Patents
Literature
818 results about "Abstract syntax tree" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
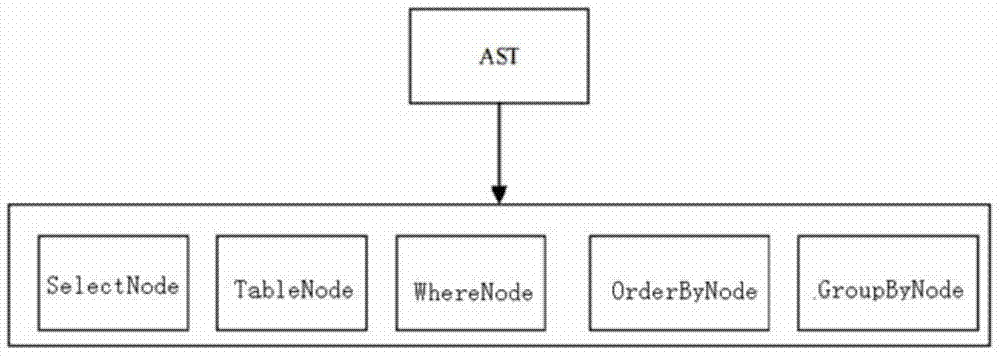
In computer science, an abstract syntax tree (AST), or just syntax tree, is a tree representation of the abstract syntactic structure of source code written in a programming language. Each node of the tree denotes a construct occurring in the source code.
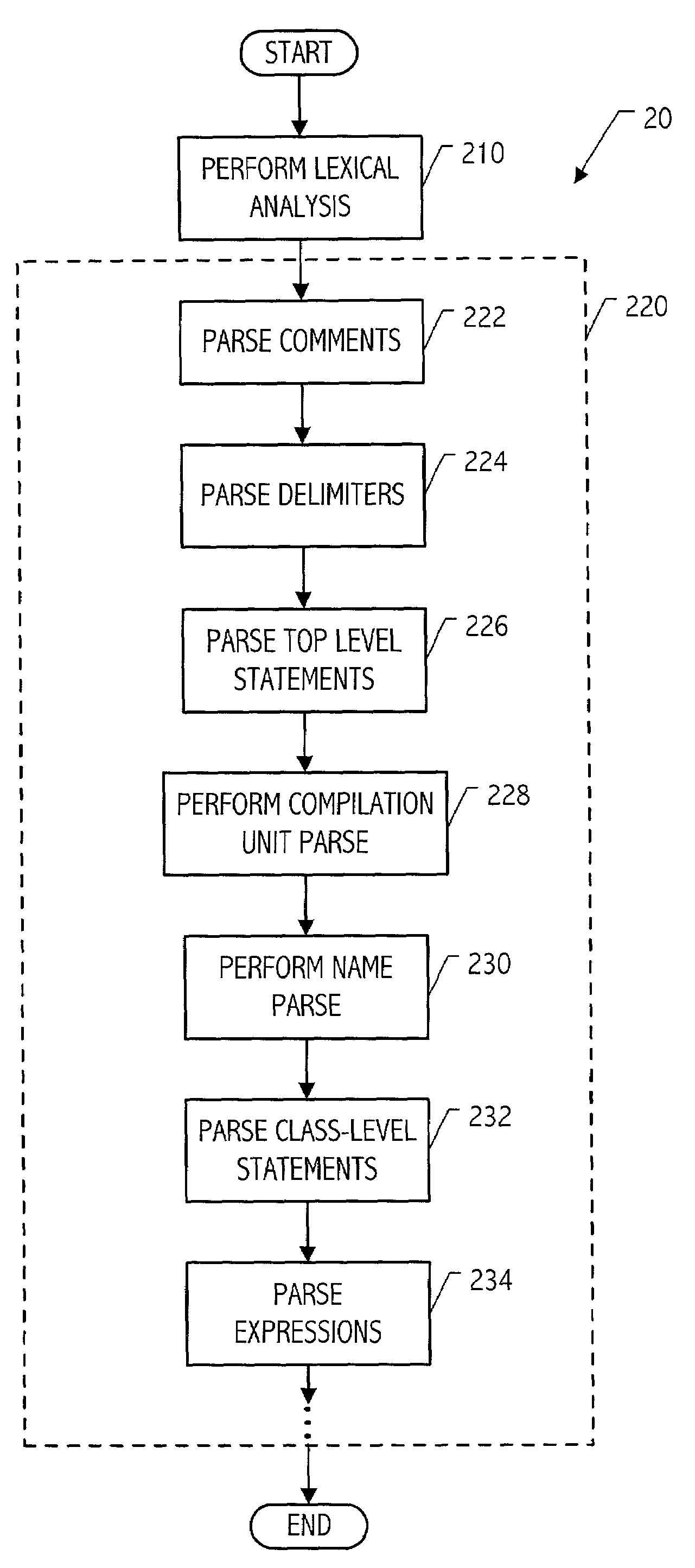
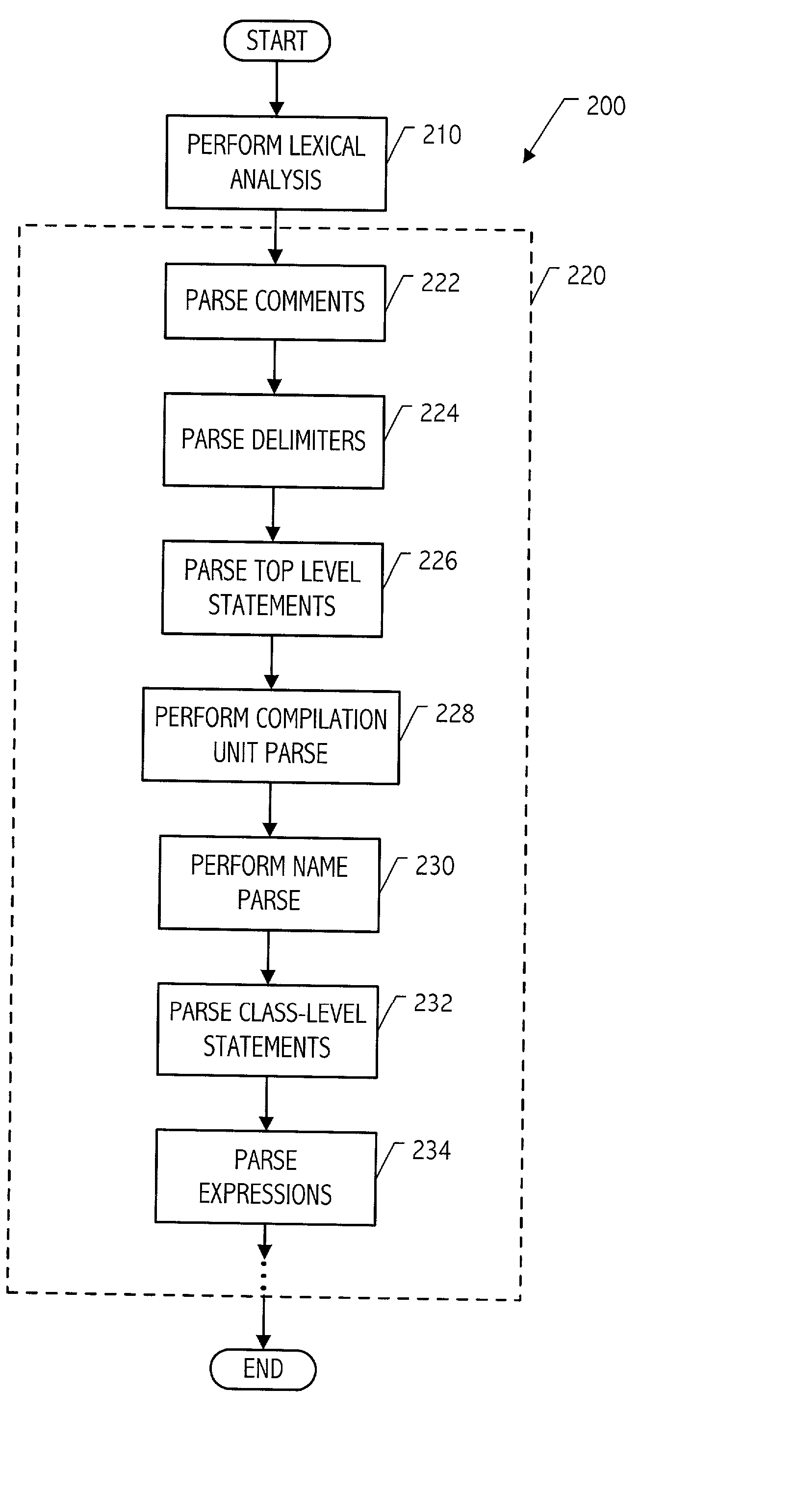
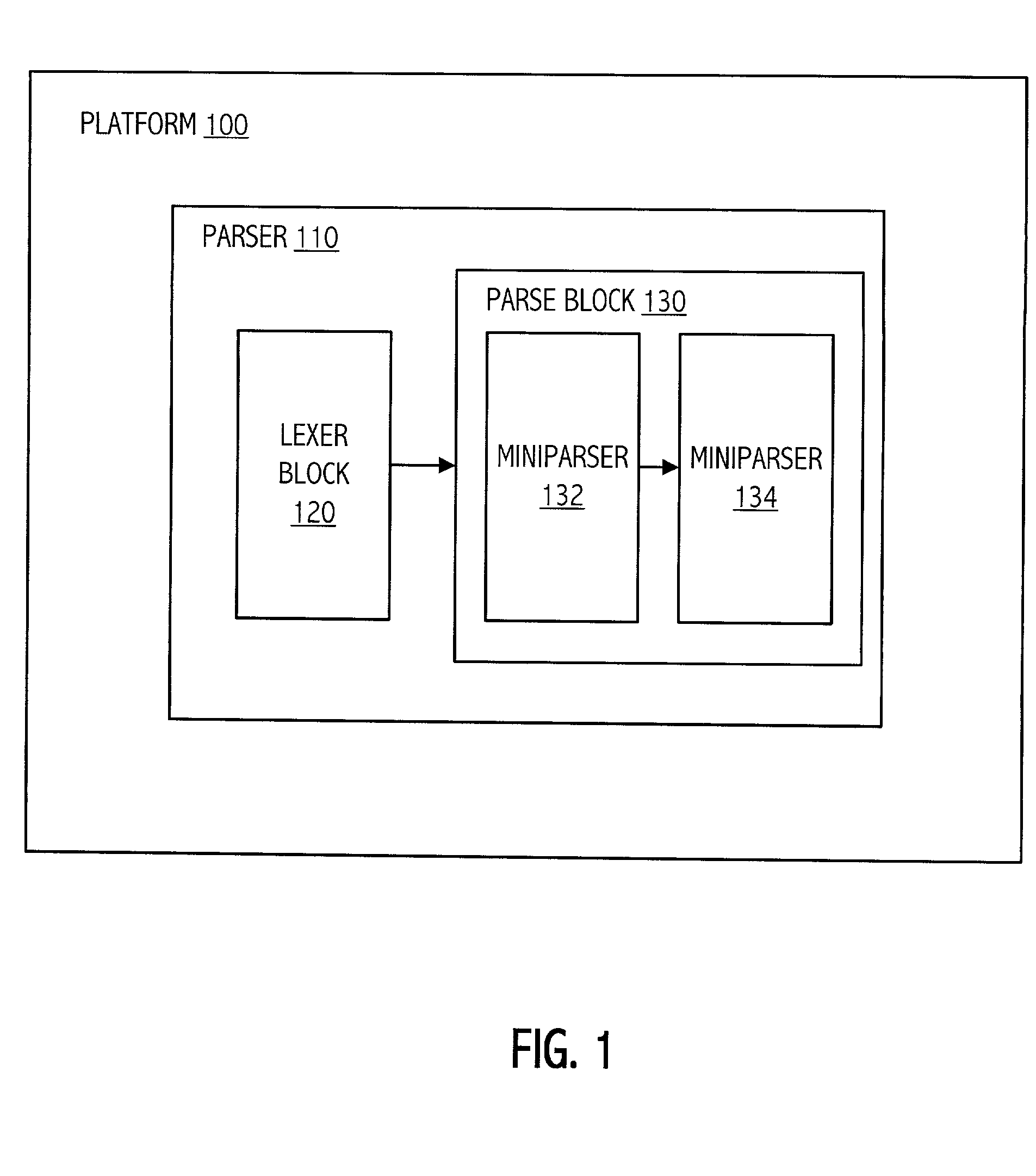
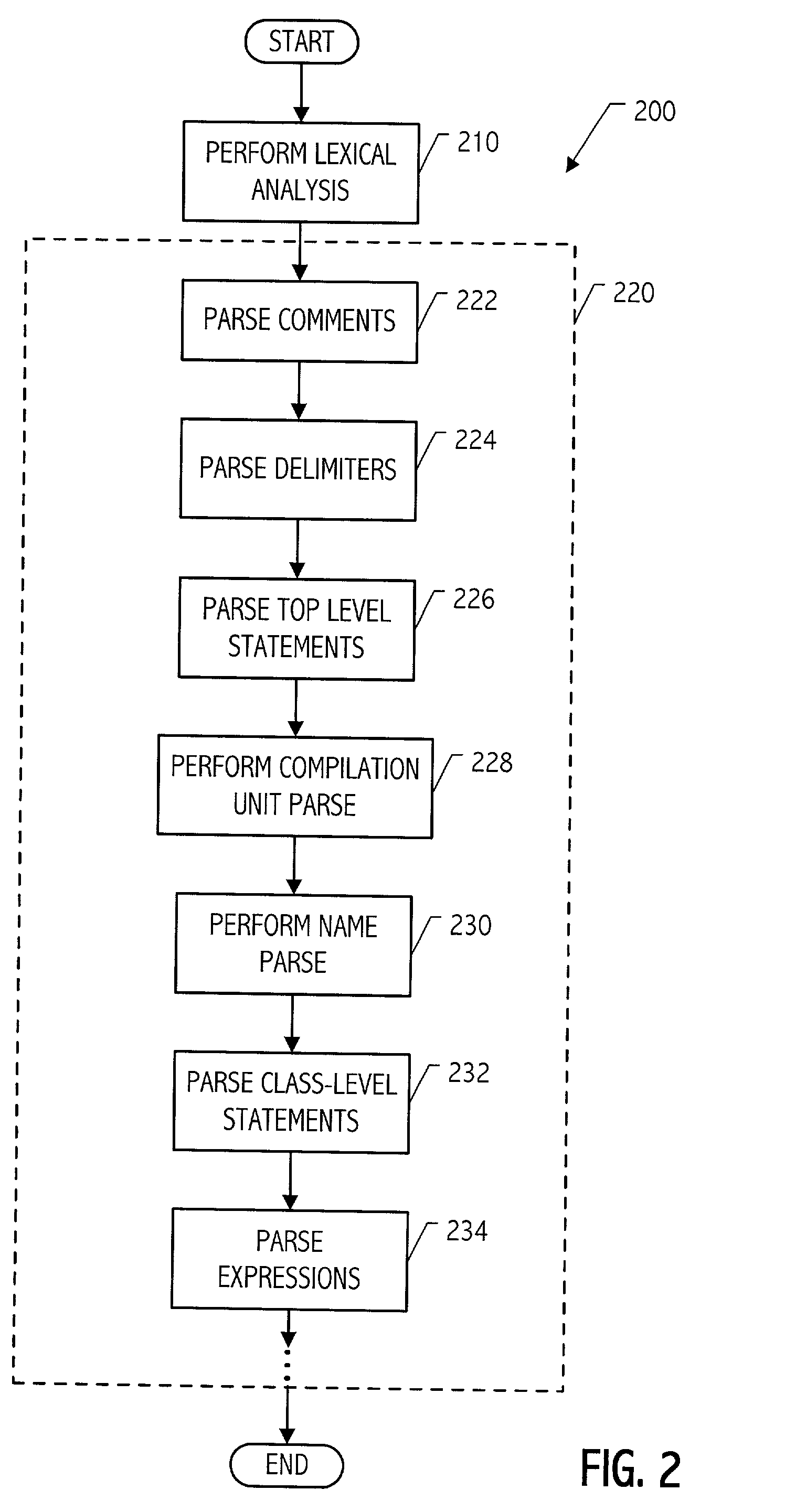
Modular parser architecture with mini parsers
InactiveUS7089541B2Software engineeringSpecific program execution arrangementsMicrocomputerLexical analysis
A modular parser architecture and methods related thereto make use of a number of miniparsers. Each miniparser is capable of receiving input and generating an output dependent thereon. In one embodiment, a lexer or a miniparser capable of lexical analysis receives certain code and provides an abstract syntax tree. Each miniparser performs operations on a set of syntactical constructs to produce a corresponding output syntax tree, which in turn may become an input syntax tree for a next miniparser which may operate on a different set of syntactical constructs.
Owner:ORACLE INT CORP
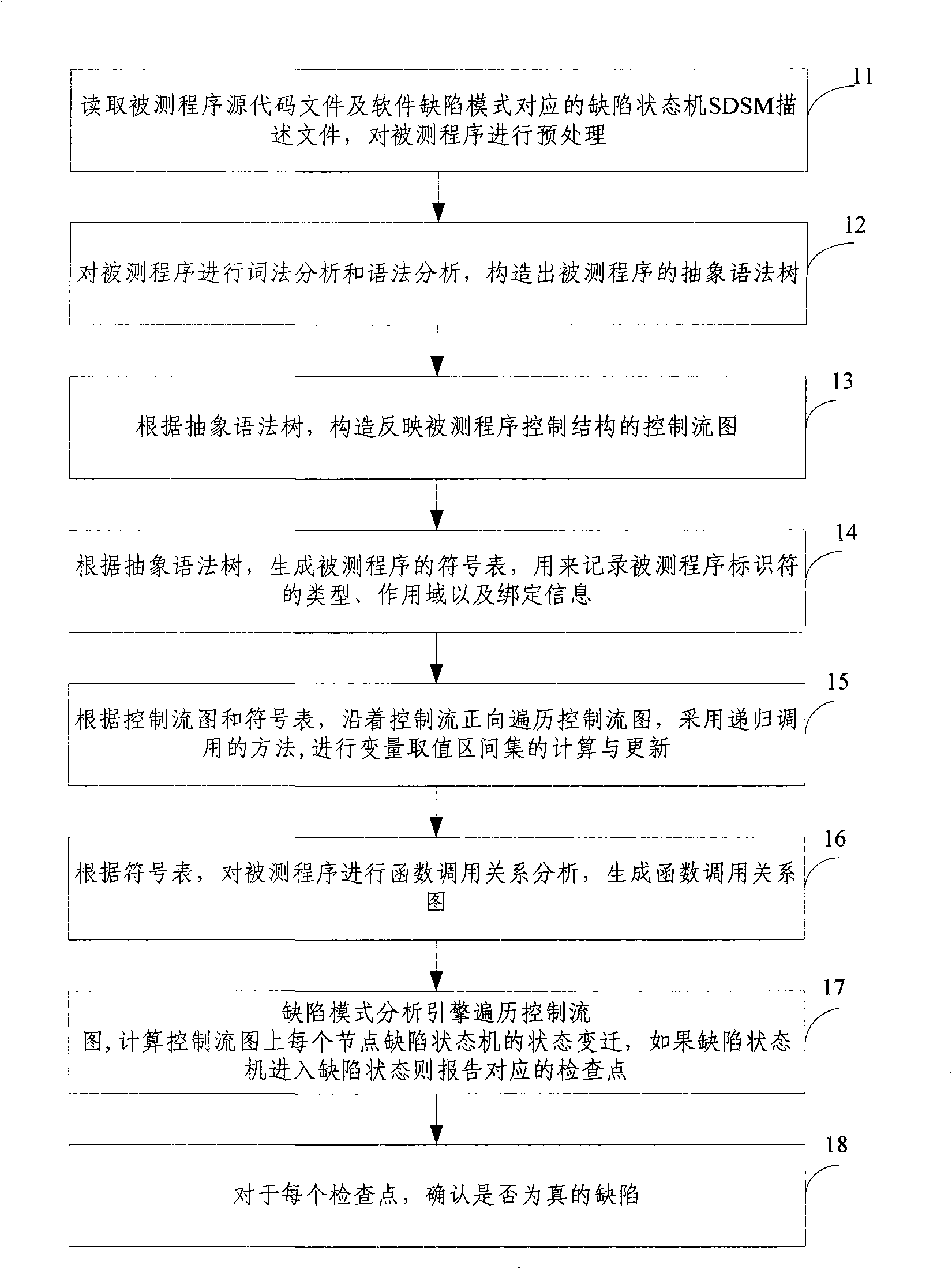
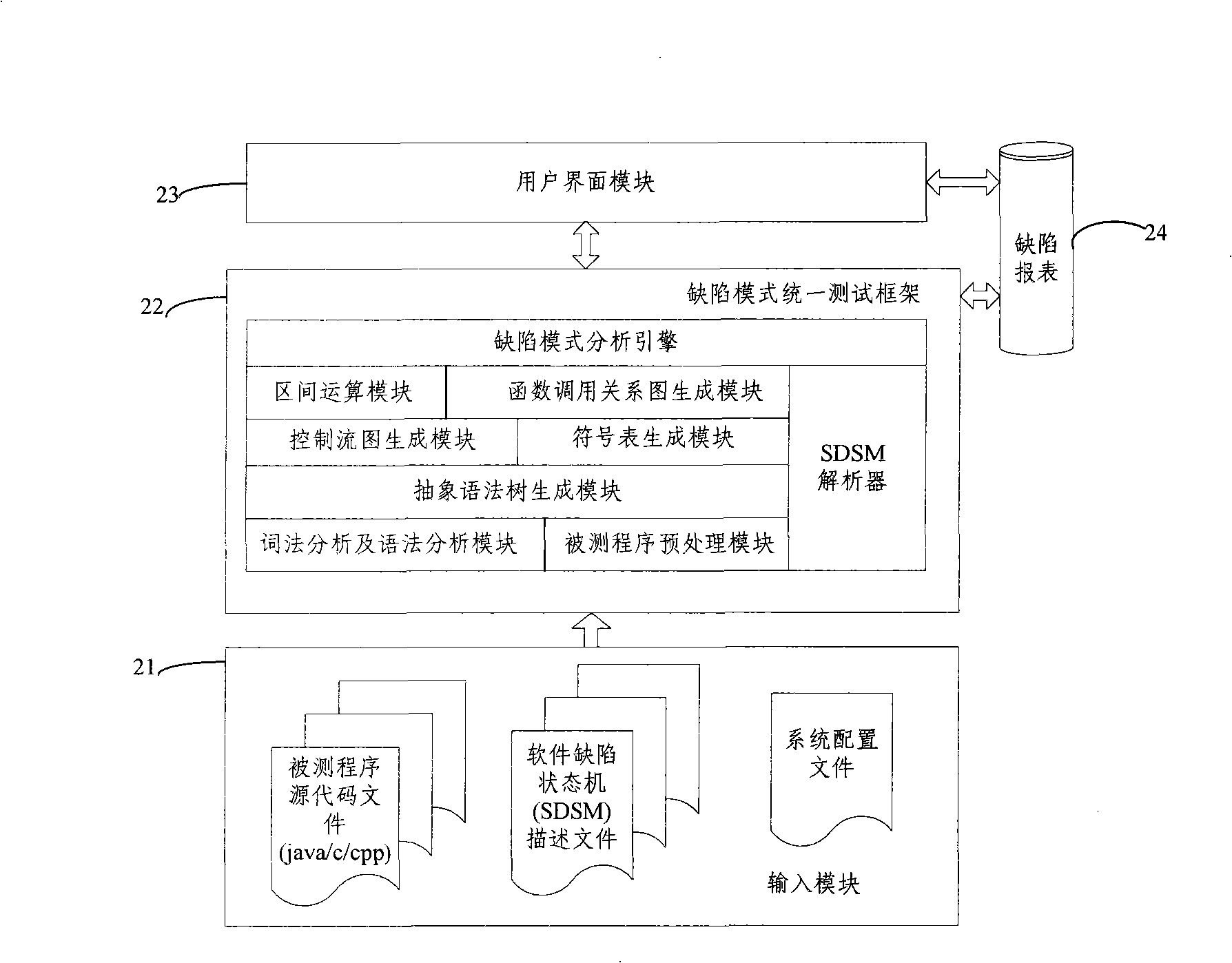
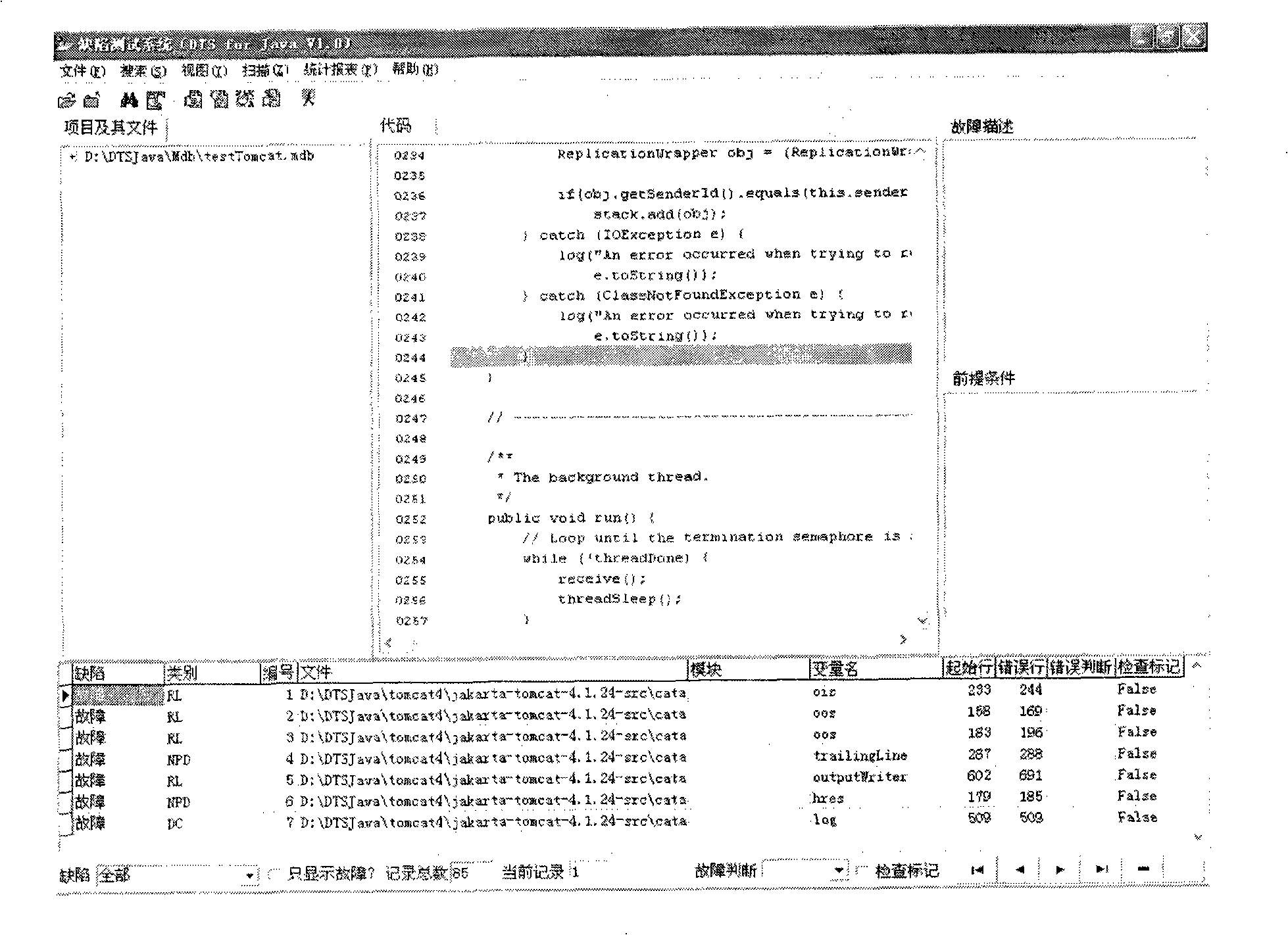
Test method and system based on software defect mode
InactiveCN101286132AReduce false positivesImprove test accuracySoftware testing/debuggingControl flowPresent method
The invention discloses a testing method based on software defect mode, comprising the steps of: reading source code files of programs to be tested and SDSM description file of a defect state machine, carrying out pre-processing of the programs to be tested, analyzing the SDSM description file; carrying out lexical analysis and grammar analysis of the programs to be tested and constructing abstract syntax tree; generating a control flow graph and a symbol table according to the abstract syntax tree and carrying out the calculating and updating of variable value interval sets according to the control flow graph and the symbol table; carrying out function invoking relation analysis of the programs to be tested and generating a function invoking relation graph; searching the control flow graph by taking the function as unit according to the function invoking relation graph, calculating the state migration of each node defect state machine on the control flow graph, and reporting corresponding checking point when the defect state machine enters the defect state. The invention also discloses a testing system based on software defect mode, which comprises an input module, a defect mode uniformity testing frame and a user interface module and completes the uniform test on the programs to be tested.
Owner:BEIJING UNIV OF POSTS & TELECOMM
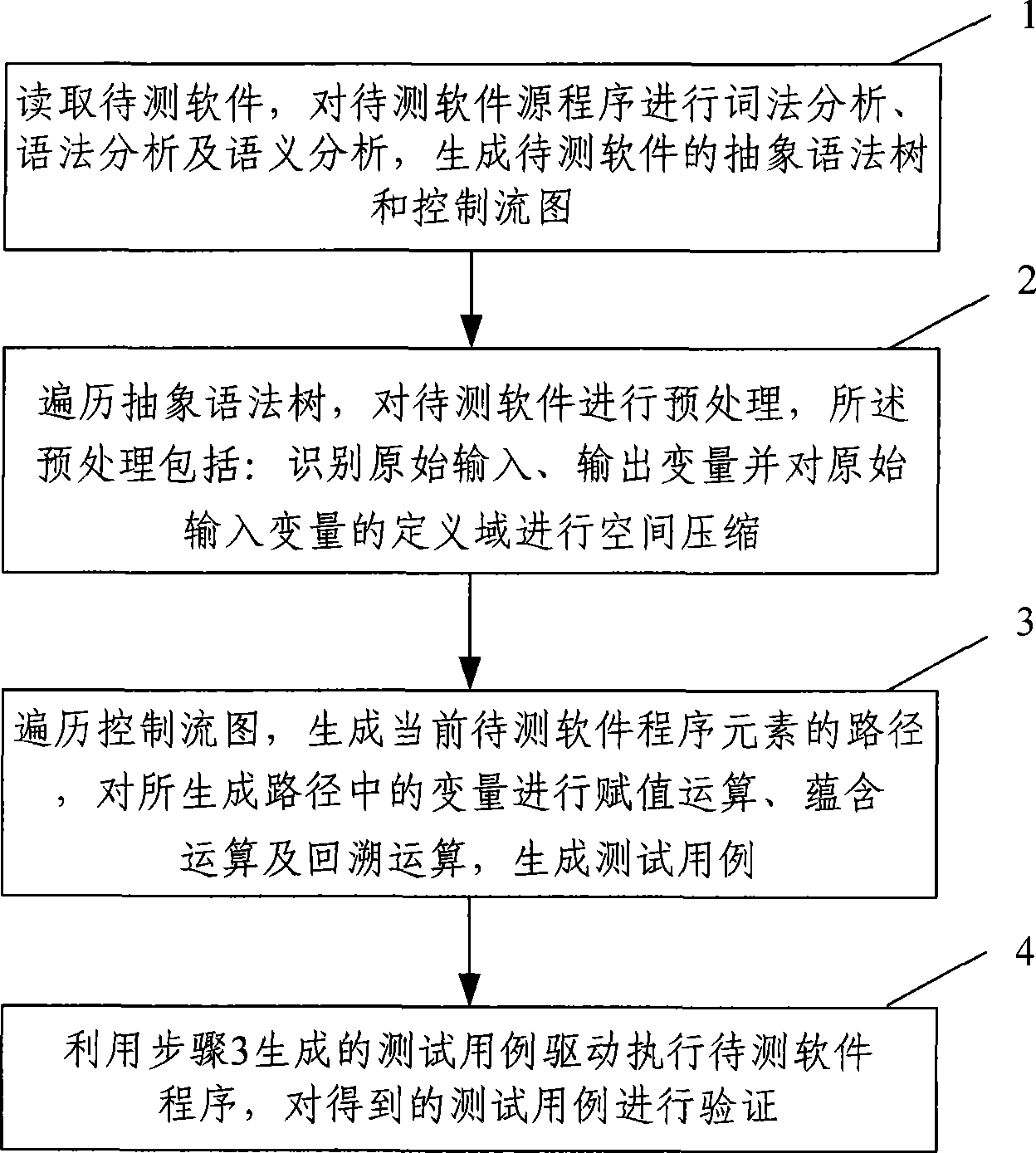
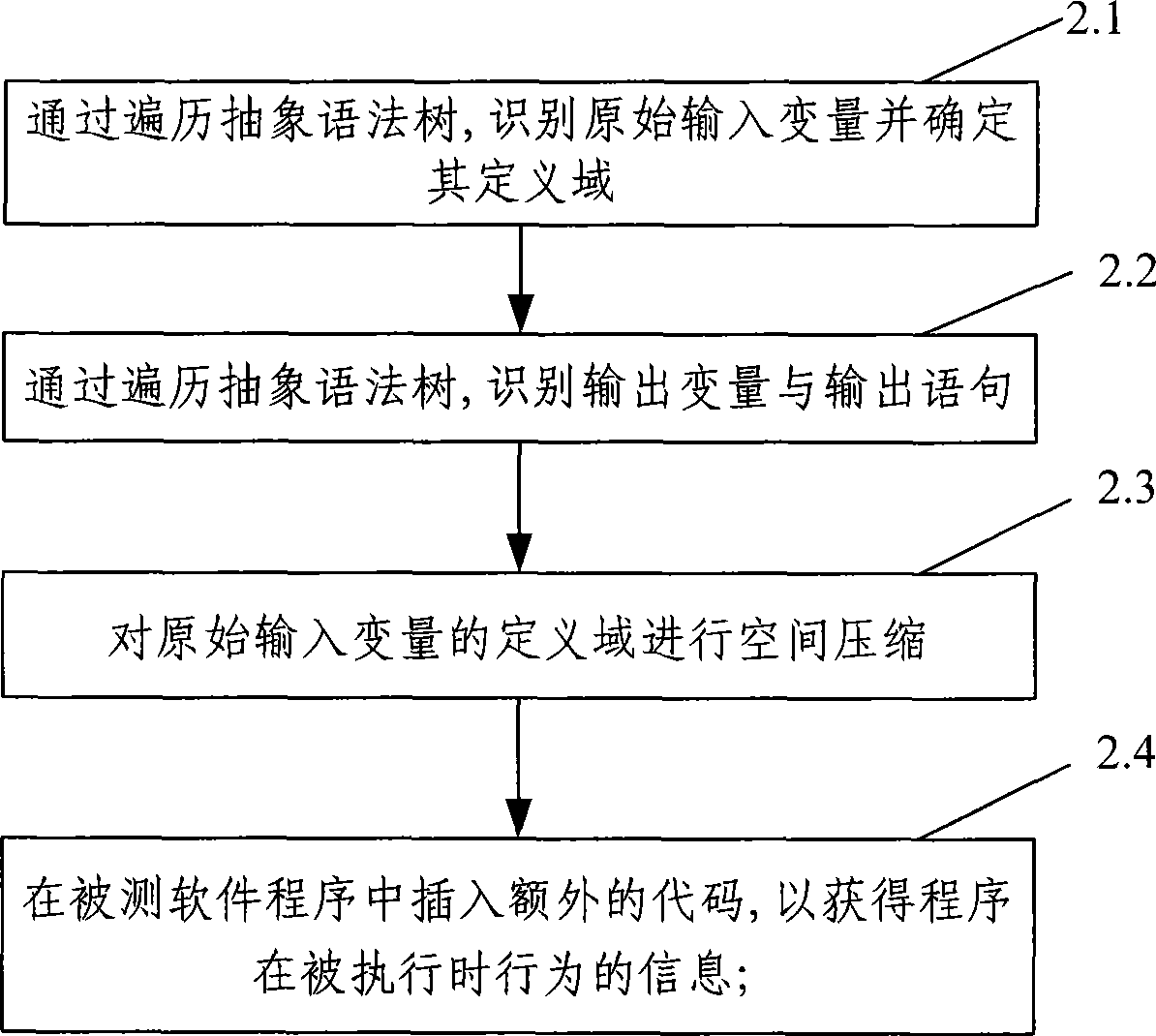
Software test case automatic generating method and system
InactiveCN101436128AImprove efficiencyHigh degree of automationSoftware testing/debuggingSpecific program execution arrangementsControl flowLexical analysis
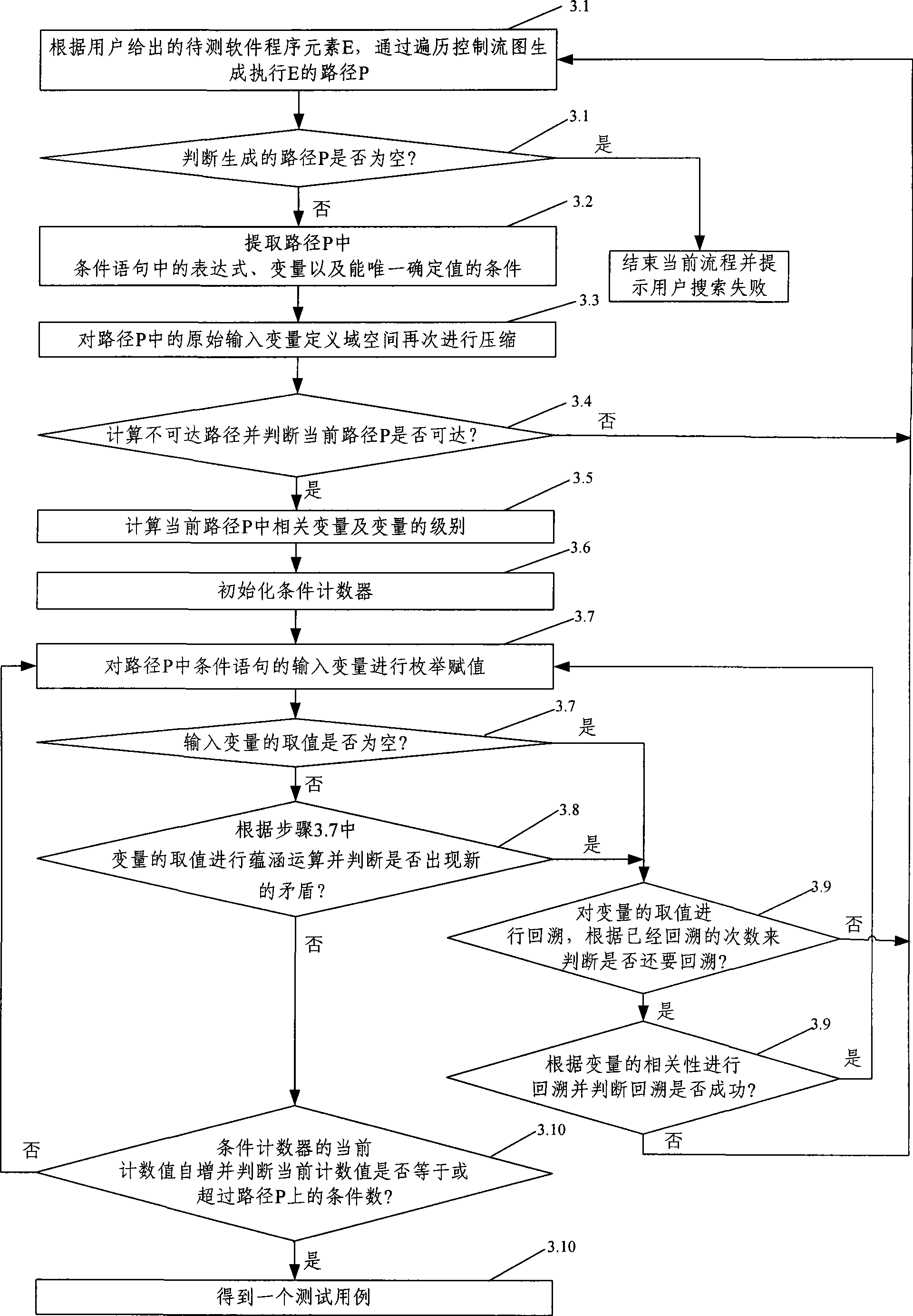
The invention provides a method for automatically generating software test cases. The method comprises the following steps of: A. reading to-be-tested software, carrying out lexical analysis, syntax analysis and semantic analysis on a source program of the to-be-tested software and generating an abstract syntax tree and a control flow graph of the to-be-tested software; B. preprocessing the source program of the to-be-tested software by traversing the generated abstract syntax tree, identifying initial input-output variables and compressing the space of a definition domain of the initial input variables; and C. generating a path of program elements of the current to-be-tested software by traversing the control flow graph, carrying out assignment operation, implication operation and backtracking operation on the variables in the path, and generating the test cases. The invention also provides a system for automatically generating software test cases. The method and the system for automatically generating the software test cases can accurately and automatically generate the test cases according to the given program elements of the to-be-tested software and verify the generated test cases, thereby improving the accuracy, efficiency and automation degree of the test cases.
Owner:BEIJING UNIV OF POSTS & TELECOMM
System and method for the parallel execution of database queries over CPUs and multi core processors
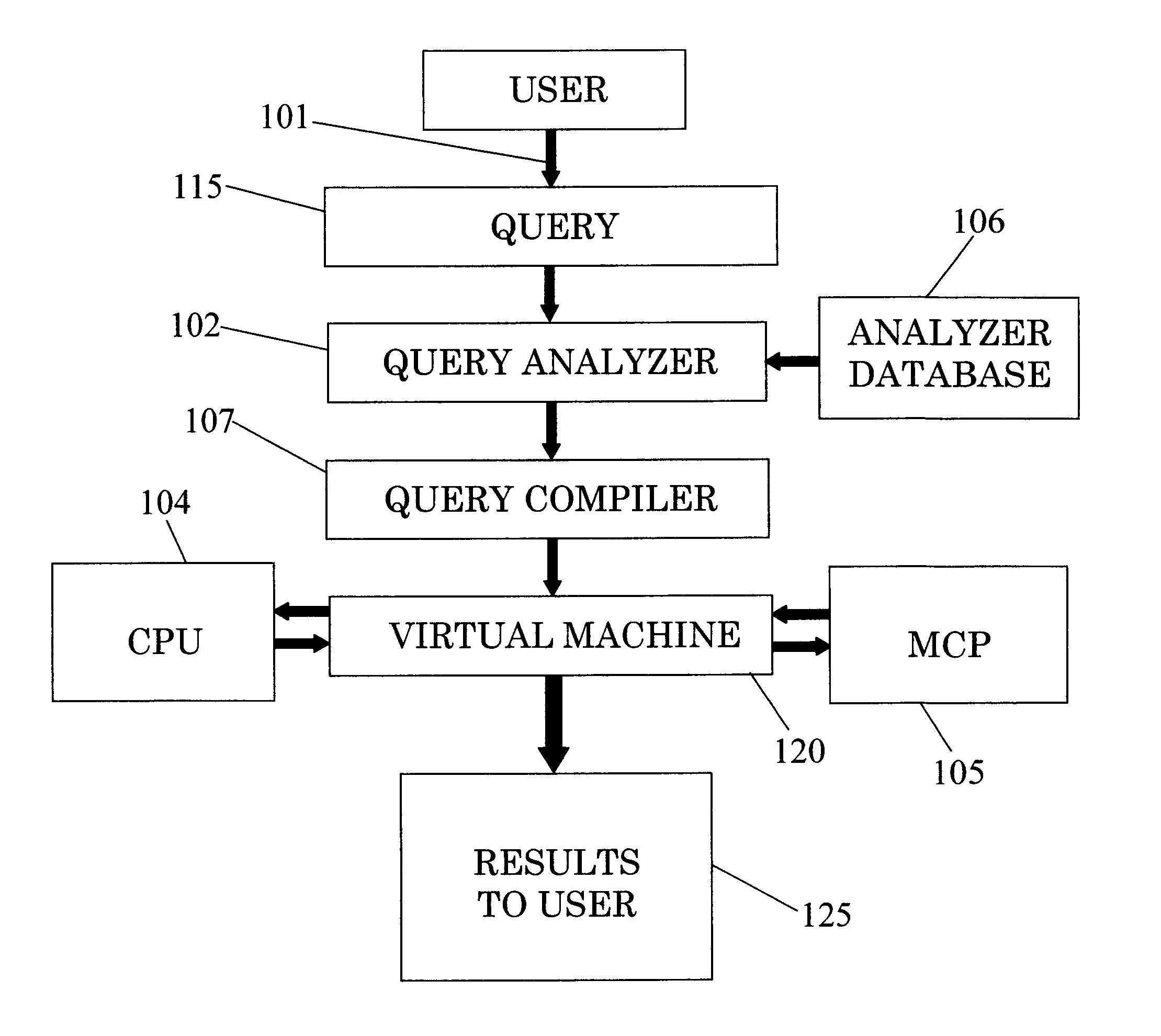
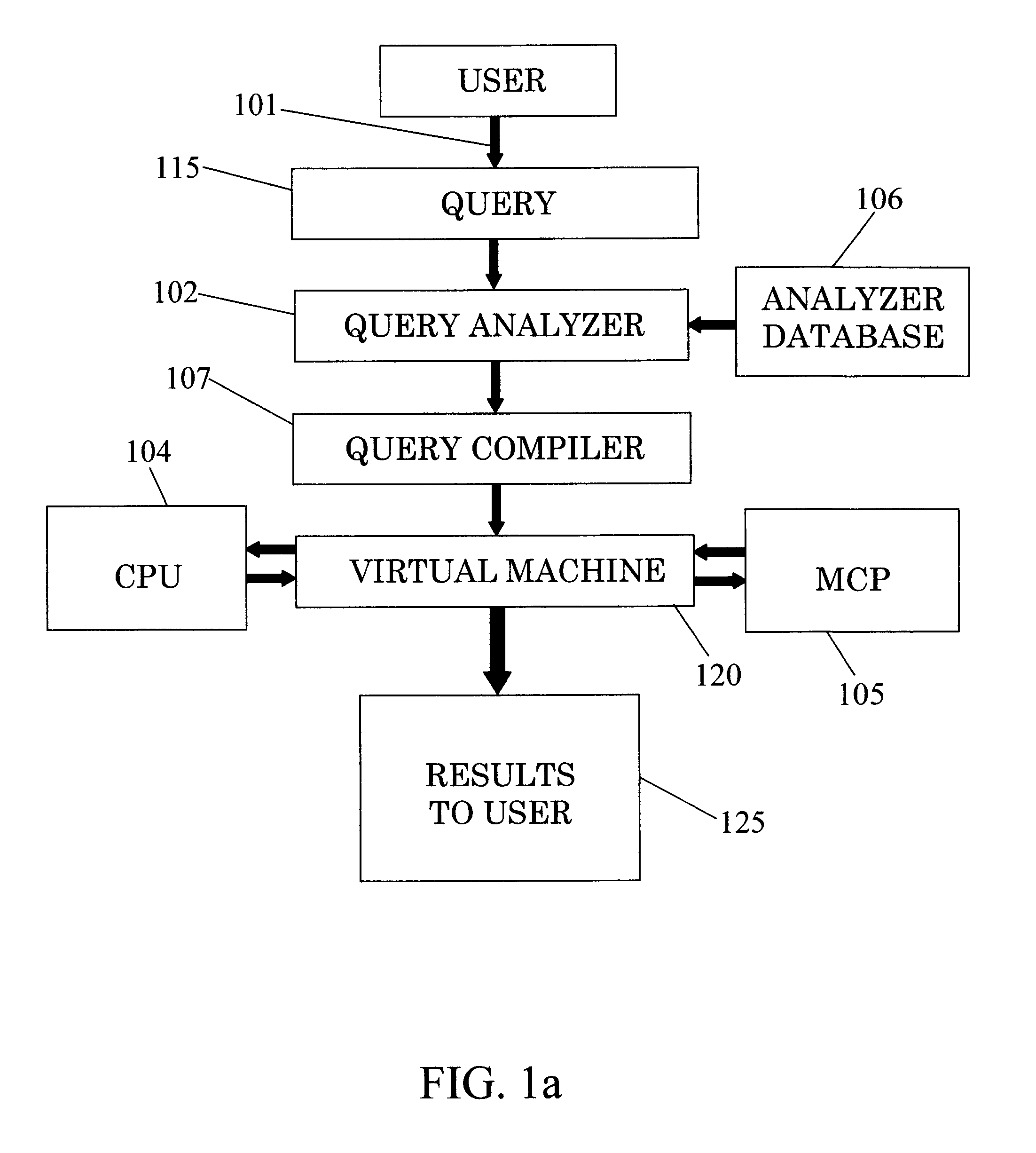
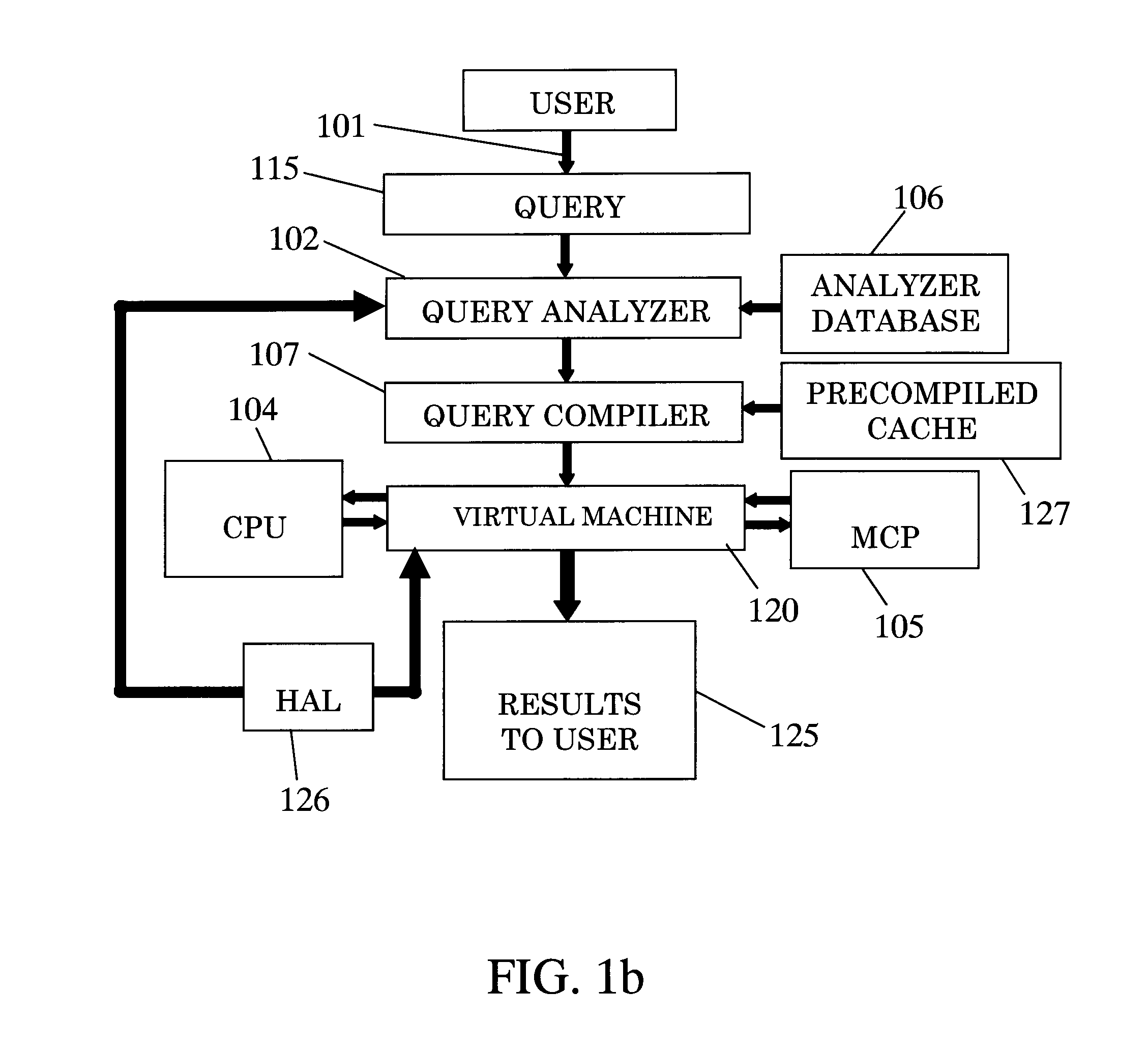
ActiveUS9298768B2DisadvantageousDigital data information retrievalResource allocationDatabase queryComputer architecture
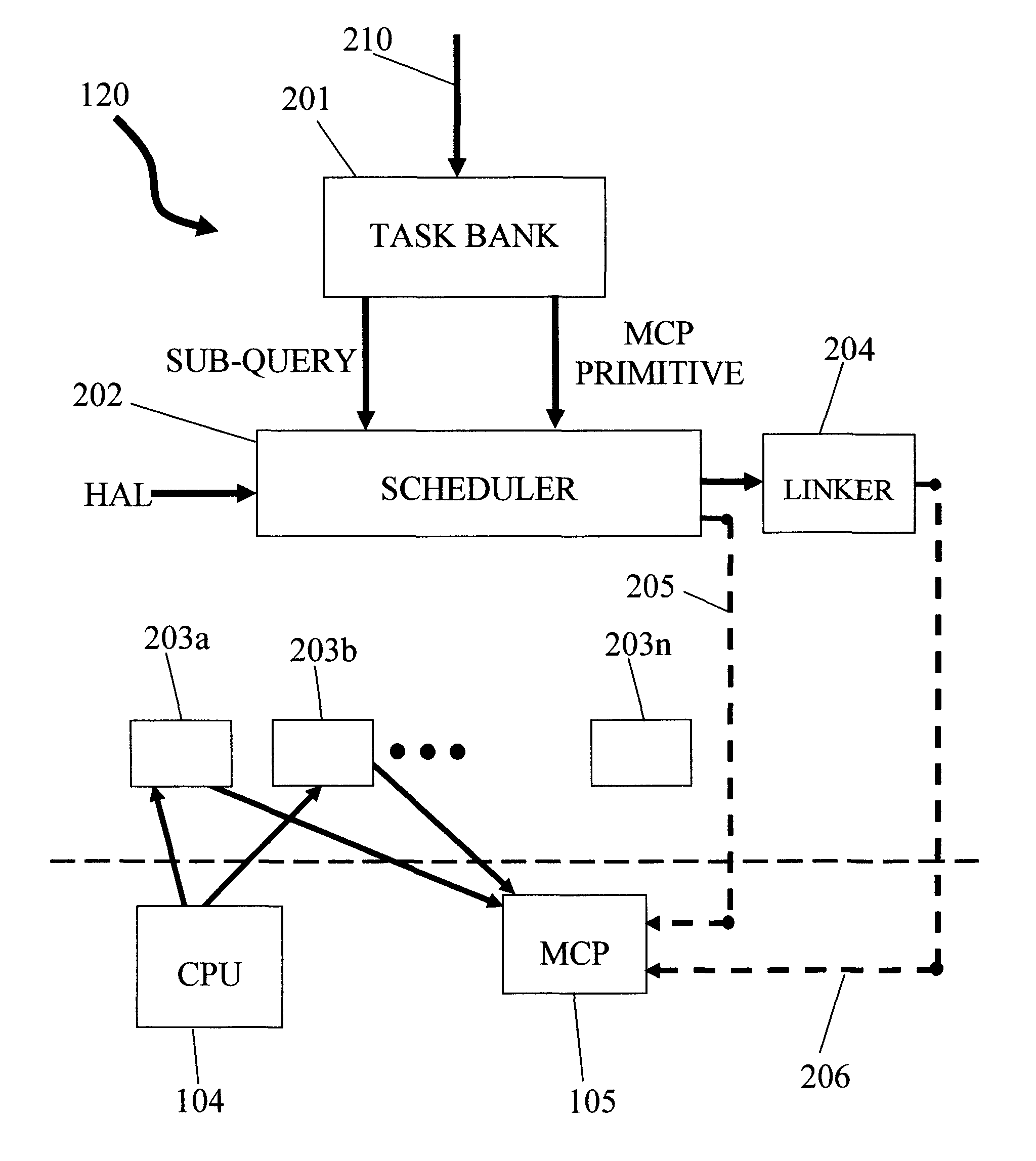
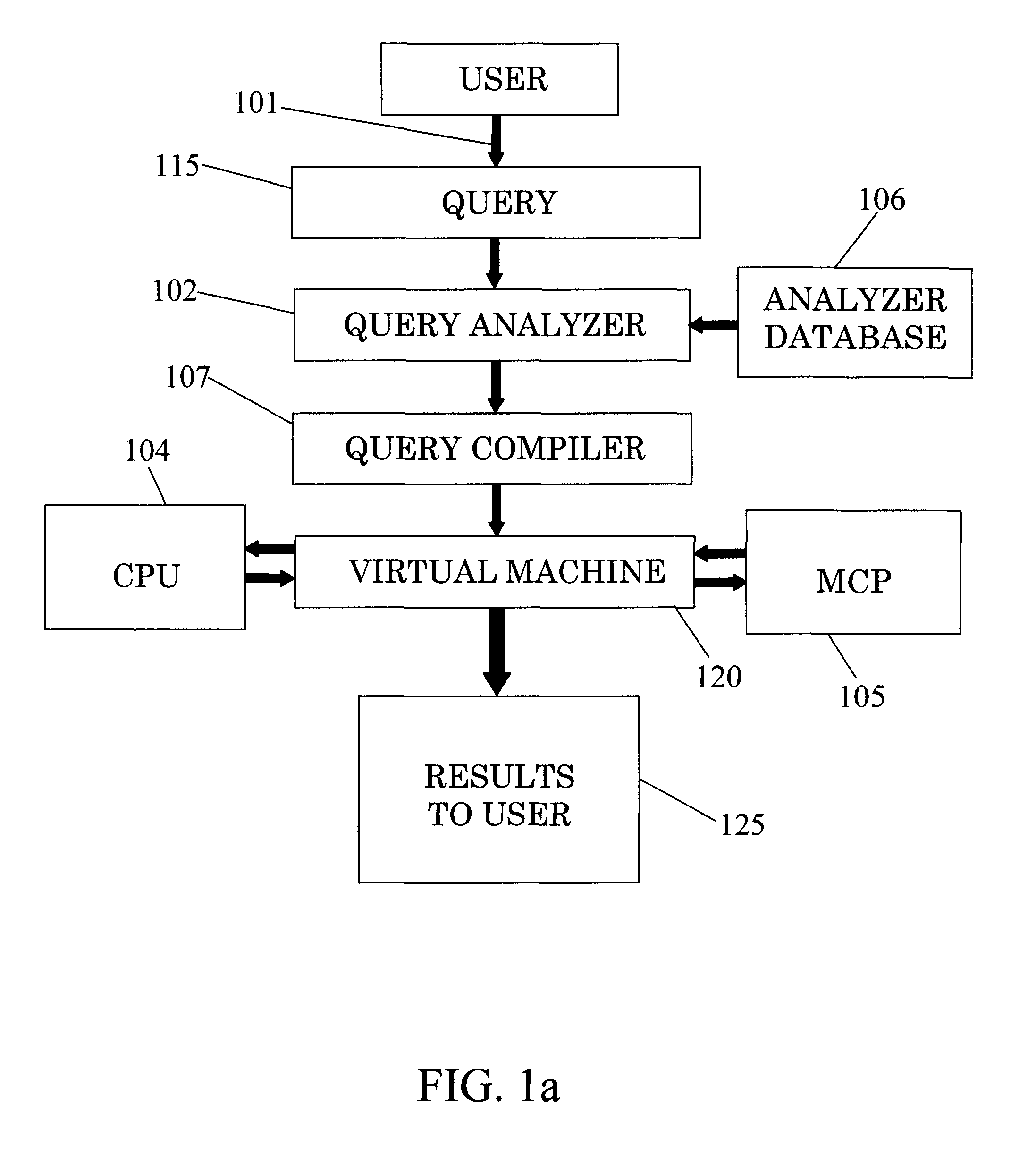
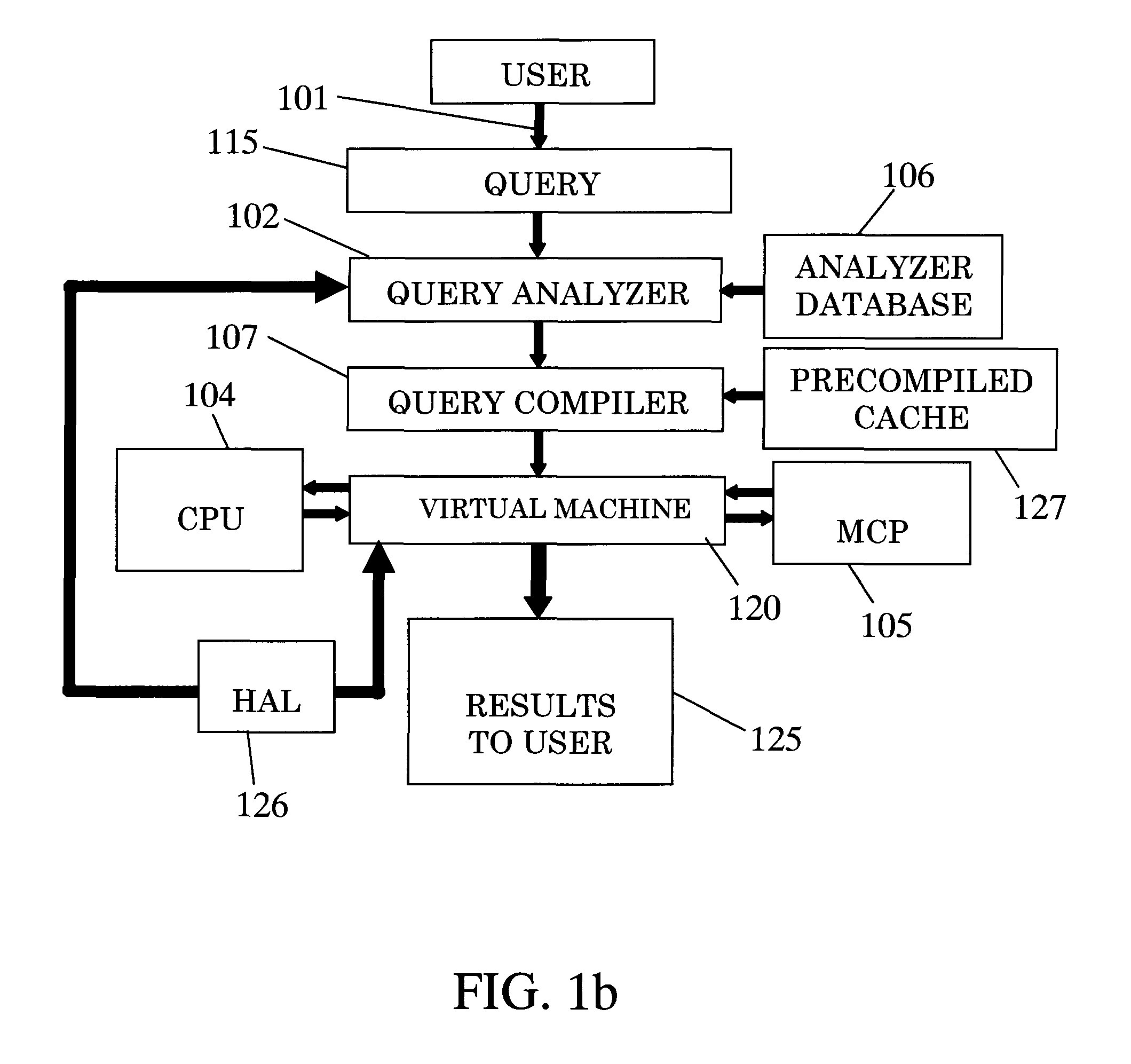
The invention relates to a system for parallel execution of database queries over one or more Central Processing Units (CPUs), and one or more Multi Core Processor, (MCPs), the system comprises (a) a query analyzer for dividing the query to plurality of sub-queries, and for computing and assigning to each sub-query a target address of either a CPU of an MCP; (b) a query compiler for creating an Abstract Syntax Tree (AST) and OpenCL primitives only for those sub-queries that are targeted to an MCP, and for conveying both the remaining sub-queries, and the AST and the OpenCL code to a virtual machine, and (A) a Virtual Machine (VM) which comprises: a task bank, a buffers; a scheduler. The virtual machine combines said sub-query results by the CPUs and said primitive results by said MCPs to a final query result.
Owner:SQREAM TECH
System and Method for the Parallel Execution of Database Queries Over CPUs and Multi Core Processors
ActiveUS20130117305A1Less energyIncrease clock frequencyDigital data information retrievalDigital data processing detailsDatabase queryQuery analysis
The invention relates to a system for parallel execution of database queries over one or more Central Processing Units (CPUs), and one or more Multi Core Processor, (MCPs), the system comprises (a) a query analyzer for dividing the query to plurality of sub- queries, and for computing and assigning to each sub-query a target address of either a CPU of an MCP; (b) a query compiler for creating an Abstract Syntax Tree (AST) and OpenCL primitives only for those sub-queries that are targeted to an MCP, and for conveying both the remaining sub-queries, and the AST and the OpenCL code to a virtual machine, and (A) a Virtual Machine (VM) which comprises: a task bank, a buffers; a scheduler. The virtual machine combines said sub-query results by the CPUs and said primitive results by said MCPs to a final query result.
Owner:SQREAM TECH
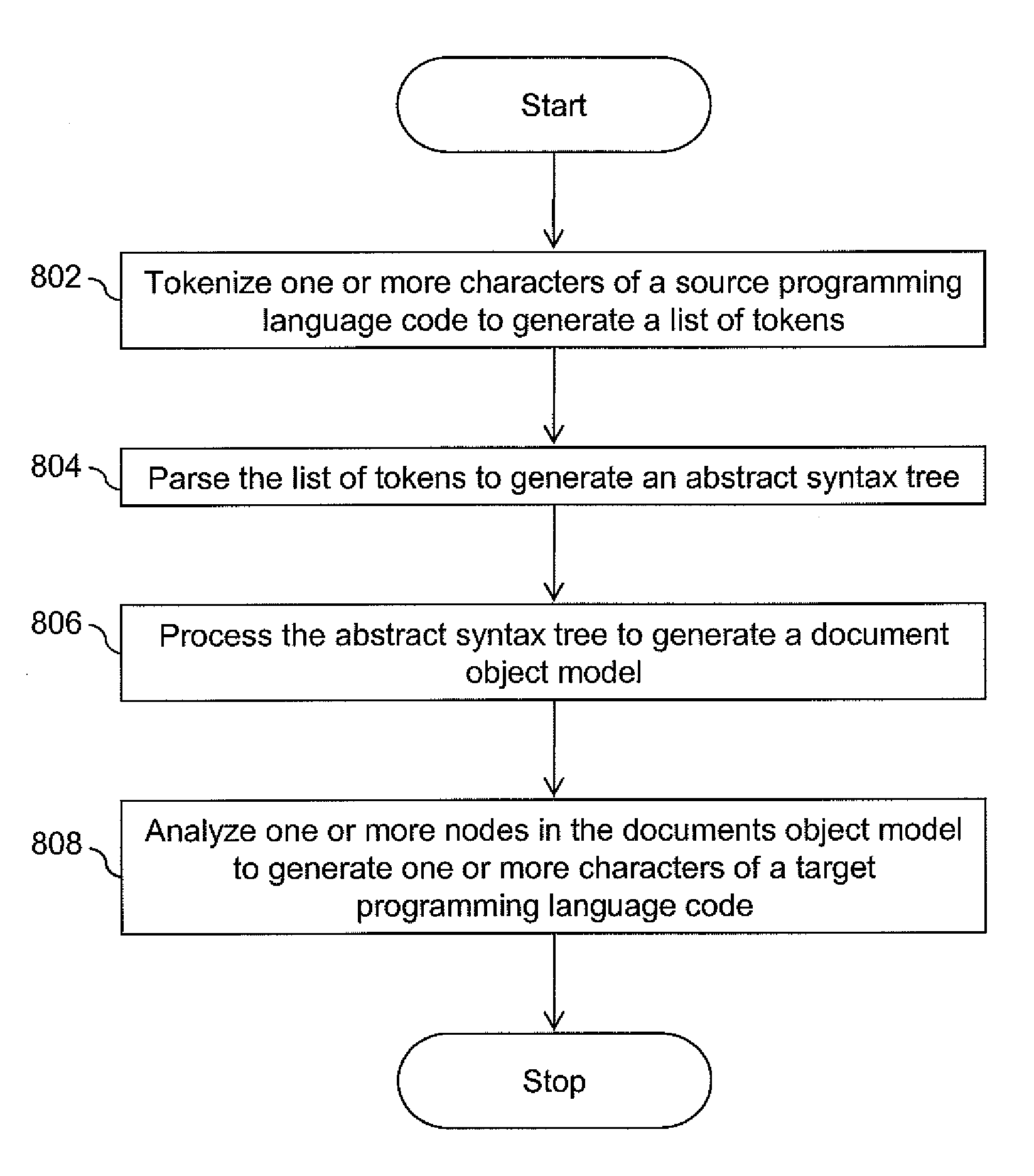
Methods and Apparatus for Automatic Translation of a Computer Program Language Code
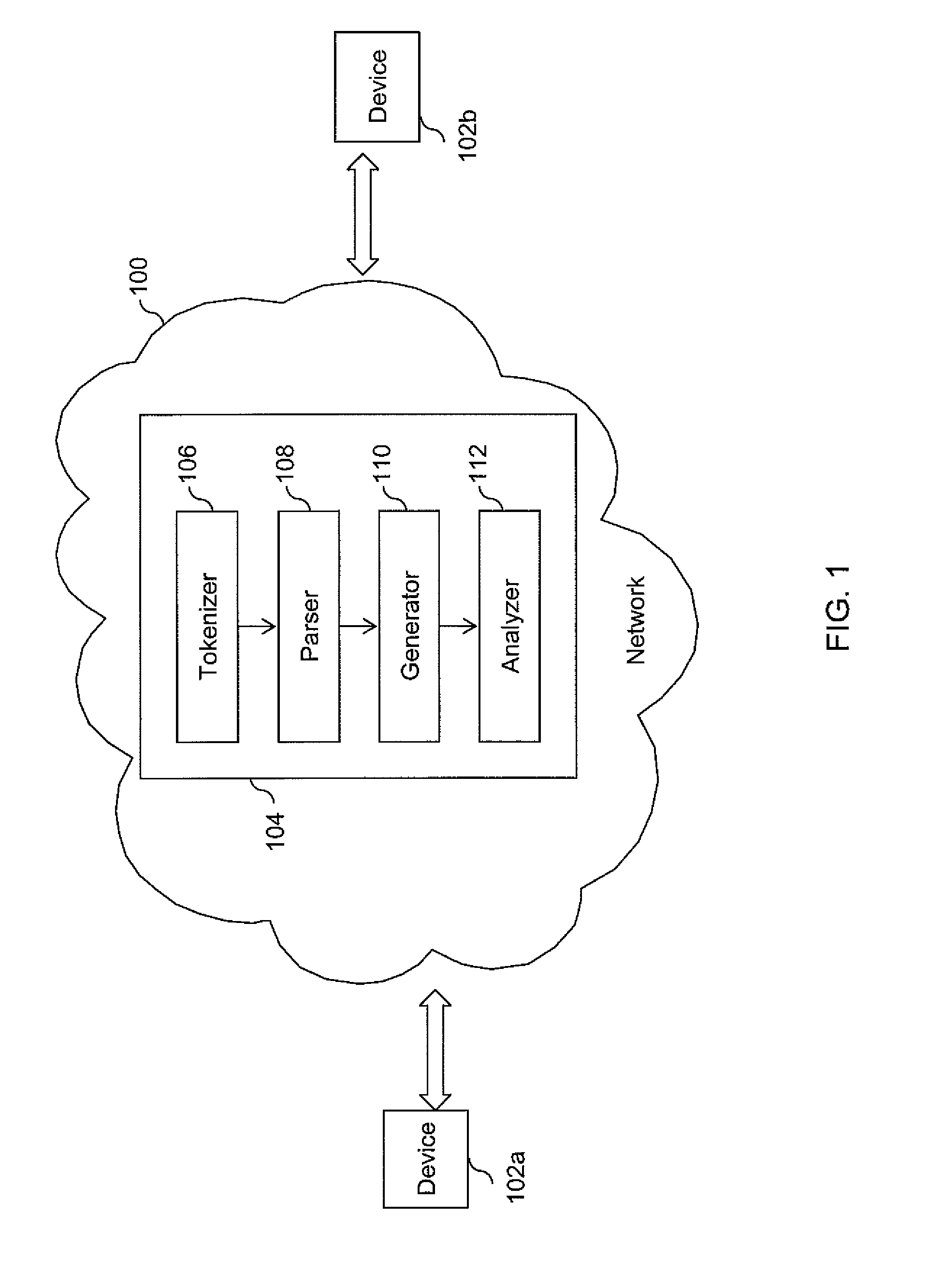
Embodiments of the methods and apparatus for automatic cross language program code translation are provided. One or more characters of a source programming language code are tokenized to generate a list of tokens. Thereafter, the list of tokens is parsed to generate a grammatical data structure comprising one or more data nodes. The grammatical data structure may be an abstract syntax tree. The one or more data nodes of the grammatical data structure are processed to generate a document object model comprising one or more portable data nodes. Subsequently, the one or more portable data nodes in the document object model are analyzed to generate one or more characters of a target programming language code.
Owner:XENOGENIC DEV LLC
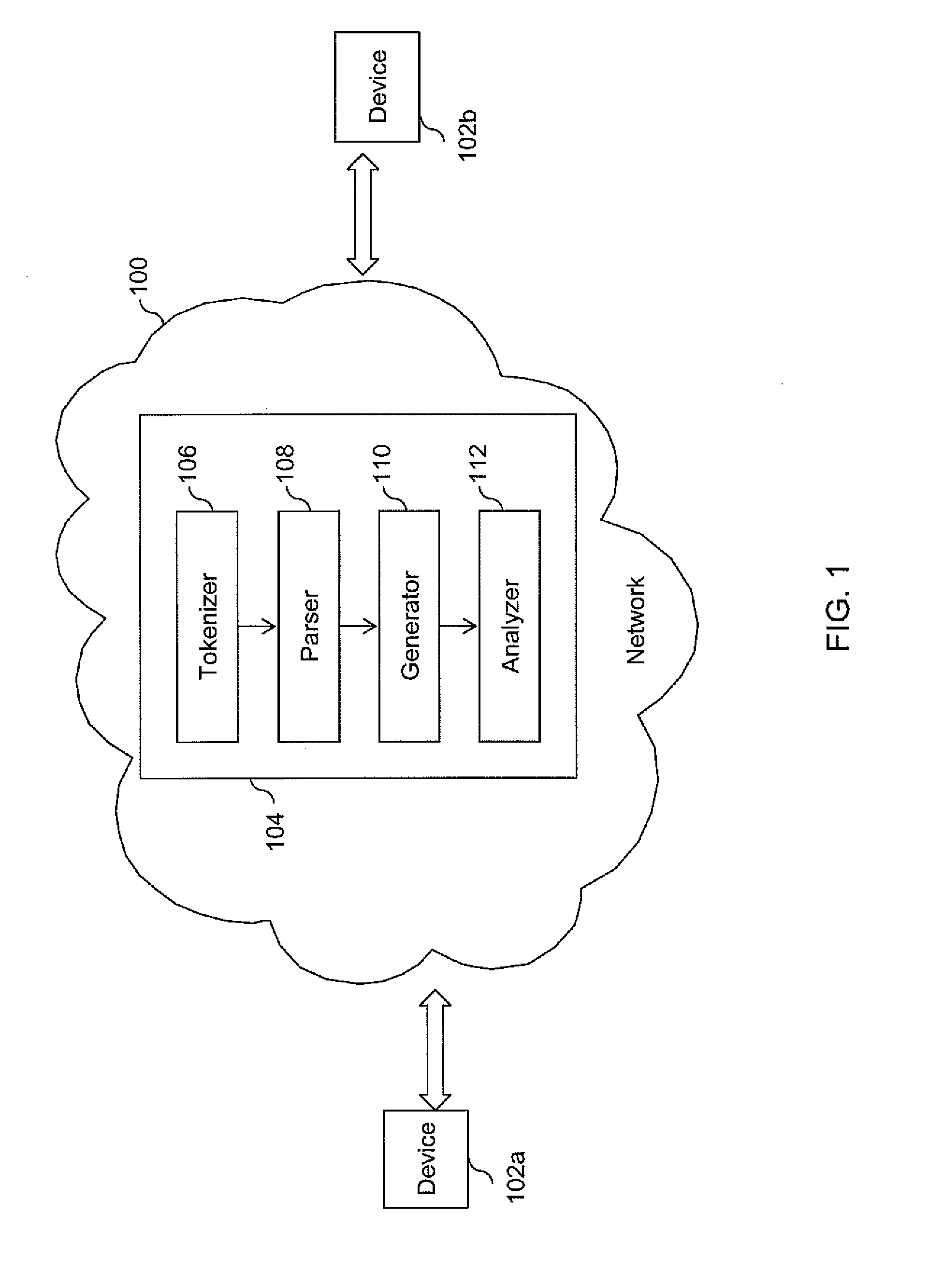
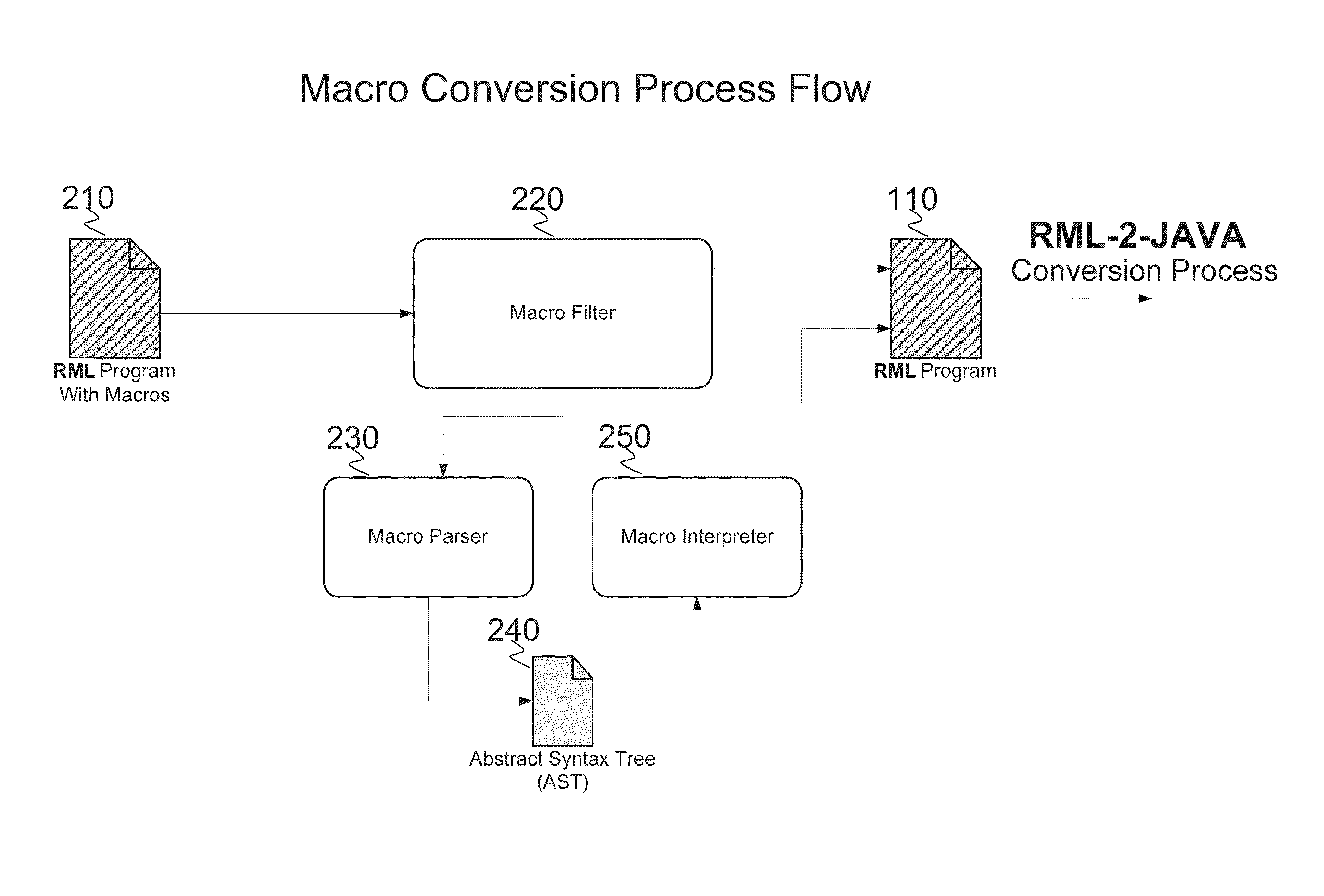
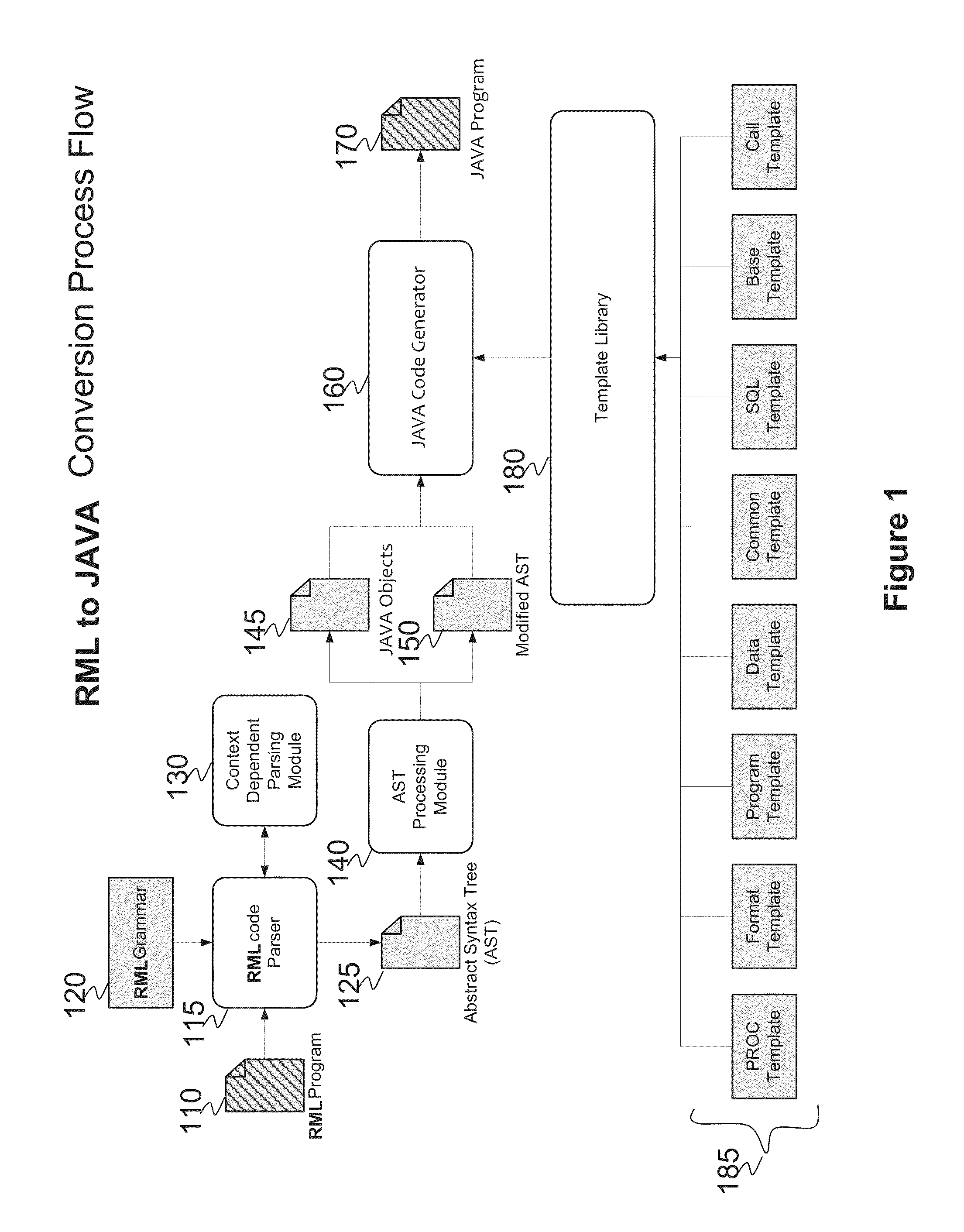
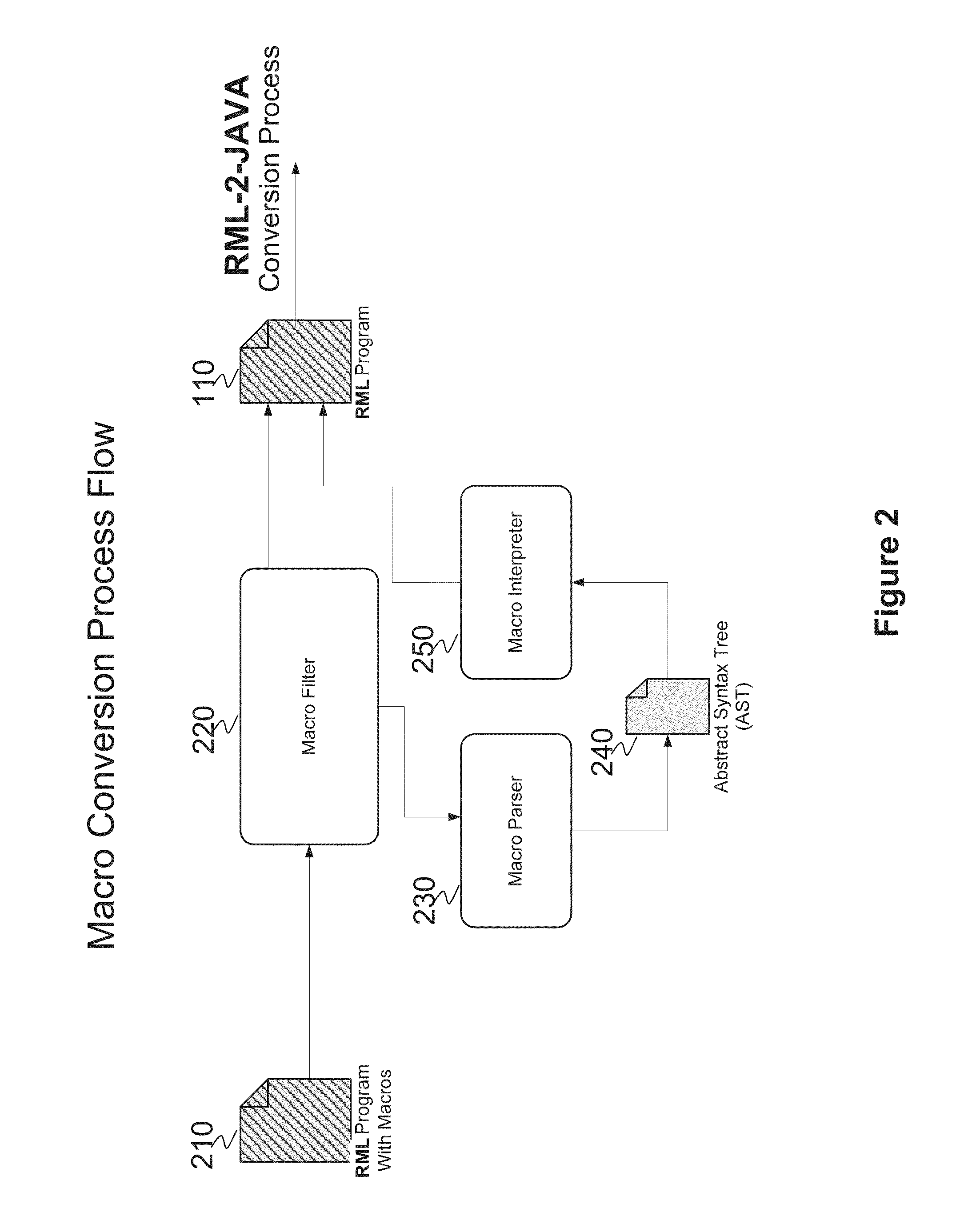
System and method for converting base SAS runtime macro language scripts to JAVA target language
ActiveUS8453126B1Overcome incidenceOvercome the impactProgram controlMemory systemsControl flowLexical analysis
A system and method for automated conversion of a SAS runtime macro language (RML) program to a target language program such as JAVA. RML macros are identified and converted for inclusion in the RML program. A lexer is applied to generate a stream of tokens, including a token type for ambiguous tokens. A context dependent parsing module, including a token filter to resolve ambiguous tokens, assists the parser in generating an abstract syntax tree (AST), which is modified to express RML specific control flow constructs with target language program elements. The elements of the modified AST are replaced with target language templates from a library, with template parameters filled from the corresponding AST element. A run time library is provided for execution of the target language program.
Owner:DULLES RES
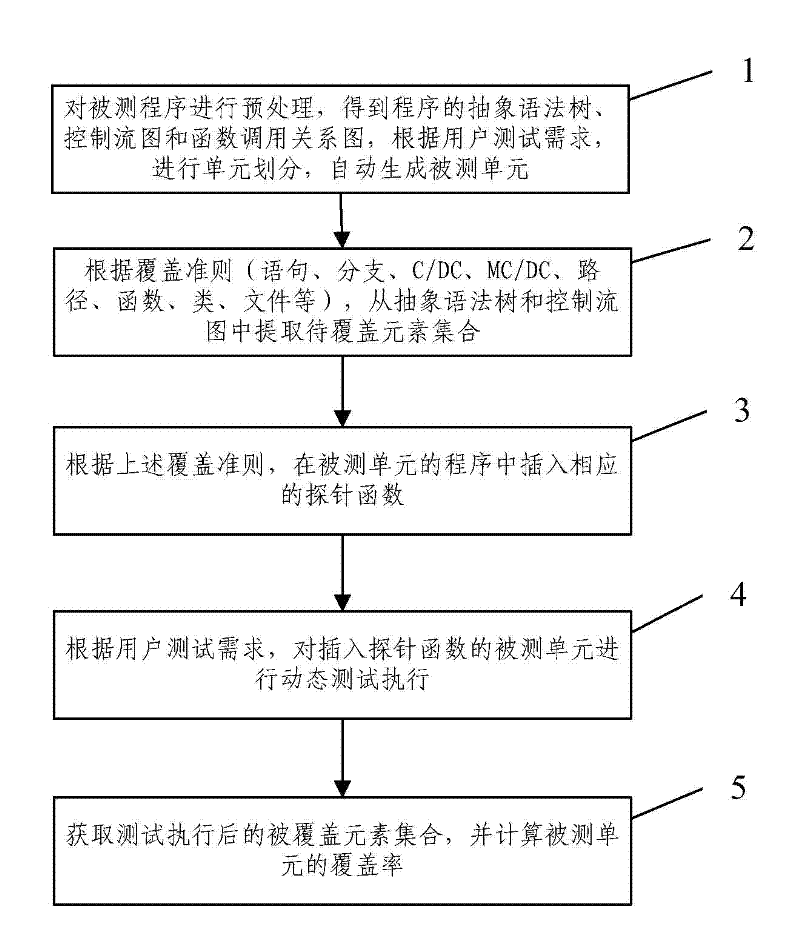
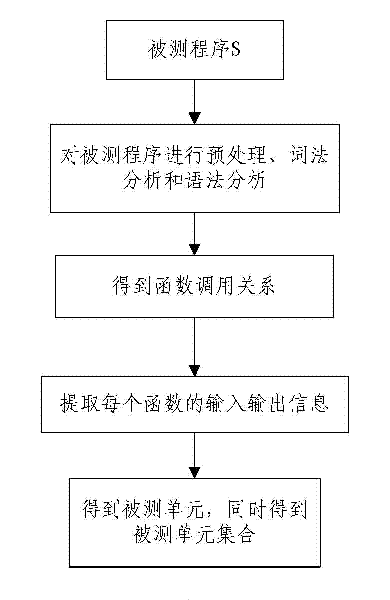
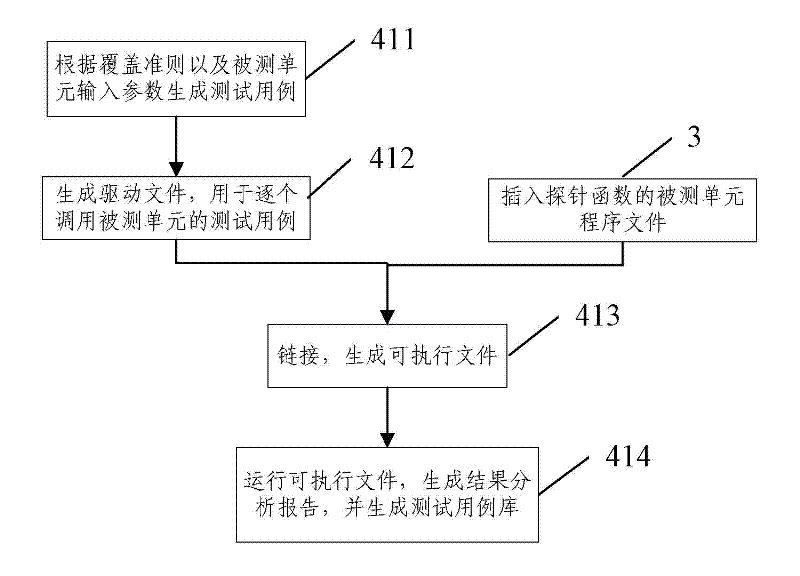
Method for determining software test process sufficiency based on coverage rate quantitative indicators
InactiveCN102419728AImprove efficiencyImprove accuracySoftware testing/debuggingAlgorithmLexical analysis
The invention provides a method for determining software test process sufficiency based on coverage rate quantitative indicators. The method comprises the following steps of: A, performing precompilation, lexical analysis and syntax analysis on a tested program to acquire the calling relationship diagram of the abstract syntax tree, the control flow graph and the function of the program, and automatically generating a tested unit according to the test requirement of a user; B, extracting a corresponding element set to be covered in the tested unit from the abstract syntax tree and the control flow graph according to a coverage criterion; C, inserting a corresponding probe function into the program of the tested unit according to the coverage criterion; D, dynamically testing the tested unit into which the probe function is inserted by selecting a system automatic executing mode or a user manual executing mode according to the test requirement of the user; and E, acquiring the covered element set of the tested unit according to the returned information of dynamic test execution, and calculating the coverage rate of the tested unit. By the method, the efficiency and the accuracy of a software evaluation test can be improved.
Owner:BEIJING UNIV OF POSTS & TELECOMM
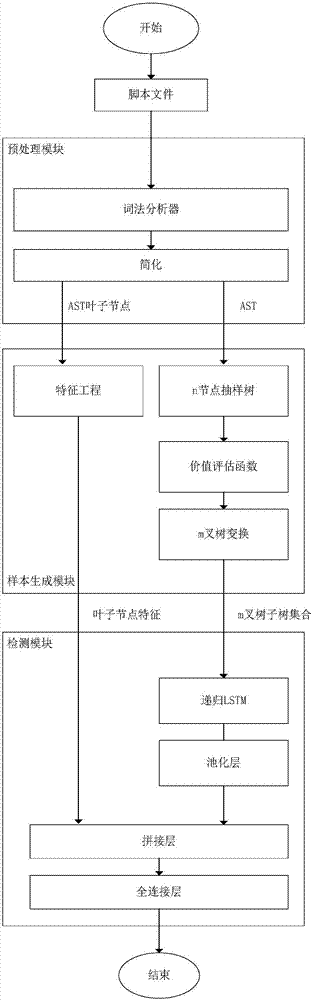
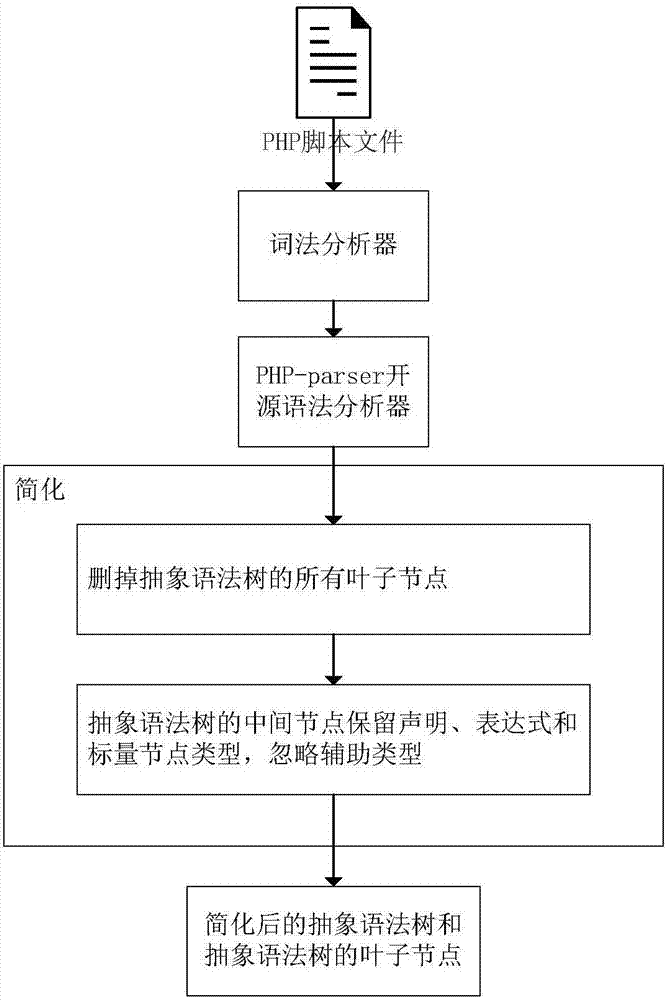
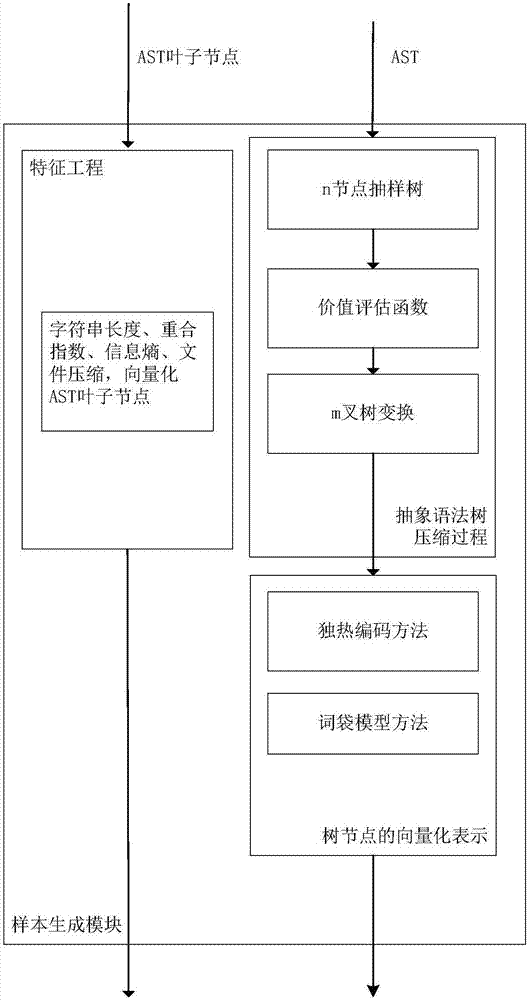
Webshell detection method based on deep neural network, and system thereof
ActiveCN107516041AImprove portabilityRespond effectivelySoftware testing/debuggingPlatform integrity maintainanceScripting languageTheoretical computer science
The invention discloses a Webshell detection method based on a deep neural network, and a system thereof. A recursion loop neural network based on an abstract syntax tree automatically obtains the morphology and grammar information of a script by aiming at a script language, the hierarchical structure characteristics of the abstract syntax tree is used for finishing feature abstraction and WebShell detection, including preprocessing, sample generation and WebShell detection; firstly, the morphology and grammar information of the script is automatically obtained, and then, the recursion loop neural network based on the abstract syntax tree is used for finishing the feature abstraction and the WebShell detection. The method disclosed by the invention has the advantages of being low in deployment cost, good in portability and high in detection accuracy.
Owner:BEIJING ANPRO INFORMATION TECH
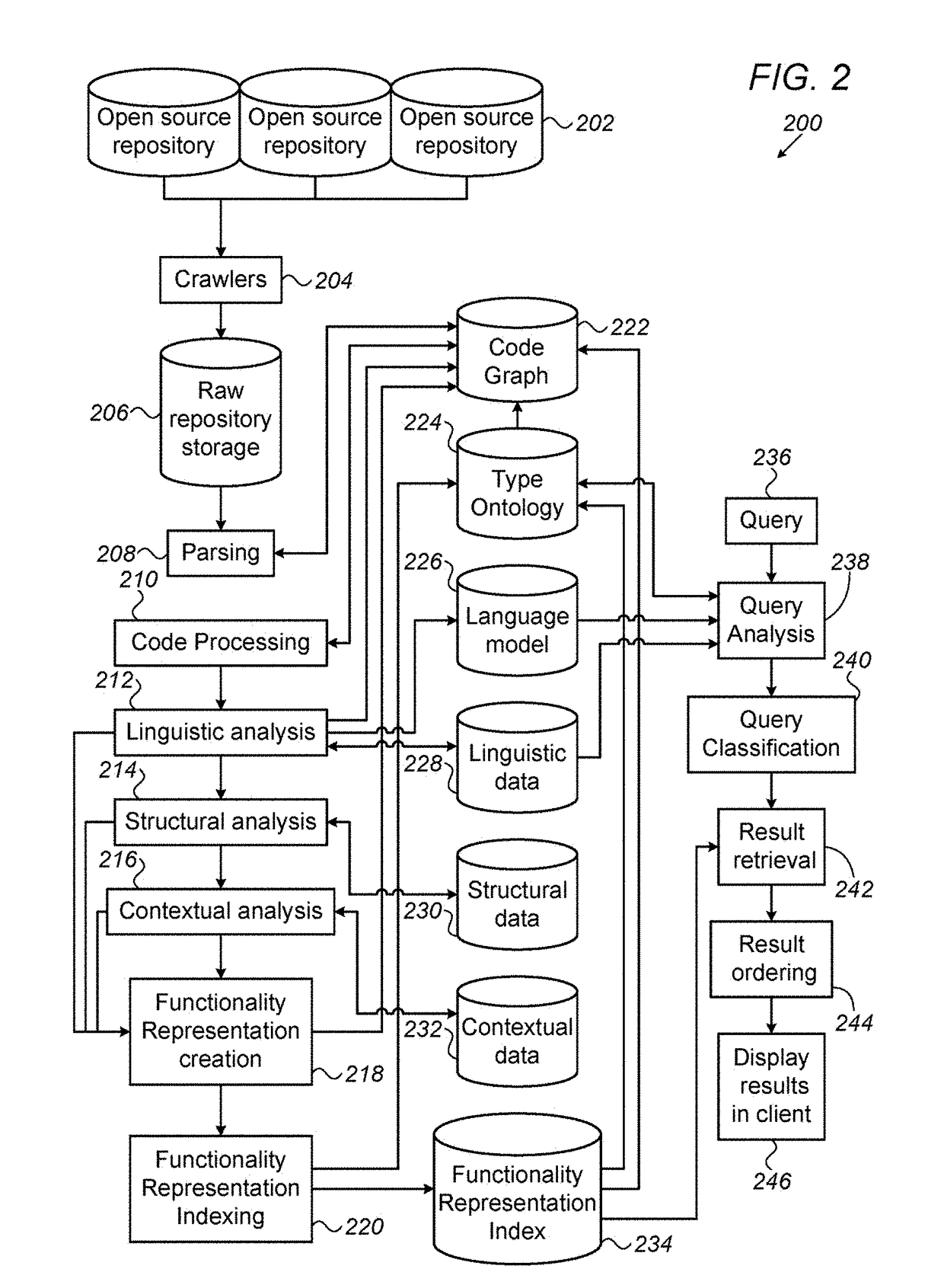
System for generating functionality representation, indexing, searching, componentizing, and analyzing of source code in codebases and method thereof
ActiveUS20180373507A1Raise the possibilityMathematical modelsWeb data indexingAbstract syntax treeData entity
Owner:COCYCLES
Method for transforming first code instructions in a first programming language into second code instructions in a second programming language
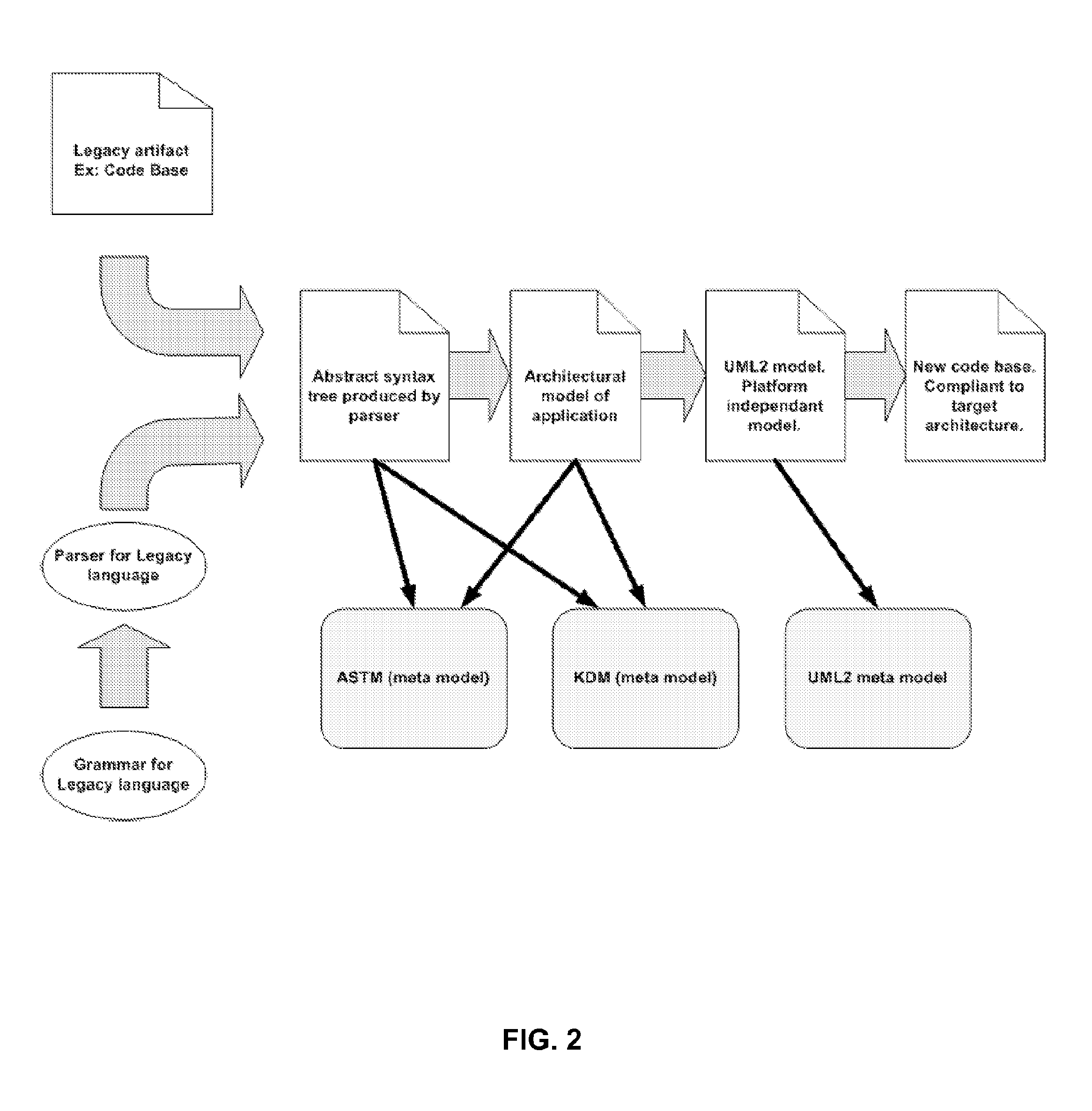
ActiveUS20160062753A1Function increaseProgram controlMemory systemsPattern matchingVisual programming language
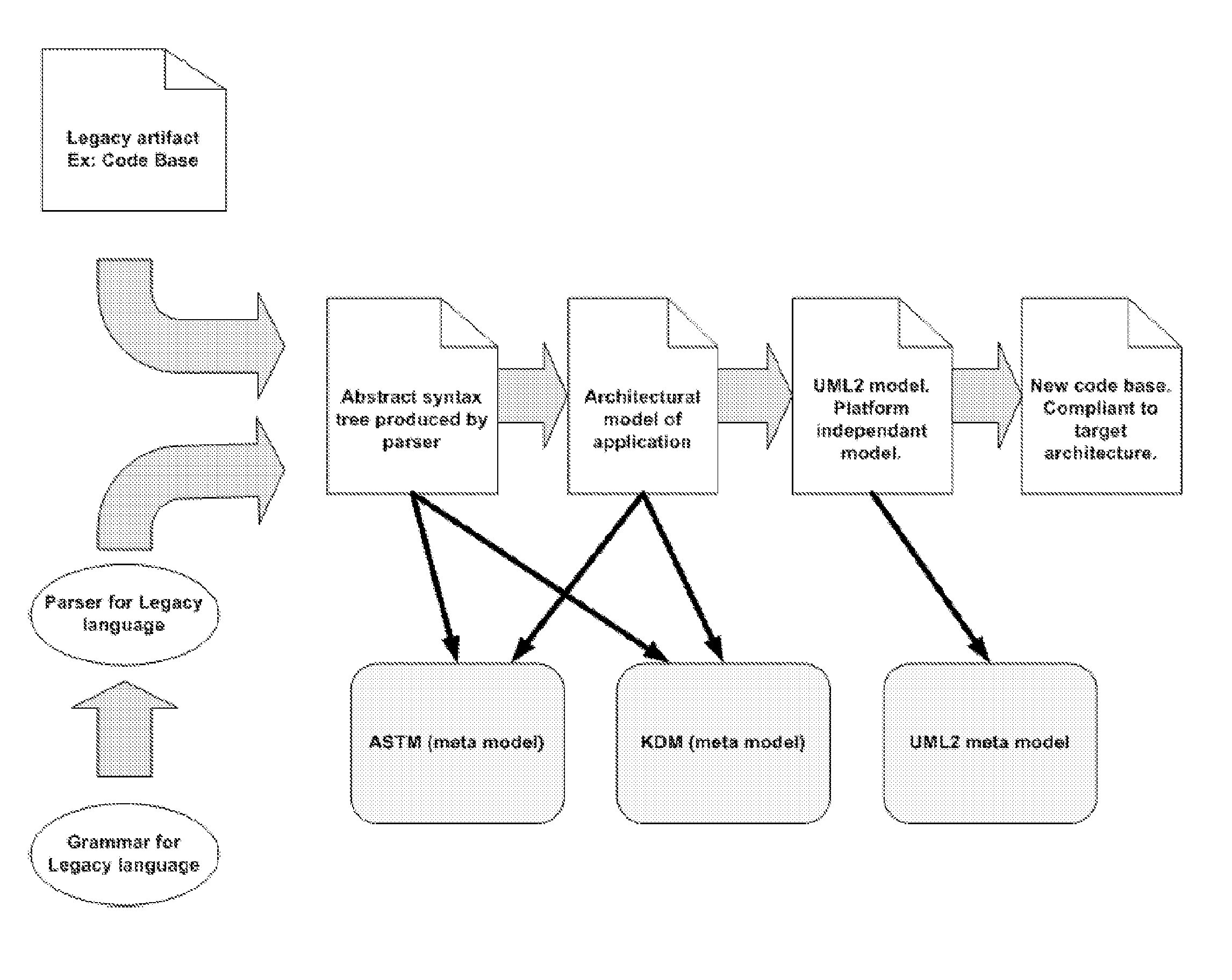
The present invention relates to a method for transforming first code instructions in a first programming language into second code instructions in a second programming language, characterized in that it comprises performing at a processing unit (11) steps of: (a) parsing the first code instructions according to semantic rules of the first programming language so as to generate an abstract syntax tree of the first code instructions; (b) mapping the abstract syntax tree into an architectural model of the first code in a knowledge description language; (c) analysing the architectural model so as to identify design patterns representative of elementary software functions of the first code instructions; (d) enriching the architectural model with semantic tags determined in function of the design patterns identified and pattern matching rules, the semantic tags resolving semantic ambiguity within the architectural model; (e) transforming the tagged architectural model into model in a software modelling language independent from the first and second programming languages; (f) generating the second code instructions in the second language from the software modelling language. The present invention also relates to a system for carrying out said method.
Owner:NETFECTIVE TECH
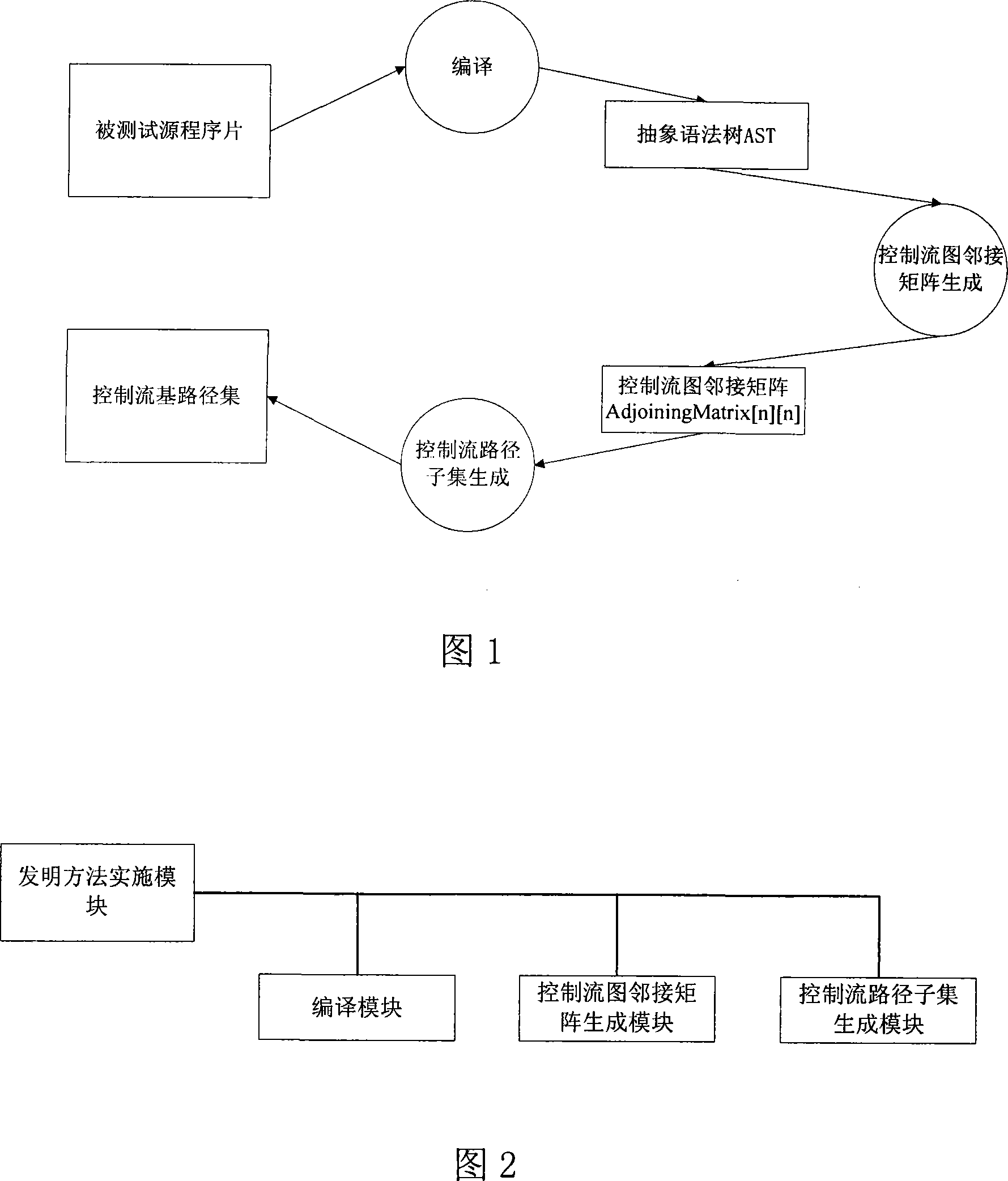
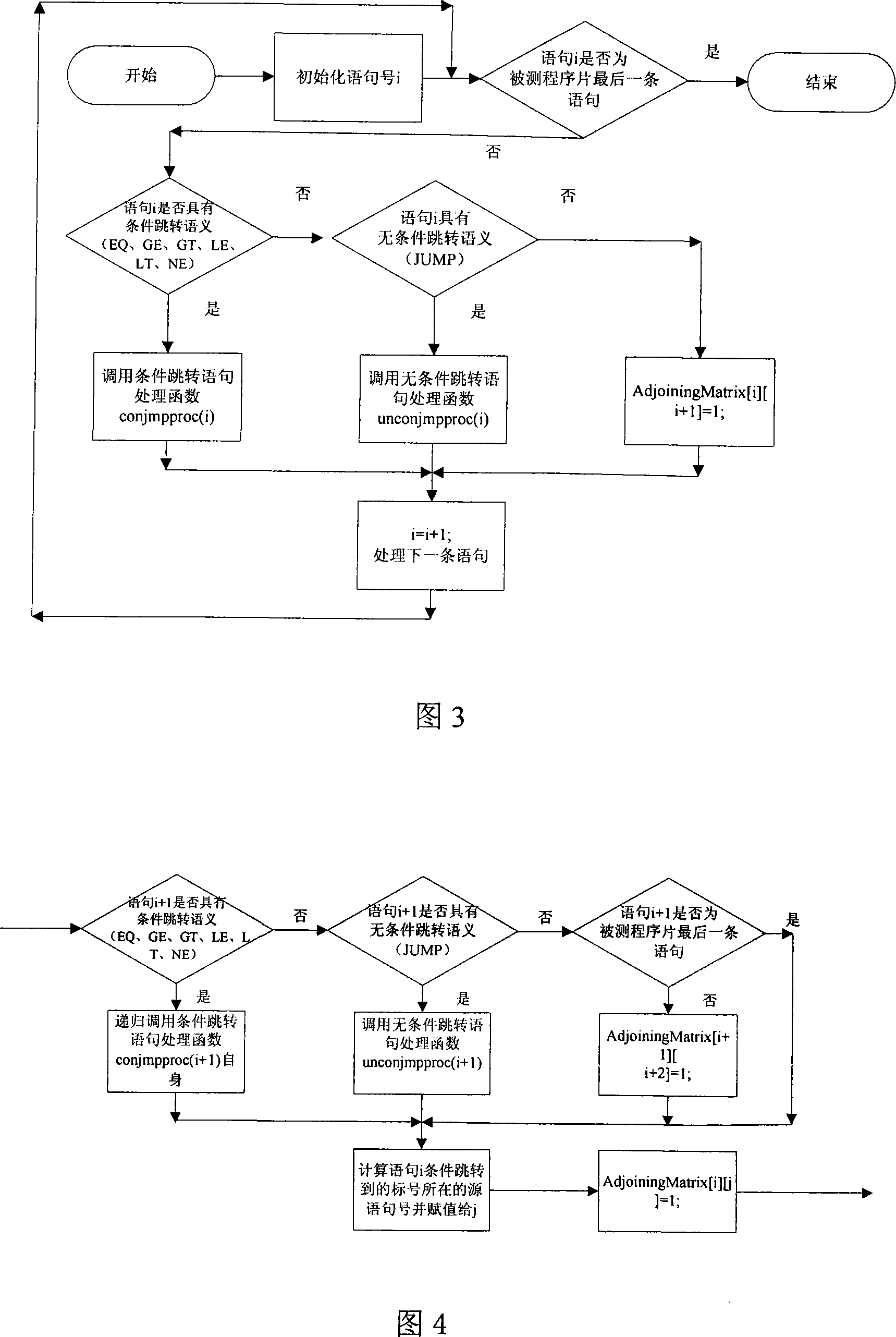
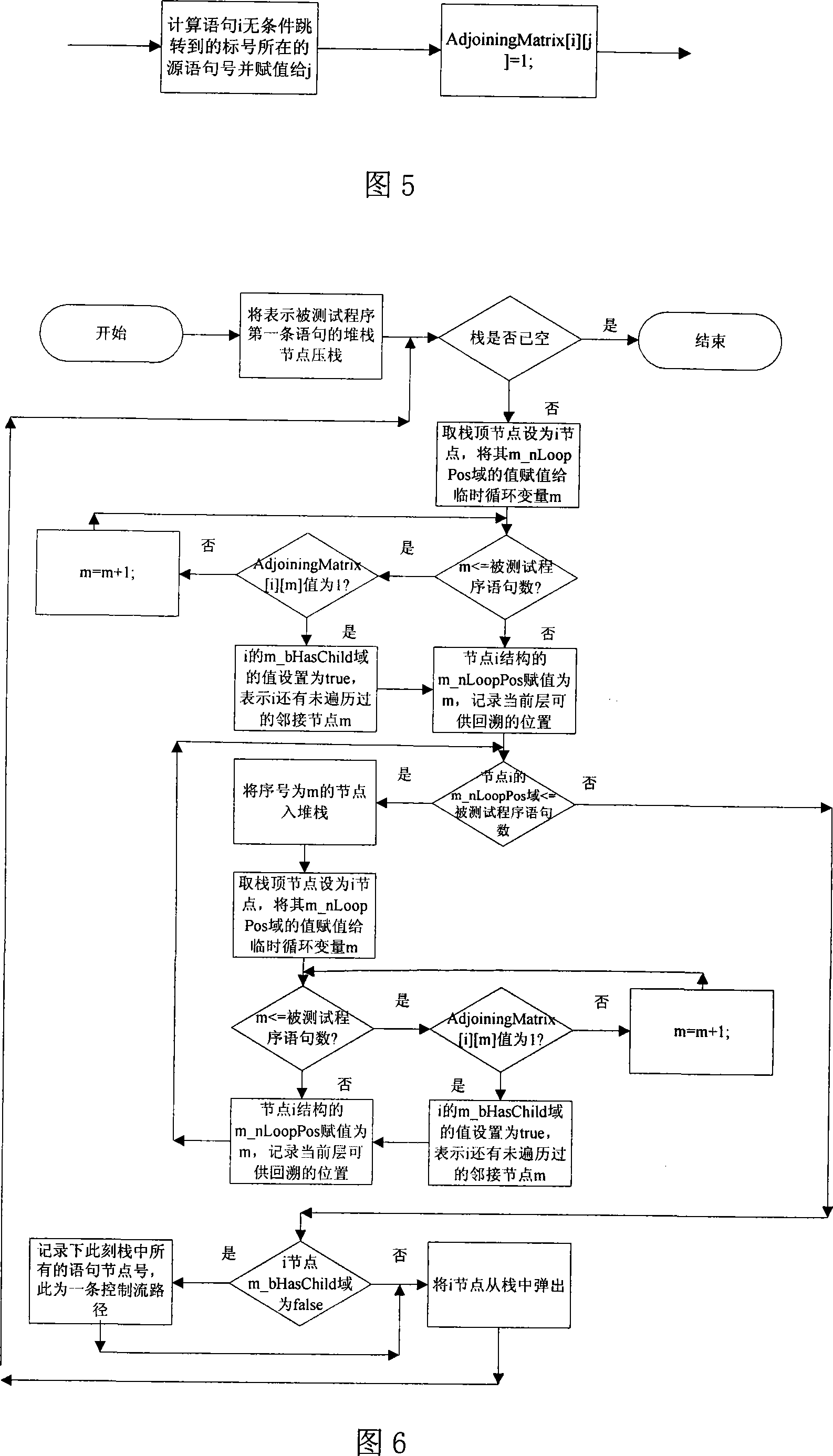
Test program control stream path set creation method based on base path
InactiveCN101216803ASolve the completeness problemSolving automation problemsSoftware testing/debuggingPath generationProgram testing
The invention pertains to a path testing in a program testing. The concept of a program control flow base path is defined through bringing in the concept of base in mathematics, a data structure showing a program structure of a source program slice is obtained by using a compiler module first; then through traversing the data structure, a control flow path generating algorithm is utilized to generate a subset compiler module of a program control flow path which is based on a base path to interpret the semanteme on a tested source program, an abstract syntax tree structure showing the structural information of the tested program control flow is output. An adjacency matrix of a control flow graph generates a module ergodicity abstract syntax tree structure, and generates the adjacency matrix representation of a program flow chart. A control flow path subset generating module acquires the control flow information of the tested program through traversing the adjacency matrix, traverses the adjacency matrix by adopting a depth-first multiple backtracking method, and processes sentence nodes, thus a program control flow path subset based on the base path is generated. The method has the outstanding advantages in generating results and flows, and can be widely used in the engineering practice of a path cover testing in a software structure testing.
Owner:SICHUAN UNIV
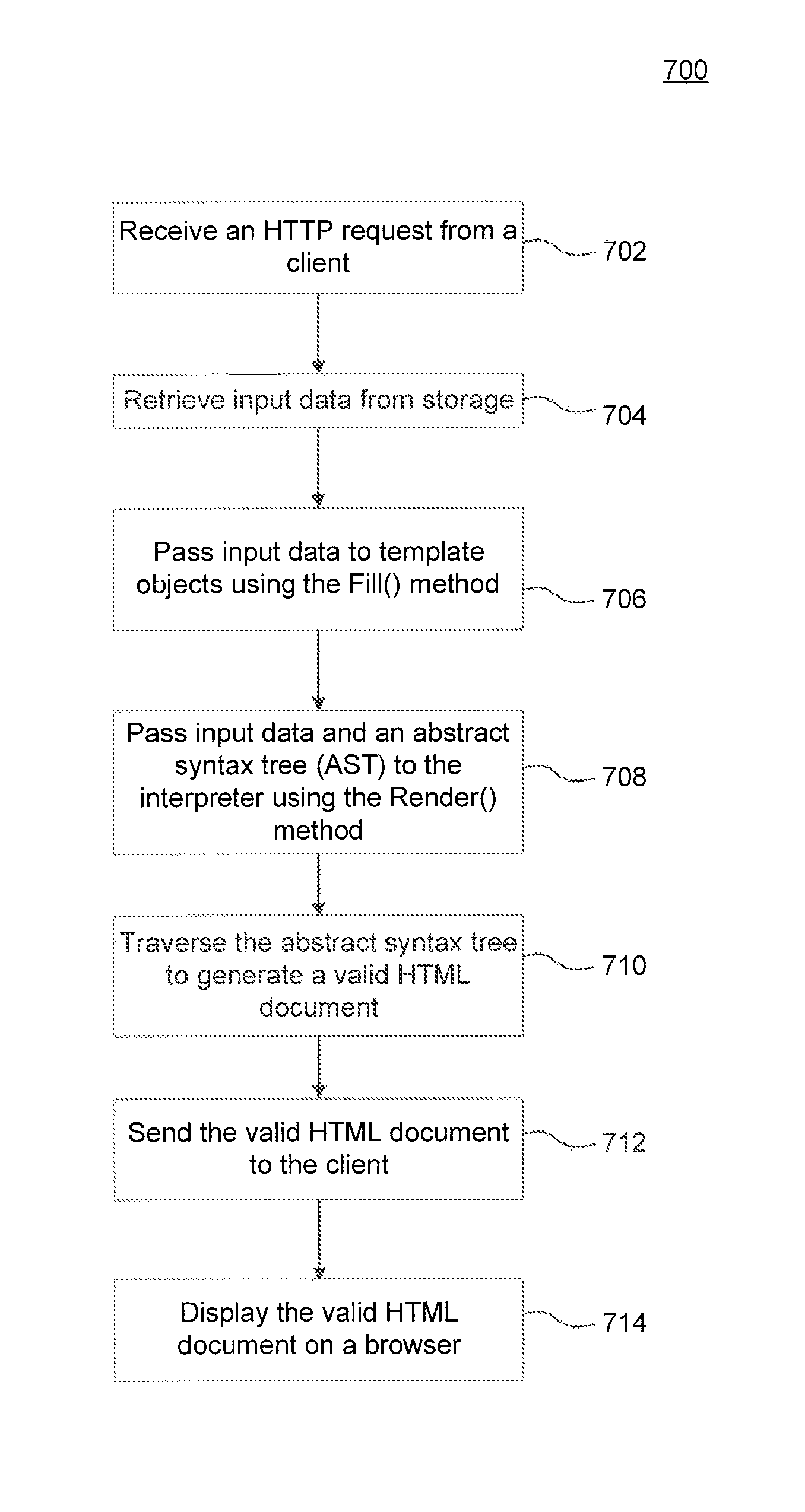
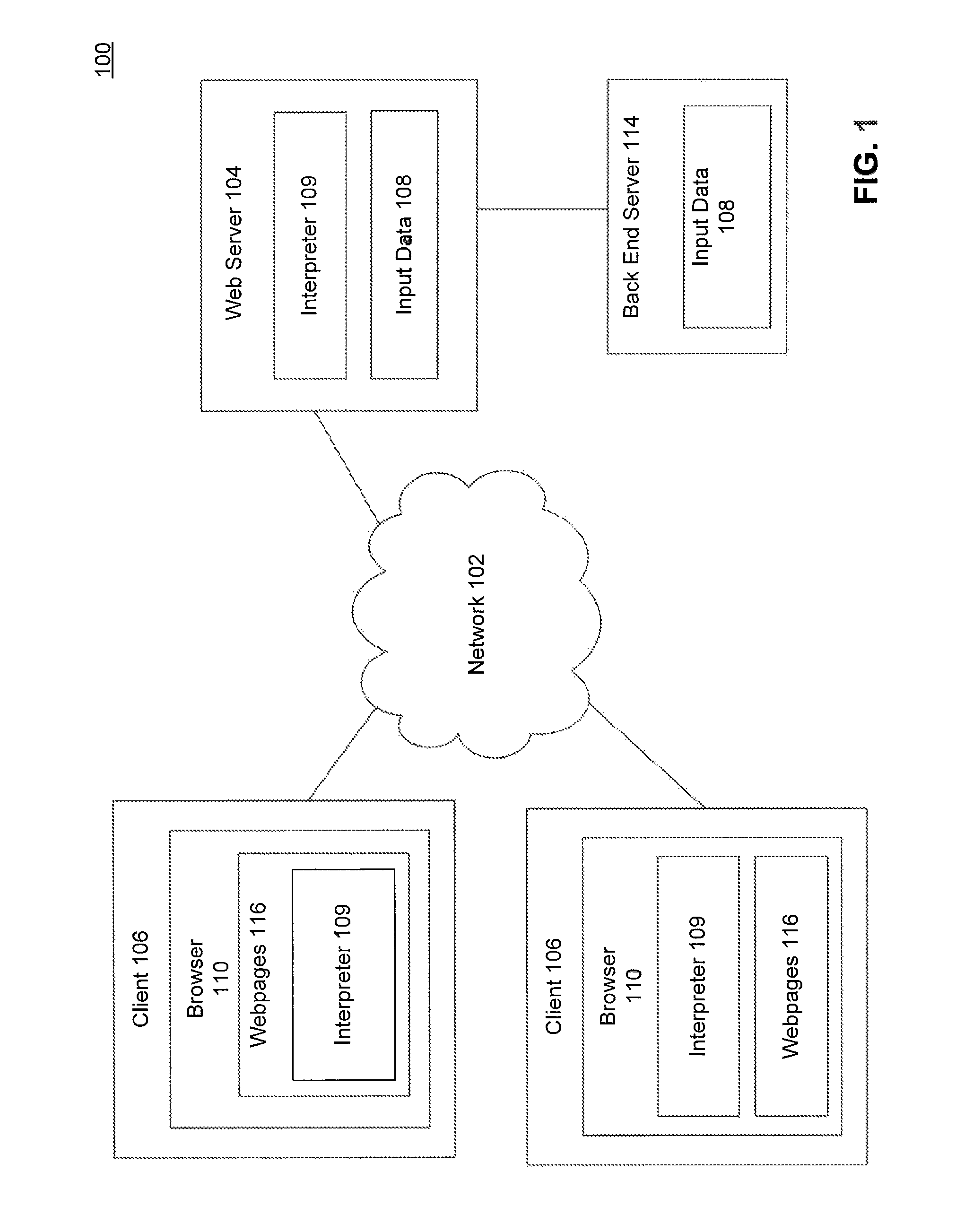
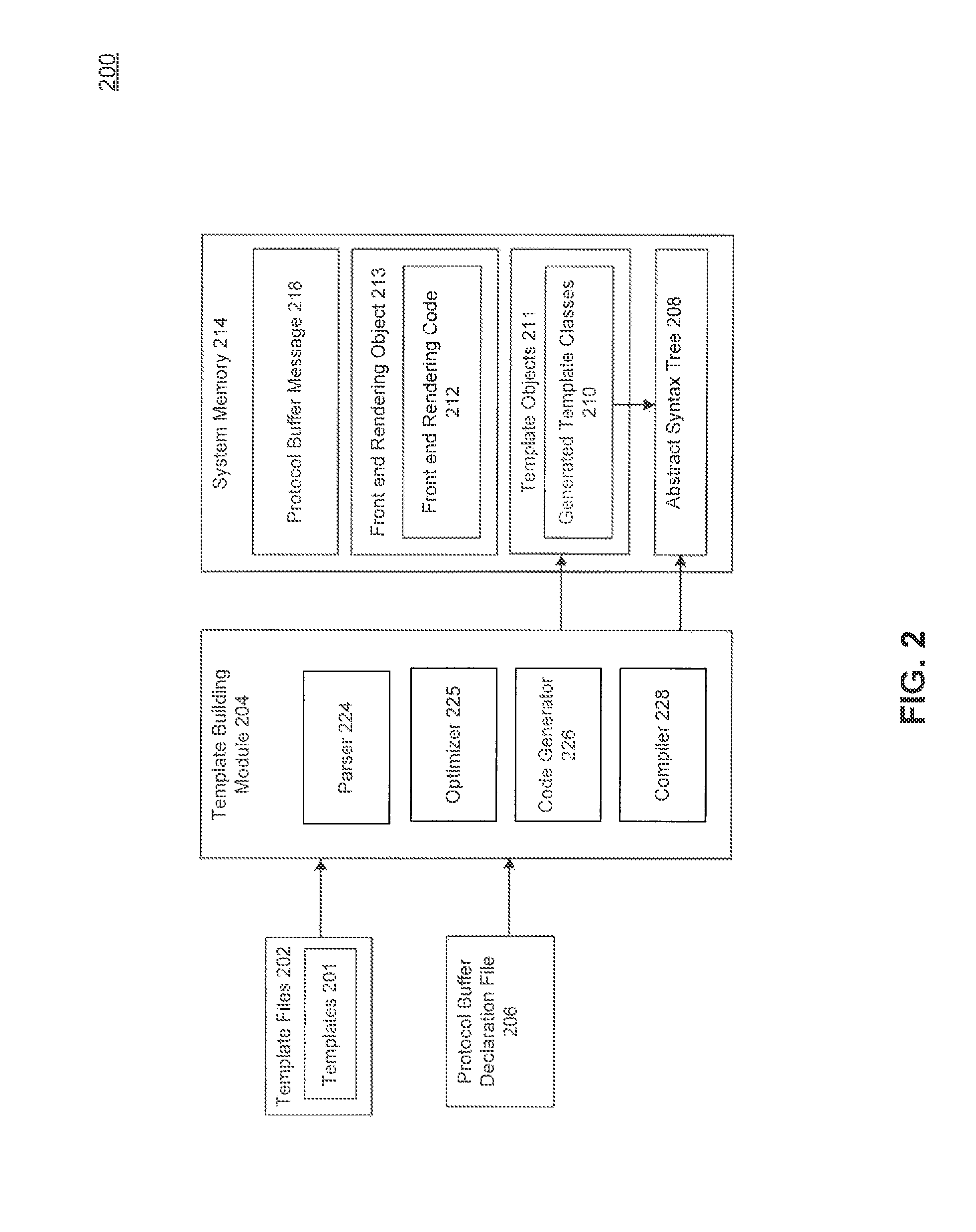
Abstract syntax tree interpreter for generating a valid HTML document
ActiveUS9026903B1Natural language data processingSpecial data processing applicationsDocument preparationAbstract syntax tree
A system, method, and a computer-readable medium for generating a valid HTML document. The method includes receiving a request from a browser and, in response, providing an abstract syntax tree, the abstract syntax tree including a plurality of nodes, where each node represents an element in a template file. The method also includes, traversing the abstract syntax tree, and for each node in the tree determining a type of the node and performing an action based on the node type. The method further includes generating the valid HTML document based on the plurality of actions and sending the valid HTML document for display to a browser.
Owner:GOOGLE LLC
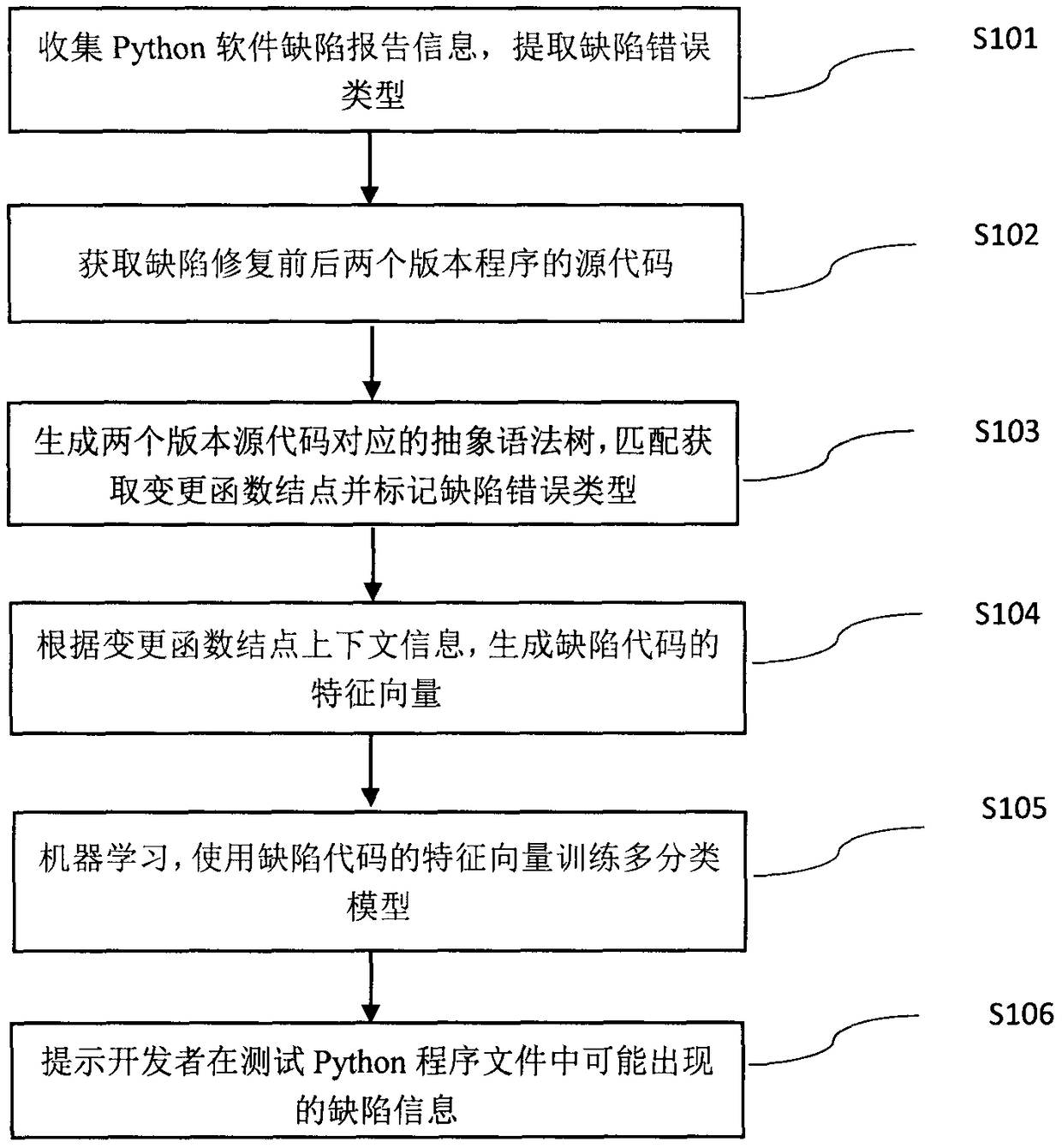
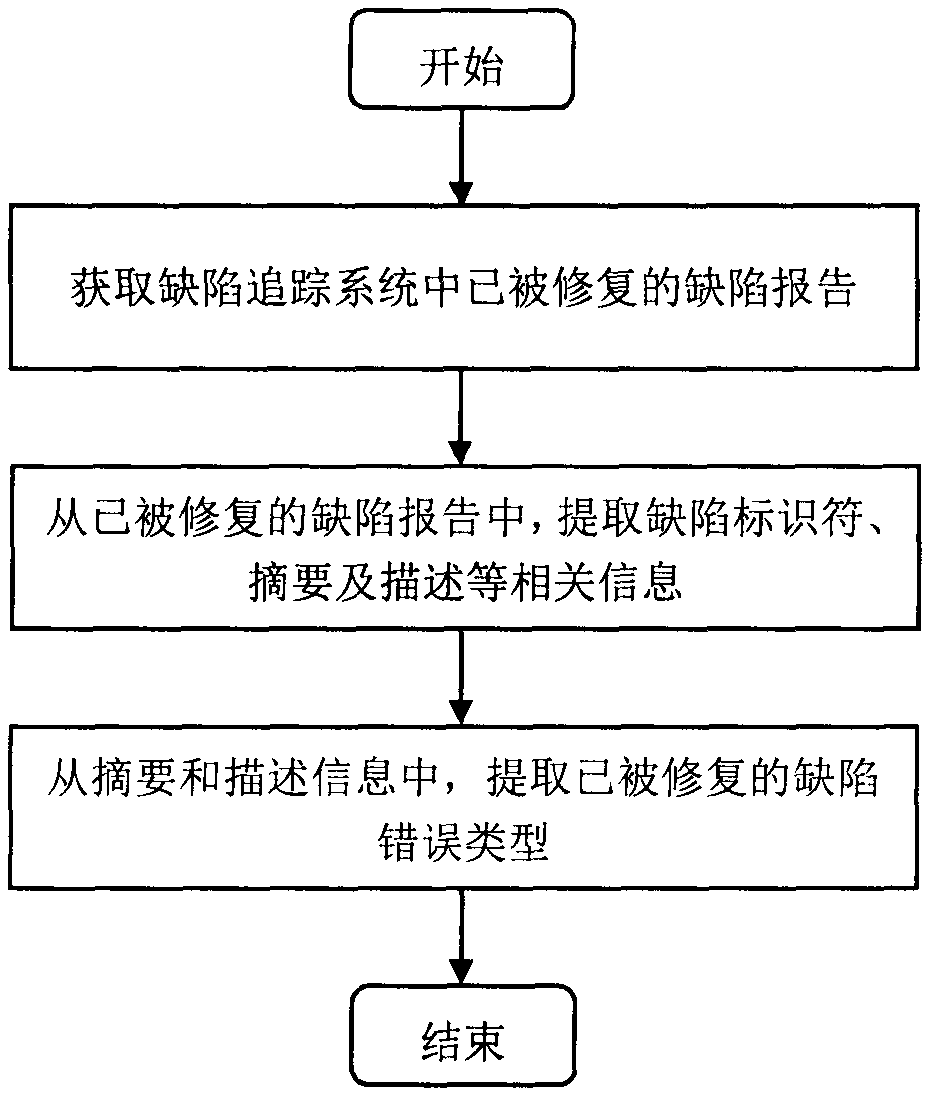
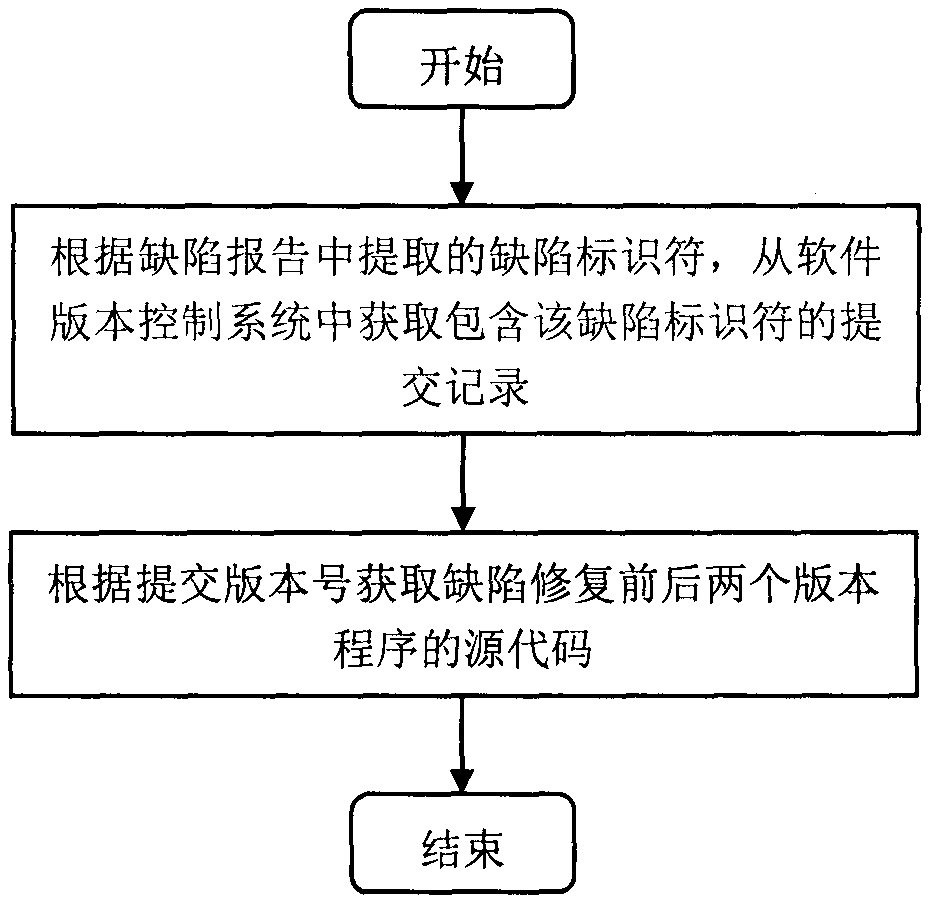
Python program type defect detection method based on abstract syntax trees
ActiveCN108932192AImprove maintainabilityVersion controlReverse engineeringPython languageFeature vector
The invention provides a Python program type defect detection method based on abstract syntax trees. The method comprises the steps of (1) collecting Python software defect report information and extracting a defect identifier and a defect error type, (2) obtaining source codes of two versions of programs before and after defect repair, (3) generating abstract syntax trees corresponding to the twoversions of source codes, matching and obtaining a change function node and marking the defect error type, (4) generating a feature vector of a defect code according to the context information of thechange function node, (5) training a multi-classification models on a defect code feature vector by using the machine learning technology, and (6) reminding a developers of possible type defect information in testing a Python program file. The invention aims to solve the problems of the lack of the type defect analysis for a Python language and the inability to detect a possible defect error typeat present, thus the management of software quality is guided, and the maintainability of the software is improved.
Owner:NANJING UNIV
Modular parser architecture
ActiveUS20030106049A1Software engineeringSpecific program execution arrangementsMicrocomputerLexical analysis
A modular parser architecture and methods related thereto make use of a number of miniparsers. Each miniparser is capable of receiving input and generating an output dependent thereon. In one embodiment, a lexer or a miniparser capable of lexical analysis receives certain code and provides an abstract syntax tree. Each miniparser performs operations on a set of syntactical constructs to produce a corresponding output syntax tree, which in turn may become an input syntax tree for a next miniparser which may operate on a different set of syntactical constructs.
Owner:ORACLE INT CORP
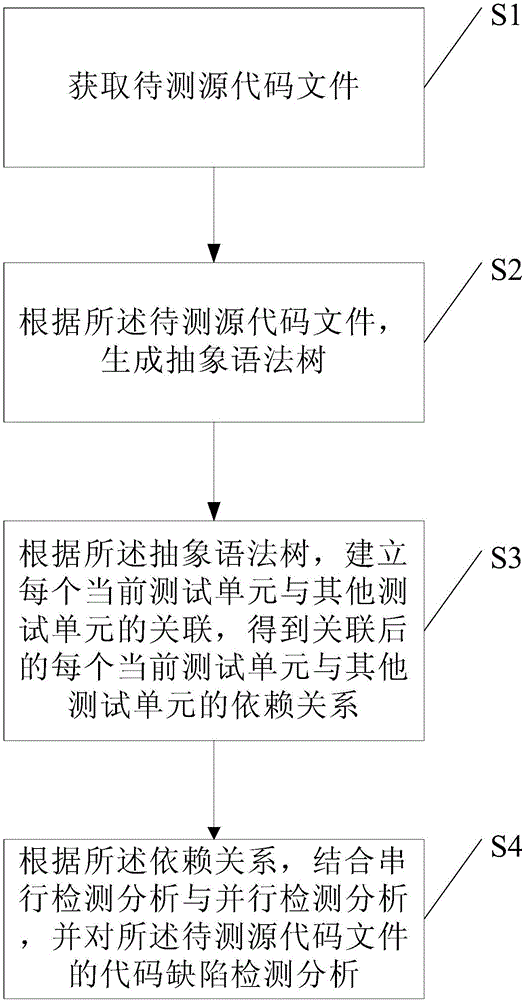
Detection analysis method and device for static code defects
ActiveCN106294156ASmall scaleImprove the efficiency of defect detection analysisSoftware testing/debuggingSource code fileAbstract syntax tree
The embodiment of the invention discloses a detection analysis method and device for static code defects. The problem that the existing code defect detection analysis of a to-be-detected source code file is low in efficiency is solved. The detection analysis method includes the steps that a to-be-detected source code file is obtained, wherein the to-be-detected source code file comprises test units of a plurality of to-be-detected source code file sections; according to the to-be-detected source code file, an abstract syntax tree is generated; according to the abstract syntax tree, correlations between all present test units and other test units are set, and the correlated dependency relationships between all the present test units and the other test units are obtained, wherein the other test units are the other test units except for the present test unit in the multiple test units; according to the dependency relationships, serial detection analysis and parallel detection analysis are combined, code defects of the to-be-detected source code file are detected and analyzed, and the detection analysis efficiency of the code defects of the to-be-detected source code file is improved.
Owner:BEIJING UNIV OF POSTS & TELECOMM
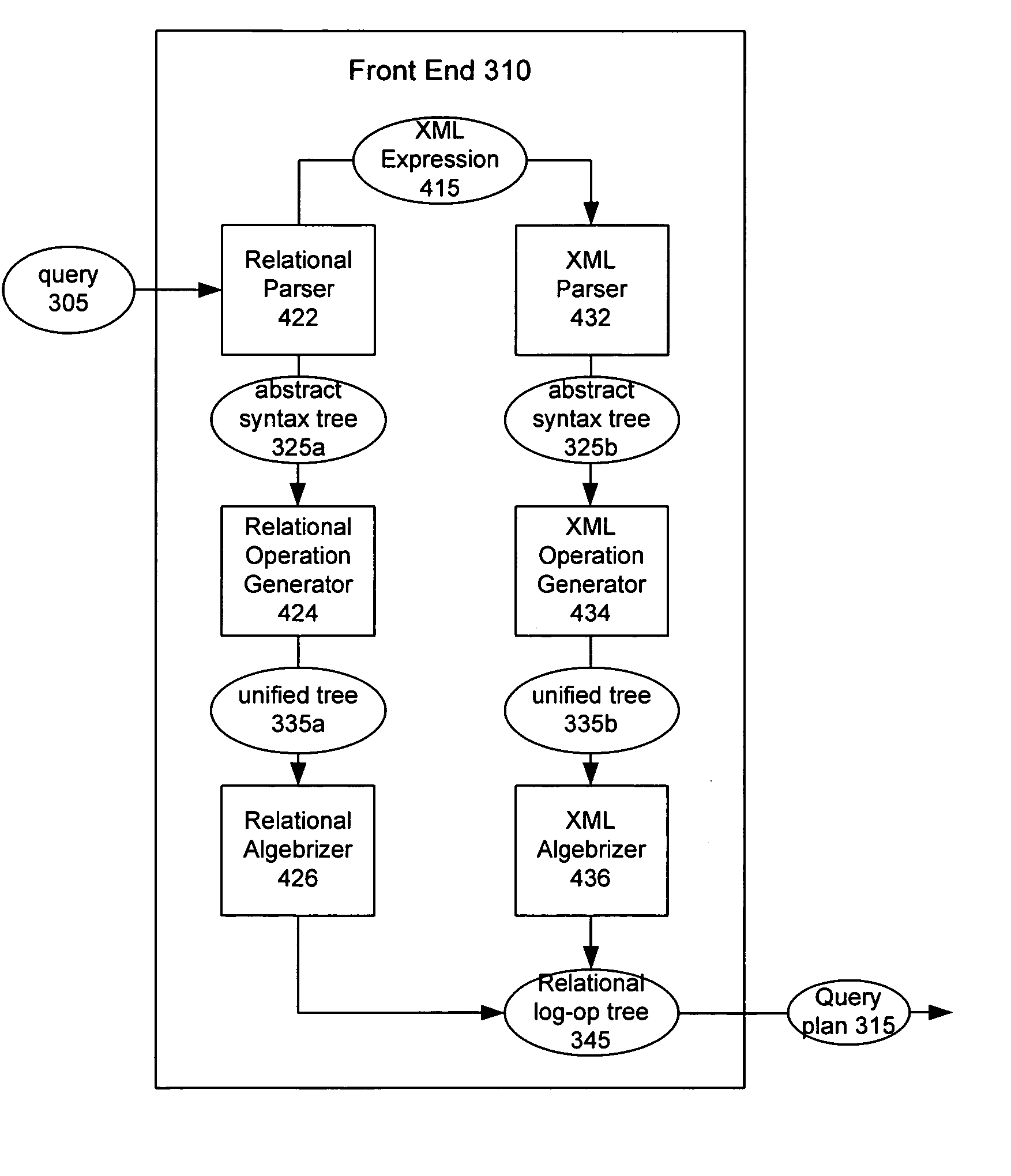
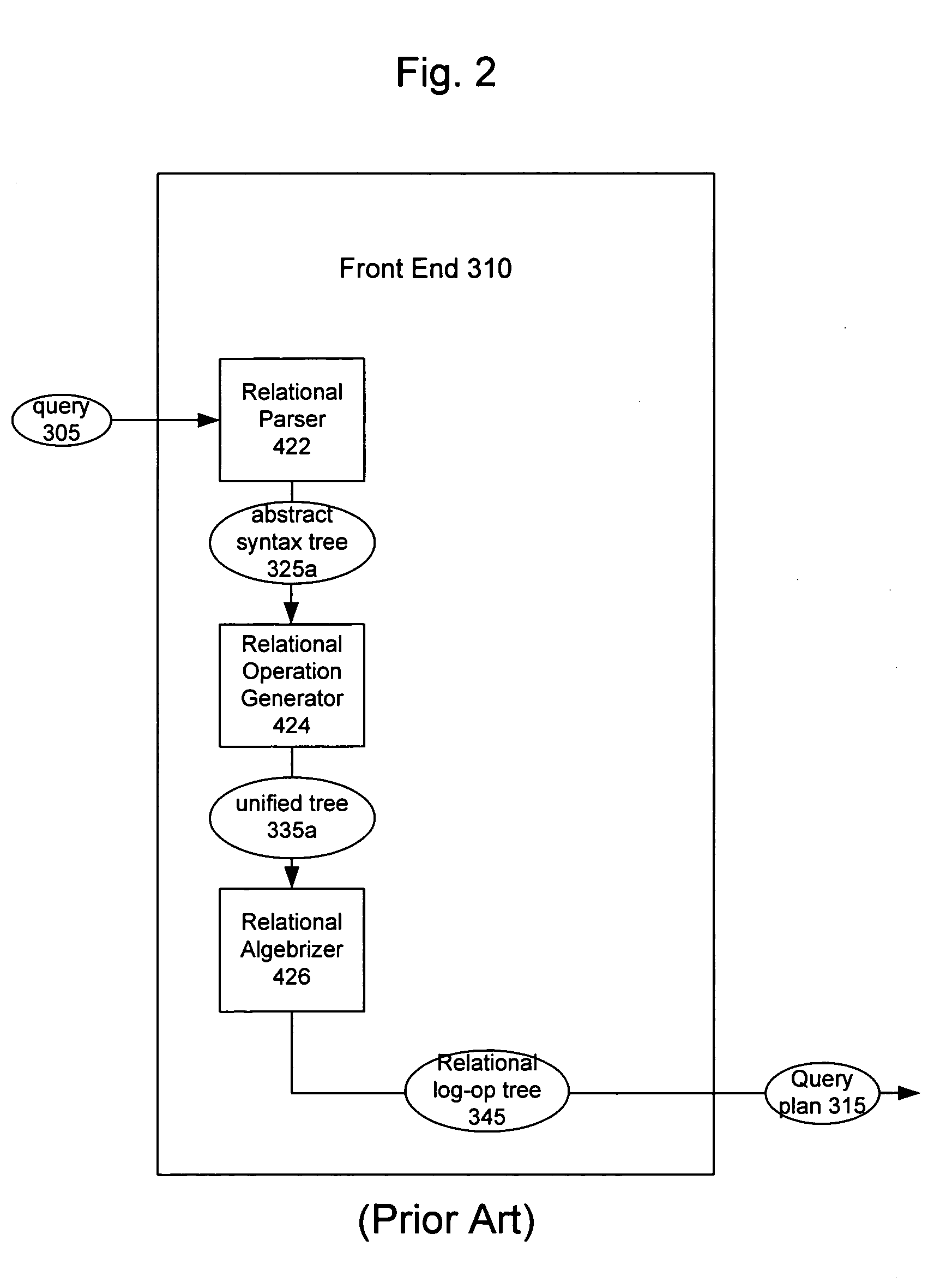
System and method for compiling an extensible markup language based query
InactiveUS20050210002A1Digital data information retrievalDigital data processing detailsRelational algebraExtensible markup
An extensible markup language (XML) expression included in a query is parsed to yield an abstract syntax tree. The abstract syntax tree is then transformed into a unified tree including XML algebra operations. The unified tree is then converted into a relational tree including enhanced relational algebra operations. The relational tree is then forwarded to a query processor for optimization and execution of the query at the query processor.
Owner:MICROSOFT TECH LICENSING LLC
Method and device for determining data consanguinity based on structural data
InactiveCN109325078AImplement parsingNatural language data processingDatabase modelsGranularitySource field
The present invention provides a method and device for determining data consanguinity based on structural data. The method comprises: parsing a selection statement to obtain a source abstract syntax tree, and organizing the table information and the field information obtained by traversing the source abstract syntax tree into a source list layer by layer; obtaining the target abstract syntax treeby parsing the insertion statement, and organizing the table information and the field information obtained by traversing the target abstract syntax tree into the target list layer by layer; traversing the source manifest to obtain the source table information and traversing the target manifest to obtain the target table information to obtain the table granularity data kinship relationship; extracting the target field information for the target table from the target manifest, starting from the first layer of the source manifest, finding the source field in the source table with the same name as the target field information of the target table layer by layer, and when the source table to which the source field belongs no longer comes from the subquery, determining the corresponding source field to be the source field with blood relationship corresponding to the target field information. The scheme can parse the field-level granularity of data consanguinity based on structured data.
Owner:RAJAX NETWORK &TECHNOLOGY (SHANGHAI) CO LTD
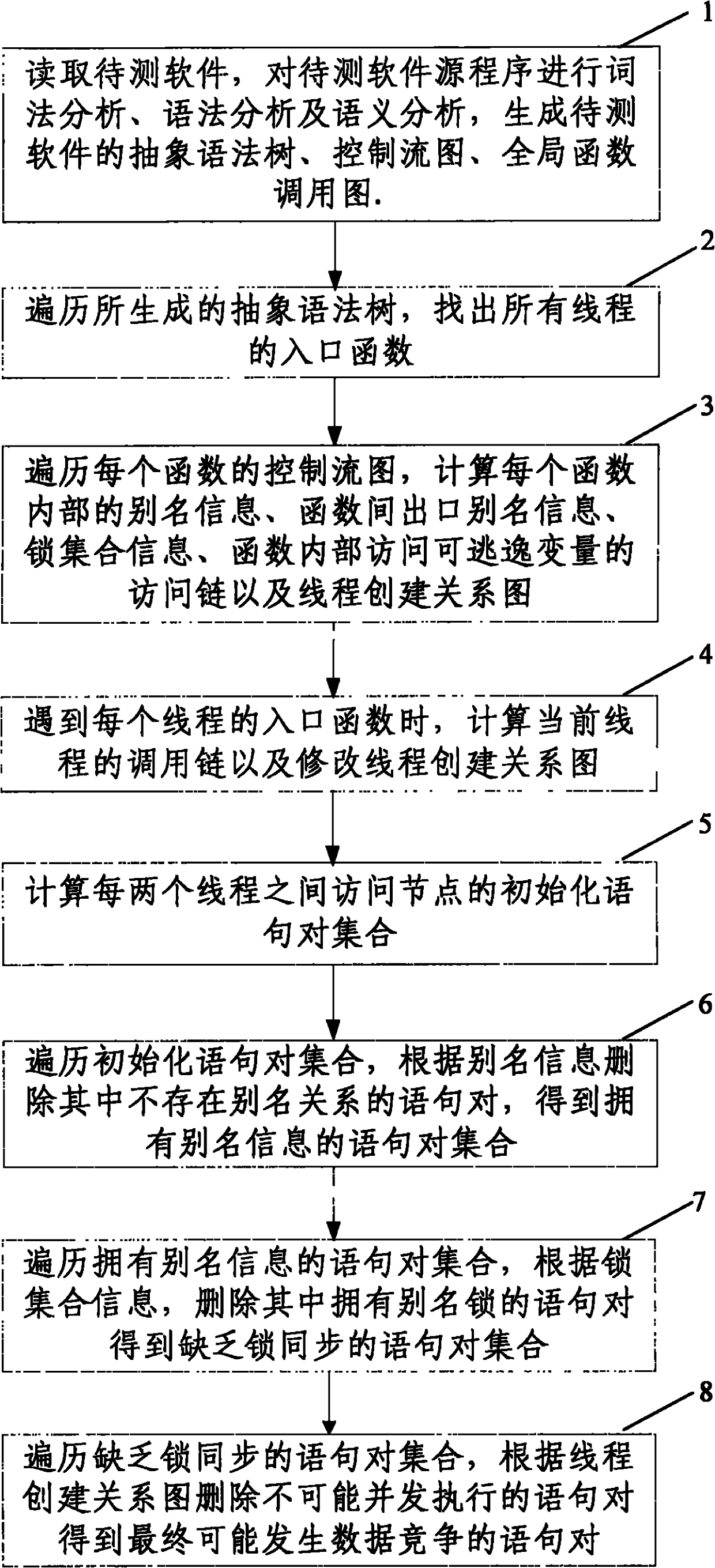
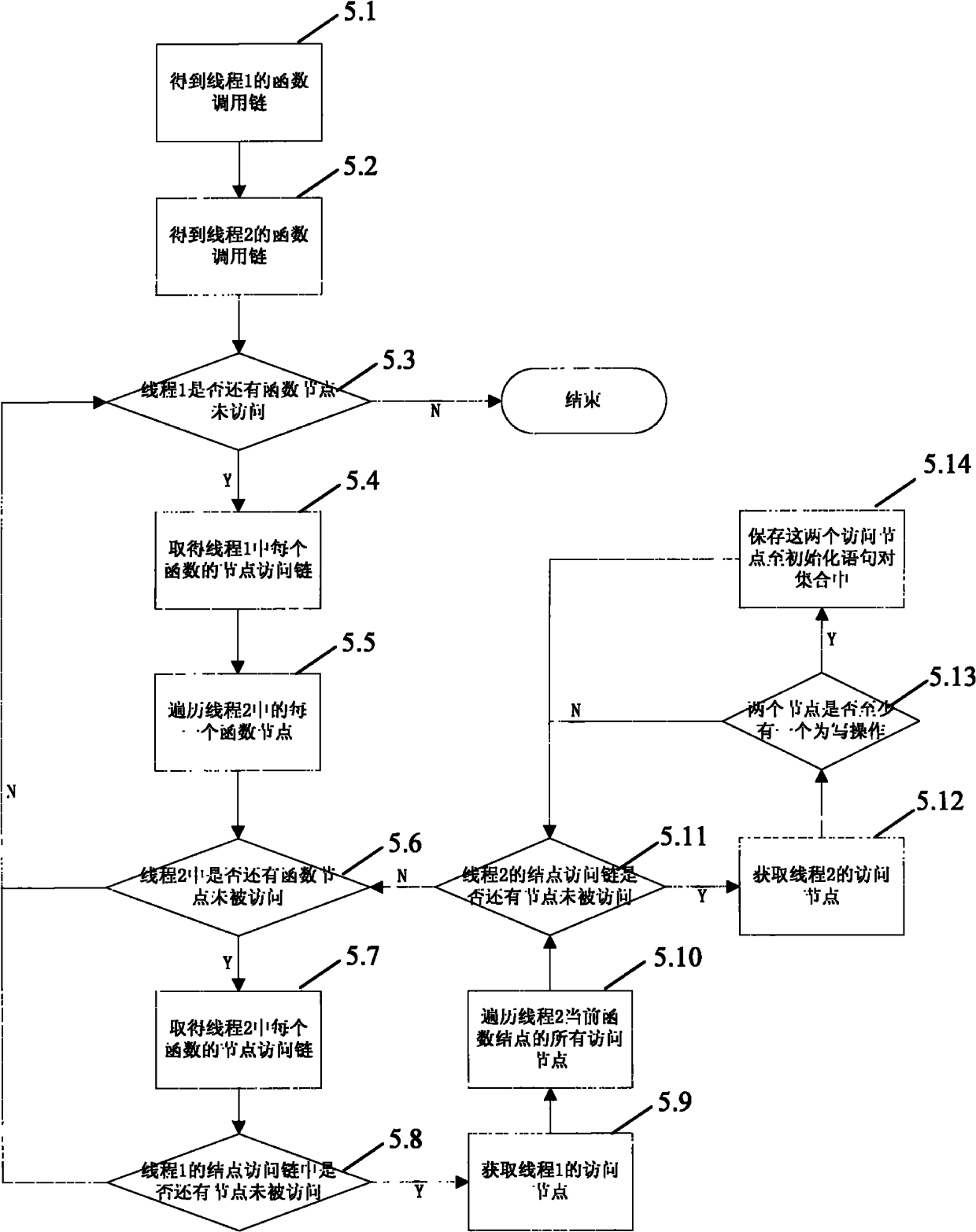
Code static analysis-based data race detecting method and system thereof
The invention discloses a code static analysis-based data race detecting method and a system of the detecting method. The method comprises the following steps of: reading software to be detected, statically analyzing a source program of the software to be detected, and generating an abstract syntax tree, a control flow graph and a global function call graph of the software to be detected; on thatbasis, computing alias information in each function, outlet alias information among functions, lock assembly information, an access link of an access escapable variable quantity in each function and a thread building relational graph; computing a plurality of initialized sentence pair sets of a plurality of access nodes in every two threads; and gradually eliminating the sets according to the alias information, the lock assembly information and a concurrency relation to obtain a sentence pair which can finally have the data race. The detecting method and the detecting system can effectively detect the data race of a multi-thread program compiled by C / C++, thereby having the characteristics of high test precision and high automaticity, and being applied to detecting the data race caused bytwo threads or multiple threads.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Methods and apparatus for automatic translation of a computer program language code
Embodiments of the methods and apparatus for automatic cross language program code translation are provided. One or more characters of a source programming language code are tokenized to generate a list of tokens. Thereafter, the list of tokens is parsed to generate a grammatical data structure comprising one or more data nodes. The grammatical data structure may be an abstract syntax tree. The one or more data nodes of the grammatical data structure are processed to generate a document object model comprising one or more portable data nodes. Subsequently, the one or more portable data nodes in the document object model are analyzed to generate one or more characters of a target programming language code.
Owner:XENOGENIC DEV LLC
Orchestration of business processes using templates
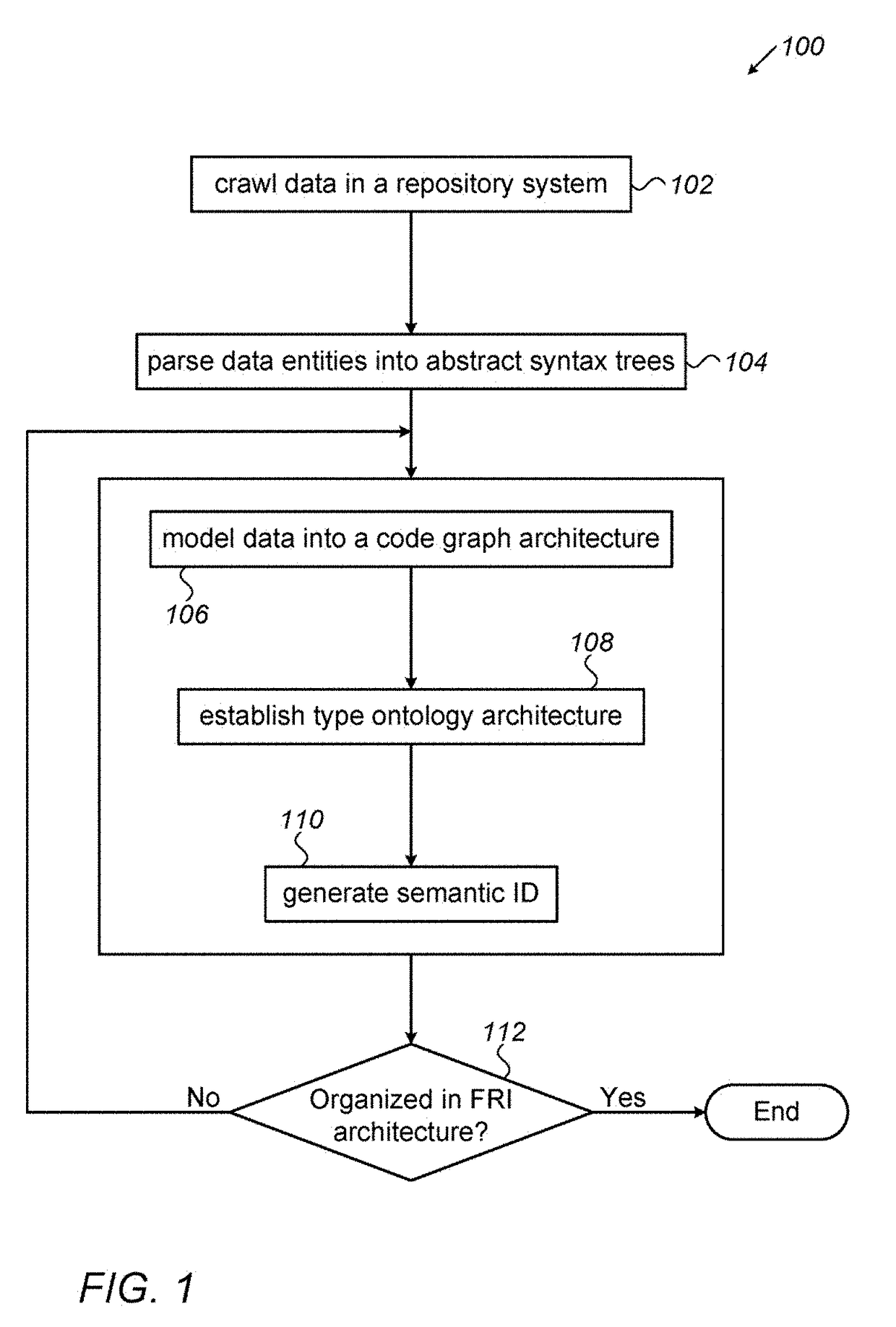
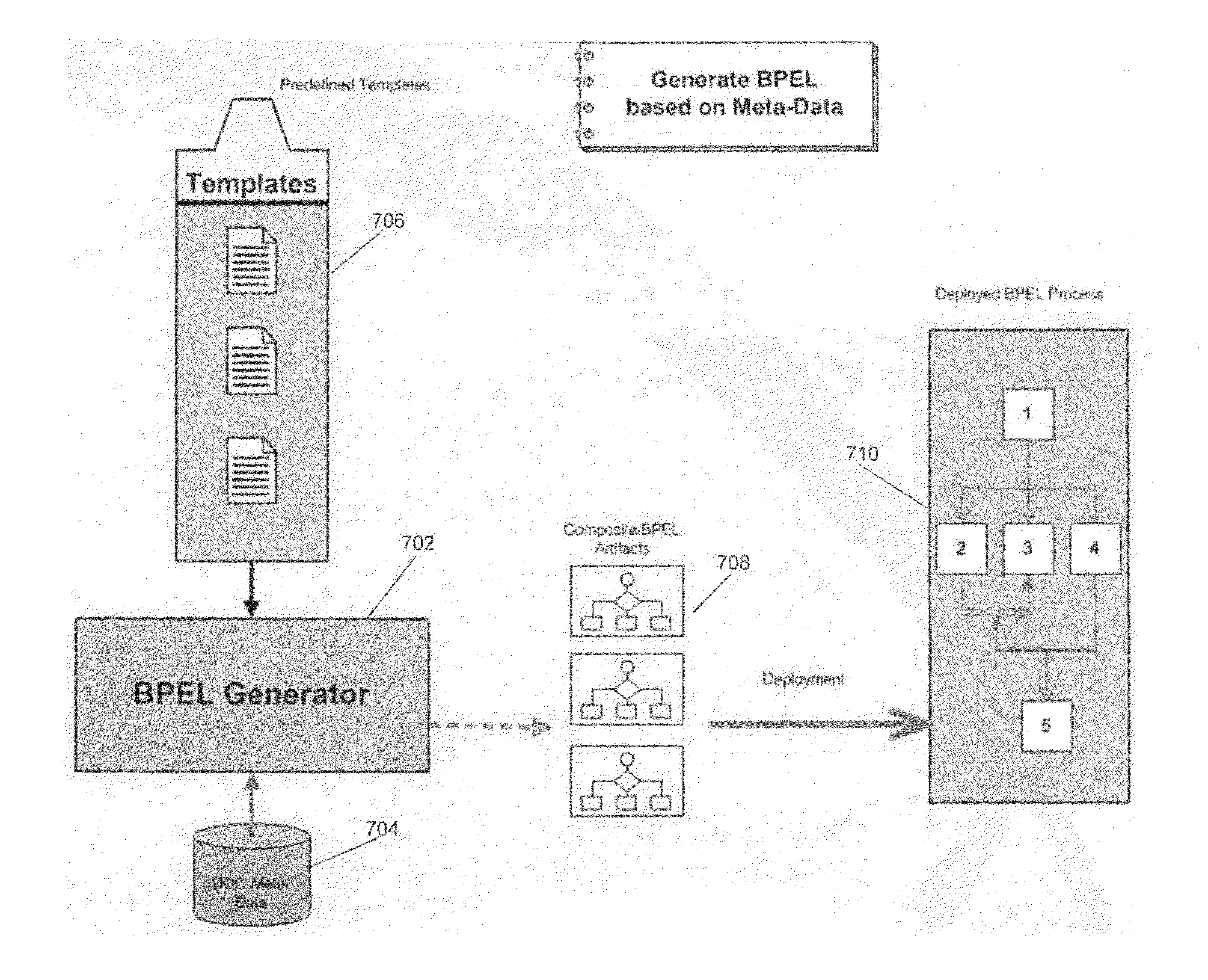
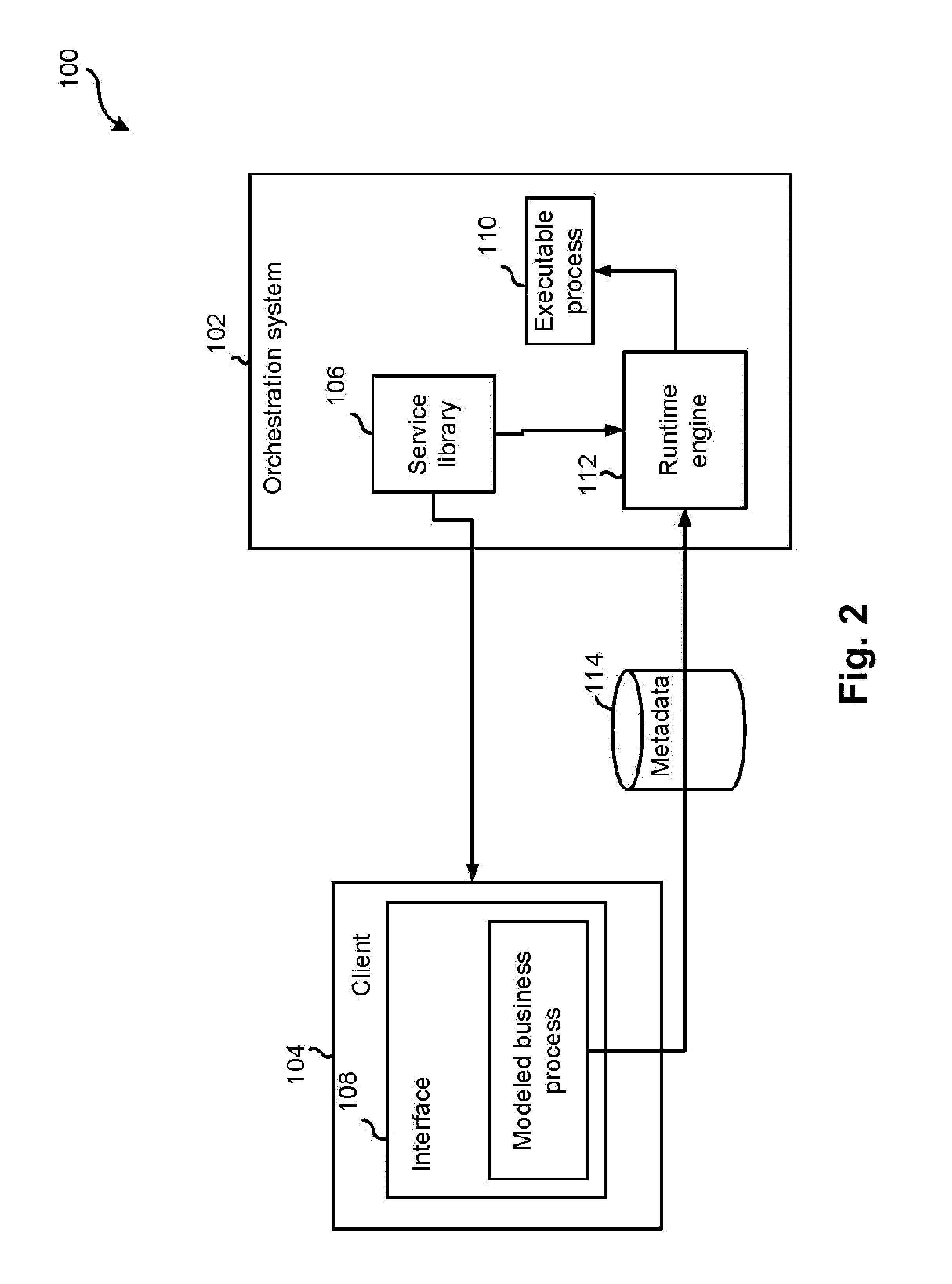
ActiveUS20110191383A1Digital data information retrievalDigital data processing detailsOrder fulfillmentTheoretical computer science
A distributed order orchestration system for orchestrating a business process of an order fulfillment system receives from an interface a definition of the business process and generates metadata from the definition. The system then generates an abstract syntax tree from the metadata. The tree includes a plurality of nodes and one or more of the nodes correspond to a predefined template. The system then generates executable orchestration code based on the abstract syntax tree and the predefined template.
Owner:ORACLE INT CORP
Detection method for software vulnerability
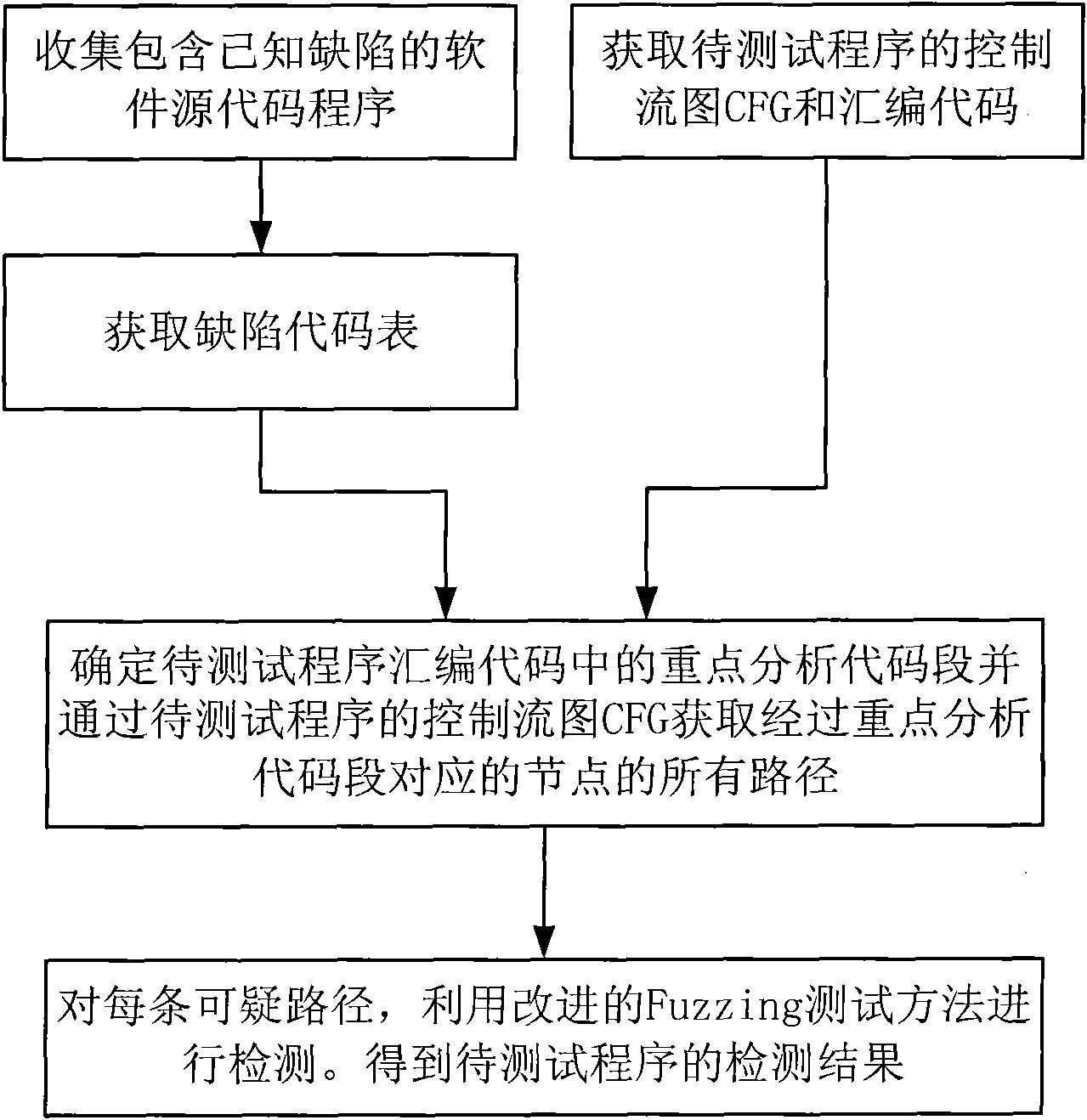
InactiveCN102385550AGuaranteed validityEfficient detectionSoftware testing/debuggingCode tableInformation security
The invention relates to a detection method for software vulnerability, and belongs to the technical field of information security. The detection method comprises the following specific steps of: (1) collecting a software source code program containing known vulnerability; (2) obtaining a vulnerability code table; (3) obtaining a control flow graph CFG and an assembly code of the program to be tested; (4) determining key analysis code segments in the assembly code of the program to be tested and obtaining all paths of passing through nodes corresponding to the key analysis code segments through the control flow graph CFG of the program to be tested; and (5) for each suspicious path, an improved Fuzzing test method is used for detection to obtain the test results of the program to be tested. In the invention, when a fitness function is determined, the dependence on the source code of the tested program is eliminated, and the availability of information is kept; and the redundant information in an abstract syntax tree is eliminated and the integrity of useful information is kept, therefore, the practicality is better, and the efficiency is higher.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Method and device for detecting security flaws of source files
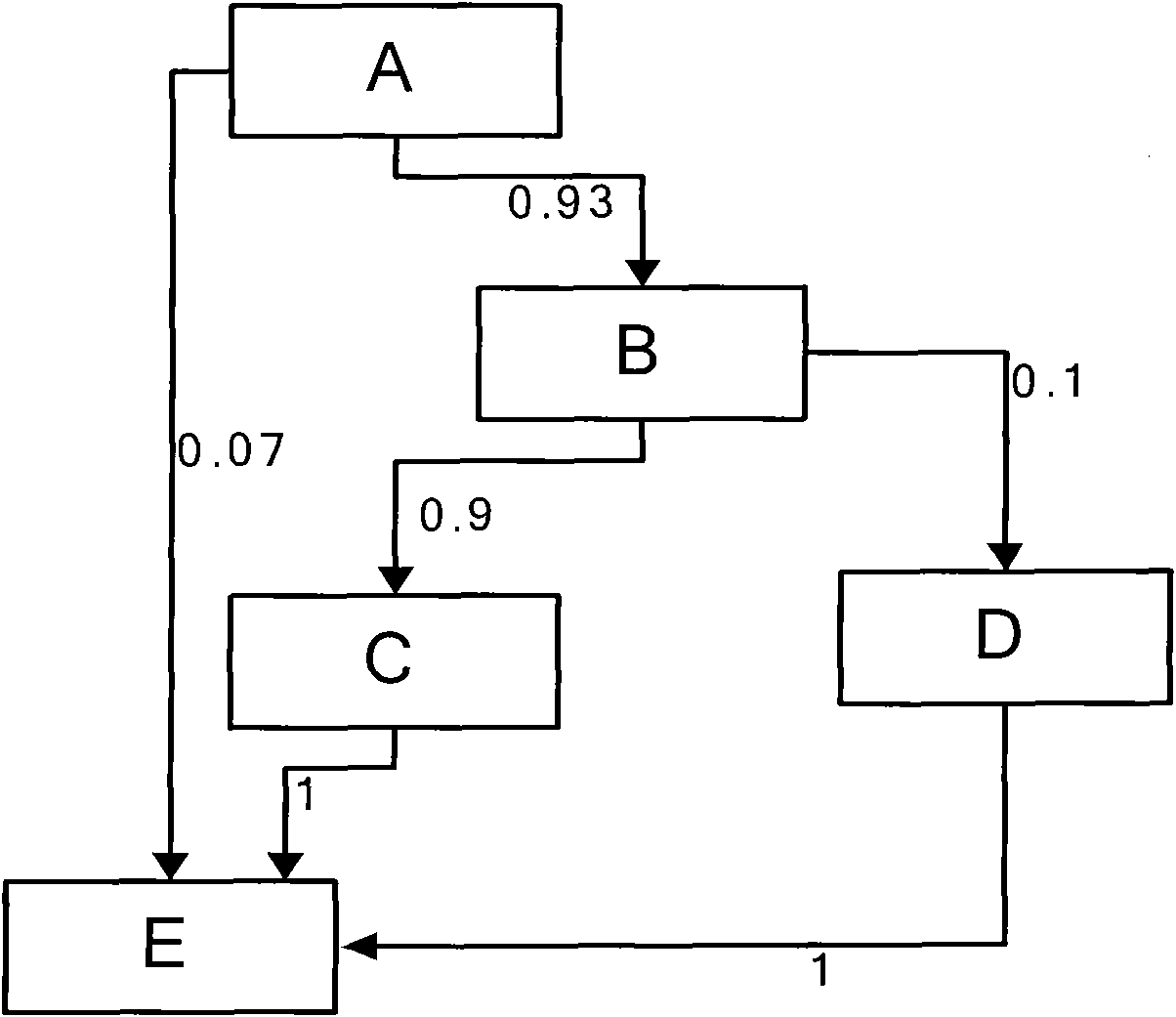
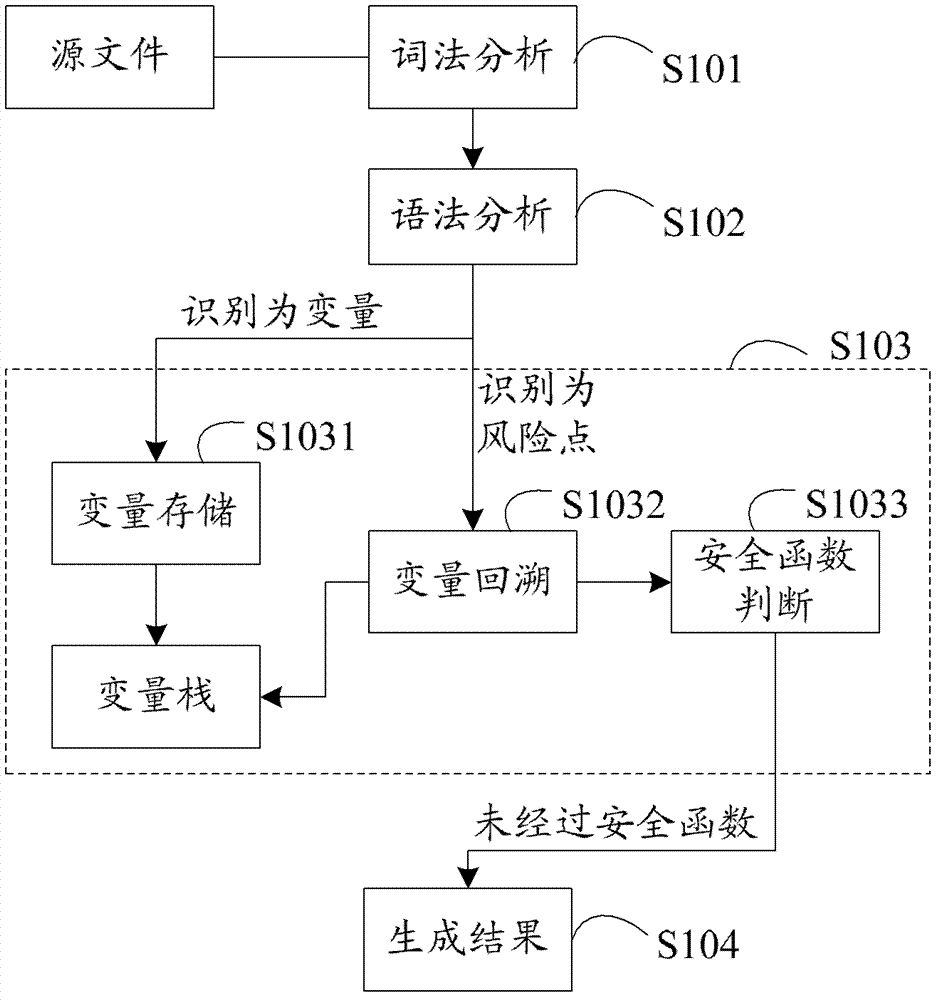
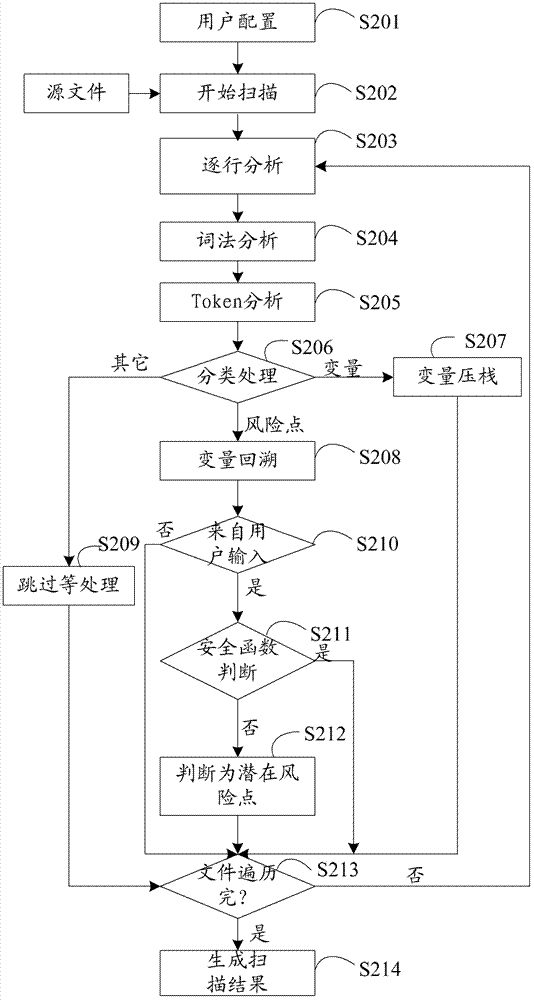
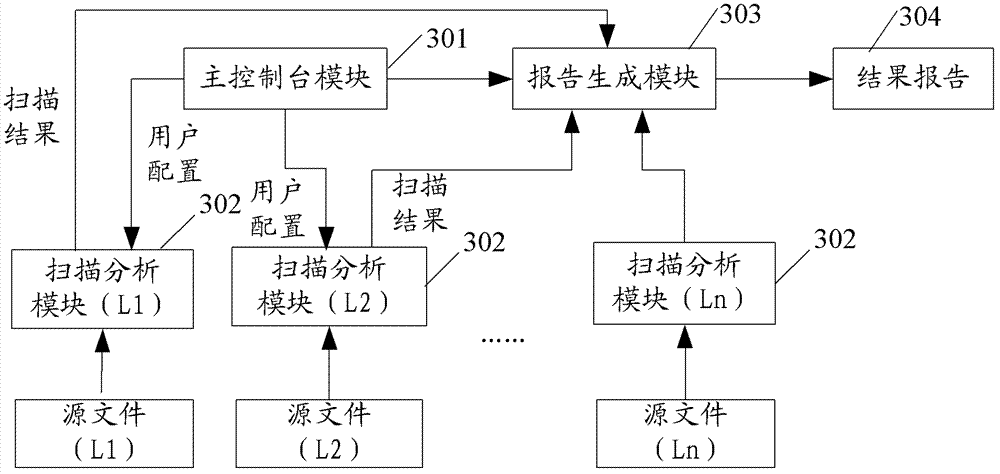
ActiveCN102955914ASave resourcesImprove scanning efficiencyPlatform integrity maintainanceIdentifying VariableLexical analysis
The invention provides a method and a device for detecting security flaws of source files. The method includes scanning the source files one by one and executing steps on the scanned source files including subjecting the source files to lexical analysis and grammatical analysis, performing variable identification operation and risk point identification operation in the process of the lexical analysis, wherein the variable identification operation includes identifying variables and storing identified variables; the risk point identification operation includes identifying risk points, backtracking the stored variables by means of parameters of the risk points which are identified, and if the parameters of the risk points can be backtracked to an importable point, considering the risk point is potential risk points to cause security flaws when without security function processing in the process of backtracking. Compared with the prior art, the method for detecting security flaws of the source files has no need to build up an abstract syntax tree, processing procedures are simplified, resources of a testing system are saved, and code scanning efficiency is improved.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
Python code change reminding method on basis of abstract syntax tree node change extraction
ActiveCN105159715AStrong process controllabilityQuality improvementProgram loading/initiatingSpecial data processing applicationsPython languageNODAL
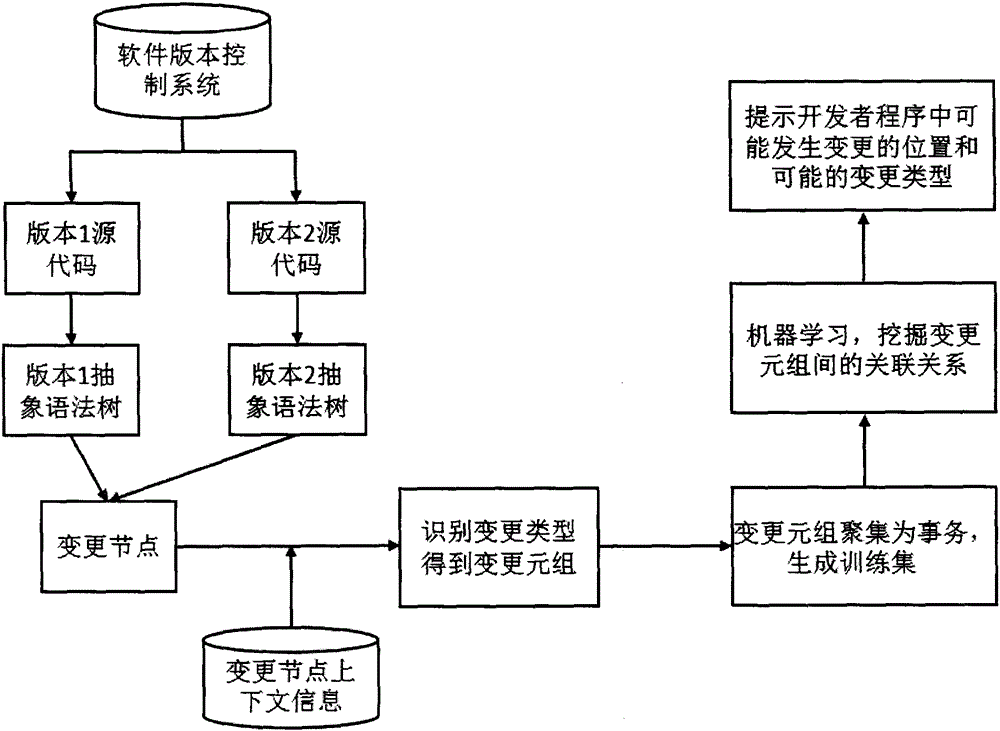
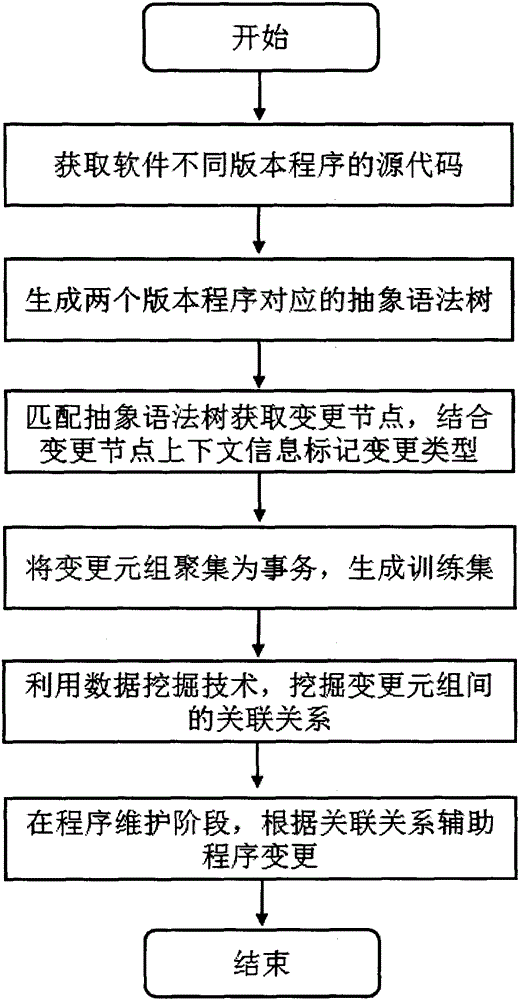
The invention provides a Python code change reminding method based on abstract syntax tree node change extraction. The method comprises the following steps of: (1) obtaining source code of different-version programs of the same software; (2) generating abstract syntax trees corresponding to two versions of source programs; (3) matching the abstract syntax trees to obtain a change node, and combining change node context information to mark the node change type; (4) gathering change tuples into transactions to construct a training set; (5) mining the association relationship in the change tuples by using a data mining technology; and (6) reminding a developer of possibly occurring change positions and possible change types in the according to the programs mined association relationship. The Python code change reminding method solves the problems that in the prior art, the possible code change type cannot be reminded due to the lack of software evolution analysis aiming at the python language, and the like. The management of the software life cycle is further guided, and the software evolution controllability is improved, so that the quality of a software product can be well controlled.
Owner:NANJING UNIV
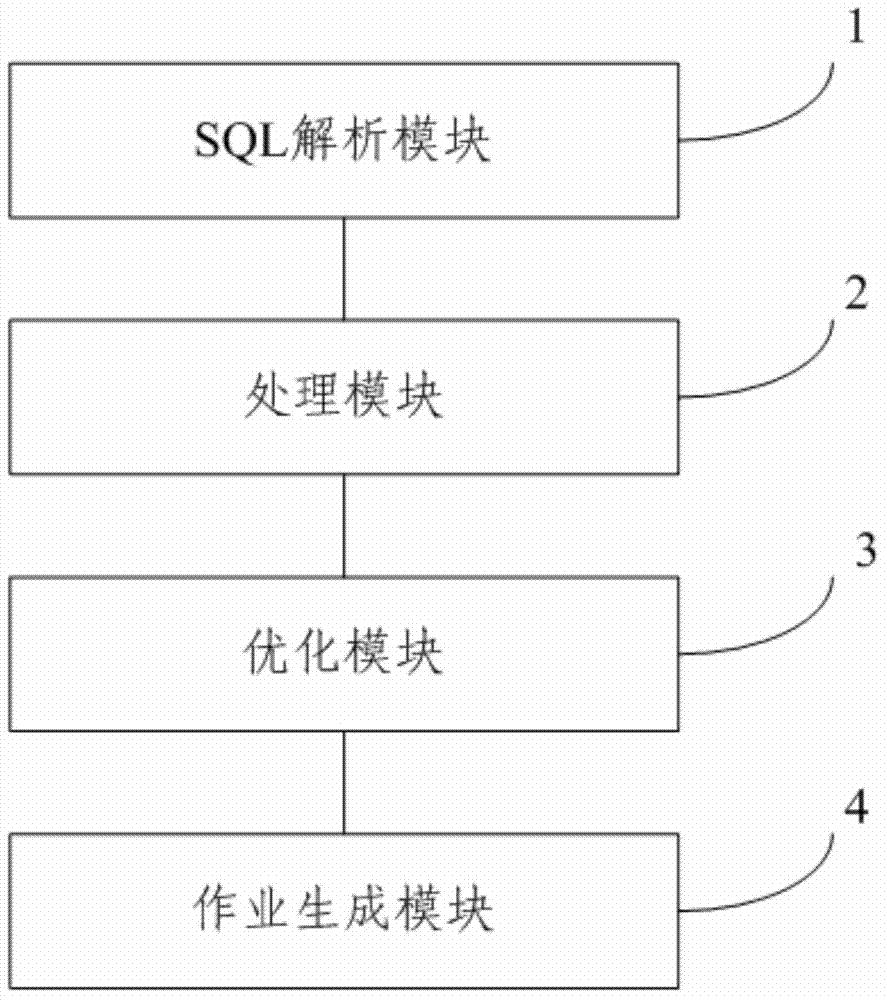
Structured query language (SQL) based MapReduce operation generating method and system
ActiveCN103761080AGuaranteed execution efficiencySpecific program execution arrangementsSpecial data processing applicationsQuery planTheoretical computer science
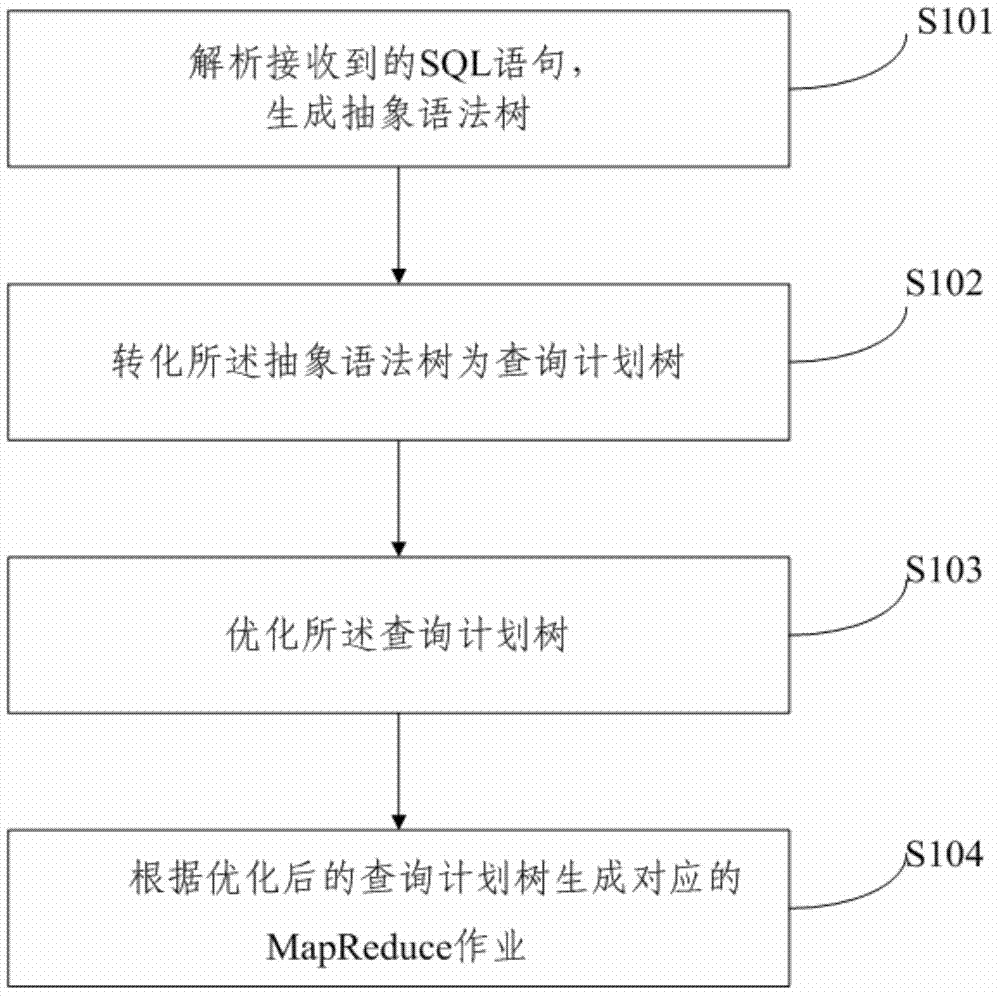
The invention relates to a structured query language (SQL) based MapReduce operation generating method and system. The method includes analyzing received SQL sentences to generate an abstract syntax tree, converting the abstract syntax tree into a query plan tree, optimizing the query plan tree, and generating a corresponding MapReduce operation according to the optimized query plan tree. According to the system, an another tool for language recognition (Antlr) is based on to generate the abstract syntax tree (AST) from the SQL sentences, further, the AST is based on to generate a query plan tree, and finally, the MapReduce operation is generated on the basis of the query plan tree; meanwhile, corresponding optimization policies are further provided, so that the generated MapReduce operation has higher execution efficiency.
Owner:CHINA AGRI UNIV
Method and device for detecting security flaws of software source codes
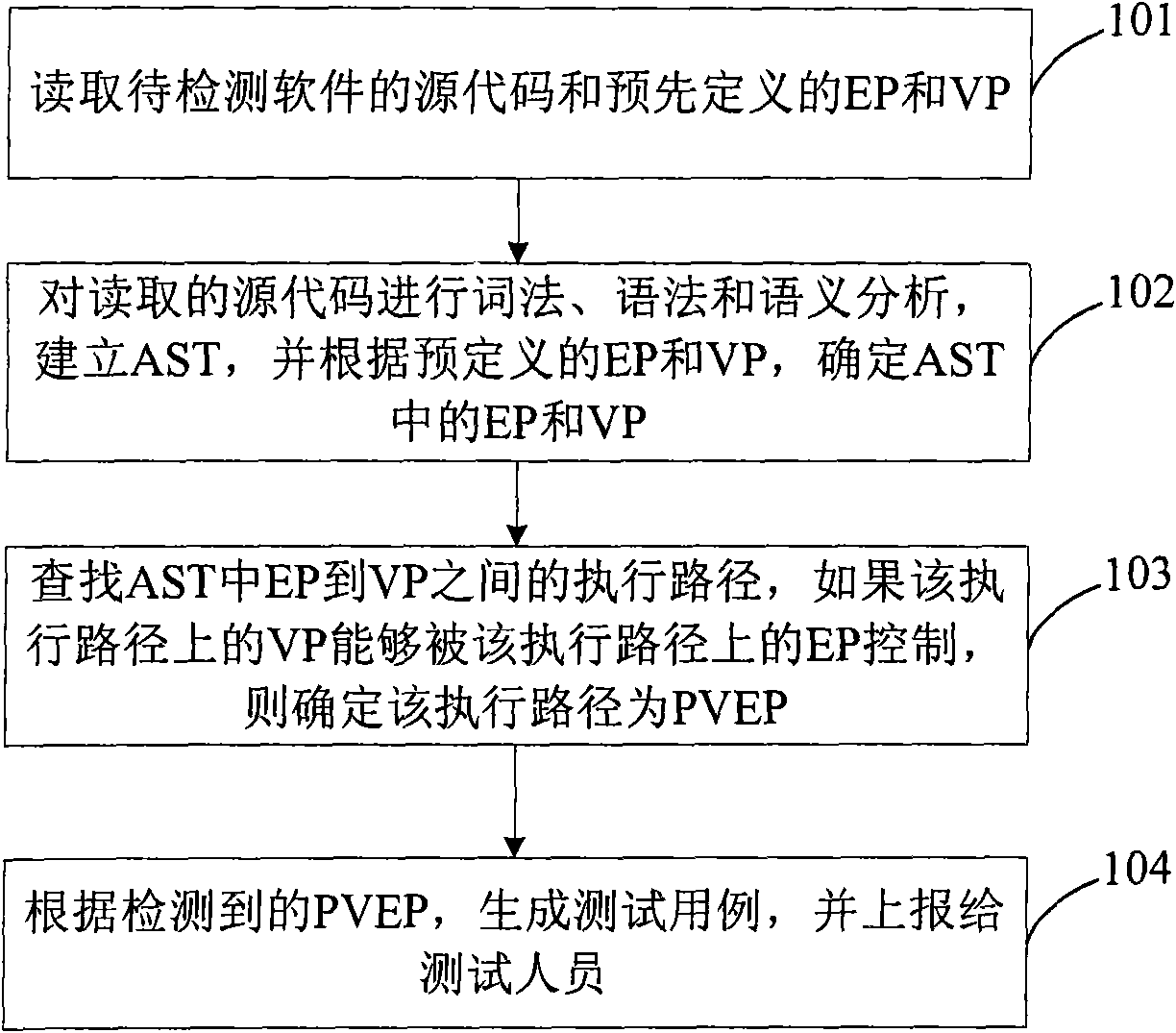
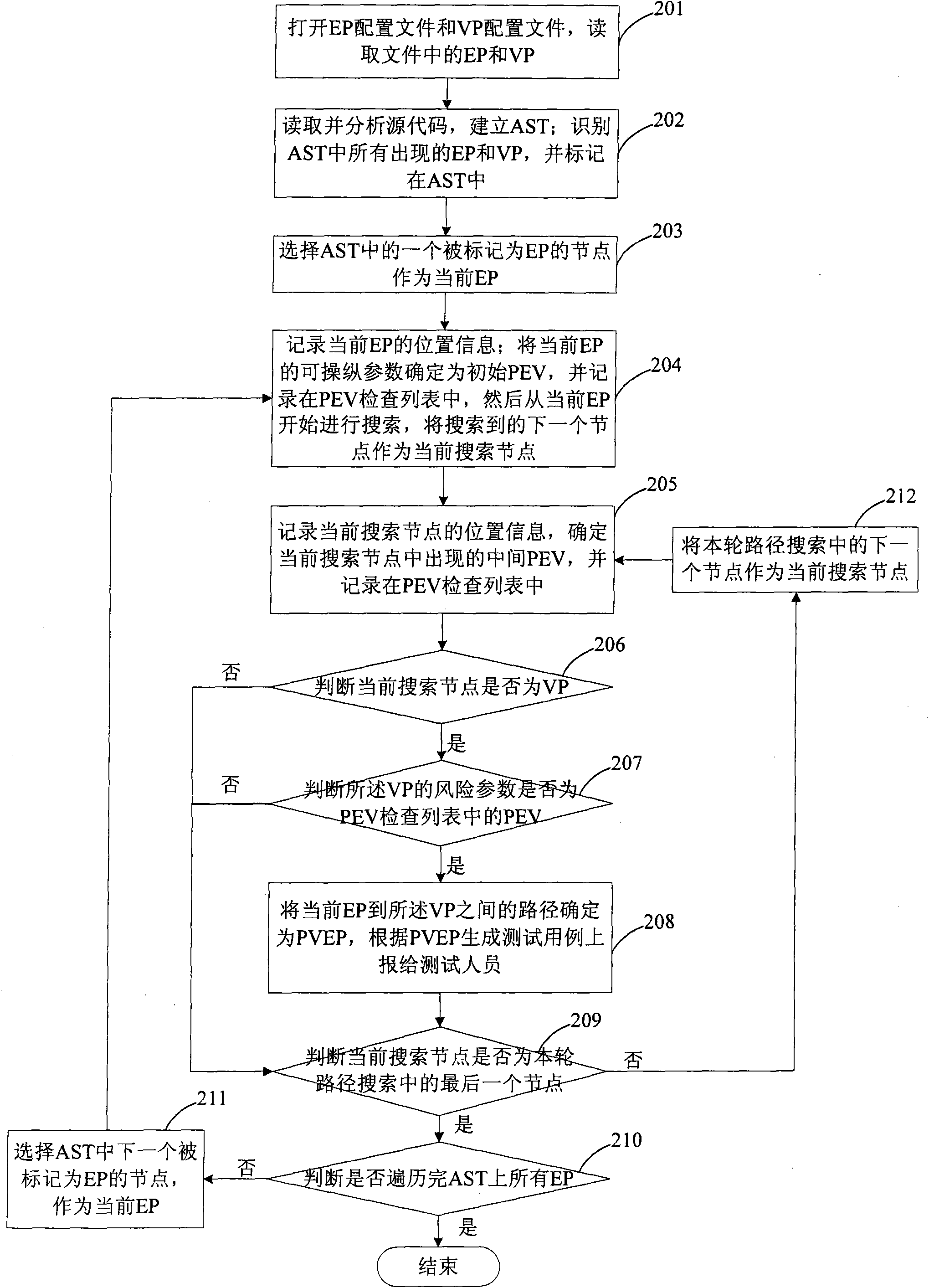
ActiveCN101661543AEasy to analyzeEfficient searchPlatform integrity maintainanceSource codeAbstract syntax tree
The invention discloses a method for detecting security flaws of software source codes. The method comprises the following steps: establishing an abstract syntax tree AST corresponding to source codesof software to be detected; determining controllable points and risk points of each node of the established AST according to predefined controllable points and risk points; and searching an executionpath between the controllable points and the risk points in the AST, and if the risk points on the execution path can be controlled by the controllable points on the execution path, the execution path is determined as a potential risk execution path probably causing the security flaws. The invention also discloses a device for detecting the security flaws of the software. The method and the device can effectively detect the security flaws existing in the source codes of the software.
Owner:SIEMENS CHINA
Method for detecting redundant code defects based on static analysis
InactiveCN102231134AReduce false detection rateReduce missed detection rateSoftware testing/debuggingStatic timing analysisAbstract syntax tree
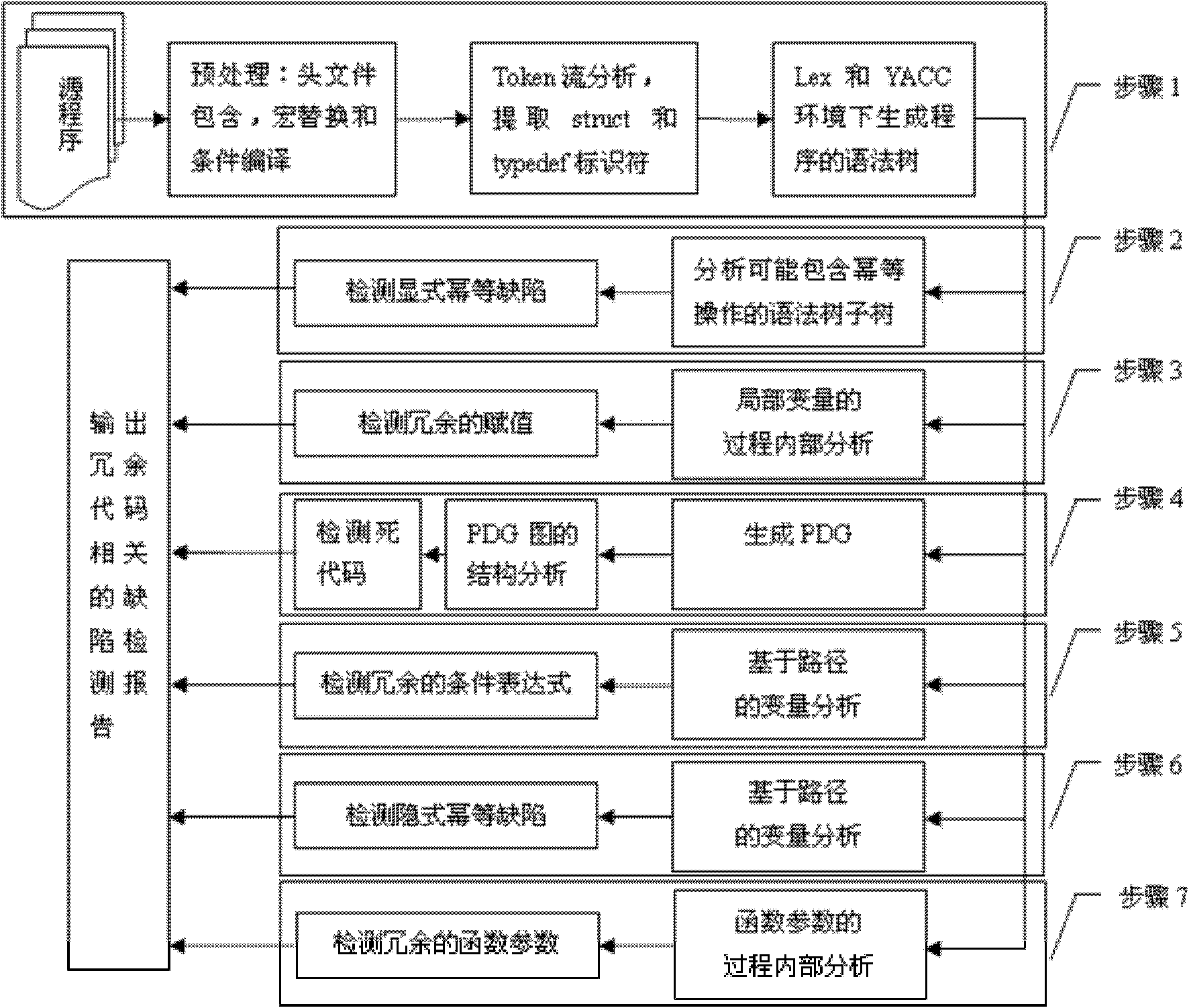
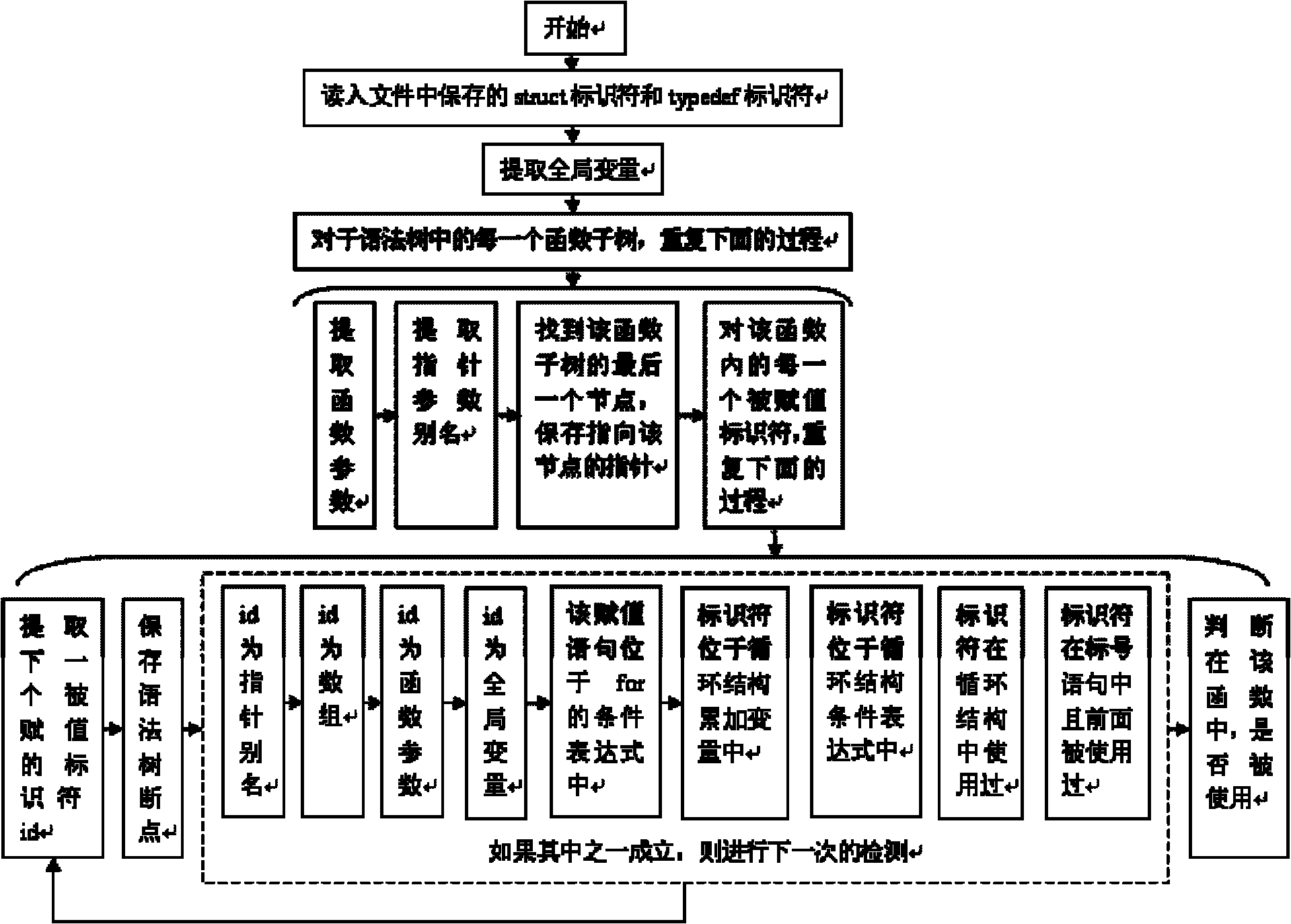
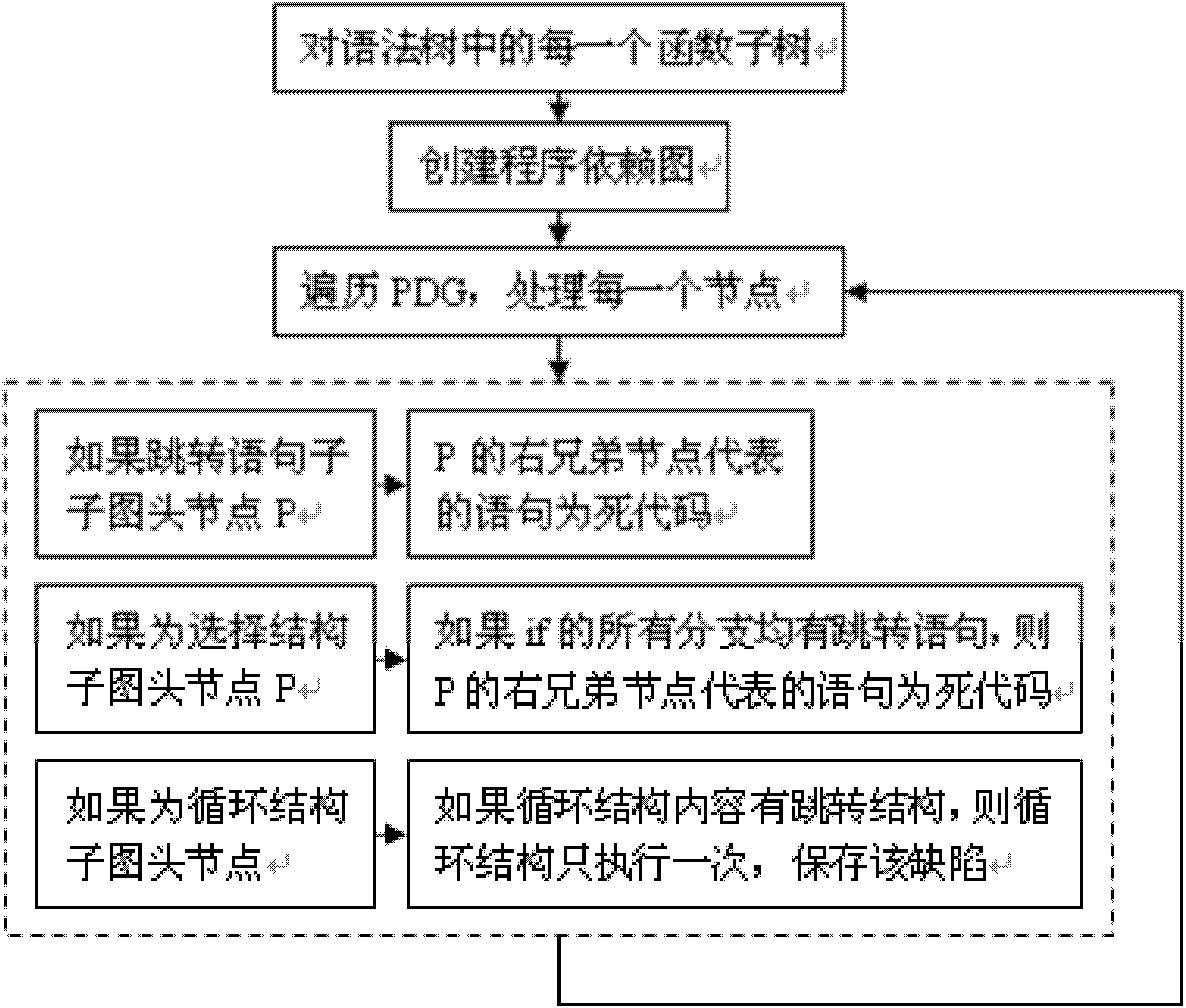
The invention discloses a method for detecting redundant code defects based on static analysis, for solving the problem lacking of a mature method for detecting redundant codes and related defects currently. The method comprises the following steps of: 1, inputting a program to be tested; analyzing the program into an abstract syntax tree; 2, analyzing statements possibly including operations of explicit power and the like; detecting the operations of the explicit power and the like; 3, for locally defined variables, detecting redundant assignment statements by using an internal process analysis method; 4, traversing the abstract syntax tree of the program; searching structures including the defects on the basis of a standardized program dependency graph; detecting dead codes; 5, detecting redundant conditional expressions; 6, detecting operations of implicit power and the like; and 7, detecting redundant function parameters; and giving a defect detection report according to the six defect detection results obtained in the steps 2-7. The method disclosed by the invention is applicable for analyzing large-scale program codes.
Owner:HARBIN INST OF TECH
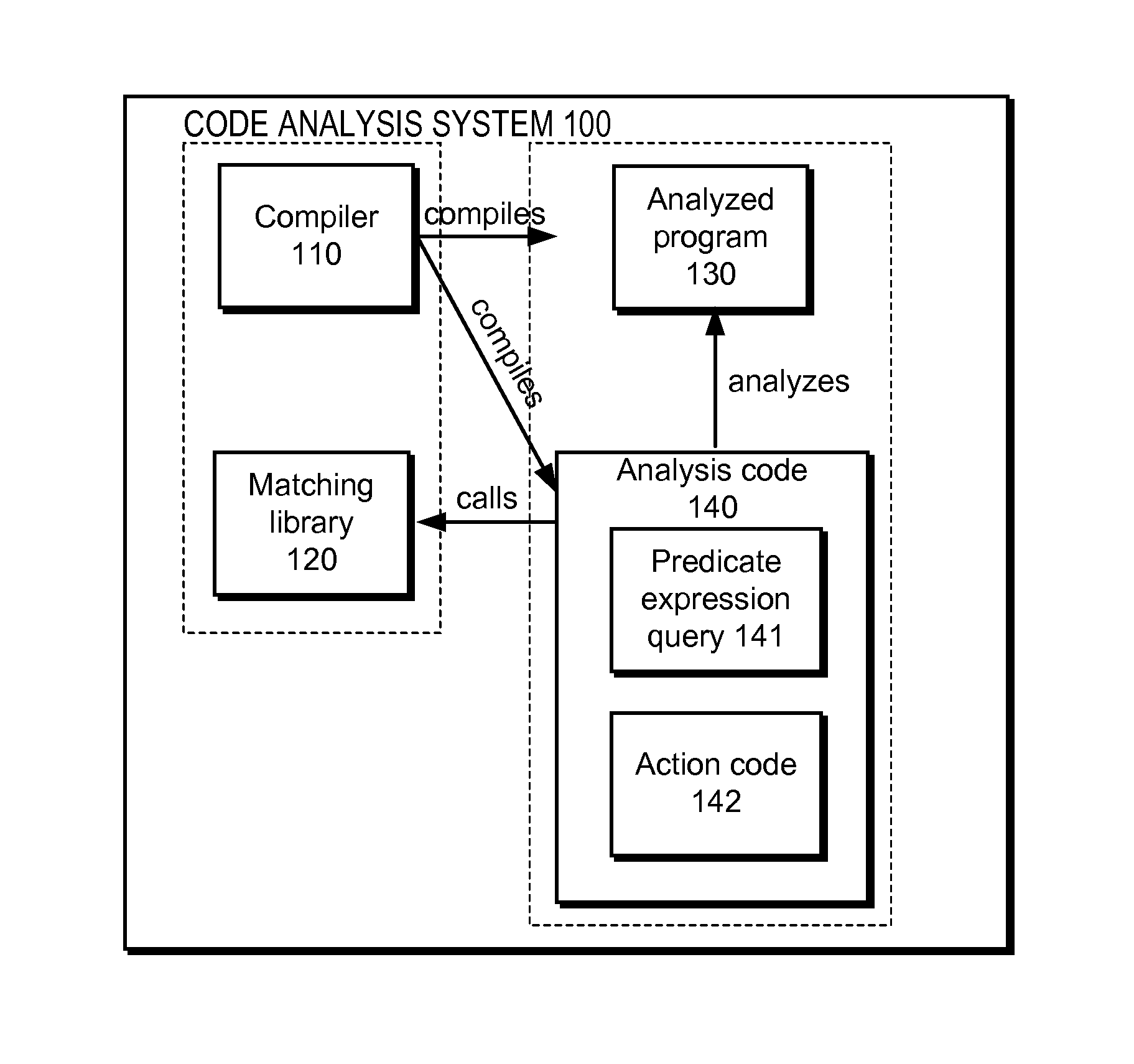
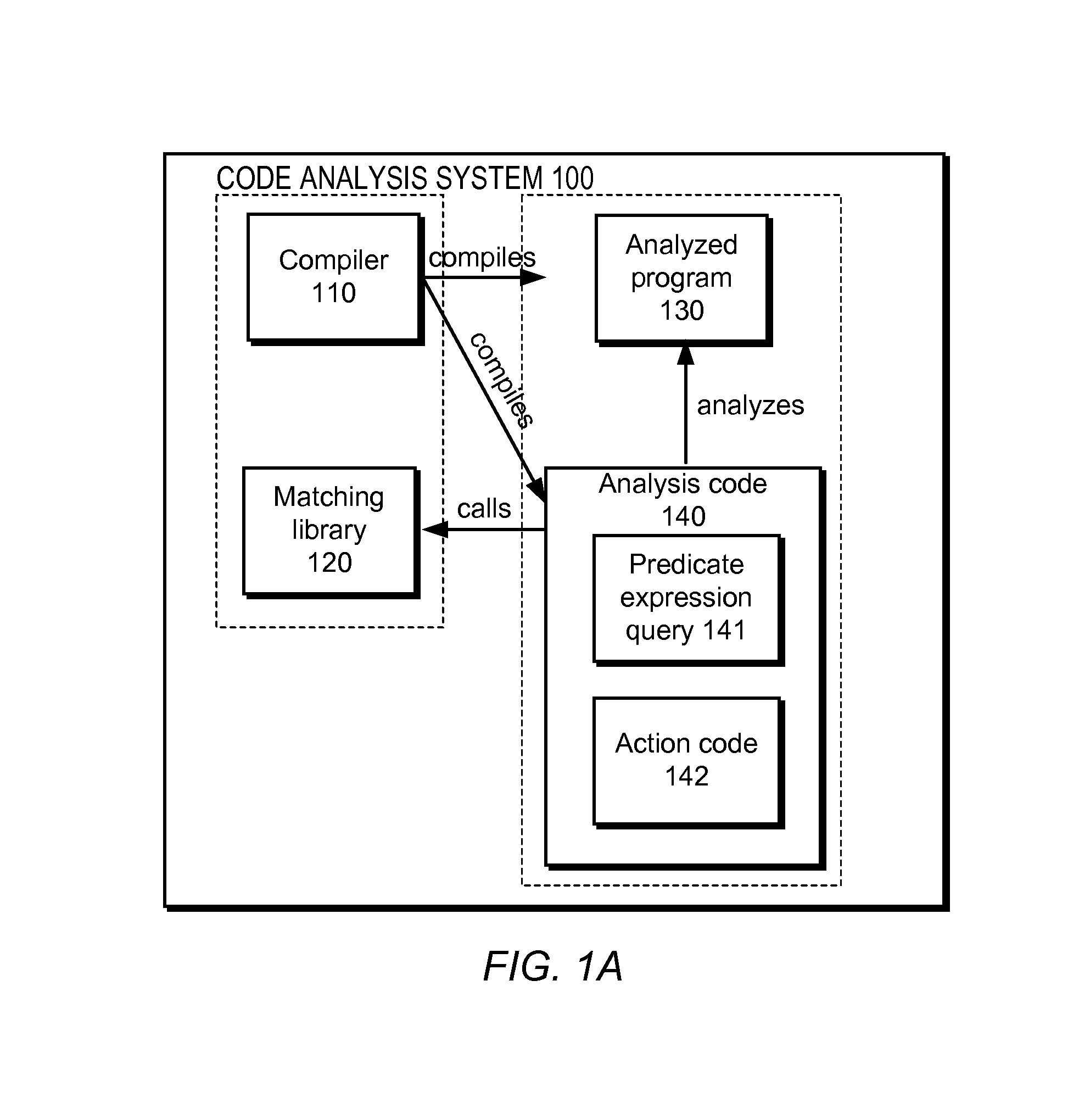
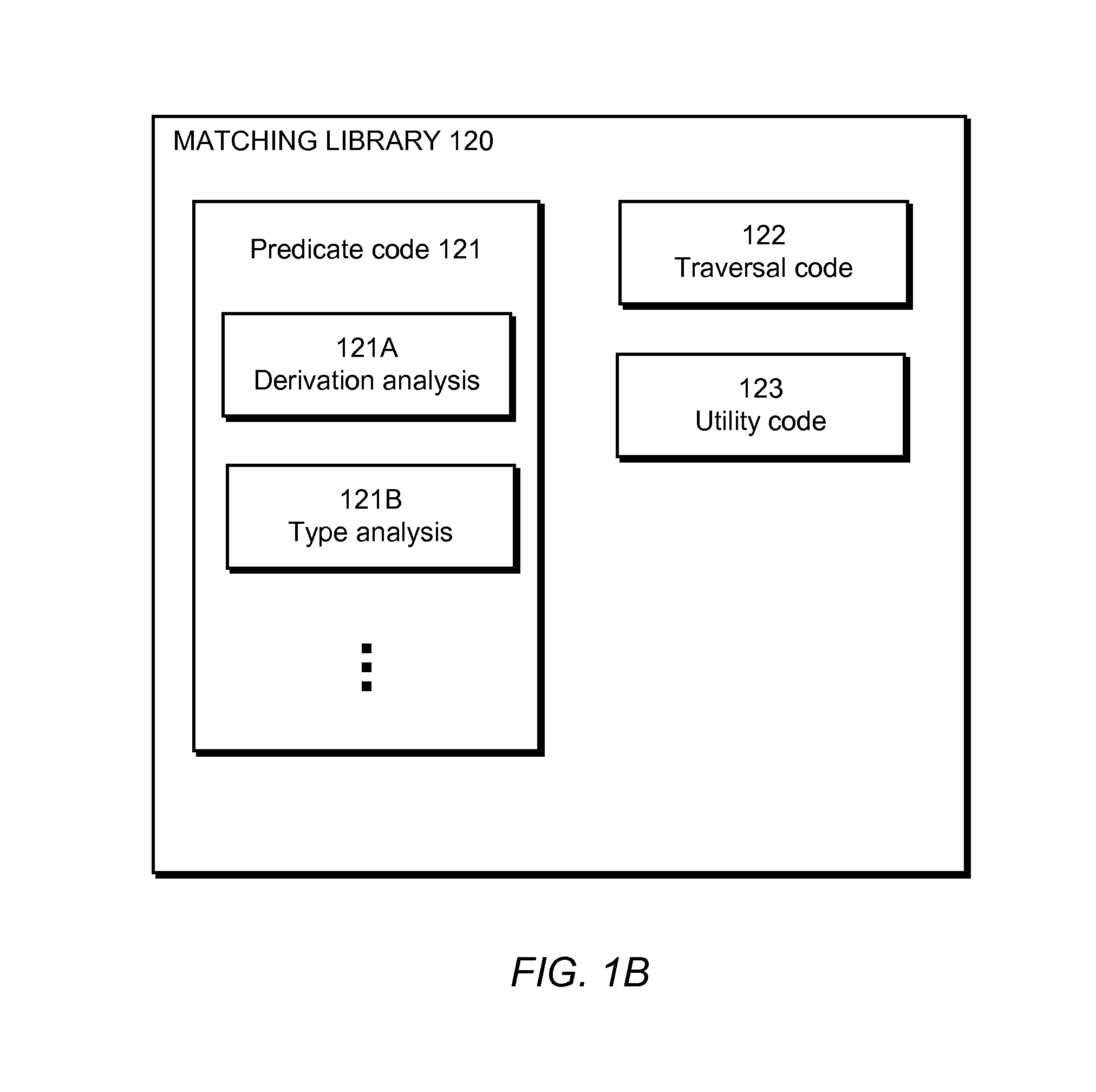
Predicate matching library for complex program analysis
A matching library of a code analysis system defines a number of predicates applicable to an abstract syntax tree (AST) corresponding to program code being analyzed. The predicates represent whether or not nodes of the program code's AST have corresponding properties, such as representing a class that inherits from another given class. The code analysis system obtains an AST to analyze, a predicate expression query that includes predicates of the matching library, and action code. The code analysis system identifies nodes of the AST that match the predicate expression query by executing code of the matching library and executes the action code against the identified nodes.
Owner:GOOGLE LLC
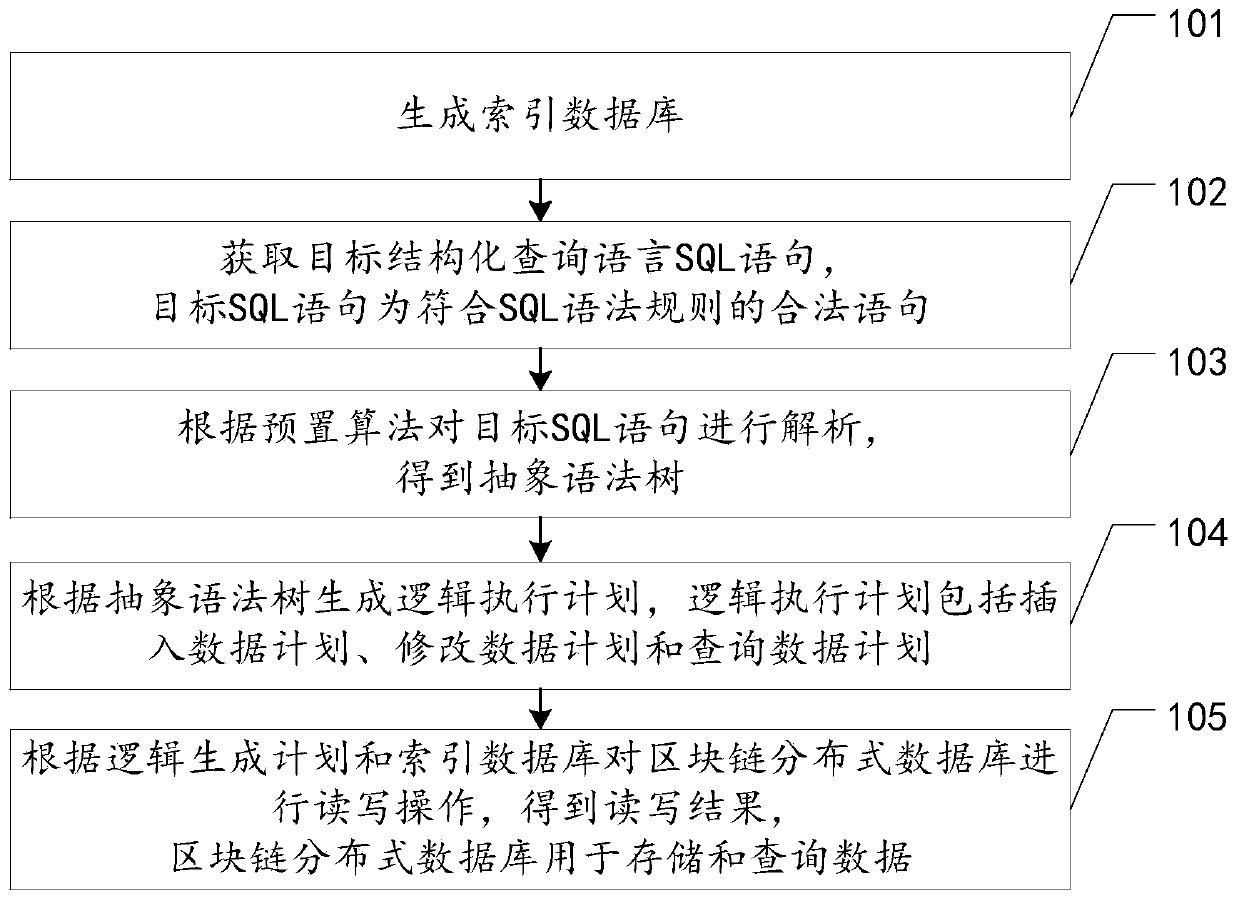
Block chain data storage and query method, device and equipment and storage medium
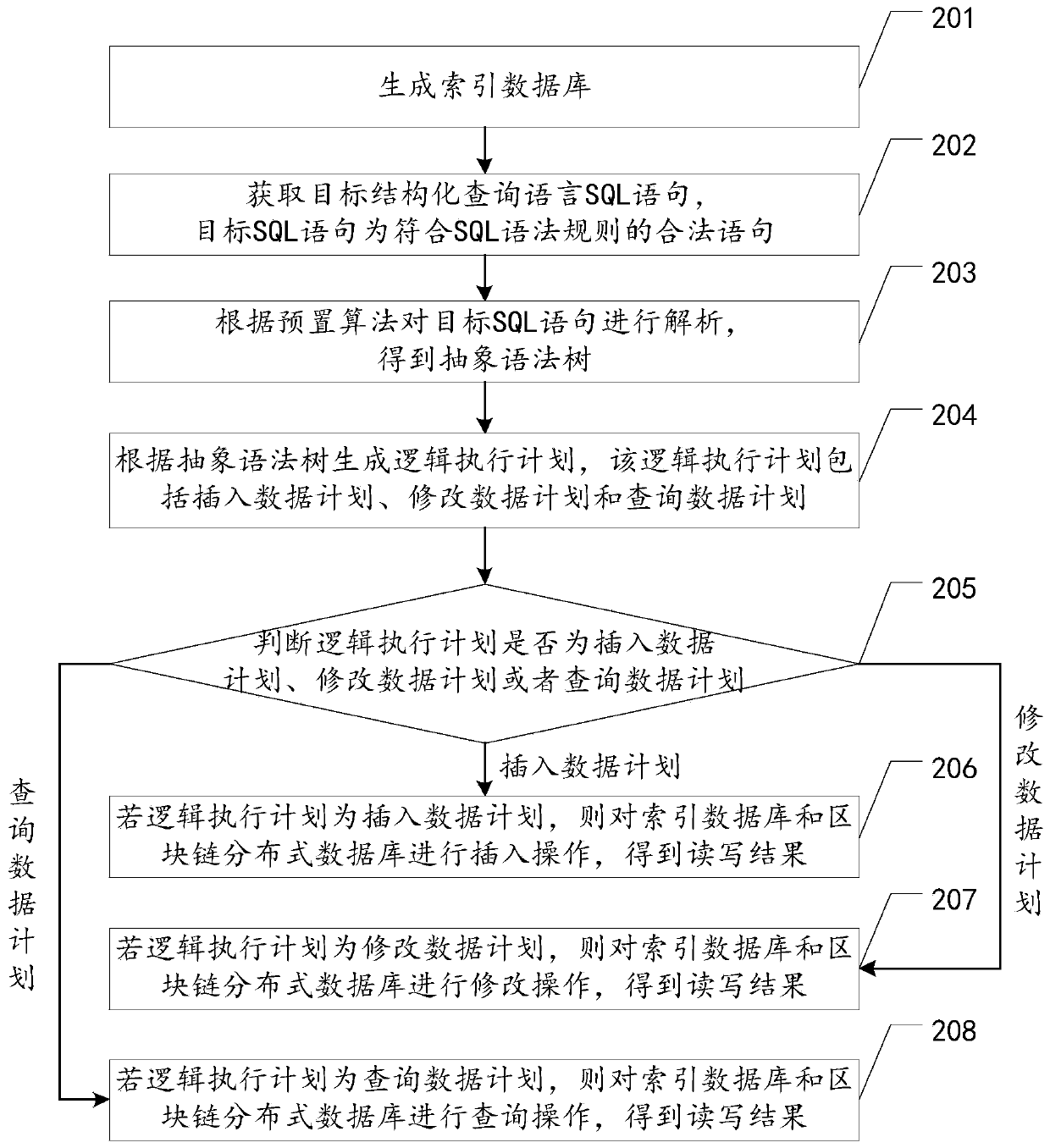
PendingCN110309196AImprove retrieval efficiencyRealize on-chain storageSpecial data processing applicationsDatabase indexingExecution planLayer interface
The invention relates to the field of block chains, in particular to the field of block structure improvement, and discloses block chain data storage and query method, device and equipment and a storage medium. The block chain data storage and query method comprises the steps: generating an index database; obtaining a target structured query language (SQL) statement, wherein the target SQL statement is a legal statement conforming to an SQL grammar rule; analyzing the target SQL statement according to a preset algorithm to obtain an abstract syntax tree; generating a logic execution plan according to the abstract syntax tree, wherein the logic execution plan comprises a data insertion plan, a data modification plan and a data query plan; and performing read-write operation on the block chain distributed database according to the logic generation plan and the index database to obtain a read-write result, the block chain distributed database being used for storing and querying data. By packaging the block chain bottom layer interface, the block chain data storage and query method uses the SQL statements and the index database to achieve data chaining storage and query, can lower thedevelopment threshold, and can improve the retrieval and development efficiency.
Owner:ONE CONNECT SMART TECH CO LTD SHENZHEN
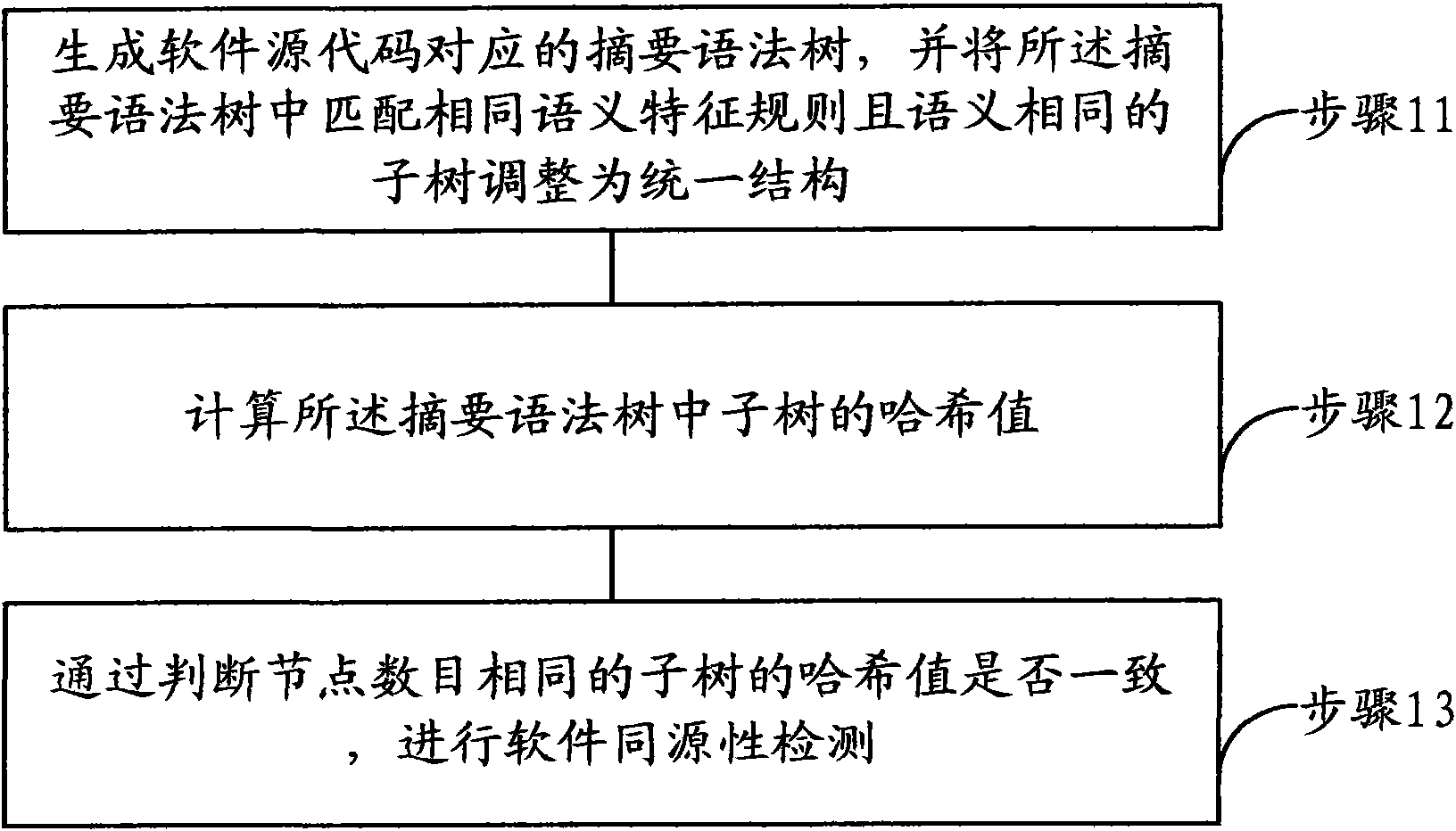
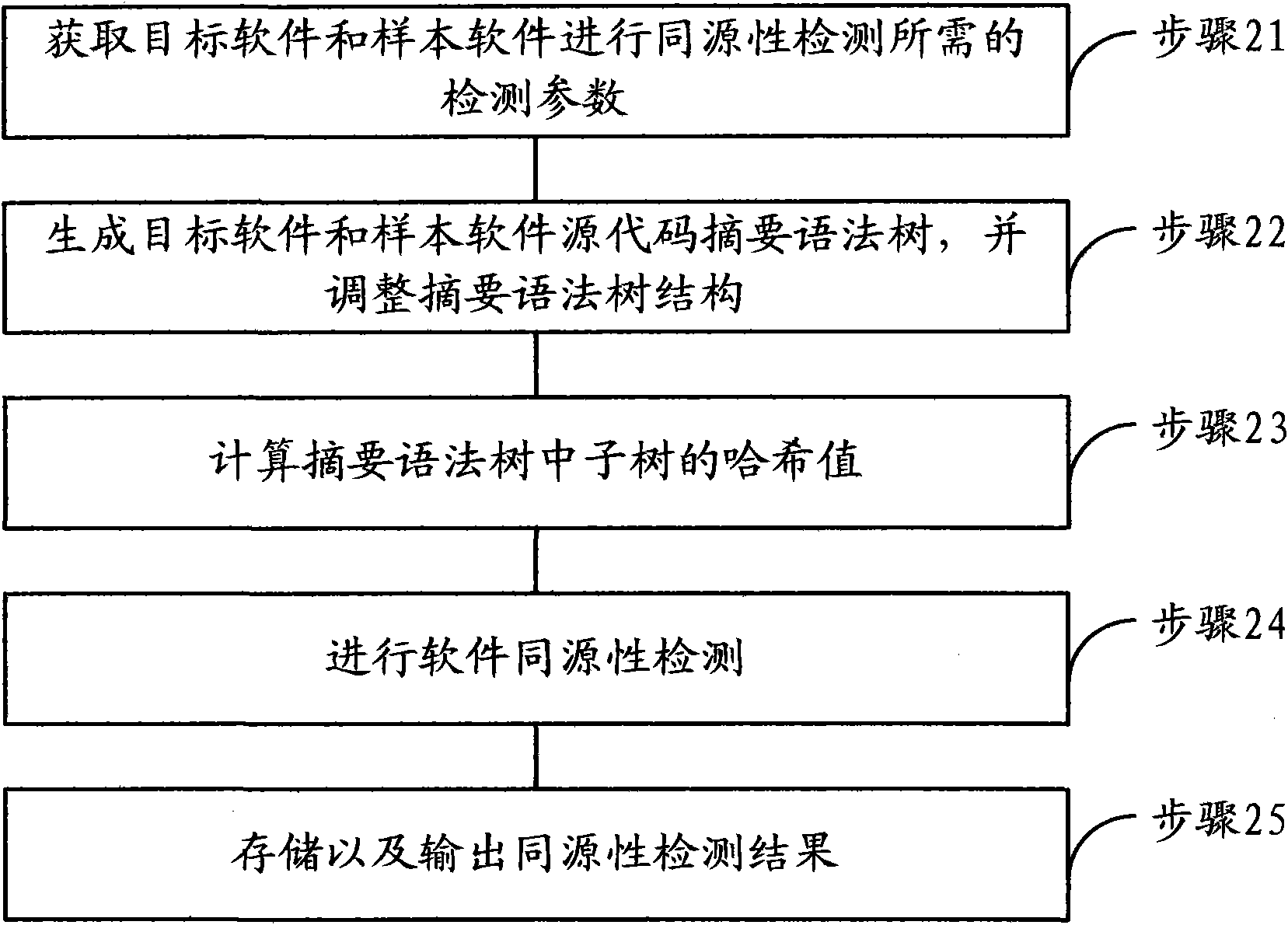
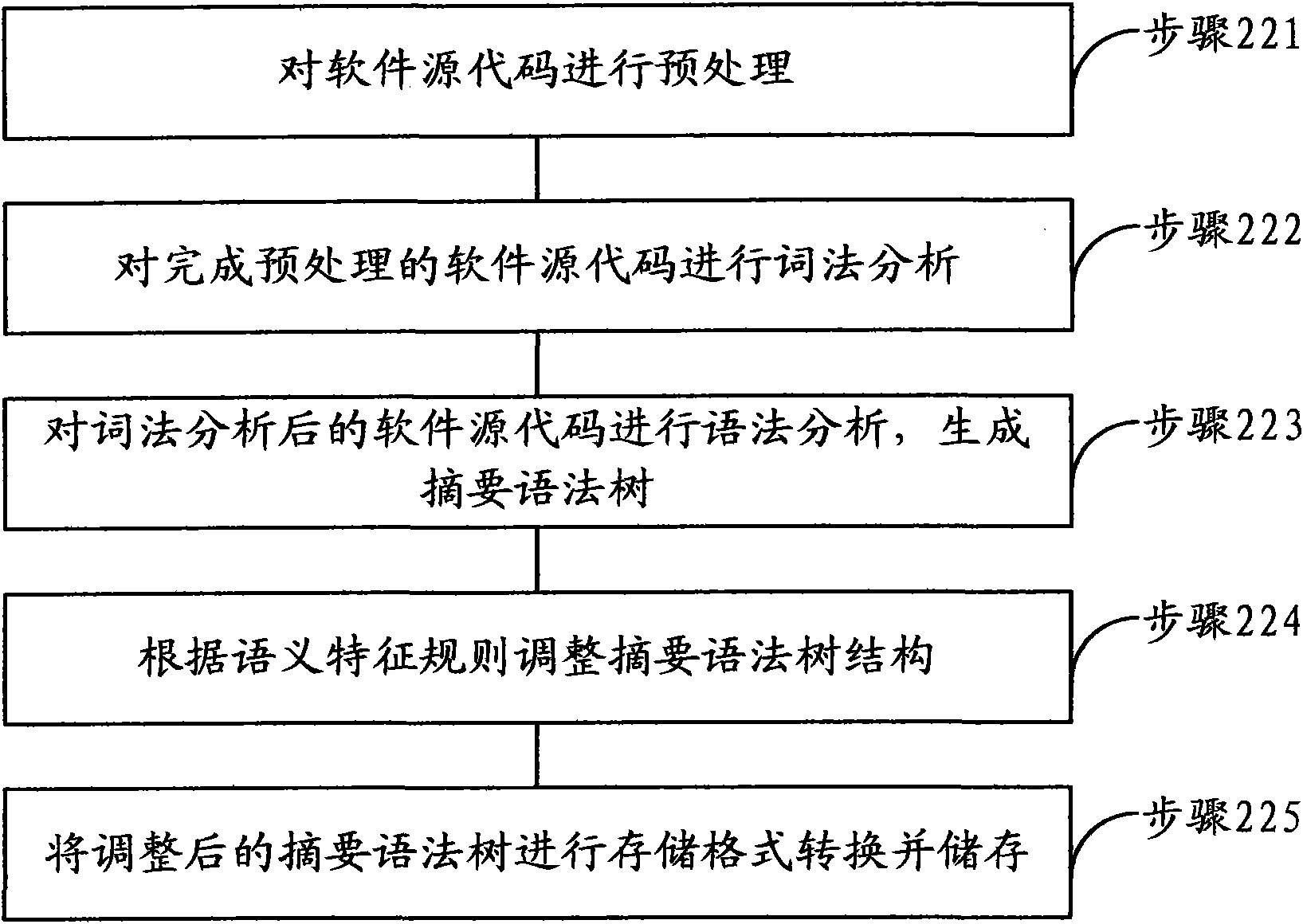
Software homology detection method and device based on abstract syntax tree and semantic matching
InactiveCN101894236AHomology detection is accurate and efficientPlatform integrity maintainanceAlgorithmSemantic matching
The invention relates to a software homology detection method and a device based on an abstract syntax tree and semantic matching. The method comprises the following steps: generating an abstract syntax tree corresponding to software source codes, and regulating subtrees which match with the same semantic feature rule and have the same semantics in the abstract syntax tree to a unified structure; calculating the hash values of subtrees in the abstract syntax tree; and performing software homology detection through judging whether the hash values of subtrees with the same number of nodes are consistent, thereby performing accurate and effective software homology detection by combining semantics in grammatical level.
Owner:北京华夏信安科技有限公司 +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com