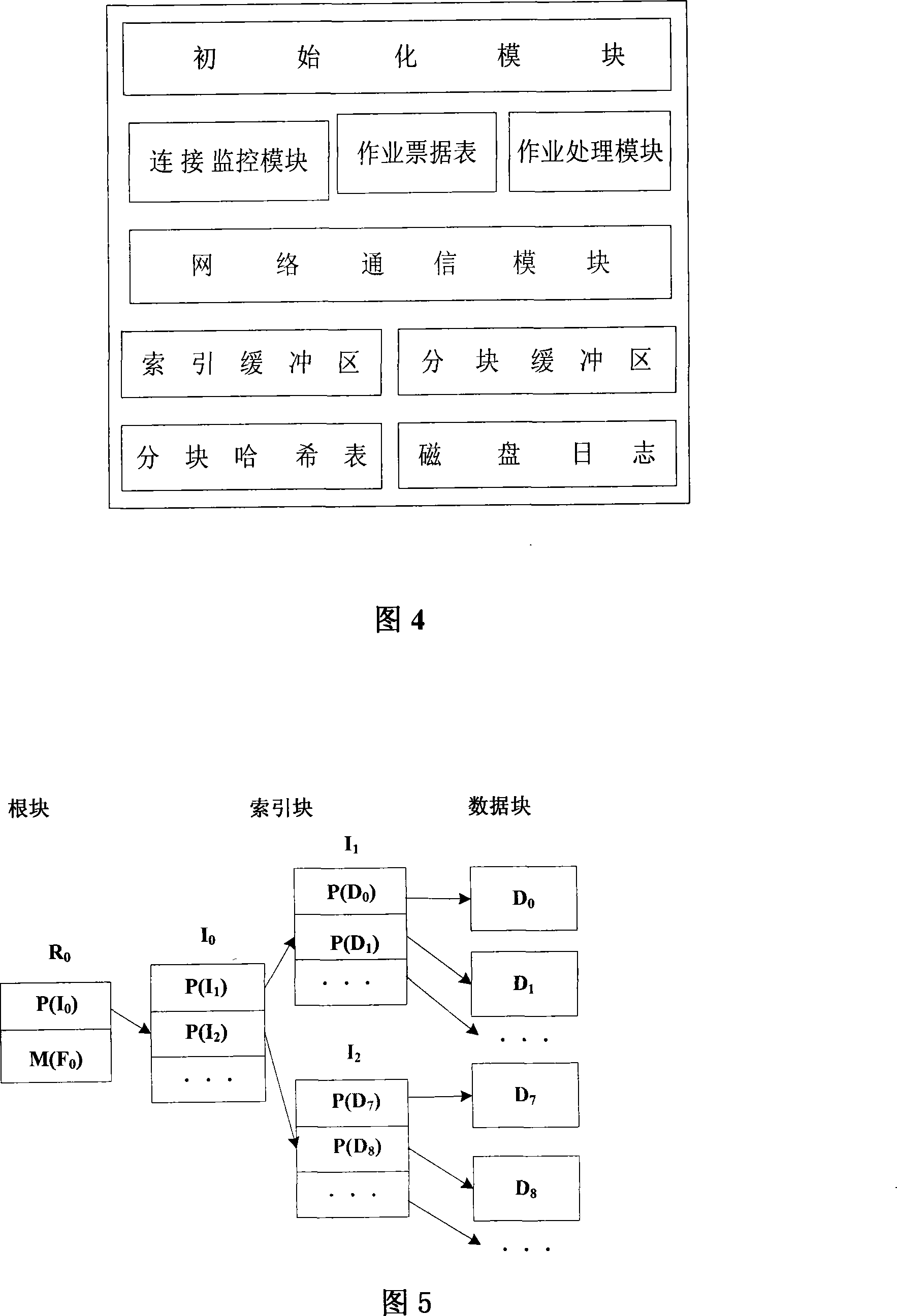
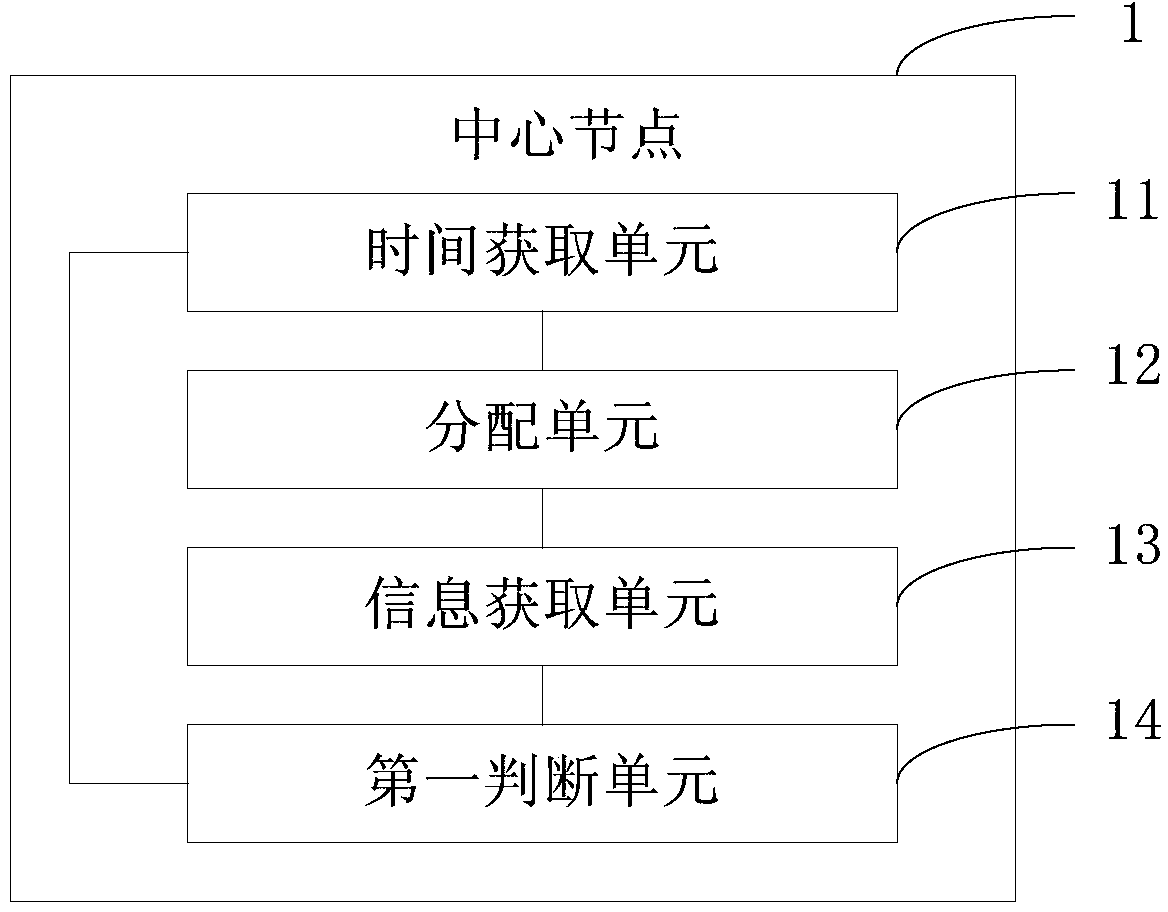
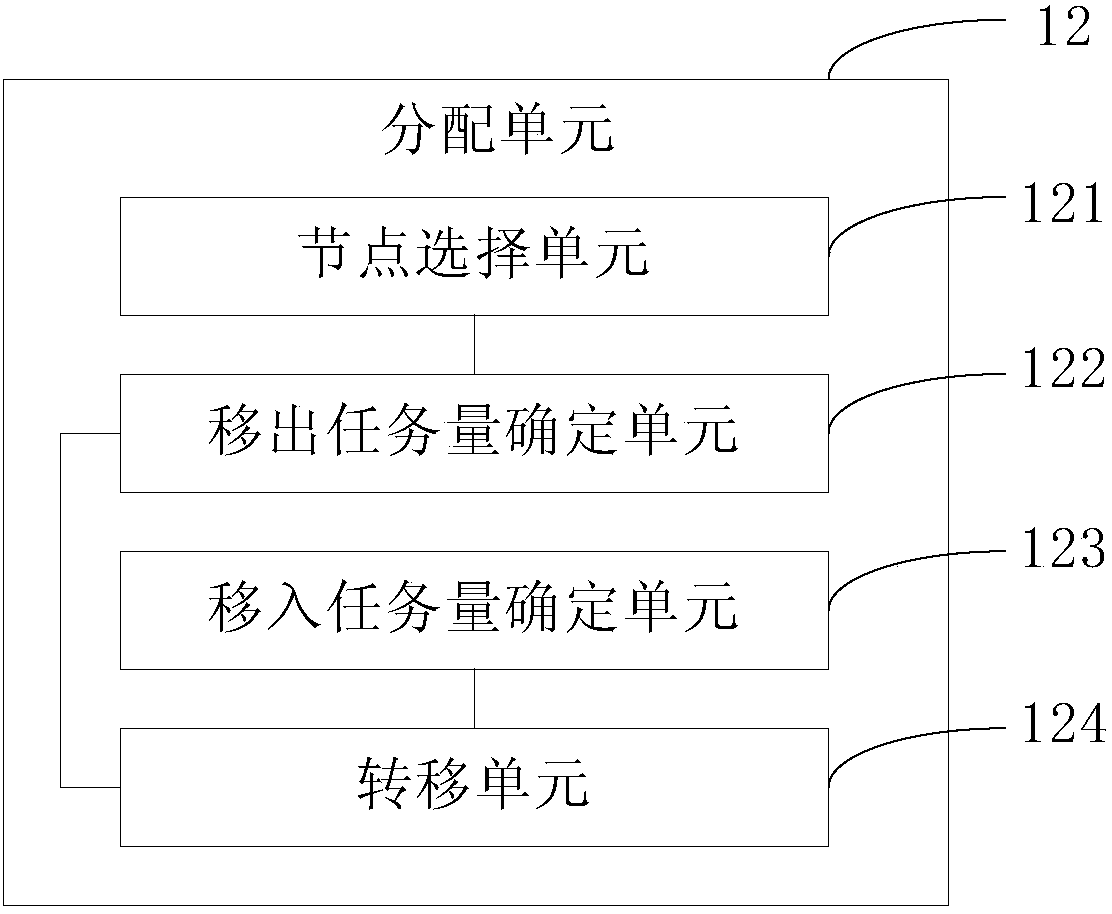
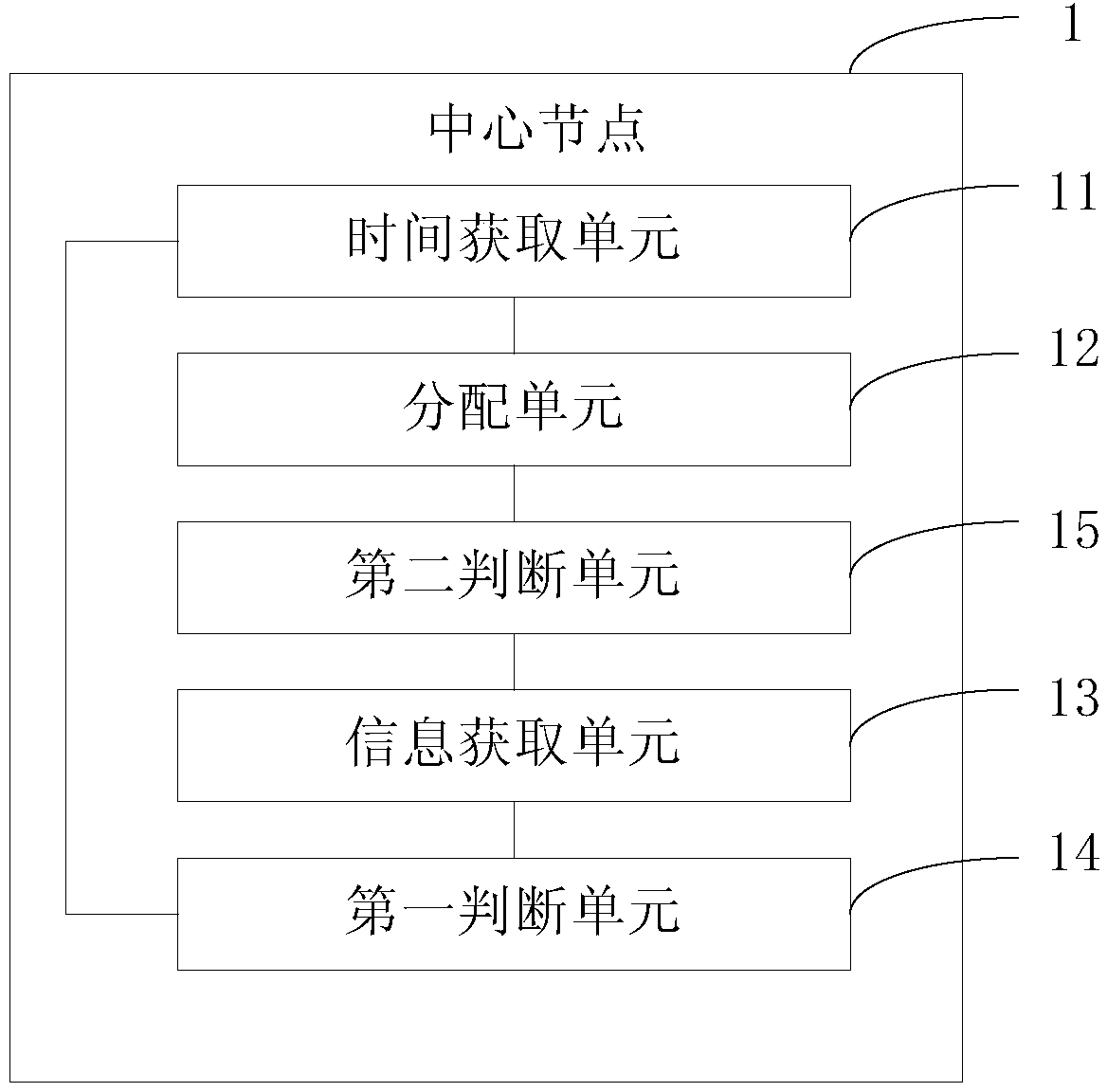
Patents
Literature
730 results about "Network overhead" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Network overhead is the header data that is required to route and transport data over network, whereas fork overhead is the additional time and memory cost of creating and managing new processes within operating system. overhead. An overhead throw. overhead(Noun) An overhead projector.
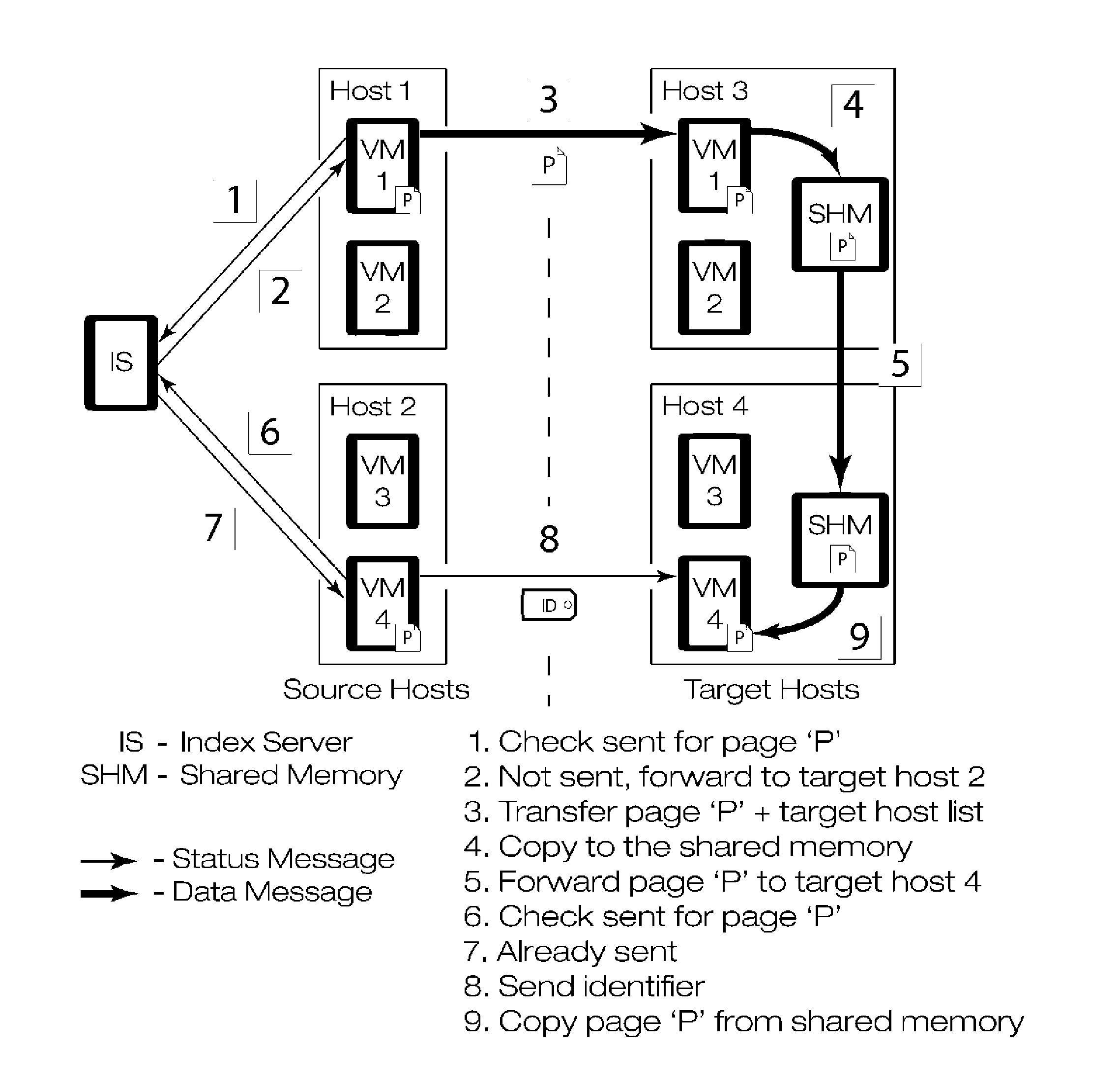
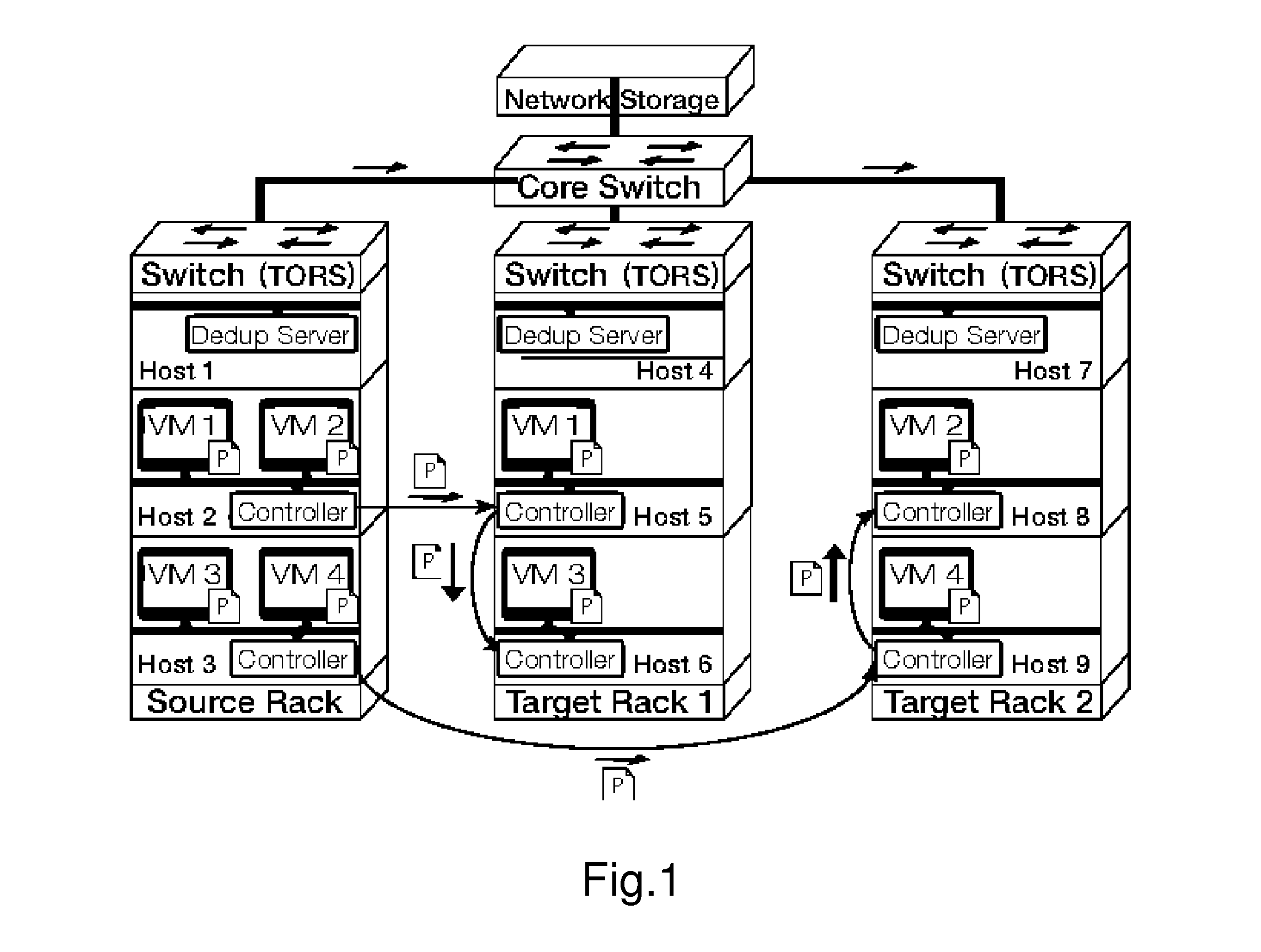
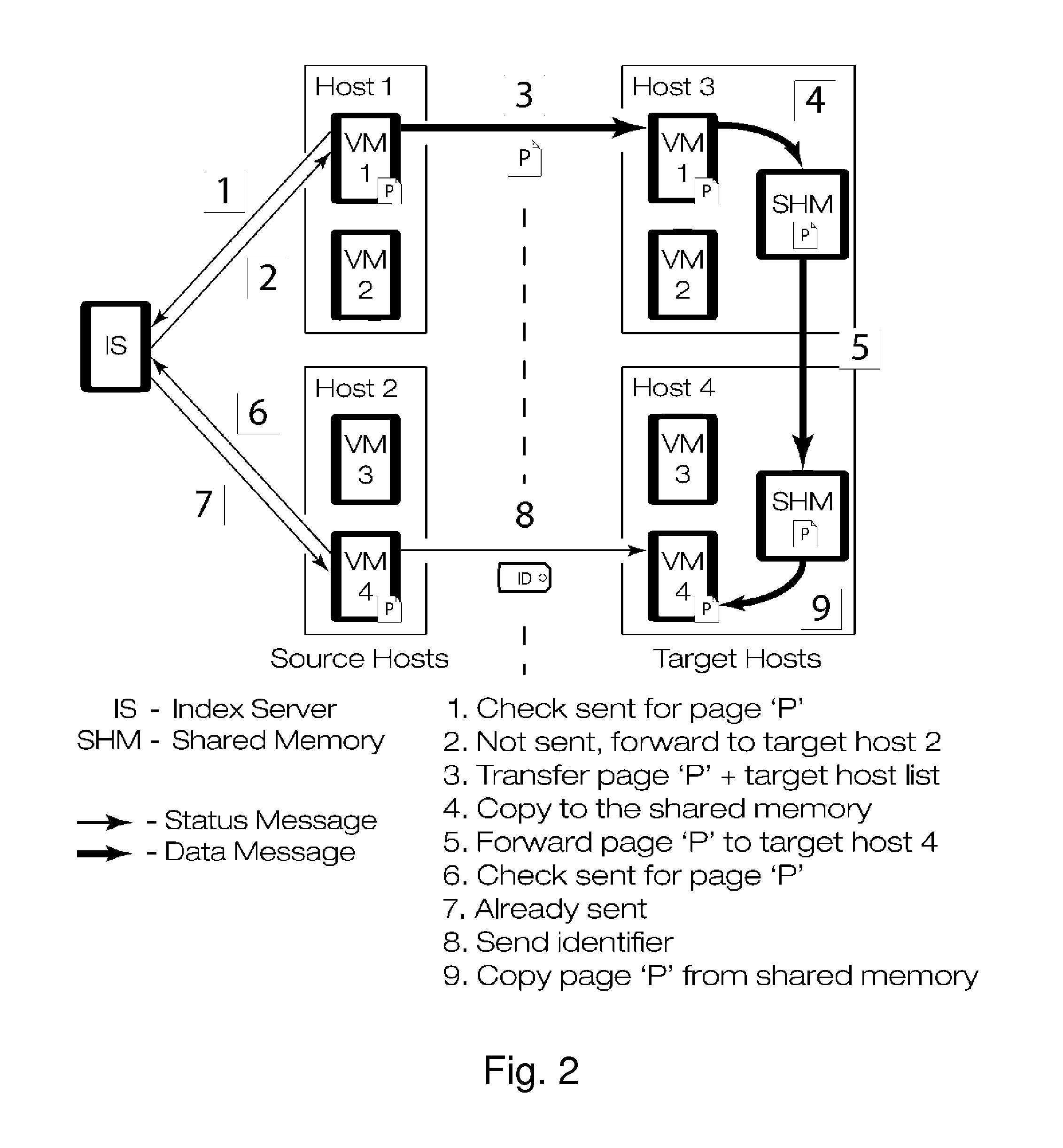
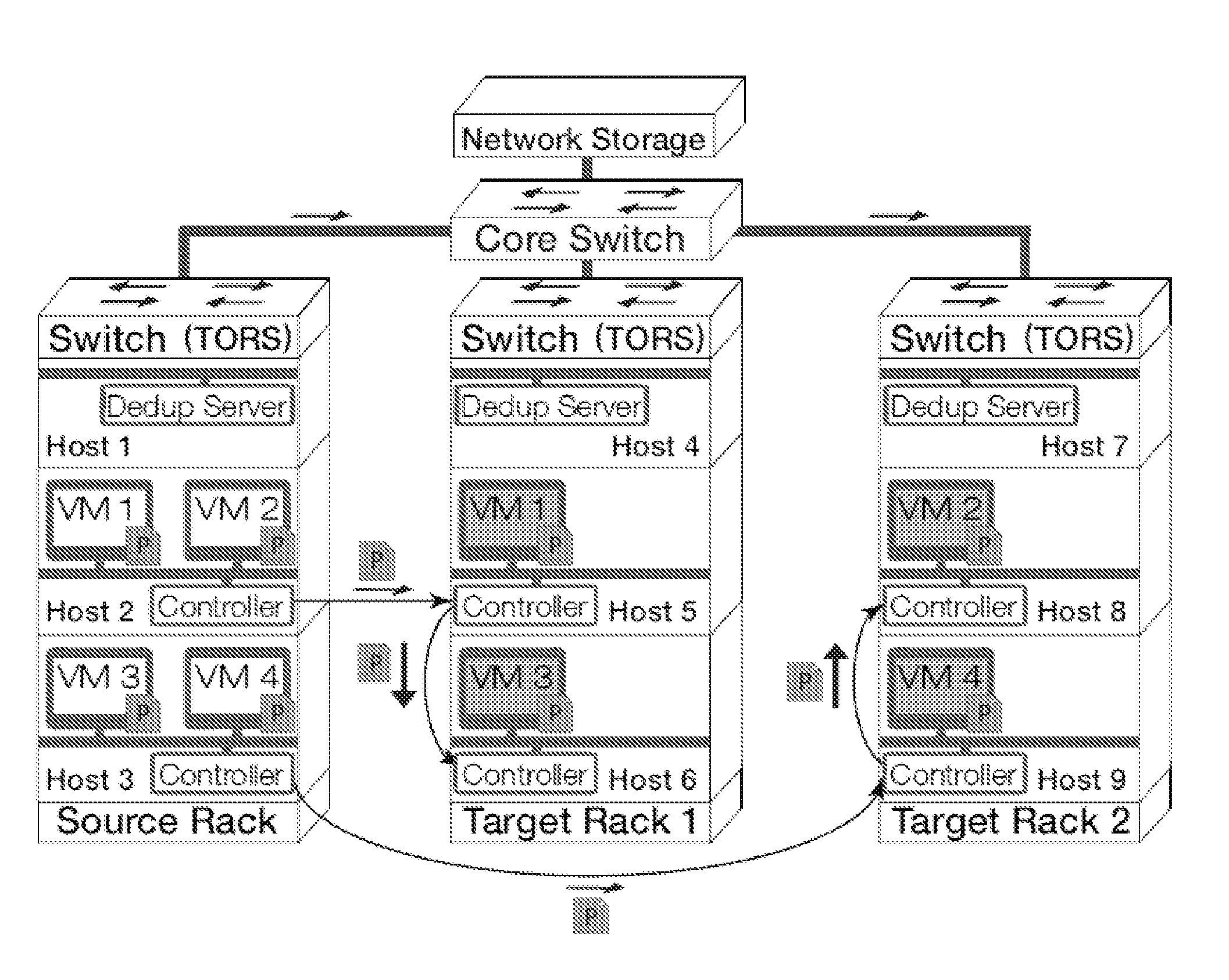
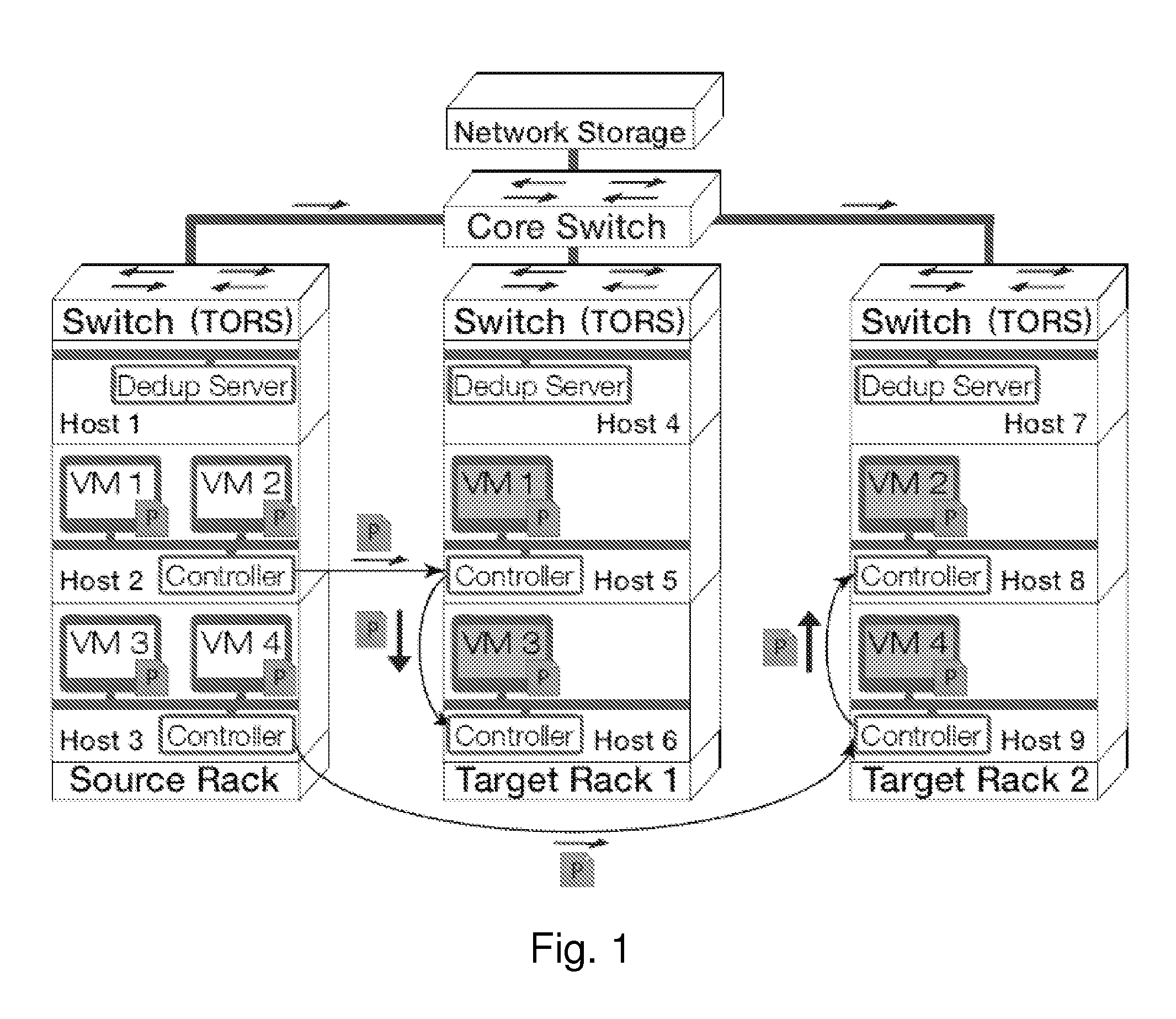
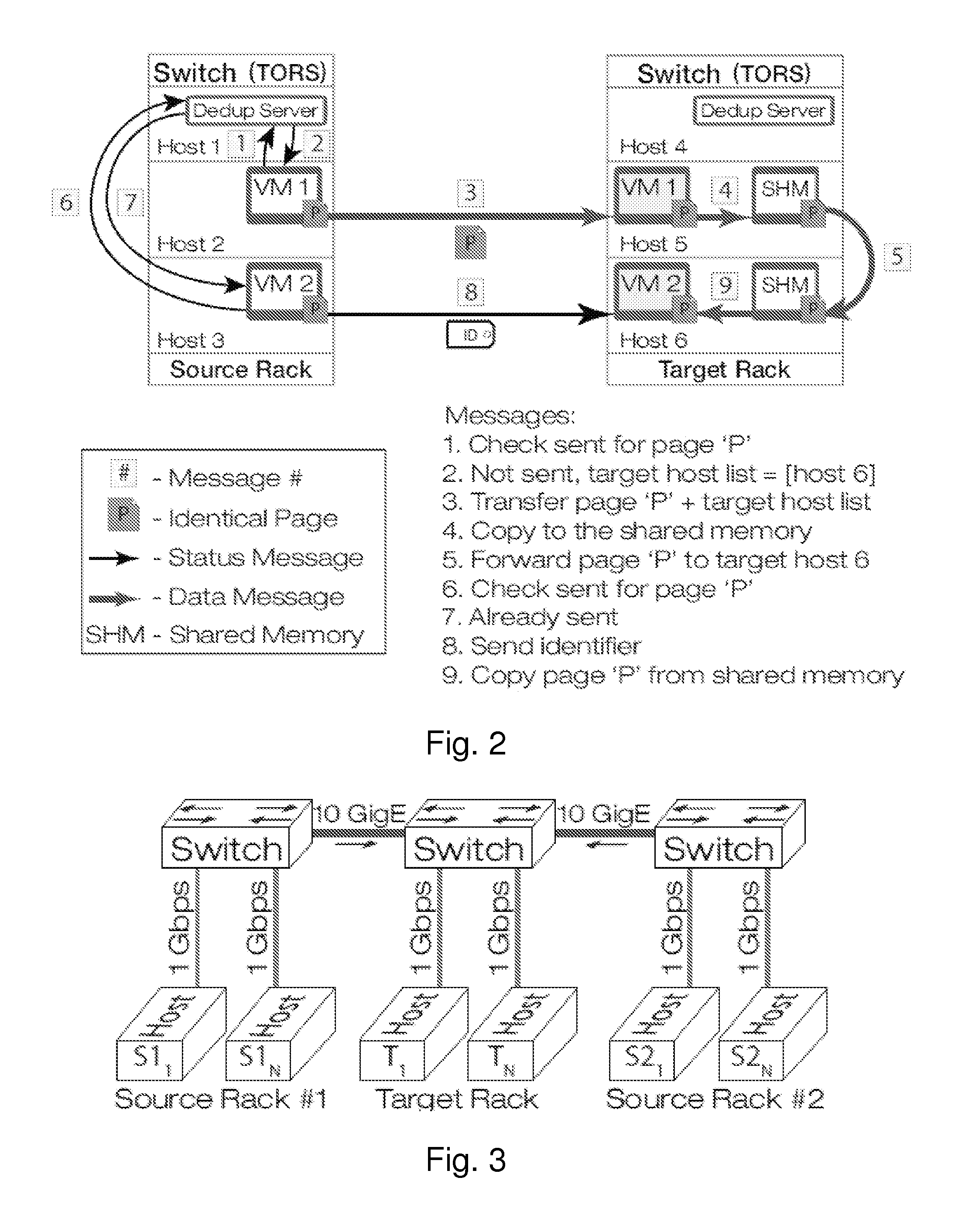
Gang migration of virtual machines using cluster-wide deduplication
ActiveUS20140196037A1Reduce throughputIncrease delayMemory architecture accessing/allocationProgram initiation/switchingTraffic capacityData center
Datacenter clusters often employ live virtual machine (VM) migration to efficiently utilize cluster-wide resources. Gang migration refers to the simultaneous live migration of multiple VMs from one set of physical machines to another in response to events such as load spikes and imminent failures. Gang migration generates a large volume of network traffic and can overload the core network links and switches in a data center. The present technology reduces the network overhead of gang migration using global deduplication (GMGD). GMGD identifies and eliminates the retransmission of duplicate memory pages among VMs running on multiple physical machines in the cluster. A prototype GMGD reduces the network traffic on core links by up to 51% and the total migration time of VMs by up to 39% when compared to the default migration technique in QEMU / KVM, with reduced adverse performance impact on network-bound applications.
Owner:THE RES FOUND OF STATE UNIV OF NEW YORK
Apparatus and method for reducing power consumption in ad-hoc network
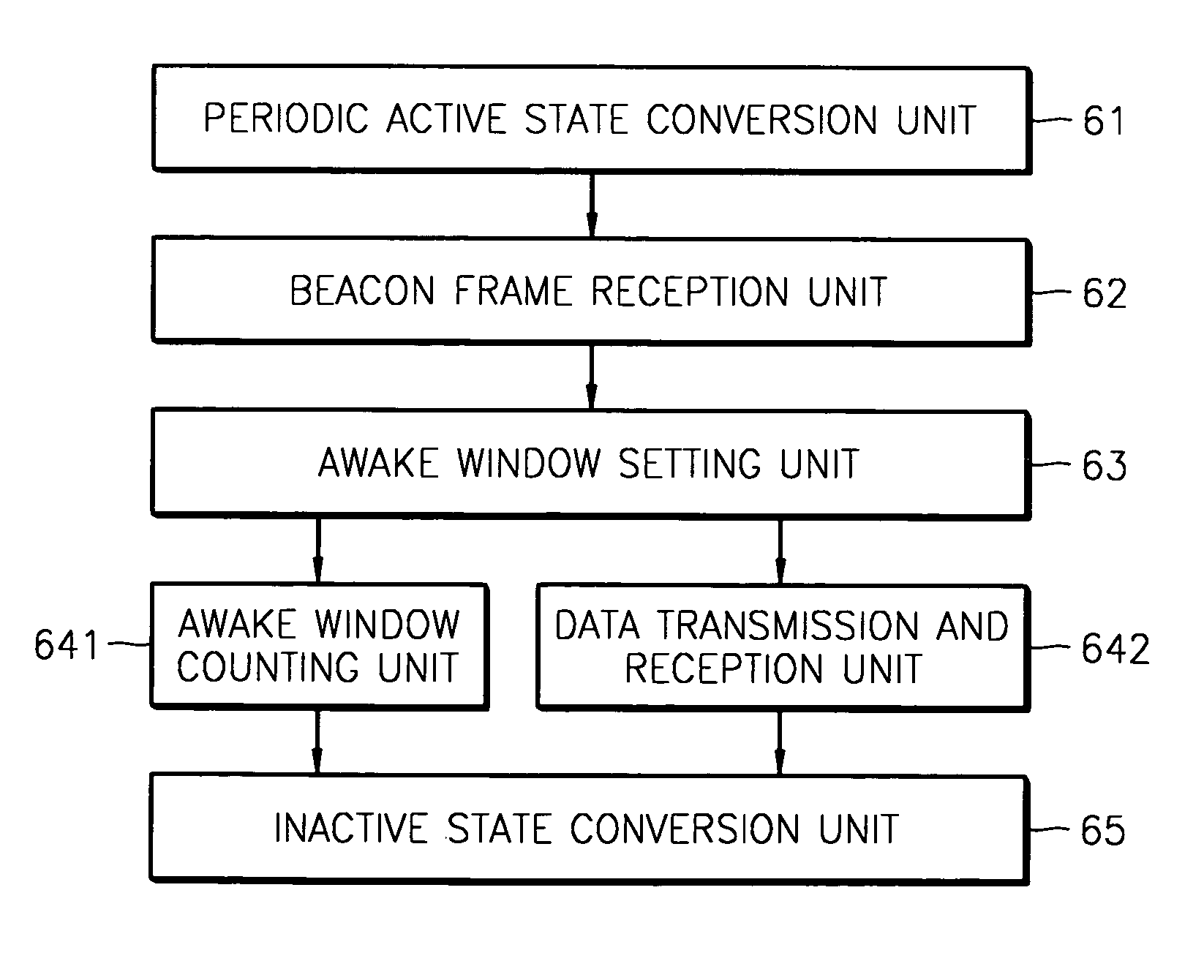
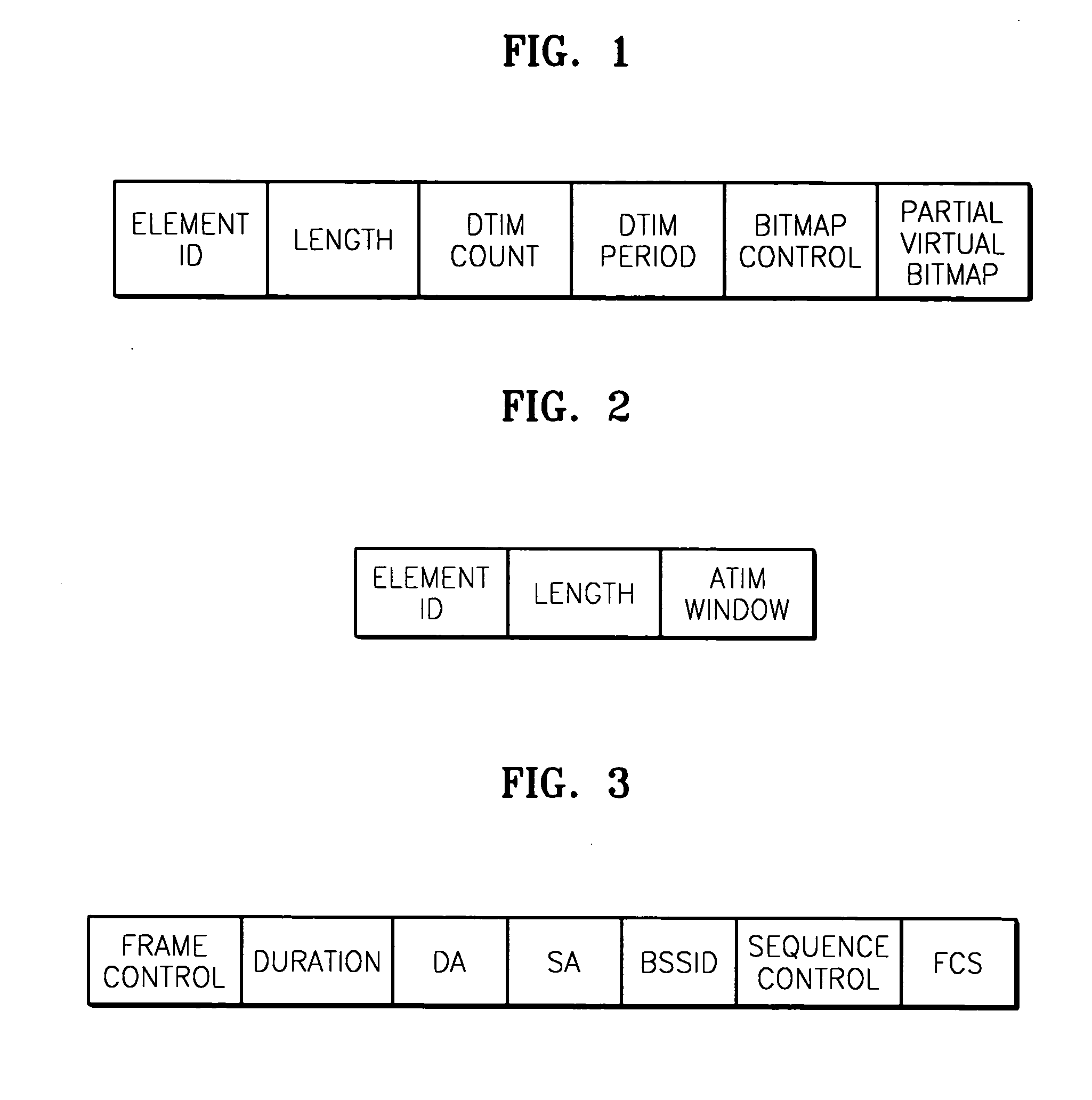
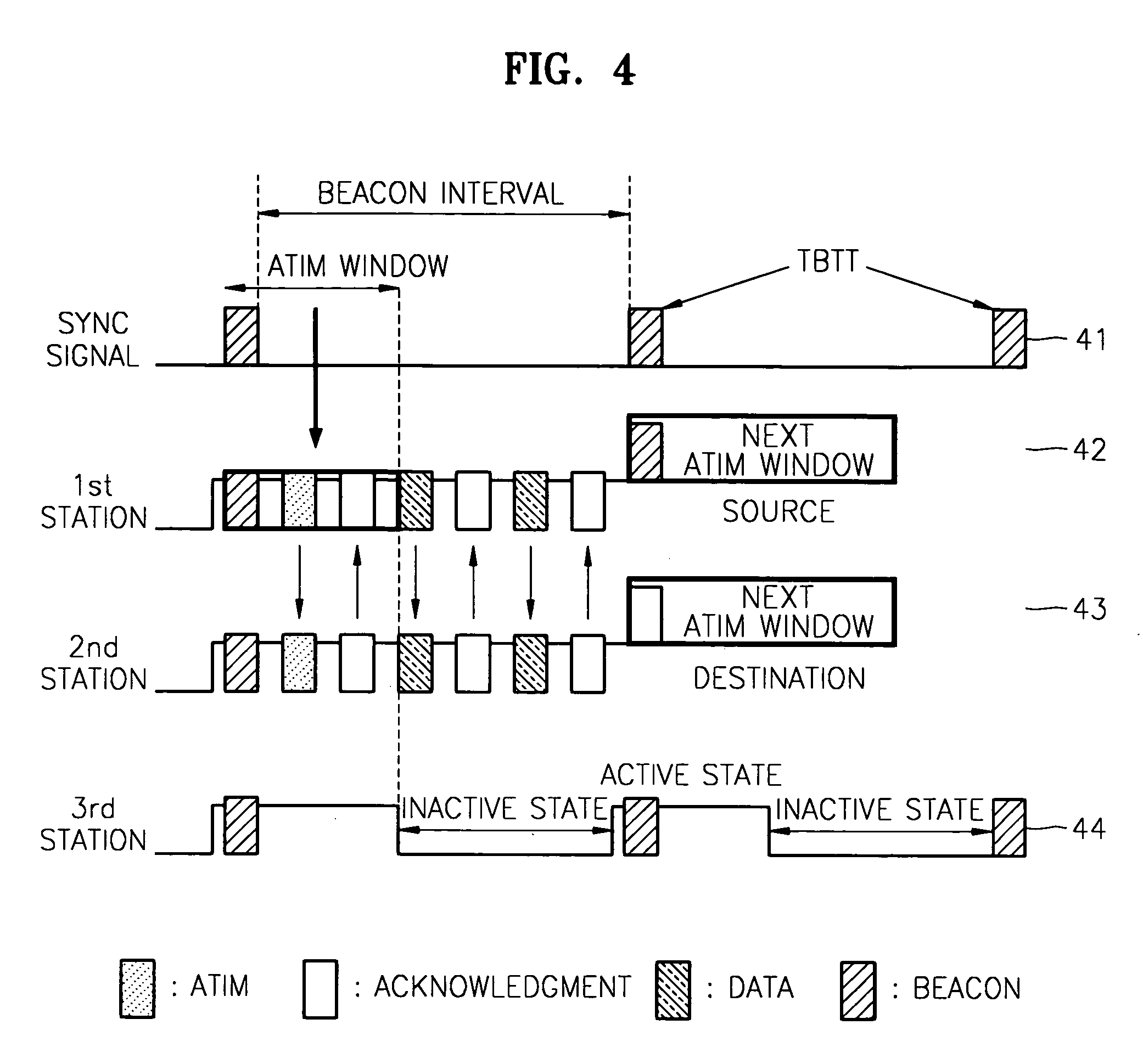
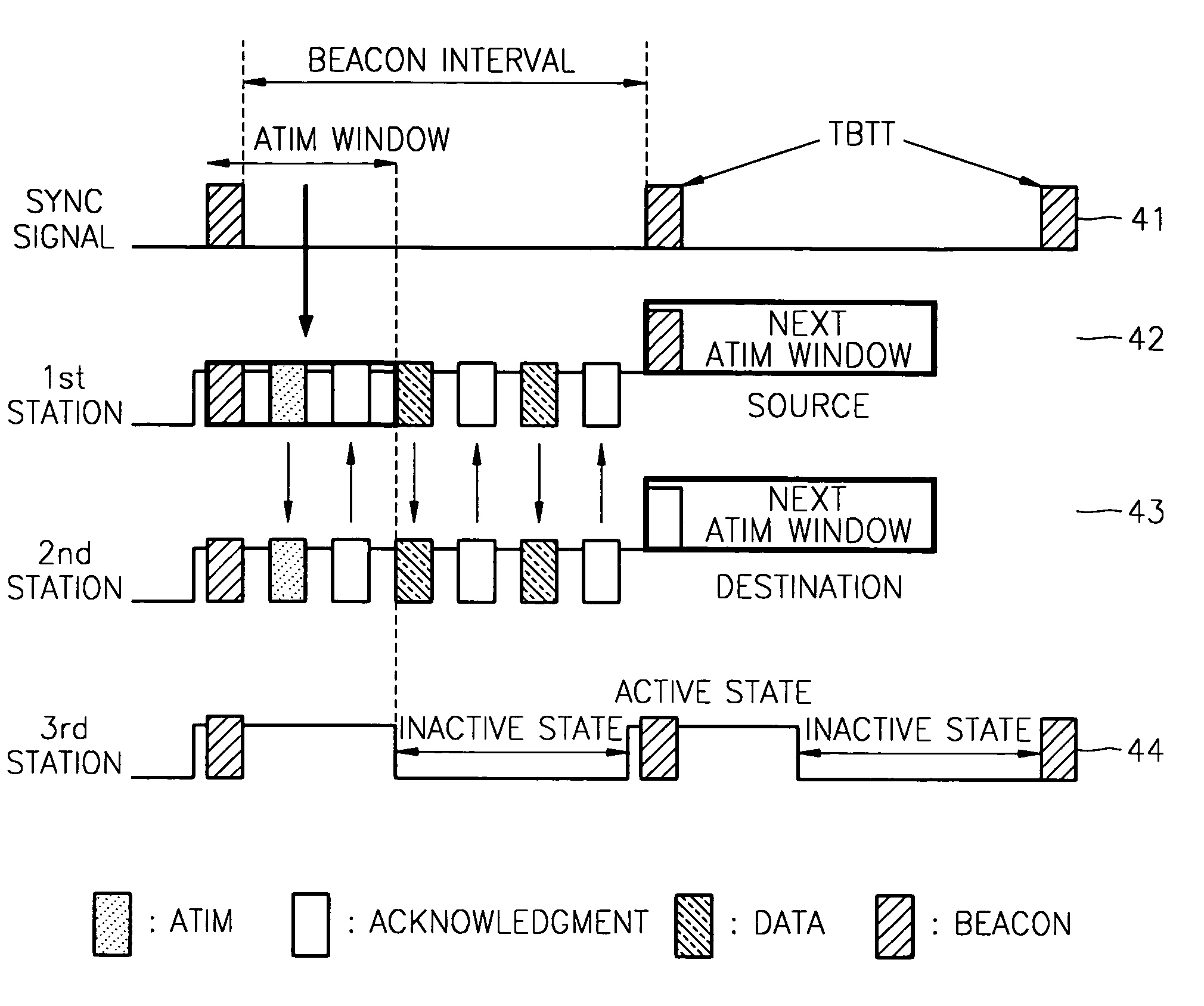
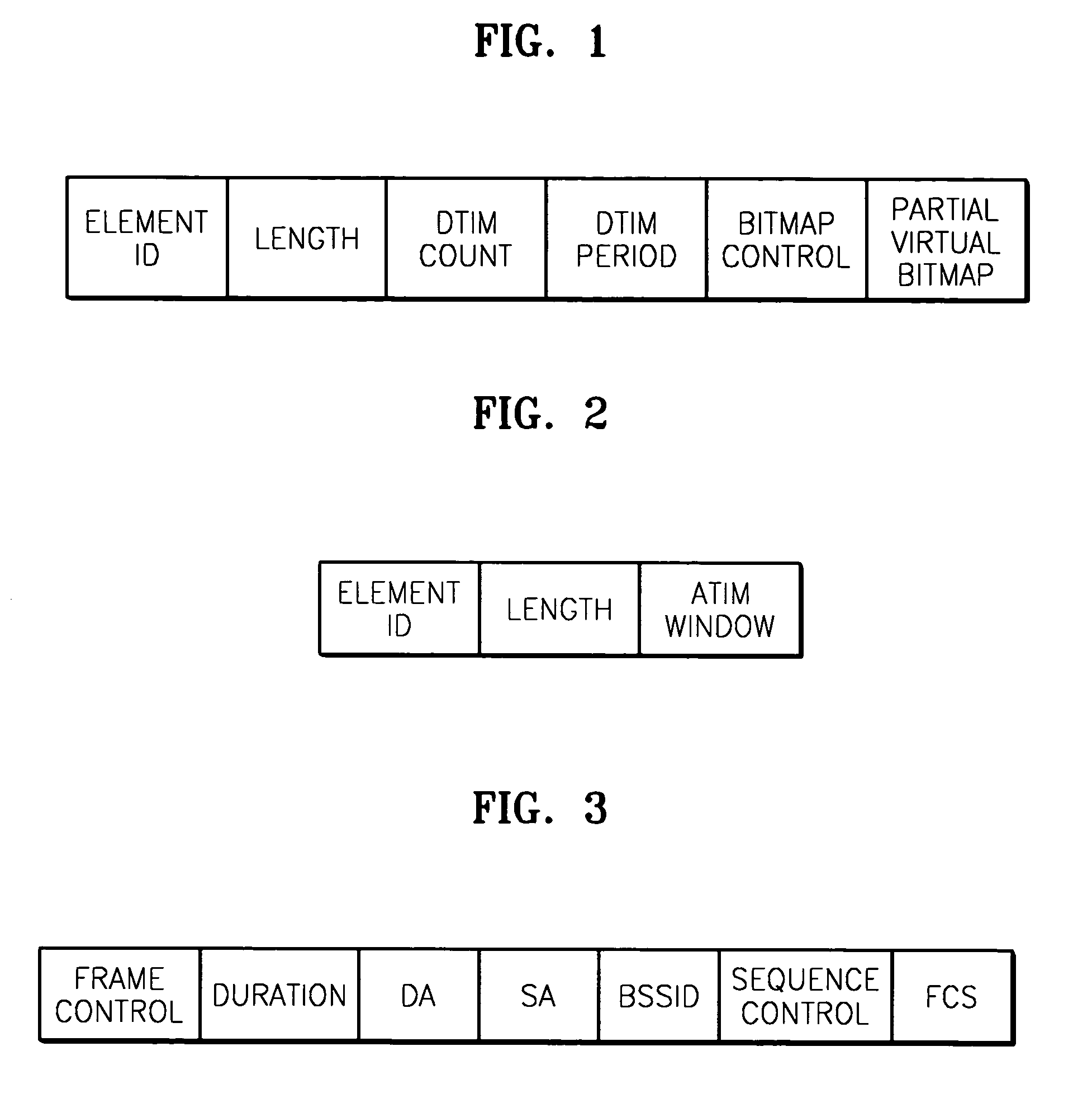
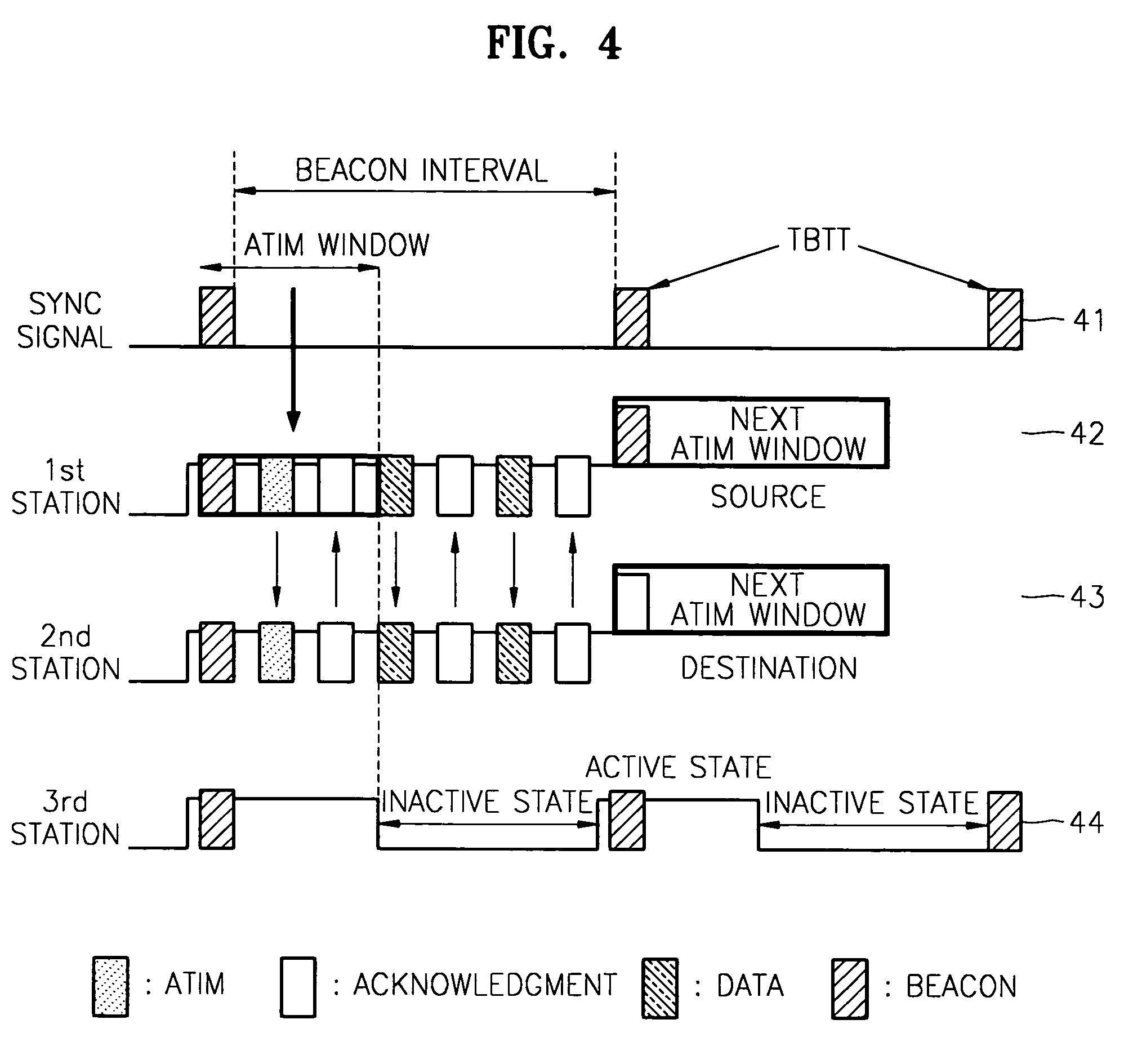
A power consumption reducing apparatus and method are provided wherein the apparatus includes a periodic active state conversion unit which converts an inactive state into an active state; a beacon frame reception unit which, in an active state, receives a beacon frame; an awake window setting unit which sets the awake window; an awake window interval counting unit which counts the interval value in the awake window; and an inactive state conversion unit which converts the awake window into an inactive state. According to the apparatus, an active state needs to be maintained only during a window interval such that power consumption can be reduced during an inactive interval. In addition, an ATIM window is replaced by an awake window such that an ATIM message that has been regarded as a network overhead, and an acknowledgement response frame to the message are removed, that is, the network overheads are removed.
Owner:SAMSUNG ELECTRONICS CO LTD
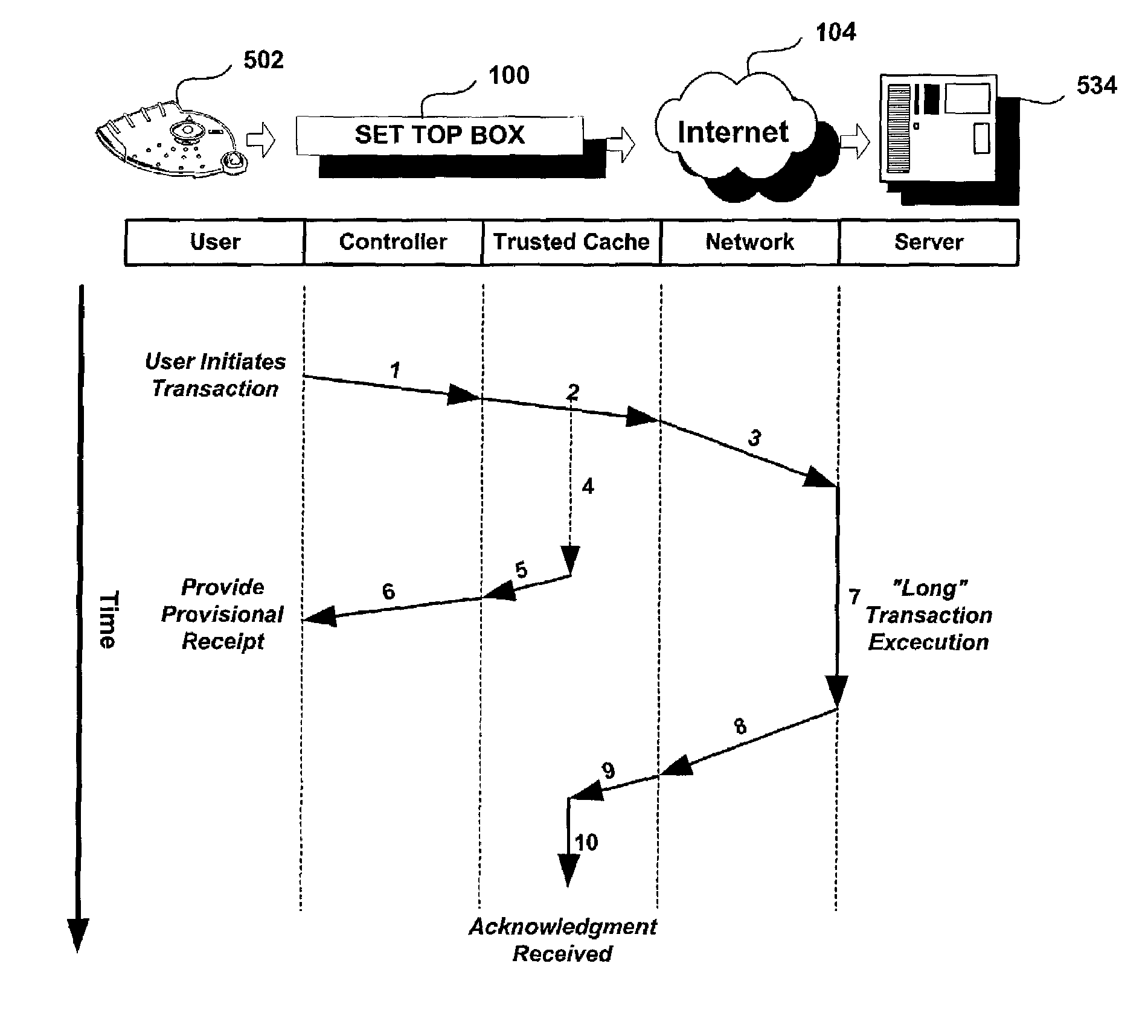
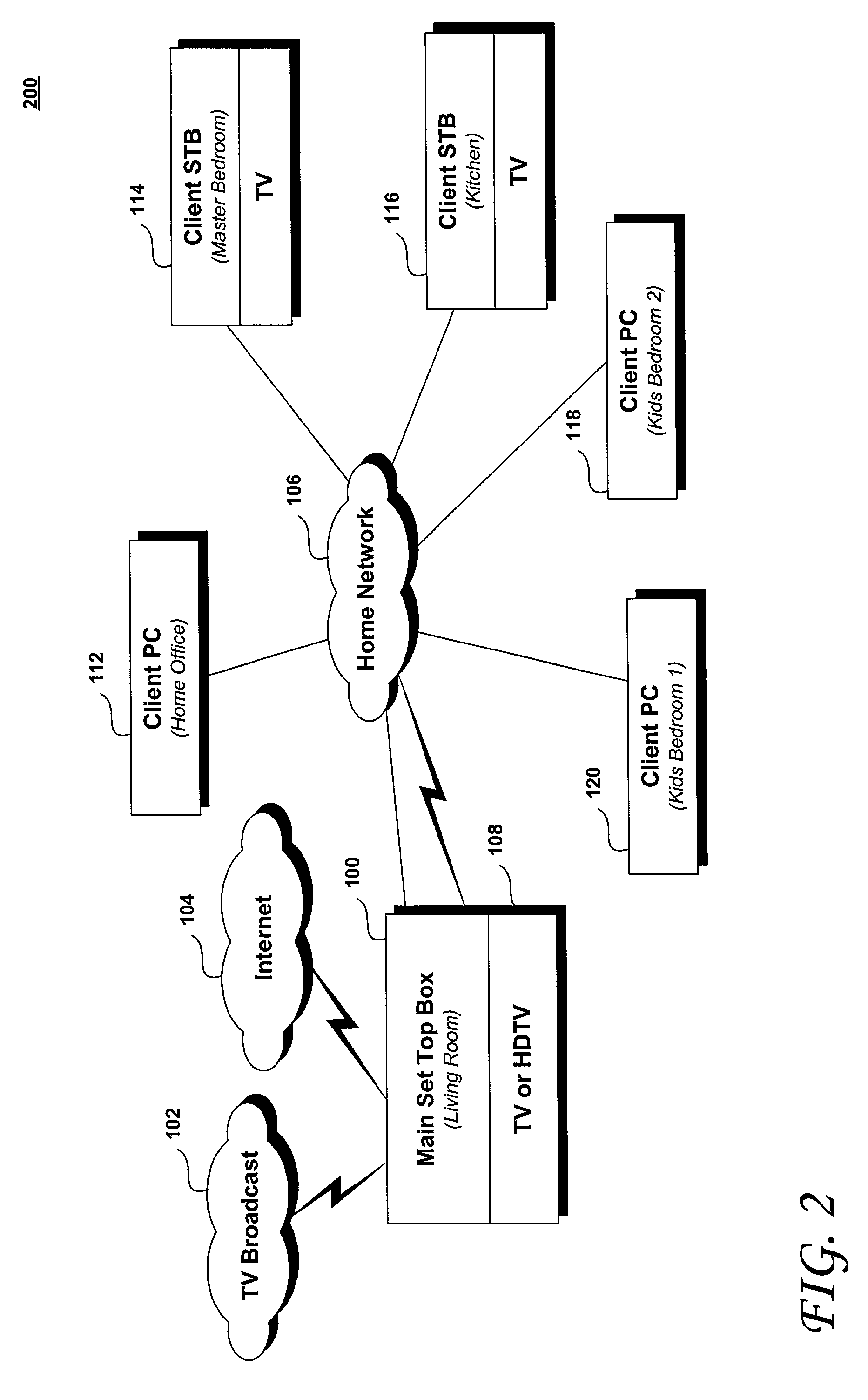
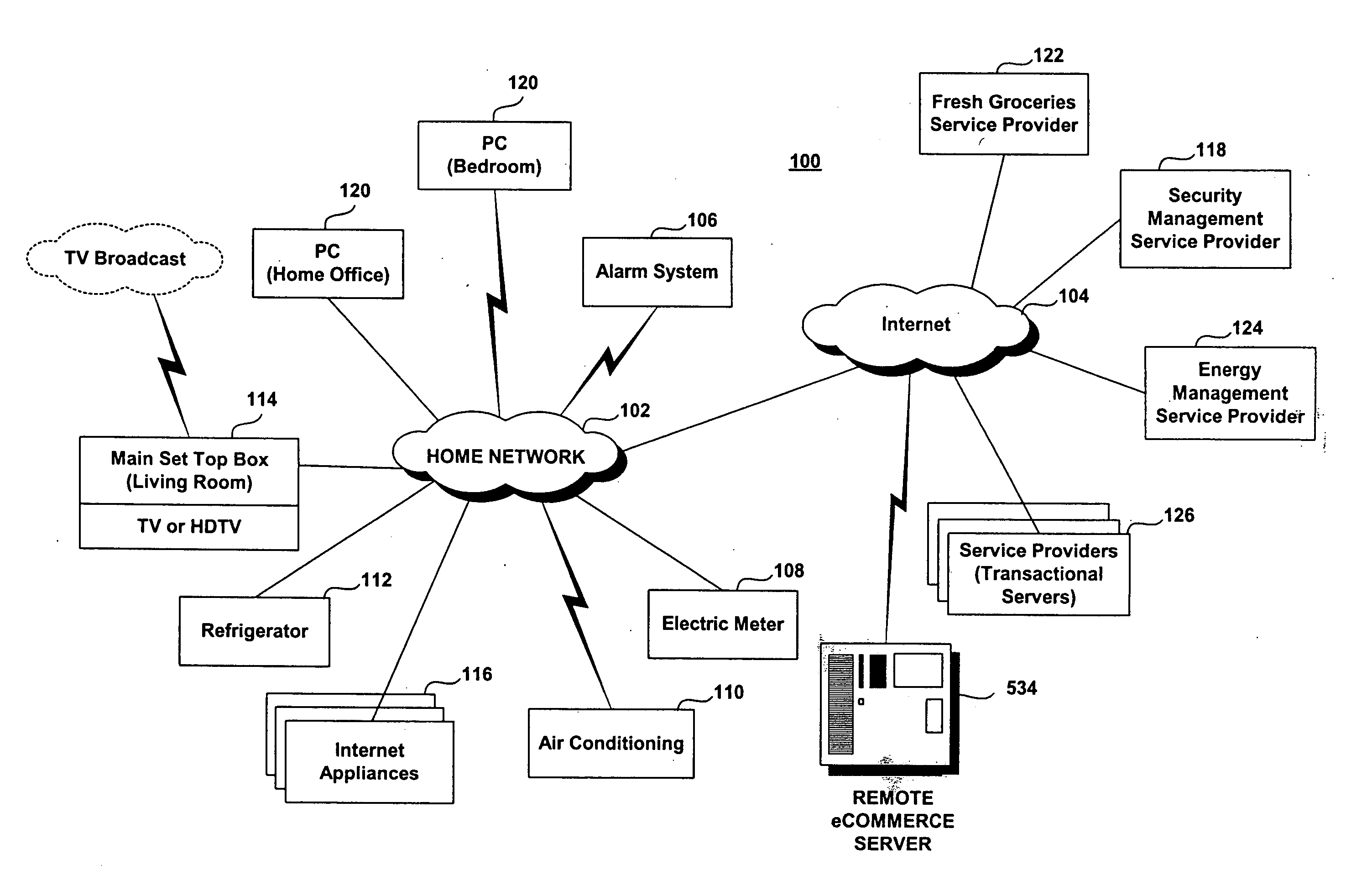
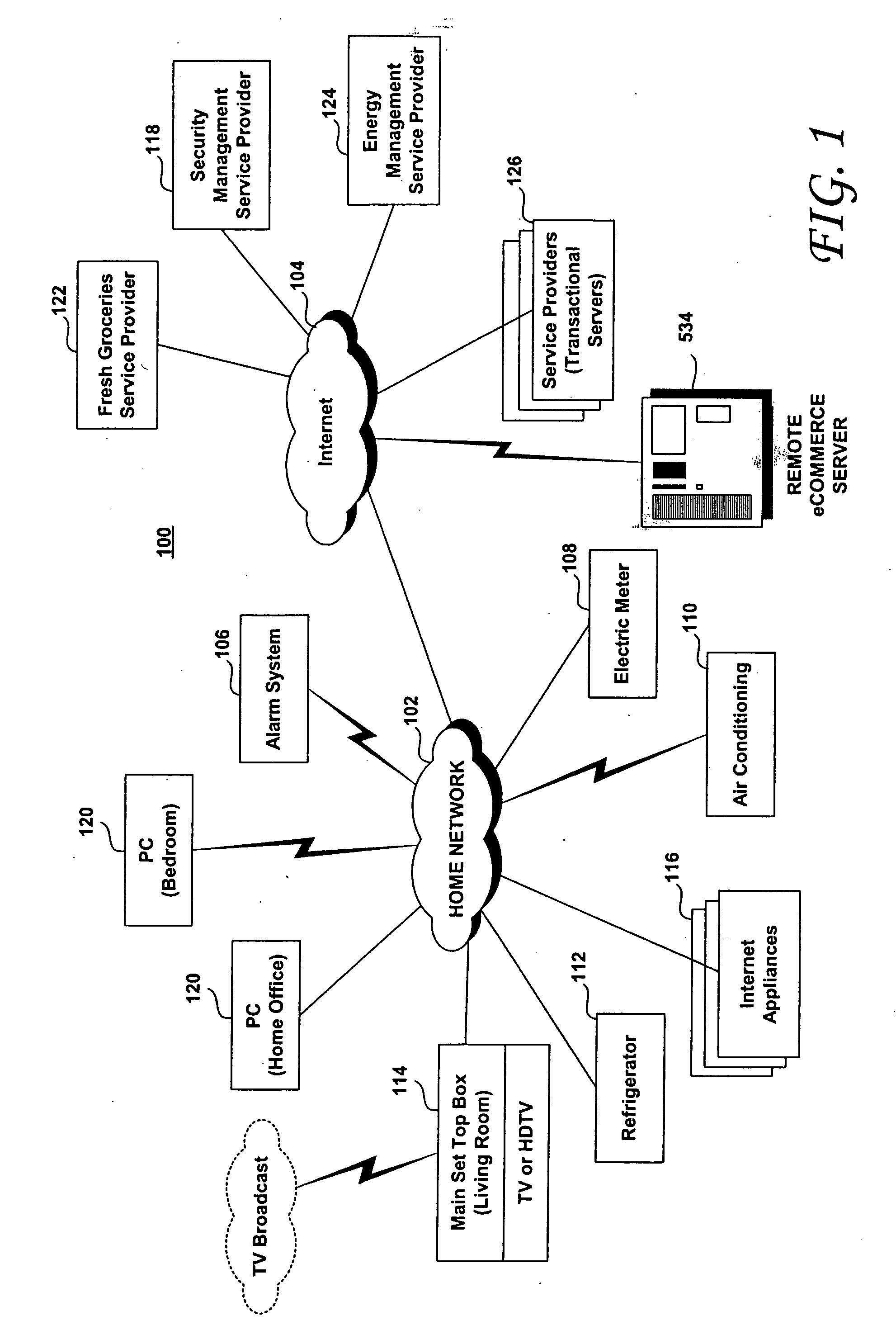
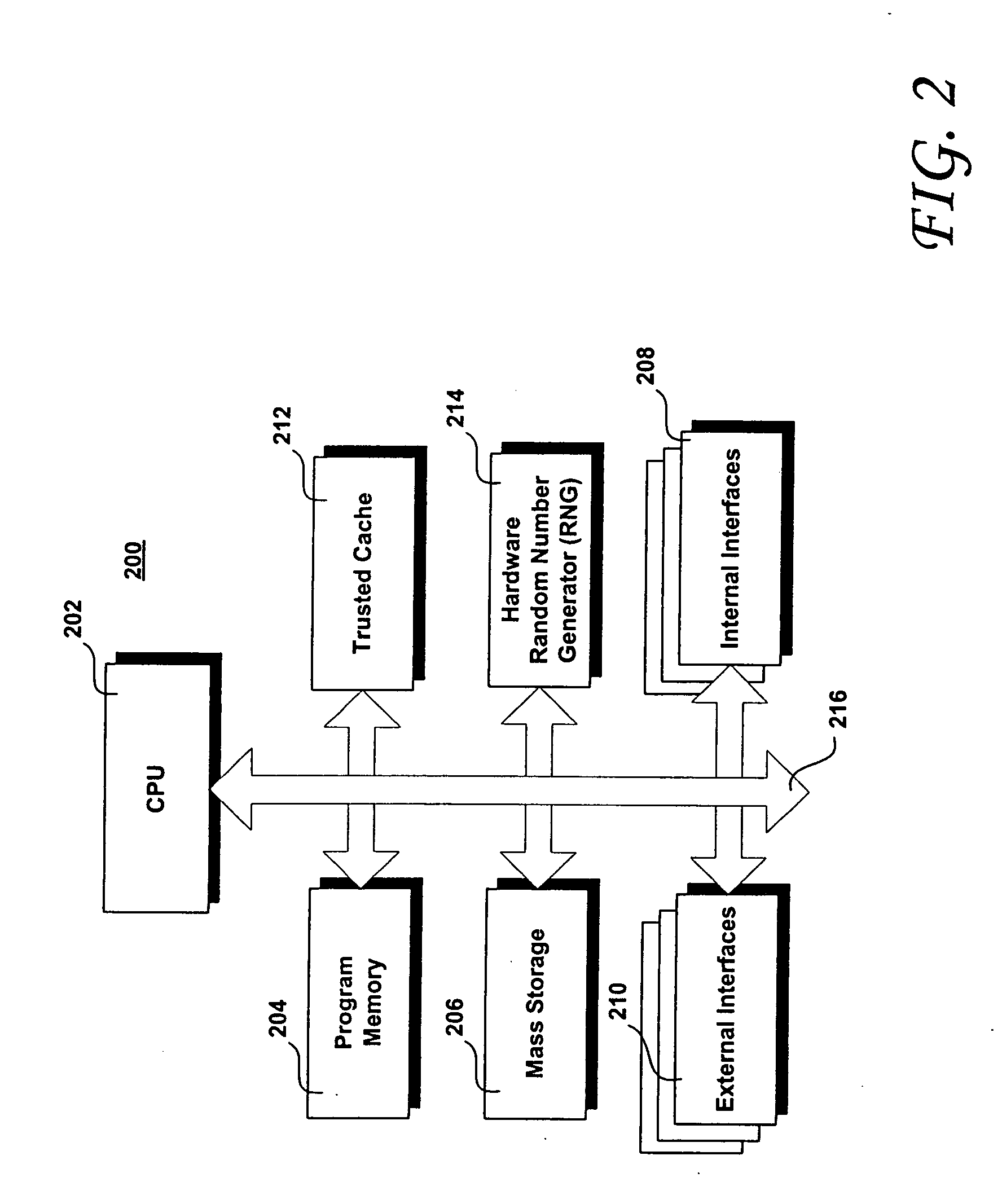
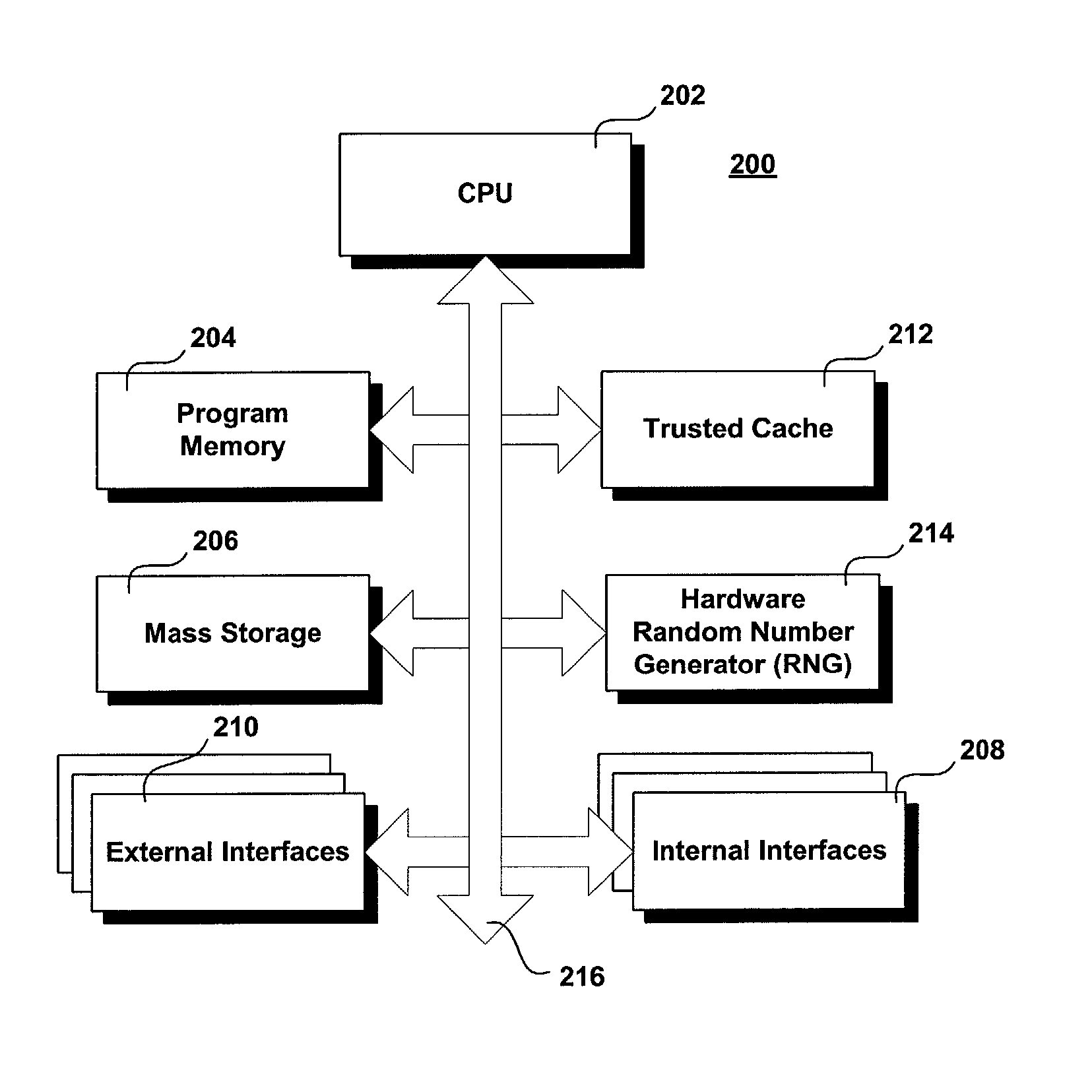
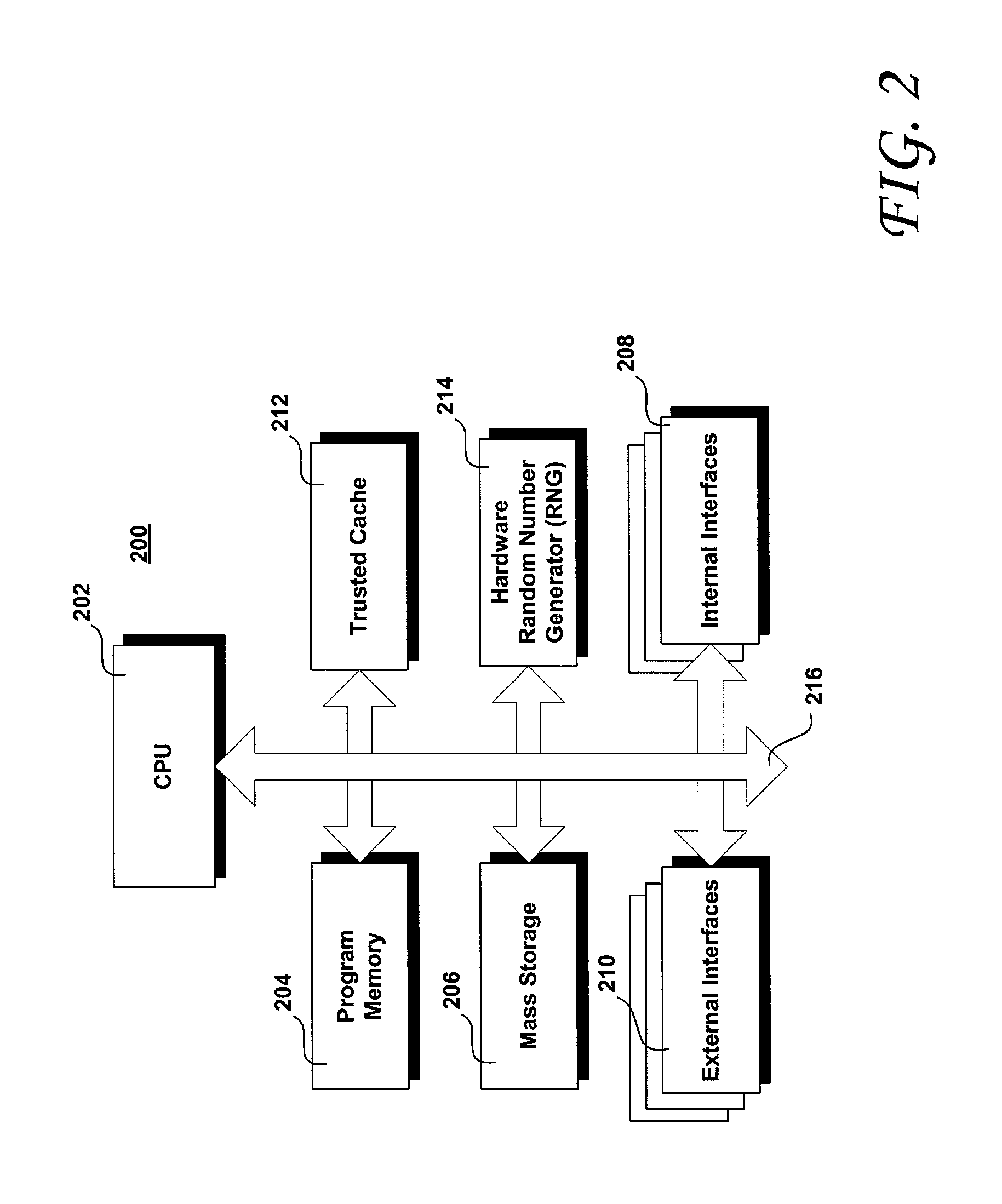
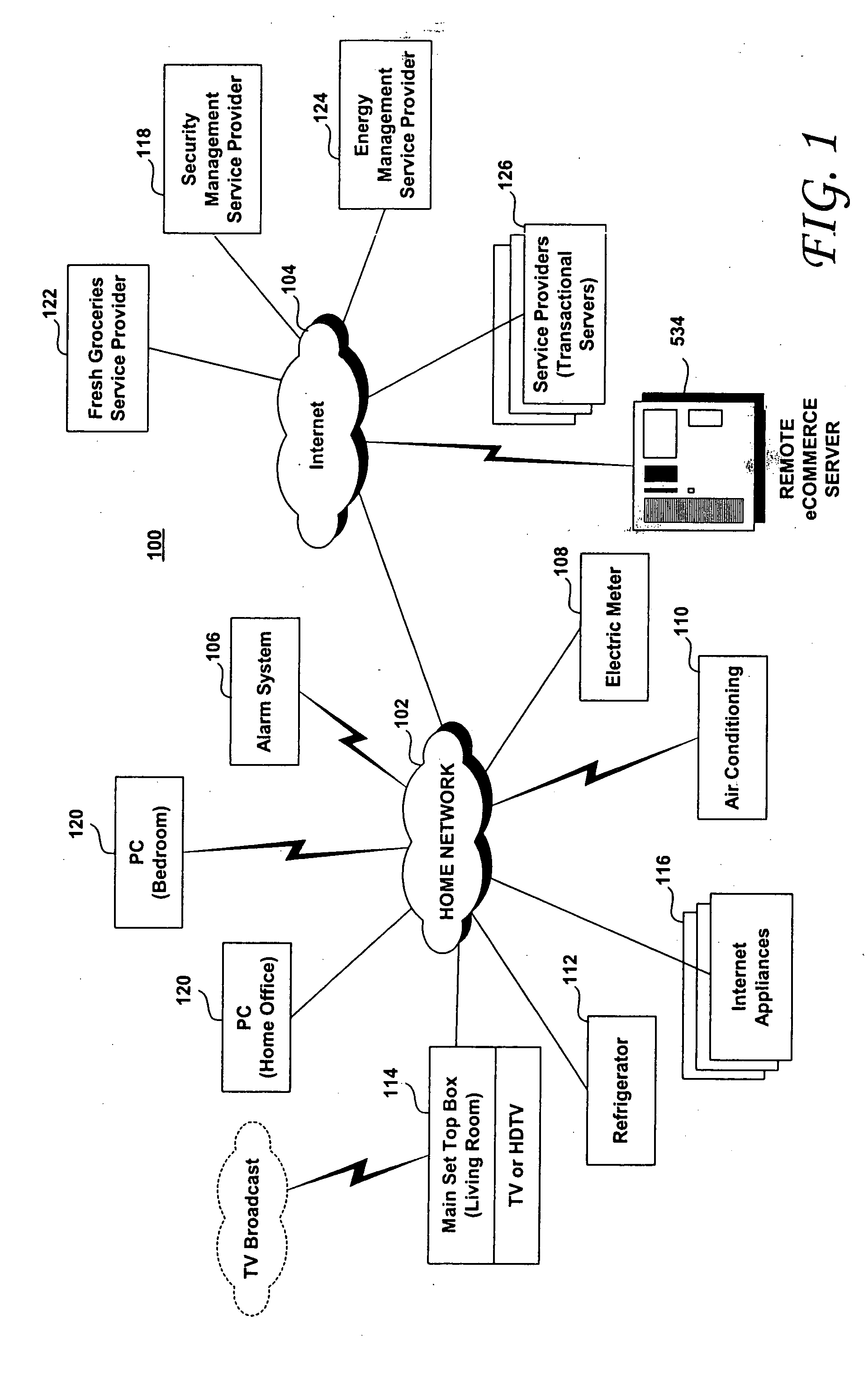
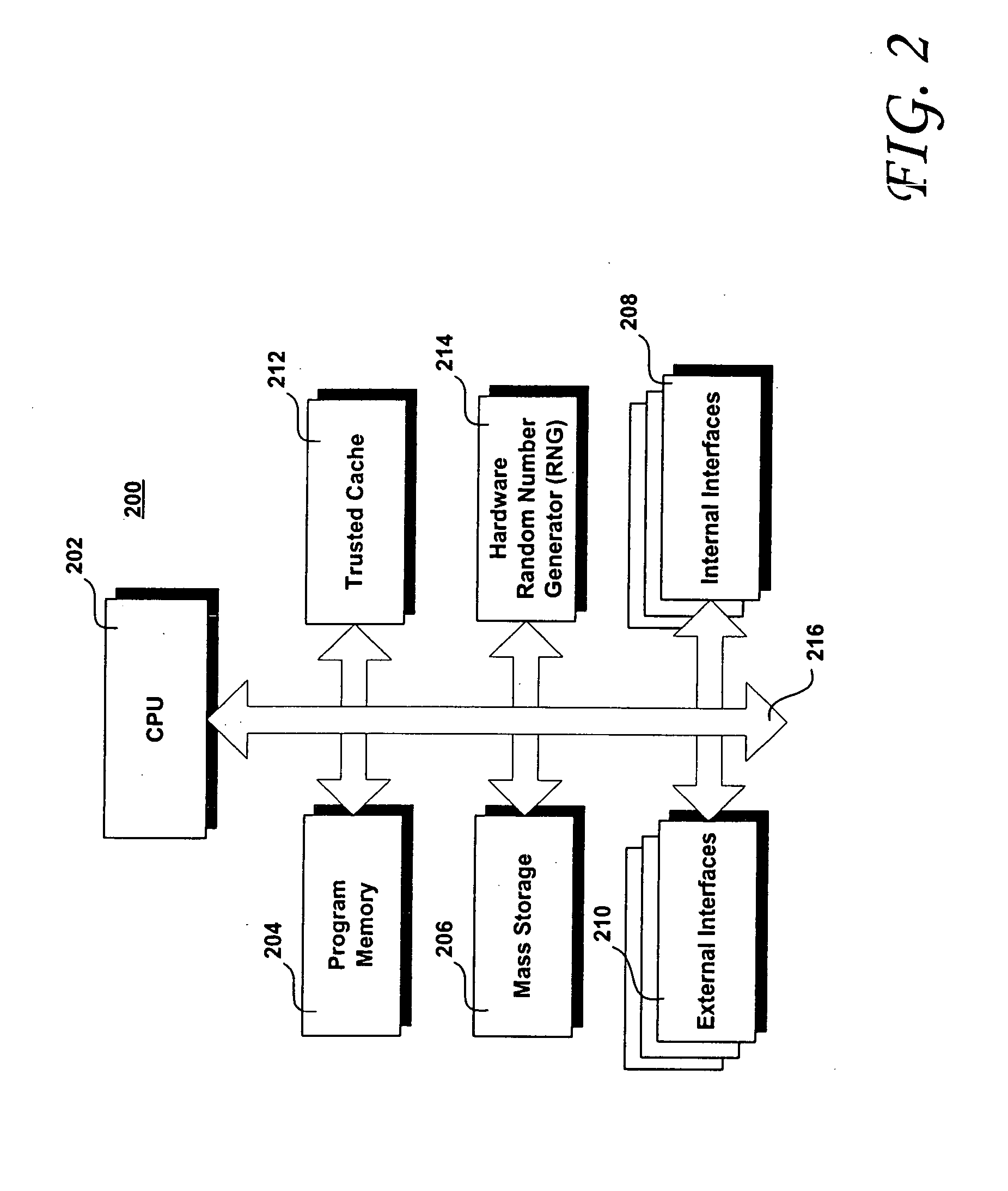
Trusted transactional set-top box
InactiveUS7346917B2Poor resolutionMaximum safetyTelevision system detailsAnalogue secracy/subscription systemsPrivate networkThe Internet
A set top box (STB) includes a trusted transactional cache and associated transactional protocol and enables e-commerce transactions to be securely committed to a remote server extremely quickly and with little network overhead. The invention does away with the user concern of whether the transaction was successful. The STB operates equally well on robust private networks as on unpredictable Internet or wireless networks, and avoids upsetting users who would otherwise have to wait in front of a display screen for confirmation of completion of the transaction after a temporary communication failure with the central site. The method may advantageously be used to provide cost-effective micro-payments solutions. The STB may include a dual headed display capability in which data and video maybe be directed to separate displays. The STB may feature an embedded ticket printer, as well as an embedded barcode scanner. This enables non computer literate users to more conveniently track transactions committed via the STB, or to take advantage of promotional coupons. The STB features an embedded hardware true Random Number Generator to produce maximum entropy encryption keys, therefore providing maximum secure and fool-proof means to protect private data using government authorized encryption schemes.
Owner:MUDALLA TECH INC THOITS LOVE HERSHBERGER & MCLEAN
Method and apparatus for fast transaction commit over unreliable networks
InactiveUS20050086286A1Error detection/correctionMultiple digital computer combinationsElectronic controllerPrivate network
An electronic controller for conducting trusted lightweight e-commerce transactions. A trusted transactional cache and the associated transactional protocol allow e-commerce transactions to be committed to a remote server extremely quickly and with little network overhead. The end-to-end transactions are completed is just a few seconds or less. The invention operates equally well on robust private networks as on unpredictable Internet or wireless networks. The transaction is automatically completed following a temporary communication failure with the central site or following a temporary local controller failure. The invention can advantageously be used in embedded Internet products such as fixed or mobile Internet kiosks, transactional terminals, and Internet Appliances.
Owner:MUDALLA TECH INC THOITS LOVE HERSHBERGER & MCLEAN
Trusted transactional controller
InactiveUS20020174160A1Multiprogramming arrangementsBuying/selling/leasing transactionsElectronic controllerPrivate network
An electronic controller for conducting trusted lightweight e-commerce transactions. A trusted transactional cache and the associated transactional protocol allow e-commerce transactions to be committed to a remote server extremely quickly and with little network overhead. The end-to-end transactions are completed is just a few seconds or less. The invention operates equally well on robust private networks as on unpredictable Internet or wireless networks. The transaction is automatically completed following a temporary communication failure with the central site or following a temporary local controller failure. The invention can advantageously be used in embedded Internet products such as fixed or mobile Internet kiosks, transactional terminals, and Internet Appliances.
Owner:MUDALLA TECH INC THOITS LOVE HERSHBERGER & MCLEAN
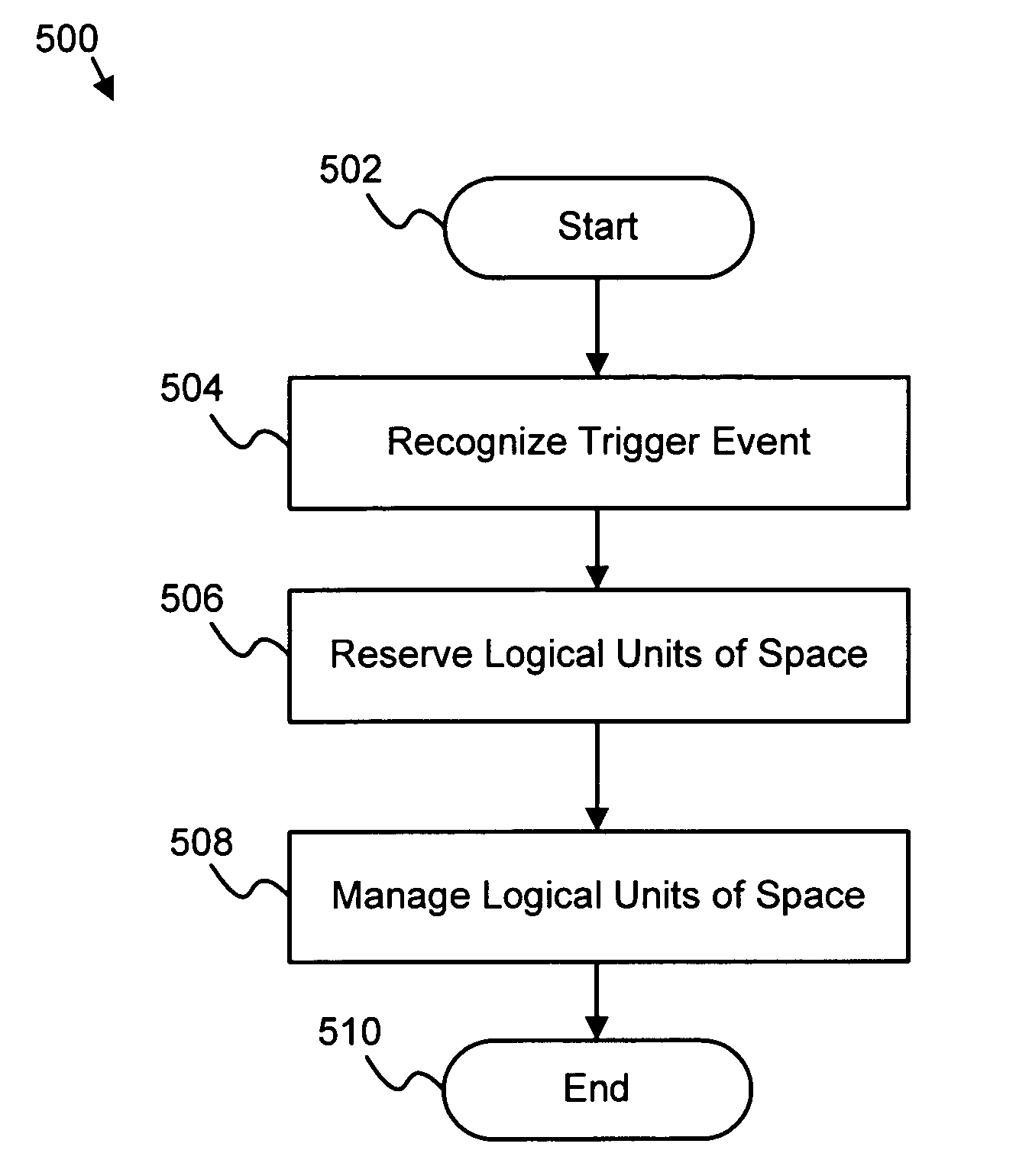
Apparatus, system, and method for managing storage space allocation
InactiveUS20060129778A1Multiple digital computer combinationsTransmissionStorage area networkFile system
An apparatus, system, and method are disclosed for managing storage space allocation. The apparatus includes a recognizing module, a reserving module, and a managing module. The recognizing module recognizes a trigger event at a client of the data storage system. The reserving module reserves logical units of space for data storage. The management module manages the logical units of space at the client. Such an arrangement provides for distributed management of storage space allocation within a storage area network (SAN). Facilitating client management of the logical units of space in this manner may reduce the number of required metadata transactions between the client and a metadata server and may increase performance of the SAN file system. Reducing metadata transactions effectively lowers network overhead, while increasing data throughput.
Owner:IBM CORP
Gang migration of virtual machines using cluster-wide deduplication
ActiveUS20150324236A1Prevent race conditionReduce network overheadInput/output to record carriersResource allocationInternet trafficEngineering
Gang migration refers to the simultaneous live migration of multiple Virtual Machines (VMs) from one set of physical machines to another in response to events such as load spikes and imminent failures. Gang migration generates a large volume of network traffic and can overload the core network links and switches in a datacenter. In this paper, we present an approach to reduce the network overhead of gang migration using global deduplication (GMGD). GMGD identifies and eliminates the retransmission of duplicate memory pages among VMs running on multiple physical machines in the cluster. The design, implementation and evaluation of a GMGD prototype is described using QEMU / KVM VMs. Evaluations on a 30-node Gigabit Ethernet cluster having 10 GigE core links shows that GMGD can reduce the network traffic on core links by up to 65% and the total migration time of VMs by up to 42% when compared to the default migration technique in QEMU / KVM. Furthermore, GMGD has a smaller adverse performance impact on network-bound applications.
Owner:THE RES FOUND OF STATE UNIV OF NEW YORK
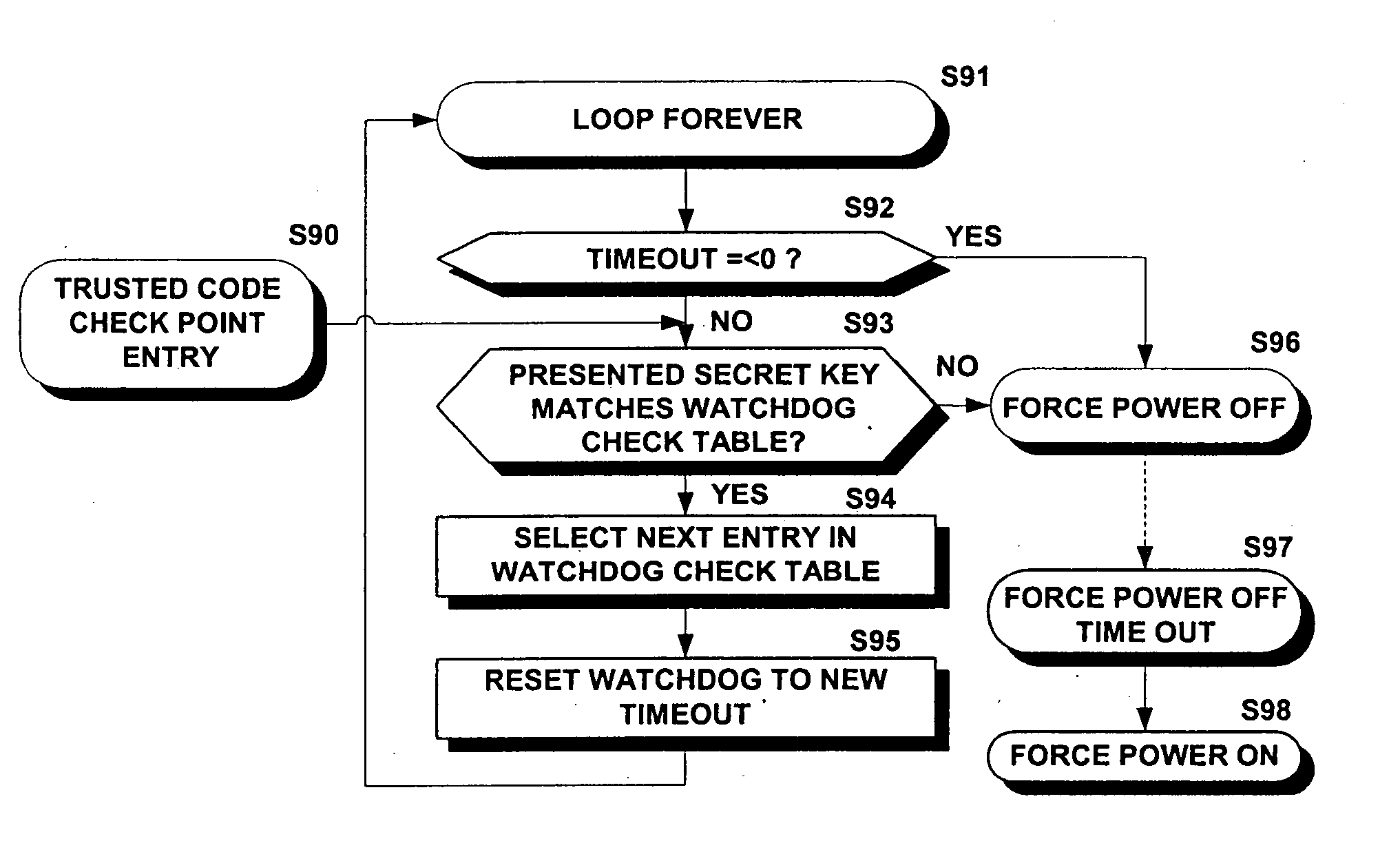
Trusted watchdog method and apparatus for securing program execution
InactiveUS20050097342A1Unauthorized memory use protectionHardware monitoringElectronic controllerPrivate network
An electronic controller for conducting trusted lightweight e-commerce transactions. A trusted transactional cache and the associated transactional protocol allow e-commerce transactions to be committed to a remote server extremely quickly and with little network overhead. The end-to-end transactions are completed is just a few seconds or less. The invention operates equally well on robust private networks as on unpredictable Internet or wireless networks. The transaction is automatically completed following a temporary communication failure with the central site or following a temporary local controller failure. The invention can advantageously be used in embedded Internet products such as fixed or mobile Internet kiosks, transactional terminals, and Internet Appliances.
Owner:CYBERVIEW TECH
Mechanism and system for transmitting vehicle emergency message based on DSRC
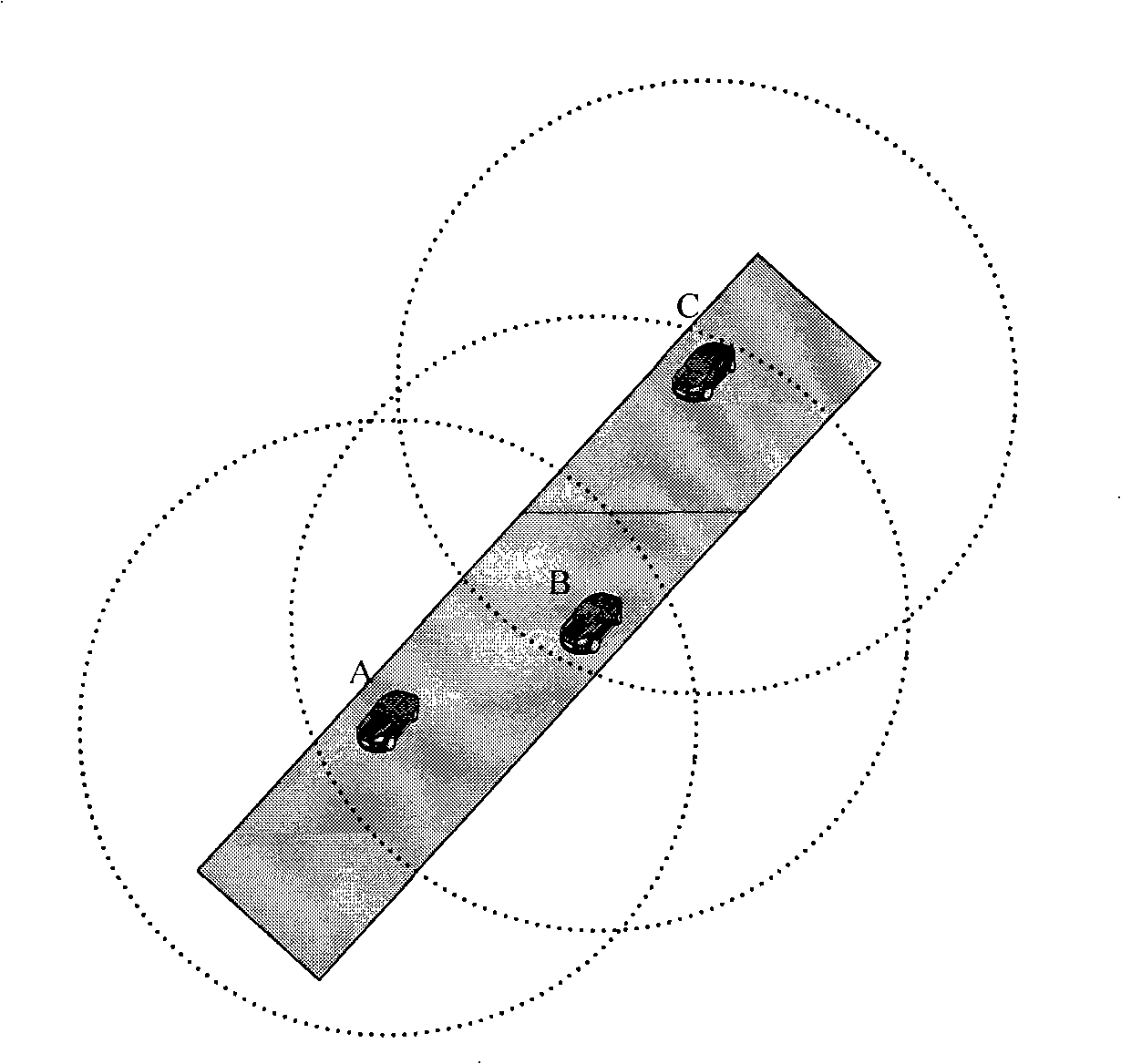
InactiveCN101350134AImprove securityImprove efficiencyAnti-collision systemsData acquisitionNetwork overhead
The invention relates to a vehicle urgent information sending mechanism and a system based on a DSRC, when a vehicle encounters a unusual condition during driving, a urgent information is automatically produced, the urgent information is sent in preference to other information. Vehicles which receive the urgent information determine whether the urgent information is transmitted at once according to respective retransmission distance threshold. The vehicle urgent information sending mechanism and the system guarantee emergency message to be rapidly and steadily sent after a vehicle has an accident. Corresponding retransmission distance thresholds are determined according to different existing environment, network spending is reduced, and the urgent information is further guaranteed to be rapidly sent simultaneously. The whole system of the invention substantially comprises a data vehicle positioning module, a data acquisition module, a memory, a processor and a data sending and receiving module.
Owner:TONGJI UNIV
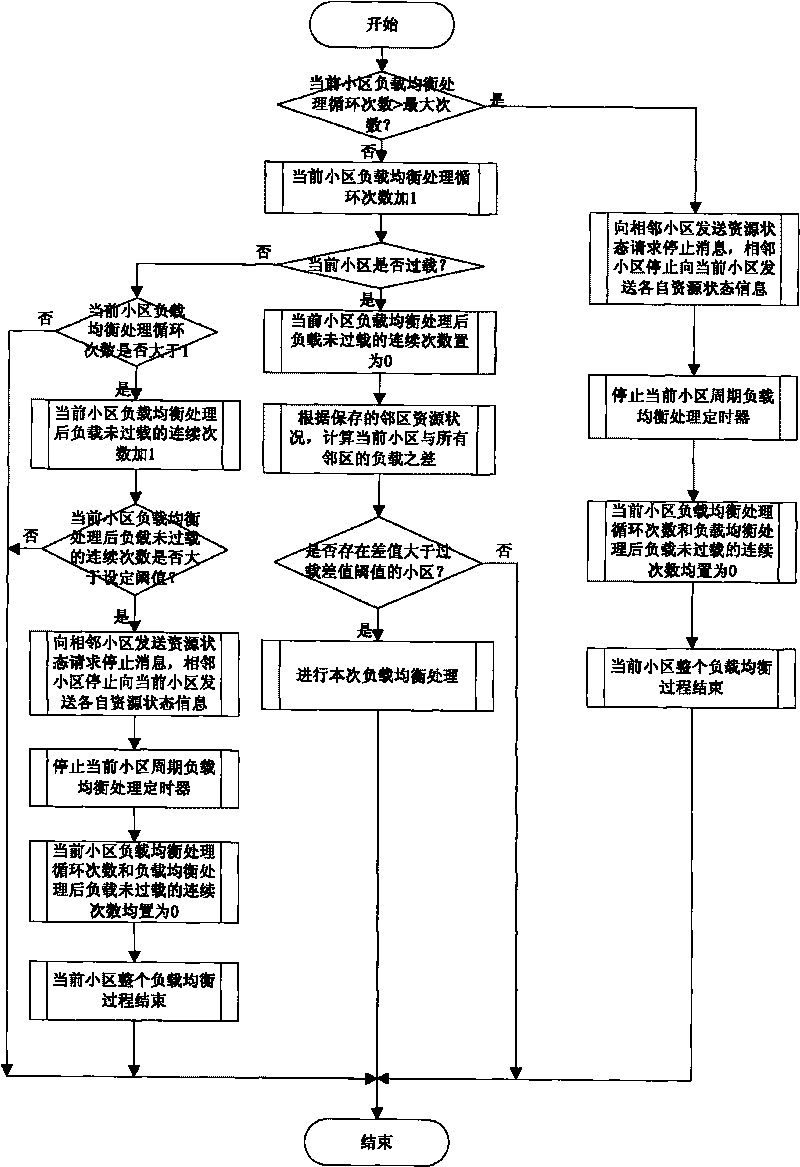
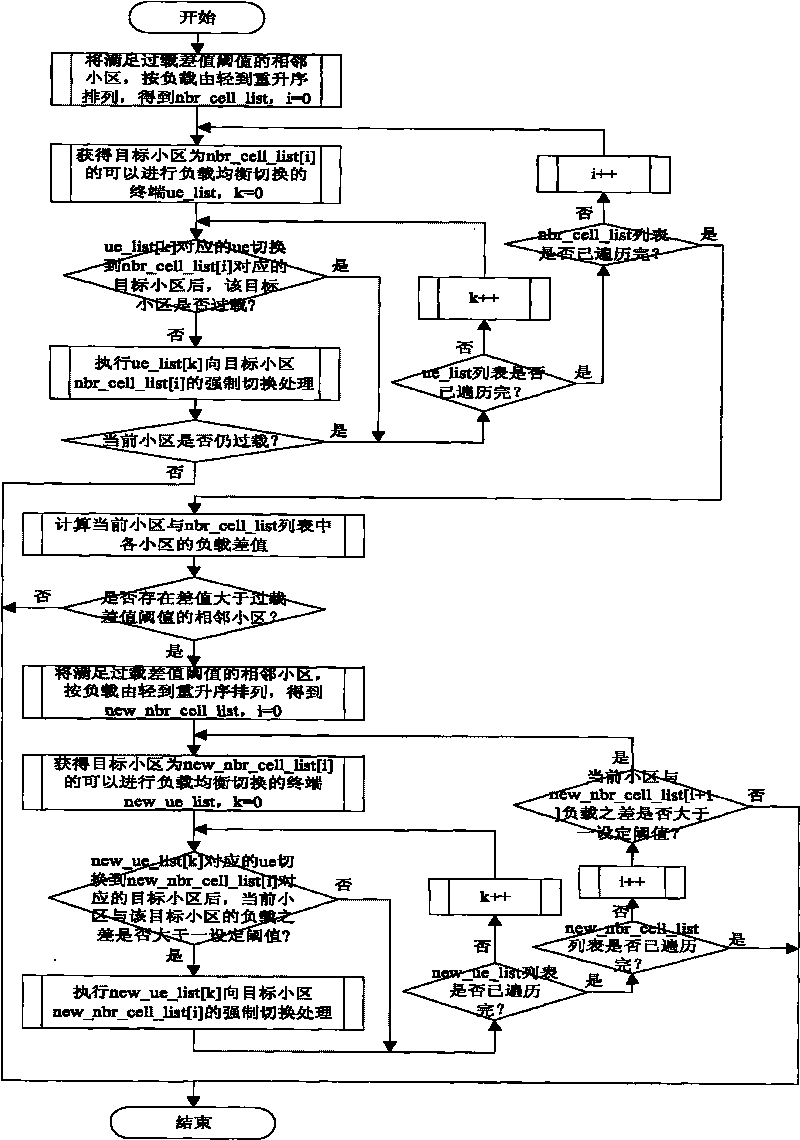
Method for balancing inter-cell load in LTE mobile communication network
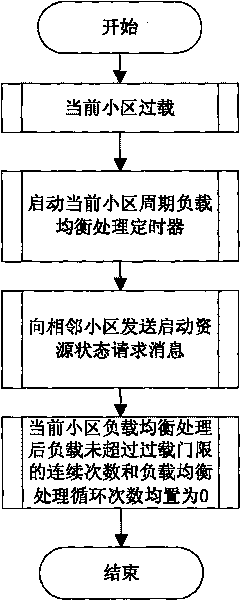
ActiveCN101742565AIncrease profitReduce overheadNetwork traffic/resource managementCurrent cellEngineering
The invention provides a method for balancing inter-cell load in an LTE mobile communication network. The invention reduces the range of seeking a terminal which meets load balancing switching by marking the terminal which meets the requirement of load balancing switching by utilizing a balancing event measurement report, thereby shortening the load balancing execution time; and in addition, the invention better realizes the inter-cell load balancing through periodic load balancing processing and two-step load balancing switching processing, prevents new load unbalancing generated by the load balancing process, enhances the load balancing convergence rate, effectively prevents the ping-pong effect, effectively reduces the network overhead because neighbour cells can report respective resource states only after a current cell is overload, enhances the utility ratio of wireless resources and reduces the dropped call rate.
Owner:WUHAN POST & TELECOMM RES INST CO LTD +1
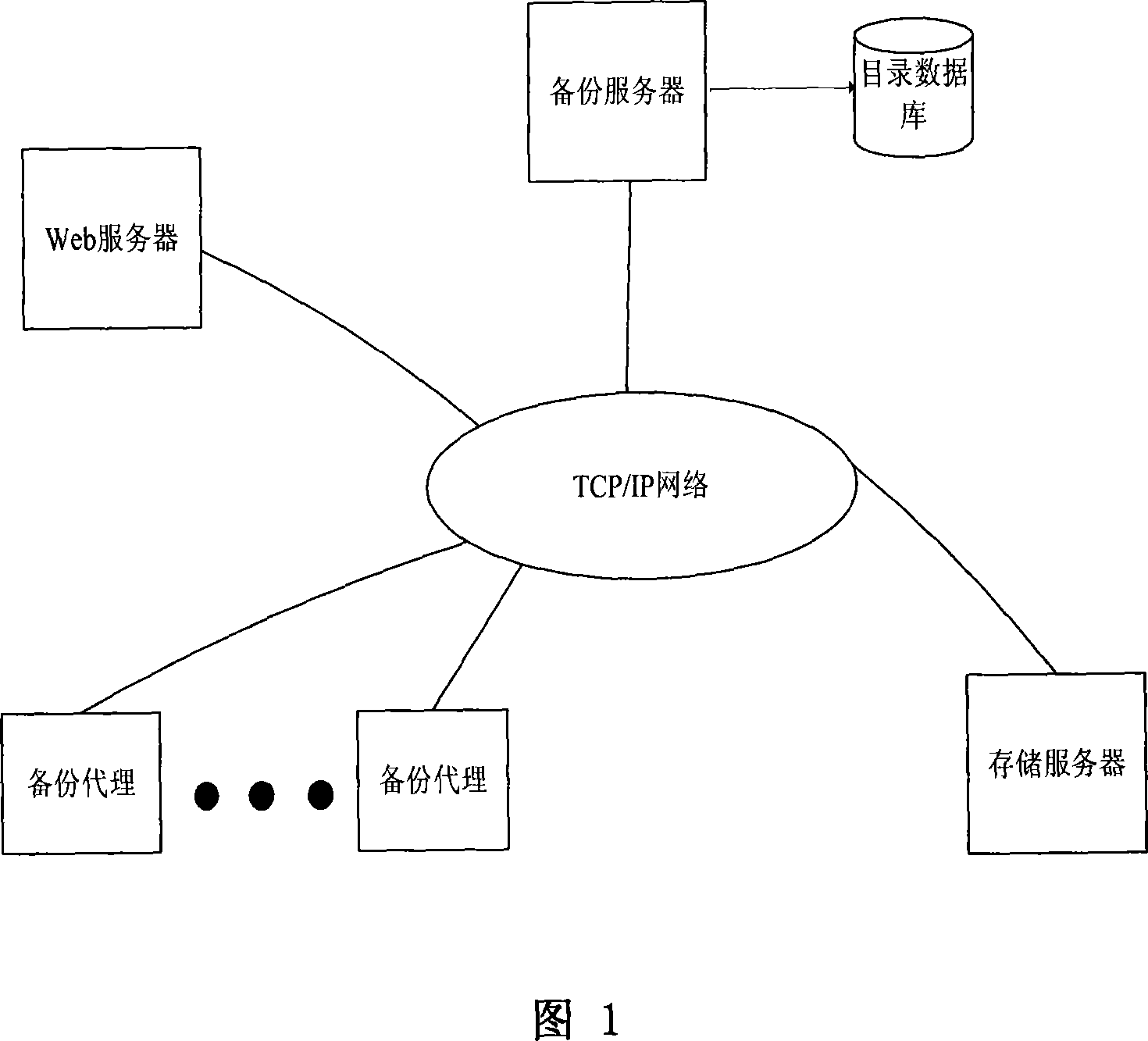
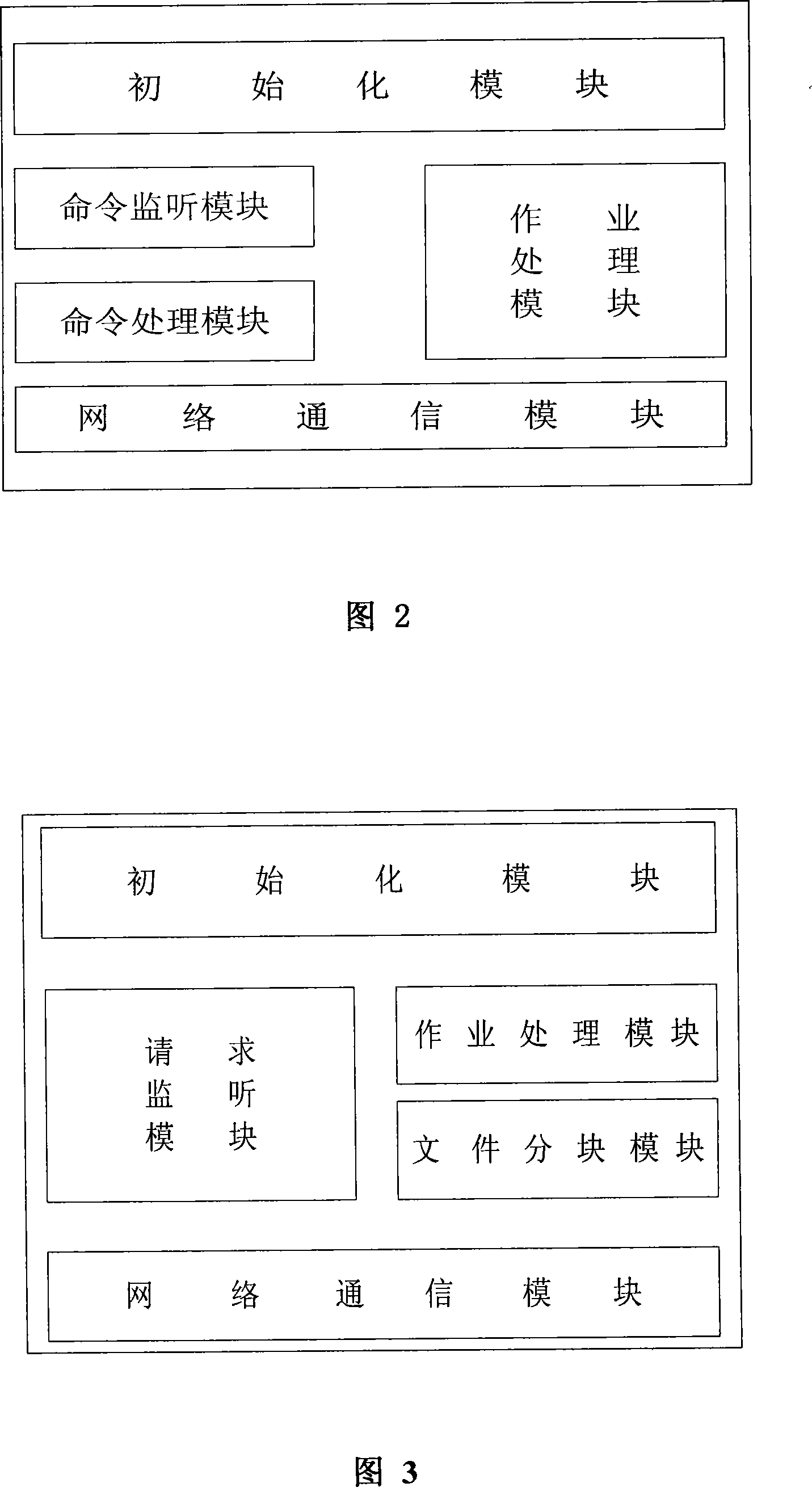
Data stand-by system based on finger print
InactiveCN101183323AReduce computational overheadHas modification stabilityMultiprogramming arrangementsTransmissionComplete dataApplication server
The invention relates to a data backup system based on fingerprints, belonging to the technical field of computer storage backup, which aims at reducing management, storage and network overhead of data backup and improving backup performance. The invention comprises a backup server, a backup agent, a storage server and a Web server which complete data backup and recovery through mutual network communication. The invention is characterized in that redundant data of backup files is recognized with the file segmentation technology based on anchors, thus the invention has the advantages that the modification stability is good and computation cost is low; data segmentations with fingerprints as the index are stored on a plurality of disk arrays of the storage server so as to eliminate backup of redundant data and save disk storage space; the data segmentations are not erased once stored and can be continuously appended on the disk so as to eliminate disk storage fragments; since the effective backup buffer strategy is adopted, the invention also has the advantages of reduced network overhead of backup, increased data backup speed and lowered backup influence to application servers.
Owner:HUAZHONG UNIV OF SCI & TECH
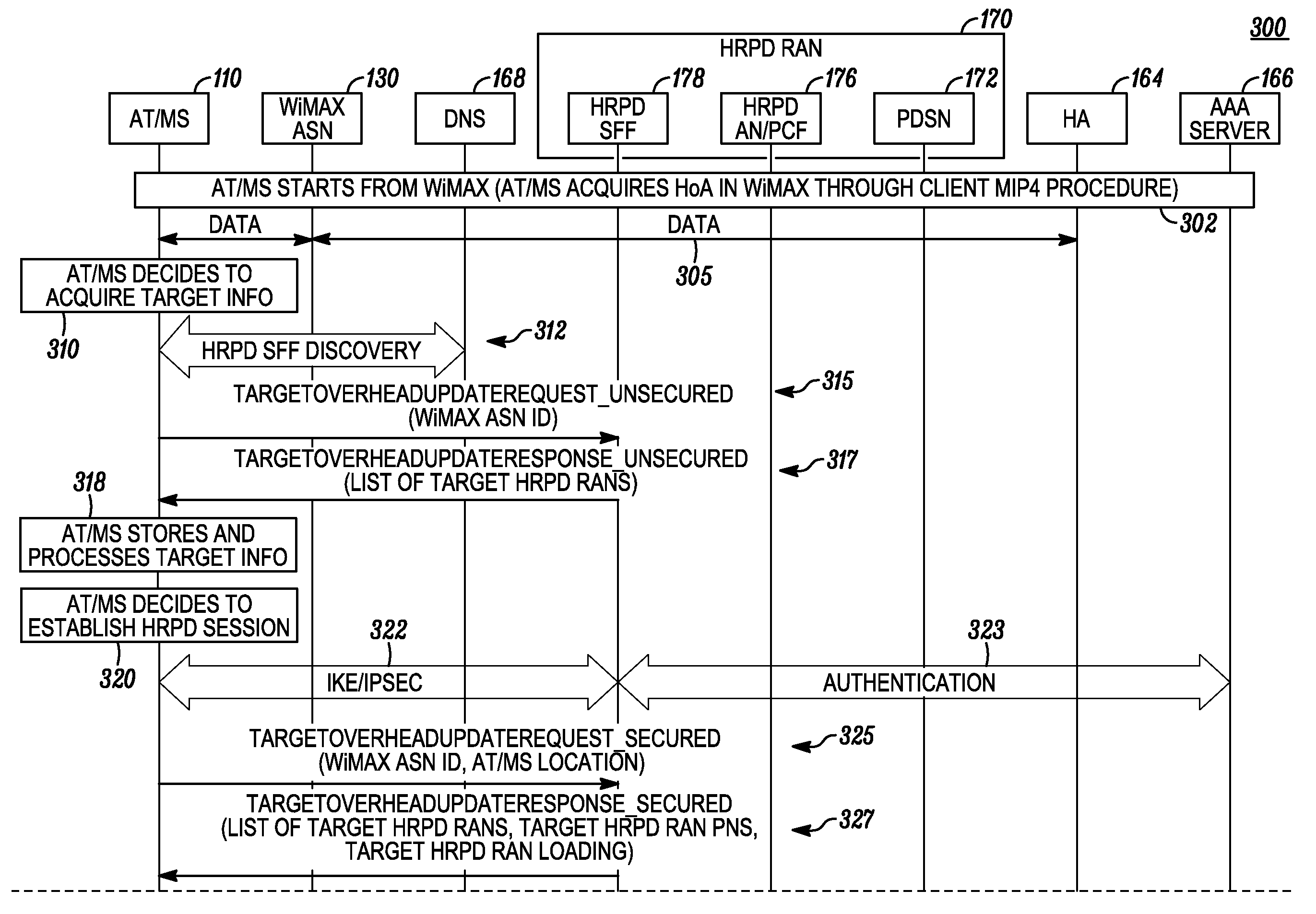
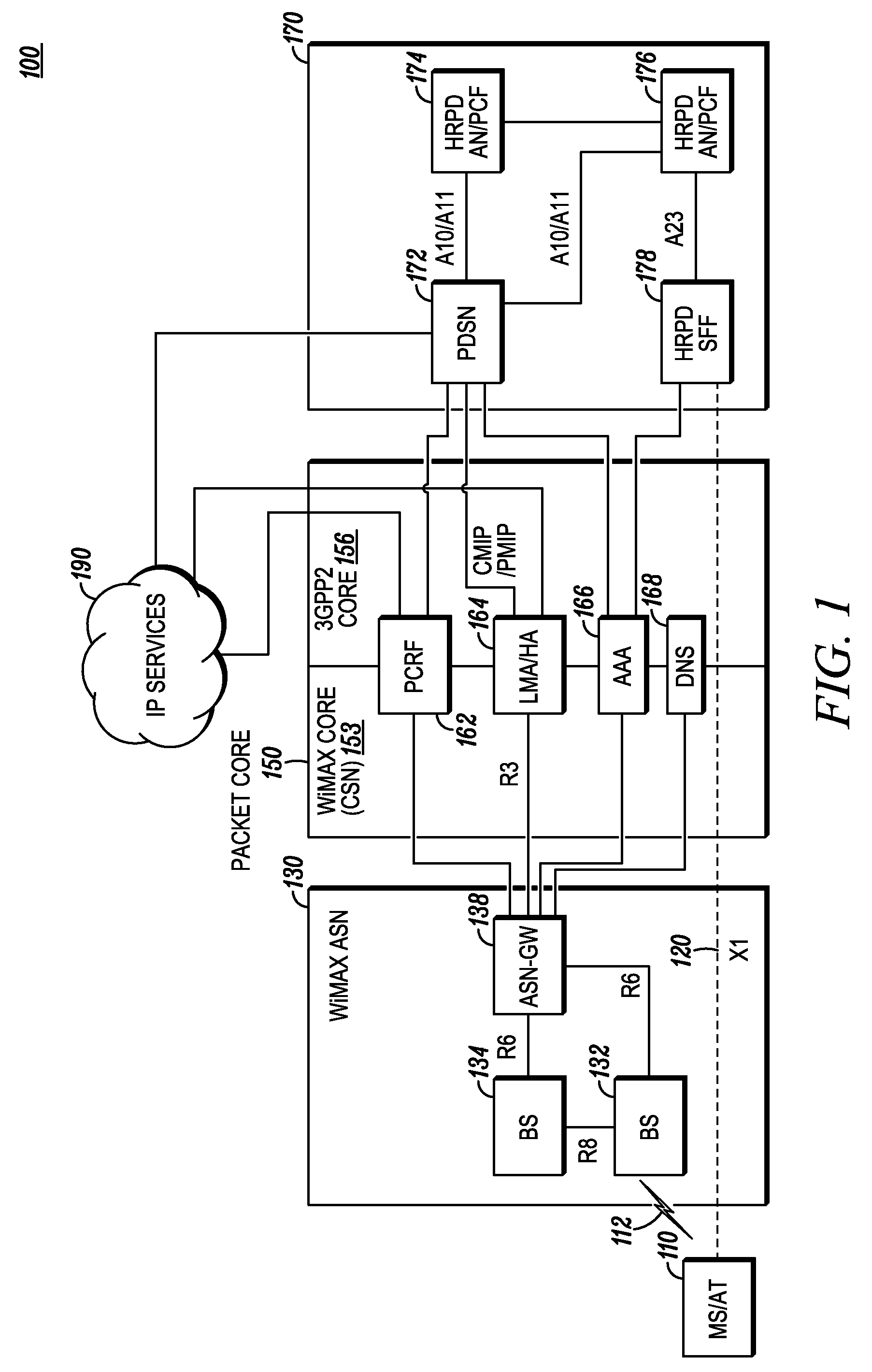
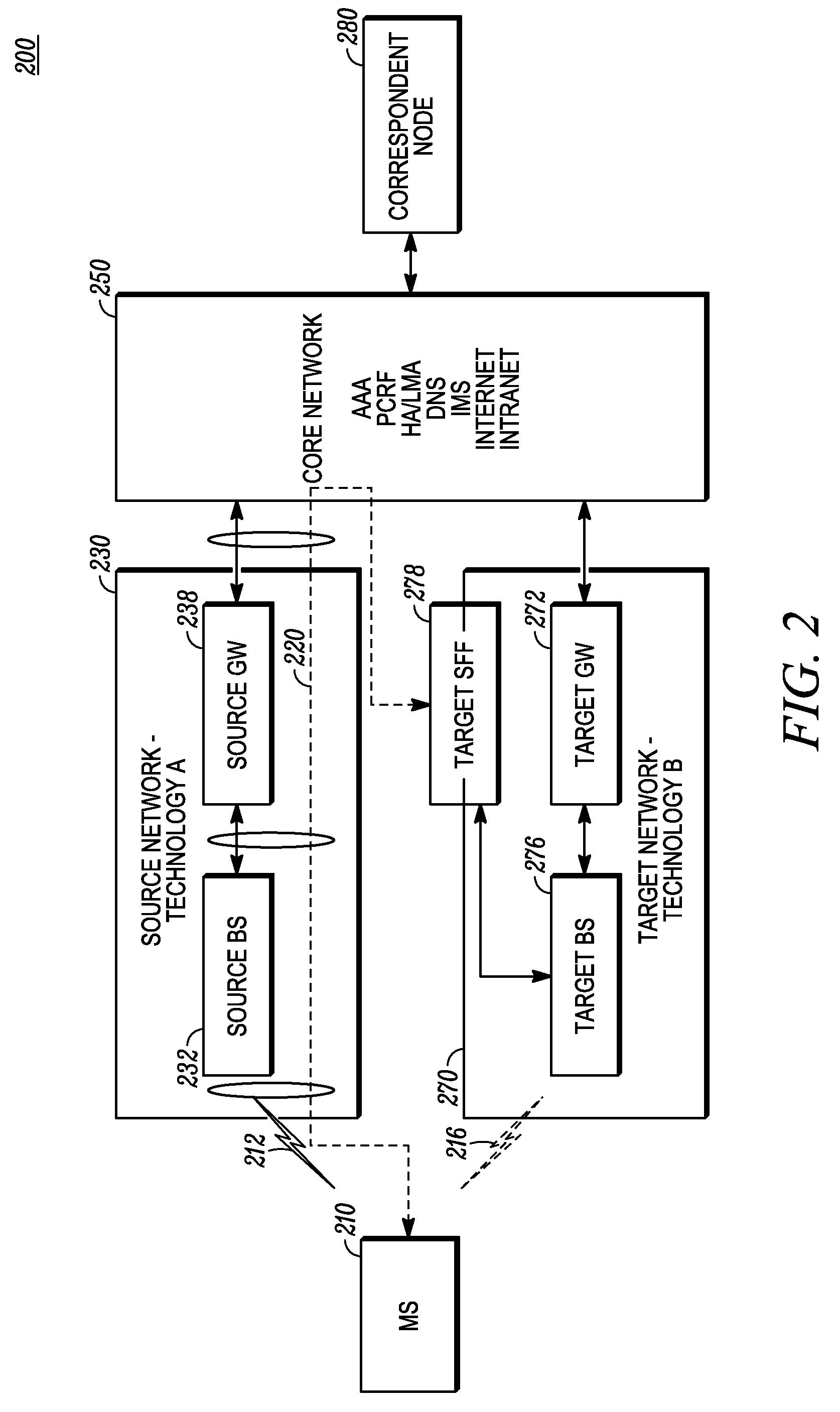
Method for Hand-Over In A Heterogeneous Wireless Network
In a heterogeneous network handover situation, a mobile terminal (110) is initially in wireless communication with a source network (130). The mobile terminal transmits, to a target network (170), a target network overhead update request message (315, 325) containing location information of the mobile terminal and receives, from the target network, a target network overhead update response message (317, 327) containing overhead message information for the target network and optionally other information such as handover willingness, network loading, and QoS availability. The update request and update response messages can be tunneled from the mobile terminal through the source network and the core network to the target network, rather than the messages being sent over-the-air from the target network to the mobile terminal.
Owner:GOOGLE TECH HLDG LLC
High availability via data services
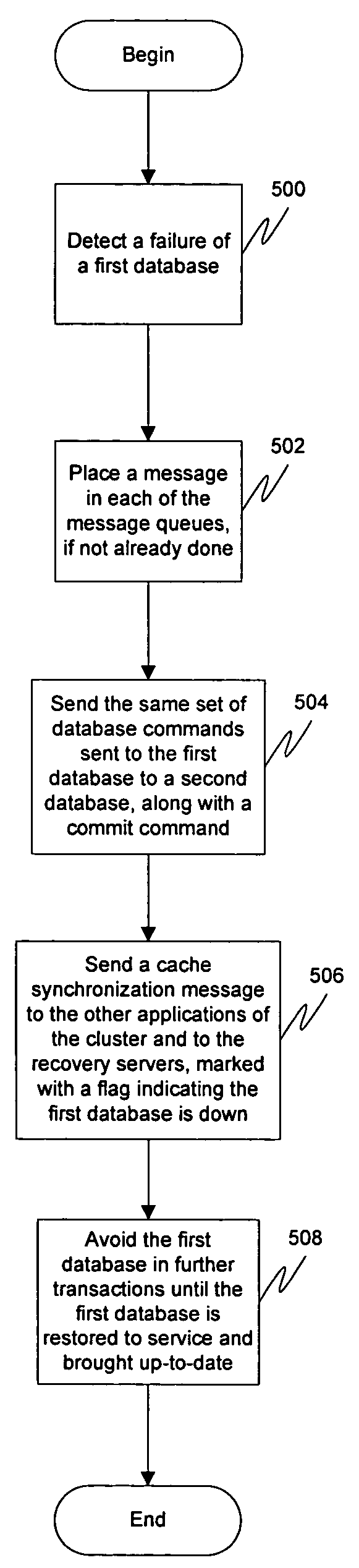
ActiveUS7290015B1Little networkComprehensive performance is smallData processing applicationsError detection/correctionMessage queueApplication server
Application-level replication, the synchronization of data updates within a cluster of application servers, may be provided by having application servers themselves synchronize all updates to multiple redundant databases, precluding the need for database-level replication. This may be accomplished by first sending a set of database modifications requested by the transaction to a first database. Then a message may be placed in one or more message queues, the message indicating the objects inserted, updated, or deleted in the transaction. Then a commit command may be sent to the first database. The set of database modifications and a commit command may then be sent to a second database. This allows for transparent synchronization of the databases and quick recovery from a database failure, while imposing little performance or network overhead.
Owner:PROGRESS SOFTWARE
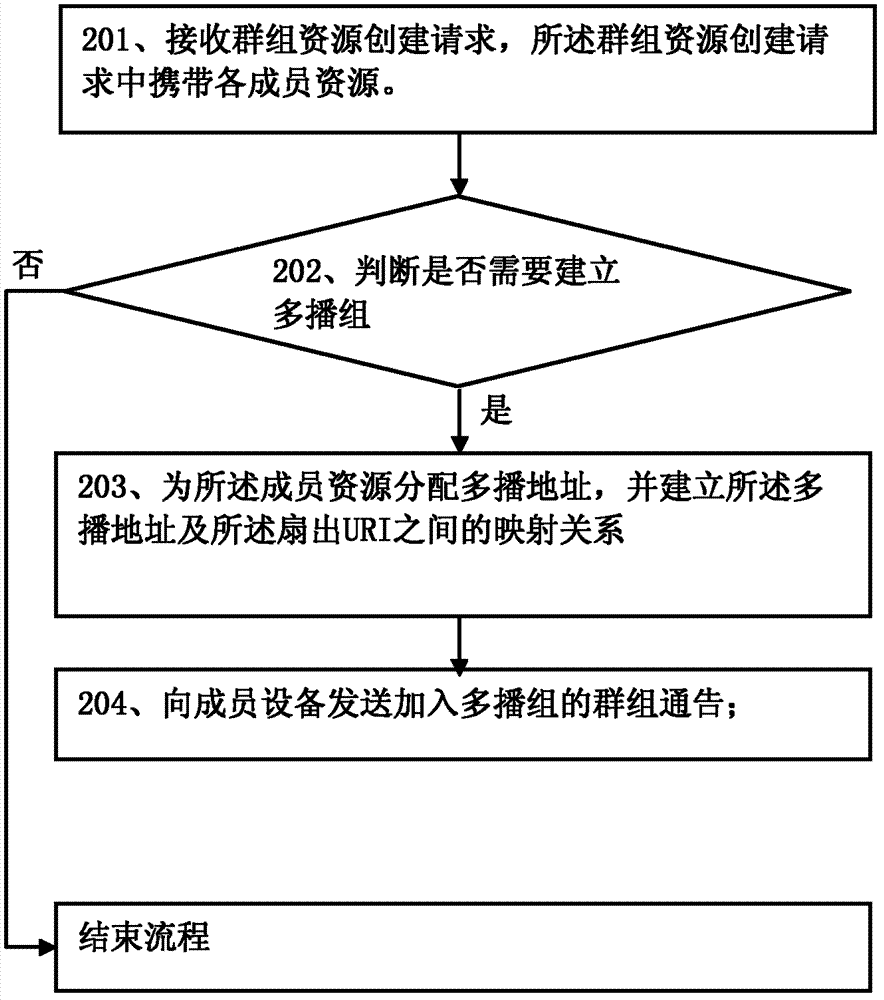
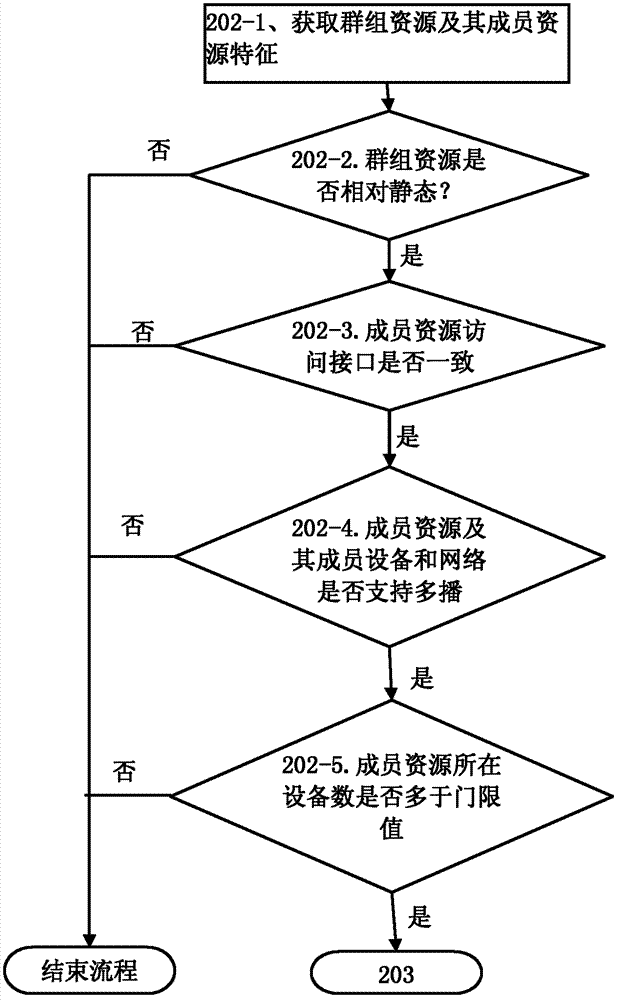
Access method of member resources, group server and member devices
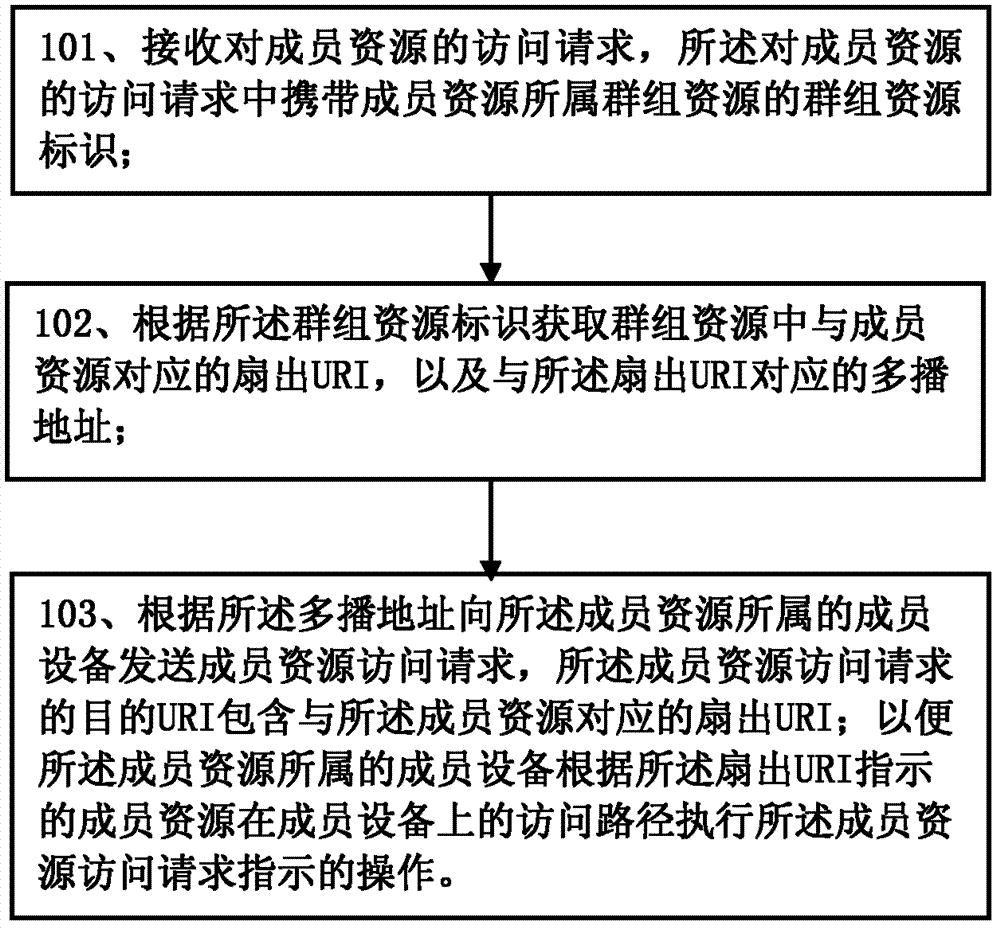
ActiveCN103200209AReduce overheadSpecial service provision for substationBroadcast service distributionAccess methodMulticast address
The invention provides an access method of member resources, a group server and member devices. Through a built mapping relation of a multicast address and a fan-out uniform resource identifier (URI) in group resources, access requests of the member resources can be sent to the member devices where the member resources of the group resources are located in a multicast mode, and the access requests of the member resources comprise the fan-out URI, so that the member devices where the member resources are located carry out operation indicated by the member access requests according to an access path of the member resources on the member devices, wherein the access path is indicated by the fan-out URI. Therefore, the group server does not need to singly cast the access requests to the member devices, and cost of a network is saved.
Owner:HUAWEI CLOUD COMPUTING TECH CO LTD
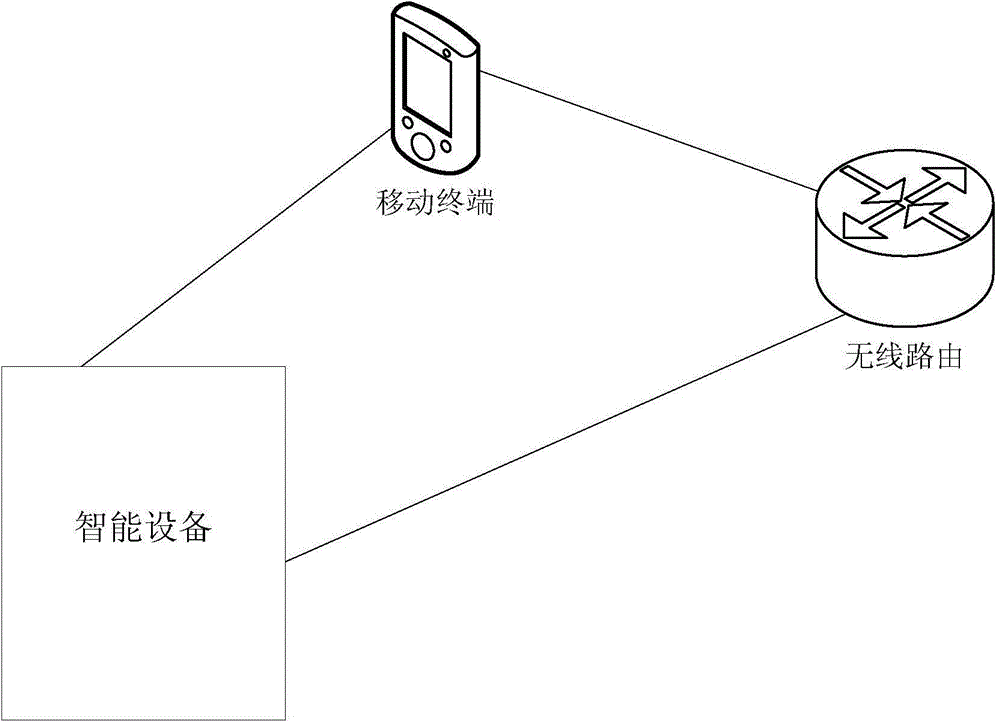
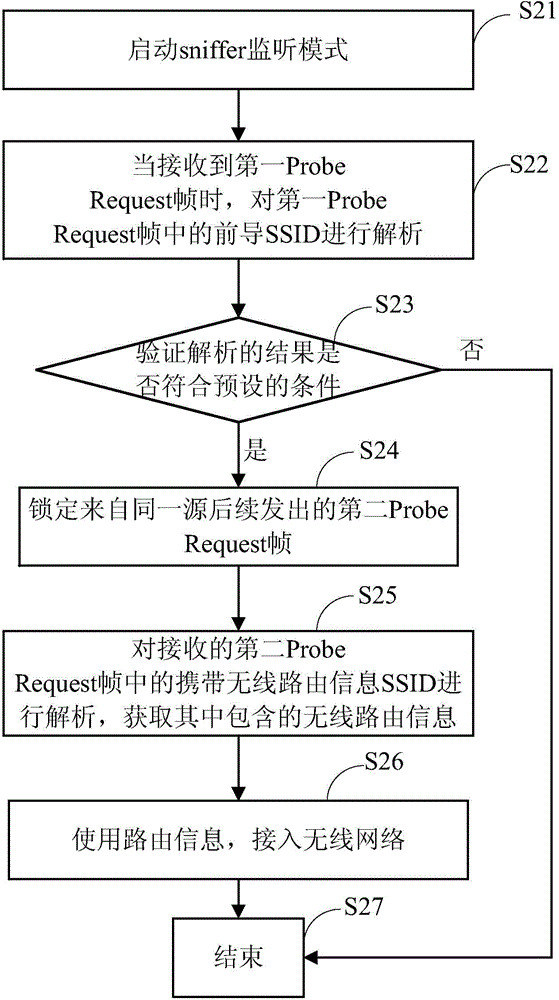
Network access method for intelligent device, intelligent device and mobile terminal
ActiveCN104618900AEasy accessWide applicabilityAssess restrictionSecurity arrangementWireless routerAccess method
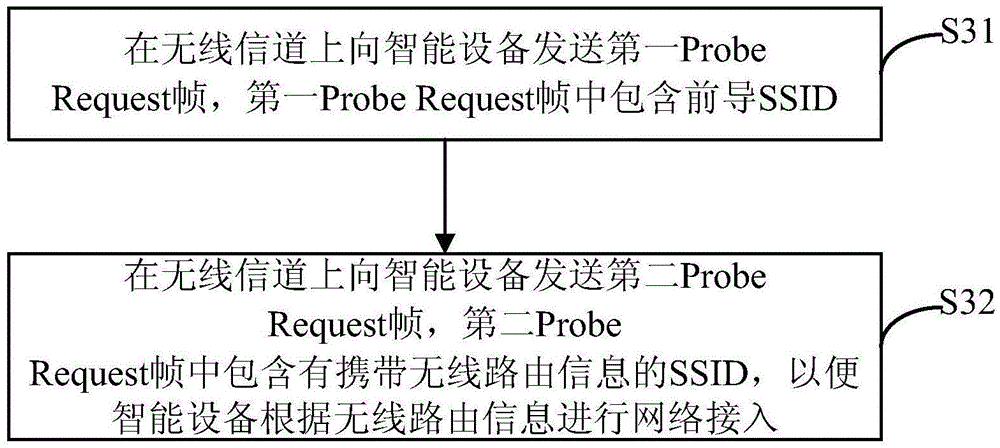
The invention provides a network access method for an intelligent device, the intelligent device and a mobile terminal. The network access method for the intelligent device comprises the steps that after a sniffer monitoring mode of the intelligent device starts, a pioneer service set identifier (SSID) in a first Probe Request frame is analyzed when the first Probe Request frame is received, when the analysis result meets preset conditions, a second Probe Request frame which is afterwards sent out by the same source is locked, an SSID, with wireless router information, in the received second Probe Request frame is analyzed, the wireless router information contained in the second Probe Request frame is obtained, and the intelligent device has access to a wireless network according to the wireless router information. According to the network access method for the intelligent device, the intelligent device which is in the sniffer monitoring mode can obtain the wireless router information rapidly, conveniently and safely so as to have access to the network, the network access method is wide in applicability, the quantity of information which can be carried in a single communication process is large, and the network expense is saved.
Owner:QINGDAO HAIER INTELLIGENT HOME TECH CO LTD
Model parameter training method and device, server and storage medium
ActiveCN108491928AReduce overheadImprove operational efficiencyNeural architecturesAttenuation coefficientAlgorithm
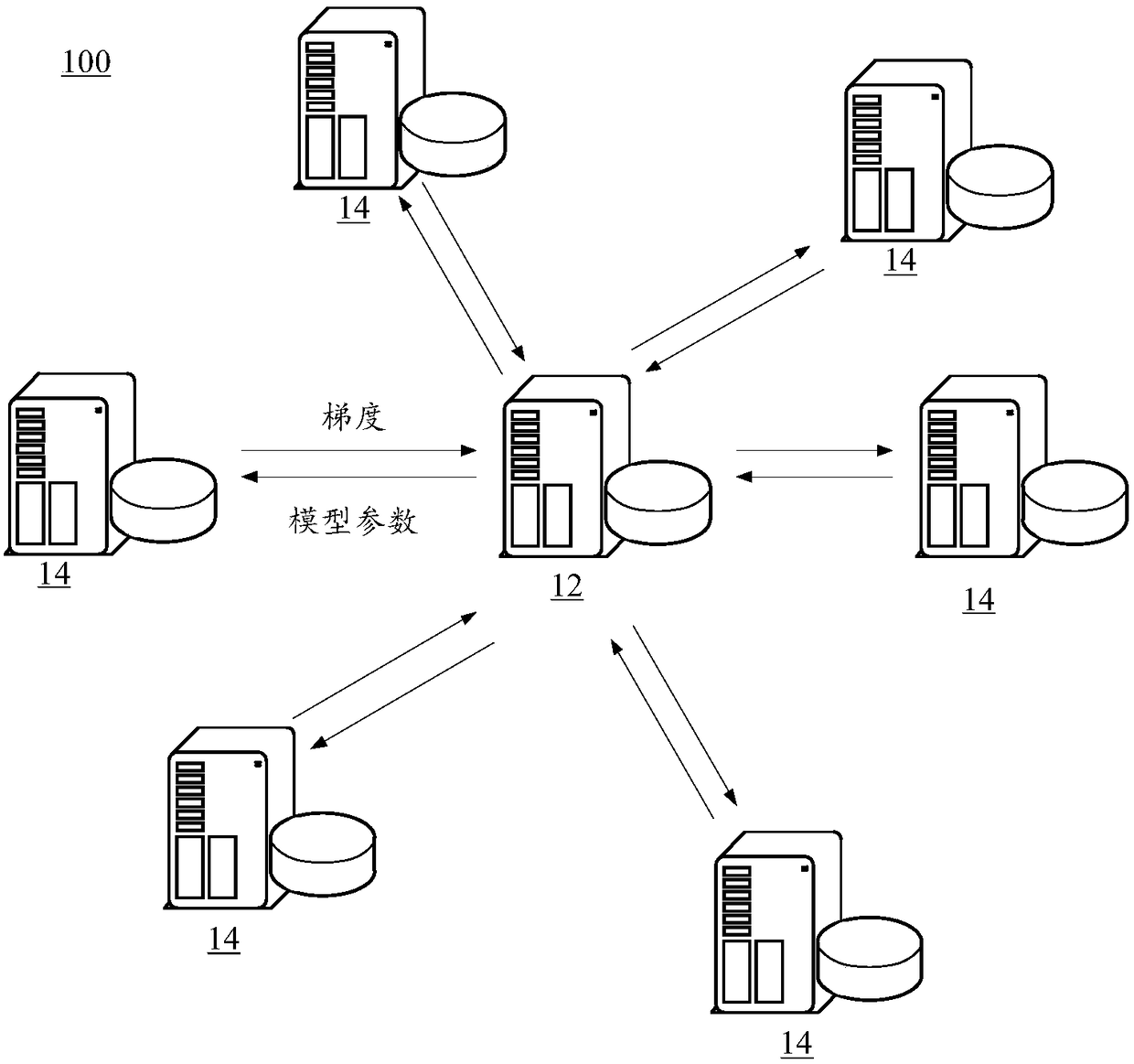
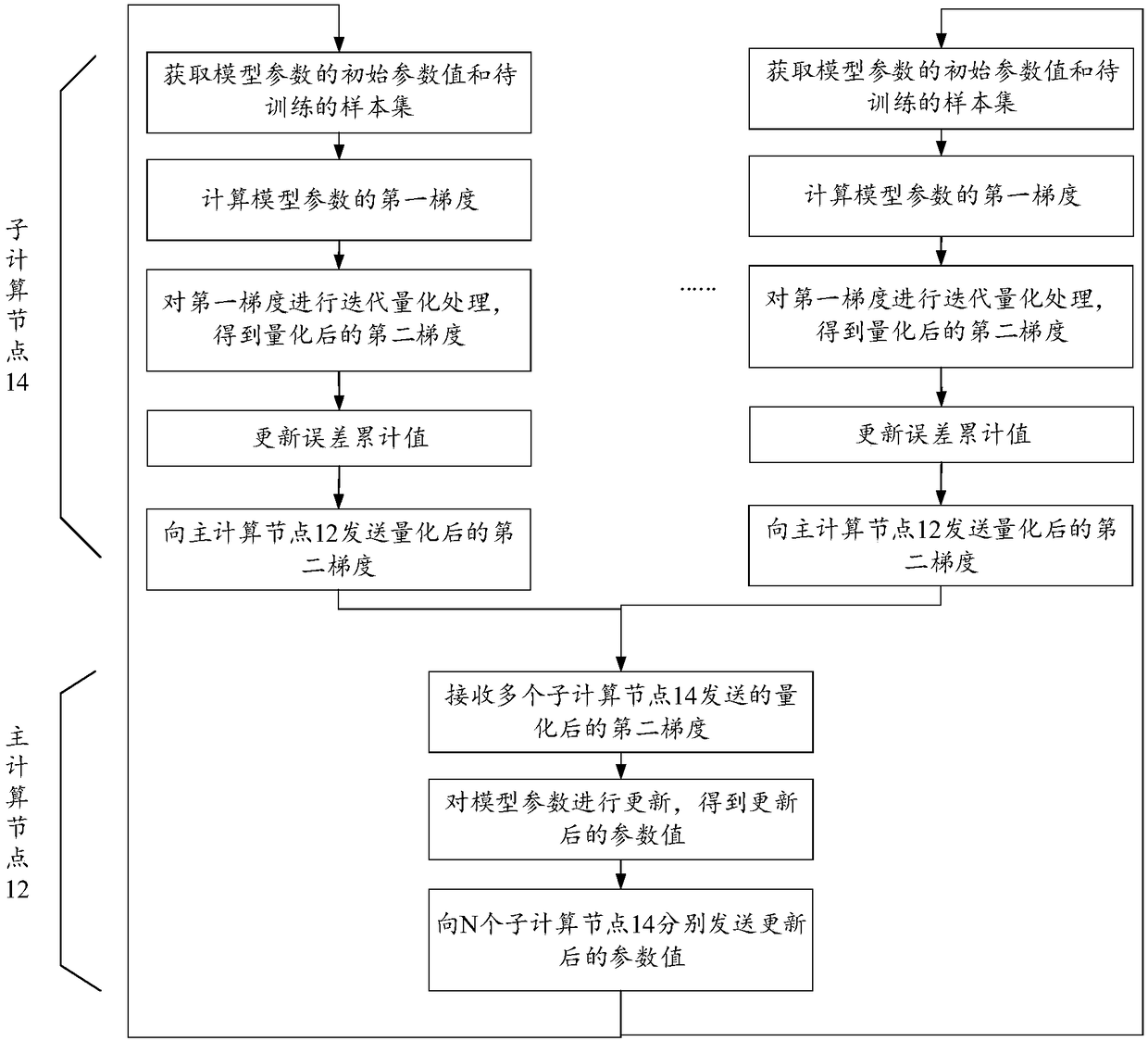
The invention discloses a model parameter training method and device, a server and a storage medium, which belongs to the technical field of information. The method comprises the steps that an initialparameter value and a sample set of a model parameter of a target model are acquired; the first gradient of the model parameter is calculated according to the initial parameter value and the sample set; iterative quantization processing is carried out on the first gradient to acquire a quantized second gradient, wherein the iterative quantization processing is quantization processing carried outbased on an error cumulative value corresponding to the t-1-th iteration round in the t-th iteration round, and the error cumulative value is a quantization error cumulative value calculated based ona preset time attenuation coefficient; and the quantized second gradient is transmitted to a primary computing node, wherein the quantized second gradient is used to instruct the primary computing node to update the initial parameter value according to the quantized second gradient to acquire an updated parameter value. According to the embodiment of the invention, a quantization error correctionmethod is used to quantize and compress the first gradient of the model parameter, which reduces the communication cost and network overhead of gradient transmission.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Apparatus and method for reducing power consumption in ad-hoc network
Owner:SAMSUNG ELECTRONICS CO LTD
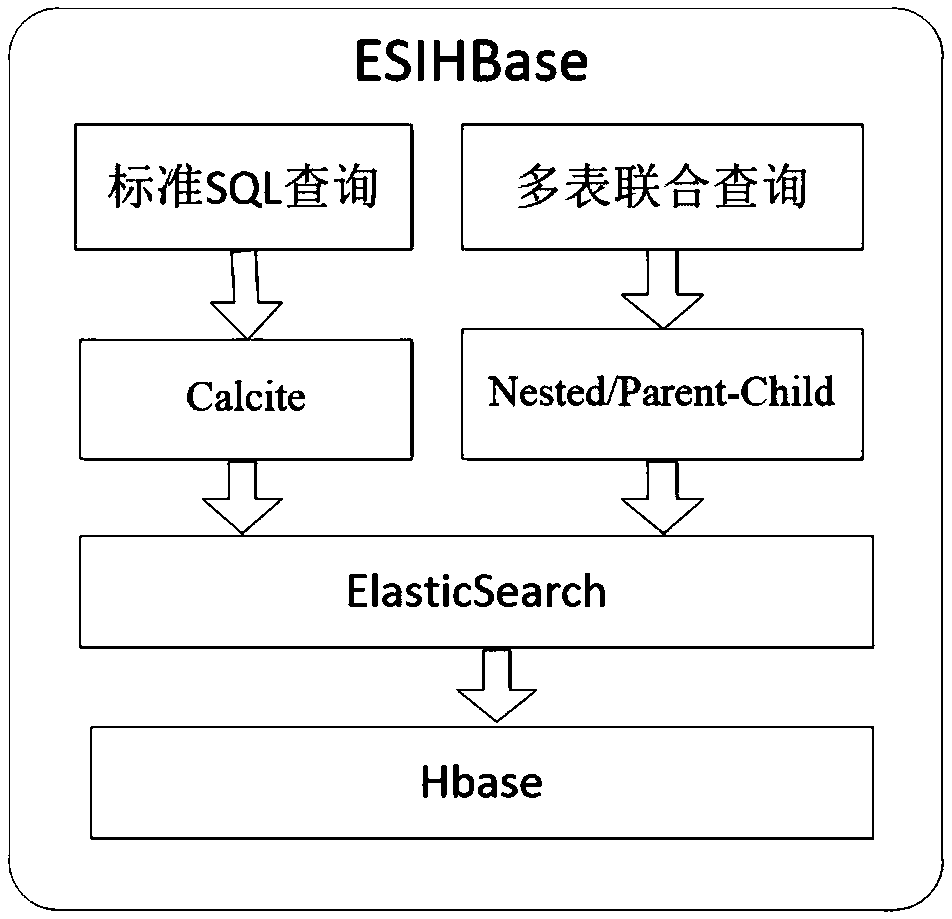
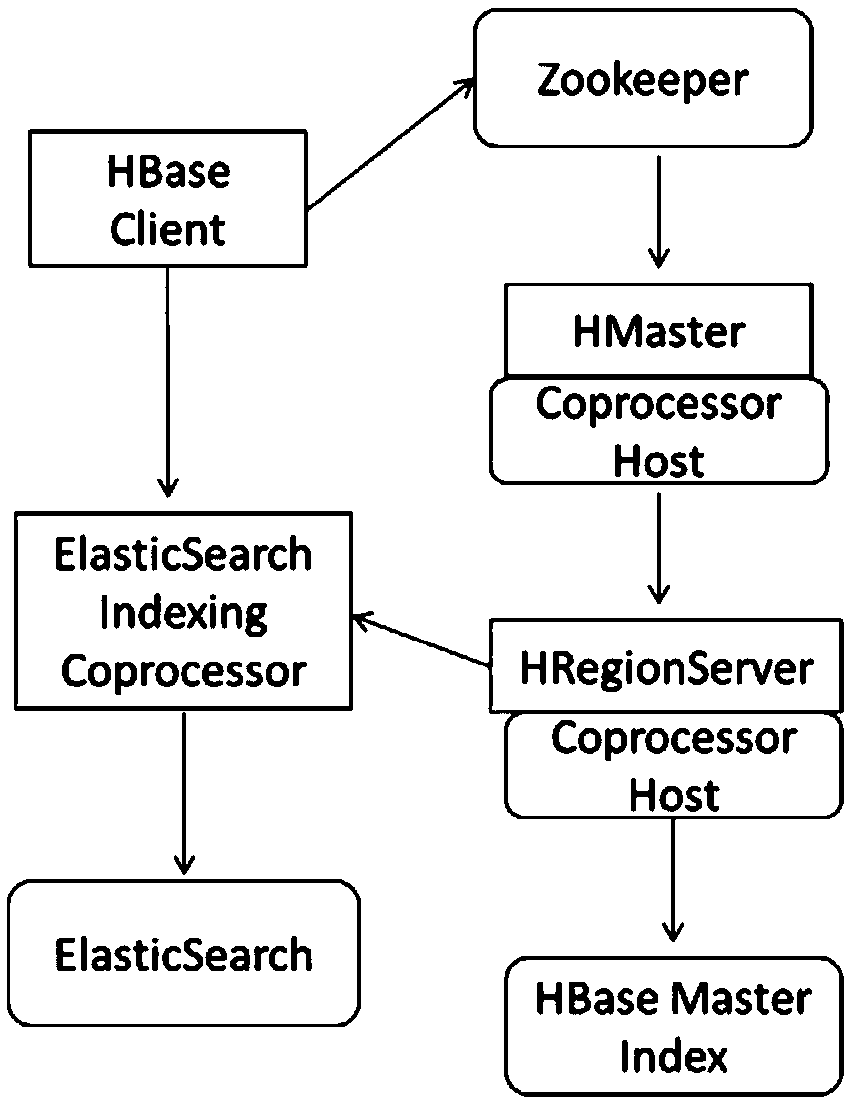
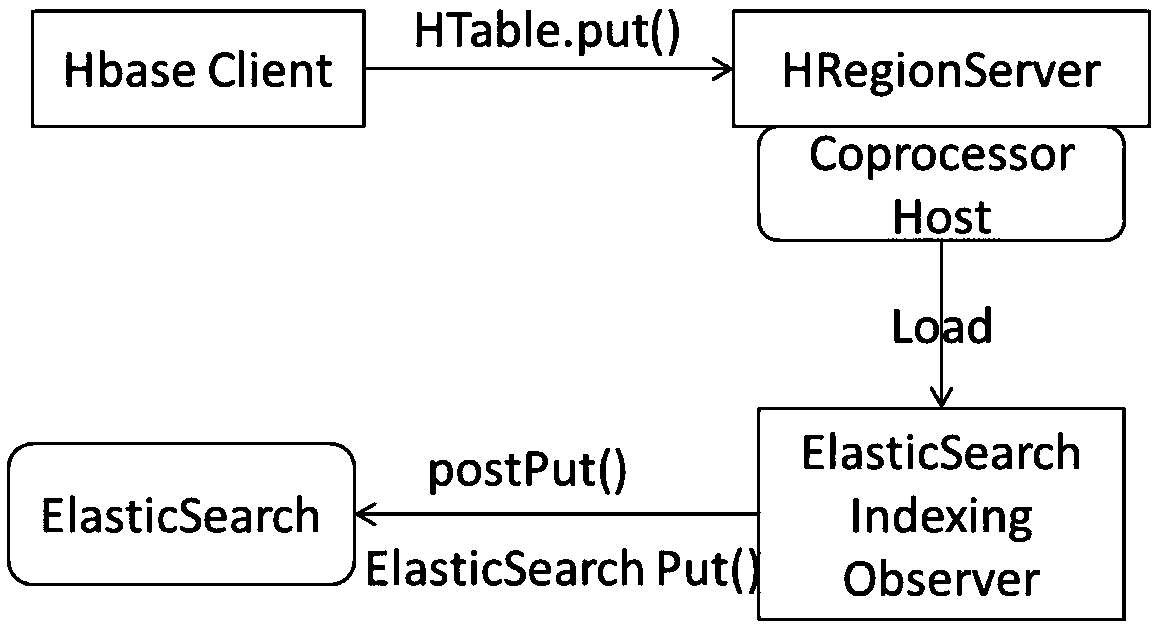
A HBase secondary index system and method based on Elastcisearch
The invention discloses a HBase secondary index system based on Elastcisearch. The system comprises a data table design module, a key-value matching module, a row key return module, a multi-table joint query module, a standard SQL query module and an interface module. It includes designing secondary index based on distributed column database, establishing index system for column value of distributed column database by secondary index technology, and creating index table automatically and efficiently by co-processor technology, which can break the defect of HBase lacking column family index. Supports the dynamic increase or decrease of index, reduces the network overhead caused by random query, and improves the scalability and practicability of secondary index. Aiming at the problem of weakSQL operation ability of distributed data storage, SQL parser and executor are designed and parallel SQL query engine is constructed. SQL operation is transformed into Region scan operation by usingdistributed column database API, coprocessor and filter, and efficient parallel SQL query is realized by making full use of two-level index mechanism.
Owner:THE 28TH RES INST OF CHINA ELECTRONICS TECH GROUP CORP
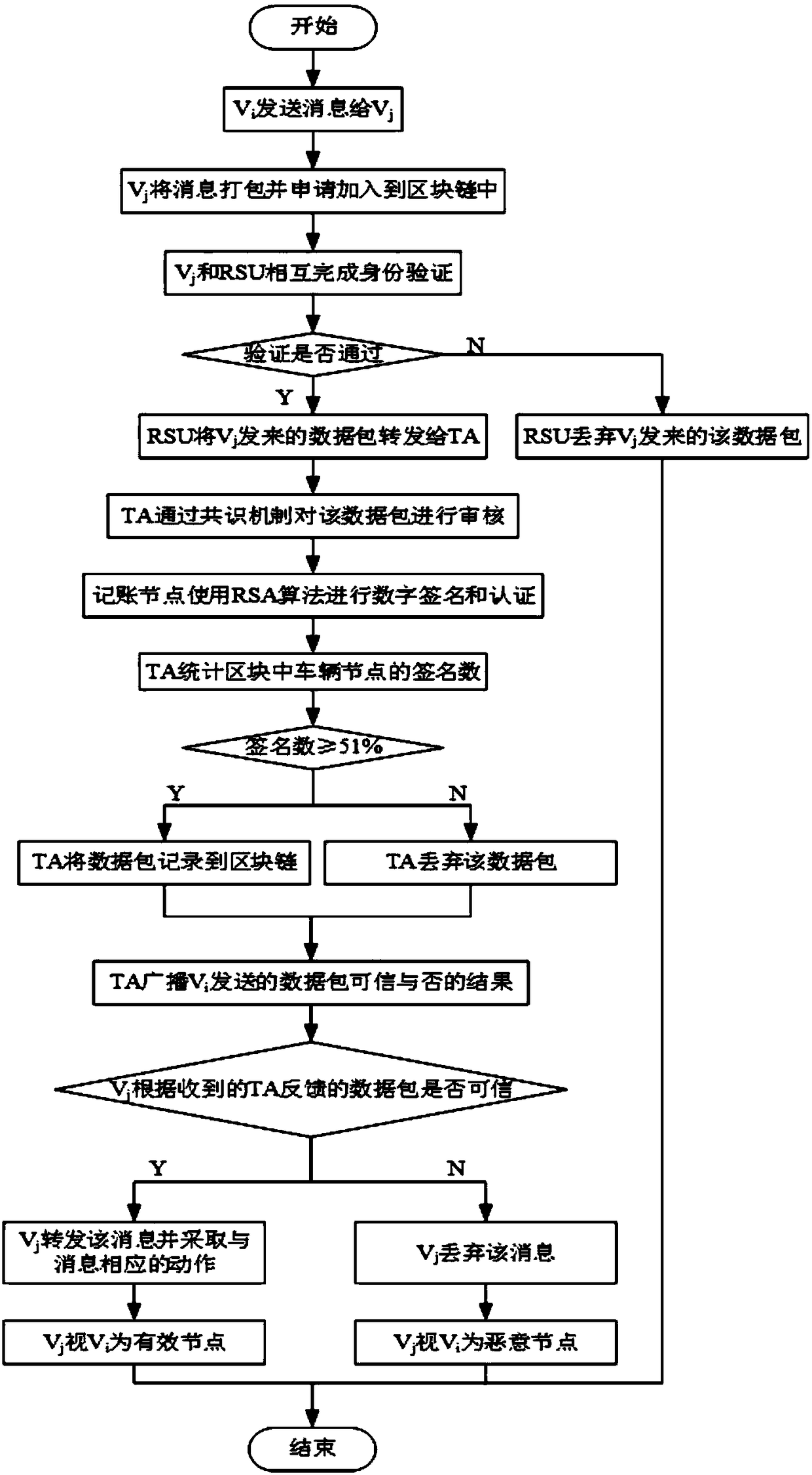
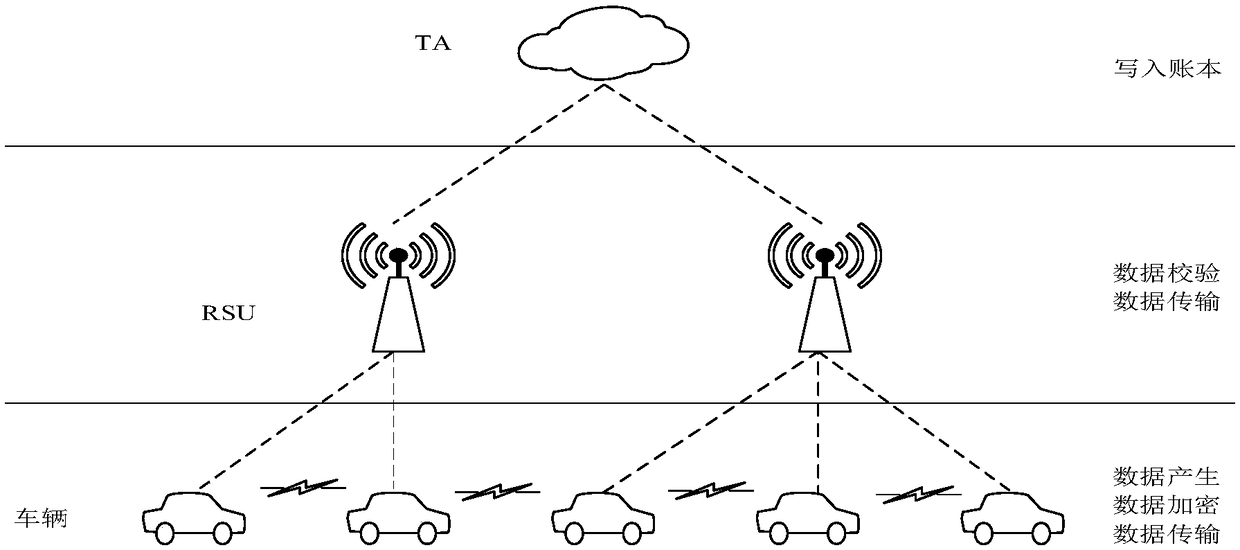
Internet of vehicles malicious node detection system and method for integrated block chain consensus mechanism
ActiveCN109462836AEfficient and accurate detectionNot easy to tamper withParticular environment based servicesVehicle wireless communication serviceDigital signatureThe Internet
The invention discloses an Internet of vehicles malicious node detection system and method for an integrated block chain consensus mechanism. Messages sent by a vehicle sending node Vi and identity information of a vehicle sending node Vi are packaged into a request authentication data packet to be sent to RSU via any vehicle receiving node Vj; after receiving the data packet, the RSU performs mutual identity authentication with the Vj; if the mutual identity authentication is passed, the RSU forwards the received data packet sent by the Vj to a TA; according to the traceability of a databaserecorded by a block chain, digital signature and information authentication are performed by using a RSA algorithm; the consensus mechanism is used for detecting whether the vehicle node is a malicious node through combining with the current state of the vehicle node. According to the method, the characteristic that the data recorded by the block chain is not easy to tamper is used, the maliciousvehicle in the Internet of vehicles can be efficiently and accurately detected, meanwhile, the problems of decentralized management and privacy protection of the Internet of vehicles also can be solved, and thus the problem that in the Internet of vehicles, the detection accuracy of the malicious node is low is solved, and the network overhead is effectively reduced.
Owner:CHANGAN UNIV
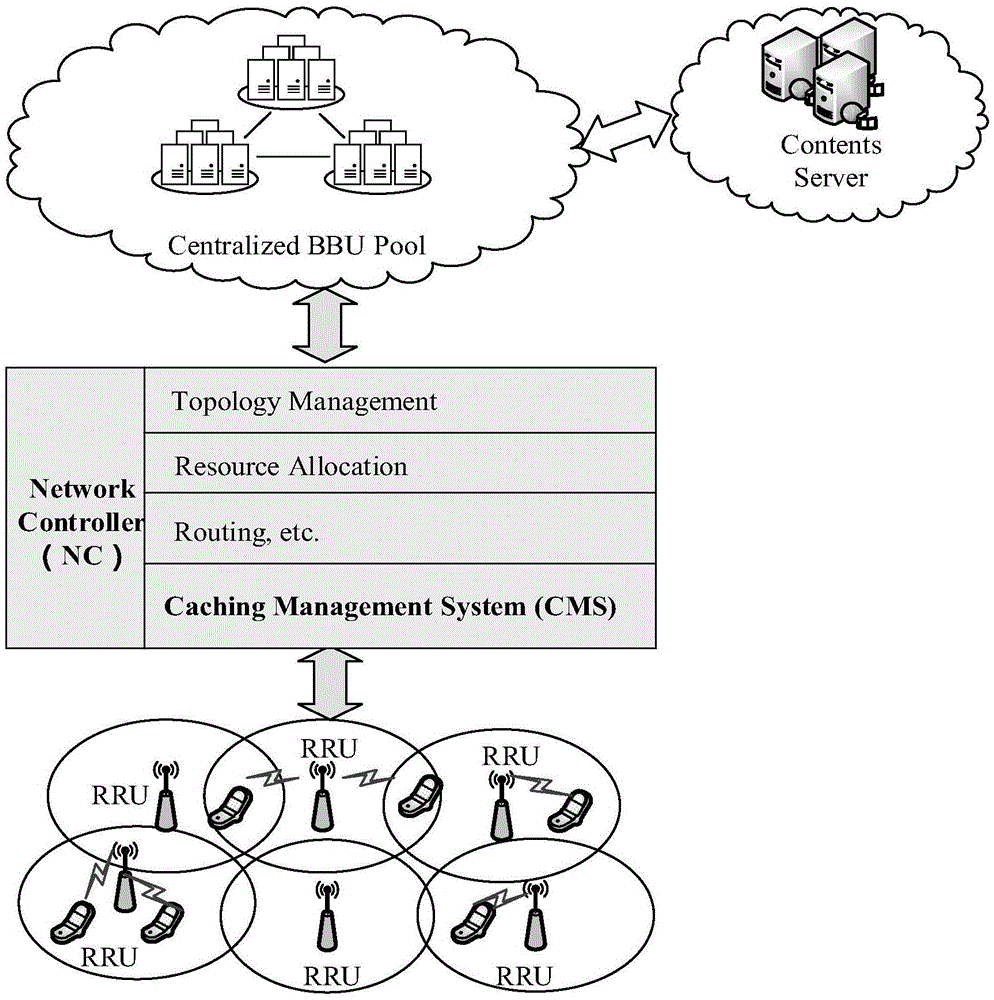
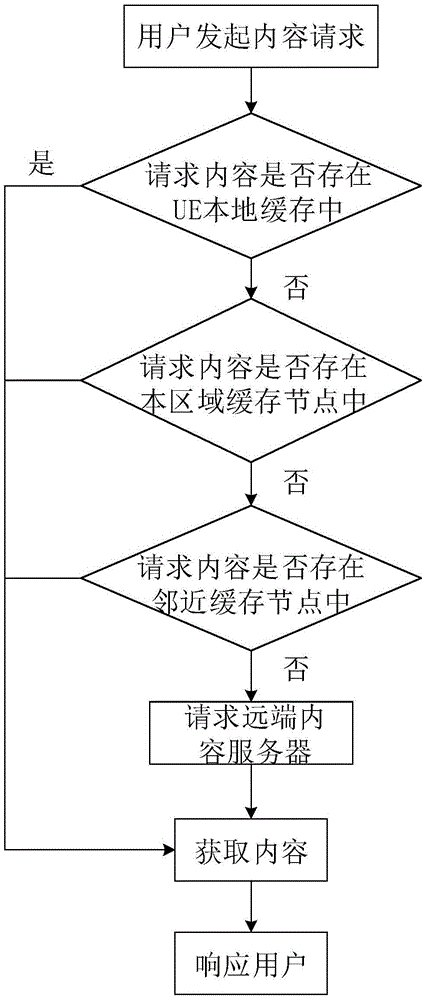
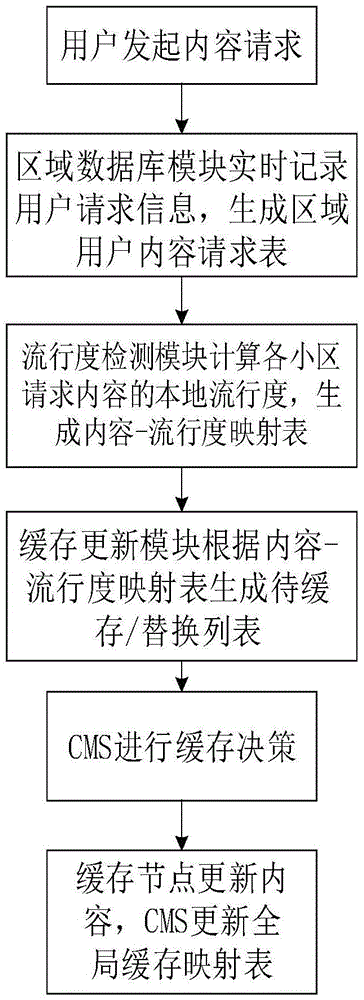
SD-RAN-based whole network collaborative content caching management system and method
The invention discloses an SD-RAN (software defined radio access network)-based whole network cooperative caching management system and method. According to the SD-RAN (software defined radio access network)-based whole network cooperative caching management system and method, a content-popularity mapping table and a wait caching / replacement list are generated through detection and content popularity statistics, and a caching decision is made according to the wait caching / replacement list, and is issued to a caching node, so that caching and update can be carried out; a real-time global caching mapping table is obtained through monitoring the caching decision; and the caching node responds to a content request and delivers corresponding content according to the content request of a user of a current cell; characteristics of limitation of content acquisition delay and the change of the popularity of different content with time and places are fully considered, and a global network view in a control layer of a software defined network is fully utilized, and therefore, the detection range of the popularity of content can be expanded; and based on whole network cooperative caching optimized content arrangement, a situation that content is repeatedly called from a remote-end content server can be avoided, and network overhead can be reduced, and user experience can be improved.
Owner:HUAZHONG UNIV OF SCI & TECH
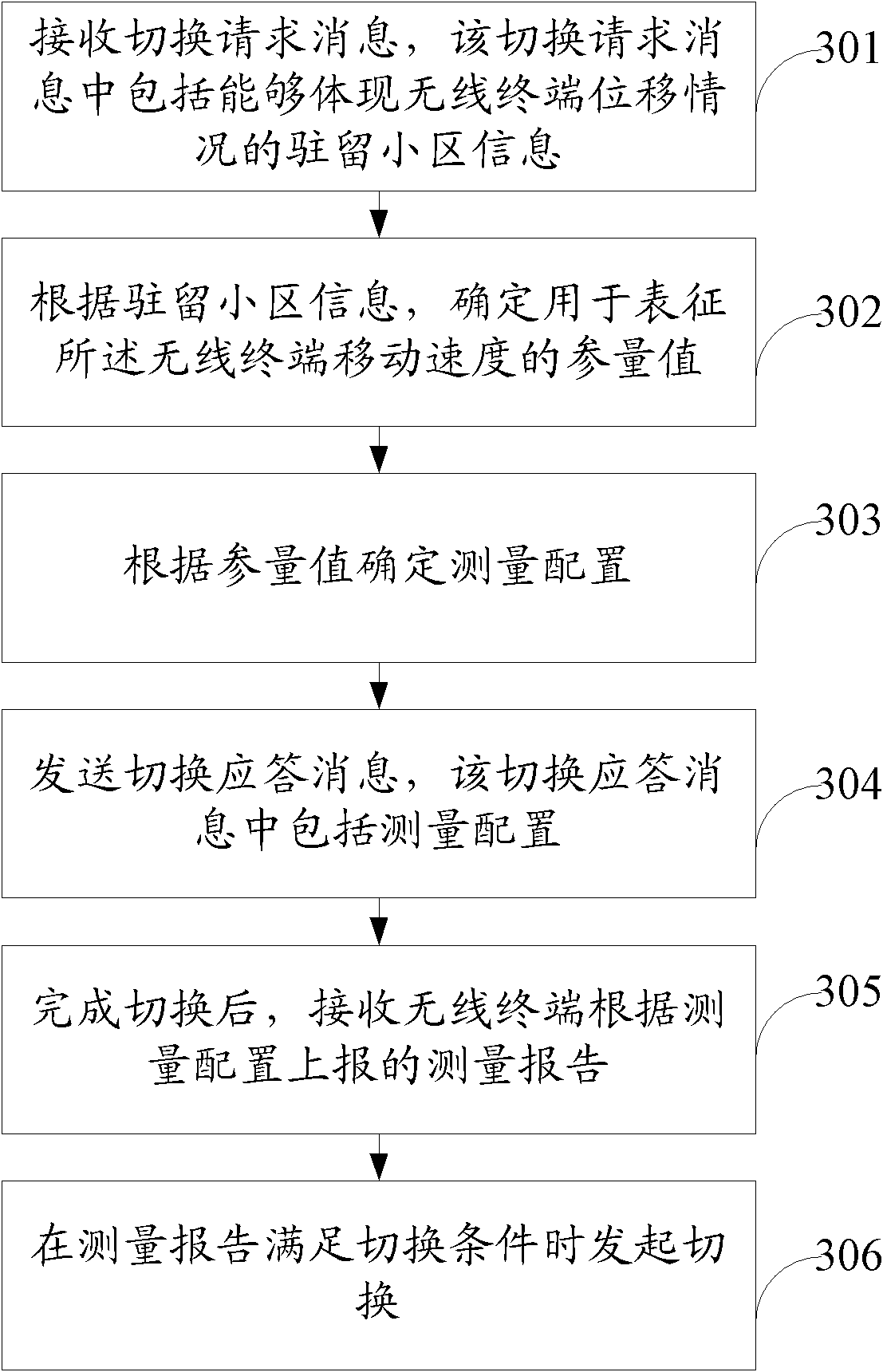
Method for setting measuring configuration during base station and user equipment (UE) switching
The invention provides a method for setting measuring configuration during base station and user equipment (UE) switching. The method for setting the measuring configuration comprises the following steps of: receiving a switching request message, wherein the switching request message comprises resident cell information which reflects the displacement situation of a wireless terminal; determining a parameter value for representing the movement speed of the wireless terminal according to the resident cell information; setting the measuring configuration according to the parameter value, determining the measuring configuration as periodic measurement when the parameter value is more than or equal to a first threshold value and determining the measuring configuration as event triggering measurement when the parameter value is less than or equal to a second threshold value; and sending a switching response message so as to allow a source base station to set the measuring configuration of the wireless terminal according to the switching response message, wherein the switching response message comprises the measuring configuration. In the embodiment of the invention, appropriate measuring configuration is set according to the movement situation of the wireless terminal, so that the situations of communication interruption during high-speed movement of the wireless terminal and the increase of network overhead during low-speed movement are reduced.
Owner:WUHAN HONGXIN TELECOMM TECH CO LTD
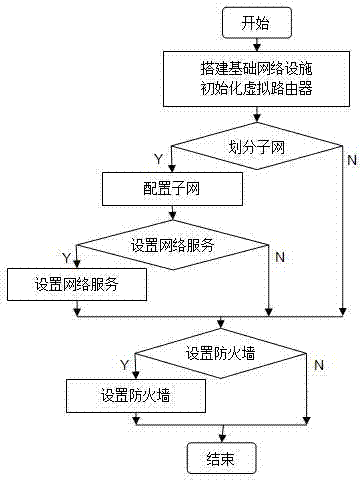
Cloud data center network deployment scheme based on virtual router
InactiveCN103595772AFlexible configurationNumber of flexible optionsData switching networksEngineeringNetwork management
The invention provides a cloud data center network deployment scheme based on a virtual router. By introducing the concept of a virtual exchanger and the virtual router which are independently developed, the network concept from the physics aspect is abstracted to the virtual aspect so that unified management can be carried out by webmasters conveniently and the network expense can be saved. The scheme includes the steps that firstly, a basic network environment is built; secondly, the virtual exchanger and the virtual router are deployed; thirdly, subnetting is carried out; fourthly, network services are configured, a network is scientifically partitioned into an external network, an internal network and a route network by in-depth investigation and research on network requirements of customers, and different levels of deployment schemes are made according to different network classifications. Flexibility requirements of customers are better met, at the same time, classified and hierarchical network management is achieved, deployment is more scientific and concise and management is facilitated.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
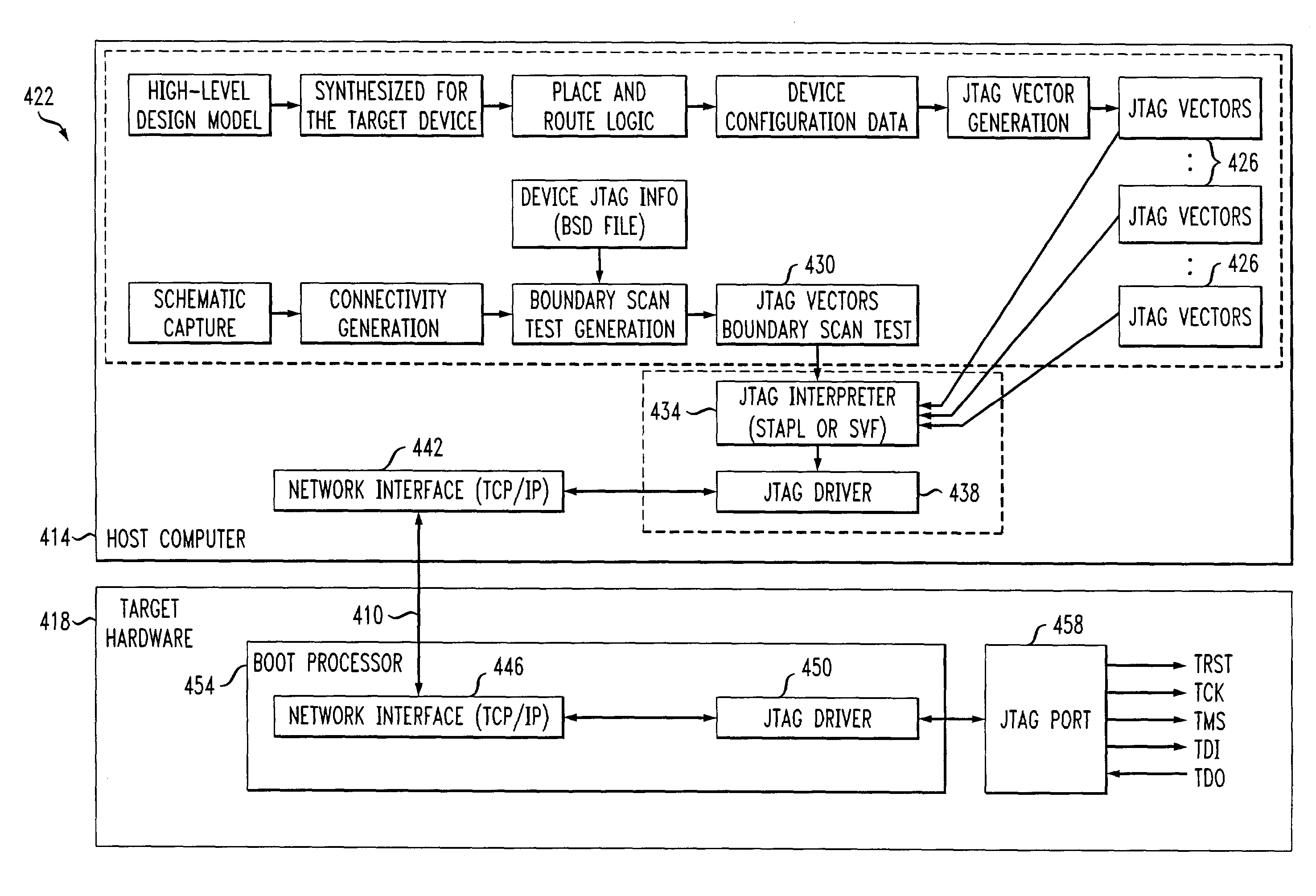
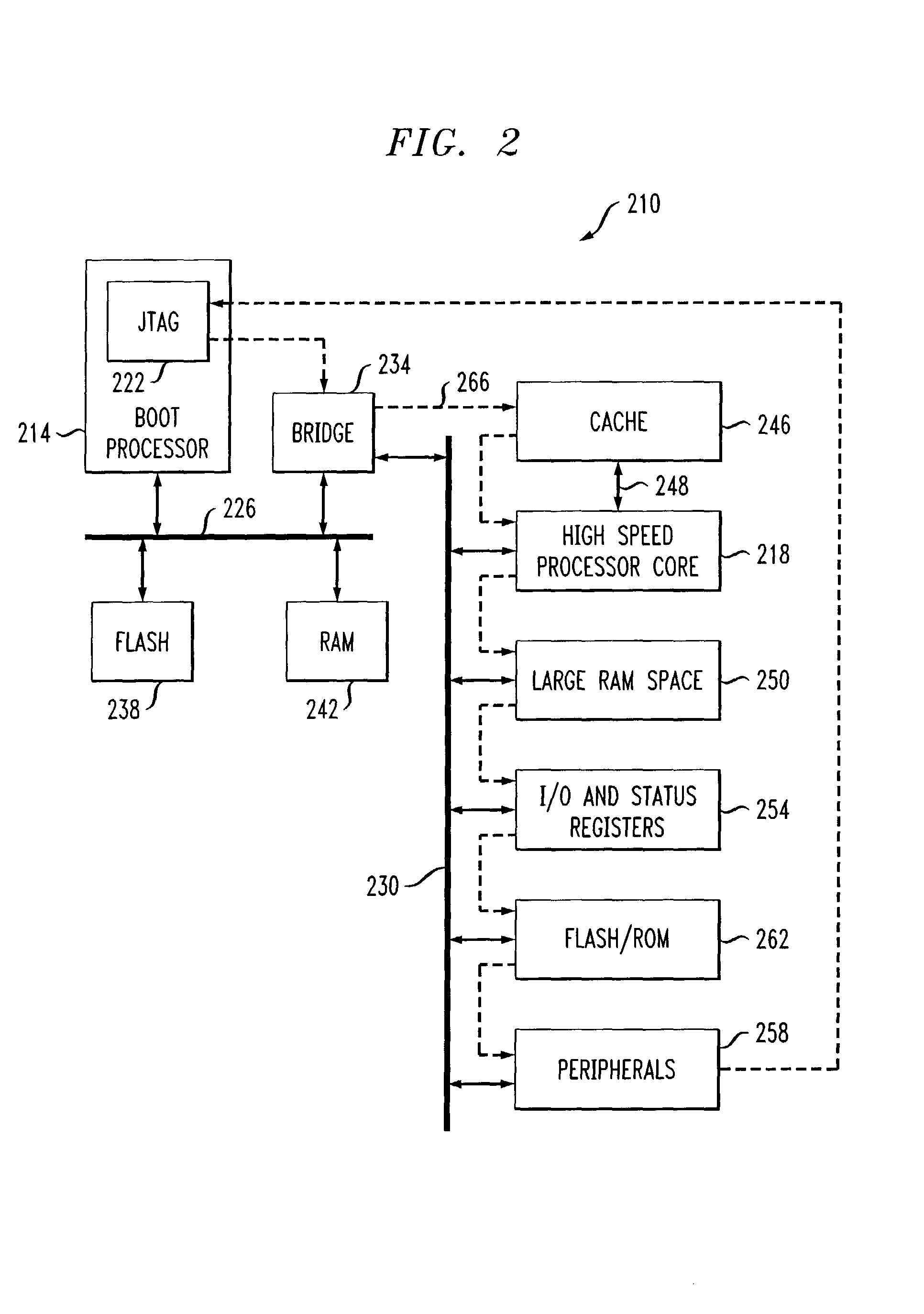
Methods and systems for remotely controlling a test access port of a target device
InactiveUS7017081B2Digital circuit testingDetecting faulty hardware by remote testNetwork linkJoint Test Action Group
JTAG operations are carried out remotely over a network interface. The host processor includes a JTAG interpreter and a host side JTAG driver. A target device includes a target side JTAG driver. The interpreter processes and translates JTAG design files. The host side JTAG driver generates messages for the target side JTAG driver based on the translation. The host JTAG driver delivers the messages to a host network interface. The host network interface is connected via a network link to a target network interface. The target network interface is connected to the target side JTAG driver. The target side JTAG driver communicates with a target boundary scan chain. The target side JTAG driver and host side JTAG driver communicate over the network link. Network overhead is reduced by buffering messages until a message requiring a return of test data is ready for transmission.
Owner:LUCENT TECH INC +1
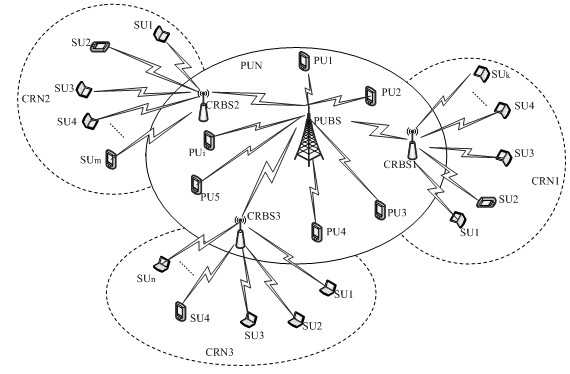
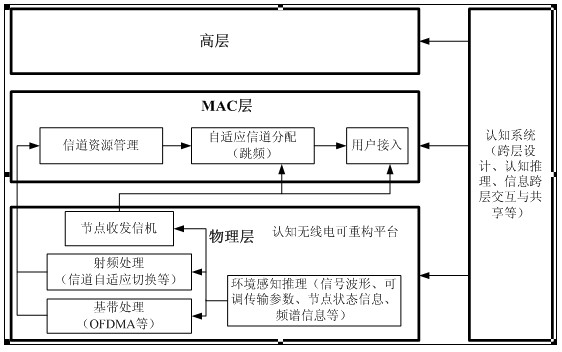
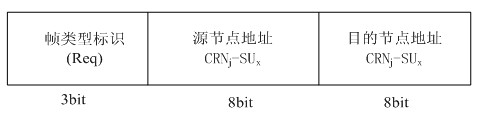
Cross-layer cognitive radio network user access method based on frequency hopping
InactiveCN102404751AImprove spectrum utilizationTake advantage ofTransmissionNetwork planningCognitive userFrequency spectrum
The invention provides a cross-layer cognitive radio network user access method based on frequency hopping, and belongs to the field of application of radio networks. According to the method, cognitive users in primary user network is divided into a plurality of clusters according to the cognitive base station service range; each cluster comprises a cognitive base station (cluster head) and a plurality of cognitive users (cluster nodes); the cognitive base station is connected with a primary user base station and is managed by the user base station; however, the communications of cognitive users are controlled and managed by the cognitive base station. Based on the fact that corresponding idle spectrum information is obtained through monitoring a primary user on the network physical layer and sensing the spectrum, a plurality of frequency hopping patterns are generated by using a frequency hopping technology, and the cognitive users are made to carry out hopping communications between a plurality of signal channels as per certain frequency hopping pattern within different frequency ranges at different time on the MAC (Media Access Control) layer, so that the cognitive user dynamic access is achieved. The invention has the excellent effects of small network expense, high utilization ratio of spectrum, small interference and flexible and efficient user access manner.
Owner:KUNMING UNIV OF SCI & TECH
Internet-of-vehicles task unloading and resource allocation method based on 5G mobile edge computing
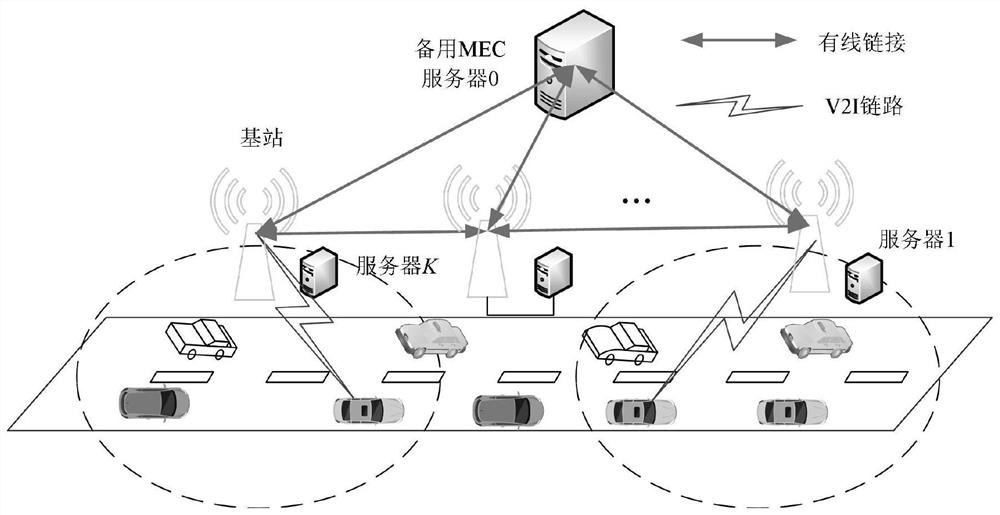
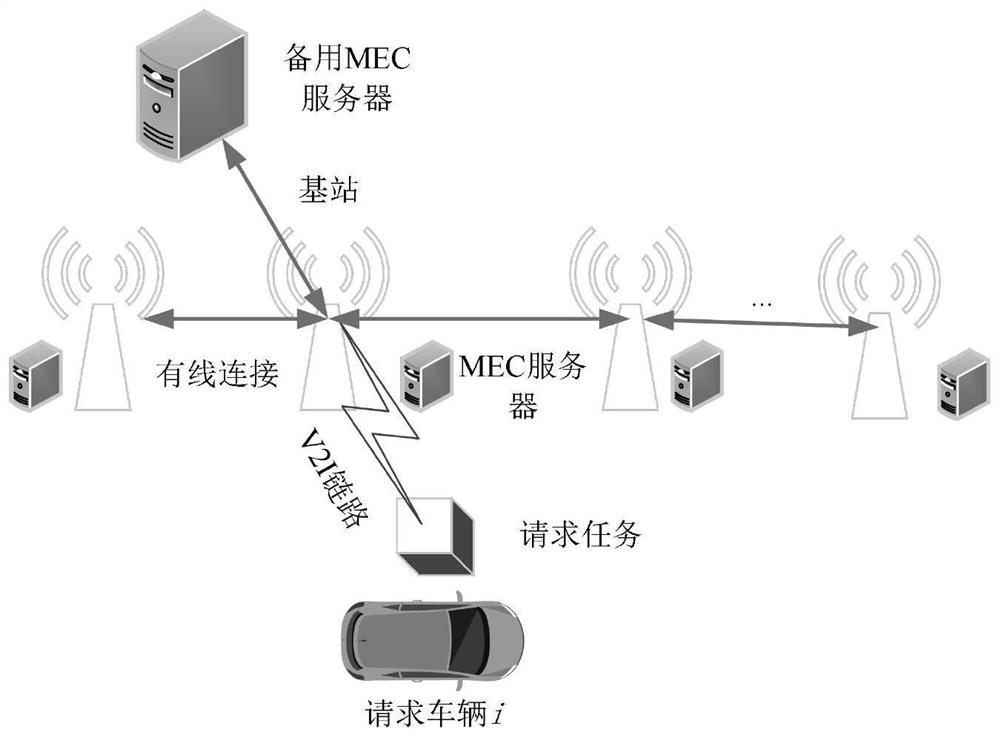
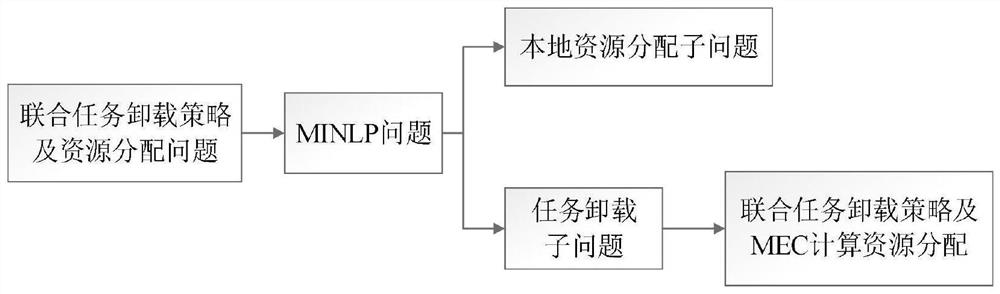
ActiveCN111918311ASolve insufficient computing resourcesMinimize overheadParticular environment based servicesVehicle wireless communication serviceResource assignmentMobile edge computing
The invention relates to an Internet-of-vehicles task unloading and resource allocation method based on 5G mobile edge computing, and belongs to the technical field of mobile communication. The problem of insufficient computing resources in a network is solved by adding a standby MEC server, the problem of unbalanced load is solved by sharing resources among MEC servers, and a task unloading strategy and computing resource allocation are combined to minimize the network overhead. Due to the fact that the optimization problem is difficult to directly solve, the invention provides a heuristic algorithm, and an original problem is converted into a local computing resource allocation sub-problem and a task unloading sub-problem to be solved respectively. Wherein the local computing resource allocation sub-problem adopts a derivative extremum solving method to obtain an optimal solution, the task unloading sub-problem is combined with task unloading and MEC resource allocation, and a Lagrange optimization algorithm is adopted to solve, so that the network time delay and the energy consumption overhead are minimized.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
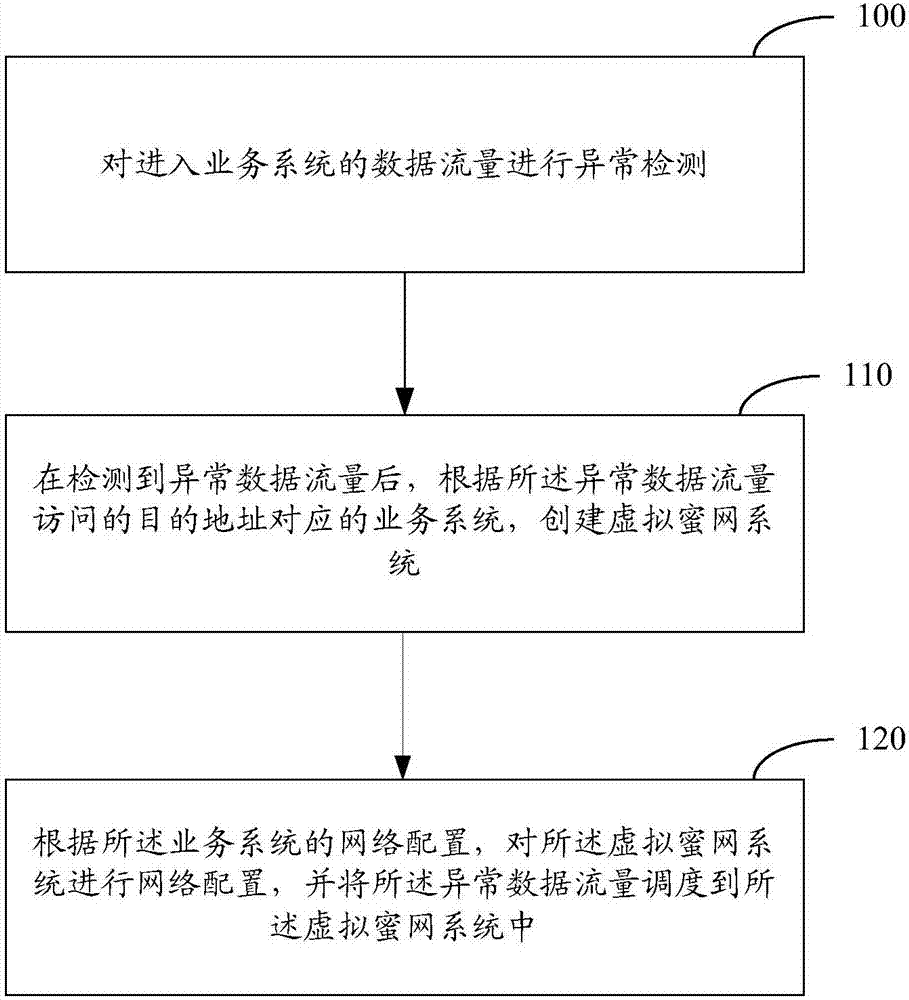
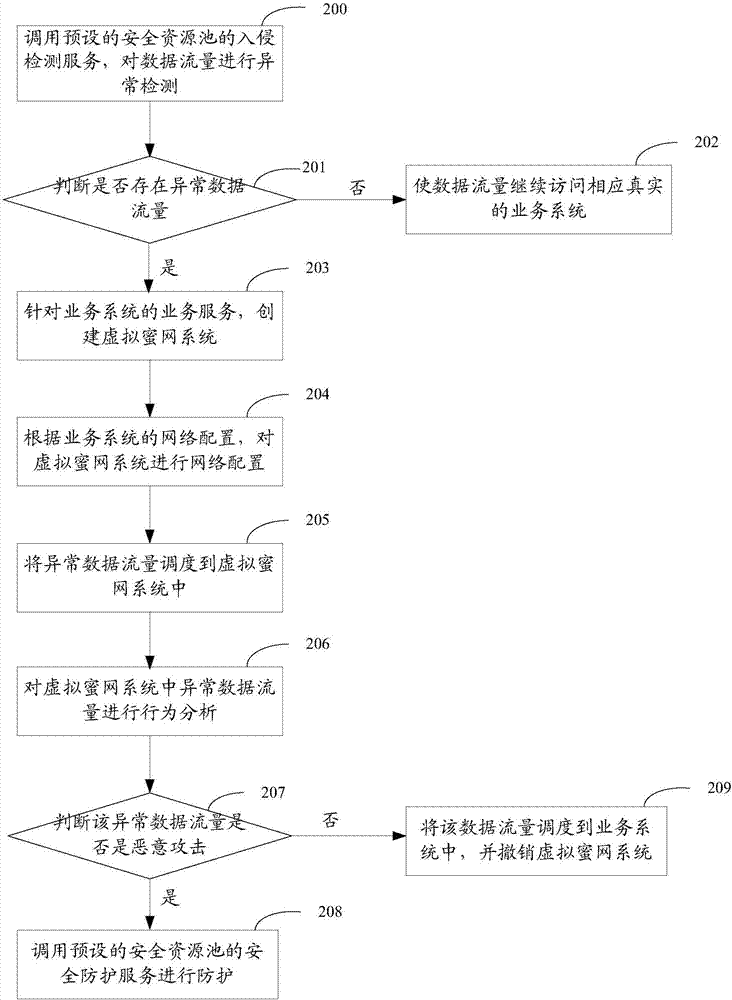
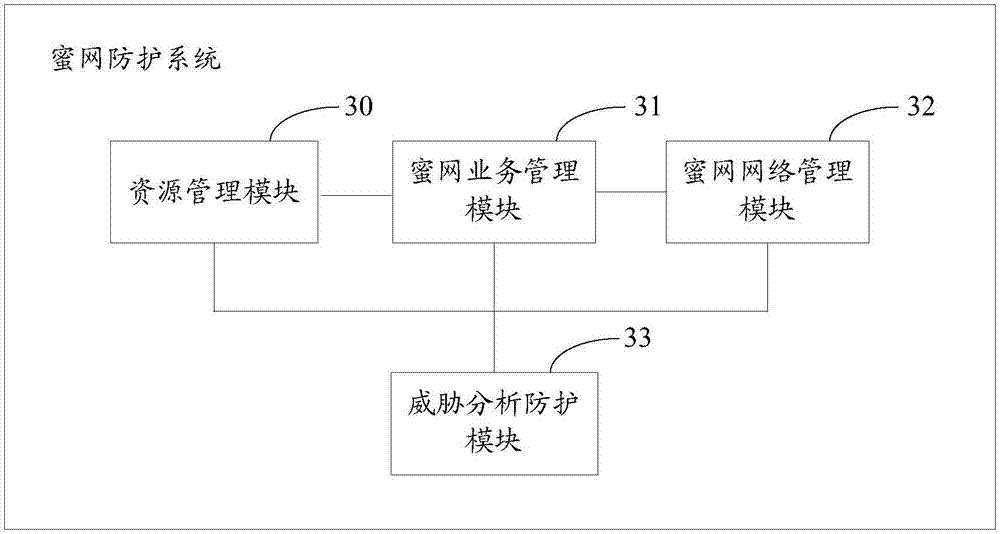
Honeynet protection method and system
ActiveCN107370756AImprove concealmentAchieve consistencyTransmissionAnomaly detectionNetwork overhead
The invention relates to the field of network security, and especially relates to a Honeynet protection method and system. The method includes the following steps: detecting whether the data traffic entering a business system is abnormal; after detecting abnormal data traffic, creating a virtual Honeynet system according to a business system corresponding to a destination address accessed by the abnormal data traffic; and carrying out network configuration on the virtual Honeynet system according to the network configuration of the business system, and scheduling the abnormal data flow to the virtual Honeynet system. The virtual Honeynet system consistent with the business service of the business system is created, and network configuration is carried out on the virtual Honeynet system. The consistency between the virtual Honeynet system and the business system in business logic and network configuration is ensured, the virtual Honeynet system is more concealed, and attack seduction and forensic analysis are more concealed and less detectable to attackers. Moreover, the deployment is relatively simple, and the method and the system can be quickly deployed to an SDN (Software Defined Network) to achieve security protection without increasing the overhead of the business network.
Owner:NSFOCUS INFORMATION TECHNOLOGY CO LTD +1
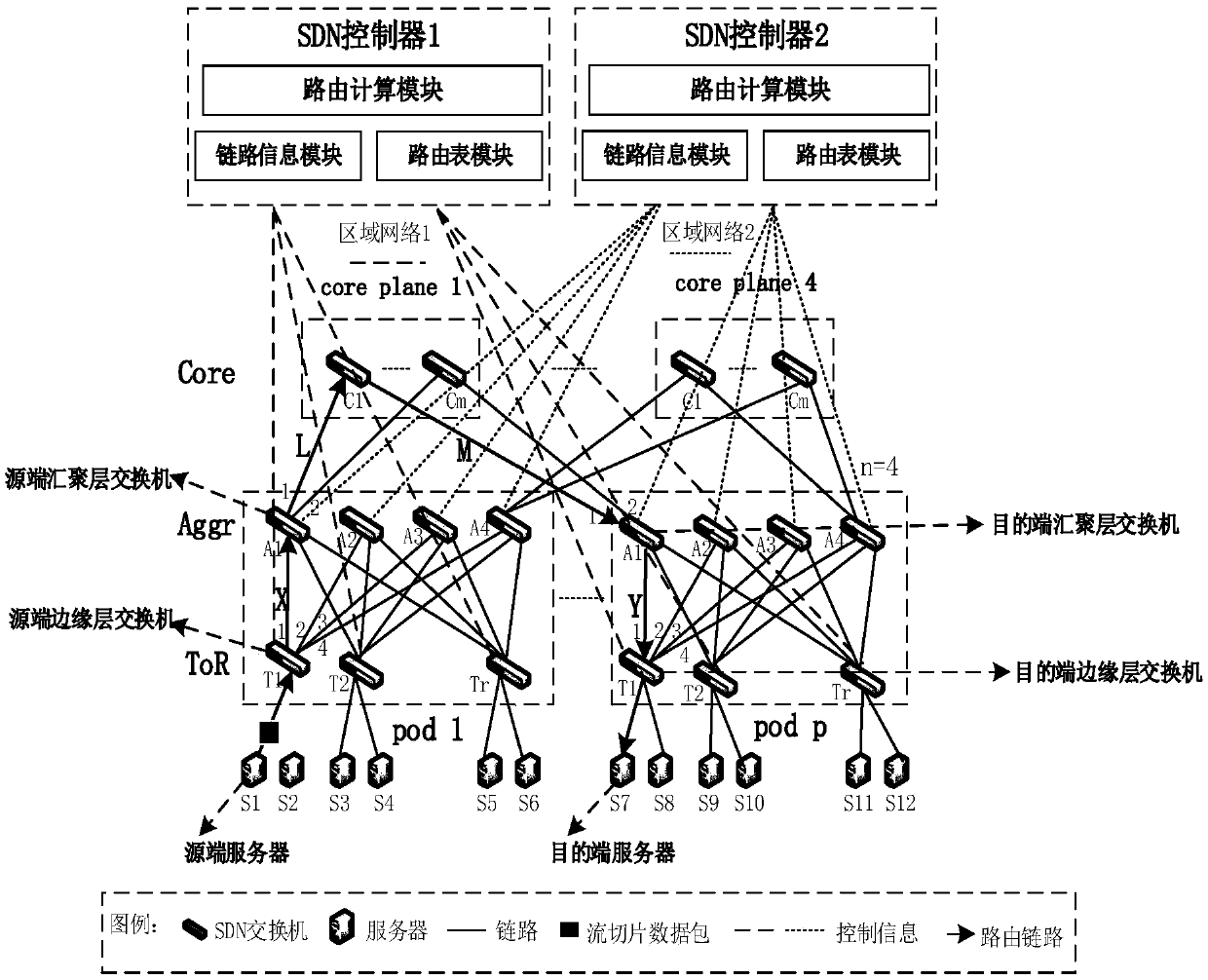
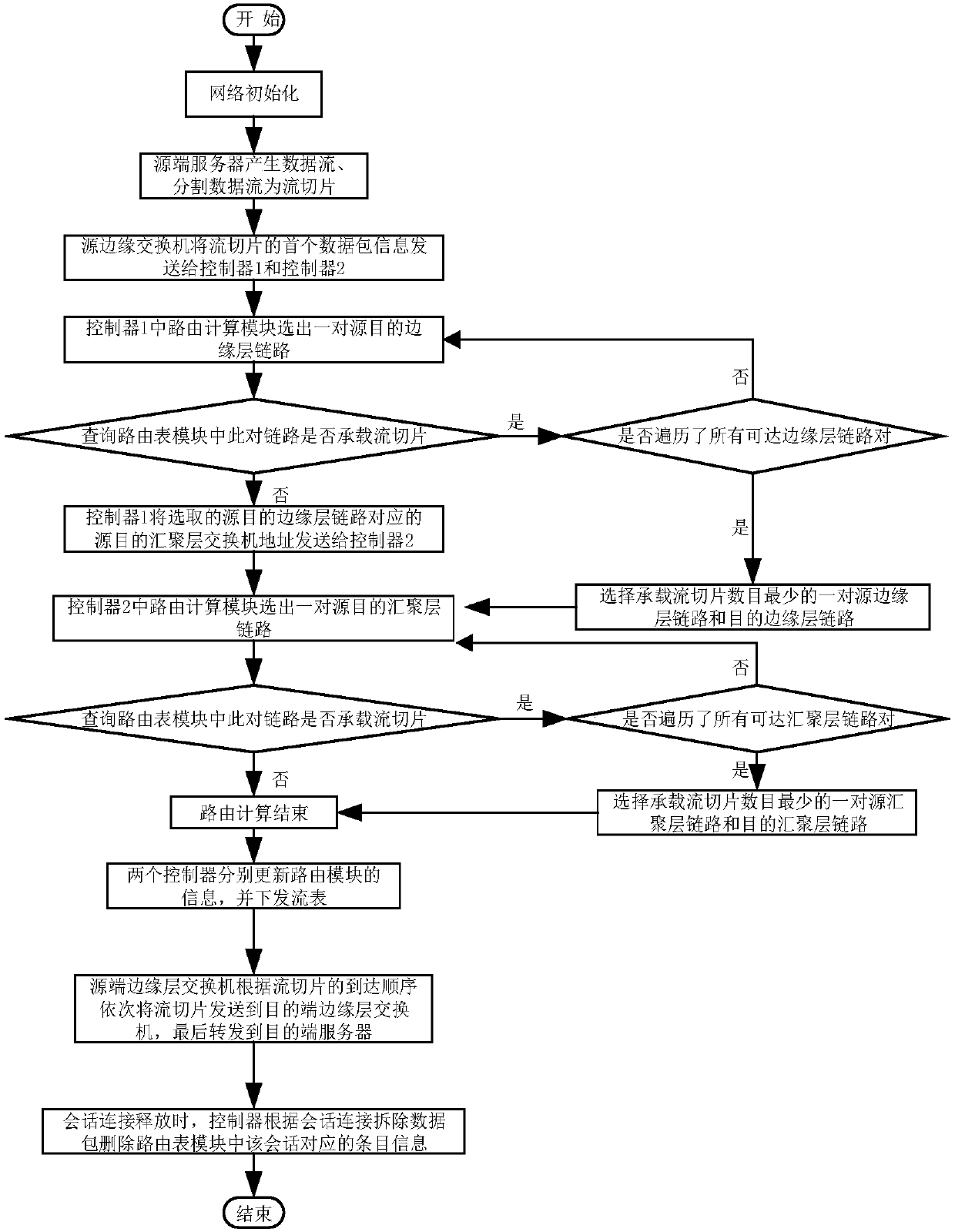
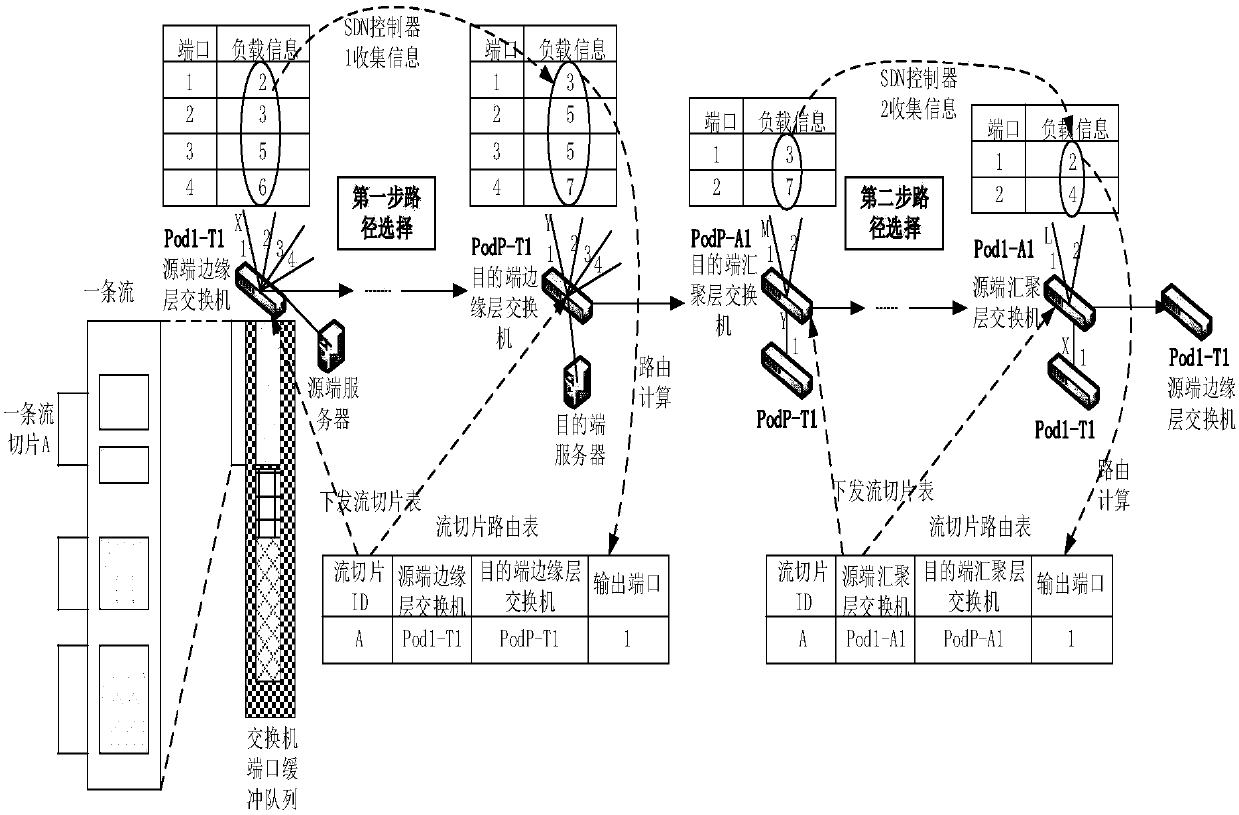
SDN based distributed control load balancing system and method
ActiveCN107819695AOvercoming the Distributed Scaling ProblemOvercome overheadData switching networksData streamRouting table
The invention discloses an SDN based distributed control load balancing system and method, aiming at mainly solving the problems of distributed extension, network overheads, uneven load and link congestion in existing small-scale single data center networks. The system disclosed by the invention comprises a three-layer Clos underlying network and two SDN controllers, wherein the SDN controller isadditionally provided with link information, a routing table and a routing calculation module, and the above modules act together to calculate a path for a data stream. The load balancing method includes the following steps: adopting two-step path selection, partitioning the data stream into stream slices in a buffer area of an end host, separately monitoring and collecting local link informationof two local area networks by using the two controllers, and taking a queuing delay of each port of a switch as the link information to optimize the selection of routing links. According to the schemeof the invention, the distributed multi-controller and two-step path selection are adopted in the three-layer Clos network, and a significant network balancing effect can be achieved; and the schemecan be used for load balancing control of large-scale single data center networks.
Owner:XIDIAN UNIV +1
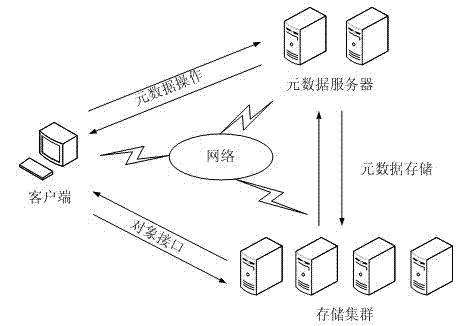
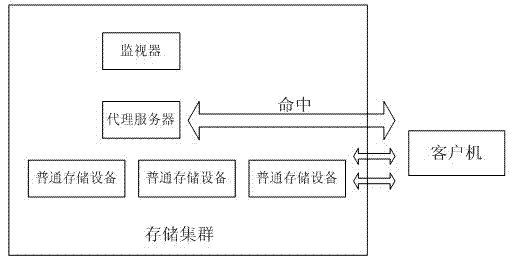
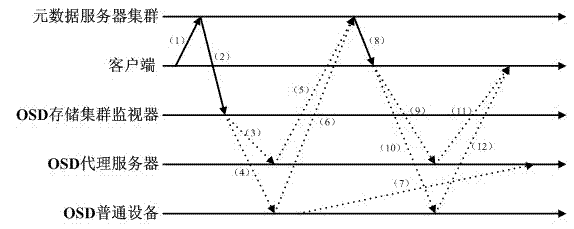
Storage caching method of object-based distributed file system
ActiveCN102523285AReduced I/O performanceImprove read and write speedTransmissionSpecial data processing applicationsObject basedDistributed File System
The invention relates to a storage caching method of an object-based distributed file system. The traditional object-based distributed file system has the problems that the network cost is instable and the whole I / O (Input / Output) performance is low in a heterogeneous storage environment. The architecture of the object-based distributed file system changes the traditional data access mode thereof, establishes caching by arranging a proxy server in a storage cluster, and adopts the caching replacement strategy in the invention to perform caching process of hot object files which are accessed very frequently. By utilizing the method, the file access speed of the distributed file system can be increased, the network transmission cost can be reduced, and the I / O performance of the whole system can be increased.
Owner:HANGZHOU DIANZI UNIV
Data mining method and node
ActiveCN105446979AReduce overheadAvoid load balancing processResource allocationData miningNetwork overheadReal-time computing
The invention provides a data mining method and node; the method comprises the following steps: obtaining an estimated execution time of each calculating sub-node in a present round iteration task, and assigning corresponding task data bulk for the calculating sub-nodes according to the estimated execution time; collecting execution condition information of each calculating sub-node of the present round iteration task after the present round iteration task is executed, and determining whether to adjust the task data bulk or not for each calculating sub-node of next round iteration task; carrying out the next round iteration task according to the adjusted task data bulk, thus assigning corresponding task data bulk according to the ability of each calculating sub-node, and adjusting the task data bulk for each calculating sub-node of the present round iteration task according to the execution conditions of the previous round; the method and node can prevent unnecessary load balancing process, reduce network expenditure, and can improve system data mining performance.
Owner:HUAWEI TECH CO LTD
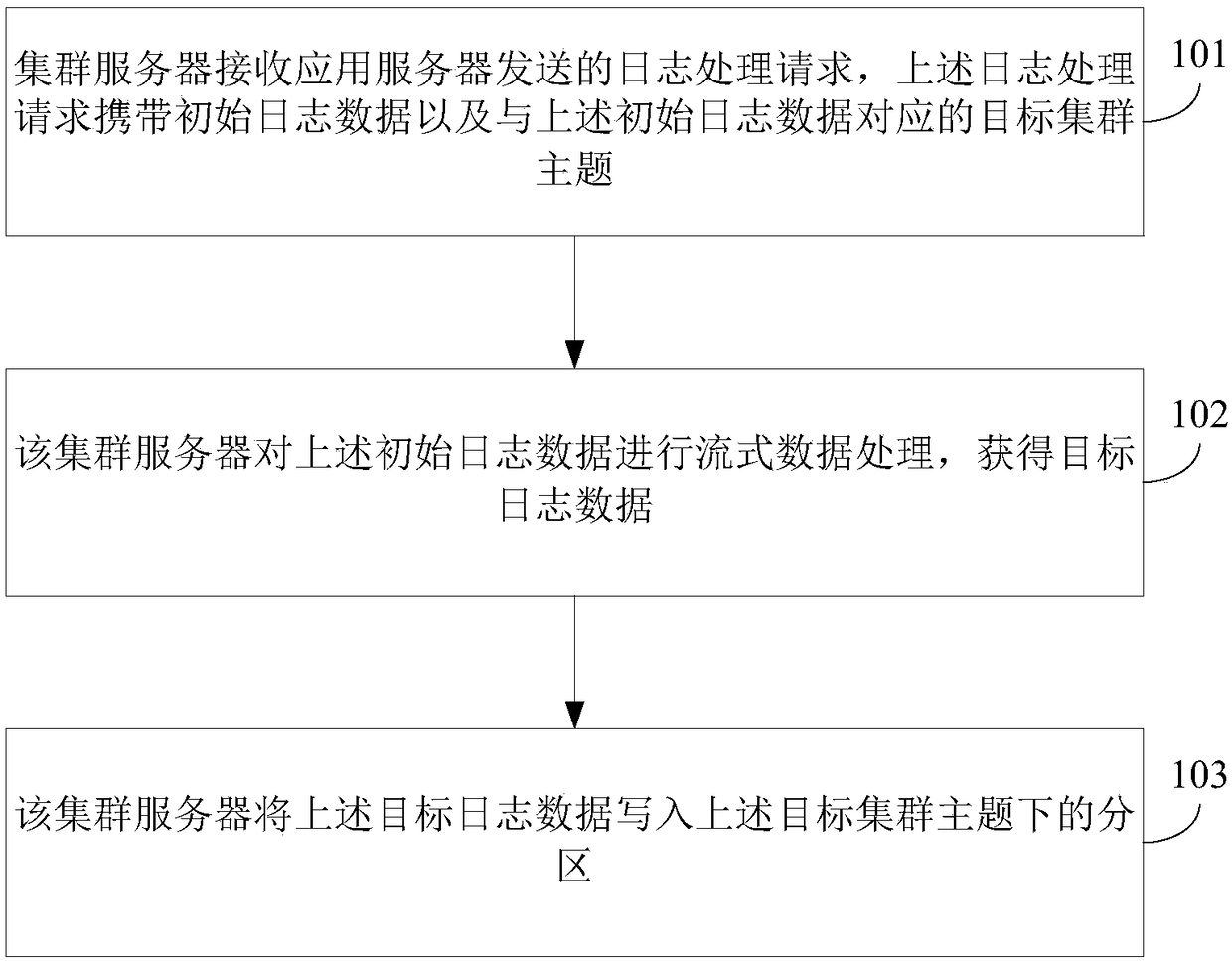
Log parsing method, equipment and computer readable medium
InactiveCN108365971AReduce overheadReduce IO overheadData switching networksData synchronizationData platform
The embodiment of the invention discloses a log parsing method, equipment and a computer readable medium. The method comprises the steps that a log processing request sent by an application server isreceived, wherein the log processing request carries initial log data and a target cluster theme corresponding to the initial log data; streaming data processing is conducted on the initial log data to obtain target log data; and the target log data is written into a partition under the target cluster theme. According to the method, data synchronization operations between a service server and a big data platform when a log is generally parsed through an off-line program can be reduced, the network overhead of data transmission and the IO overhead of a disk are reduced, the processing time is shortened, therefore, the processing timeliness of log parsing is improved, and by analyzing a log parsing result, the advertising popularity and the user distribution condition can be obtained, the expense of an advertiser can be reasonably charged, and the industry development direction can be provided.
Owner:SHENZHEN GIONEE COMM EQUIP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com