A realization method of cloud security communication based on an HTTP protocol end
An HTTP protocol and secure communication technology, applied in the implementation field of cloud secure communication based on HTTP protocol, can solve problems such as replay attacks, data tampering with plaintext interface data, and affect business operations, etc., and achieve the effect of ensuring security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
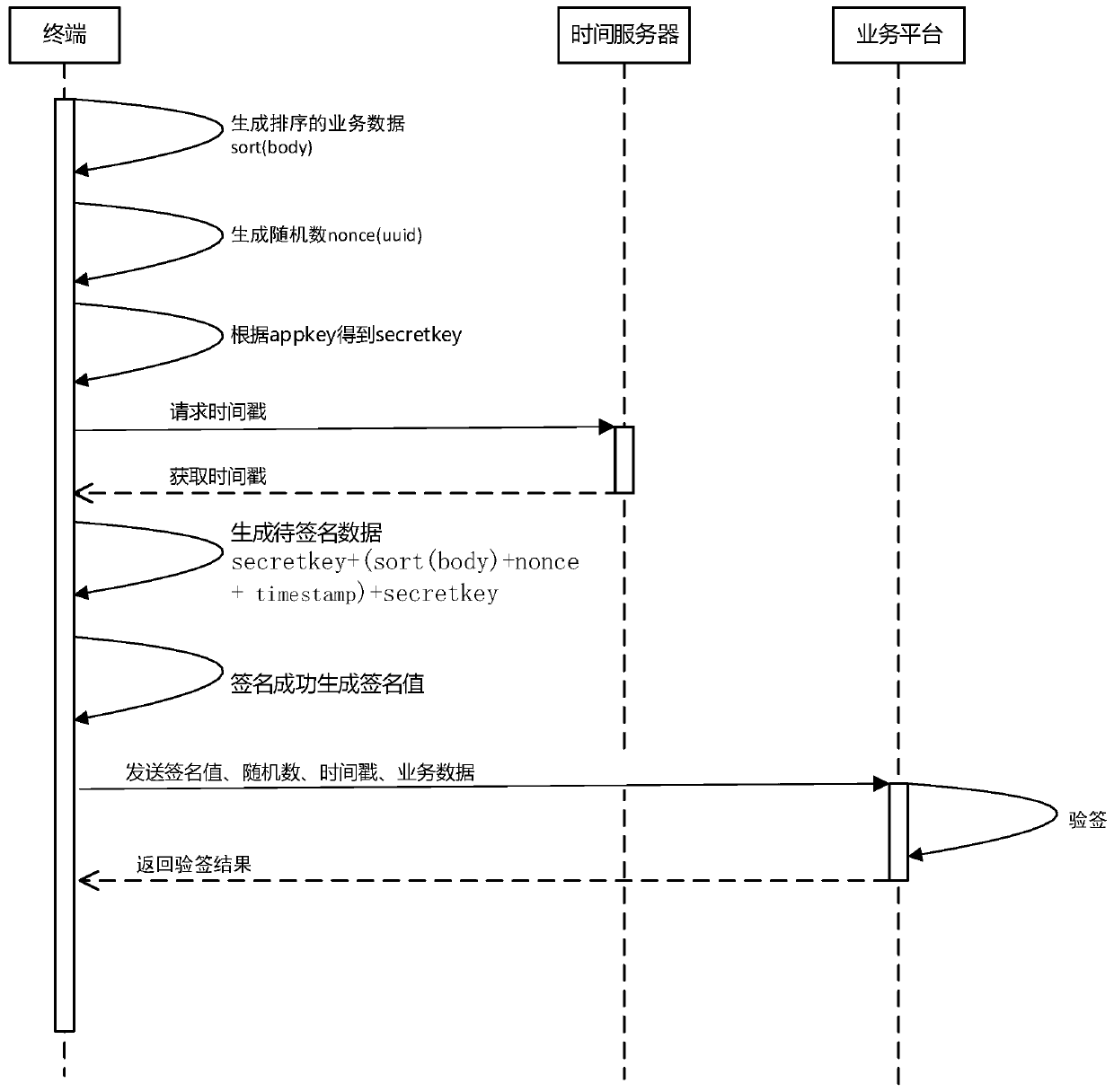
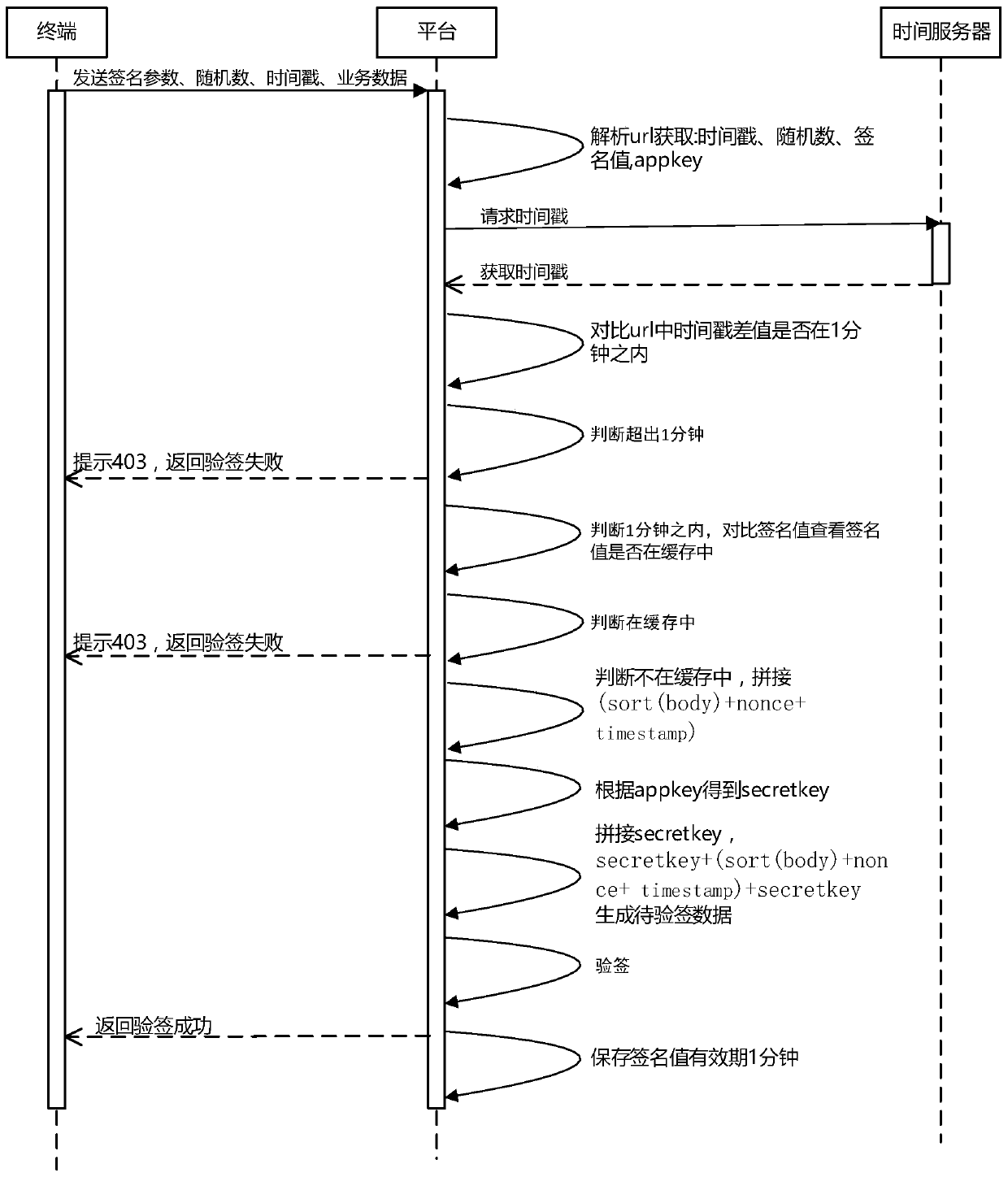
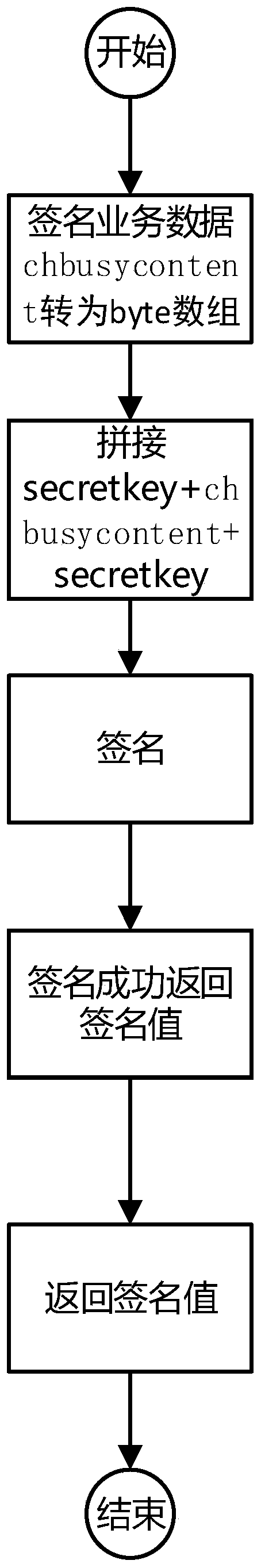
[0026] A method for implementing secure communication between the terminal and the cloud based on the HTTP protocol, including designing a secure API format, designing a new terminal signature data method in the process of verifying the legitimacy of terminal data in the cloud, and designing a method for verifying terminal signature data in the cloud. In the process of verifying the legitimacy of cloud data, design a new cloud signature process and terminal signature verification process, wherein the terminal signature data method includes the combination method of signature data, the sorting method of body data and the terminal signature process.
[0027] Wherein, when the terminal makes a service request to the cloud, it needs to first sign and the cloud performs signature verification, specifically, the terminal digitally signs the requested service data. When requesting, send the signature value, business data, timestamp, and random number (uuid) to the cloud server. After ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com