Patents
Literature
148results about How to "Improve trustworthiness" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
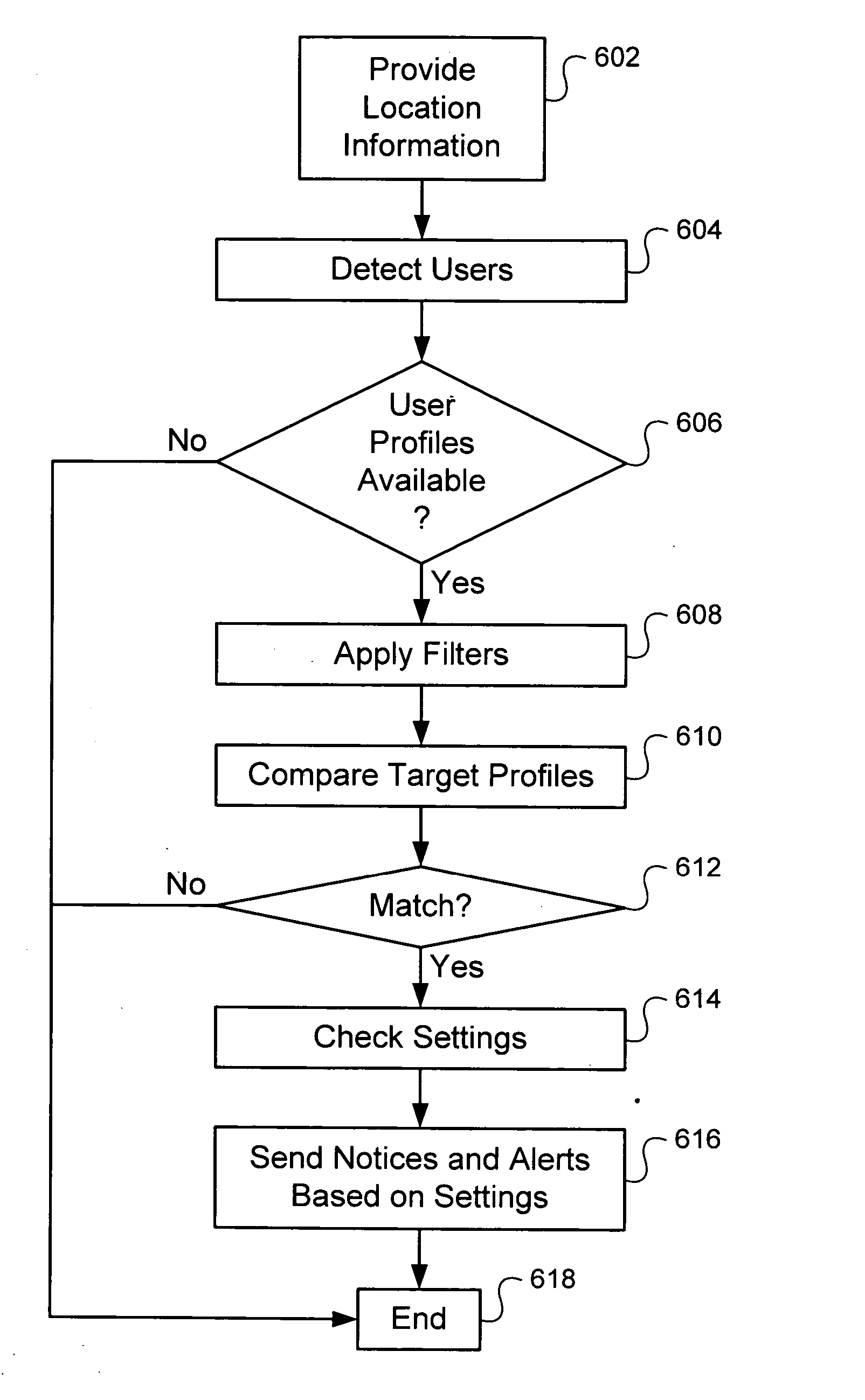
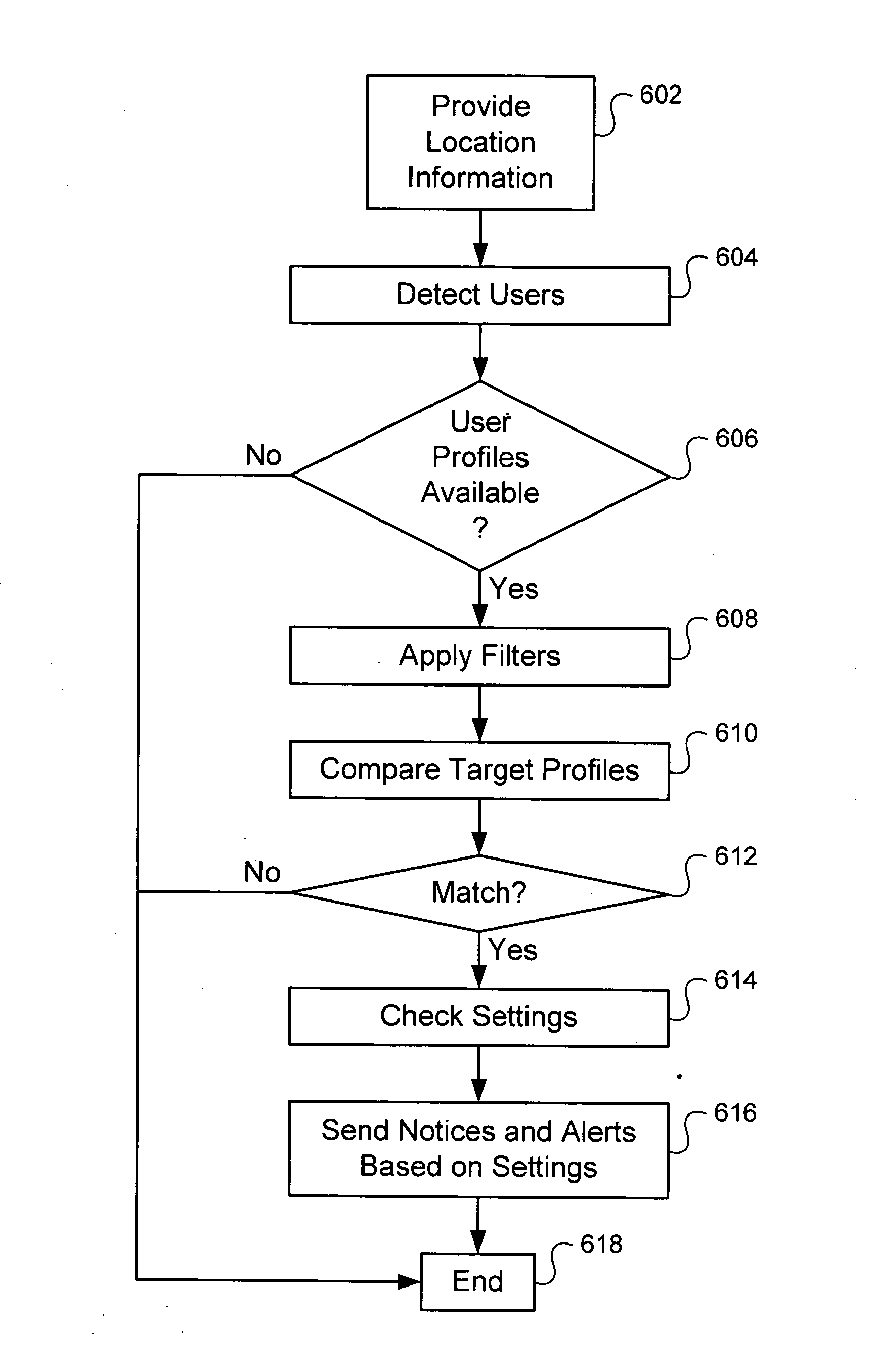
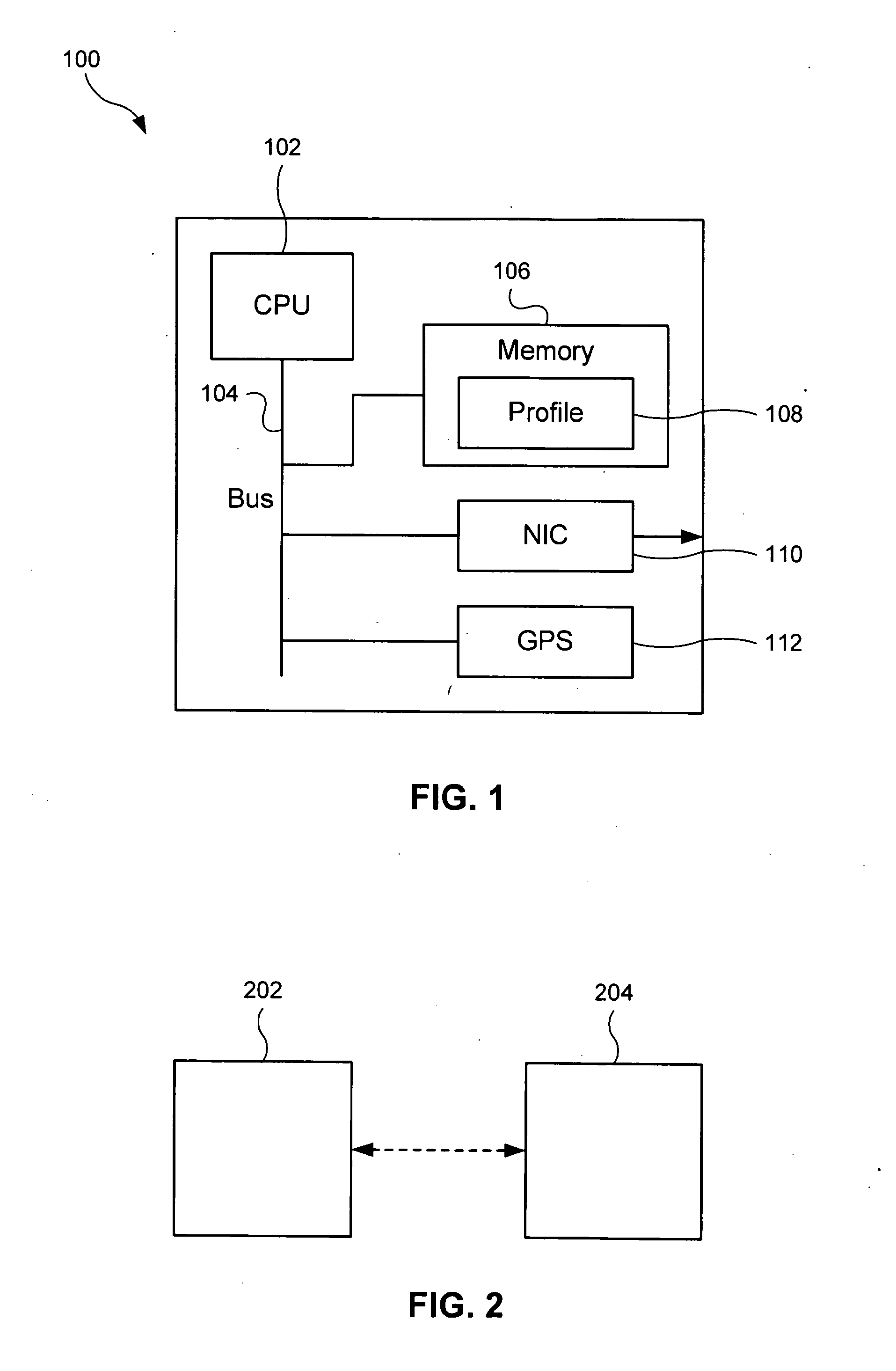
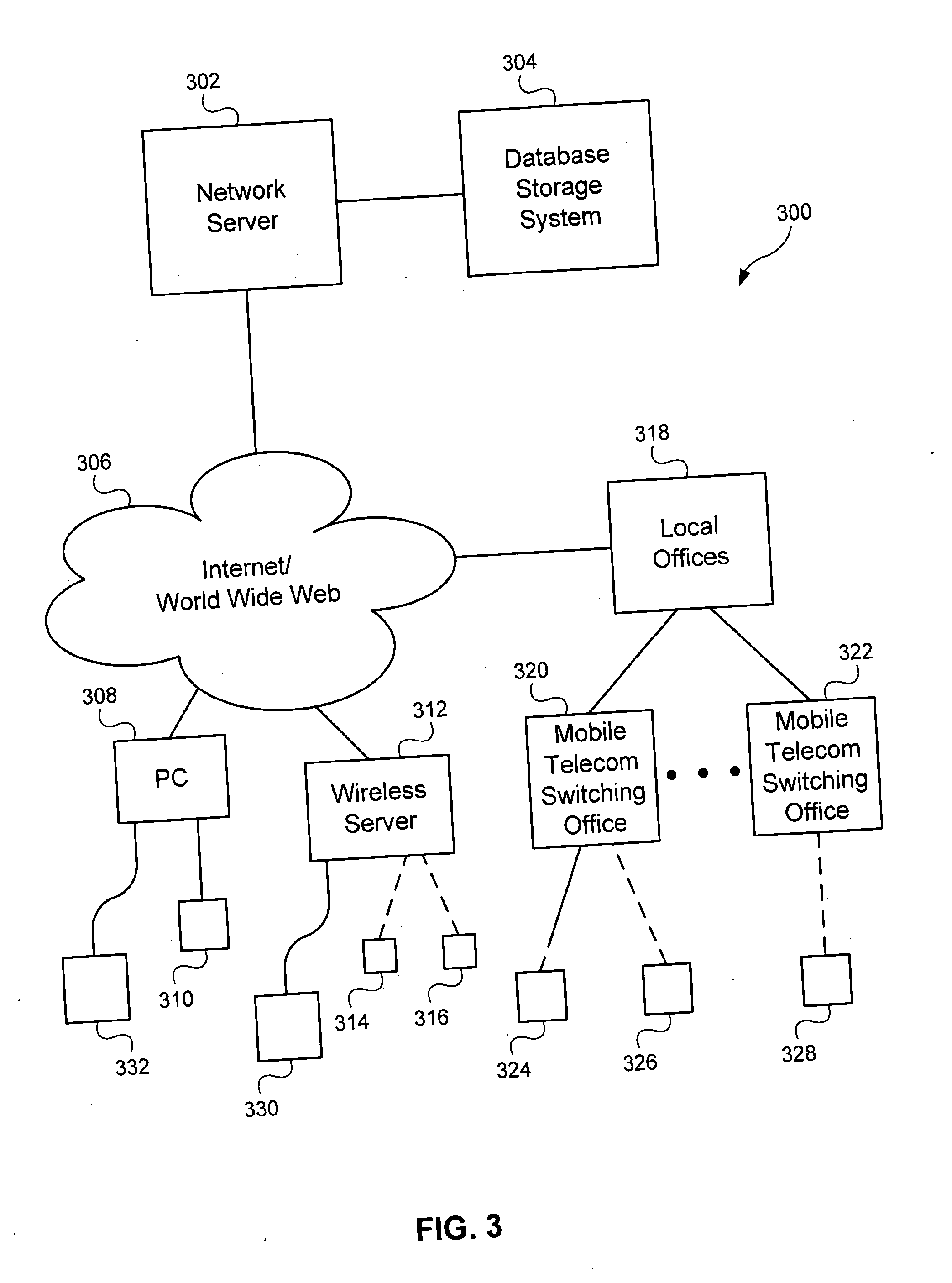
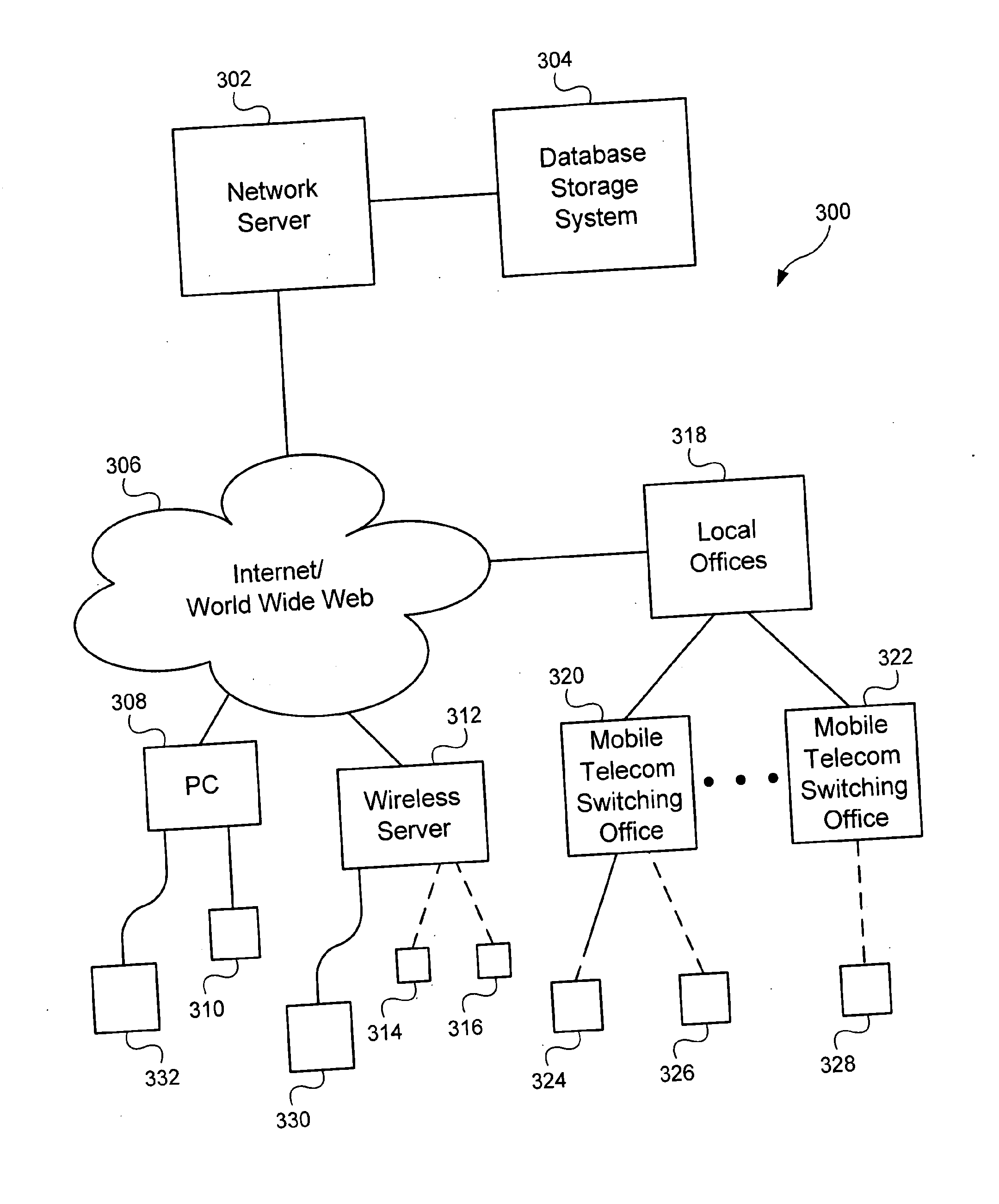
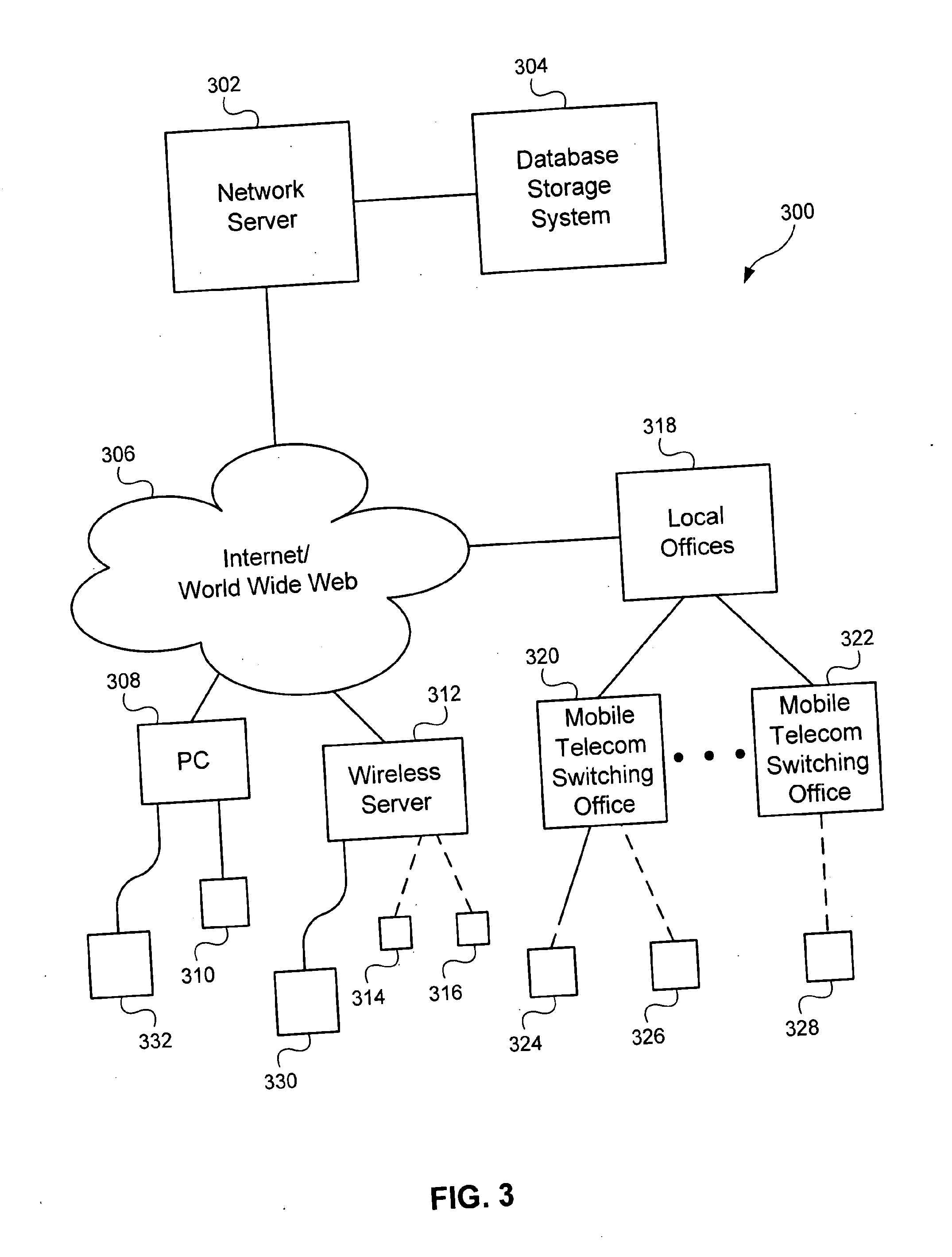
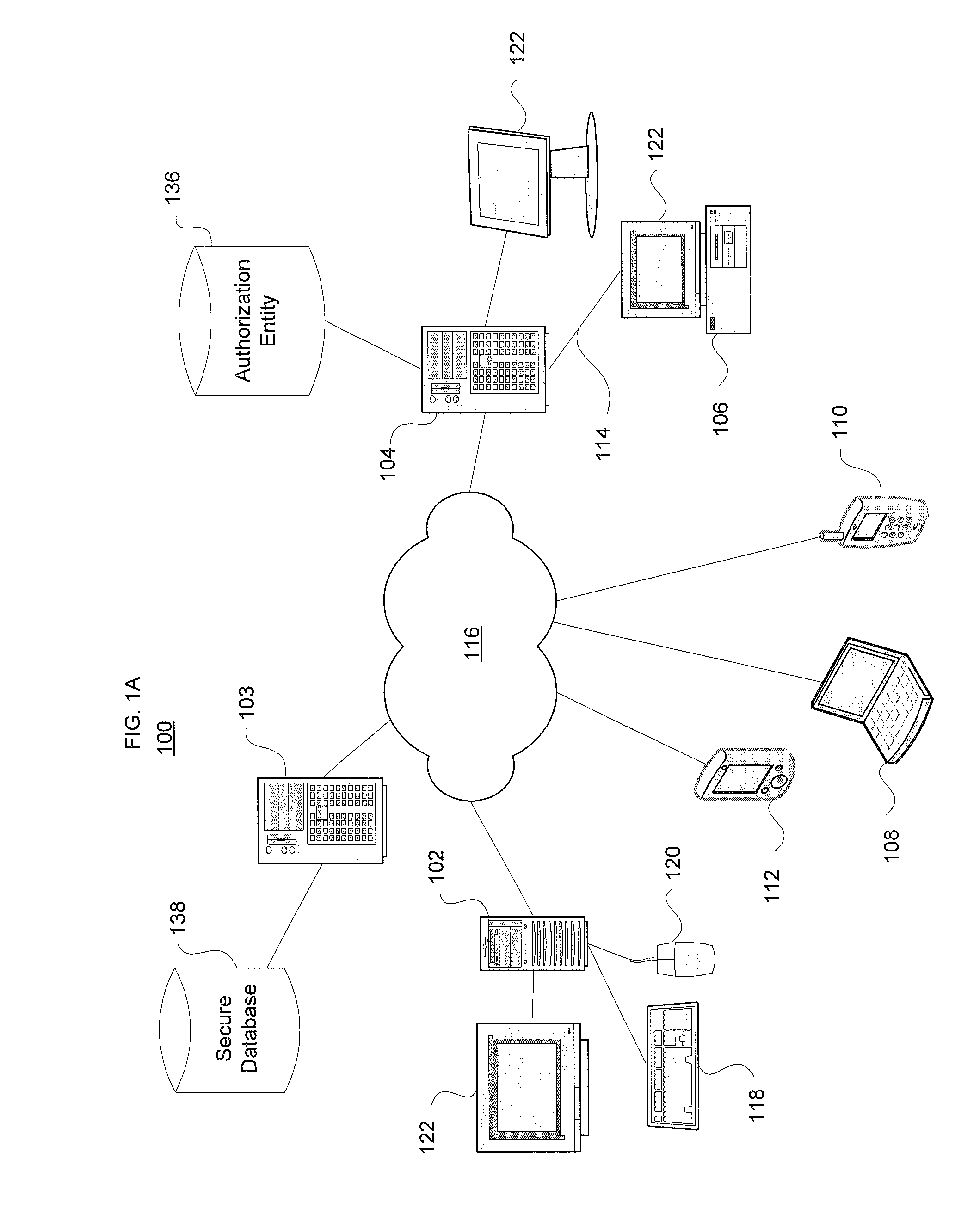
System and method for location based social networking
ActiveUS20060085419A1Quality improvementImprove trustworthinessDigital data information retrievalAdvertisementsPosition dependentSocial web
Systems and methods for social networking. Location-related data and other behavioral and exogenously generated characteristics are used to replace or supplement self-generated profiles in order to enhance the quality and trustworthiness of the matches made using the system and facilitate the inputting of profile information.
Owner:VERIZON PATENT & LICENSING INC
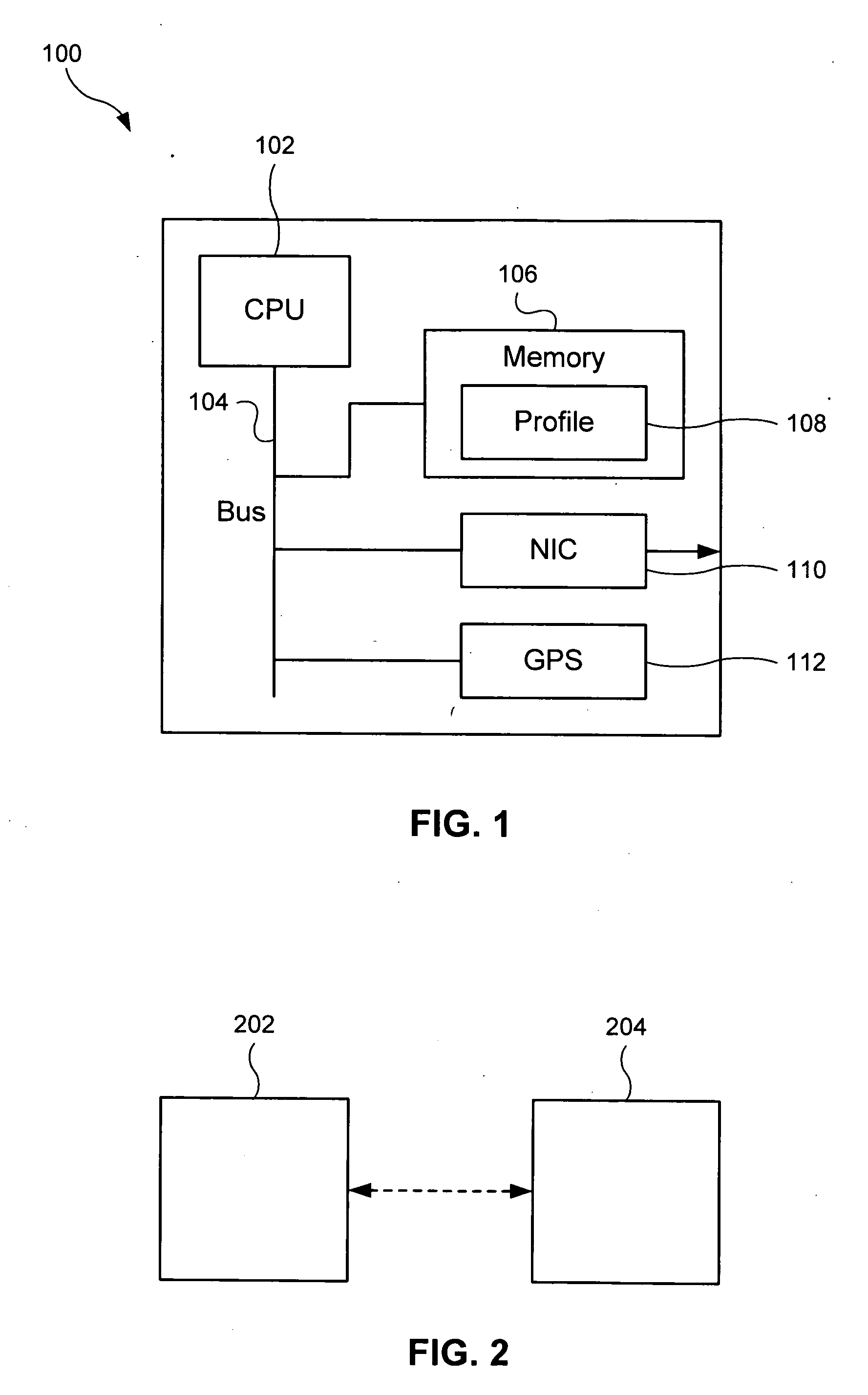
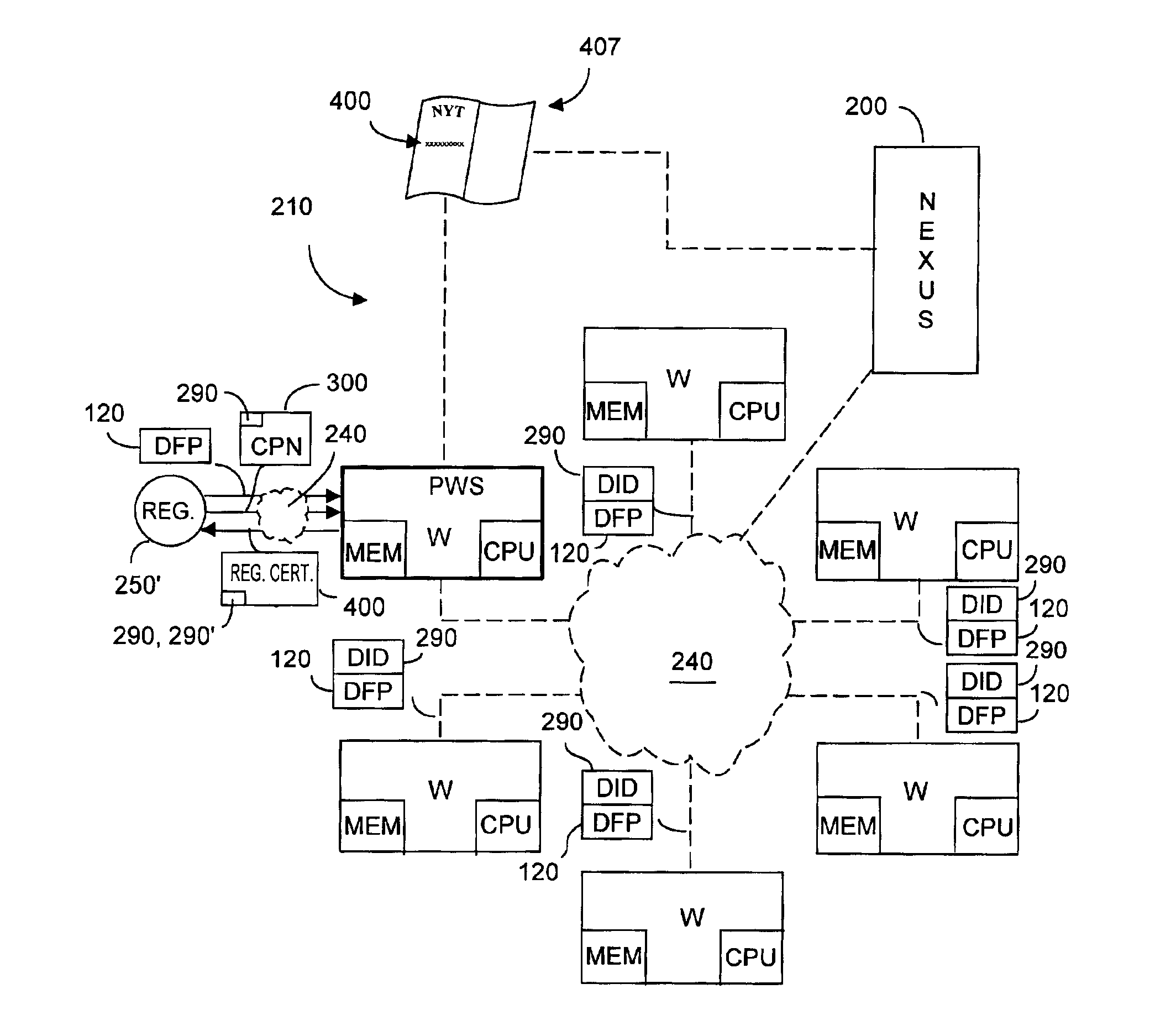
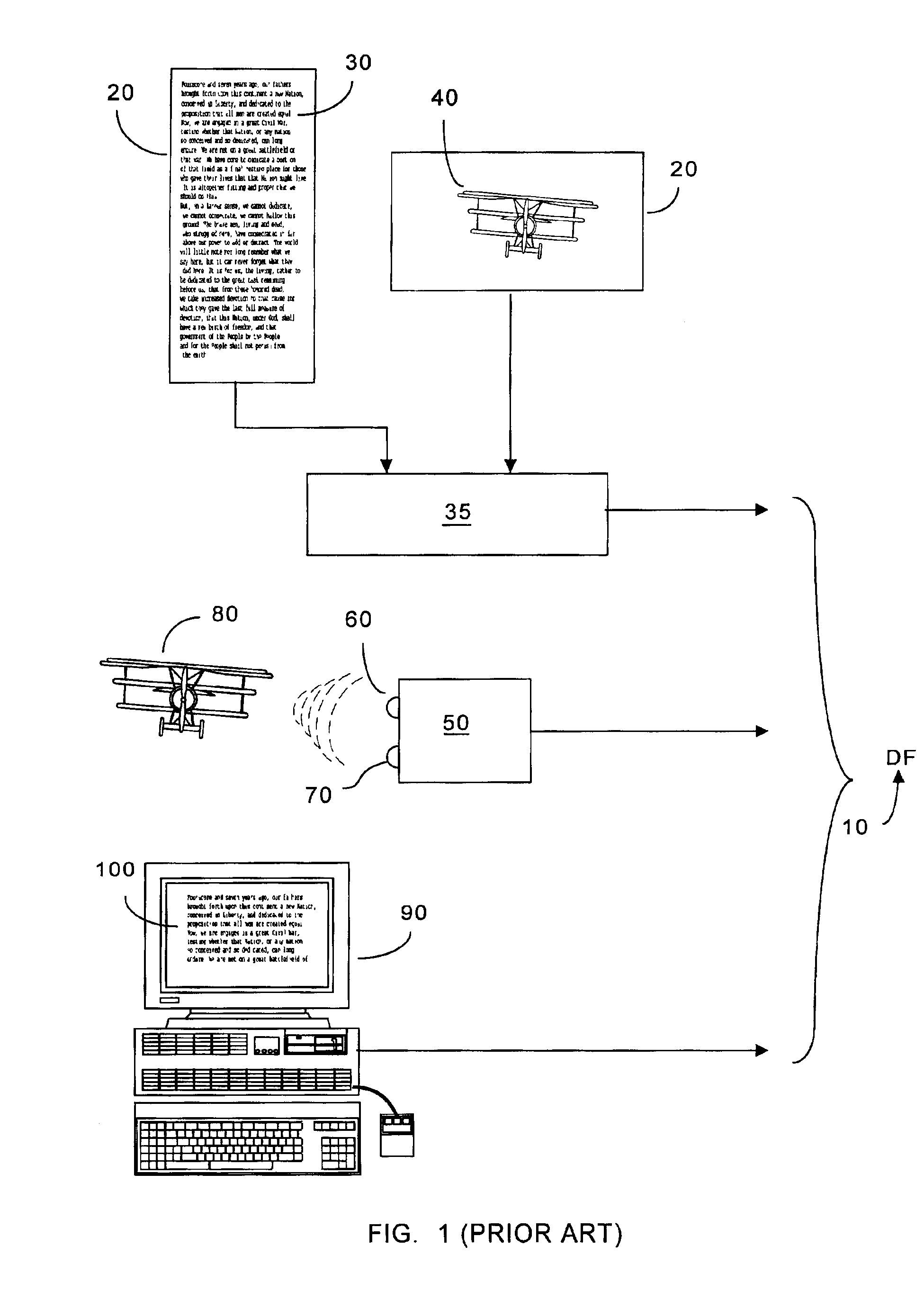
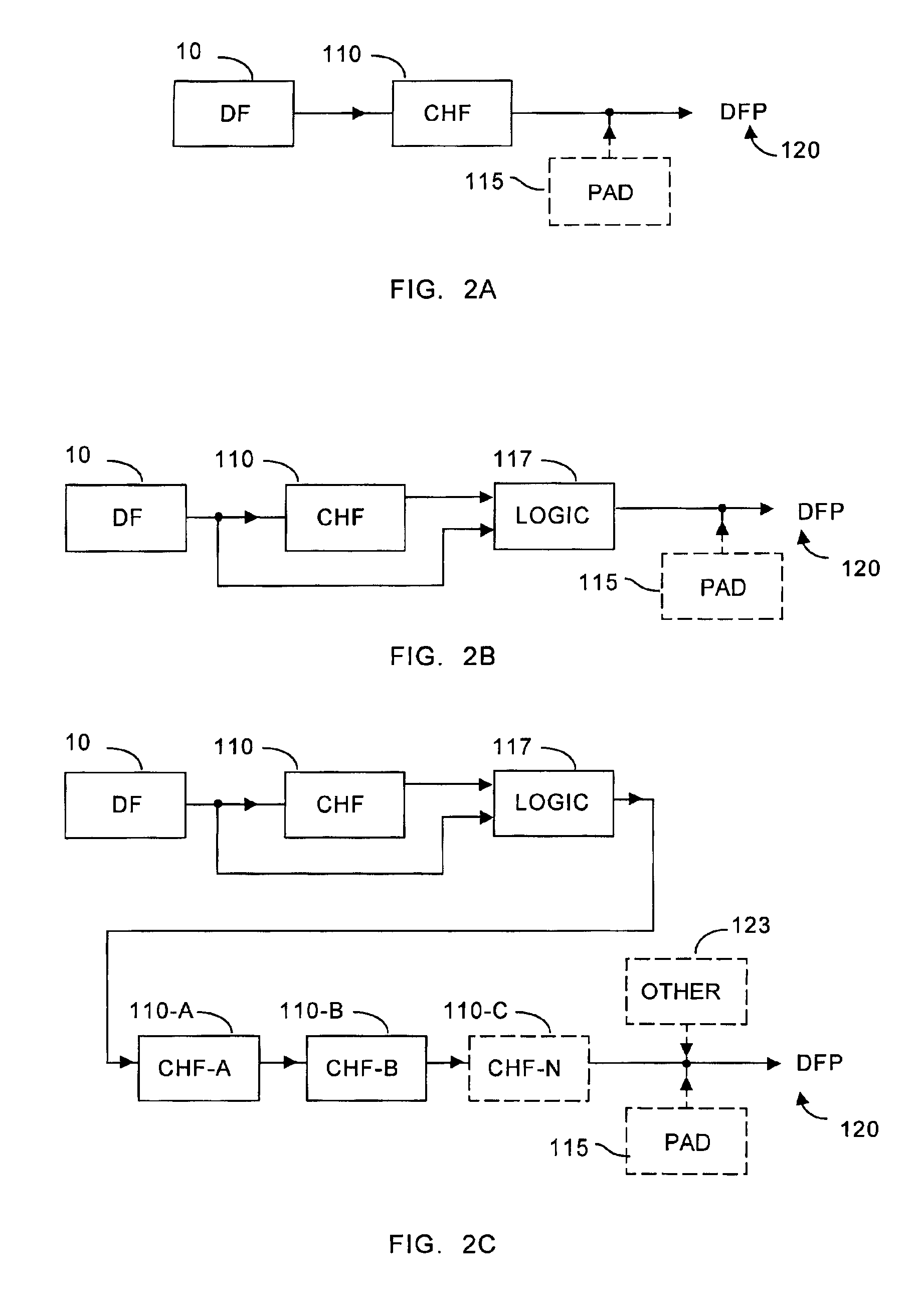
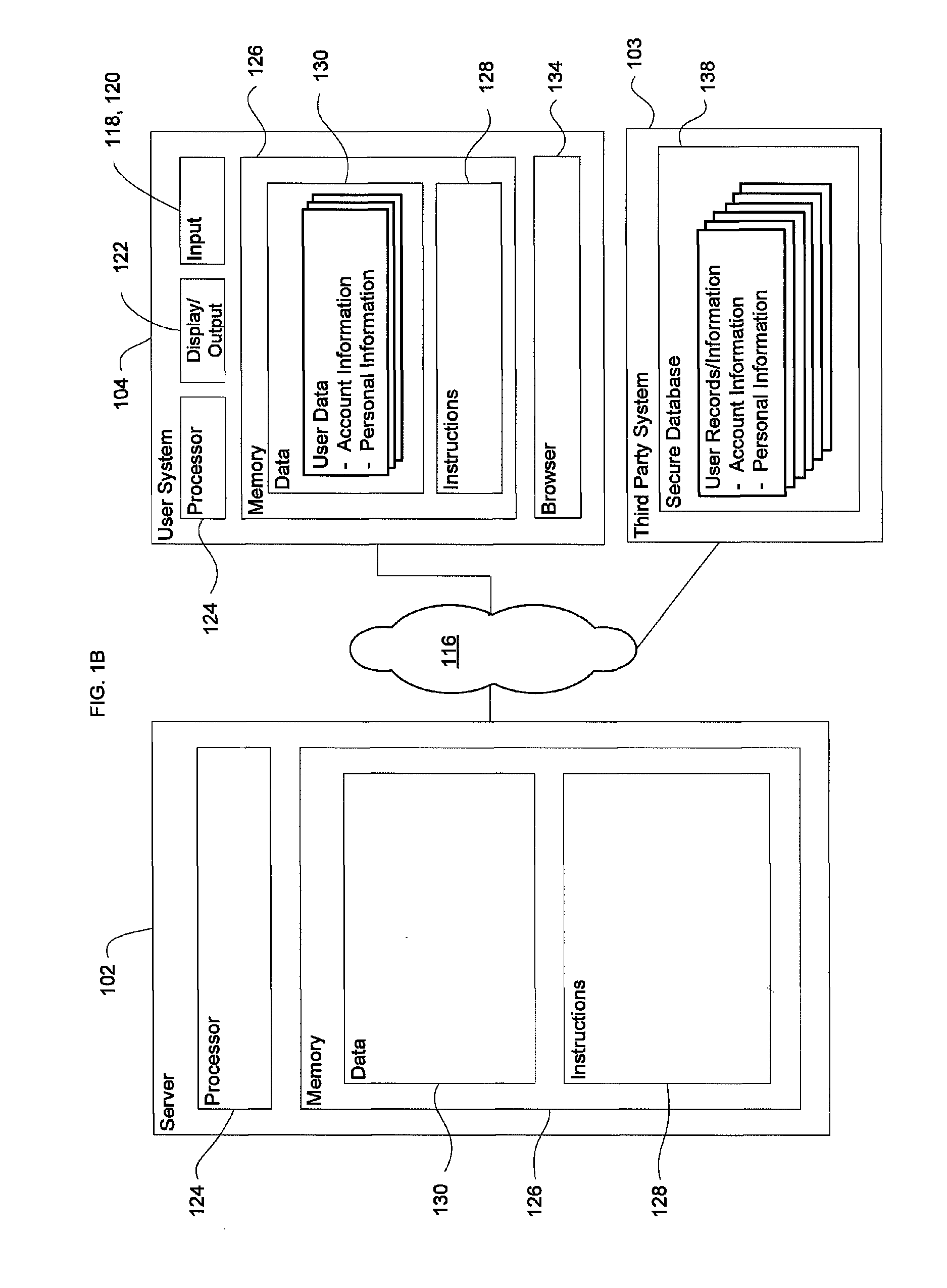
Distributed information system and protocol for affixing electronic signatures and authenticating documents
InactiveUS6938157B2System overhead associated with couponsImprove effectivenessUser identity/authority verificationUnauthorized memory use protectionCryptographic hash functionCryptogram
A system can process a digital representation (DF) of a document with a one-way cryptographic hash function (CHF) to yield a digital fingerprint (DFP) value that is associated with the DF. A document identification number (DID) is created, uniquely associated with the DFP, and with DID and DFP are associated optional credential information (C). A registration certificate DFC that represents an optional electronic signature associated with the document and that includes the DID and DFP is promulgated and archived at a plurality of storage locations. The system can authenticate whether a putative document is the original document by generating a digital fingerprint value for the putative document and comparing it to DFP retrieved from various of the storage locations. Authentication can confirm that the electronic signature is unaltered.
Owner:DISTRIBUTED TRUST MANAGEMENT
Social network for mapping gradations to target intent
ActiveUS20110282750A1Quality improvementImprove trustworthinessDigital data information retrievalAdvertisementsSocial webTrustworthiness
Owner:VERIZON PATENT & LICENSING INC
Social network for location sensing
InactiveUS20110282972A1Quality improvementImprove trustworthinessAdvertisementsTelephonic communicationSocial webData science
Systems and methods for social networking. Location-related data and other behavioral and exogenously generated characteristics are used to replace or supplement self-generated profiles in order to enhance the quality and trustworthiness of the matches made using the system and facilitate the inputting of profile information.
Owner:VERIZON PATENT & LICENSING INC +1
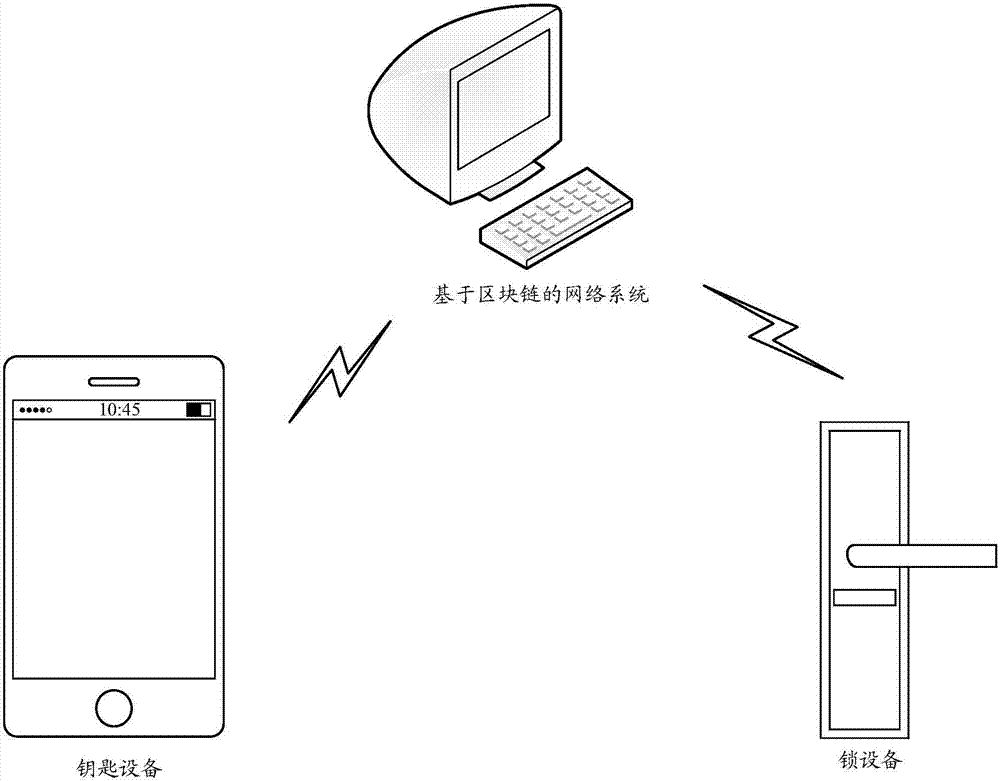
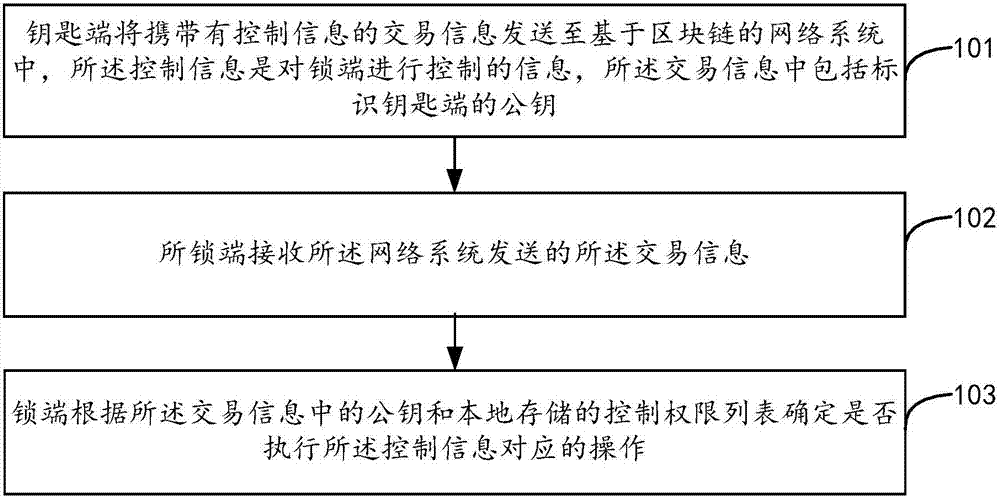
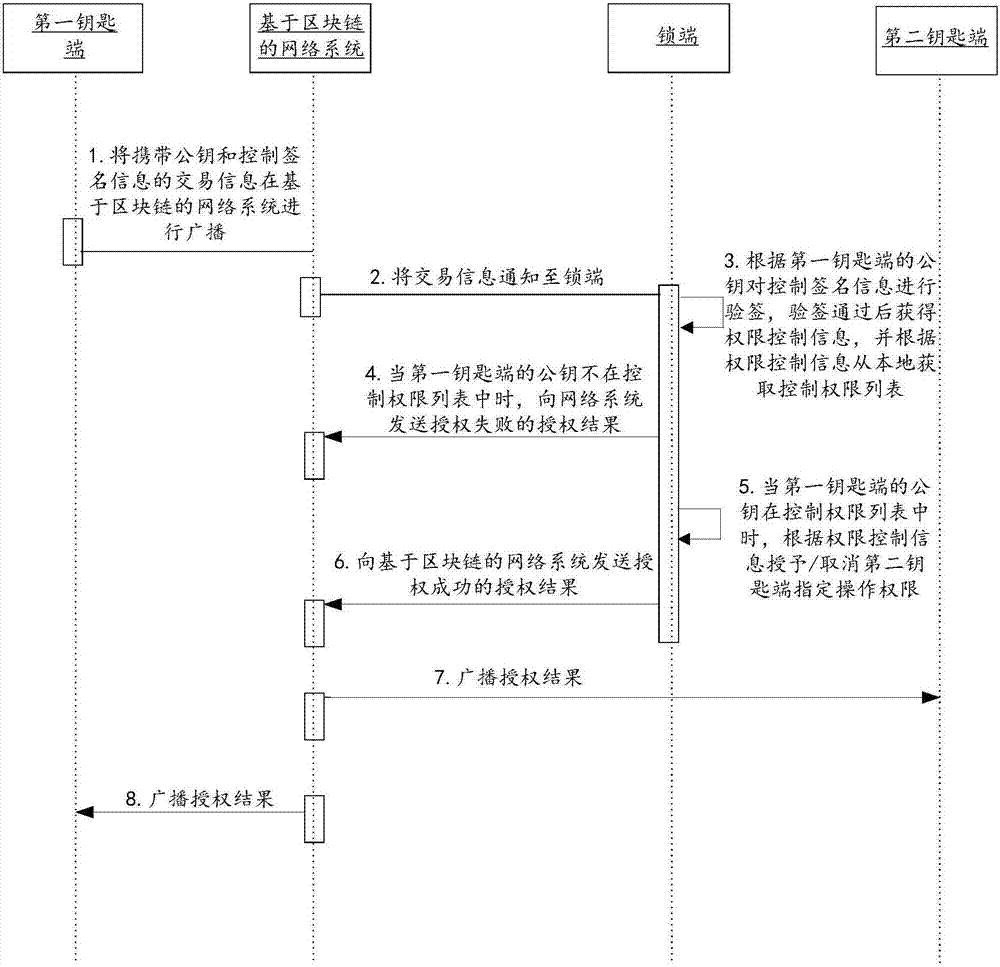
Control method and device for intelligent lock and intelligent lock
ActiveCN106875518AImprove trustworthinessGuaranteed reliabilityDigital data authenticationIndividual entry/exit registersNetworked systemTrustworthiness
The application relates to a control method and a control device for an intelligent lock and the intelligent lock. The method comprises the following steps that a key end sends transaction information carrying control information to a network system based on a block chain, wherein the control information is information for controlling a lock end, and the transaction information includes public key for identifying the key end; the lock end receives the transaction information sent by the network system; the lock end determines whether to execute operation corresponding to the control information or not according to the public key in the transaction information and a locally stored control authority list. Therefore, the trustworthiness of a user for the intelligent lock is improved; moreover, the problem that the maintenance cost of a centered service is high is avoided.
Owner:ADVANCED NEW TECH CO LTD
Privacy preserving name verification
ActiveUS8347093B1Maintain privacyIncrease credibility and trustworthinessUser identity/authority verificationUnauthorized memory use protectionUser privacyUser identifier
Aspects of the invention pertain to preserving the privacy of users in on-line systems while also enabling verification that the users are who they purport to be. Confidential personal information may be communicated from a user to a trusted third party via a web-based application or other service. However, the personal information is encrypted so that the application or service is unable to access it. The trusted third party accesses the personal information and uses it to verify that a user ID such as an email address is associated with a particular user. This information is provided to the web-based application or service to certify the identity of the user. As a result, the application or server verifies to other users that the certified user is who he / she purports to be.
Owner:GOOGLE LLC
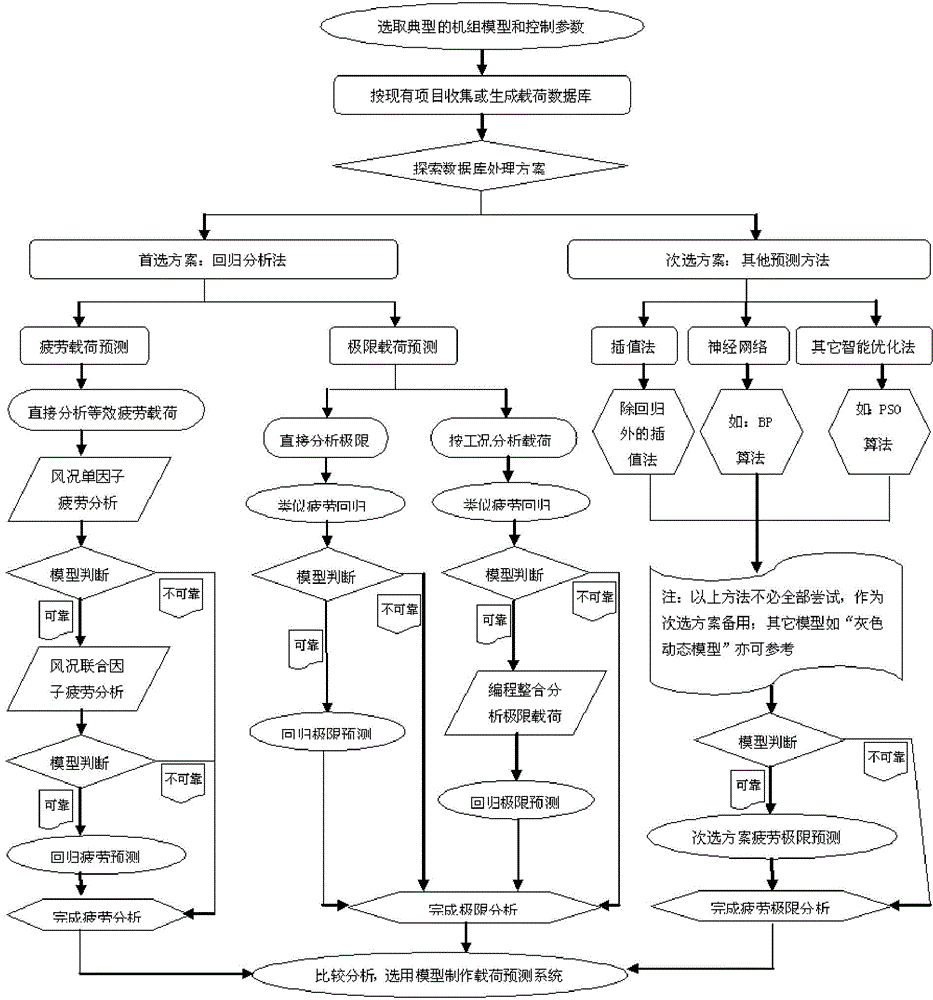
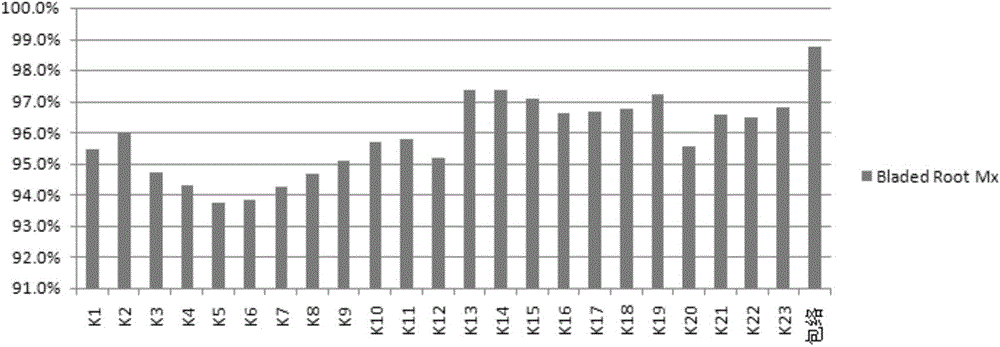
Method for establishing predicated response system based on wind turbine generator load database
ActiveCN104537424AQuick responseSolve the problem of slow response speedForecastingElectricityConsequence analysis
The invention discloses a method for establishing a predicated response system based on a wind turbine generator load database. The method comprises the following steps: (1) establishing a load database; (2) exploring a processing scheme of the load database, wherein the processing scheme comprises a first choice scheme and a secondary choice scheme, and the first choice scheme is a regression analysis method; and (3) analyzing and comparing a processing result of the first choice scheme and the processing result of the secondary choice scheme to establish a proper load prediction response system. The advantages and the disadvantages of the prior art are combined to quickly establish the proper prediction response system, the established prediction response system can solve a problem that a load adaptability analysis or anticipation method is low in response speed on model selection requirements, the quick response of the model selection and the micro-location selection of the wind turbine generator is realized through a quick "wind resource-load-strength-adaptability judgment" response mode of the predicated response system, the load situation of each point location can be quickly predicted to be obtained so as to basically realize the "refinement" of the load adaptability analysis.
Owner:BEIJING TIANYUAN SCI & TECH CREATION WINDPOWER TECH
Modal distance constraint-based multimodal fusion image classification method
ActiveCN108345903AGuaranteed sparsityImprove trustworthinessCharacter and pattern recognitionDiagnostic Radiology ModalityClassification methods
The invention discloses a modal distance constraint-based multimodal fusion image classification method. The method includes the following steps that: first step, the rs-fMRI (resting-state functionalmagnetic resonance imaging) data and DTI (diffusion tensor imaging) data of a plurality of subjects are obtained; second step, a brain function network feature vector and a brain structure network feature vector are constructed for each subject; third step, feature filtering operation is performed on the feature vectors of two modalities based on the Kendall tau correlation coefficient and an overlap mode; fourth step, the relative distance constraint of the feature vectors of two modalities of the same subject before and after mapping is added on the original basis of the K-support norm, andthe objective function of a multimodal feature selection model is constructed, and the optimal feature vectors of two modalities are screened out; and fifth step, a classifier is trained on the basisof a multi-kernel support vector machine model, and the optimal feature vectors of two modalities of the subjects are inputted into the trained classifier, and the category labels of the subjects arepredicted. The classification accuracy of the method of the invention is high.
Owner:THE SECOND XIANGYA HOSPITAL OF CENT SOUTH UNIV
Detecting system for tank bottom leakage optical fiber of atmospheric storage tank
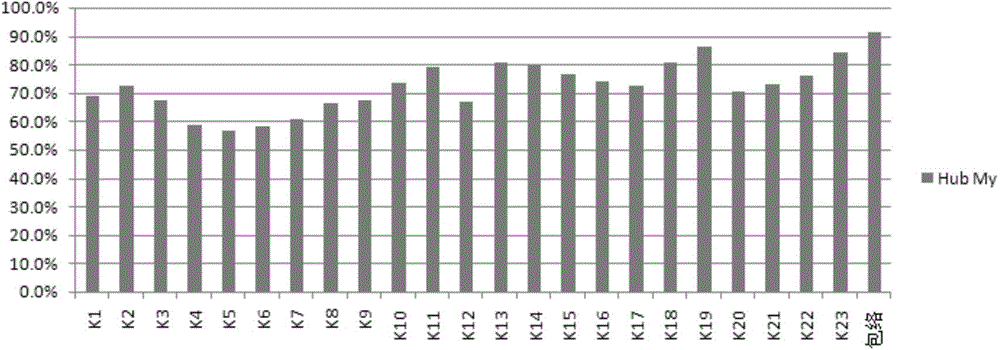
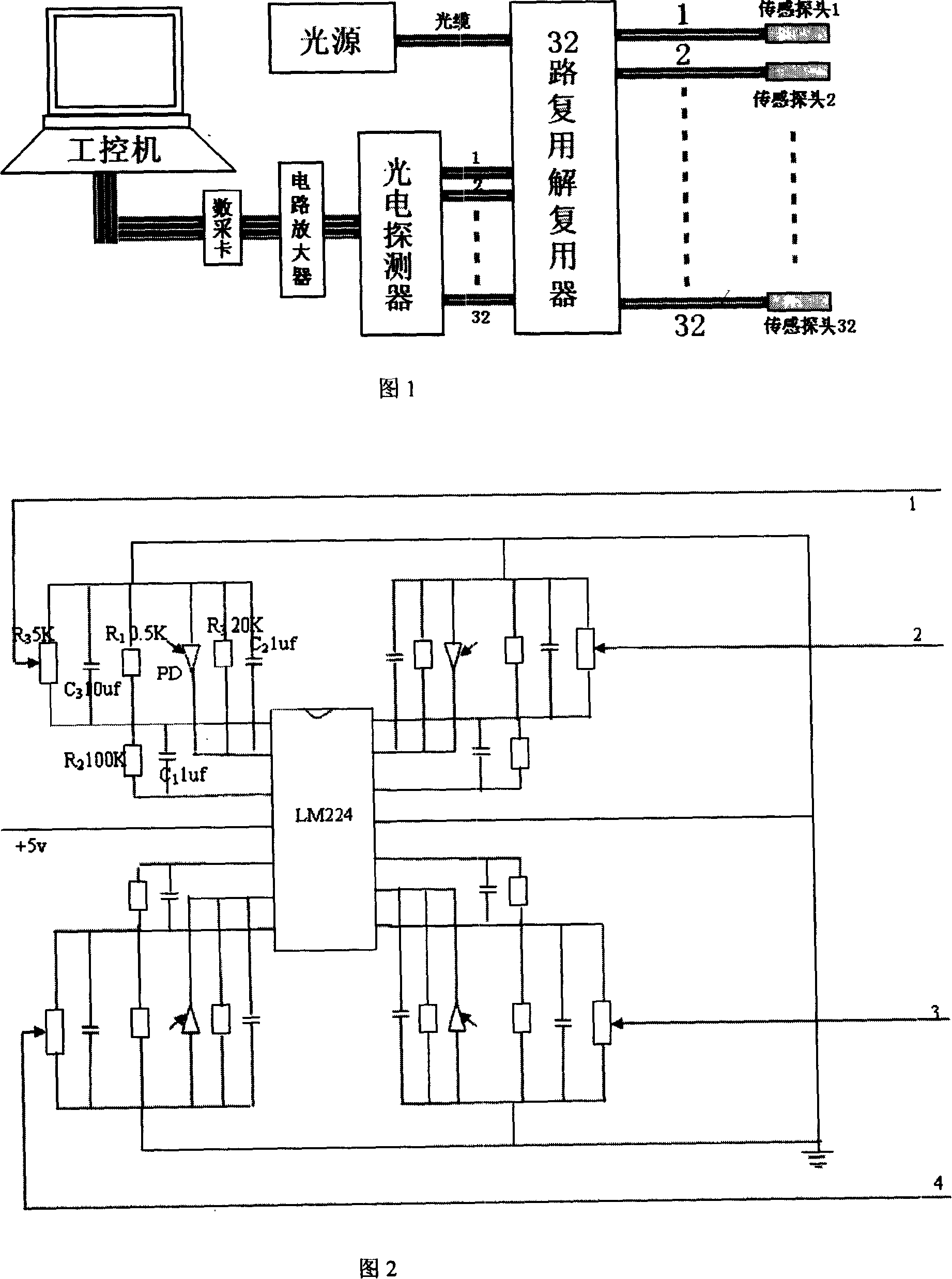
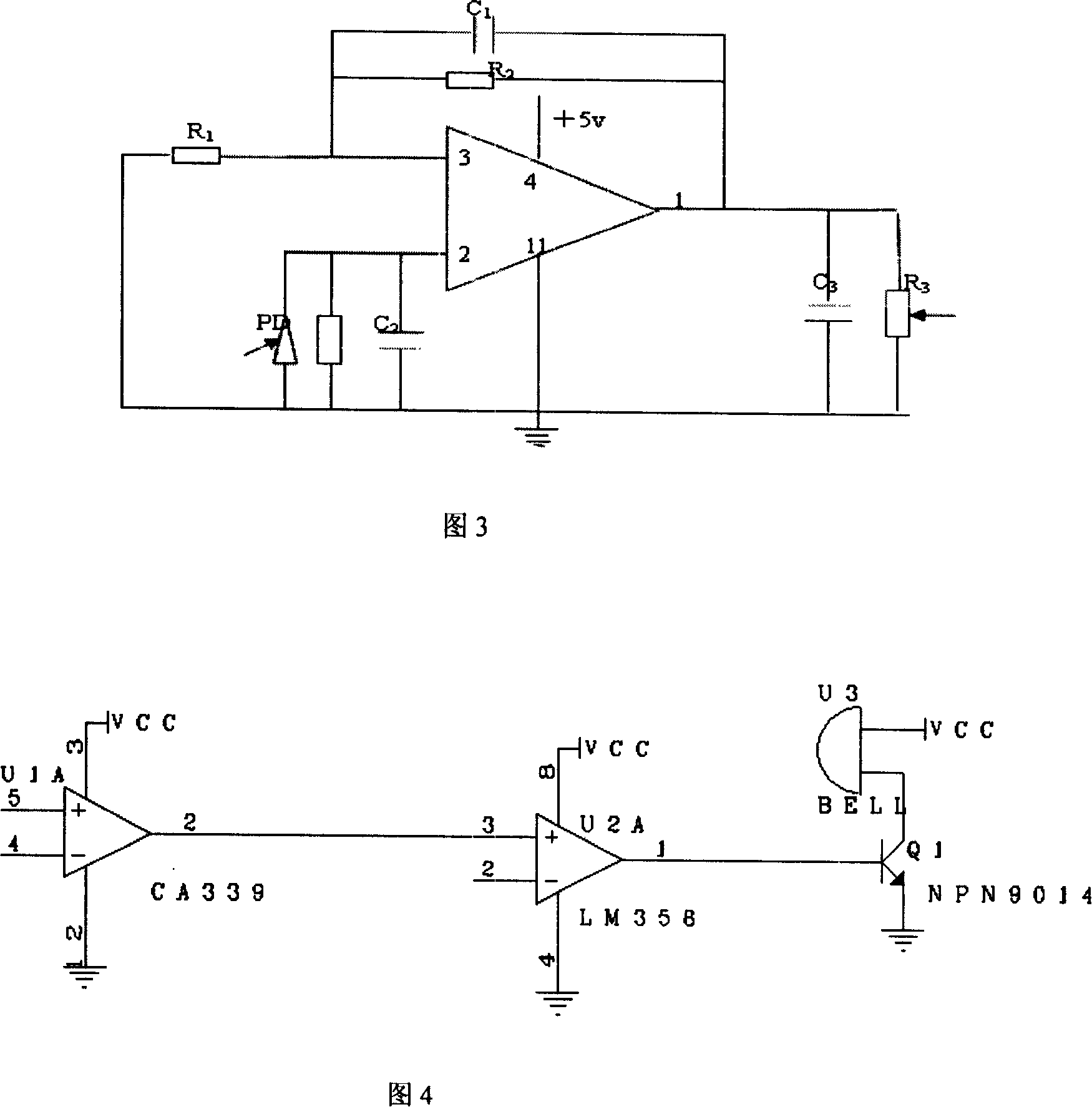
InactiveCN101153827AImmune to electromagnetic interferenceHigh sensitivityLarge containersFluid-tightness measurement using lightLight sourceSensing system
The invention discloses a detection system for optic-fibre leakage at the bottom of a normal atmosphere storage tank, which comprises a plurality of sensing systems. lasers are adopted for the plurality of sensing systems as incoming ray sources which are connected to optical intensity style optical fibre sensing probes via optical fibres and are divided into a plurality of routes via optical-fibre couplers and reach a plurality of sensing probes, reflex detected by the sensing probes enters PIN tubes and are connected with a data collection card via a photoelectric conversion circuit and an amplifying circuit, the data collection card is connected with an industrial computer for data analysis, processing, displaying and recording. The detecting system alarms by software automatically. The system has high precision detection, rapid speed, timely alarm, accurate location, strong anti-interference capability, high safety and convenient system operation, can display where the storage tank leaks and how long the storage tank leaks in real-time by curve mode and digital mode and has aural and visual alarm. Due to the flexible system communication mode, the invention can realize off-site search and monitoring, thereby accelerating processing speed, decreasing economic loss and reducing environment pollutions.
Owner:CHINA PETROLEUM & CHEM CORP
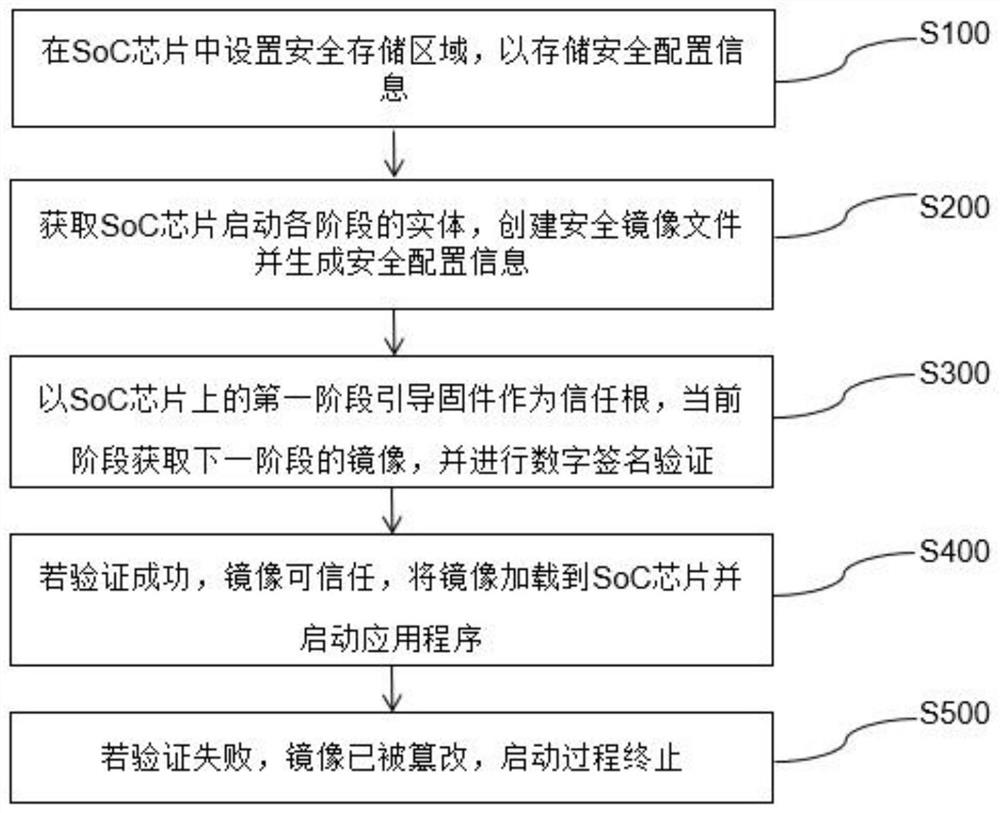
SoC chip security design method and hardware platform
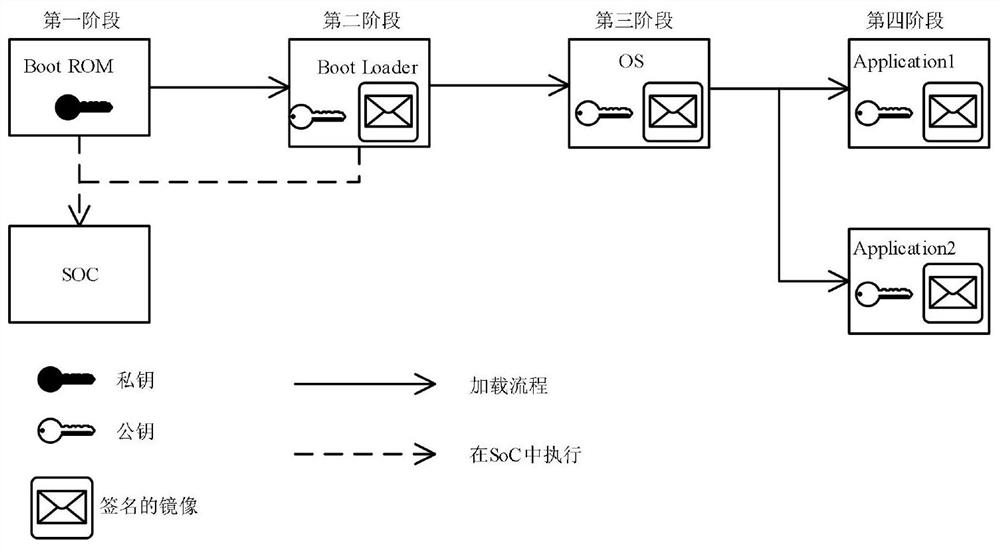
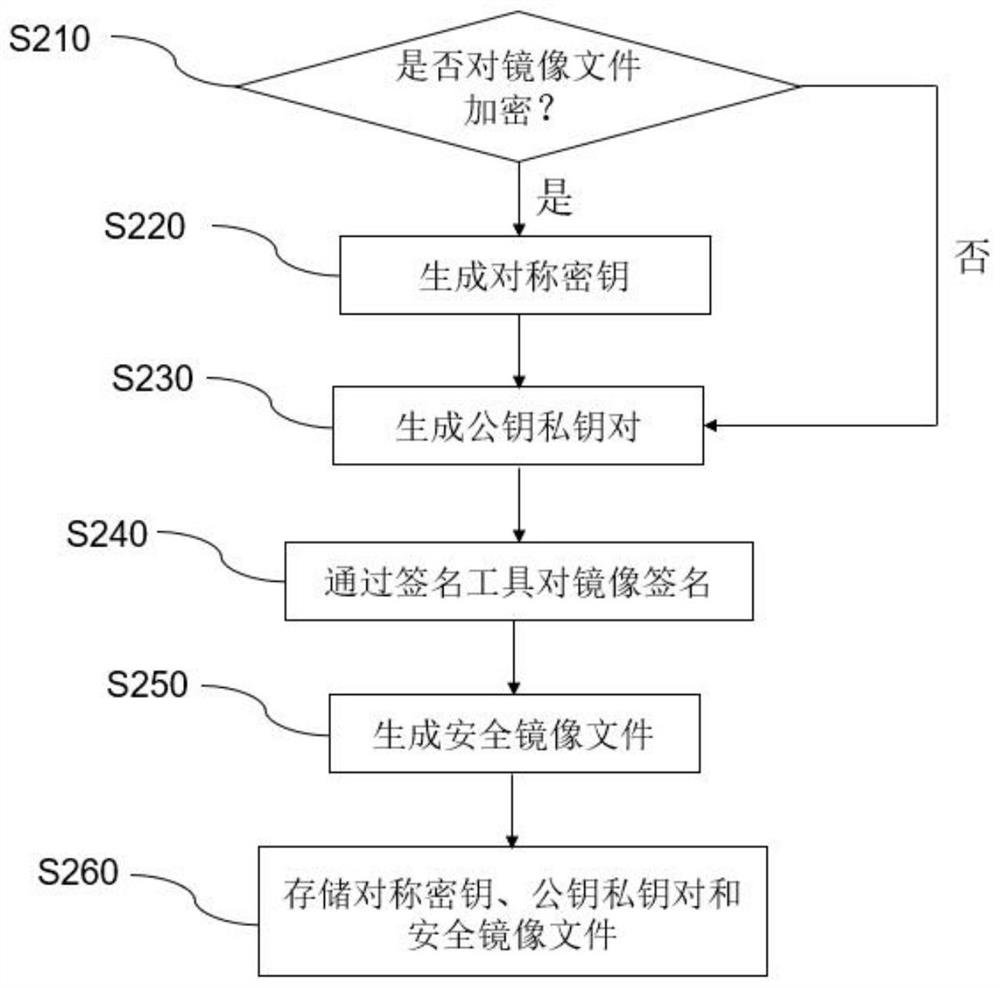
InactiveCN112784280ASave wiring spaceImprove securityInternal/peripheral component protectionPlatform integrity maintainanceOperational systemDigital signature
The invention discloses an SoC chip security design method, and the method comprises the following steps: setting a security storage area in an SoC chip to store security configuration information; obtaining entities of all stages of SoC chip starting, creating a security mirror image file and generating security configuration information; taking first-stage boot firmware on an SoC chip as a root of trust, acquiring a mirror image of a next stage at a current stage, and performing digital signature verification; if verification succeeds, the mirror image is trusted, the mirror image is loaded, and starting is executed; if verification fails, tampering the mirror image, and terminating the starting process. The verification of the bootstrap program, the operating system and the application program is realized by means of encryption and digital signature, the security and credibility of firmware and software are ensured, the key is safely stored, and the security is improved.
Owner:INSPUR SUZHOU INTELLIGENT TECH CO LTD
Memory test system
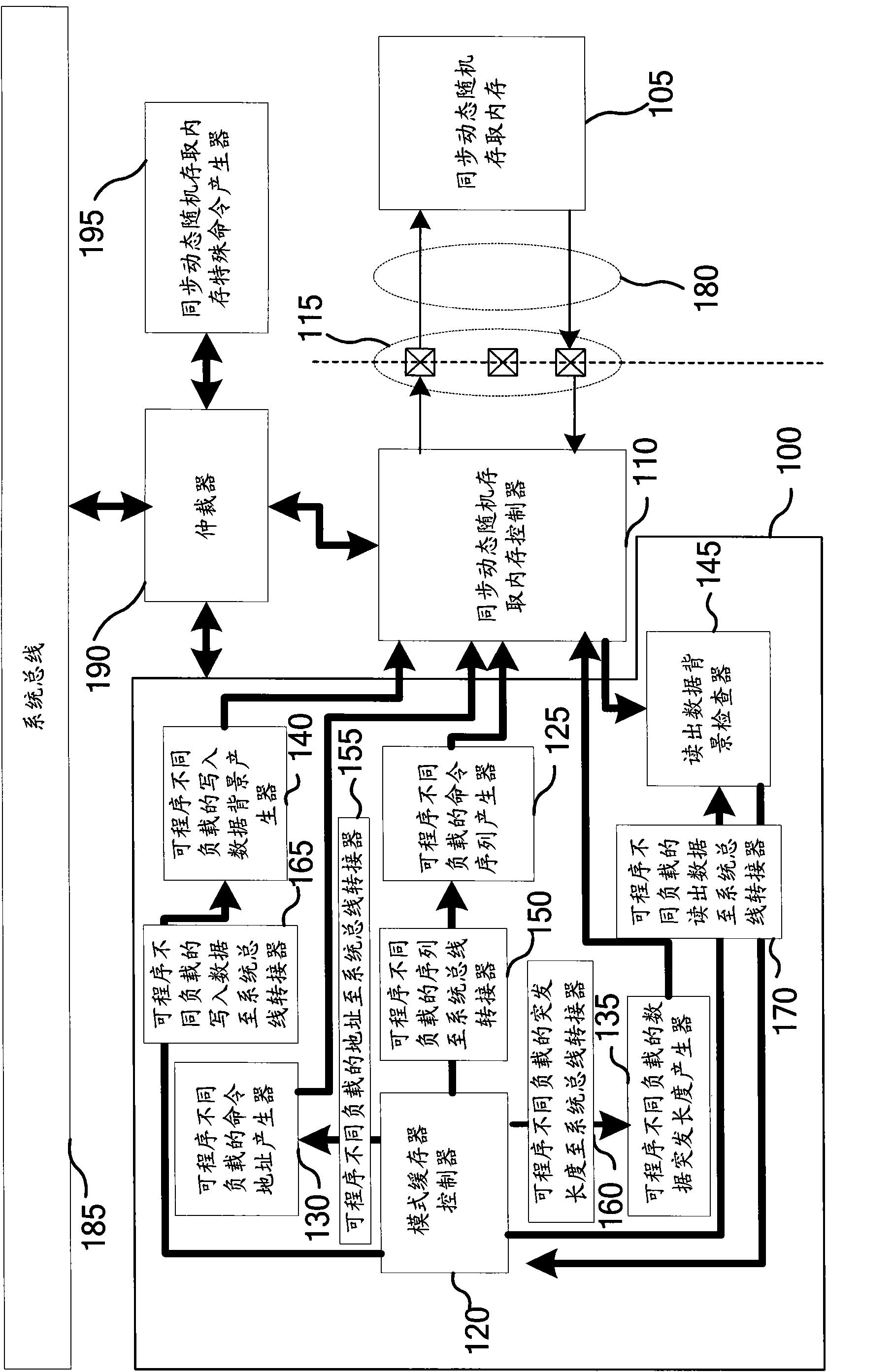
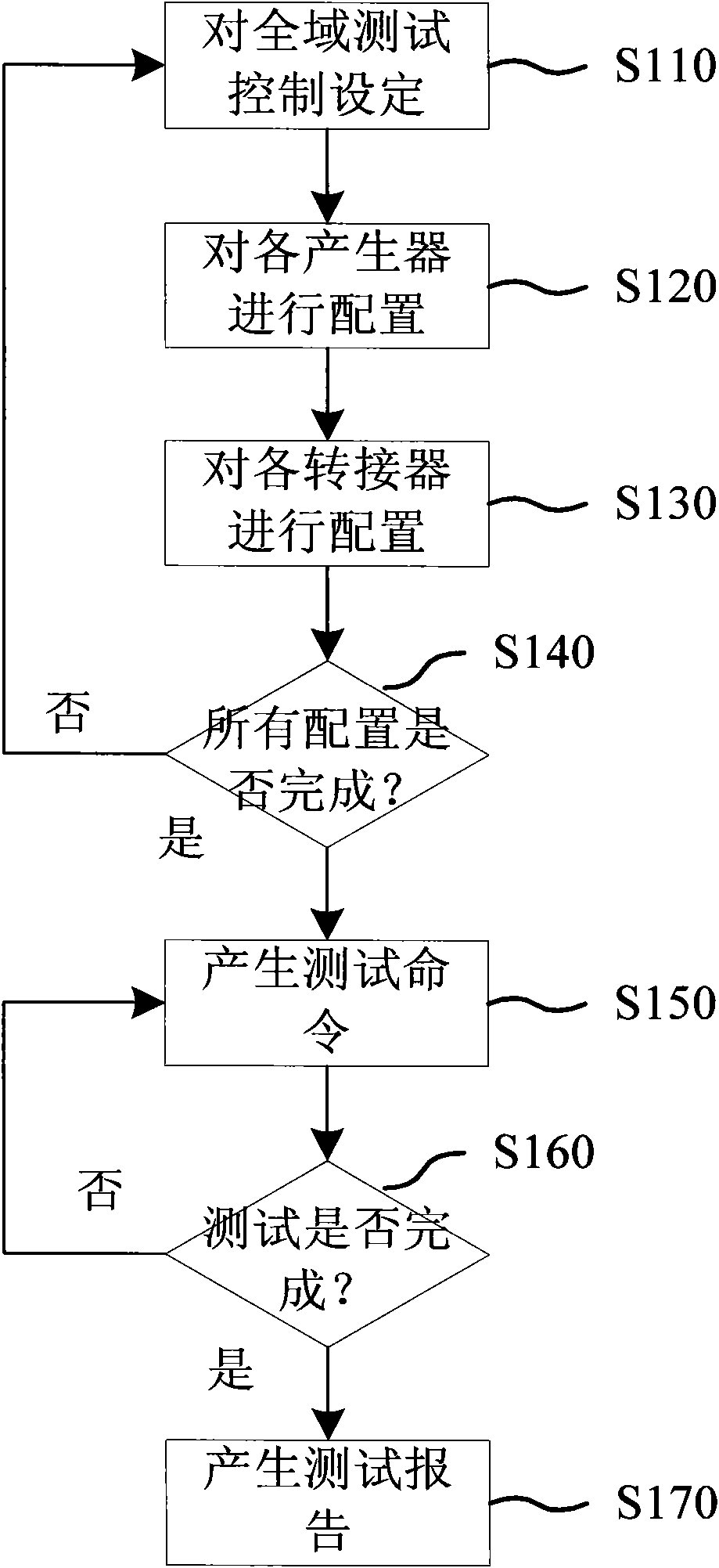
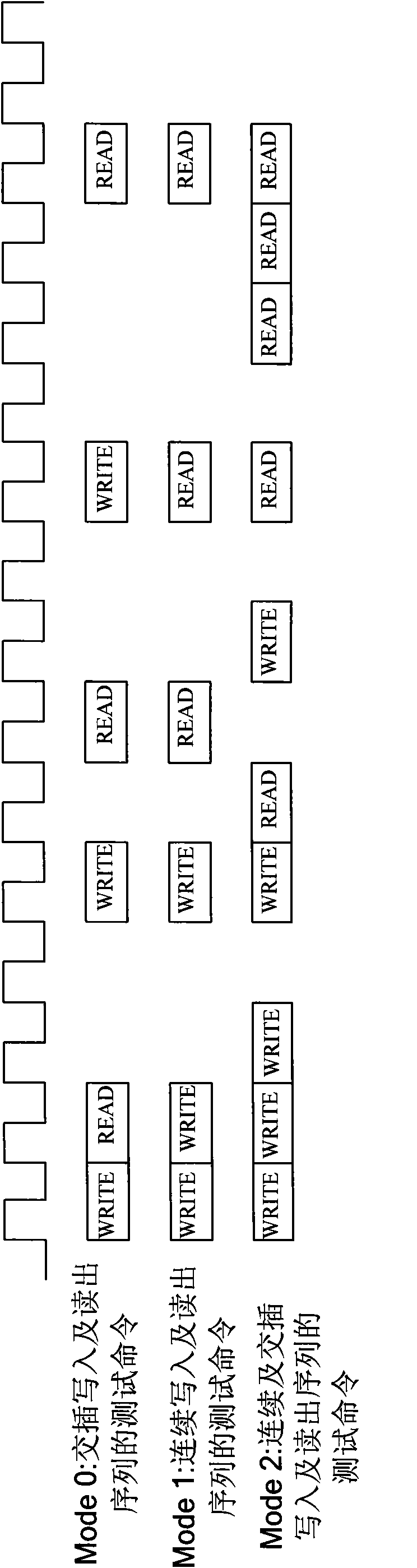
InactiveCN101916593AImprove trustworthinessSolve test problemsStatic storageHigh speed memoryTest sample
The invention provides a memory test system, which can solve a test problem caused by a high-speed memory interface and a synchronous dynamic random access memory (SDRAM). Each hardware mode in the memory test system can be set independently so as to combine into diversity of test samples, which can execute programmable test of difficult loads, practical example test and write-in feedback test. Simultaneously the write-in feedback test of the memory test system can independently test a memory controller, so that the system can test a memory controller which is embedded into an integrated circuit without communicating with an entity SDRAM. In addition, in a validation stage of the integrated circuit, the technology of the invention can be used for analyzing and distinguishing whether a problem point is in or out of the integrated circuit, and testing a write-in command and a read-out command.
Owner:SUNPLUS TECH CO LTD
Block-chain-technology-based encrypted payment storage system and method
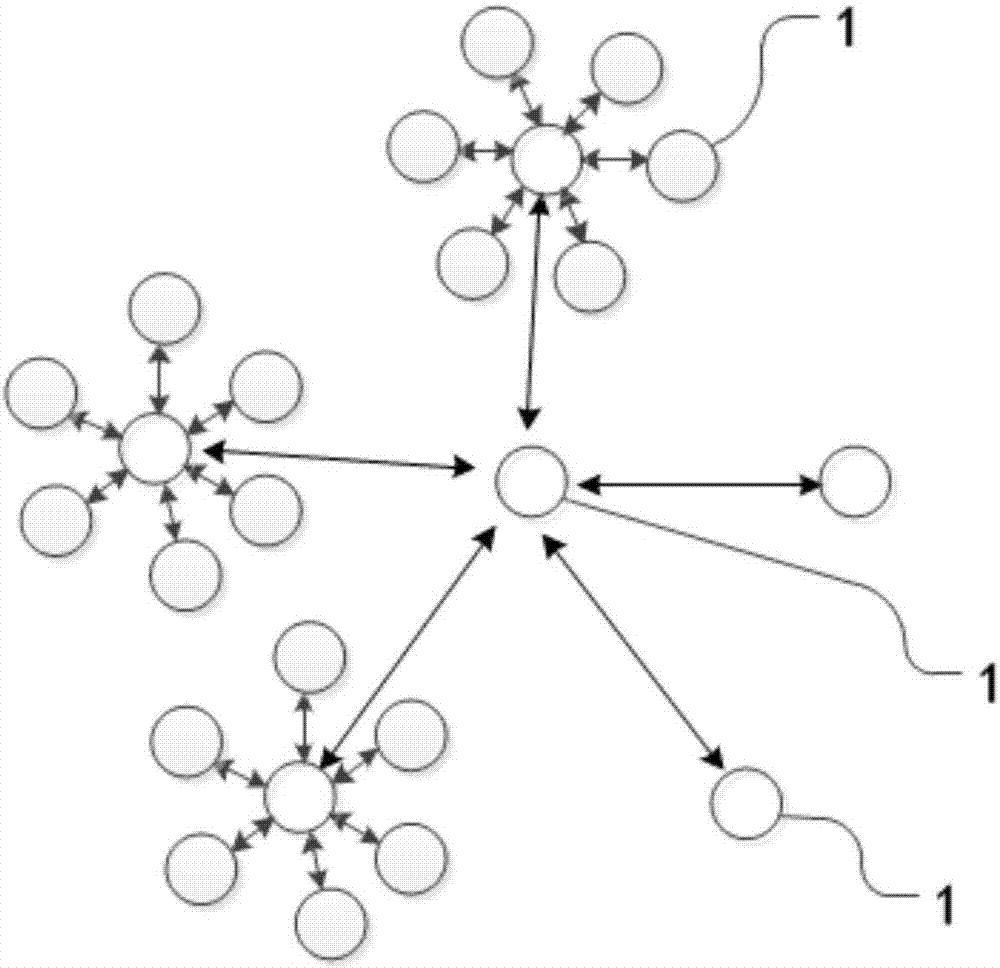
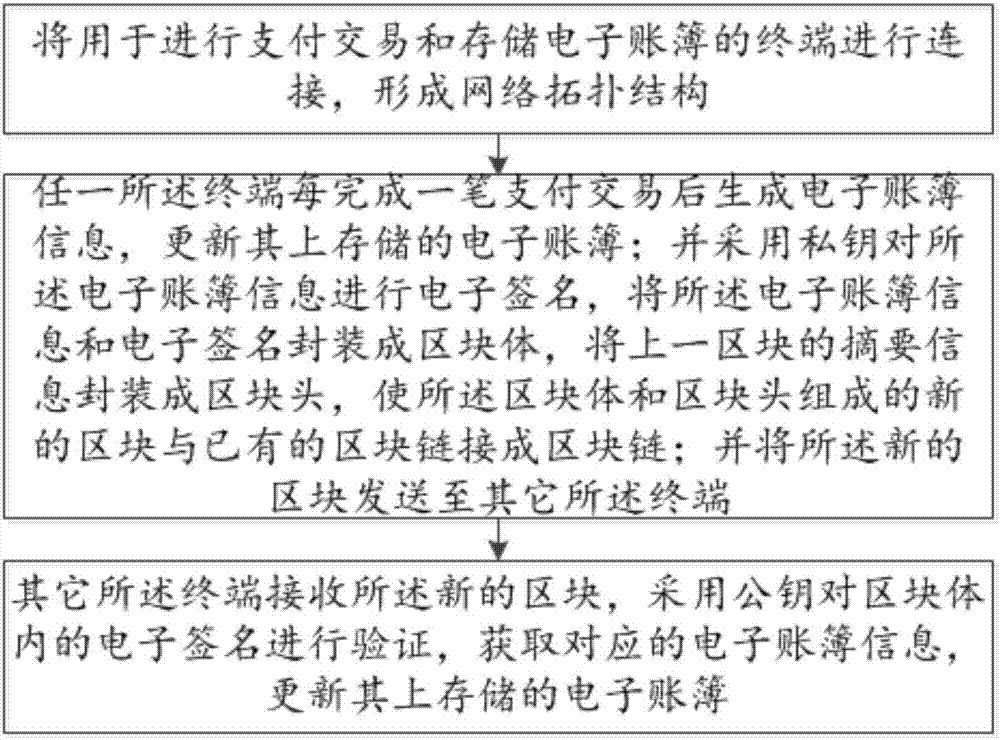
InactiveCN106910066AAchieve decentralizationImprove trustworthinessUser identity/authority verificationPayment protocolsPayment transactionInformation transparency
The invention relates to a block-chain-technology-based encrypted payment storage system and method. Terminals for payment transaction and electronic book storage are connected to form a network topology structure; any of the terminals generates electronic book information after payment transaction completion each time and updates the stored electronic book; Encrypting the electronic book information by using a private key, encapsulating the electronic book information and the electronic signature into a block, and electronic signature processing is carried out on the electronic book information by using private keys, the electronic book information and electronic signatures are packaged into block bodies, abstract information of the last blocks are packaged into block heads, and new blocks formed by the block bodies and the block heads and the existing blocks are linked to form a block chain; the new blocks are sent to the other terminals; the other terminals receive the new blocks, verify the electronic signatures in the block bodies by using a public key, obtain the corresponding electronic book information, and update the stored electronic books. Therefore, decentration and distributed sharing of electronic books are realized; the information transparency is high; and trustworthiness of electronic payment is enhanced.
Owner:WUHAN HUITONGYUN INFORMATION TECH CO LTD
Internet of Things access control method and system
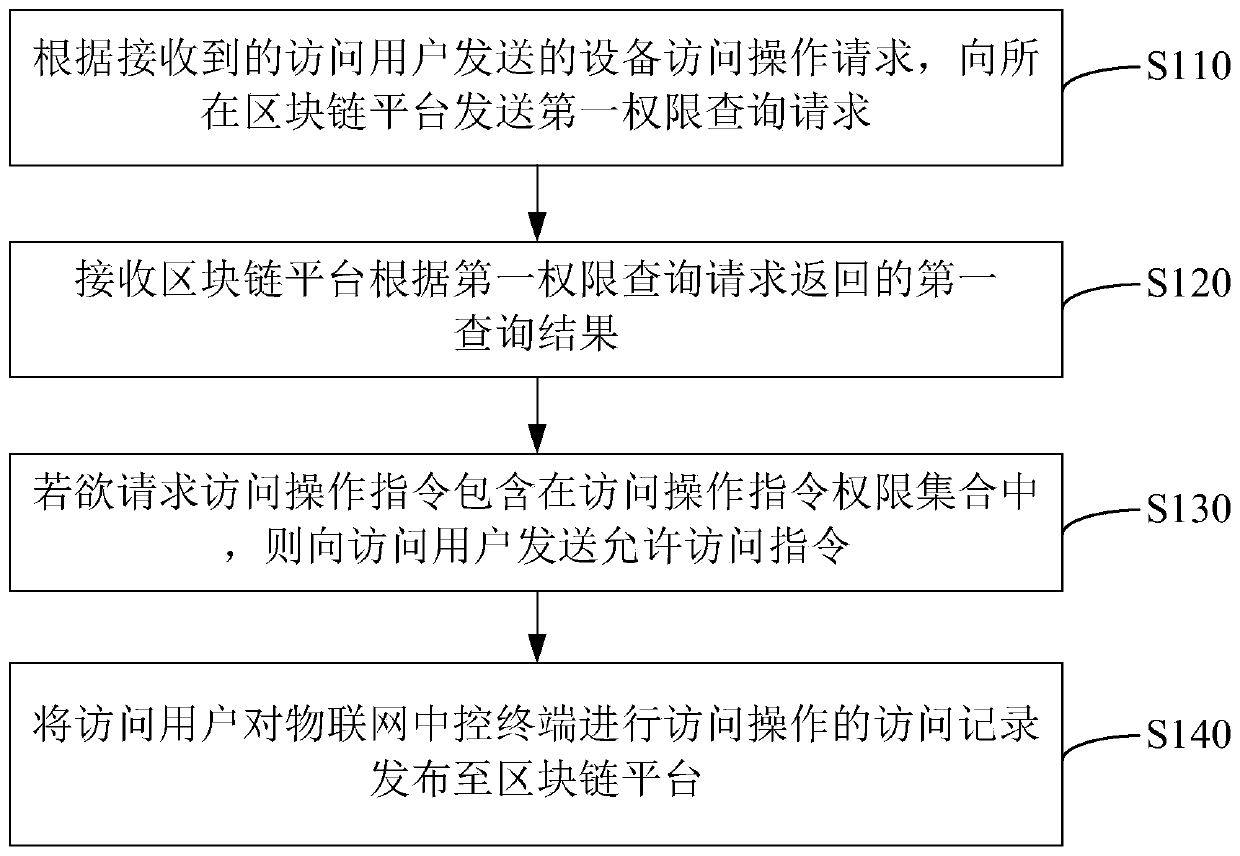
ActiveCN110535880AImprove securityImprove trustworthinessSecuring communicationThe InternetComputer terminal
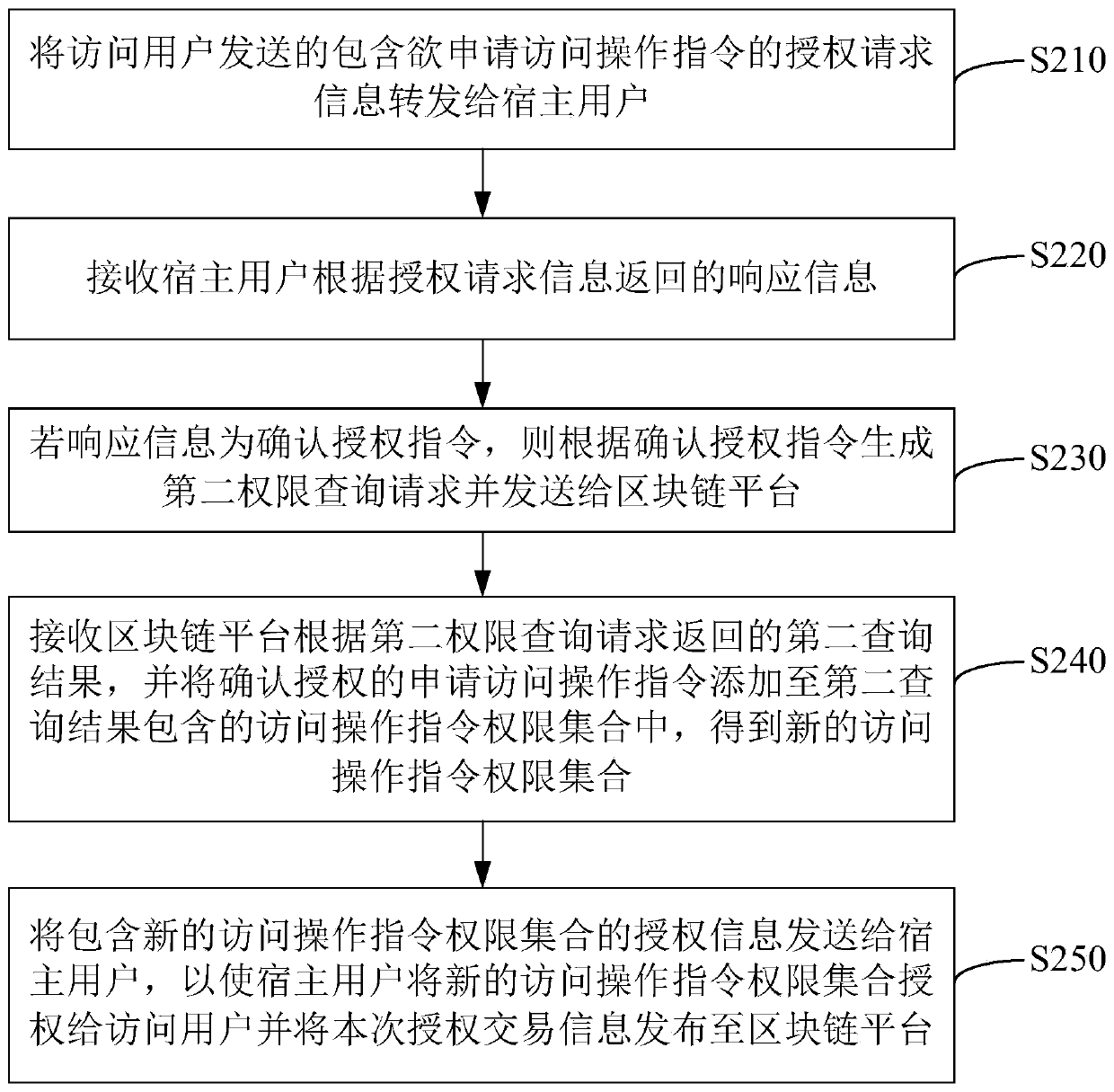
The embodiment of the invention discloses an Internet of Things access control method and system, which are applied to a central control terminal of the Internet of Things. The method comprise the following steps: sending a first authority query request to a block chain platform according to a received device access operation request sent by an access user; wherein the equipment access operation request comprises an access operation request instruction; receiving a first query result returned by the blockchain platform according to the first permission query request; wherein the first query result comprises an access operation instruction permission set of the access user to the Internet of Things central control terminal; if the access operation instruction to be requested is included inthe access operation instruction permission set, sending an access permission instruction to the access user; and publishing the access record of the access operation of the access user on the centralcontrol terminal of the Internet of Things to the blockchain platform. According to the invention, privacy leakage of the user is further prevented, and normal use of each intelligent device in the Internet of Things is ensured.
Owner:SICHUAN NORMAL UNIVERSITY
Bank bill obstacle-free payment platform
InactiveCN101127106AImprove trustworthinessImprove convenienceFinancePayment architecturePaymentOperational costs
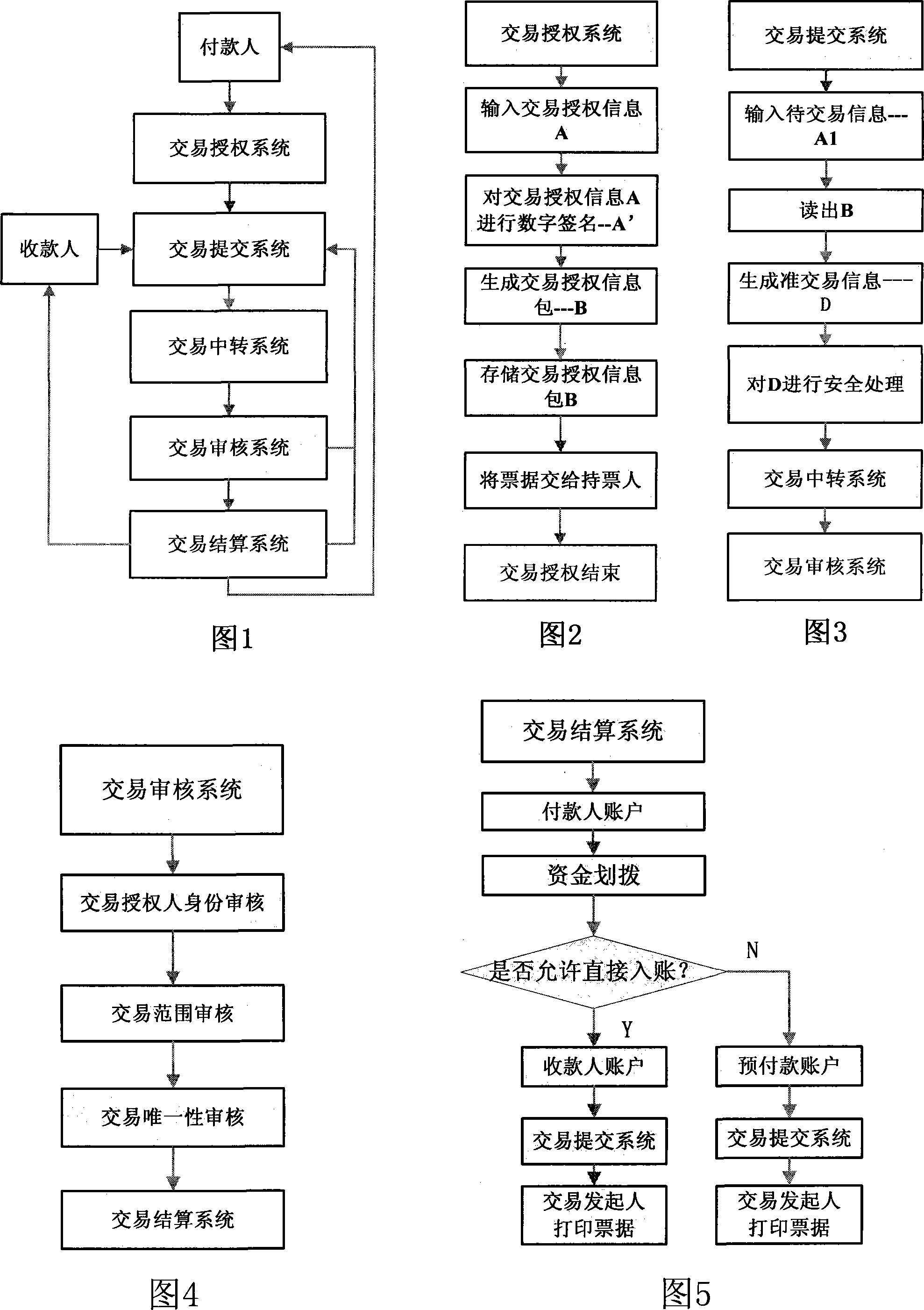
The utility model provides an obstacle-free payment platform for bank bills; at first, payers carry out digital authorization about trade content in the trade authorizing system and confirms by private key signature; then the trade contents and authorized information are stored digitally by means of two-dimensional bar code technology; buyers and sellers return the digital paper bank bills to the Internet through trade submission system and trade transfer system; after passing safety verification of a trade auditing system, buyers and sellers can fulfill safe and real-time trade through a final trade balance system and a trade entering-account system and realize obstacle-free payment of paper bank bills. The utility model has the advantages of realizing safe and obstacle-free payment of paper bank bills by use of the Internet, guaranteeing the safety of trade, avoiding trade risk of financial enterprises in an unprecedented manner, reducing operation cost of financial enterprises and establishing an obstacle-free payment platform for paper bank bills for customers nationwide or even worldwide.
Owner:王忠杰
Communication method and system for realizing two-dimension code-based labeling on electronic map
InactiveCN104598576AIncrease contentAvoid retrievingSpecial data processing applicationsElectronic mapInstant messaging
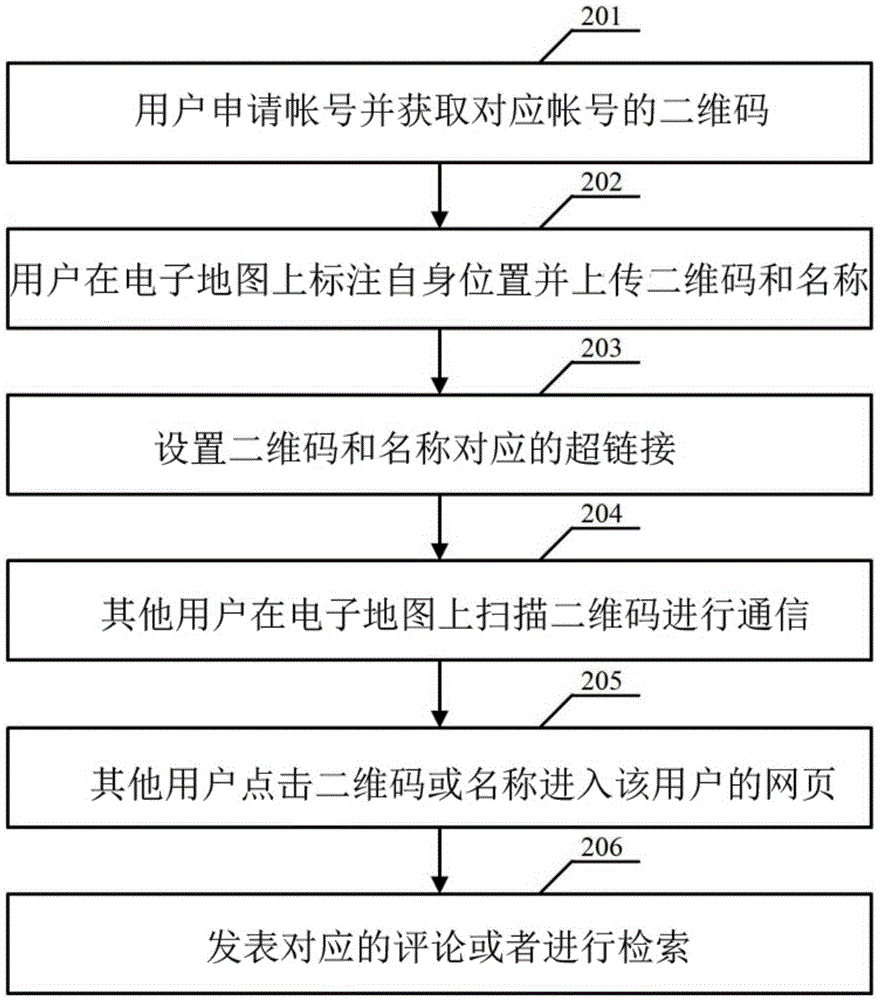
The invention provides a communication method for realizing two-dimension code-based labeling on an electronic map. A service provider provides an account number application service and an associated two-dimension code downloading service for a user, after the user successfully applies, the user labels the own position by using a two-dimension code on the electronic map, and other users can scan the two-dimension code to communicate with the user. According to the communication method and system, a merchant can label by itself, the contents of the electronic map are richened, the effect that circumjacent information can be retrieved on the electronic map is effectively realized, instant messaging is carried out by means of the two-dimension code which is labeled on the electronic map, the users can conveniently communicate, the information of the other party which is needed to communicate can be easily checked, the credibility is increased, and time is prevented from being wasted.
Owner:李宝玉
Anti-counterfeiting traceability information processing method and system based on block chain
PendingCN111445273AImprove trustworthinessFast and efficient development of cloud service collectionsPayment protocolsTransmissionInformation processingPurchasing
The invention provides an anti-counterfeiting traceability information processing method and system based on a block chain. A block chain node of a client is provided for each process of commodity circulation so as to realize anti-counterfeiting traceability; each client uses an independent program; when the block chain node of one client is entered with data through an asymmetric encryption algorithm and forms a block upper chain; the data is sent to the block chain nodes of all clients in the block chain, wherein the block chain nodes comprise a commodity production block chain node, a two-dimensional code setting block chain node, a warehouse-in storage block chain node, a warehouse-out area block chain node, a logistics distribution block chain node, a seller signing block chain node,a commodity placement block chain node, a consumer purchasing block chain node and a two-dimensional code scanning block chain node; and more efficient and reliable anti-counterfeiting and traceability can be realized for commodity circulation.
Owner:重庆新致金服信息技术有限公司
Improved method for integrating touch screen closely
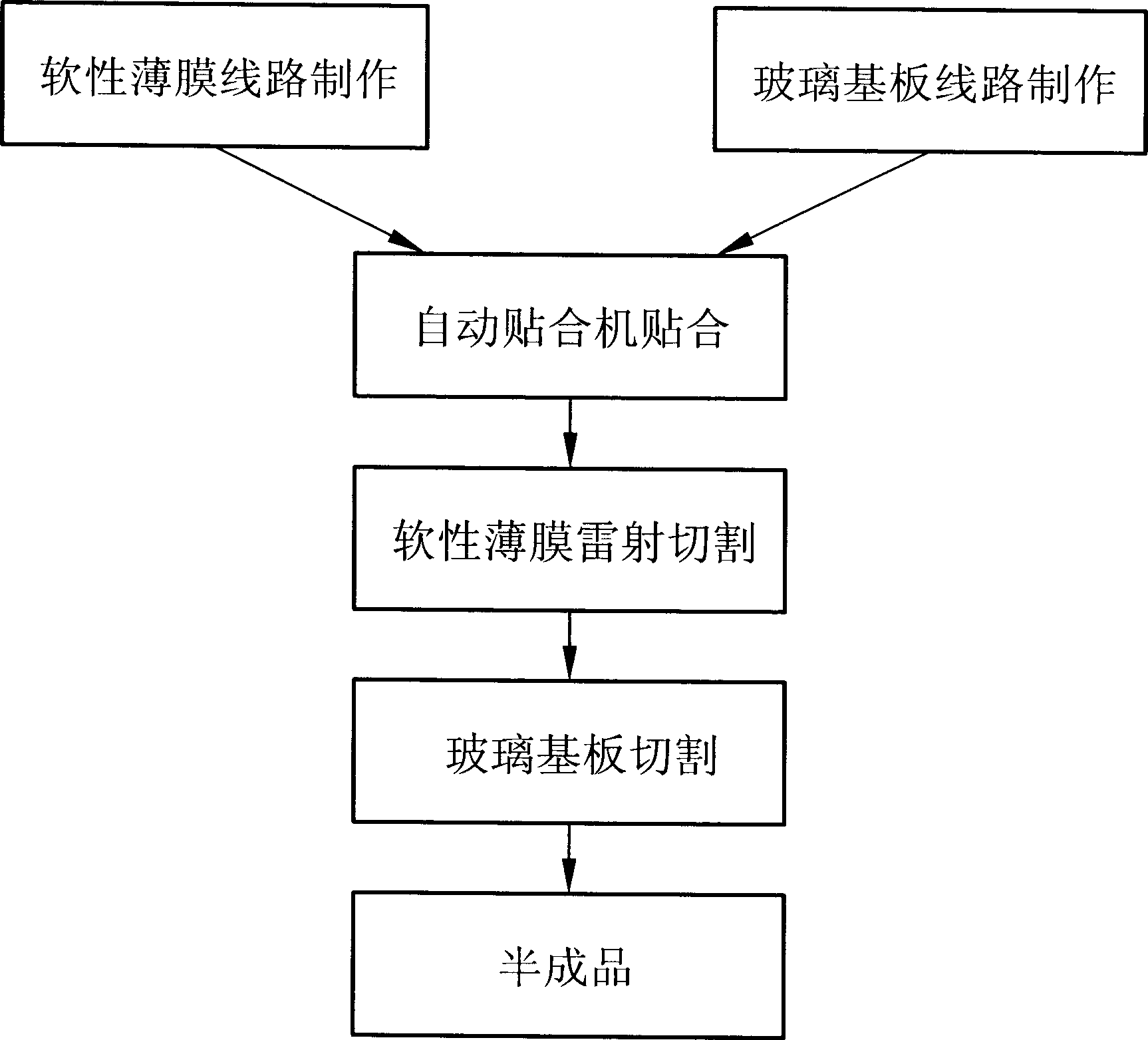
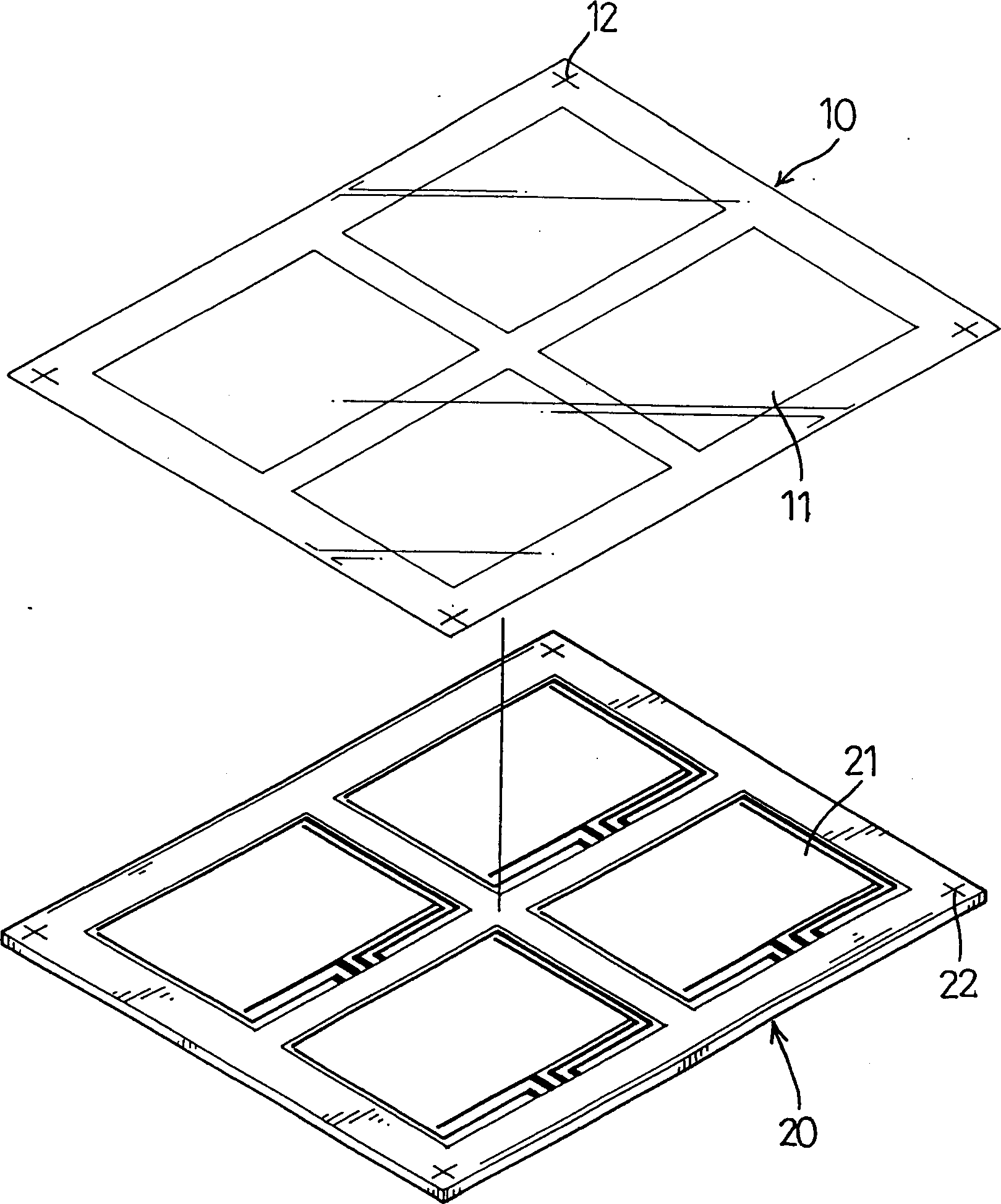
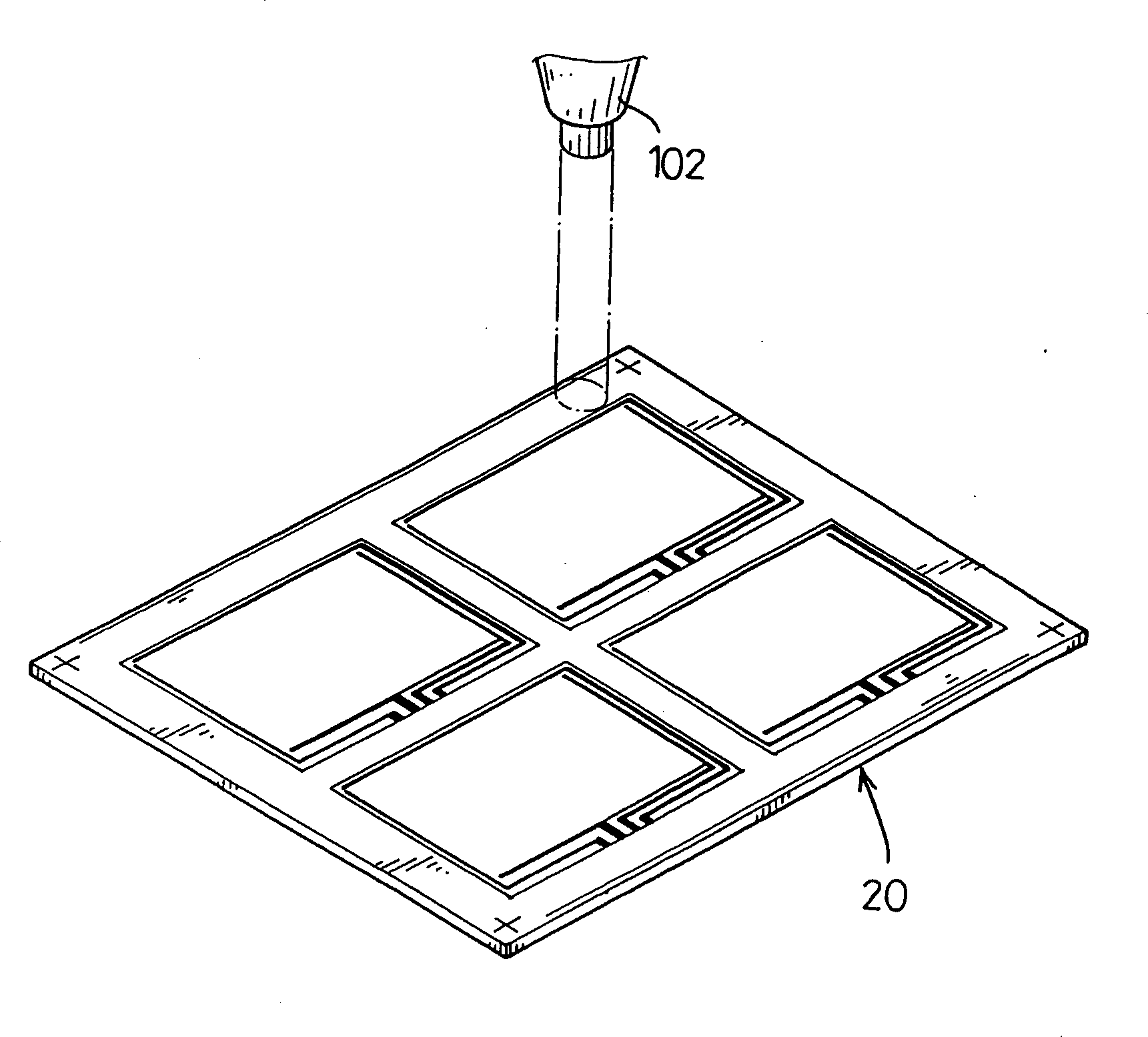
InactiveCN1431578AImprove fitting methodFast fittingLayered productsDigital output to display deviceIndiumIndium tin oxide
On the soft thin film and glass base plate, which constitute the touch screen layer, with the corresponding circuit diagrams being arranged in desired positions, the preparation for etching circuits are producing the tin indium oxide conducting layer are carried out. The location points are set up the four corners on the soft thin film and glass plate. The film is integrated to the glass plate closely by using the automatic lining machine. The laser cutter removes the unused soft thin film on the circumference of the circuit pattern. Then, the glass plate cutter cuts the glass plate to desired pieces. The invention increases the qualification rate and the production efficiency.
Owner:苏州瑞阳光电有限公司
Structure for assembling faceplate
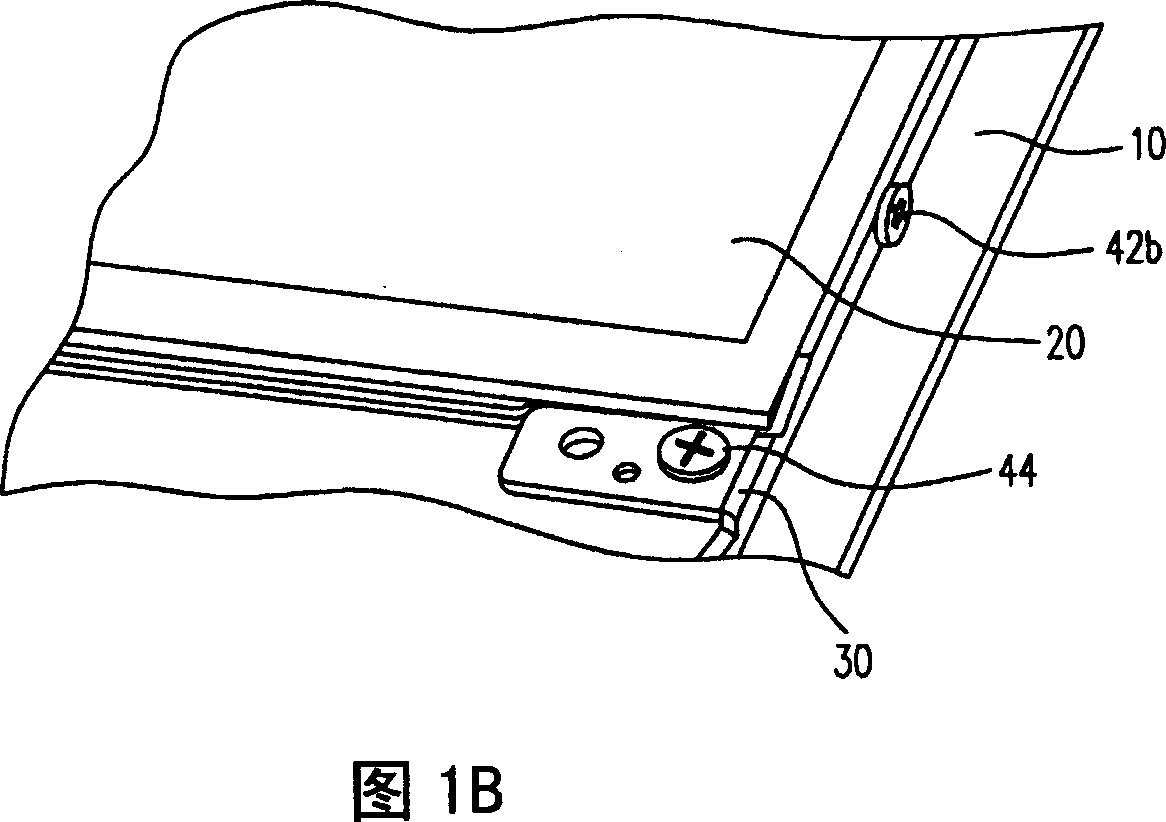
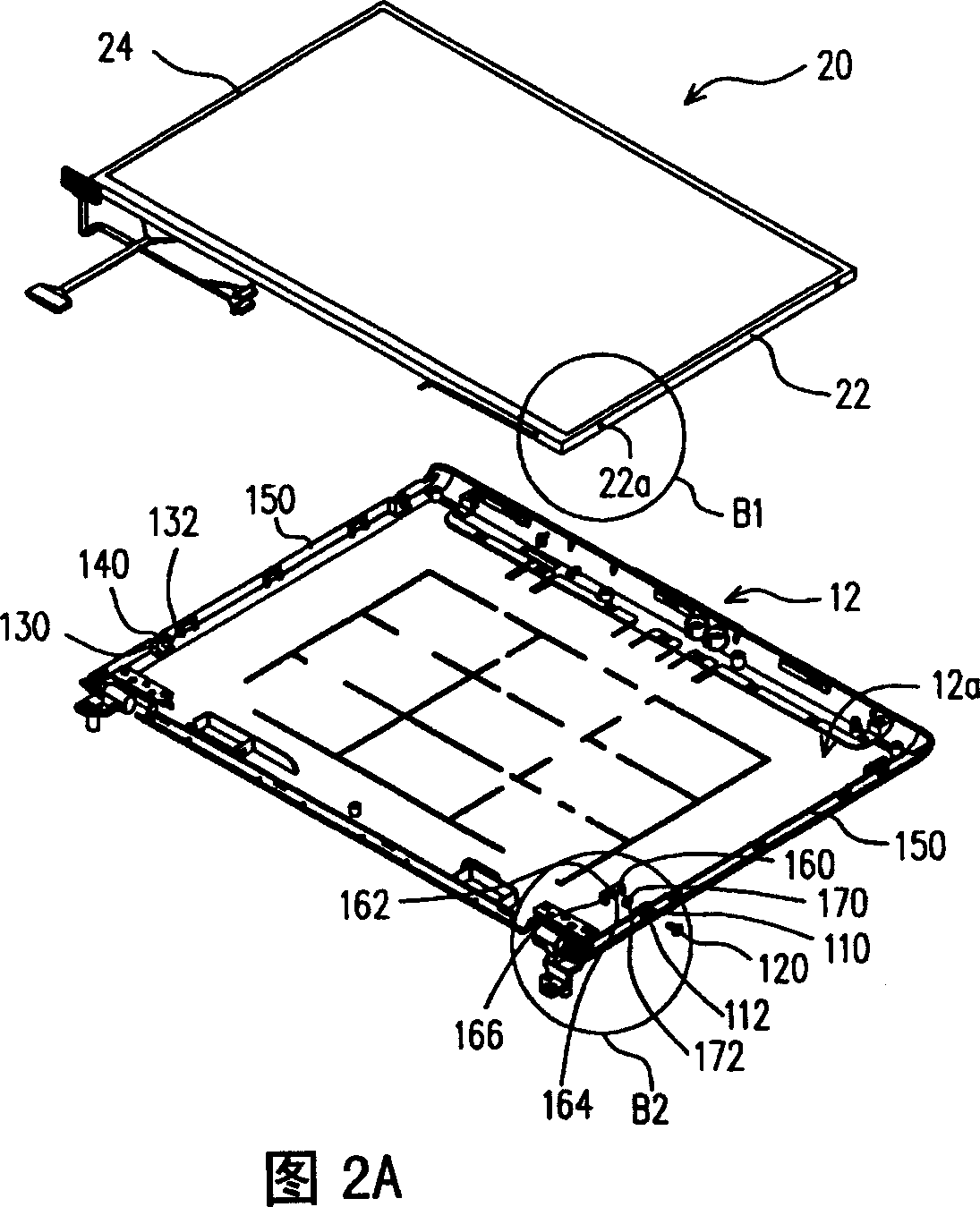
InactiveCN101094575AReduce weightAvoid damageDigital data processing detailsRack/frame constructionEngineeringElectrical and Electronics engineering
Owner:COMPAL ELECTRONICS INC
Heat exchanger and method for manufacturing same
InactiveCN104969021AImprove qualityImprove trustworthinessSemiconductor/solid-state device detailsSolid-state devicesThin metalEngineering
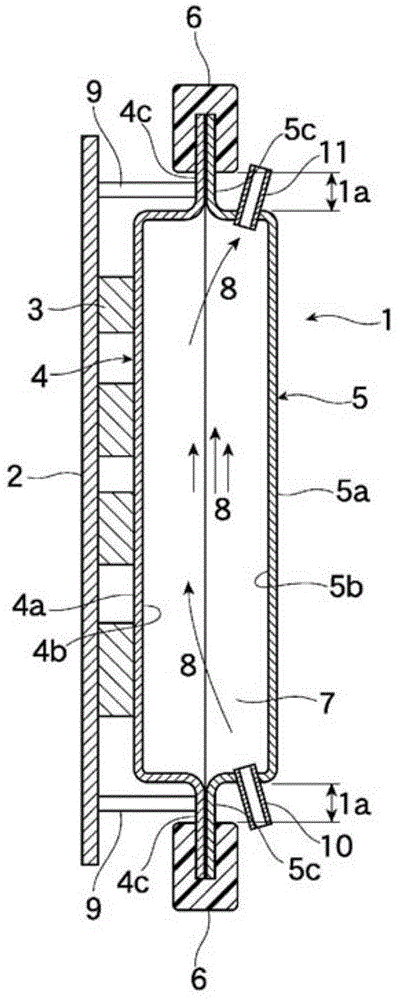
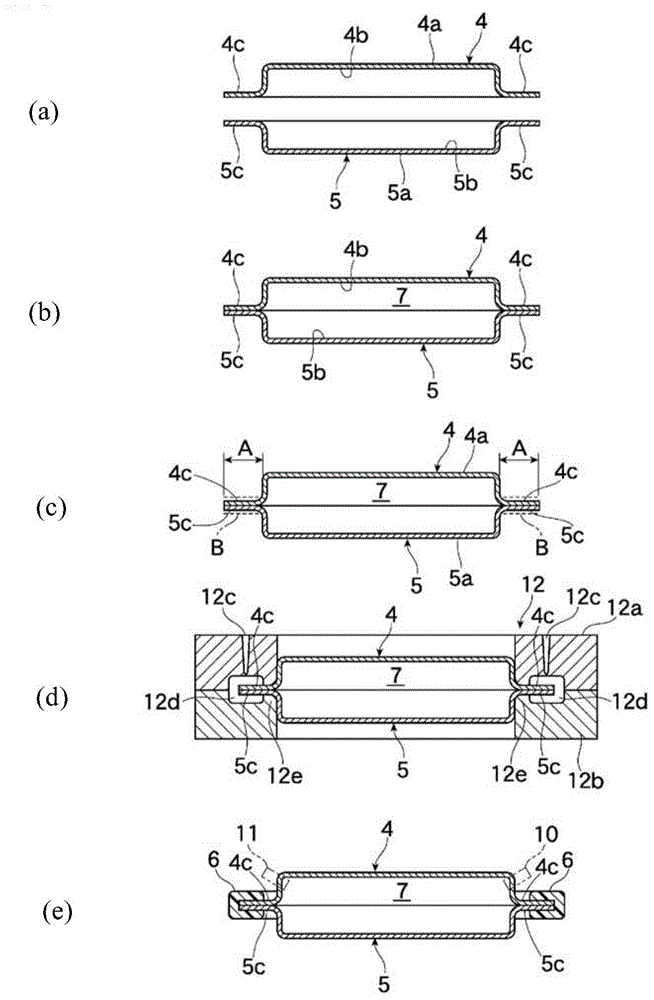
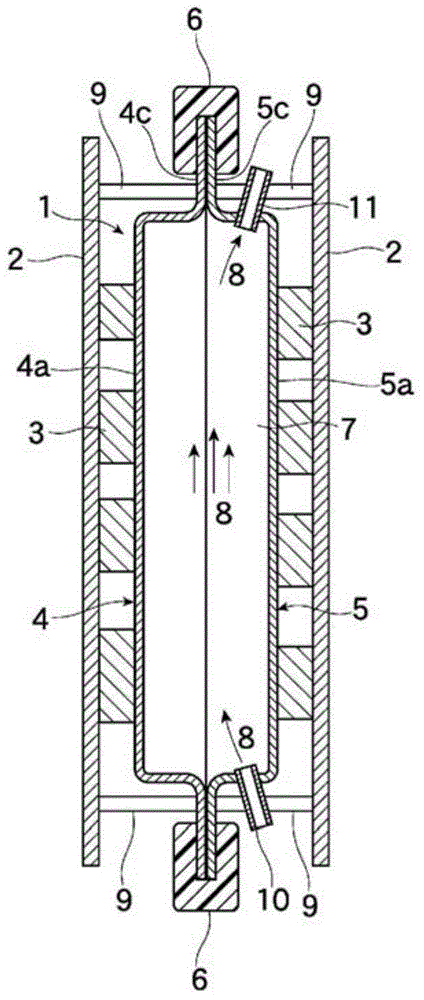
According to the present invention, the manufacturing process is simplified, the weight and cost are reduced, and a safe and reliable structure is obtained, using a generic metal plate. This heat exchanger has outer surfaces (4a, 5a) positioned on the side toward the electronic component (3) that is the object of heat exchange, and resin-coated inner surfaces (4b, 5b). A thin metal plate having a predetermined thickness is press-worked to a predetermined shape and a first shaped body (4) and a second shaped body (5) are formed. The two shaped bodies are combined so that the inner surface (4b, 5b)-sides face each other, and the inner surface (4b) at the edge parts (4c) and the inner surface (5b) at the edge parts (5c) are thermally fused by heat press-working. The edge parts (4c, 5c) are subjected to ultra-fine processing and then inserted into a die, and a thermoplastic resin composition is injected into the cavity of the die and a joining member (6) is shaped. The space section (7) created by the combining has a feed port (10) and an outlet port (11), and represents a fluid channel for a heat medium (8). The heat exchanger (1) is imparted with the structure described above. The outer surfaces (4a, 5a) are brought into contact with the electronic component (3) and heat exchange is performed with the heat medium flowing through the fluid channel.
Owner:TAISEI PLAS CO LTD
Industrial user demand response oriented transaction settlement control method based on blockchain
PendingCN111160880APreserve integrityEnsure fairnessFinancePayment protocolsCyber-attackData platform
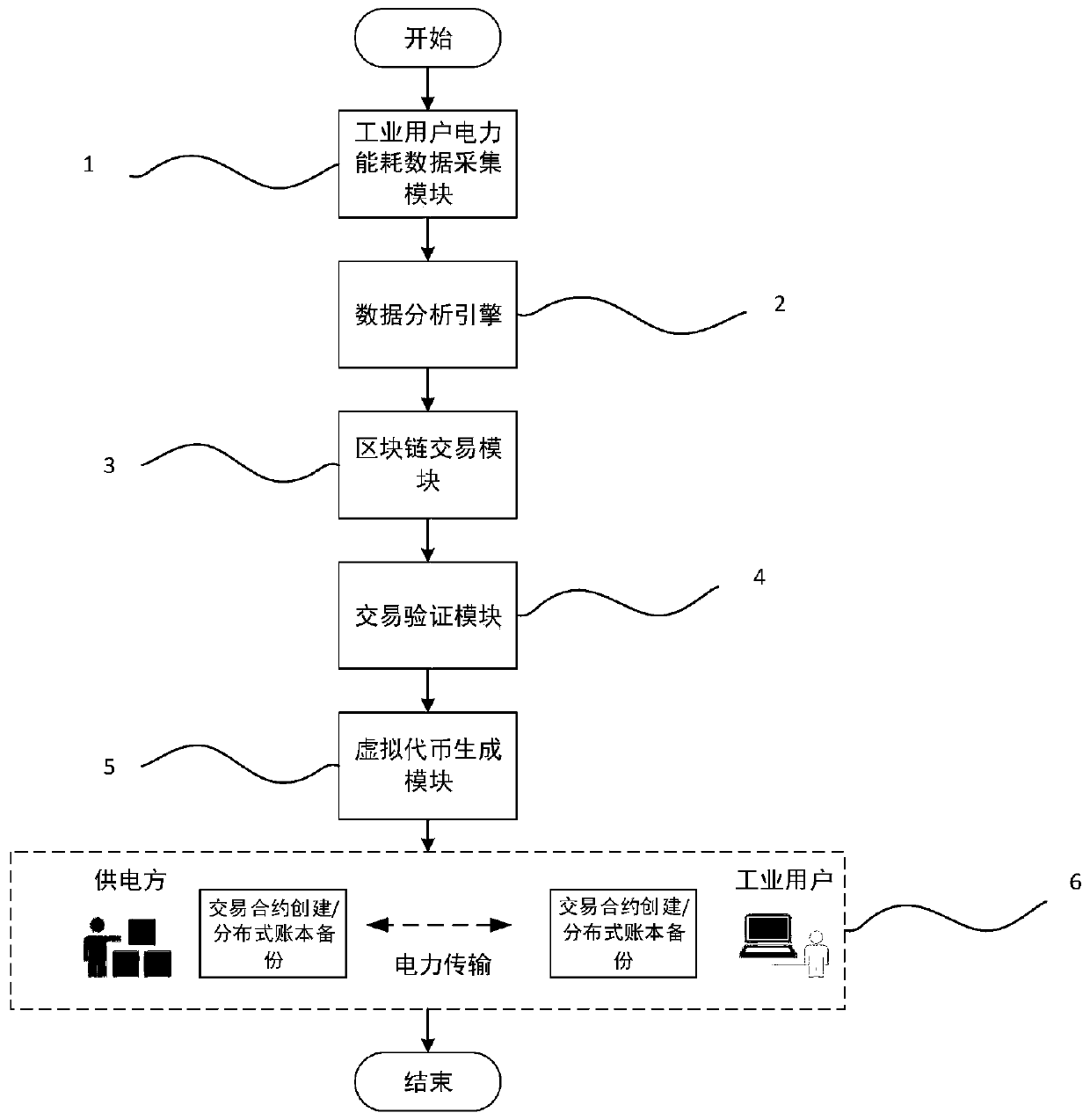
The invention relates to an industrial user demand response oriented transaction settlement control method based on a blockchain. The method is mainly and technically characterized by comprising the steps of collecting industrial user power energy consumption data; constructing a demand response strategy by using a data analysis engine according to the planned power reduction quantity and the basic power consumption condition; according to the demand response strategy, establishing a power transaction model by using a blockchain technology; establishing a transaction verification model based on the power transaction model; generating virtual tokens as the circulation volume of the transaction; and completing the transfer of the virtual token and completing the transaction through an intelligent contract mechanism. The method is reasonable in design, and a reasonable and effective demand response strategy can be formulated; according to the method, the industrial user demand response isestablished, the blockchain technology is adopted, fairness and safety of industrial user power transaction are guaranteed, the blockchain technology is used in the industrial user demand response implementation process, data exception can be rapidly detected, the capacity of detecting and responding to network attacks is enhanced, the reliability of a data platform is enhanced, and the integrityof data is reserved.
Owner:STATE GRID TIANJIN ELECTRIC POWER +2
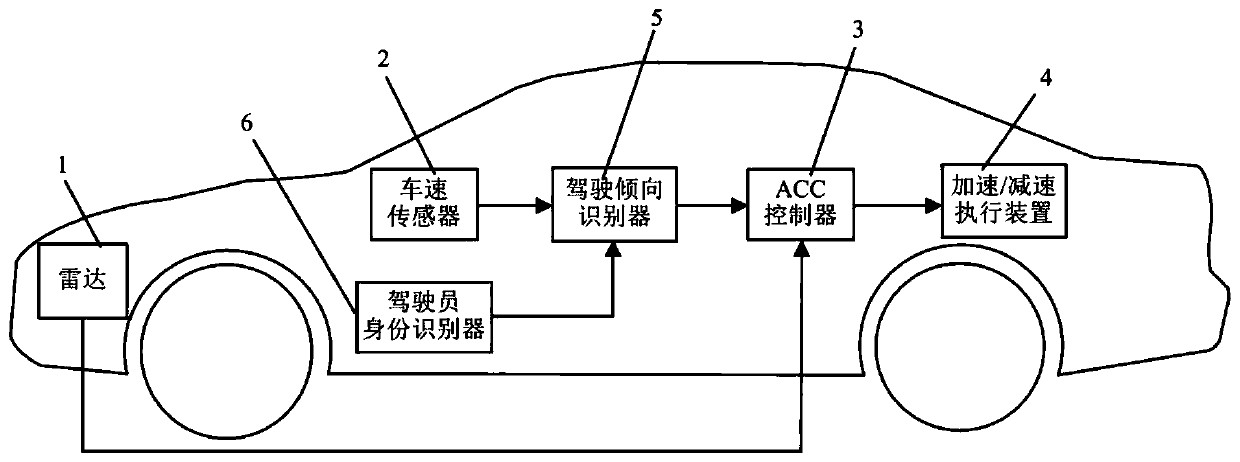
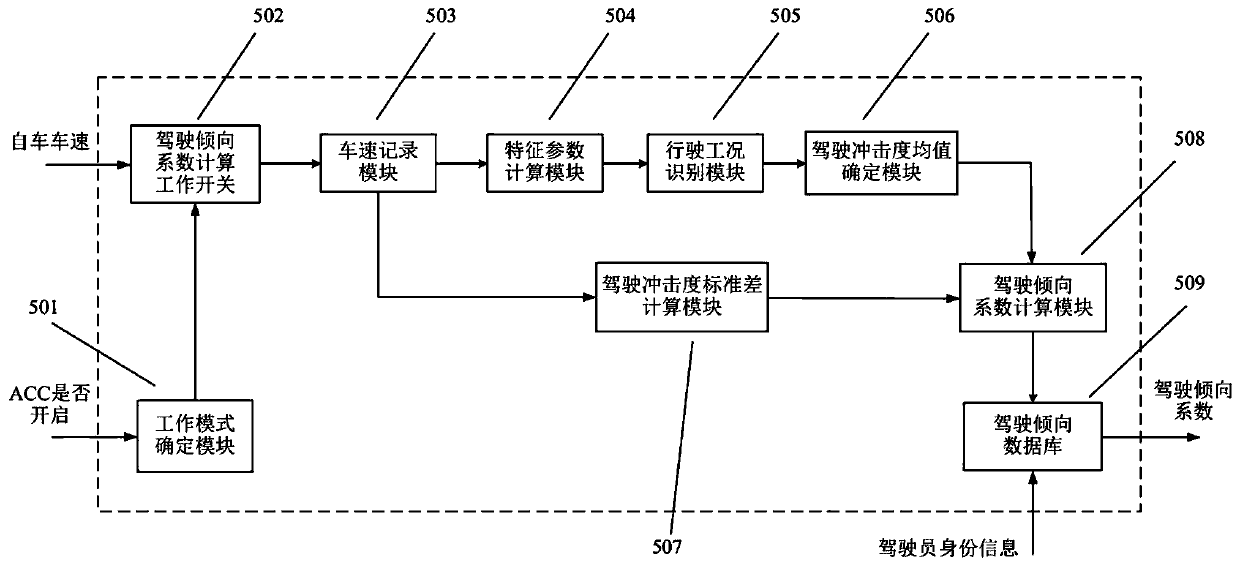
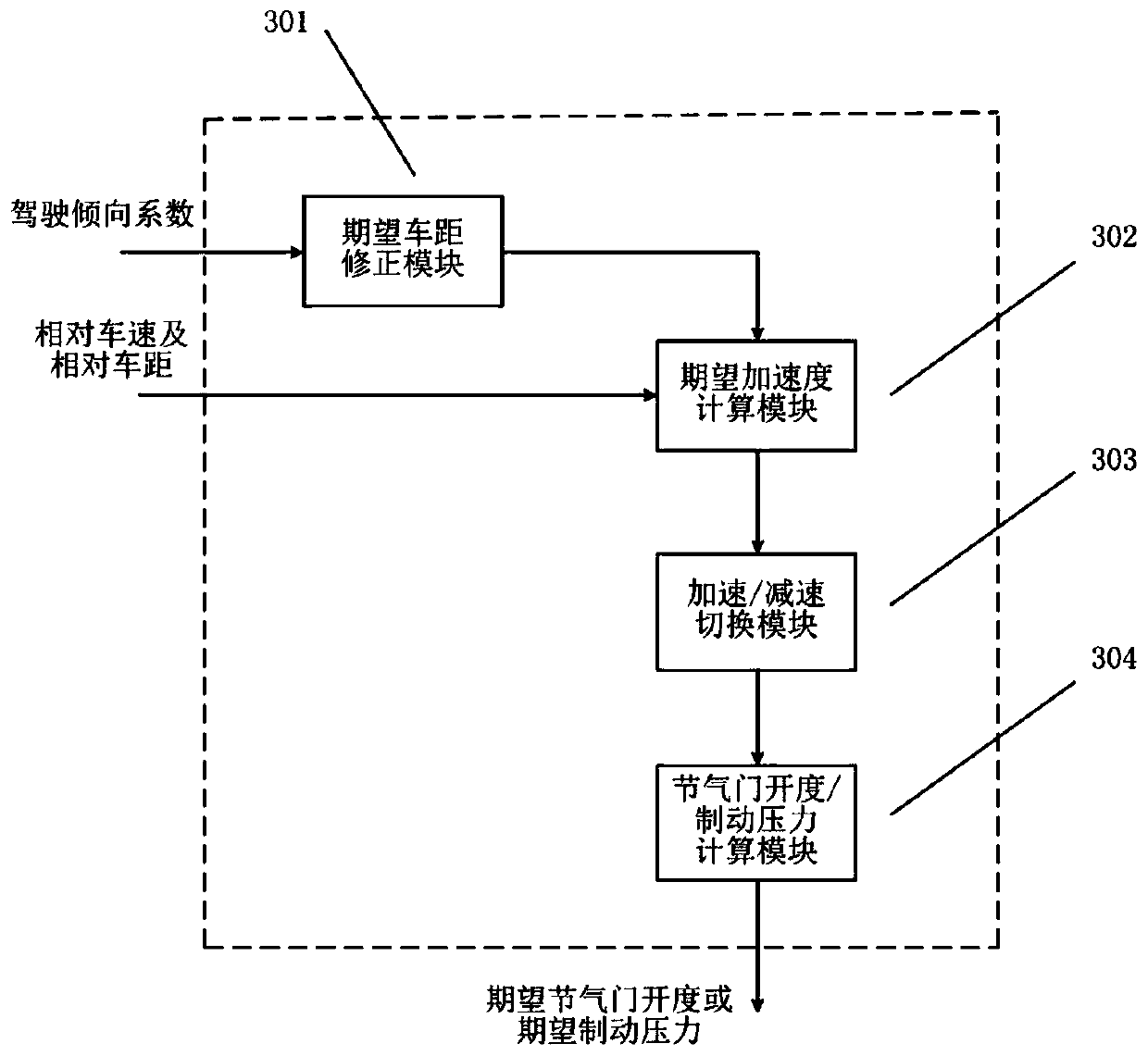
Vehicle adaptive cruise control system and method capable of recognizing driving tendency
ActiveCN110949386AAdjust the desired vehicle distance in real timeImprove trustworthinessDriver/operatorCruise control
The invention discloses a vehicle adaptive cruise control system and method capable of recognizing driving tendency. The vehicle adaptive cruise control system comprises a radar, a vehicle speed sensor, an ACC controller, an acceleration / deceleration execution device, a driving tendency recognizer and a driver identity recognizer. When the vehicle is driven manually, the driving tendency recognizer enters a driving tendency recognition working mode, calculates driving tendency coefficients of the driver and stores the driving tendency coefficients in one-to-one correspondence with driver identity information. When the vehicle is subjected to adaptive cruise driving, the driving tendency recognizer enters a driving tendency extraction working mode to extract a driving tendency coefficient corresponding to the current driver identity; and the ACC controller corrects the expected vehicle distance according to the driving tendency coefficient, so that the corrected expected vehicle distance conforms to the driving habit and psychological expectation of the current driver, and the method has the beneficial effect that the trust degree and the utilization rate of each driver to the adaptive cruise control system can be effectively improved.
Owner:JIANGSU UNIV
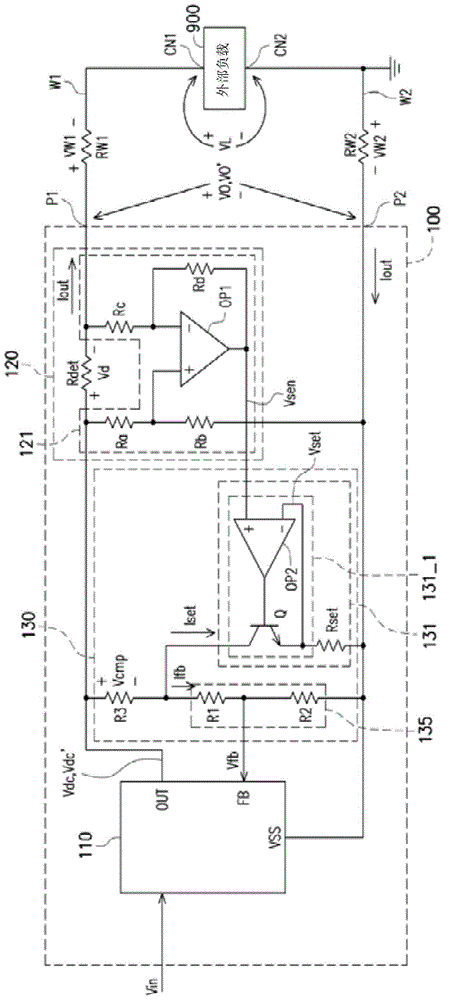
Power supply device with electric wire drop compensation
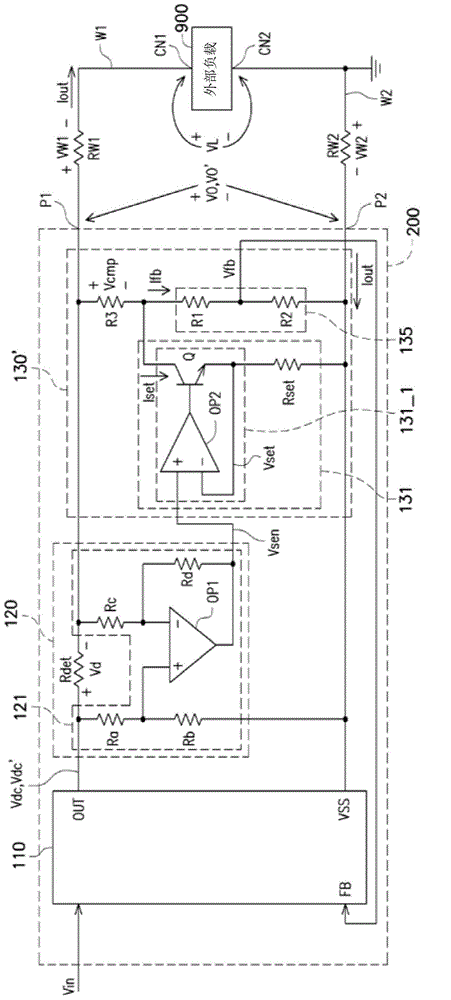
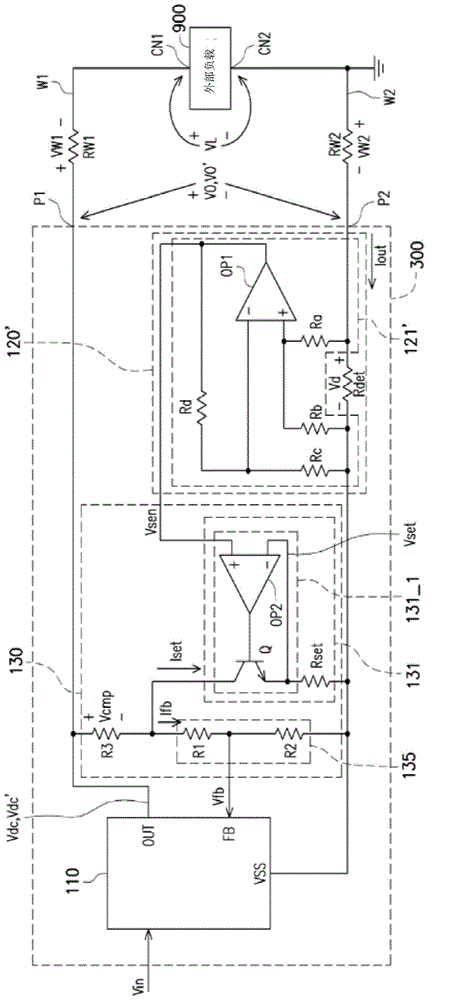
ActiveCN106325343AImprove stabilityImprove trustworthinessElectric variable regulationVoltage dropEngineering
The invention provides a power supply device with electric wire drop compensation. The power supply device comprises a first power source pin, a second power source pin, a direct current output voltage stabilizer, a current sensing circuit and a compensation circuit, wherein the first power source pin and the second power source pin are coupled to external loads by a first wire and a second wire respectively; the direct current output voltage stabilizer receives an input voltage and a feedback voltage, and generates an output voltage and an output current on the basis; the current sensing circuit is used to sense the output current and generate a sensing voltage on the basis; the compensation circuit responds to the sensing voltage so as to generate a compensation voltage, wherein the compensation voltage is equal to the sum of a voltage drop of the first wire and a voltage drop of the second wire; and the compensation circuit compensates the output voltage according to the compensation voltage, so that a load voltage of the external loads can be maintained at a stable voltage value.
Owner:ACER INC
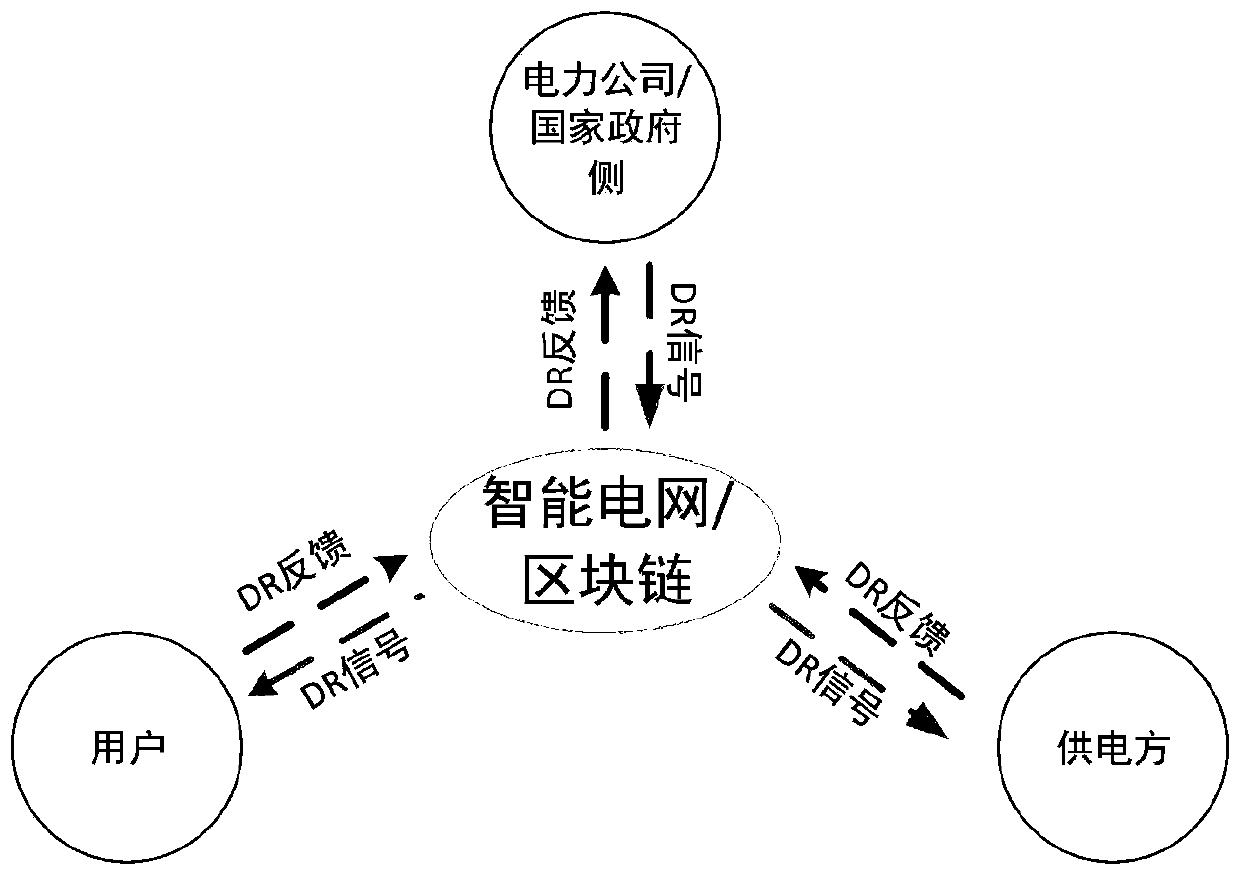
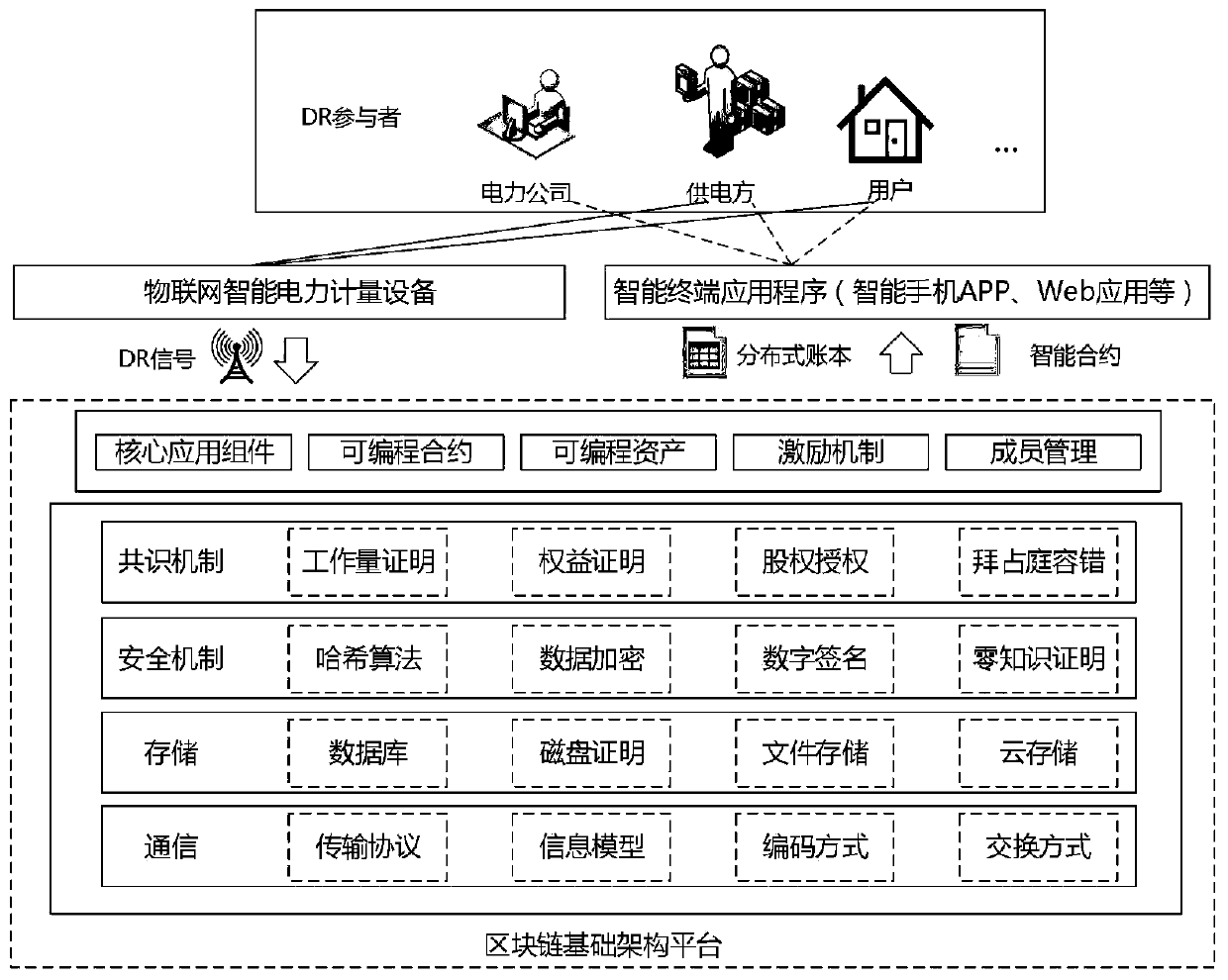
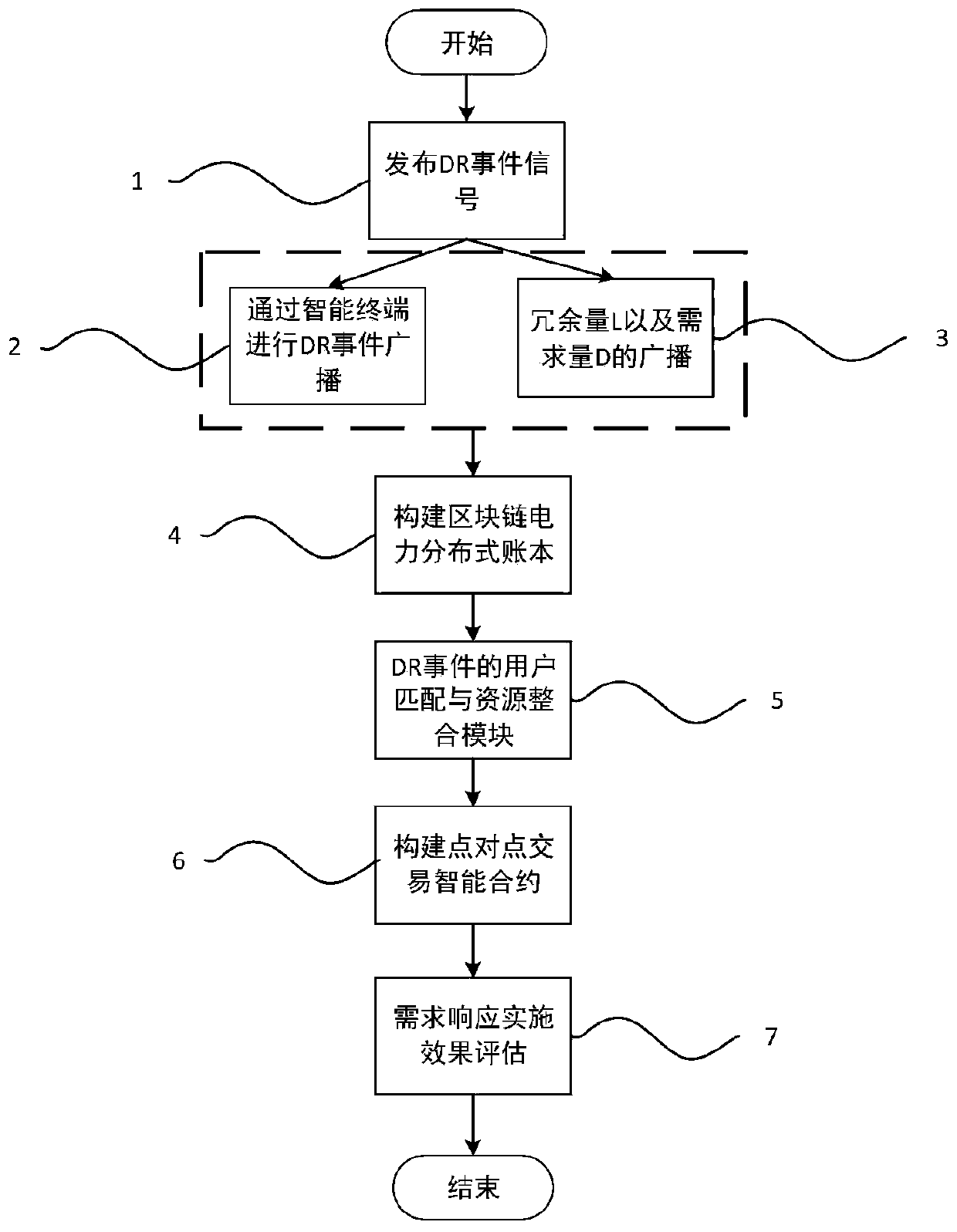
Control method of demand response management platform based on block chain technology
PendingCN111178682AImprove trustworthinessPreserve integrityResourcesInformation technology support systemIntegratorPower grid
The invention relates to a control method of a demand response management platform based on a block chain technology. The control method comprises the following steps: enabling a smart power grid to issue a DR event signal; broadcasting a DR event signal through the intelligent terminal; broadcasting redundancy and demand quantity; constructing a block chain electric power distributed account book; and performing user matching and resource integration of the DR event, and constructing a point-to-point transaction smart contract. The design is reasonable, the method is used for distributed management, control and DR verification in an intelligent power grid. Traceable and tamper-proof flexible transaction and nearly real-time DR verification are realized through the characteristics of the block chain. High reliability and decentralized operation are ensured; the whole demand response management platform is composed of a plurality of peer nodes including a power producer, a power company, a user, a load integrator, a supervision mechanism and the like, all stakeholders can carry out interaction coordination through an architecture platform based on a block chain, comprehensive and scattered energy demand and power generation cooperation are supported, and stable operation of a power grid is ensured.
Owner:STATE GRID TIANJIN ELECTRIC POWER +3
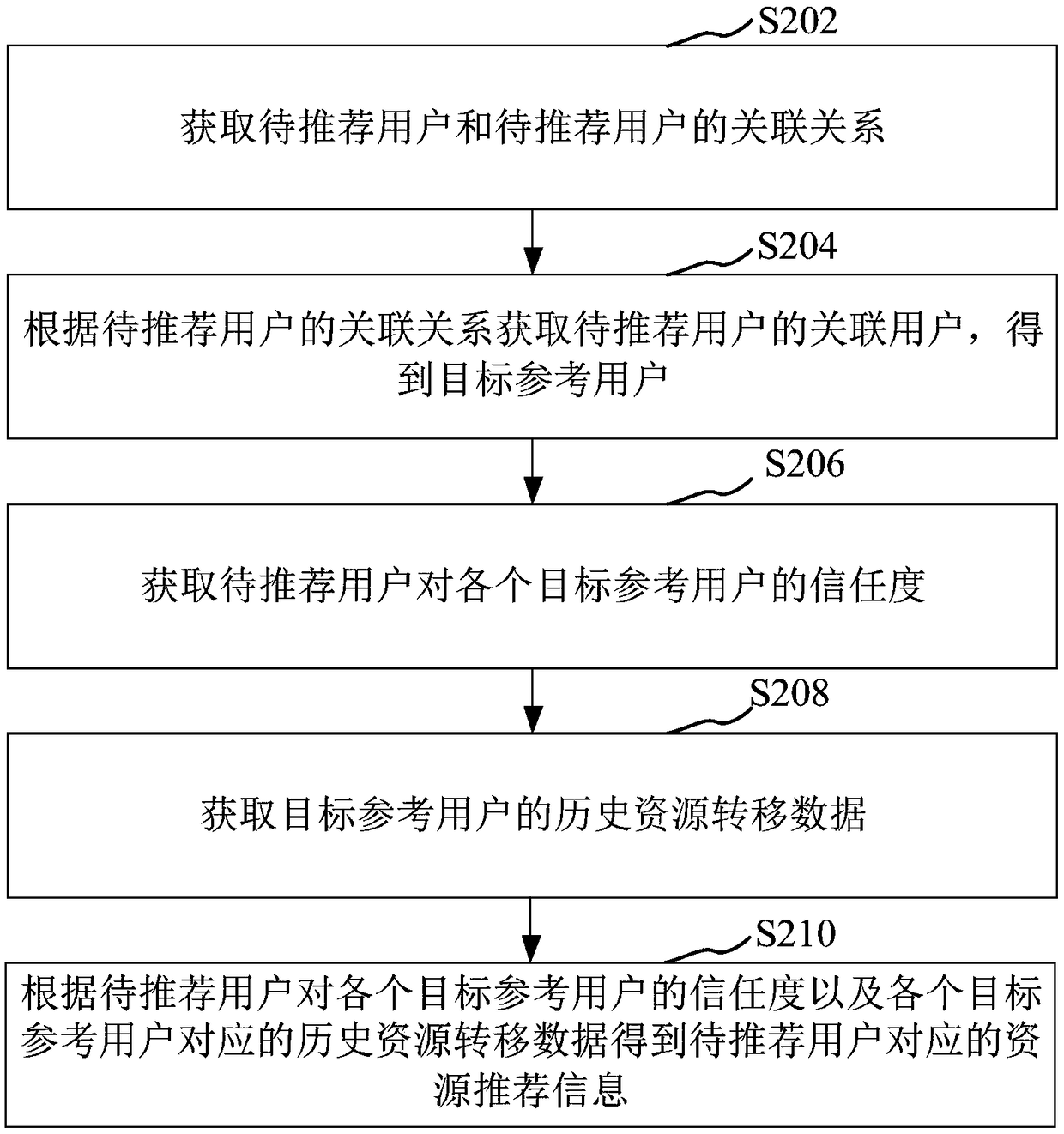
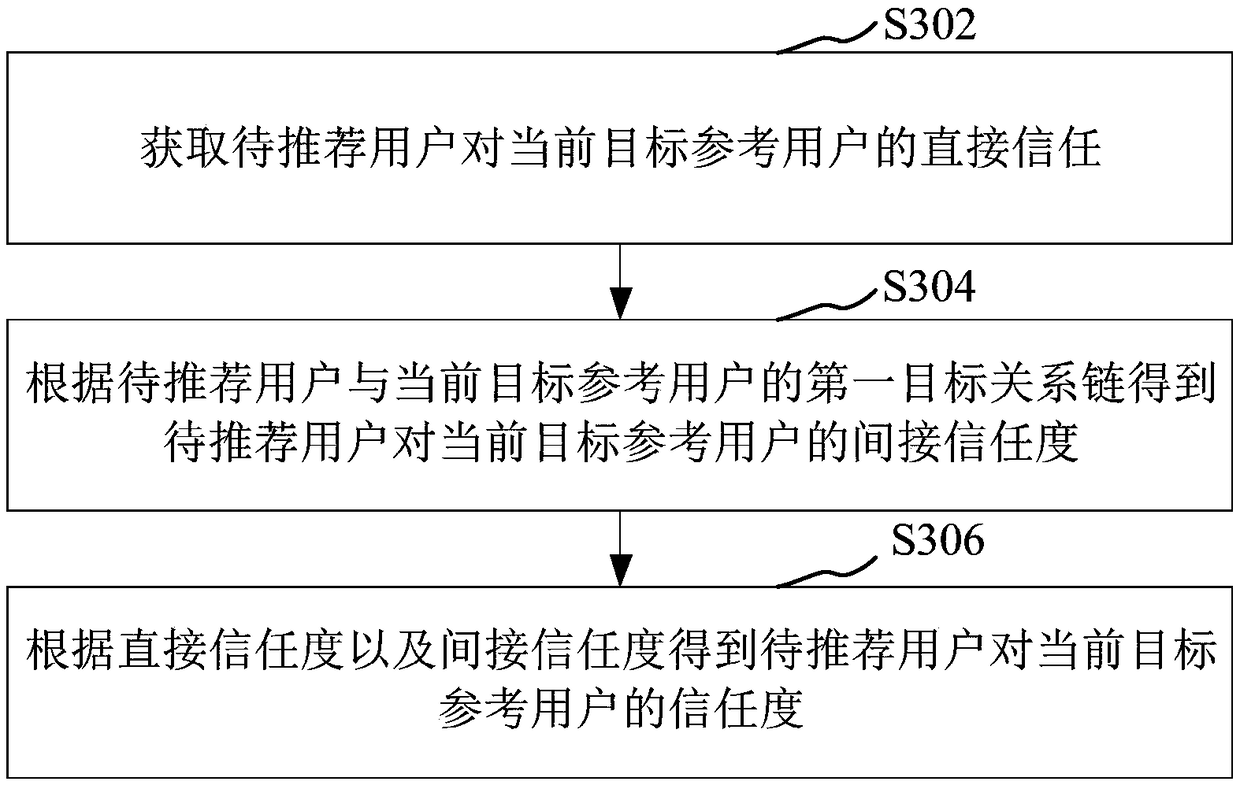
Information processing method and device, computer device and storage medium
PendingCN109426985AIncrease acceptance rateImprove trustworthinessMarketingInformation processingInternet privacy
The invention relates to an information processing method and device, a computer device and a storage medium. The method comprises the following steps of acquiring an association relationship betweena user to be recommended and the user to be recommended; obtaining an associated user of the user to be recommended according to the associated relationship of the user to be recommended, and obtaining a target reference user; obtaining the trust degree of the user to be recommended to the target reference user; acquiring the historical resource transfer data of the target reference user; obtaining the resource recommendation information corresponding to the user to be recommended according to the trust degree of the user to be recommended to the target reference user and the historical resource transfer data corresponding to the target reference user. The method can recommend the reliability of information, is high in user acceptance rate, can reduce the invalid recommendation, and avoidsthe interference of spam information.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Duplex air governor and its control method
InactiveCN101089500AImprove trustworthinessImprove stabilitySpace heating and ventilation safety systemsLighting and heating apparatusCondensation temperatureEngineering
The present invention relates to a duplex air conditioner and its control method. It is characterized by that in the duplex air conditioner composed of outdoor machine in which an outdoor heat exchanger, a compressor and on electronic expansion valve are mounted and several indoor machines which are connected together a detection portion for determining temperature of above-mentioned outdoor heat exchanger, suction temperature and discharge temperature of compressor and condensation temperature of every indoor machine and a control portion which can be used for controlling above-mentioned electronic expansion valve, making it utilize the compressor suction temperature determined by above-mentioned election portion and temperature of outdoor heat exchanger to calculate temperature difference and judge suction super heating temperature, at the same time making the suction super heating temperature be raised to more than defined temperature according to the condensation temperature of above-mentioned indoor machine are included. Besides, said invention also provides the concrete steps of its control method.
Owner:LG ELECTRONICS (TIANJIN) APPLIANCES CO LTD
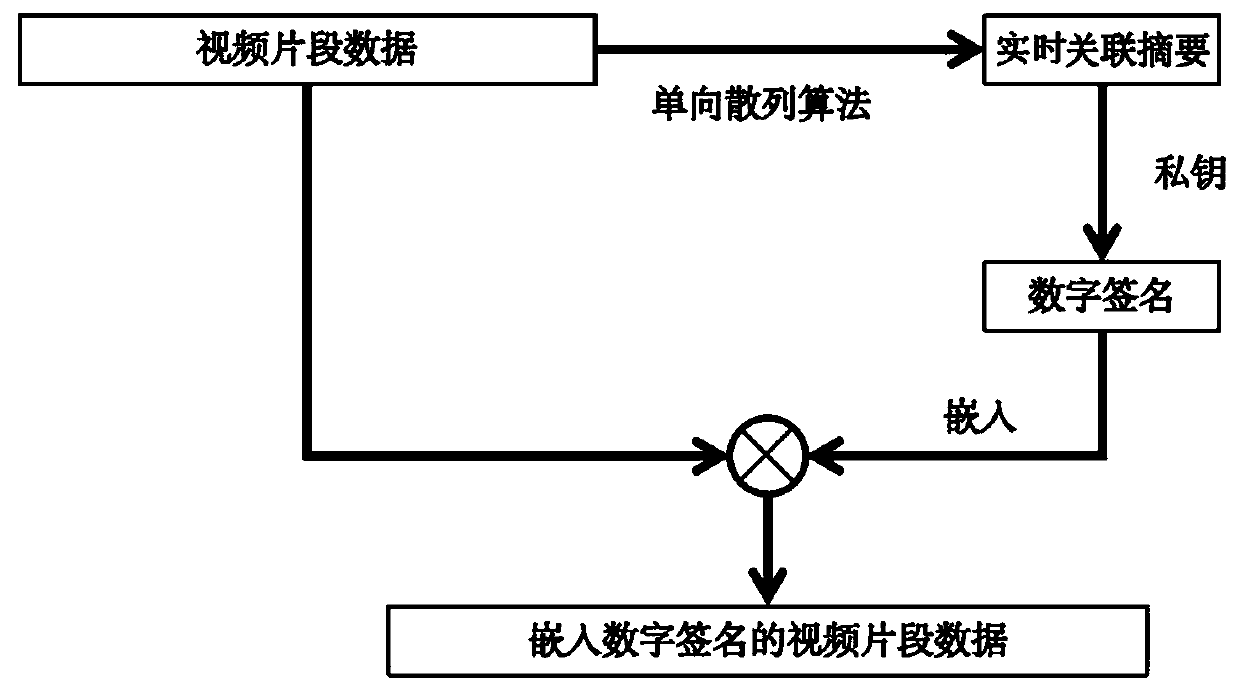
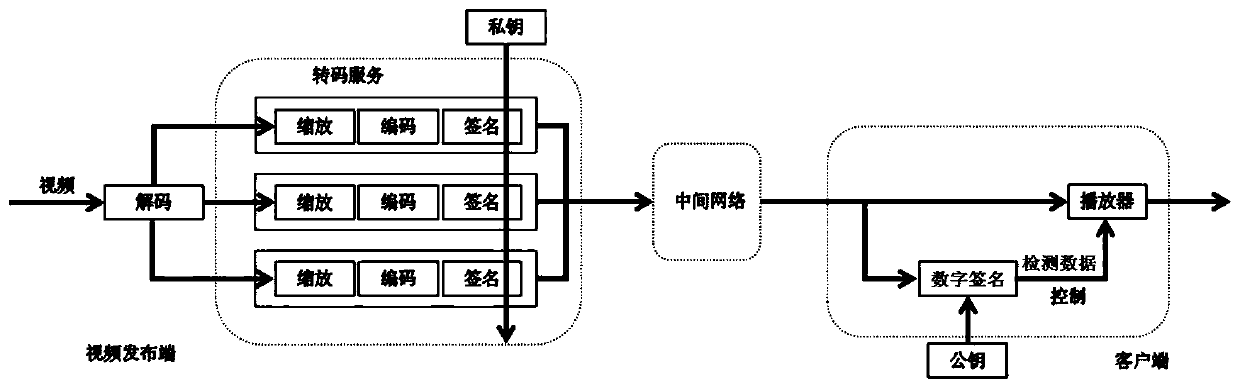
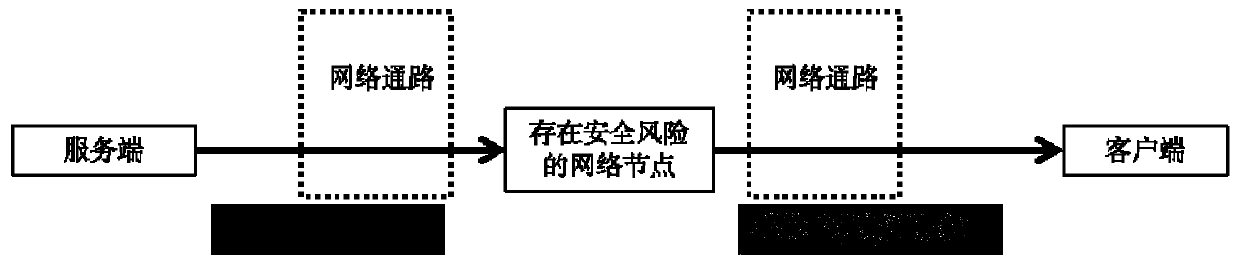
Video and audio credible playing method based on asymmetric encryption
ActiveCN110602570AReduce engineering overheadImprove trustworthinessSelective content distributionDigital signatureThe Internet
The invention discloses a video and audio credible playing method based on asymmetric encryption, and relates to the technical field of digital security, and the method comprises the steps that a publishing end embeds a digital signature encrypted by a private key into a video streaming media in a general transcoding service process of the video streaming media, and pushes the video streaming media embedded with the digital signature to an intermediate network; the client receives the video streaming media through the intermediate network; digital signatures therein is extracted, the digitalsignature is decrypted by using the public key to obtain data for detection; and a detection result is deduced according to the detection data to control the player to play the video streaming media content. According to the invention, the detection process is transferred from the Internet to the transceiving end; by combining the one-way hash algorithm and the asymmetric encryption technology, while it is ensured that the behaviors of tampering and replacing the streaming media in the transmission process can be detected by the user side, the calculation overhead is greatly reduced, the complex asymmetric encryption technology can be applied to video streaming media application, and the basic real-time requirement of the streaming media is met.
Owner:CHENGDU SOBEY DIGITAL TECH CO LTD
Automatic testing system for automobile electrical-appliance power supply variation, and testing method thereof
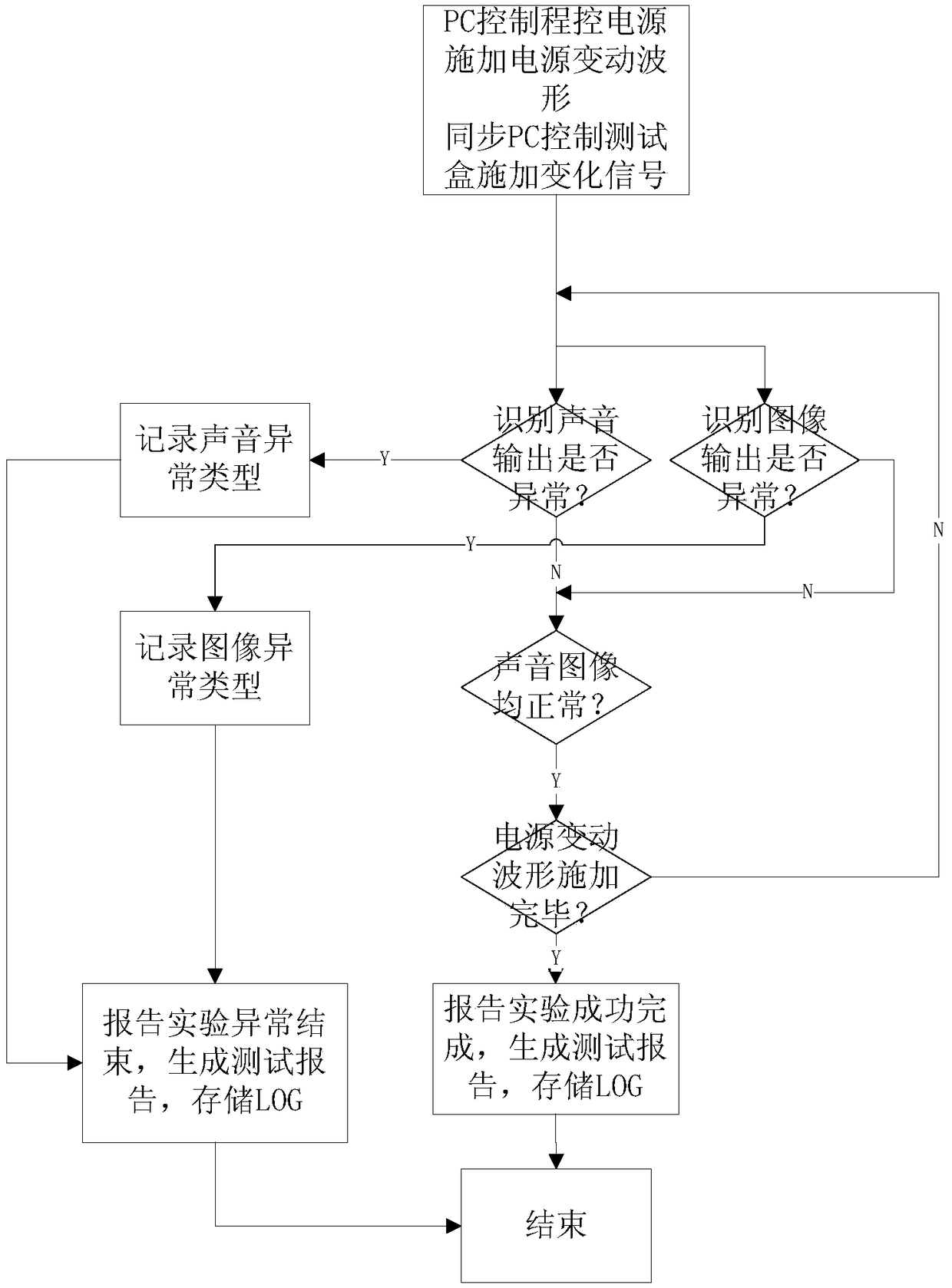
InactiveCN108918991AEliminate missed detectionsImprove consistencyTesting electric installations on transportControl powerAutomatic testing
The invention provides an automatic testing system for automobile electrical-appliance power supply variation, and a testing method thereof. The automatic testing system comprises control equipment, aprogram-controlled power supply, a testing box, tested equipment, and information collecting equipment. Through the control equipment, the program-controlled power supply generates a power supply variation testing waveform, the testing box generates a signal associated with the power supply variation testing waveform, and the power supply variation testing waveform and the signal are applied to the tested equipment; and by identifying information from the information collecting equipment, the information output by the tested equipment can be analyzed in real time, and whether the tested equipment is in a breakdown state or not is judged automatically.
Owner:THUNDERSOFT
Blockchain-based student file system
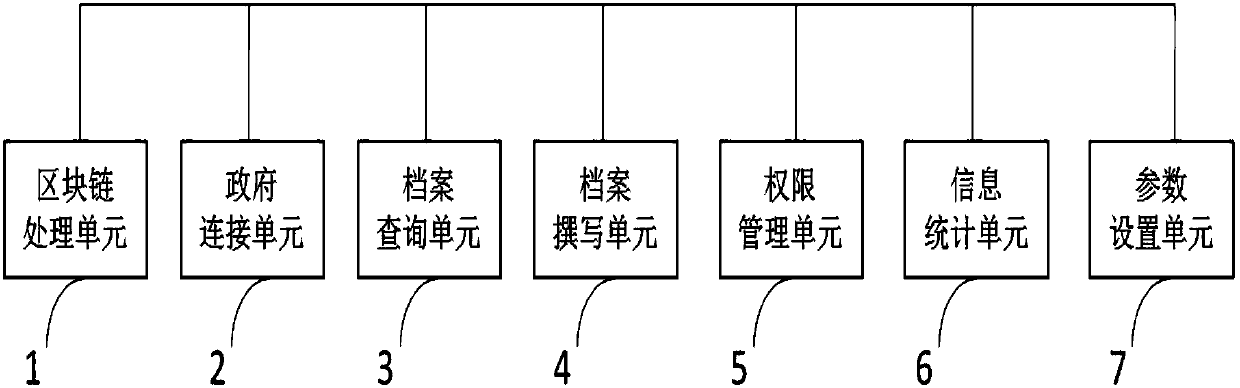
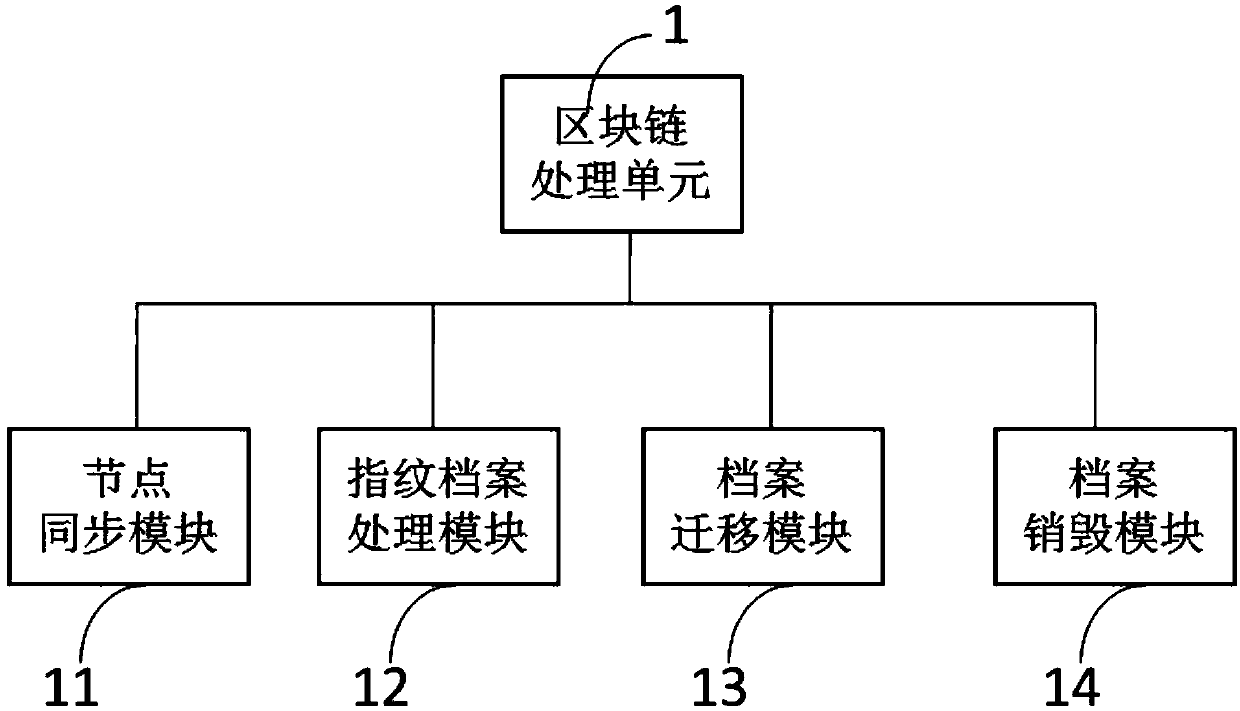
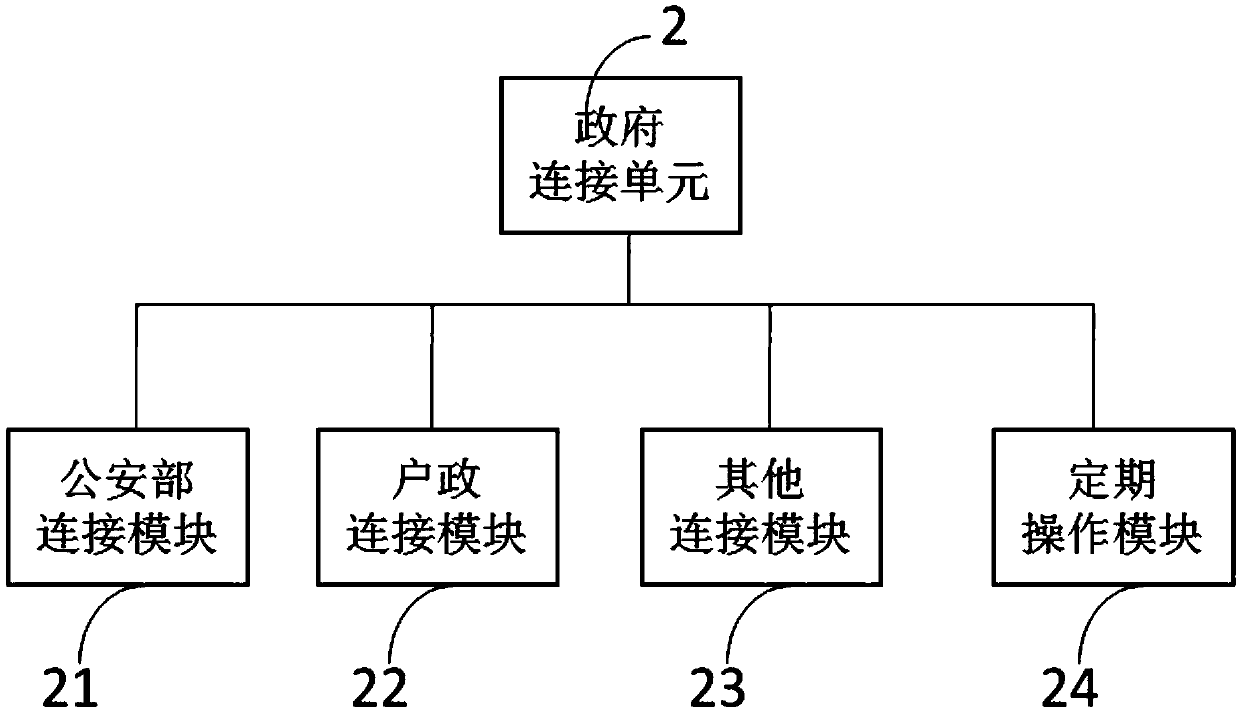
InactiveCN107644064AGuaranteed reliabilityImprove trustworthinessData processing applicationsSpecial data processing applicationsManagement unitFile system
The invention discloses a blockchain-based student file system. The system comprises a file writing unit, a blockchain processing unit, a government connection unit, a right management unit, and a file inquiry unit, wherein the file writing unit is used for building an electronic student file and / or scanning a paper file so as to obtain an electronic image of a student, the blockchain processing unit comprises a file processing module for generating a digital fingerprint and registering the digital fingerprint in a blockchain and a node synchronization module for synchronizing and identifyingmultiple nodes of the blockchain in a preset time, the government connection unit comprises a government connection unit, a household-government connection module, and a regular operation module for controlling a public security department connection module and the household-government connection module to acquire student information in a preset period and sending the information to the blockchainprocessing unit to update the file, the right management unit is used for adding, deleting, modifying and inquiring the right of a user, and the file inquiry unit is used for enabling a user with a right to search and read a student file. The blockchain-based student file system provides a public credit mechanism and can record accurate information.
Owner:雷虹
Delicious food recommendation list generation method and device, equipment and storage medium
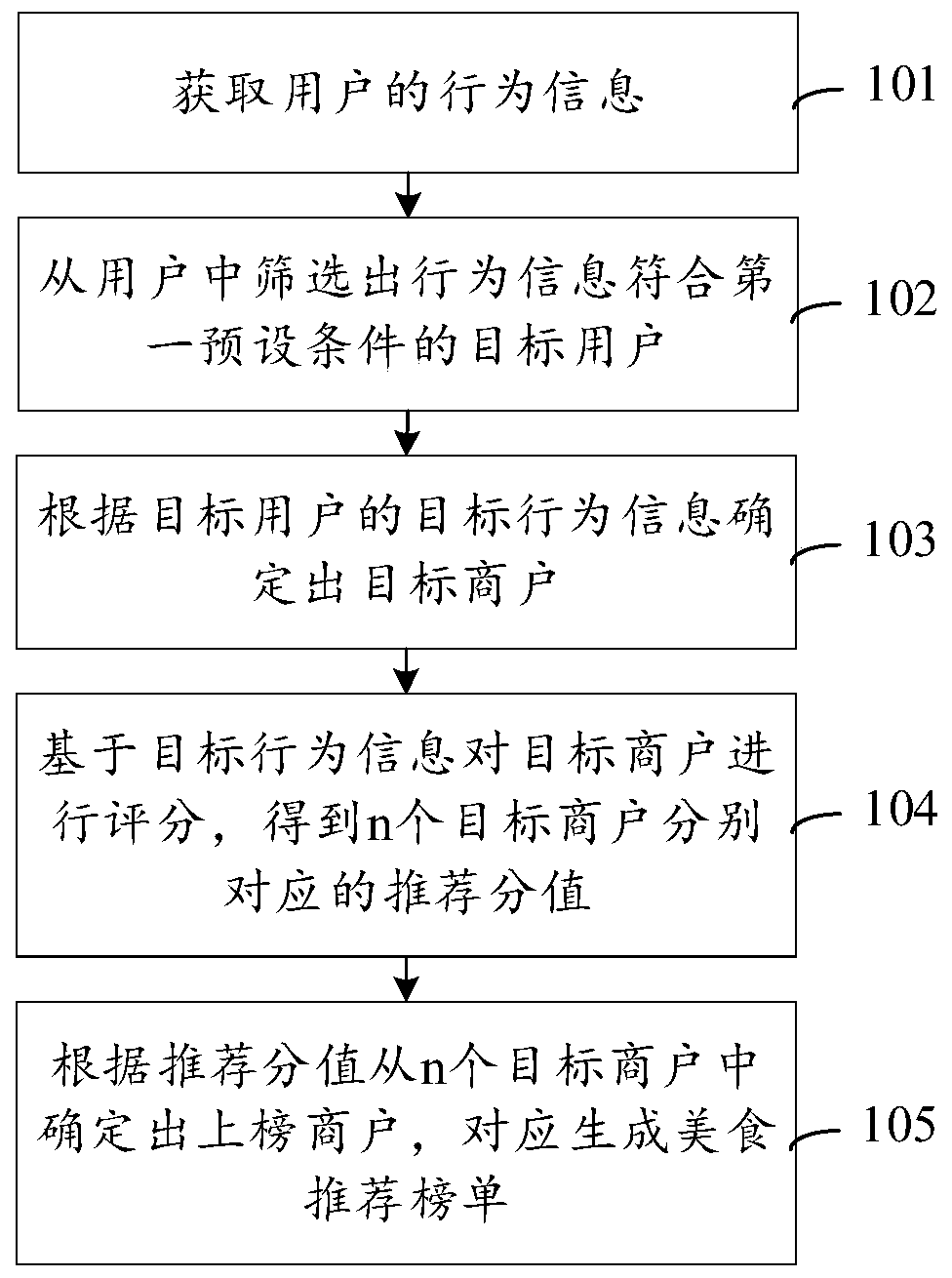
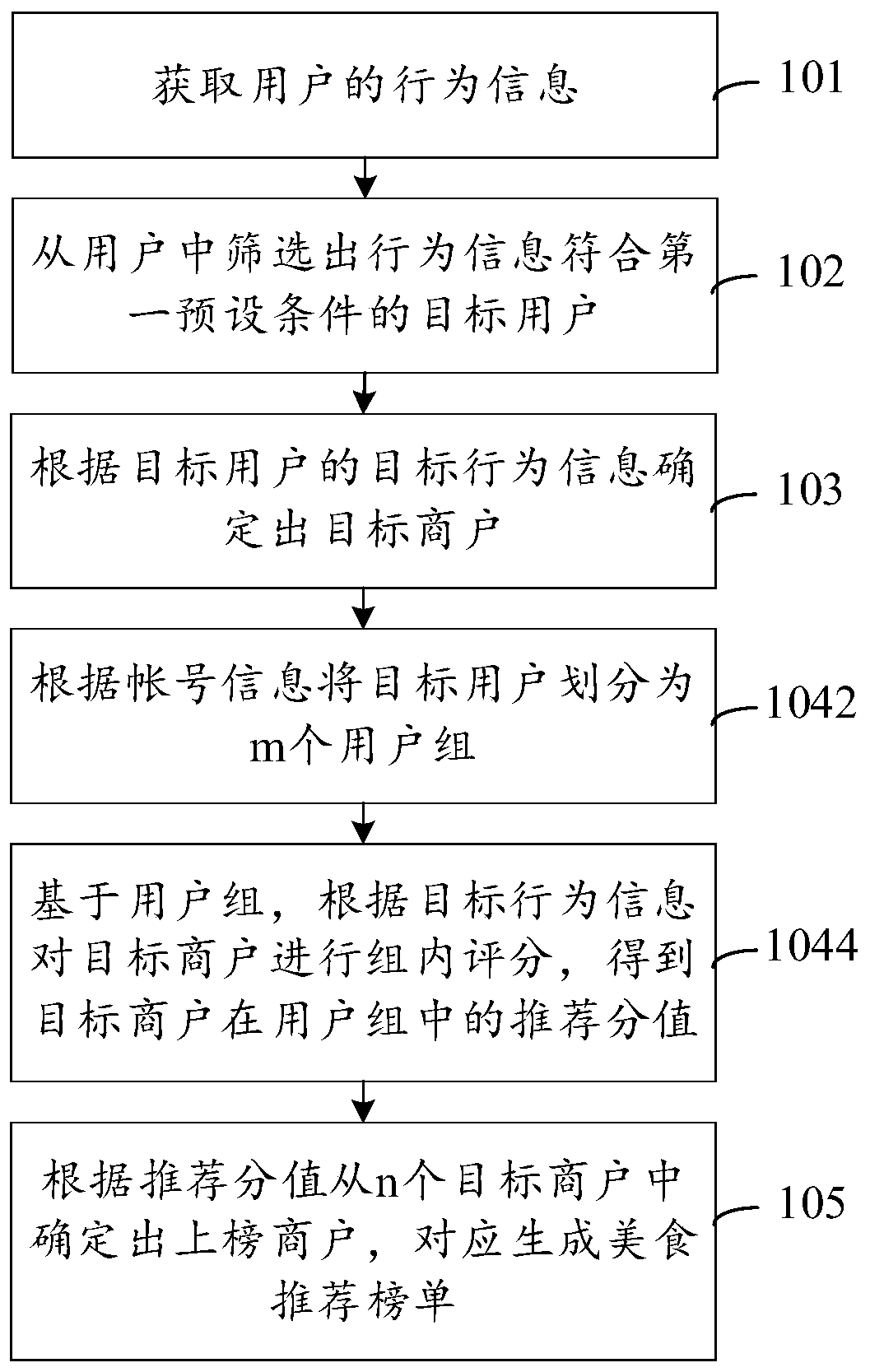
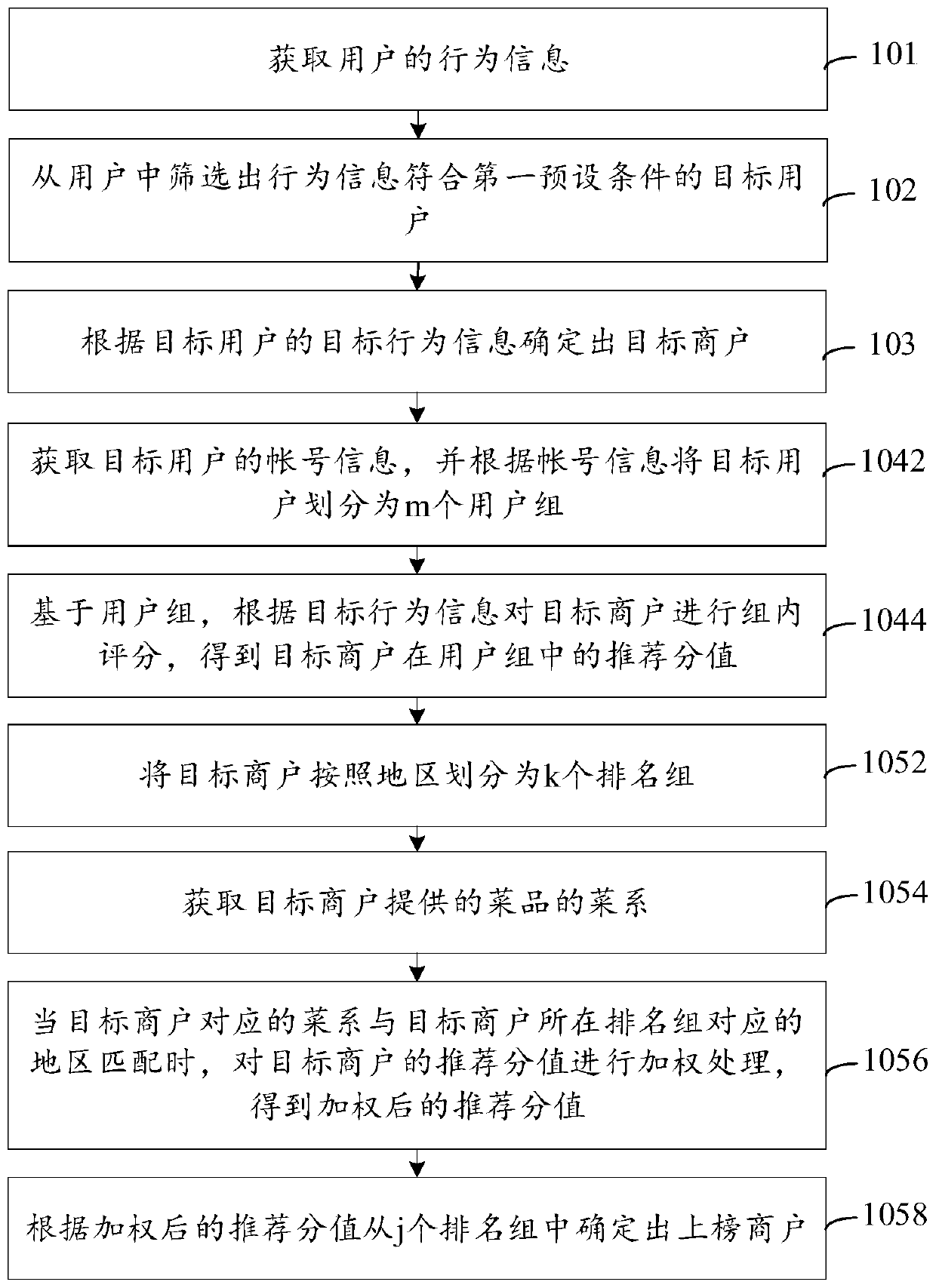
PendingCN110942344AHigh reference valueImprove trustworthinessBuying/selling/leasing transactionsMarketingApplication softwareComputer science
The invention discloses a delicious food recommendation list generation method and device, equipment and a storage medium, and is applied to the field of application programs.The method comprises thesteps that behavior information of a user is acquired; screening out a target user whose behavior information meets a first preset condition from the users, and determining a target merchant accordingto the target behavior information of the target user; scoring the target merchants based on the target behavior information to obtain recommendation scores corresponding to the n target merchants; and determining a listed merchant from the n target merchants according to the recommendation score, and correspondingly generating a delicious food recommendation list. According to the method, listedmerchants are determined through big data analysis; according to the method, the listed merchants of the delicious food recommendation list are determined by utilizing the approval degree of the qualified user to the delicious food, so that the delicious food provided by the listed merchants better conforms to the taste and opinions of the public, the reliability of the screened listed merchantsis improved, and more reliable delicious food recommendation information is provided for the user.
Owner:HANHAI INFORMATION TECH SHANGHAI
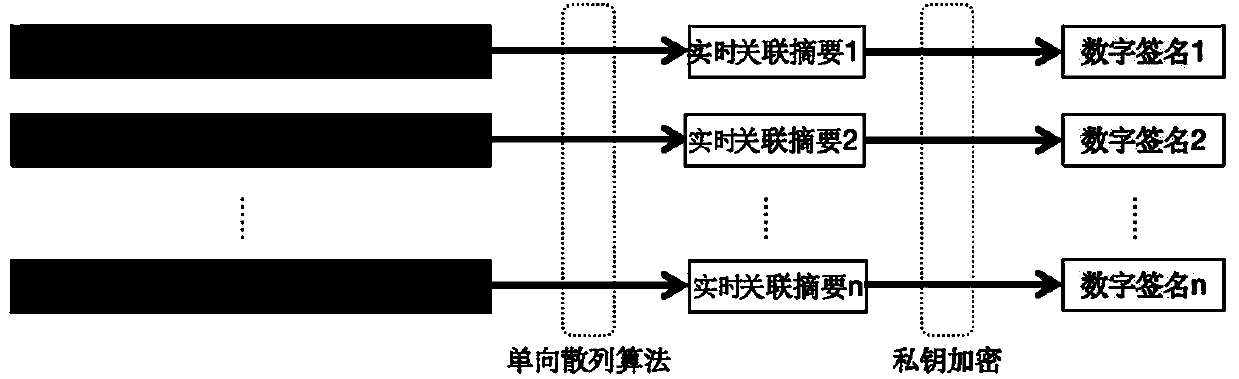
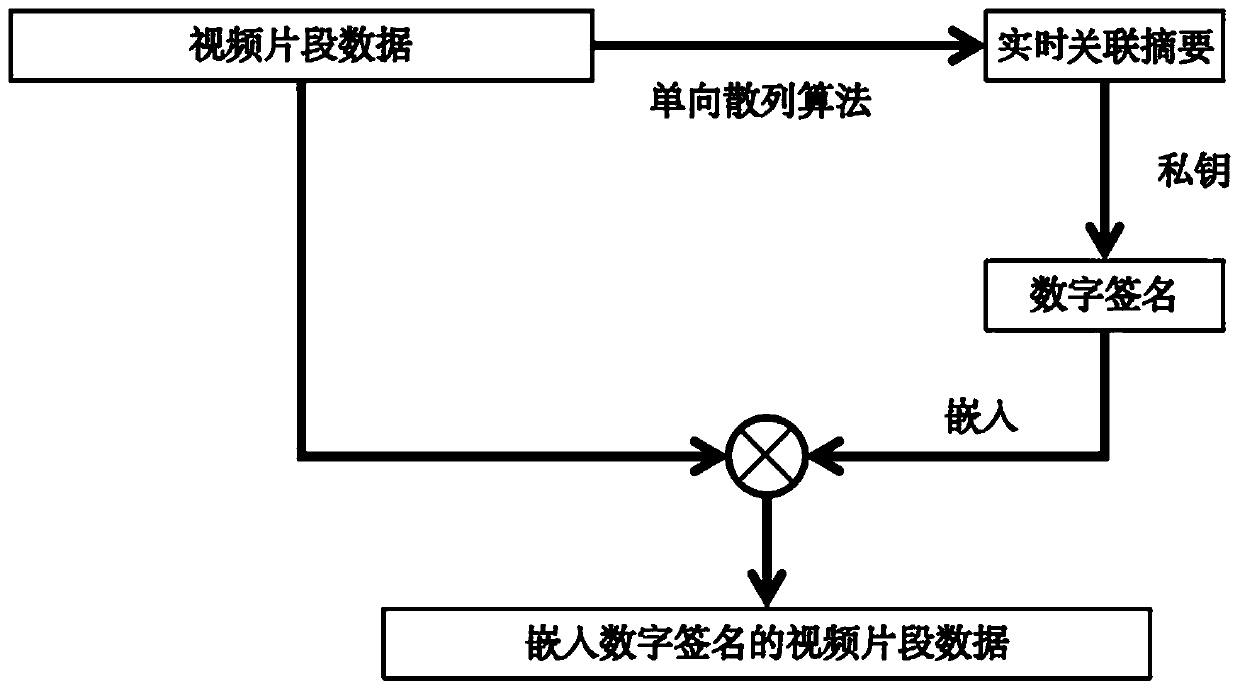
Video and audio credible playing method for generating associated abstract based on intra-frame extraction
ActiveCN110868413AReduce engineering overheadImprove trustworthinessTransmissionSelective content distributionData setData segment
The invention discloses a video and audio credible playing method for generating an associated abstract based on intra-frame extraction, and relates to the technical field of digital security. The method comprises the following steps: in the transcoding service process of the video streaming media, a publishing end extracts data segments with a certain length in each video frame of a video clip atintervals according to a set intra-frame extraction rule to form a data set corresponding to the video frame, and generates a real-time associated abstract corresponding to the video frame by using aone-way hash algorithm; the real-time associated abstract is utilized to obtain a digital signature aggregate; the client receives the video clip embedded with the digital signature assembly, and extracts the digital signature assembly and the original video clip; the digital signature assembly is decrypted to generate a receiving association abstract corresponding to the video frame;and the received associated abstract is compared with the real-time associated abstract, and a player is controlled to play the video clip content according to a comparison result. According to the method, the security policy for ensuring credible playing is transferred to the streaming media receiving end and the streaming media transmitting end from the complex intermediate network, and the engineering overhead of the security policy is reduced.
Owner:CHENGDU SOBEY DIGITAL TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com