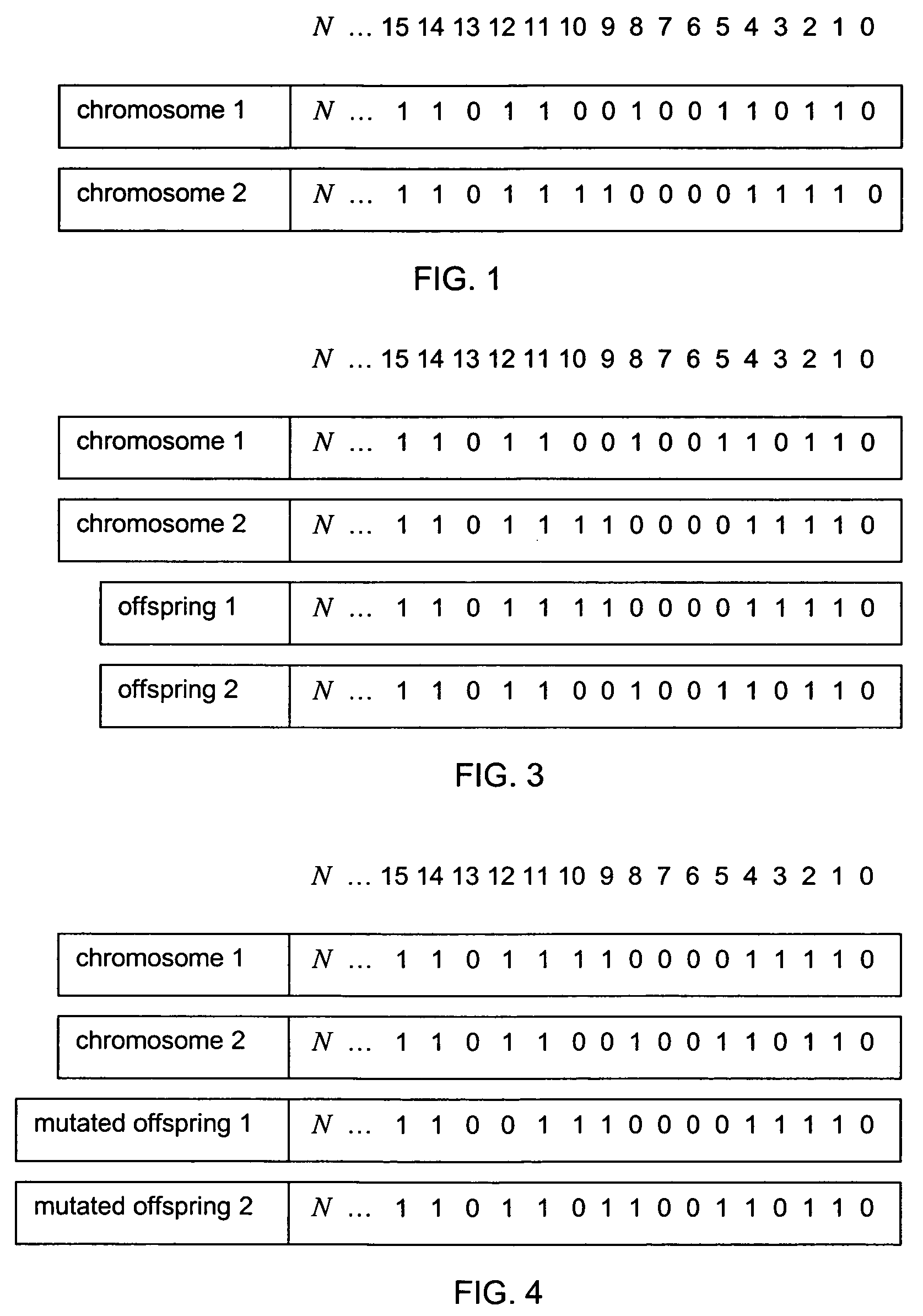
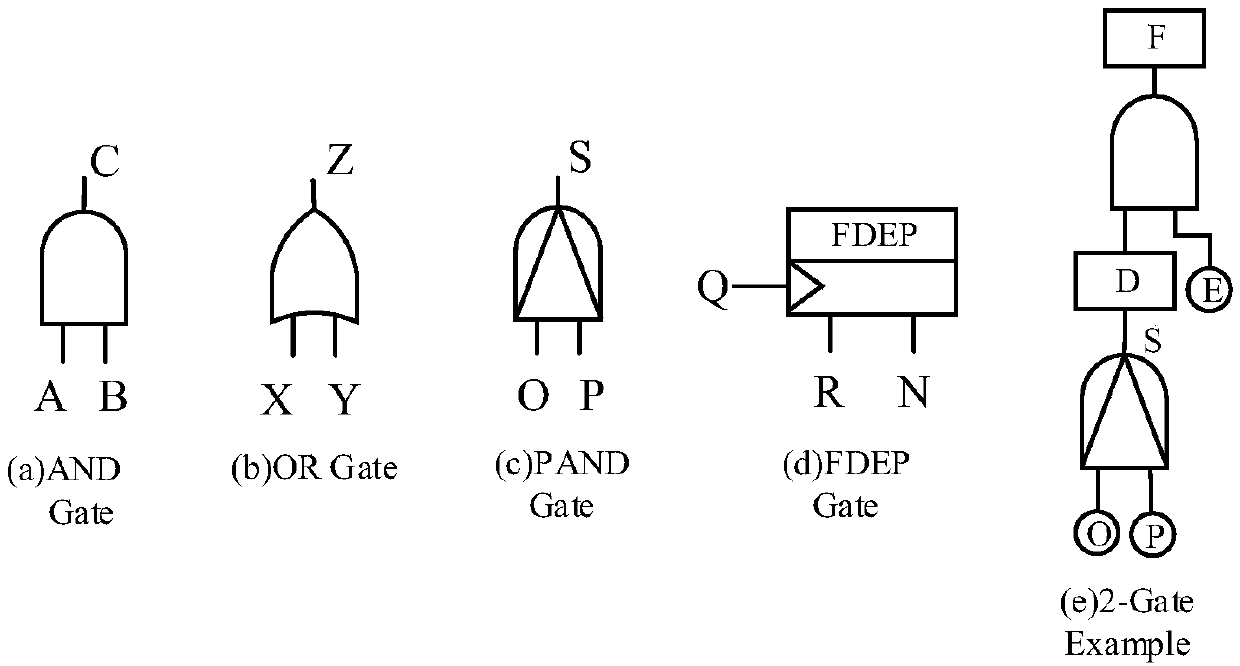
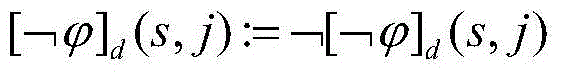Patents
Literature
88 results about "Temporal logic" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In logic, temporal logic is any system of rules and symbolism for representing, and reasoning about, propositions qualified in terms of time (for example, "I am always hungry", "I will eventually be hungry", or "I will be hungry until I eat something"). It is sometimes also used to refer to tense logic, a modal logic-based system of temporal logic introduced by Arthur Prior in the late 1950s, with important contributions by Hans Kamp. It has been further developed by computer scientists, notably Amir Pnueli, and logicians.
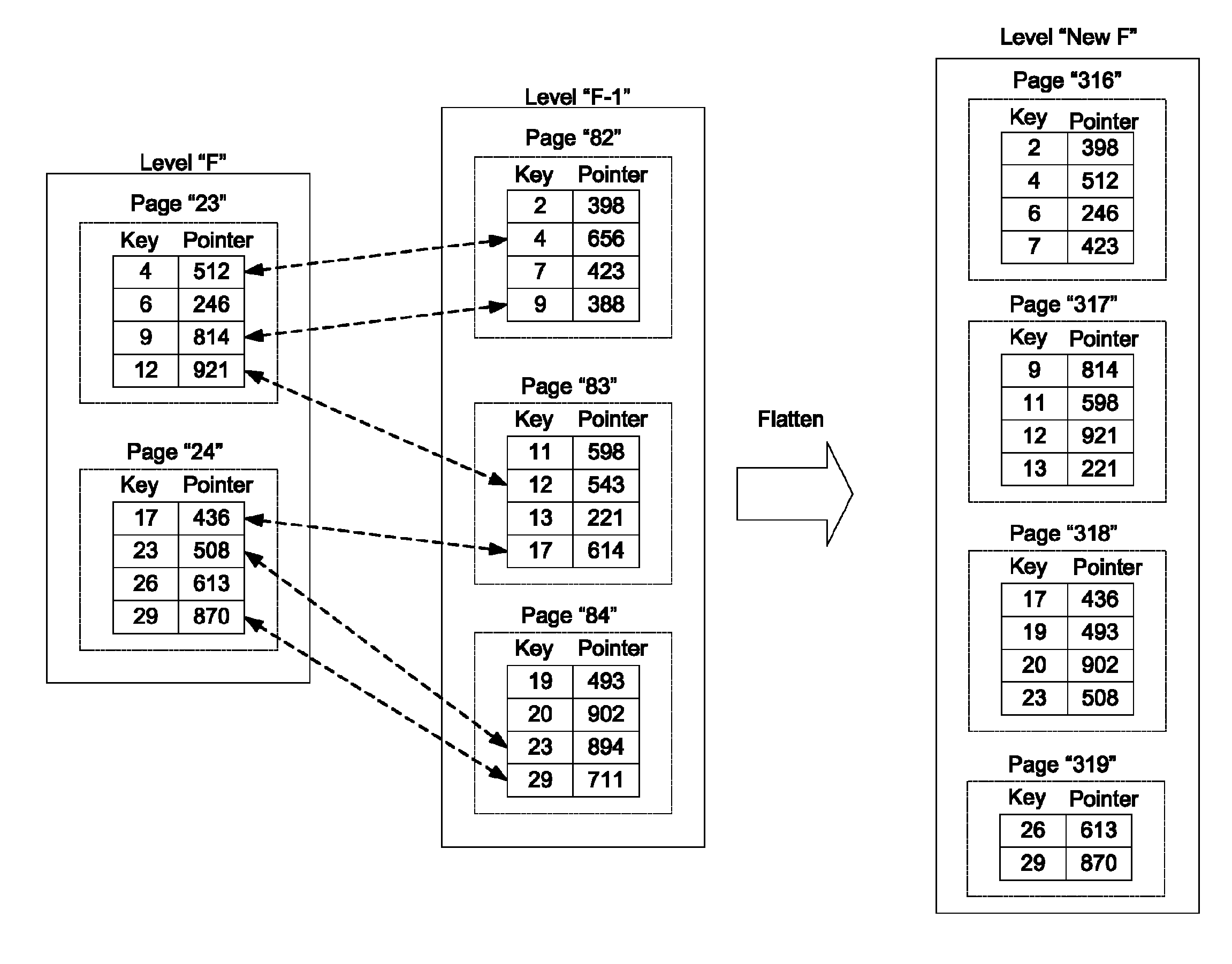
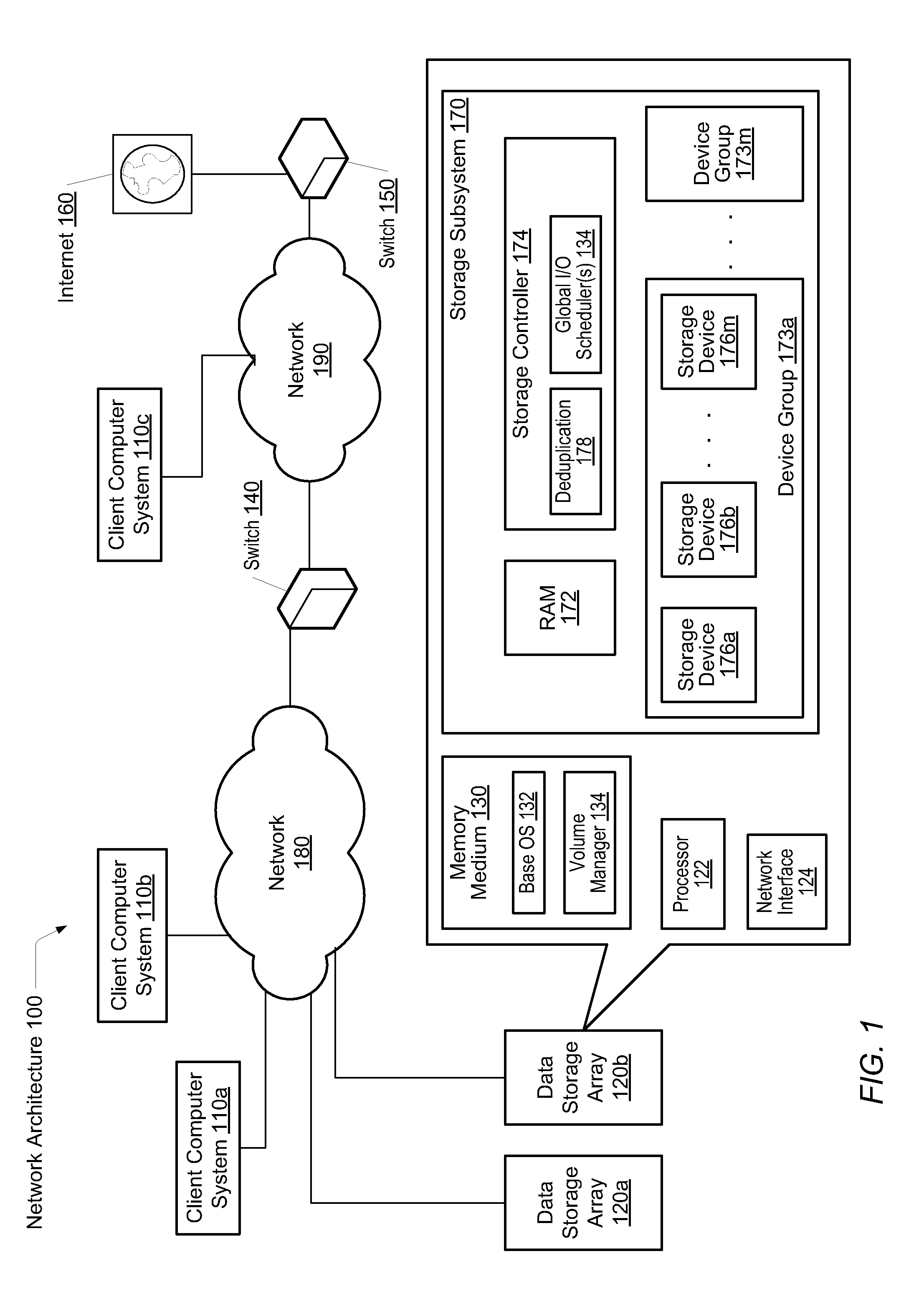
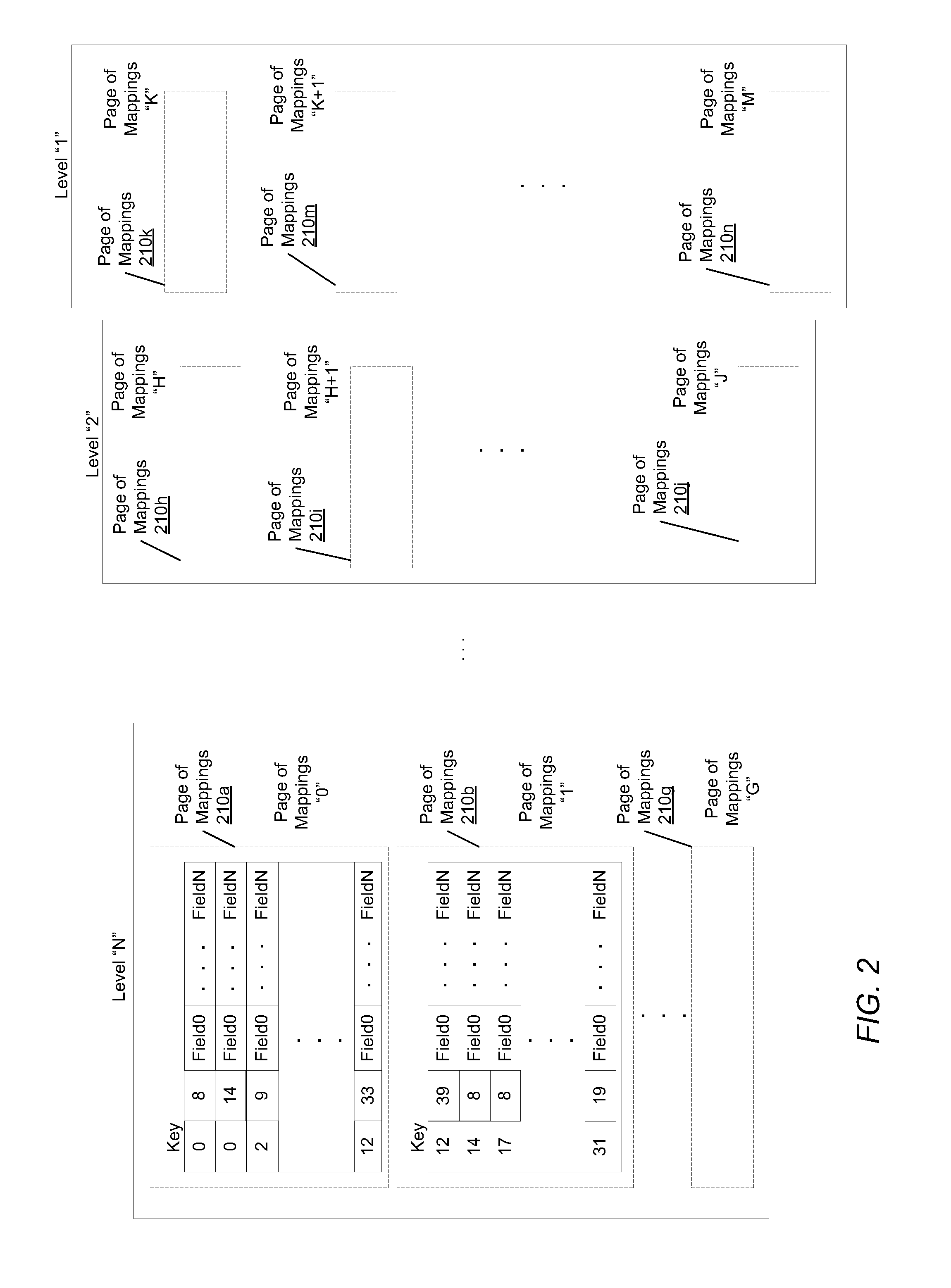
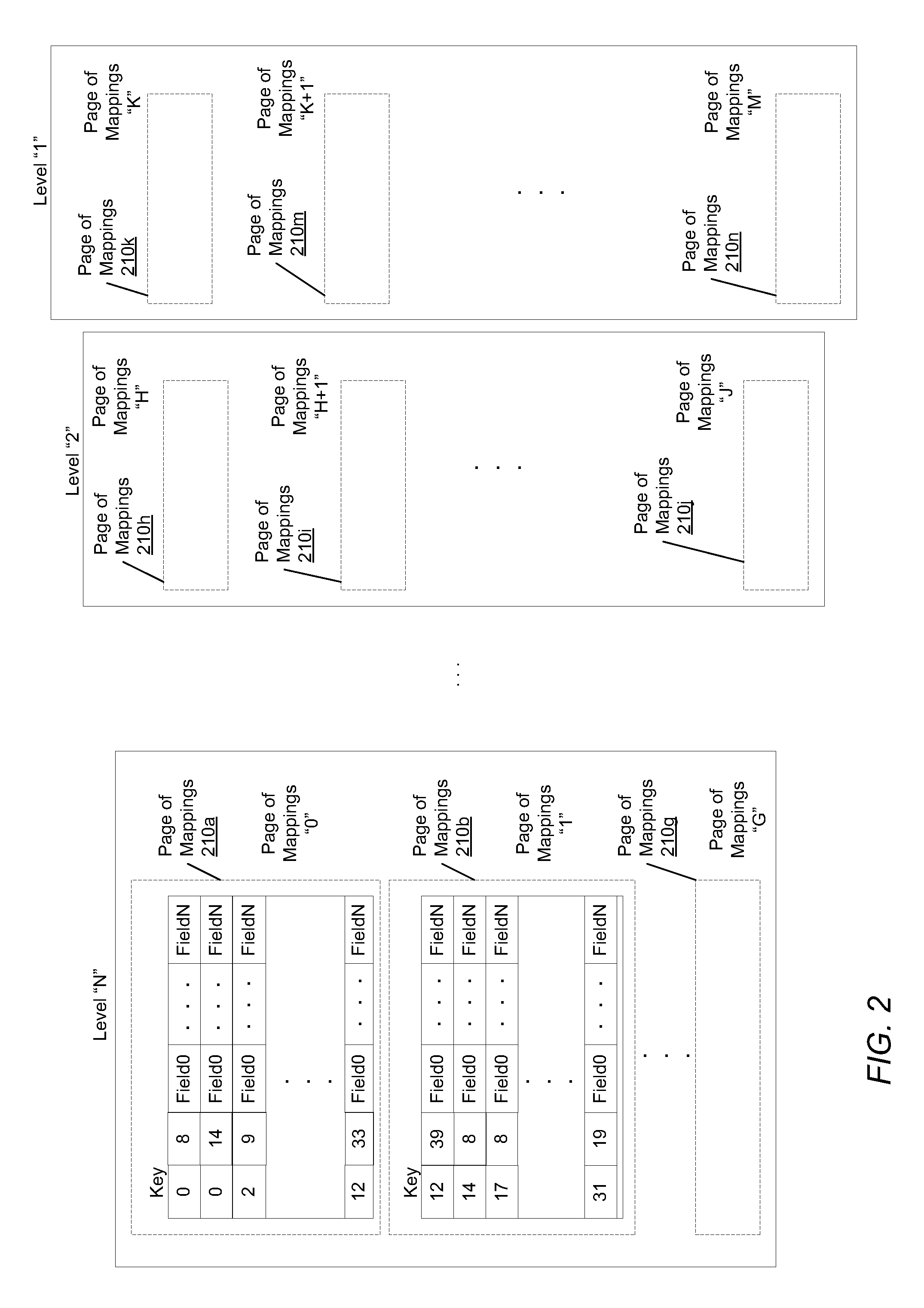
Mapping in a storage system
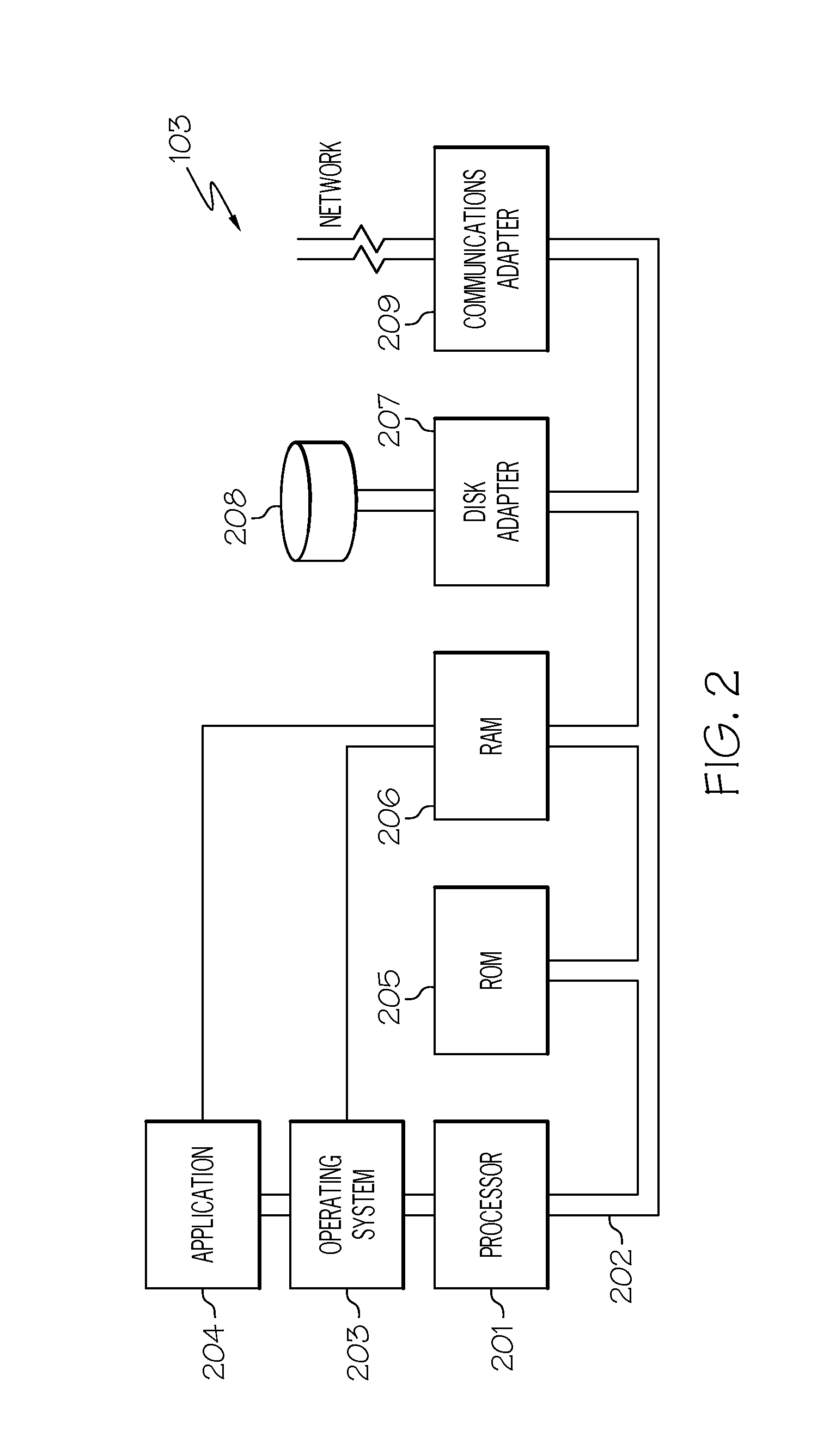
ActiveUS8806160B2Efficient managementInput/output to record carriersDigital data processing detailsTemporal logicOperating system
A system and method for maintaining a mapping table in a data storage subsystem. A data storage subsystem supports multiple mapping tables. Records within a mapping table are arranged in multiple levels which may be logically ordered by time. Each level stores pairs of a key value and a pointer value. New records are inserted in a created new (youngest) level. All levels other than the youngest may be read only. In response to detecting a flattening condition, a data storage controller is configured to identify a group of two or more adjacent levels of the plurality of levels for flattening which are logically adjacent in time. A new level is created and one or more records stored within the group are stored in the new level, in response to detecting each of the one or more records stores a unique key among keys stored within the group.
Owner:PURE STORAGE
Mapping in a storage system
ActiveUS20130046949A1Efficient managementMemory systemsInput/output processes for data processingTemporal logicOperating system
A system and method for maintaining a mapping table in a data storage subsystem. A data storage subsystem supports multiple mapping tables. Records within a mapping table are arranged in multiple levels which may be logically ordered by time. Each level stores pairs of a key value and a pointer value. New records are inserted in a created new (youngest) level. All levels other than the youngest may be read only. In response to detecting a flattening condition, a data storage controller is configured to identify a group of two or more adjacent levels of the plurality of levels for flattening which are logically adjacent in time. A new level is created and one or more records stored within the group are stored in the new level, in response to detecting each of the one or more records stores a unique key among keys stored within the group.
Owner:PURE STORAGE
System, methods and apparatus for complex behaviors of collectives of intelligent mobile software agents
InactiveUS20060167917A1Optimizes adaptive self-organizing operationImprove productivityDigital data processing detailsArtificial lifeMolecular modellingArtificial neural network
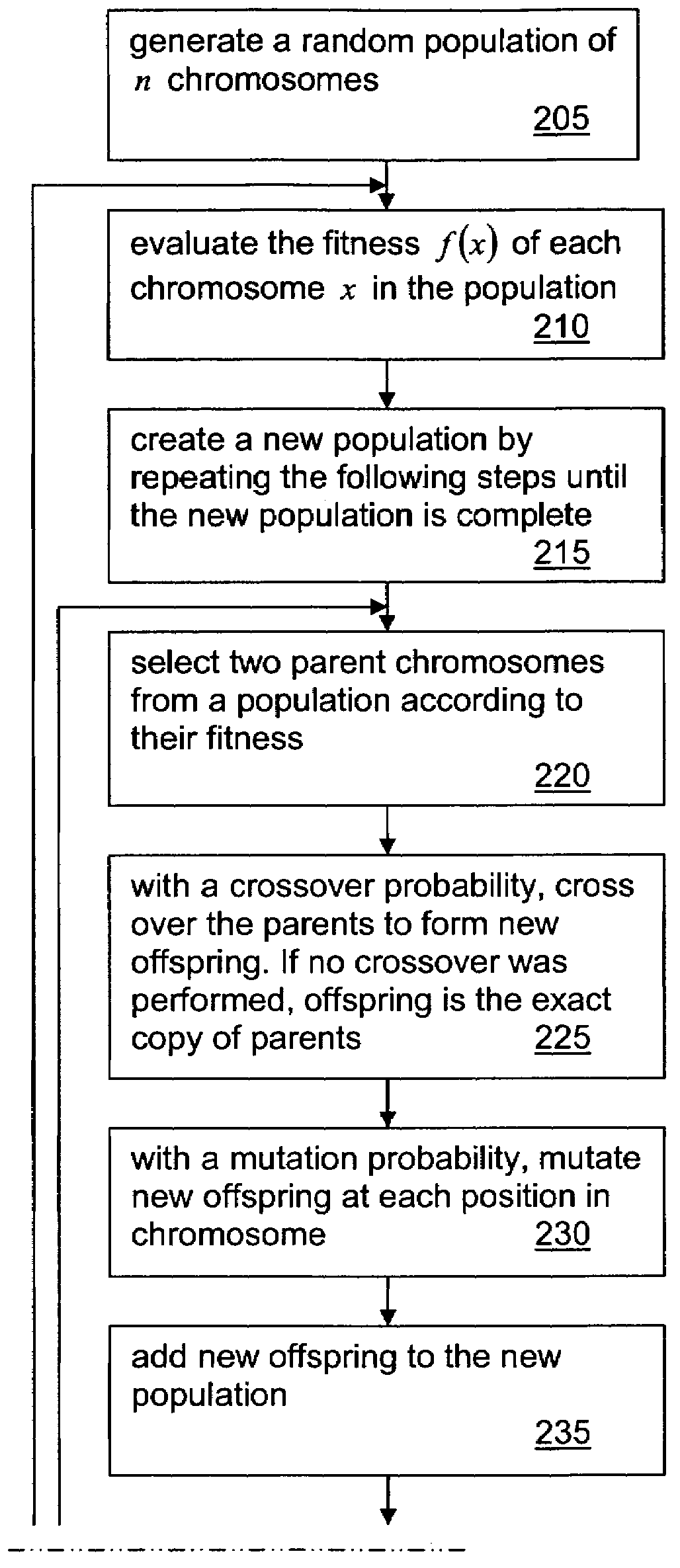
A system, methods and apparatus are described involving the self-organizing dynamics of networks of distributed computers. The system uses intelligent mobile software agents in a multi-agent system to perform numerous functions, including search, analysis, collaboration, negotiation, decision making and structural transformation. Data are continuously input, analyzed, organized, reorganized, used and output for specific commercial and industrial applications. The system uses combinations of AI techniques, including evolutionary computation, genetic programming and evolving artificial neural networks; consequently, the system learns, anticipates and adapts. The numerous categories of applications of the system include optimizing network dynamics, collective robotics systems, automated commercial systems and molecular modeling systems. Given the application of complexity theory and modal and temporal logics to self-organizing dynamic networks, a novel model of intelligent systems is presented.
Owner:SOLOMON RES
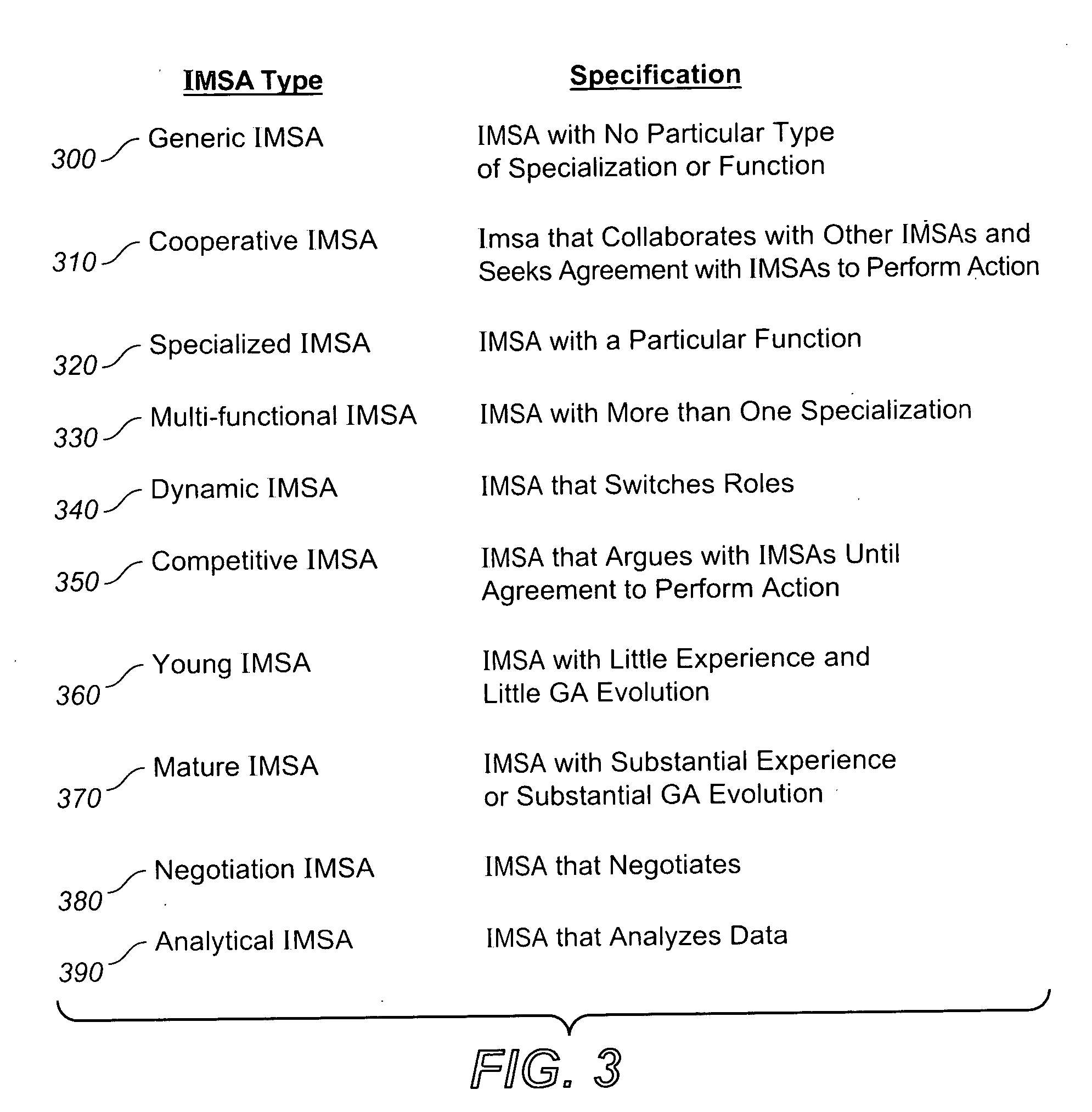
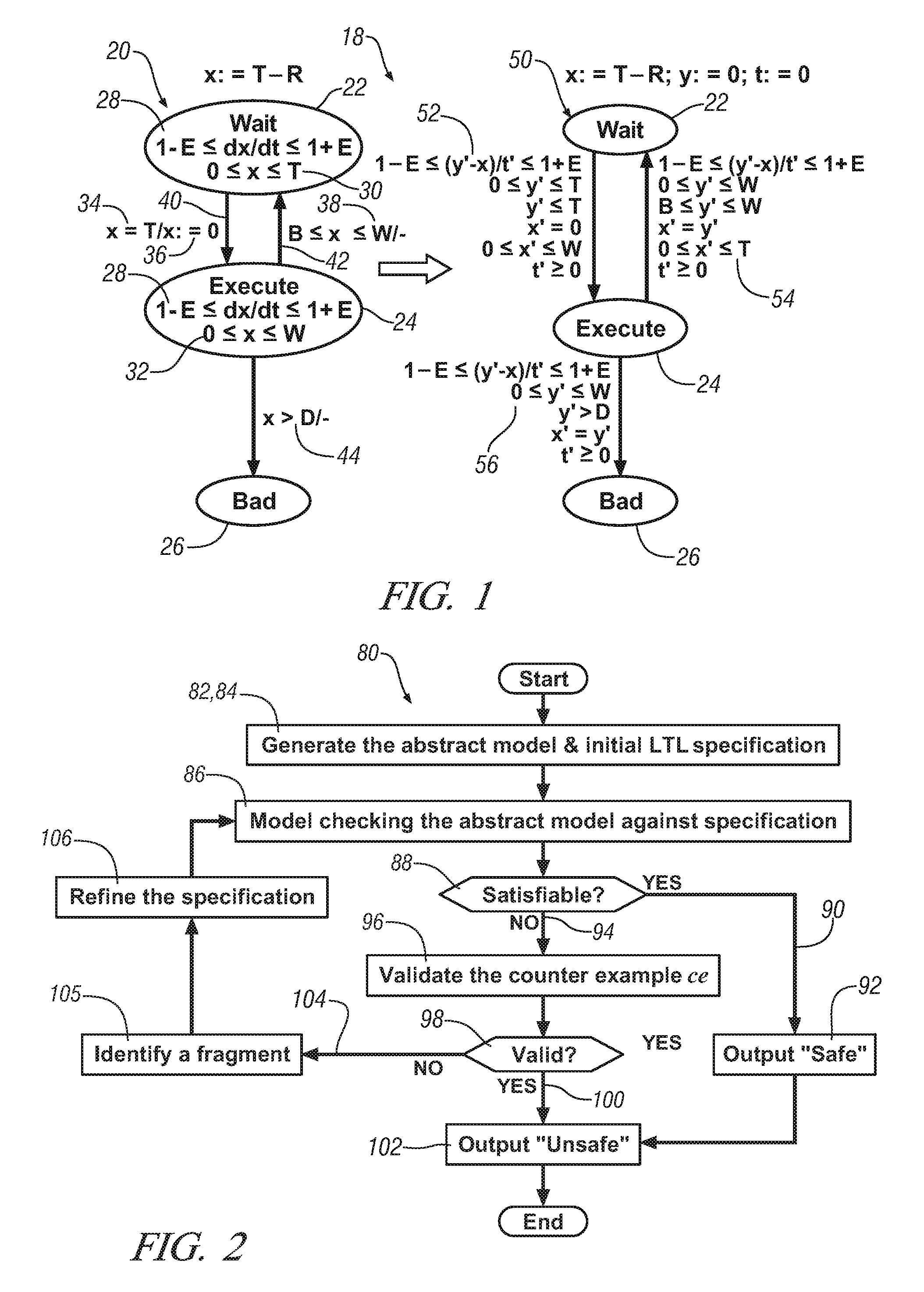
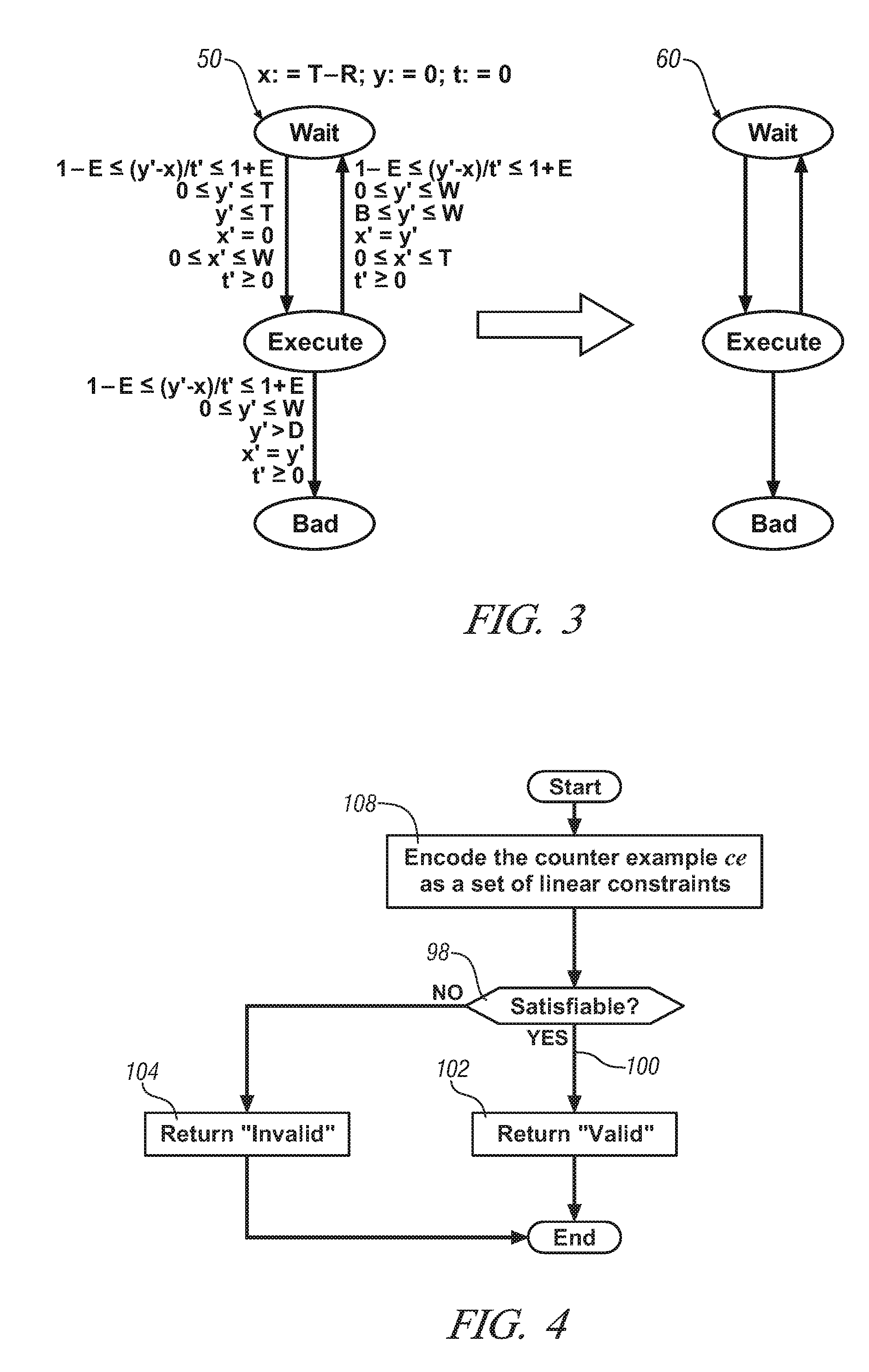
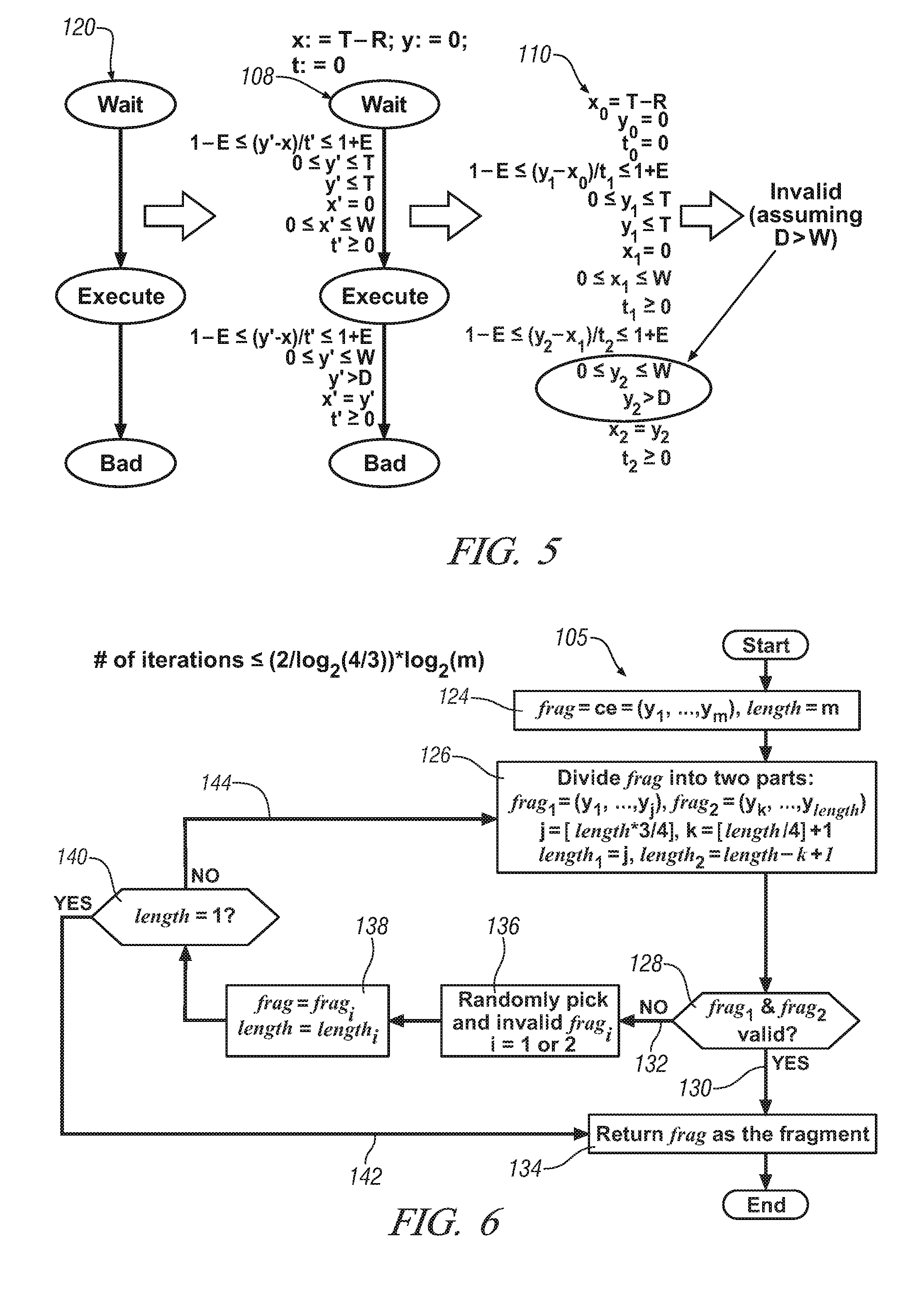
Verification of Linear Hybrid Automaton
The present invention provides a method for verification of linear hybrid automaton by generation an initial abstract model based on an original Linear-Time Temporal Logic (LTL) specification, validating a counterexample using an approach of linear constraints, identifying a fragment in the counterexample by iteratively applying an approach of linear constraints satisfaction in a limited number of times, and refining the original LTL specification based on the fragment derived.
Owner:GM GLOBAL TECH OPERATIONS LLC
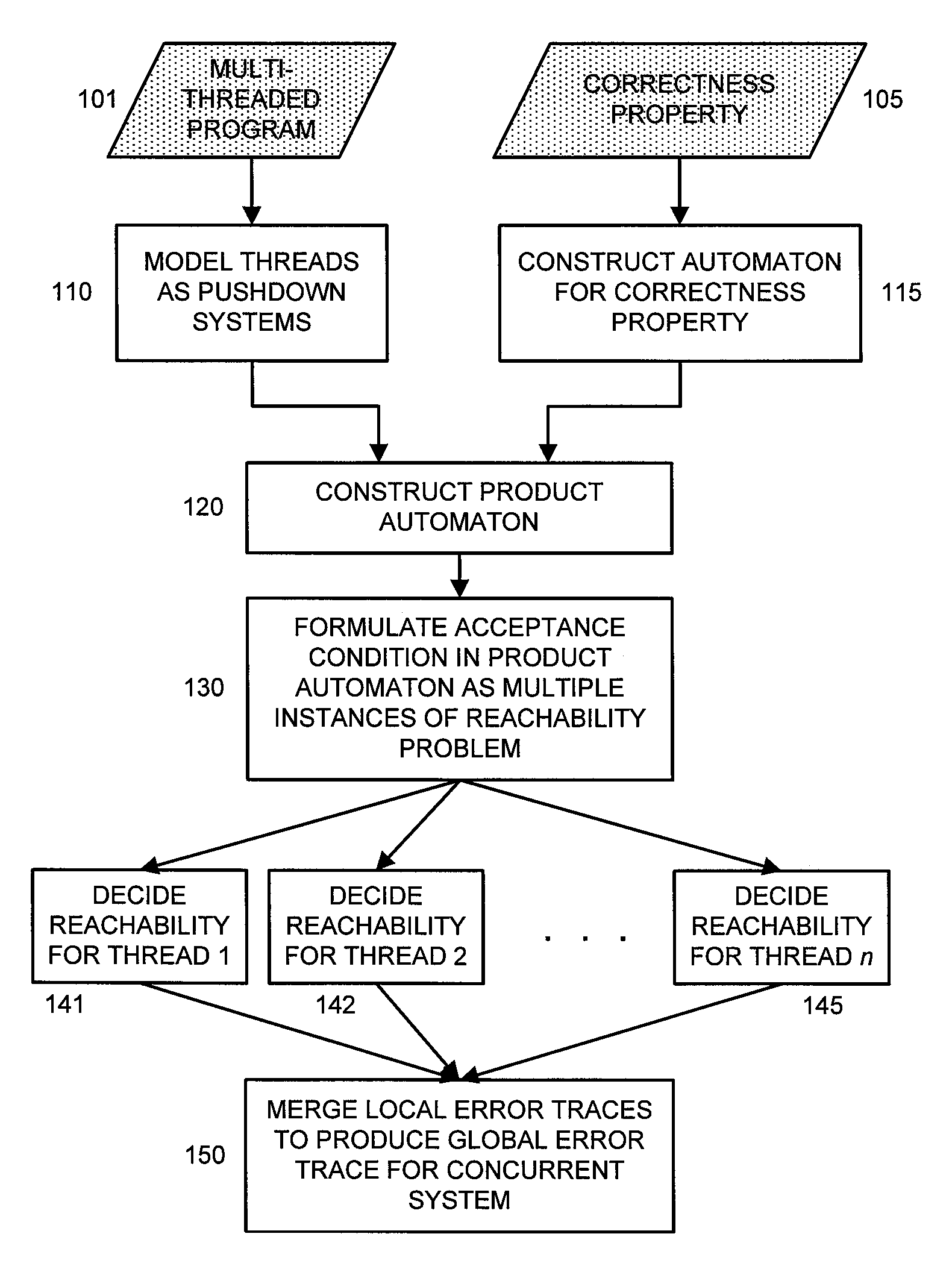
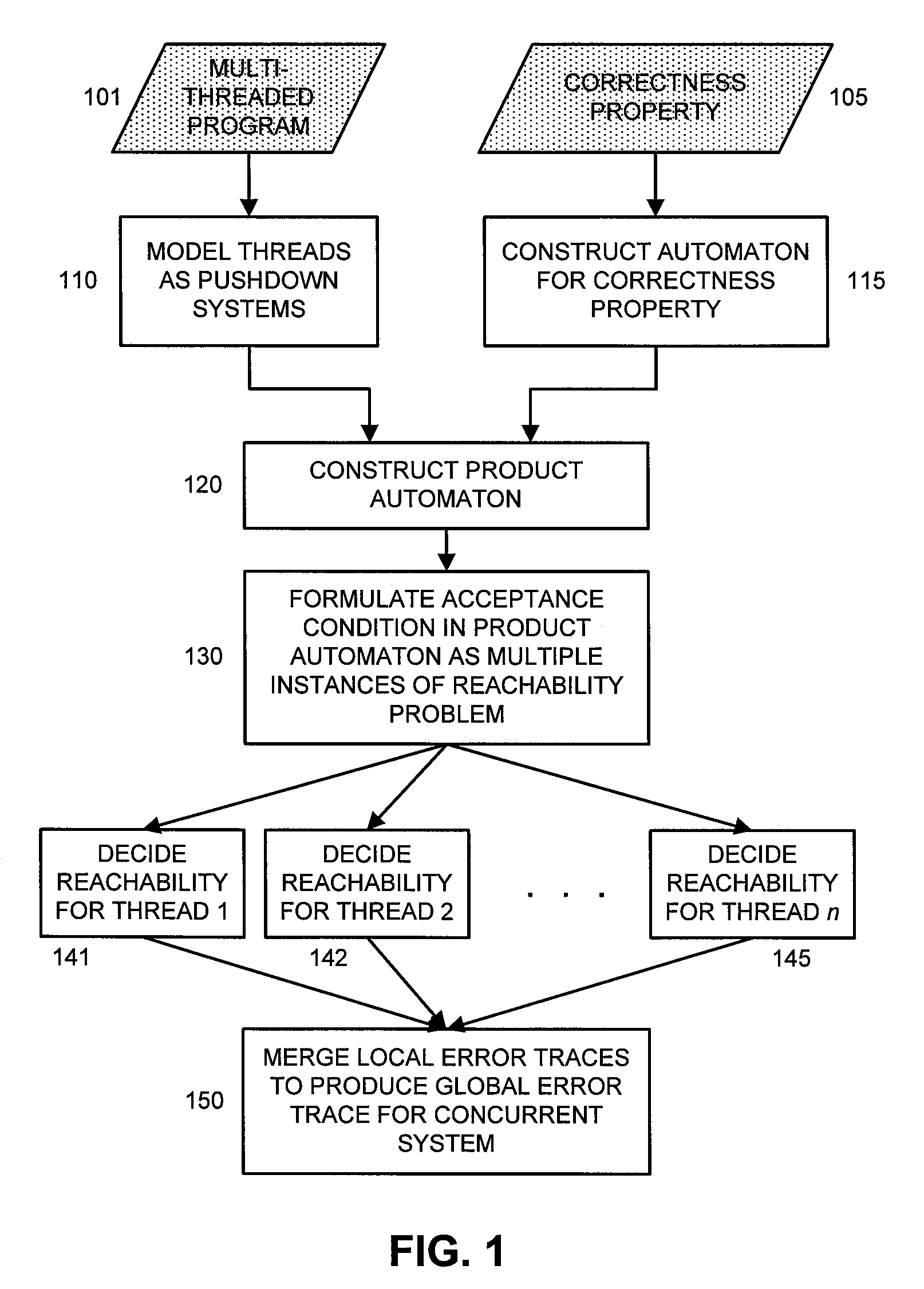
Model Checking of Multi Threaded Software
ActiveUS20060218534A1Avoid problemsError detection/correctionSpecific program execution arrangementsTemporal logicLinearity
A technique for model checking of multi-threaded software is herein disclosed which advantageously can be used to verify correctness properties expressed using temporal logic, e.g., linear time temporal logic and branching time temporal logic. The model checking problem of a concurrent system is decomposed into a plurality of model checking problems on individual threads of the multi-threaded software.
Owner:NEC CORP
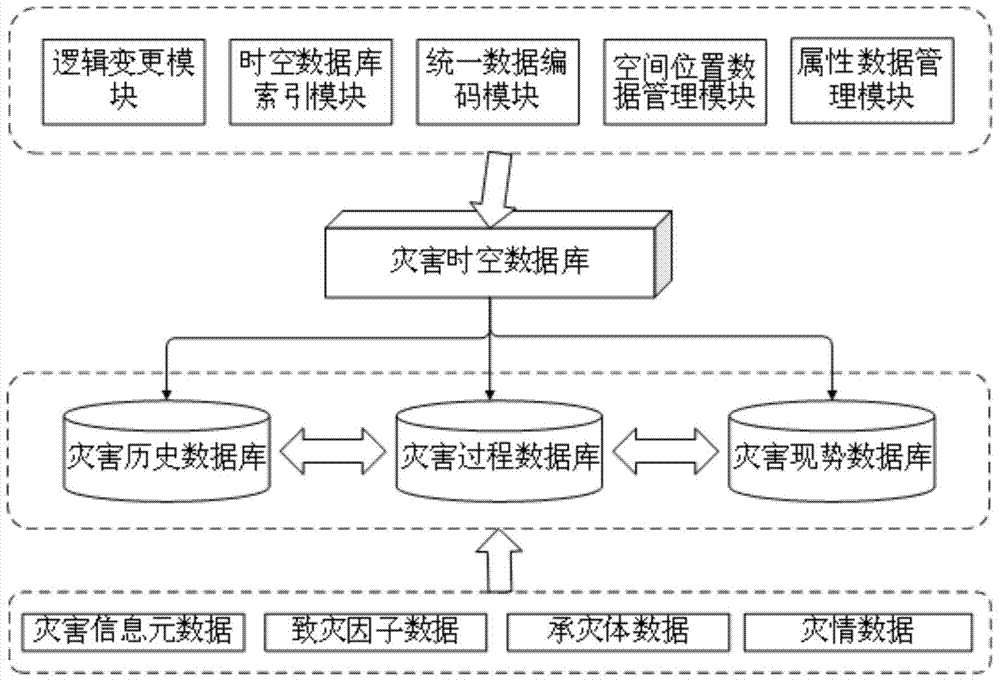
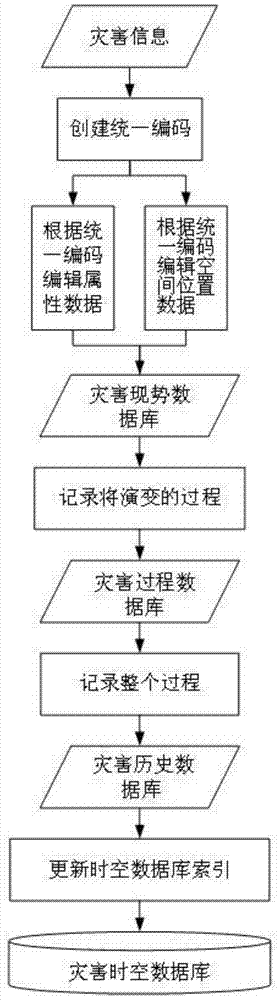
Disaster information spatial-temporal database
InactiveCN103678712AEnhanced backtracking query capabilitiesImprove efficiencySpecial data processing applicationsDatabase design/maintainanceCode moduleTemporal database
The invention provides a disaster information spatial-temporal database, which comprises three disaster information databases including a disaster current simulation database, a disaster process database and a disaster historical database, wherein a unified coding module carries out layered coding on the received disaster information data, an attribute data management module and a space position management module guide in disaster information attribute data and space position data to the corresponding disaster information database, the disaster information data is transmitted among all disaster information databases through a logic conversion module, a spatial-temporal database index module builds updating index for the disaster information spatial-temporal database according to the time sequence, the logic conversion module and the spatial-temporal database index module form the basis of the disaster information spatial-temporal database, and the preparation is made for the disaster attribute management and maintenance, spatial-temporal logic index conversion and maintenance, statistics data entry, index and spatial-temporal inquiry. The disaster information spatial-temporal database solves the problems of lower work efficiency and high data redundancy during the realization of spatial-temporal data storage, management and historical review.
Owner:SHANGHAI NORMAL UNIVERSITY
Symbolized model detection method
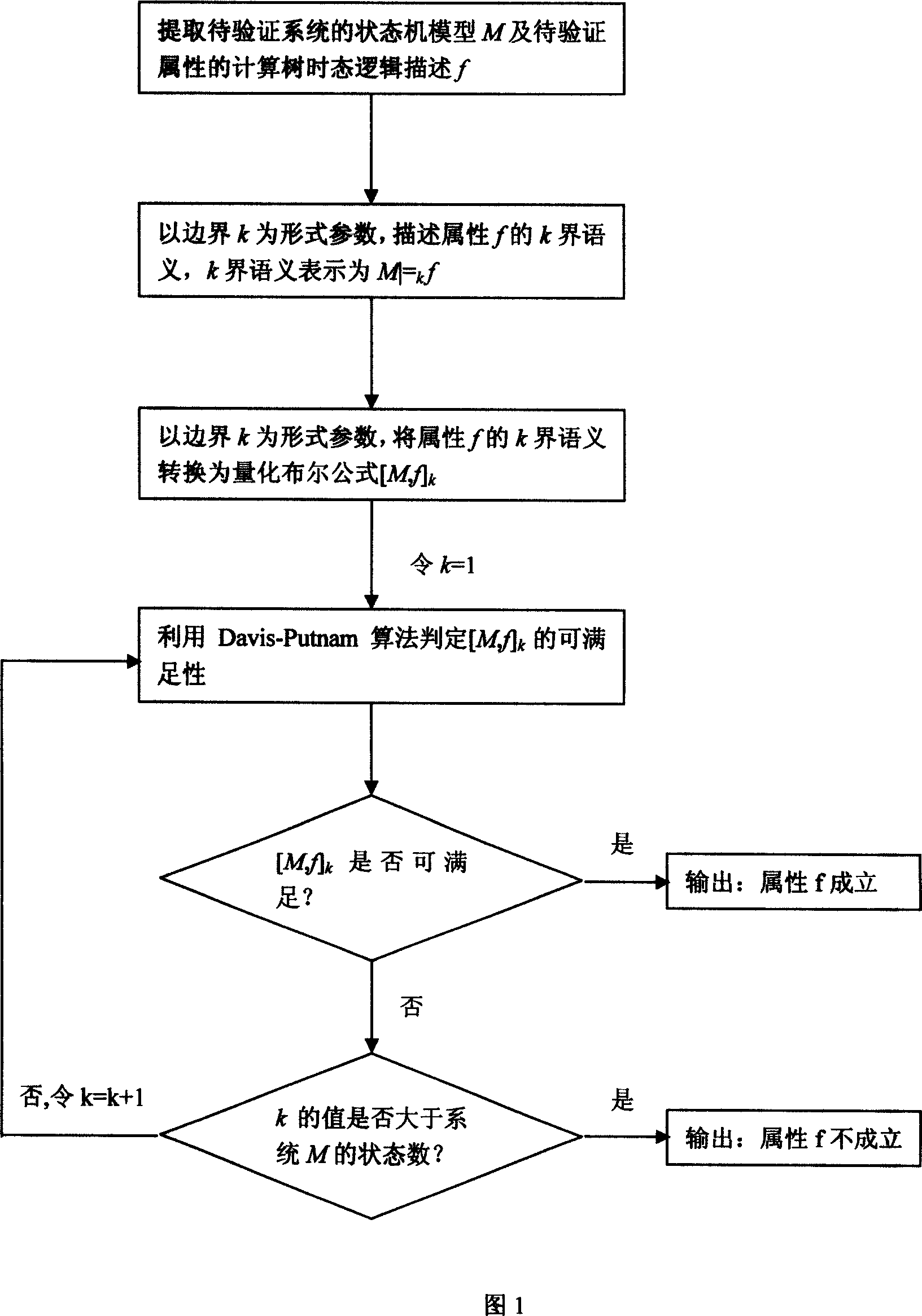
InactiveCN101013452AOvercoming the state space explosion problemImprove reliabilitySpecial data processing applicationsTemporal logicModel testing
This symbol model detection method is a method to make the model testing practical; the main principle is to use Boolean formula quantitative determination to instead of the CTL model testing. Their method: 1.) extract state machine M of the tested system and the attributes of the tested tree temporal logic description; 2.) taking border k as the form parameters, describe k sector semantics of the attributes f; 3.) taking border k as the form parameters, convert the k sector semantic of attribute f to quantify Boolean formula [M, f] k: 4.) progressive determine whether the system M meets the reliable attribute f: the approach integrates the advantages of symbol model testing based on binary decision diagram and bounded model checking based proposition equitation meeting judgment, also overcomes their shortcomings, which are not dependent on the sort of Boolean variables, or dependent on the property to verify the full name attribute.
Owner:JIANGSU UNIV
High real-time multichannel data acquisition system
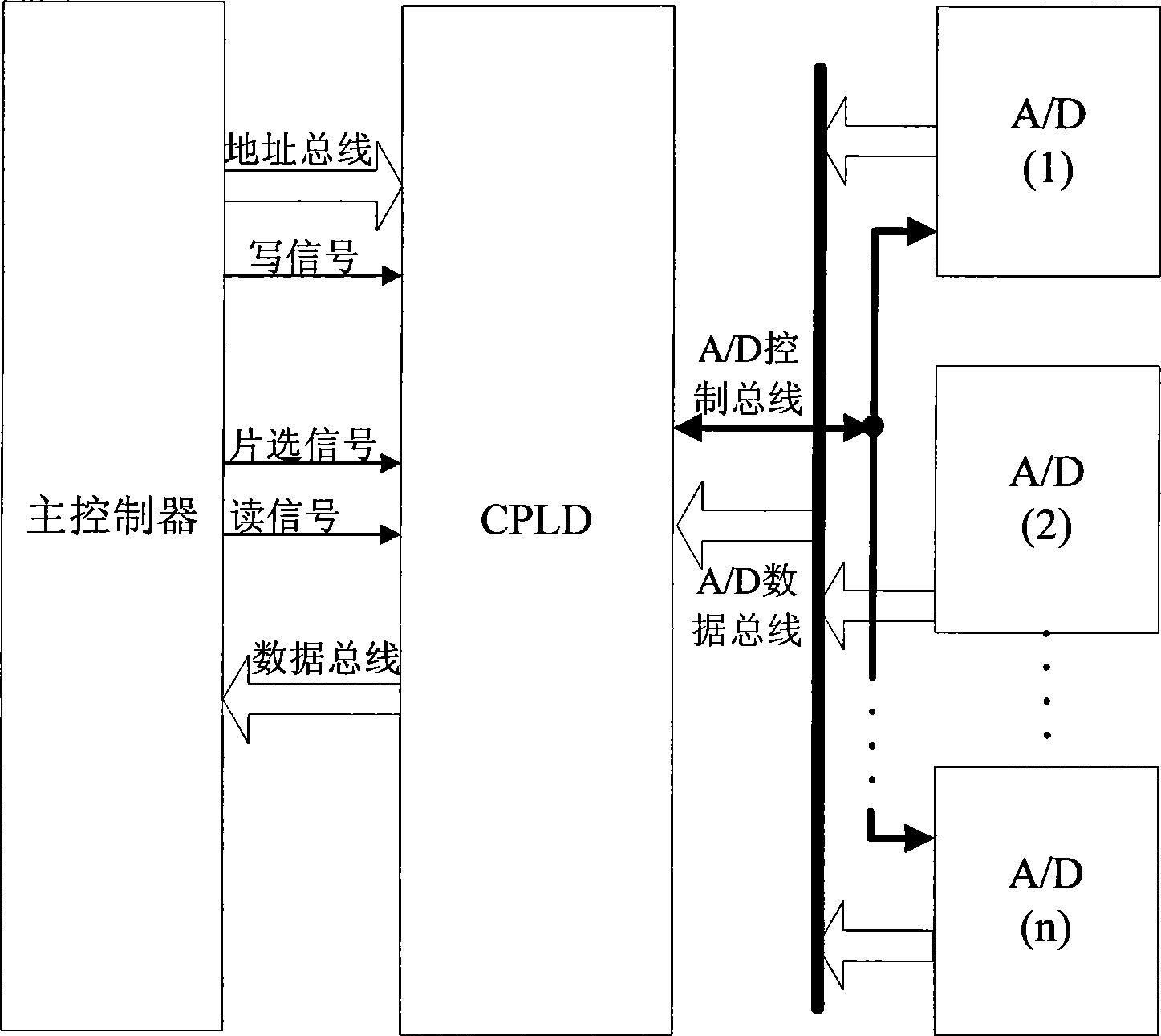
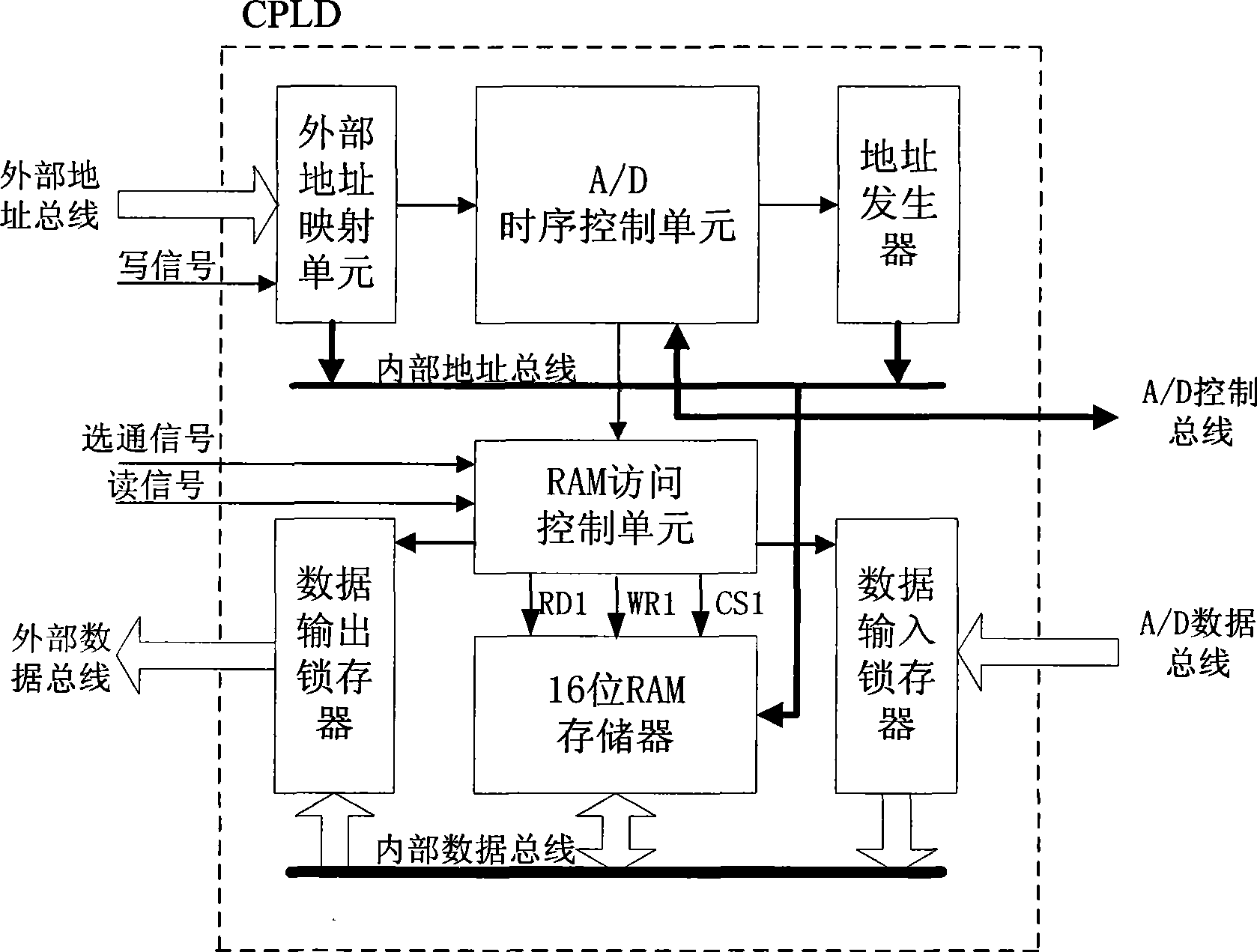
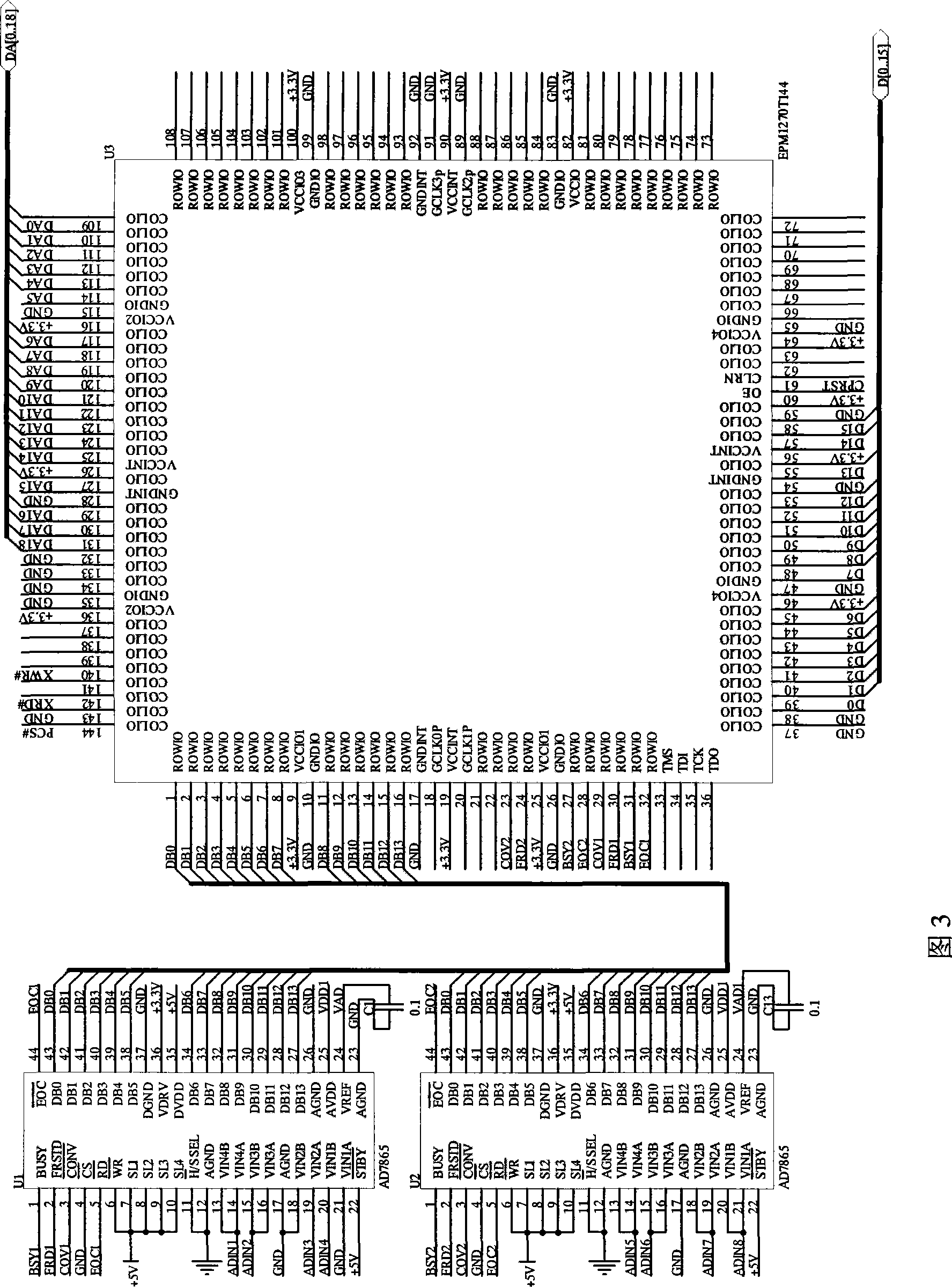
InactiveCN101364097AReduce the burden onImprove real-time performanceProgramme controlComputer controlExternal storageTemporal logic
The invention relates to a real-time multichannel data acquisition system which achieves the effect of high-speed high-accuracy real-time data acquisition of multichannel A / D by adopting a programmable logic device and a multichannel high-resolution A / D converter. The system adopts the programmable logic device as the master controller and the intermediate link for the A / D converter. Based on the temporal logic of the programmable logic device, the multichannel A / D are controlled at the same time to complete the high-speed sequential sampling, the sampling value is latched in the programmable logic device and simultaneously mapped to the external address space of the master controller, and the A / D sampling result is read from the master controller and converted to the visit to an external storage, thereby ensuring the high-speed real-time transmission characteristics of the multichannel data acquisition. The real-time multichannel data acquisition system has the advantages of simple hardware circuit, flexible software design and effect of high-speed high-accuracy real-time data acquisition and transmission; and is widely applied in the fields of network, communication, information domestic appliances and industrial automation.
Owner:中国兵器工业第二〇六研究所
System and method for editing and controlling the behavior of a movable robot
InactiveCN102448678AFriendly editorProgramme controlProgramme-controlled manipulatorGraphicsTemporal logic
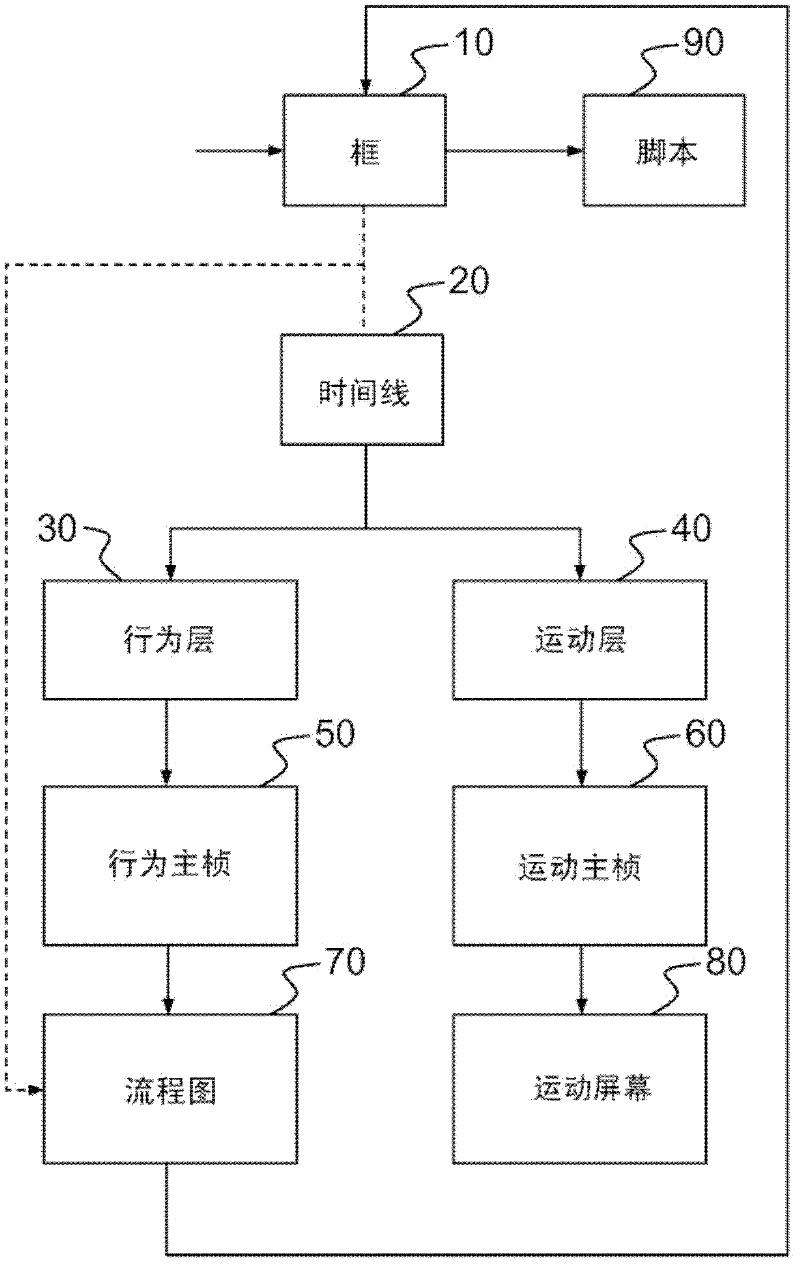
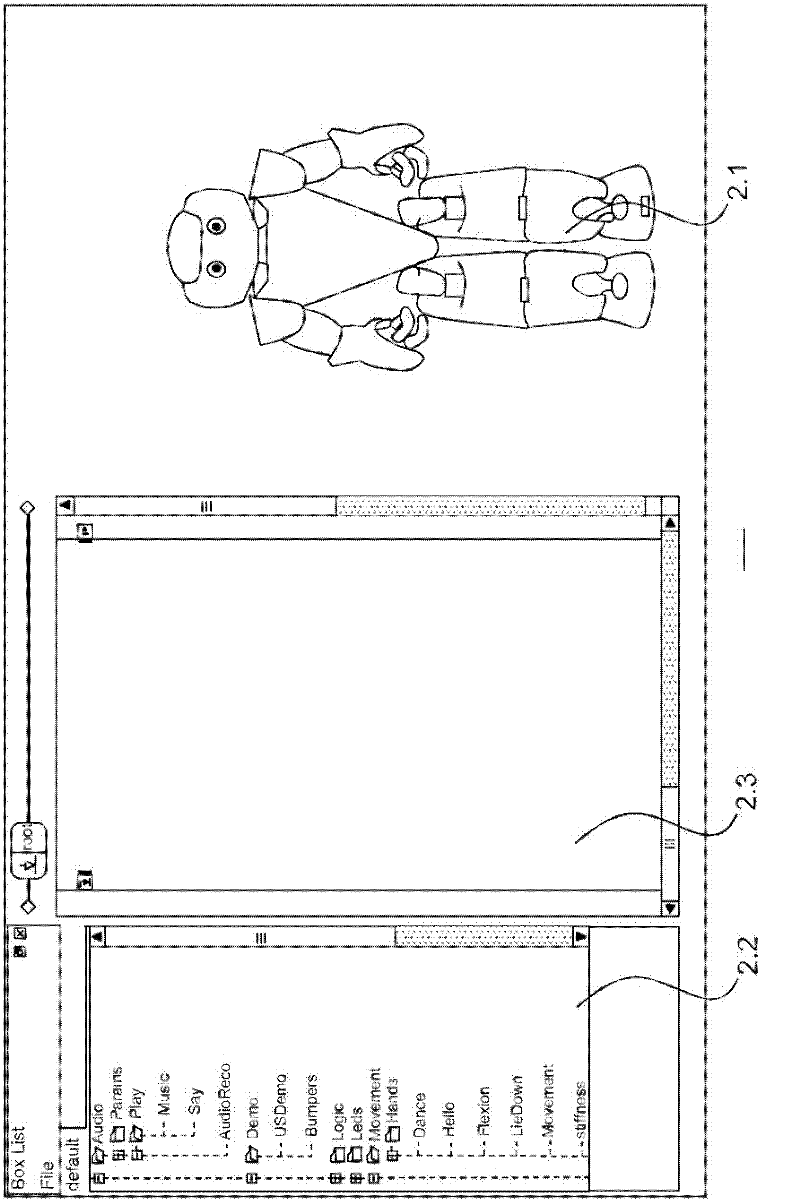
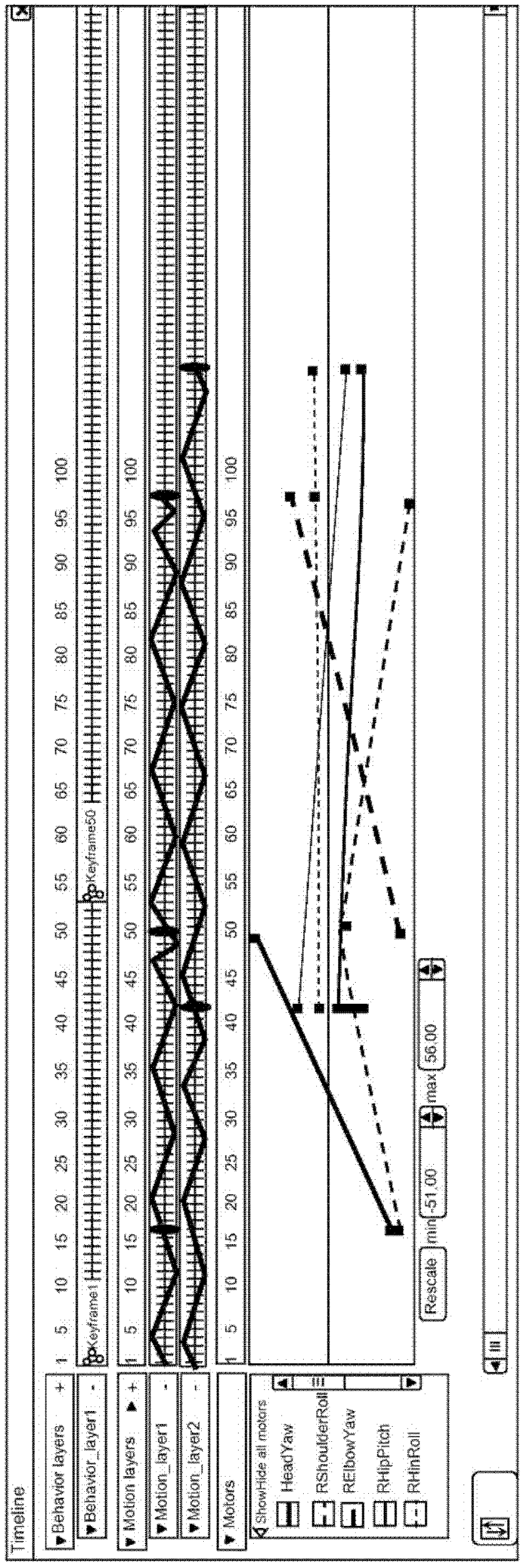
The invention relates to a system and method for editing and controlling the actions of a movable robot. The invention enables in particular the creation and modification of behaviour and movements according to a factual logic as well as to a time logic, the latter controlling the factual logic and thus enabling the synchronisation of the behaviour and movements of the various sub-units of the robot. For this purpose, the system is organised into behaviour and movement layers which comprise sequences of actions and a timeline. The actions may be programmed via boxes interconnected by signals which convey information. The boxes are arranged into a hierarchical structure in which the lowest level includes a script that can be interpreted by a virtual robot which simulates the execution of commands and, when applicable, by a physical robot. The movements of the robot can also be controlled in a graphical manner by means of movement screens.
Owner:ALDEBARAN ROBOTICS SA
Use and construction of time series interactions in a predictive model
InactiveUS20080154808A1Digital computer detailsElectric digital data processingData setTemporal logic
A gene is disclosed for use in a predictive genetic algorithm that performs time series interactions between dataset variables. The temporal logic that performs the interaction is encoded as a binary string.
Owner:EGAN MANAGED CAPITAL II
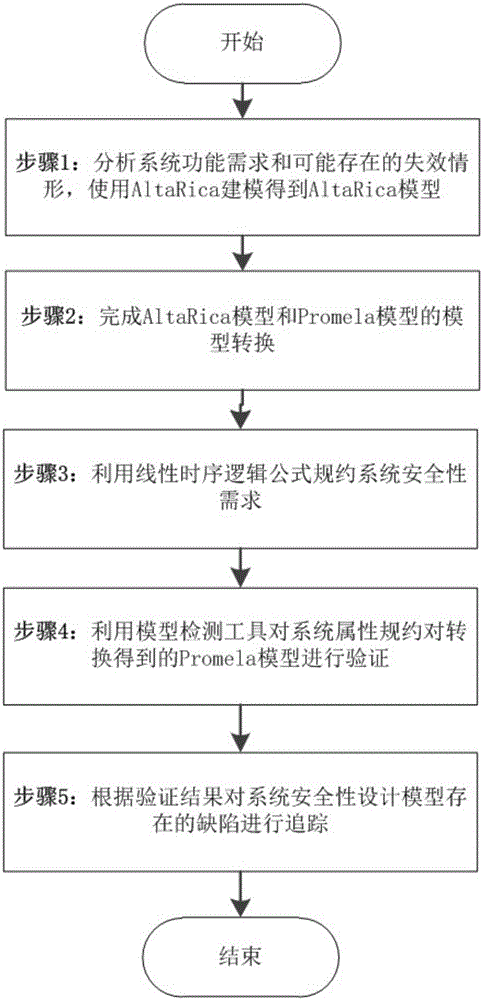
Validation method for design of system security of AltaRica model
InactiveCN105938502ATroubleshoot conversion issuesSpecial data processing applicationsTemporal logicValidation methods
The invention discloses a validation method for design of system security of an AltaRica model. The method comprises following steps: step 1, establishing an AltaRica model for design of system security; step 2, defining the rule for model transformation from the AltaRica model to a Promela model; obtaining the Promela model after conversion of the AltaRica model; step 3, utilizing lineal temporal logic to describe the system security demand in a formalized manner; step 4, utilizing a model detector to validity security of a system model; step 5, obtaining a security demand counter-example that does not satisfy the step 4, tracking the system security design model and finishing validation of the system security design model.The validation method for design of system security of the AltaRica model has following beneficial effects: a model conversion problem is effectively solved; operation on AltaRica is conducted by a model detection tool SPIN; and the validation method provides a new way of thinking for analyses of system security such that conversion rules are accurately defined.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
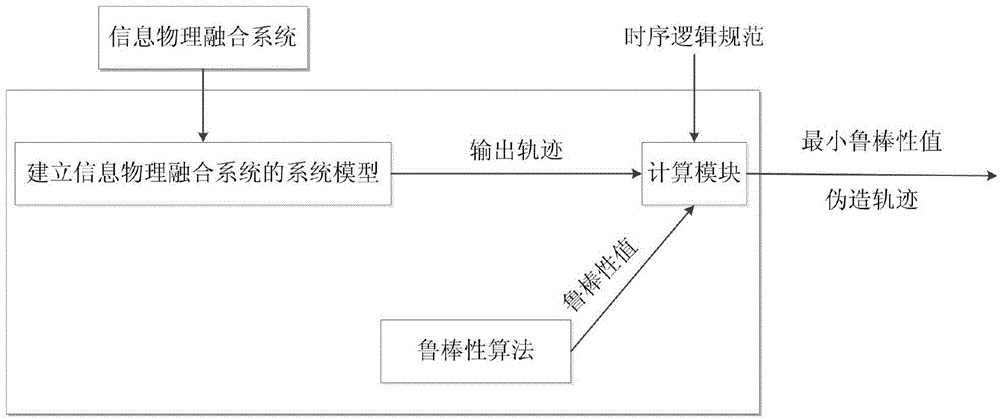
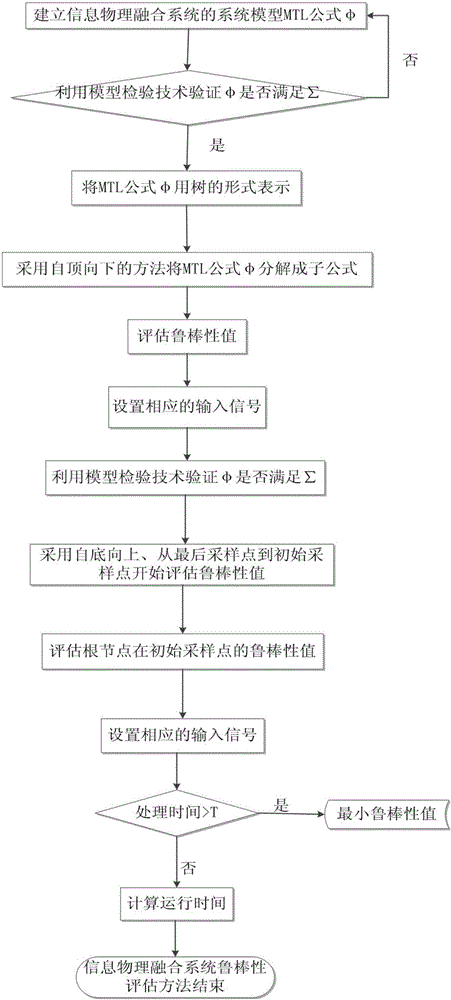
Temporal logic robustness assessment method for information physical fusion system
ActiveCN104657610AEasy to understand the operation processGuaranteed correctnessSpecial data processing applicationsModel testingWork time
The invention provides a temporal logic robustness assessment method for an information physical fusion system. The method comprises the following steps of: firstly, capturing and abstracting the dynamic characteristics of the information physical fusion system by adopting a temporal logic, converting the information physical fusion system into an user-defined system model, and expressing a limited track of the system by use of a temporal logic formula; secondly, verifying the established model by virtue of a model testing technology so as to ensure the correctness of the model, feeding back a counter-example, namely a forged track which does not conform to the formula, in the system to users; finally, performing robustness assessment by adopting an optimization method according to the track and temporal logic standard of the system, setting time domain intervals according to a certain method and a certain procedure, obtaining the robustness values of different state sequences under different sampling points, and feeding back a finally-calculated robustness value which represents the whole system to the users. The linear working time and the constant memory usage are realized, the memory space can be saved, the working time of the system is reduced, and the efficiency of the system is improved.
Owner:NANJING UNIV OF POSTS & TELECOMM
Hysteretic controlled switch regulator with fixed off time
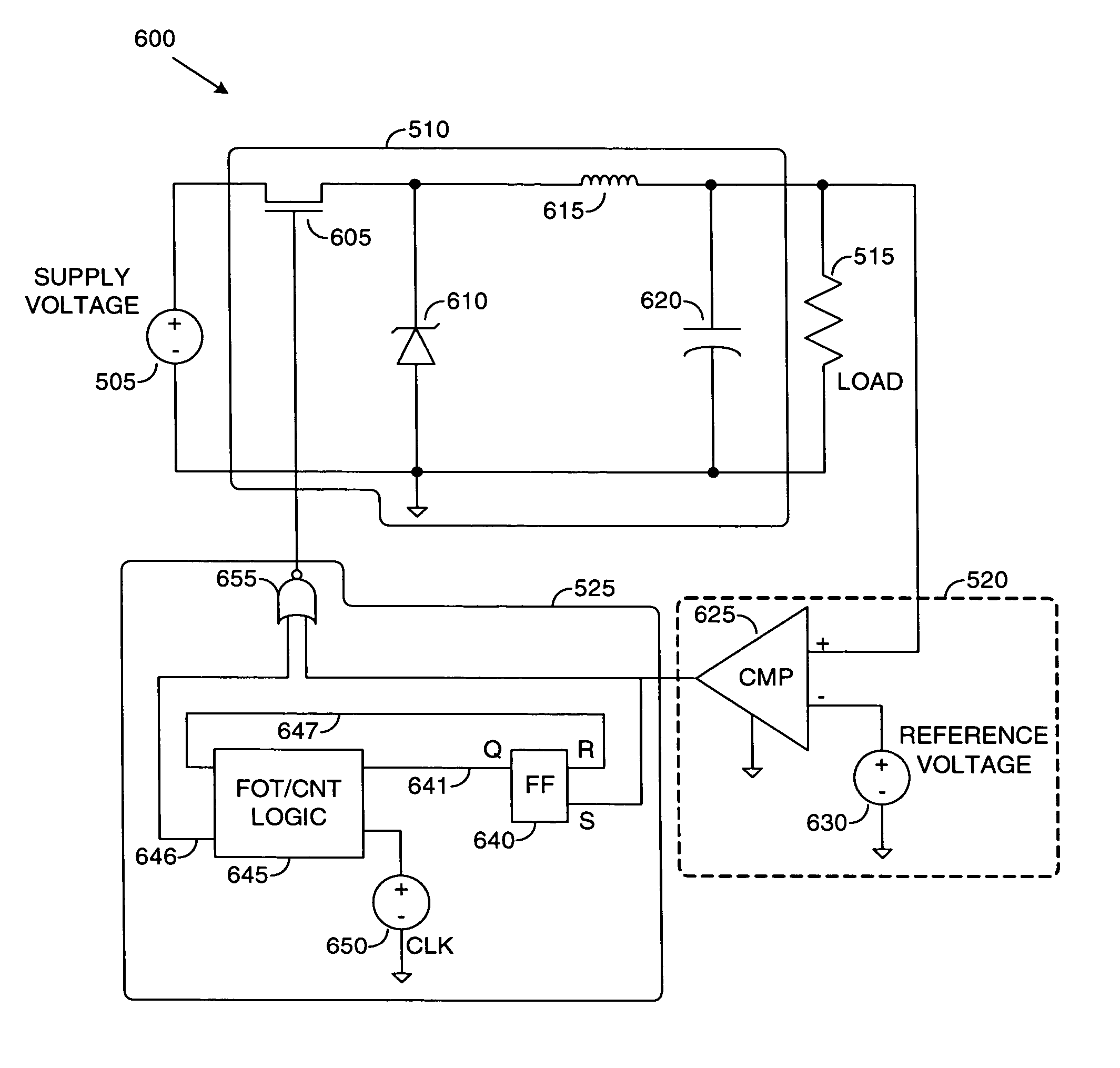
ActiveUS7034512B2Operation is requiredReduce overheadDc network circuit arrangementsDc-dc conversionTemporal logicVoltage reference
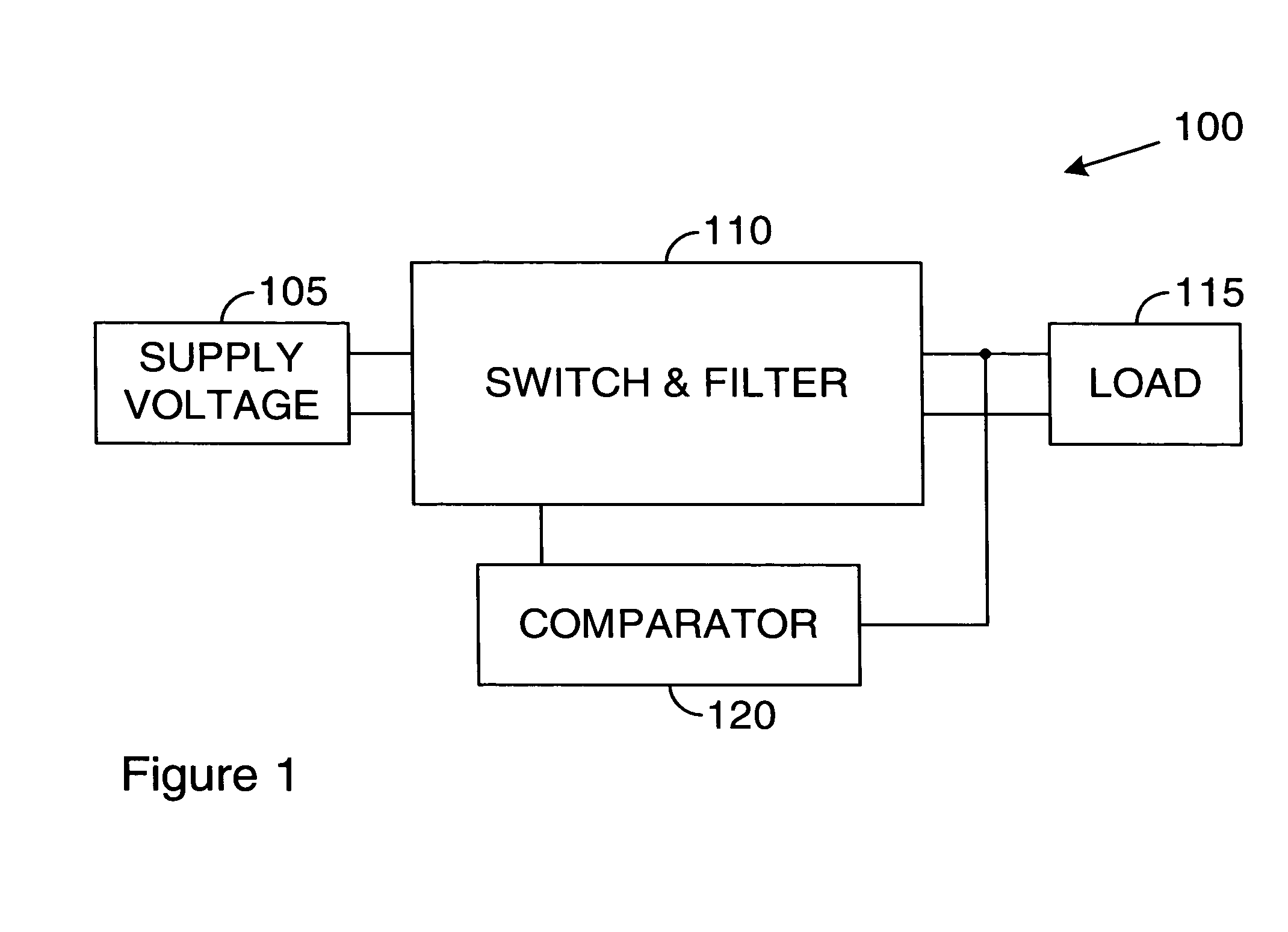
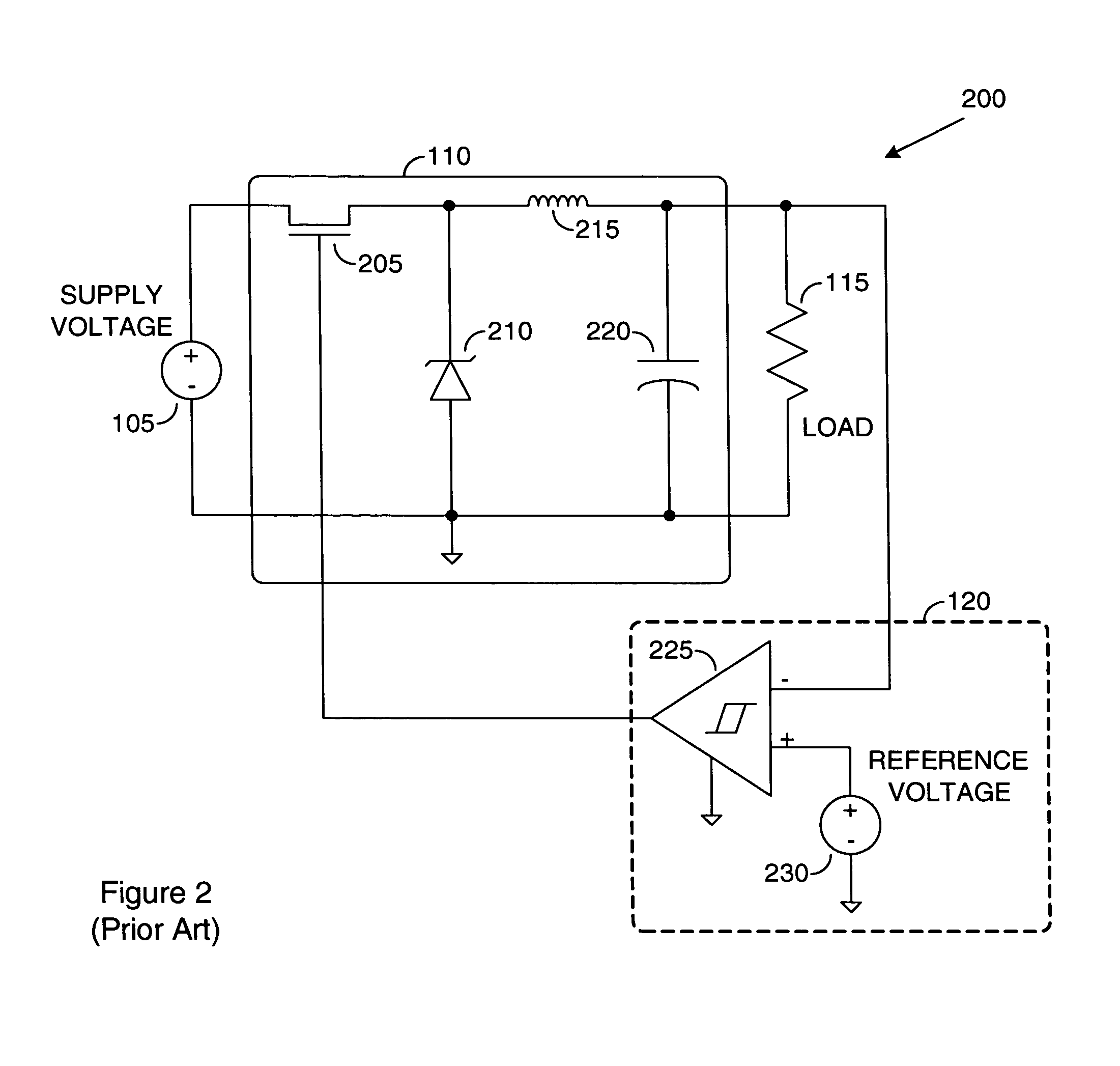
System for providing a switched regulator with an adjustable operating frequency range. A preferred embodiment comprises a voltage supply and a load, a switch and filter block (SFB) (such as the SFB 510), a comparator (such as the comparator 520), and a fixed off time logic (FOTL) (such as the FOTL 525). The comparator compares an output voltage with a reference voltage. When the output voltage is equal to or exceeds the reference voltage, the comparator asserts a value on a signal line to the FOTL. The FOTL then shuts down the SFB for a specified period of time. During the off time, the output voltage decays. After the specified period of time expires, the SFB is turned back on and the output voltage can recharge. The duration of time that the SFB remains on is a function of the supply voltage, thus permitting an adjustable operating frequency.
Owner:TEXAS INSTR INC
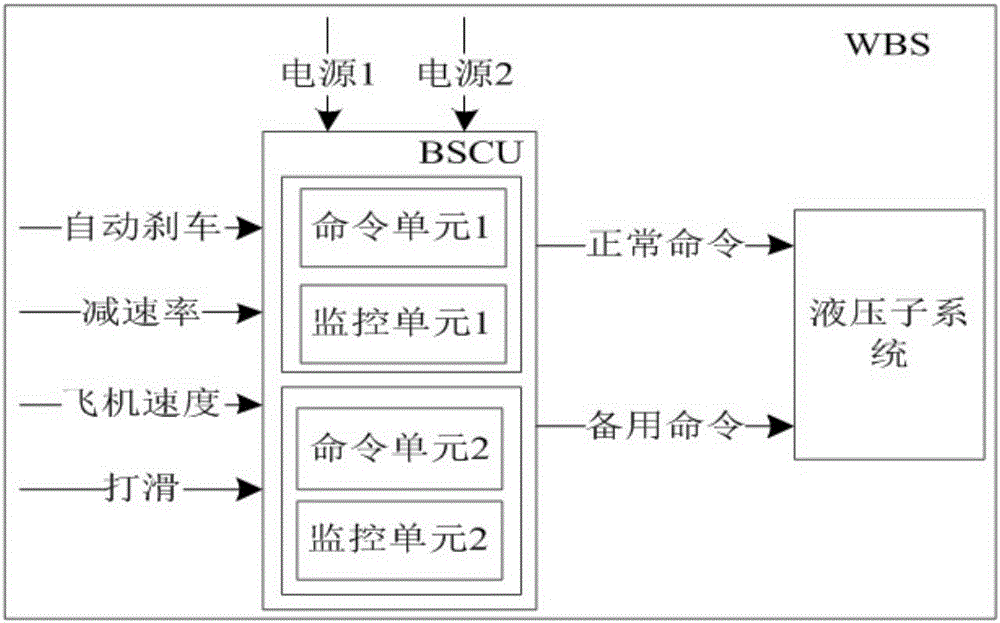
Aeroengine airworthiness safety verification method
InactiveCN108829955AAddressing Computational ComplexityAddress calculation accuracyGeometric CADDesign optimisation/simulationProbit modelAviation
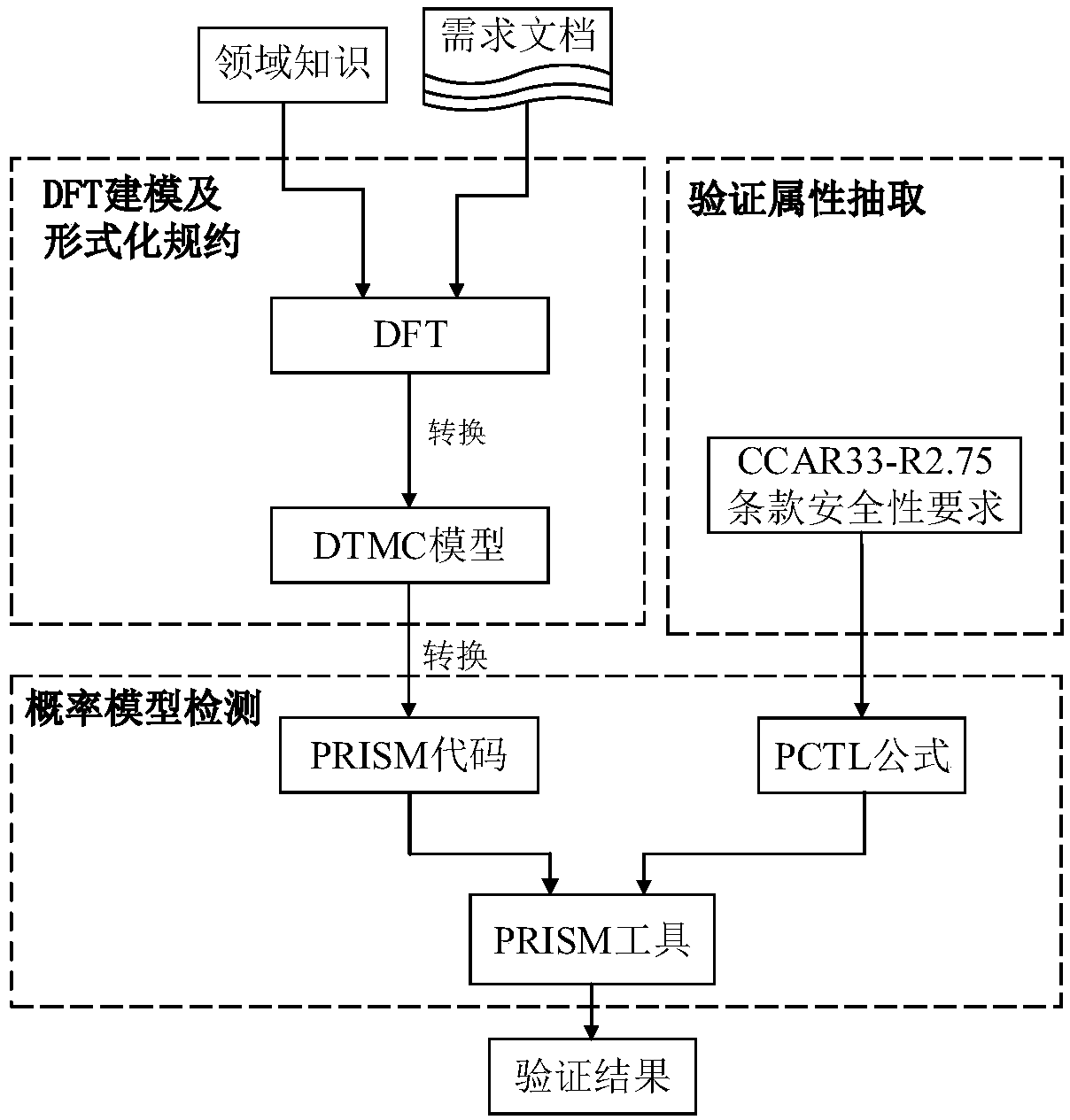
The invention discloses an aeroengine airworthiness safety verification method, and belongs to the technical field of system safety verification. According to the aeroengine airworthiness safety verification method, dynamic behaviors of an aeroengine system are described through introduced dynamic logic gates describing temporal logic relationships in a dynamic fault tree, temporal relationships among aeroengine component faults are modeled, formalized specification is carried on the generated dynamic fault tree, the same is converted into a DTMC model, then the DTMC model is described and expressed through a method of probabilistic model detection, and formalized verification is carried out on airworthiness safety requirement attributes. According to the method, the temporal relationshipswhich aeroengine system fault occurrence has are considered, and the problem that traditional analysis methods often assume that fault occurrence has independence is solved.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
Data acquisition and processing system of reactor core neutron fluence rate
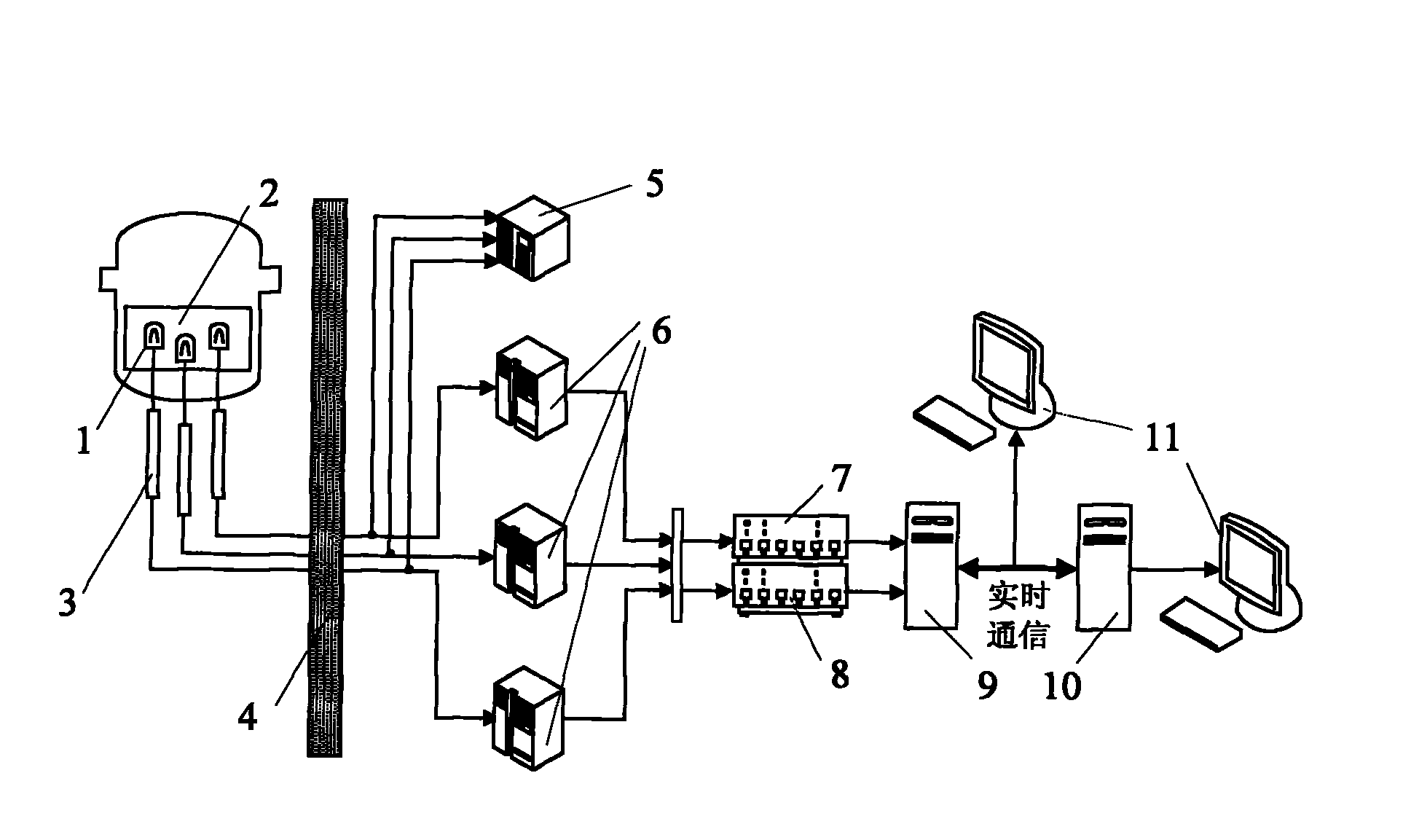
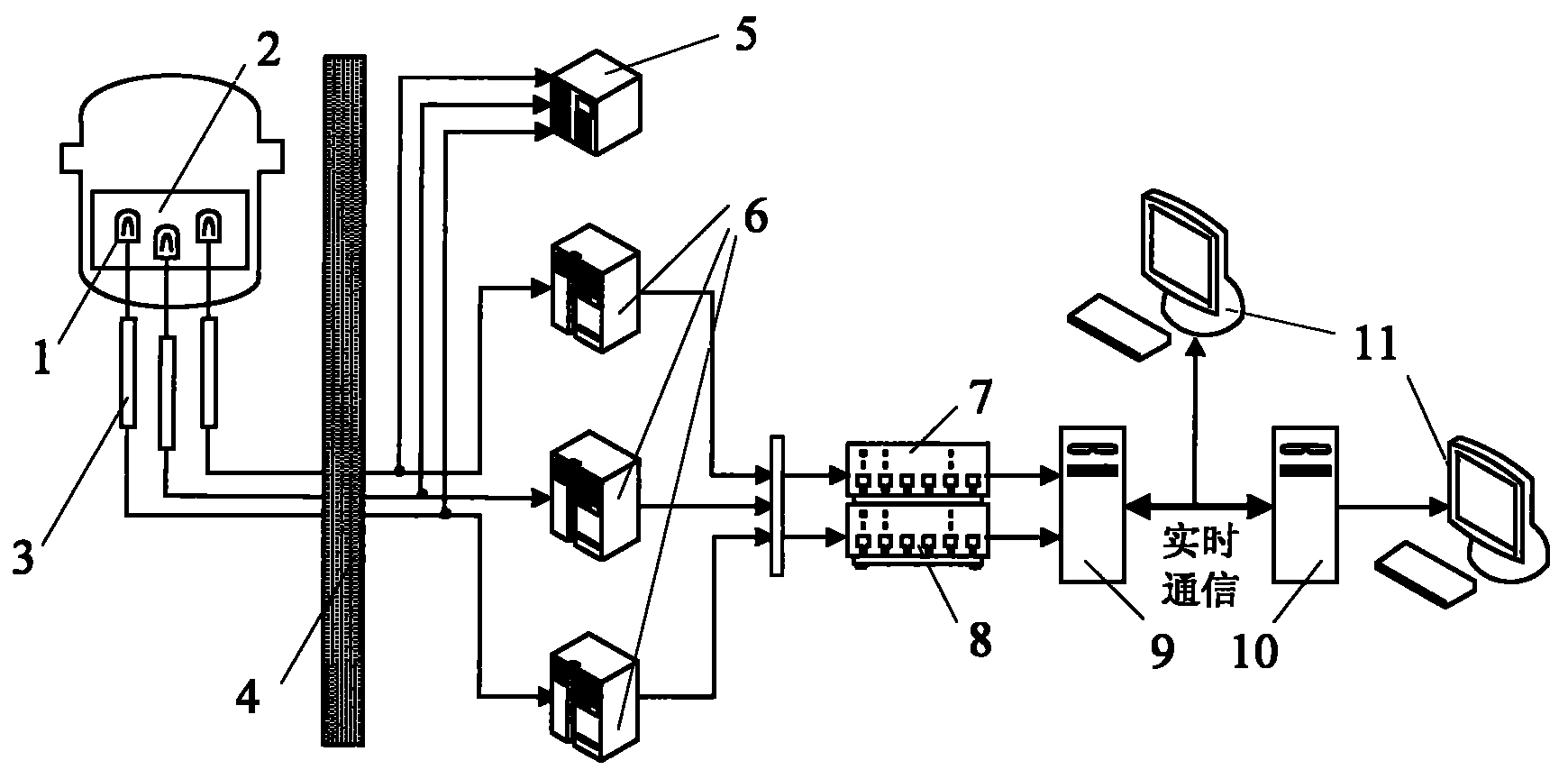
ActiveCN102081979AQuality improvementGuaranteed reliabilityNuclear energy generationNuclear monitoringNuclear powerData acquisition
The invention belongs to the field of reactor core power monitoring of reactors in nuclear power plants, and in particular, relates to data acquisition and processing system of reactor core neutron fluence rate. The system comprises core testing device and data processing device. The core testing device comprises multiple measuring cabinets and one synchronously shared cabinet. Measuring cabinetsand the synchronously shared cabinet are respectively connected to the mobile detector in core through the measuring pipe. Each measuring cabinet has a corresponding mobile detector and multiple mobile detectors are installed in different measuring pipes which are different from their neutron fluence rate. There are two data processors in the data processing device. One connects to the measuring cabinet containing core testing device to realize the acquisition of data. Real-time communication between the first and second processor is ensured. The second processor will carry out the real-time response to the signals collected by the first processor including test of the abnormal temporal logic signals and error correction for analog signals of neutron fluence rate.
Owner:SHANGHAI NUCLEAR ENG RES & DESIGN INST CO LTD
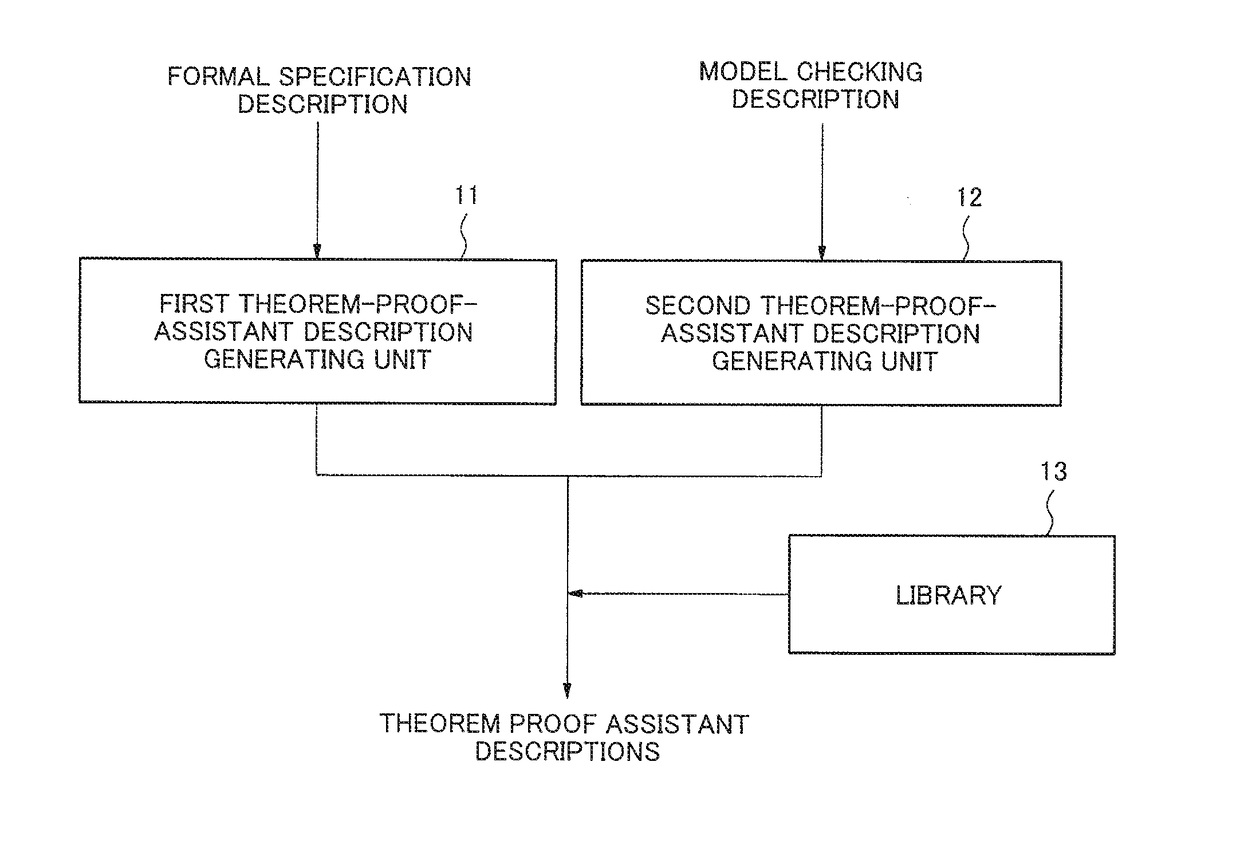
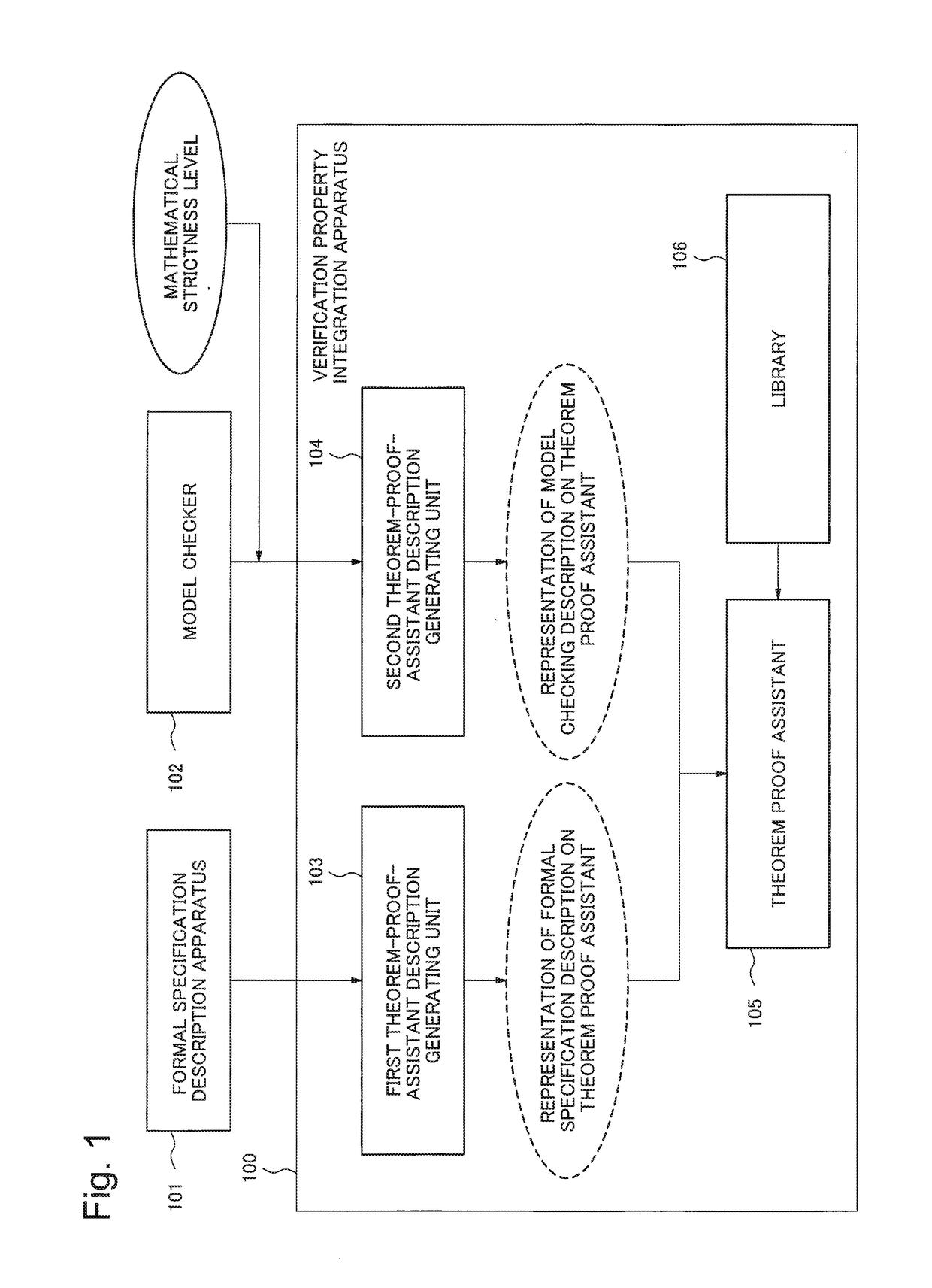
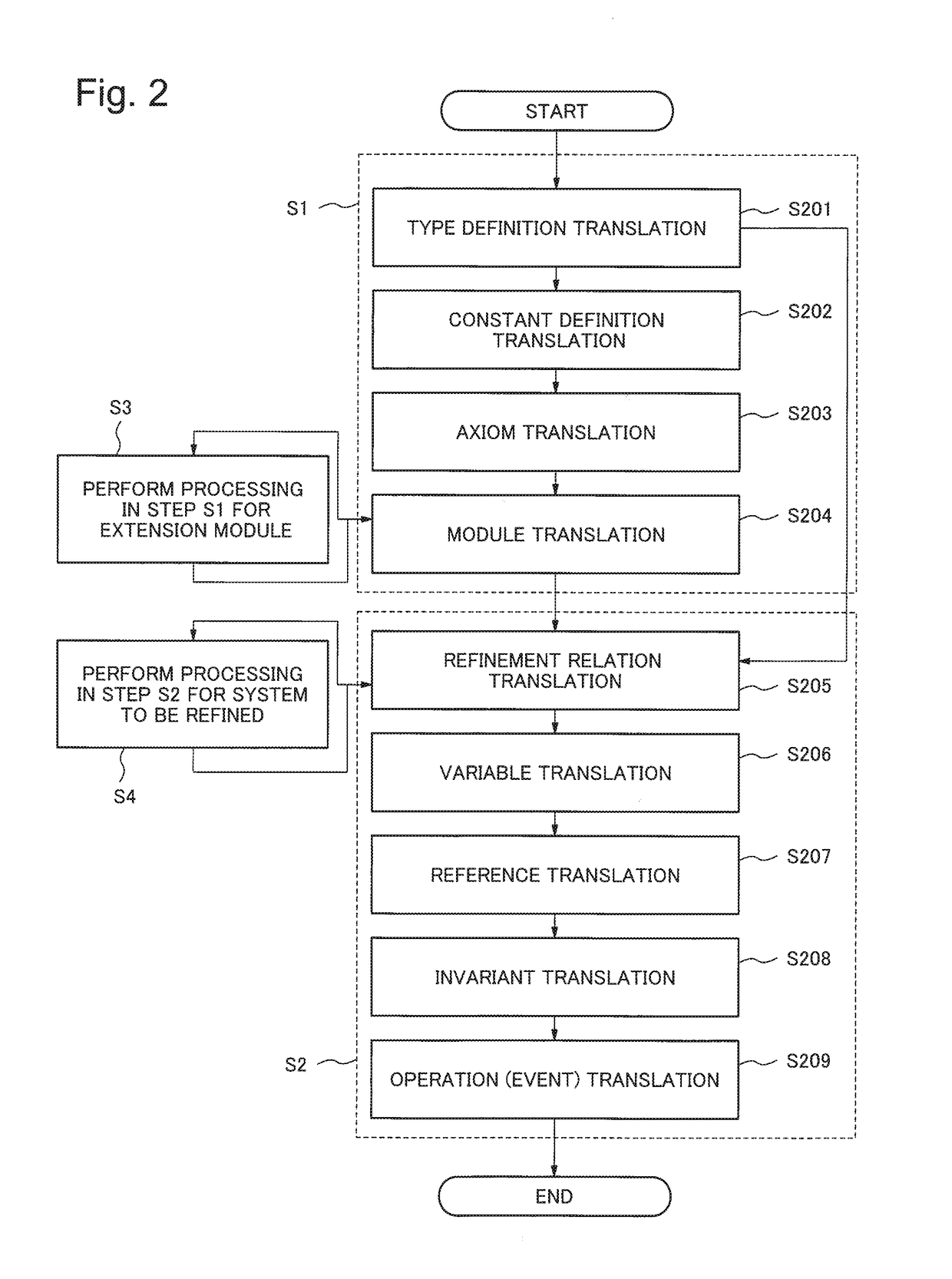
Verification property integration apparatus, verification property integration method, and storage medium
A verification property integration device that enables verification of a product or system integrated by products verified by different formal techniques, such as by formal specification description or model inspection. The apparatus includes a library, a first theorem-proof-assistant description generating unit, and the second theorem-proof-assistant description generating unit. The library is configured to provide definition of semantics of a formal specification description and a model checking description which are to be provided to a theorem-proof-assistant description. The first theorem-proof-assistant description generating unit is configured to translate the formal specification description into a representation on a theorem proof assistant which is defined and to be verified by using the library. The second theorem-proof-assistant description generating unit is configured to translate a model and a temporal logic formula in the model checking description into a representation on the theorem proof assistant which is defined and to be verified by using the library.
Owner:NEC CORP
Dynamic accident deduction simulation-based failure mode and influence analysis method
ActiveCN108170892AThe analysis result is accurateSimulate Dynamic Association BehaviorDesign optimisation/simulationSpecial data processing applicationsFailure rateTemporal logic
The invention discloses a dynamic accident deduction simulation-based failure mode and influence analysis method. According to the method, in allusion to characteristics of analyzed objects, a function box of each module at the lowest agreed layer is constructed to construct a function box map; being different from the traditional operation of adding failure rates and carrying out reliability analysis on function modules, the method is characterized by constructing a dynamic accident deduction simulation model which comprises elements such as state, event and the like for internal behaviors ofeach function box, connecting all the function boxes into a whole through constructing logic and time relationships between the function boxes, and finally simulating dynamic operation processes of systems through a dynamic discrete event simulation method so as to find out failure events and generation probabilities of the systems and then carry out further failure influence and hazard analysis.The method disclosed by the invention is capable of solving the problem that the traditional failure mode and influence analysis method cannot carry out temporal logic analysis and combined functionfailure analysis.
Owner:CHINA AERO POLYTECH ESTAB
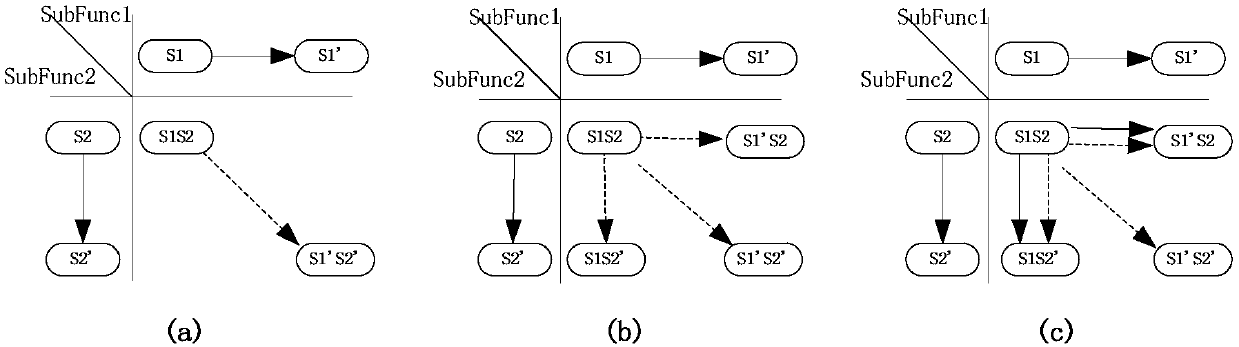
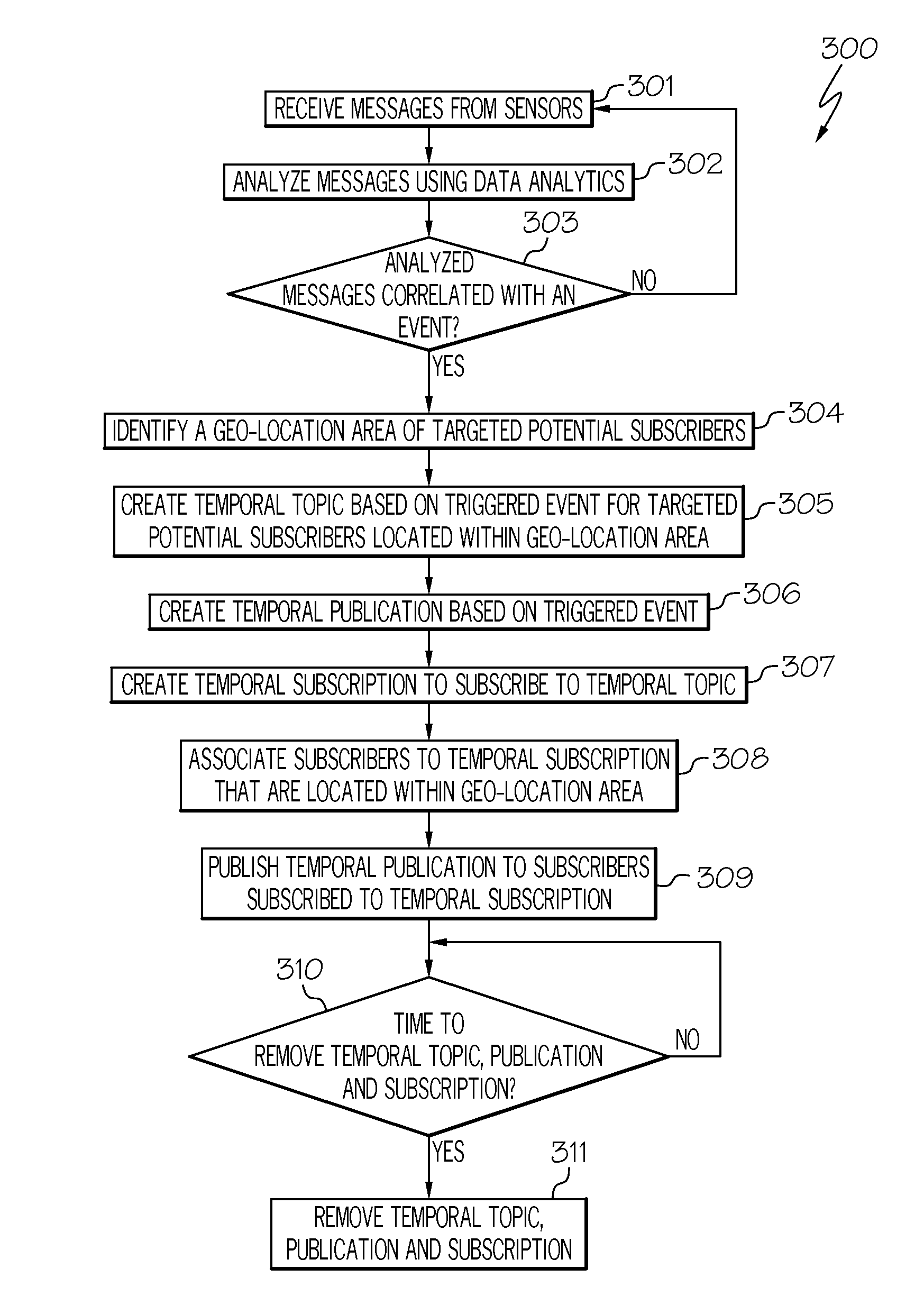
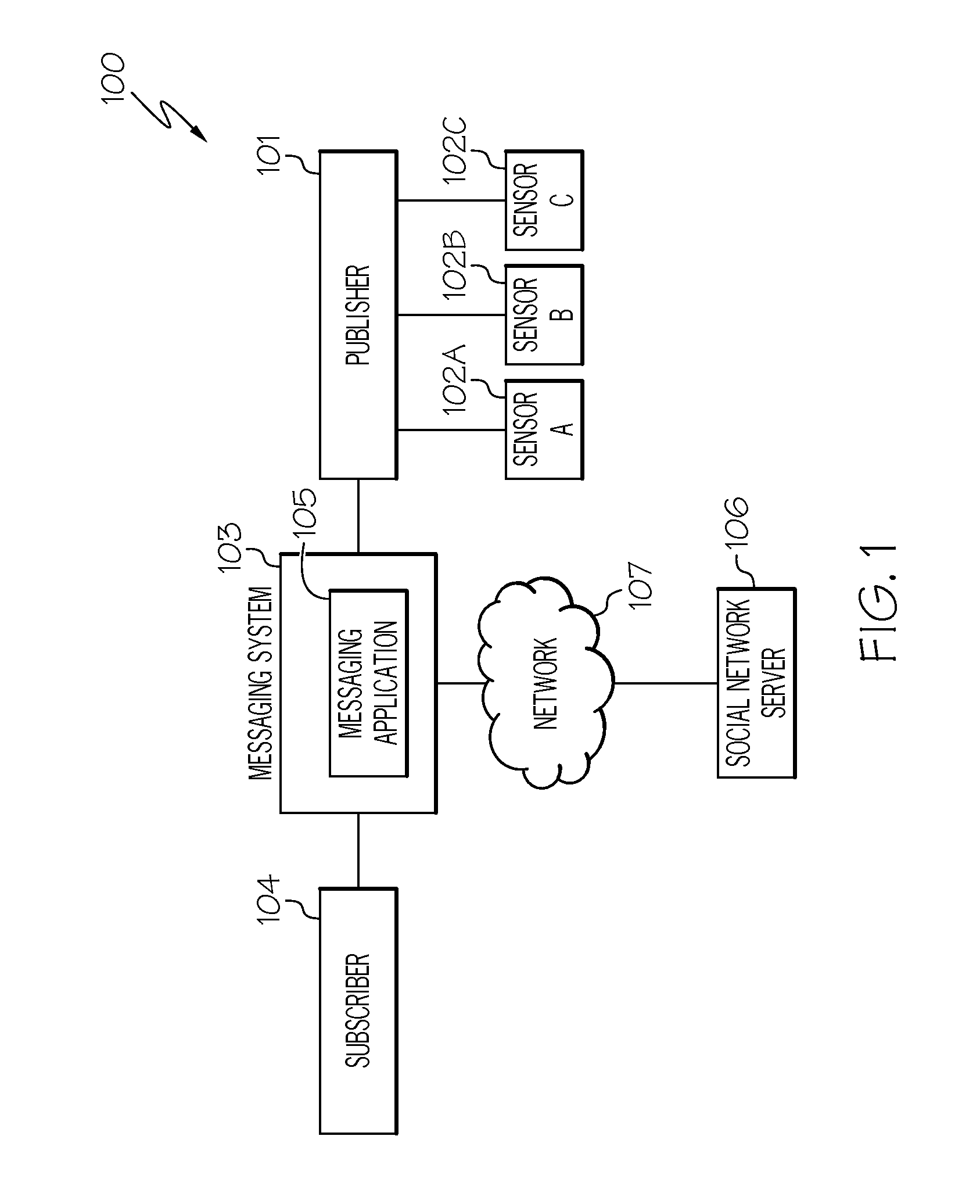
Dynamically routing messages in a publish/subscribe system by creating temporal topics for subscriptions and publications
ActiveUS20150199903A1Service provisioningArrangements for variable traffic instructionsSocial mediaGeolocation
A method, system and computer program product for dynamically routing messages in a publish / subscribe system. A messaging application receives messages from sensors (e.g., road condition sensors). Upon analyzing the messages using data analytics, an event (e.g., icy road condition) may be correlated with the analyzed messages. In such a scenario, a temporal topic based on the triggered event is created. Furthermore, a temporal publication (e.g., “icy road condition near exit 40”) and a temporal subscription are created. Potential subscribers to be associated with the temporal subscription are identified by using either geo-location information or social media information. Once those subscribers are identified, they are associated with the temporal subscription. The temporal publication is then published to the subscribers associated with the temporal subscription. In this manner, messages are dynamically routed to the appropriate subscribers that may have previously been excluded based on dynamically created temporal topics, subscriptions and publications.
Owner:IBM CORP
Mapping in a storage system
ActiveUS20140365745A1Efficient managementInput/output to record carriersMemory systemsTemporal logicOperating system
A system and method for maintaining a mapping table in a data storage subsystem. A data storage subsystem supports multiple mapping tables. Records within a mapping table are arranged in multiple levels which may be logically ordered by time. Each level stores pairs of a key value and a pointer value. New records are inserted in a created new (youngest) level. All levels other than the youngest may be read only. In response to detecting a flattening condition, a data storage controller is configured to identify a group of two or more adjacent levels of the plurality of levels for flattening which are logically adjacent in time. A new level is created and one or more records stored within the group are stored in the new level, in response to detecting each of the one or more records stores a unique key among keys stored within the group.
Owner:PURE STORAGE
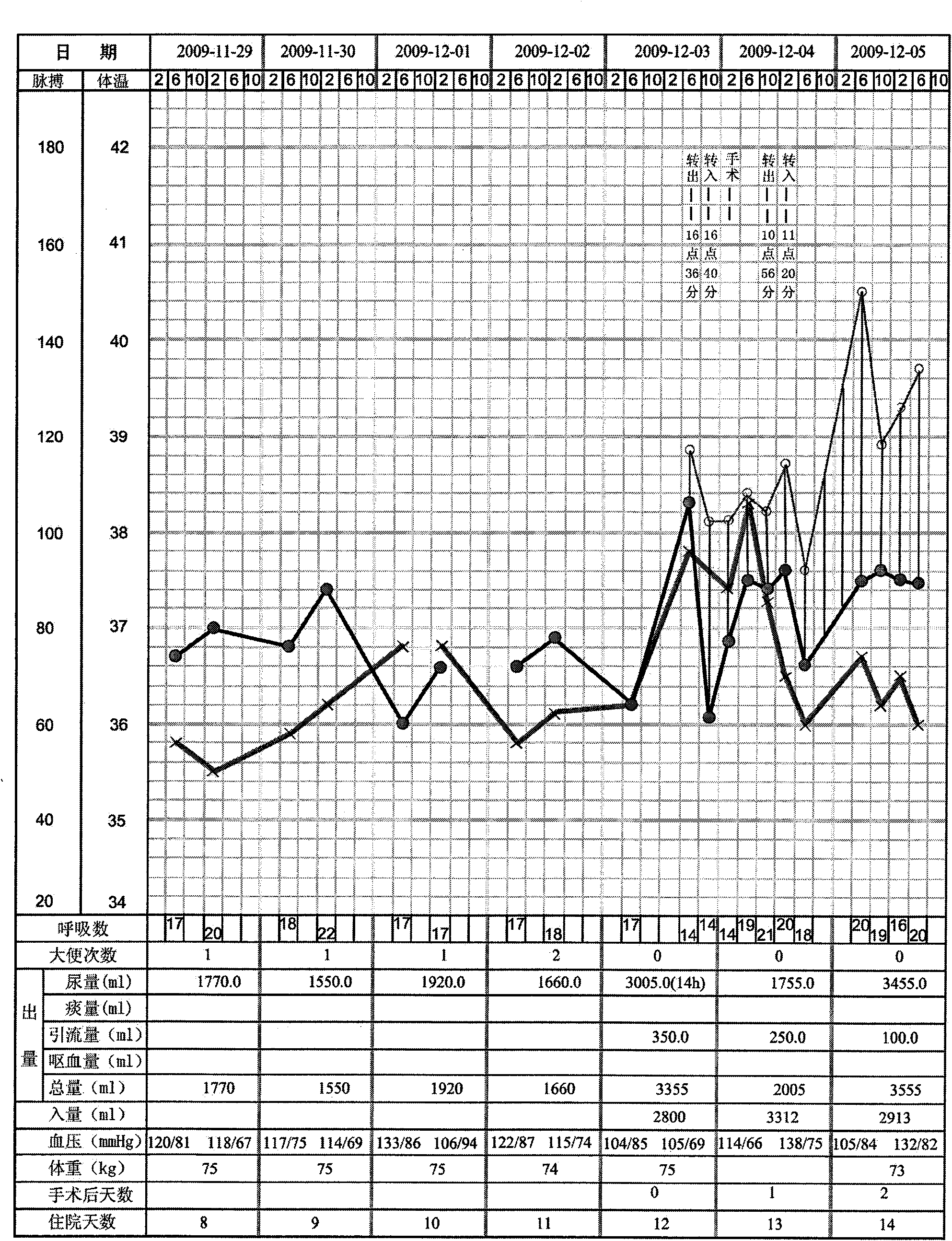
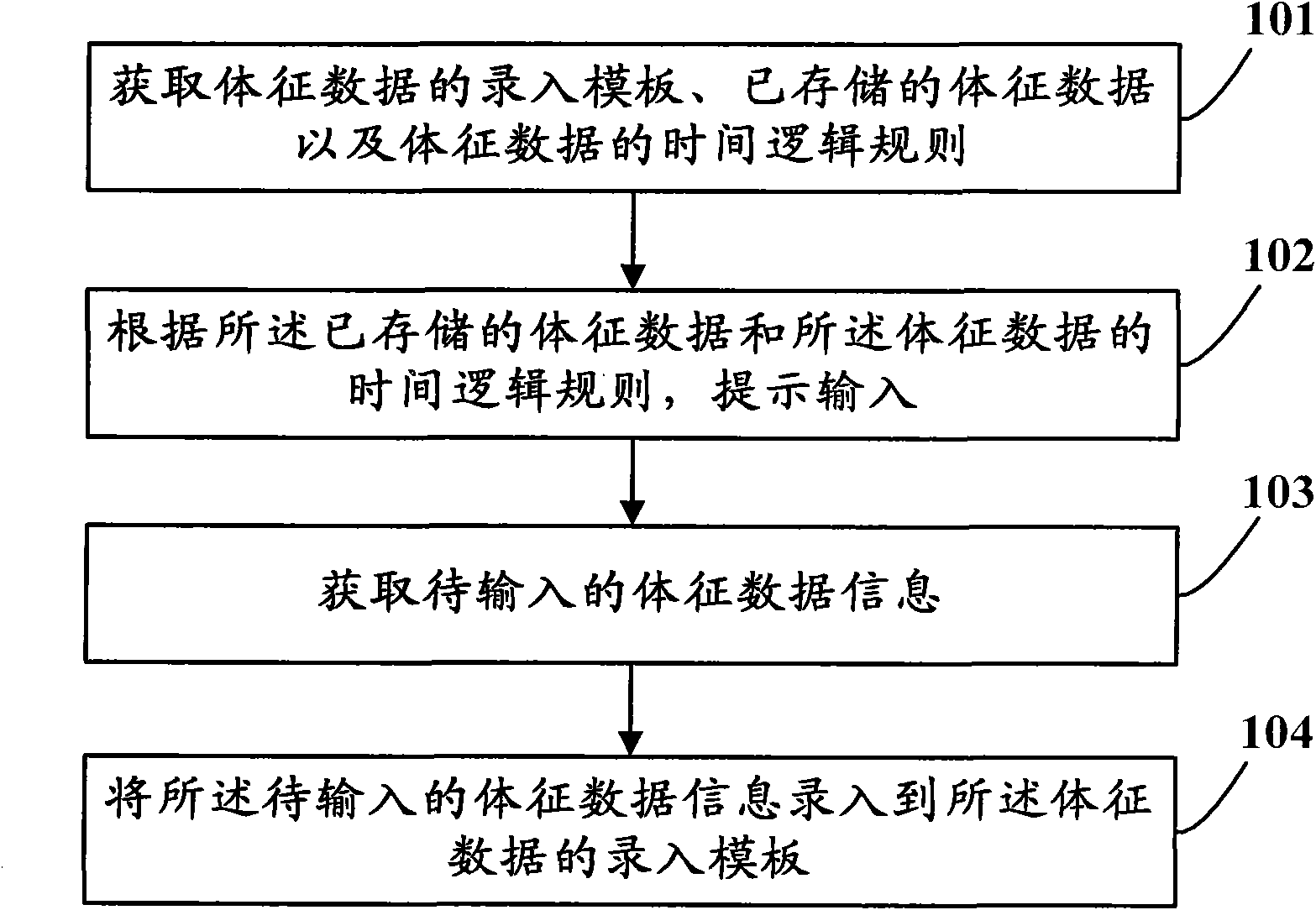
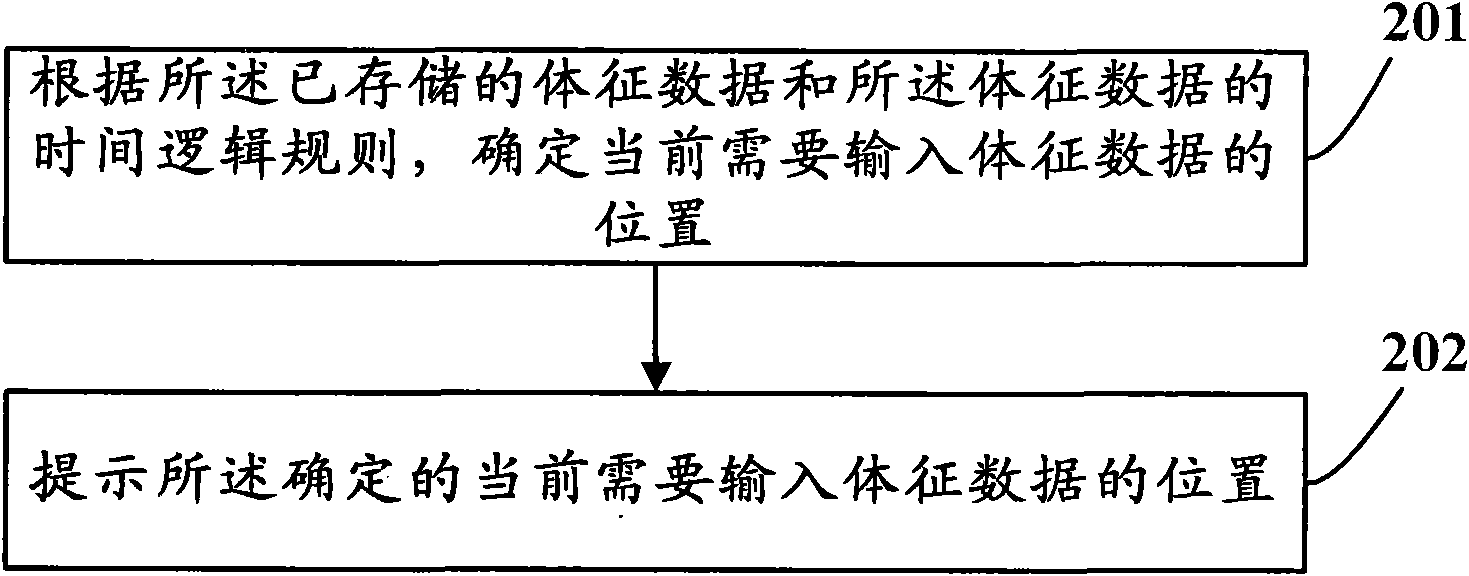
Sign data entry method and device
InactiveCN102117373AImprove entry efficiencyReduce entry errorsSpecial data processing applicationsTemporal logicData information
The invention discloses a sign data entry method which relates to the technical field of data information processing and aims at solving the problems that the entry efficiency is low and entry errors are easily caused since the sign data entry is input to a computer system by nursing staffs in the prior art. The sign data entry method comprises the steps of obtaining an entry template of the sign data, the sign data stored and the time logic rule of the sign data; promoting for input according to the sign data stored and the time logic rule of the sign data; obtaining the sign data information to be input; and typing the sign data information to be input into the entry template of the sign data. With the method and device, the sign data entry efficiency can be improved and the entry errors can be reduced.
Owner:PEKING UNIV FOUNDER GRP CO LTD +1
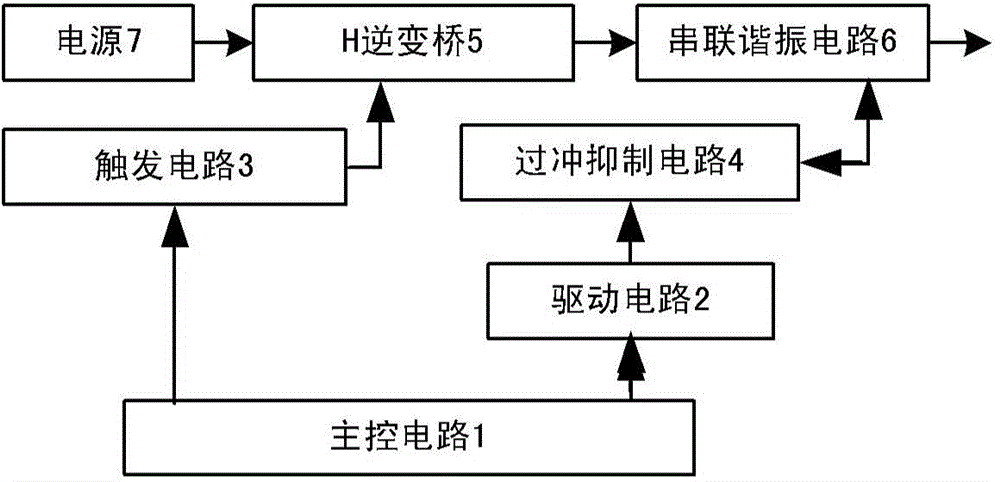
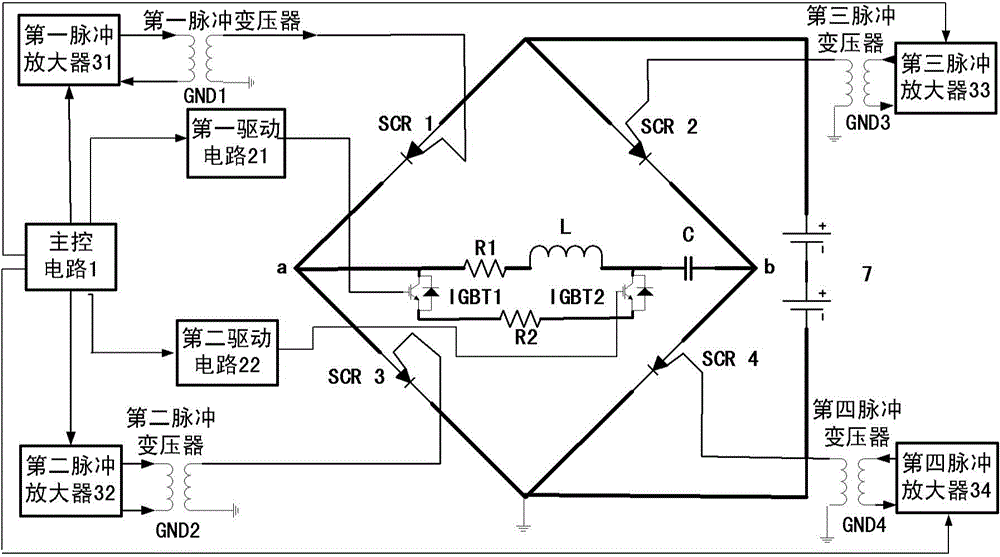
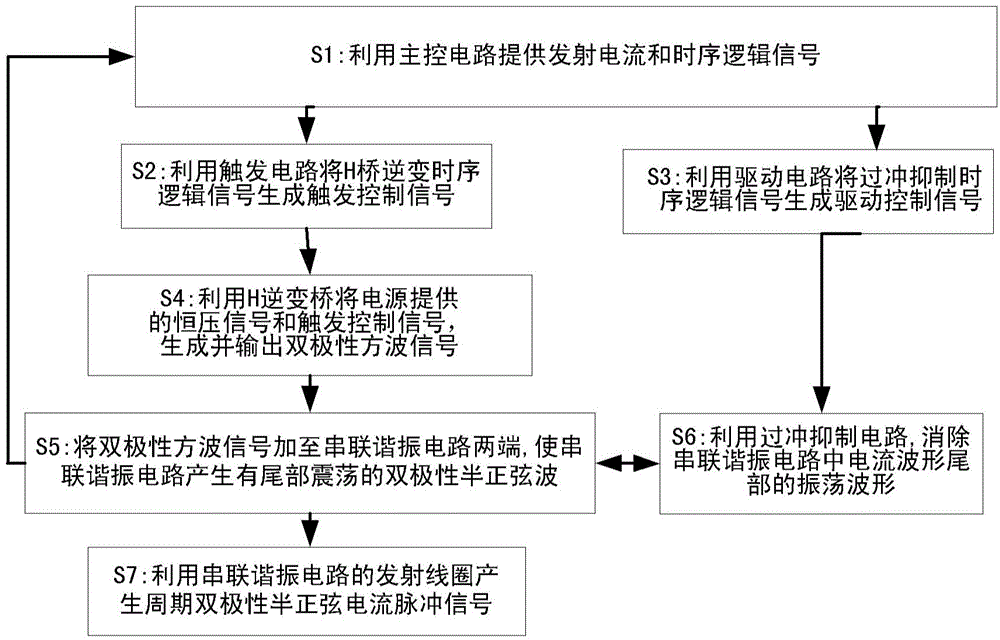
Bipolar half-sine current generating device and method for full-ATEM (airborne transient electromagnetic system)
The invention provides a bipolar half-sine current generating device and method for a full-ATEM (airborne transient electromagnetic system). The bipolar half-sine current generating device comprises a master control circuit, wherein a driving circuit is located between the master control circuit and an overshoot suppression circuit, connected with the master control circuit and the overshoot suppression circuit and used for generating an overshoot suppression temporal logic signal and providing a driving control signal for the overshoot suppression circuit; a trigger circuit is located between the master control circuit and an H inverter bridge, connected with the master control circuit and the H inverter bridge and used for generating a trigger control signal from an H-bridge inverting temporal logic signal; the H inverter bridge is connected with a power supply and used for outputting a bipolar square signal according to a constant-voltage signal of the power supply and the trigger control signal; the overshoot suppression circuit is connected with a series resonance circuit and used for supplying energy release access to oscillation waveform at the tail of current waveform contained in the series resonance circuit and eliminating the oscillation waveform at the tail of the current waveform; the series resonance circuit is connected with the H inverter bridge and used for generating bipolar half-sine current waveform meeting the current waveform requirement according to the bipolar square signal and eliminating oscillation at the tail of the current waveform by using the overshoot suppression circuit.
Owner:INST OF ELECTRONICS CHINESE ACAD OF SCI
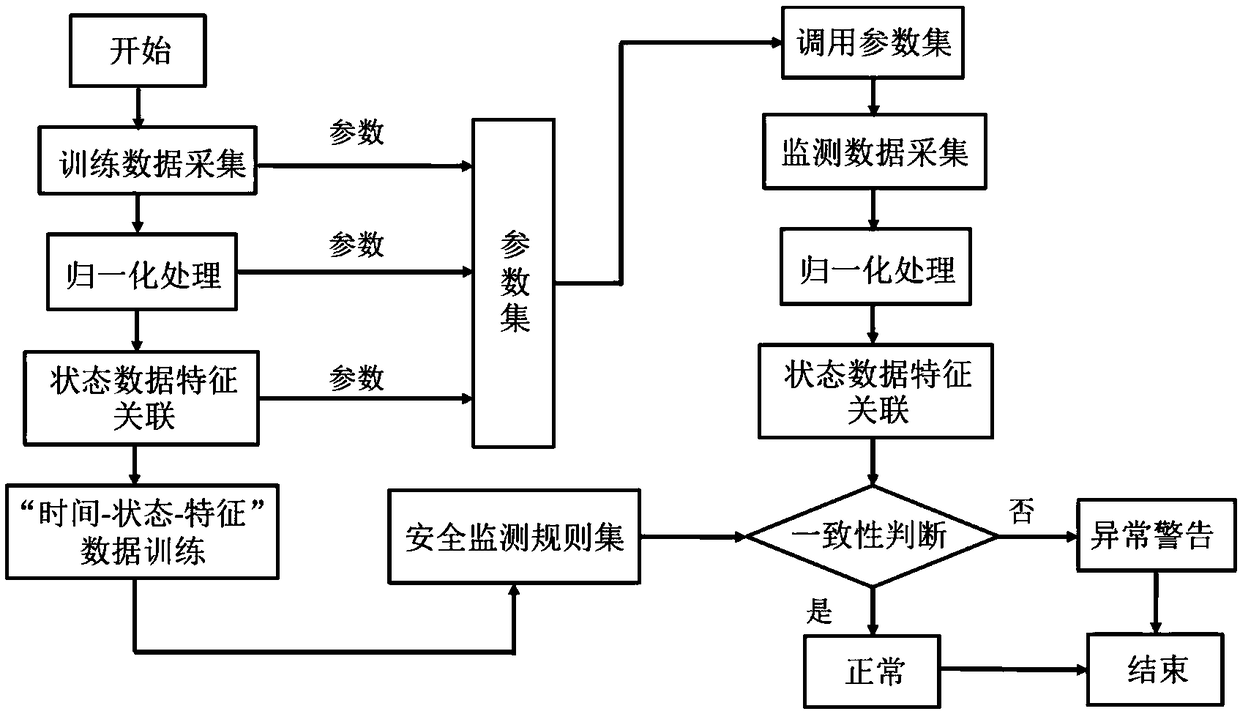
Safety monitoring method of electric power industrial control terminal based on service logic consistency
The invention discloses a safety monitoring method of electric power industrial control terminal based on service logic consistency, the invention aims at the safety problem of the electric power industrial control terminal equipment introduced by the diversified information in the 'Internet +' intelligent grid system, breaks through the existing attack detection method simply relying on the network space information, and puts forward a safety method of the electric power industrial control terminal based on the service logic consistency. By sampling the multi-modal data of physical world information and cyberspace information, normalized processing and temporal correlation, and through training, the safety monitoring set and parameter constraint set are obtained for safety monitoring andanomaly identification. From the business level, the method can effectively early-warn the state abnormality caused by equipment performance difference, equipment failure and hacker intrusion, and realize the 'time-state-service' trinity consistency safety monitoring of the electric power industrial control terminal based on equipment time logic, state logic and business logic.
Owner:HUANAN IND TECH RES INST OF ZHEJIANG UNIV
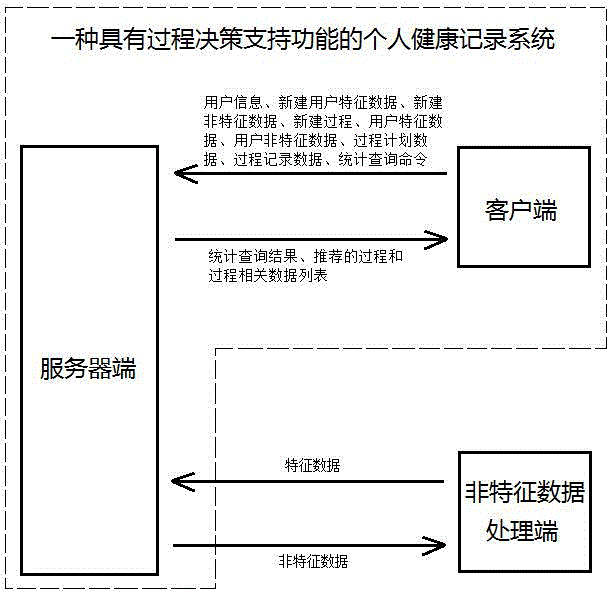
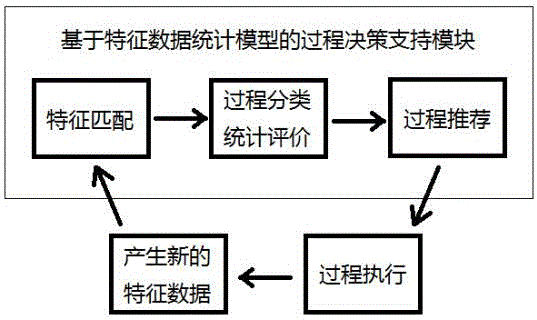
Personal health record system with process decision support function
ActiveCN106650292AEasy accessImprove playbackMedical data miningMedical automated diagnosisPersonal recordInformation analysis
The invention discloses a personal health record system with a process decision support function. By building a personal health record system of characteristic data extraction and characteristic data analytical separation, the characteristic data meeting analysis requirements is expected to be rapidly obtained. A statistics query interface based on characteristic data and time logic is improved, decision support for a user is completed through the steps of characteristic matching, process classification statistics evaluation, process recommendation and the like, and the medical big data can well execute high-level information analysis and decision support functions.
Owner:梁月强
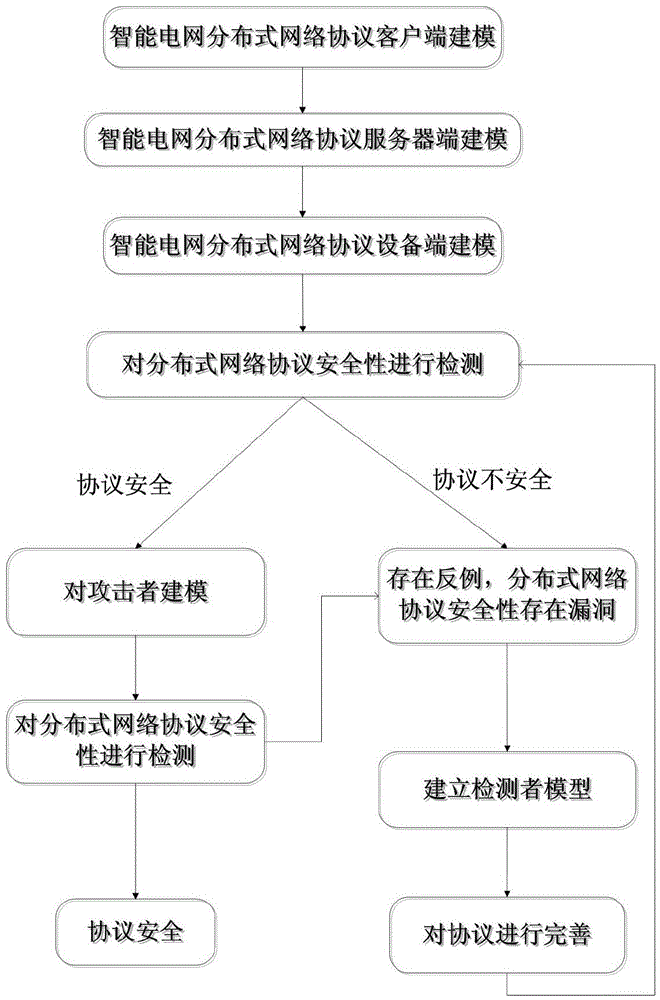
Distributed network protocol security detection method for smart power grid
The invention provides a distributed network protocol security detection method for a smart power grid. The method is that the distributed network protocol of the smart power grid is expressed by a state migration system composed of a timed automation machine; the conditions to be met by the distributed network protocol security of the smart power grid are expressed through a temporal logic formula; the distributed network protocol security is detected on the premise that no attacker appears; after introducing the attacker, the distributed network protocol safety is detected again. The method specifically comprises the steps of 1) building the state migration system based on the timed automation machine for the distributed network protocol, and detecting; 2) building an attacker model and detecting the distributed network protocol security; 3) building a detector model, improving the distributed network protocol security, and then detecting. With the adoption of the method, any security problem can be detected through the detector model, thus a user can continuously improve the protocol, and as a result, the security of the distributed network protocol of the smart power grid can be effectively improved.
Owner:青岛联众芯云科技有限公司
Conducting verification in event processing applications using formal methods
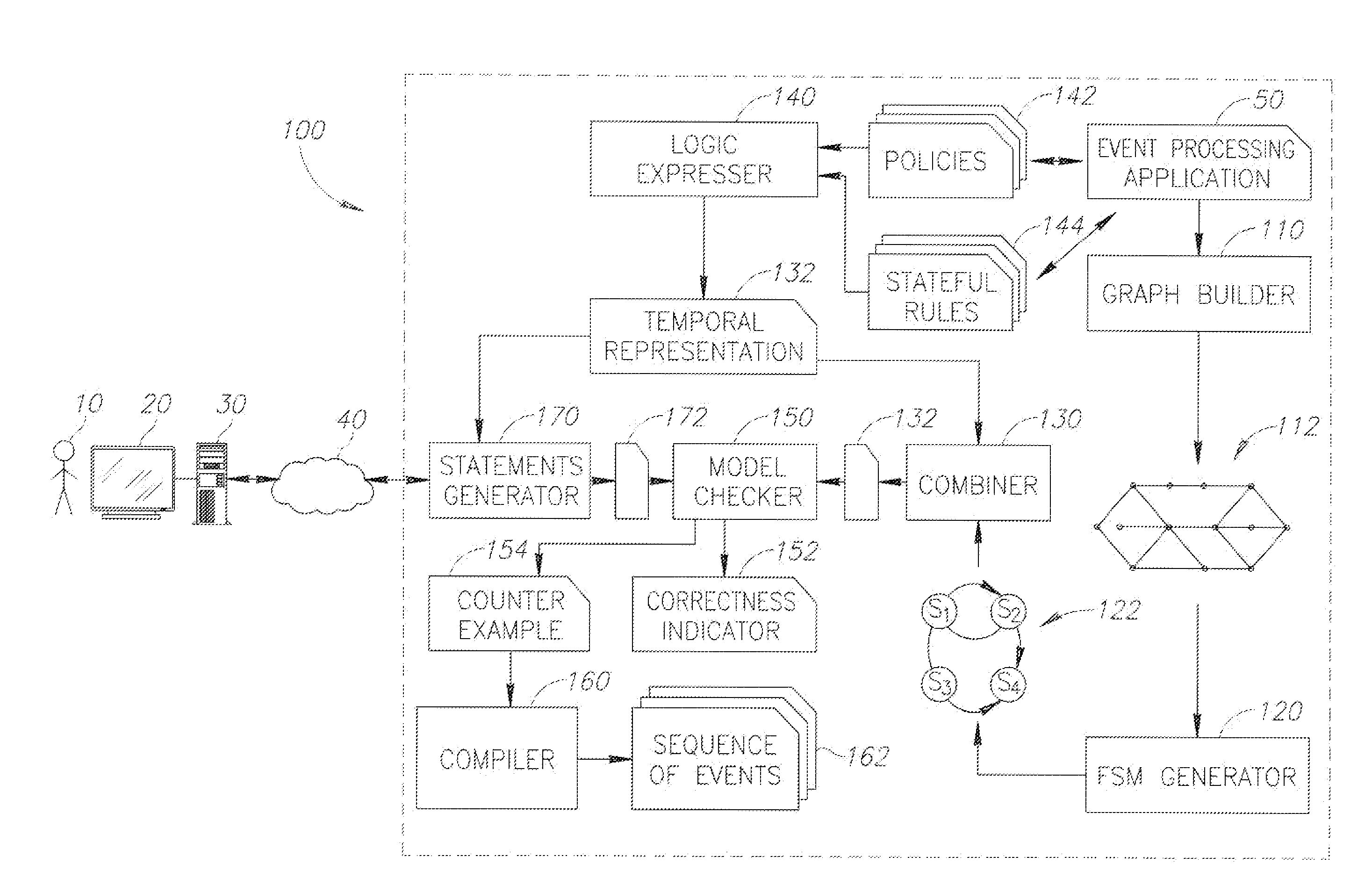
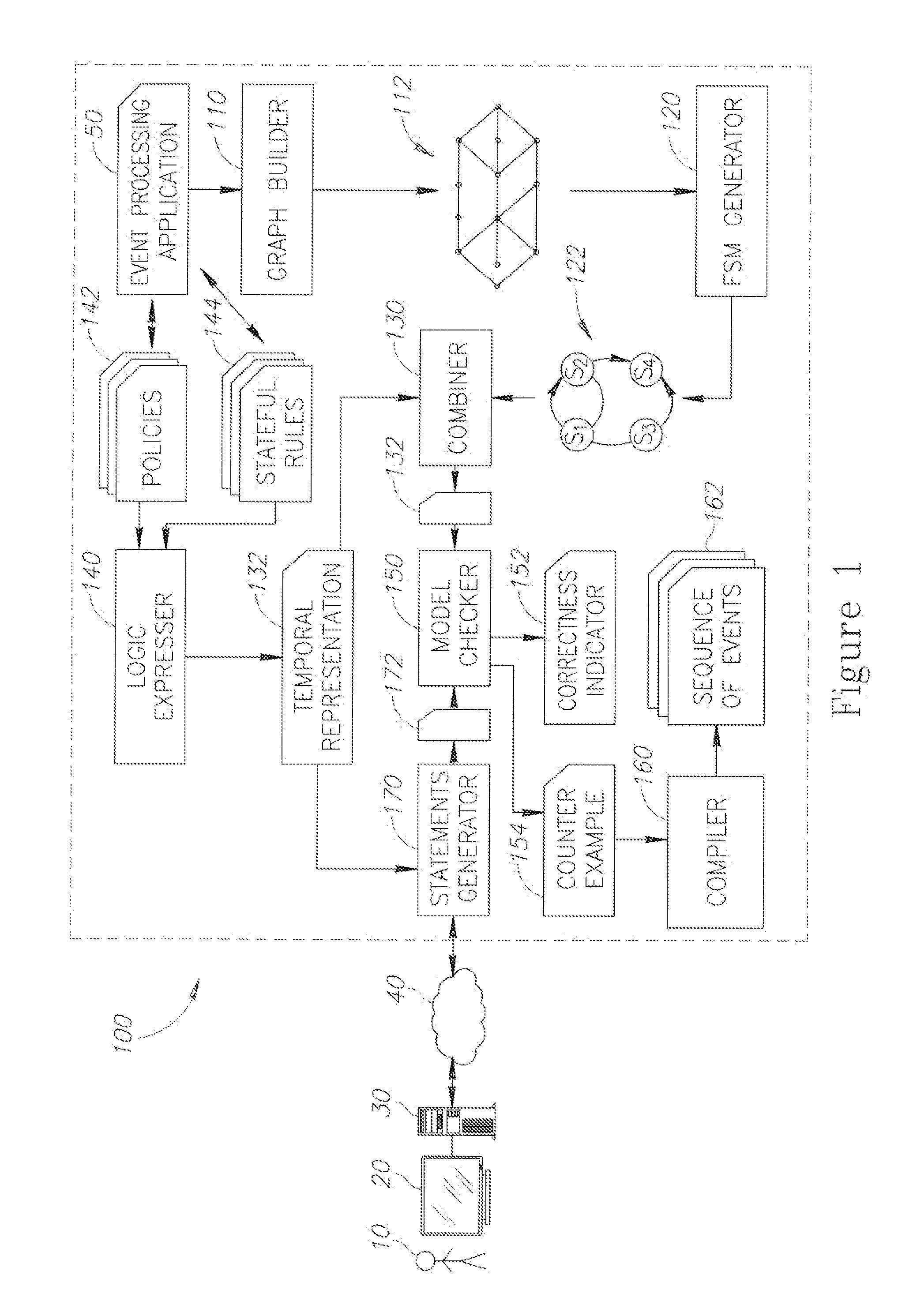
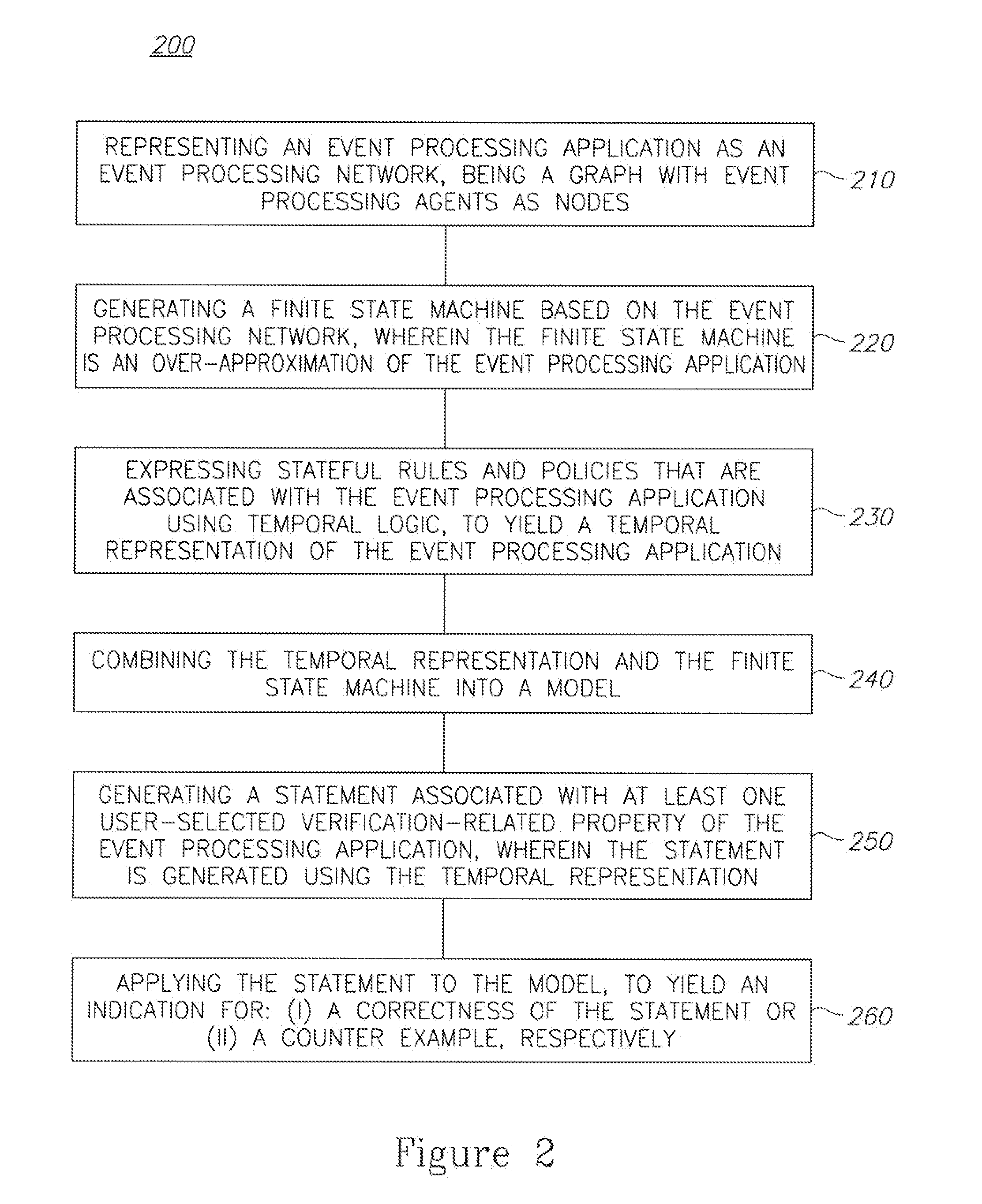
A method of applying formal verification methodologies to event processing applications is provided herein. The method includes the following stages: representing an event processing application as an event processing network, being a graph with event processing agents as nodes; generating a finite state machine based on the event processing network, wherein the finite state machine is an over-approximation of the event processing application; expressing stateful rules and policies that are associated with the event processing application using temporal logic, to yield a temporal representation of the event processing application; combining the temporal representation and the finite state machine into a model; generating a statement associated with a user-selected verification-related property of the event processing application, wherein the statement is generated using the temporal representation; and applying the statement to the model, to yield an indication for: (i) a correctness of the statement or (ii) a counter example, respectively.
Owner:IBM CORP
Privacy-aware signal monitoring systems and methods
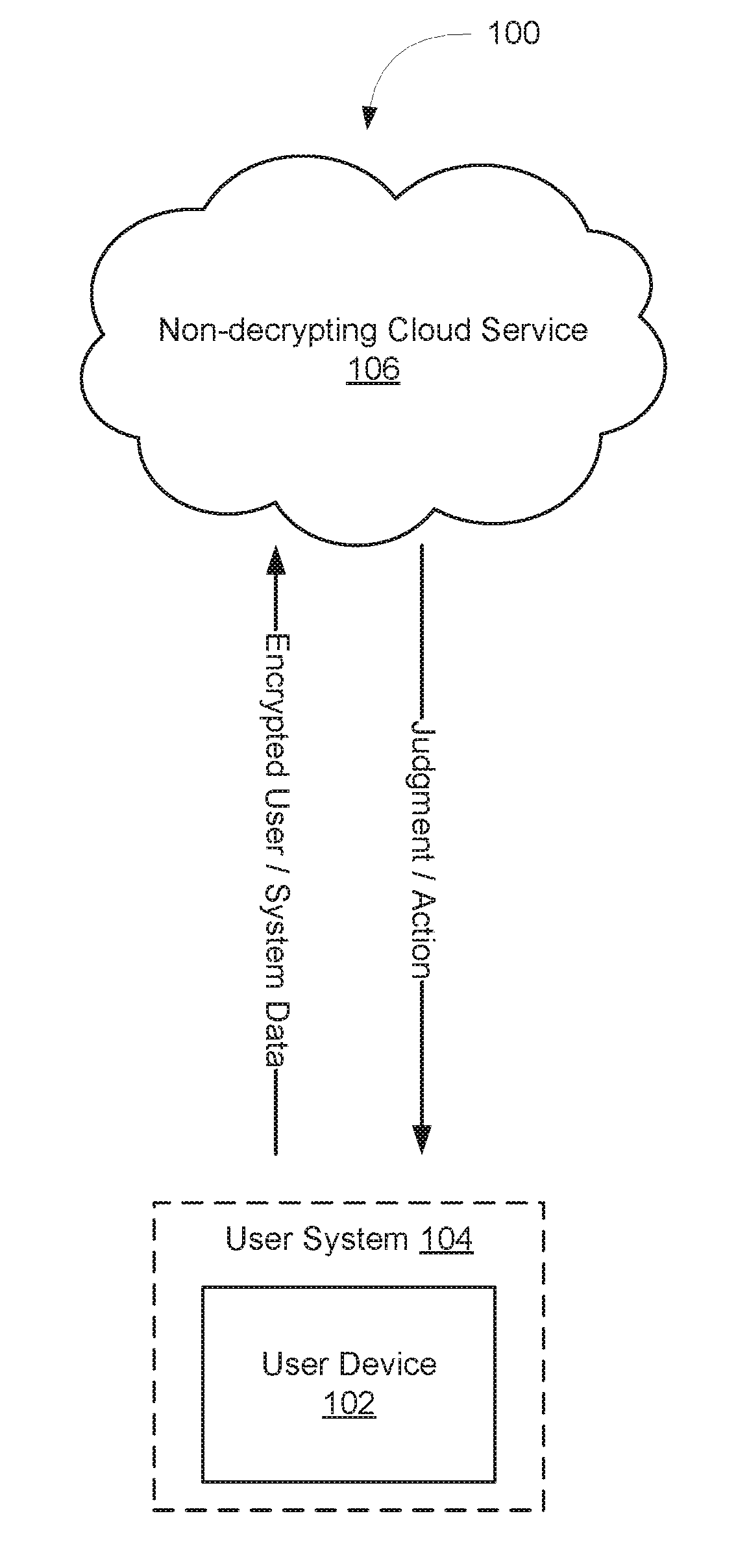
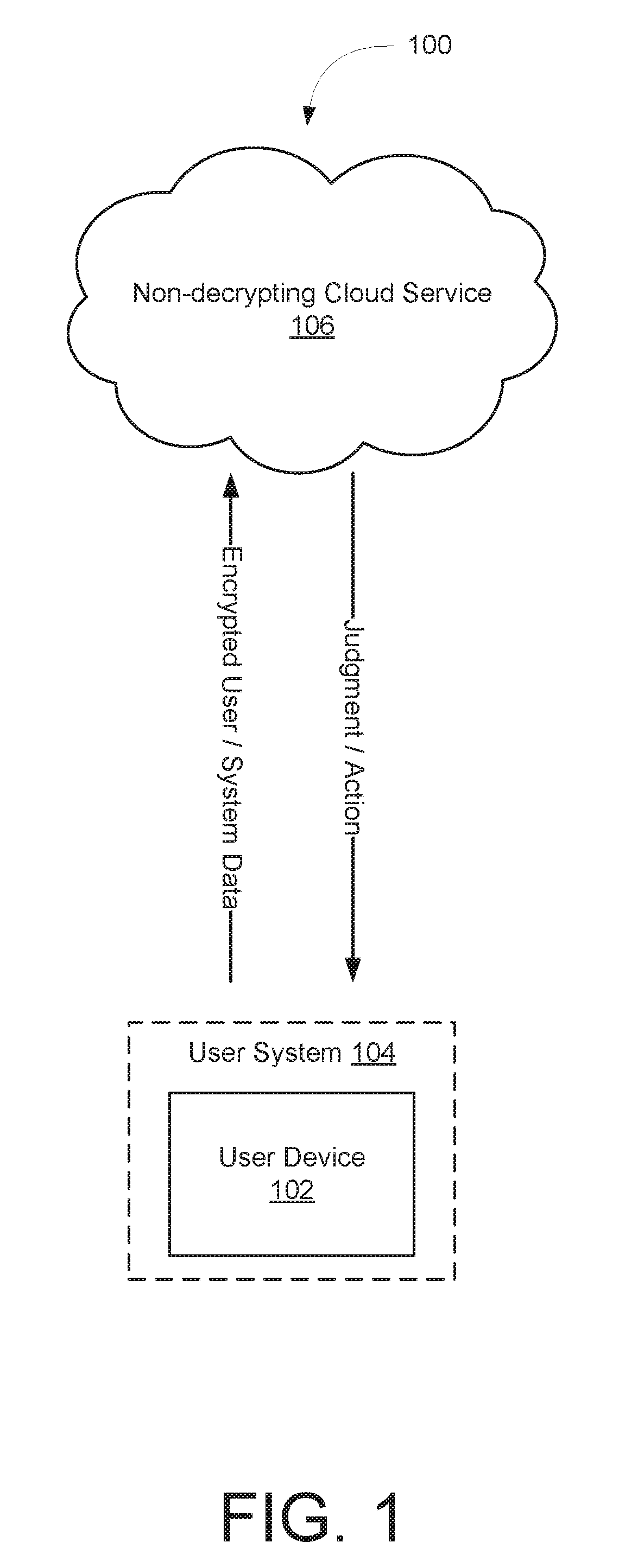
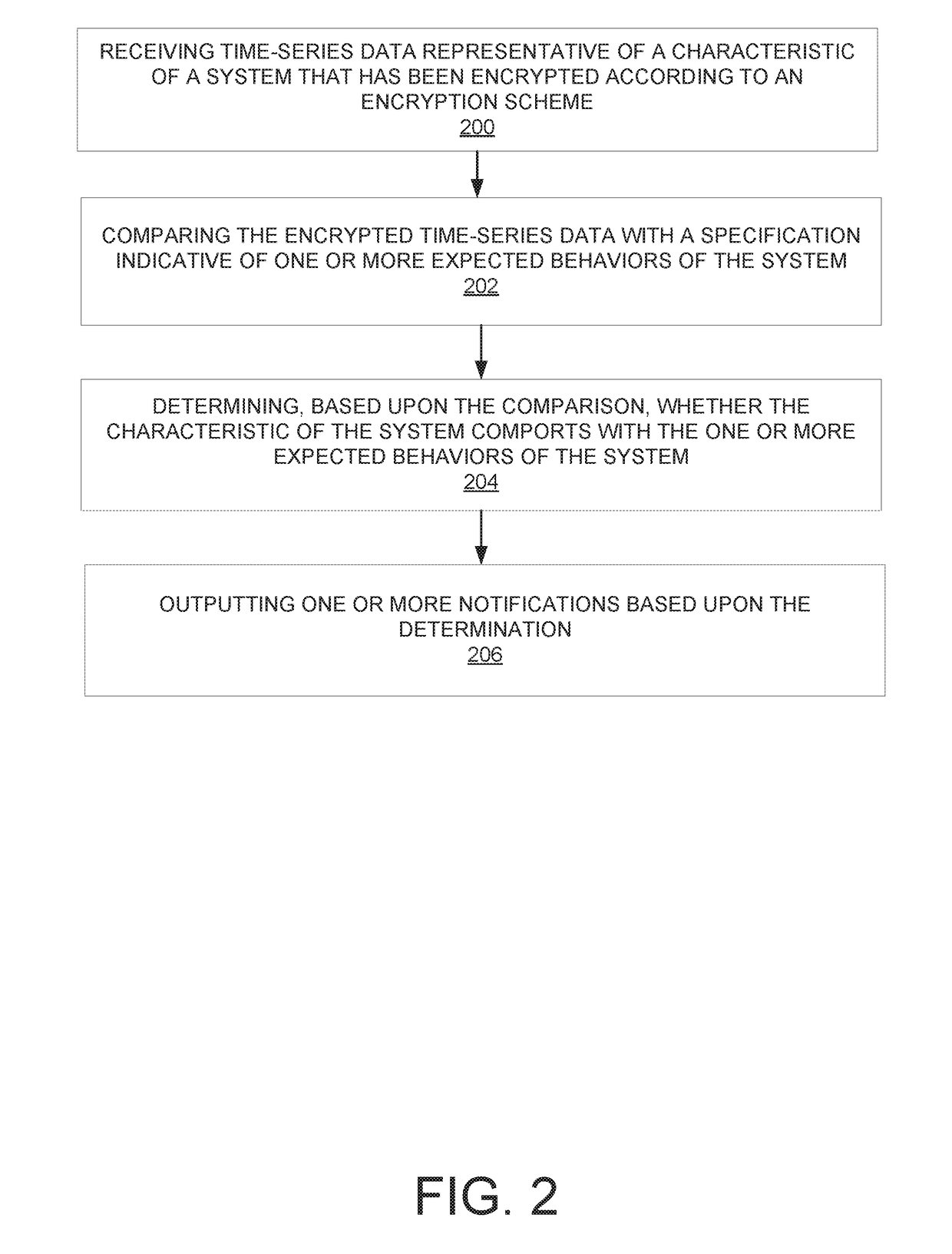
ActiveUS20180286143A1Registering/indicating working of vehiclesTransmissionBatch processingTemporal logic
Systems and methods are provided for monitoring time-series data relative to a temporal logic specification regarding expected behavior of a system, such as a vehicle. The time-series data and a threshold value(s) specified in the temporal logic specification may be encrypted and analyzed without decrypting the time-series data to maintain the privacy of a user(s) of the vehicle. Encryption of the time-series data and the threshold value(s) may be accomplished using an order preserving encryption scheme. Analysis of the time-series data may be accomplished utilizing a batch processing-type architecture or a continuous processing-type architecture. When utilizing the continuous processing-type architecture, historical time-series data may be stored and utilized to determine whether currently-monitored time-series data satisfies the temporal logic specification.
Owner:TOYOTA JIDOSHA KK
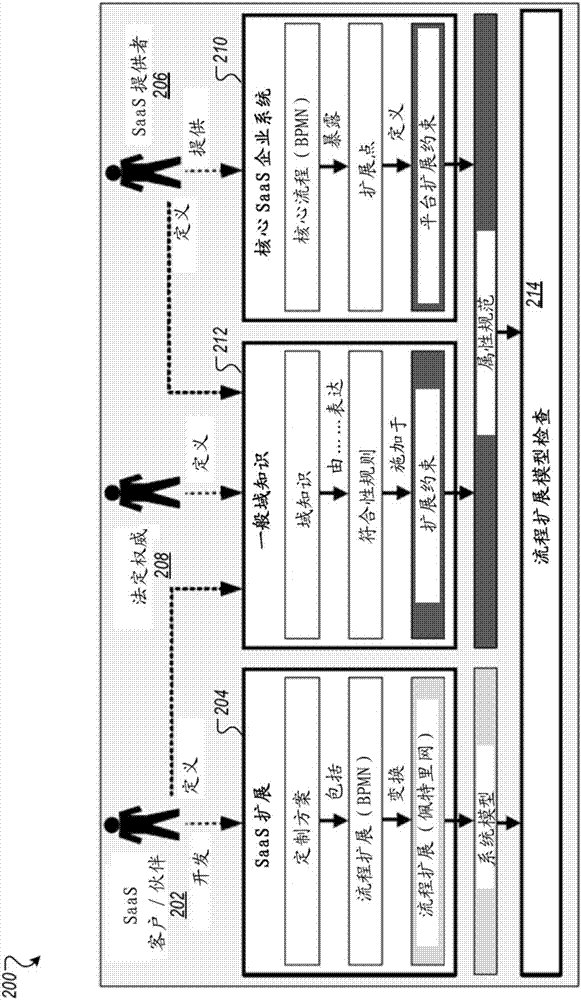
Software-as-a-Service Reference Flow Extensions validation framework
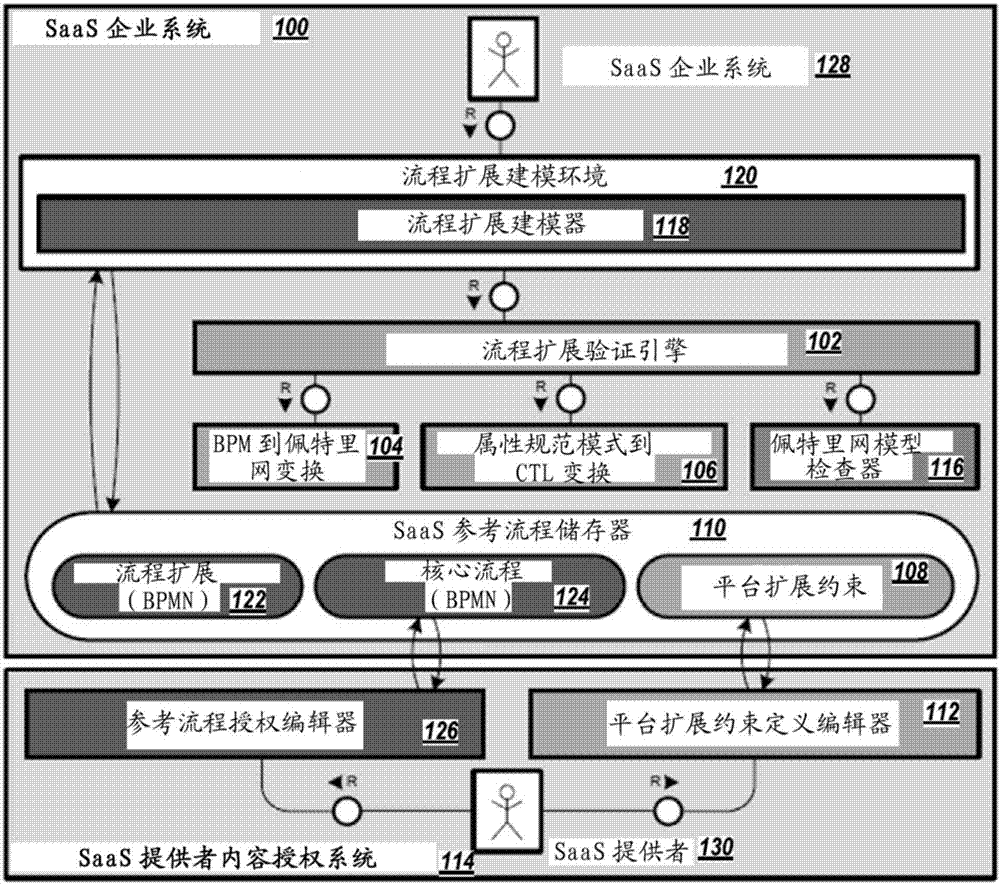
ActiveCN107015794ASoftware designSpecific program execution arrangementsTemporal logicSoftware as a service
The present disclosure describes methods, software, and systems, including methods of providing extension points for core process models. The extension point is provided to the core process model associated with the core process. The extension points are predefined and annotated with constraints that specify extended behavior of the extended behavior that is inserted into the core process model at the extension point. The extension point is formulated in a process extension constraint definition language and allows runtime constraints. The process extension constraint definition language is based on temporal logic and enhances the existing attribute specification pattern with specific support to establish constraints on the extended task type level for activities included in the process extension. An instruction to receive an instance of the selected extension into the core process model from the user. Each selected extension includes the user-defined behavior for the extension. An instance of the core process model is confirmed.
Owner:SAP AG
Method and device for model resolution and its use for detecting attacks against computer systems
InactiveUS7043755B1High-performance specification resolutionData processing applicationsMemory loss protectionTemporal logicAlgorithm
The present invention relates to a method and device for model resolution and its use for detecting attacks against computer systems. The device comprises adapter software for translating the information from the log file, formulated in the specific language of the machine, into a language understandable by the interpreter, an interpreter receiving the information from the adapter and receiving the formulation of the specification in the temporal logic in a specification formula in order to expand this formula and fill in the table and the stack of worked subformulas described above resulting from the scanning of the machine's log file, and a clause processing algorithm for resolving the Horn clauses using the information from the table and the stack of worked subformulas, this clause processing algorithm generating an output file or generating an action.
Owner:BULL SA +1
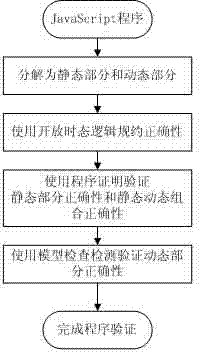
Method for verifying correctness of JavaScript procedure in mixed mode
InactiveCN103488571AReduce state space specificationSolve the state explosion problemSoftware testing/debuggingTemporal logicValidation methods
The invention discloses a method for verifying the correctness of a JavaScript procedure in a mixed mode. The method for verifying the correctness of the JavaScript procedure in the mixed mode comprises the following steps that the JavaScript procedure is divided into a static portion and a dynamic portion; the correctness of the JavaScript procedure is specified based on the open temporal logic; the correction of the static portion and the correction of the composition of the static portion and the dynamic portion are verified according to the procedure verification method; the correctness of the dynamic portion is verified according to the model checking method. The method for verifying the correctness of the JavaScript procedure in the mixed mode can be applicable to multiple grammar characteristics and application occasions of the JavaScript language, can support an automatic model detection tool and can effectively reduce the state searching space, and therefore the verification efficiency of the JavaScript procedure is effectively improved.
Owner:ZHEJIANG UNIV CITY COLLEGE
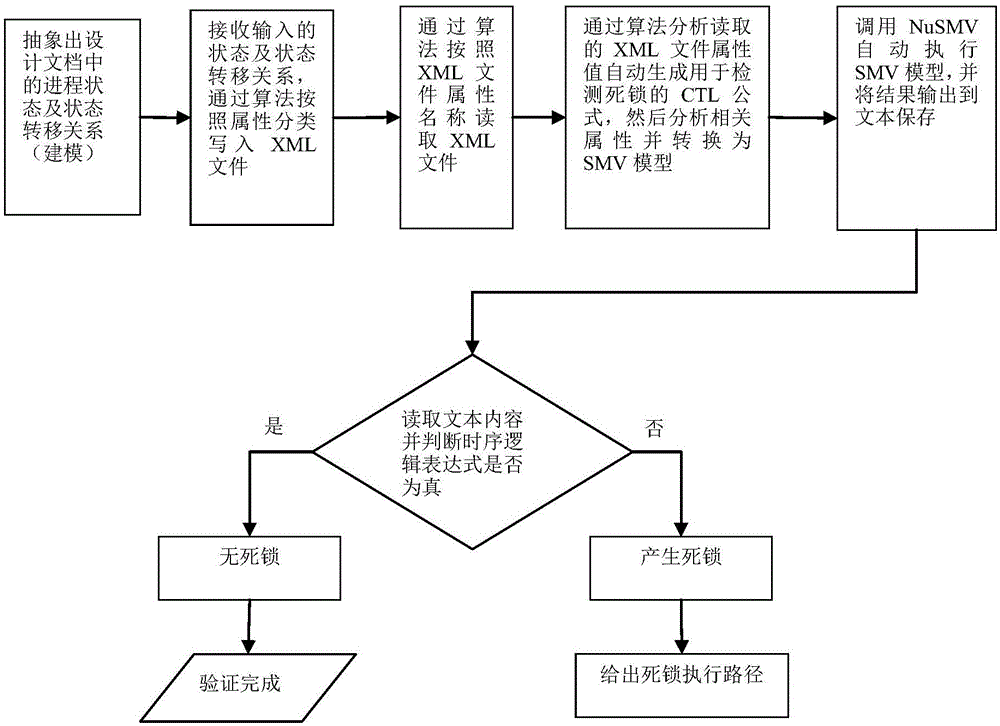
Deadlock detection verification method
InactiveCN105022692AReduce difficultyReduce lossesSoftware testing/debuggingSystems designRelevant information
The invention discloses a deadlock detection verification method, which comprises the following steps: extracting the state and the state transferring relationship of a progress to be extracted; establishing different deadlock detection templates; independently writing the state and the state transferring relationship of the progress as well as a modeling attribute into an XML (Extensive Markup Language) configuration file according to categories; reading the XML configuration file, and selecting the corresponding deadlock detection template to carry out model detection: generating a temporal logic expression CTL (Computing Tree Logic), and converting the state and the state transferring relationship of the progress as well as the temporal logic expression CTL into a SMV (Symbolic Model Verification) model; and executing the SMV model, analyzing a truth value of the temporal logic expression CTL in an execution result, and judging whether a design document contains deadlock or not. The deadlock detection verification method automatically analyzes the input of the relevant information of the deadlock detection to automatically select and convert the corresponding template into a prototype of the SMV model, lowers a deadlock detection difficulty, is free from the restriction of software development languages, can carry out deadlock detection on a design scheme in a system design stage and reduces unnecessary losses if being compared with a situation that the deadlock is found in a software development stage.
Owner:SICHUAN UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com