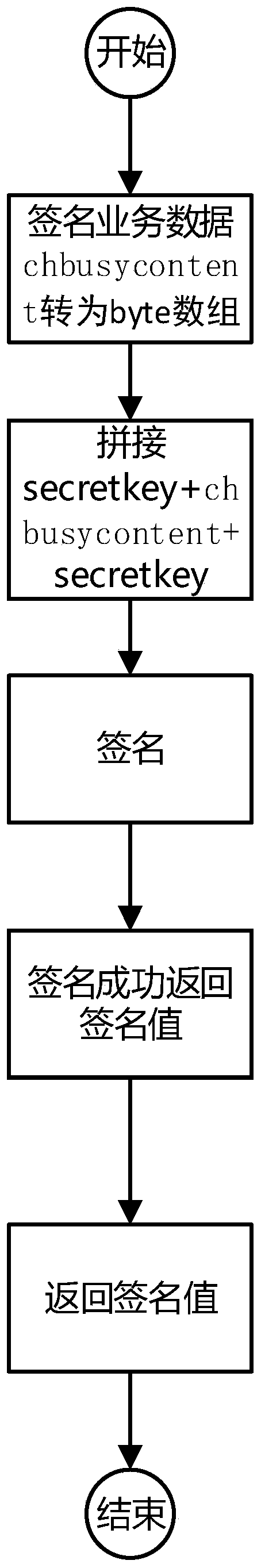
Patents
Literature
125 results about "Security design" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
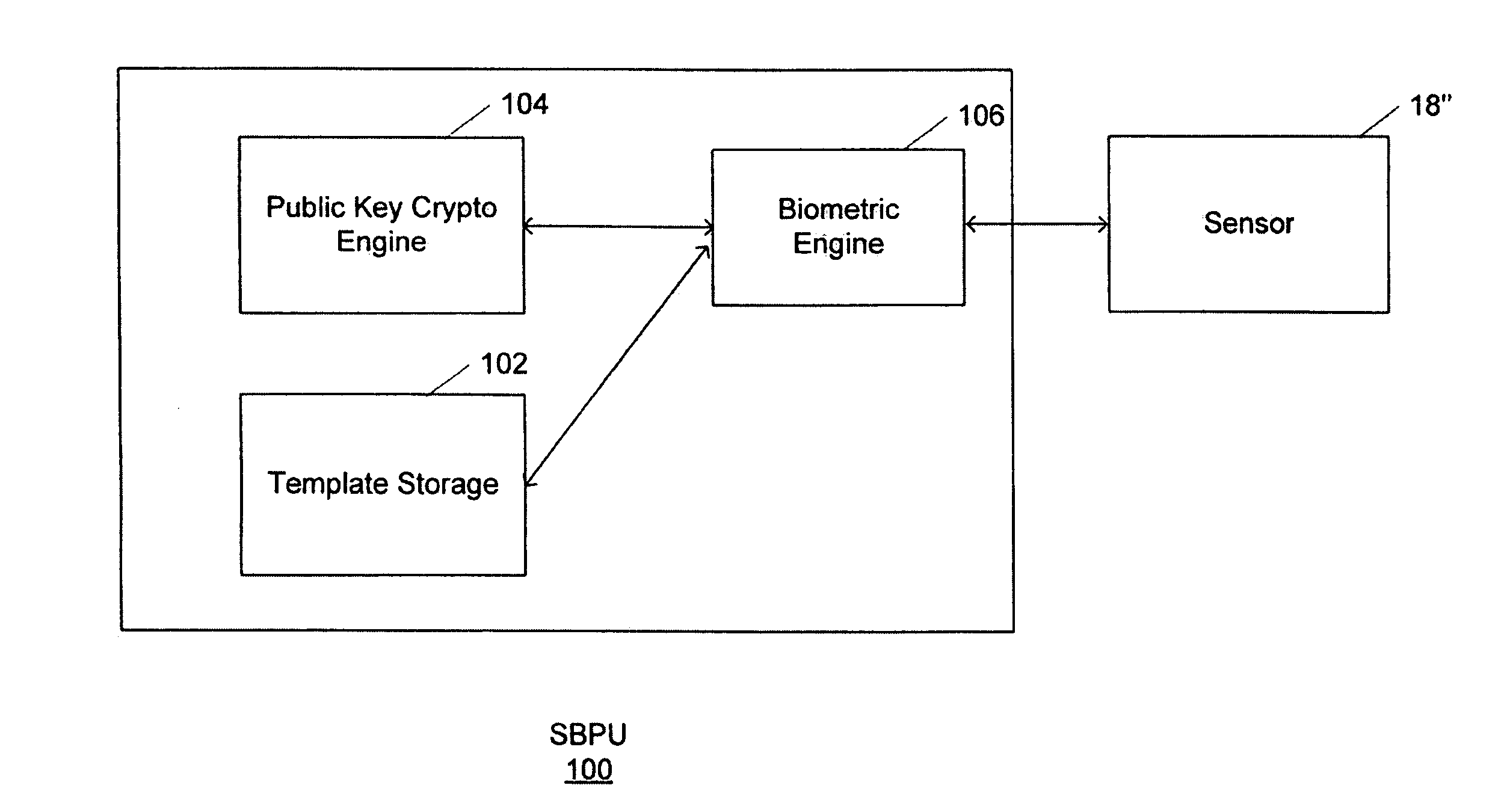
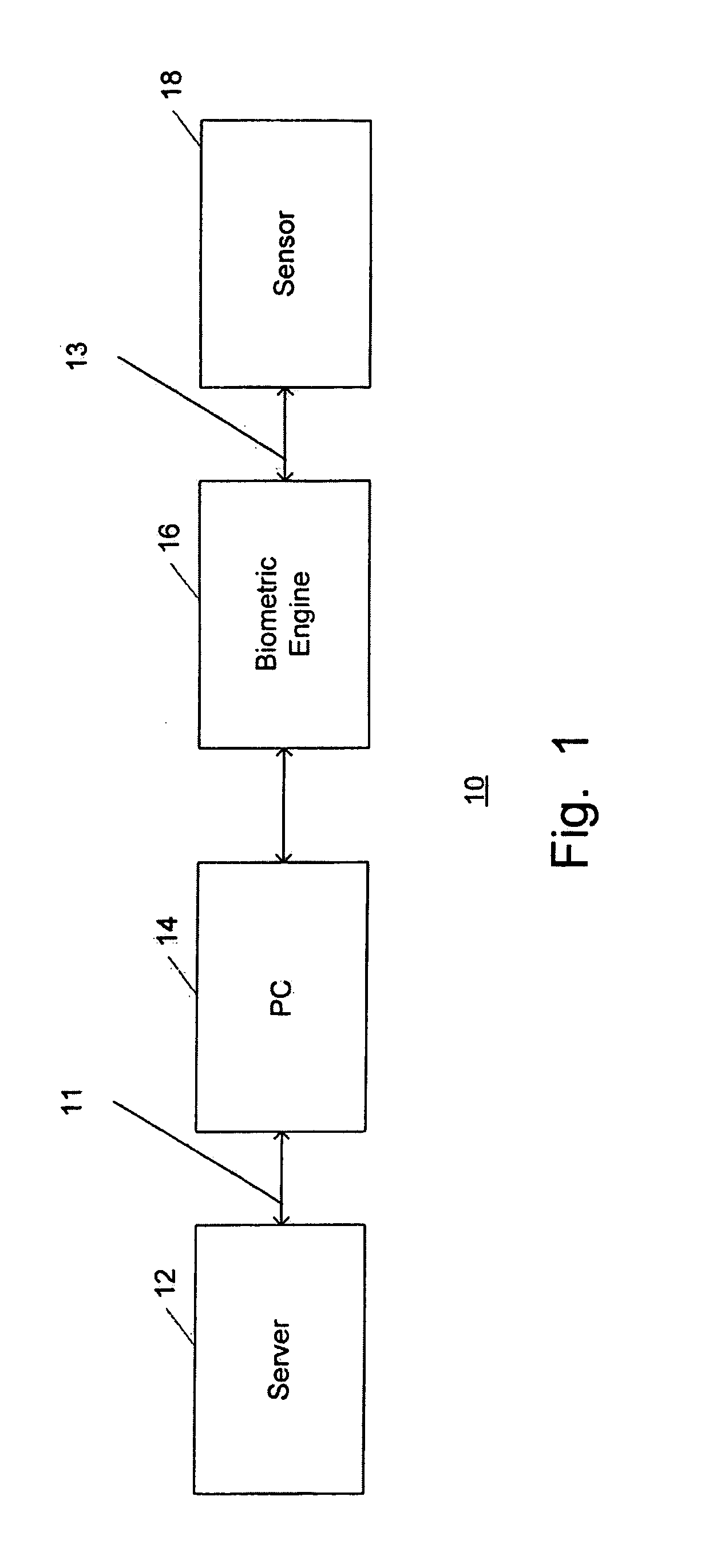
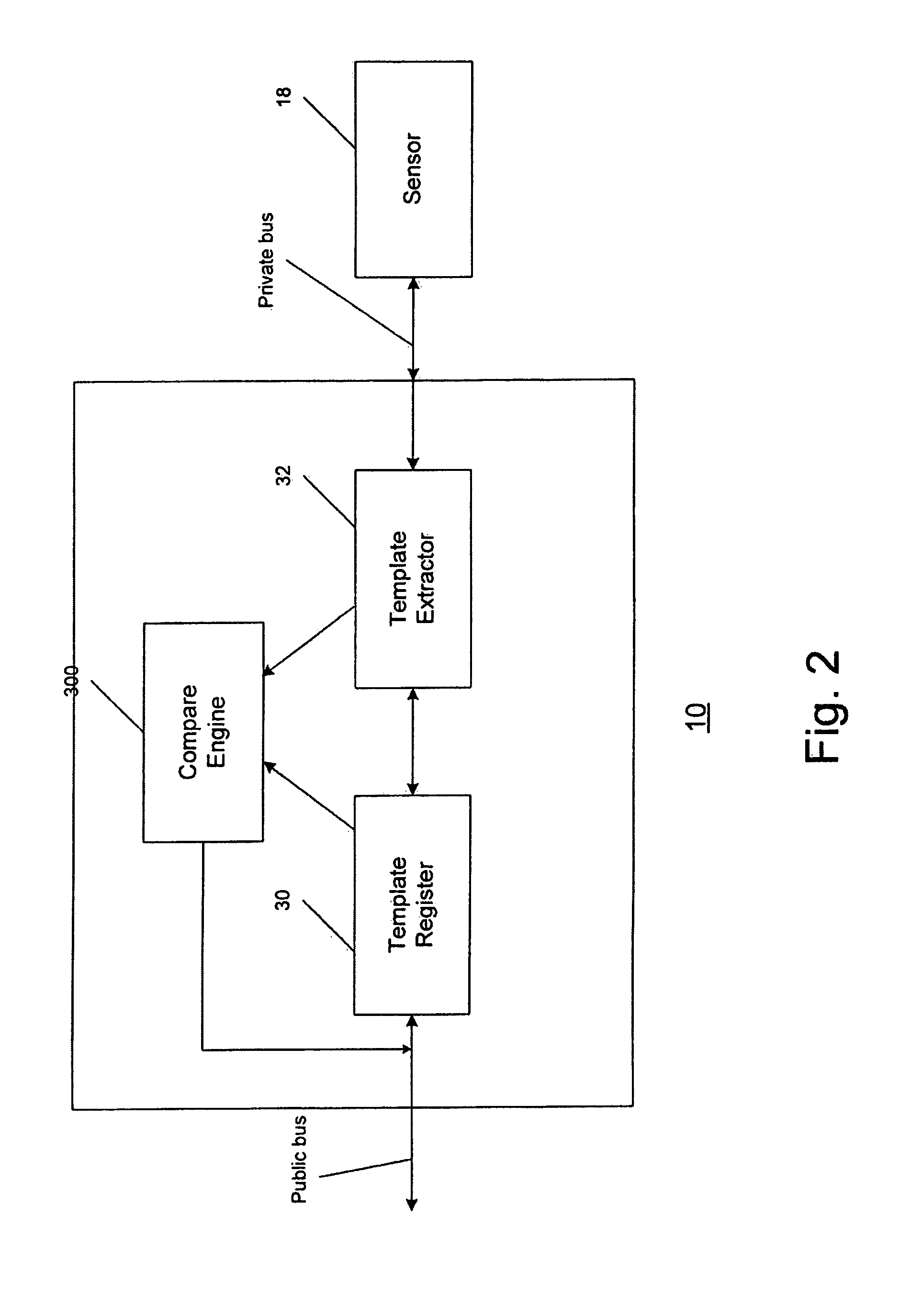
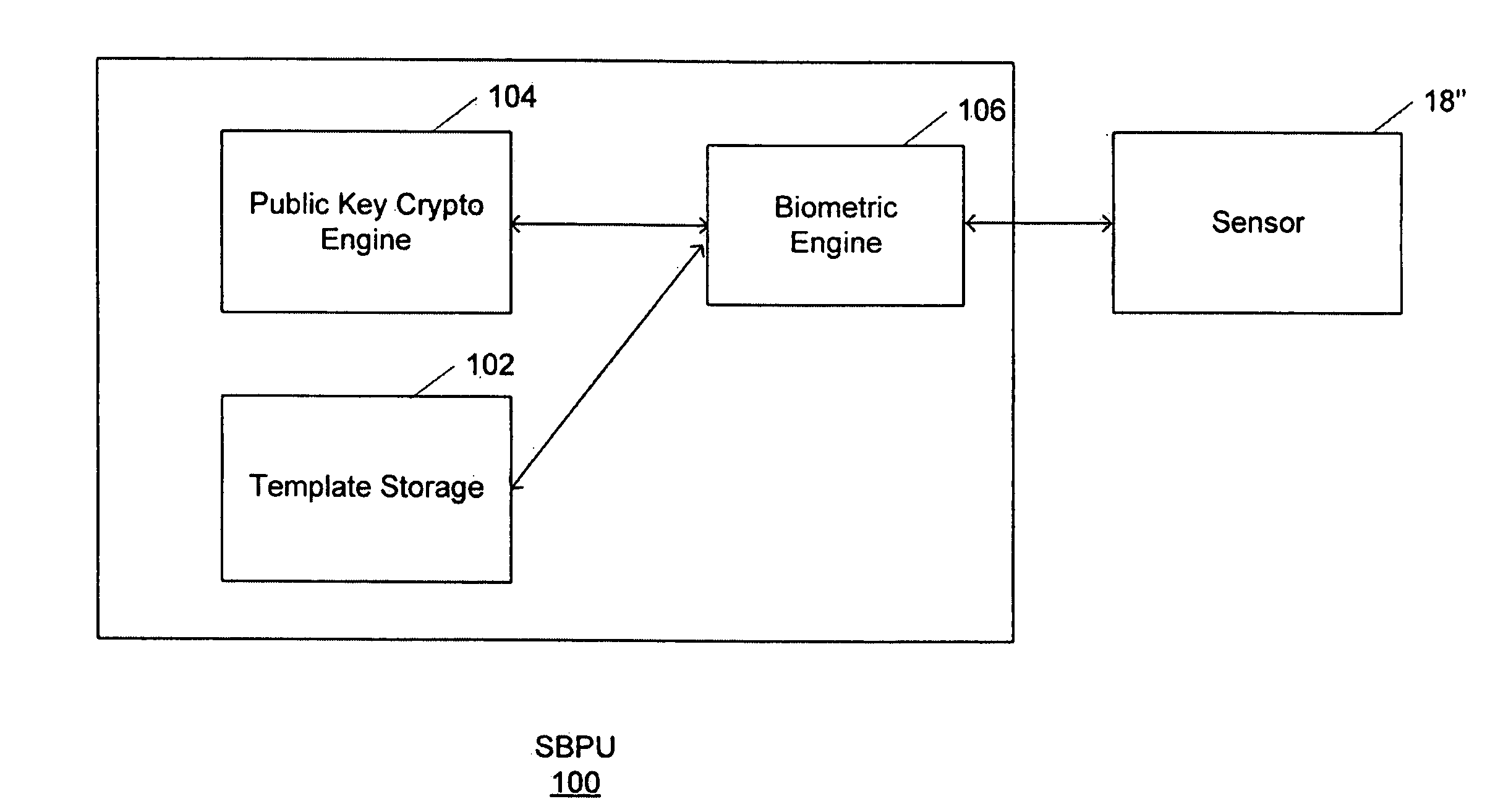
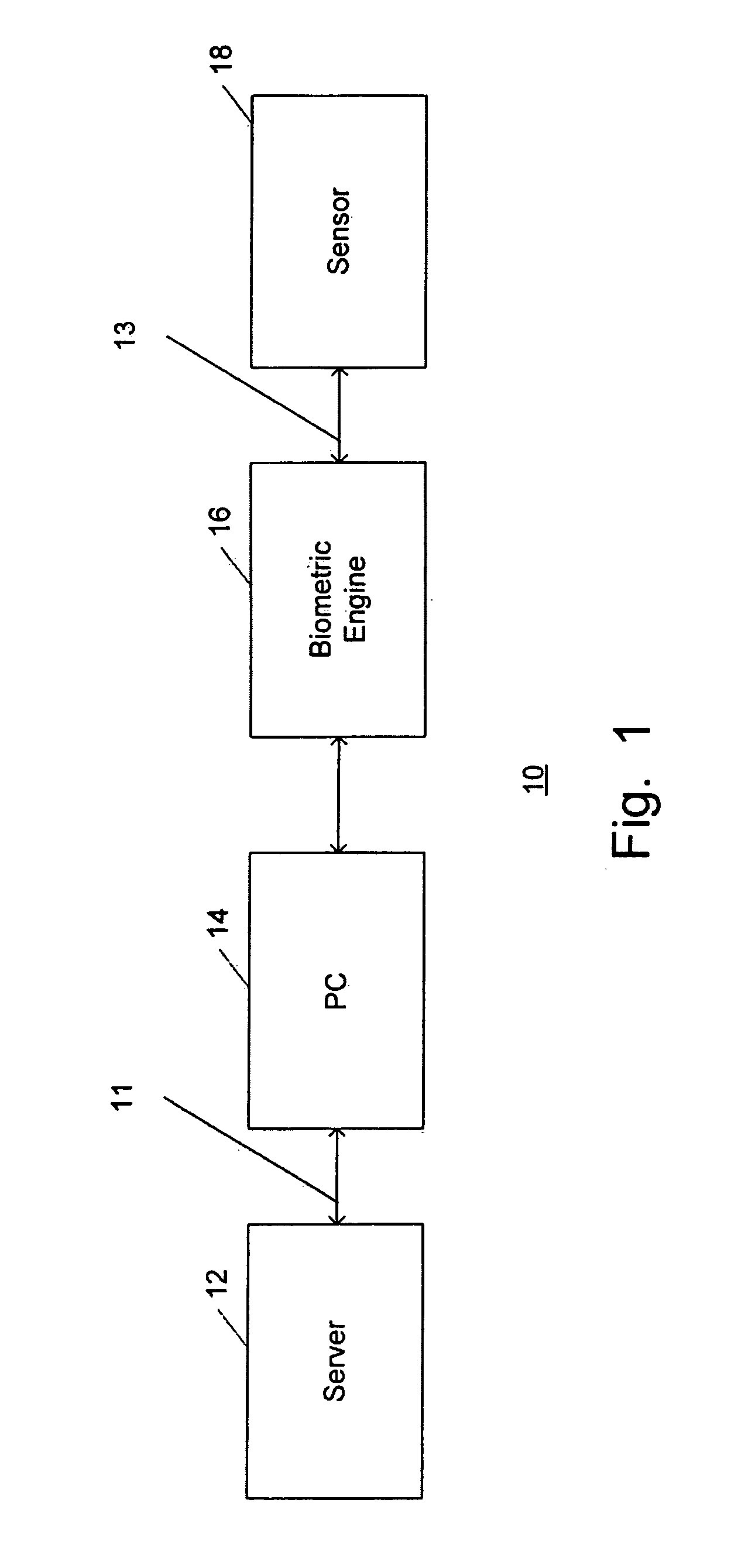
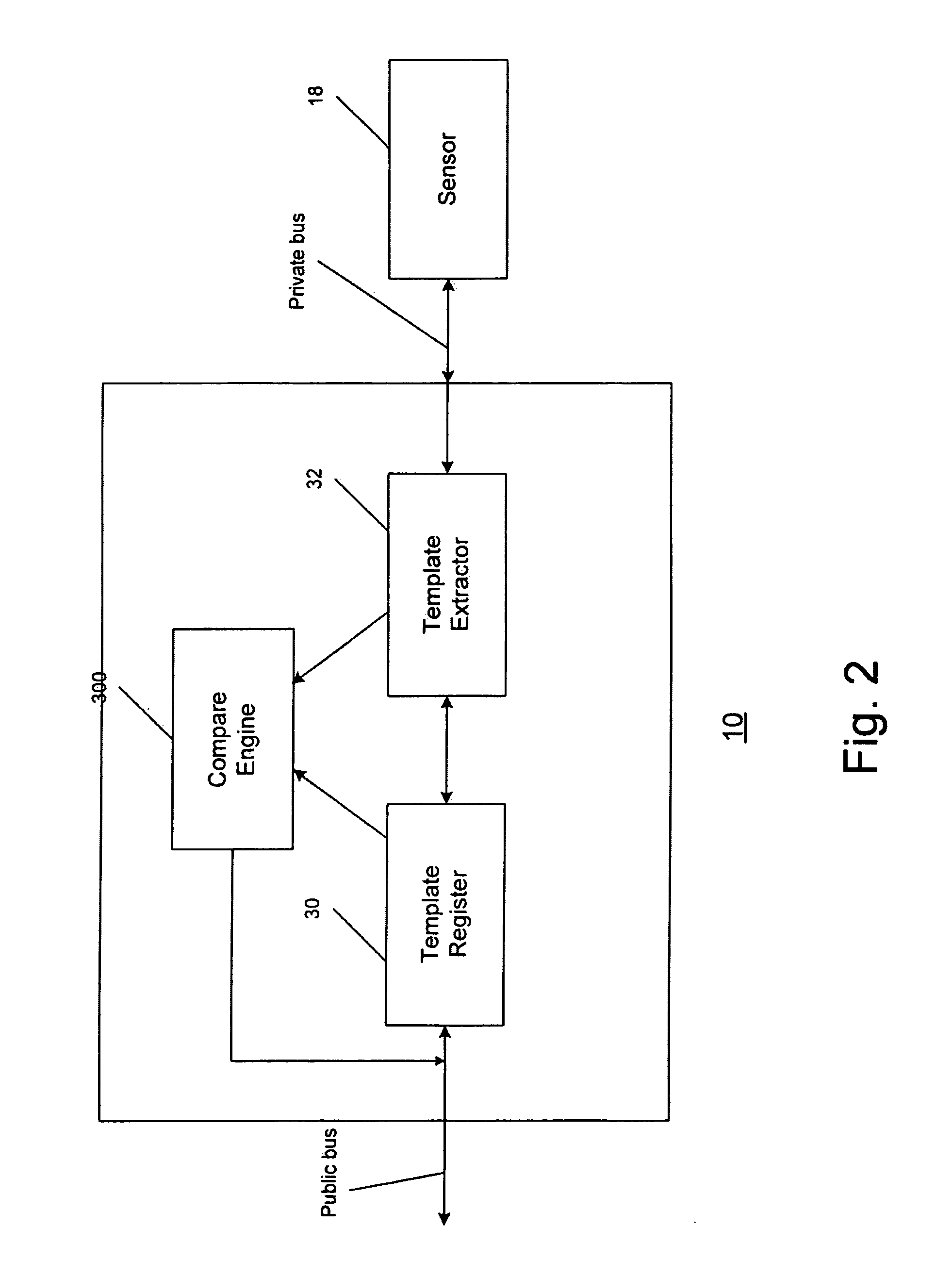
Secure biometric processing system and method of use
InactiveUS20070237366A1Programme controlElectric signal transmission systemsSecurity designHandling system
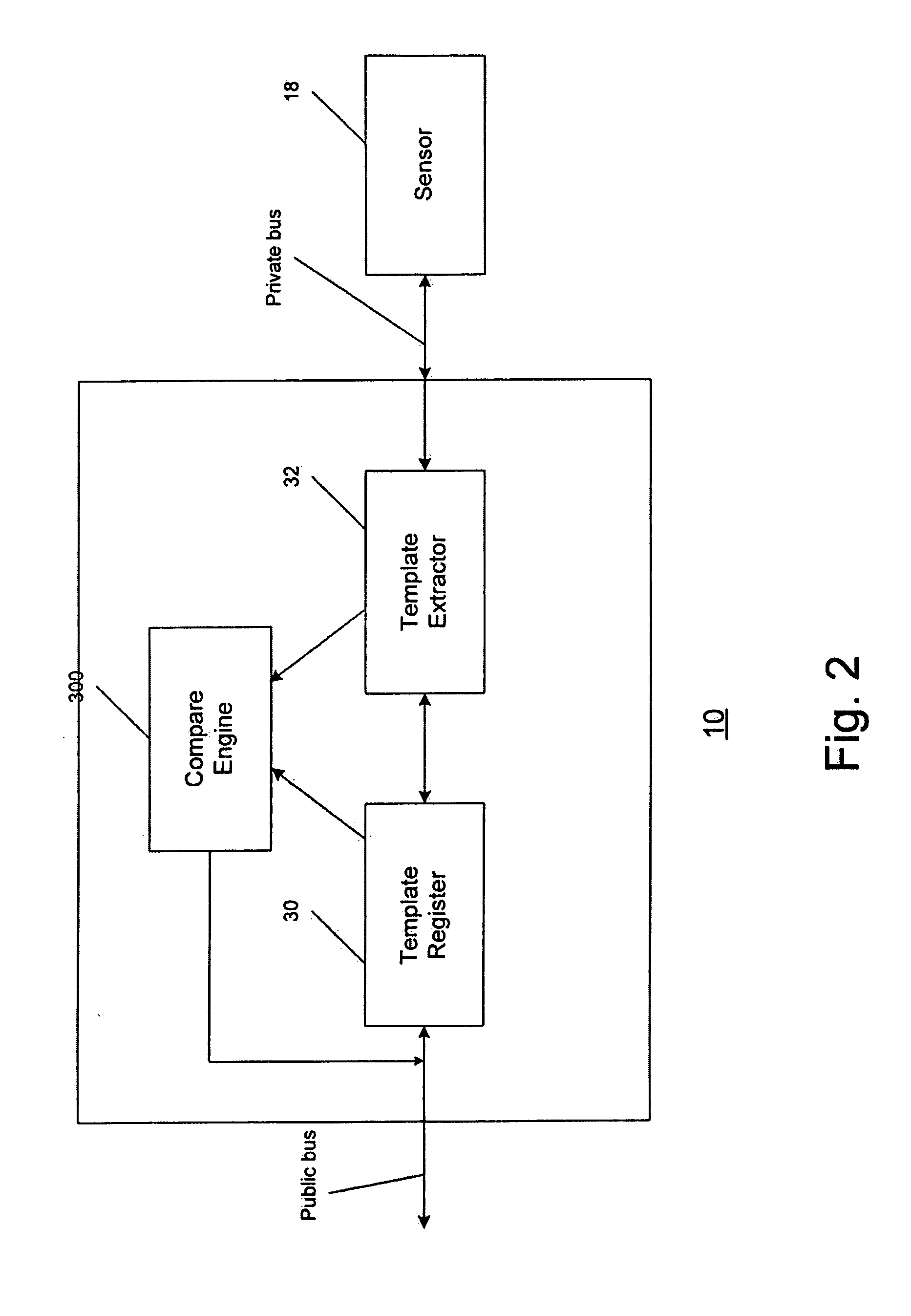
A secure biometric processing system is disclosed. The system comprises a processing system for providing image acquisition and biometric comparison. The processing unit utilizes public key cryptography for handling templates securely and authenticating operations using the template. The system includes a complete biometric engine which implements image reconstruction, template extraction and matching. The secure design of the system combines complete privacy with security, while offering a flexible usage model including on-chip template storage along with encrypted and authenticated communications to the system.
Owner:ATMEL CORP
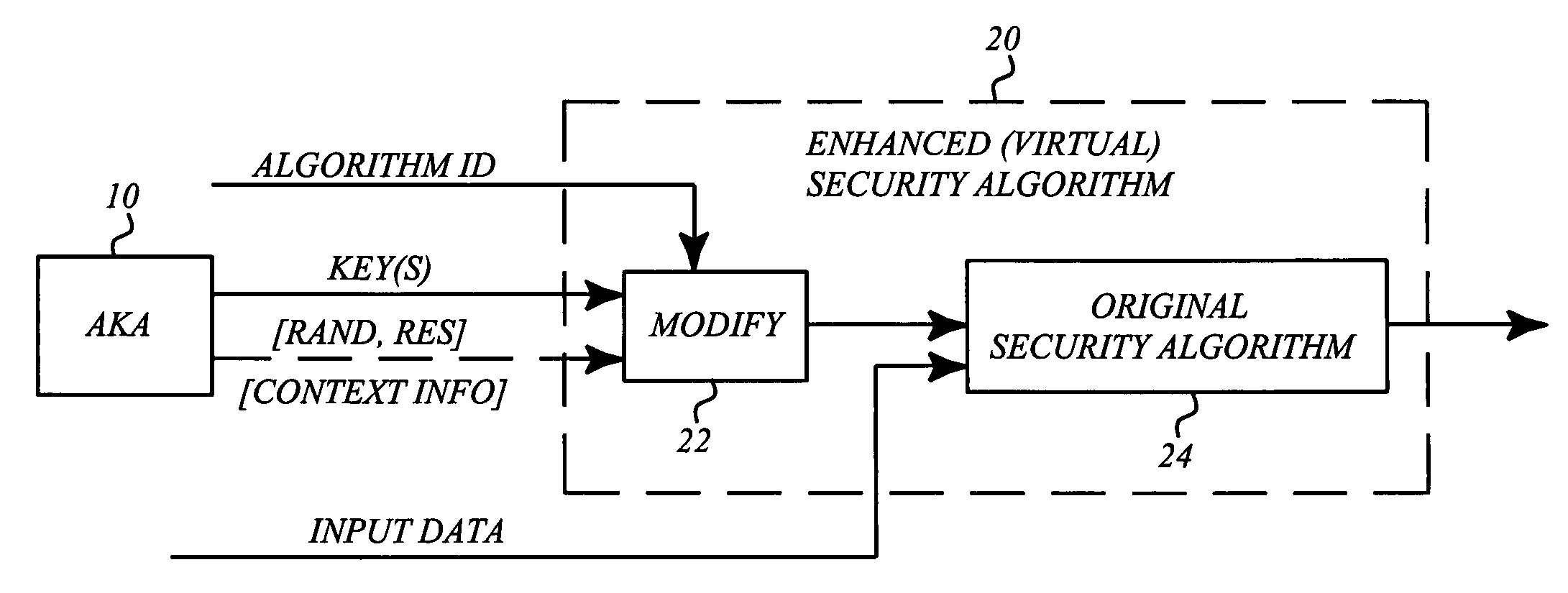
Enhanced security design for cryptography in mobile communication systems
ActiveUS20050111666A1Simple designEasy to manageKey distribution for secure communicationUser identity/authority verificationSecurity designMobile communication systems
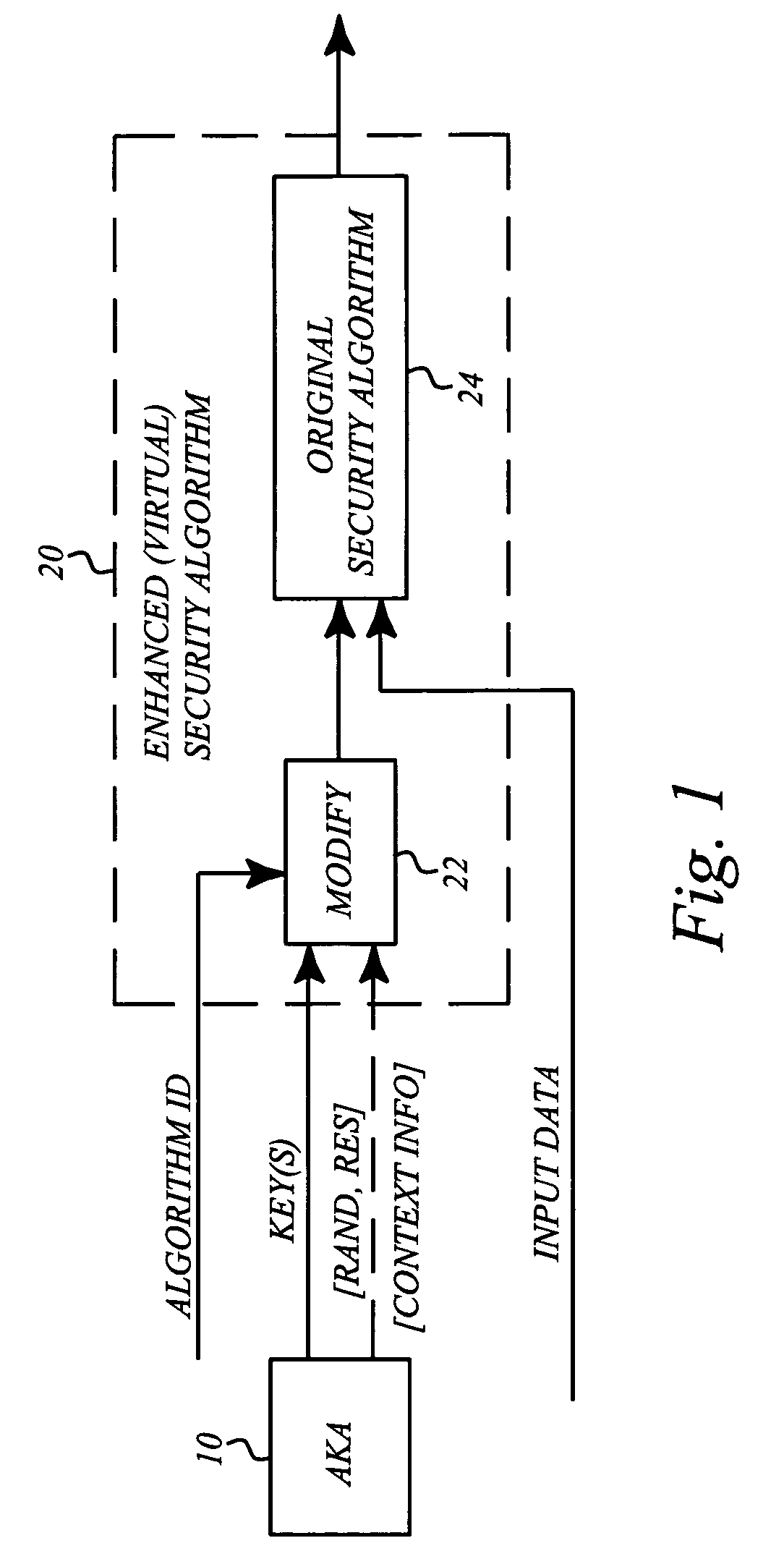
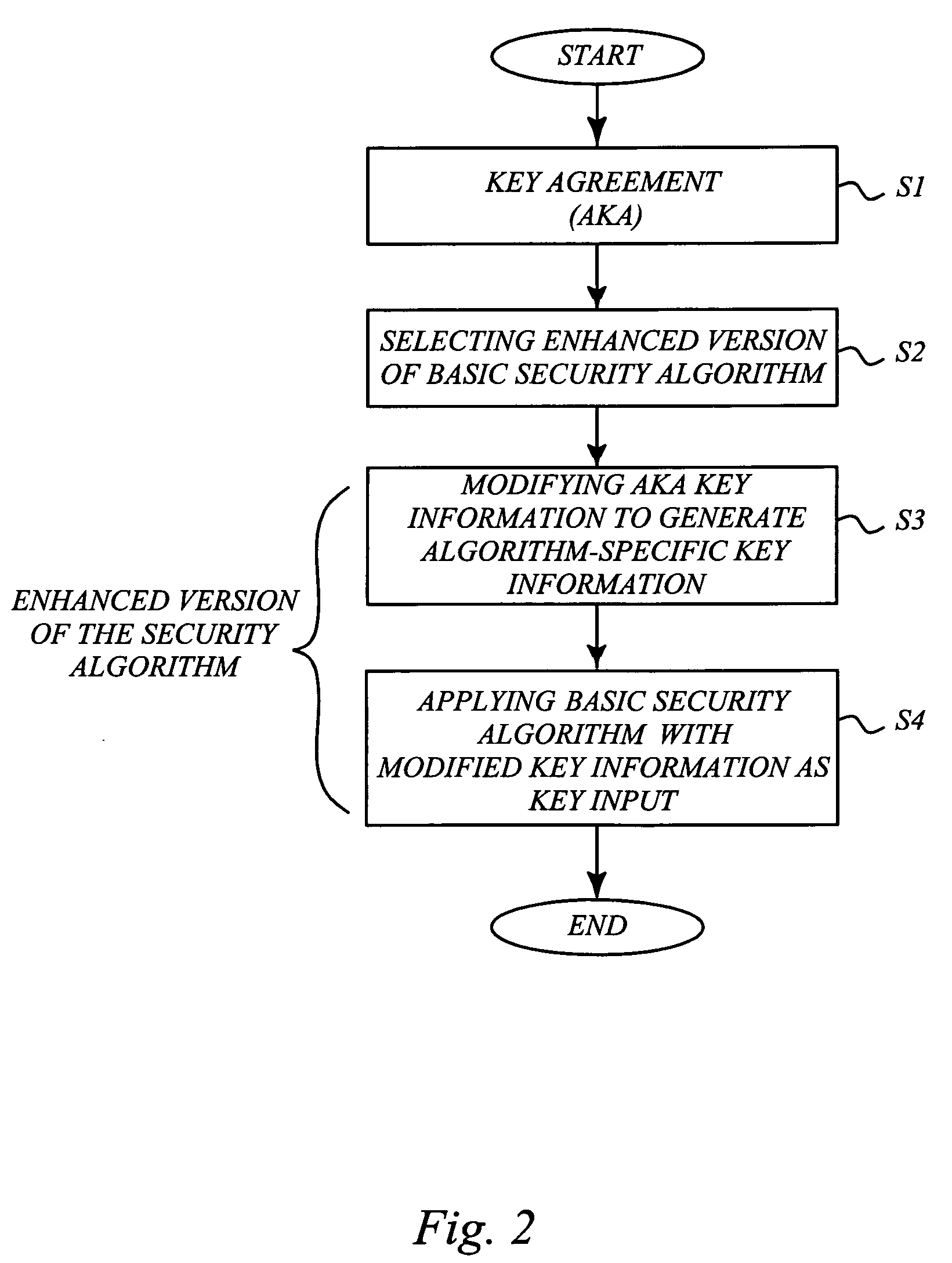
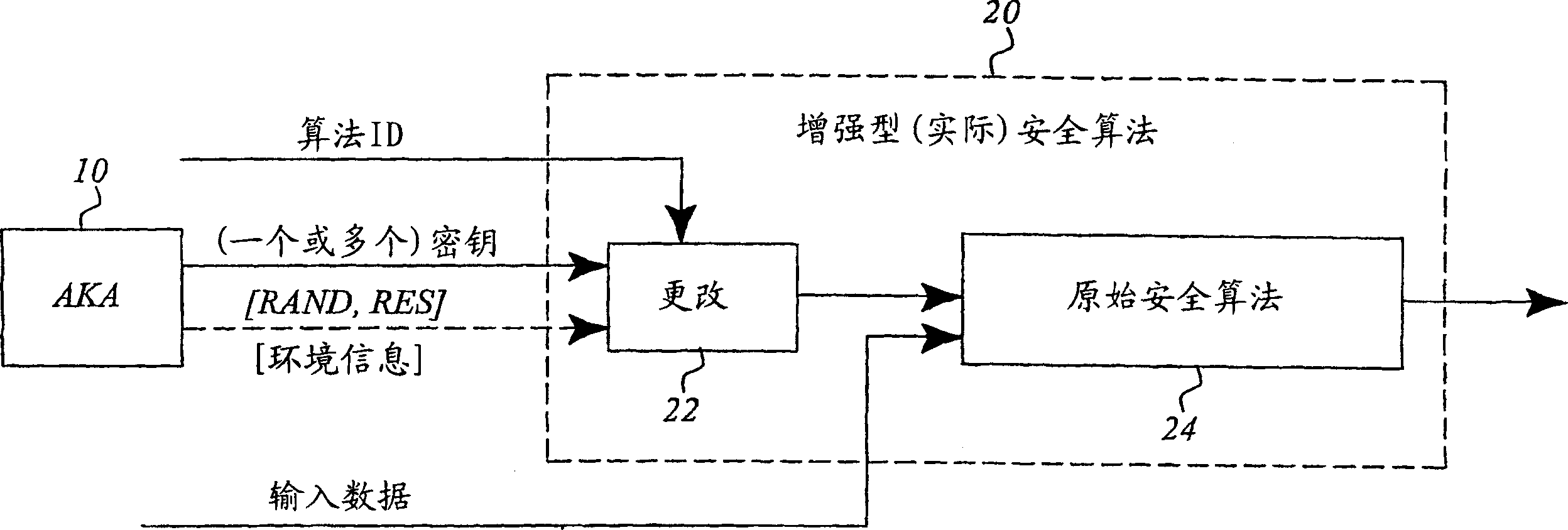
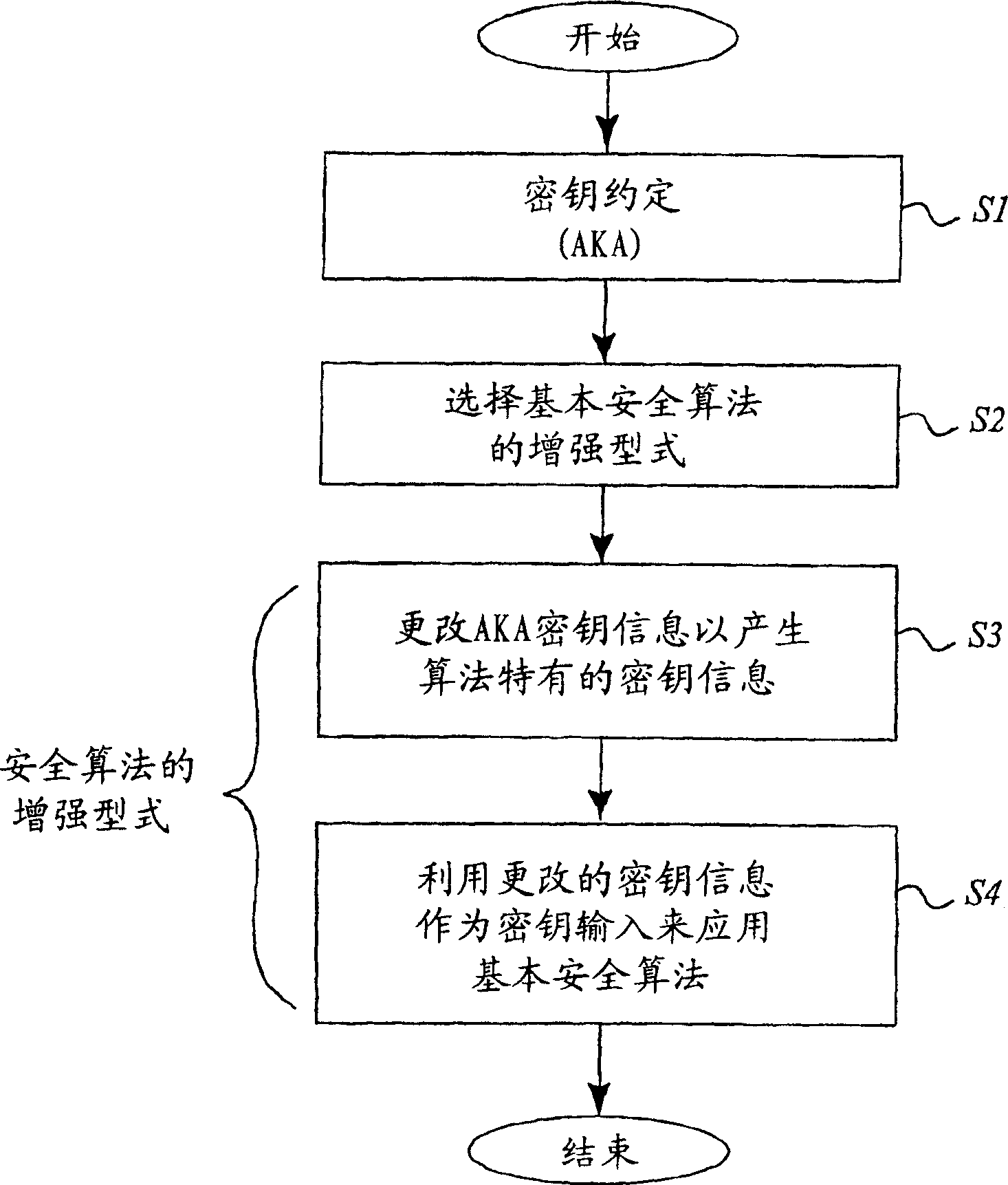
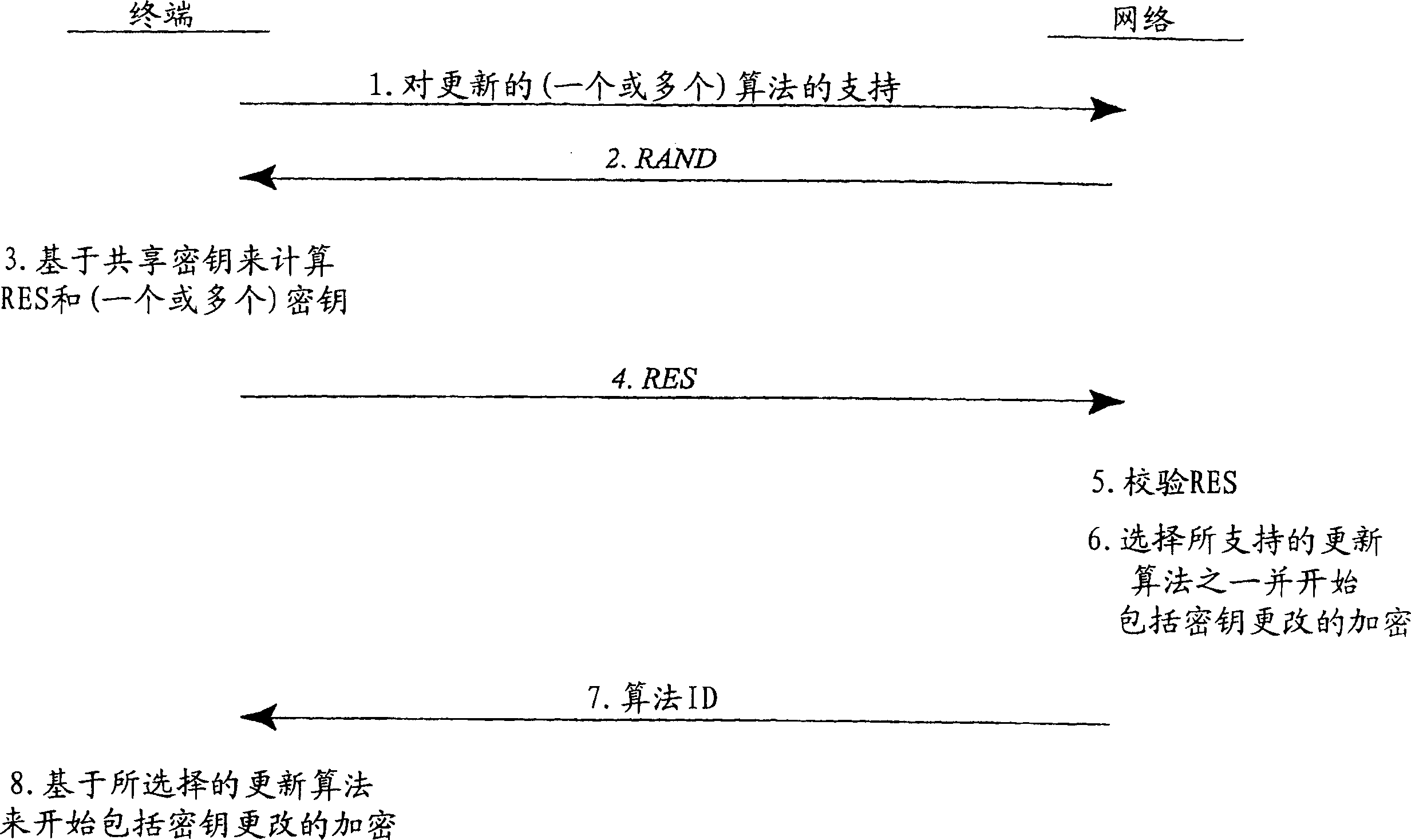
A basic idea according to the invention is to enhance or update the basic cryptographic security algorithms by an algorithm-specific modification of the security key information generated in the normal key agreement procedure of the mobile communication system. For communication with the mobile terminal, the network side normally selects an enhanced version of one of the basic cryptographic security algorithms supported by the mobile, and transmits information representative of the selected algorithm to the mobile terminal. The basic security key resulting from the key agreement procedure (AKA, 10) between the mobile terminal and the network is then modified (22) in dependence on the selected algorithm to generate an algorithm-specific security key. The basic security algorithm (24) is then applied with this algorithm-specific security key as key input to enhance security for protected communication in the mobile communications network.
Owner:TELEFON AB LM ERICSSON (PUBL)
High-temperature creep deformation prediction and creep damage analysis method for high-chrome steel component
InactiveCN106529017AAccurate predictionAchieving Precise ForecastingGeometric CADDesign optimisation/simulationSecurity designEngineering
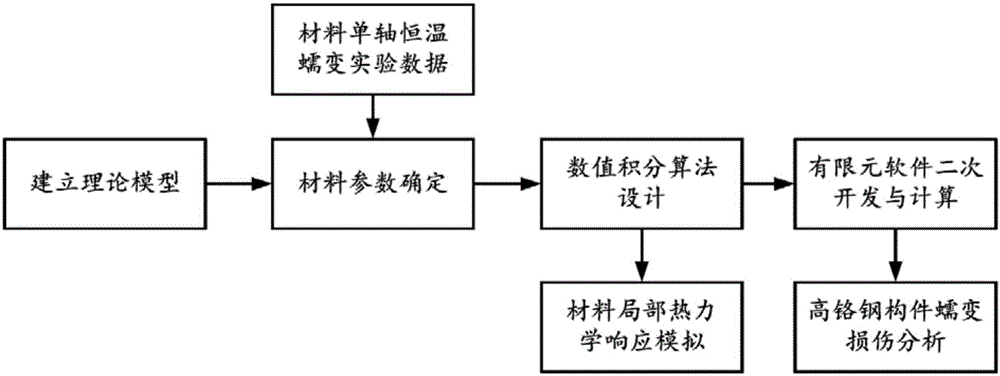
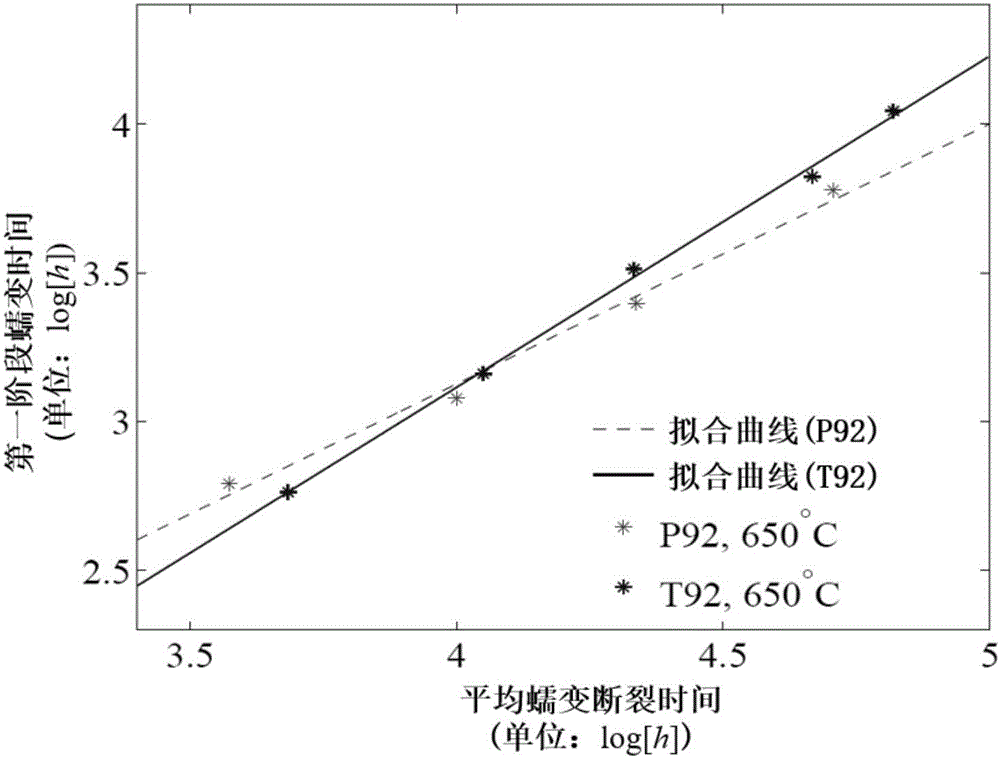
The invention discloses a high-temperature creep deformation prediction and creep damage analysis method for a high-chrome steel component. The method comprises the following steps of: establishing a theoretical model, determining material parameters, designing a numerical integration algorithm, carrying out the secondary development of finite element software, carrying out the creep damage analysis of the component and the like. Compared with an existing technical scheme, the method disclosed by the invention is characterized in that a great improvement is carried out, the accurate prediction of the creep behavior and the creep damage of the high-chrome steel component can be realized, and therefore, the method has an important application value in the fields of the security design and the residual life evaluation of high-temperature high-pressure components in a supercritical generator set.
Owner:SOUTH CHINA UNIV OF TECH
Secure biometric processing system and method of use
InactiveUS20070226514A1Internal/peripheral component protectionDigital data authenticationSecurity designImage acquisition
A secure biometric processing system is disclosed. The system comprises a processing system for providing image acquisition and biometric comparison. The processing unit utilizes public key cryptography for handling templates securely and authenticating operations using the template. The system includes a complete biometric engine which implements image reconstruction, template extraction and matching. The secure design of the system combines complete privacy with security, while offering a flexible usage model including on-chip template storage along with encrypted and authenticated communications to the system.
Owner:ATMEL CORP
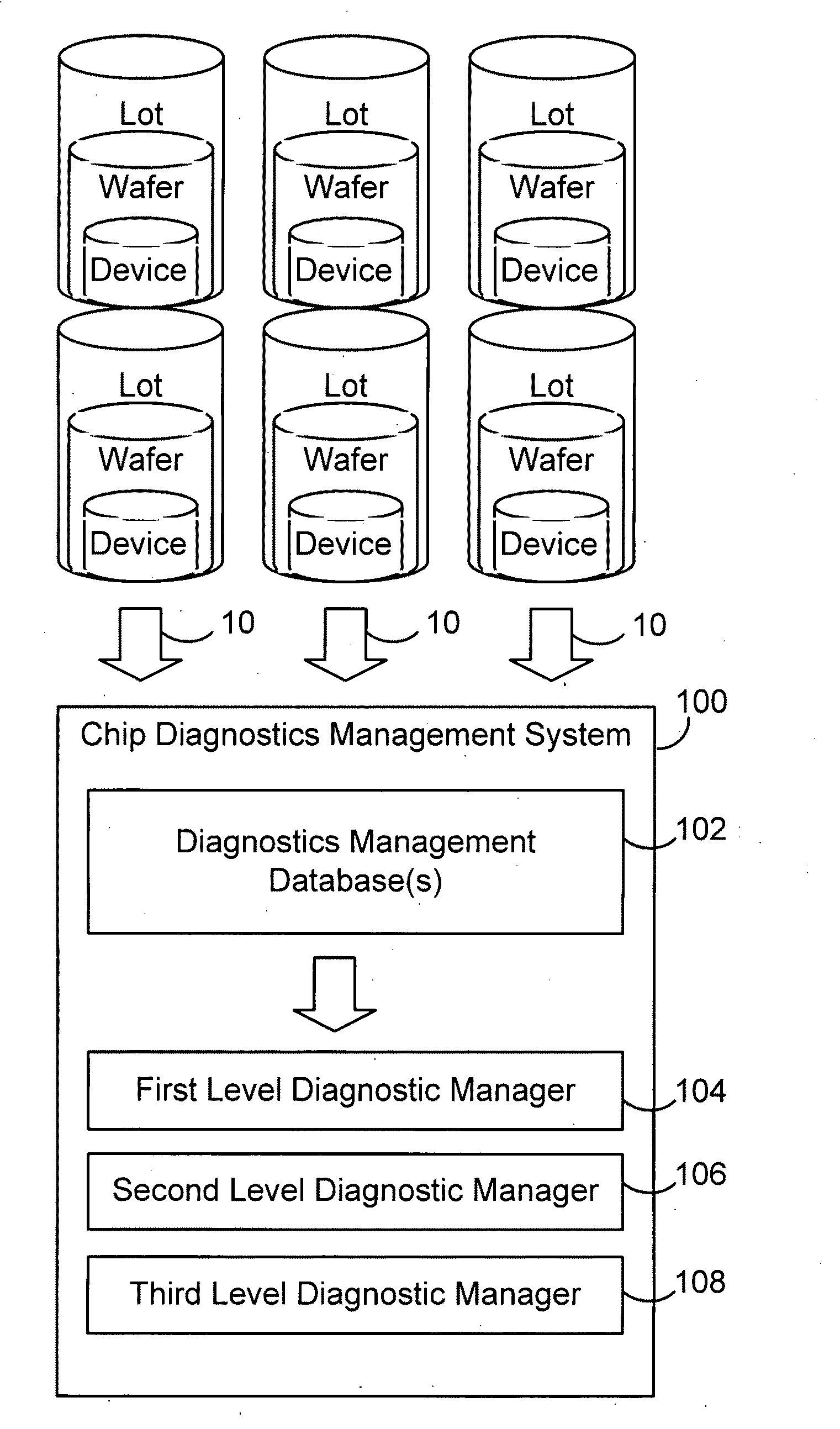
Secure test-for-yield chip diagnostics management system and method
ActiveUS20100332172A1Quick discoveryElectrical testingSpecial data processing applicationsSecurity designDiagnosis management
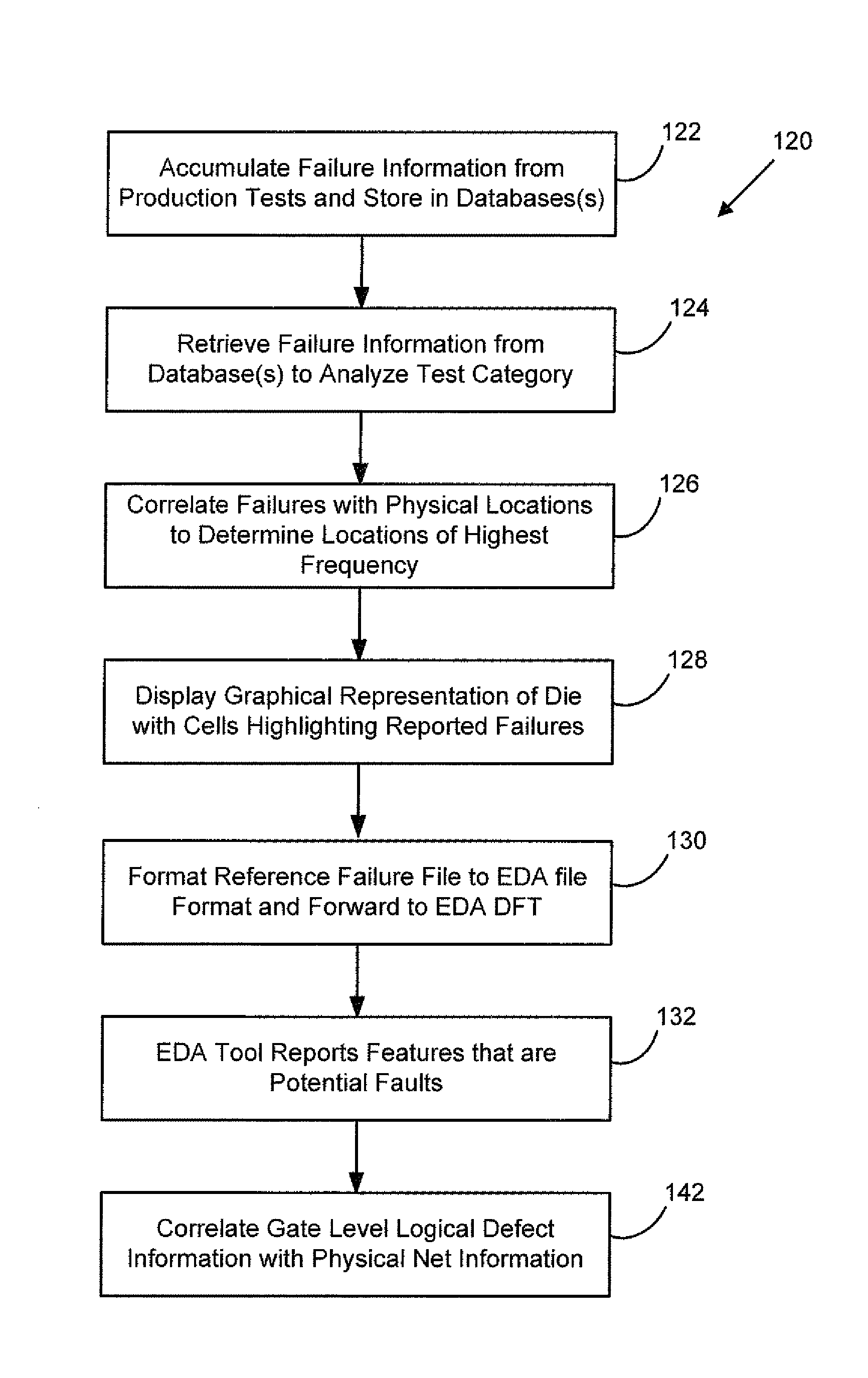
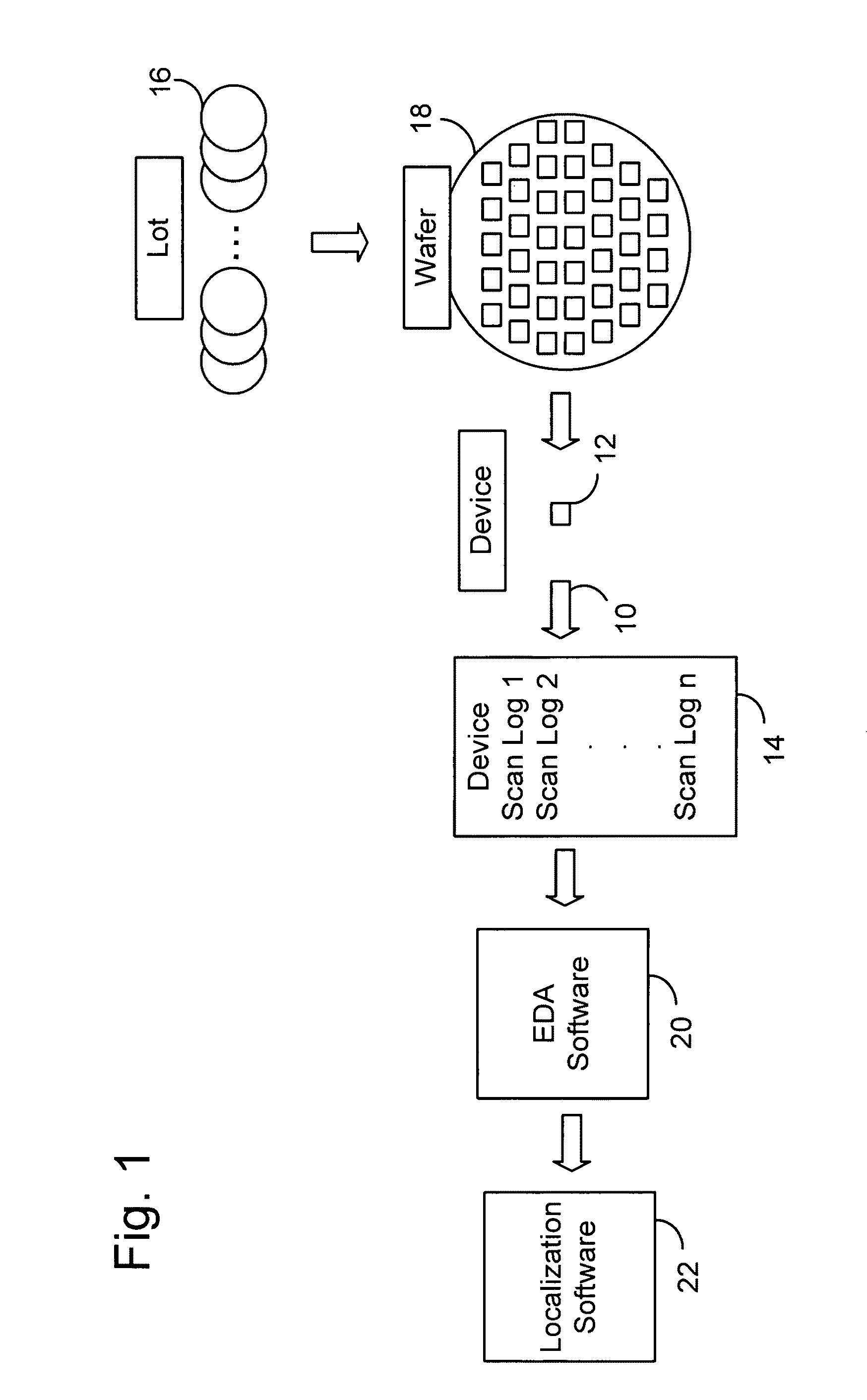
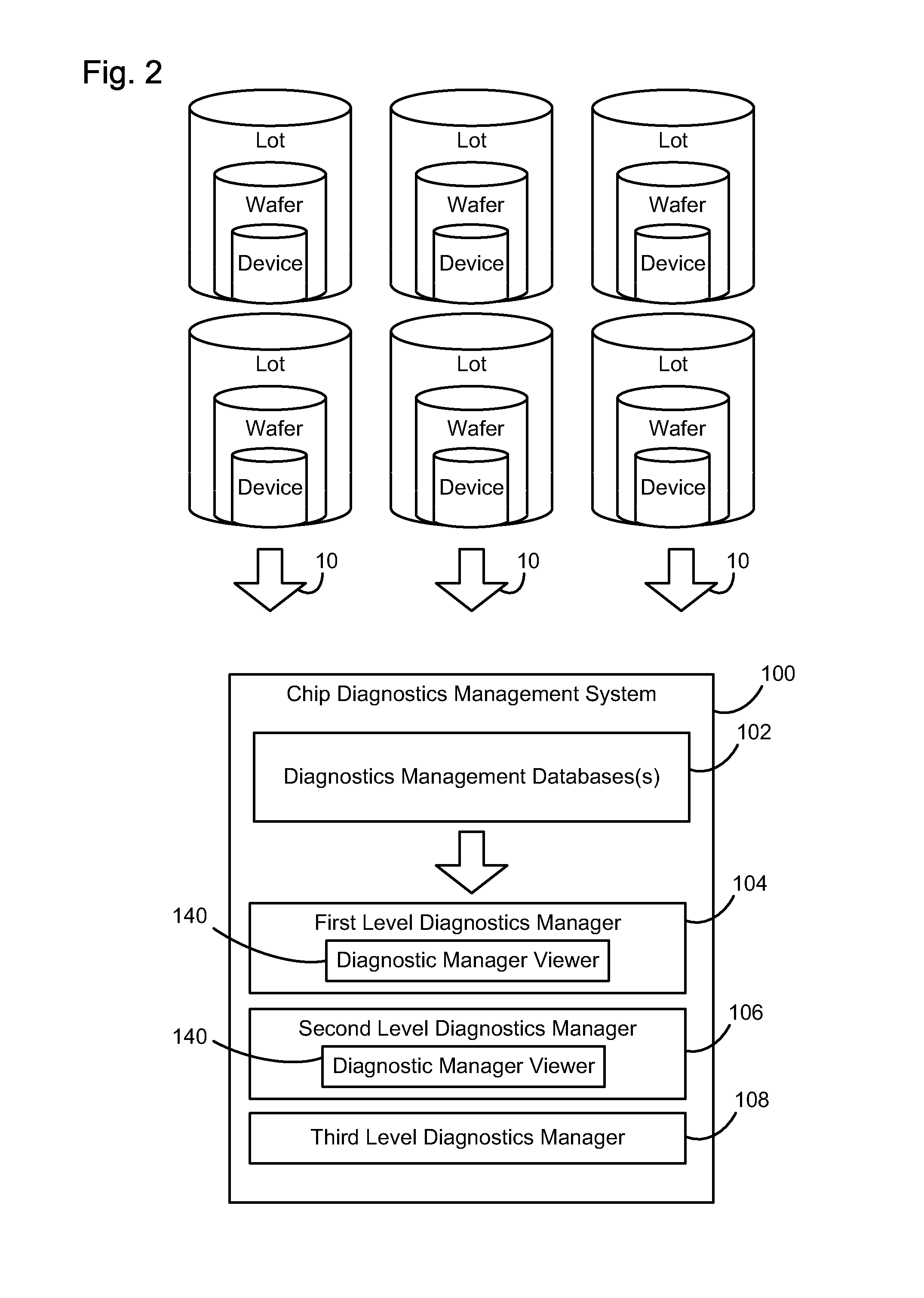
A chip diagnostics management system includes secure design information that define production features of integrated circuit devices and are accessible according to selected levels of access privilege. A database of device defect information includes information of defects of devices produced according to the production features of the design information and associated wafers, production lots, and dies in or with which the devices were produced. A diagnostic manager correlates device defect information from plural wafers with the design information to identify a device location with a probability of being associated with the device defect information. A diagnostic manager viewer indicates the device location together with an amount of design information correlated the level of access privilege assigned to a selected user.
Owner:TESEDA CORP
Secure cloud control method and system
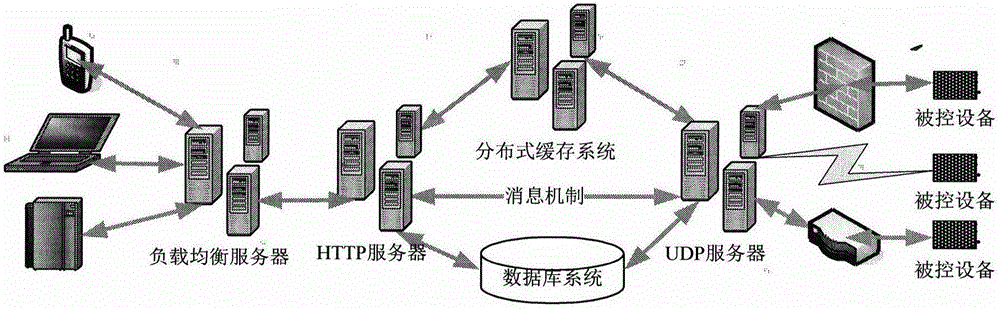
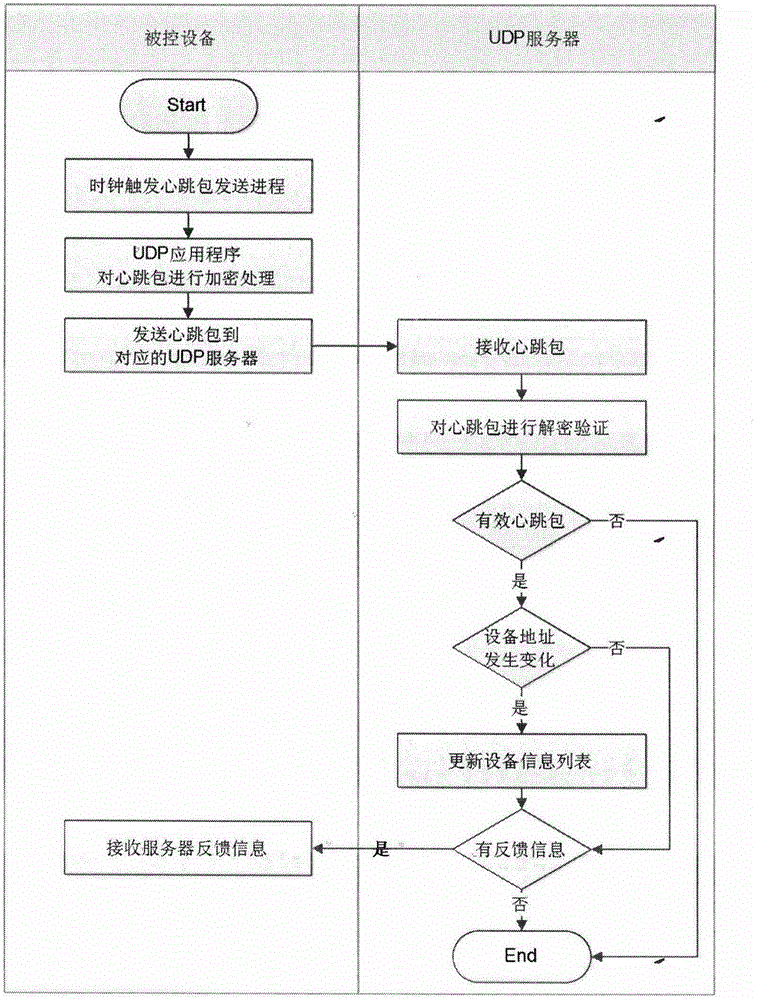
The invention discloses a secure cloud control method and system. Based on a UDP (user datagram protocol) with low network overhead, communication design is performed, user configurable strategies are used for security design, various encryption algorithms are preset at a could and a controlled device, a user can perform configuration according to application requirements, a cloud server is set up by the aid of high concurrency technology, and the requirements of large-scale internet of things application and particularly intelligent home popularization for cloud control convenience, security and high concurrency are met.
Owner:谢杰涛
Cloud computing-based network invoicing method by using mobile phone
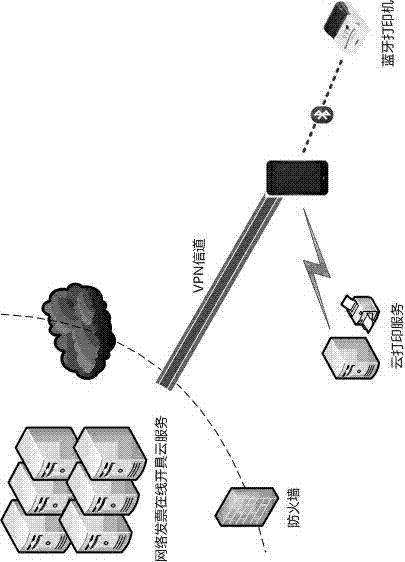
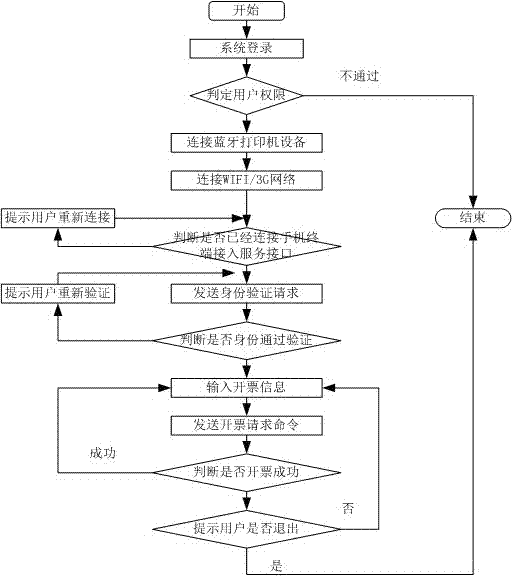
The invention discloses a cloud computing-based network invoicing method by using a mobile phone, and belongs to the field of cloud application. The method is characterized by comprising the following steps of: establishing an access service interface for a terminal of the mobile phone at a cloud end; receiving a network invoice business data package sent from the terminal of the mobile phone through a link layer protocol, a data transmission protocol and a security design negotiated with the terminal of the mobile phone; analyzing a communication protocol command and business data of the package, and responding and returning a processing result; and carrying out physical invoice printing through a bonded printer after the terminal of the mobile phone receives a response of the business data so as to finish the operation of the network invoicing. Compared with the prior art, the method disclosed by the invention fully utilizes the characteristics (the application is wide, the cost is low, the carry is easy, and the like) of a terminal device of the mobile phone, so that a safe and reliable mobile network invoicing method is provided for tax payers.
Owner:INSPUR QILU SOFTWARE IND
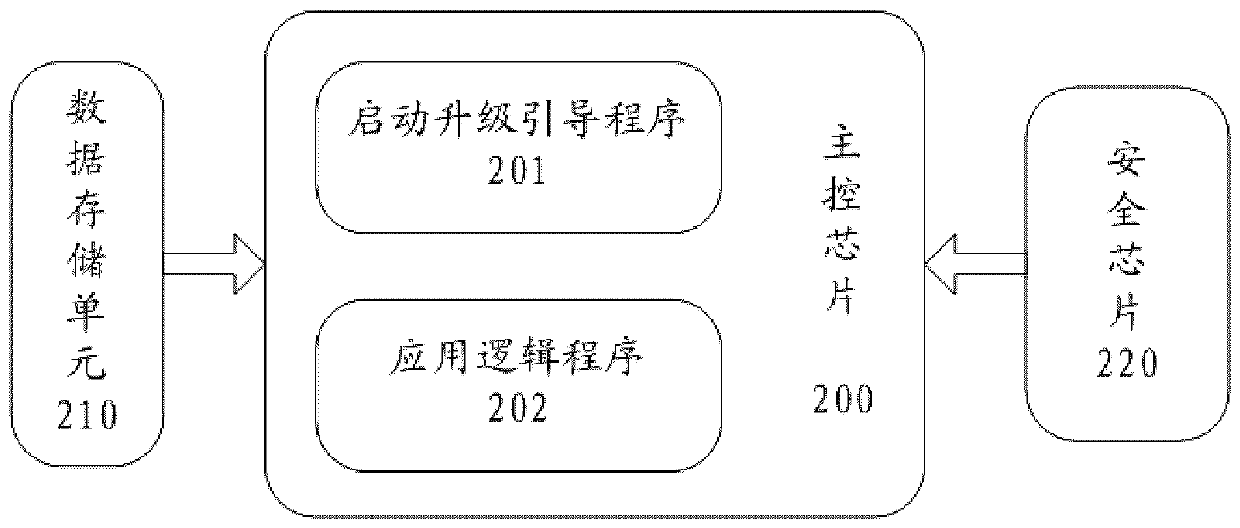
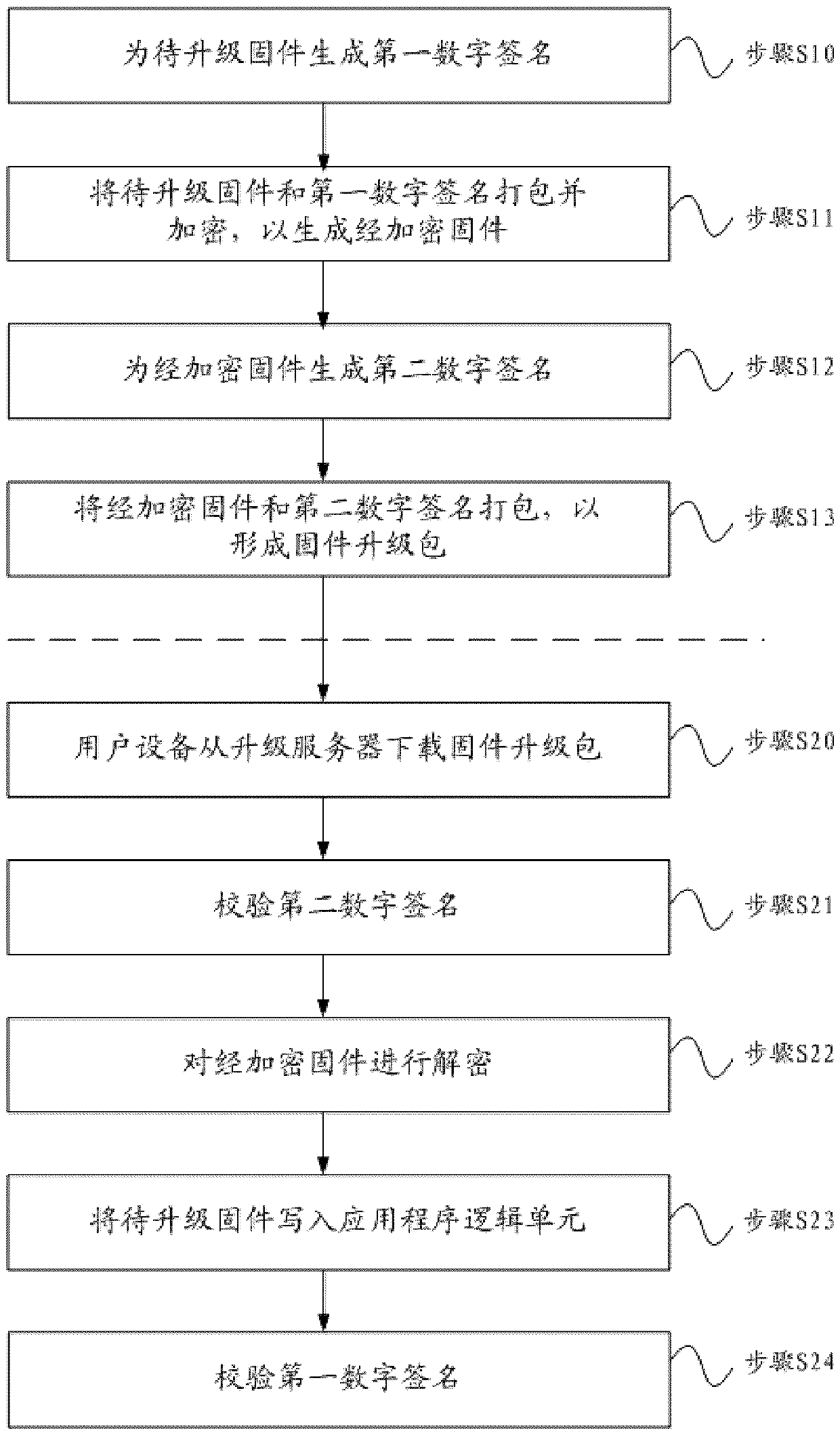
Firmware upgrading method
ActiveCN110532735AGuaranteed uptimeAvoid security risksDigital data authenticationPlatform integrity maintainanceDigital signatureSecurity design
The invention relates to a firmware upgrading method, which comprises the following steps that: user equipment establishes secure connection with an upgrading server, and downloads a firmware upgrading packet through an encryption channel to obtain encrypted firmware and a second digital signature; the second digital signature is verified to verify the integrity and / or legality of the encrypted firmware; the encrypted firmware is decrypted by using a decryption algorithm to obtain to-be-upgraded firmware and a first digital signature; the user equipment writes the firmware to be upgraded intothe application logic program unit; and the user equipment verifies the first digital signature to verify the integrity and legality of the firmware to be upgraded. According to the method, integral security design is carried out on all process links of firmware upgrading, and security risks existing in each link can be effectively prevented.
Owner:HONEYWELL ENVIRONMENTAL & COMBUSTION CONTROLS (TIANJIN) CO LTD
Cooperative editing system and method for document based on centralized data control
InactiveCN107273343AImprove access rateSpeed upNatural language data processingOffice automationData controlData synchronization
Owner:BEIJING INST OF COMP TECH & APPL
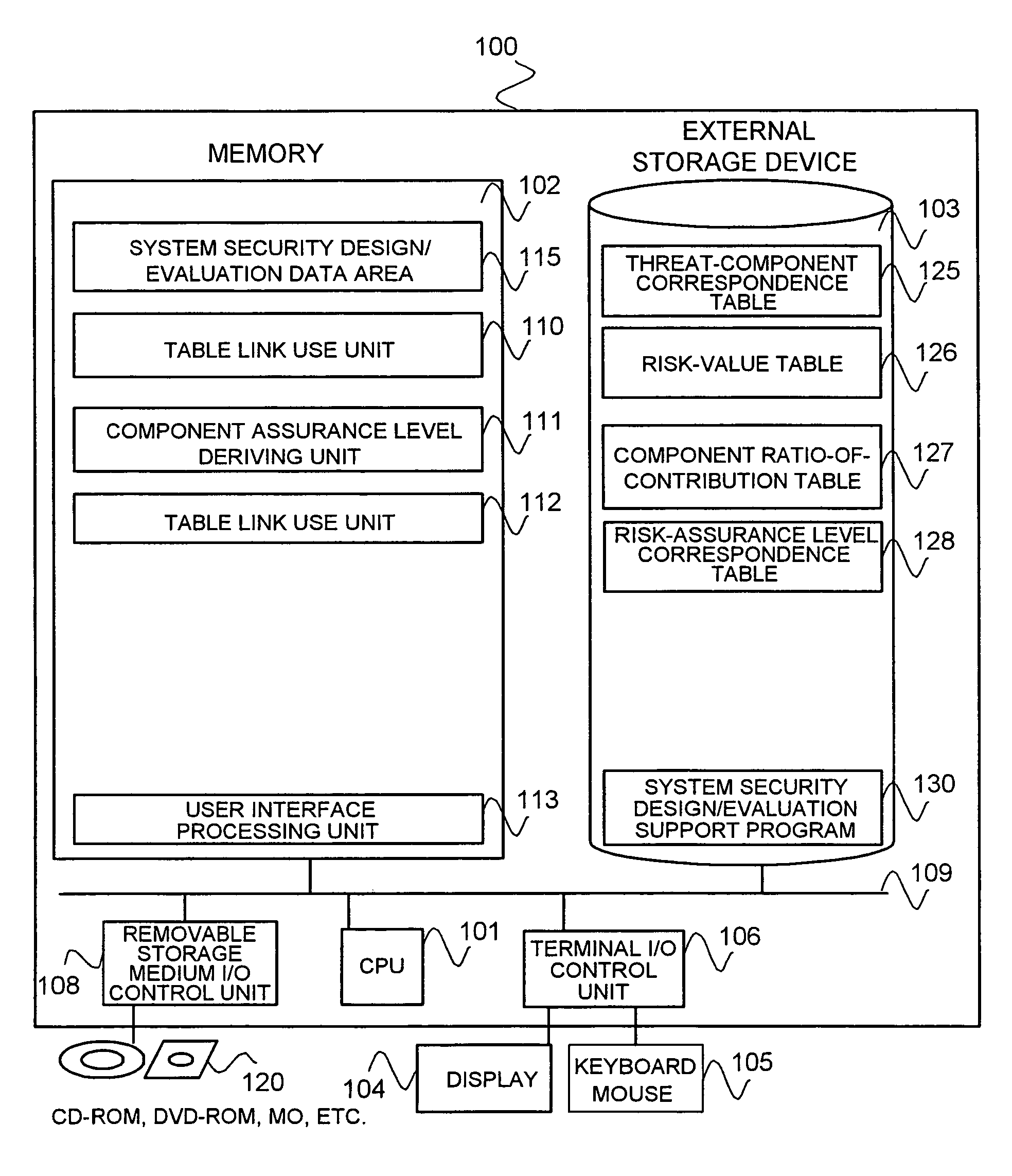
Tool, method, and program for supporting system security design/evaluation
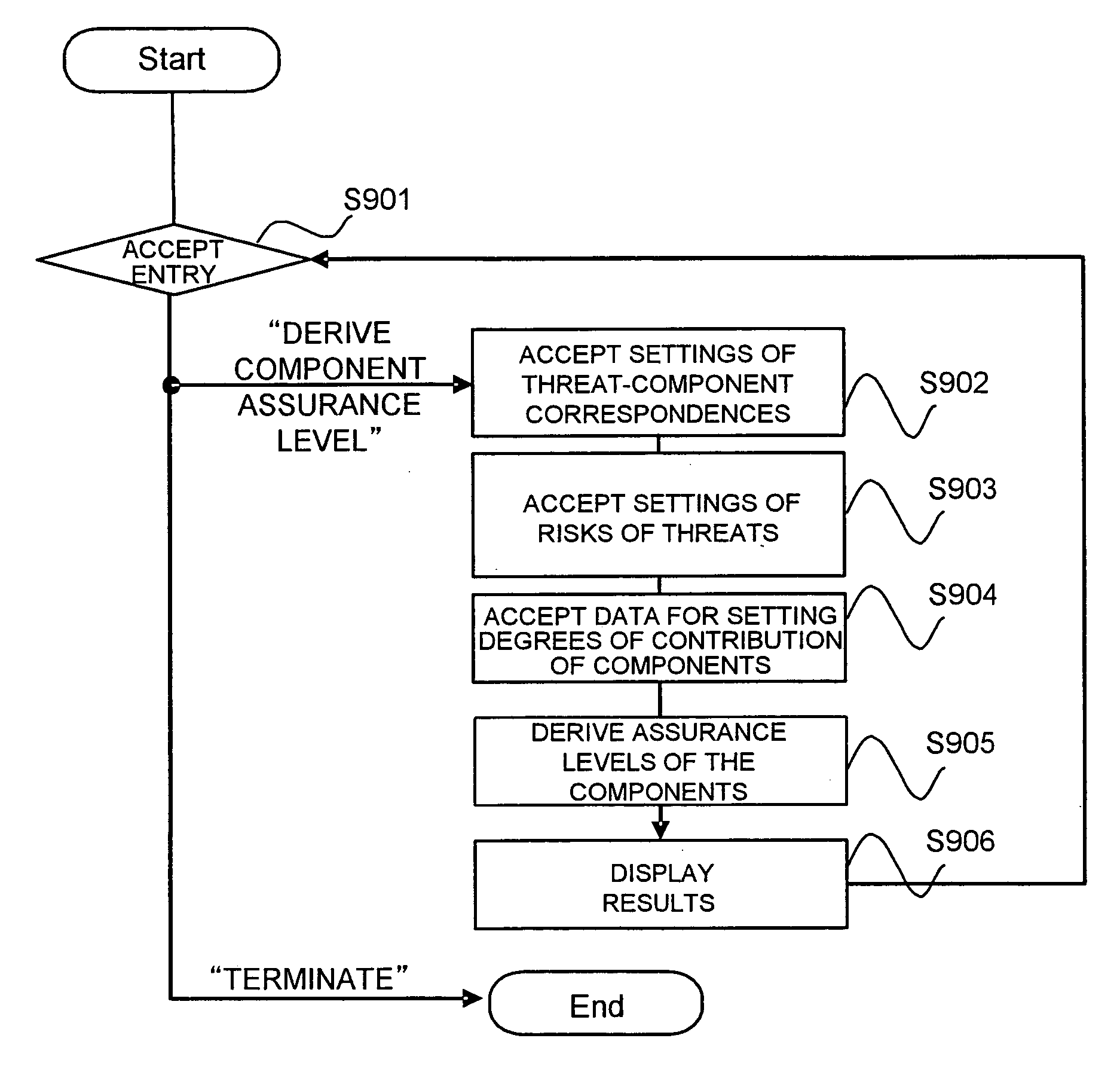
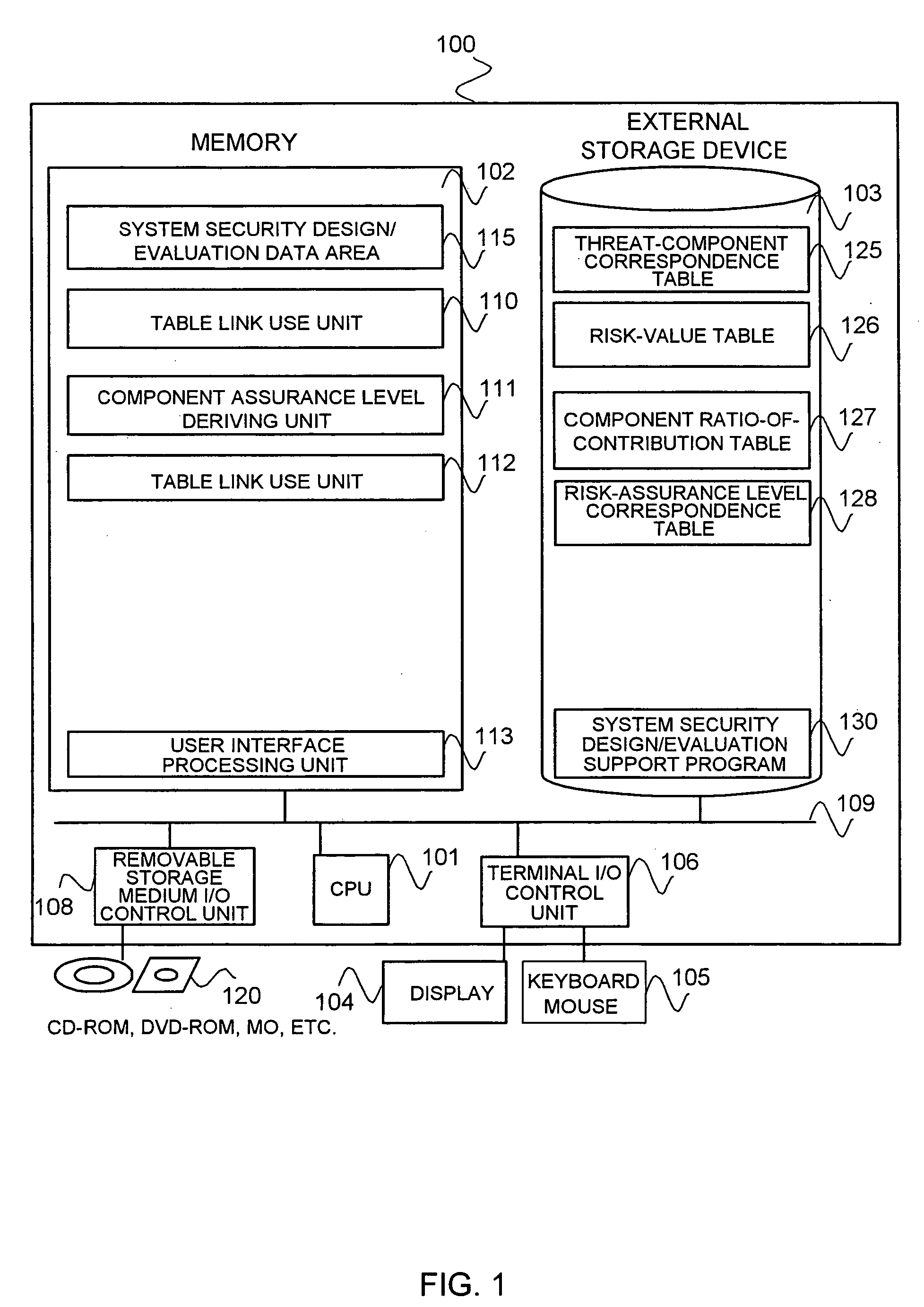
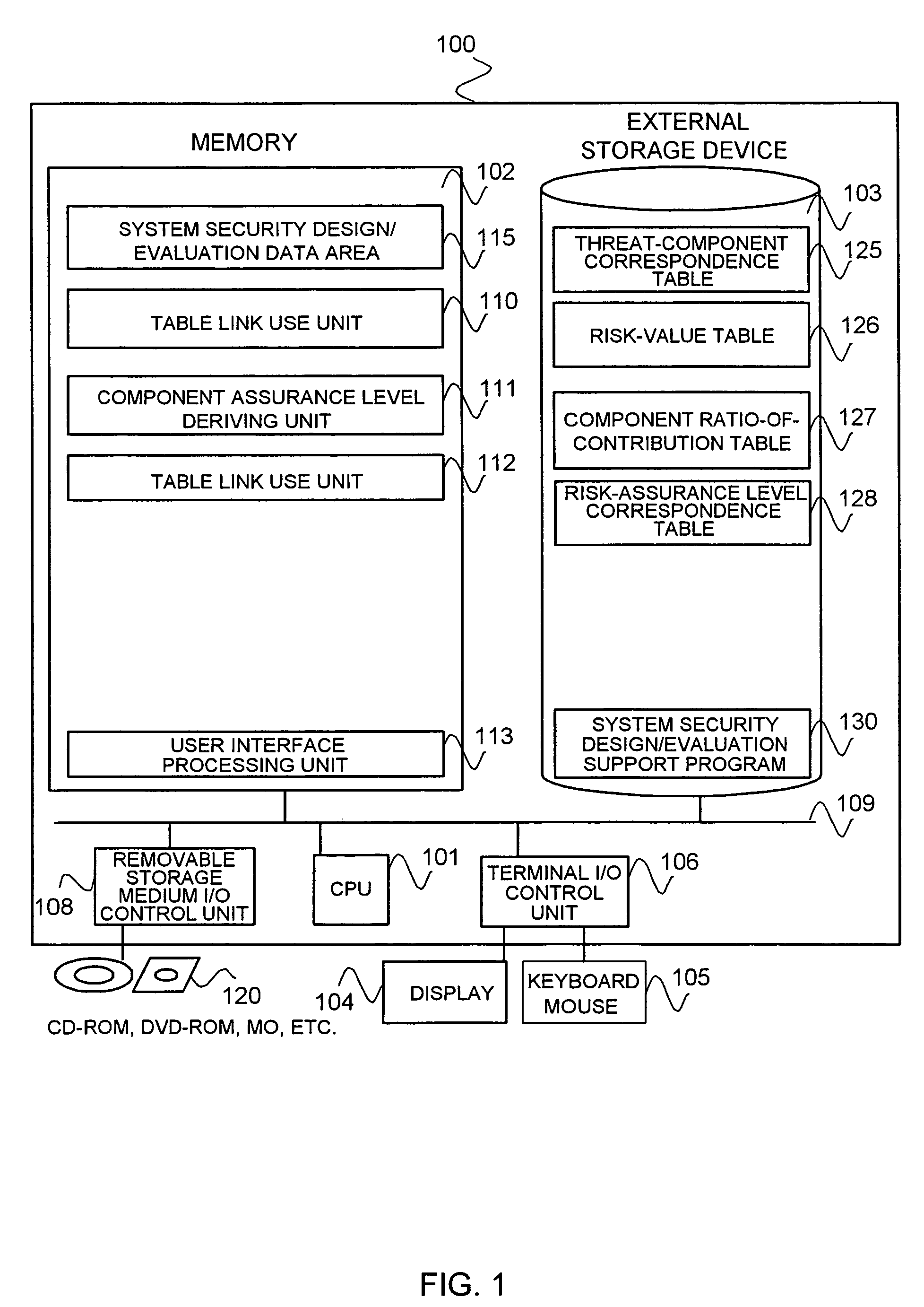
InactiveUS20060242711A1Safety be assureMeet functional requirementsMemory loss protectionDigital data processing detailsSupporting systemSecurity design
A design / evaluation support tool 100 is constructed from a table link use unit 110 identifying linkages between a threat-to-component correspondence table 125, a risk-value table 126, a component contribution rate table 127, and a risk-to-assurance level correspondence table 128, based on their respective duplicate items; and a component assurance level deriving unit 111 deriving an assurance level of each of components that conforms to a risk value of a threat that a security function of each of the components counters by weighting the risk value of the threat by a component rate of contribution based on linkages of the tables.
Owner:HITACHI LTD
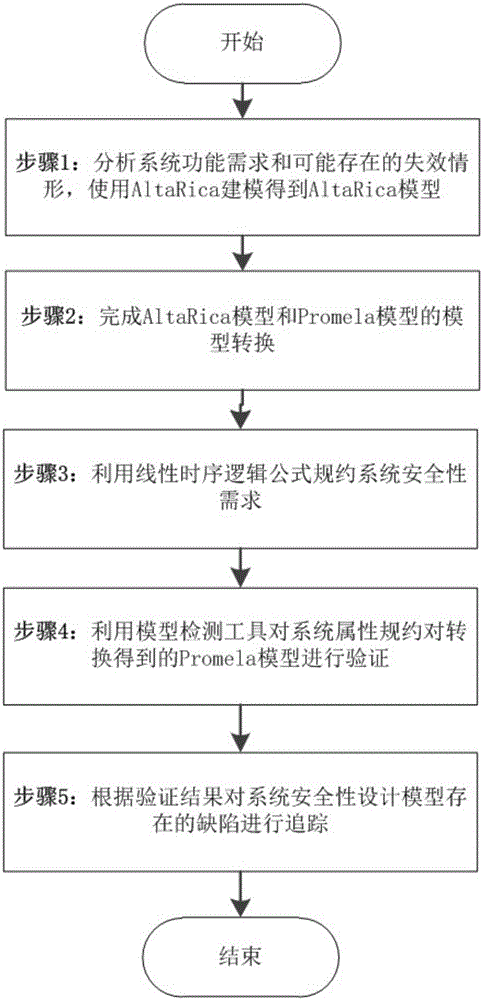
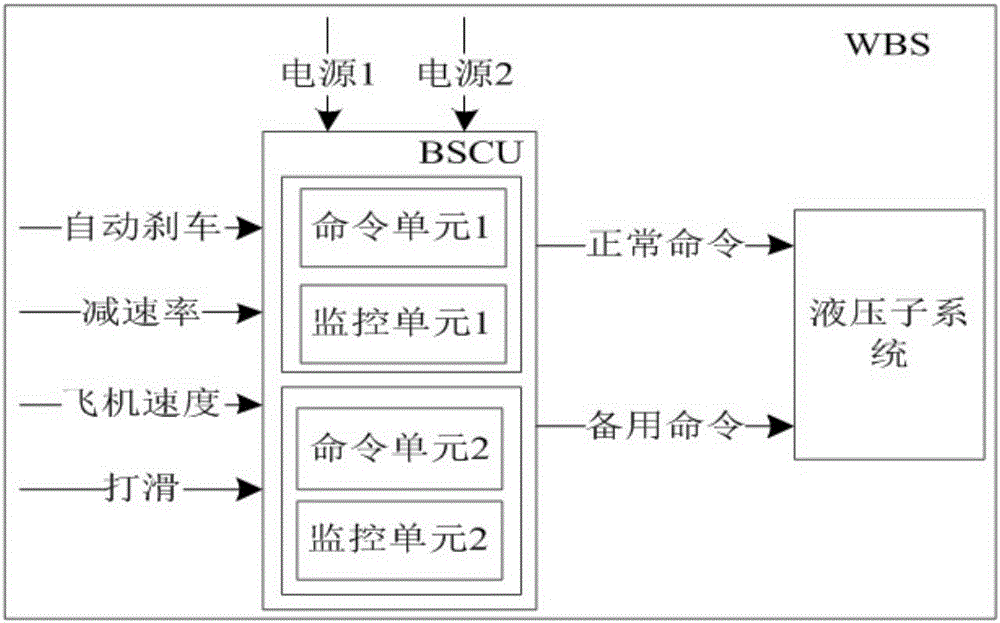
Validation method for design of system security of AltaRica model
InactiveCN105938502ATroubleshoot conversion issuesSpecial data processing applicationsTemporal logicValidation methods
The invention discloses a validation method for design of system security of an AltaRica model. The method comprises following steps: step 1, establishing an AltaRica model for design of system security; step 2, defining the rule for model transformation from the AltaRica model to a Promela model; obtaining the Promela model after conversion of the AltaRica model; step 3, utilizing lineal temporal logic to describe the system security demand in a formalized manner; step 4, utilizing a model detector to validity security of a system model; step 5, obtaining a security demand counter-example that does not satisfy the step 4, tracking the system security design model and finishing validation of the system security design model.The validation method for design of system security of the AltaRica model has following beneficial effects: a model conversion problem is effectively solved; operation on AltaRica is conducted by a model detection tool SPIN; and the validation method provides a new way of thinking for analyses of system security such that conversion rules are accurately defined.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
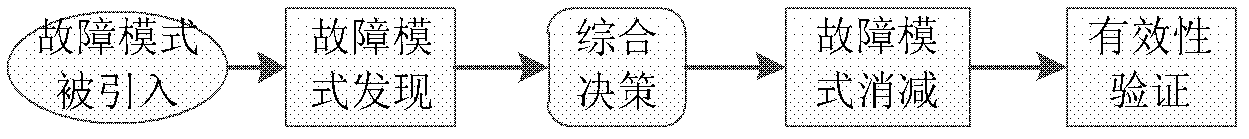
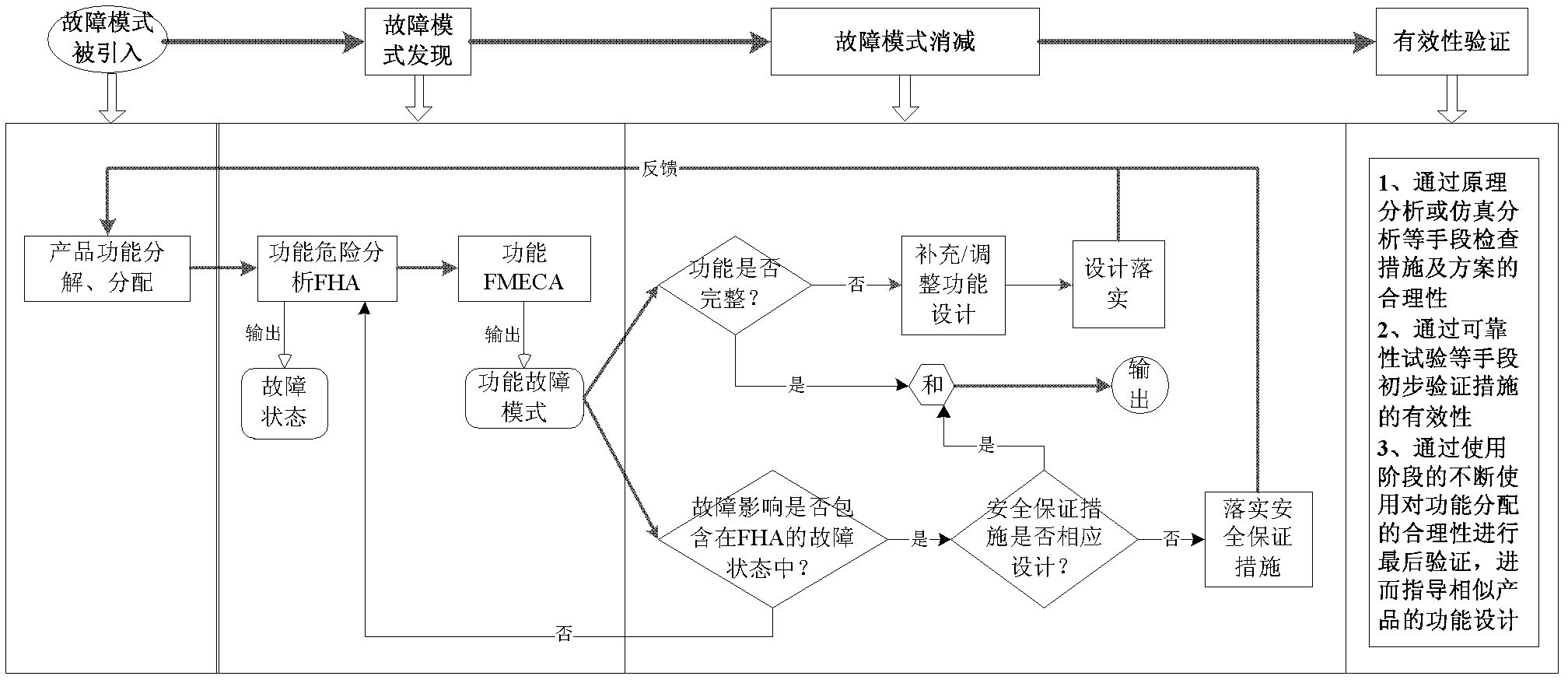
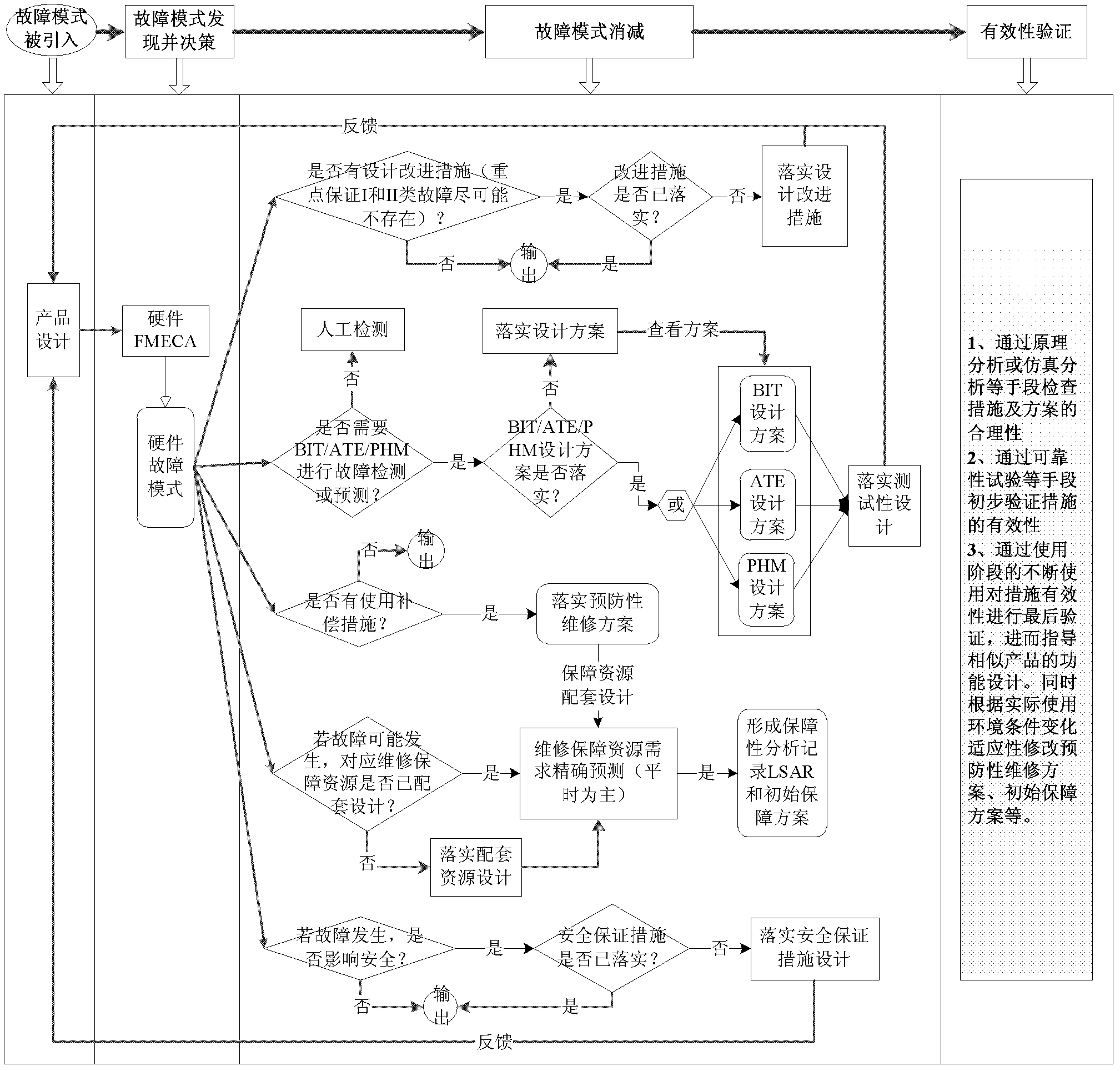
Fault mode subduction closure method based on logic decision
A failure mode subduction closure method based on a logic decision comprises four steps: step 1. Developing a FMECA analysis and classifying a result according to a certain standard; step 2. Taking a classified fault mode set as an object, calculating an influence of the fault mode subduction on an RMS index, calculating and determining an optimal fault mode subduction scheme based on a rough set theory; step 3. Implementing the fault mode subduction; step 4. Implementing validity verification. By using the method of the invention, design personnel takes the fault mode as a center, systematically considers a relation between a qualitative design and quantification index realization, simultaneously monitors each related reliability, maintainability, guarantee, testability and a security design condition and solves defects and insufficiencies one by one in the design so as to rapidly and effectively realize an RMS index requirement, shorten a development period and reduce development cost.
Owner:北京可维创业科技有限公司
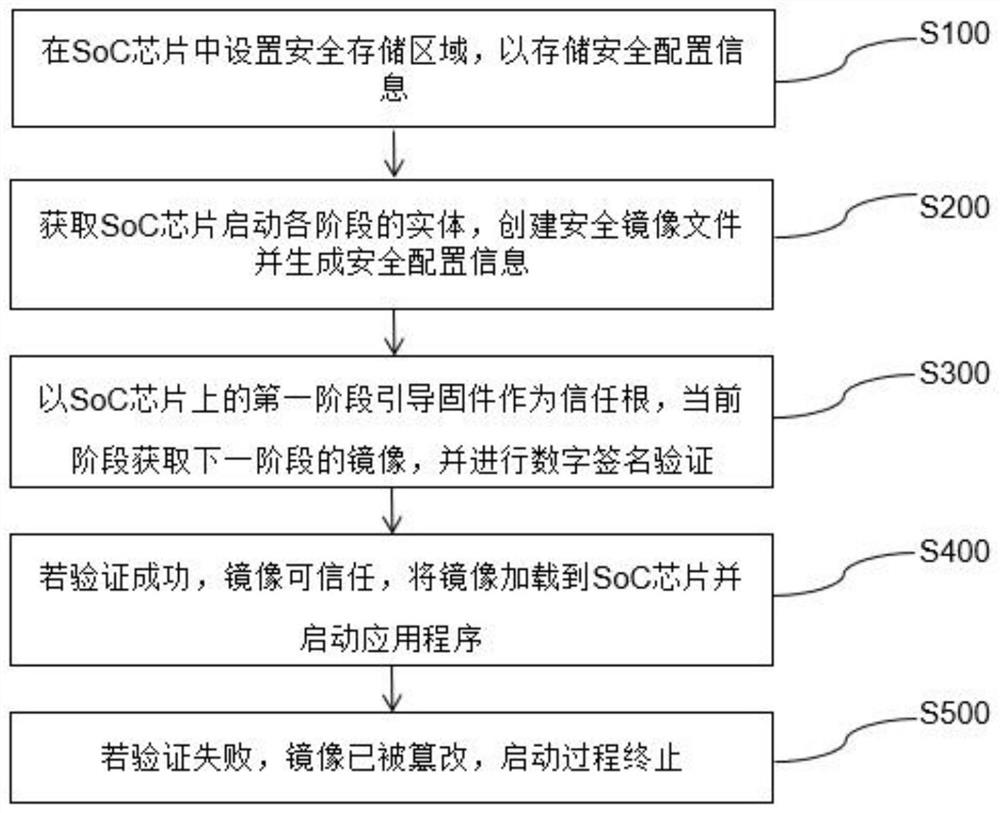
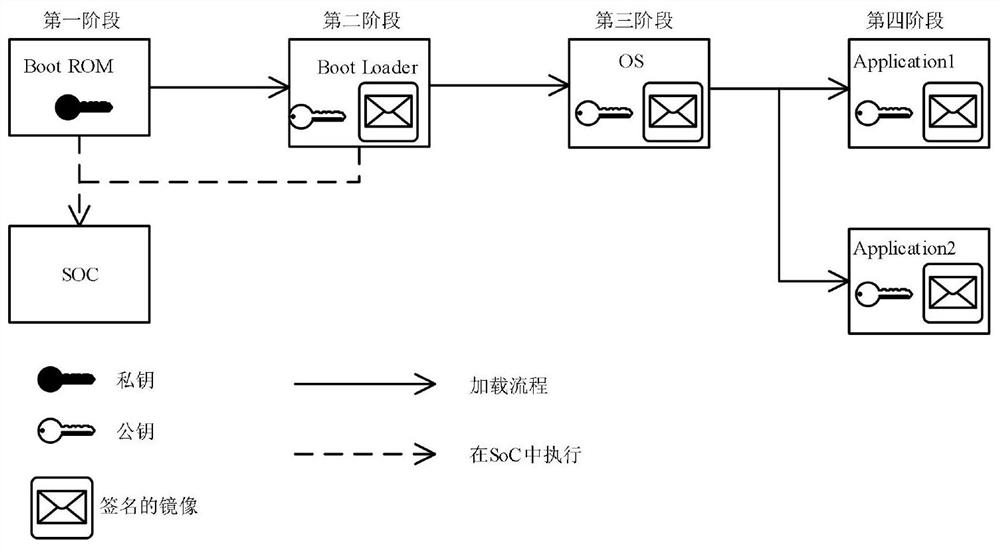
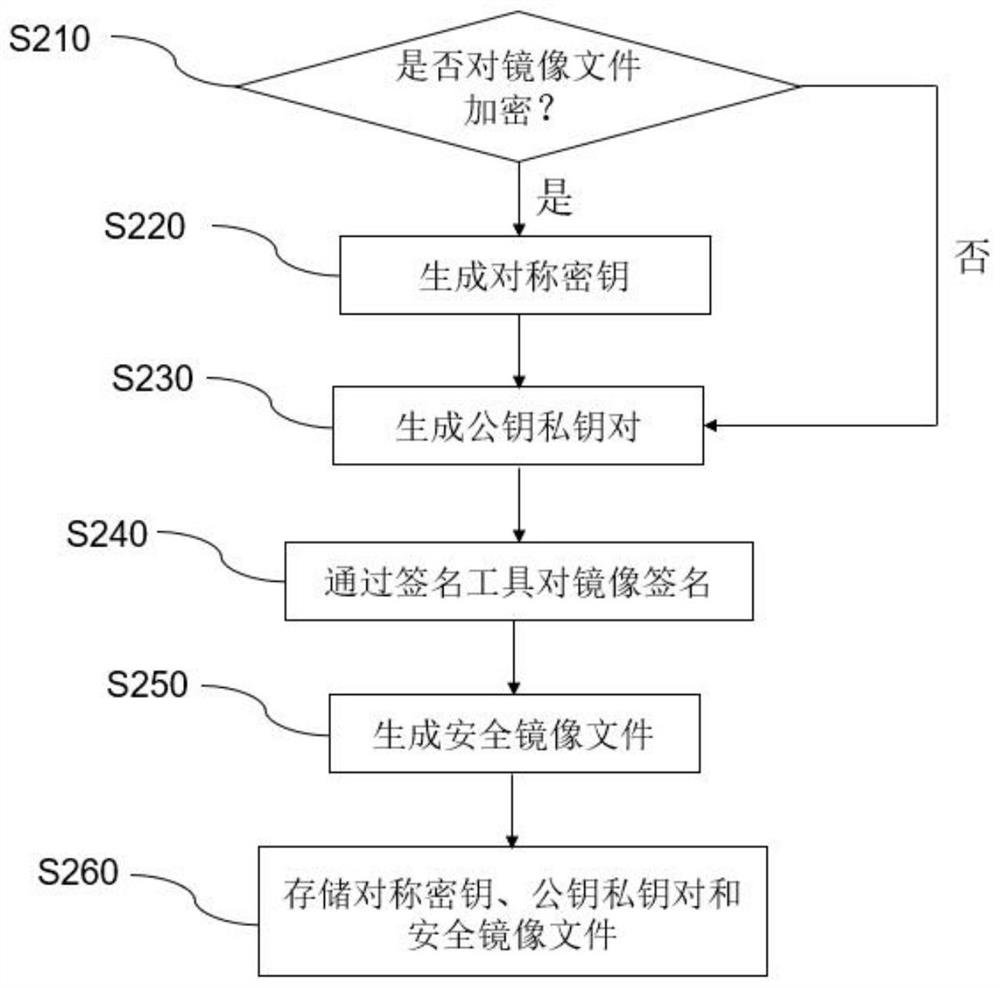
SoC chip security design method and hardware platform
InactiveCN112784280ASave wiring spaceImprove securityInternal/peripheral component protectionPlatform integrity maintainanceOperational systemDigital signature
The invention discloses an SoC chip security design method, and the method comprises the following steps: setting a security storage area in an SoC chip to store security configuration information; obtaining entities of all stages of SoC chip starting, creating a security mirror image file and generating security configuration information; taking first-stage boot firmware on an SoC chip as a root of trust, acquiring a mirror image of a next stage at a current stage, and performing digital signature verification; if verification succeeds, the mirror image is trusted, the mirror image is loaded, and starting is executed; if verification fails, tampering the mirror image, and terminating the starting process. The verification of the bootstrap program, the operating system and the application program is realized by means of encryption and digital signature, the security and credibility of firmware and software are ensured, the key is safely stored, and the security is improved.
Owner:INSPUR SUZHOU INTELLIGENT TECH CO LTD
Enhanced security design for cryptography in mobile communication systems
ActiveCN1857024ASmall standardized workQuick adoptionKey distribution for secure communicationUser identity/authority verificationSecurity designMobile communication systems
A basic idea according to the invention is to enhance or update the basic cryptographic security algorithms by an algorithm-specific modification of the security key information generated in the normal key agreement procedure of the mobile communication system. For communication with the mobile terminal, the network side normally selects an enhanced version of one of the basic cryptographic security algorithms supported by the mobile, and transmits information representative of the selected algorithm to the mobile terminal. The basic security key resulting from the key agreement procedure (AKA, 10) between the mobile terminal and the network is then modified (22) in dependence on the selected algorithm to generate an algorithm-specific security key. The basic security algorithm (24) is then applied with this algorithm-specific security key as key input to enhance security for protected communication in the mobile communications network.
Owner:TELEFON AB LM ERICSSON (PUBL)
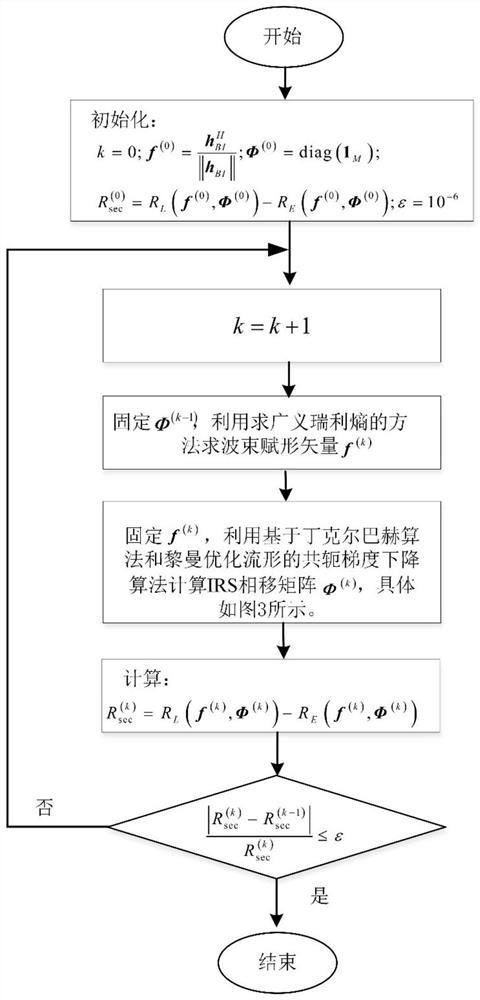
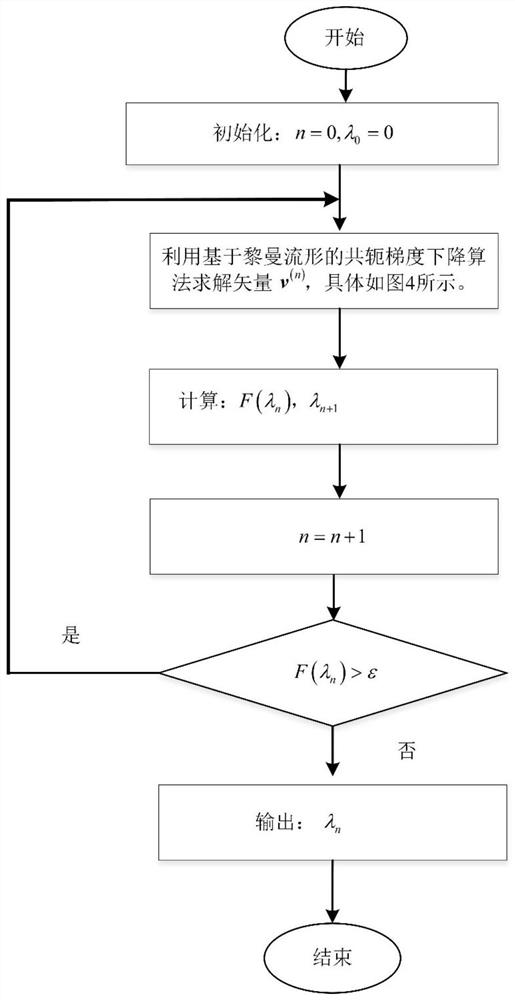
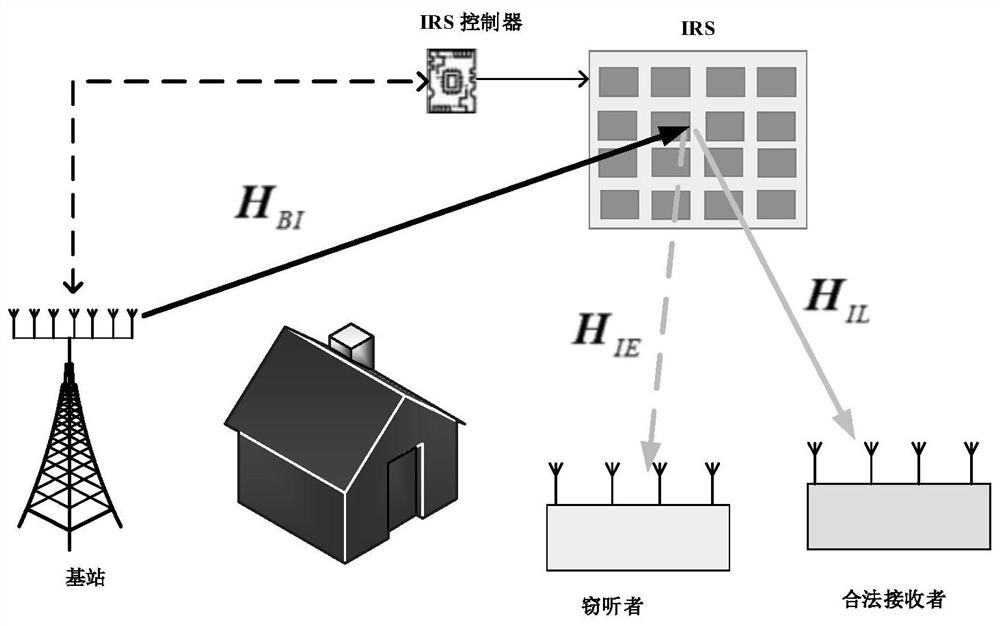
Physical layer security design method based on alternate iteration in IRS-assisted MISO system
ActiveCN113037349AReduce complexityIncrease confidentiality rateSpatial transmit diversityRound complexityAlgorithm
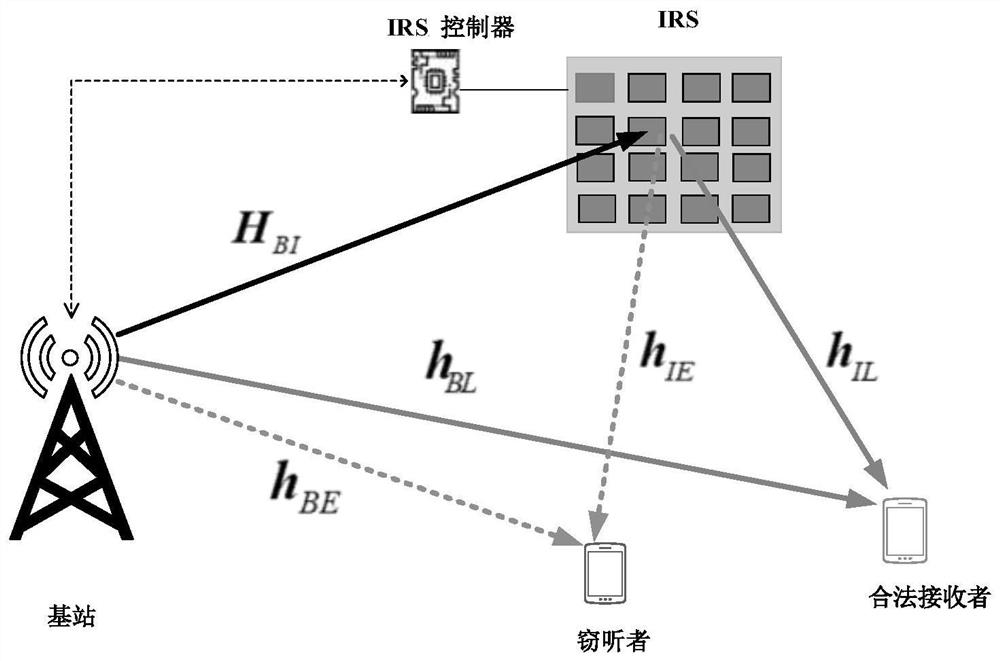
The invention relates to a physical layer security design method based on alternate iteration in an IRS-assisted MISO system, and belongs to the technical field of wireless communication. The method comprises the steps: constructing an objective function with non-convex constraint, wherein the objective function is composed of a beam forming vector and an intelligent reflection surface phase shift matrix, and the objective function is iteratively solved by adopting an alternating iteration thought; taking the maximizing of the secrecy rate of the system as the purpose, solving a beam forming vector by using a generalized Rayleigh entropy solving method, and then solving an intelligent reflection surface phase shift matrix by using a Dinkelbach algorithm and a Riemannian manifold-based conjugate gradient descent method. Compared with a traditional method for solving the intelligent reflection surface phase shift matrix through a semi-definite relaxation method, the method has the advantages that the operation complexity can be reduced, and the secrecy rate of a system can be increased. The method is simple in implementation process and has a better application prospect.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Secure biometric processing system and method of use
InactiveUS20070226515A1Digital data authenticationSecret communicationSecurity designHandling system
A secure biometric processing system is disclosed. The system comprises a processing system for providing image acquisition and biometric comparison. The processing unit utilizes public key cryptography for handling templates securely and authenticating operations using the template. The system includes a complete biometric engine which implements image reconstruction, template extraction and matching. The secure design of the system combines complete privacy with security, while offering a flexible usage model including on-chip template storage along with encrypted and authenticated communications to the system.
Owner:ATMEL CORP
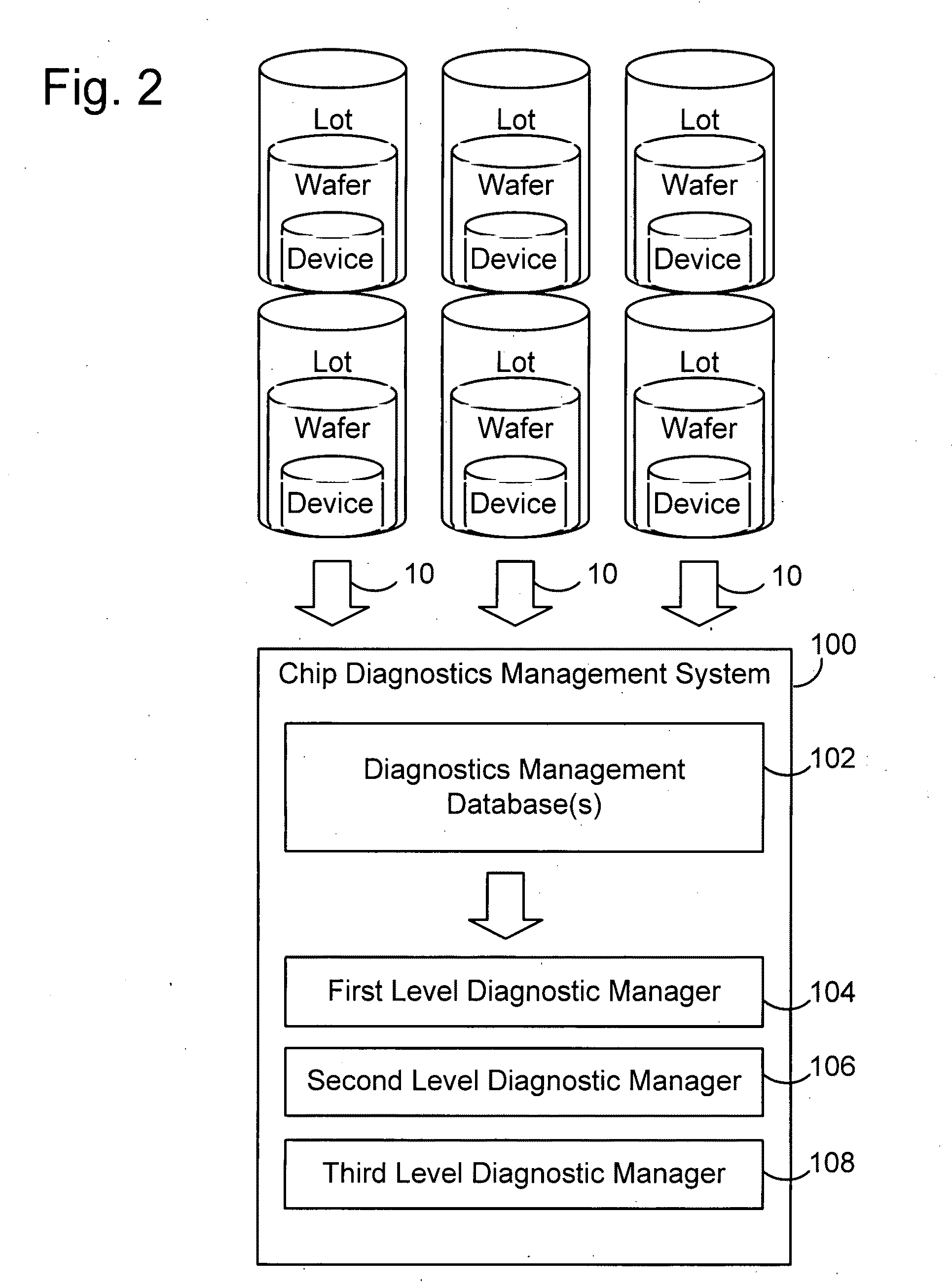
Secure test-for-yield chip diagnostics management system and method
ActiveUS8626460B2Quick discoverySimultaneous indication of multiple variablesData acquisition and loggingSecurity designDesign information
A chip diagnostics management system includes secure design information that define production features of integrated circuit devices and are accessible according to selected levels of access privilege. A database of device defect information includes information of defects of devices produced according to the production features of the design information and associated wafers, production lots, and dies in or with which the devices were produced. A diagnostic manager correlates device defect information from plural wafers with the design information to identify a device location with a probability of being associated with the device defect information. A diagnostic manager viewer indicates the device location together with an amount of design information correlated the level of access privilege assigned to a selected user.
Owner:TESEDA CORP
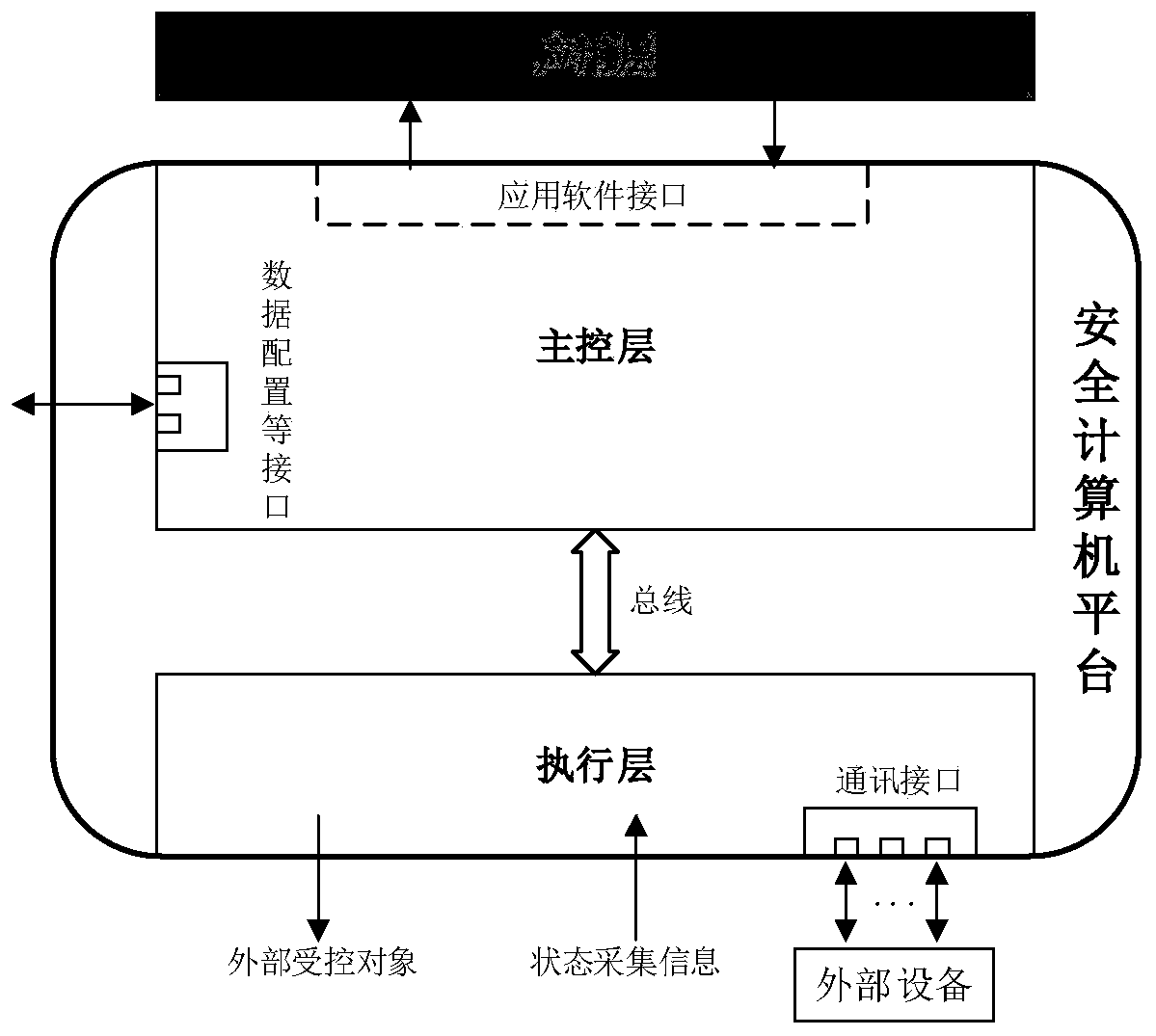
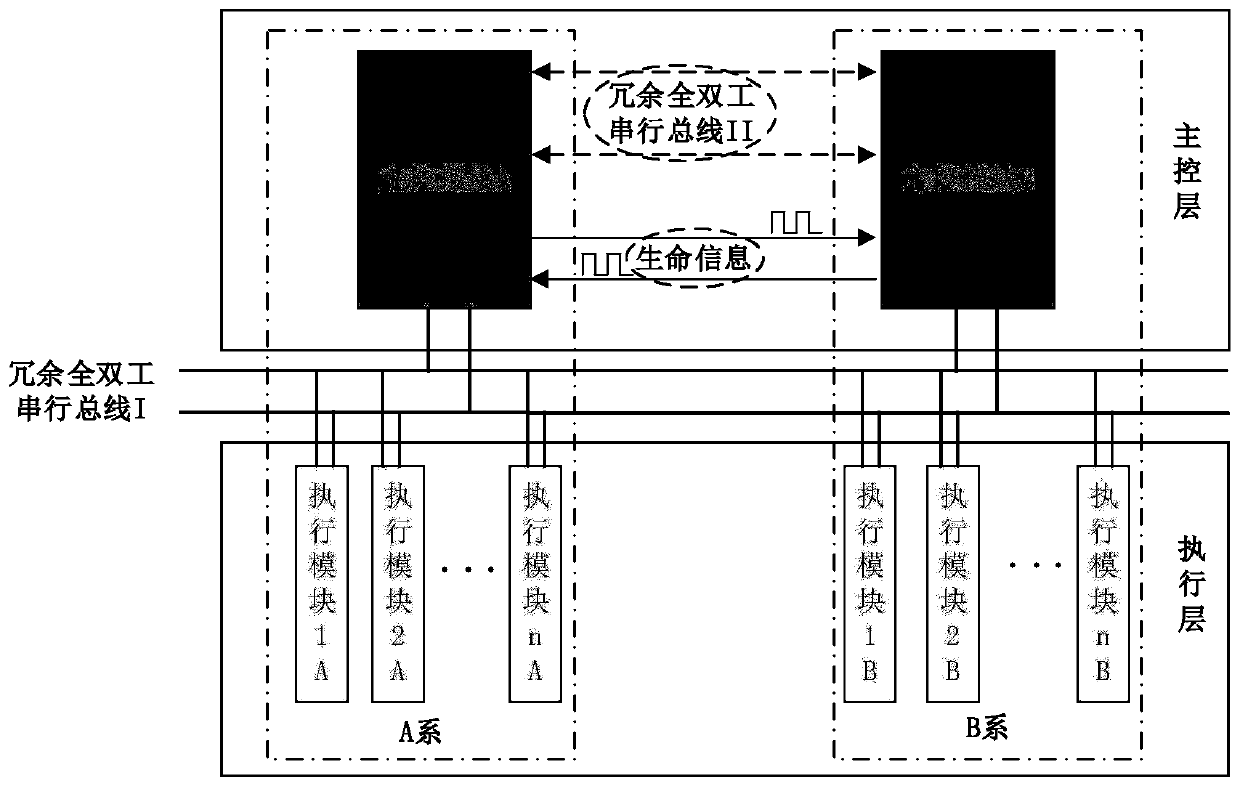
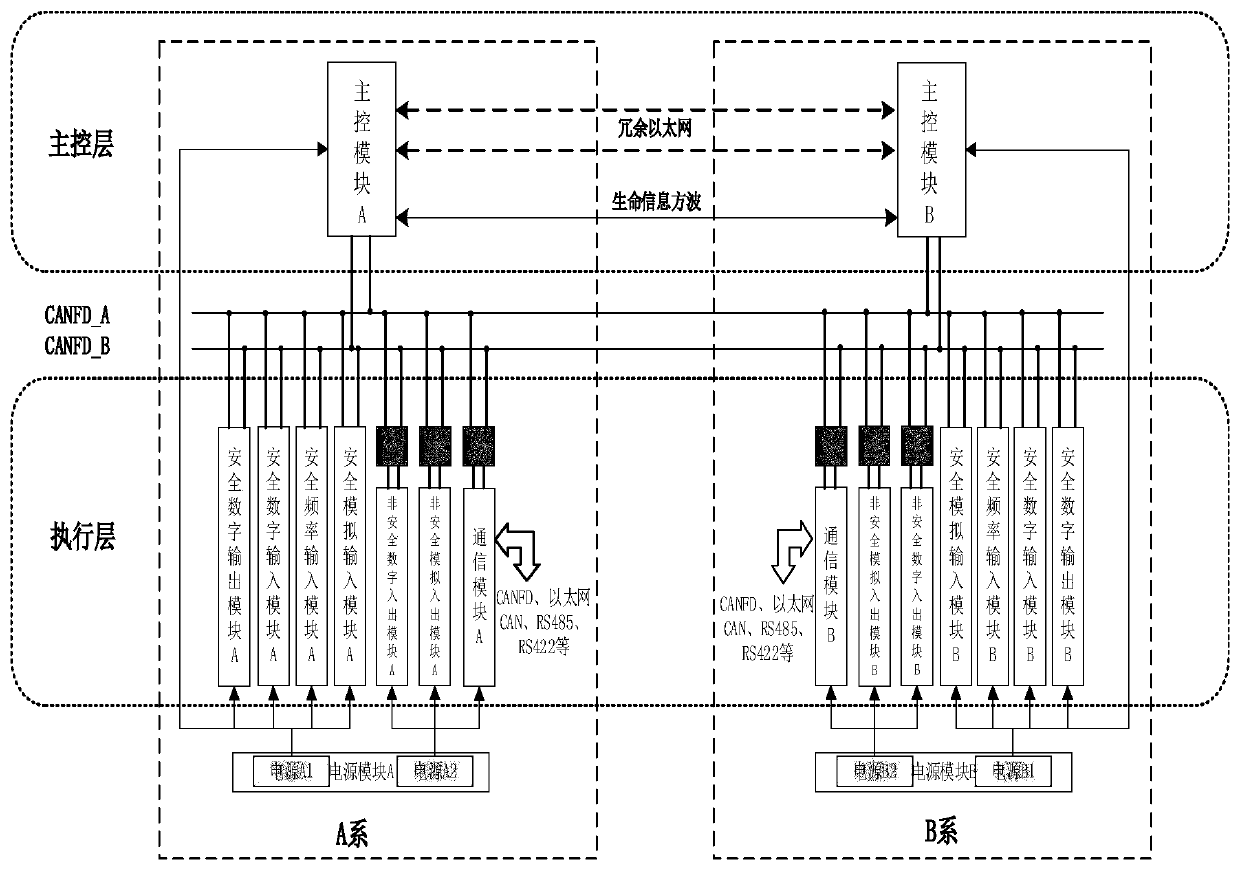
Dual-system synchronous safety computer platform
ActiveCN110376876AImprove reliabilityImprove securitySafety arrangmentsTotal factory controlControl layerComputer module
The invention provides a dual-system synchronous security computer platform, which is composed of a main control layer and an execution layer, wherein the main control layer is composed of a main control module, and is divided into main and standby systems, that is, is divided into a main control module A and a main control module B; the execution layer consists of a certain number of expandable execution modules, each of which is further divided into a security-related module and a non-security-related module, and the design of power supply isolation and bus isolation is carried out for the security function modules and the non-security function modules; the security computer platform adopts a double 2-vote-2 security redundancy architecture; all modules of the platform are connected by means of internal redundant CANFD buses; and the main control modules of the main and standby systems in the main control layer adopt Ethernet buses to implement main and standby machine synchronization and data interaction communication of the main and standby systems. The dual-system synchronous security computer platform has the technical advantages that the expansibility is excellent, the independent and redundant bus architecture is adopted between the main and standby systems, the security modules and non-security modules adopt the power supply isolation and bus isolation security design,and the reliability and security are higher.
Owner:BEIJING JIAODA SIGNAL TECH
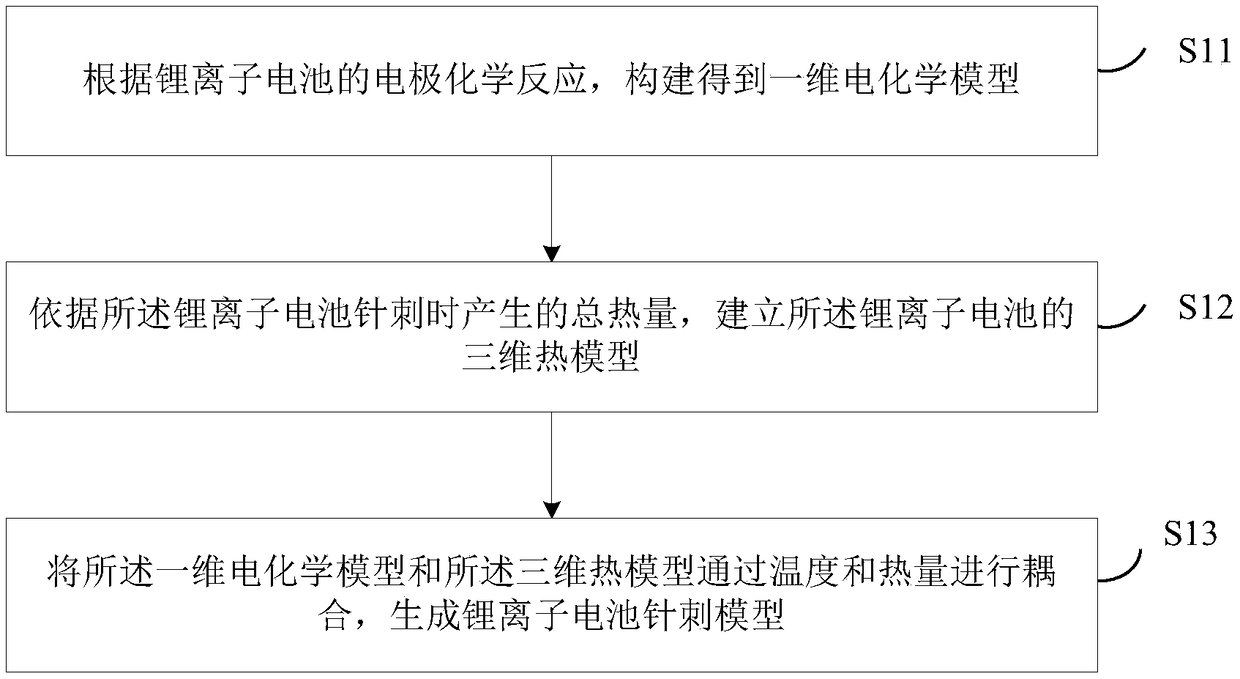
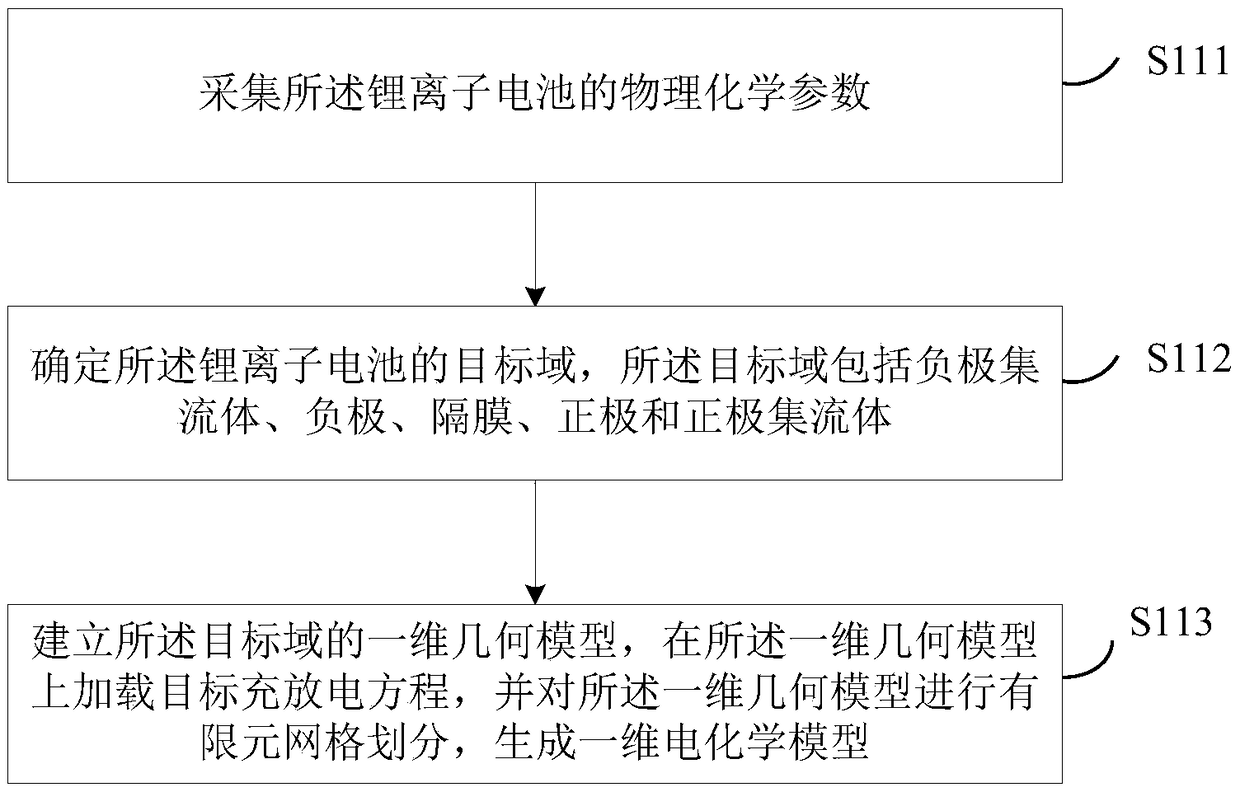
Establishment method and device of lithium ion battery acupuncture model
PendingCN108829929ABeneficial safety designImprove securityDesign optimisation/simulationSpecial data processing applicationsChemical reactionElectrical battery
The invention discloses an establishment method and device of a lithium ion battery acupuncture model. The method comprises the following steps: constructing to obtain a one-dimension electrochemicalmodel according to an electrode chemical reaction of the lithium ion battery; establishing a three-dimensional thermal model of the lithium ion battery according to the total heat produced by the lithium ion battery in acupuncture; and coupling the one-dimension electrochemical model with the three-dimensional thermal model through the temperature and the heat, thereby generating a lithium ion battery acupuncture model. The one-dimension electrochemical model and the three-dimensional thermal model are coupled so as to generate the lithium ion battery acupuncture model, thereby accurately outputting the battery internal and battery surface temperature distribution; the security design of the battery is convenient, and the aim of improving the lithium ion battery security is realized.
Owner:NINGBO INST OF MATERIALS TECH & ENG CHINESE ACADEMY OF SCI
Laser ignition system with double-security design
InactiveCN102840799APrevent electrostatic breakdownAvoid misuseProximity fuzesDetonatorSecurity design
The invention discloses a semiconductor laser ignition system with a double security design, which belongs to the field of semiconductor laser ignition systems. The semiconductor laser ignition system comprises a singlechip system, a voltage-controlled current source, a laser, a first optical fiber connector, a second optical fiber connector, a laser detonator joint, a laser detonator, a photoelectric detector, an upper computer, a current-limiting resistor, a current-limiting switch and a normally-closed relay, wherein the singlechip system is connected with the upper computer, the voltage-controlled current source, the current-limiting switch, the normally-closed relay and the photoelectric detector respectively; the current-limiting switch is connected in parallel to two ends of the current-limiting resistor; the normally-closed relay is connected in parallel to two ends of the laser; the laser is connected with the voltage-controlled current source, the current-limiting resistor, the current-limiting switch and the first optical fiber connector respectively; the photoelectric detector is connected with the second optical fiber connector; and the laser detonator joint is connected with the laser detonator. In a security mode, static electricity is prevented from puncturing the laser. In a detection mode, the detection light power output by the laser is kept in a safe range. In an ignition mode, the laser can work in a rated state.
Owner:CHANGCHUN INST OF OPTICS FINE MECHANICS & PHYSICS CHINESE ACAD OF SCI
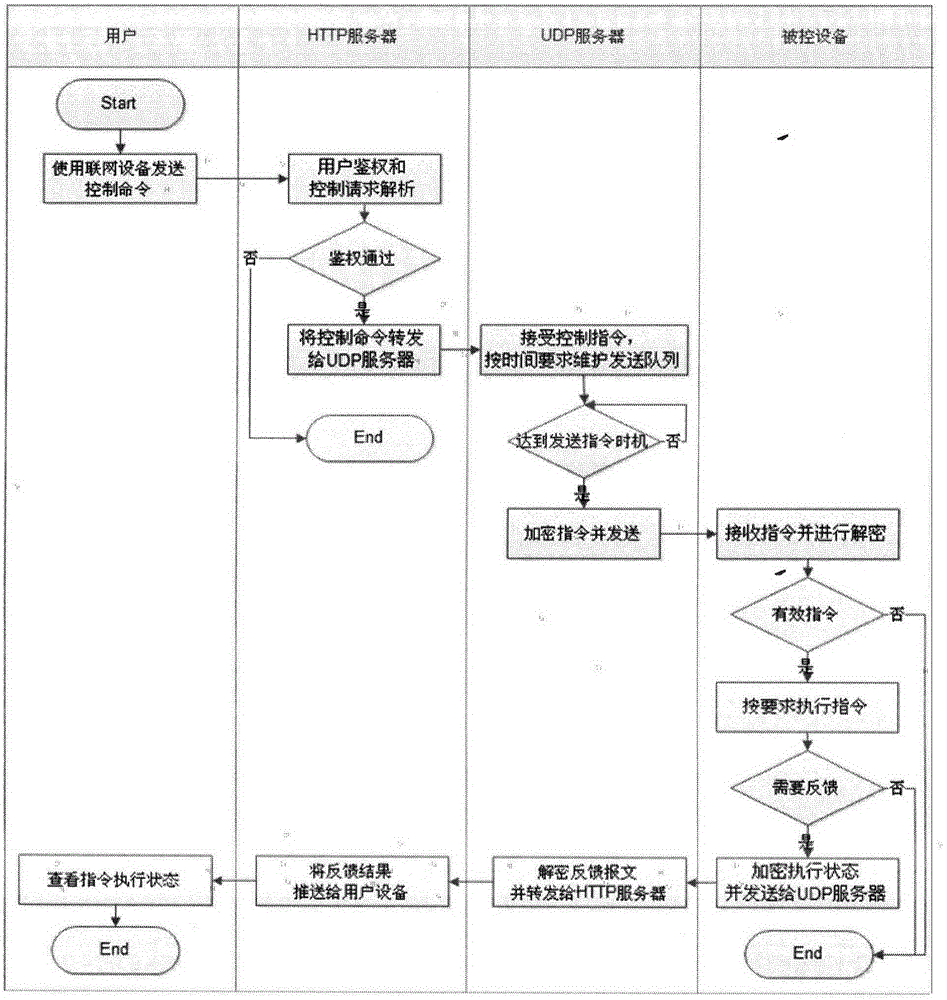
A realization method of cloud security communication based on an HTTP protocol end
ActiveCN109714370AEnsure safetyRealize anti-masquerading attackKey distribution for secure communicationUser identity/authority verificationTamper resistanceData information
The invention discloses a method for realizing cloud security communication based on an HTTP protocol end. The method comprises the steps of designing a secure API format, verifying the terminal datalegality at the cloud end; designing a new terminal signature data mode and a cloud verification terminal signature data mode; In the process that the terminal verifies the legality of the cloud data,a new cloud signature process and a new terminal signature verification process are designed, and the terminal signature data mode comprises a signature data combination mode, a body data sorting mode and a terminal signature process. According to the method provided by the invention, through the security design of the interface, security functions of anti-counterfeiting attack, tamper-proofing attack, replay attack prevention, data information leakage prevention and the like can be realized, and the security of WEB interface communication is ensured.
Owner:SICHUAN CHANGHONG ELECTRIC CO LTD
Secure network device for electronic detonator initiation system and use method of secure network device
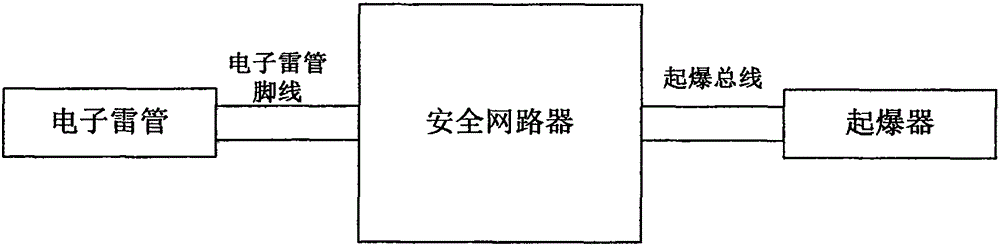
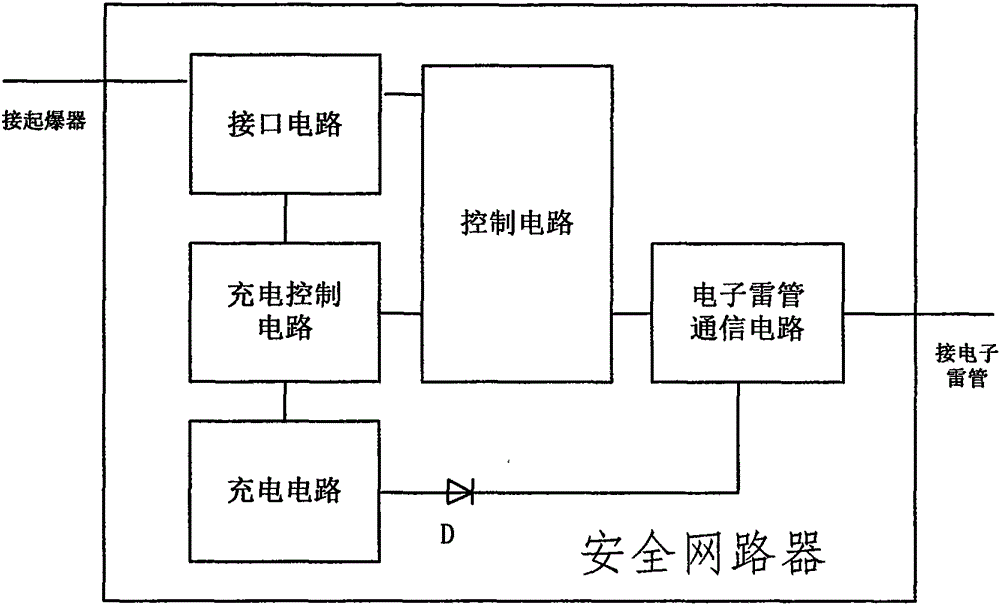
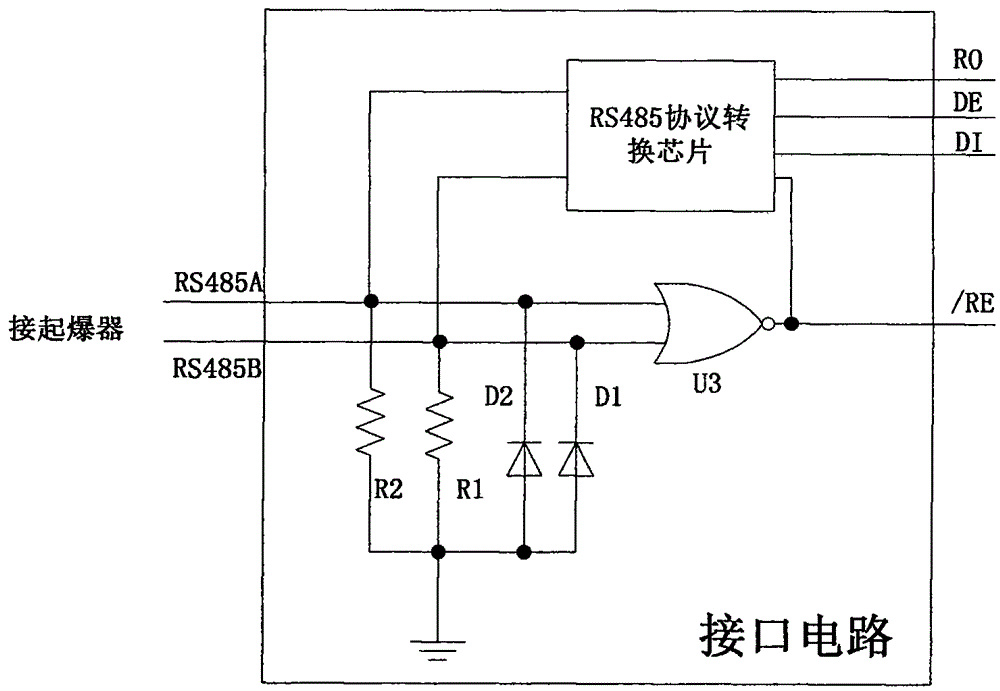
ActiveCN105043178AImprove securityAvoid the possibility of accidental explosionBlastingDetonatorSecurity design
Owner:北京百裕和科技有限公司
A captive balloon anchoring platform and a use method
ActiveCN109693806APromote construction and developmentEfficient use ofAnchoring installationsLighter-than-air aircraftSecurity designEngineering
The invention belongs to the technical field of captive balloon operation and security design, and relates to a captive balloon anchoring platform and a using method. The captive balloon anchoring platform comprises a ball seat, a spare part chamber in the ball seat, an empennage storage chamber, a take-off recovery chamber, a maintenance chamber and a plurality of take-off recovery devices. The ball seat is in a trapezoid shape, a conformal curved surface matched with the lower surface of the balloon is arranged in the middle of the upper surface of the ball seat; cross arm sliding rails, cross arms installed on the cross arm sliding rails and a plurality of upper captive rigging bodies are arranged on two sides of the upper surface of the ball seat. The ball seat is provided with a doorfor entering the maintenance chamber; a plurality of bottom captive rigging bodies are arranged at the bottom in the take-off recovery chamber; during anchoring, helium in the sphere can be released,the sphere becomes flat and is placed in the conformal curved surface, and a covering plate is tightly fixed through the cross arm sliding rails so as to resist extreme climate such as strong storm; by means of the captive balloon anchoring platform, an application area can be continuously expanded to areas with complex geographical and topographic conditions such as ocean islands, steep mountainous regions and wetland mudflats.
Owner:CHINA SPECIAL TYPE FLIER RES INST
Tool, method, and program for supporting system security design/evaluation
InactiveUS7748041B2Meet functional requirementsCost containmentMemory loss protectionDigital data processing detailsSupporting systemSecurity design
A design / evaluation support tool 100 is constructed from a table link use unit 110 identifying linkages between a threat-to-component correspondence table 125, a risk-value table 126, a component contribution rate table 127, and a risk-to-assurance level correspondence table 128, based on their respective duplicate items; and a component assurance level deriving unit 111 deriving an assurance level of each of components that conforms to a risk value of a threat that a security function of each of the components counters by weighting the risk value of the threat by a component rate of contribution based on linkages of the tables.
Owner:HITACHI LTD
Security protection authentication encryption method of intelligent network load interaction terminal information
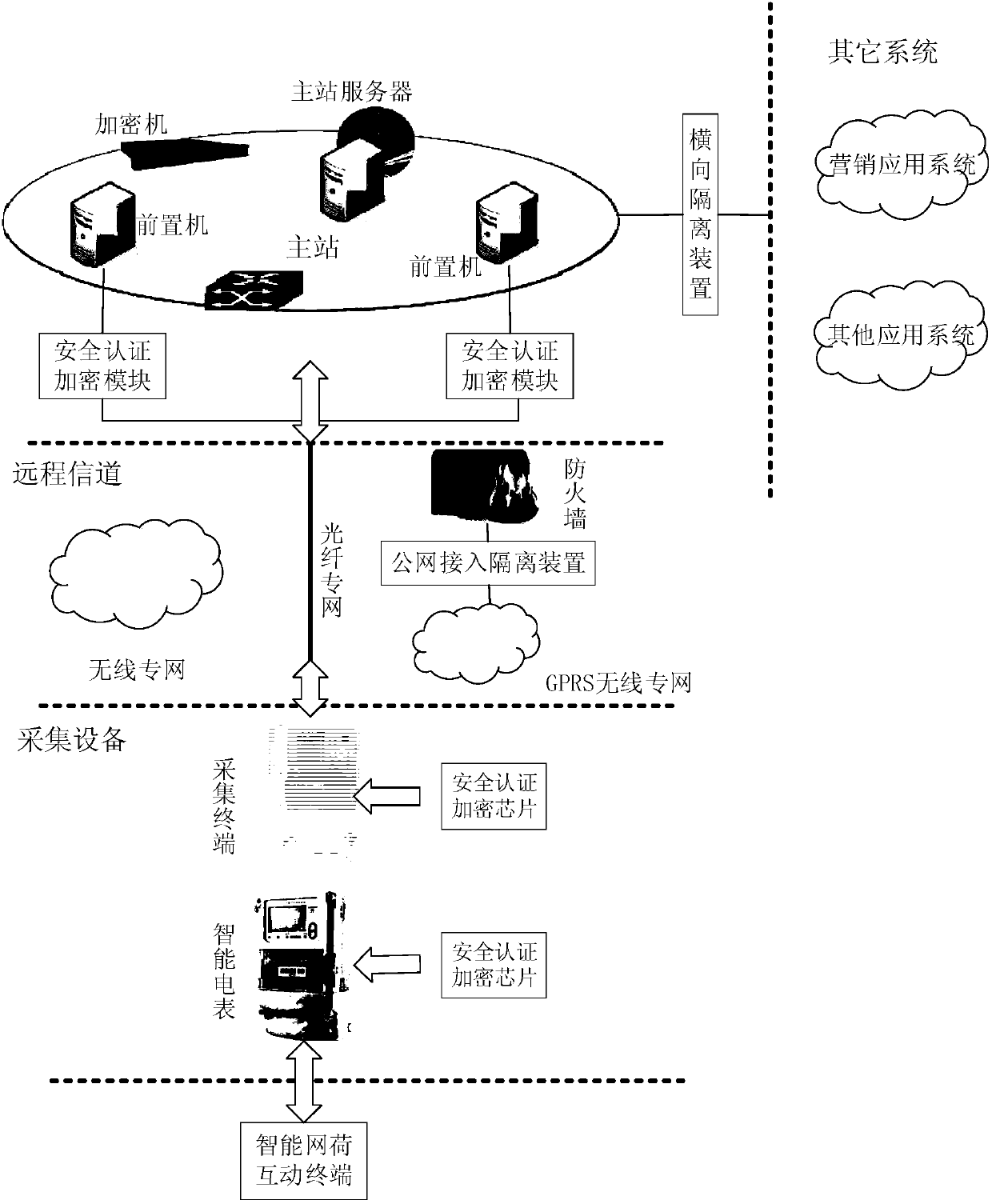
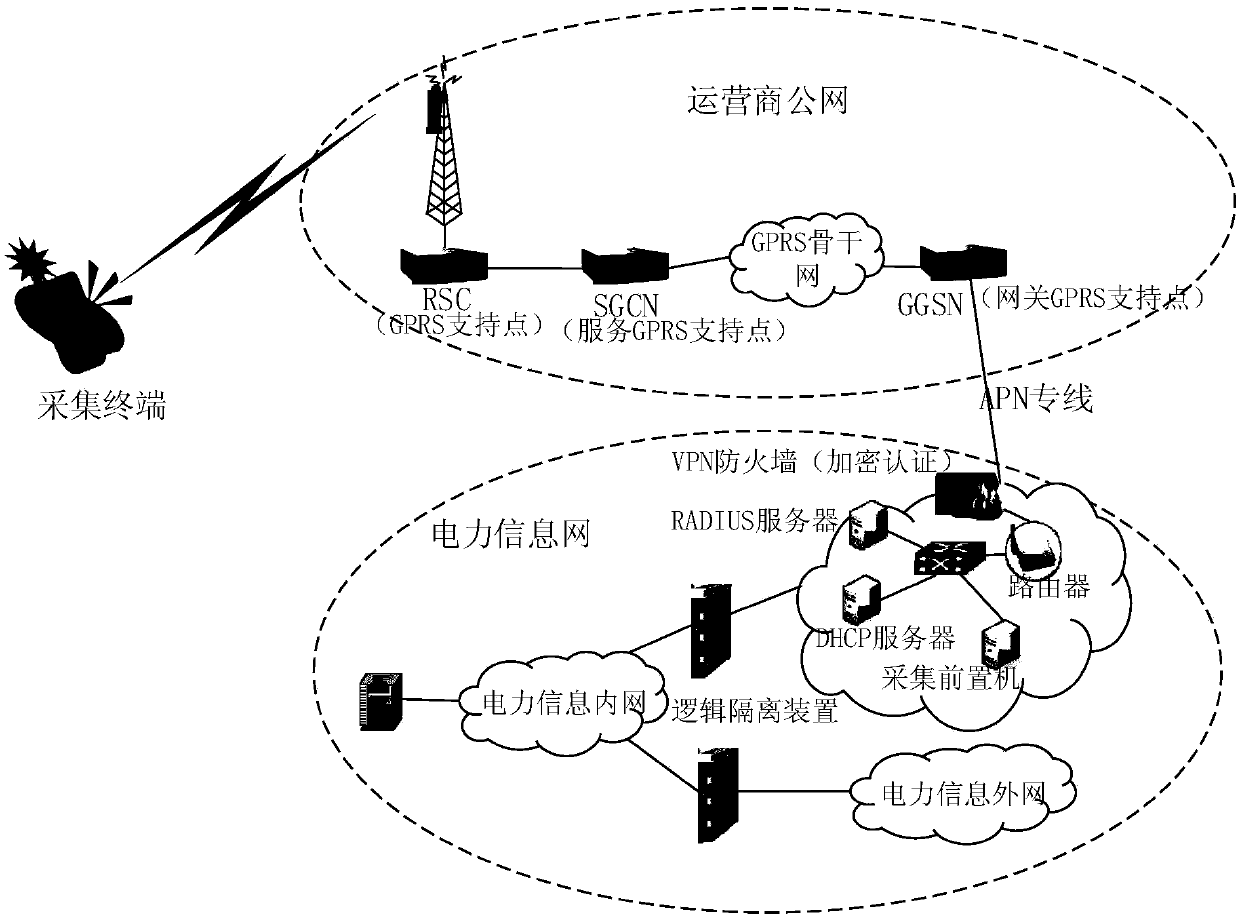
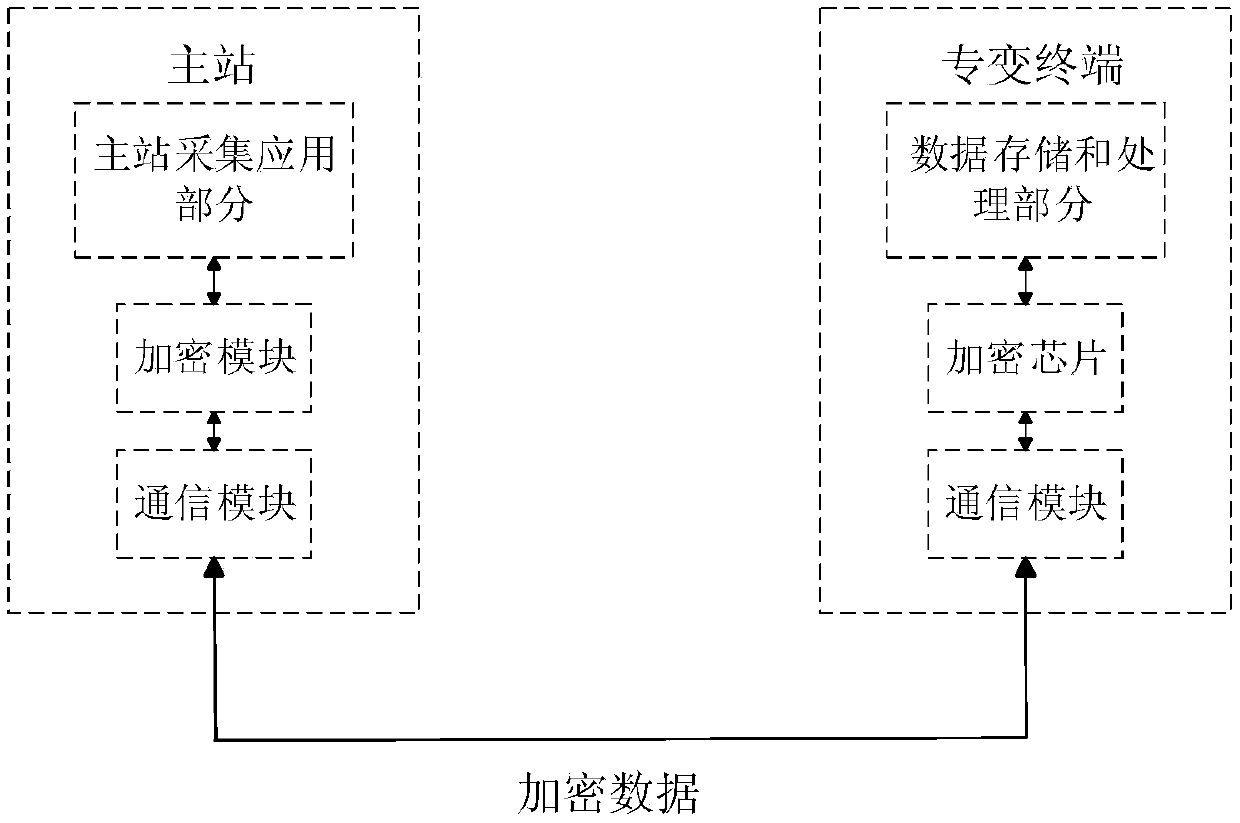
InactiveCN107920089AImprove the protective effectSafe and stable operationTransmissionSecurity designInformation security
The invention discloses a security protection authentication encryption method of intelligent network load interaction terminal information. From three aspects of system master station protection, collection channel protection and collection equipment protection, coordinated and unified security protection technology and a security management method are adopted to perform a security design on an authentication encryption system. A system master station protection module ensures the security of the a system master station by setting a security protection measures of the master station and setting network boundary security protection; a collection channel protection module adopts the GPRS access network protection, power information internal network protection, optical fiber special networkprotection and power line carrier protection, and adopts an identity authentication mechanism and a data encryption measure to improve the security protection ability of the collection equipment. By adoption of the information security protection authentication encryption method, a dynamic and sustainable overall security protection scheme is constructed to provide more reliable protection services for the intelligent network load interaction terminal information.
Owner:NARI TECH CO LTD +3
IRS and artificial noise assisted MIMO system physical layer security design method
ActiveCN113037346AIncrease confidentiality rateThe implementation process is simpleSpatial transmit diversityHigh level techniquesInterior point methodSecurity design
The invention relates to an IRS and artificial noise assisted MIMO system physical layer security design method, and belongs to the technical field of wireless communication. According to the invention, the method comprises the steps: processing a secrecy rate objective function equivalently based on a mean square error criterion, solving a beam forming matrix and an artificial noise covariance matrix by using an interior point method in convex optimization in an alternate iteration mode, and fixing the two variables; solving an intelligent reflection surface phase shift matrix by using a branch and bound method; and executing the two processes alternately until the secrecy rate objective function reaches convergence. Compared with a traditional semi-definite relaxation method, the secrecy rate of the system can be remarkably improved. The method is simple in implementation process and has a better application prospect.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Virtual intelligent password key
InactiveCN109412795AEasy to operateLow costKey distribution for secure communicationUser identity/authority verificationStorage securityCiphertext
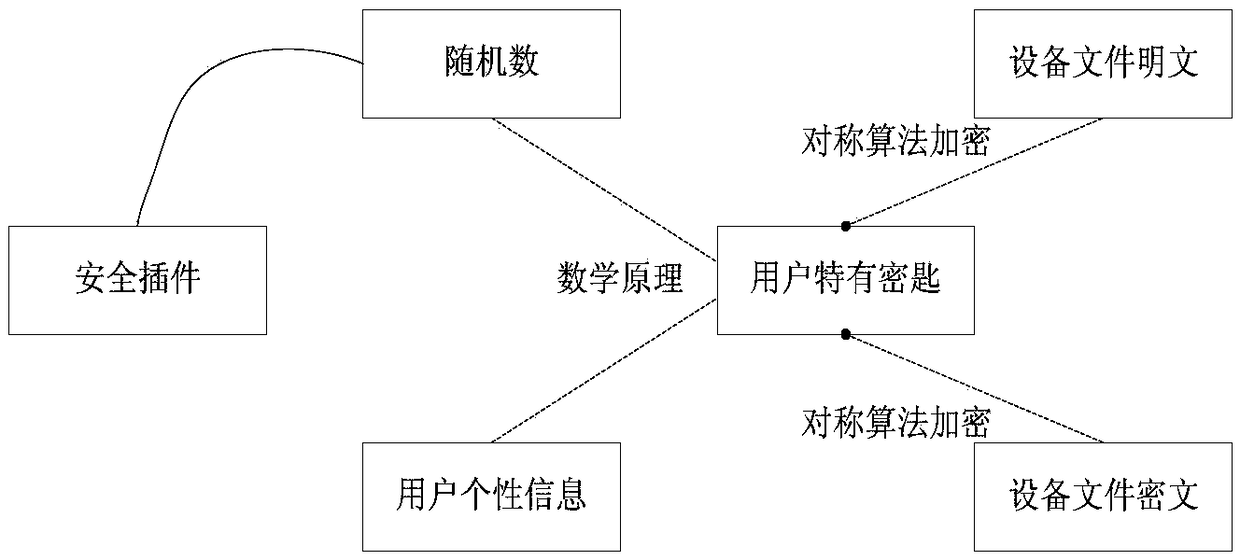
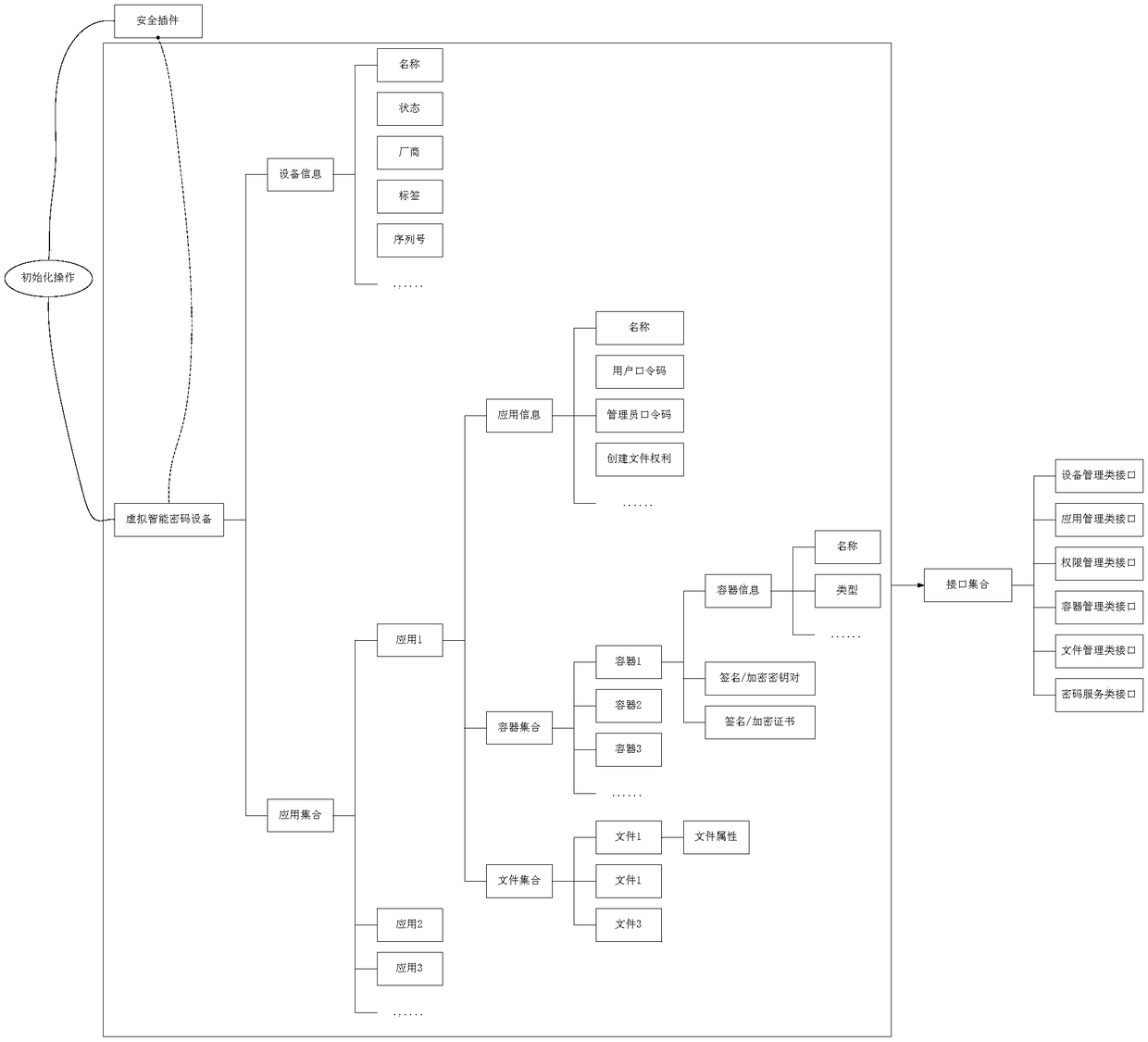
The invention discloses a virtual intelligent password key which is characterized by comprising security design and logic design. The security design comprises the working processes of generating a random number via a security plug-in, and dispersing a data encryption key via an algorithm; encrypting data or a file needing to be encrypted by combining with an encryption key to form a data ciphertext, and storing the random number and the data ciphertext by a terminal; and when in decryption, according to the random number and equipment information, performing inverse operation of a symmetric algorithm on the data ciphertext in combination with the data encryption key to acquire a decrypted original file. The logic design can be divided into the following modules of initialization, right control, equipment management, application management, container management, file management and password security service. The virtual intelligent password key is used as sensitivity data of a mobile terminal, so that secure storage is also important; the encryption key dynamically generated by multiple factors is used for performing encryption protection; even the user leaks the file of the password key, the other people cannot decrypt either, and the storage security is ensured.
Owner:JIANGSU WAFA INFORMATION TECH
System-level chip security design method based on untrusted IP core
ActiveCN109960879ADoes not change the original schemaAchieve positioningInternal/peripheral component protectionCAD circuit designData setHardware Trojan
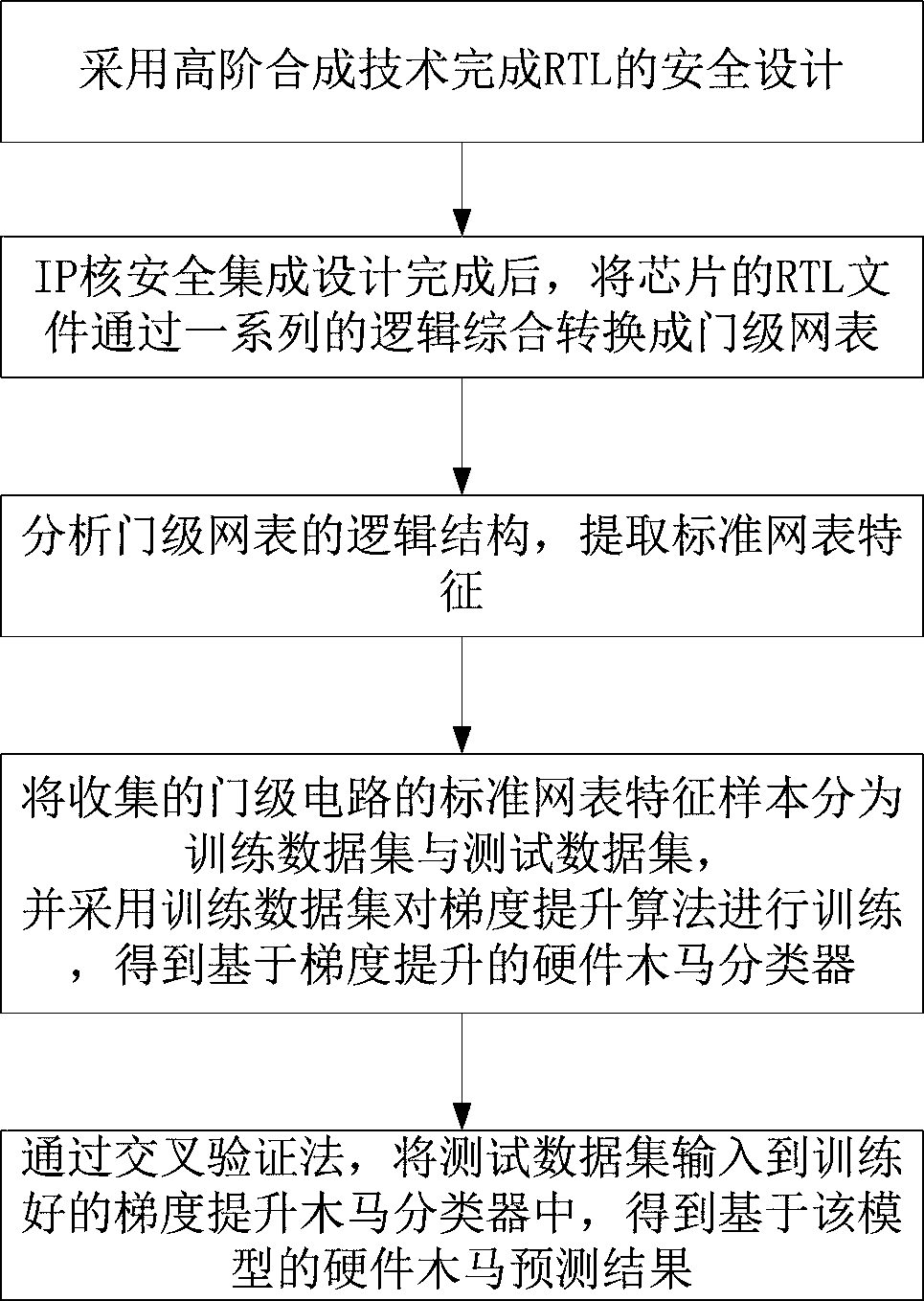
The invention relates to a system-level chip security design method based on an untrusted IP core. The method comprises the following steps: firstly, completing security design of an RTL by adopting ahigh-order synthesis technology; converting the RTL file of the chip into a gate-level netlist through a series of logic synthesis; analyzing the logic structure of the gate-level netlist, and extracting the characteristics of the standard netlist; dividing the collected standard netlist feature samples of the gate-level circuit into a training data set and a test data set, and training a gradient lifting algorithm by adopting the training data set to obtain a hardware Trojan horse classifier based on gradient lifting; and finally, inputting the test data set into the trained gradient liftingTrojan classifier through a cross validation method to obtain a hardware Trojan prediction result based on the model. According to the invention, an SoC security design architecture with strong adaptability, high reusability, wide expansibility, rapidness and intelligence is designed from the source of an IP supply chain.
Owner:FUZHOU UNIV
Zero-trust data storage access method and system
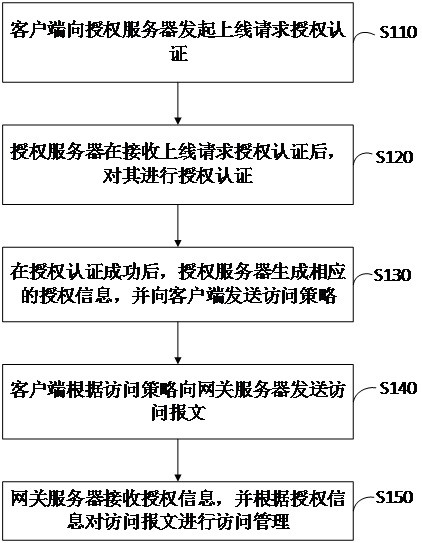
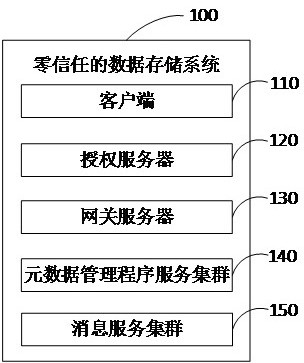
ActiveCN112100675AImprove the problem that the security of data access cannot be guaranteedDigital data protectionObject storageSecurity design
The invention provides a zero-trust data storage access method and system, and relates to the technical field of data processing. The method comprises the following steps that: a client initiates an online request authorization authentication to an authorization server; after receiving the online request authorization authentication, the authorization server performs authorization authentication on the online request authorization authentication; after the authorization authentication succeeds, the authorization server generates corresponding authorization information and sends an access strategy to the client, so that the client sends an access message to a gateway server according to the access strategy; and the gateway server receives the authorization information and performs access management on the access message according to the authorization information. According to the method, through safety design of a zero-trust storage scheme, a conventional storage safety protection meansis broken through, and all types of accessible data storage is not limited to block storage, file storage and object storage.
Owner:南京云信达科技有限公司
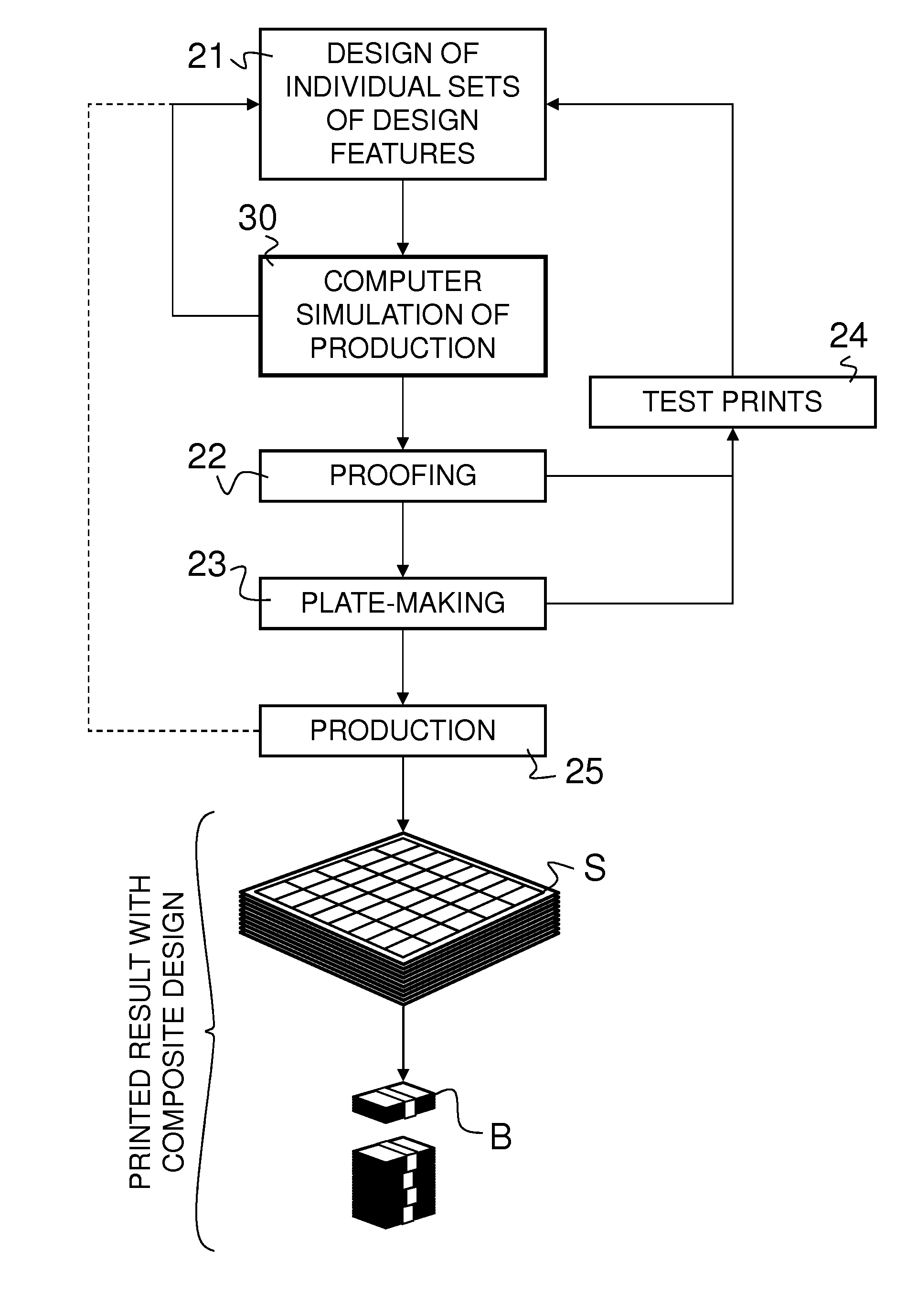
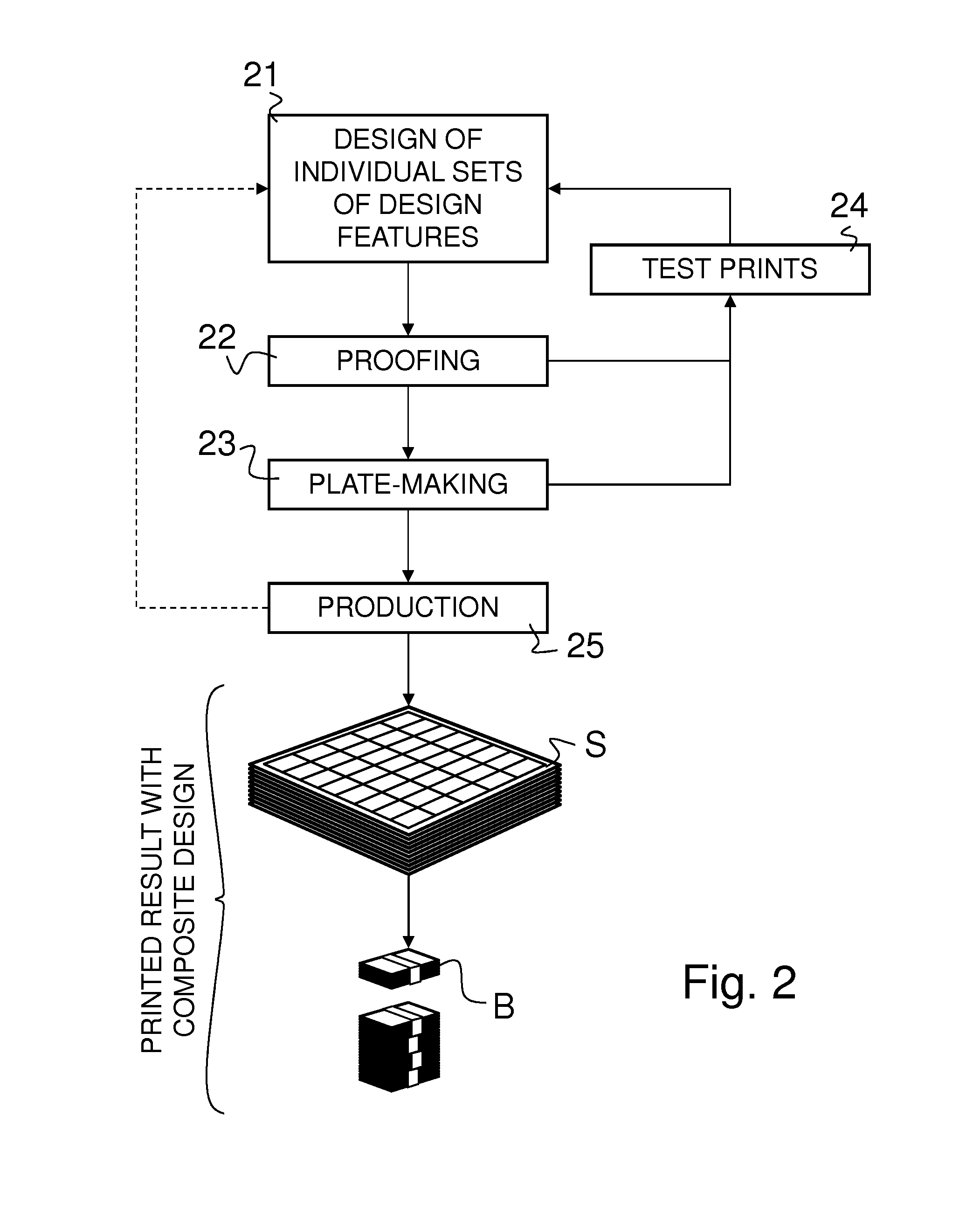
Method of checking producibility of a composite security design of a security document on a line of production equipment and digital computer environment for implementing the same
ActiveUS20150088477A1Efficiently and reliably checkEasy to solvePattern printingDesign optimisation/simulationSecurity designManufacturing line
There is described a method of checking producibility of a composite security design of a security document, in particular of a composite banknote design, on a line of production equipment, the composite security design being the product of a combination of multiple sets of design features that are to be provided on a substrate as a result of a plurality of successive production operations carried out by means of the line of production equipment. The method comprises the steps of (a) providing digital design data representative of the composite security design of the security document, (b) modelizing, in a computer environment, the line of production equipment by means of which the composite security design is intended to be produced, (c) performing a computer simulation of production results of the plurality of successive production operations on the basis of the digital design data and the modelized line of production equipment, and (d) evaluating the computer simulated production results and determining, on the basis of these computer simulated production results, whether the composite security design can be produced on the line of production equipment.
Owner:KBA NOTASYS SA
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com