Patents
Literature
131results about How to "Alteration can be prevented" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
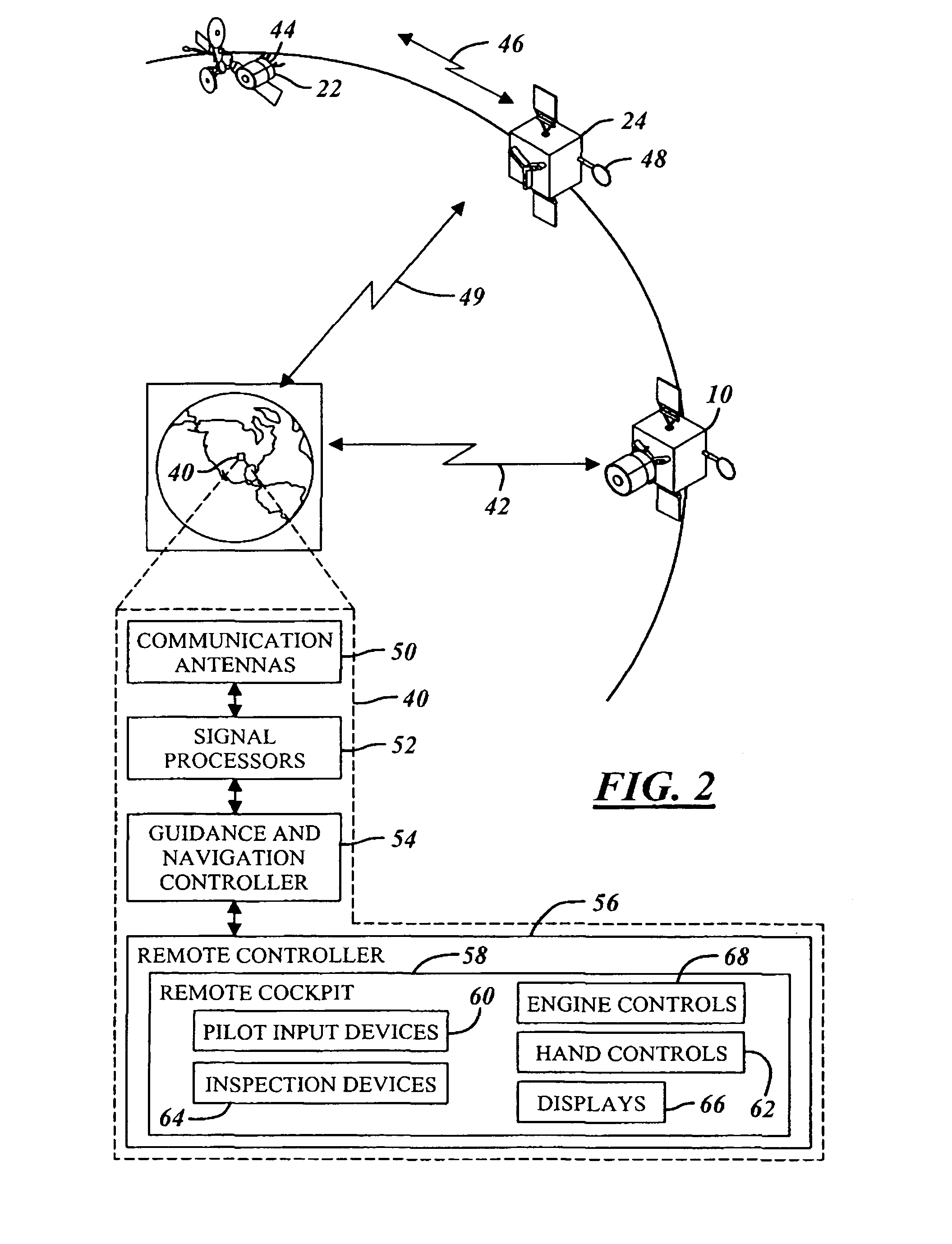
Auditable security for cargo containers and other repositories
ActiveUS20060164232A1Alteration can be preventedCo-operative working arrangementsSubscribers indirect connectionMotor vehicle partLaptop
This invention relates to a method and system for authenticating and for preventing alteration of histories of events occurring within at least one repository (e.g. a cargo container, fixed warehouse or a movable vehicle) for objects (e.g. auto parts, pharmaceutical materials, computer parts, laptops, etc.) held for a period of time, where the repository is exposed to an unauthorized intrusion therewithin (and potential theft of said objects therefrom and potential insertion of dangerous items therewithin). The events include changes in environmental conditions (e.g. light levels, infrared levels, temperature, air pressure, etc) which indicate an unauthorized intrusion.
Owner:VISIBLE ASSET INC
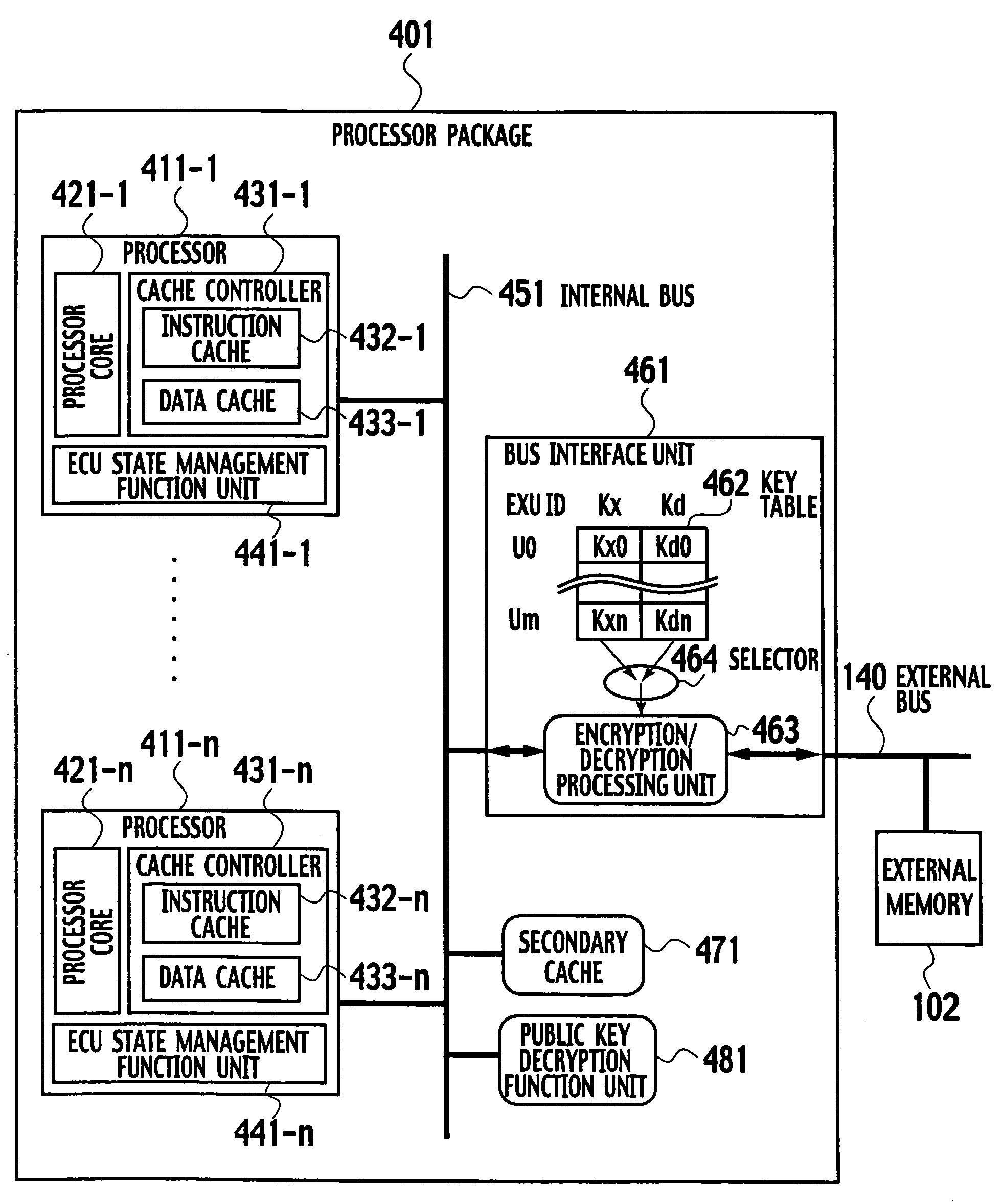
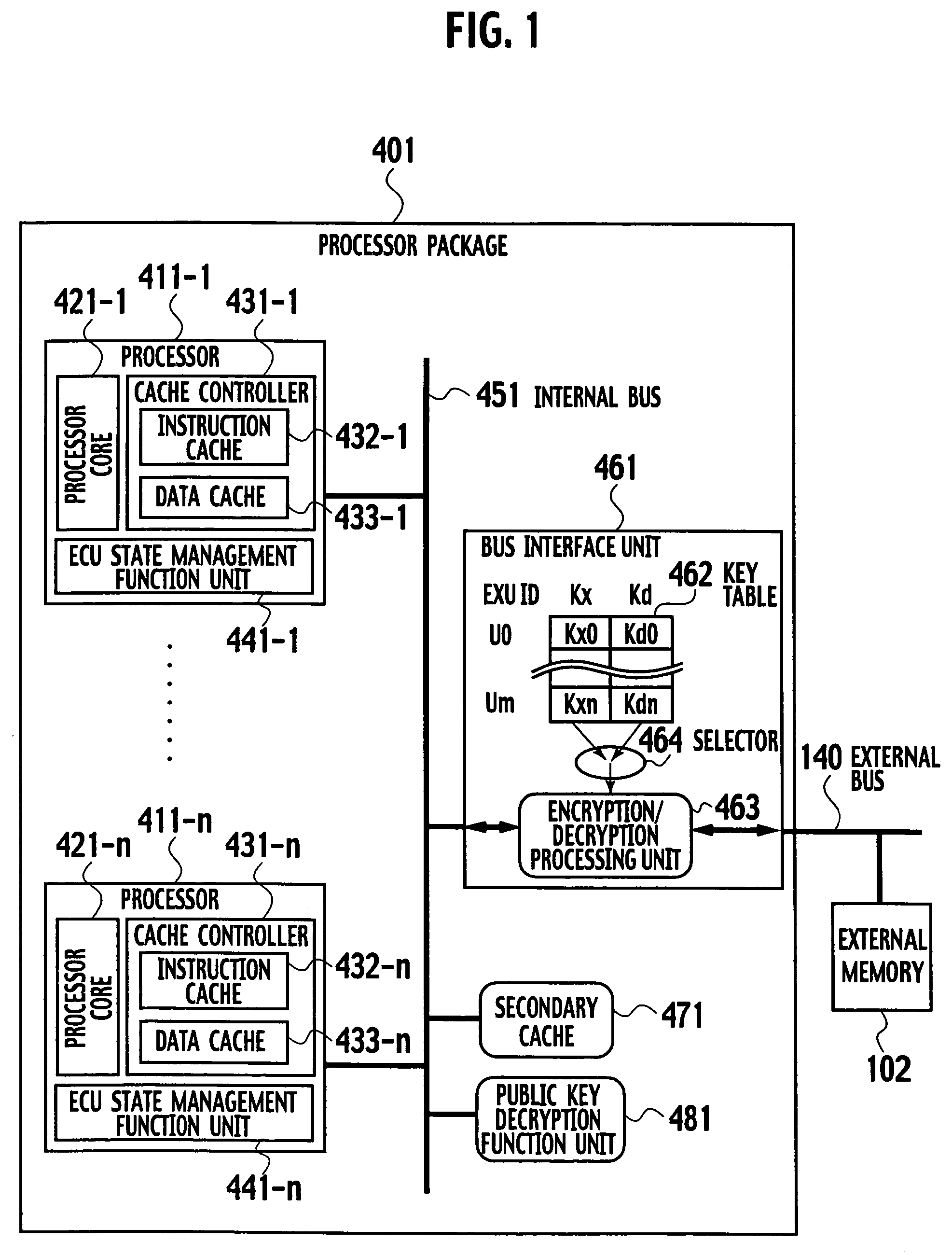
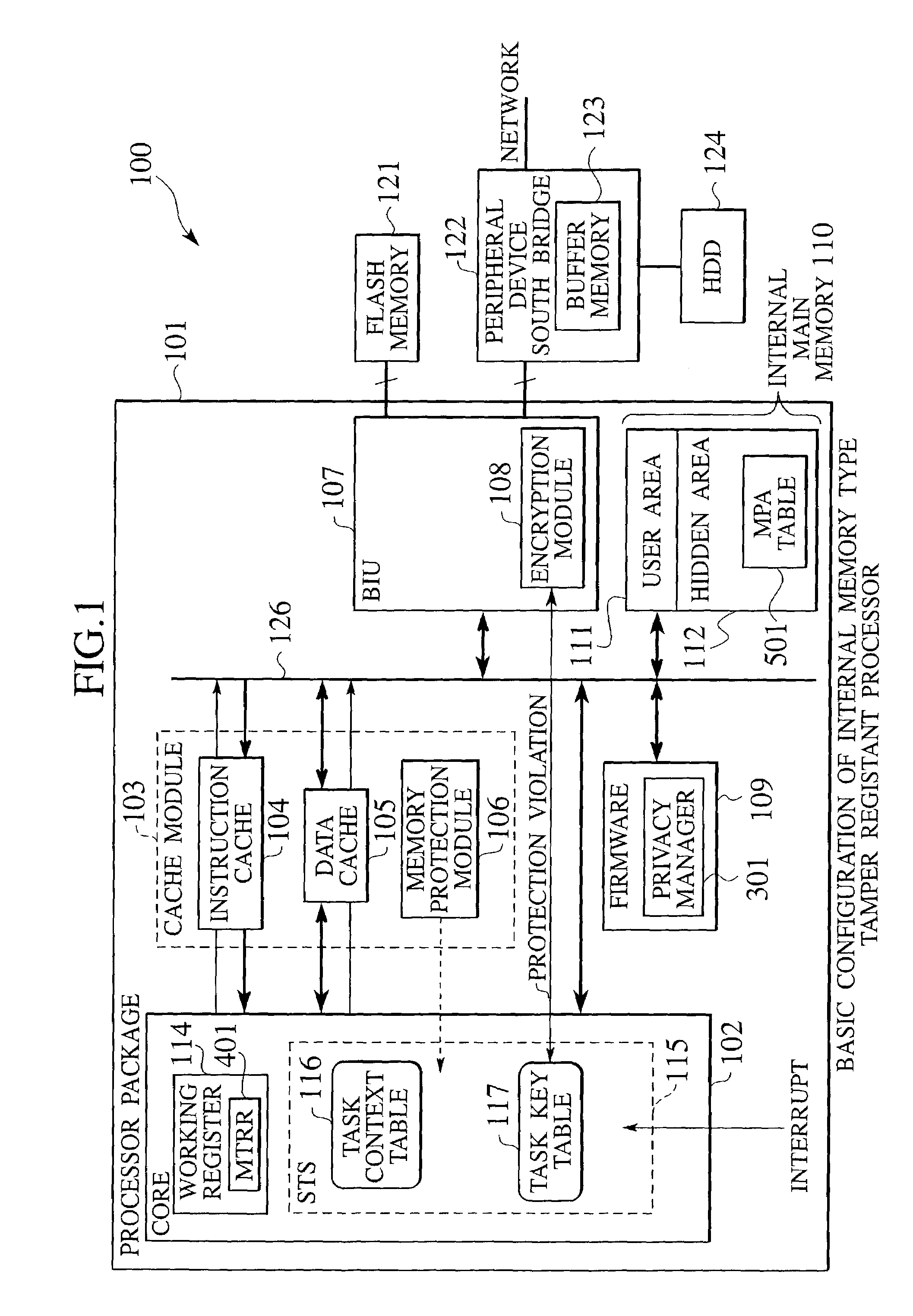
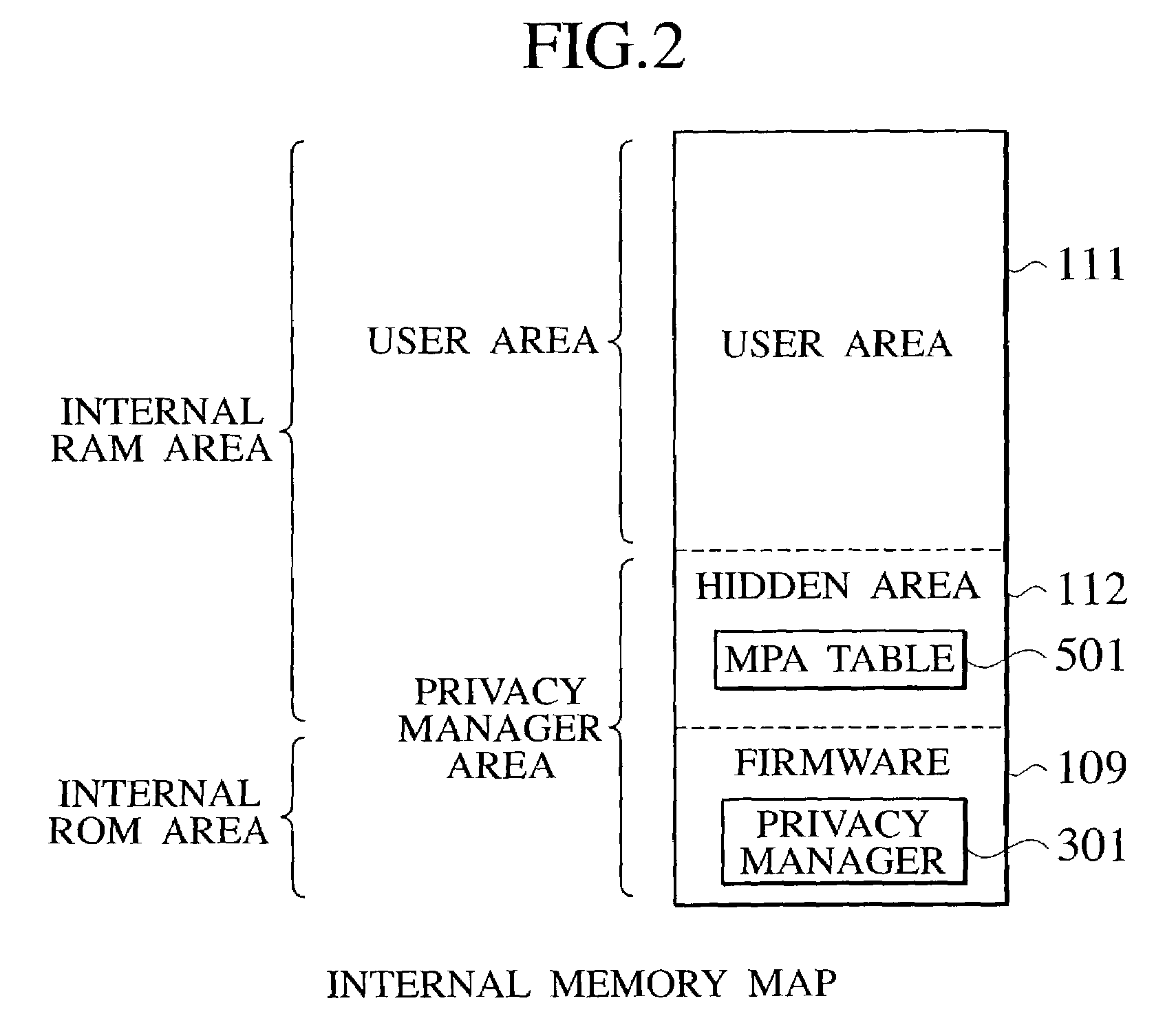
On-chip multi-core type tamper resistant microprocessor
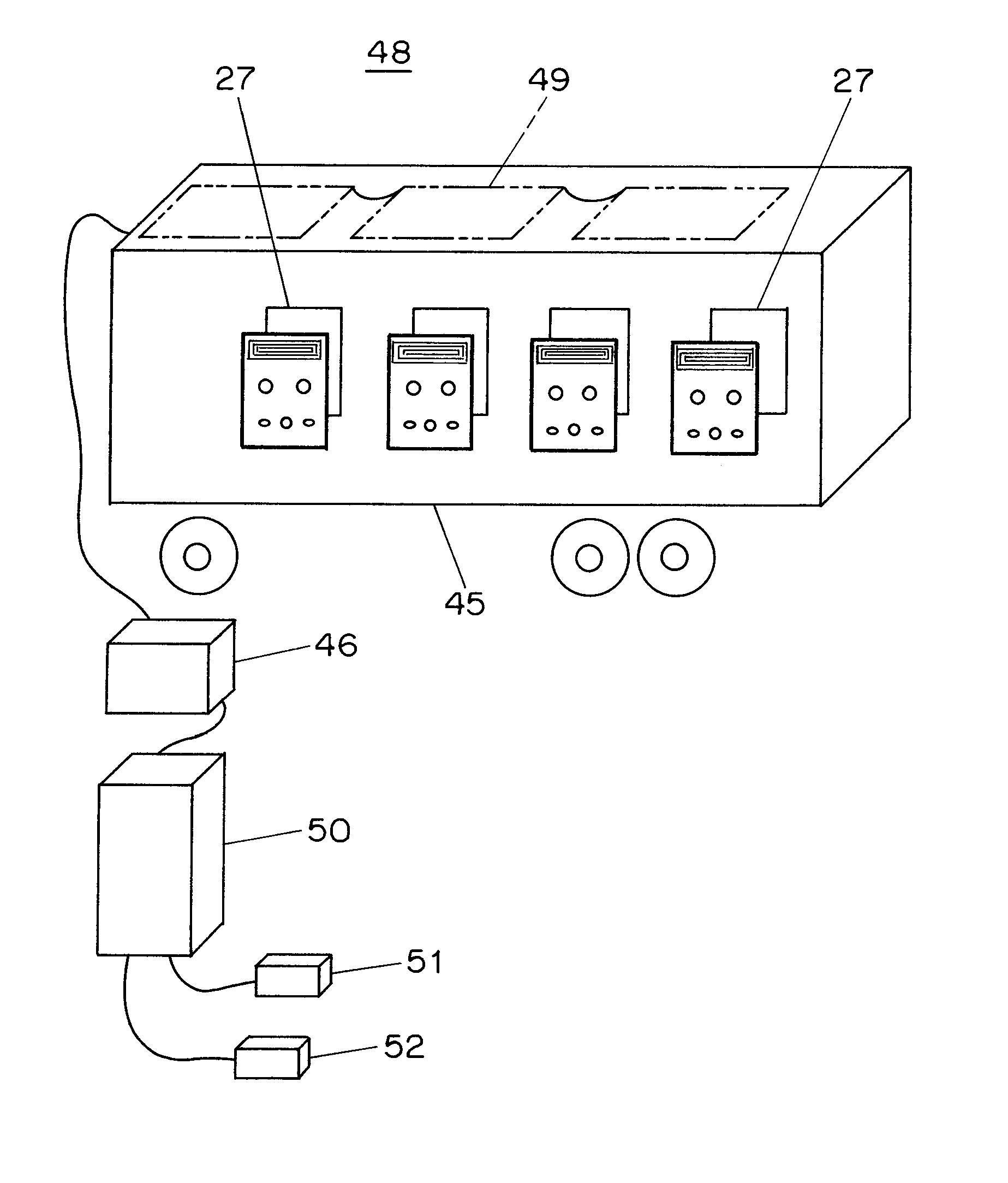
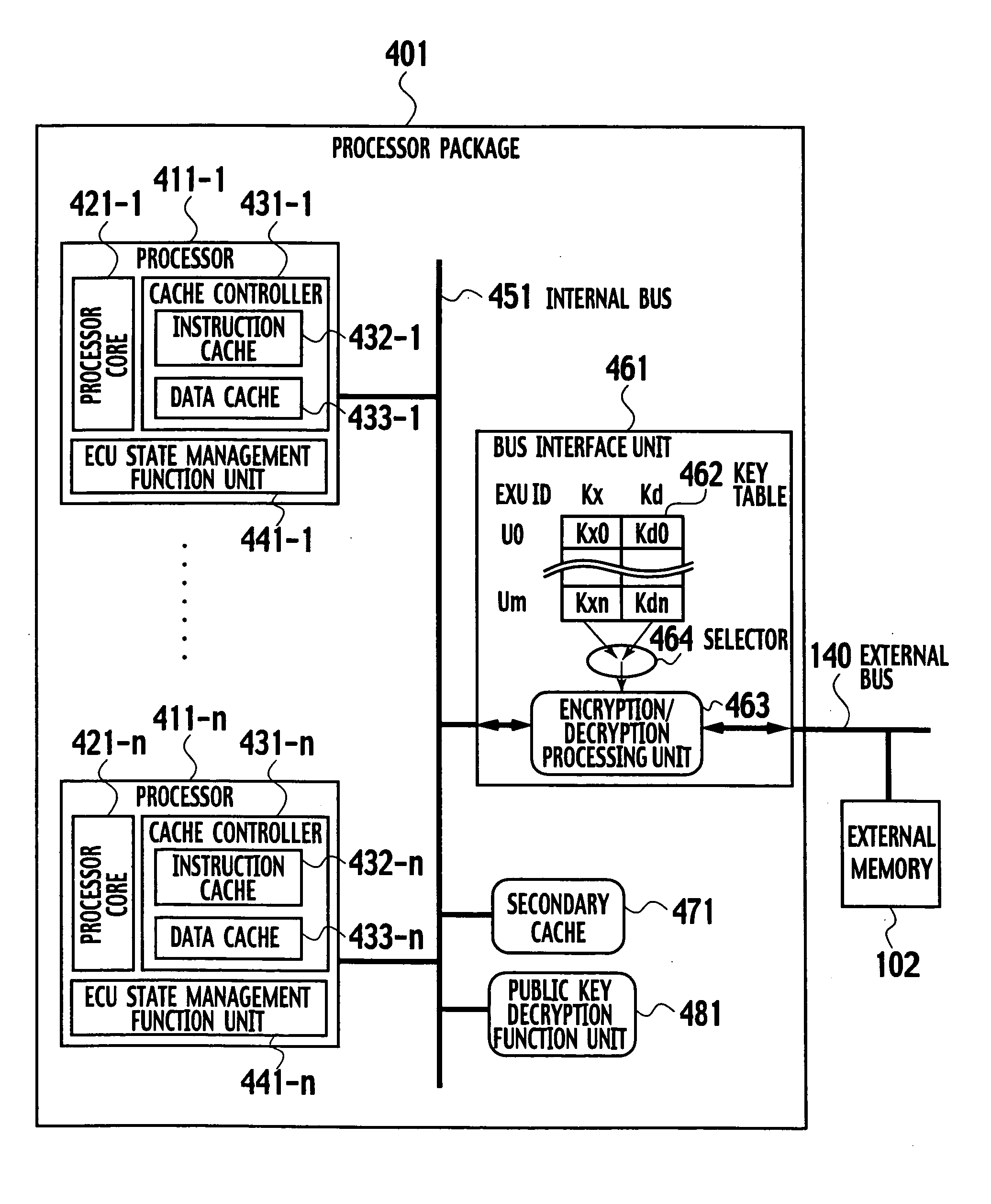
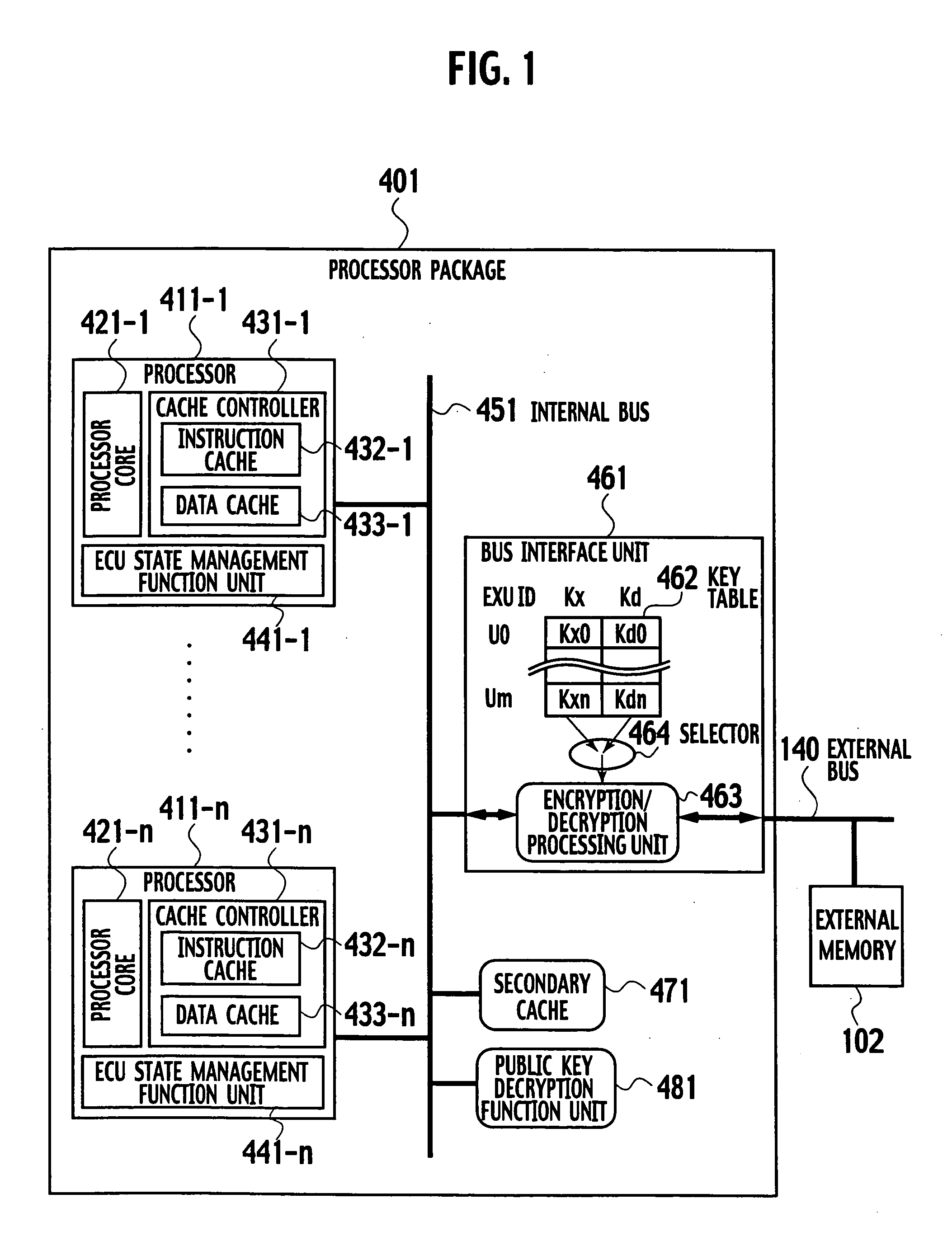
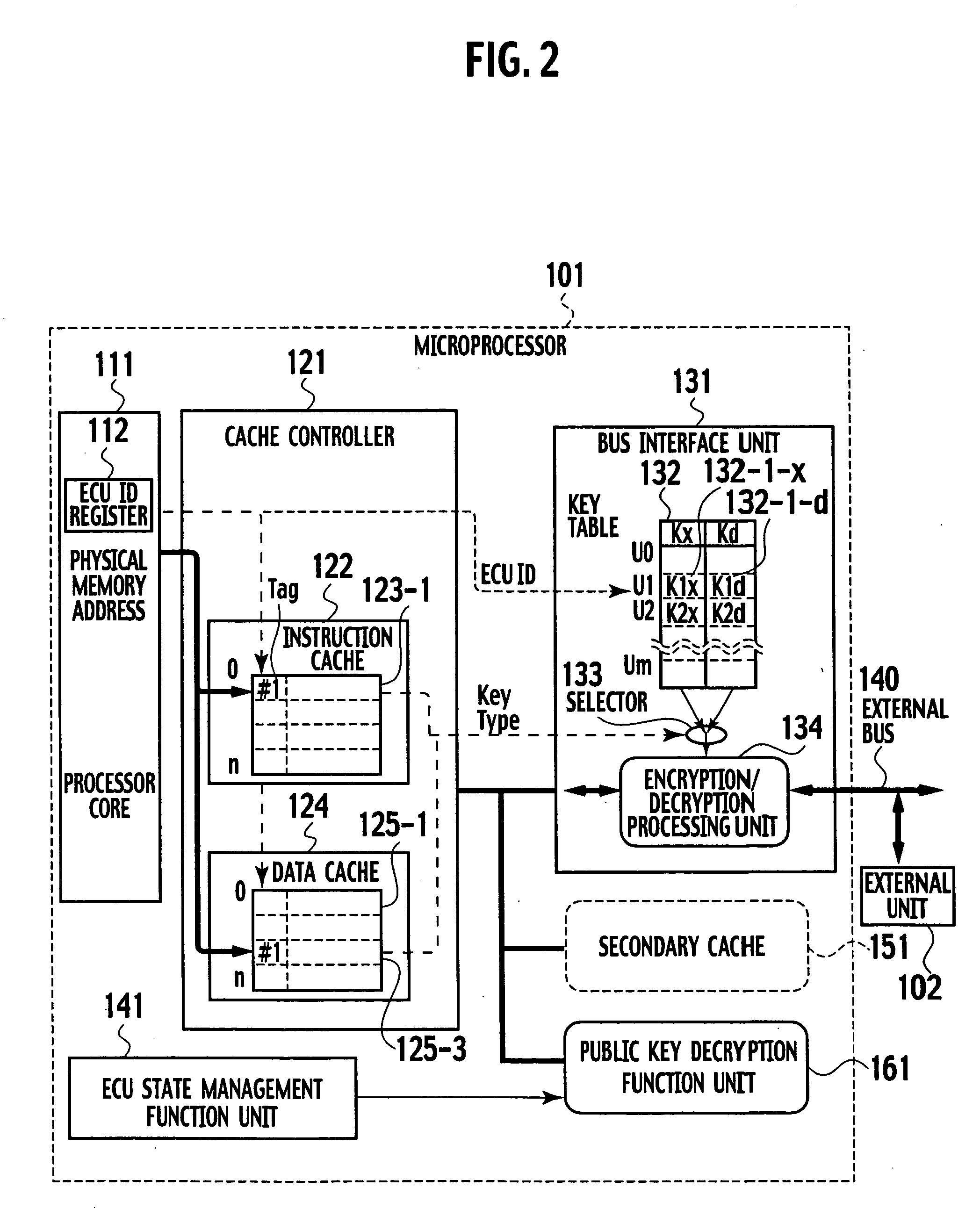
ActiveUS20050105738A1Preventing illegal alterationAlteration can be preventedMultiple keys/algorithms usageDigital data processing detailsMulti processorMicroprocessor
The on-chip multi-core type tamper resistant processor has a feature that, on the microprocessor package which has a plurality of instruction execution cores on an identical package and an ciphering processing function that can use a plurality of ciphering keys in correspondence to programs under a multi-task program execution environment, a key table for storing ciphering keys and the ciphering processing function are concentrated on a single location on the package, such that it is possible to provide a tamper resistant microprocessor in the multi-processor configuration that can realize the improved processing performance by hardware of a given size compared with the case of providing the key table and the ciphering processing function distributedly.
Owner:KK TOSHIBA
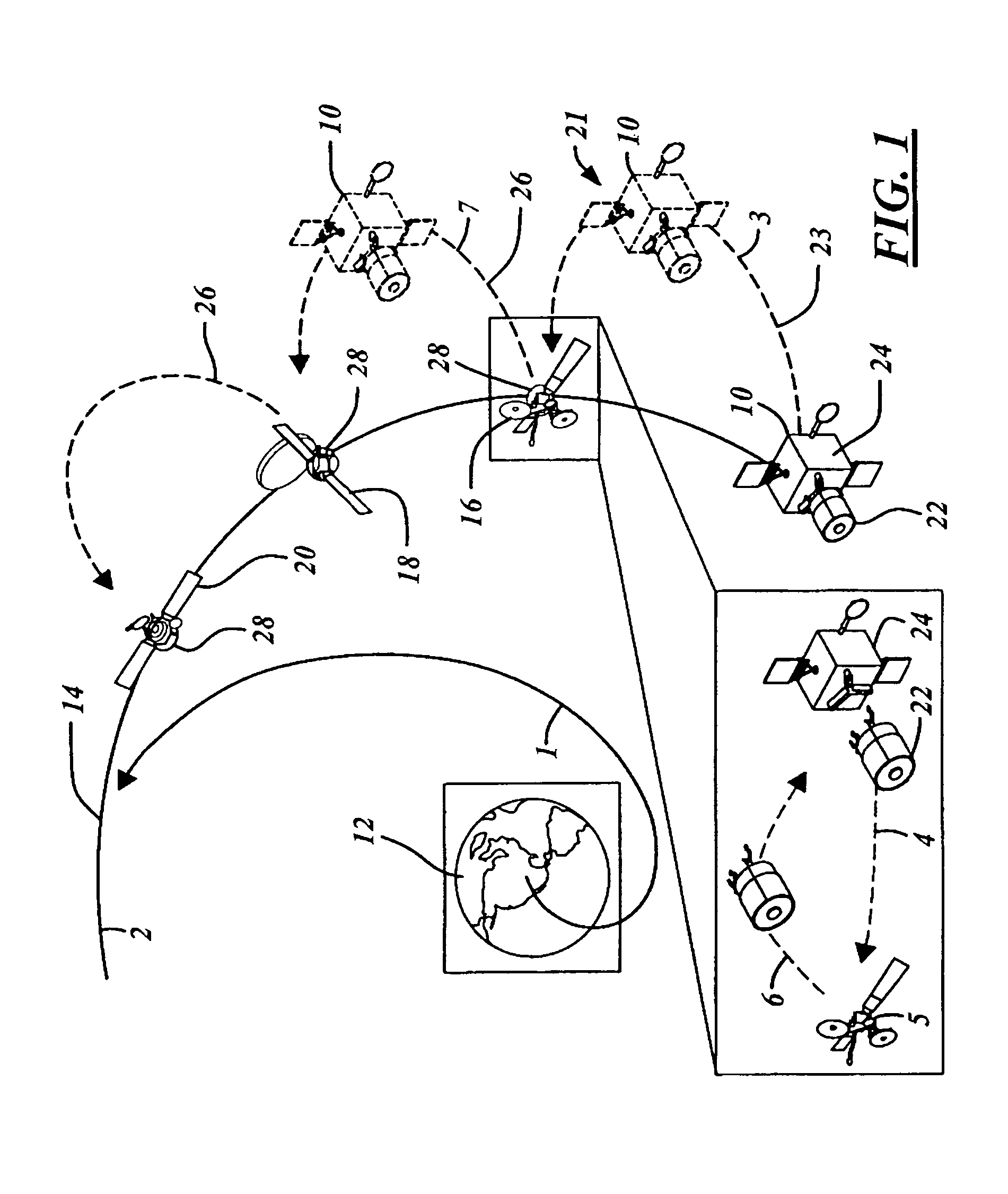
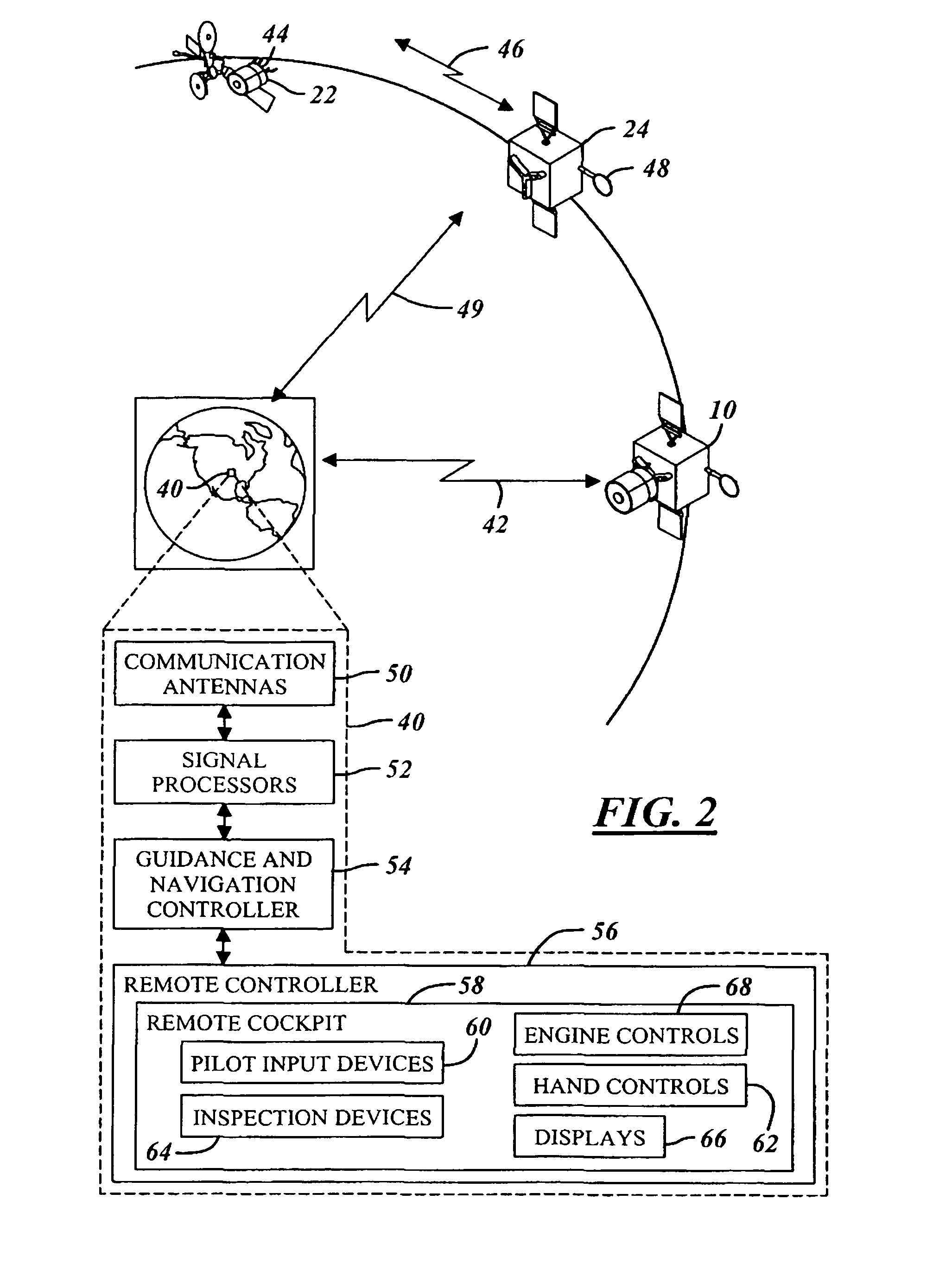
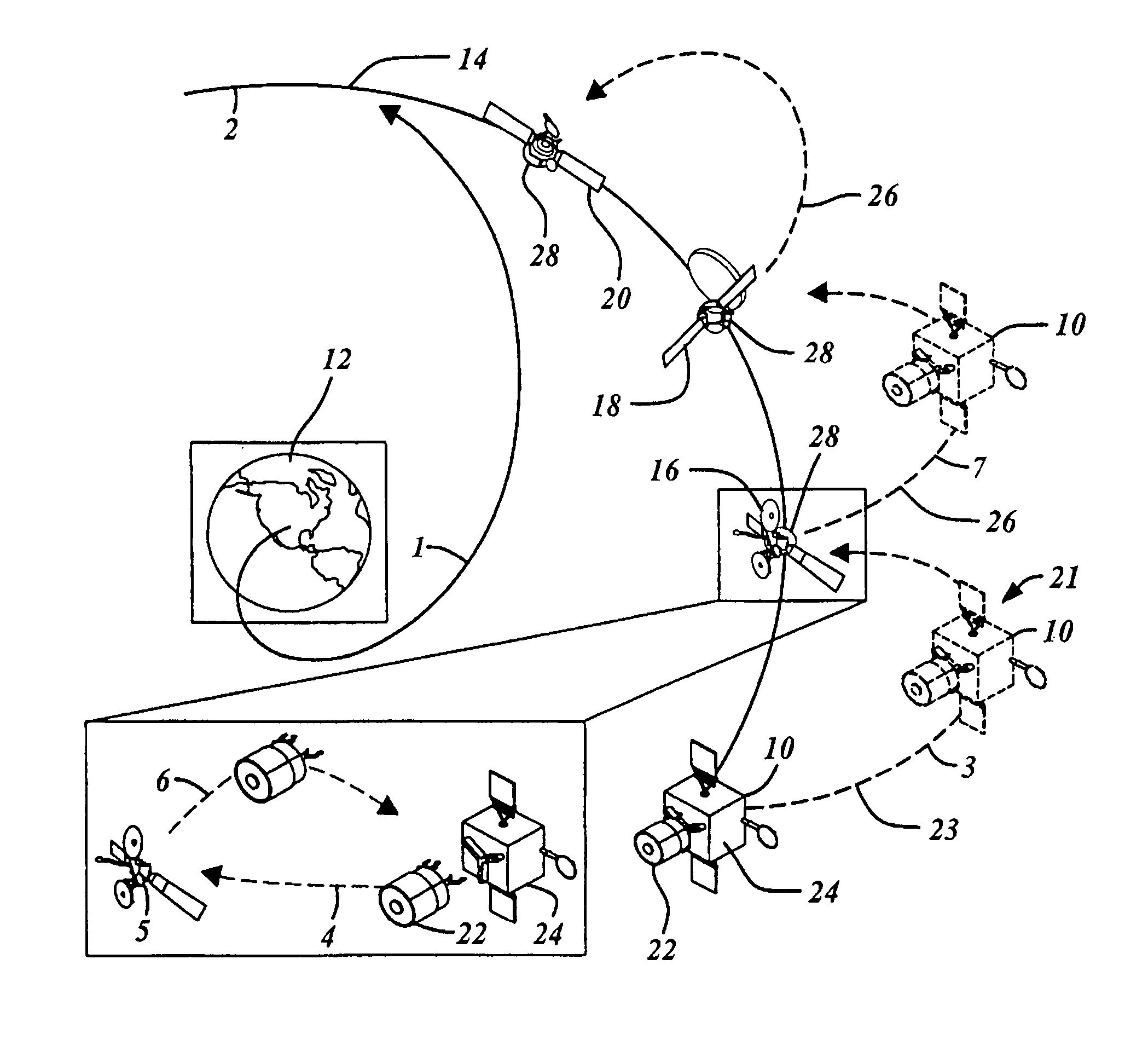
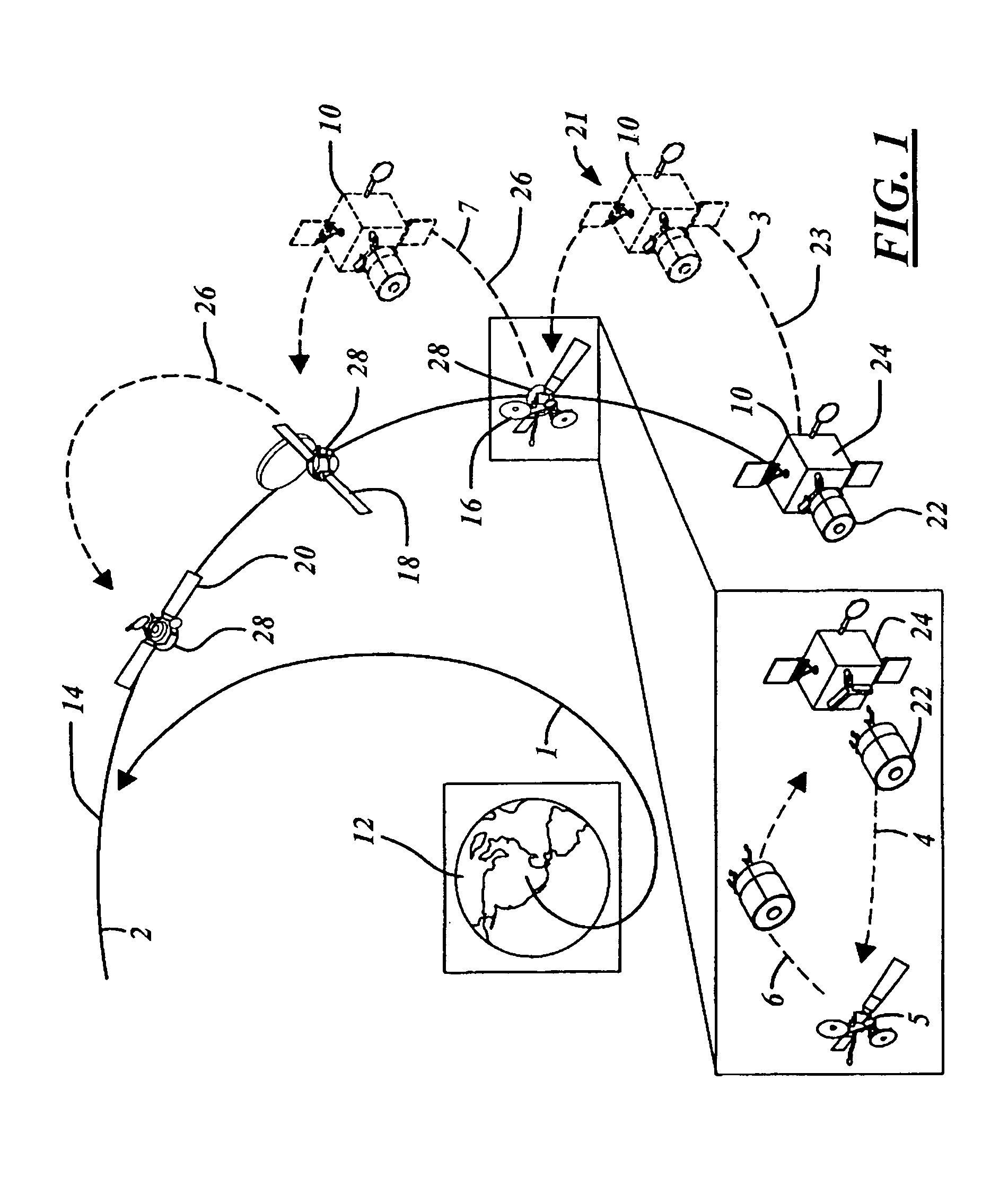
Two part spacecraft servicing vehicle system with adaptors, tools, and attachment mechanisms
InactiveUS20070228220A1Minimize requirementReliable connectionCosmonautic vehiclesCosmonautic component separationService systemFlight operations
Owner:THE BOEING CO
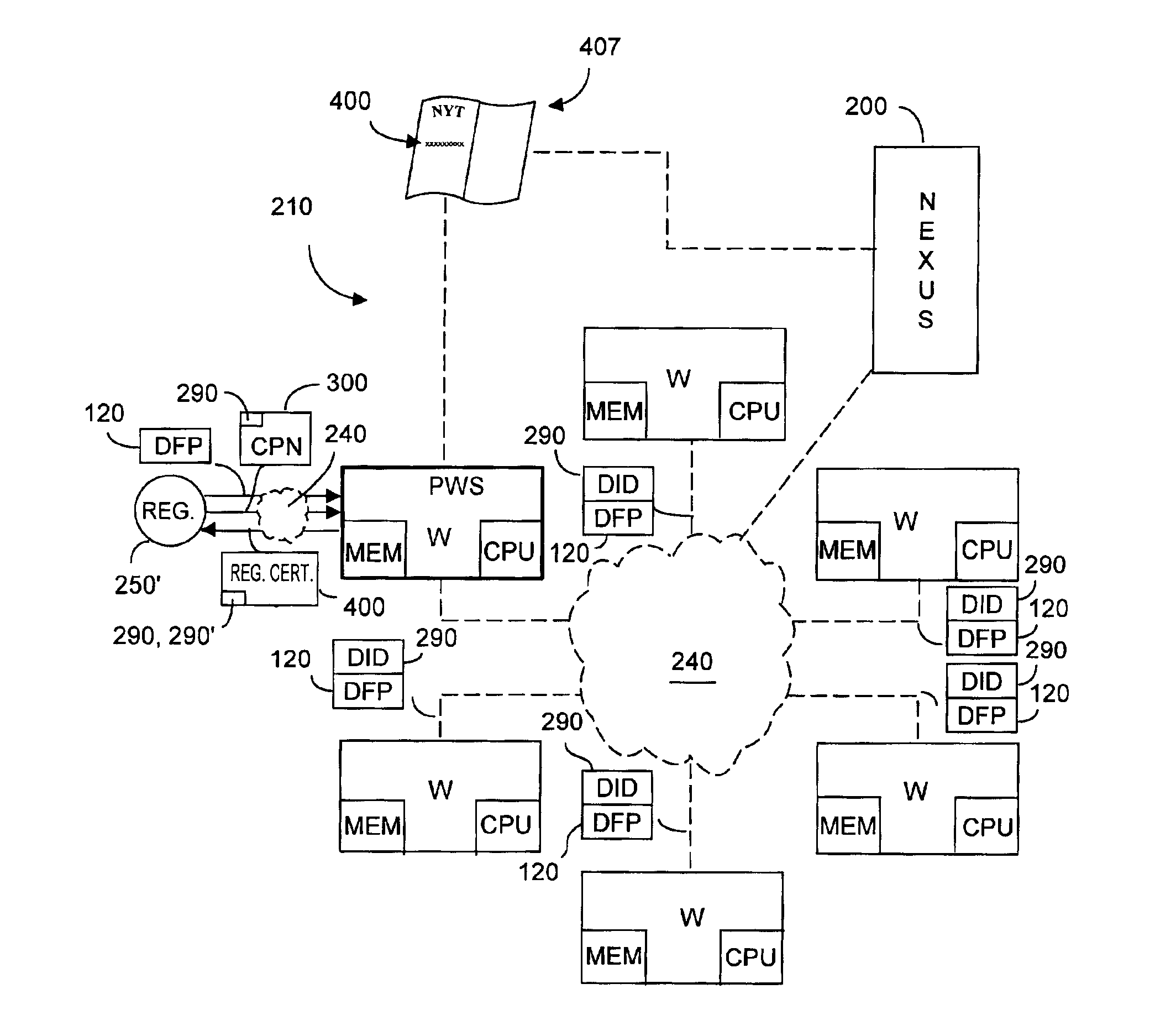
Distributed information system and protocol for affixing electronic signatures and authenticating documents
InactiveUS6938157B2System overhead associated with couponsImprove effectivenessUser identity/authority verificationUnauthorized memory use protectionCryptographic hash functionCryptogram
A system can process a digital representation (DF) of a document with a one-way cryptographic hash function (CHF) to yield a digital fingerprint (DFP) value that is associated with the DF. A document identification number (DID) is created, uniquely associated with the DFP, and with DID and DFP are associated optional credential information (C). A registration certificate DFC that represents an optional electronic signature associated with the document and that includes the DID and DFP is promulgated and archived at a plurality of storage locations. The system can authenticate whether a putative document is the original document by generating a digital fingerprint value for the putative document and comparing it to DFP retrieved from various of the storage locations. Authentication can confirm that the electronic signature is unaltered.
Owner:DISTRIBUTED TRUST MANAGEMENT
Wire management system
InactiveUS6101773AEasy accessSpace minimizationPipe supportsPublic buildingsPatch panelComputer module
A wire management system for use with furniture panels and being especially useful for the management of voice and data wiring includes a support plate and a plurality of vertically arranged rows of slots for receiving mounting blocks for patch panel brackets and the like. The slots may be provided in the plate itself or in a series of channel members attached to the plate. The blocks can be rotated 90 degrees to facilitate the connection of wiring to wiring connection devices when the blocks are in a first position and to a second position in which the wires and associated equipment occupy a minimum amount of space. The cover for the wire management system is preferably hinged at the top or side. A lock may be provided therefore for security, and a prop rod may be provided to hold the cover in an open position. In a most preferred embodiment, the plate may be adjusted using telescoping components to accommodate different size openings in the furniture module. In another aspect of the invention, strain relief brackets are provided and are coupled to the slots below the mounting blocks.
Owner:STEELCASE DEV INC
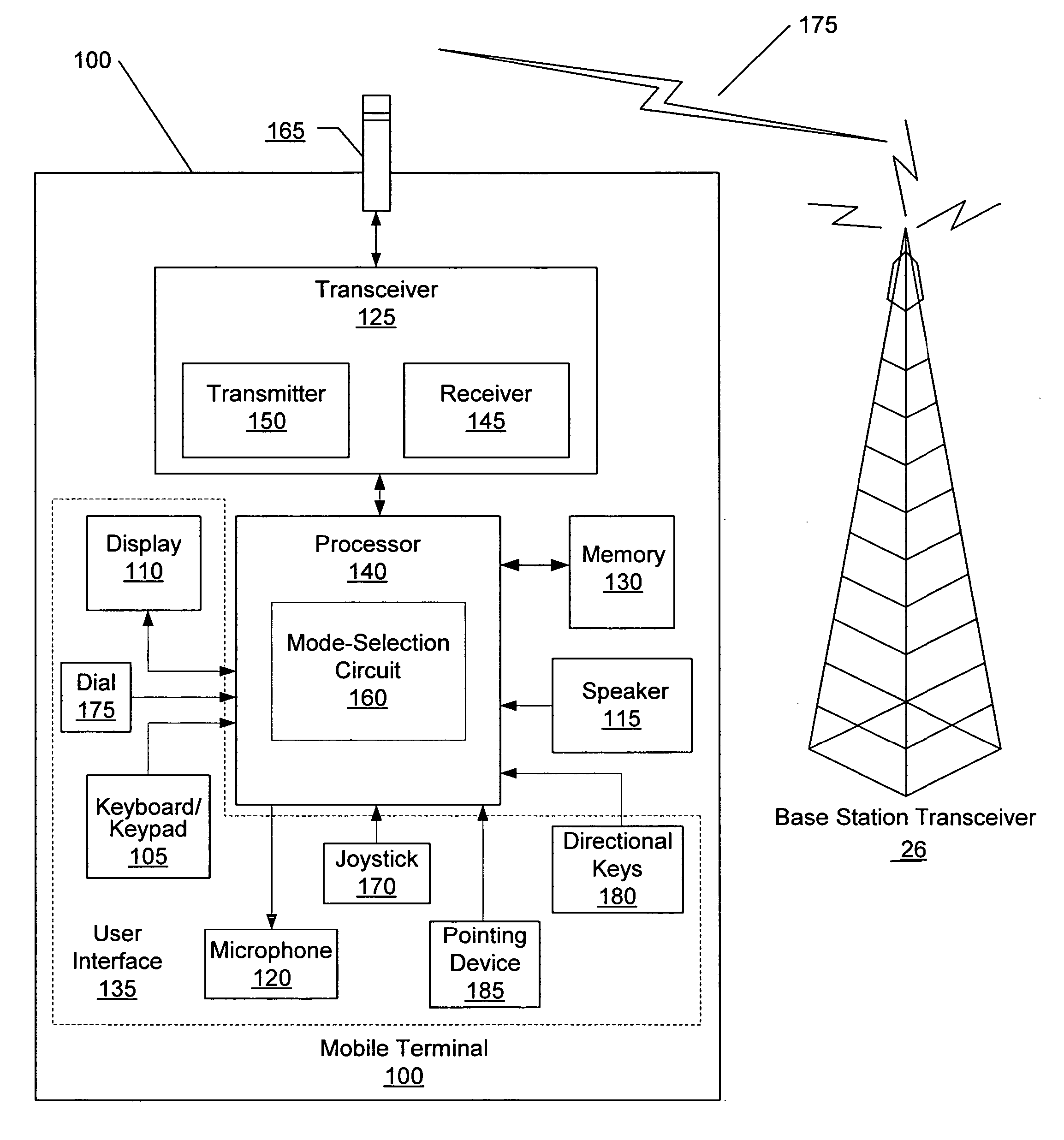
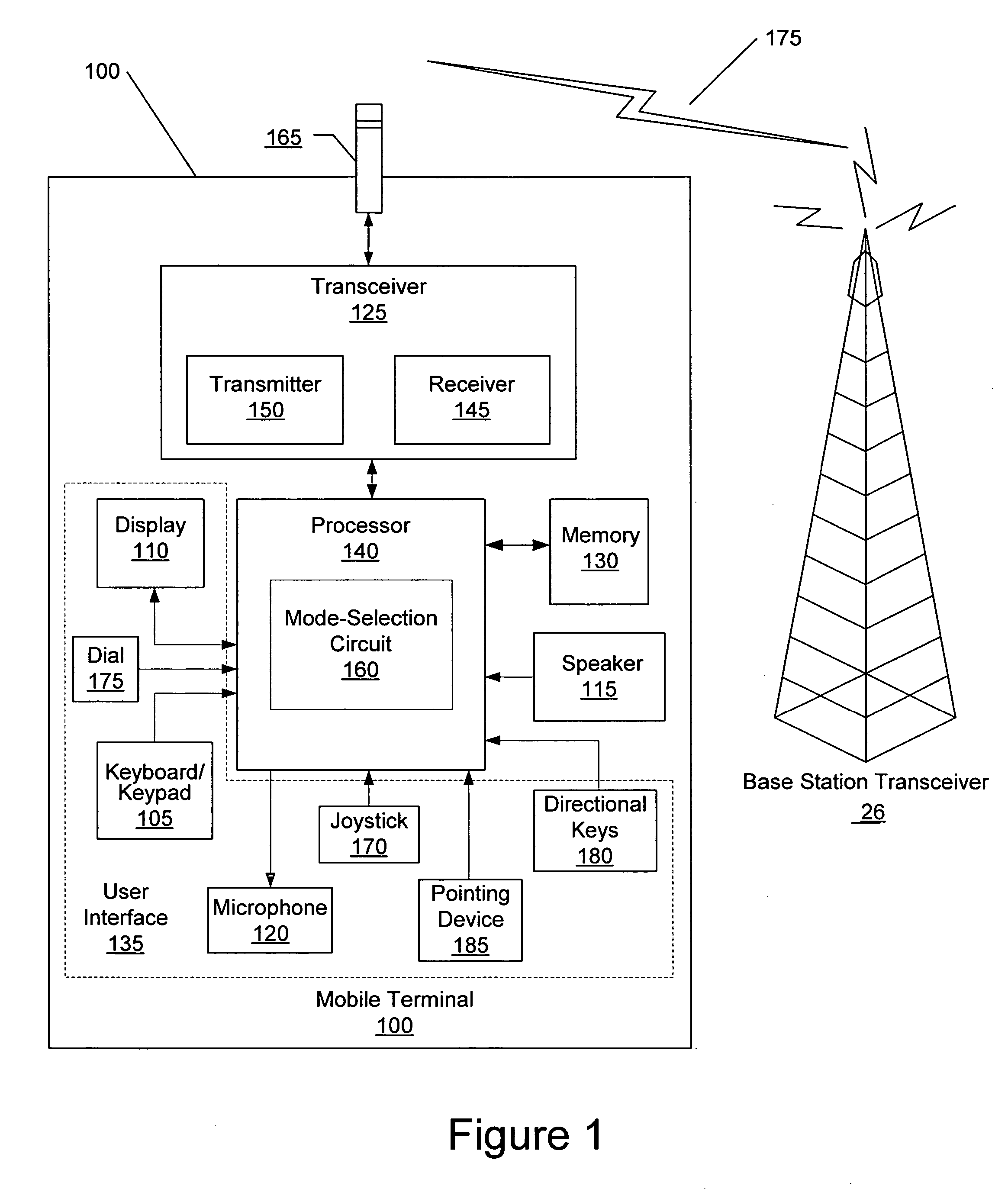
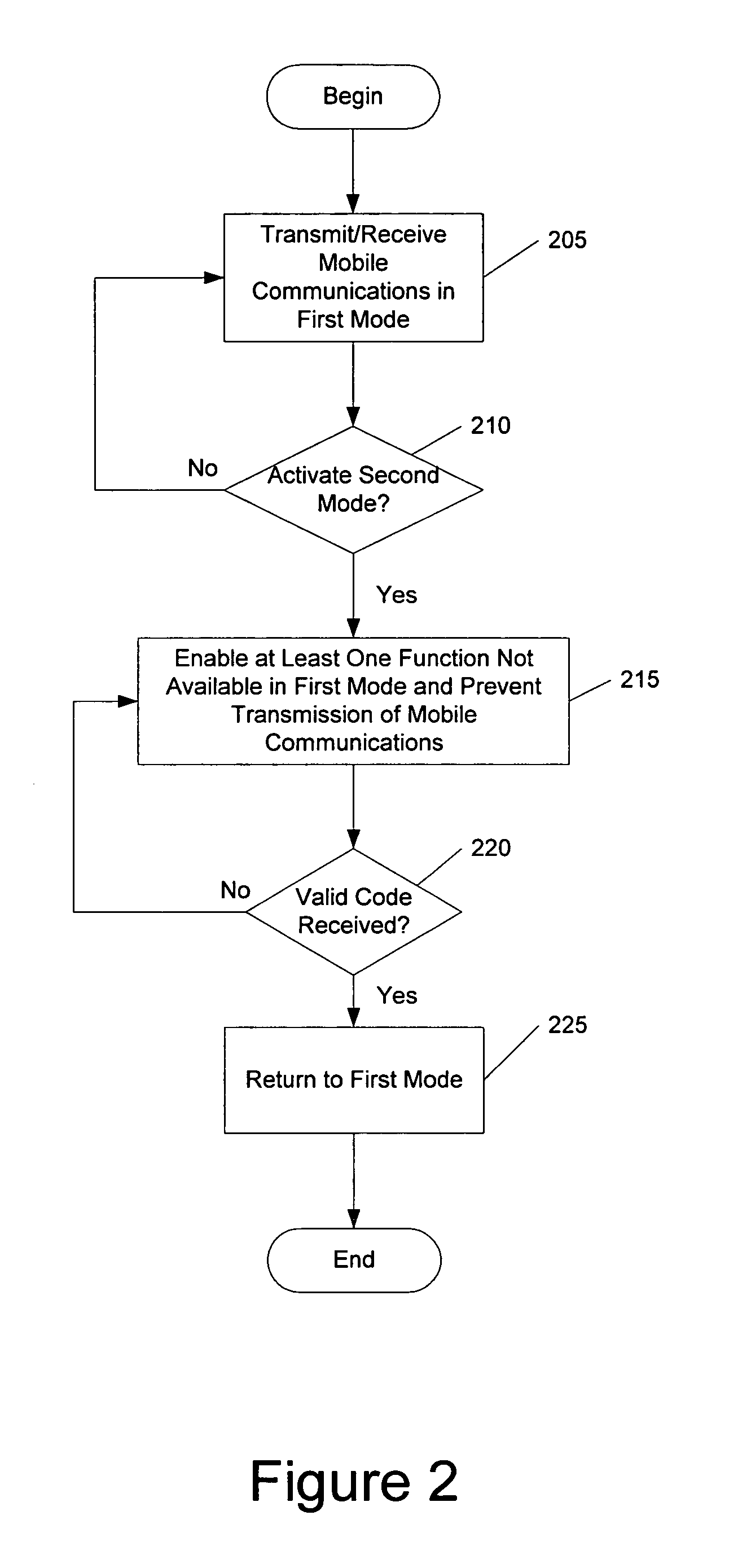
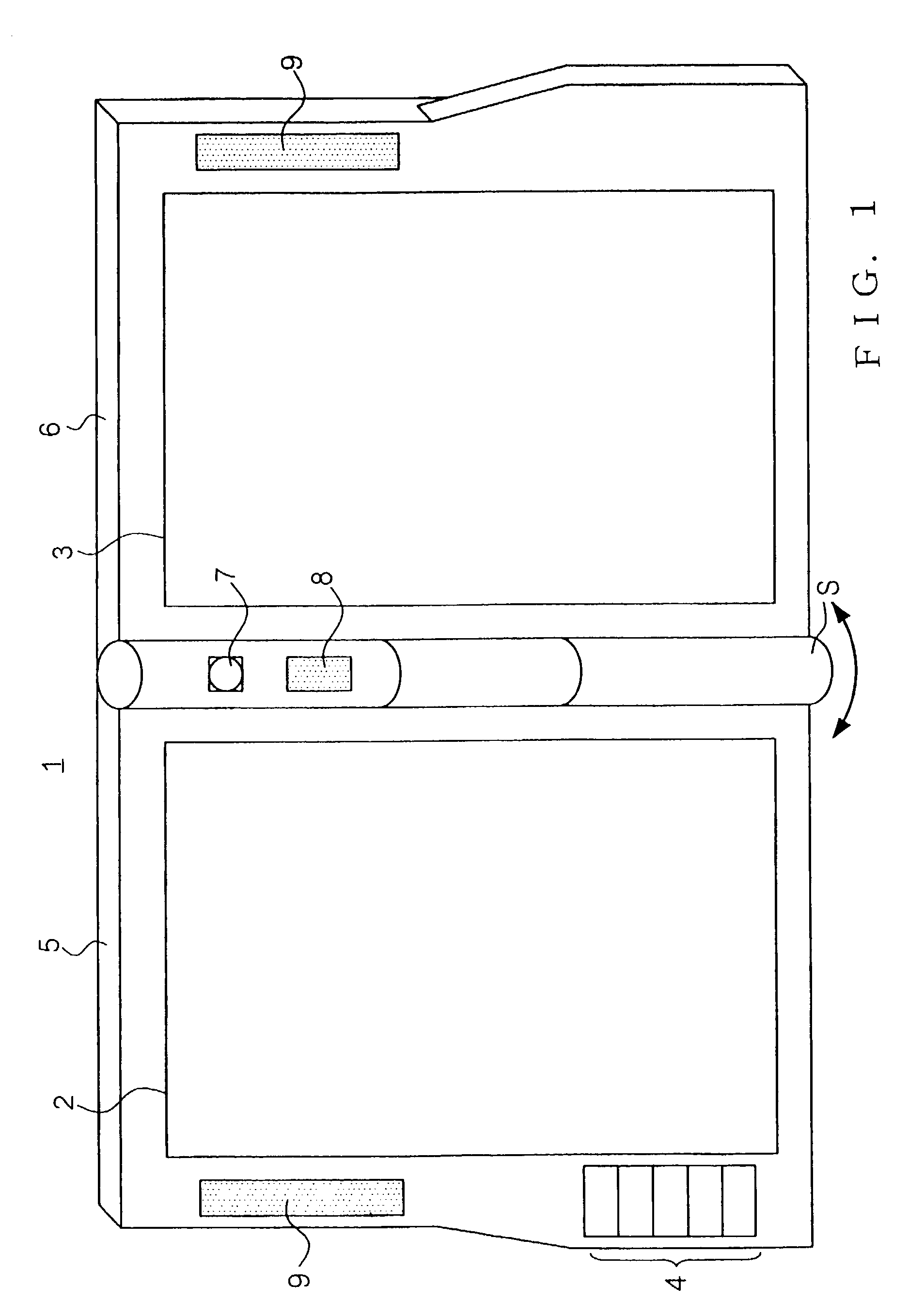
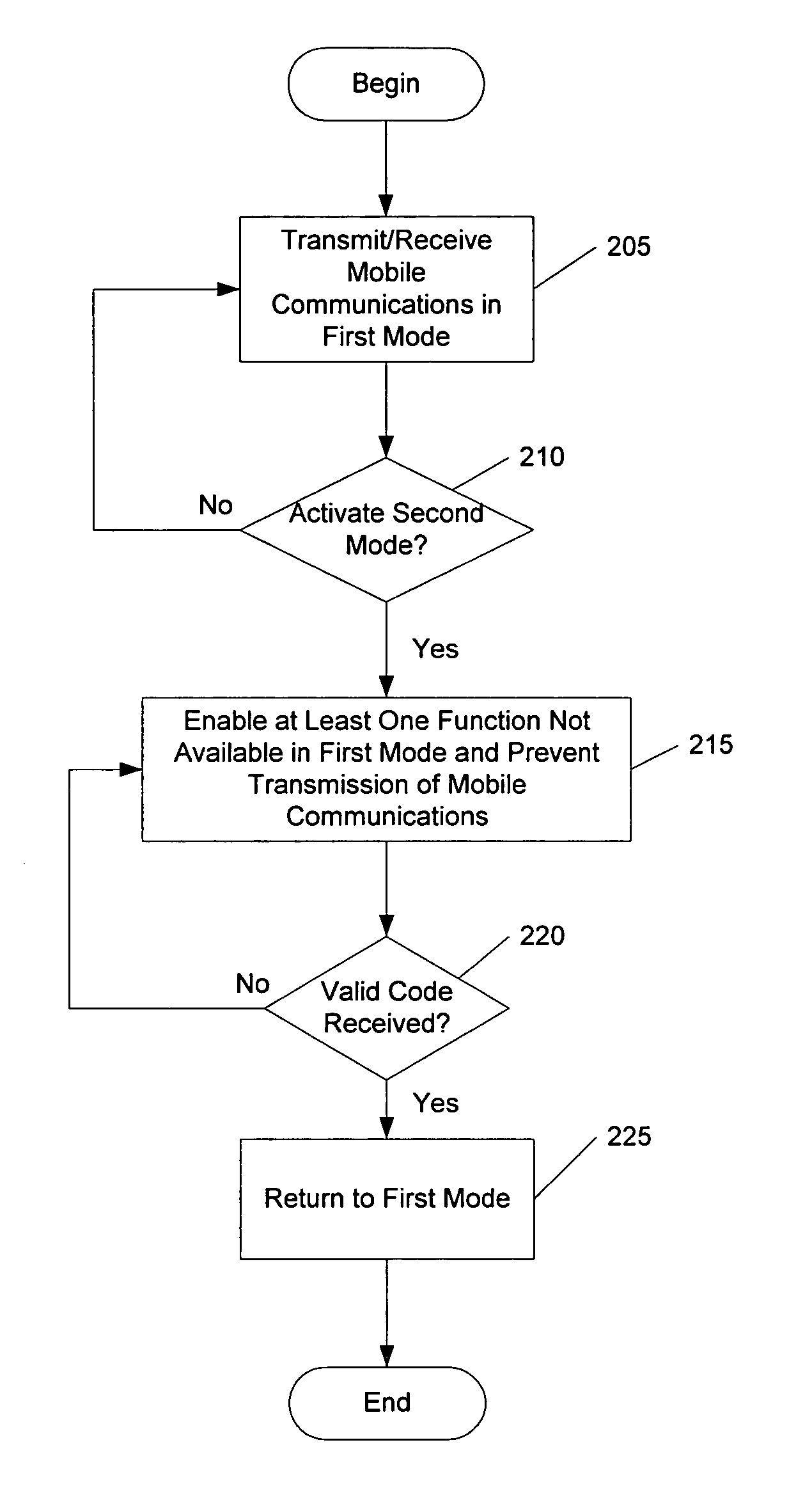
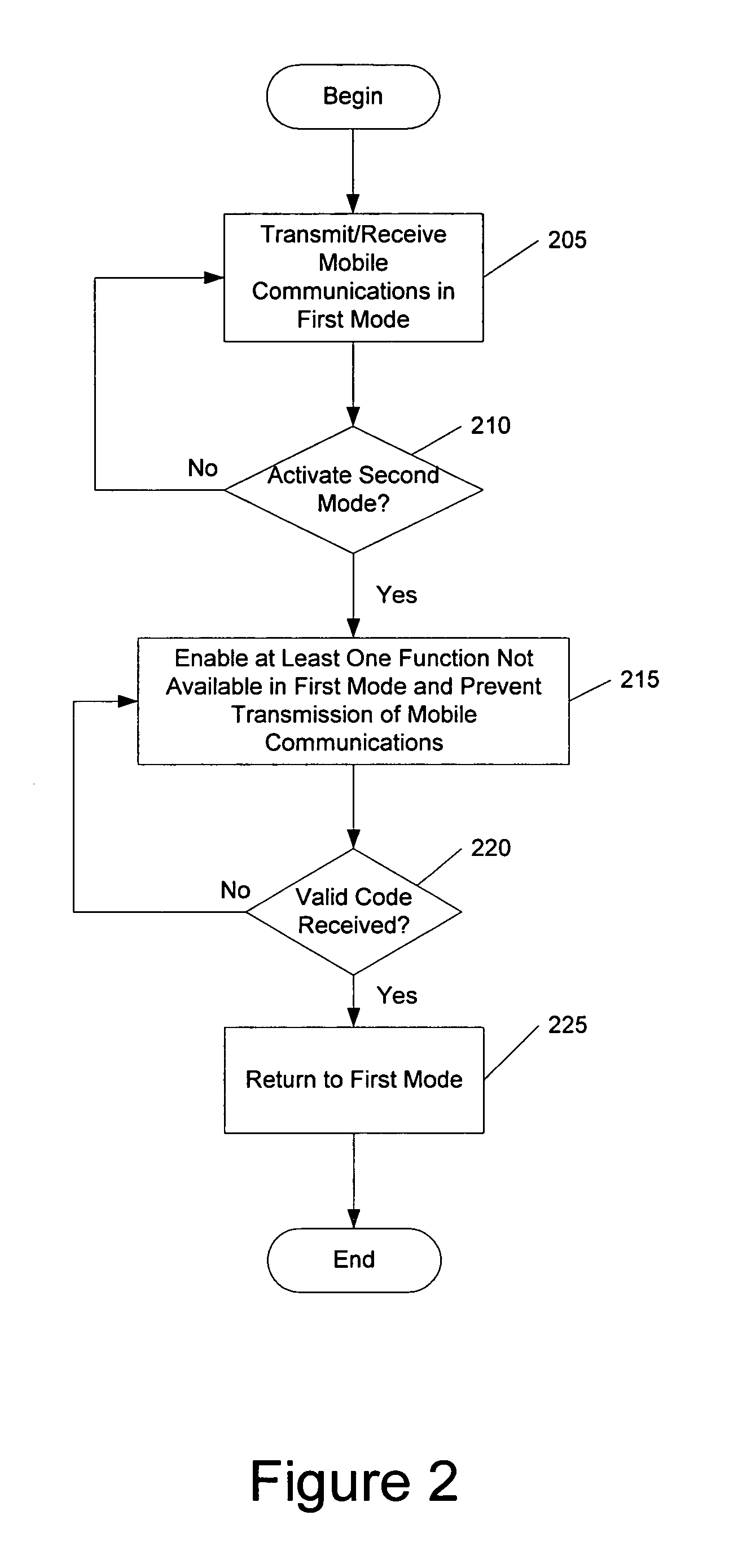
Methods, devices, and computer program products for providing multiple operational modes in a mobile terminal
ActiveUS20060211412A1Avoid changeAlteration can be preventedSubstation equipmentAutomatic exchangesComputer hardwareOperation mode
A method of operating a mobile terminal includes receiving mobile communications and transmitting mobile communications in a first mode of operation, and enabling at least one function that is not available in the first mode of operation while preventing transmission of mobile communications in a second mode of operation. The first mode of operation is activated responsive to receiving a valid authorization code in the second mode of operation. Related devices and computer program products are also discussed.
Owner:SONY CORP
Protective hardmask for producing interconnect structures
InactiveUS6720249B1Deep unityAlteration can be preventedSemiconductor/solid-state device detailsSolid-state devicesSilicon dioxideScratching
The present invention provides a permanent protective hardmask which protects the dielectric properties of a main dielectric layer having a desirably low dielectric constant in a semiconductor device from undesirable increases in the dielectric constant, undesirable increases in current leakage, and low device yield from surface scratching during subsequent processing steps. The protective hardmask further includes a single layer or dual layer sacrificial hardmask particularly useful when interconnect structures such as via openings and / or lines are formed in the low dielectric material during the course of making the final product. The sacrificial hardmask layers and the permanent hardmask layer may be formed in a single step from a same precursor wherein process conditions are altered to provide films of differing dielectric constants. Most preferably, a dual damascene structure has a tri-layer hardmask comprising silicon carbide BLoK(TM), PECVD silicon nitride, and PECVD silicon dioxide, respectively, formed over a bulk low dielectric constant interlevel dielectric prior to forming the interconnect structures in the interlevel dielectric.
Owner:IBM CORP
Two part spacecraft servicing vehicle system with adaptors, tools, and attachment mechanisms
InactiveUS7823837B2Alteration can be preventedRequires minimizationCosmonautic vehiclesCosmonautic component separationAviationPropellant tank
Owner:THE BOEING CO
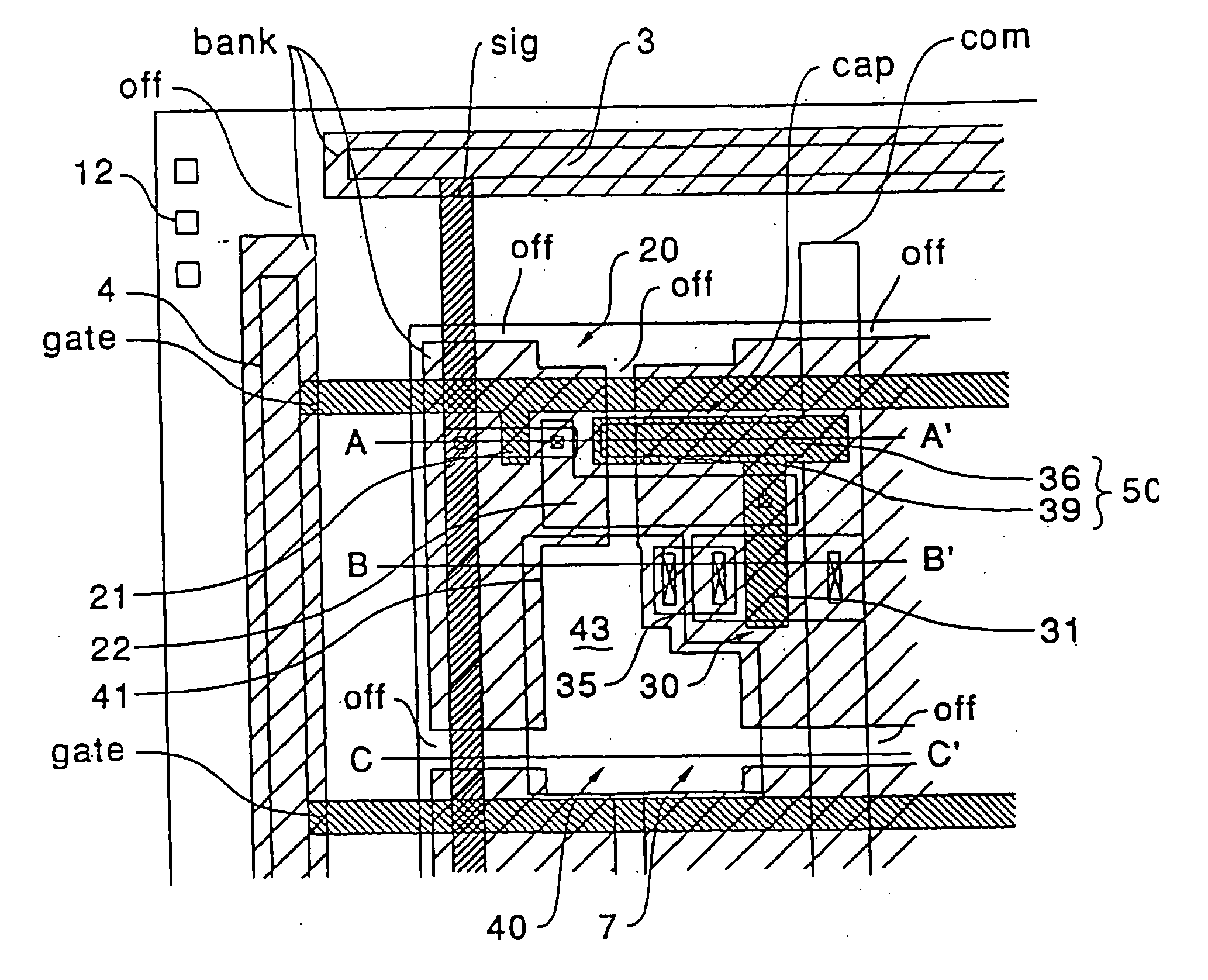
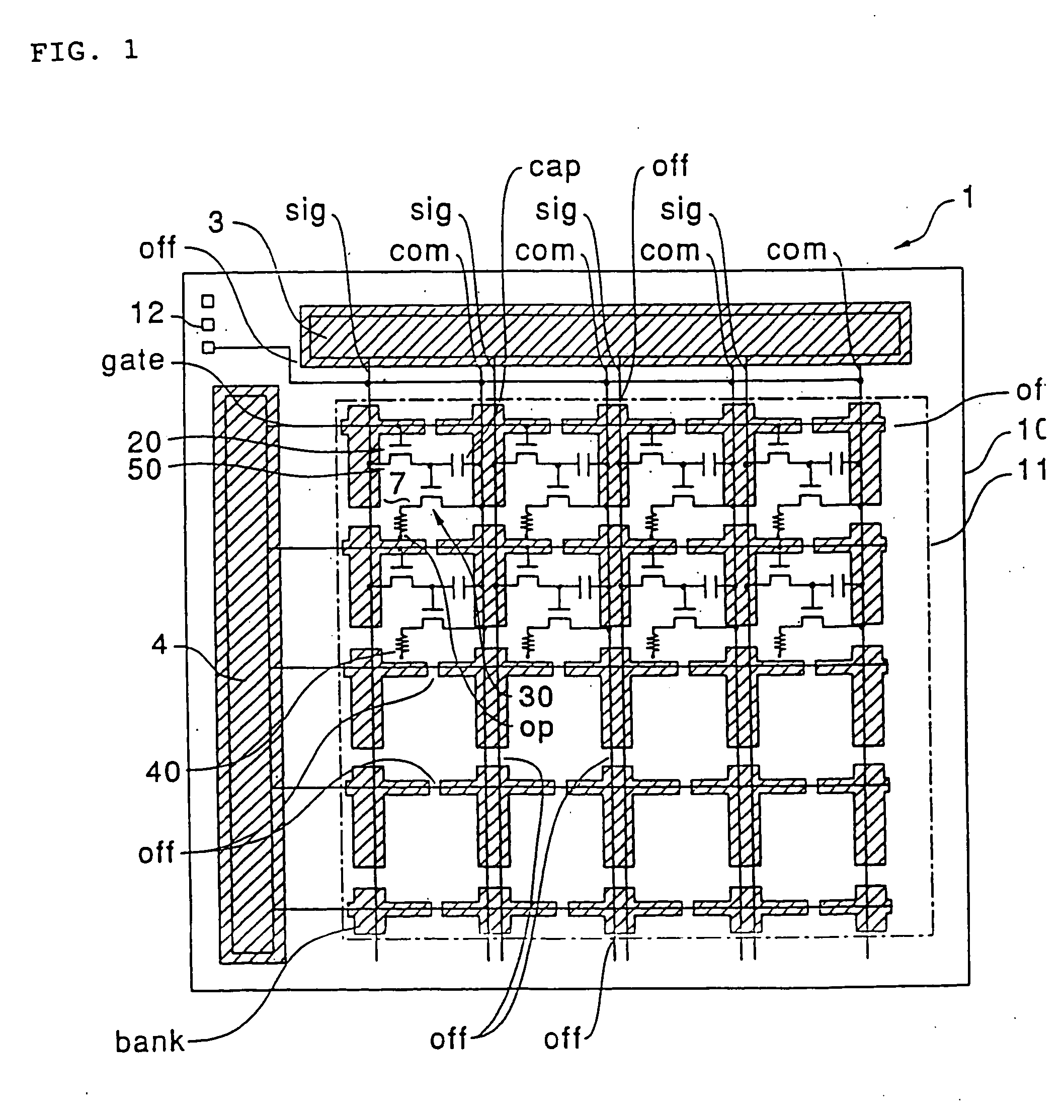
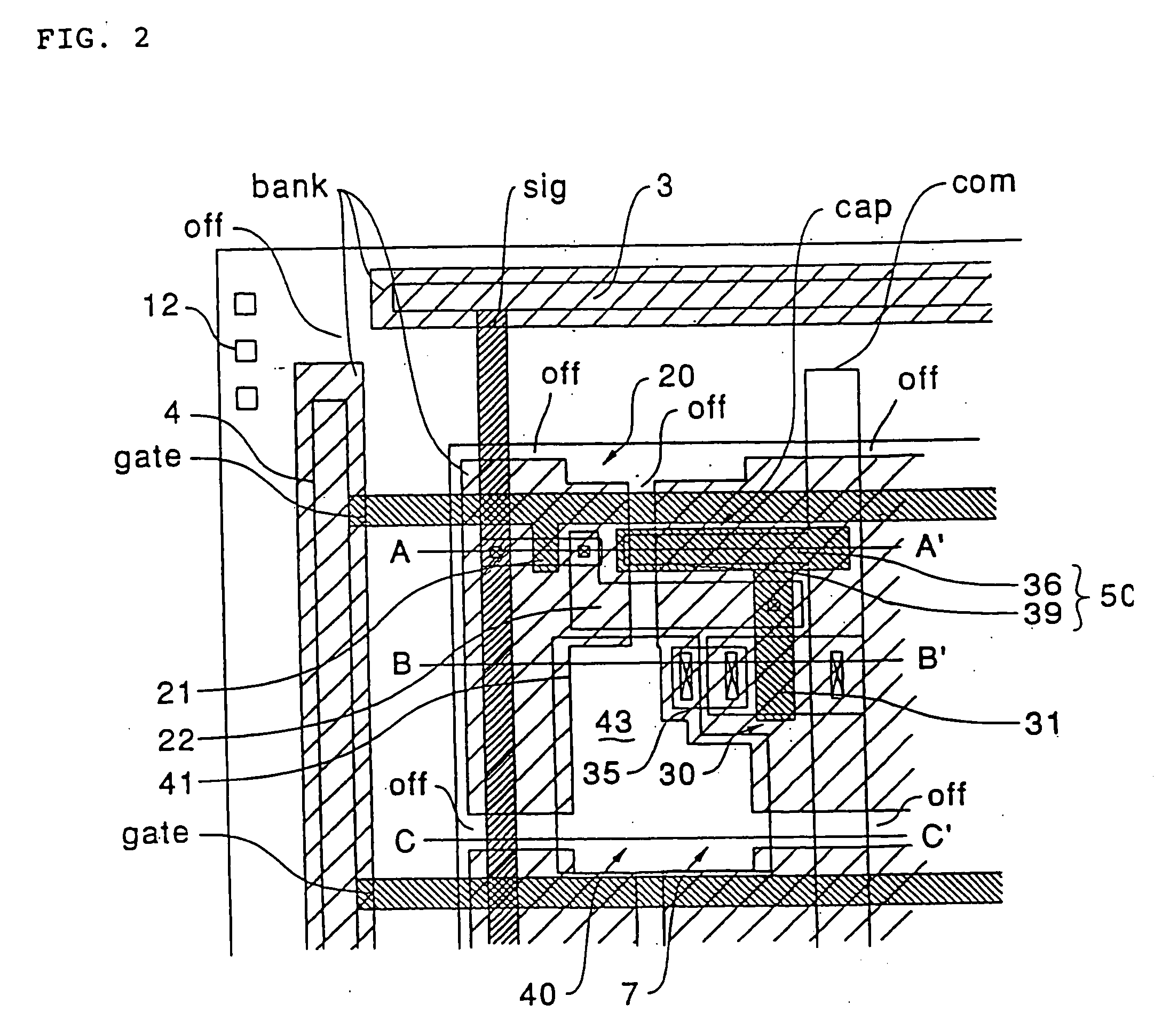
Active matrix display device
InactiveUS20080036699A1Reduce dataReduce capacitanceStatic indicating devicesElectroluminescent light sourcesResistActive matrix
Owner:INTELLECTUAL KEYSTONE TECH LLC
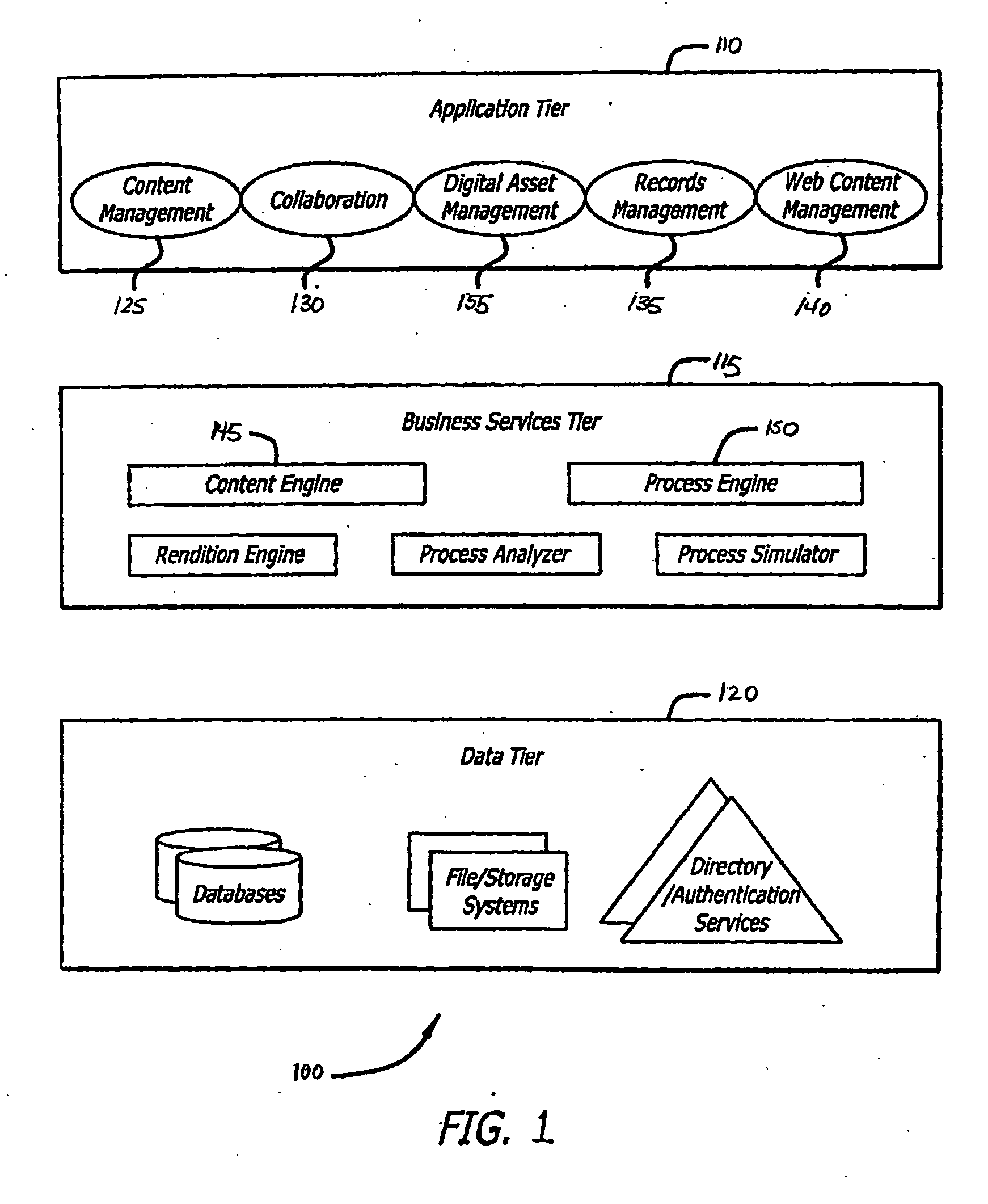
Automated records management with enforcement of a mandatory minimum retention record
InactiveUS20060149735A1Alteration can be preventedData processing applicationsError detection/correctionRetention periodProgram planning
A records management system and method includes a file plan that has one or more segments associated with compliance data. Data stored in these segments of the file plan have a mandatory minimum retention period during which they cannot be modified or deleted. Additionally, the information about the mandatory minimum retention period may not be altered or removed.
Owner:IBM CORP
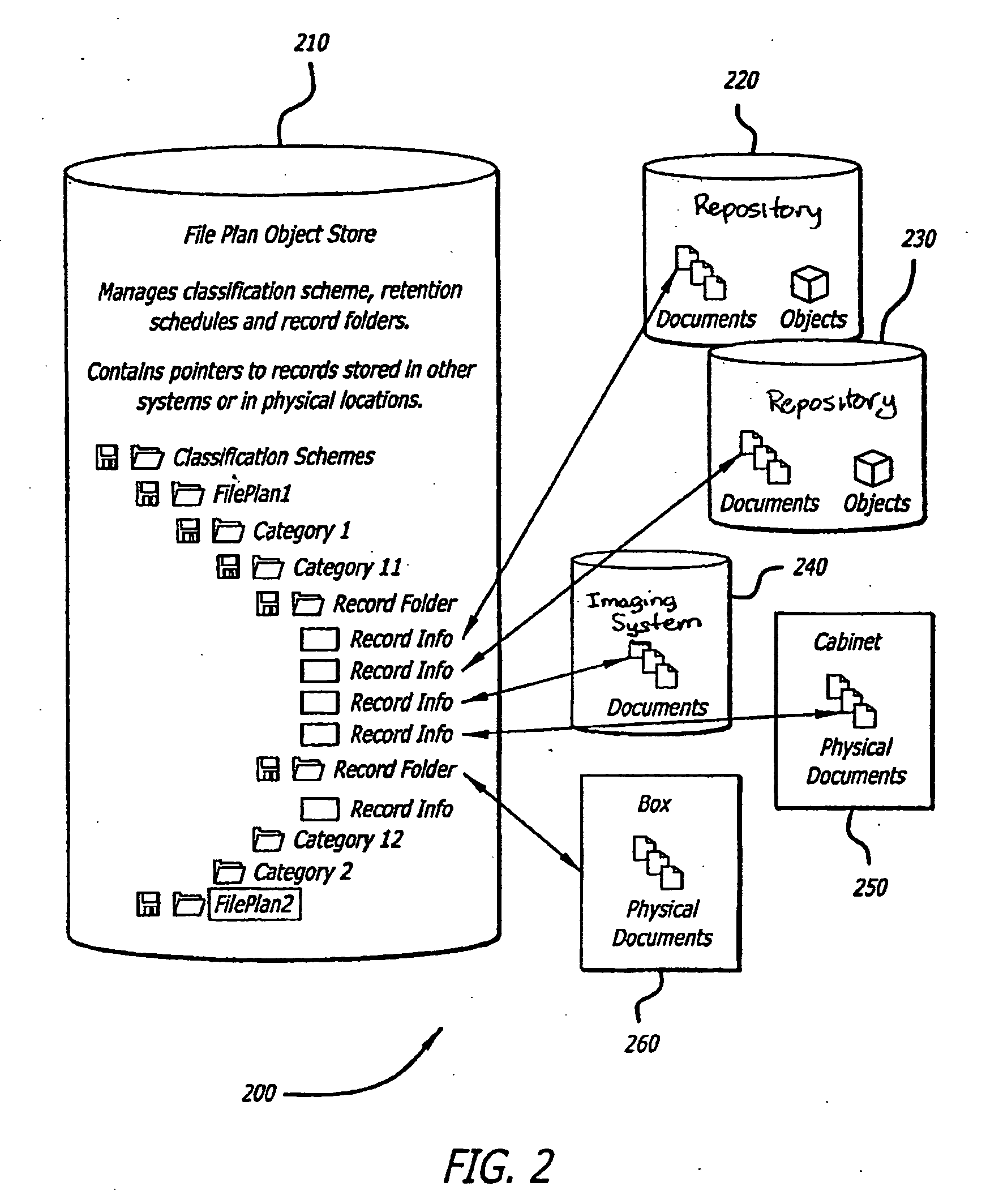
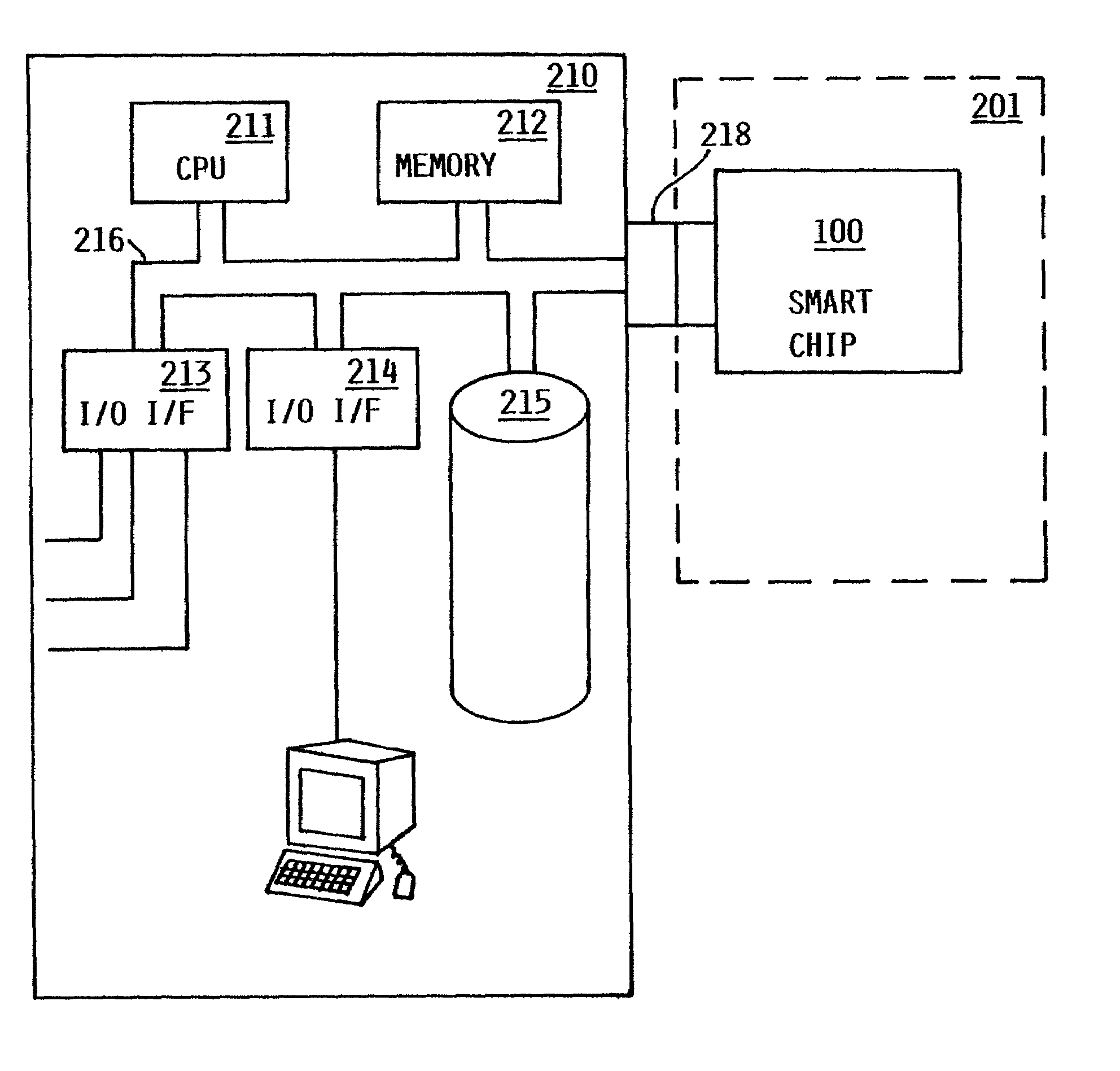
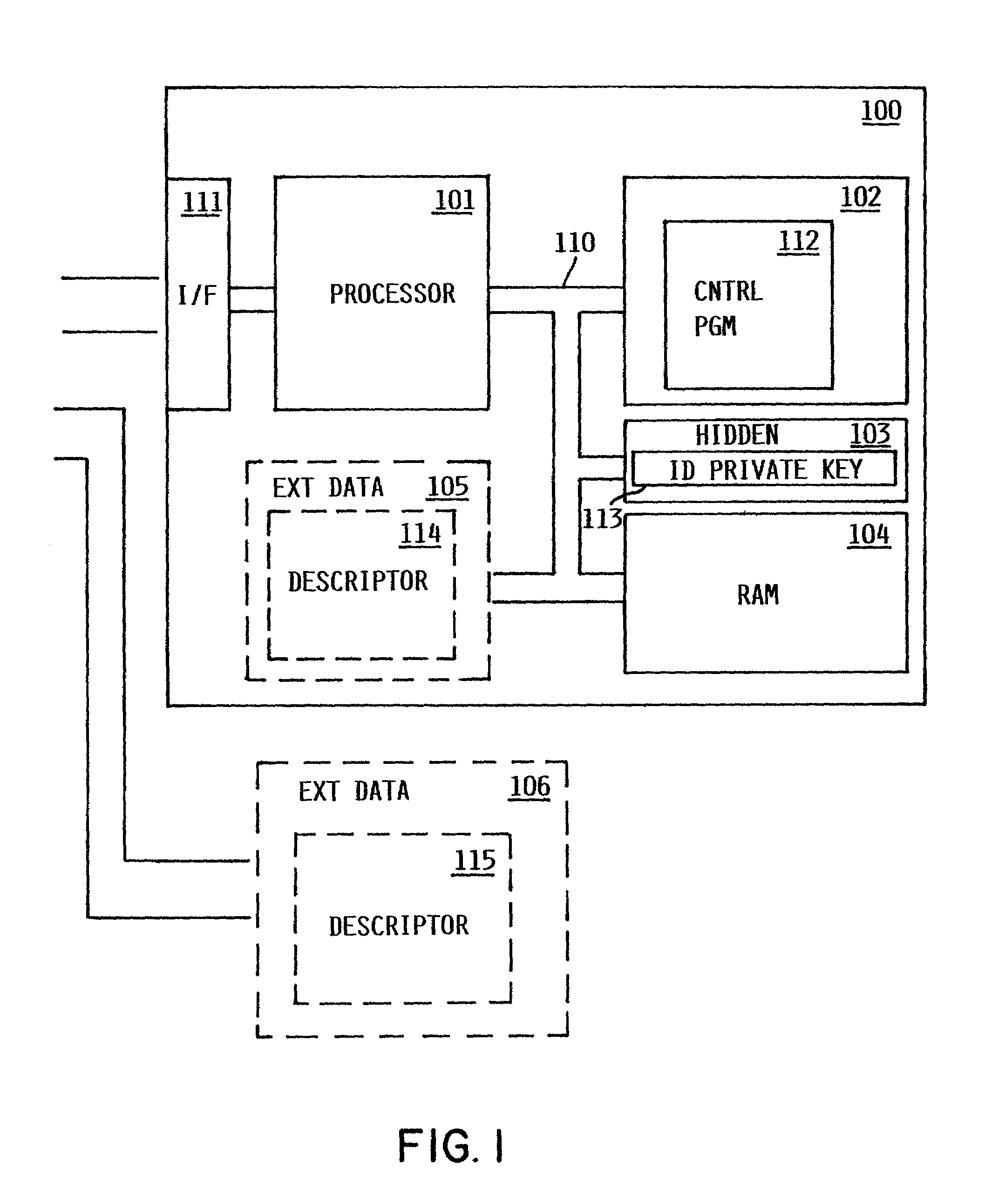
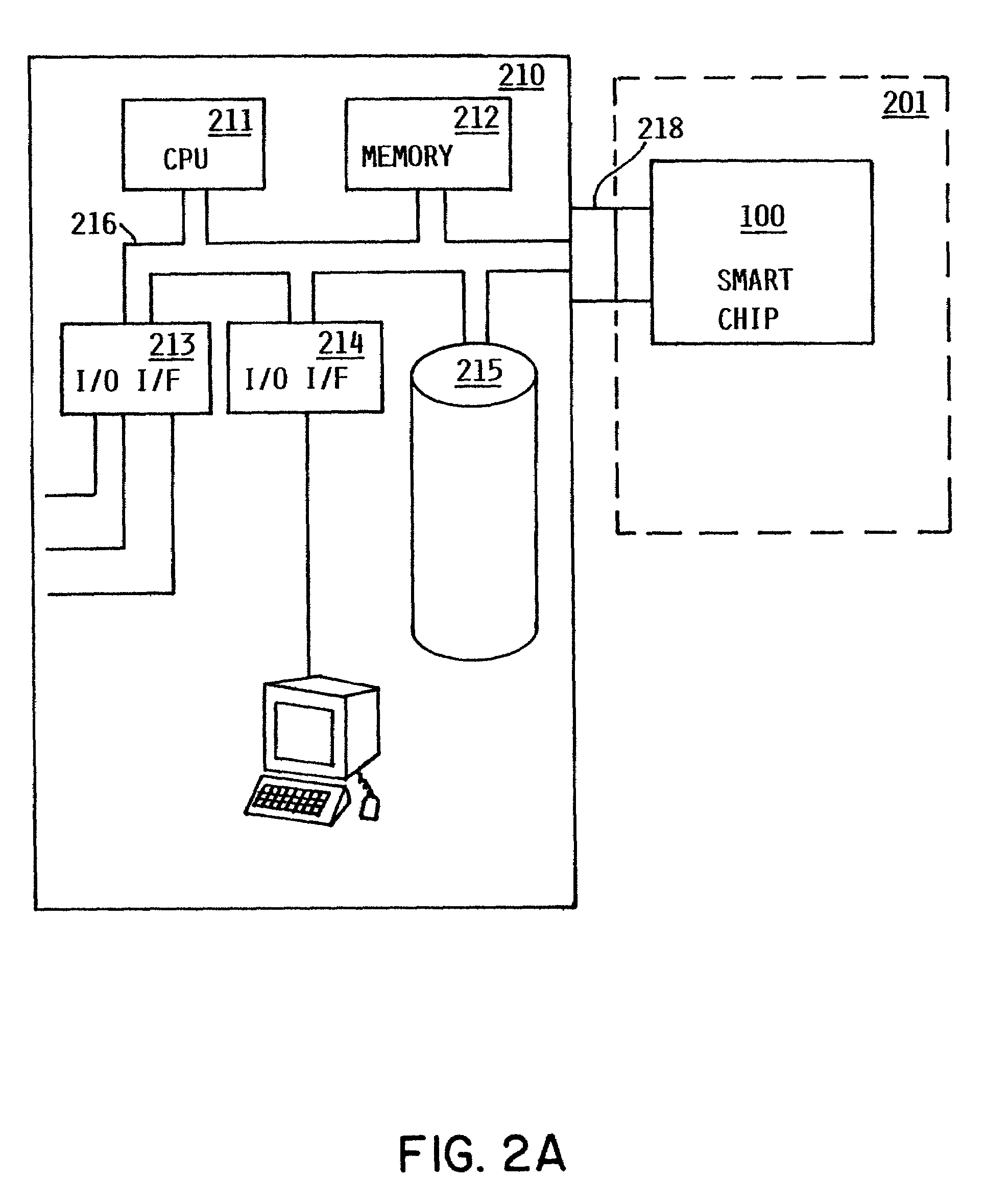
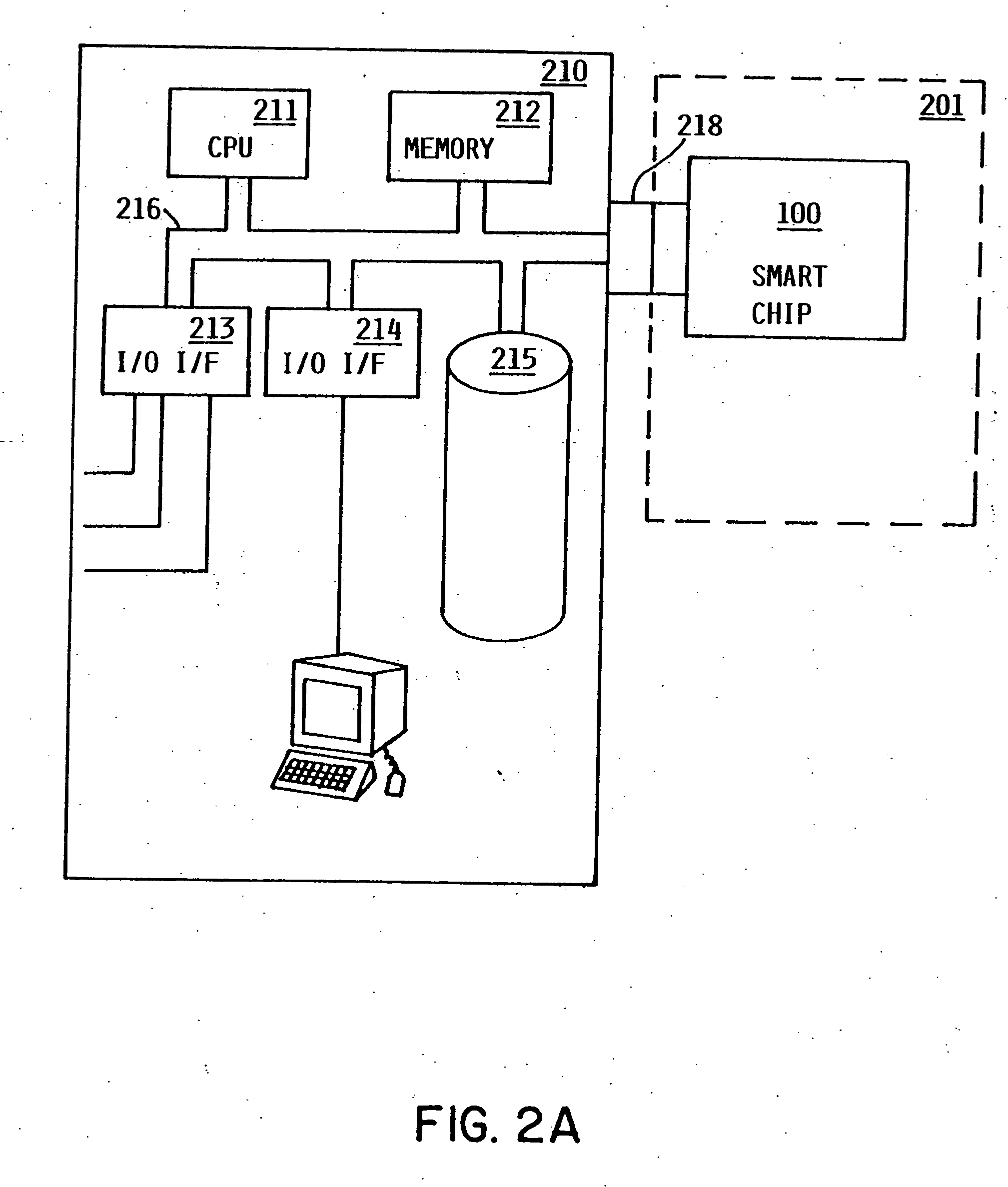
Method and apparatus for uniquely and authoritatively identifying tangible objects
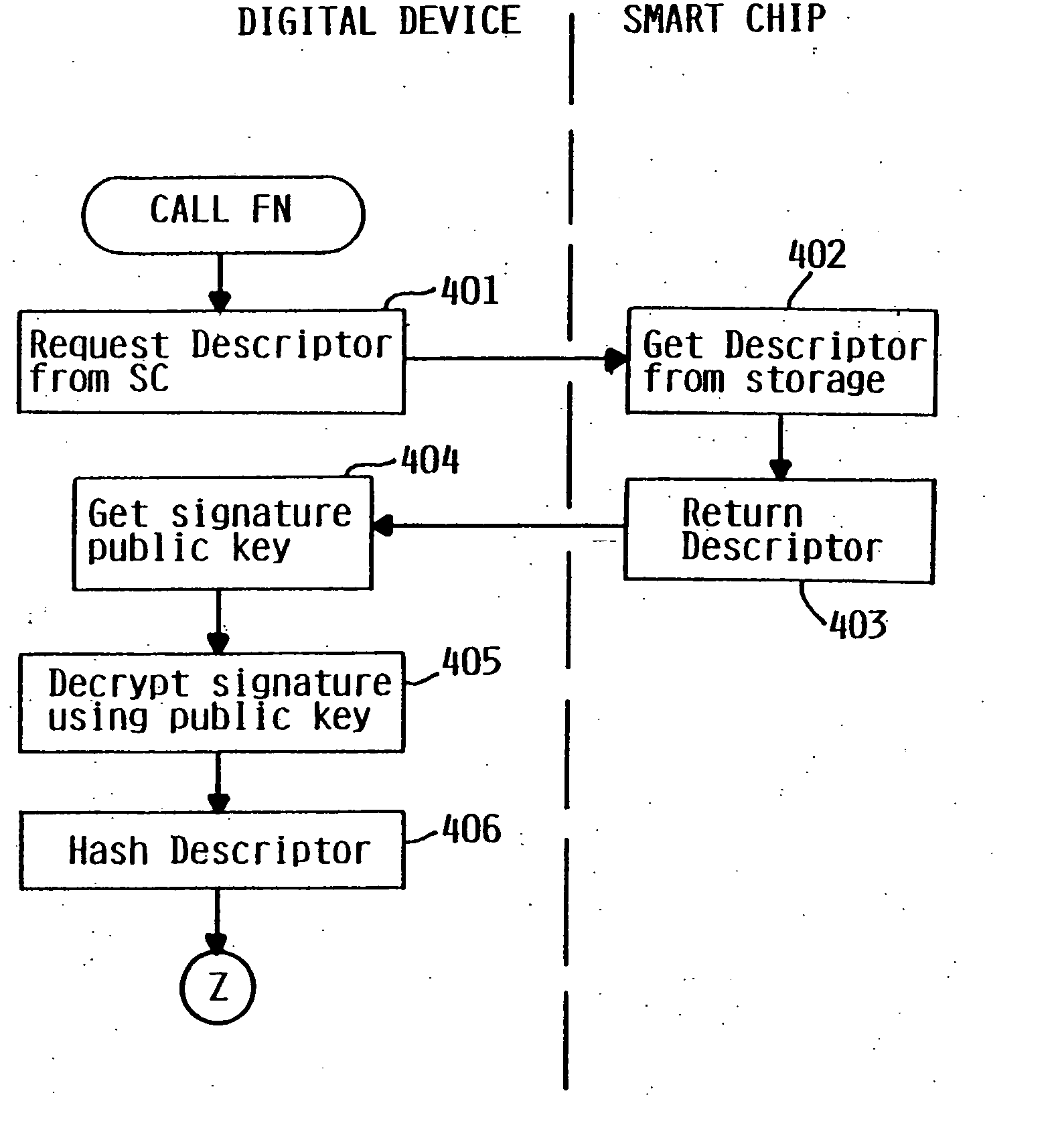
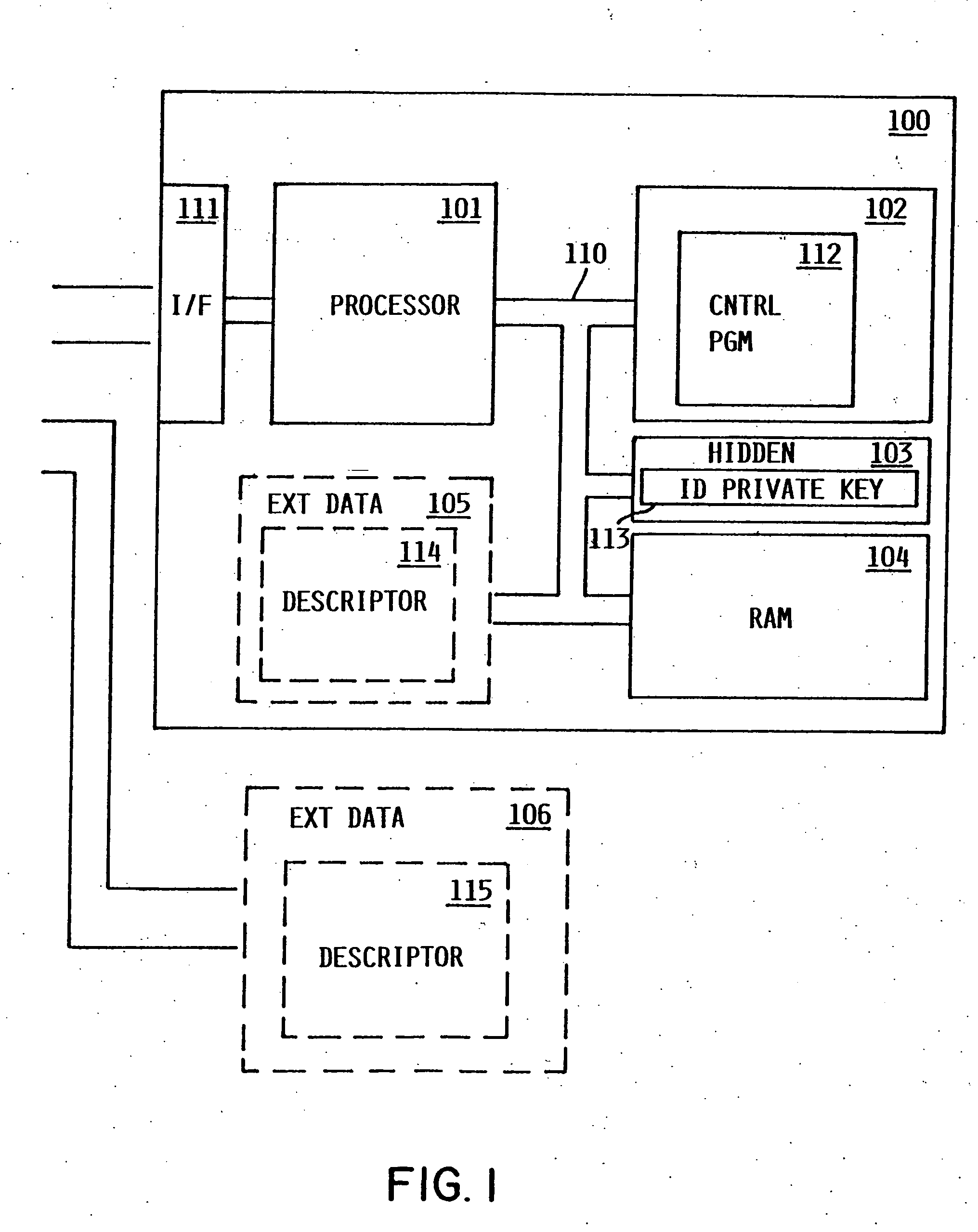
InactiveUS7000115B2Alteration can be preventedEasy to readDigital data processing detailsUser identity/authority verificationDigital signatureTangible object
A smart chip protection system contains a unique public / private identity key pair and uses a separate public / private signature key pair. The identity private key is stored in permanent, secure storage such that it can not be read outside the chip. An issuing entity generates a descriptor containing the identity public key, attribute data, and a digital signature. The digital signature is generated by enciphering a derivation of the identity public key and the attribute data with the signature private key known only to the issuer. The authenticity of the descriptor data is verified by decrypting the signature with the signature public key using a known algorithm, and comparing the result to the derivation of the descriptor data. The identity of the object can be verified requesting the smart chip ro perform an encryption / decryption operation using its identity private key, and performing the complement using the public key.
Owner:IBM CORP
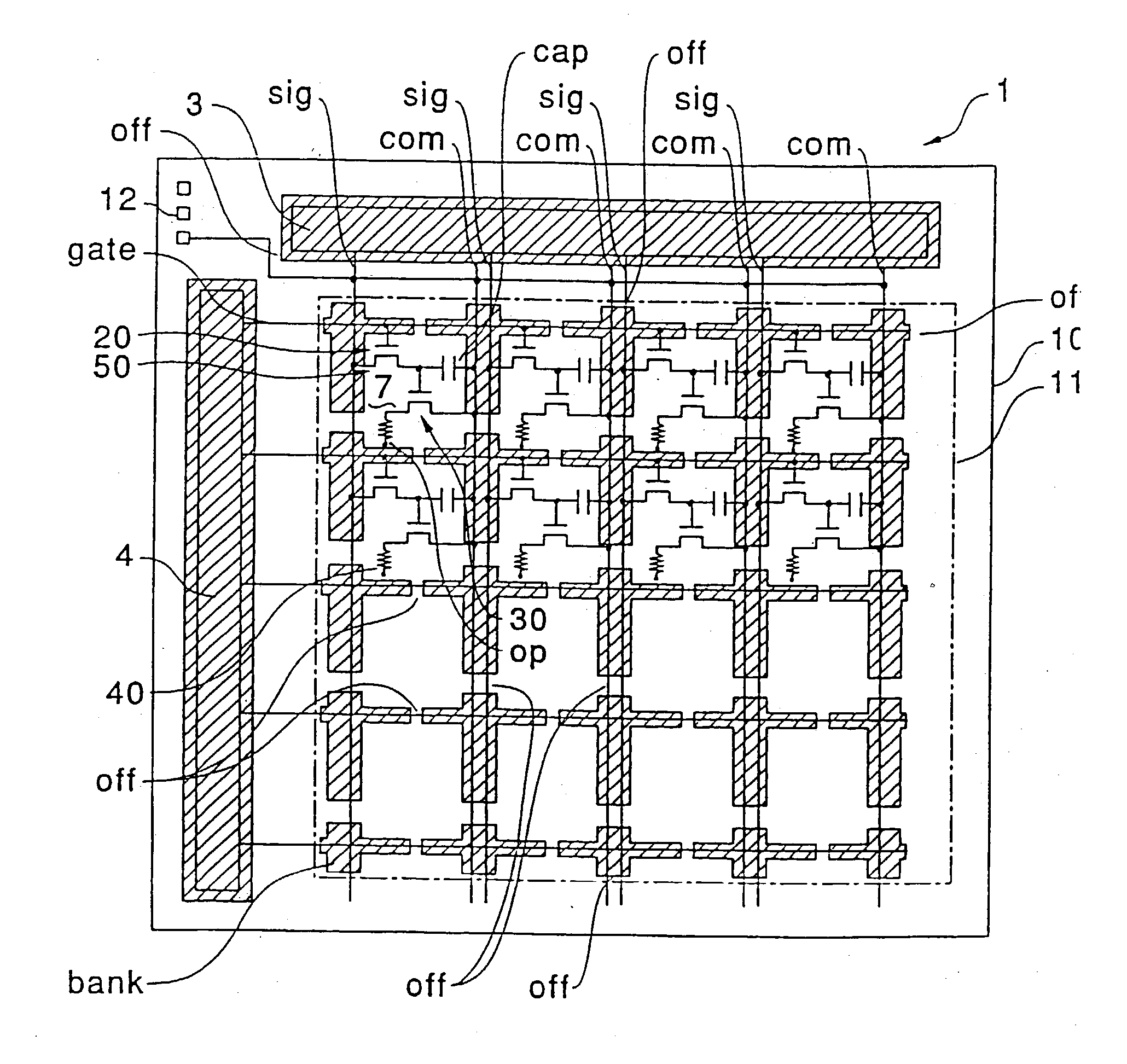
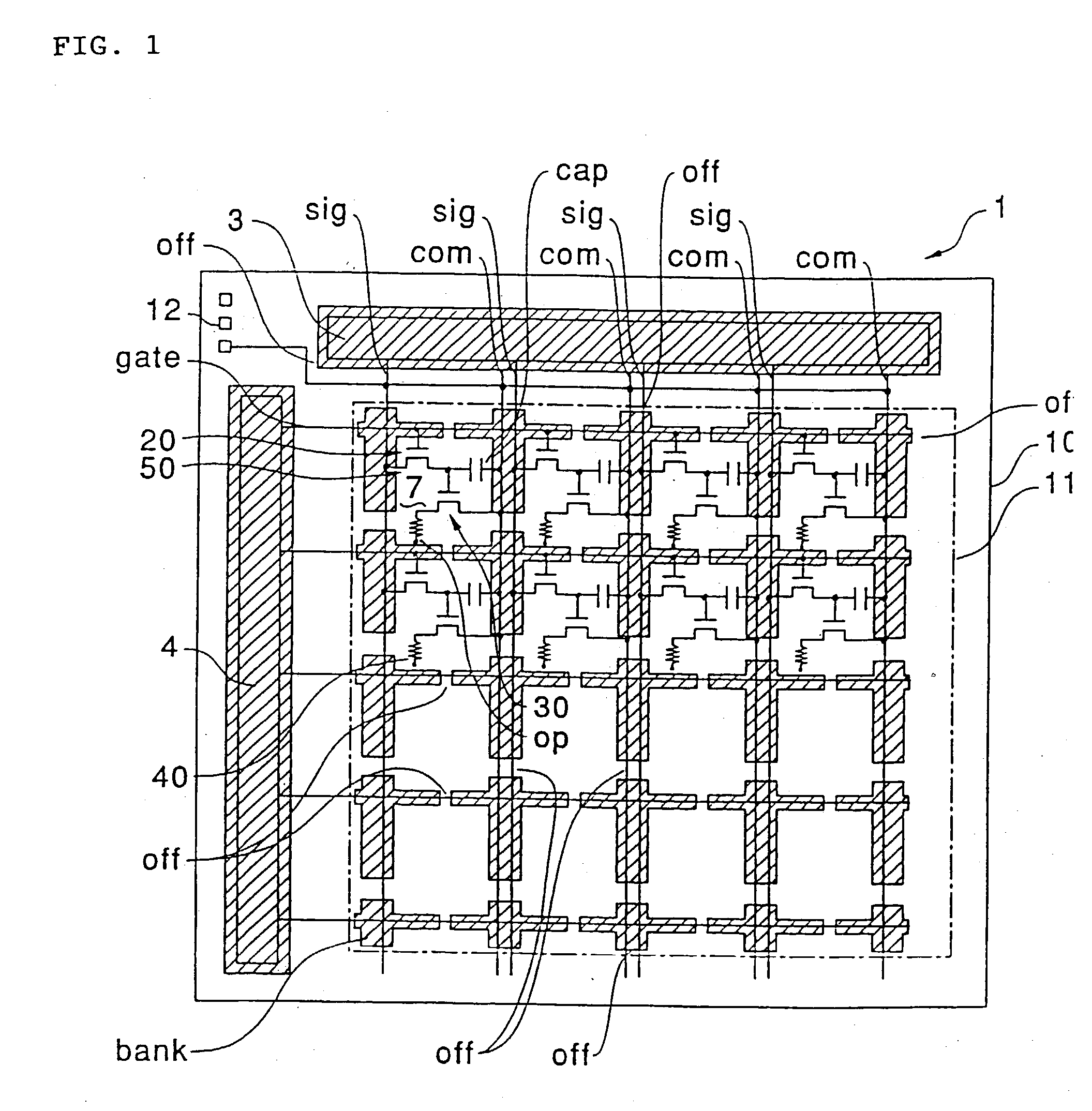
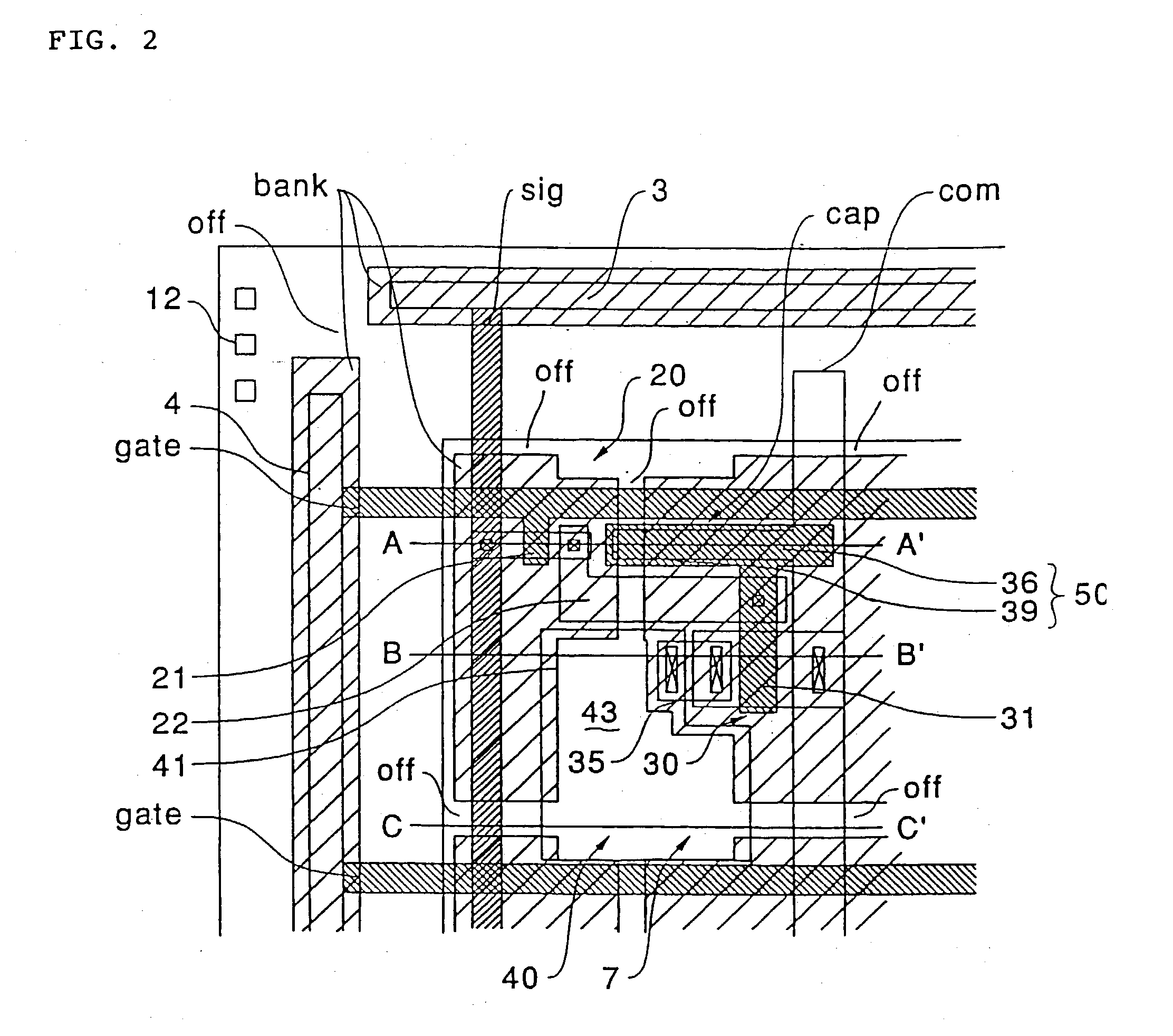
Active matrix display device
InactiveUS20030206144A1Reduce power consumptionPrevent capacitanceStatic indicating devicesElectroluminescent light sourcesResistCapacitance
An active matrix display device is provided in which parasistic capacitance or the like is suppressed by forming a thick insulating film around an organic semiconductor film, and disconnection or the like does not occur in an opposing electrode formed on the upper layer of the thick insulating film. In the active matrix display device, first, a bank layer composed of a resist film is formed along data lines and scanning lines. By depositing an opposing electrode of a thin film luminescent element on the upper layer side of the bank layer, capacitance that parasitizes the data lines can be suppressed. Additionally, a discontinuities portion is formed in the bank layer. Since the discontinuities portion is a planar section which does not have any a step due to the existence of the bank layer, disconnection of opposing electrode does not occur at this section. When an organic semiconductor film is formed by an ink jet process, a liquid material discharged from an ink jet head is blocked by the bank layer.
Owner:SEIKO EPSON CORP
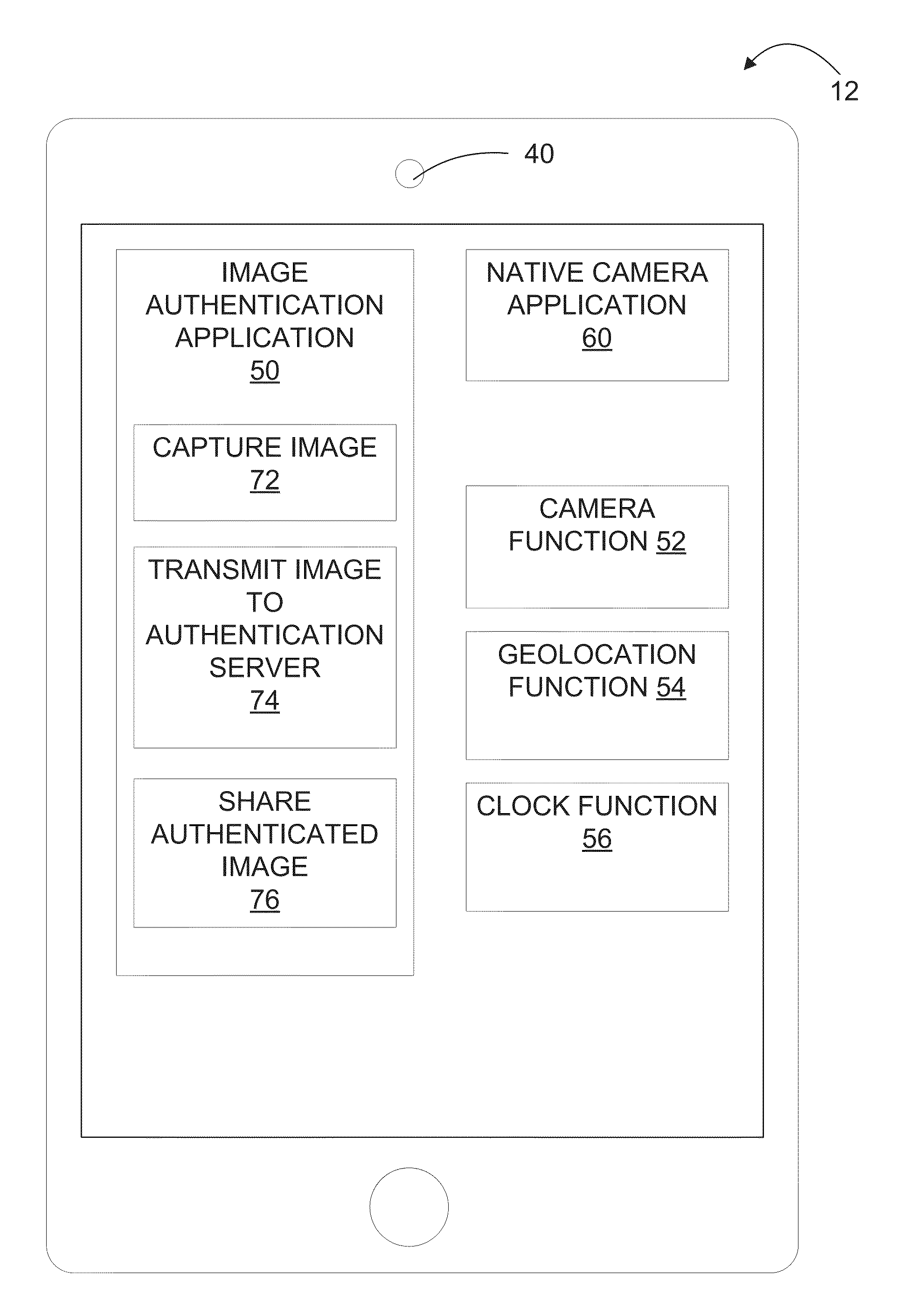
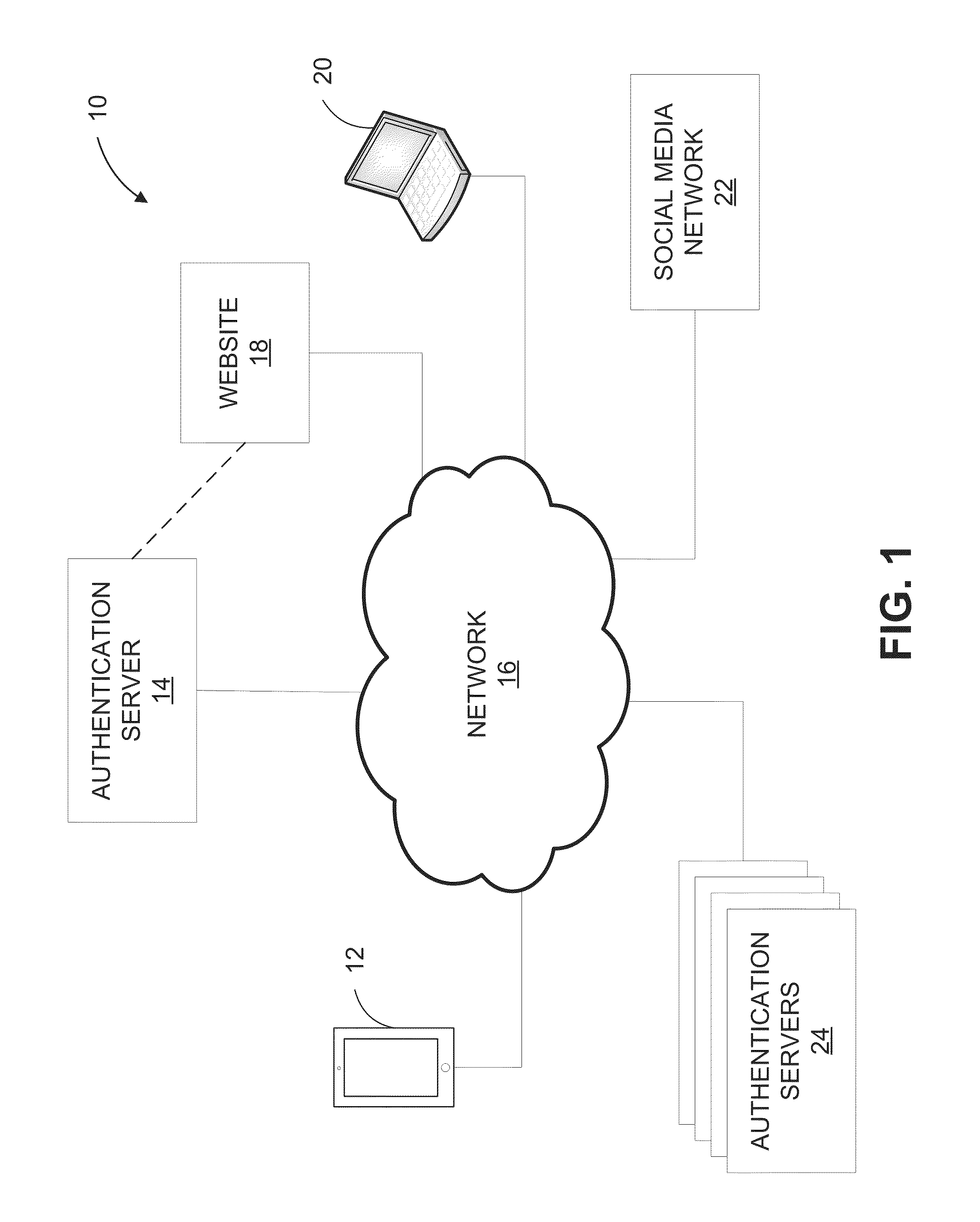
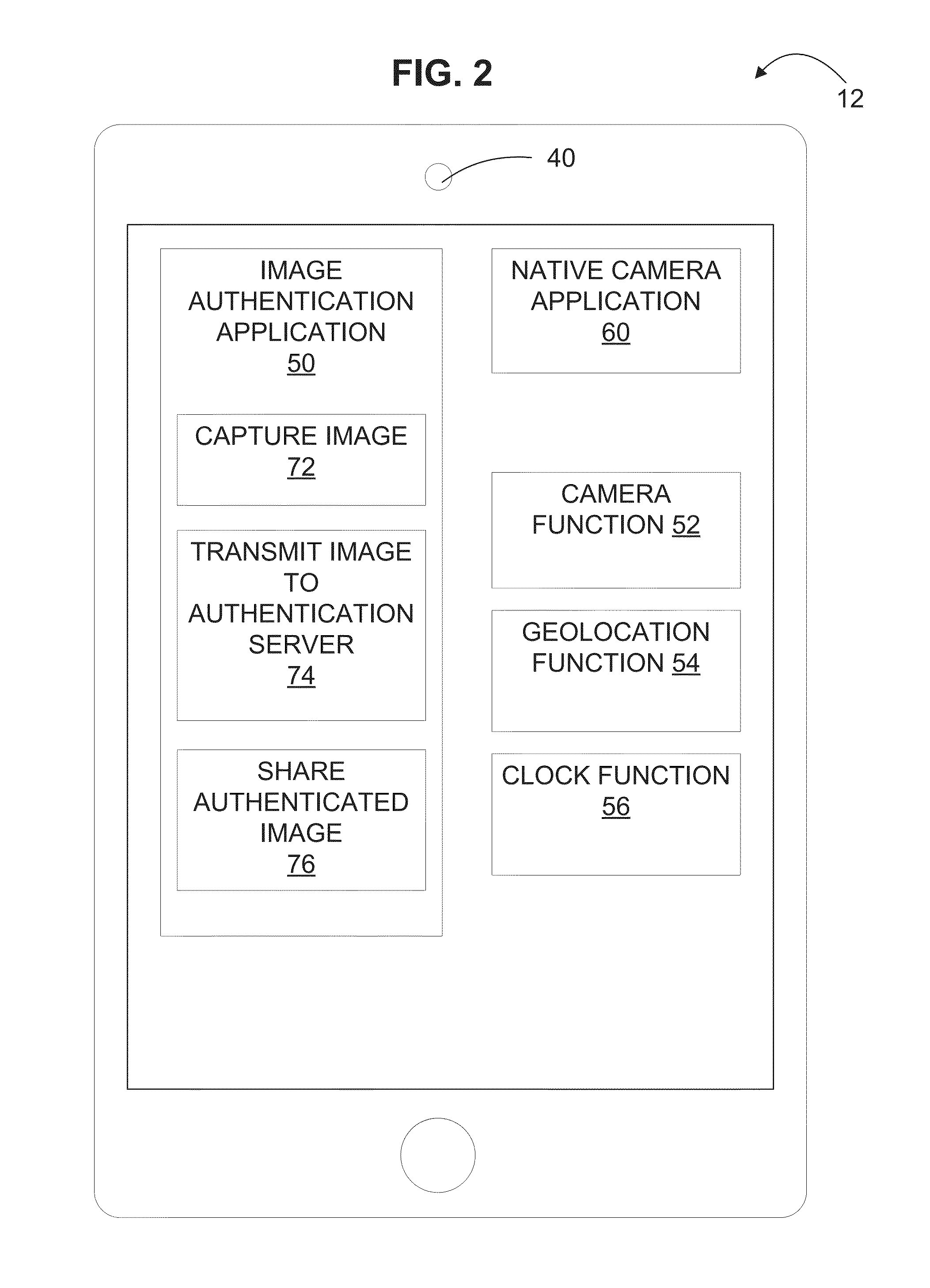
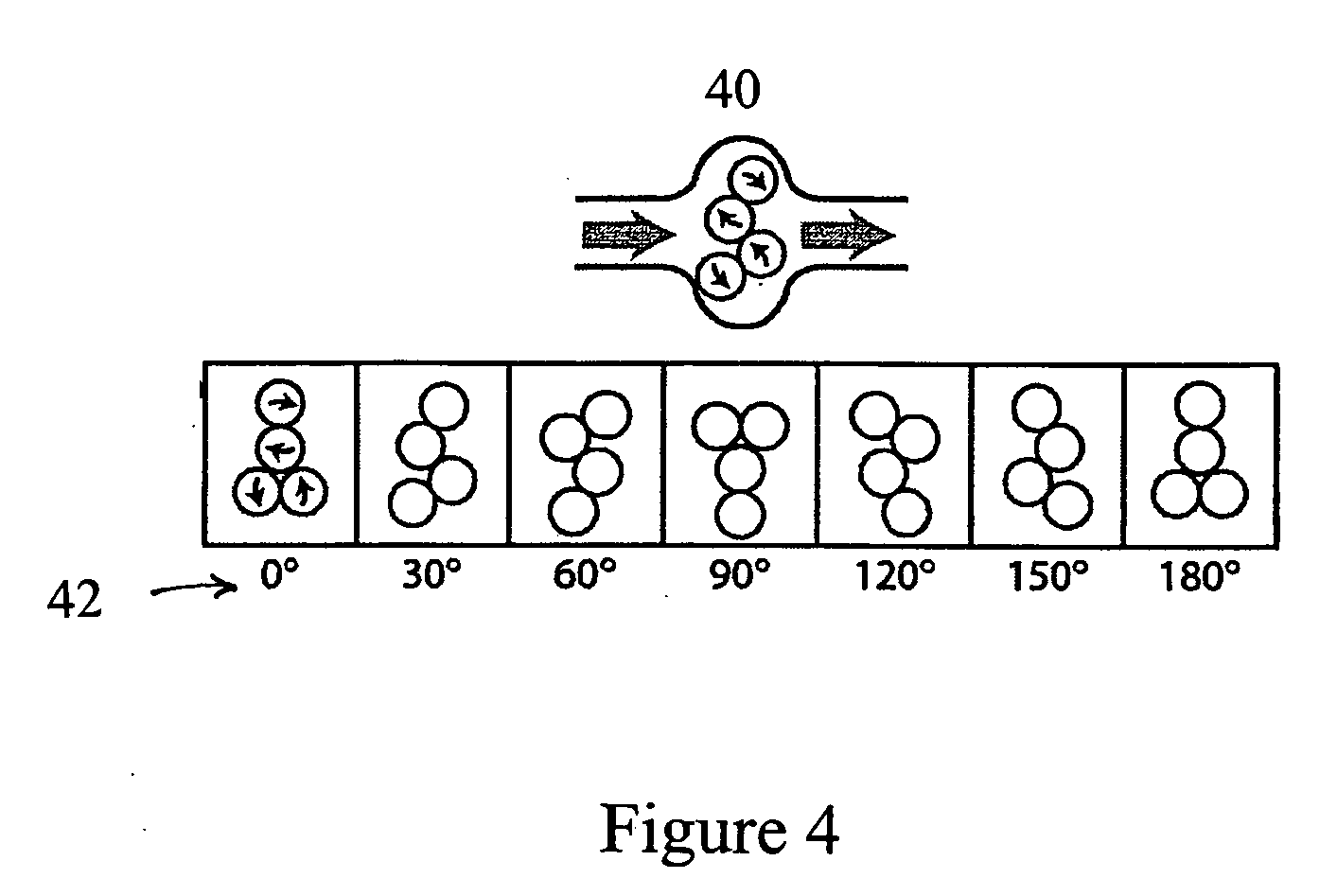
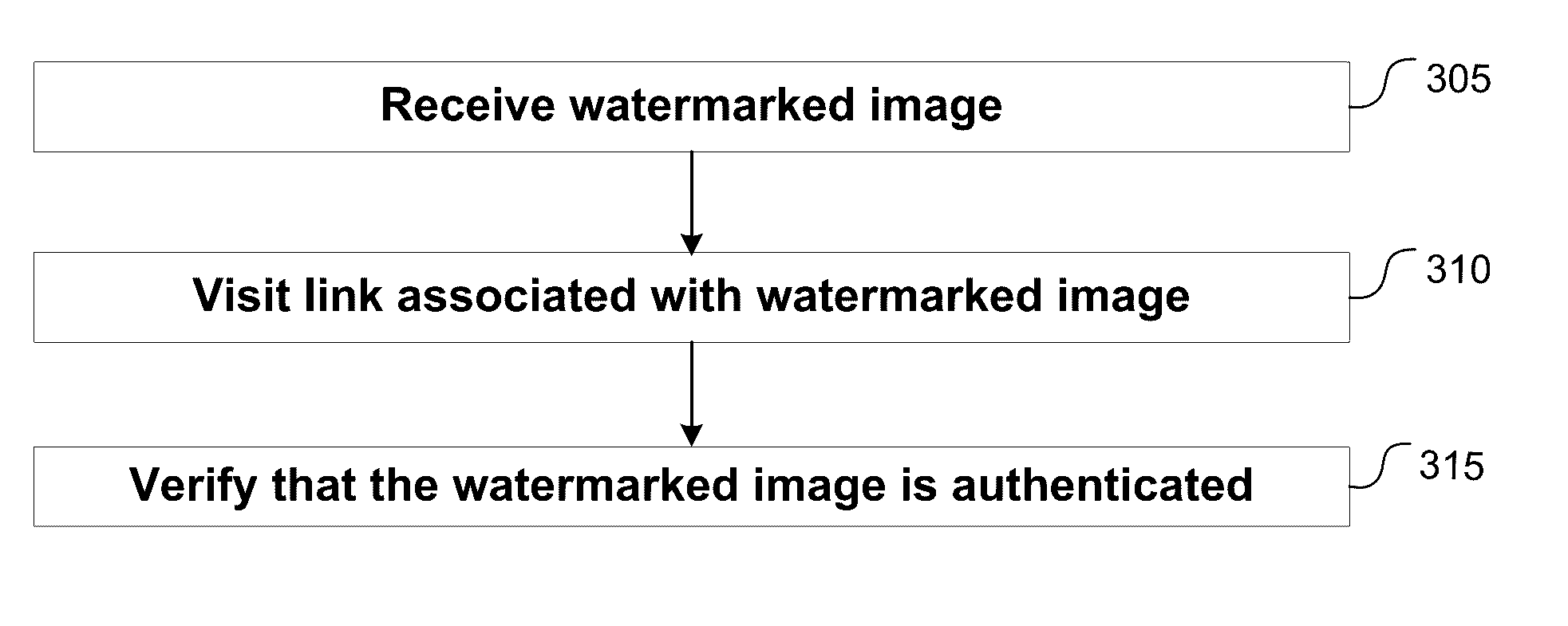
Systems and methods for authenticating photographic image data
ActiveUS9300678B1Reduce the possibilityAlteration can be preventedDigital data protectionTransmissionTime informationData file
The present disclosure provides systems and methods for authenticating photographic data. In one embodiment, a method comprises providing an image authentication application for use on a client device, the application configured to control image capture and transmission; receiving an image data file from the application at the authentication server comprising a photographic image captured by the application and metadata associated therewith; applying a watermark to the photographic image to create a watermarked image; applying date and time information to the tagged image; applying location information to the tagged image; creating a web address associated with the image data file; uploading the photographic image, the tagged image, or both to the web address; and transmitting an authenticated image file to the client device, the authenticated image file comprising one or more of: the watermarked image, the photographic image, the date and time information, geographic information, and the web address.
Owner:TRUEPIC INC
Two part spacecraft servicing vehicle system with universal docking adaptor
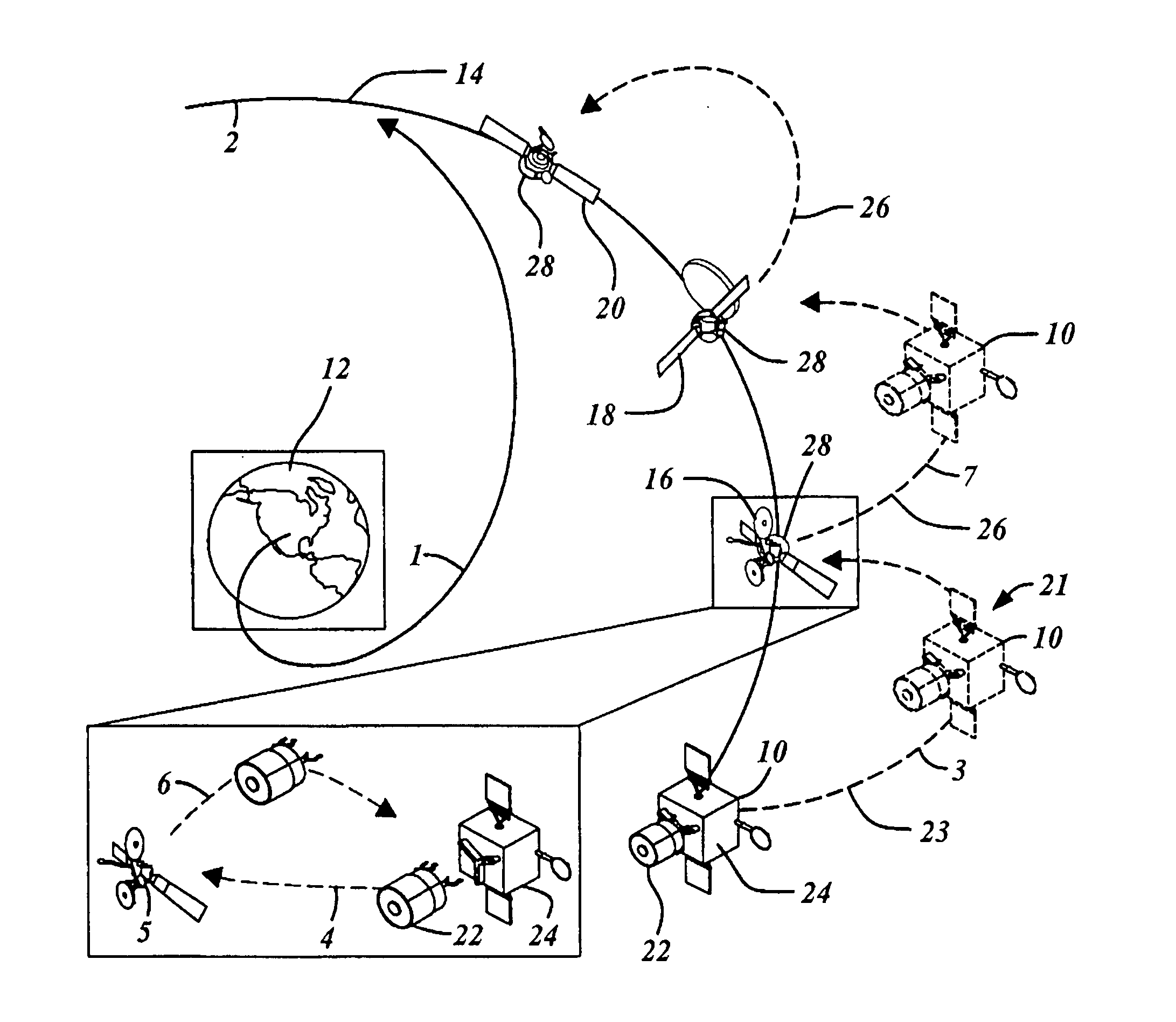
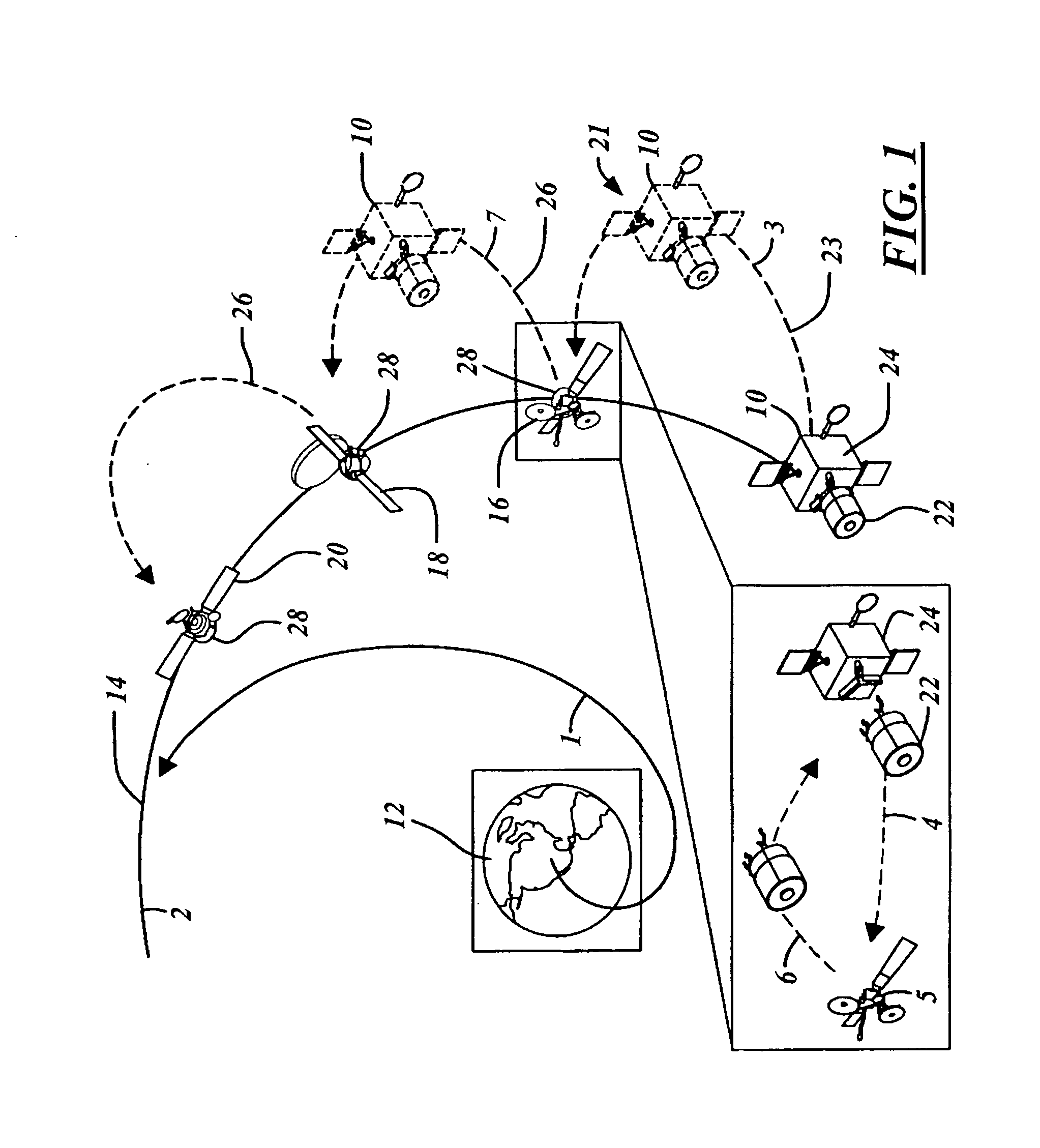
InactiveUS7861975B2Alteration can be preventedRequires minimizationCosmonautic vehiclesCosmonautic component separationAviationCo operative
An in-space spacecraft servicing system (10) includes a servicing spacecraft (22) and a propellant module (24). The servicing spacecraft includes a client servicing system (136), as well as navigation avionics (108) for independent flight operation and a servicing propellant tank (170). The propellant module moves the servicing module from an upper stage drop off location and releases it in proximity to a client spacecraft (16) for a servicing mission. It has a propellant tank (172) with capacity for multiple missions and is used to refill the servicing spacecraft's propellant tanks between missions. Either or both the servicing spacecraft and the propellant module may have navigation avionics. The servicing spacecraft also has a universal docking adaptor (70) for different client spacecraft, and can convert a client spacecraft from non-cooperative to cooperative.
Owner:THE BOEING CO
Two part spacecraft servicing vehicle system with universal docking adaptor
InactiveUS20070228219A1Alteration can be preventedRequires minimizationCosmonautic vehiclesCosmonautic component separationAviationCo operative
An in-space spacecraft servicing system (10) includes a servicing spacecraft (22) and a propellant module (24). The servicing spacecraft includes a client servicing system (136), as well as navigation avionics (108) for independent flight operation and a servicing propellant tank (170). The propellant module moves the servicing module from an upper stage drop off location and releases it in proximity to a client spacecraft (16) for a servicing mission. It has a propellant tank (172) with capacity for multiple missions and is used to refill the servicing spacecraft's propellant tanks between missions. Either or both the servicing spacecraft and the propellant module may have navigation avionics. The servicing spacecraft also has a universal docking adaptor (70) for different client spacecraft, and can convert a client spacecraft from non-cooperative to cooperative.
Owner:THE BOEING CO
On-chip multi-core type tamper resistant microprocessor
ActiveUS7590869B2Alteration can be preventedMultiple keys/algorithms usageDigital data processing detailsMulti processorMicroprocessor
The on-chip multi-core type tamper resistant processor has a feature that, on the microprocessor package which has a plurality of instruction execution cores on an identical package and an ciphering processing function that can use a plurality of ciphering keys in correspondence to programs under a multi-task program execution environment, a key table for storing ciphering keys and the ciphering processing function are concentrated on a single location on the package, such that it is possible to provide a tamper resistant microprocessor in the multi-processor configuration that can realize the improved processing performance by hardware of a given size compared with the case of providing the key table and the ciphering processing function distributedly.
Owner:KK TOSHIBA
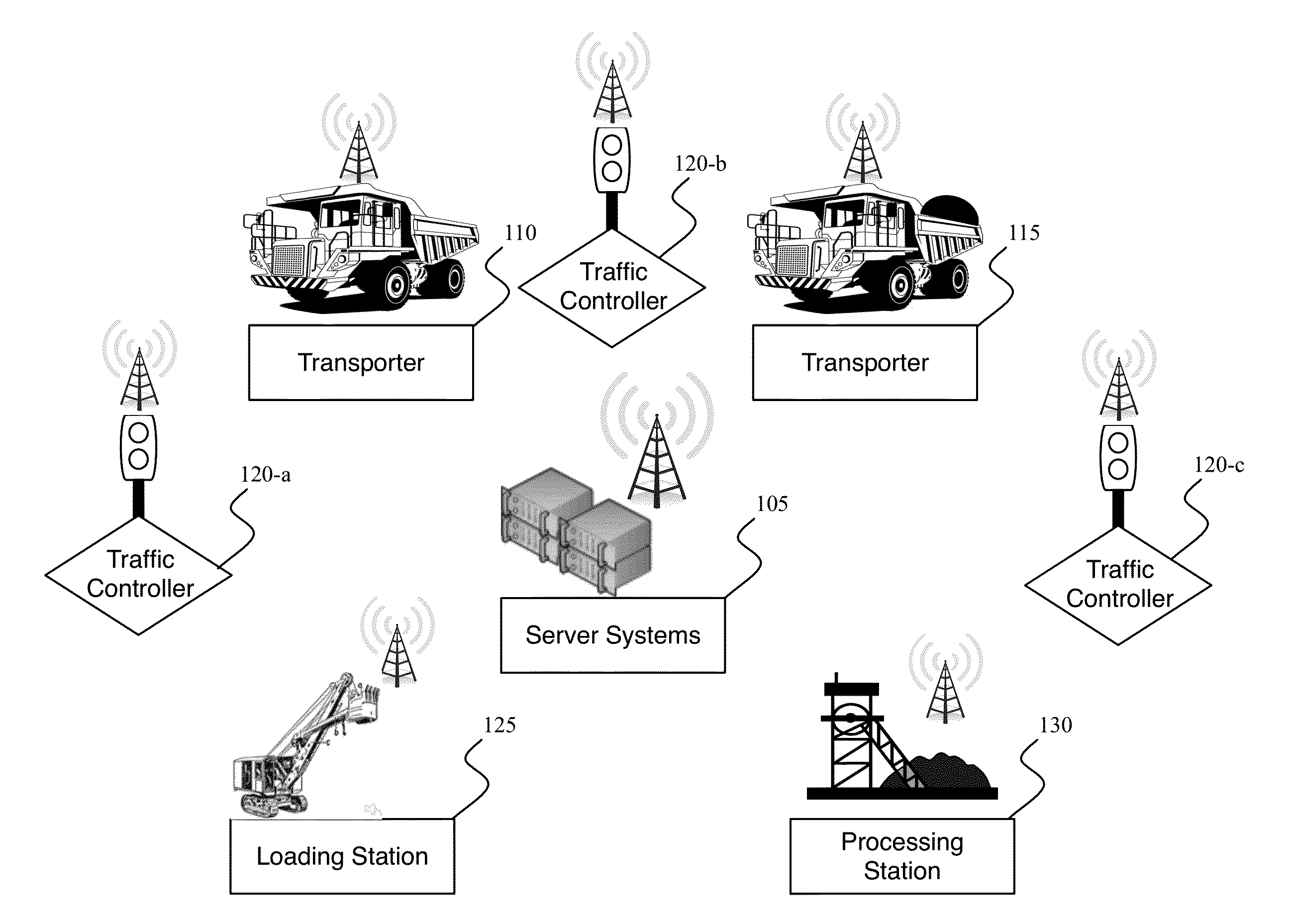
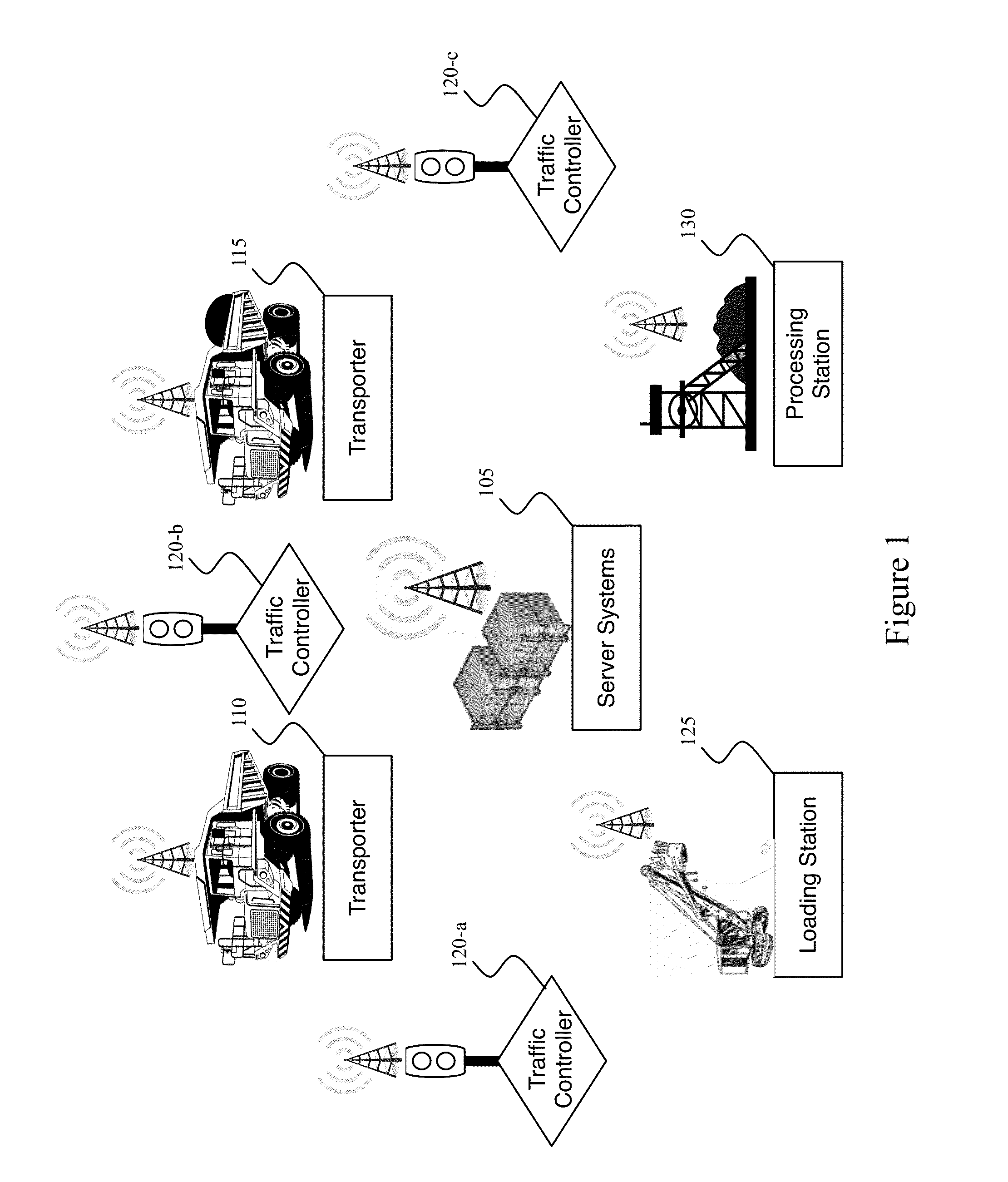
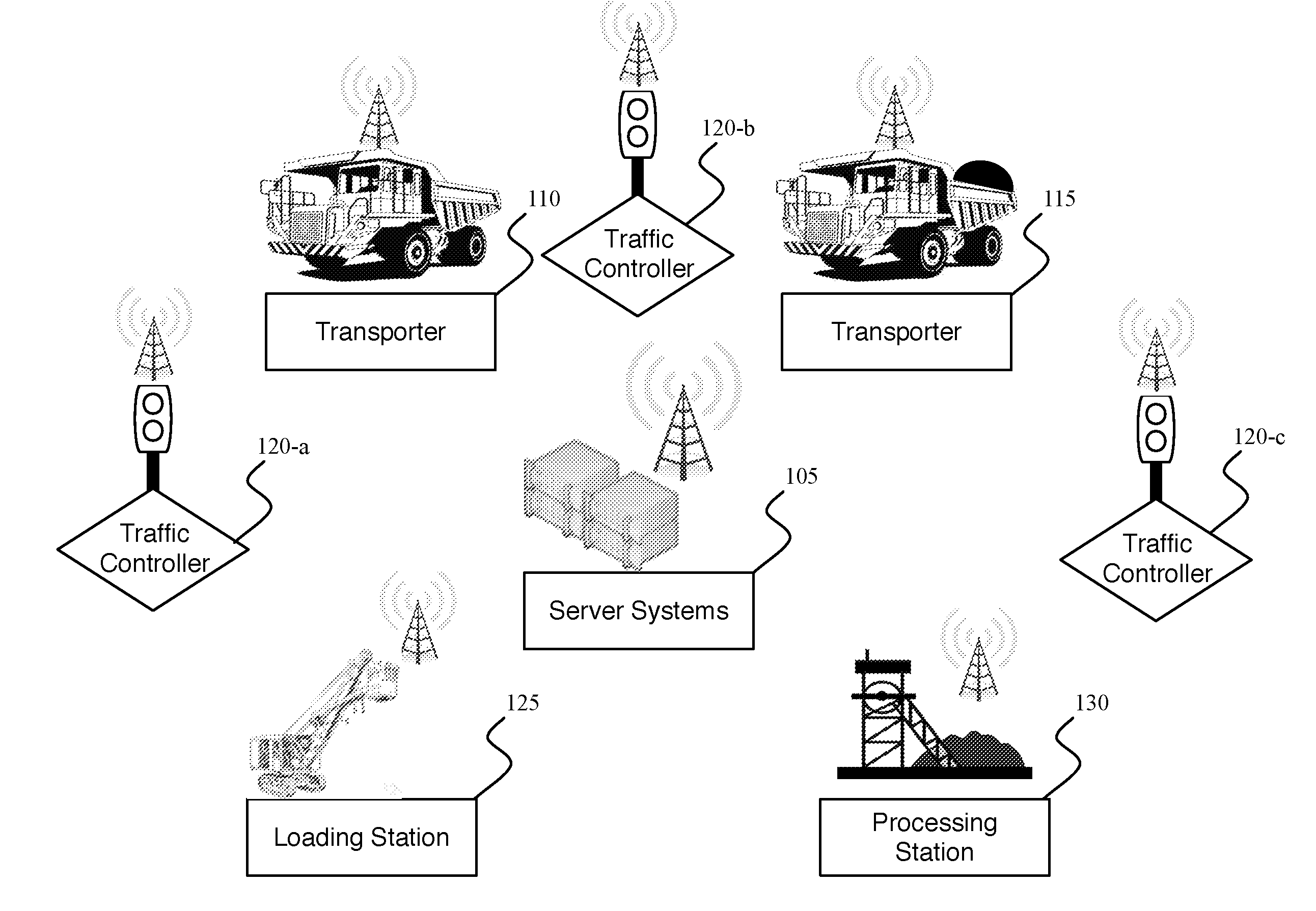
Traffic control system and method of use
InactiveUS20150310737A1Reduce and eliminate error and risk and intelligence limitationReduce and eliminate errorControlling traffic signalsRemote monitoring and controlEmbedded system
An automated traffic control process and system providing automatic remote monitoring the locations of one or more remote vehicles, determining which vehicles fall within one or more preference categories, and if a vehicle in a particular preference category is detected as approaching a remote intersection, issuing a preemption instruction to a traffic signal controller for the remote intersection. Various other process and system features can include one or more among: monitoring numerous vehicles and intersections, vehicle location monitoring, categorization, and issuance of preemption instructions on a centralized computing system; safety or other condition assessment and control of issuance of signaling instructions accordingly; determination of whether one or more the traffic intersection signaling controller should be operating according to one among differing hierarchical condition categories, and issuance of instructions causing remote traffic signaling to lock in a particular state, such as, for example in a right of way state.
Owner:HAWS CORP
Blood concentrate detector
InactiveUS20090310123A1Alteration can be preventedAvoiding characteristicInvestigating moving fluids/granular solidsBiological testingLight energyLight beam
A blood concentrate detector is disclosed for non-invasive, optical, detection of blood in translucent fluids, within translucent tubes, wherein the fluid is formed into a biconvex lens to 1st disperse the light beam, being emitted through a 0.03 to 0.06 inch orifice, across the inner diameter of the tube, then 2nd for that dispersed light to be refocused, via the fluid acting as a lens in the second half of the tube, and directed through a 0.030 to 0.06 inch aperture on the opposing side for detection purposes; whereas the detector measures the reduction in light energy do to the absorption by blood particles of light being emitted in the visible light range of 400 to 800 nm wavelength. Diffusing the light energy throughout the fluid creates an increase ratio of light energy absorption, whereby the electronic circuit can calculate the percentage of blood concentrate within the fluid.
Owner:THOMSON ROBERT JOHN
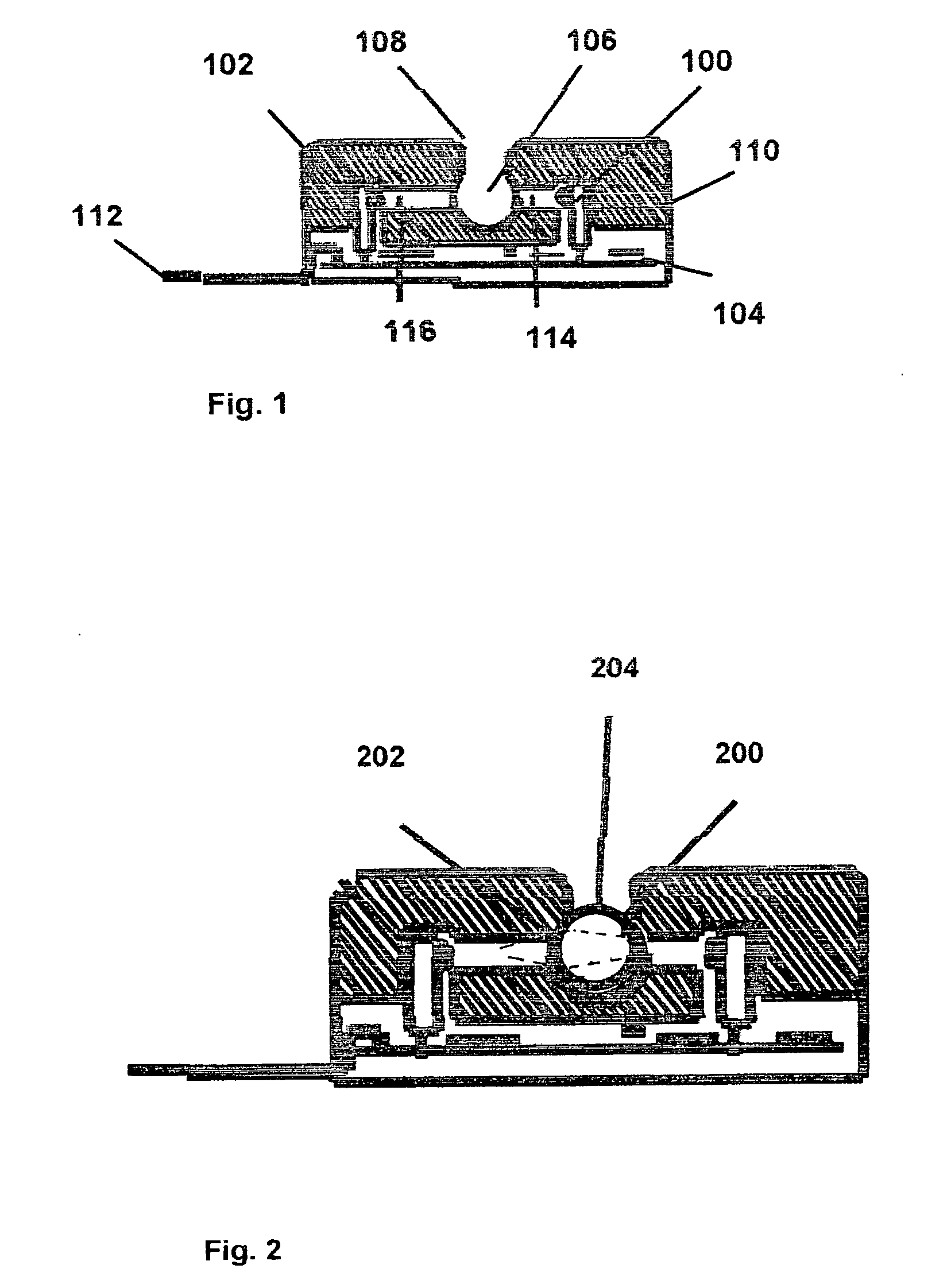
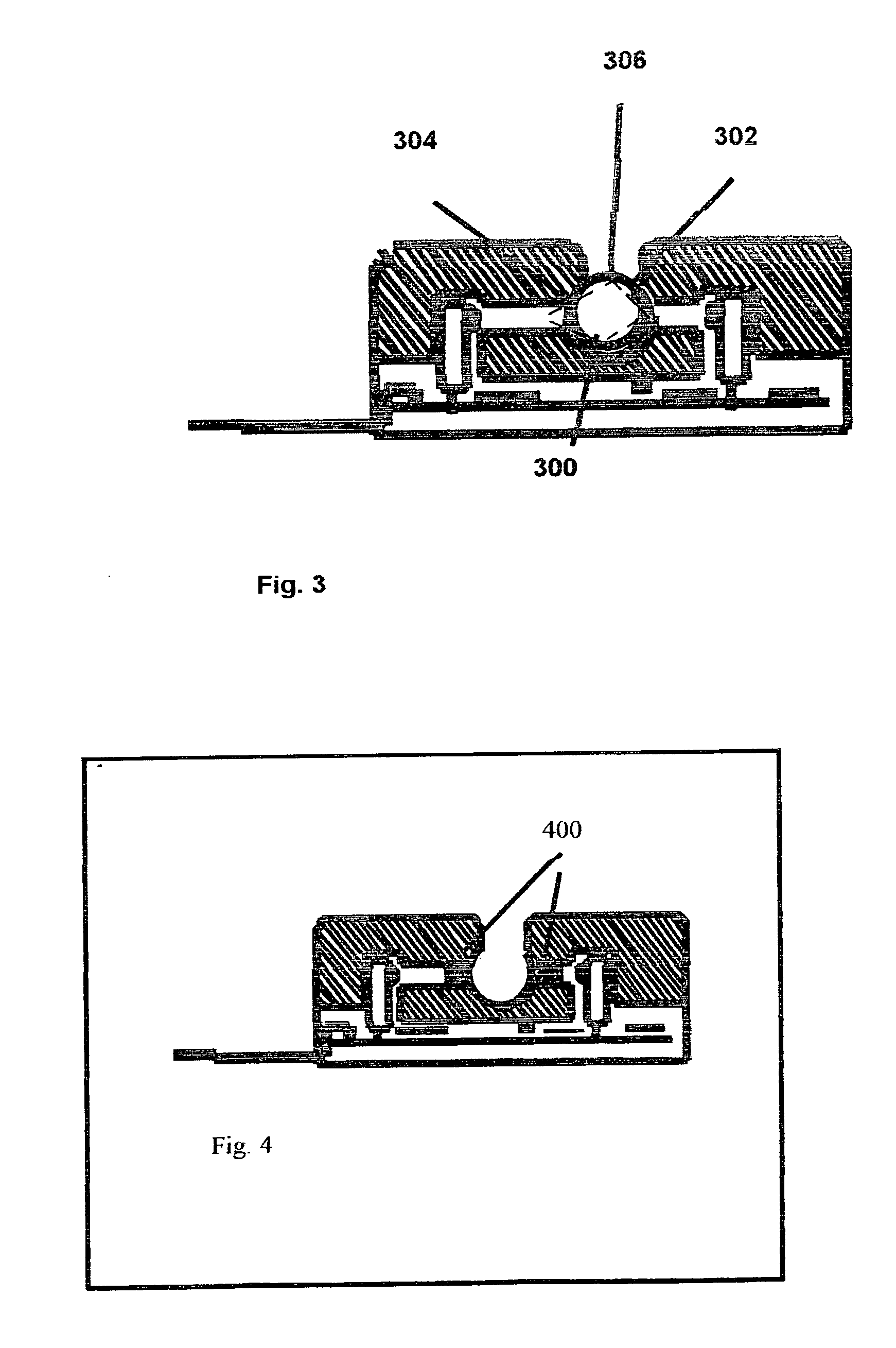
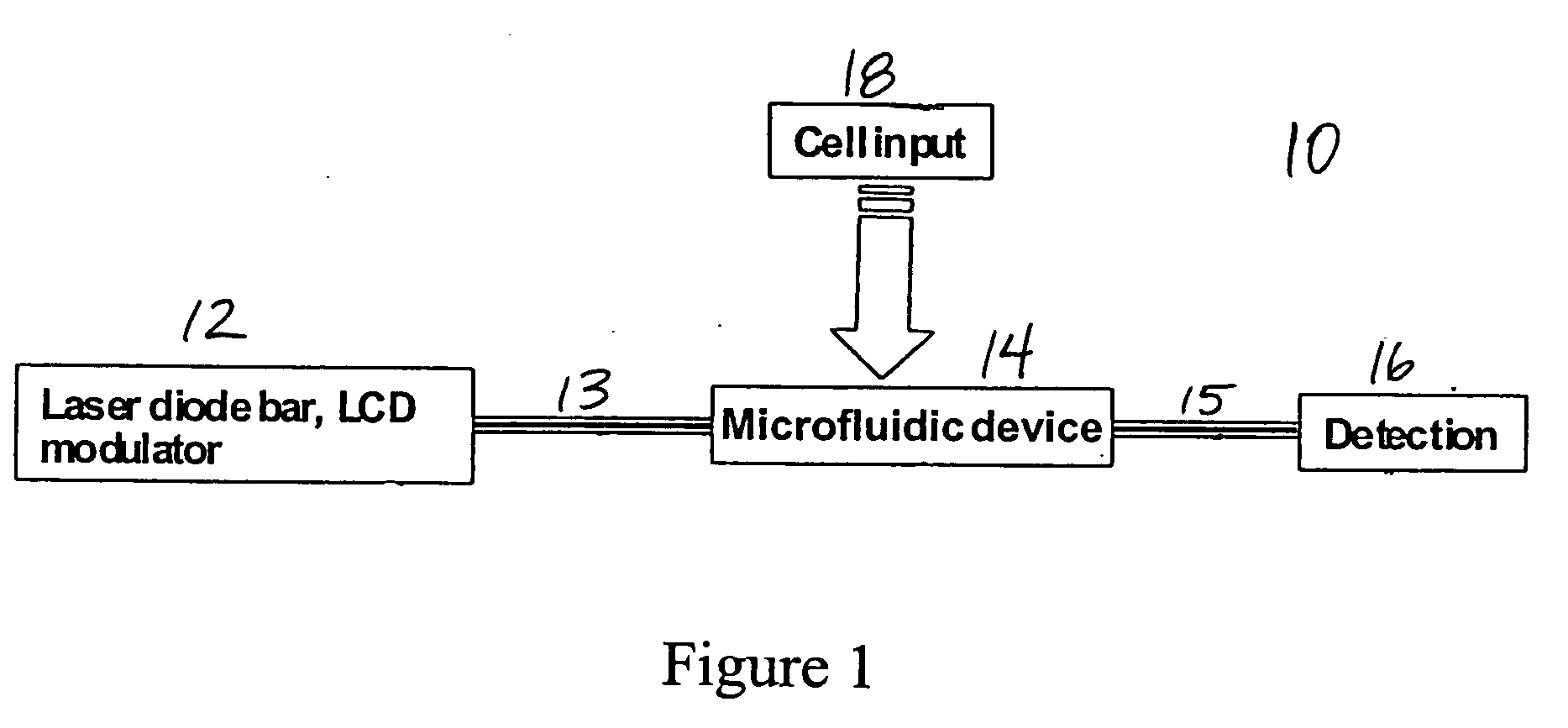
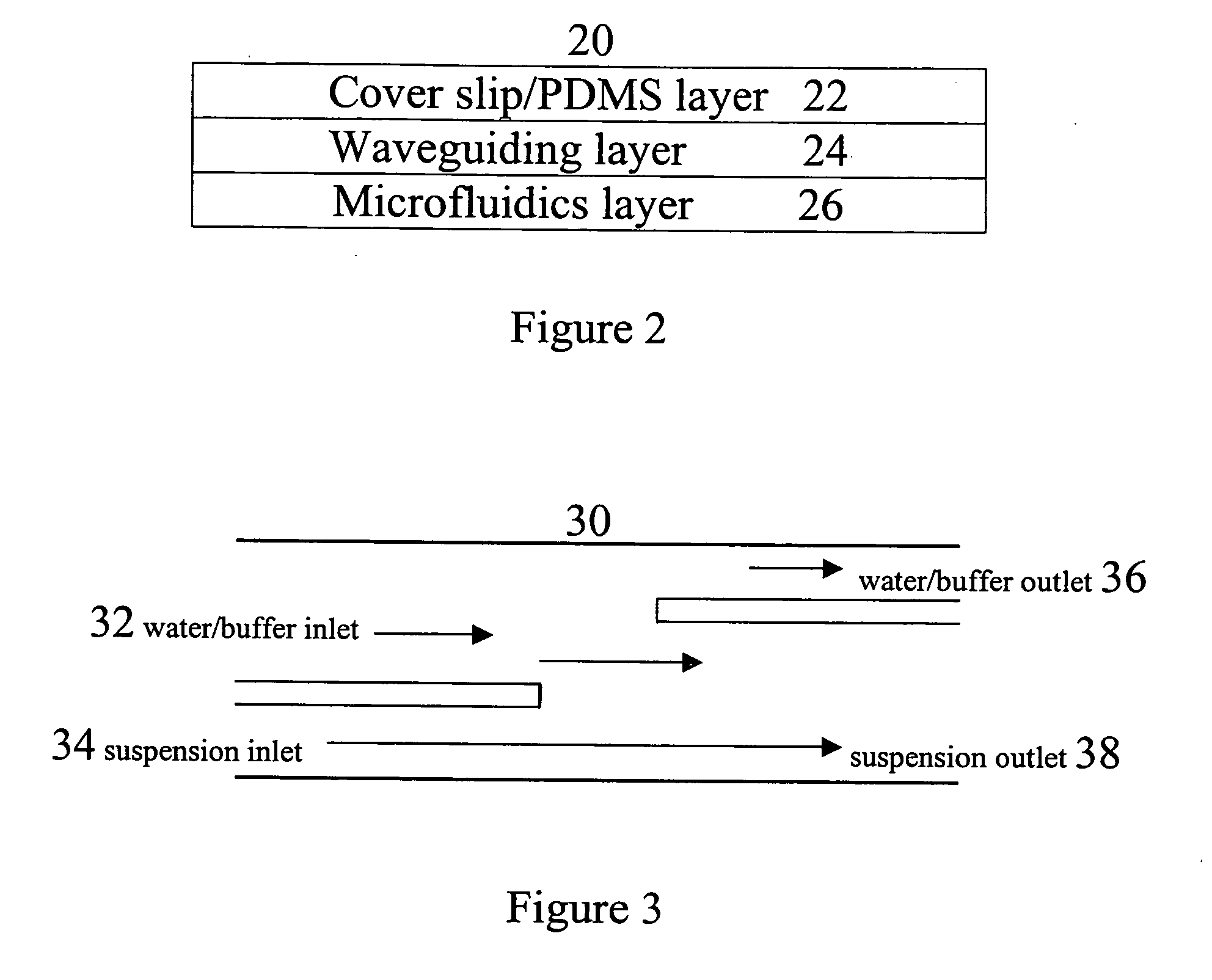
Microfluidic systems incorporating integrated optical waveguides
InactiveUS20060171846A1Efficiently sortRapidly manipulateMaterial analysis by optical meansLight waveEngineering
The invention provides microfluidic systems incorporating optical waveguides integrated, which can be used to optically interrogate particulate such as cells flowing through the system. The waveguides within these systems may be arranged to form optical traps, which may be used to power pumps and valves in the microfluidic systems, to trap and interrogate particles within these systems, and to sort trapped particles into different channels of microfluidic flow.
Owner:COLORADO SCHOOL OF MINES
Systems and methods for authenticating photographic image data
ActiveUS20170041328A1Reduce the possibilityAlteration can be preventedDigital data protectionTransmissionTime informationData file
The present disclosure provides systems and methods for authenticating photographic data. In one embodiment, a method comprises providing an image authentication application for use on a client device, the application configured to control image capture and transmission; receiving an image data file from the application at the authentication server comprising a photographic image captured by the application and metadata associated therewith; applying a watermark to the photographic image to create a watermarked image; applying date and time information to the tagged image; applying location information to the tagged image; creating a web address associated with the image data file; uploading the photographic image, the tagged image, or both to the web address; and transmitting an authenticated image file to the client device, the authenticated image file comprising one or more of: the watermarked image, the photographic image, the date and time information, geographic information, and the web address.
Owner:TRUEPIC INC
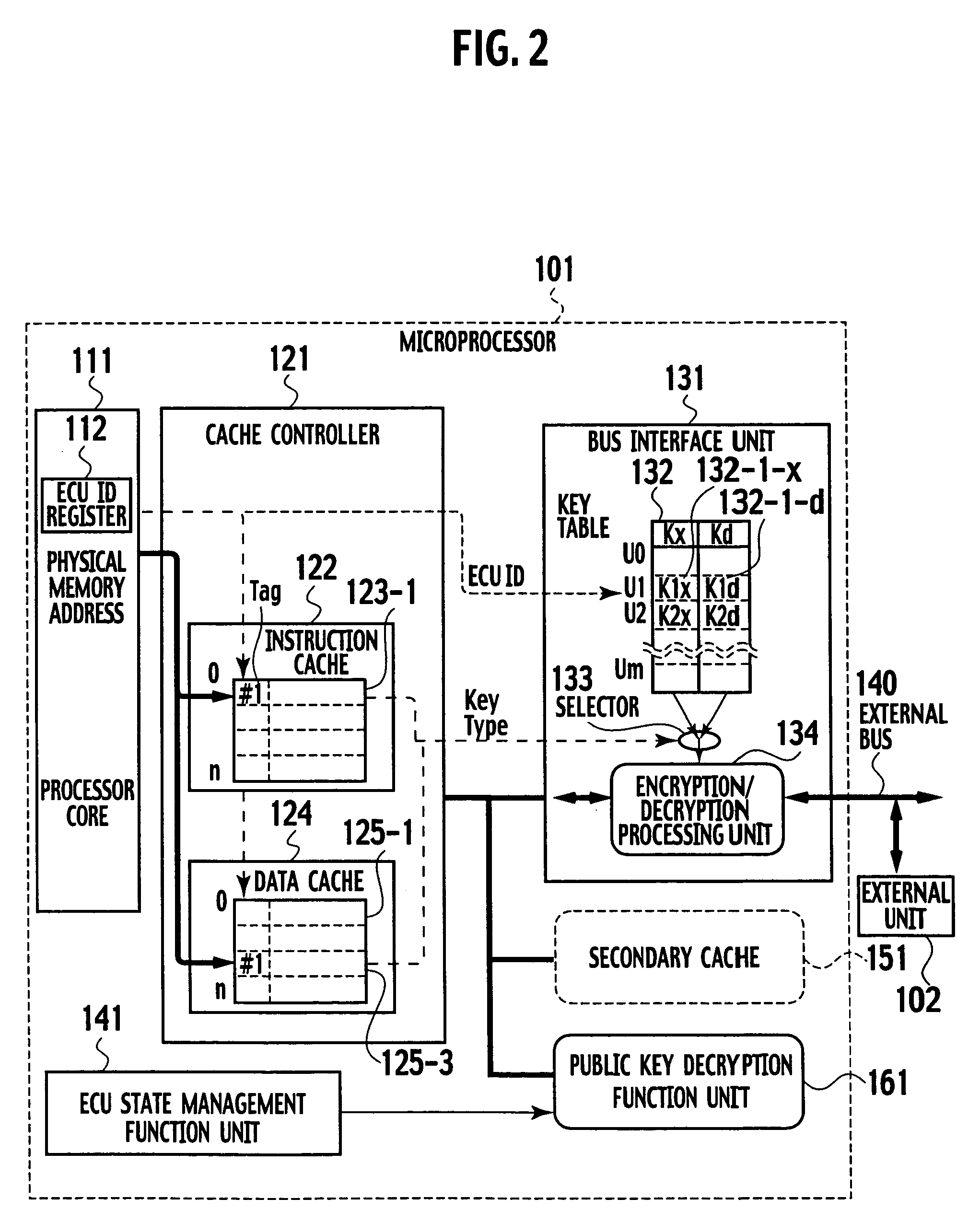
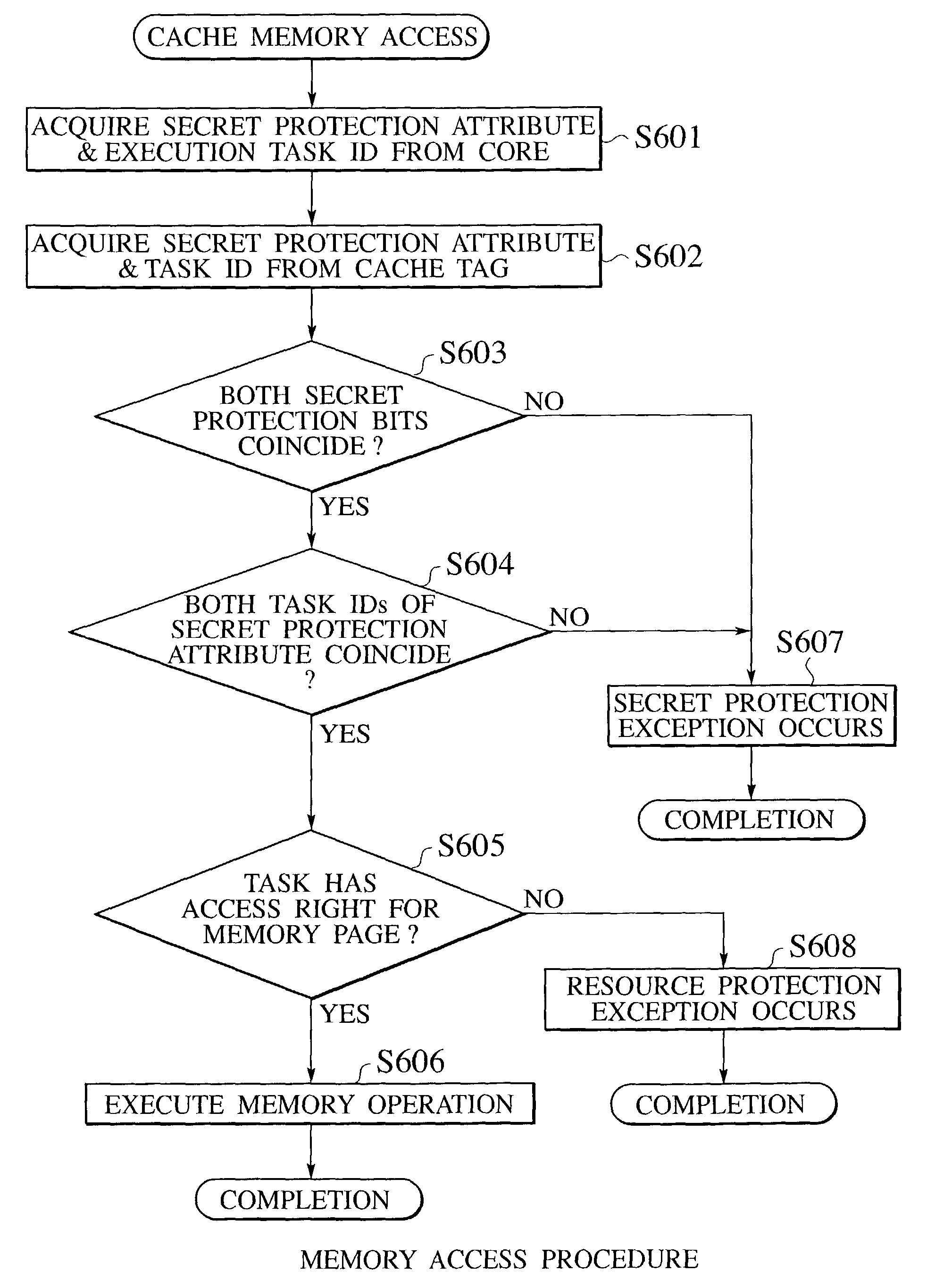
Internal memory type tamper resistant microprocessor with secret protection function
InactiveUS7219369B2Large capacityAlteration can be preventedDigital data processing detailsMultiprogramming arrangementsMemory typeInternal memory
In an inner memory type tamper resistant microprocessor, a requested secret protection attribute requested for each access target memory page by a task is set and stored exclusively from other tasks, at a time of reading a program into memory pages and executing the program as the task, and a memory secret protection attribute is set and stored for each access target memory page by the task, at a time of executing the task. Then, an access to each access target memory page is refused when the requested secret protection attribute for each access target memory page and the memory secret protection attribute for each access target memory page do not coincide.
Owner:KK TOSHIBA
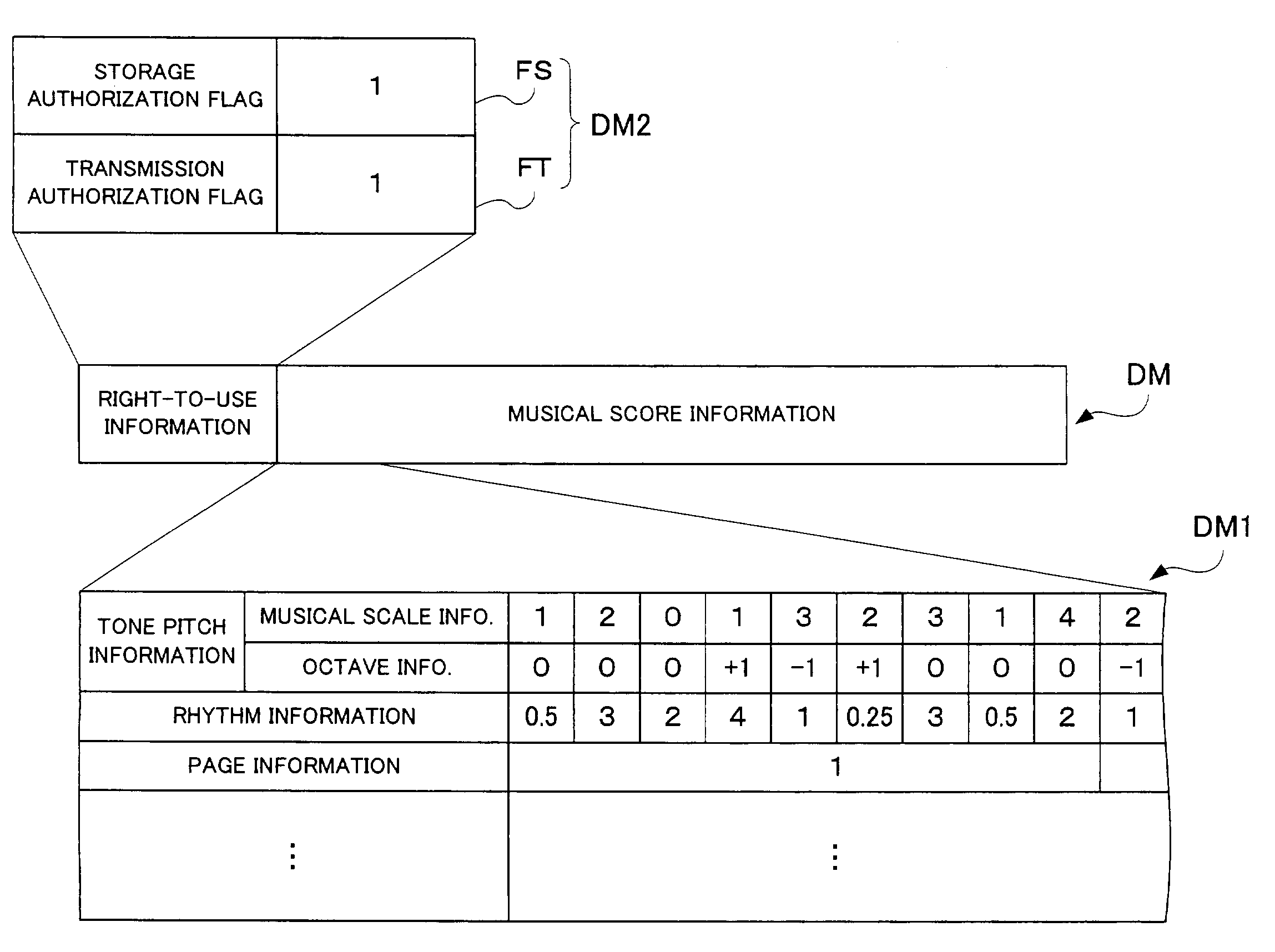
Musical-score-generating information processing apparatus and method
InactiveUS7019204B2Alteration can be preventedElectrophonic musical instrumentsDigital computer detailsInformation processingData set
Musical-score-related data set, including musical score information and right-to-use information defining a usable range of the musical score information, is distributed via a network or the like, and such a musical-score-related data set is stored in memory of an apparatus having received the data set. The right-to-use information includes information indicating that storage of the corresponding musical score is authorized or not authorized. When the musical score is to be displayed, the musical score information of the memory-stored musical-score-related data set is read out so that the musical score is visually displayed on a display device. When a musical score storage instruction or musical-score-display termination instruction is given by a user, a determination is made, on the basis of the right-to-use information of the memory-stored musical-score-related data set, whether storage of the musical score is authorized or not, and, if the storage of the musical score is not authorized, the corresponding musical score data set is deleted from the memory. The right-to-use information also includes information indicating that transmission of the corresponding musical score is authorized or not authorized, and, only when it is determined that the transmission is authorized, the transmission, to another apparatus, of the musical score is authorized.
Owner:YAMAHA CORP
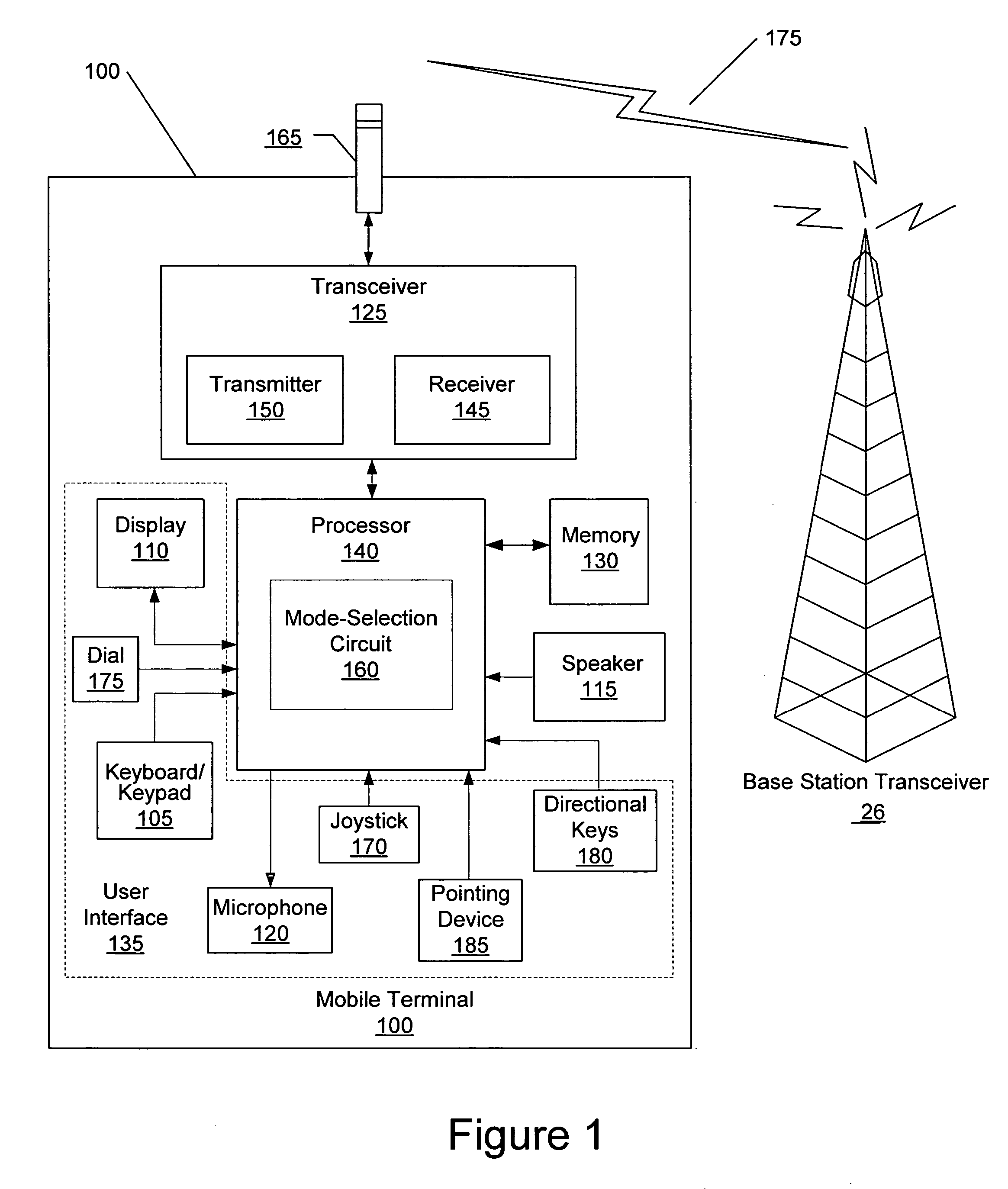
Methods, devices, and computer program products for providing multiple operational modes in a mobile terminal
ActiveUS7546130B2Alteration can be preventedUnauthorised/fraudulent call preventionEavesdropping prevention circuitsComputer hardwareOperation mode
A method of operating a mobile terminal includes receiving mobile communications and transmitting mobile communications in a first mode of operation, and enabling at least one function that is not available in the first mode of operation while preventing transmission of mobile communications in a second mode of operation. The first mode of operation is activated responsive to receiving a valid authorization code in the second mode of operation. Related devices and computer program products are also discussed.
Owner:SONY CORP
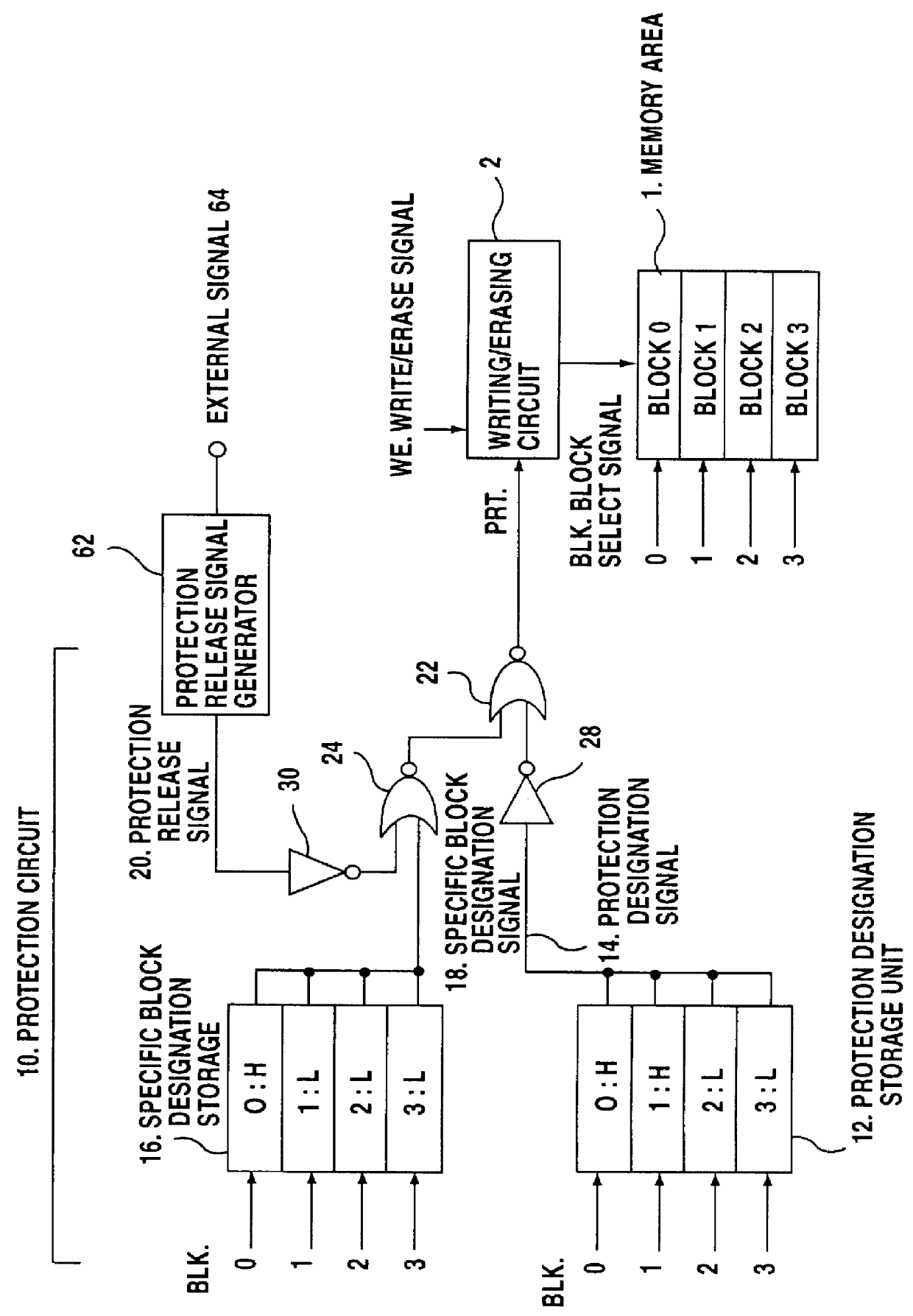
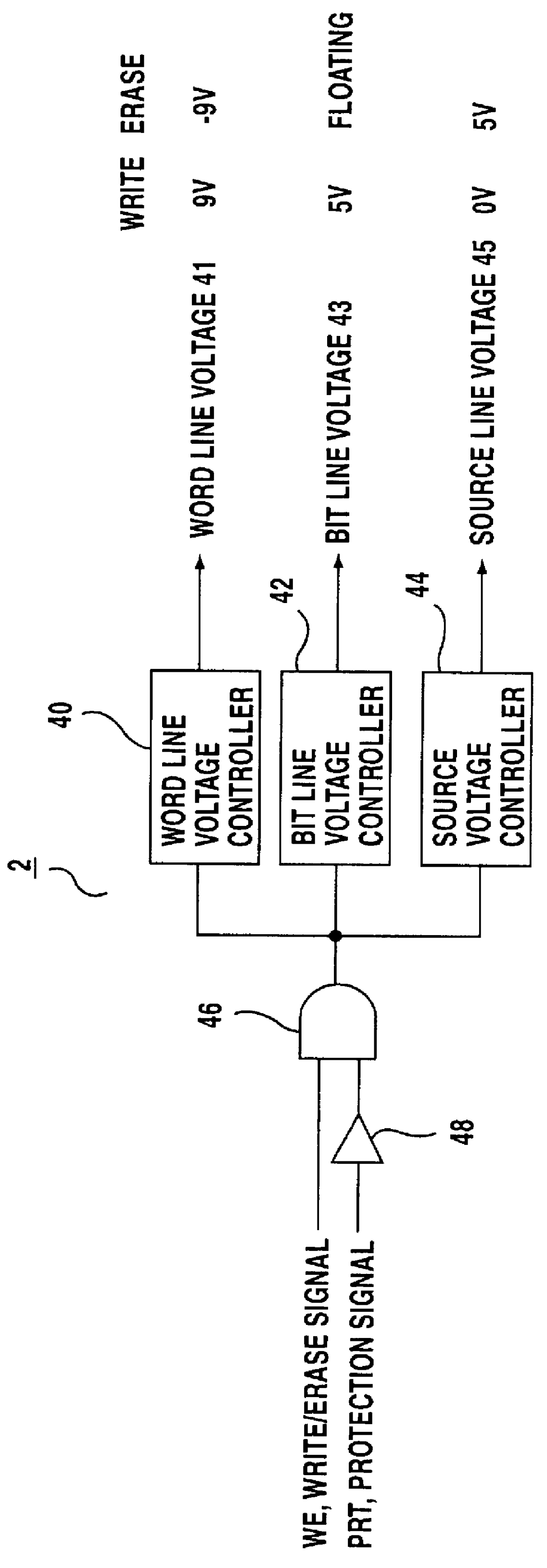
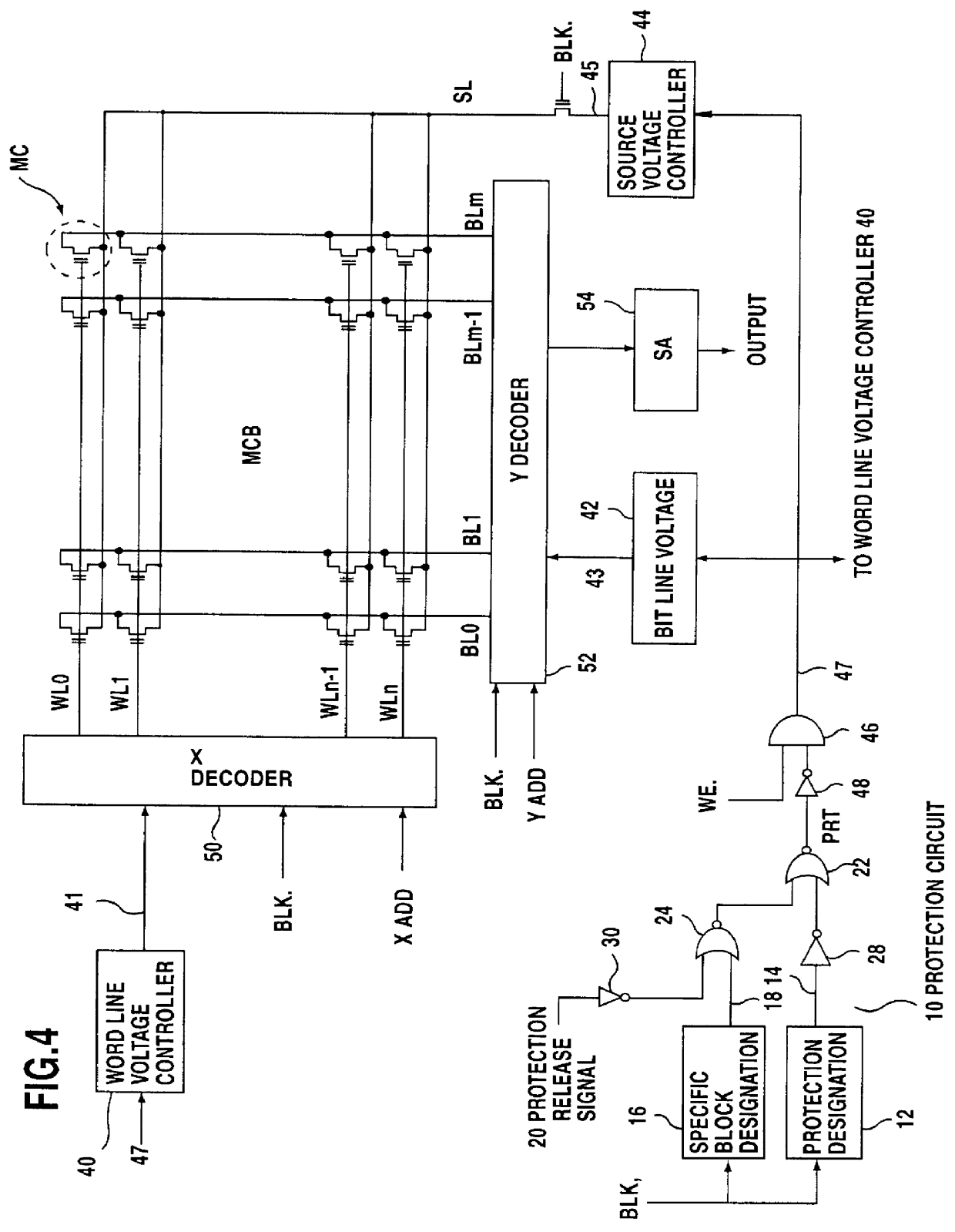
Memory device
InactiveUS6108235APrevent stateImprove protectionRead-only memoriesUnauthorized memory use protectionOperating systemStorage cell
A memory device for performing the writing and erasing of data in an individual block, including a protection designation storage unit for storing, for each memory block, protection designation data for inhibiting the writing and erasing of data; and a specific block designation storage unit for storing, for each memory block, specific block designation data for inhibiting the release of protection. When a memory block continues to be designated as a specific block according to specific block designation data, even though a protection-released state for disregarding protection designation data has been set in accordance with a protection release signal, the protection release signal is disregarded. As a result, even in the protection released state, the writing and the erasing of data is inhibited relative to the memory block which has been designated a specific block, and double data protection levels can be provided. When the writing or the erasing of data is to be performed in a memory block designated as a specific block, simply setting the protection release signal in the protection-released state is not enough, and a more complicated operation, i.e., altering the protection designation data, is required whereby the security provided for protected data is increased.
Owner:SOCIONEXT INC
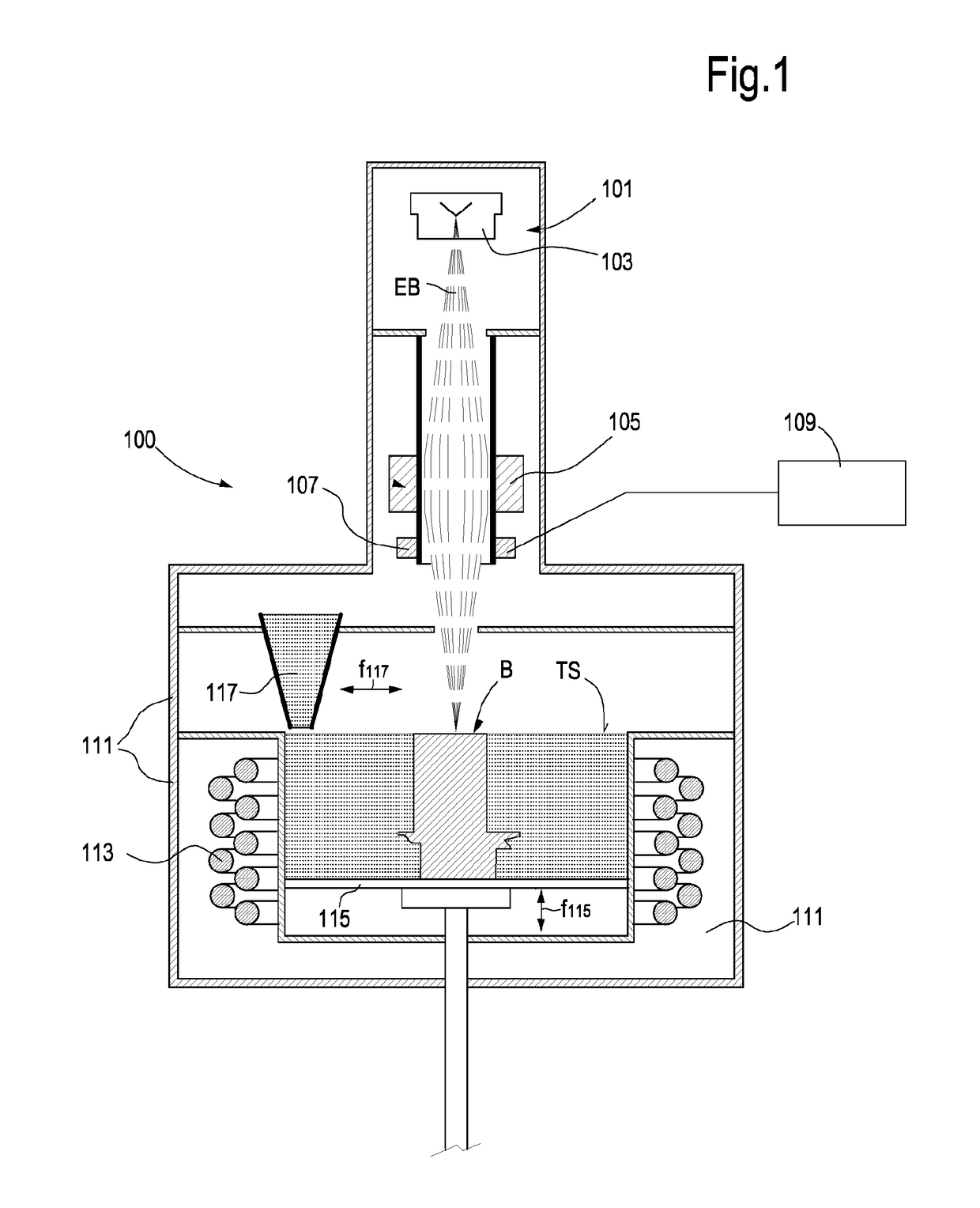
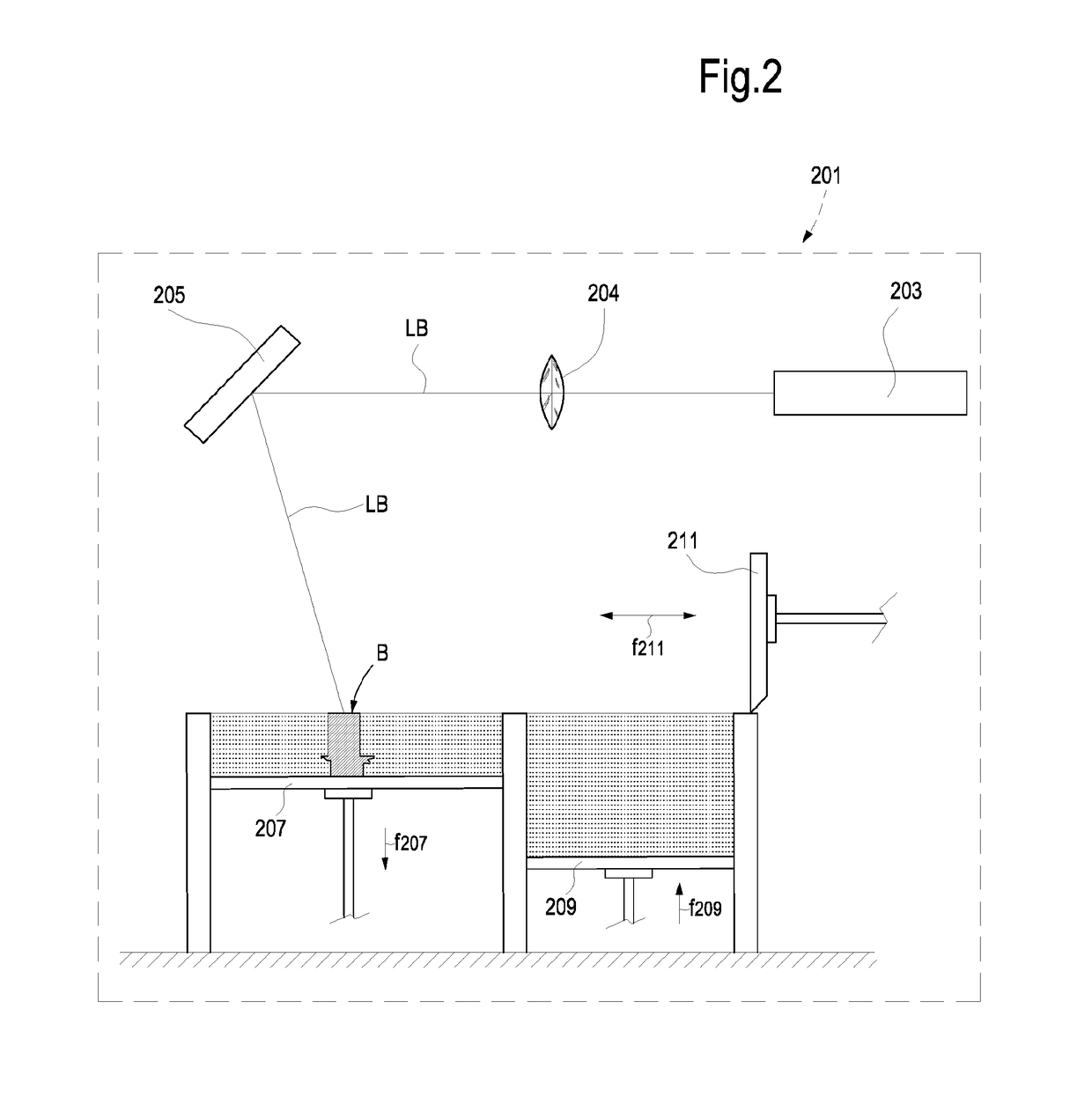
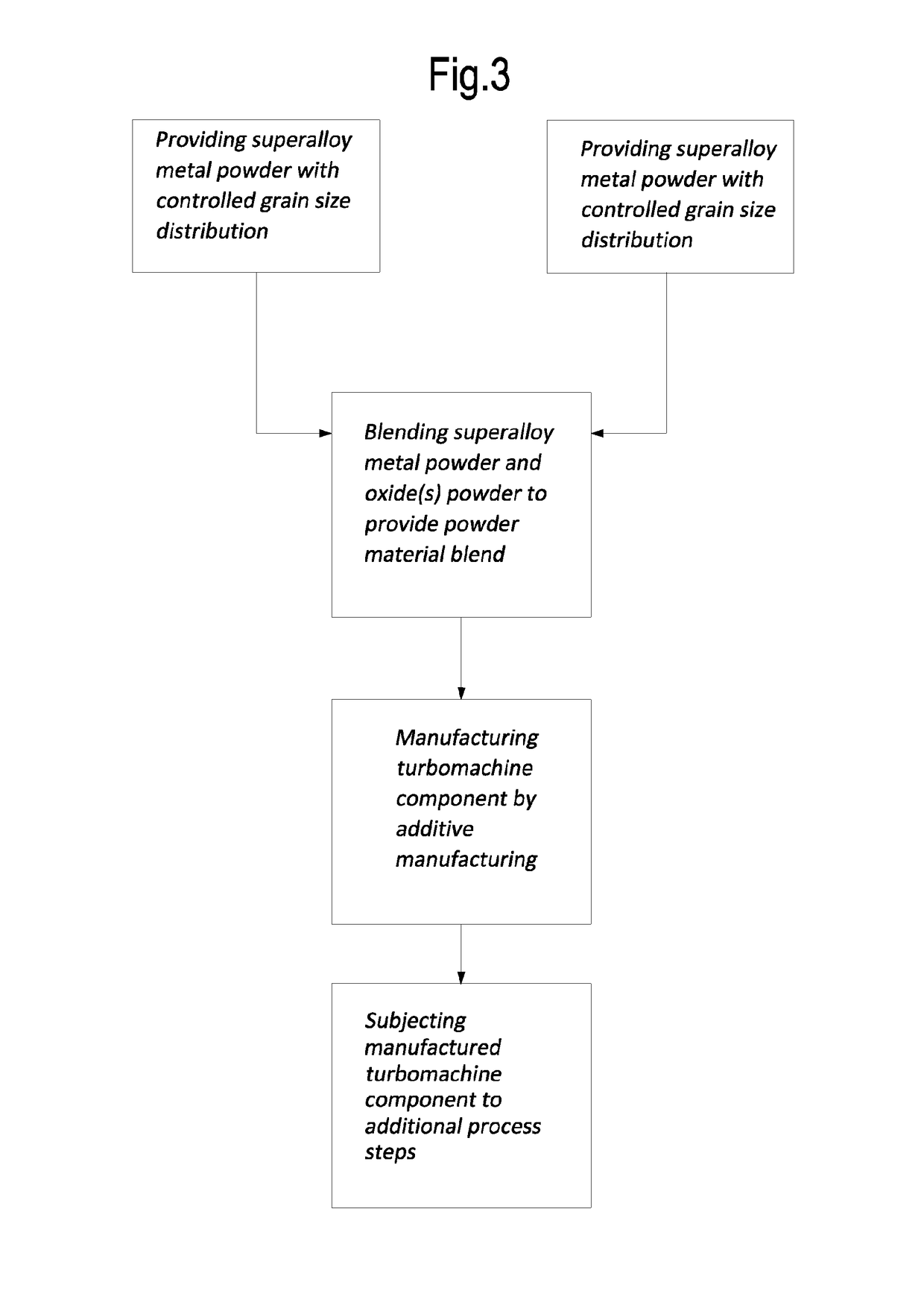
Method for manufacturing machine components by additive manufacturing
ActiveUS20170209923A1Improve creep resistanceWithout adversely affecting fragilityTurbinesAdditive manufacturing apparatusPowder mixtureAdditive layer manufacturing
A method for manufacturing a machine component made of metal-based material is described. The method comprises the steps of: providing a powder blend comprising at least one metal-containing powder material and at least one strengthening dispersor in powder form, wherein the strengthening dispersor in powder form has an average grain size less than an average grain size of the metal-containing powder material; and forming the machine component by an additive manufacturing process using the powder blend.
Owner:BAKER HUGHES INC +1
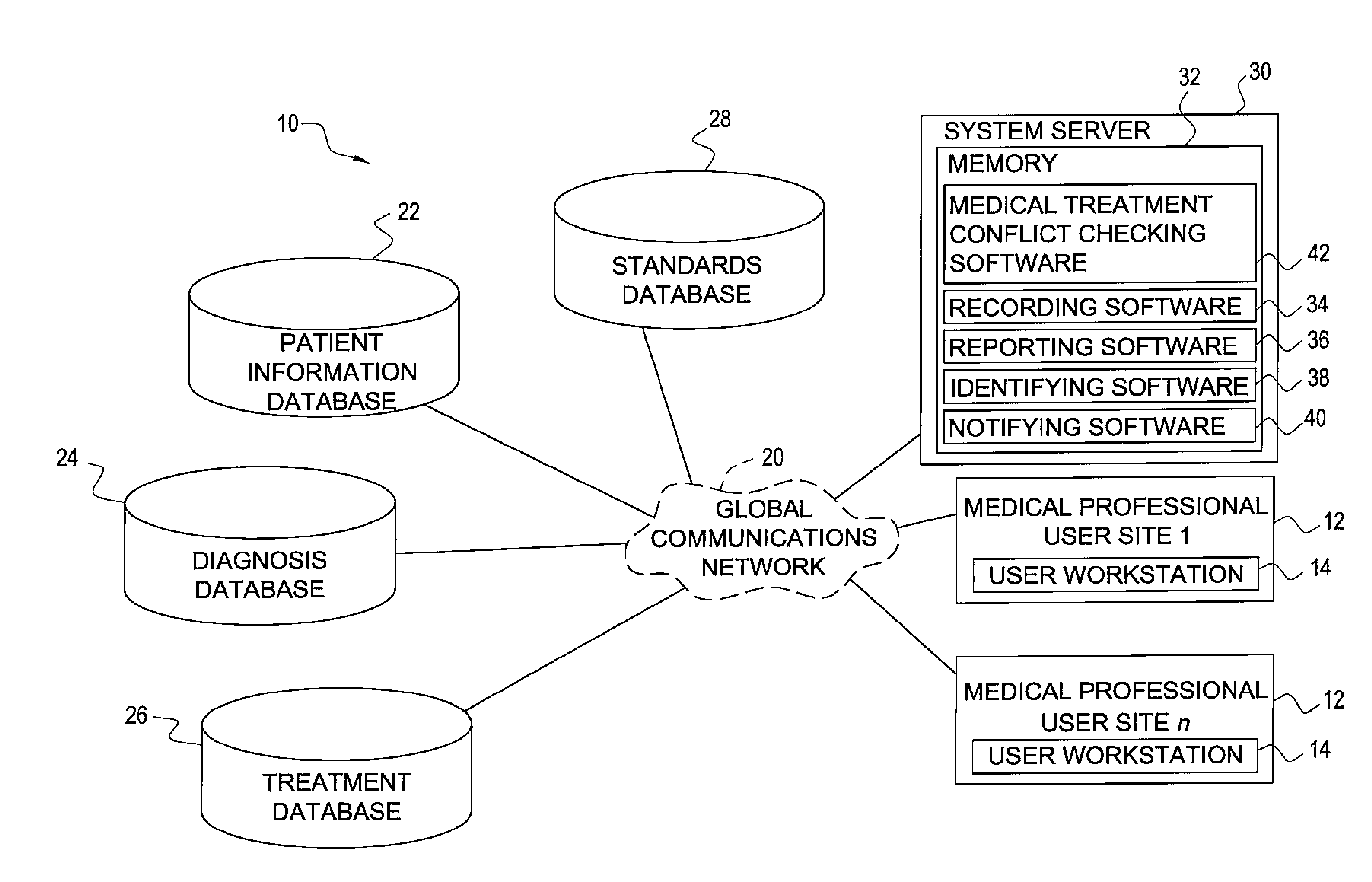
Medical decision system including medical observation locking and associated methods
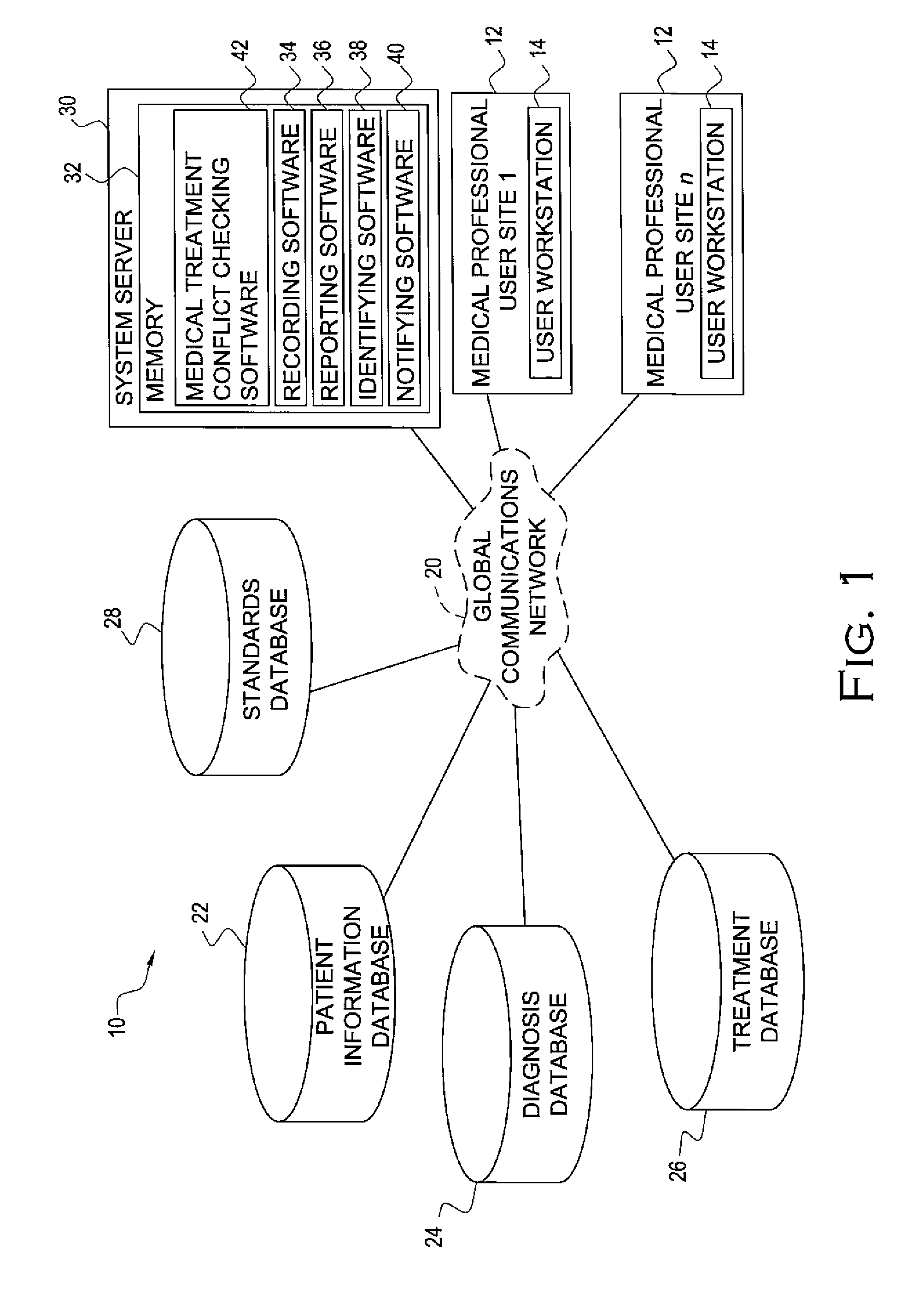
InactiveUS20110112850A1Minimizing fraudEasy accessTherapiesDigital data processing detailsDecision systemQuestion Text
A medical decision system includes a patient information database including patient information, a questions database including a plurality of questions to be presented to a user, each having question text associated therewith and a predetermined question code associated with the question text, an answers database including a plurality of answers each having answer text associated therewith and a predetermined answer code associated with the answer text, and a plurality of medical related information databases including medical related information. At least one of the question text and answer text are locked to prevent alteration thereof.
Owner:BERAJA IP
Method and apparatus for uniquely and authoritatively identifying tangible objects
InactiveUS20060107058A1Alteration can be preventedAvoid readingDigital data processing detailsUser identity/authority verificationDigital signatureTangible object
A smart chip protection system contains a unique public / private identity key pair and uses a separate public / private signature key pair. The identity private key is stored in permanent, secure storage such that it can not be read outside the chip. An issuing entity generates a descriptor containing the identity public key, attribute data, and a digital signature. The digital signature is generated by enciphering a derivation of the identity public key and the attribute data with the signature private key known only to the issuer. The authenticity of the descriptor data is verified by decrypting the signature with the signature public key using a known algorithm, and comparing the result to the derivation of the descriptor data. The identity of the object can be verified requesting the smart chip ro perform an encryption / decryption operation using its identity private key, and performing the complement using the public key.
Owner:IBM CORP
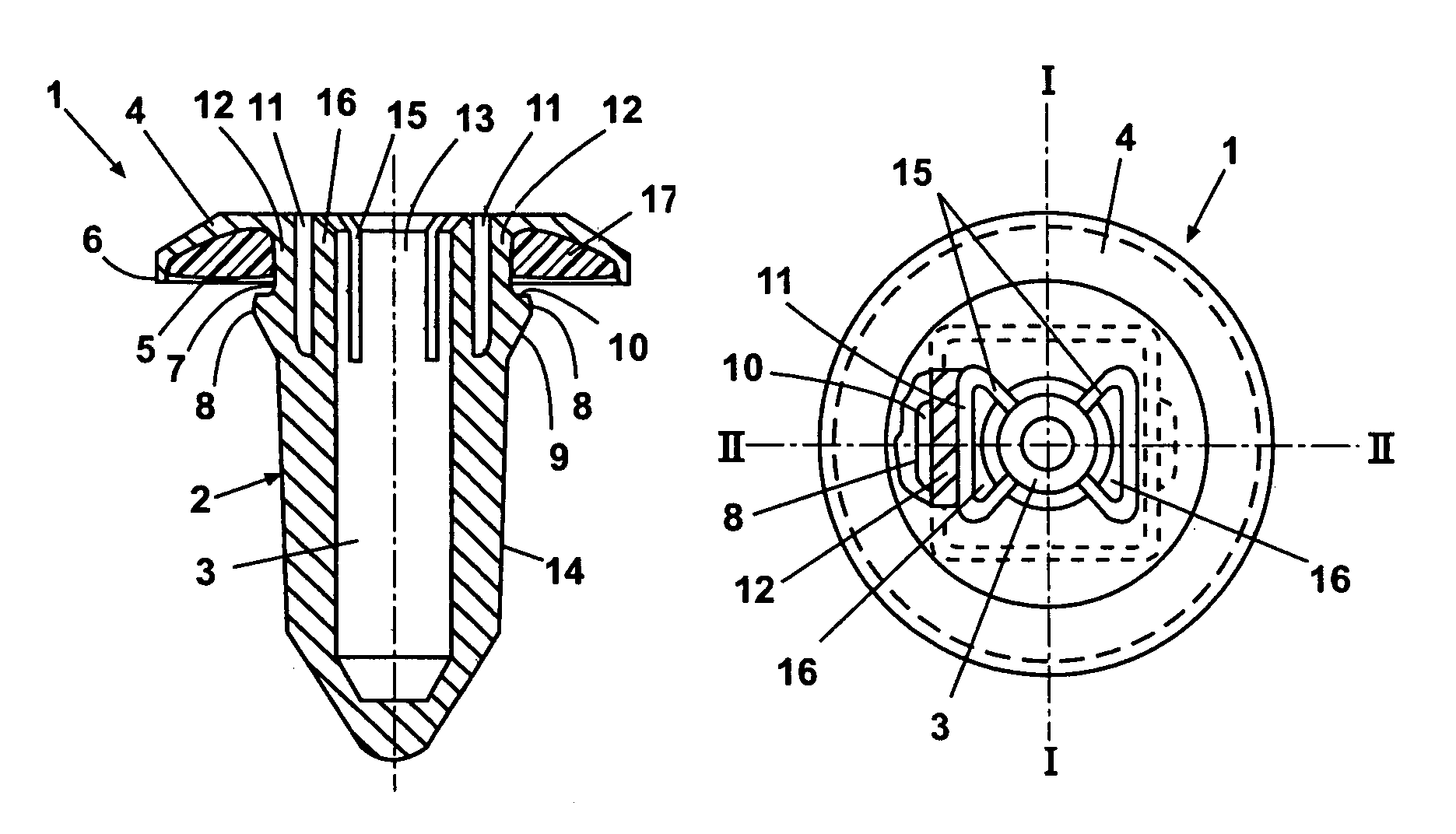
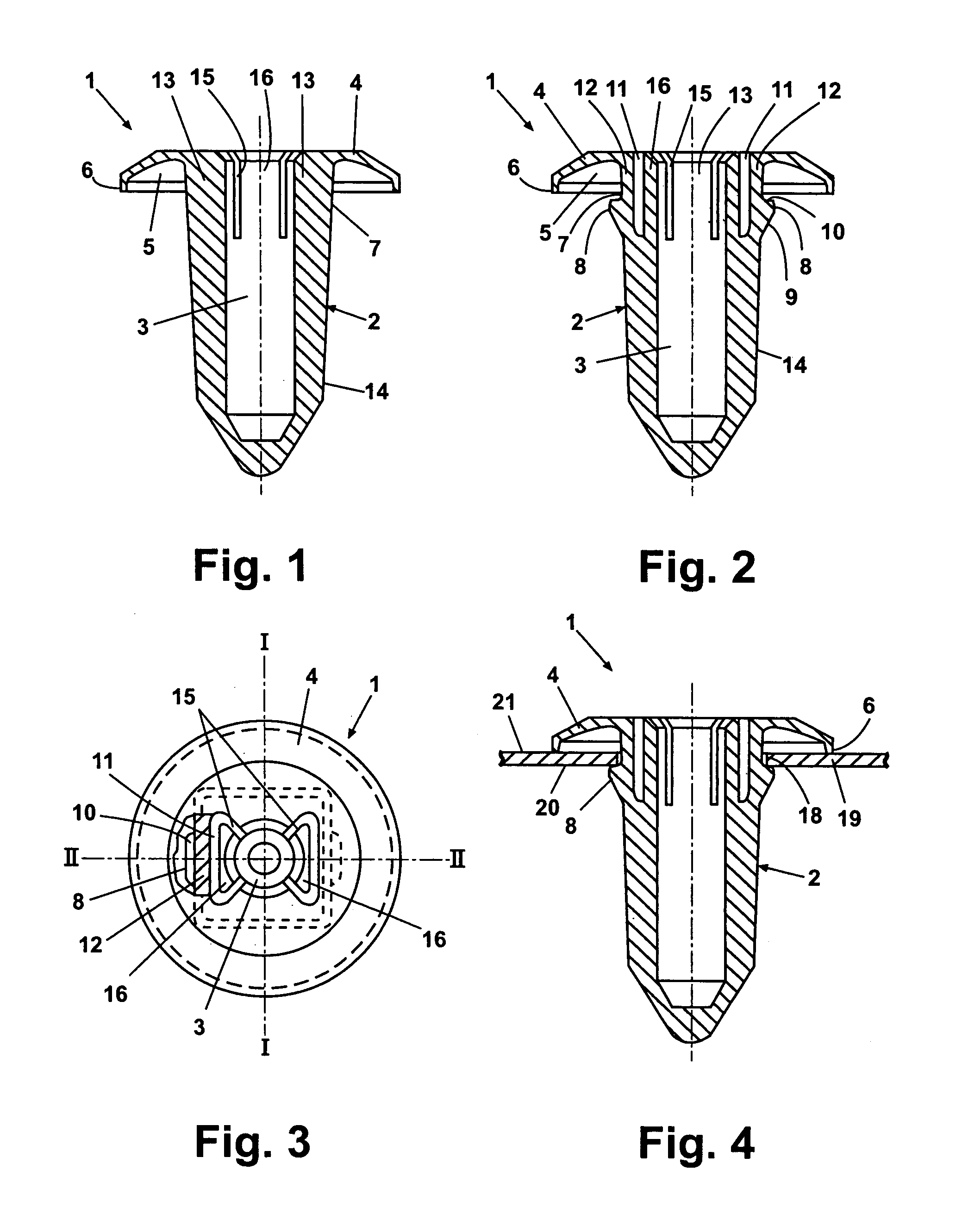
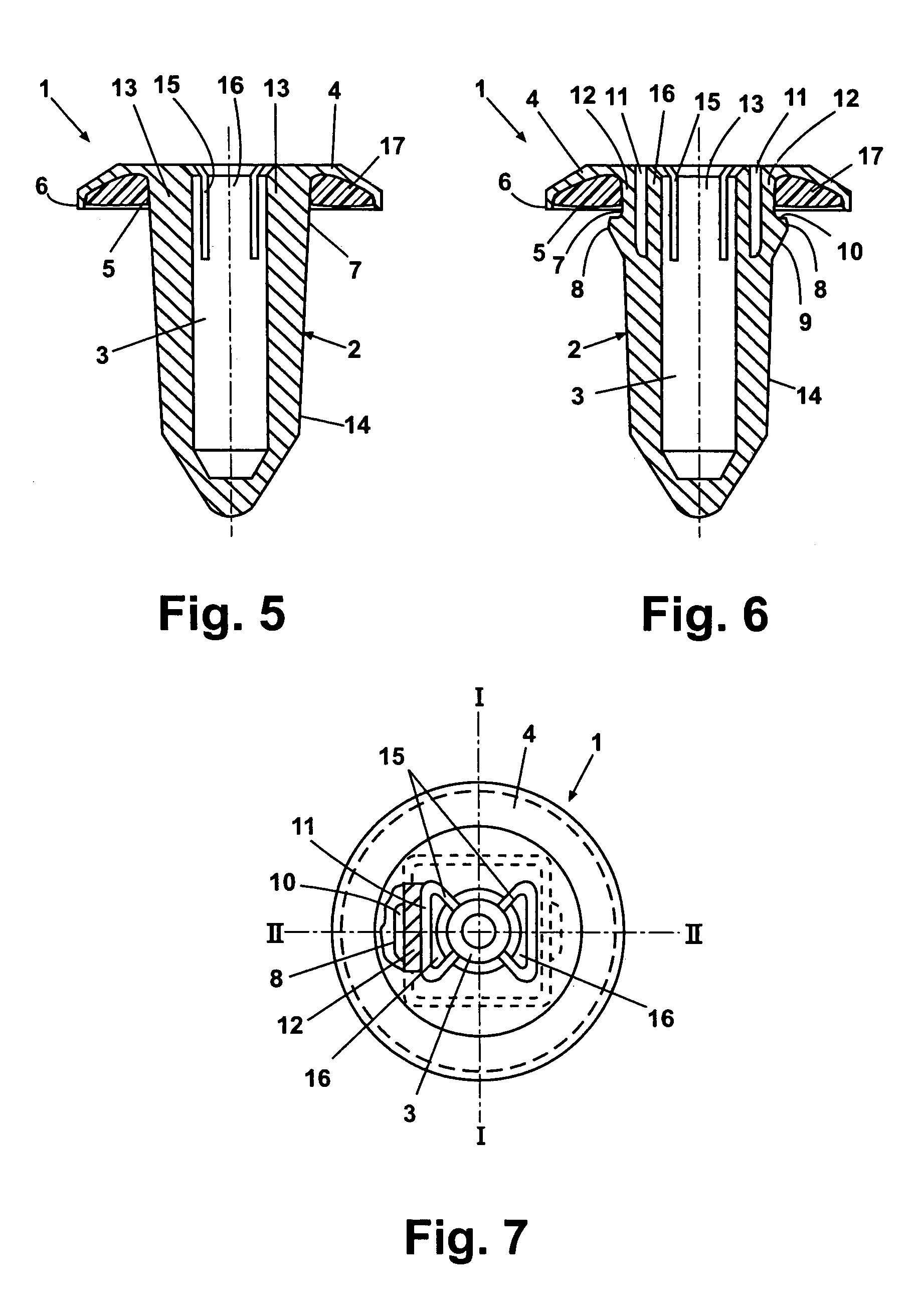
Insert part for a wall opening, in particular on a vehicle body
InactiveUS7048486B2Precise positioningNeat appearance of the bond on the flange side of the insert part is assuredPinsNutsEngineeringFlange
An insert part (1) for insertion in an opening in a wall has a neck (7) to pass through the opening and a flange (4) arranged on the neck (7) and comprising a depression (5) on the under side facing the neck (7). The depression (5) is bounded on the outside by an elevated circumferential edge and contains a body (17) of adhesive capable of being brought into a flowable state by heating. To secure the insert part in the opening of the wall, catches (8) are attached to the neck (7). The body (17) is of such size that it is completely accommodated by the depression (5), and the insert part (1) is of such conformation that, in the installation position in which it is secured by the catches (8) in the opening of the wall, the circumferential edge (6) of the flange (4) is firmly pressed into contact with the wall.
Owner:NEWFREY
Traffic control system and method of use
InactiveUS20160379490A1Reduce and eliminate errorReduce and eliminate and and limitationControlling traffic signalsRoad traffic controlCentralized computing
Owner:HAWS CORP
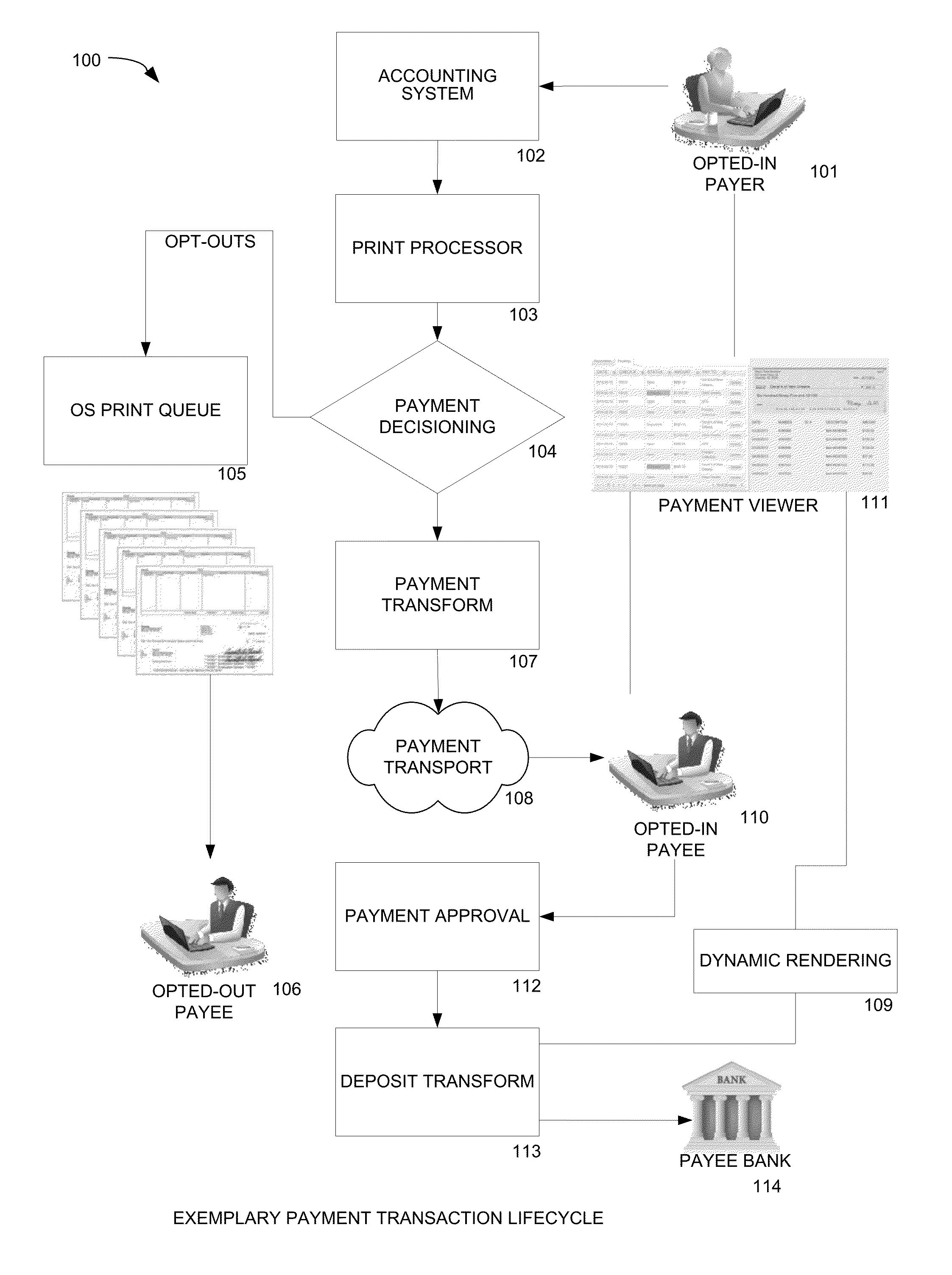
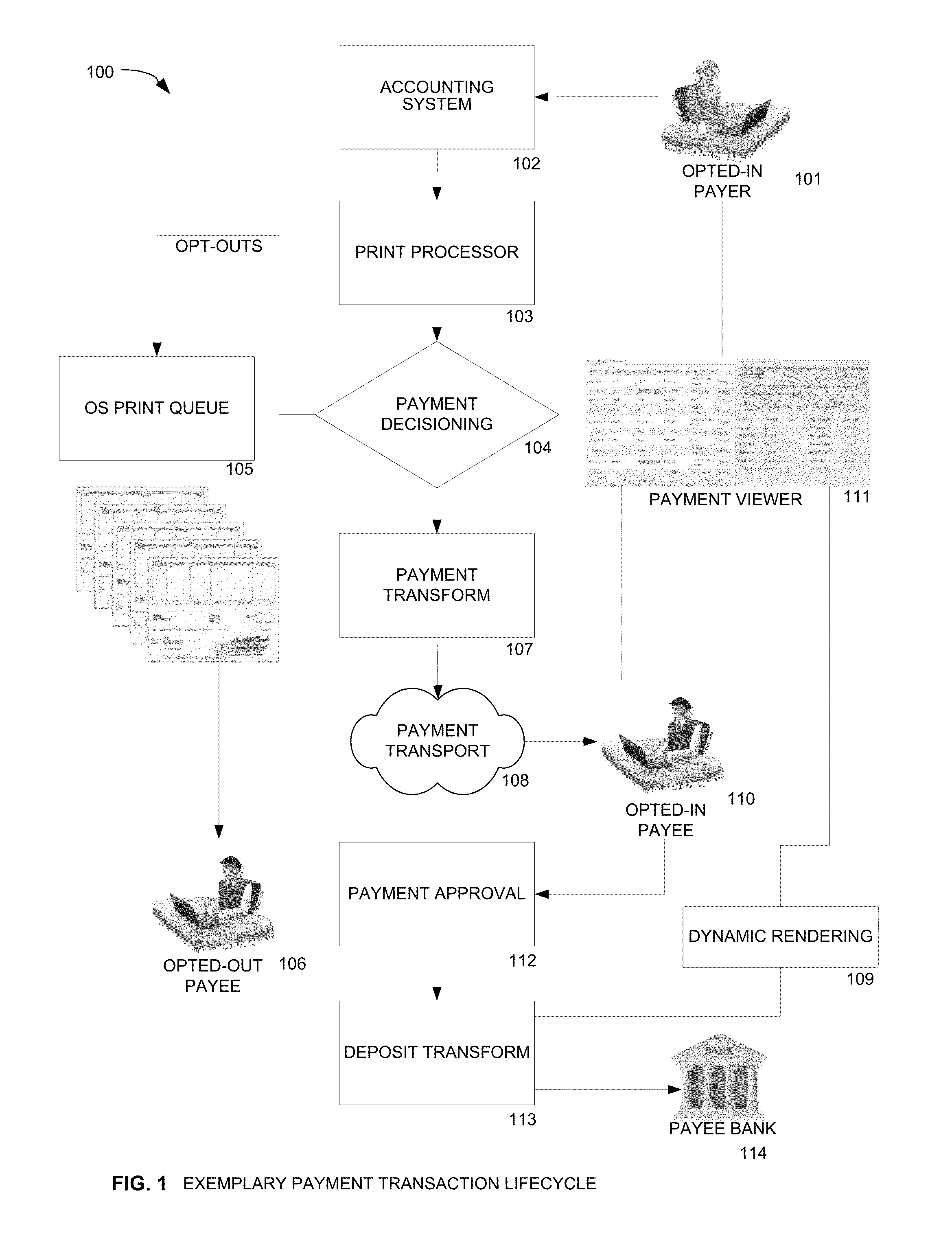
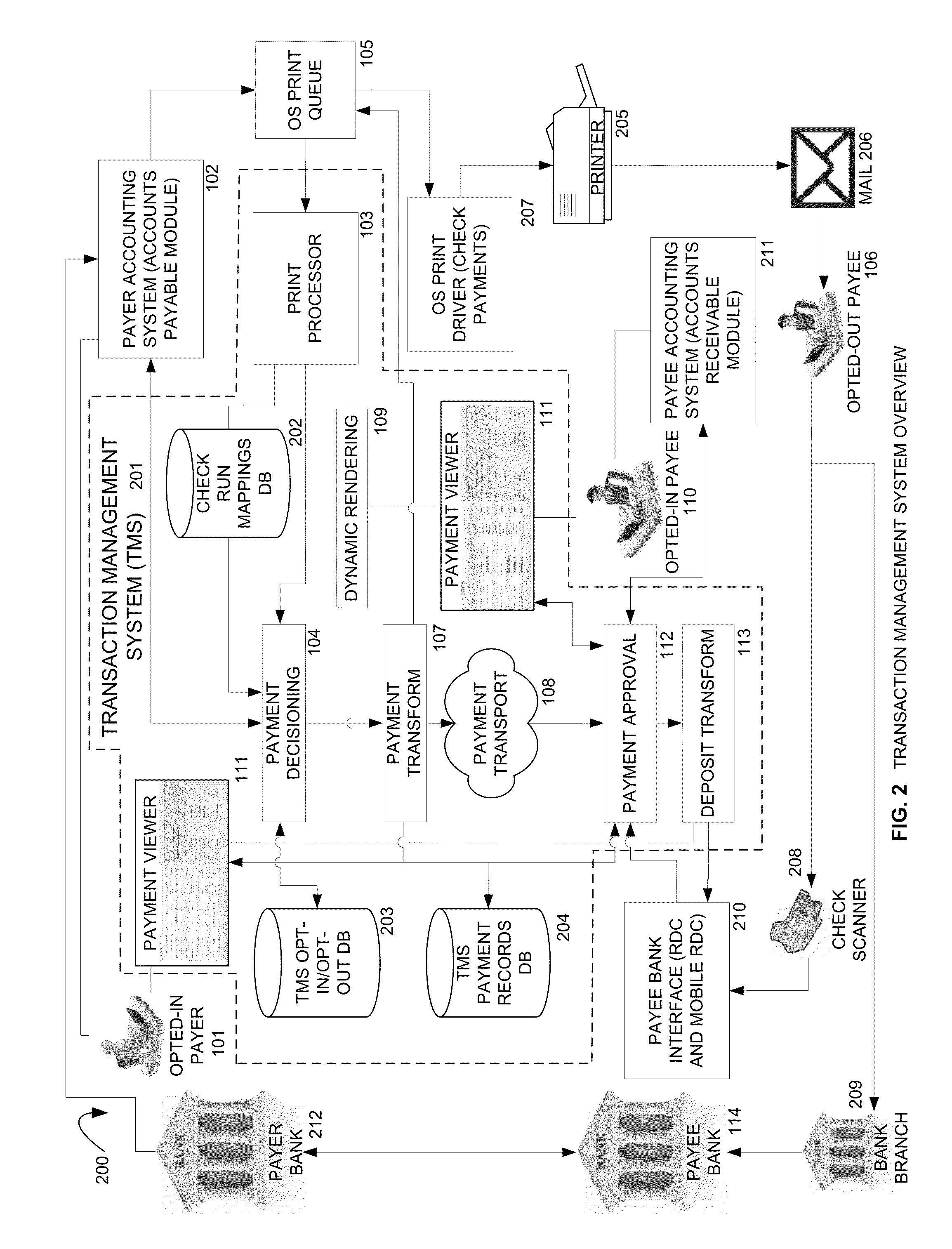
Electronic Payment System Operative with Existing Accounting Software and Existing Remote Deposit Capture and Mobile RDC Software
InactiveUS20140279310A1Alteration can be preventedPrevent theftComplete banking machinesFinanceChequePayment system
Methods and systems for providing an electronic payment to a payee on behalf of a payer. A transaction management system (TMS) receives payments data from an accounting system. The payments data is processed to determine if a payee has opted-in to receive electronic payments. If so, an electronic payment instruction is generated. If the payee has opted-out or is not in a payee file, a print file is generated for printing a conventional paper check. The payee is notified of the payment and can access the system to view a list of payments and remittance information. The payee can indicate a status for a payment on the list, e.g. accept or dispute the electronic payment. In response to selecting a payment in the payments list, the payee is provided with a view of an electronic check representation generated from the electronic payment instruction. The payer can access the payment status in the system to determine if a payment has been accepted. If accepted, the electronic payment instruction is transmitted to a payment recipient system in the form of electronic check representation.
Owner:KOKOPAY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com