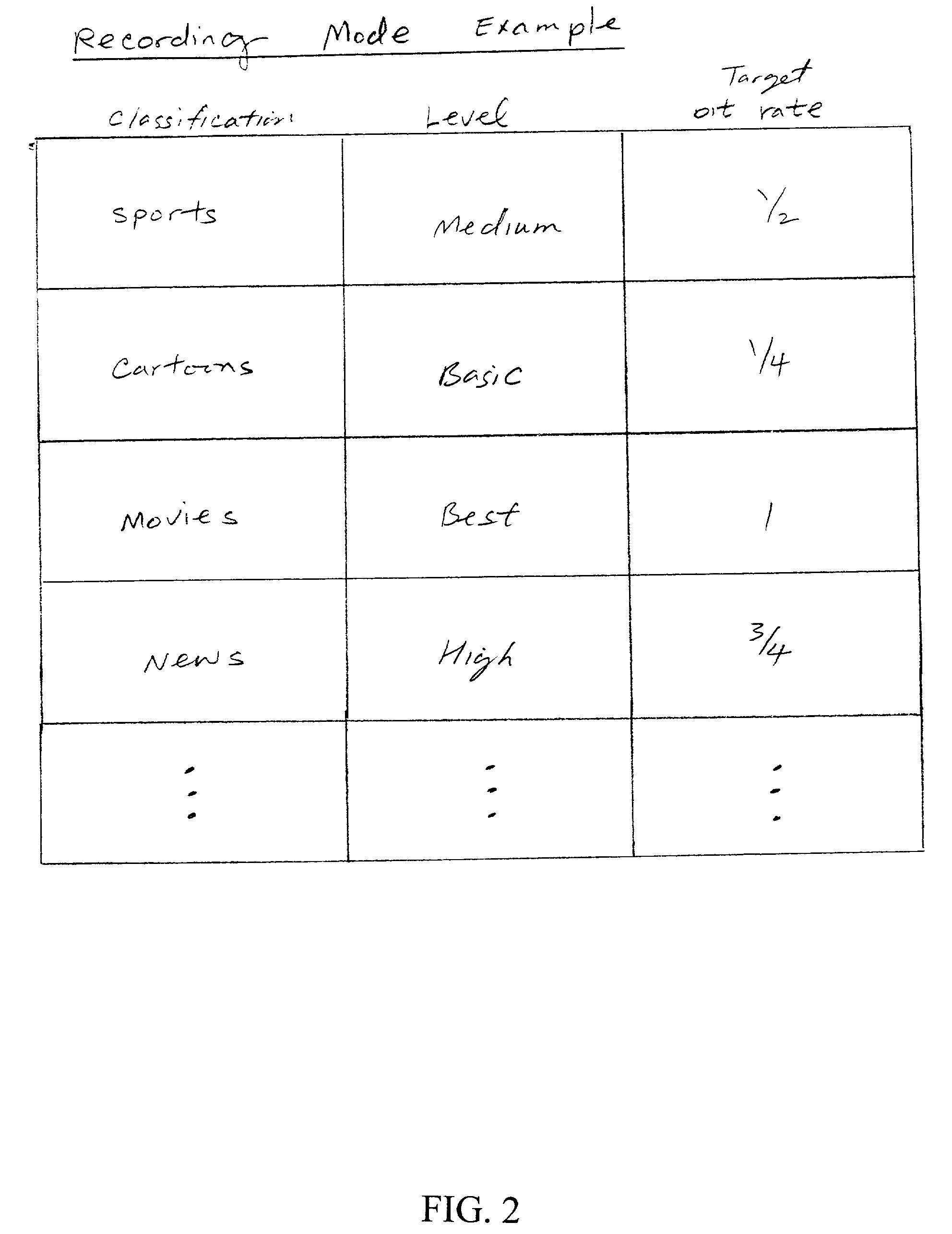
InactiveUS20020136538A1Television system detailsColor television signals processingRecords managementBit rate
An apparatus for automatically adjusting the recording quality of incoming video data is provided. The apparatus includes a content analyzer for evaluating an incoming stream of video programs; a recording manager for determining the target recording bit rate according to the type of video programs received by the content analyzing device, a bit rate controller for adjusting the recording bit rate of the incoming video stream, an encoder / transcoder device for transforming the incoming video programs into a video stream at a specified bit rate designated by the bit rate controller, and a disk storage medium for storing video programs provided by the encoder / transcoder device. The method includes the steps of: analyzing the content of incoming video information representative of dynamic video signal streams; determining an appropriate bit rate for recording in the storage medium according to predetermined criteria; and, recording the incoming video information representative of dynamic video signal streams according to the determined bit rate.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
Automated records management with enforcement of a mandatory minimum retention record
InactiveUS20060149735A1Alteration can be preventedData processing applicationsError detection/correctionRetention periodProgram planning
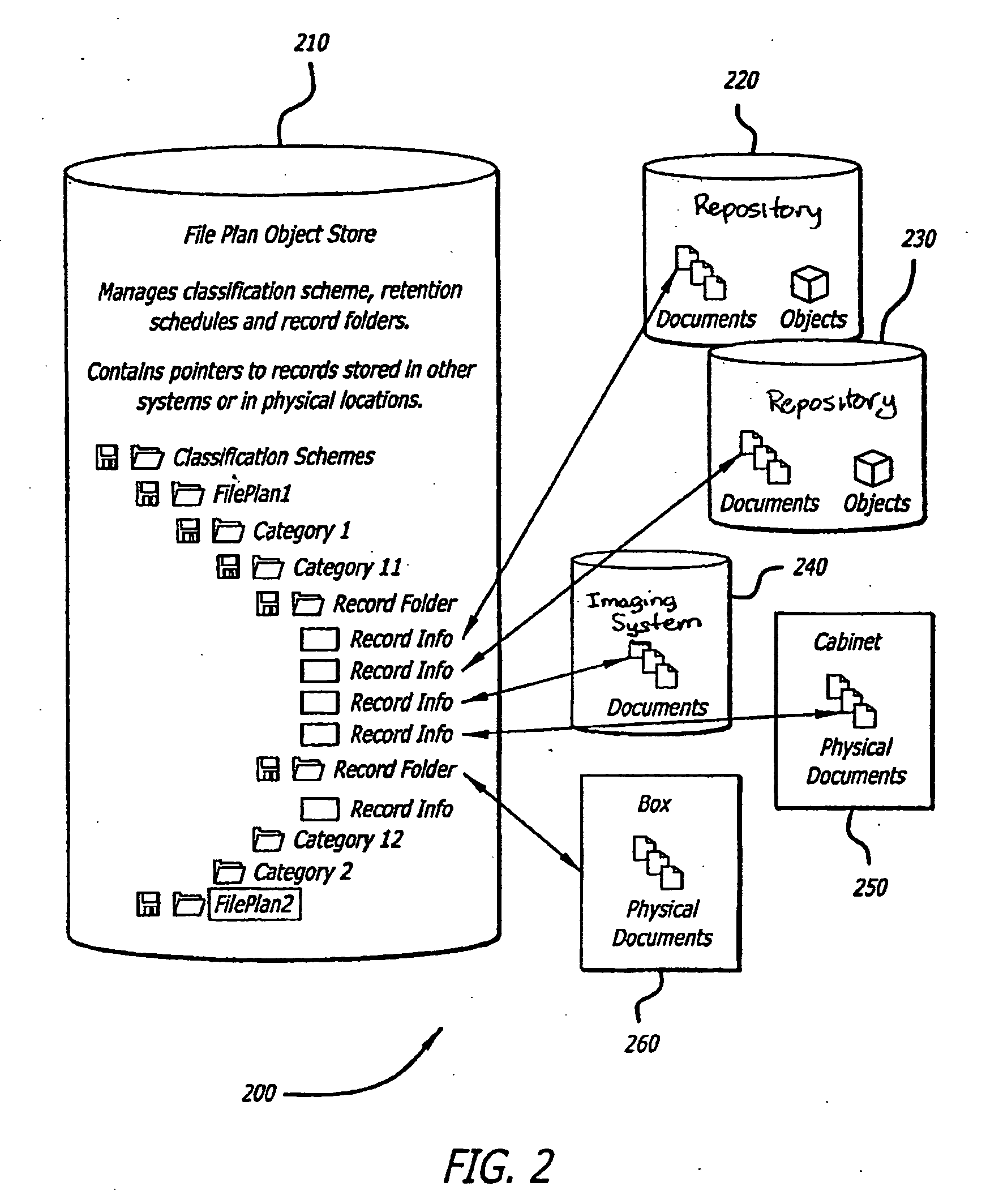
A records management system and method includes a file plan that has one or more segments associated with compliance data. Data stored in these segments of the file plan have a mandatory minimum retention period during which they cannot be modified or deleted. Additionally, the information about the mandatory minimum retention period may not be altered or removed.
Owner:IBM CORP
Automatic records management based on business process management
InactiveUS20060085374A1Digital data information retrievalFinanceRecords managementClassification scheme
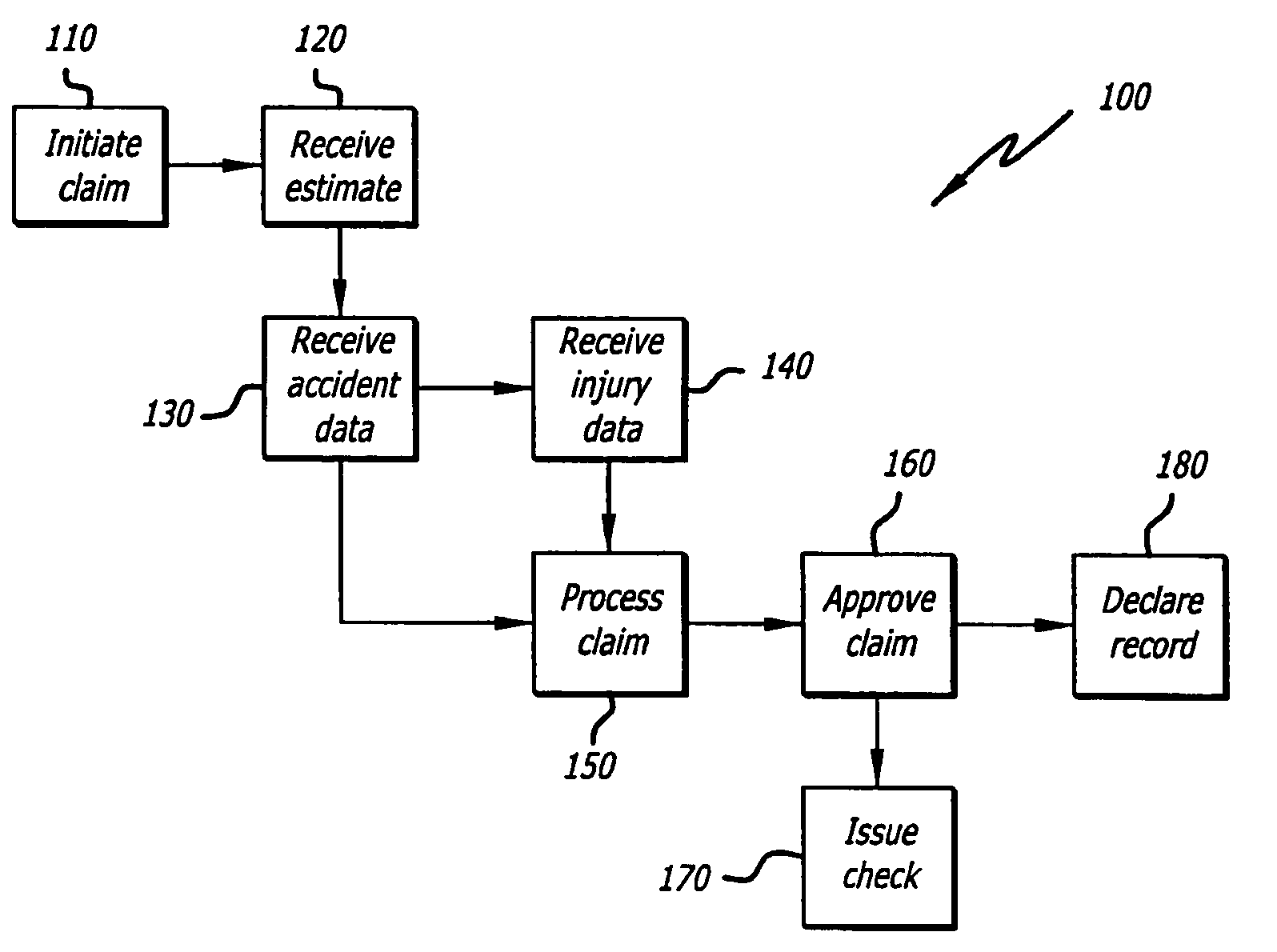
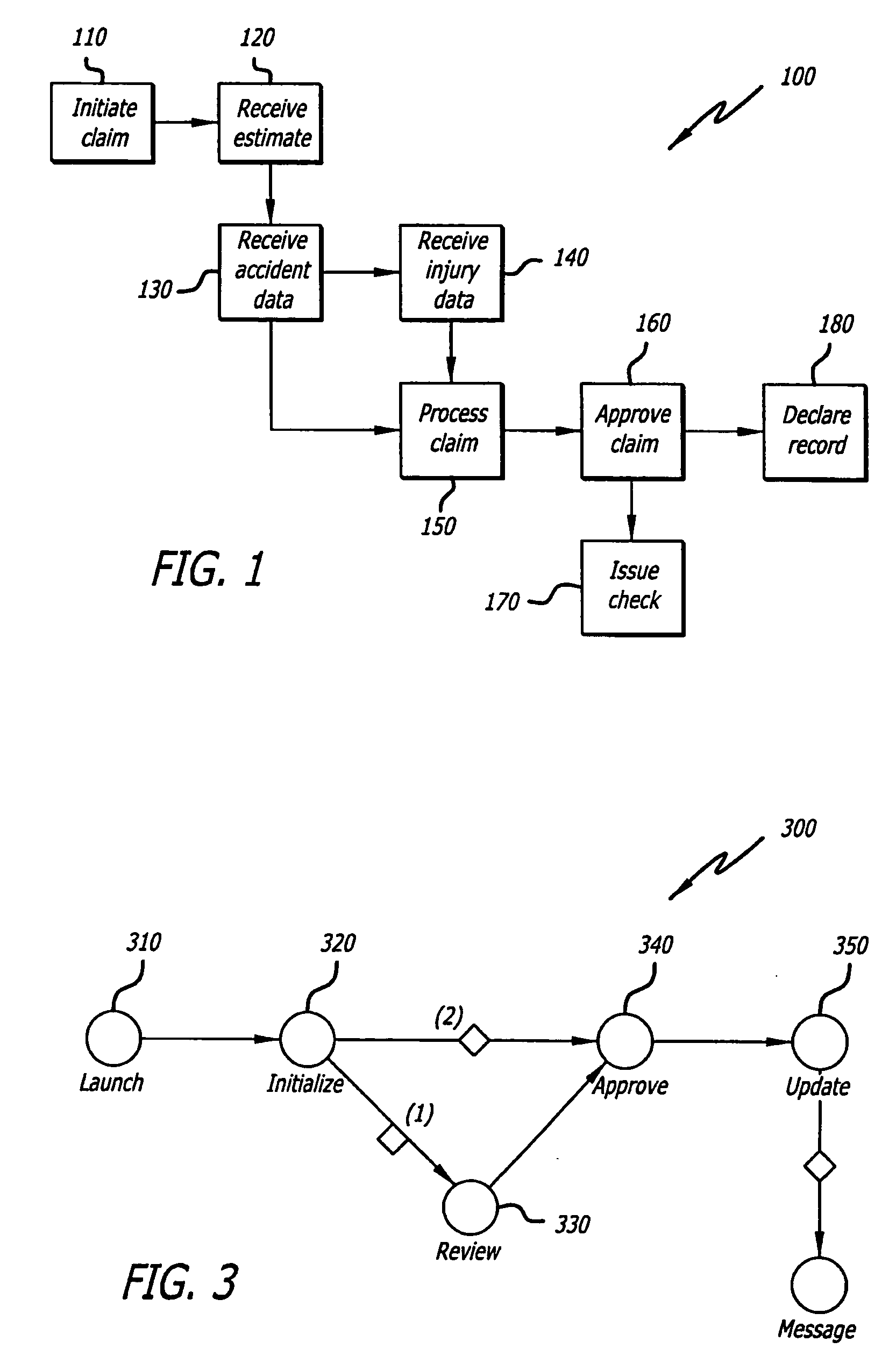
A records management method that automatically classifies records and manages the records based on the classification. The method incorporates processes for receiving a classification scheme for a record, receiving declaration of an asset as a record, automatically classifying the record according to the classification scheme, and workflow processes for vital records review and review for approval of disposition of records. Numerous method variations, as well as related systems and computer-readable media are also disclosed.
Owner:IBM CORP
Apparatus for measuring pressure distribution and method for measuring thereof
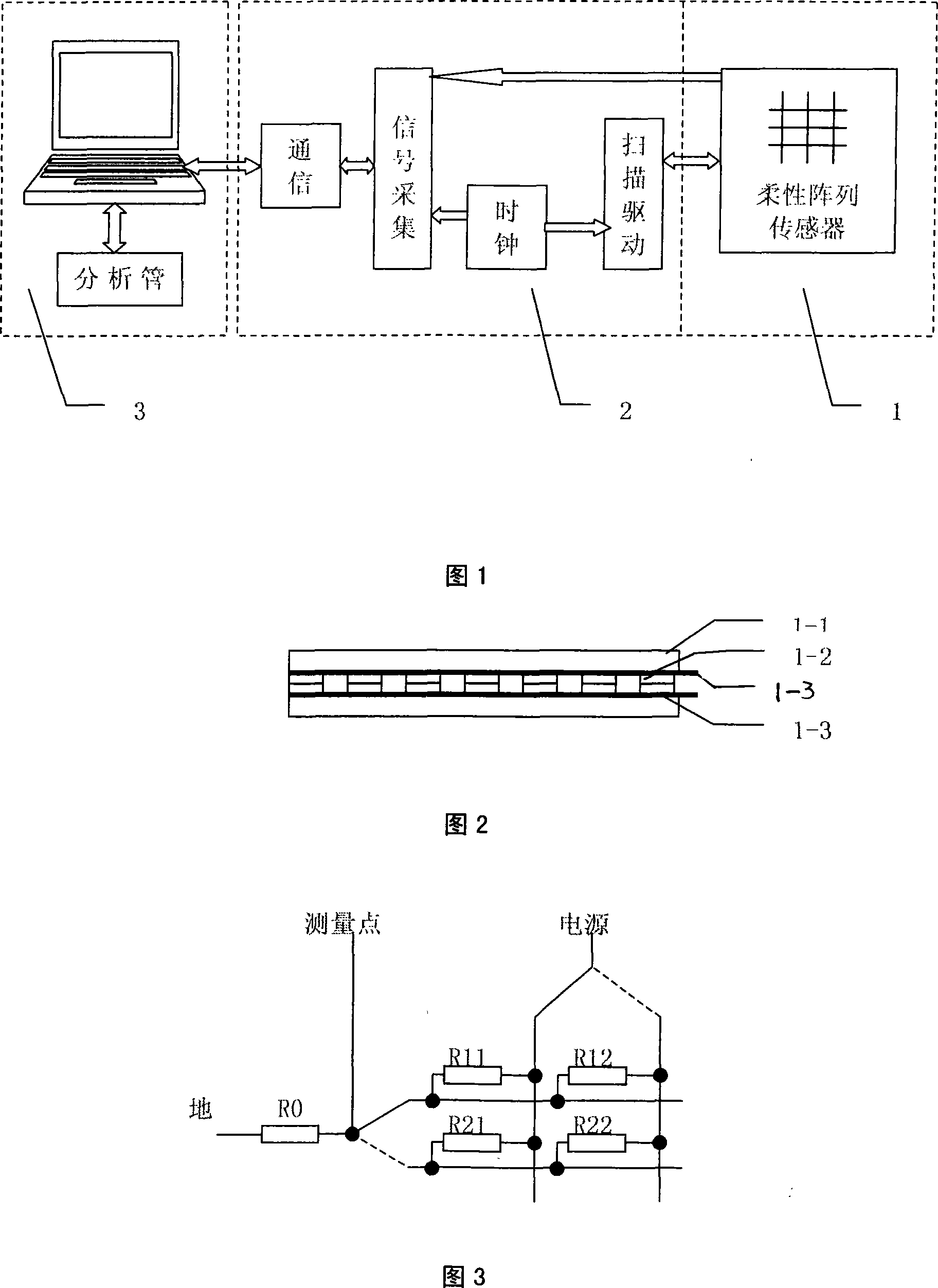
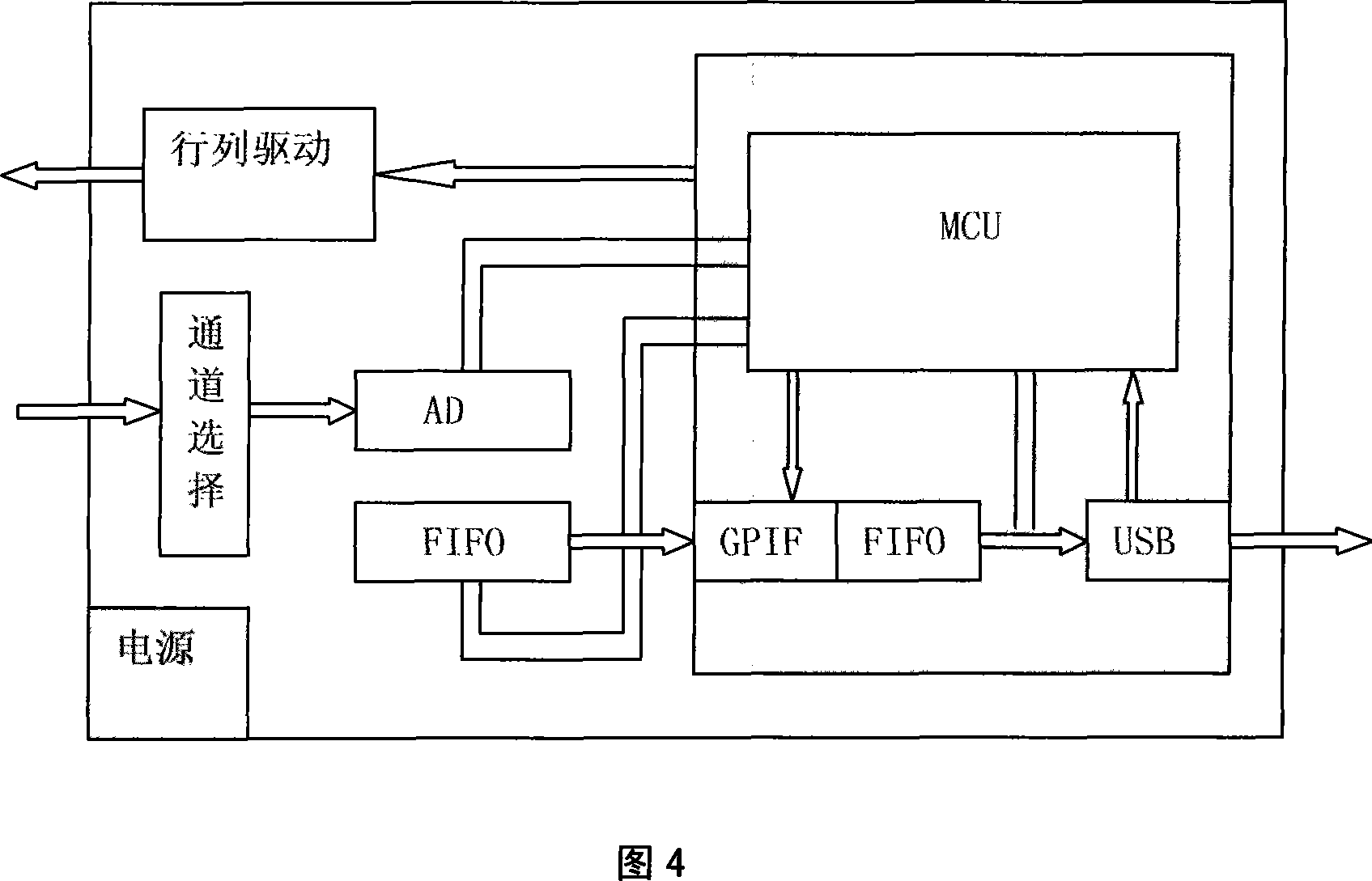
ActiveCN101201279AElectric signal transmission systemsForce measurement using piezo-resistive materialsAthletic trainingData access
The invention provides a pressure distribution measuring device and a measuring method thereof. The pressure distribution measuring device consists of a flexible array sensor (1), an embedded signal drive collection unit (2) and computer analysis processing software (3). The embedded signal drive collection unit (2) has the function of scanning drive of array lines and rows, and the function of collection of pressure signals of array points. The embedded signal drive collection unit (2) is connected with a computer through a USB 2.0 interface. The computer analysis and processing software comprises a communication interface module, a data access module, a data analysis module, a records management module and a print driver module. The computer gets the information of the acting force, the distribution information of the acting force, the center of pressure, the information about the power spectrum and so on through collecting the information of the acting force output by the force sensor and the analysis software. The invention provides scientific basis for athletic research, instruction of athletic training, scientific research of medical treatment, disabled body recovery training instruction and so on.
Owner:ANHUI BIOFORCEN INTELLIGENT TECH
Non-intrusive, automated upgrading of electronic records
InactiveUS20040015521A1Database updatingSpecial data processing applicationsData fieldRecords management
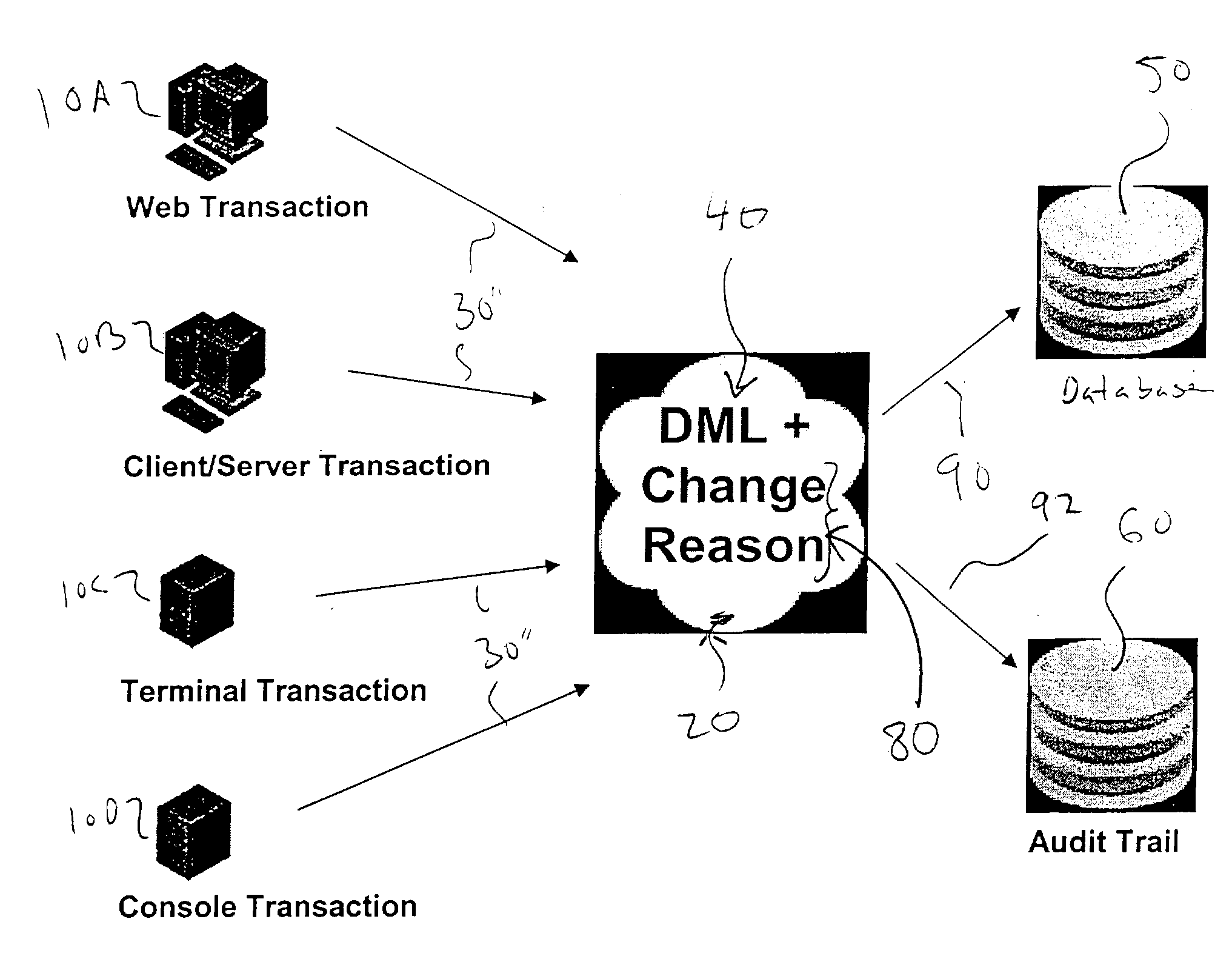
Change-reason functionality is imparted to an existing records management system by providing a software layer that monitors manipulation requests to one or more data fields of the existing records management system; detecting a manipulation request using the software layer; presenting a notification to a user that a change-reason is required for the proposed manipulation request; and in the event that the user has provided the change-reason, selectively updating the one or more data fields.
Owner:HUDICKA JOSEPH R
Method for controlling access to informational objects
ActiveUS20060117389A1Digital data processing detailsUser identity/authority verificationInternet privacyInformation object
The described embodiments of invention comprises a method and an apparatus for regulating access to objects by authorized entities. Authorized entities are entities authorized for access by either an owner entity of the regulated object or an entity authorized to authorize access to the regulated object. Each user, which may be a physical person or another information system, is identified using standard user validation techniques. When an object is first created or introduced to the system, that information is associated with an owner, who is one user on the system. The present embodiment allows the owner to define relationships with other users, either generally or regarding a particular object. The owner may or may not have trusted relationships with other users. A second user that has a trusted relationship with the owner automatically has access to the object without additional intervention by the owner. In addition, the second user may have a trusted relationship with another user. In the above example, the records administrator may have an assistant. This third user will also have access to the records. This Web of Trust may link users infinitely, but such a case would create an undue risk of compromise of the information. Thus, the present embodiment includes a facility for the owner to designate a maximum number of trusted links from the owner and other users.
Owner:OPTIMIZATION ZORN CORP DBA OZ SYST INC
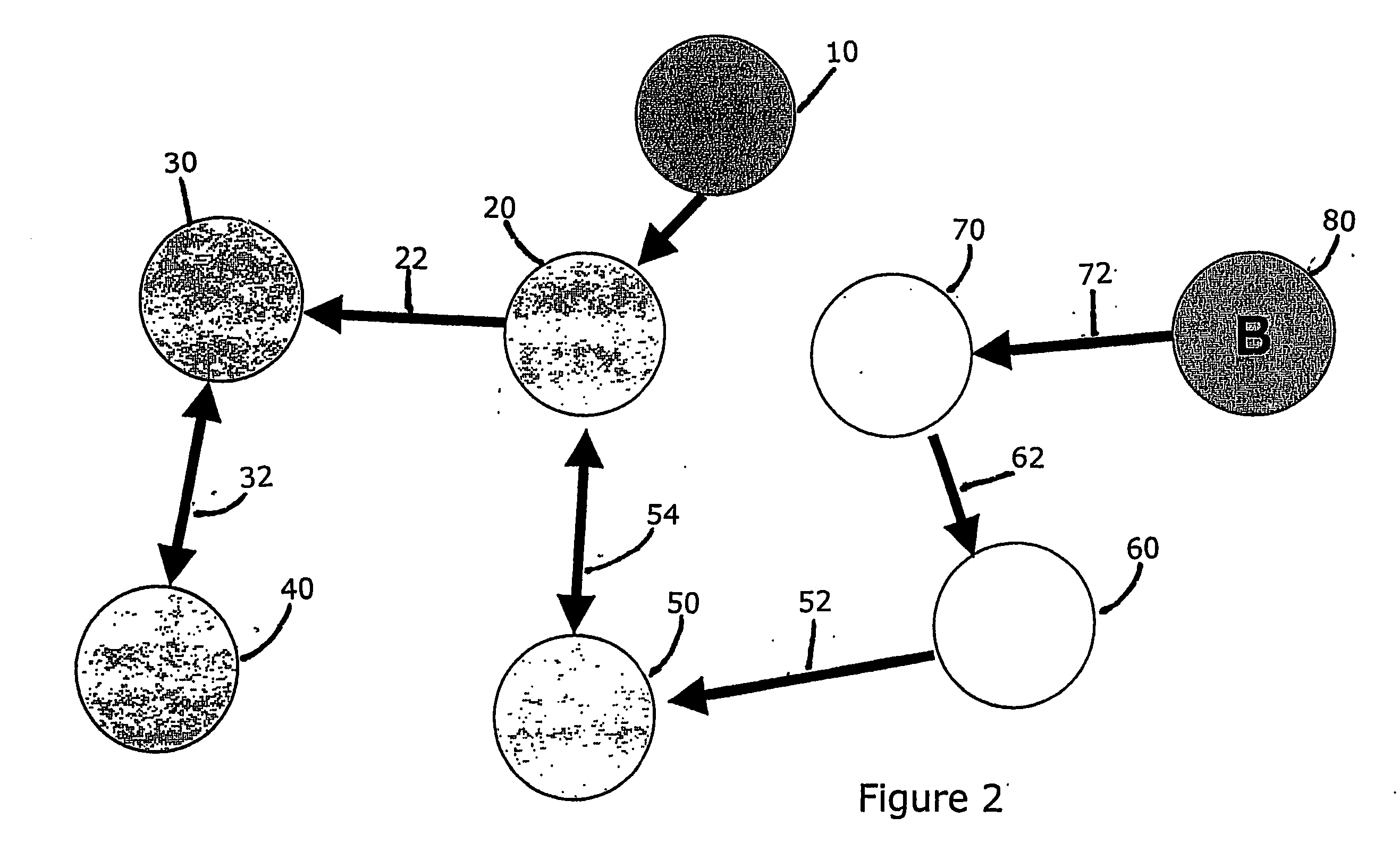
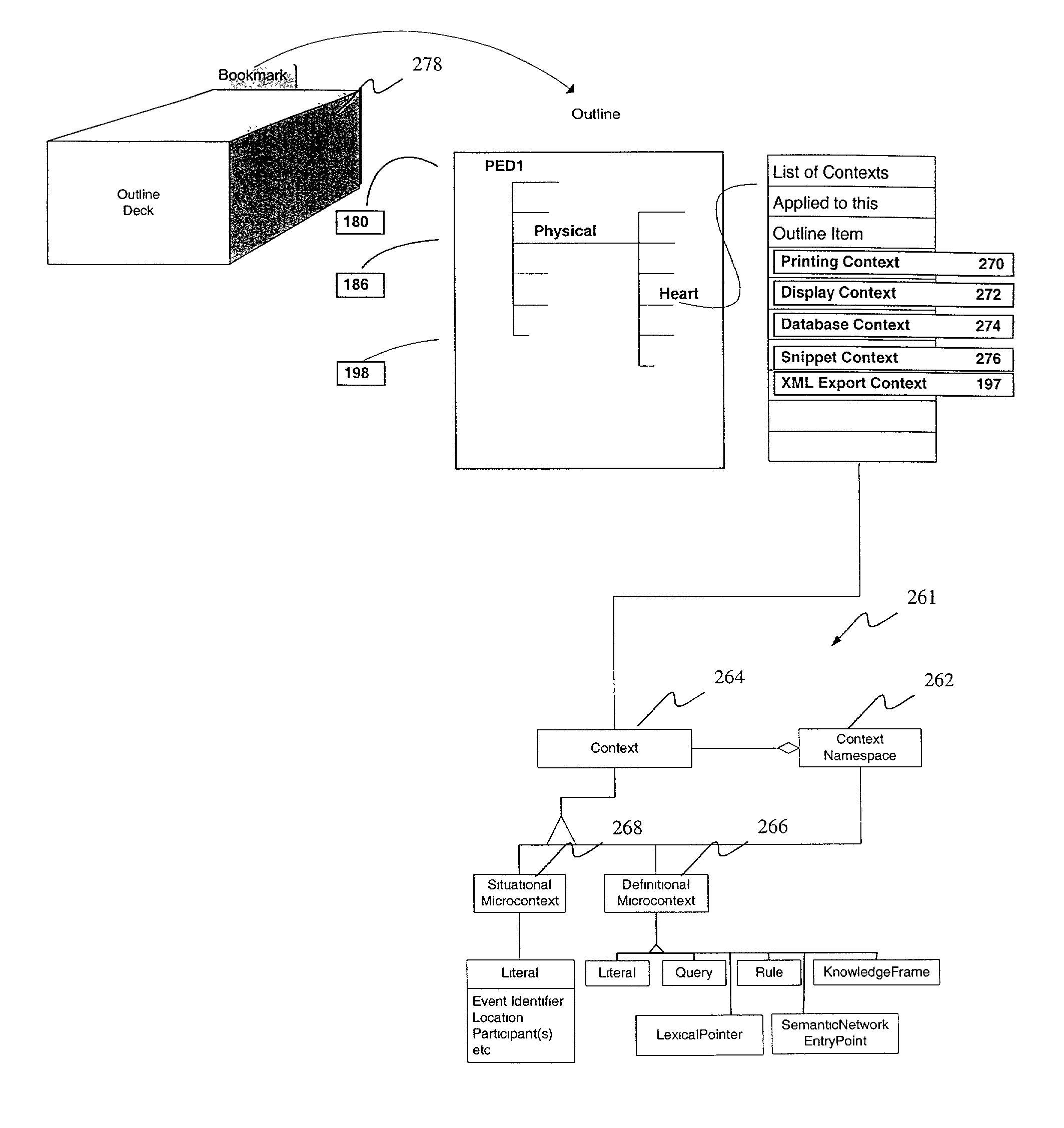
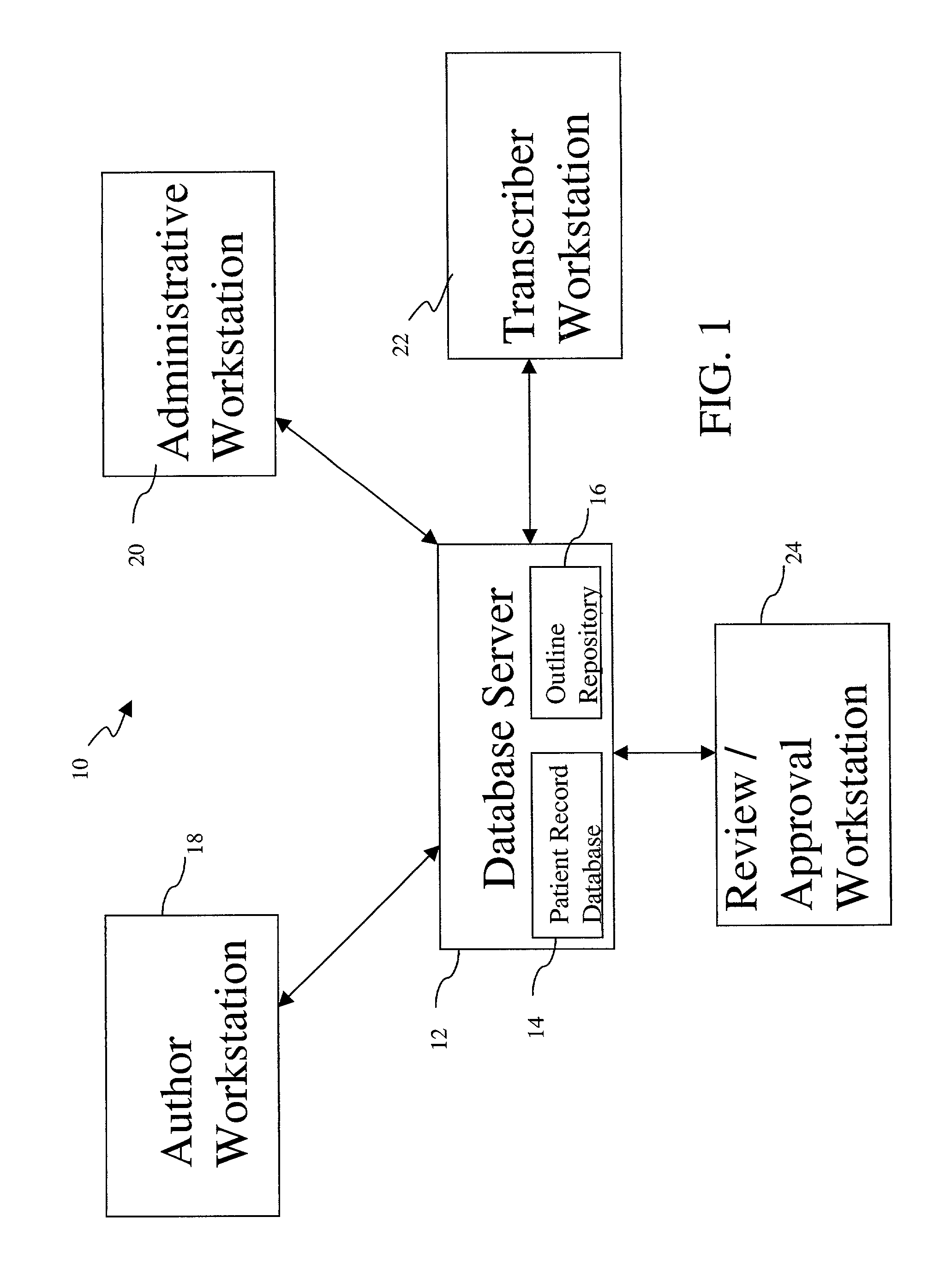
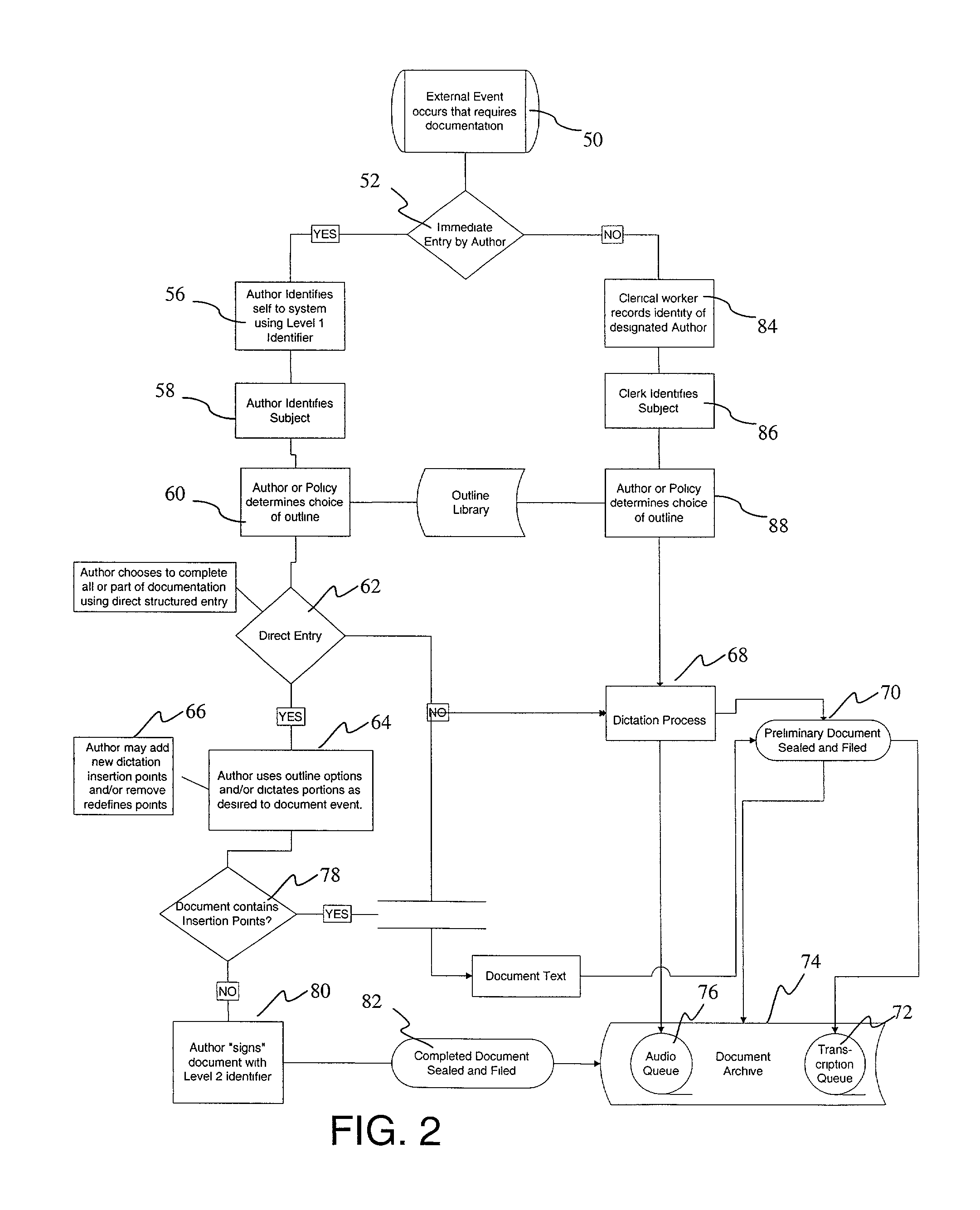
Electronic record management system
InactiveUS7802183B1Office automationSpecial data processing applicationsMultiple contextDocumentation procedure
An electronic record management system utilizes semi-structured documents that contain both authenticated partial texts created by an author and pointers to audio recordings that will be processed later by transcribers. The transcribed material is held in temporary storage until reviewed and approved by the author. When approved, the transcribed text may be combined with the original authenticated partial text to produce a final authenticated document. In addition, the record management system may further include a mechanism for assigning multiple context-dependent meanings to at least a portion of the information items included in a document. The record management system therefore allows a variety of encoding schemes to be automatically overlaid on each document. This creates opportunities to re-use the information for secondary purposes, such as preparing bills (such as Medicare bills) that must conform to arbitrary sets of rules.
Owner:ESSIN DANIEL J
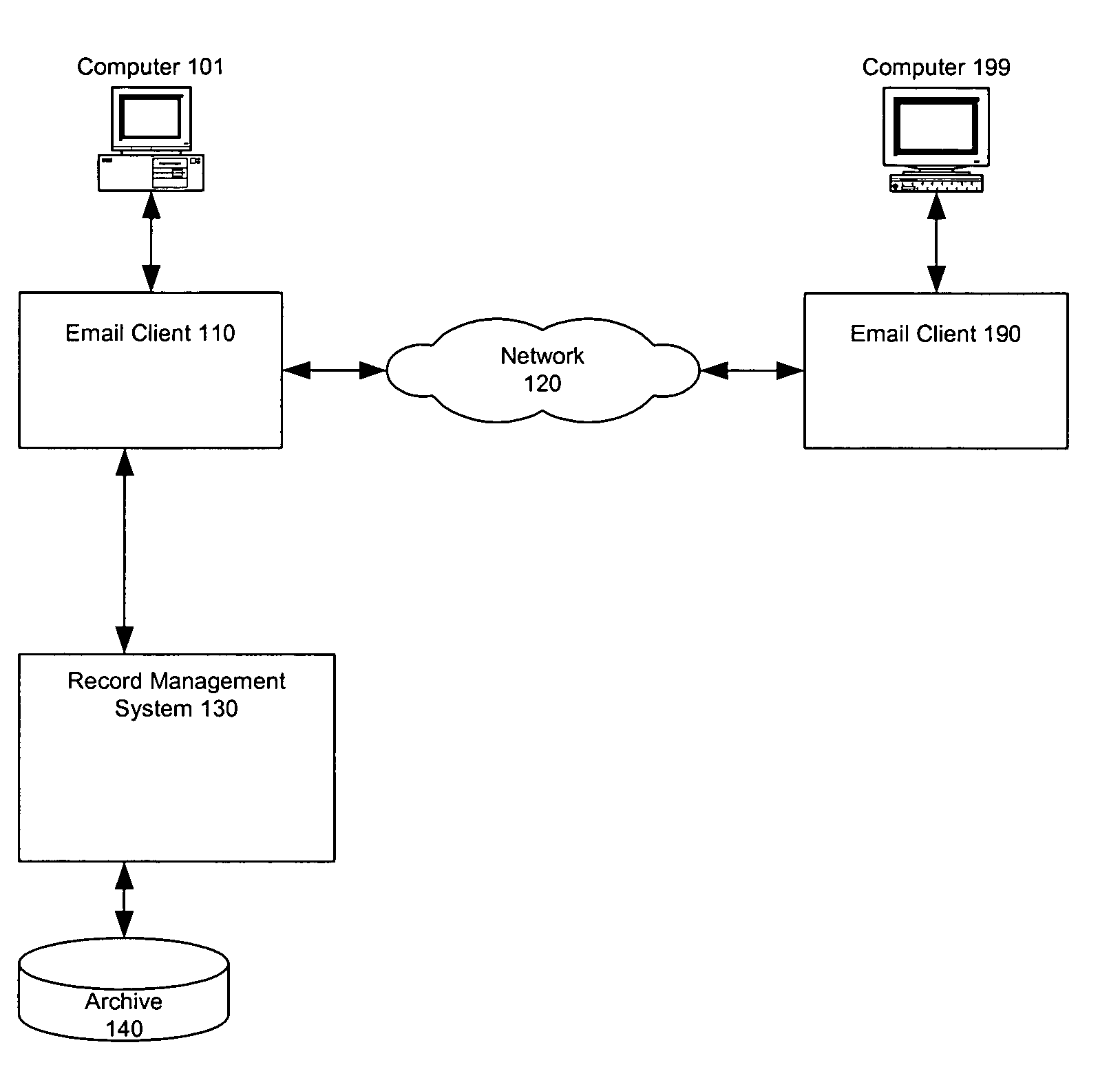
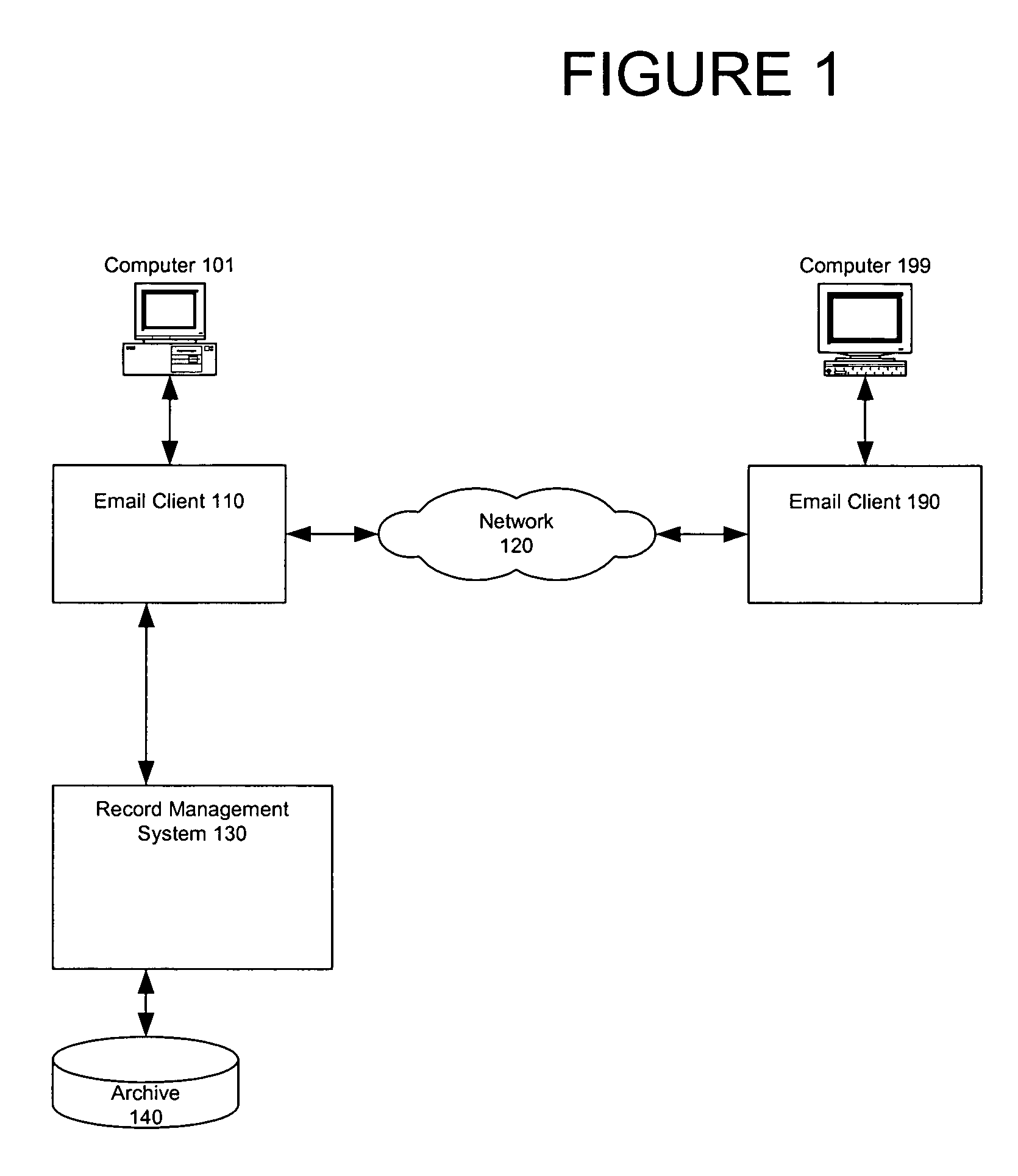
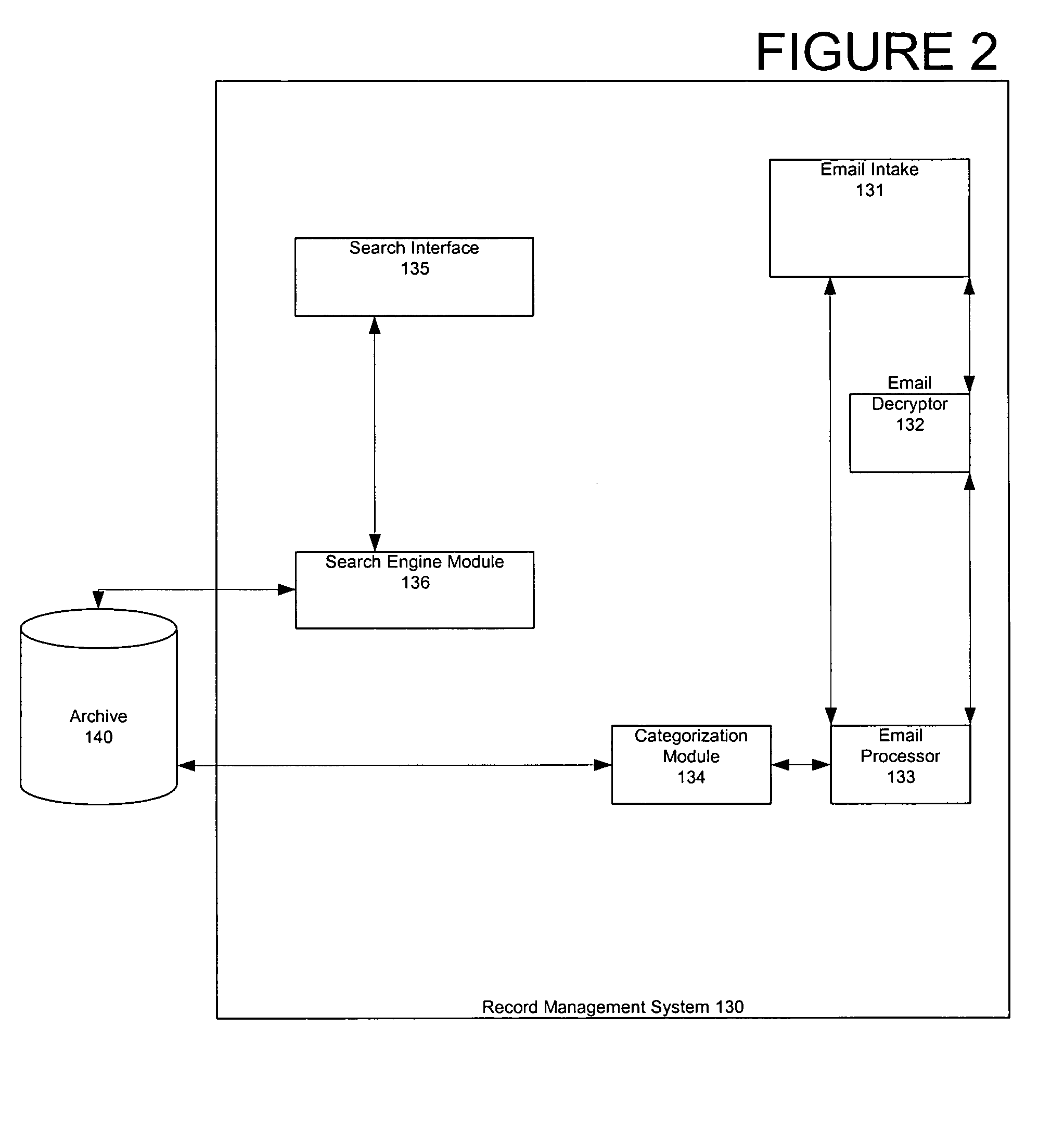
Record management of secured email
Email can be securely stored using a secure record management system. An encrypted email is received at the secure record management system. The received email is a duplicated copy of a transmitted email and is decryptable by the secure record management system. The received email is processed and providing to an archive for archiving.
Owner:SBC KNOWLEDGE VENTURES LP
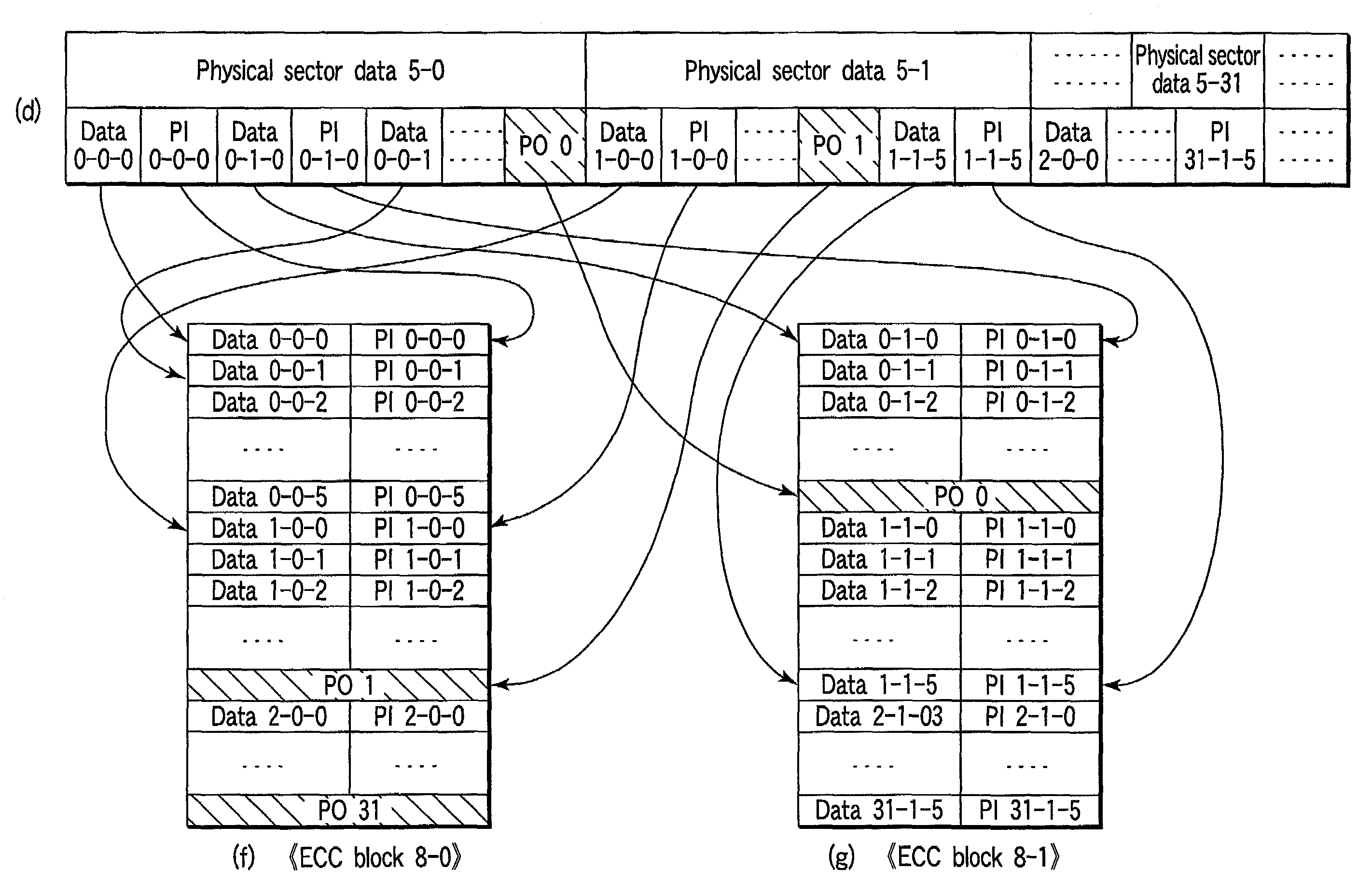
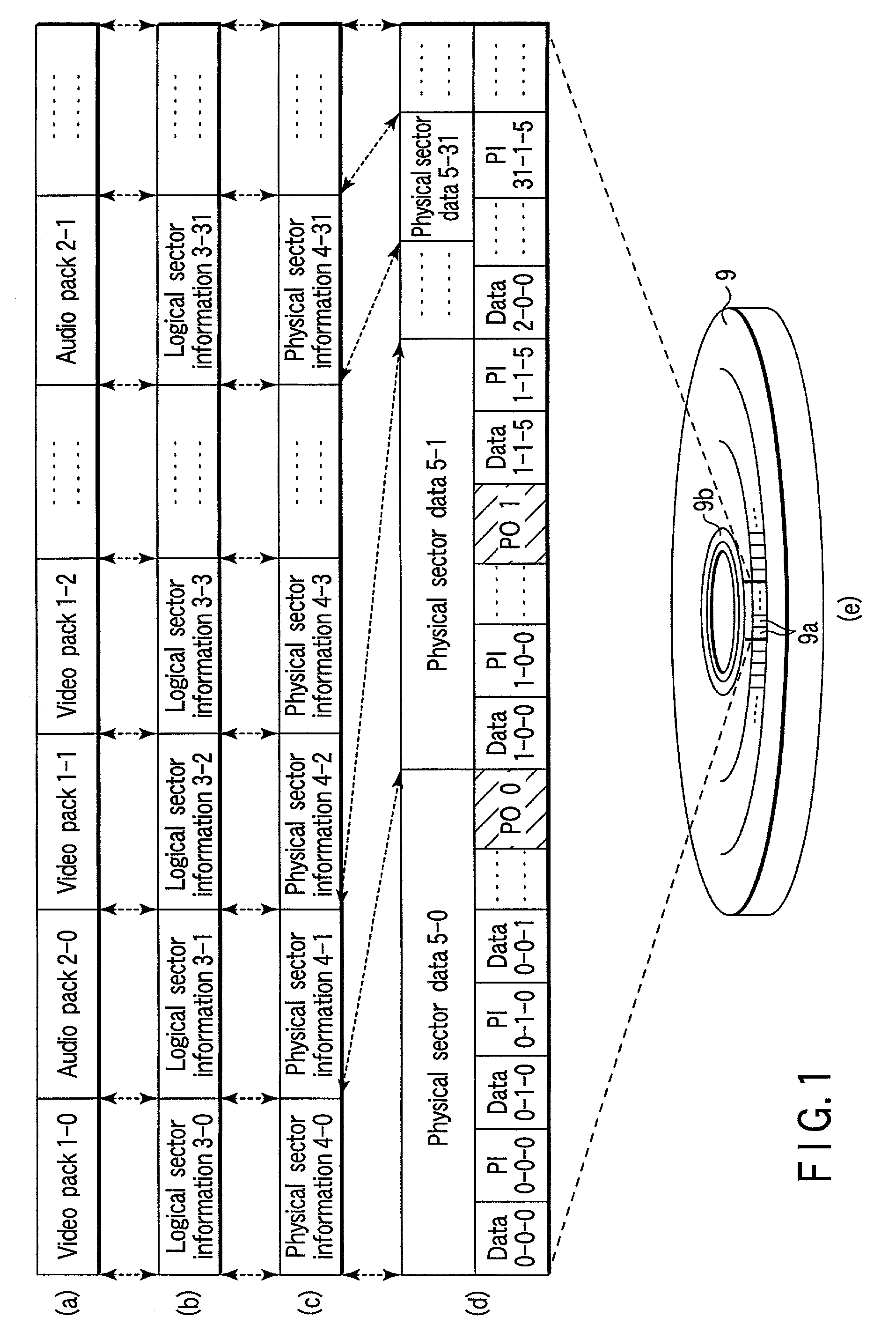
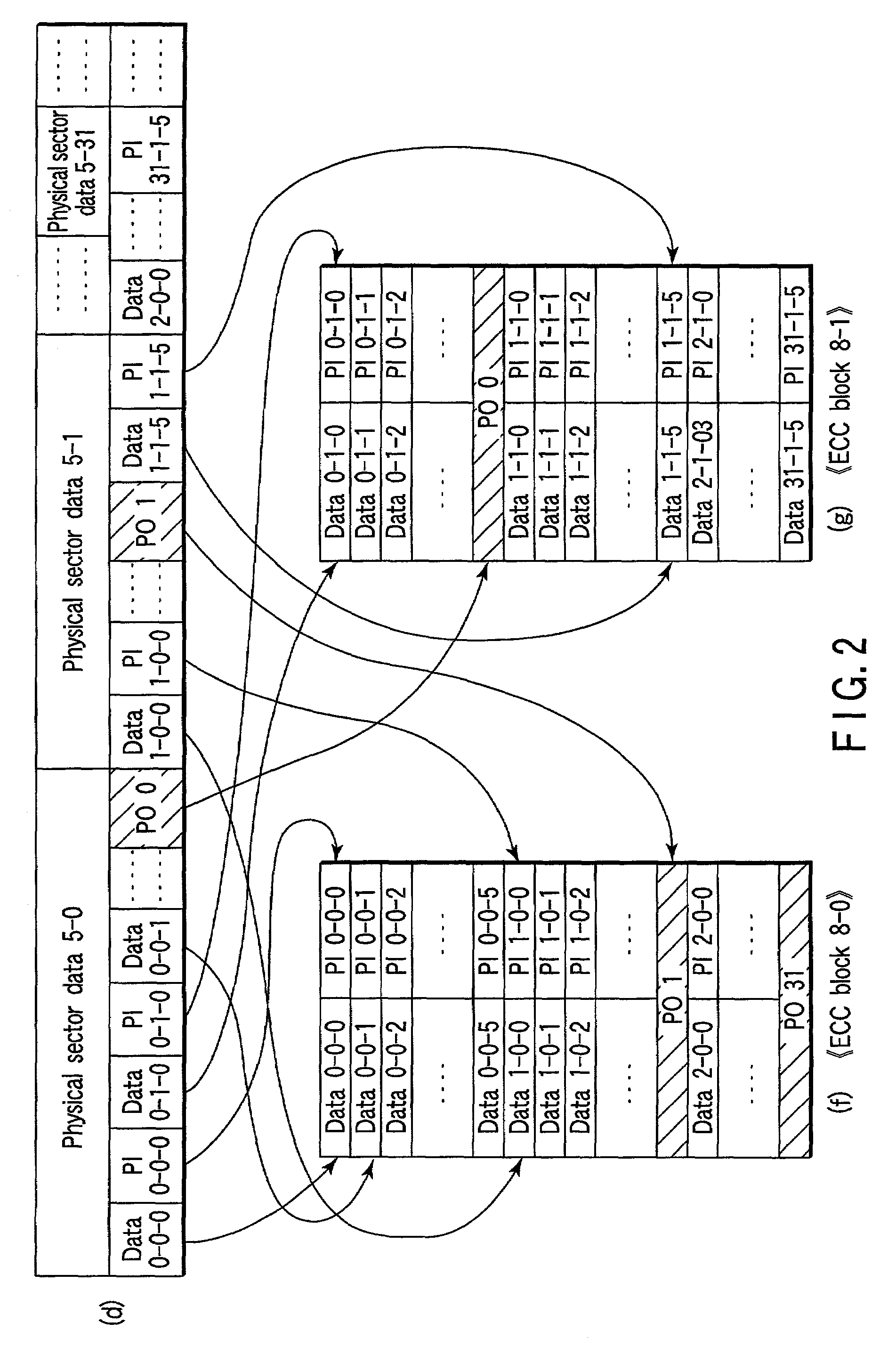
Information recording medium on which sector data generated from ECC block is recorded, information recording apparatus for recording sector data, and information reproduction apparatus for reproducing sector data
An information recording medium includes a management area where management information is recorded and a plurality of physical sector areas used to record a plurality of physical sector data blocks, which are generated by combining some data contained in a plurality of ECC blocks.
Owner:KK TOSHIBA
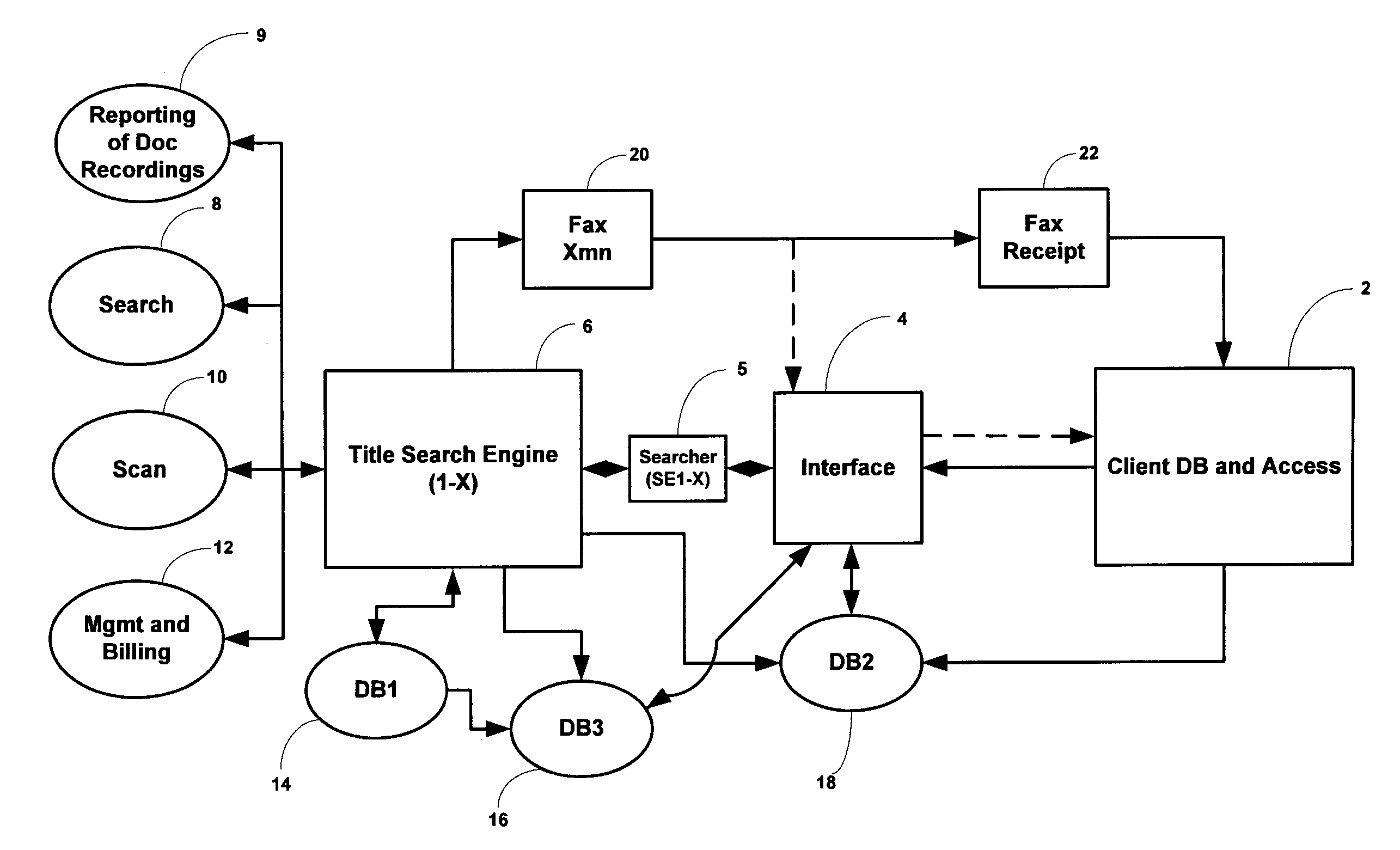
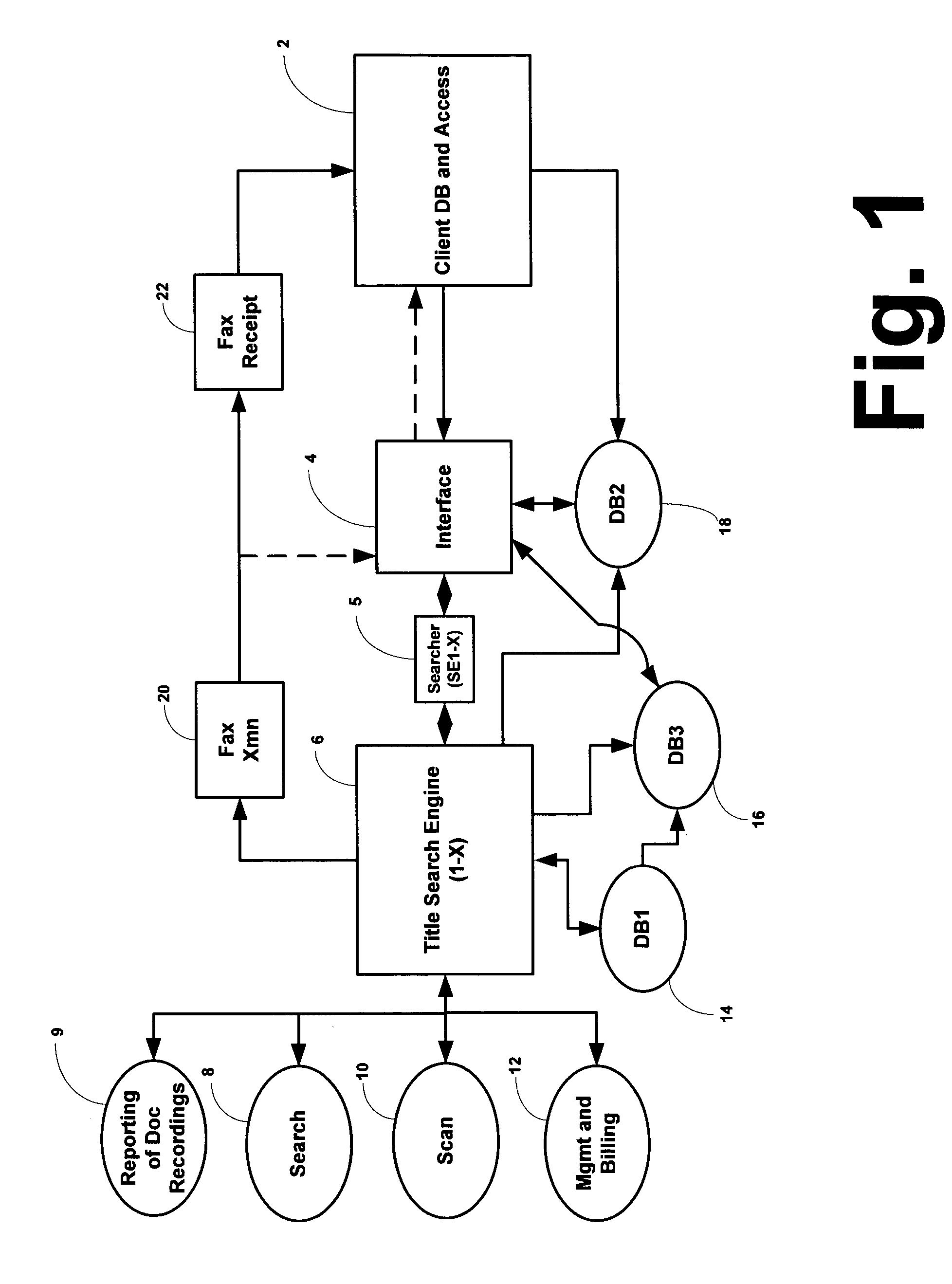
System and method for automated title searching and reporting, reporting of document recordation, and billing
InactiveUS20060020541A1Efficient and rapid mannerFinancePayment architectureDocumentation procedureFacsimile transmission
A method and system for automated title searching and reporting, having one or more generally geographically located computers each having software and one or more databases; an interface for receiving instructions from one or more clients setting forth desired title information for one or more pieces of property such that the interface determines which of said computers to which to send the received instructions and communicates those instructions; searching and gathering data concerning the desired title information from a multiplicity of locations including regional records (from county clerk(s)), an intranet or the Internet; each of the computers via its software, presenting one or more screens for interpolation of data concerning said desired title information; interpolating the data into one or more screens; storing the interpolated data on one of the database(s); and transmitting the interpolated data to the proper client. Additionally, the method and system provides for logging each of its uses, archiving the data, providing access to the archived data by the proper client, reporting the recordation of documents relating to title information, management of all the data and billing the proper client and / or examiner (or user) for the use of the method and system in the manner proscribed, and facsimile transmission either by way of fax software or by hard copy.
Owner:GOMMLICH CHRIS
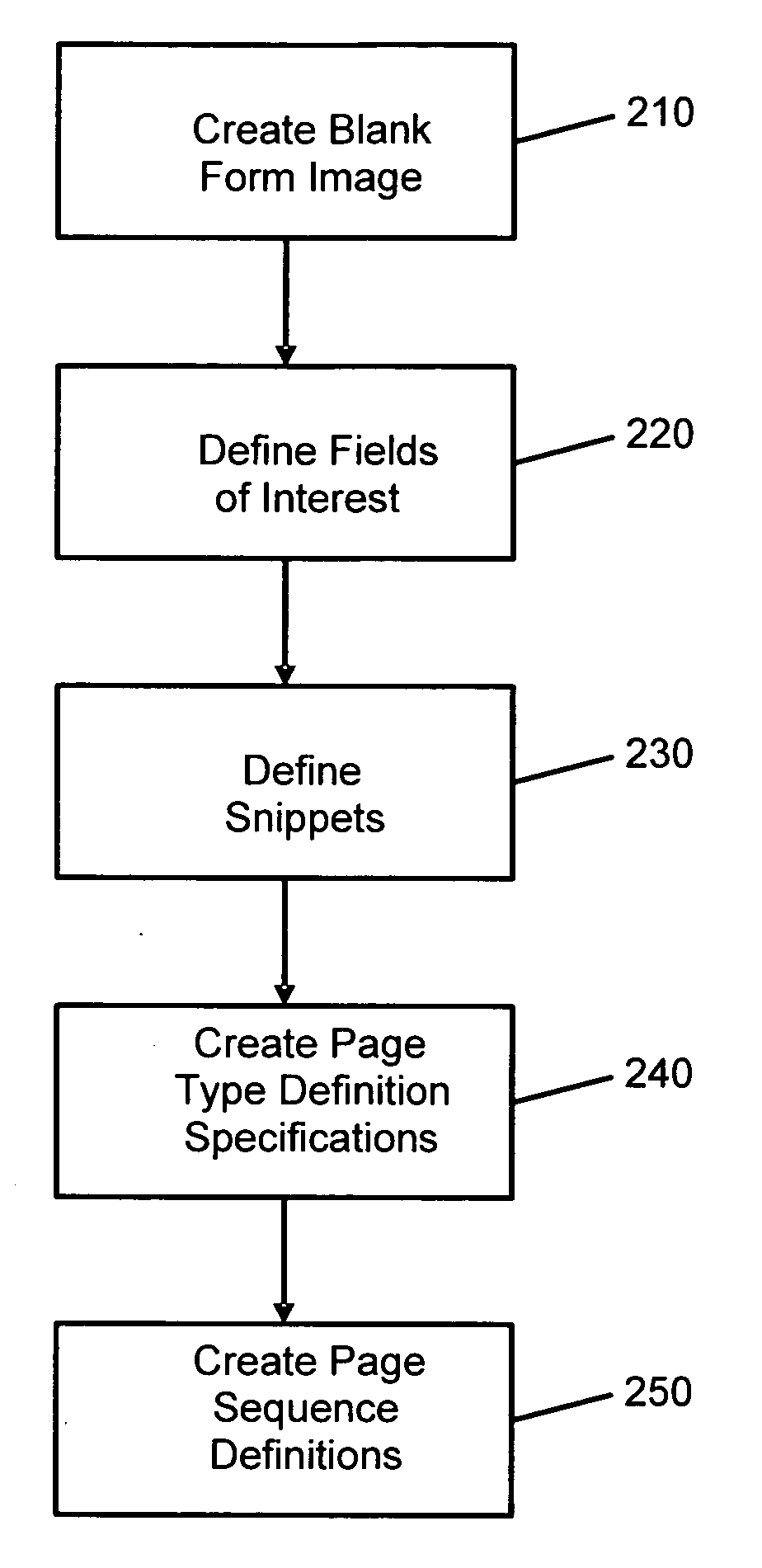
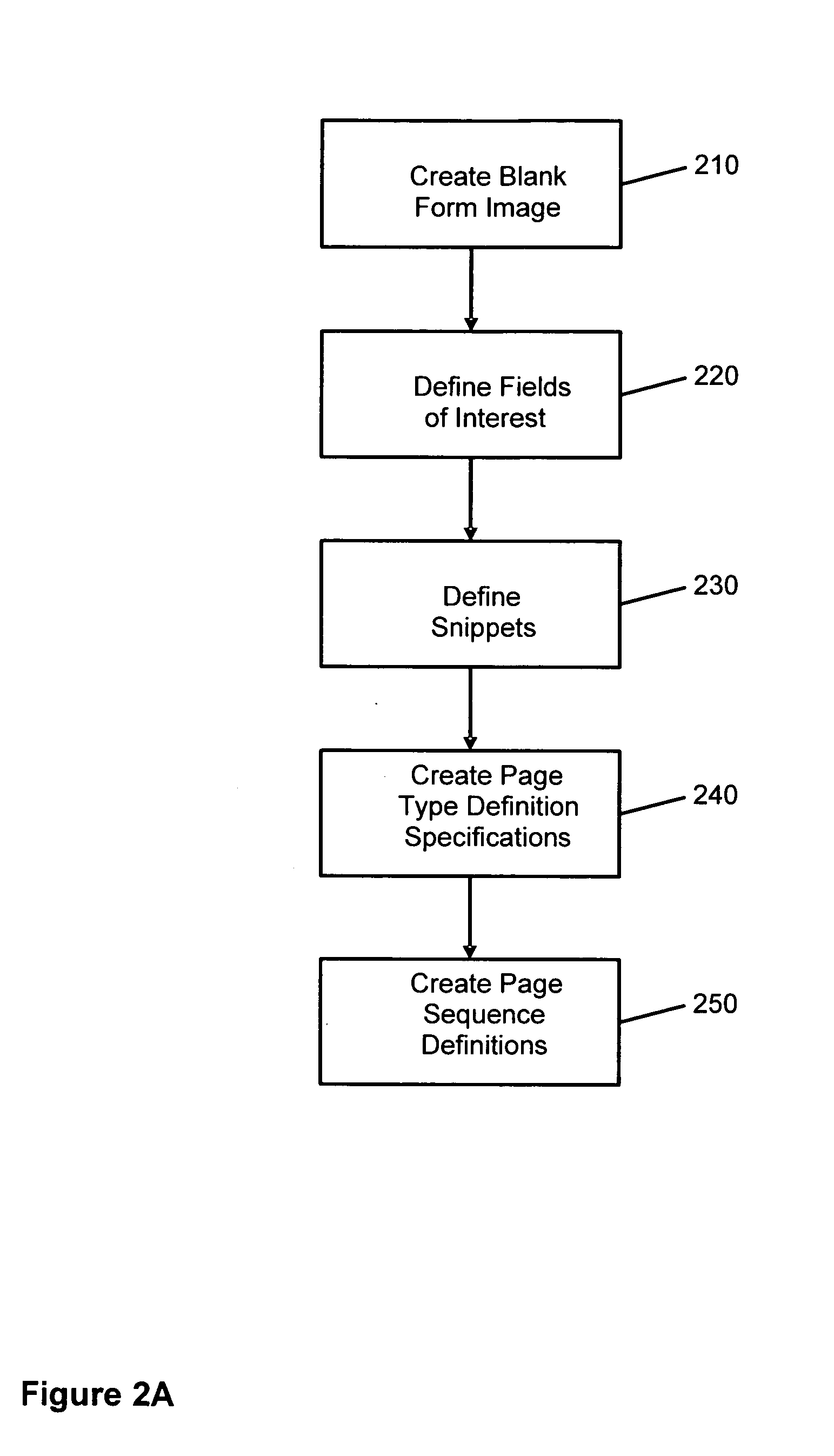
System and method for electronically processing document images
InactiveUS7529408B2Character and pattern recognitionElectrographic process apparatusElectronic documentData scraping
The system and method facilitate the control and management of information and actions related to the computerized scanning, categorization, processing, storage, and retrieval of paper documents and electronic document images for the purposes of creating electronic data; data entry; data capture; data classification and categorization; and document-, file-, and records-management. The systems and methods facilitate the conversion of paper documents into electronic images and into more useful forms.
Owner:ICHANNEX CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com