Patents
Literature
403 results about "Redundant code" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computer programming, redundant code is source code or compiled code in a computer program that is unnecessary, such as...
Parallel data redundancy removal
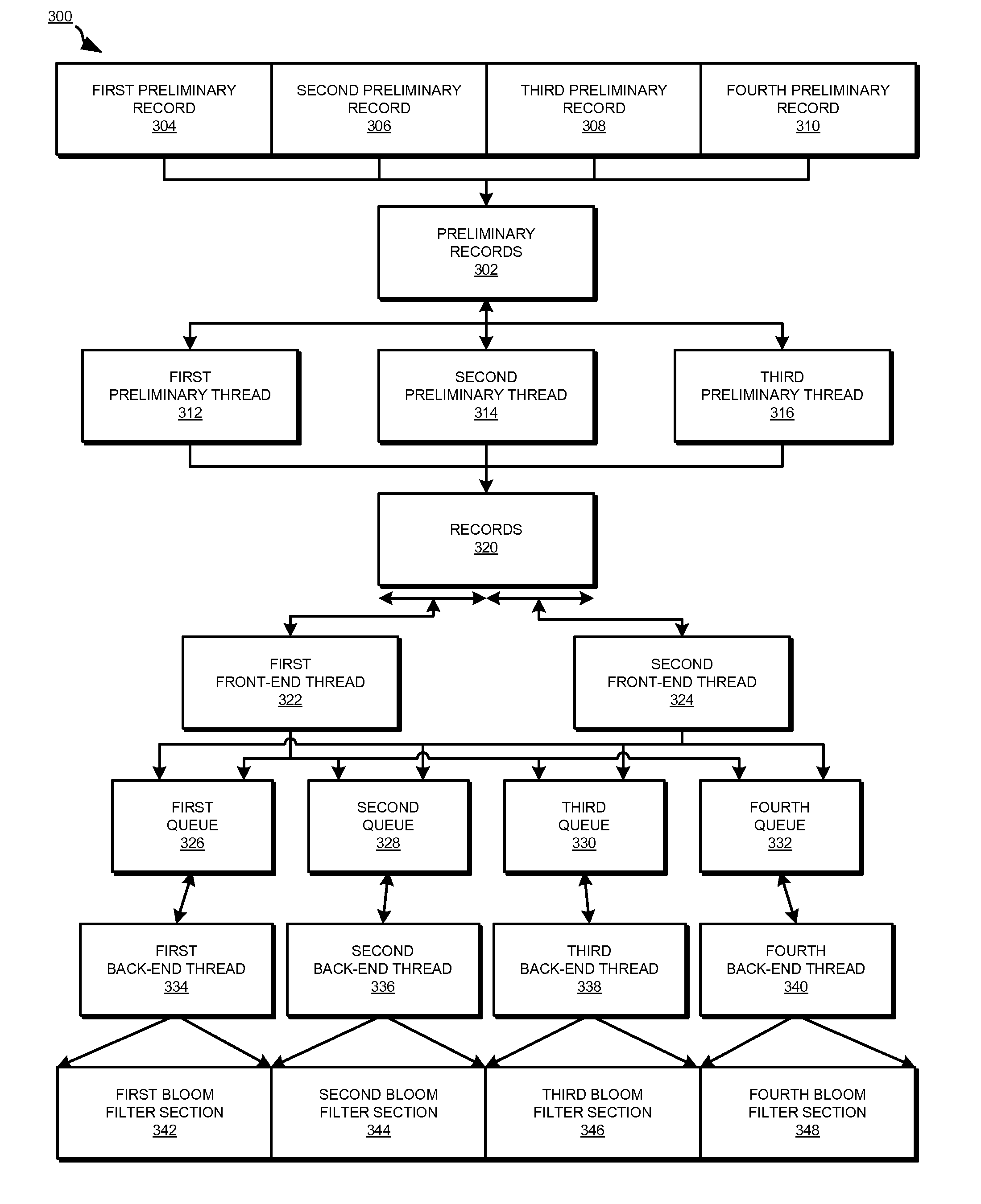
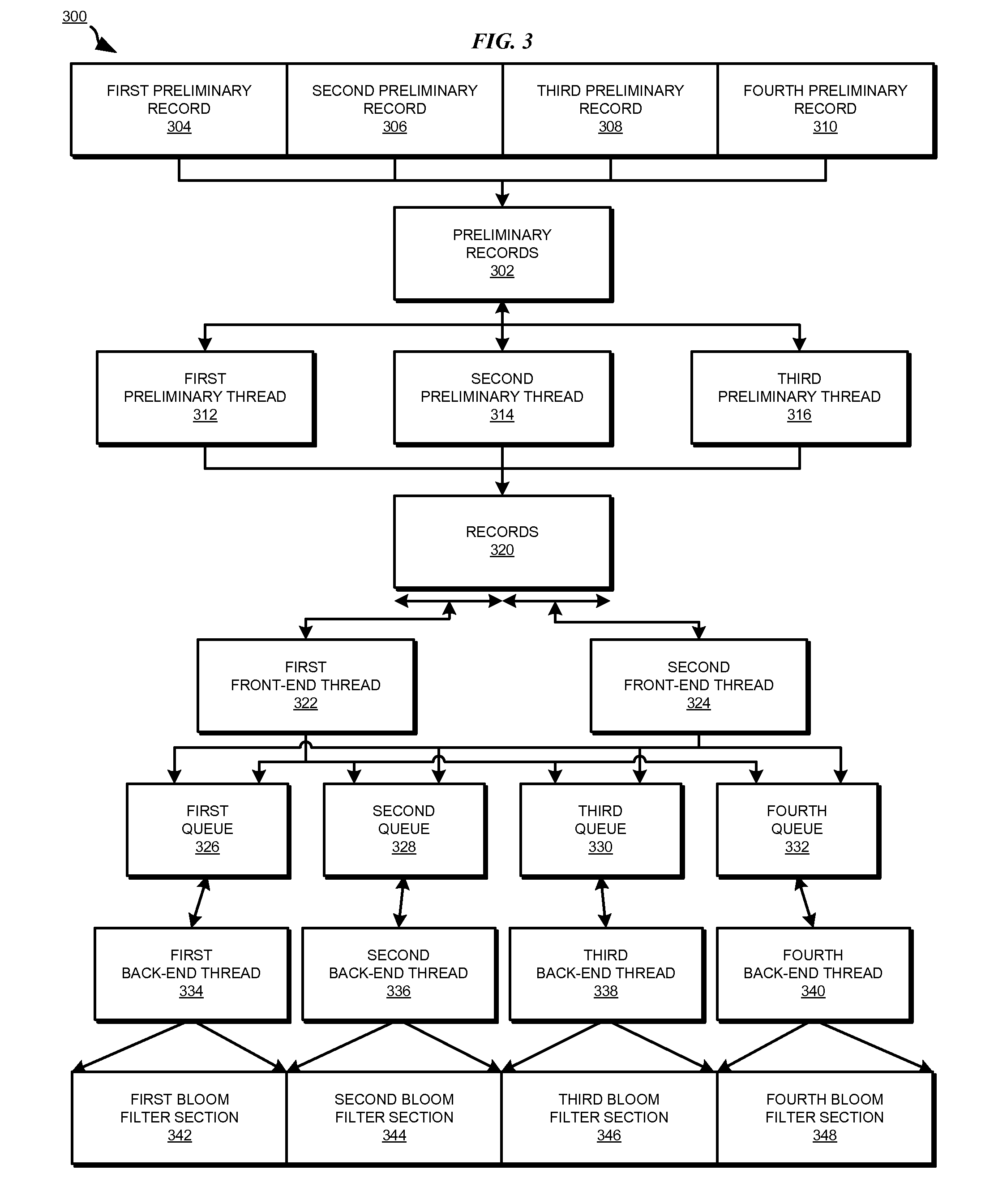
InactiveUS8332367B2Digital data information retrievalDigital data processing detailsRedundant codeBloom filter
A method, system, and computer usable program product for parallel data redundancy removal are provided in the illustrative embodiments. A plurality of values is computed for a record in a plurality of records stored in a storage device. The plurality of values for the record is distributed to corresponding queues in a plurality of queues, wherein each of the plurality of queues is associated with a corresponding section of a Bloom filter. A determination is made whether each value distributed to the corresponding queues for the record is indicated by a corresponding value in the corresponding section of the Bloom filter. The record is identified as a redundant record in response to a determination that each value distributed to the corresponding queues for the record is indicated by a corresponding value in the corresponding section of the Bloom filter.
Owner:INT BUSINESS MASCH CORP
Adaptive Forward Error Correction
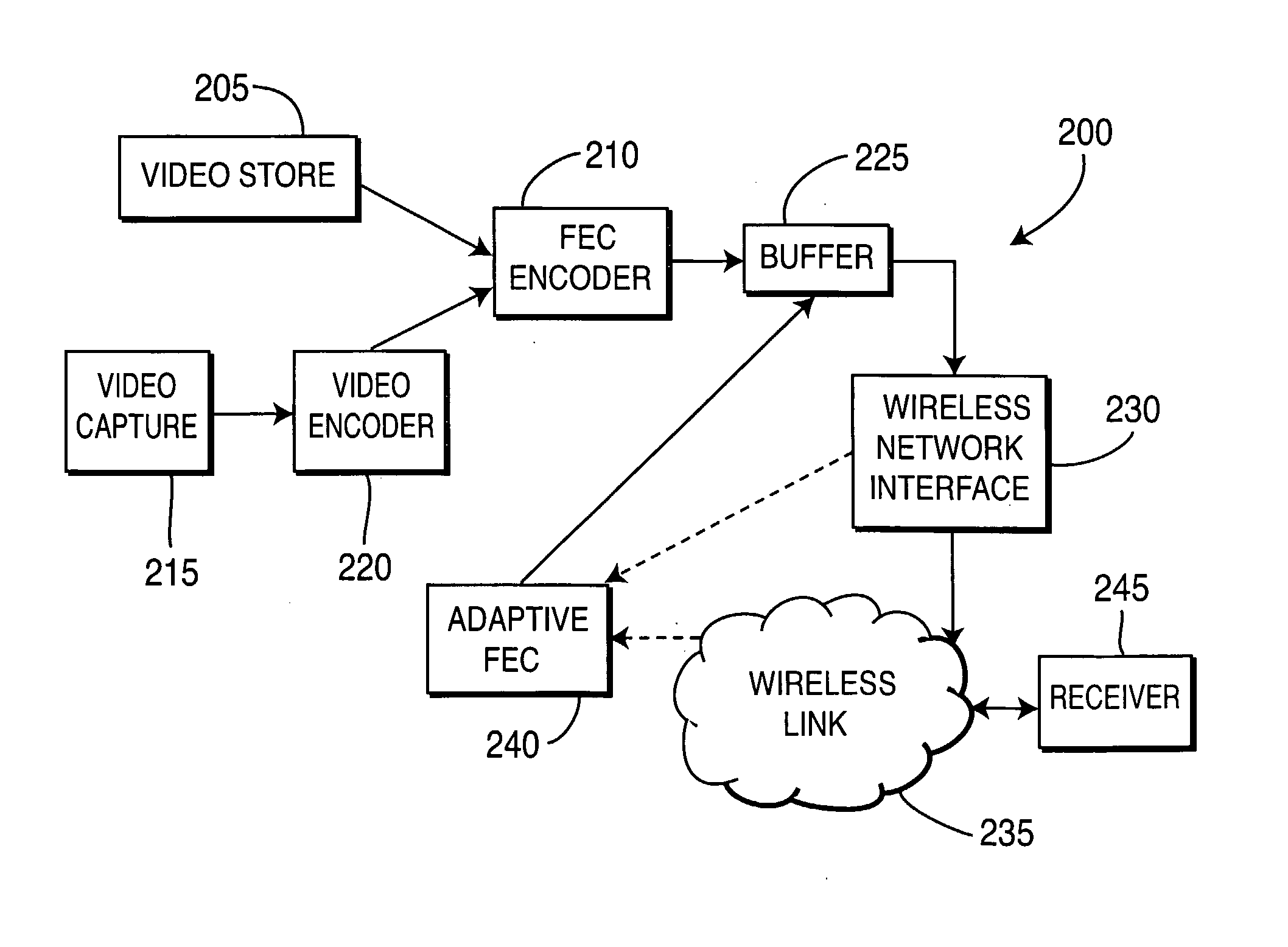
InactiveUS20080134005A1Error prevention/detection by using return channelCode conversionRedundant codeForward error correction
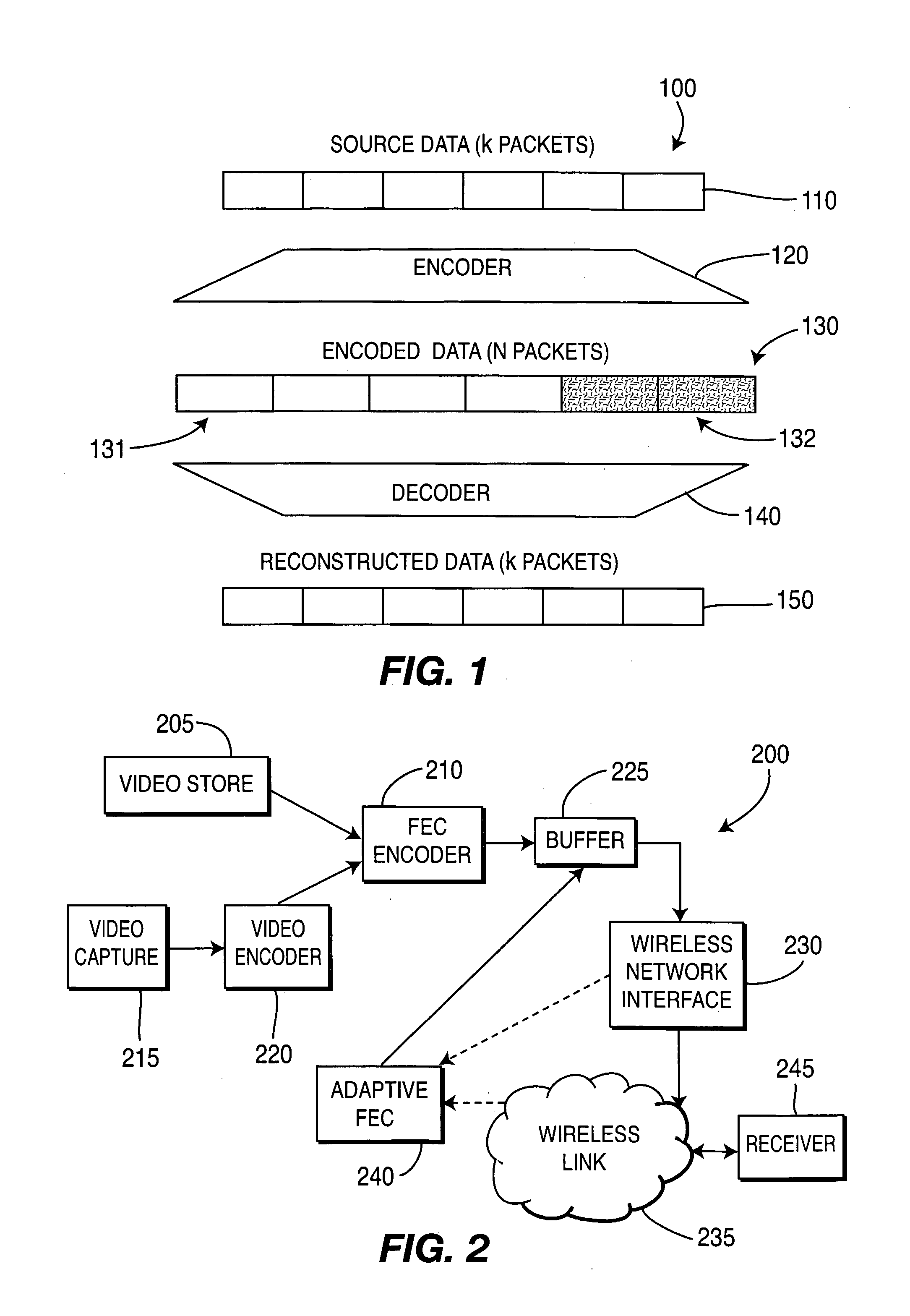
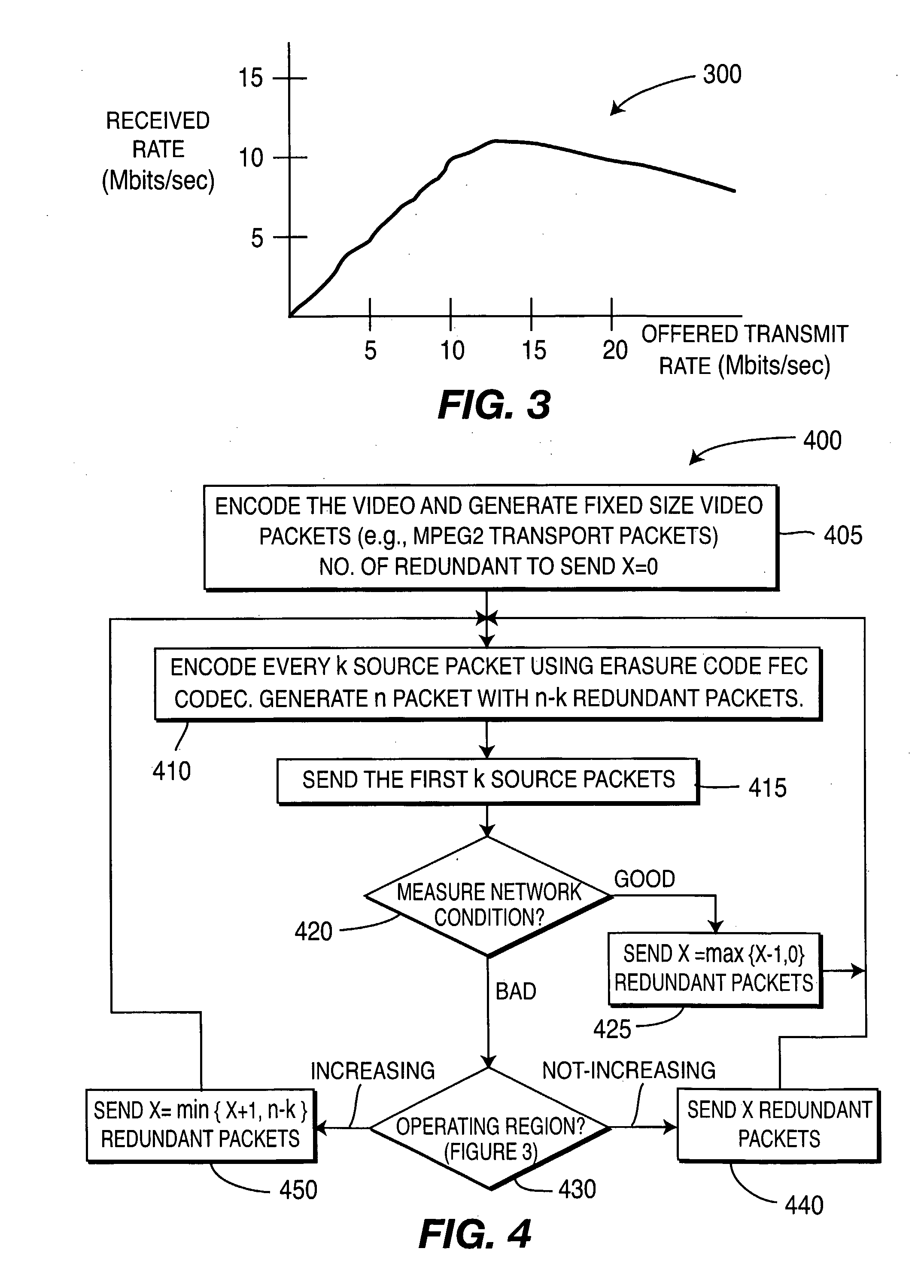
There are described apparatus and methods for adaptive forward error correction (FEC), one use being for video streaming over a wireless network. The apparatus includes an FEC encoder and an adaptive FEC device. The FEC encoder is for encoding k packets of source data into n packets, where n>k, and the n packets include redundant packets. The adaptive FEC device is for adaptively determining a number of the redundant packets to transmit with the encoded k packets, based upon receiving one or more feedback messages. The one or more feedback messages indicate a condition of the wireless network over which the encoded video is to be transmitted.
Owner:INTERDIGITAL CE PATENT HLDG
System and method for automatically verifying storage of redundant contents into communication equipments, by data comparison
InactiveUS9130918B2Digital data processing detailsUser identity/authority verificationContent IdentifierRedundant code
A method is intended for verifying storage of contents into communication equipments connected to at least one communication network. This method consists, when a first communication equipment stores a content and wants to verify that this content is still stored into a second communication equipment: i) in transmitting a first request, comprising at least an identifier of this content and first data representative of this content and requiring verification of the storage of this content into the second communication equipment, to an auxiliary communication equipment acting as an interface between the communication network and the second communication equipment, ii) in transmitting a second request, comprising at least the content identifier, to the second communication equipment, to require transmission of second data representative of the content to the auxiliary communication equipment, and in triggering a timeout having a chosen duration, and iii) if the auxiliary communication equipment has received the second data before expiration of this timeout, in comparing these received second data, possibly after having processed them, to the received first data, and in transmitting a message representative of the result of this comparison to the first communication equipment.
Owner:THOMSON LICENSING SA
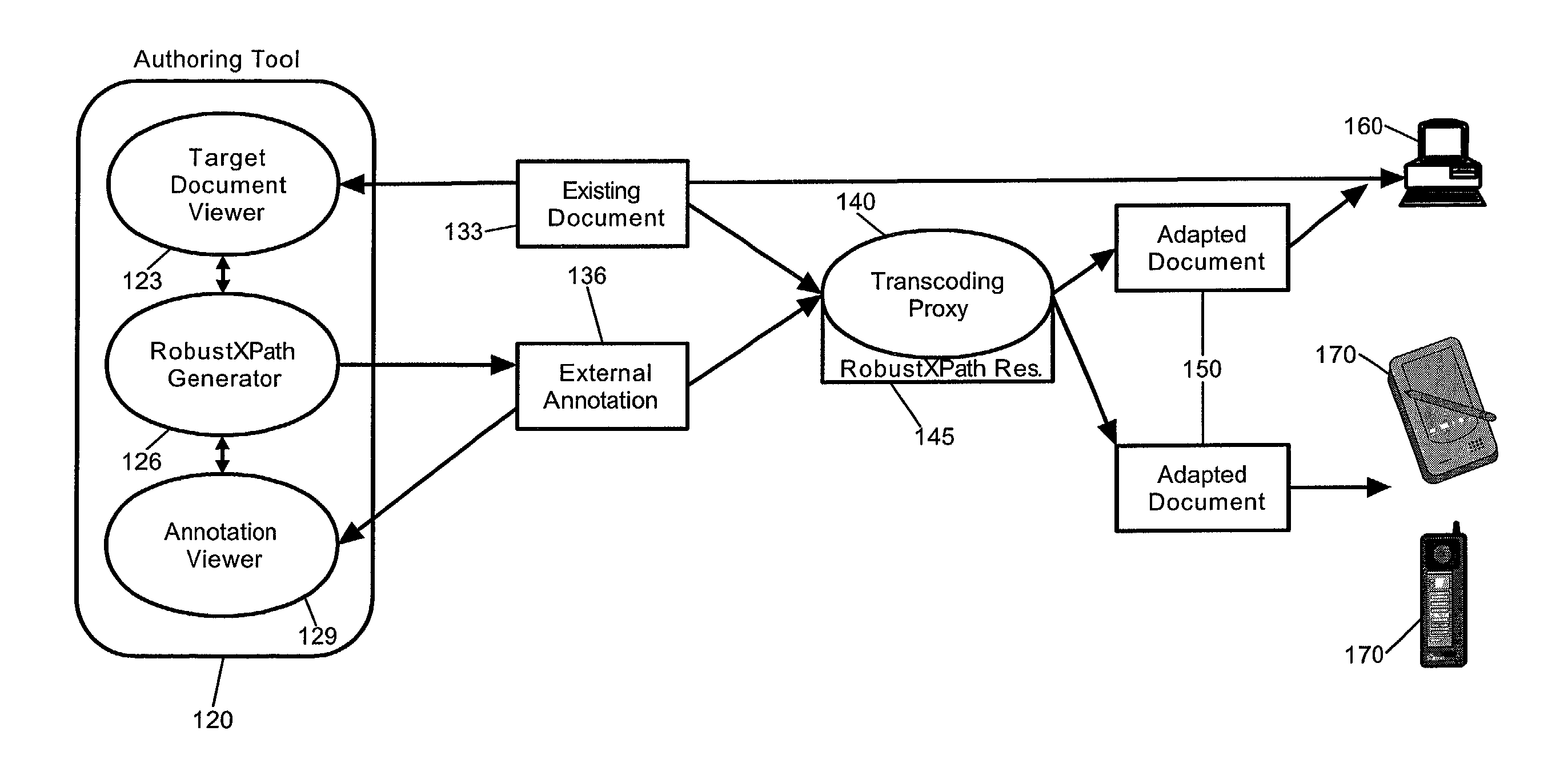
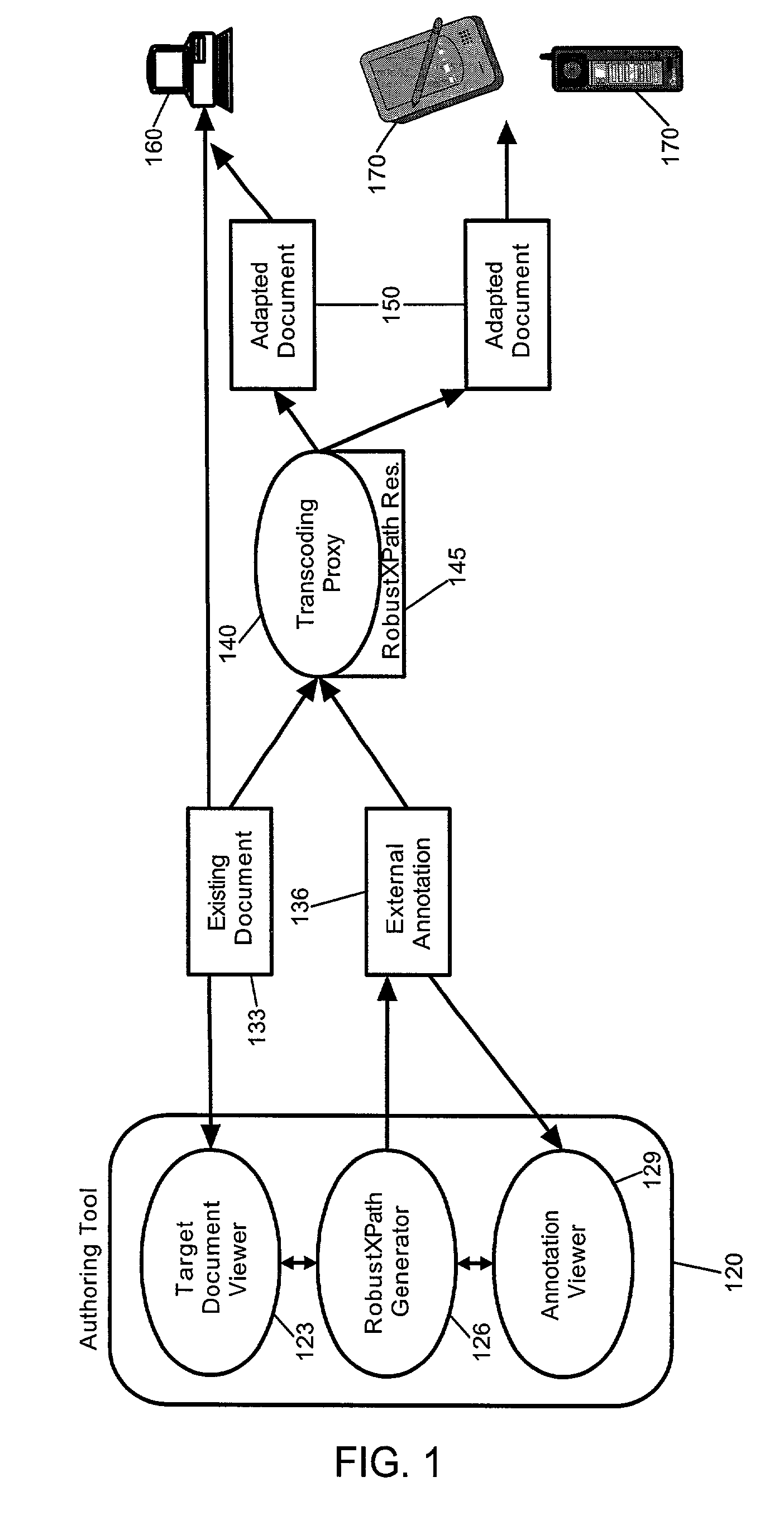
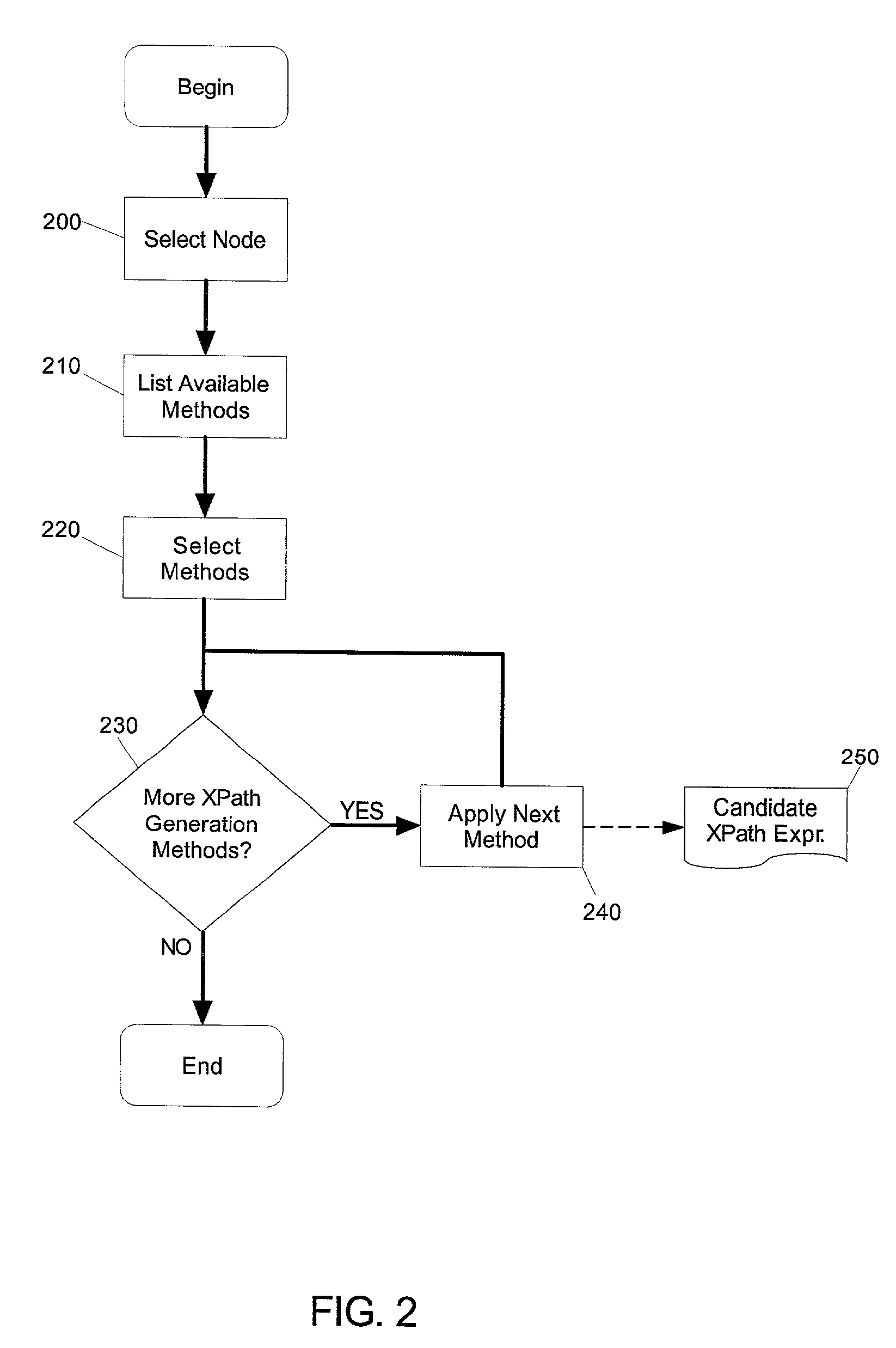
Selectable methods for generating robust XPath expressions
A method and system for generating robust XPath expressions for a selected node in transcodable markup. The system of the invention can include a set of differing XPath expression generators; an interface through which at least one of the XPath expression generators can be selected; and, an XPath generator processor configured to apply each of the selected XPath expression generators to the selected node in the transcodable markup to produce a redundant set of robust XPath expressions configured to identify the selected node. Notably, the system also can include an XPath resolution processor. The XPath resolution processor can resolve each XPath expression in the redundant set. The resolutions, in turn, can identify a set of candidate nodes, the XPath resolution processor identifying the selected node from among the set of candidate nodes based upon the XPath expressions resolving to the selected node more than any other node in the set of candidate nodes.
Owner:IBM CORP
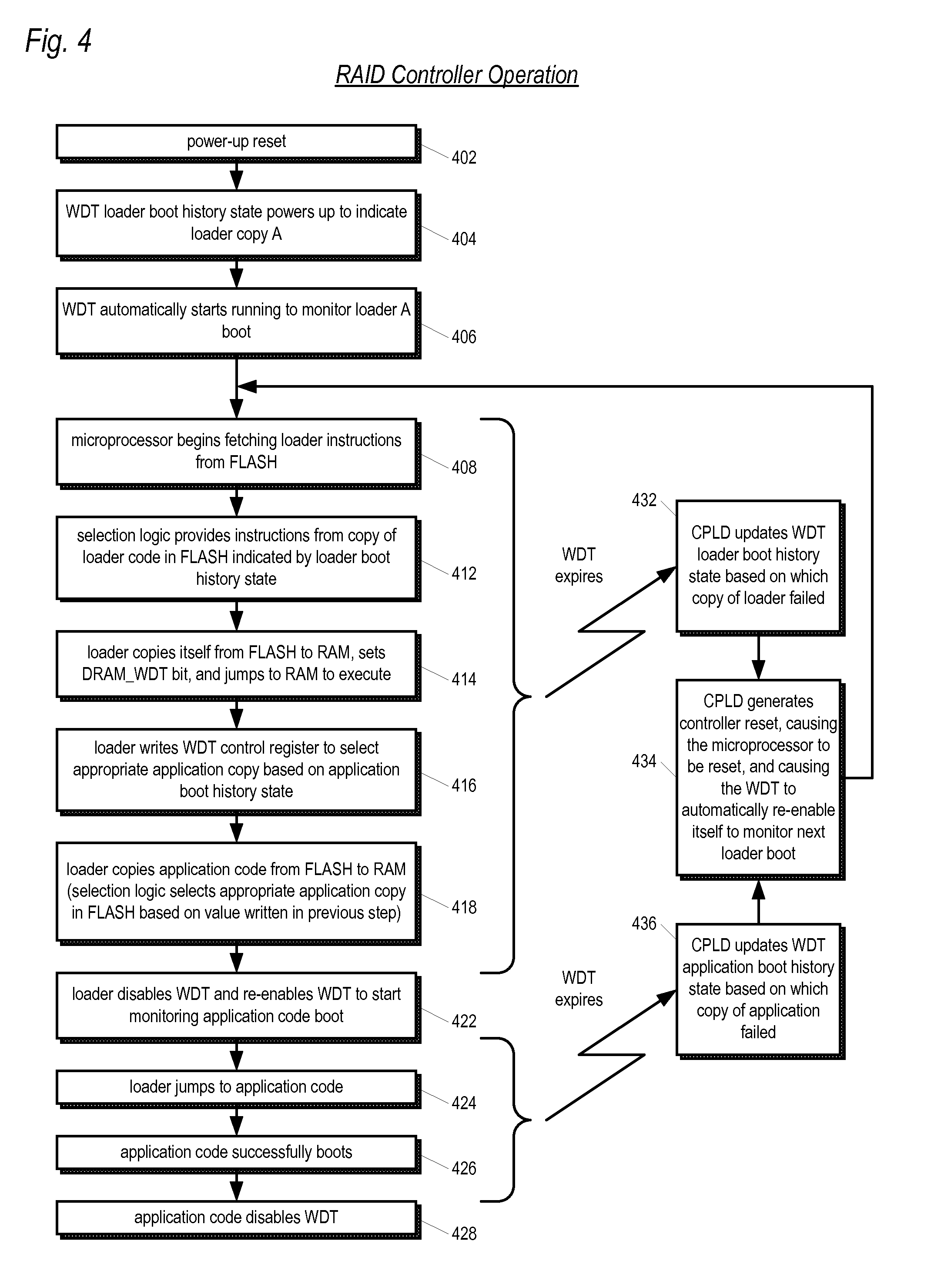
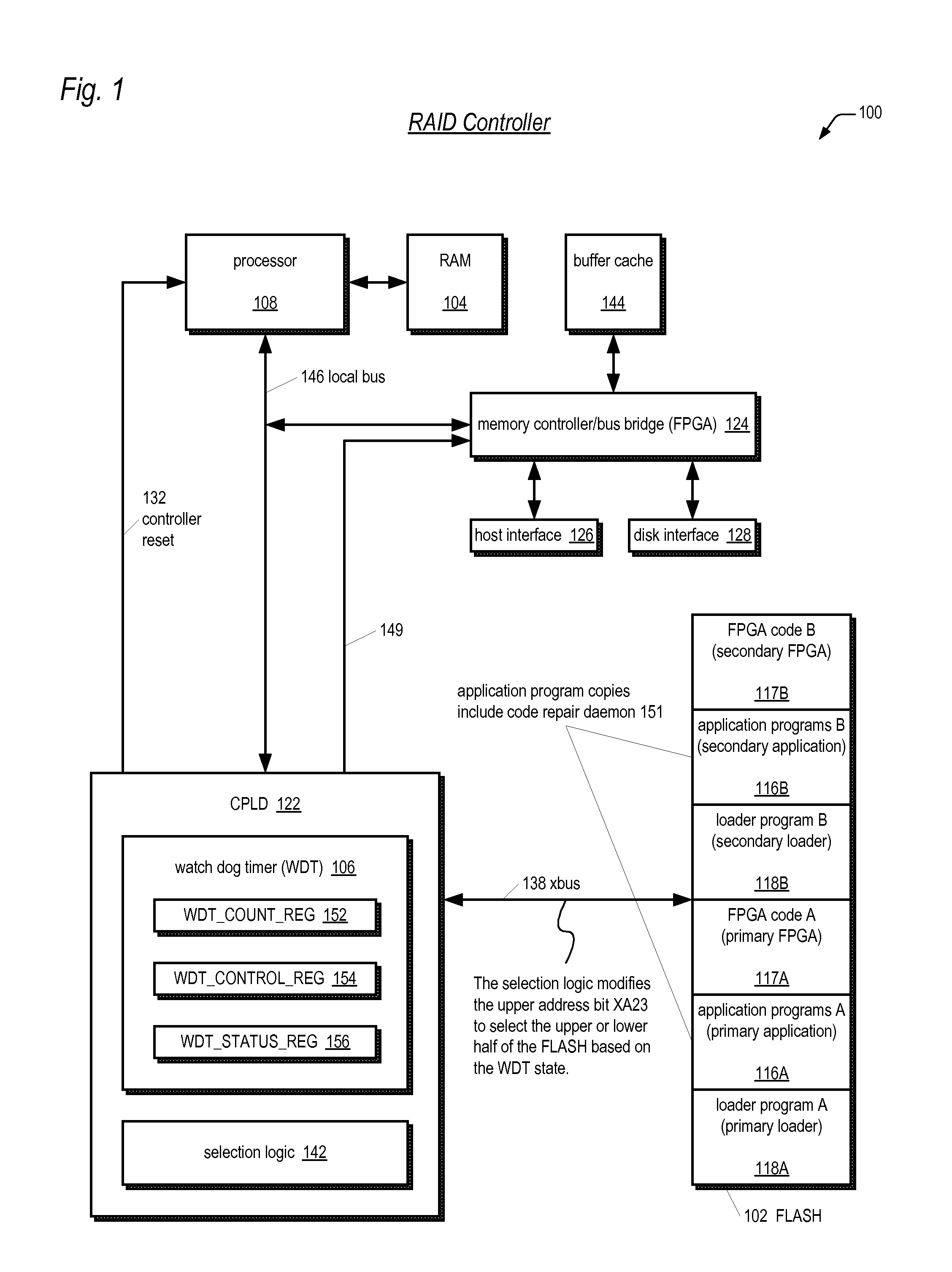
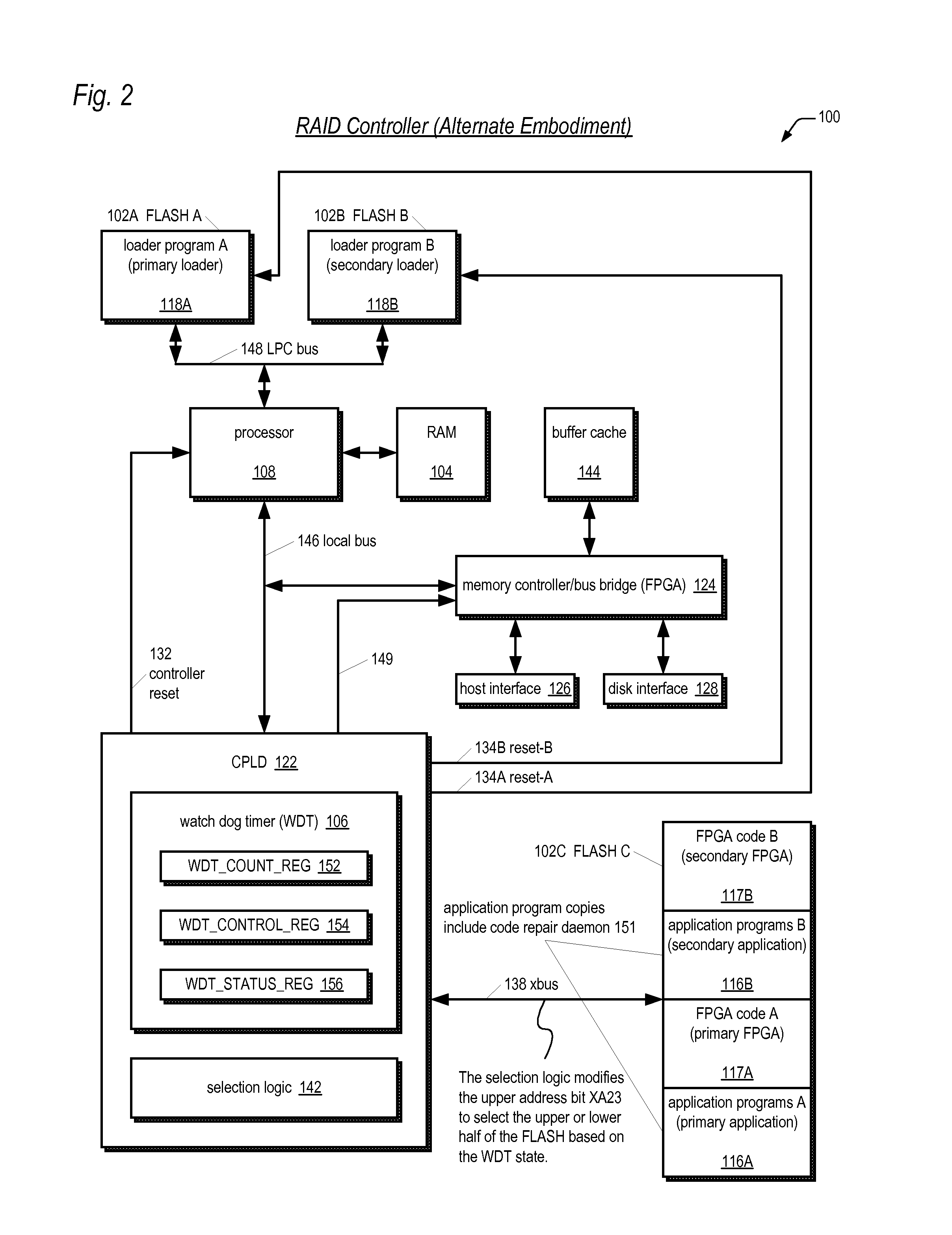
Storage system with automatic redundant code component failure detection, notification, and repair
InactiveUS20060236198A1Reduce the likelihood of failureImprove usabilityDigital computer detailsCode conversionMicrocontrollerRAID
A RAID system includes a non-volatile memory storing a first program and first and second copies of a second program, and a processor executing the first program. The first program detects the first copy of the second program is failed and repairs the failed first copy in the non-volatile memory using the second copy. The failures may be detected at boot time or during normal operation of the controller. In one embodiment, the failure is detected via a CRC check. In one embodiment, the controller repairs the failed copy by copying the good copy to the location of the failed copy. In one embodiment, the system includes multiple controllers, each having its own processor and non-volatile memory and program that detects and repairs failed program copies. The programs include a loader, an application, FPGA code, CPLD code, and a program for execution by a power supply microcontroller.
Owner:DOT HILL SYST
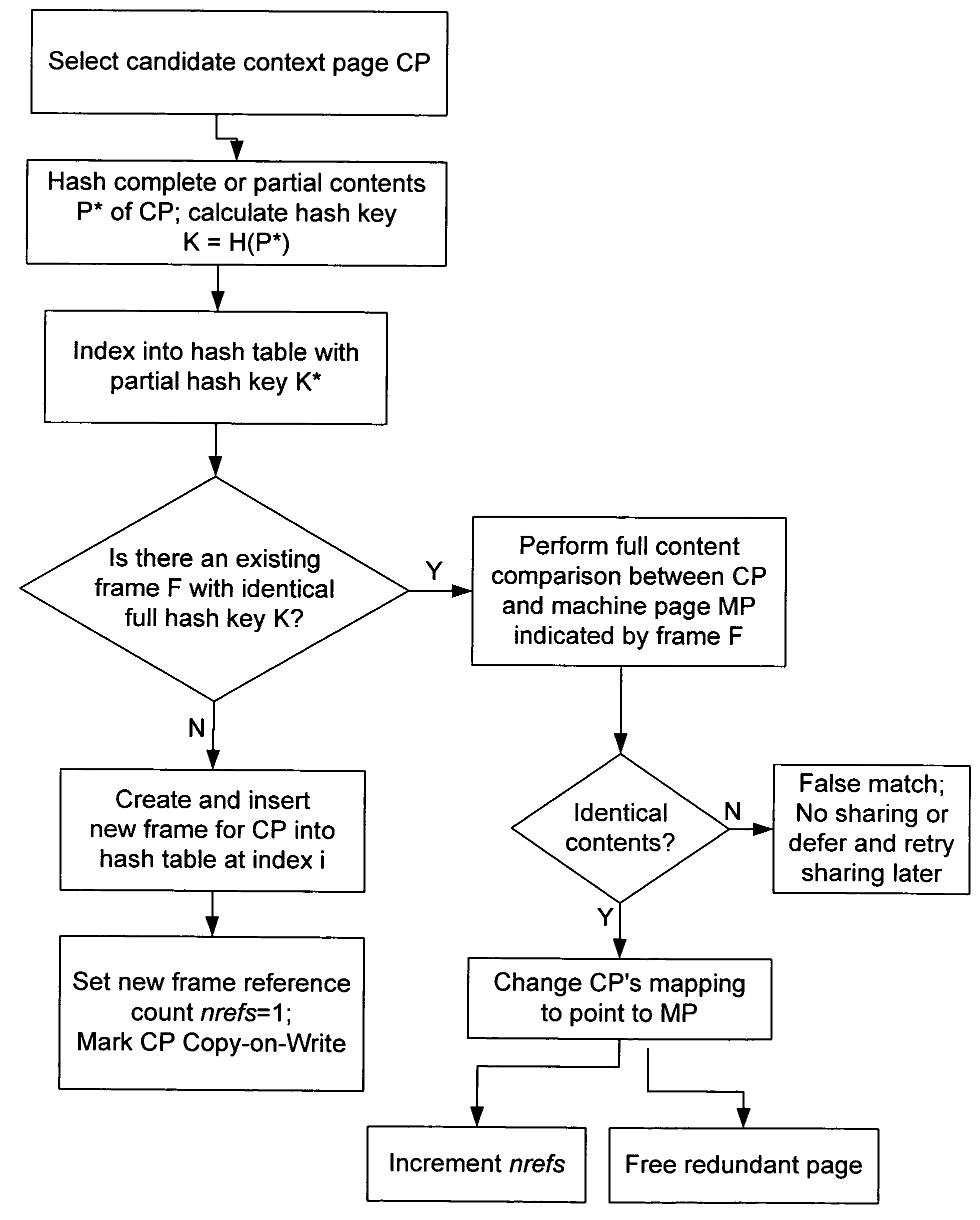
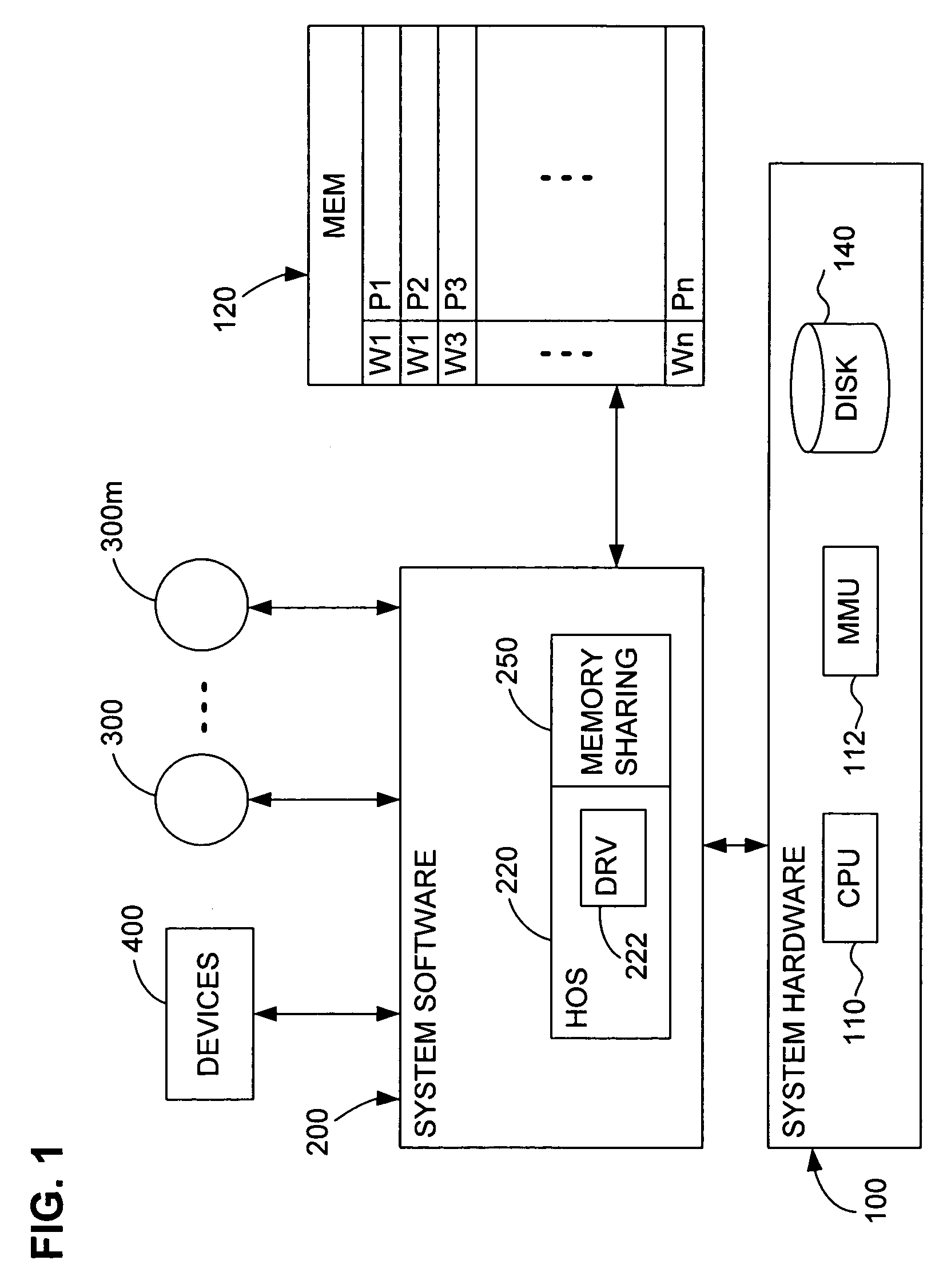
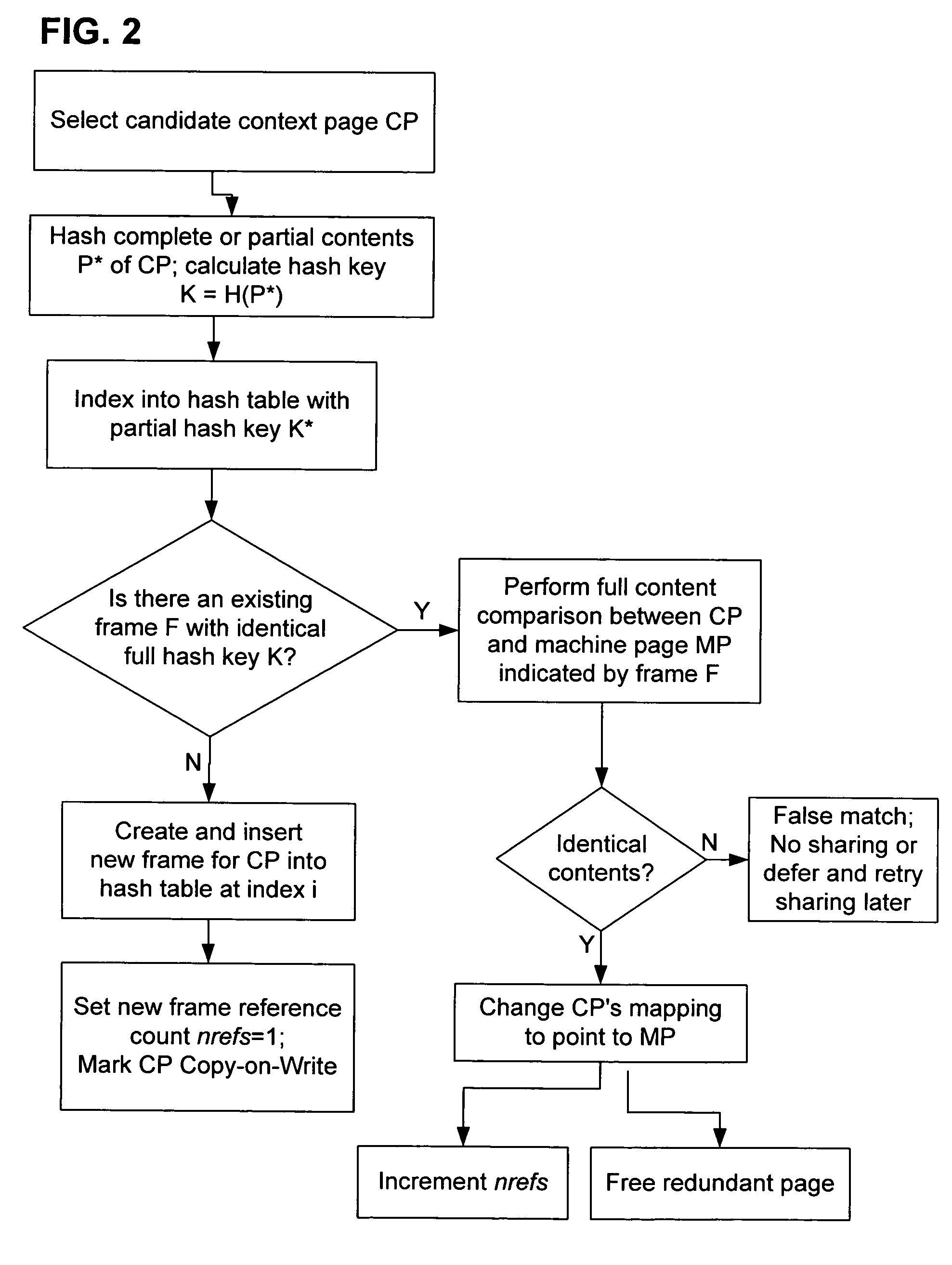
Transparent sharing of memory pages using content comparison
InactiveUS7620766B1Memory architecture accessing/allocationMemory adressing/allocation/relocationMultiple contextVirtual memory
A computer system has one or more software contexts that share use of a memory that is divided into units such as pages. In the preferred embodiment of the invention, the contexts are, or include, virtual machines running on a common hardware platform. The contents, as opposed to merely the addresses or page numbers, of virtual memory pages that are accessible to one or more contexts are examined. If two or more context pages are identical, then their memory mappings are changed to point to a single, shared copy of the page in the hardware memory, thereby freeing the memory space taken up by the redundant copies. The shared copy is then preferably marked copy-on-write. Sharing is preferably dynamic, whereby the presence of redundant copies of pages is preferably determined by hashing page contents and performing full content comparisons only when two or more pages hash to the same key.
Owner:VMWARE INC
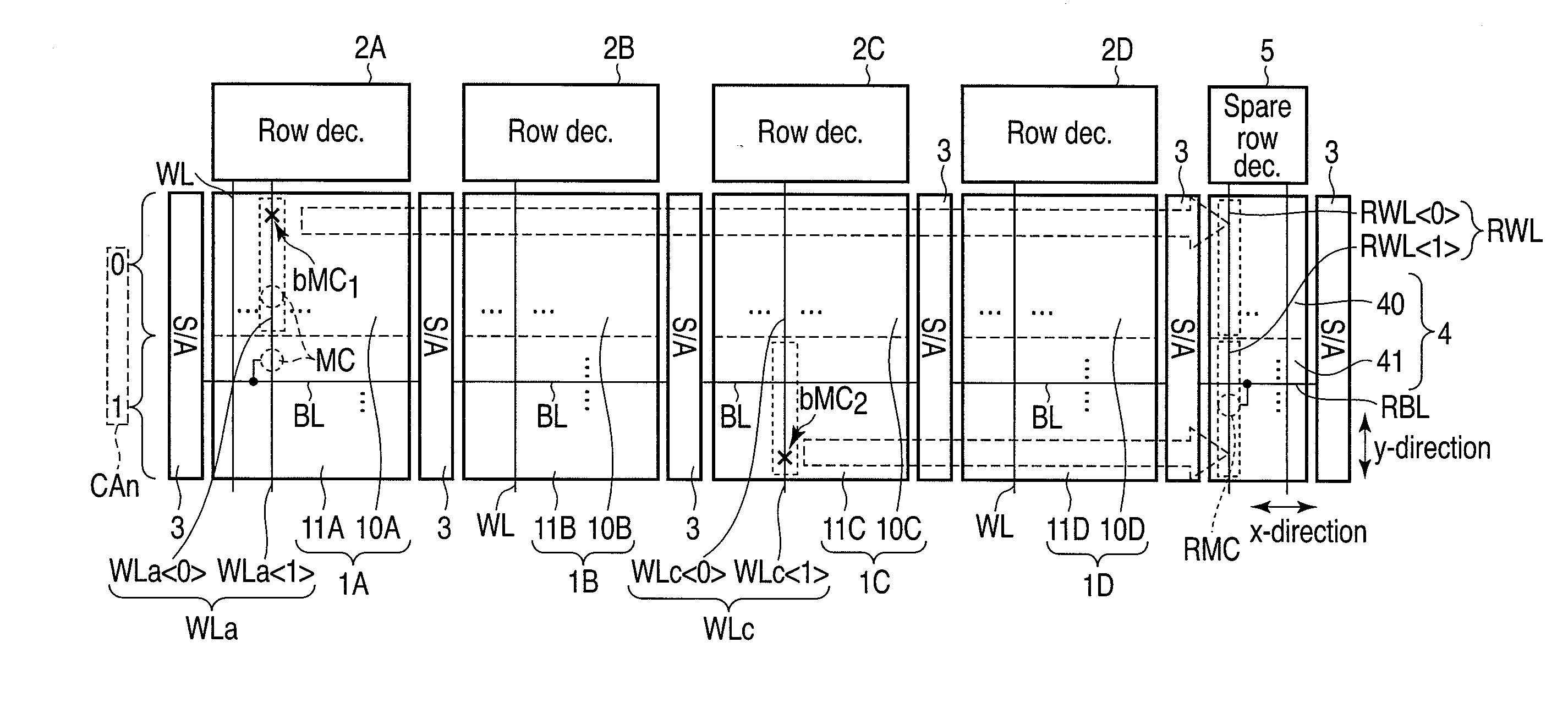
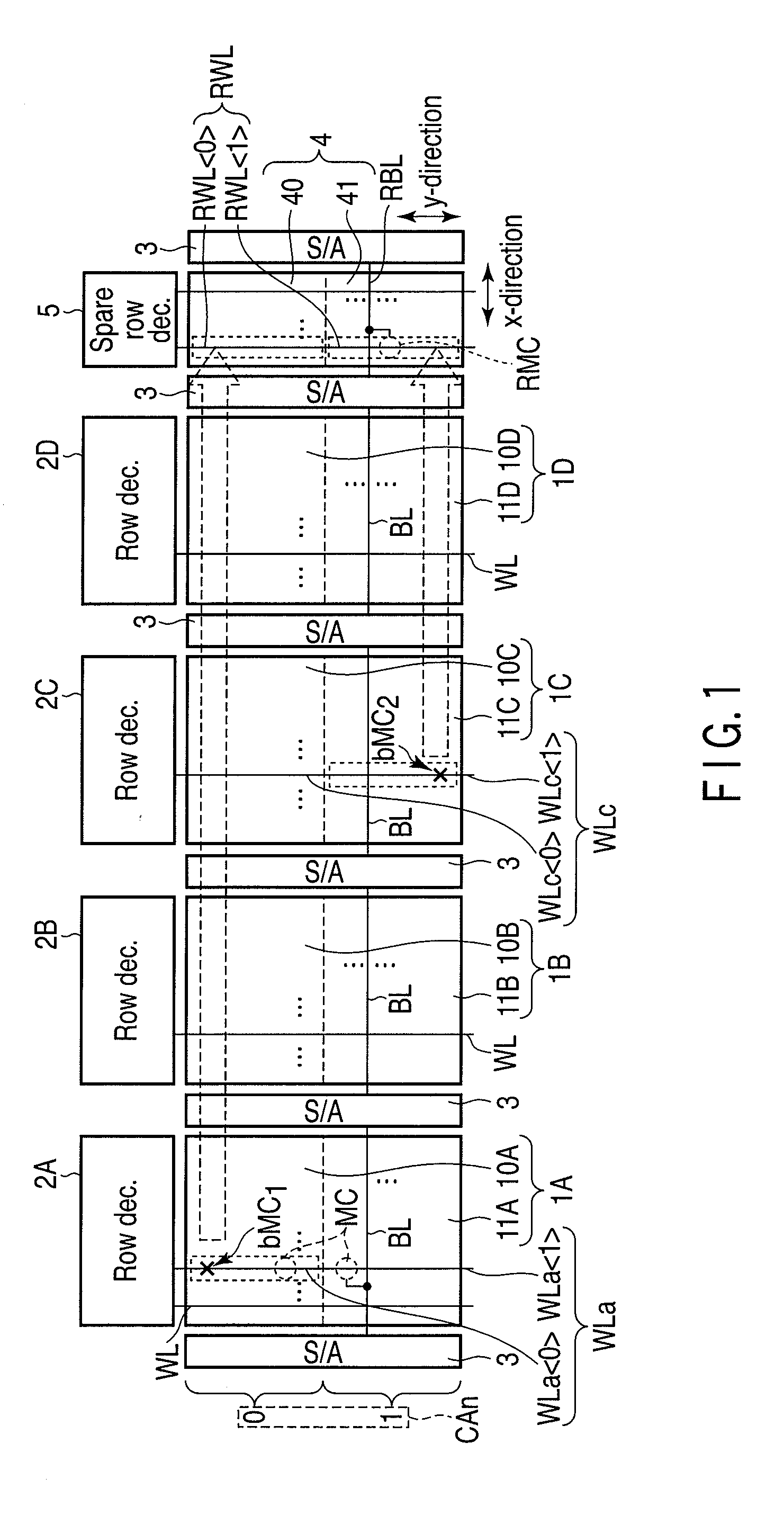
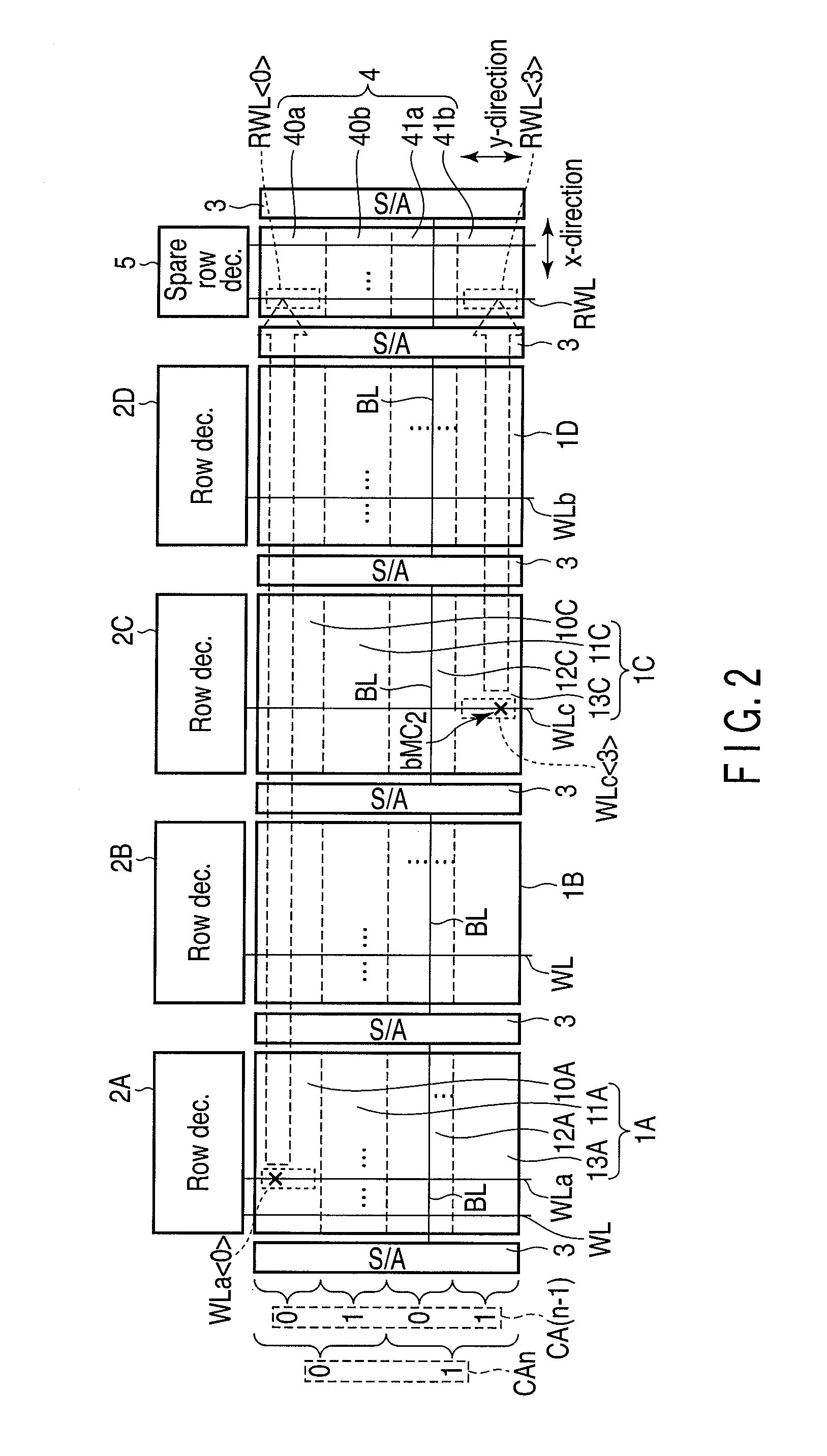
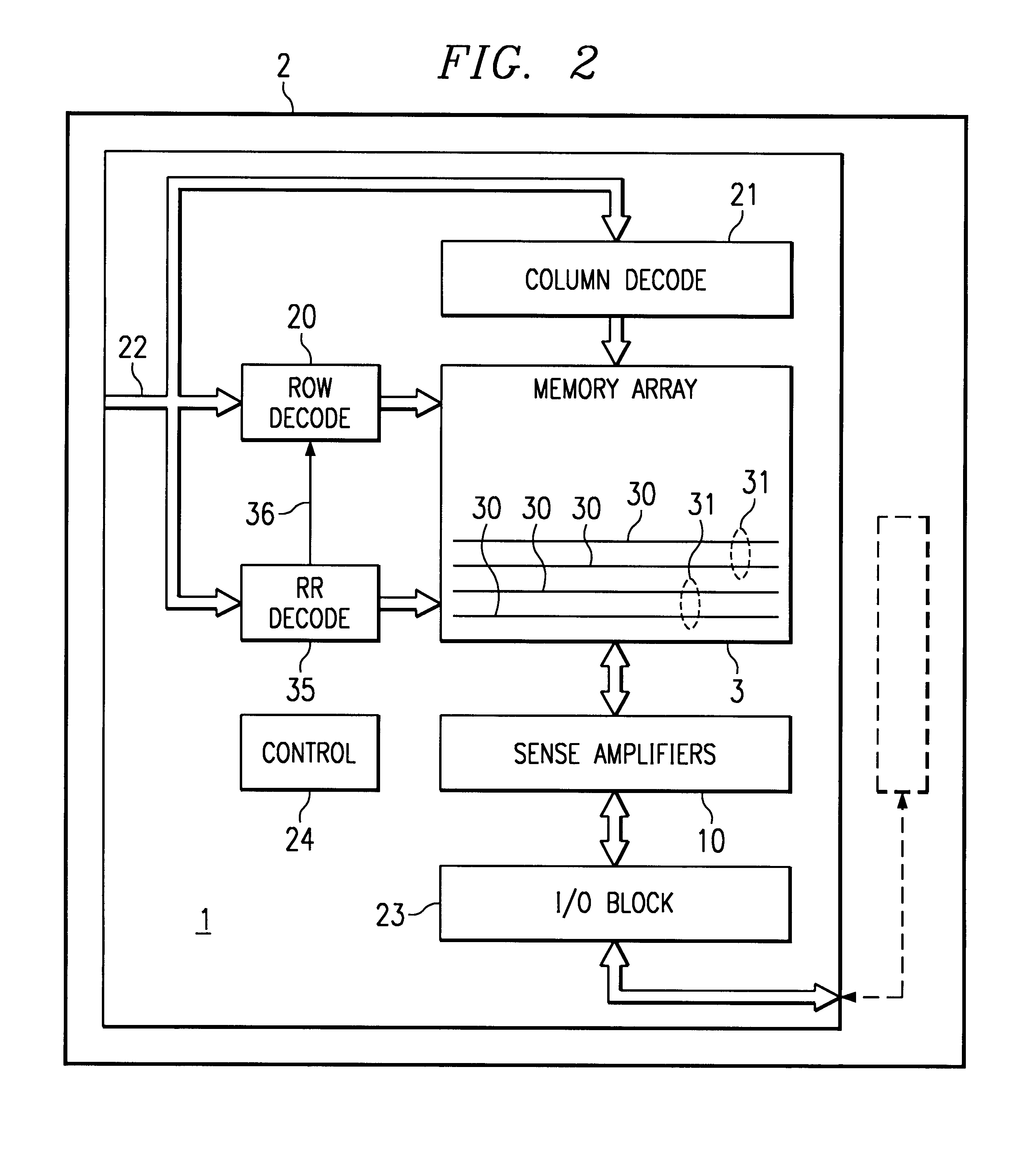
Resistance change memory
A resistance change memory of an aspect of the present invention including memory cells including resistance change memory element, word lines connected to the memory cells, a row decoder which activates the word lines, redundant cells used instead of defective cells, a redundant word line connected to redundant cells, a redundant row decoder which activates the redundant word line, a control circuit in which defect address information indicating the word line connected to the defective cell is stored and which remedies the defective cell, and regions provided in a memory cell array and a redundant cell array and identified based on column address information, wherein the control circuit replaces a part of the word line connected to the defective cell with a part of the redundant word line in accordance with each of the regions, and allows the redundant row decoder to activate the replaced redundant word line.
Owner:KK TOSHIBA
Scratch protection in tape data storage system
InactiveUS6282039B1Improve protectionEvenly distributedDigital data storage formatRecord information storageData setMagnetic tape
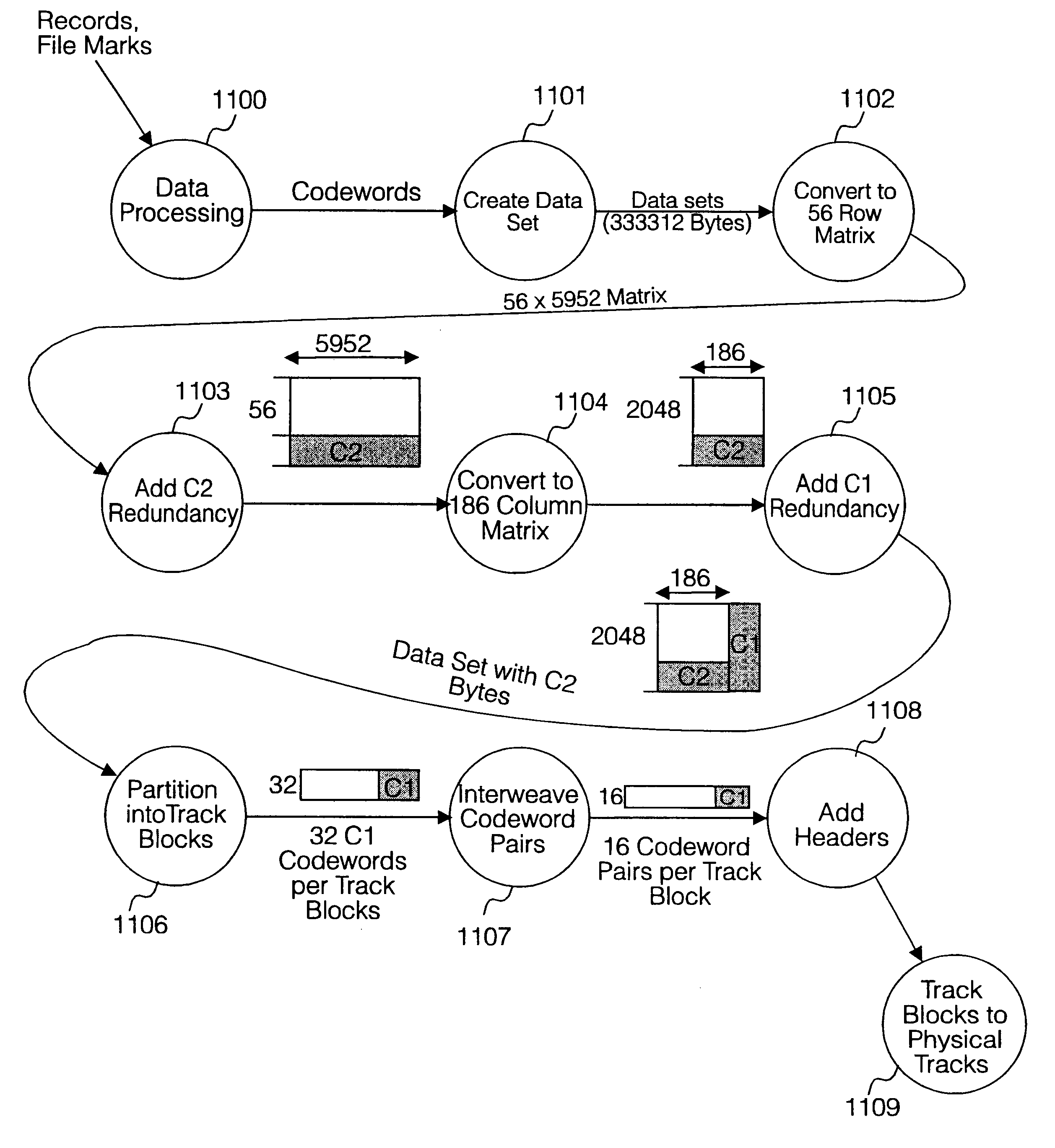
A method of redundancy coding of user data received from a host apparatus and storage of said coded data on a magnetic tape data storage medium comprises inputting a byte stream of user data into a buffer and assembling a plurality of data sets in the buffer; for each data set assembling a data set into a two-dimensional data array and (1103) applying a second redundancy coding algorithm (C2 parity) to the two-dimensional data set in a second dimension; applying (1105) a first redundancy coding (C1 parity) algorithm to the second redundancy coded data array in a first dimension to form a two-dimensional data frame having second and first redundancy coding in respective second and first dimensions, the two-dimensional data frame comprising a plurality of rows, each row comprising a first codeword and a plurality of columns, each column comprising a second codeword; partitioning the two-dimensional data frame into a plurality of logical track blocks (1106) each comprising a plurality of first codewords; and recording (1110) each logical track block to a corresponding respective physical track on the magnetic tape data storage medium. Redundancy coding of a data frame is distributed across a plurality of other data frames along the tape, and redundancy bytes of each data frame are distributed across a plurality of data tracks. Redundancy coding may be distributed diagonally across a width of the tape. Data obliterated due to damage to individual physical recorded tracks or sections of tracks on the tape may be recovered from redundant coding data distributed across other adjacent parallel physical tracks on the tape.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
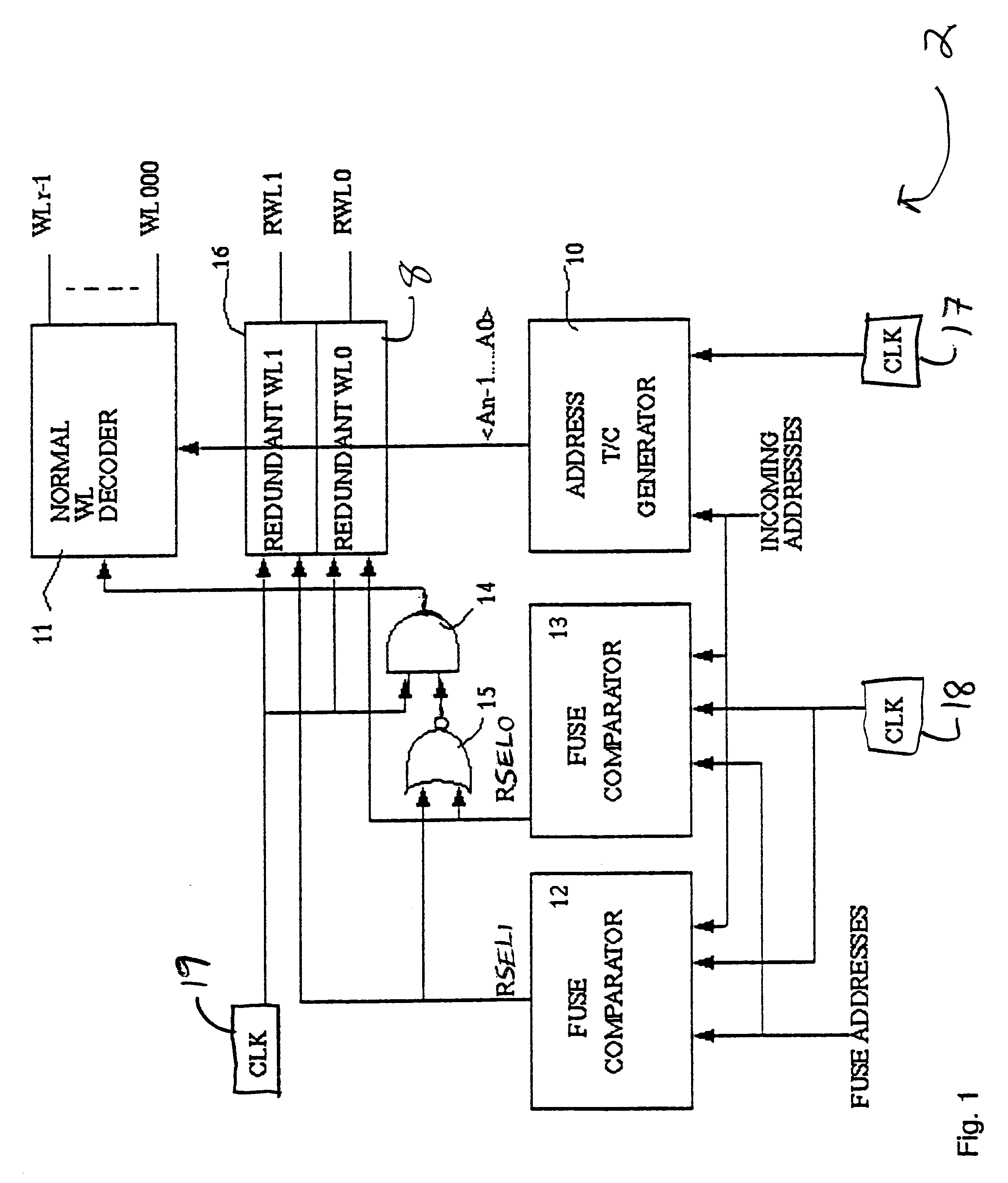
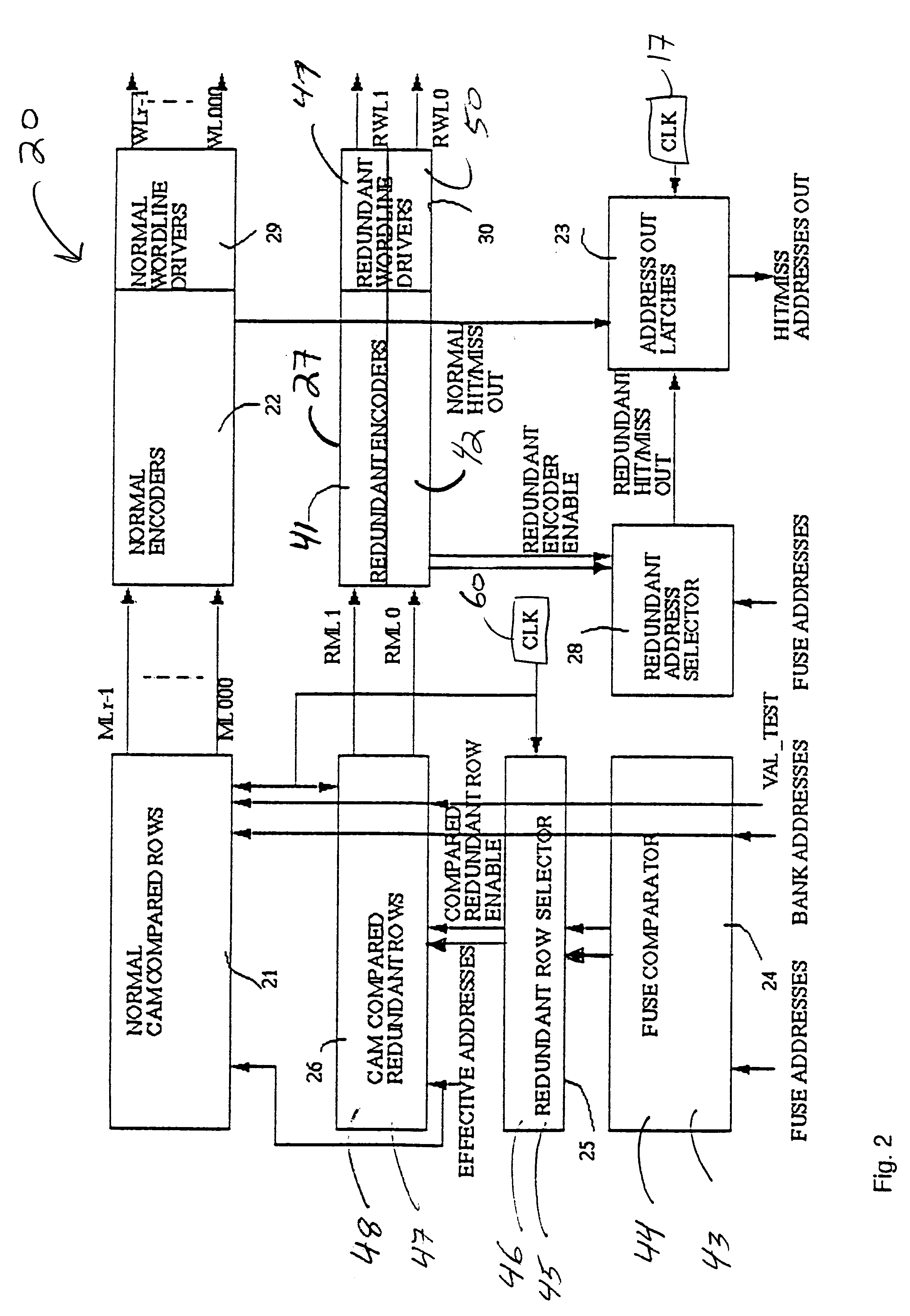
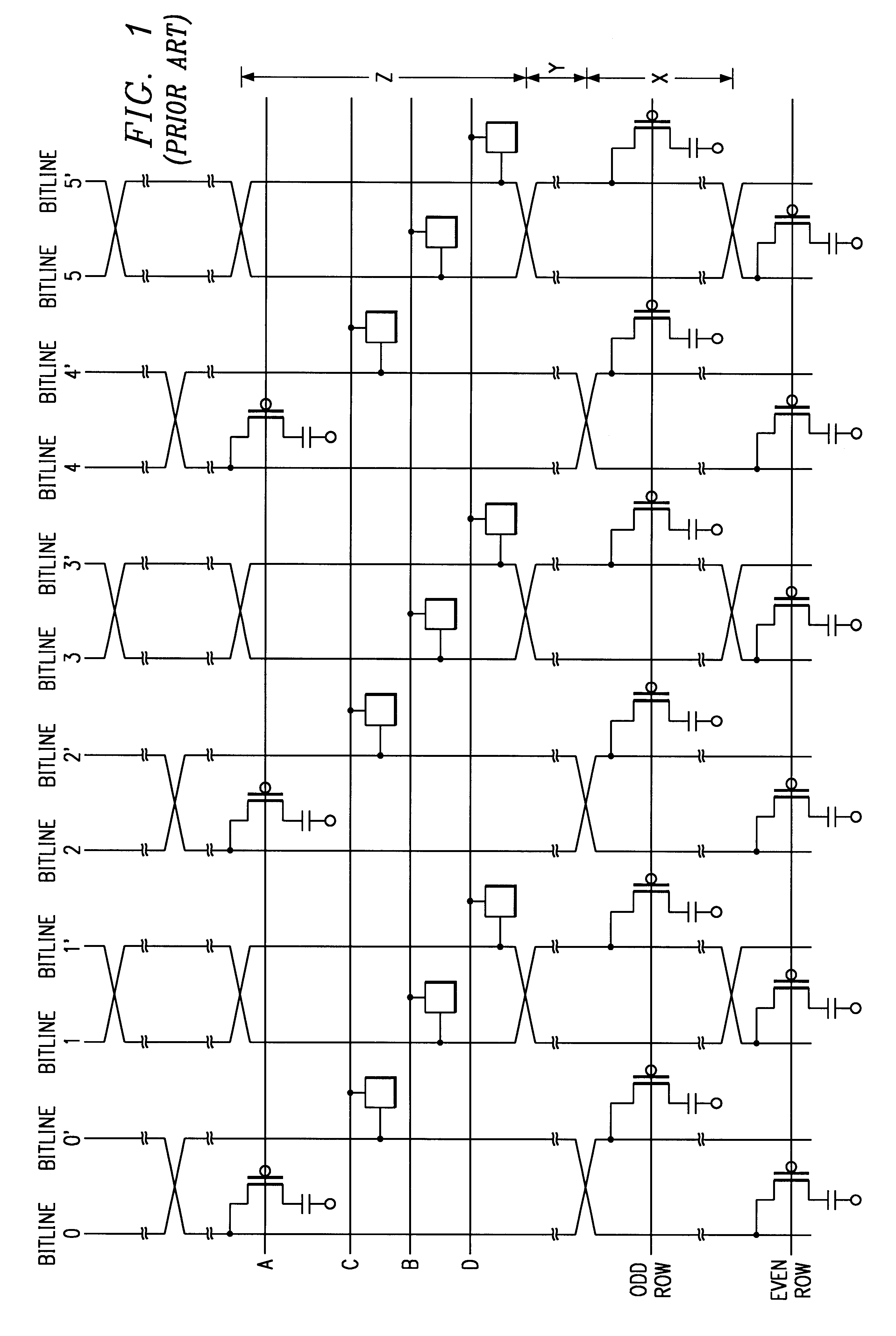
Redundant scheme for CAMRAM memory array
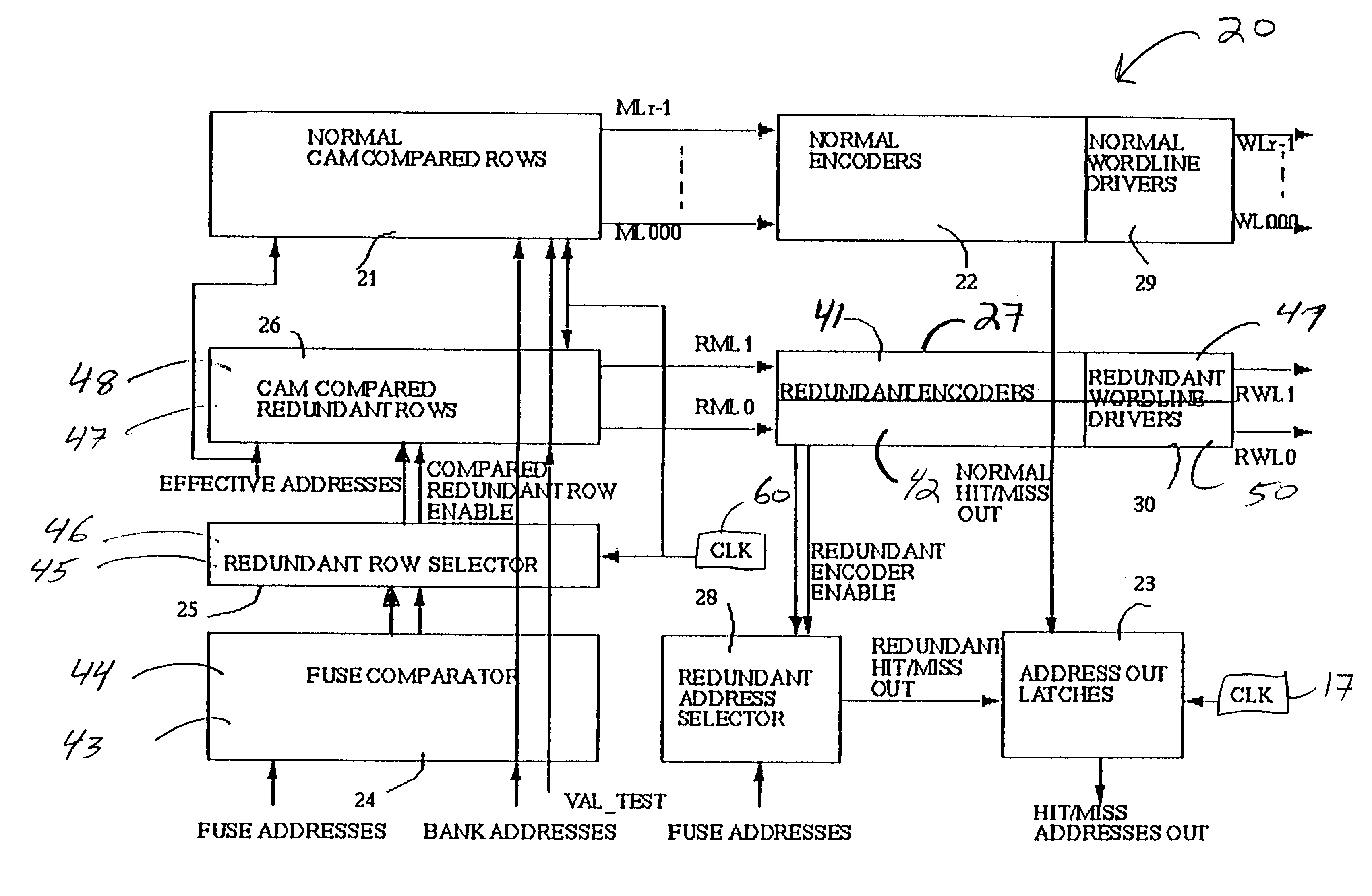
A content addressable memory (CAM) structure and method that provides a redundant scheme for an ASIC. The scheme comprises a CAM comparative means for bypassing normal encoders, including a fuse structure having a fuse address list and a "CAM row compare" structure. Redundancy is provided in "CAM Search Read" and "CAM Search Read and RAM Read" operations. Normal CAM memory address rows and redundant replacement CAM memory address rows are provided for bank addresses. A miss logic is provided for detecting a bank address miss and generating a responsive miss signal, and an "address out" logic is also provided to pass only one of a generated normal CAM memory address row, redundant replacement address row or miss signal in a bank. The method and structure can support different address sizes and different cache sizes.
Owner:GLOBALFOUNDRIES INC
Memory with retargetable memory cell redundancy
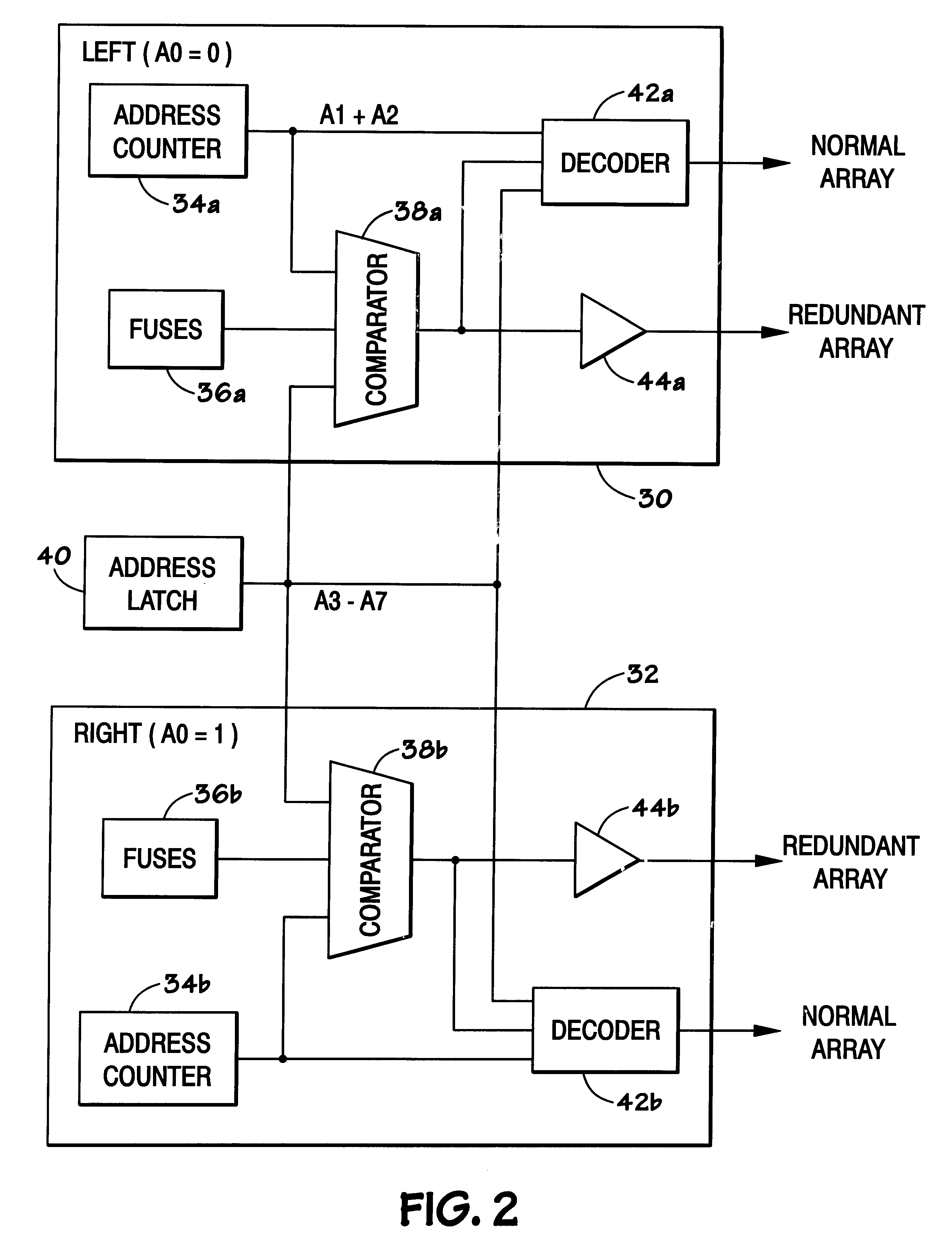
In a memory array having redundant columns, a scheme allows defective cells to be individually remapped to redundant cells in a redundant column. Redundant cells in one redundant column replace defective cells in multiple non-redundant columns. Remapping is done as part of initial test and configuration. Specific hardware can be used for the scheme or firmware in the memory controller can implement the scheme.
Owner:SANDISK TECH LLC
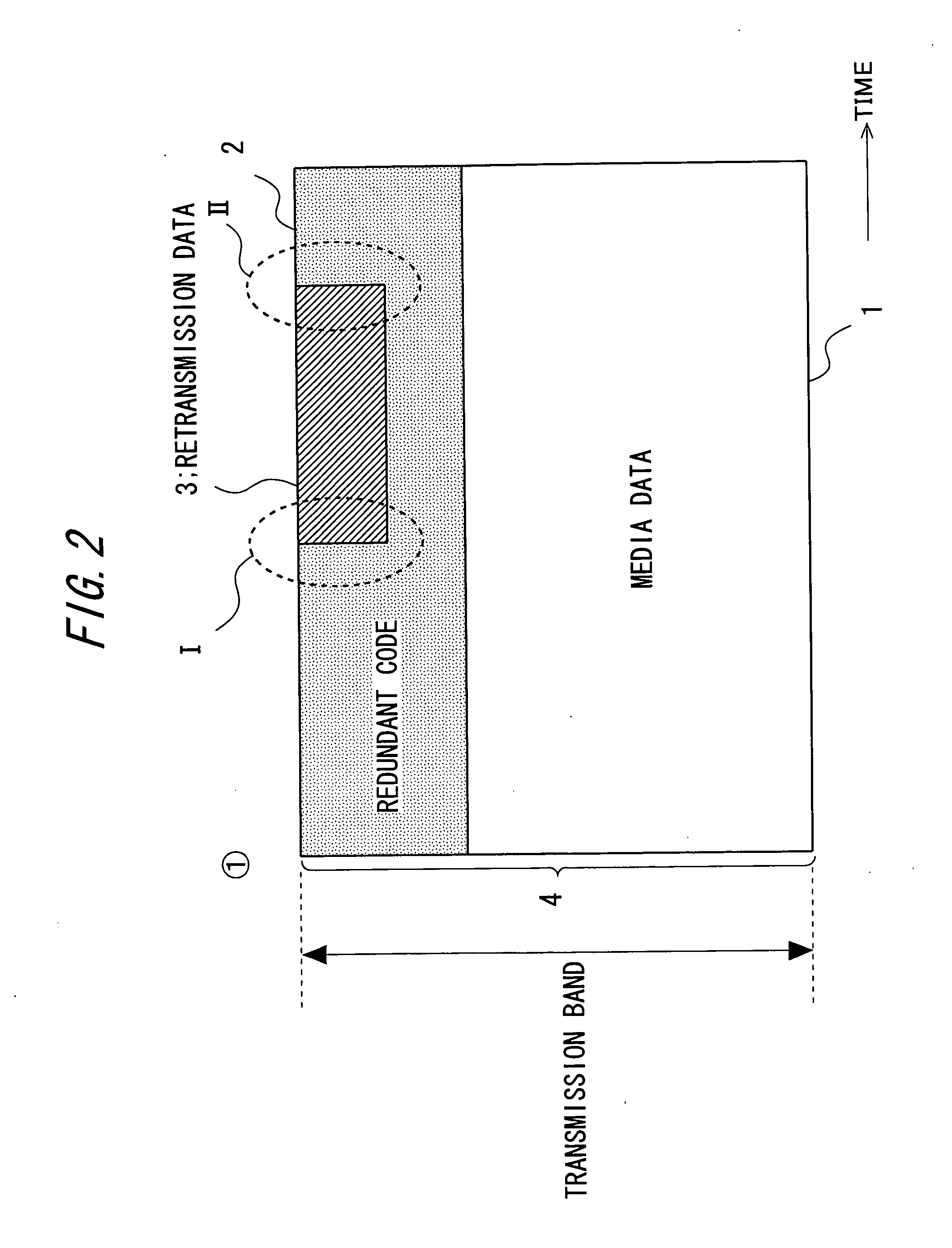
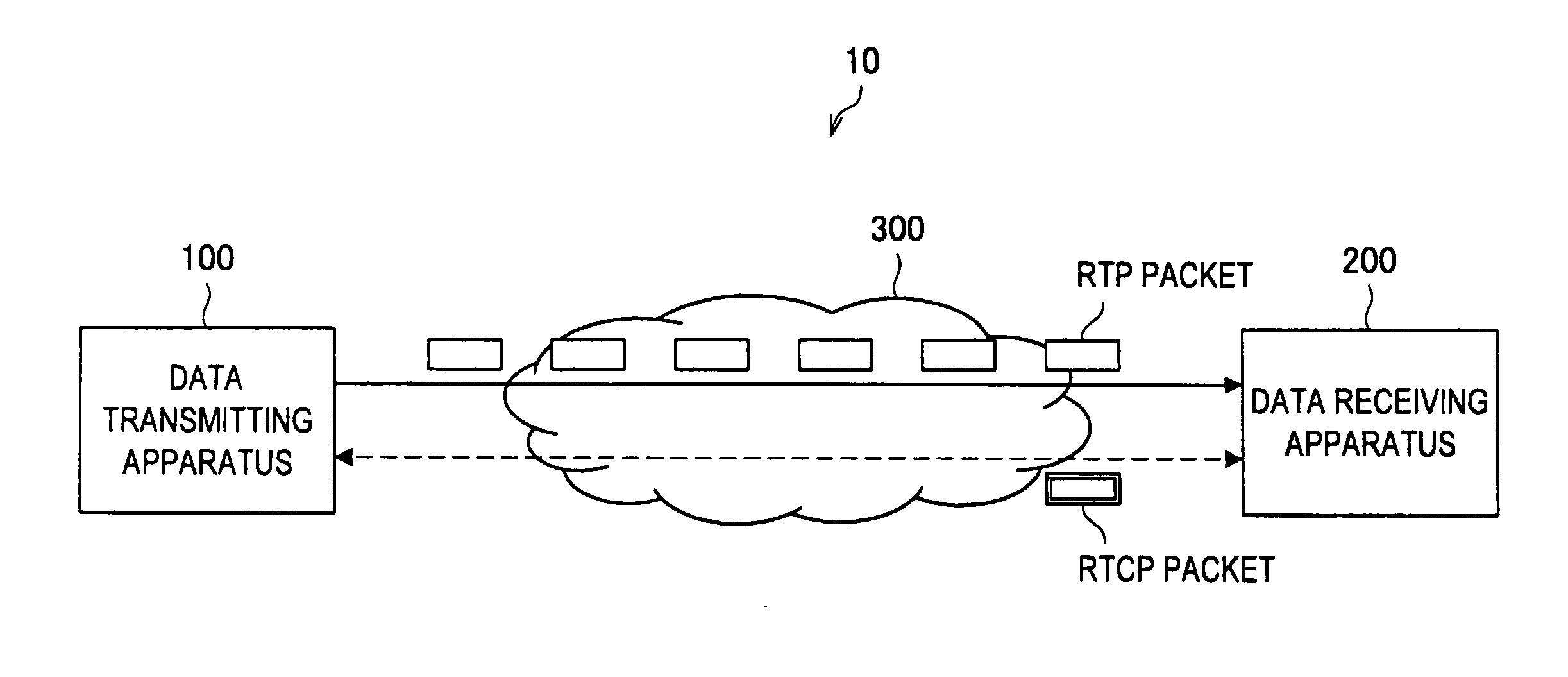
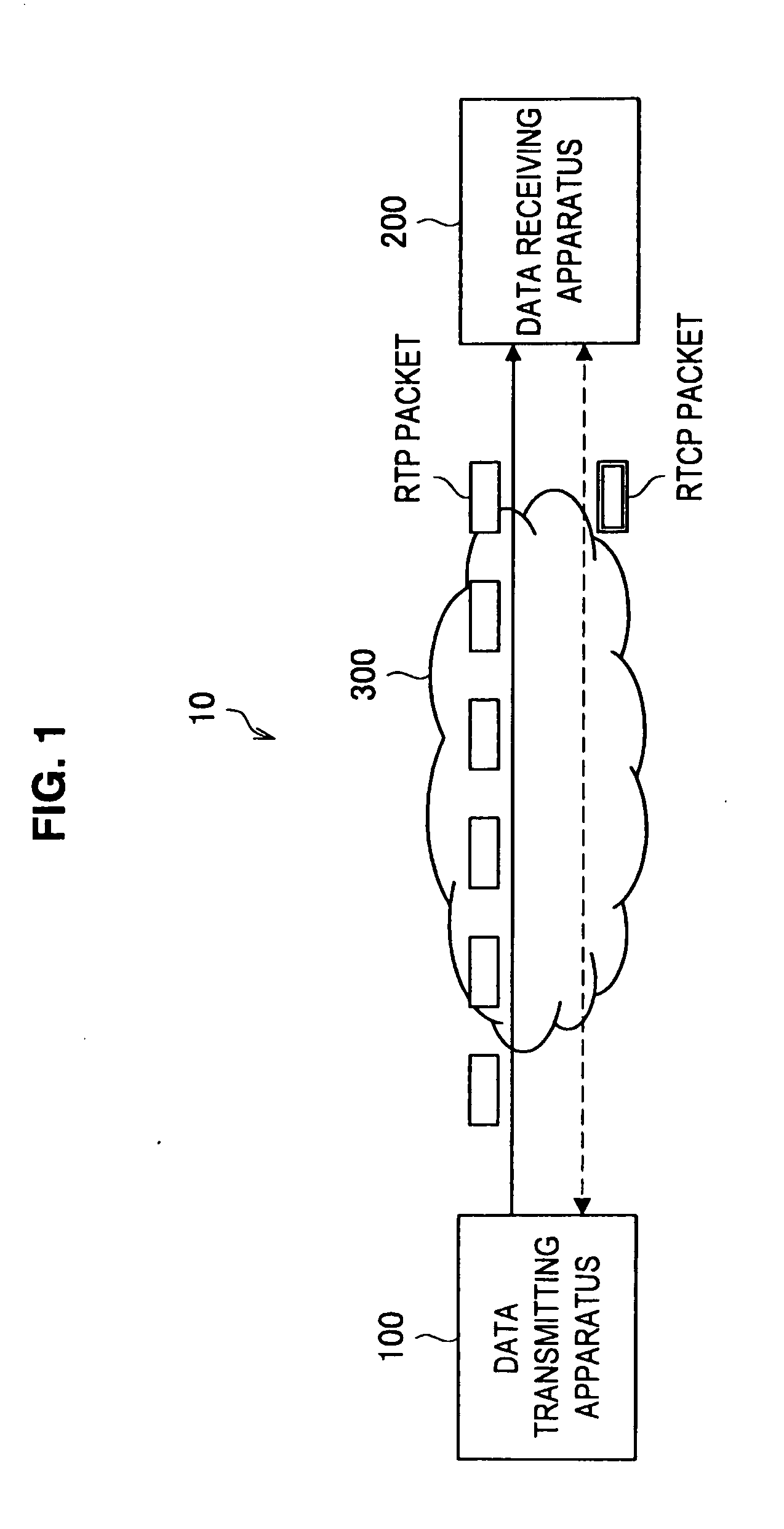
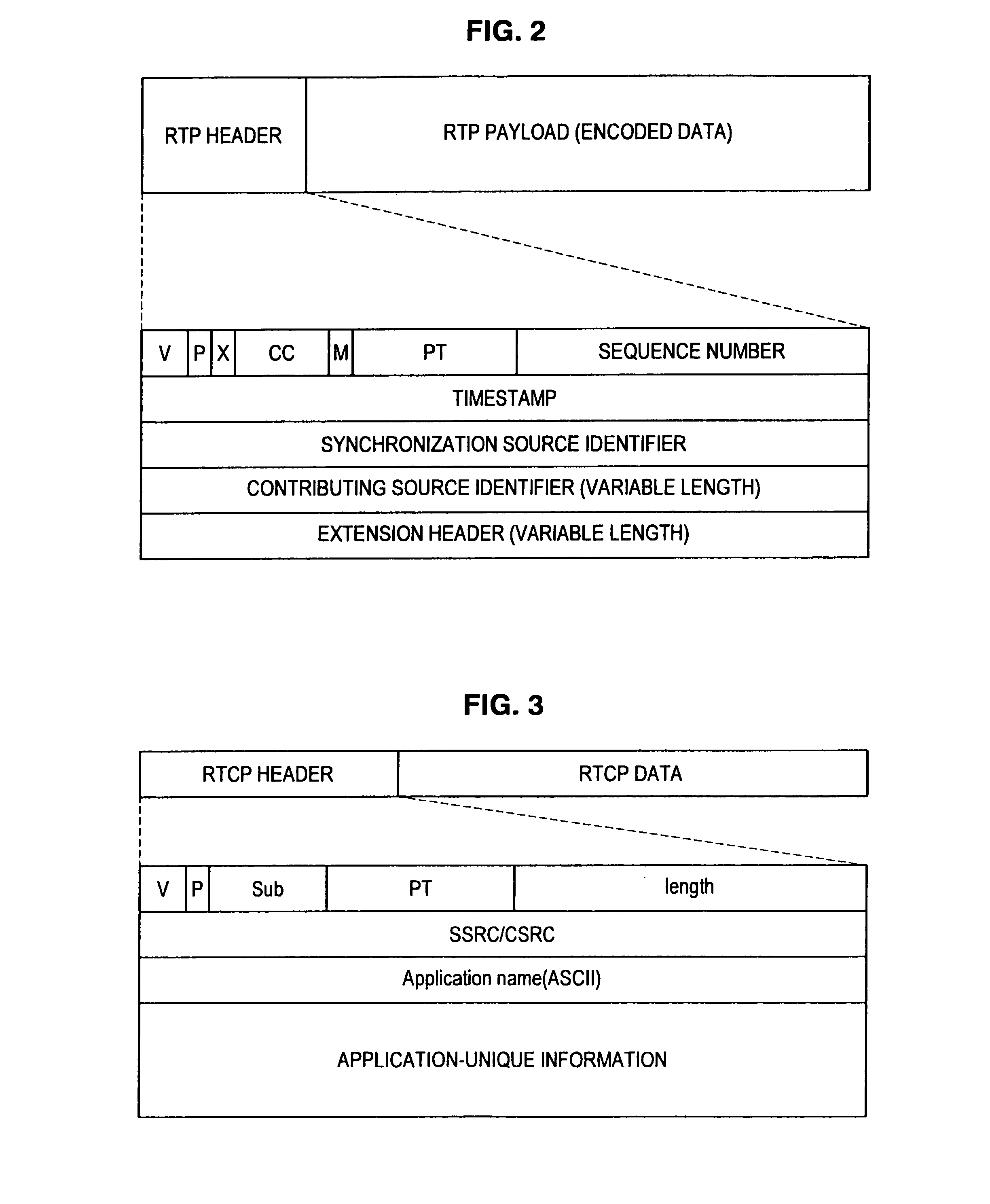
Transmission apparatus, transmission control program, and transmission method
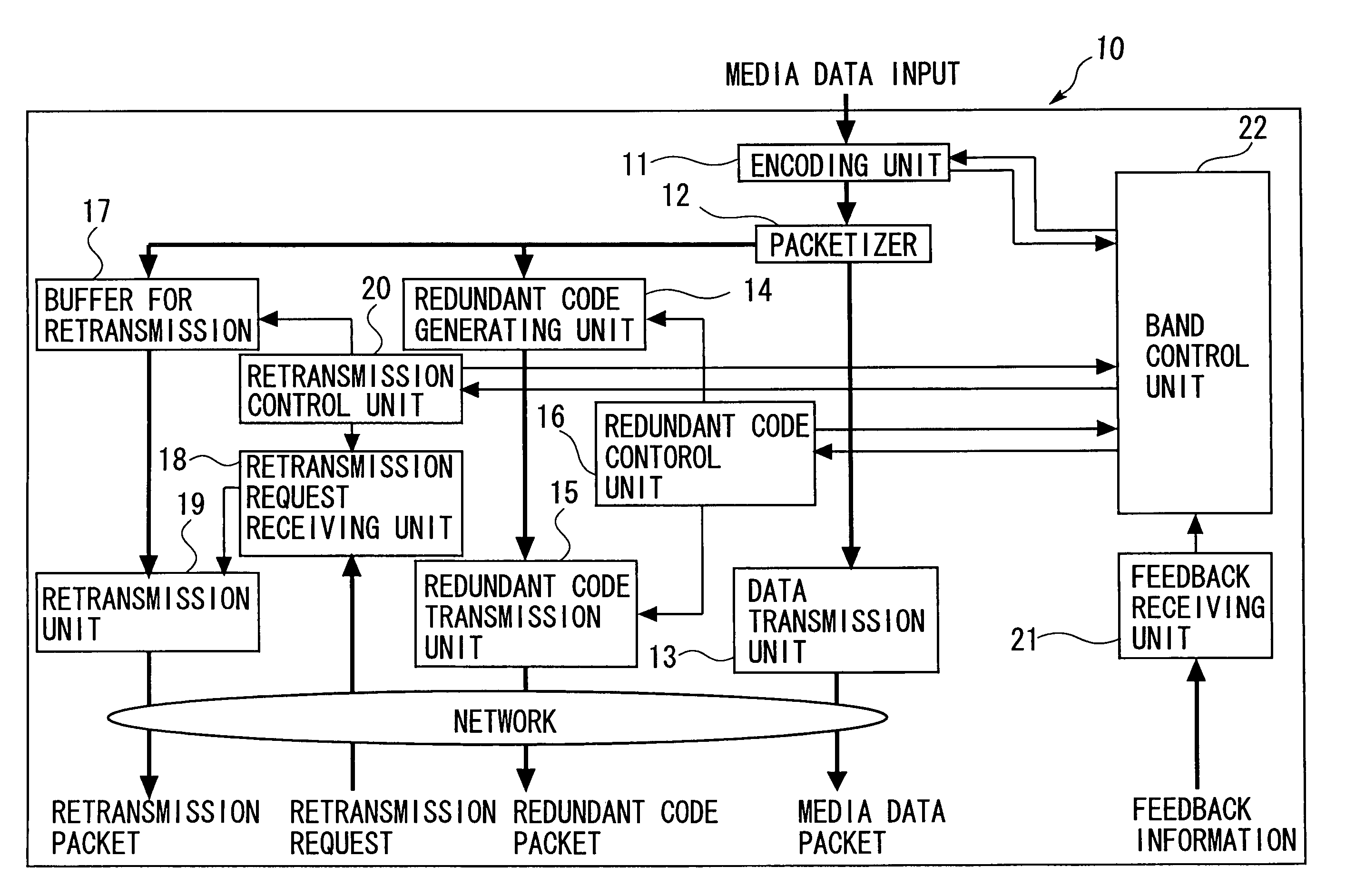
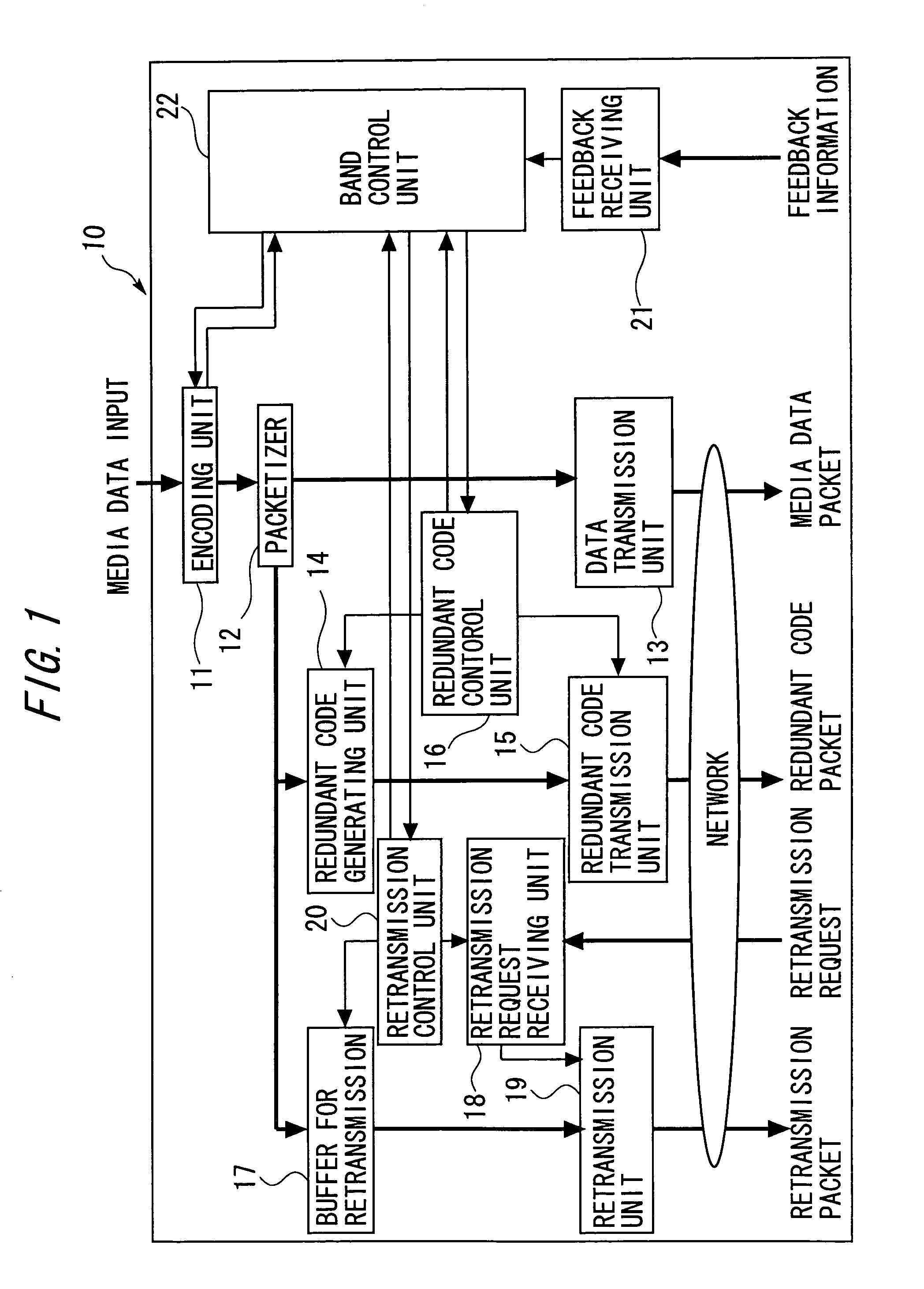
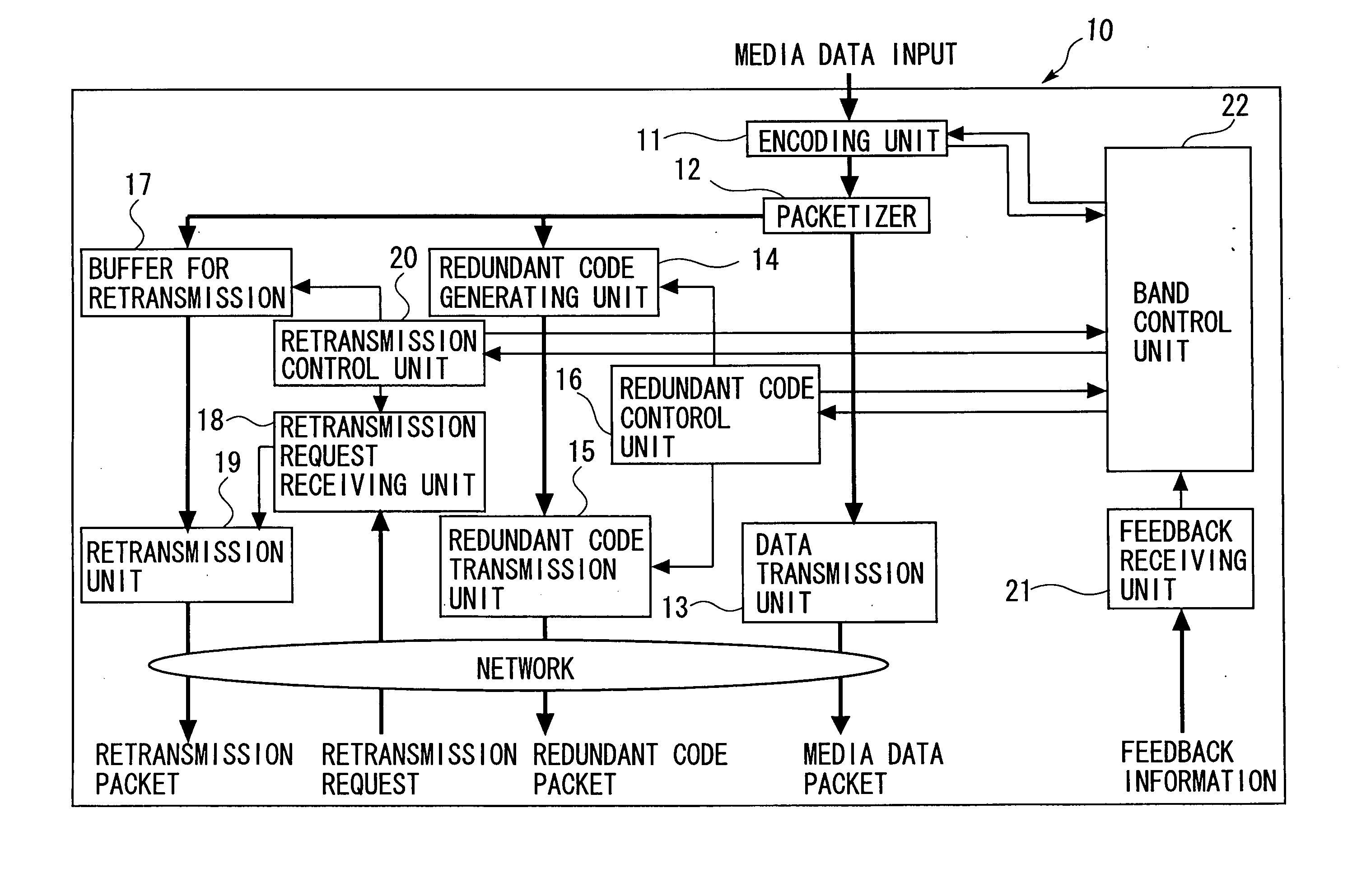
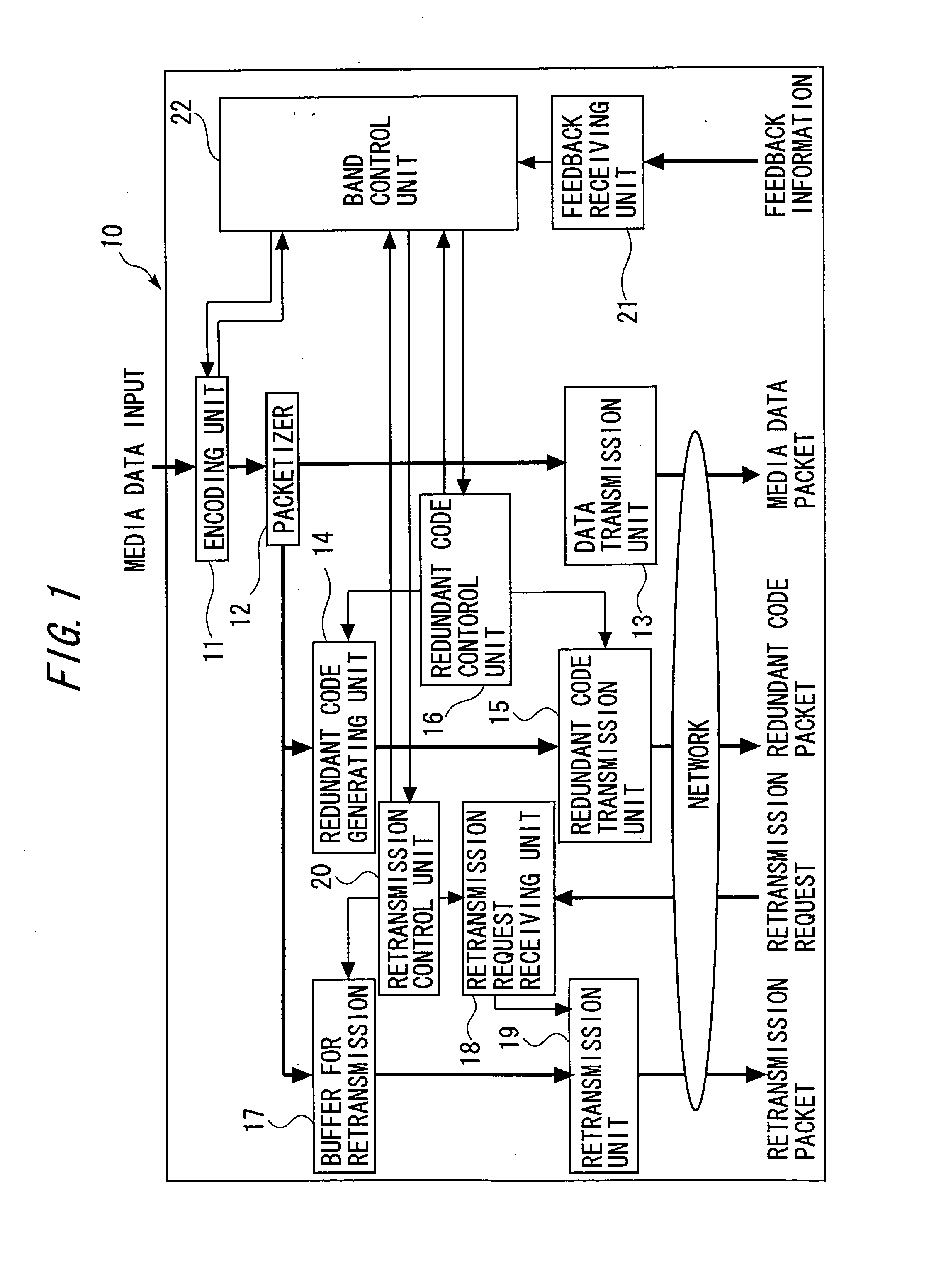
ActiveUS7376880B2Effective compensationControlling transmission line congestionError prevention/detection by using return channelOther decoding techniquesCommunication unitRedundant code
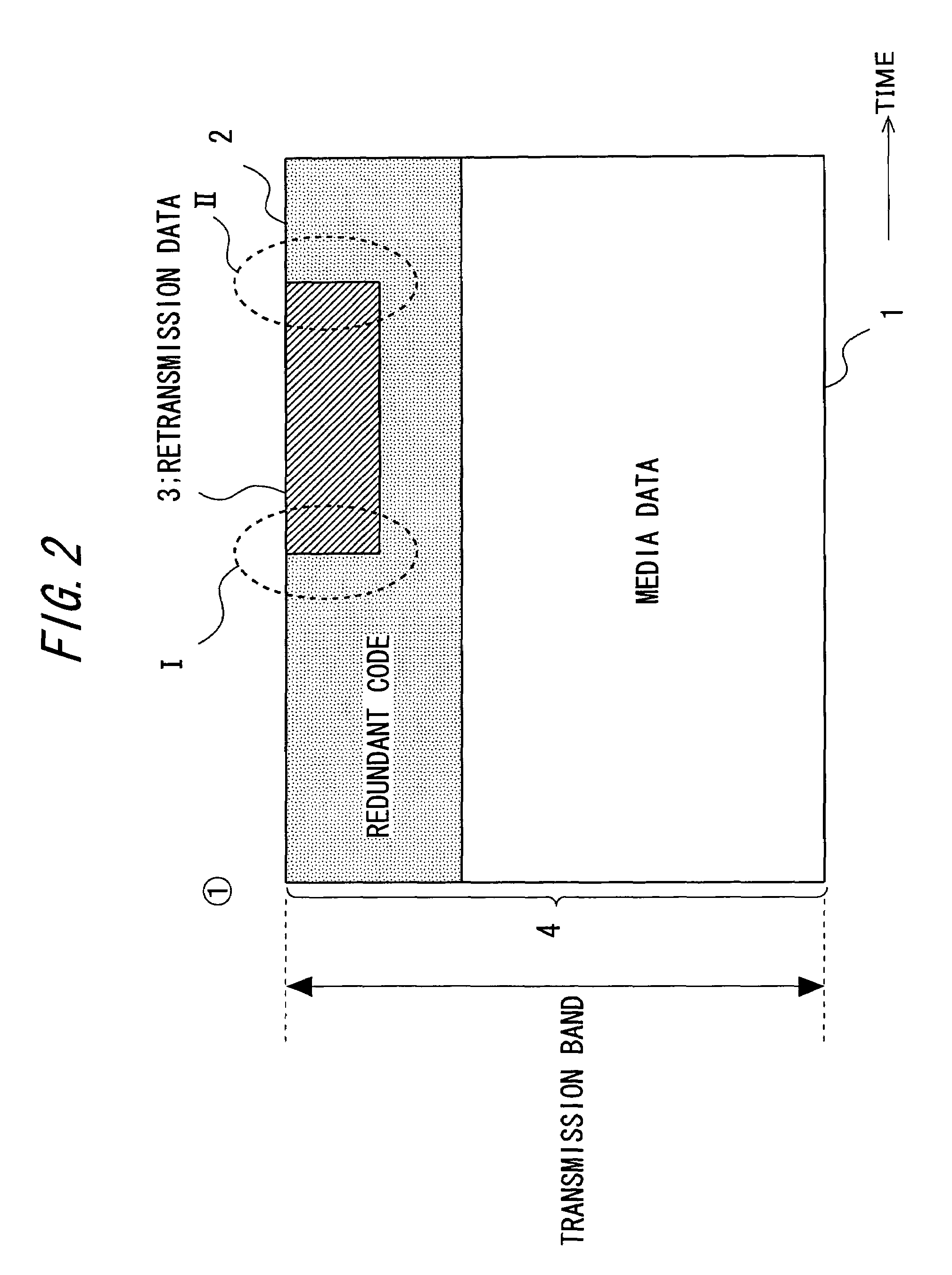
A transmission apparatus includes a communication unit for performing transmission and reception of encoded data packets with other terminals, a redundant code generating unit for generating a redundant code packet for restoring data lost due to the loss of a data packet, a redundant code control unit for controlling the band used by the redundant code packet, a buffer for accumulating retransmission packets that can be retransmitted when corresponding data are lost, a retrieval unit for retrieving a corresponding retransmission packet from the buffer for retransmission upon receiving a retransmission request for the data packet, a retransmission control unit for controlling the band used for retransmission, and a band control unit for controlling the bandwidth of a redundant code based on the band used for retransmission and the band currently used for the redundant code.
Owner:FUJITSU LTD
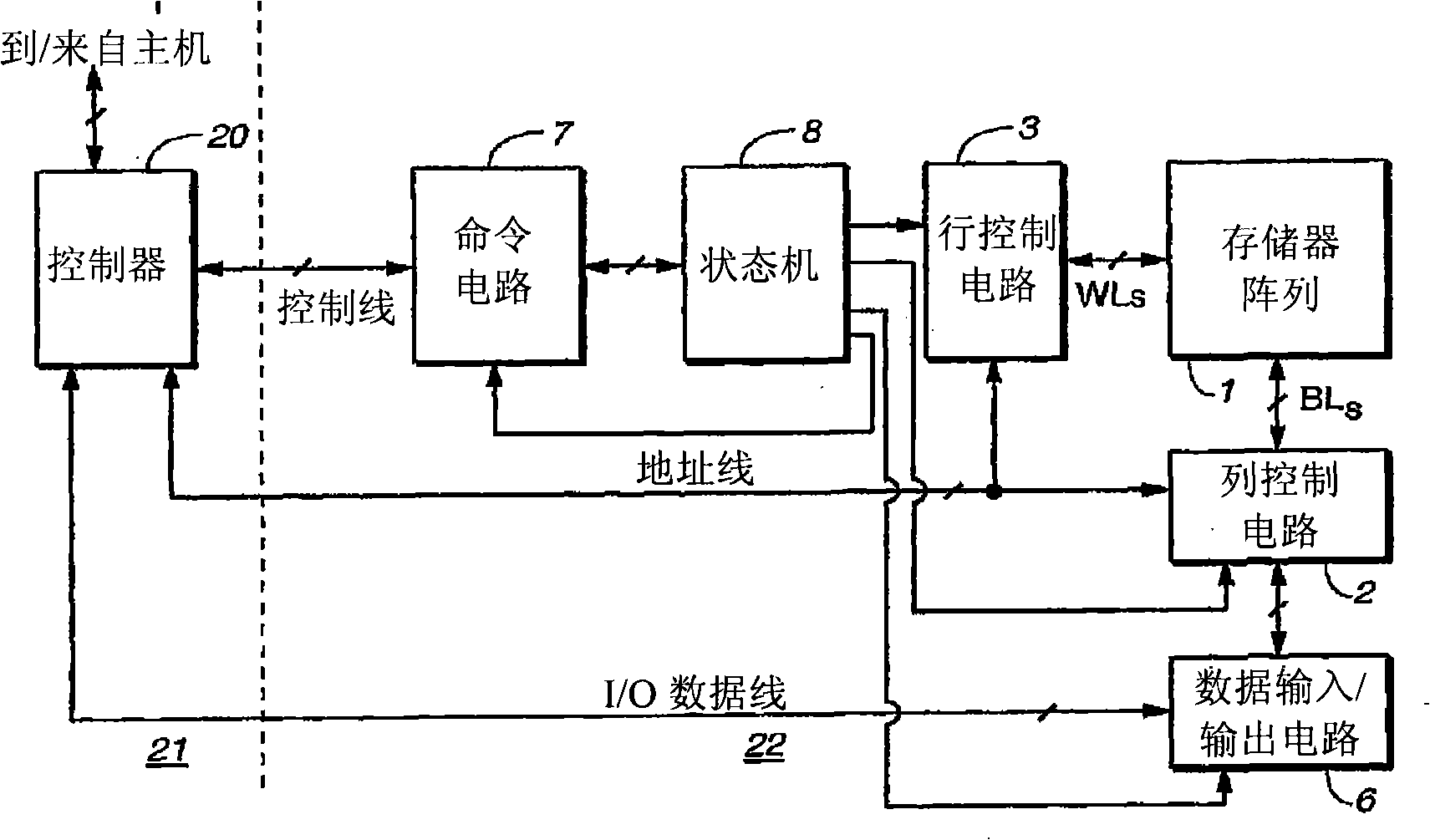
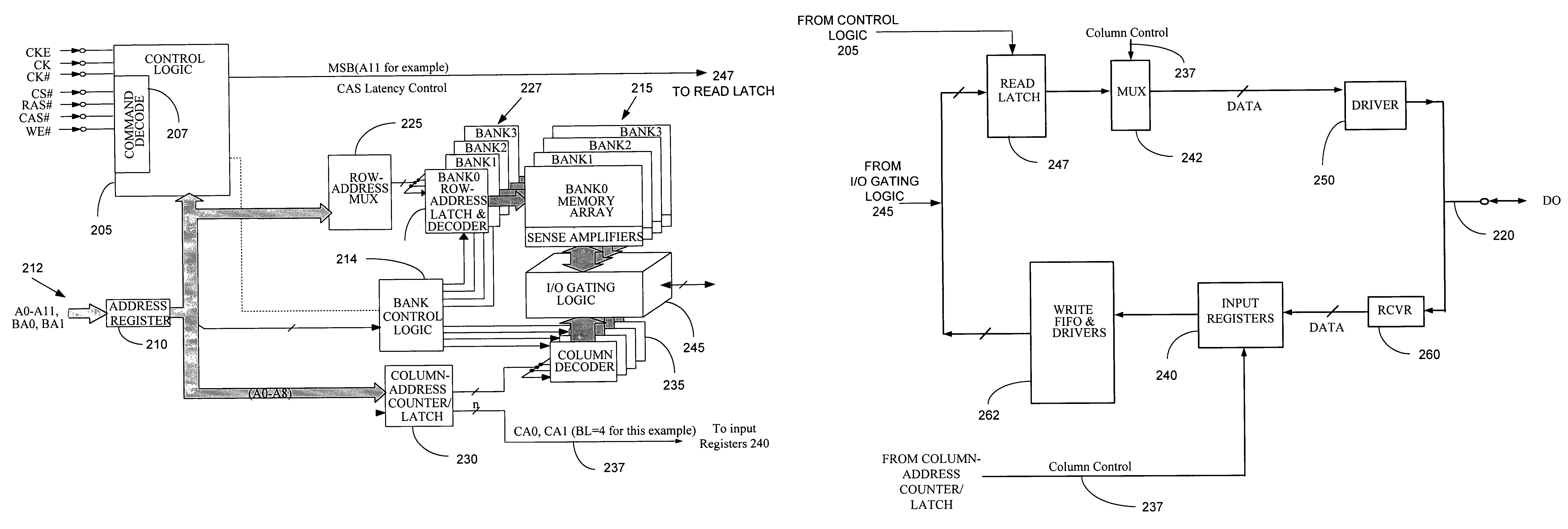
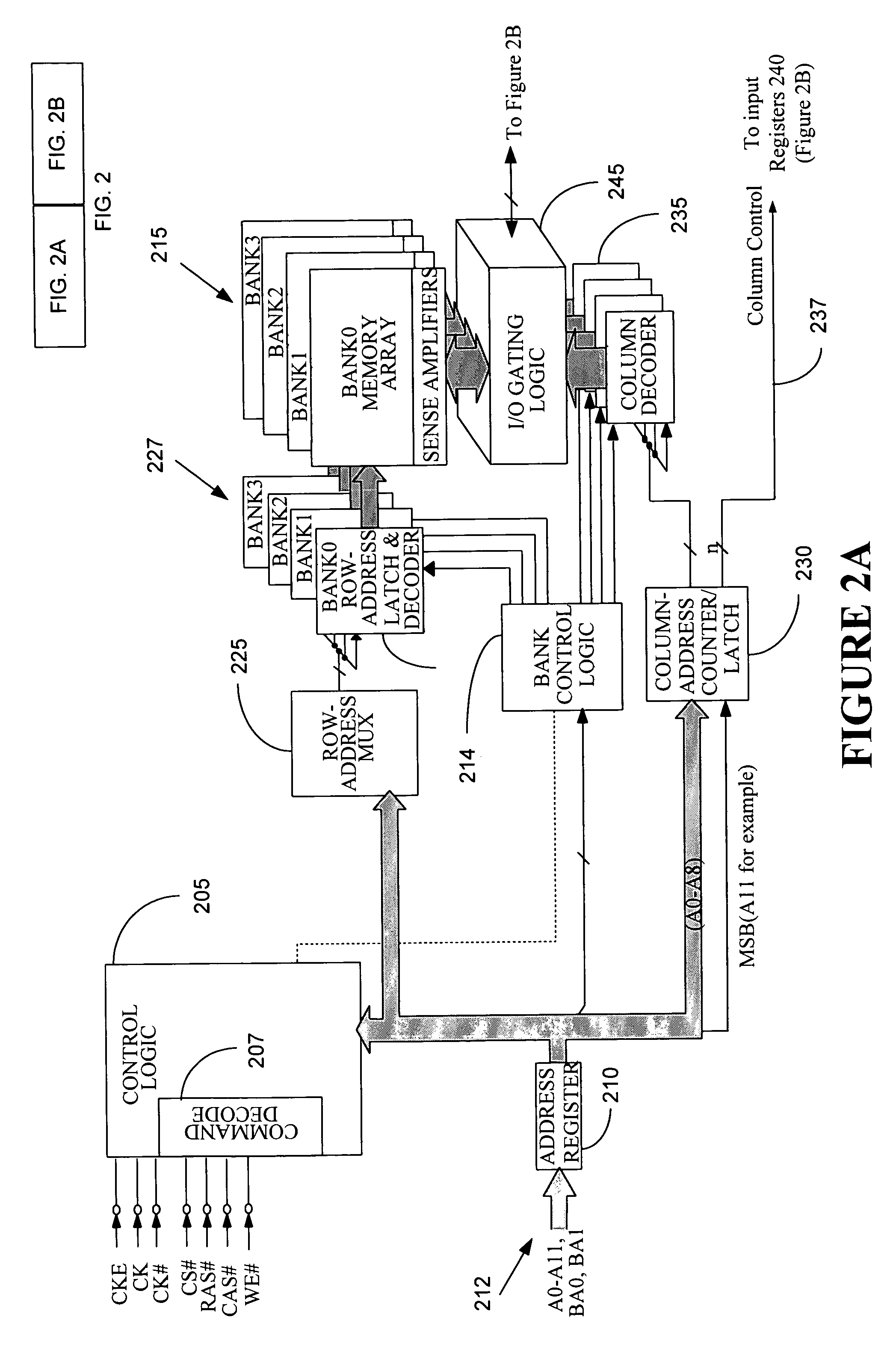
Method and apparatus for accessing a dynamic memory device by providing at least one of burst and latency information over at least one of redundant row and column address lines
Owner:MICRON TECH INC
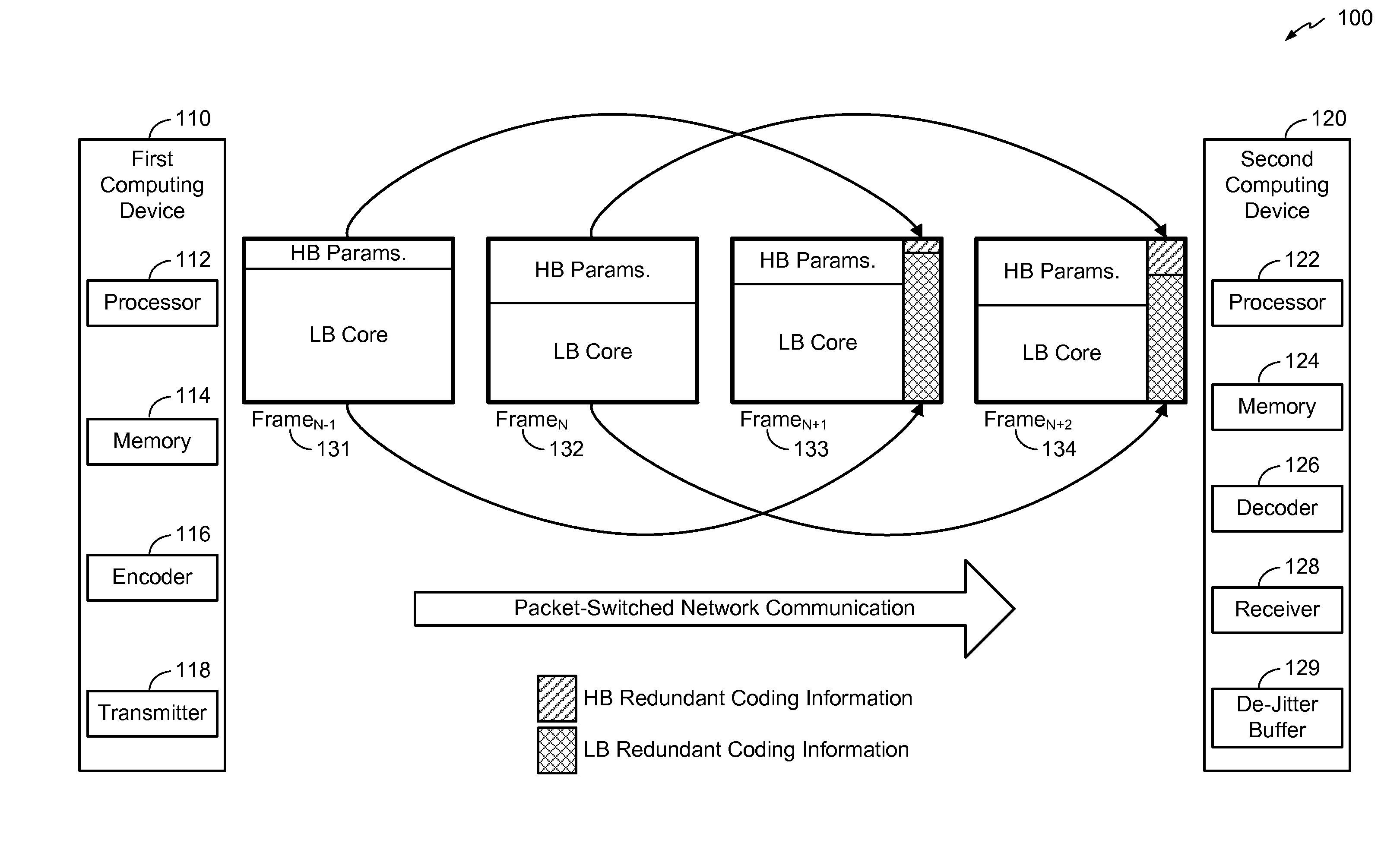
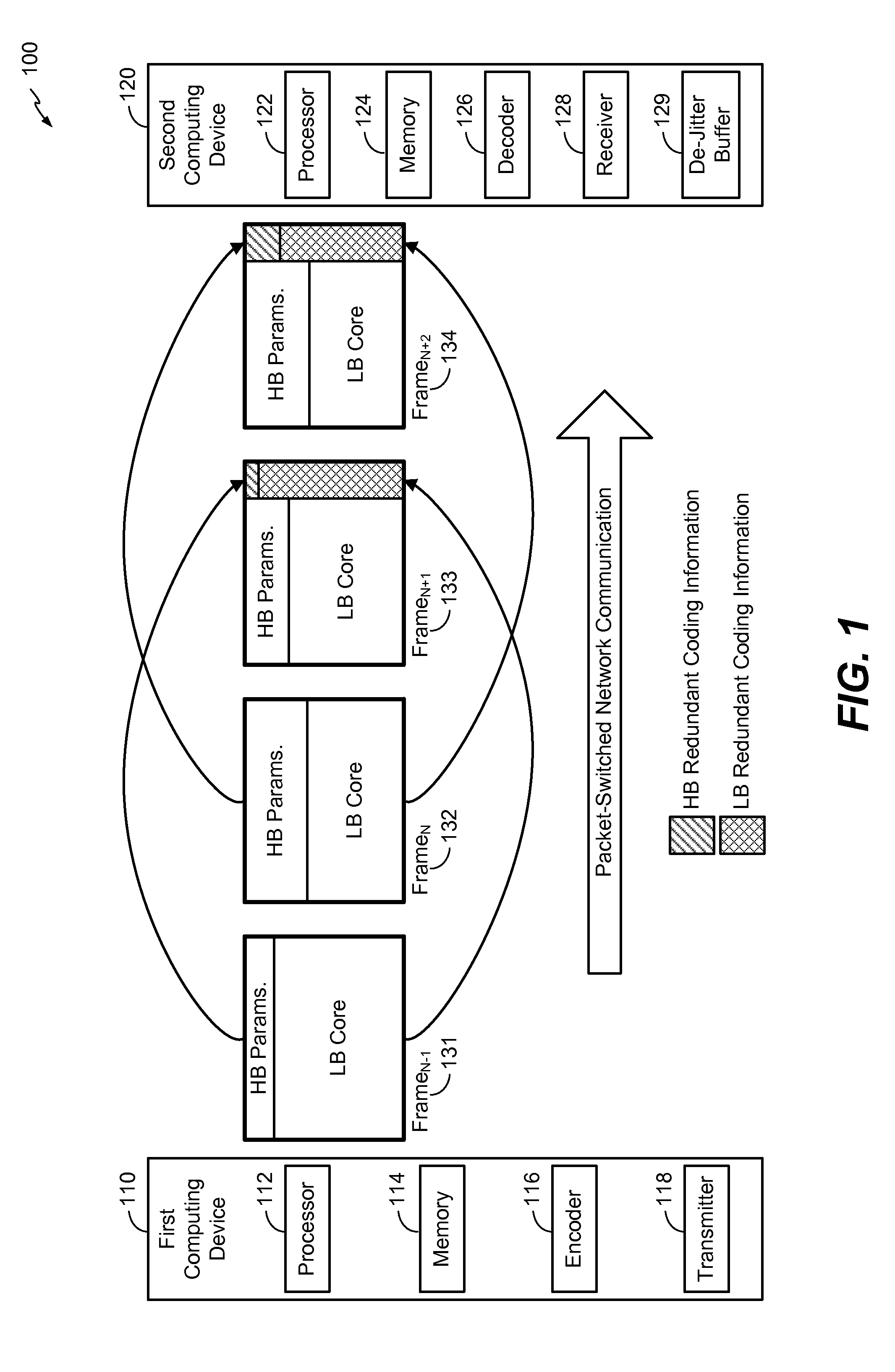
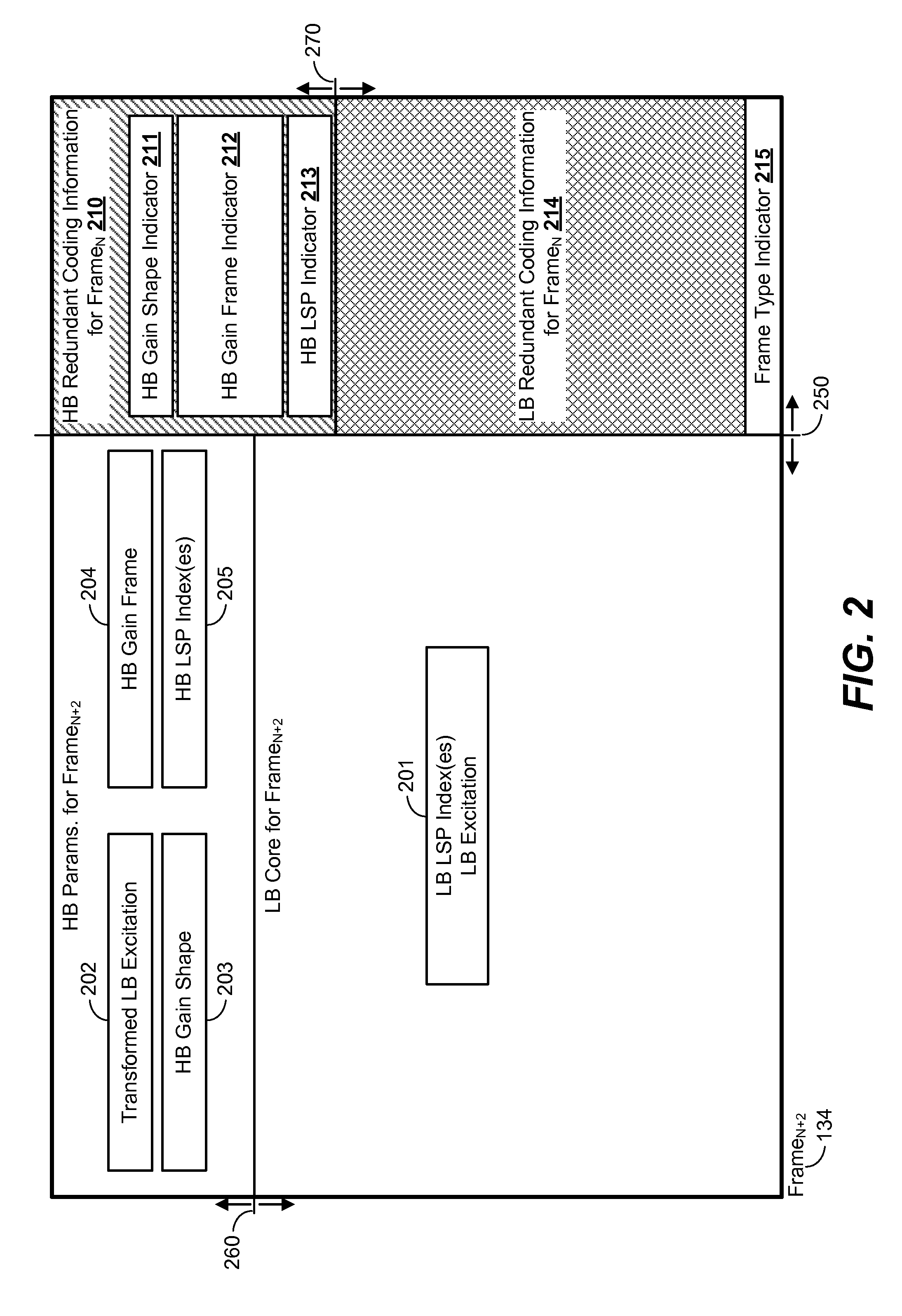
Systems and methods of communicating redundant frame information
A method includes receiving a second audio frame at a decoder. The second audio frame follows a first audio frame in an audio signal and includes a first number of bits allocated to primary coding information associated with the second audio frame, a second number of bits allocated to redundant coding information associated with the first audio frame, and an indicator of a frame type of the first audio frame. In response to a frame erasure condition associated with the first audio frame, the second number of bits is determined based on the indicator and used to decode the first audio frame. In clean channel conditions, the first audio frame is received and decoded based on primary coding bits in the first audio frame, and the first number of bits is determined based on the indicator and used to decode the second audio frame.
Owner:QUALCOMM INC
Transmission apparatus, transmission control program, and transmission method
ActiveUS20050154965A1Effective compensationAttenuation bandwidthError prevention/detection by using return channelOther decoding techniquesData packCommunication unit
A transmission apparatus includes: a communication unit performing transmission and reception of an encoded data packet with other terminals; a redundant code generating unit generating a redundant code packet for restoring a loss of the data packet; a redundant code control unit controlling a band used by the redundant code packet; a buffer for retransmission accumulating retransmission packets that are retransmitted to the other terminals at a time of the loss of the data packet; a retrieval unit retrieving a corresponding retransmission packet from the buffer for retransmission upon receiving a retransmission request for the data packet from the other terminals; a retransmission control unit controlling a band used for retransmission that is used at a time of transmission of the retransmission packet; and a band control unit controlling the bandwidth of a redundant code based on the band used for retransmission and a band used for the redundant code.
Owner:FUJITSU LTD
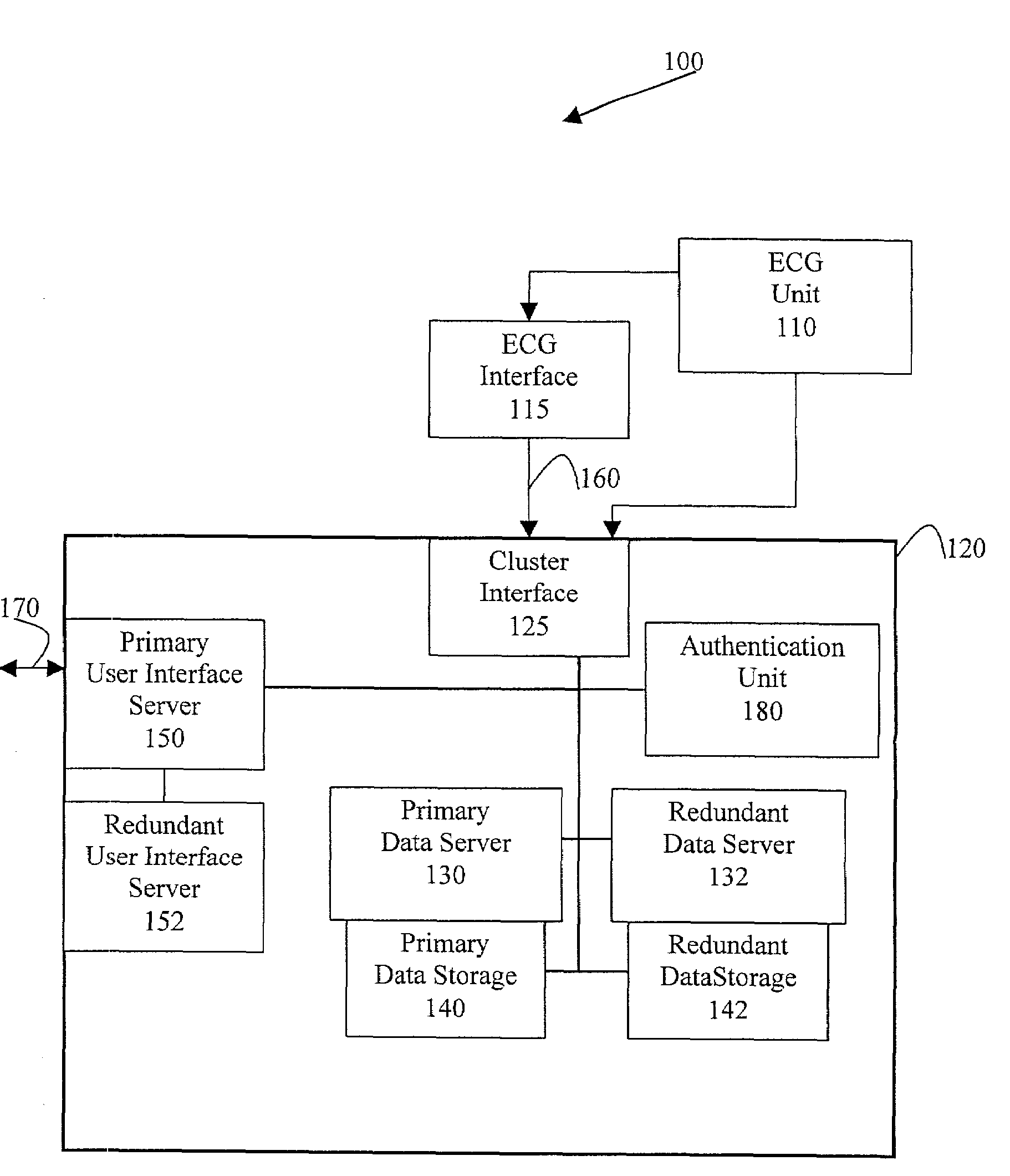
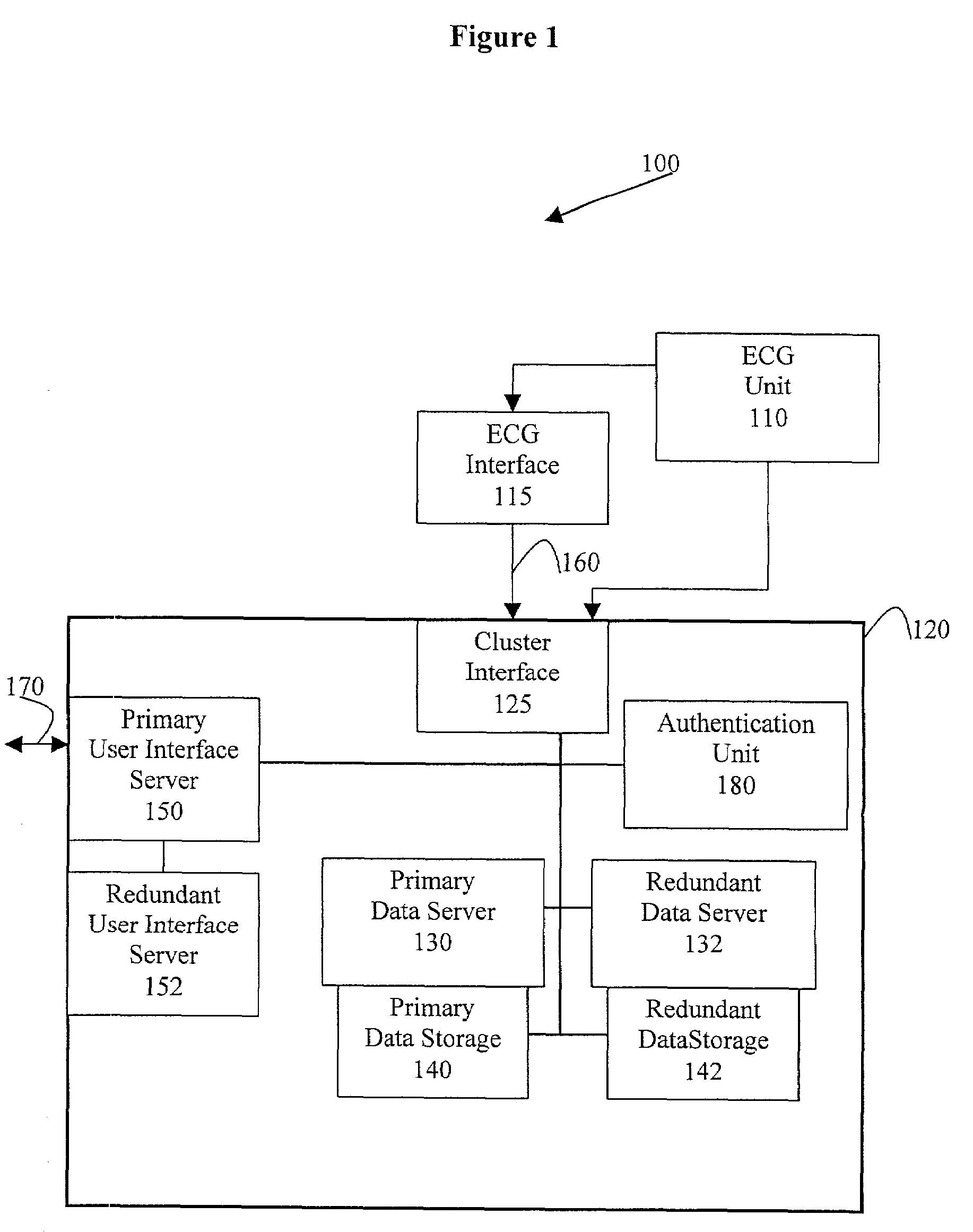
High availability deployment of an off-site management system for digital cardiac electrocardiograms operating in an application service provider model
A preferred embodiment of the present invention provides a method and system for high availability remote centralized data management. In a preferred embodiment, the system includes a primary remote centralized data storage storing medical data, and a redundant remote centralized data storage storing a redundant copy of the medical data. In a preferred embodiment, the system also includes a primary data server for storing the medical data in the primary remote centralized data storage. In a preferred embodiment, the primary data server also stores the medical data in the redundant remote centralized data storage. Preferably, the system also includes a redundant data server for storing the medical data in the redundant remote centralized data storage and also the primary remote centralized data storage. Additionally, in a preferred embodiment, the system includes an interface allowing access to the system. Preferably, the interface is a redundant interface providing high availability access to the remote centralized data management system.
Owner:GE MEDICAL SYST INFORMATION TECH
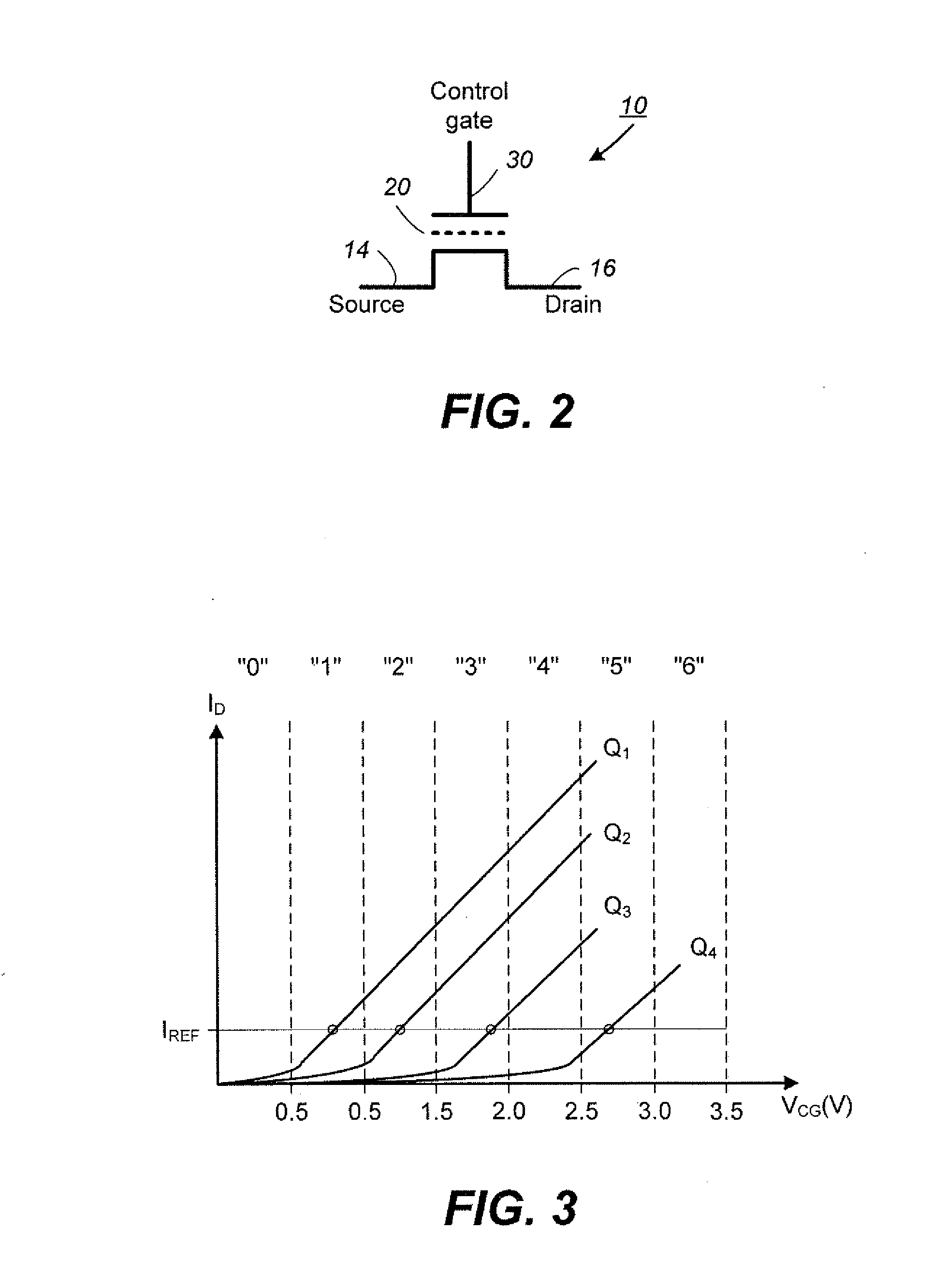
Pattern recognition
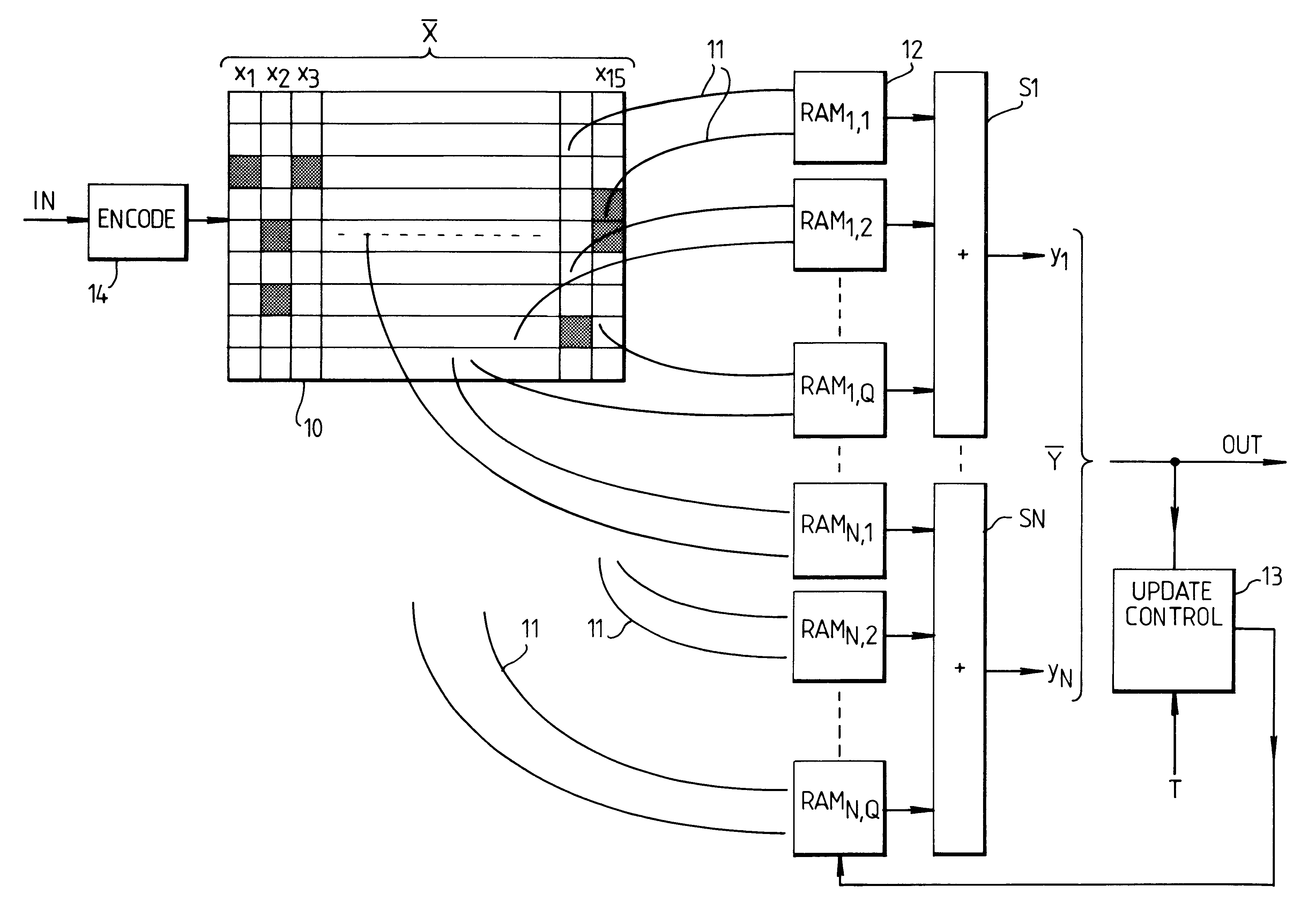
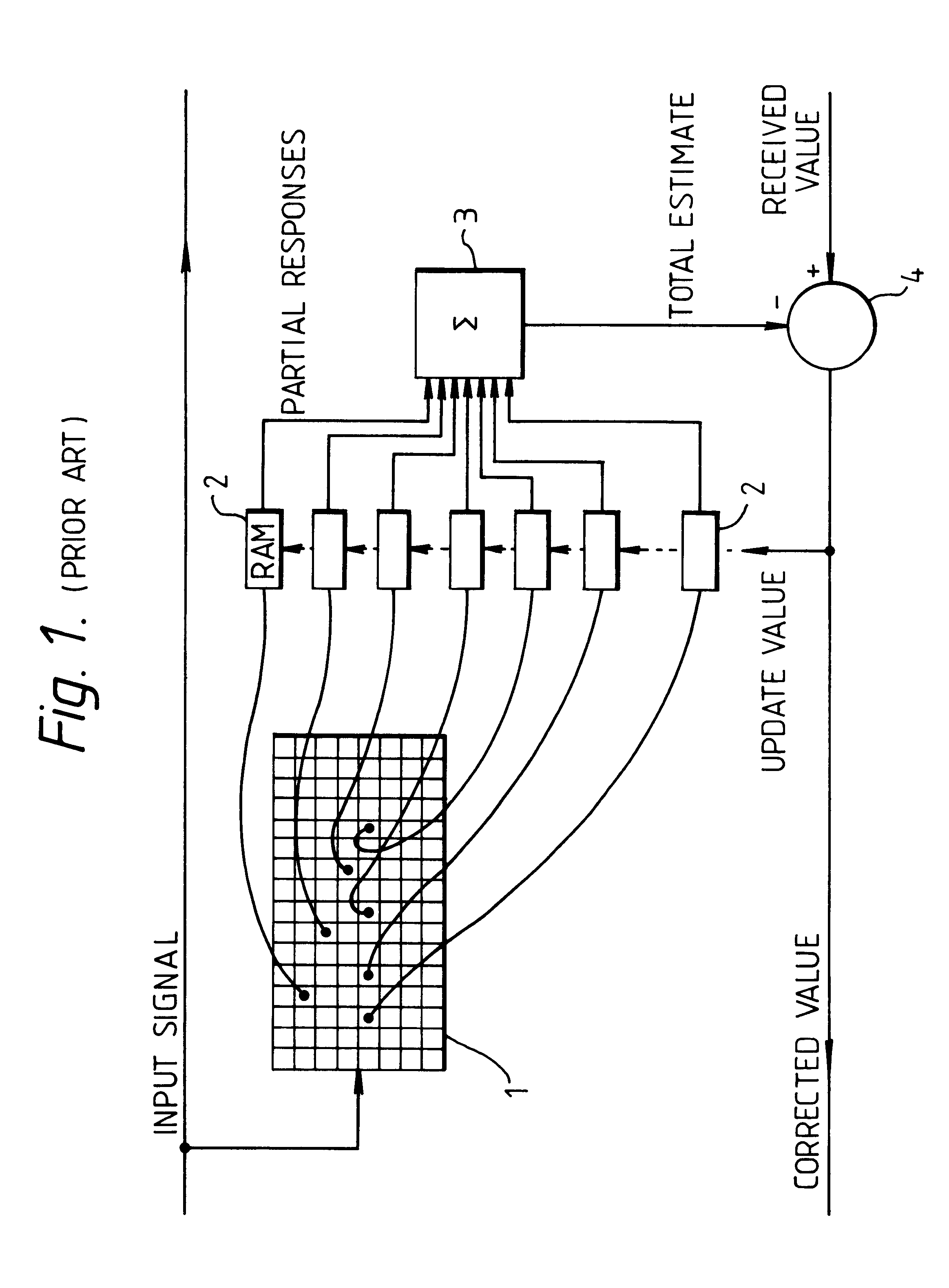
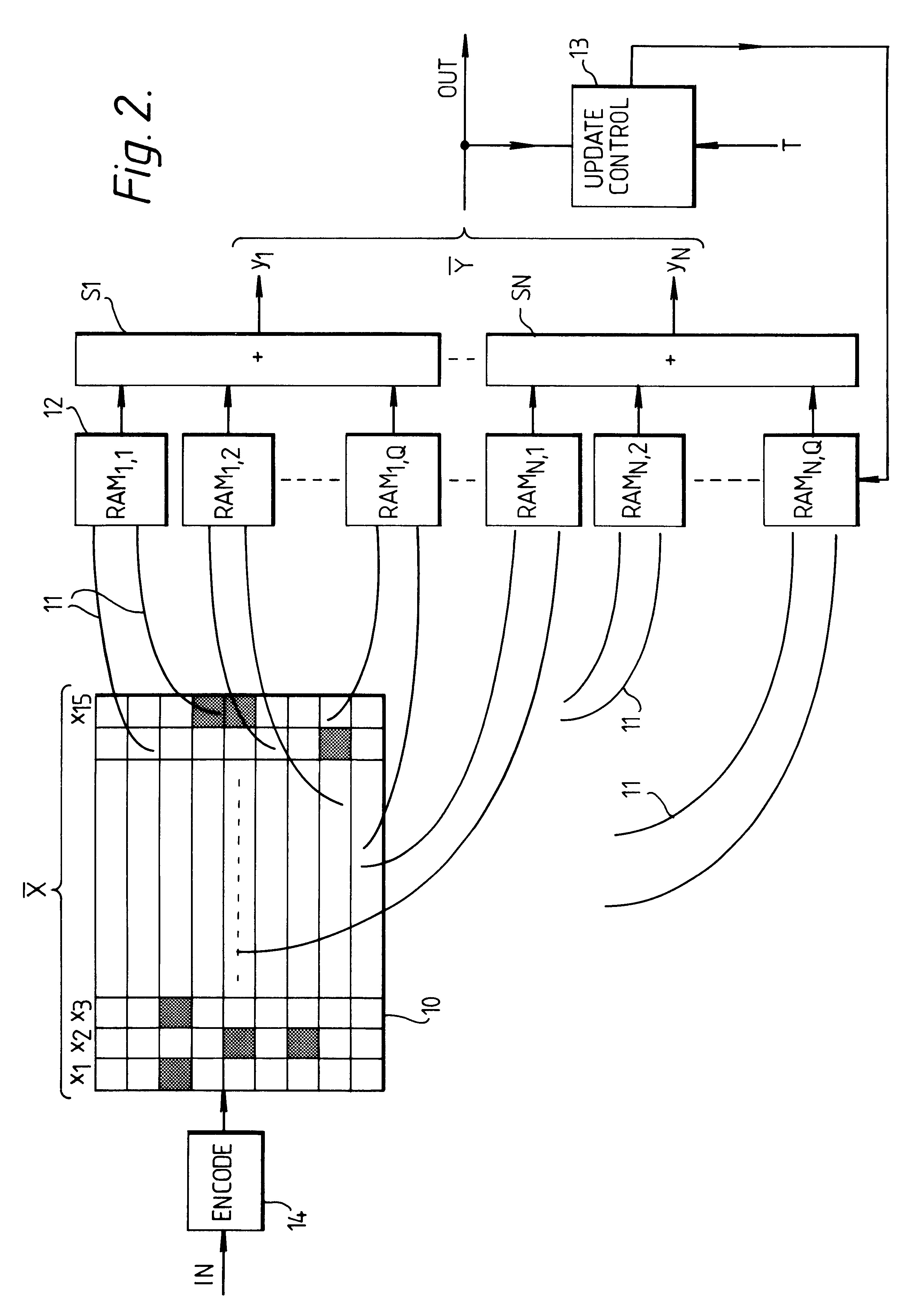
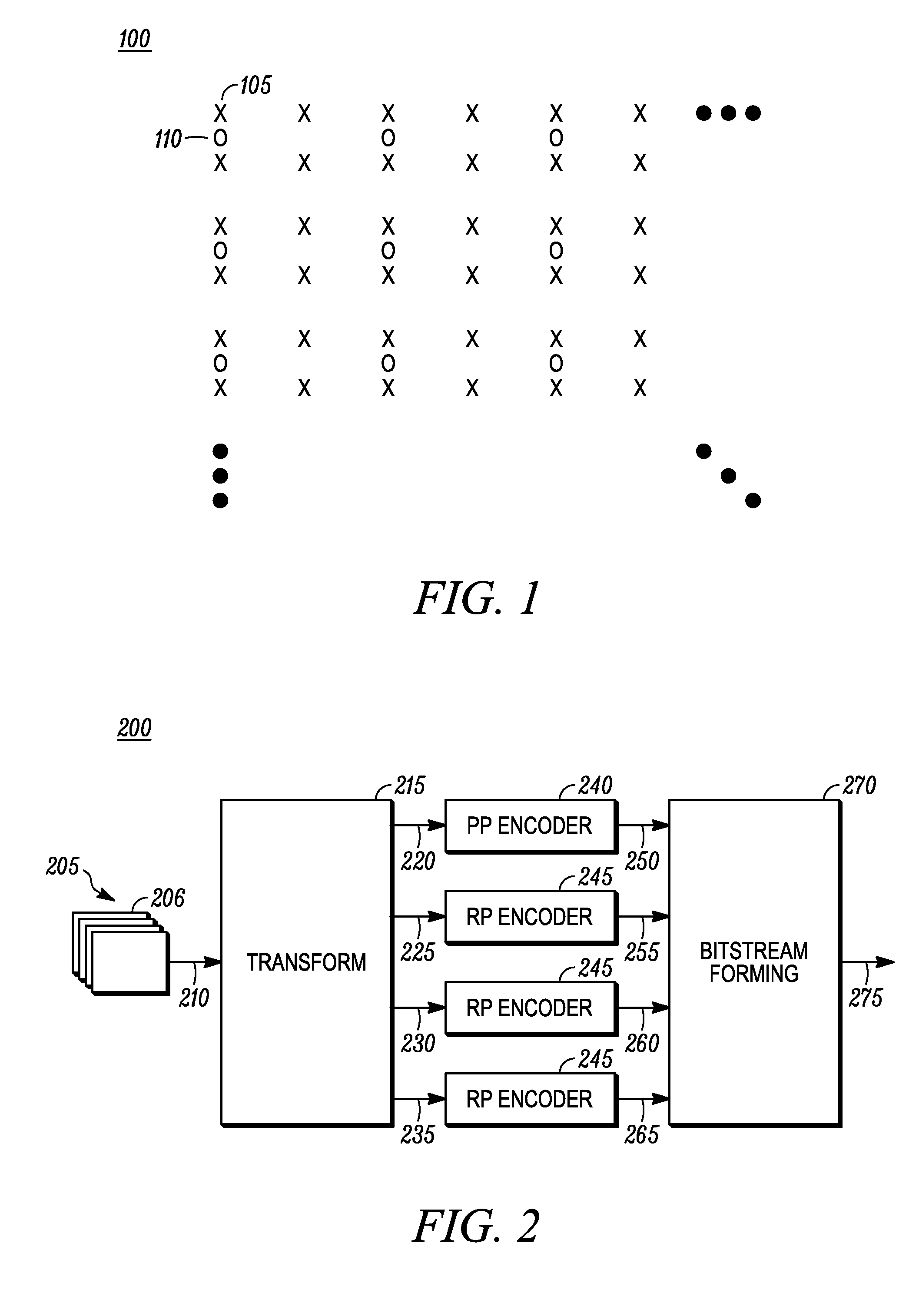
Input values are digitally represented and the bits used to address memories. A composite (e.g. the sum) of the memory outputs is formed, and update control is used during "learning" to modify the memory contents. The digital representation is formed by an encoder which encodes input values using a redundant code, which preferably has a Hamming distance to signal distance relationship which has a relatively steep initial slope and is closer to being monotonic than is the relationship for a simply binary code.
Owner:BRITISH TELECOMM PLC
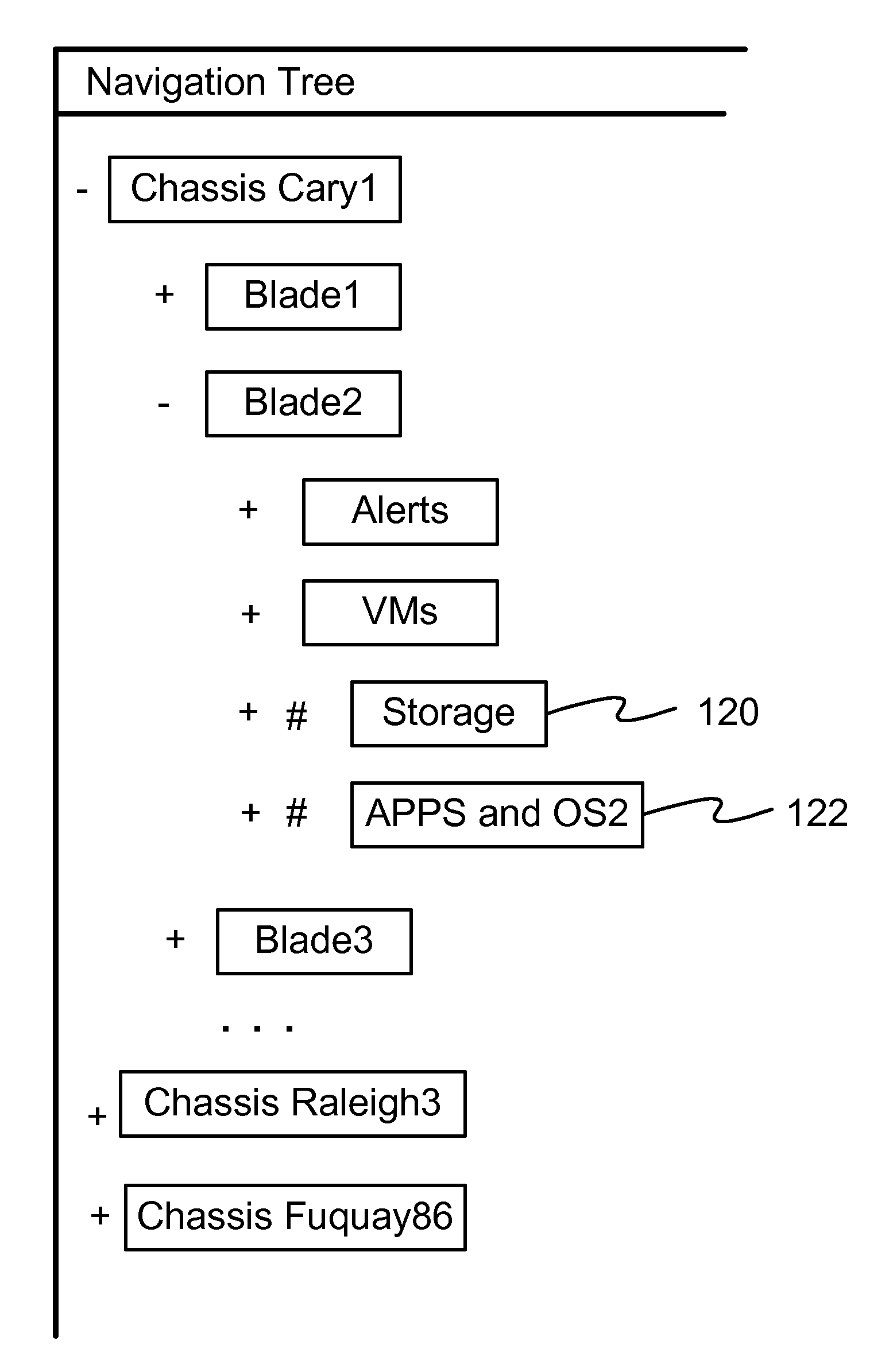
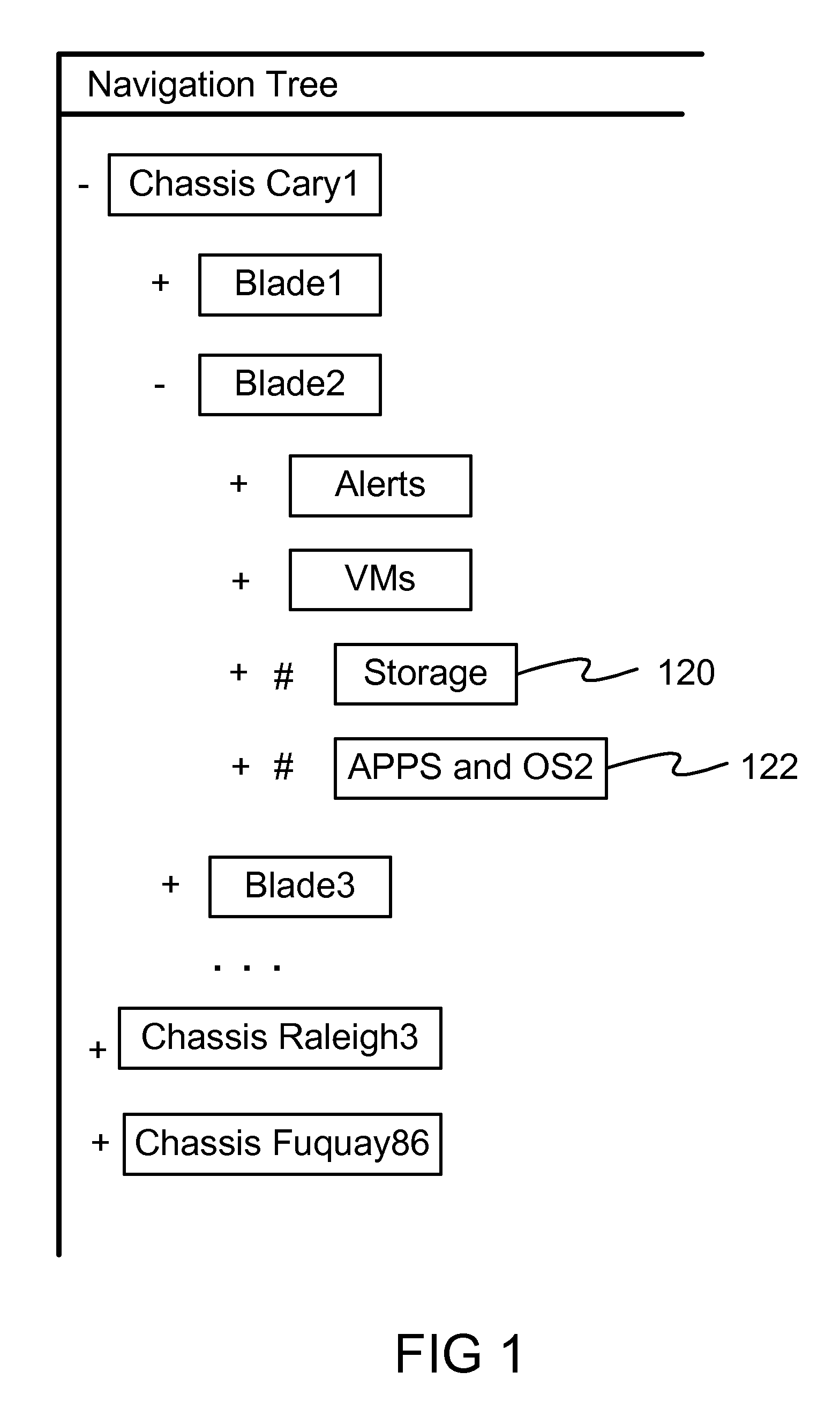
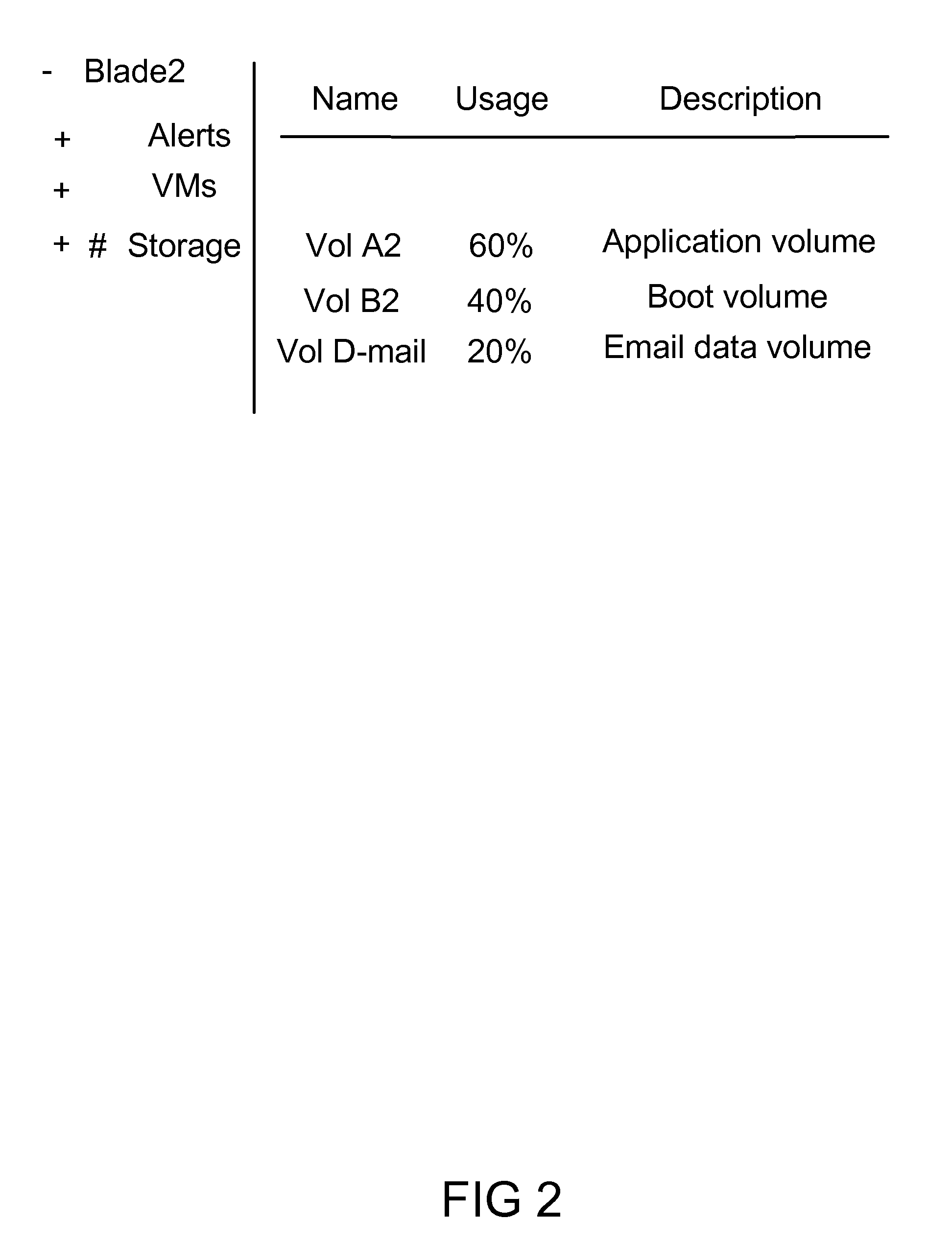
Reorienting navigation trees based on semantic grouping of repeating tree nodes
InactiveUS7669147B1More disorderlyLot of screen spaceDigital data information retrievalDigital data processing detailsRedundant codeTheoretical computer science
Non-hierarchical relationship UIs (“topology UIs”) are difficult to scale to hundreds or more items. An embodiment of this invention provides indicators and quick access controls for the nodes in navigation tree that appear more than once in a hierarchy—where a pure hierarchical navigational tree falls short. The navigational tree is structured by grouping all matching nodes together. The display area displays the most frequent and the concatenated labels of the semantically grouped redundant nodes. A set of contextual proximity and similarity information and an exception list are stored in a semantic database which is configurable by system administrators. These navigation area controls and indicators will preemptively handle non-hierarchies directly within the navigation tree.
Owner:IBM CORP
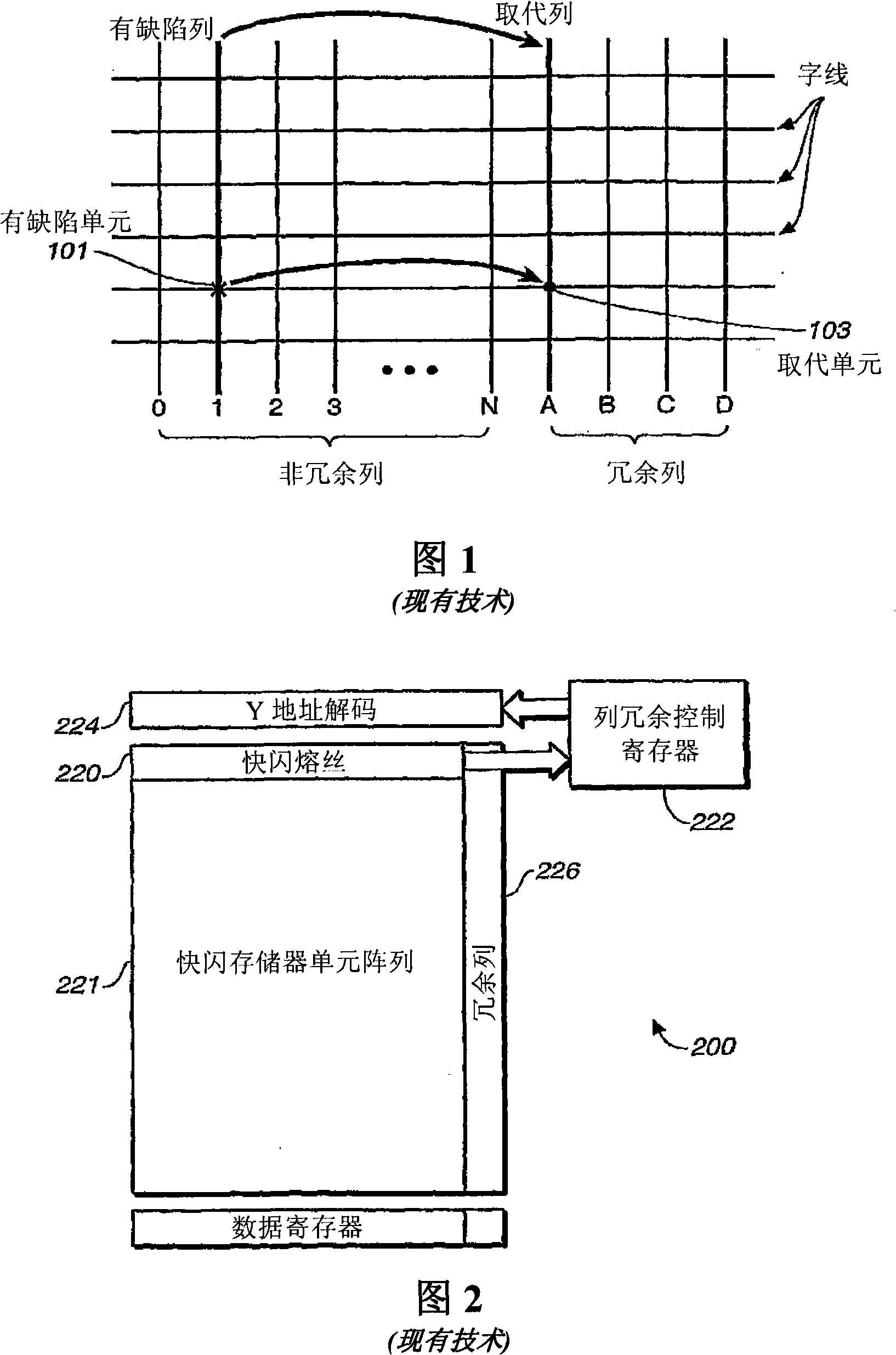
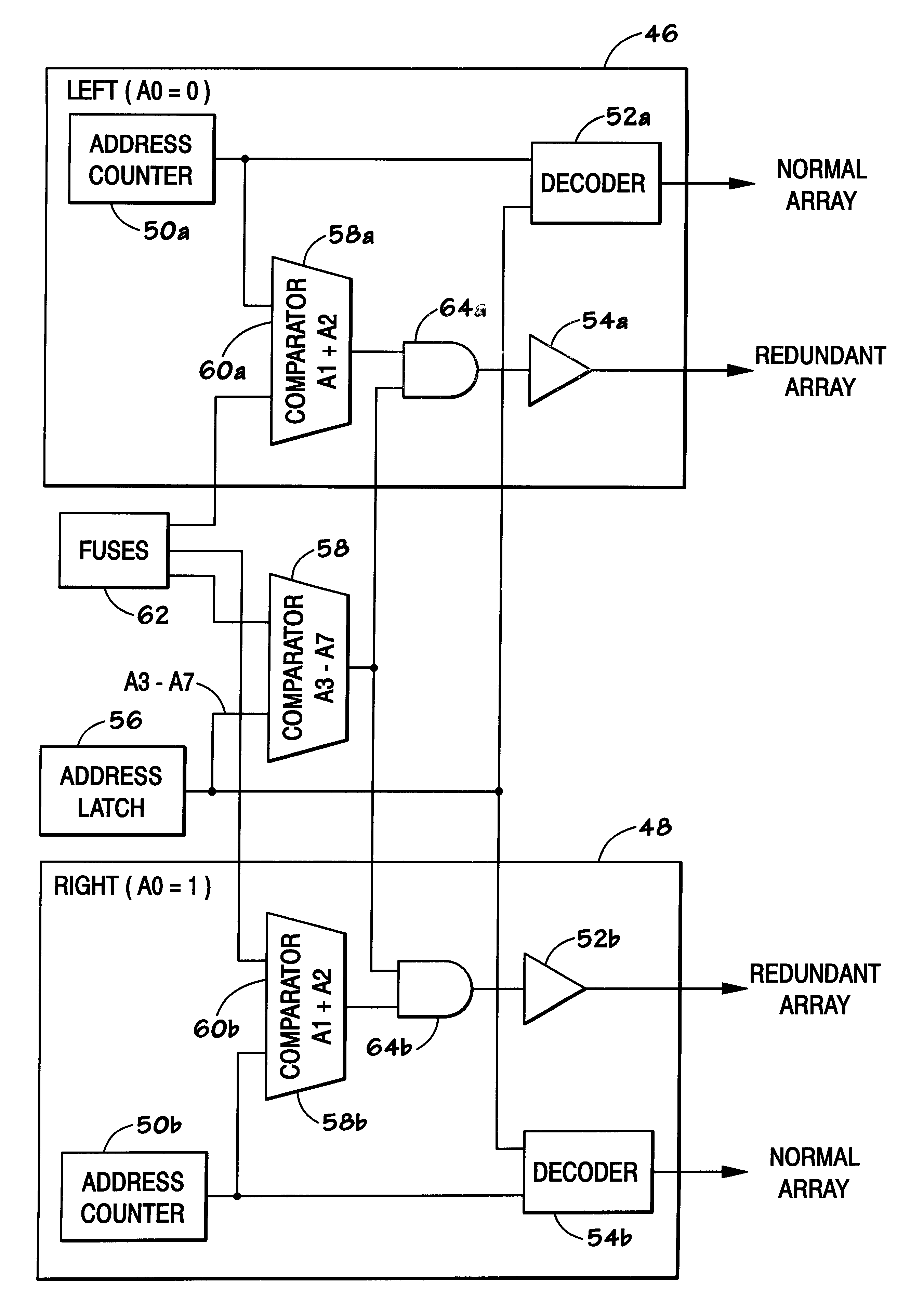
Shared redundancy for memory having column addressing
A shared redundancy prefetch scheme to provide a reduced number of fuses. DDR SDRAMs allow burst addressing at various burst lengths. DDR SDRAMs generally implement LEFT and RIGHT segment column addressing. In DDR SDRAMs which implement redundant memory arrays, fuses may be used to provide access to the redundant columns. Because burst addressing may begin with a RIGHT segment address, two different columns may be accessed on the same clock cycle. By providing a compare scheme which implements separate compare logic for the lower bits of the LEFT and RIGHT segments and compares these bits to a common fuse set used for both the LEFT and RIGHT segments, the number of fuses in the redundant DDR SDRAM scheme can be reduced.
Owner:MICRON TECH INC
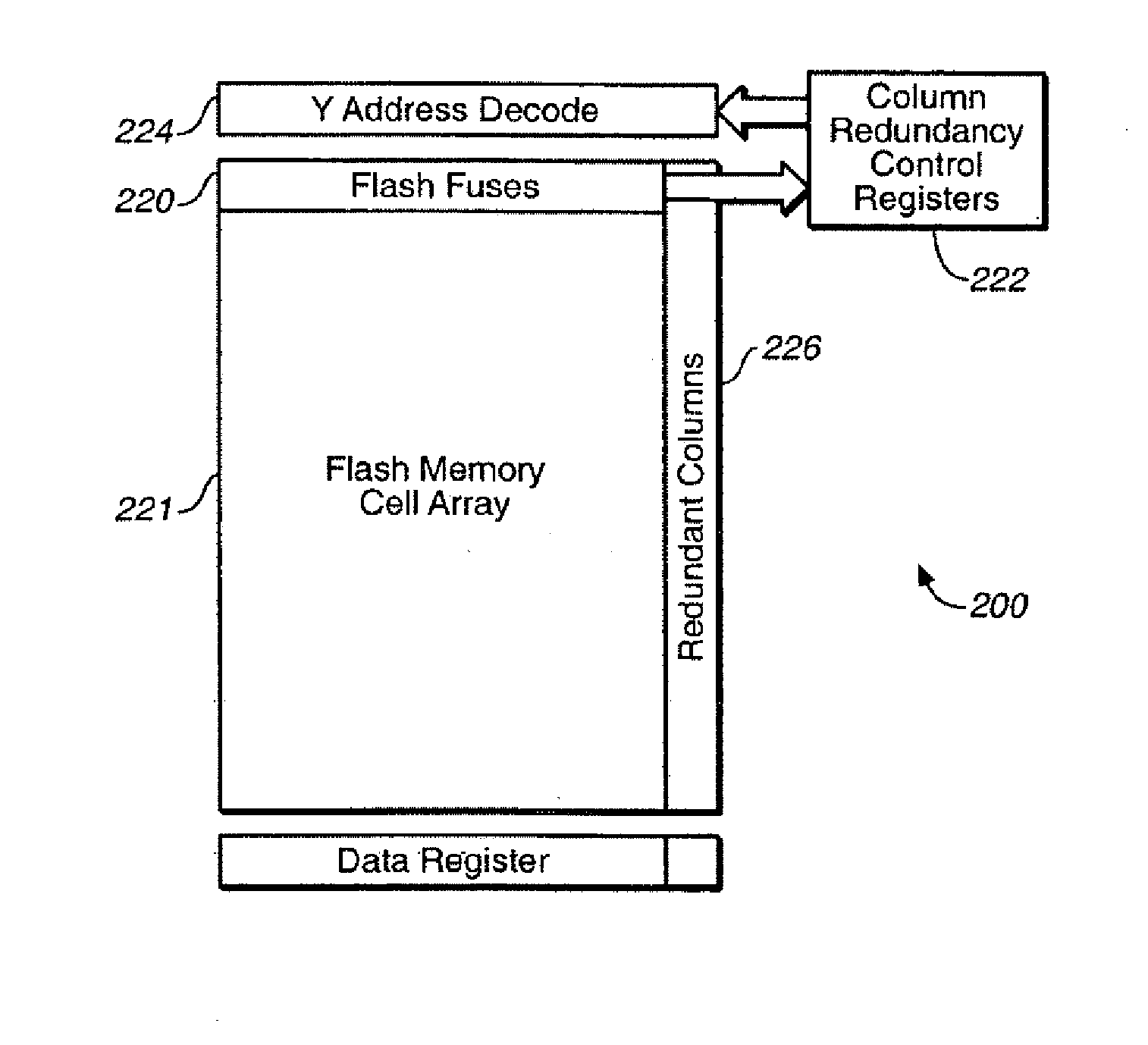
Bad Column Handling in Flash Memory
ActiveUS20140157087A1Low reliabilityStatic storageRedundant data error correctionRedundant codeComputer science
In a flash memory, redundant columns are used alternatively as replacement columns for replacing bad columns or to provide additional redundancy for ECC encoding. Locations of bad columns are indicated to a soft-input ECC decoder so that data bits from bad columns are treated as having a lower reliability than data bits from other columns.
Owner:SANDISK TECH LLC
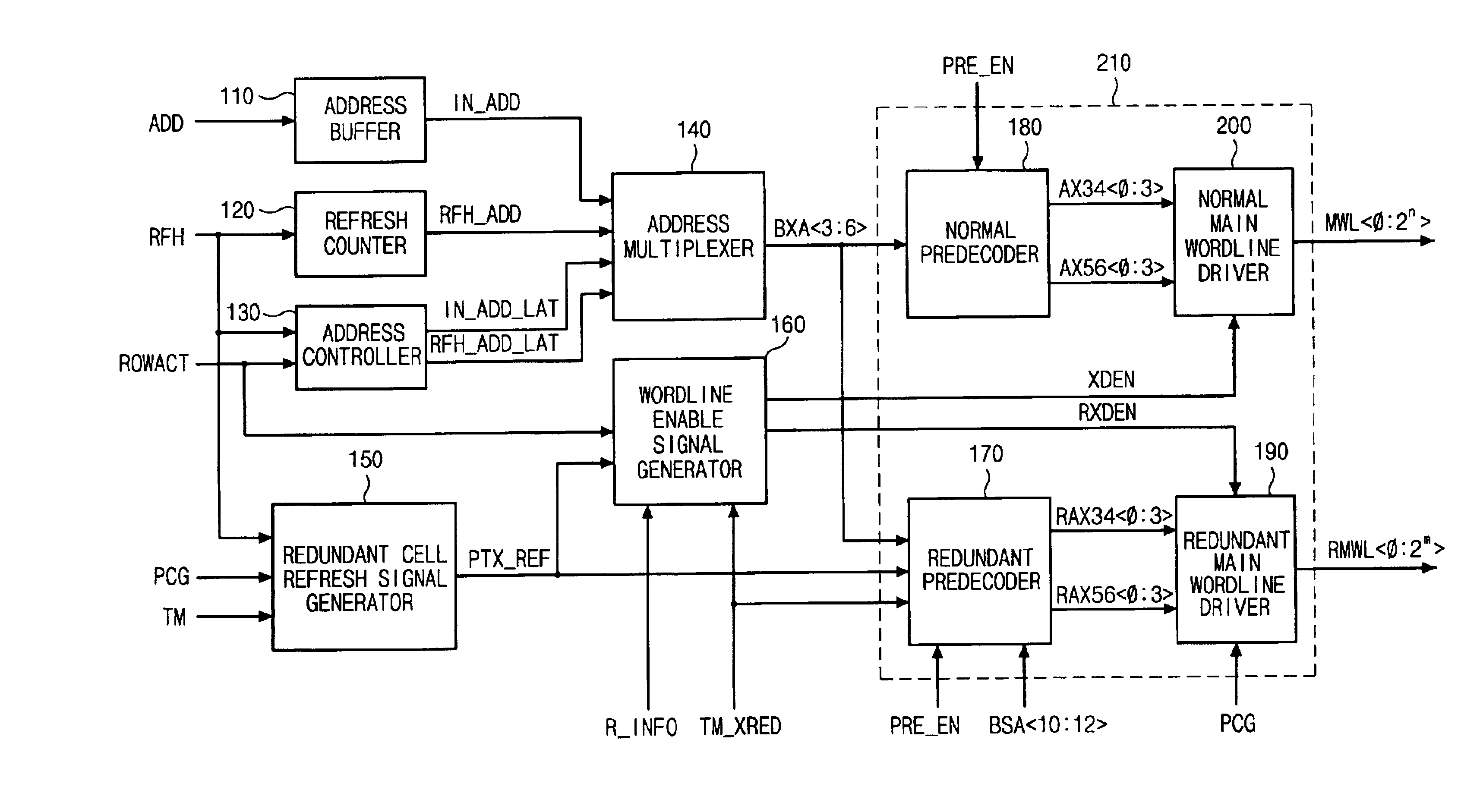
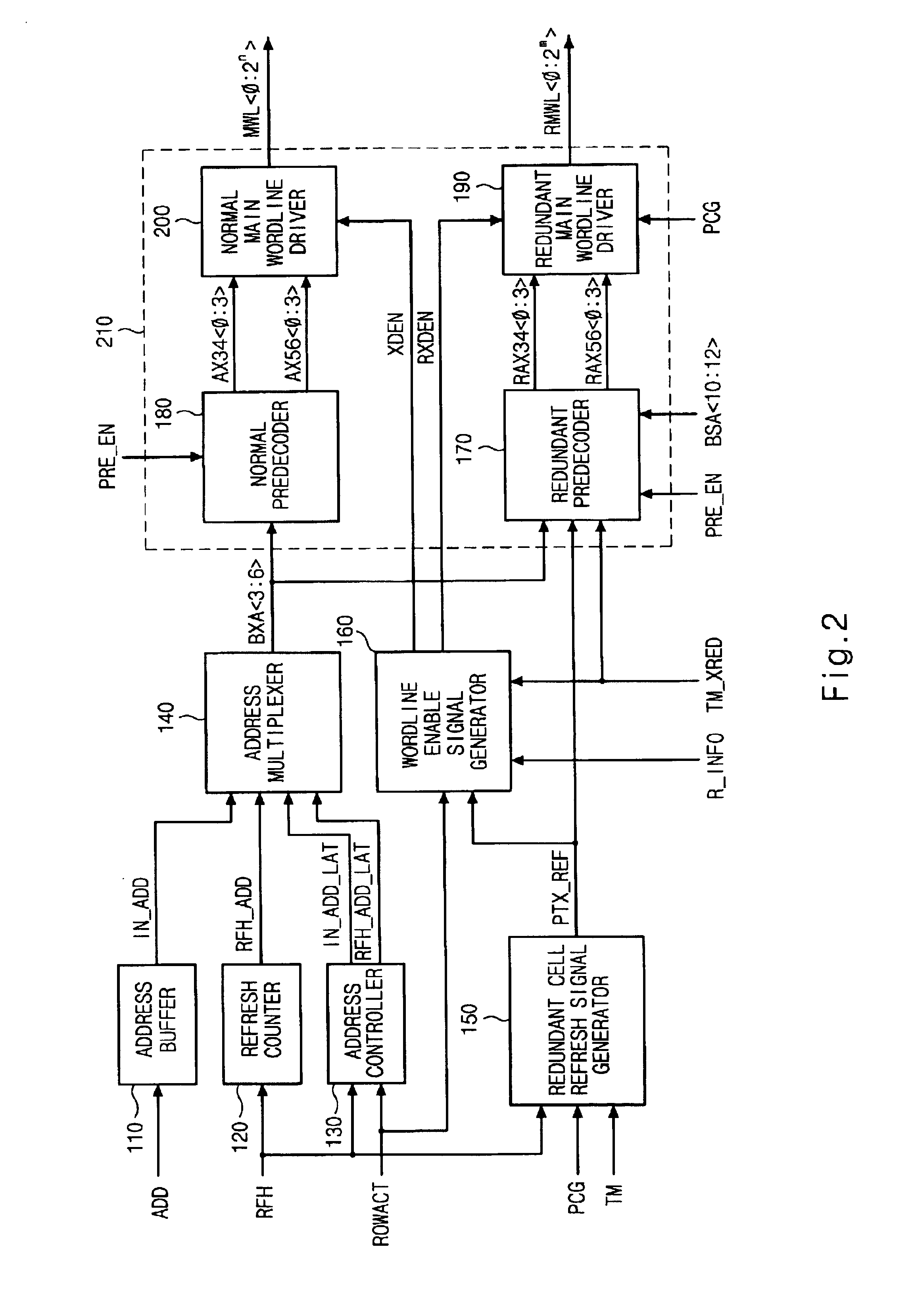
Refresh apparatus for semiconductor memory device, and refresh method thereof
A refresh apparatus for a semiconductor memory device and a refresh method thereof that can reduce a test time by simultaneously refreshing a normal cell and a redundant cell in one test mode is disclosed. The refresh apparatus for the semiconductor memory device may include a redundant cell refresh signal generator for generating a redundant cell refresh signal for refreshing a redundant cell when a refresh is requested in a test mode, a wordline enable signal generator for generating a normal main wordline enable signal and a redundant main wordline enable signal in response to the redundant cell refresh signal in a redundant cell test mode and a wordline driver for simultaneously refreshing the normal and redundant cells by simultaneously driving a normal main wordline and a redundant main wordline in response to the redundant cell refresh signal, the normal main wordline enable signal, the redundant main wordline enable signal and a row address in the redundant cell test mode.
Owner:SK HYNIX INC
System and method to display raster images with negligible delay time and reduced memory requirements
The present invention is directed to a general purpose raster image system. The present invention performs transformations on an original raster image, and optimizes the raster image decoding and display techniques, to dramatically increase the display performance capabilities by a factor of up to fifteen times the performance provided by previous raster devices. The present invention employs two primary enhanced display features to produce fast raster image decode and display results: (1) data reduction and transformations and (2) optimized algorithmic implementations. Data reduction and transformations operate as follows: a raster image is divided into strips, which are processed individually. A feature of the optimized algorithmic implementation is to increase processing thruput of the display process by optimizing the use of available resources required to decode and display the raster images. In one embodiment, scaling operations are converted from calculation based algorithms, to data lookup tables indexed by the position of the raster image data in the original scan line. Raster image decoding algorithms are changed from iterative conditional loops to redundant code segments individually tailored for specific occurrences of raster image data. Additionally implementation of assembly language in time critical sections of display procedures allocates CPU register resources more efficiently and significantly increases performance.
Owner:UNISYS CORP
Semiconductor integrated circuit device
InactiveUS6324104B1Memory architecture accessing/allocationMemory adressing/allocation/relocationAudio power amplifierRedundant code
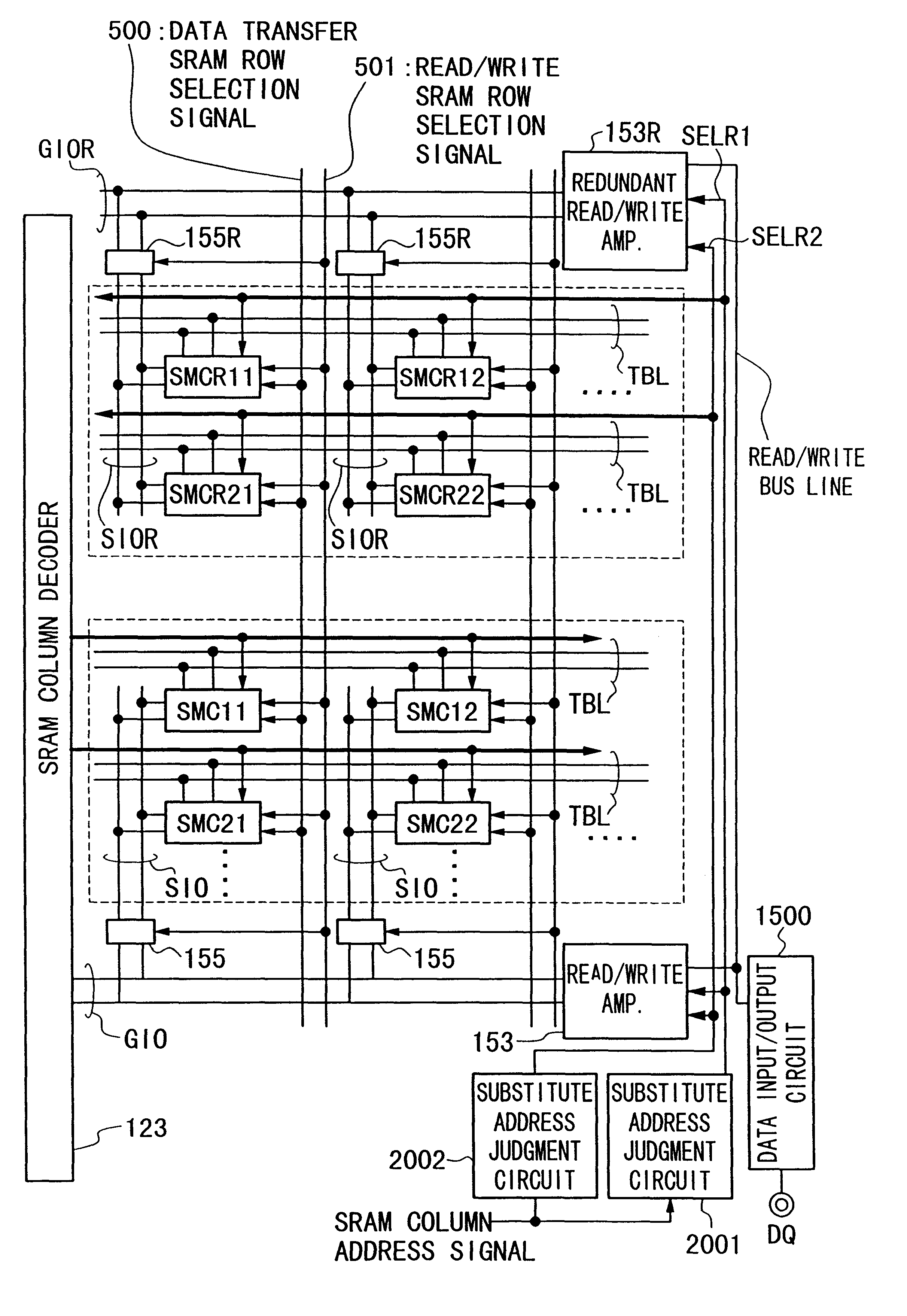
A semiconductor integrated circuit device which can save defect bits in an auxiliary storage portion functioning as a cache memory is provided. A redundant SRAM cell array MAR is provided so as to be adjacent to a SRAM cell array MA of a SRAM portion functioning as a cache memory, and with the positions of rows matching. Redundant cells which are alternatively selected based on redundant selection signals, are arranged in matrix form in this redundant SRAM cell array MAR. Moreover, a data input / output line SIOR is provided in each row of this SRAM cell array MAR, and each data input / output line SIOR is connected to a global data input / output line GIOR via a data input / output line connection circuit which is alternatively conduction controlled based on a predetermined selection signal. This global data input / output line GIOR is connected to a read / write bus line together with a read / write amplifier which is used at normal times.
Owner:RENESAS ELECTRONICS CORP
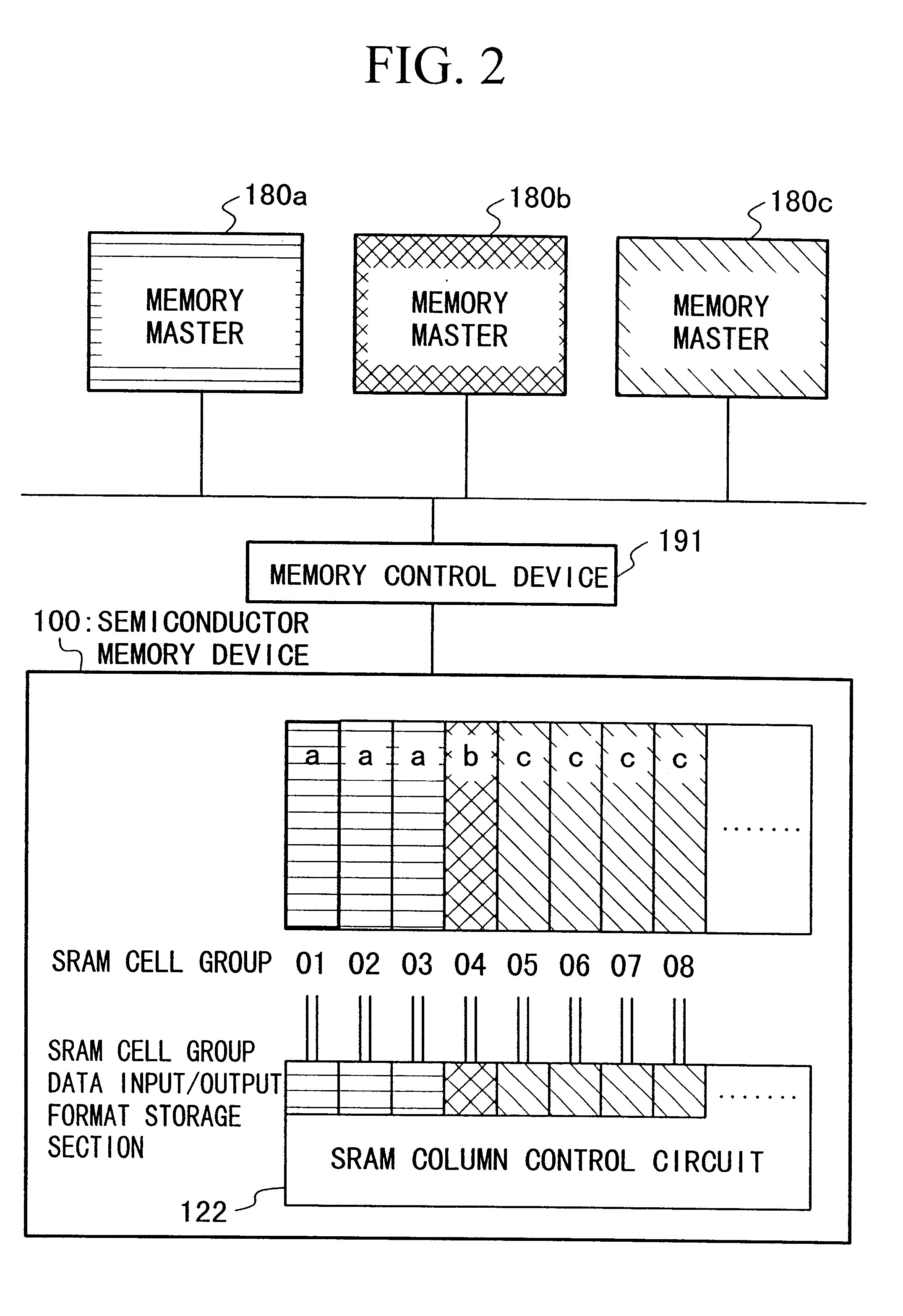
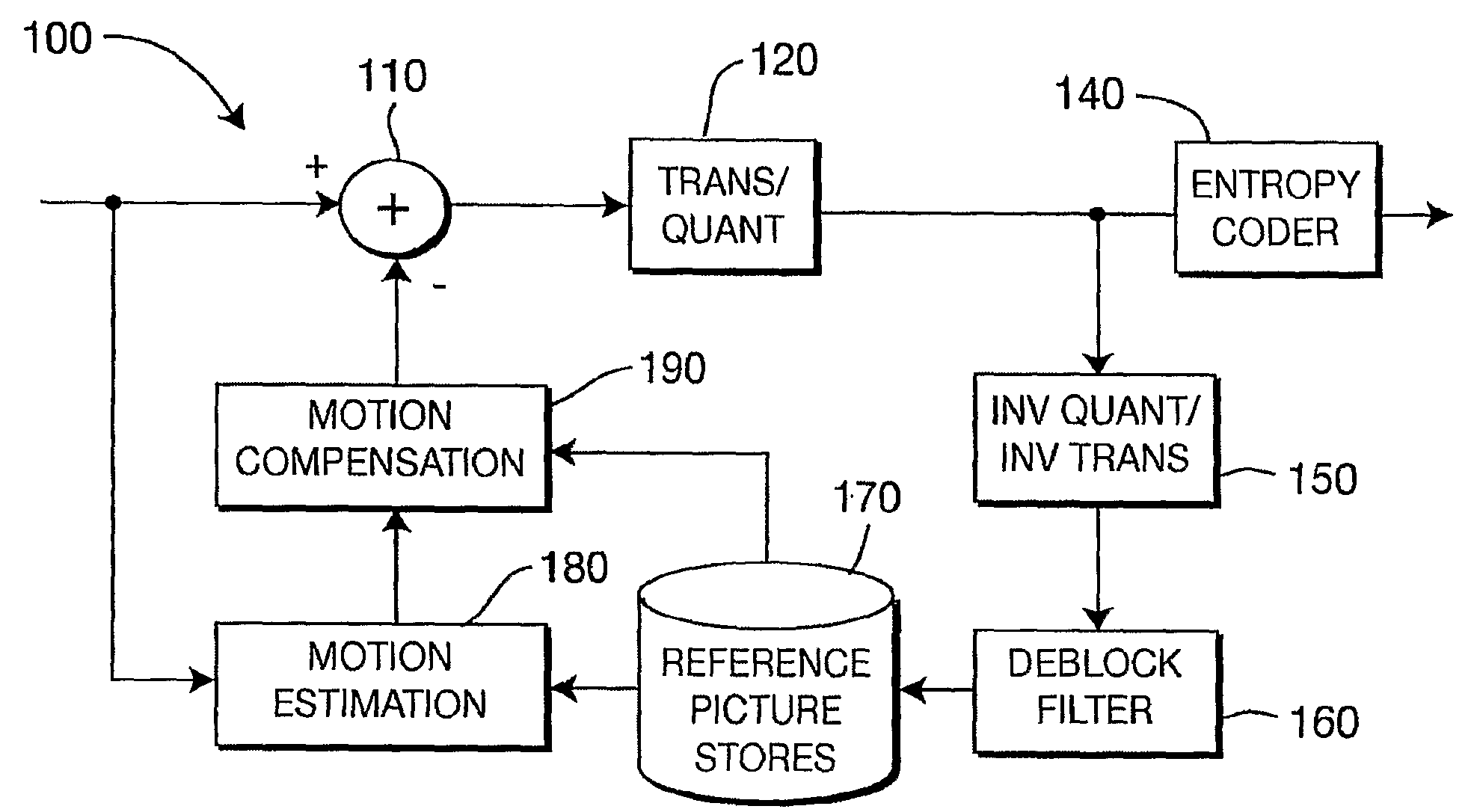
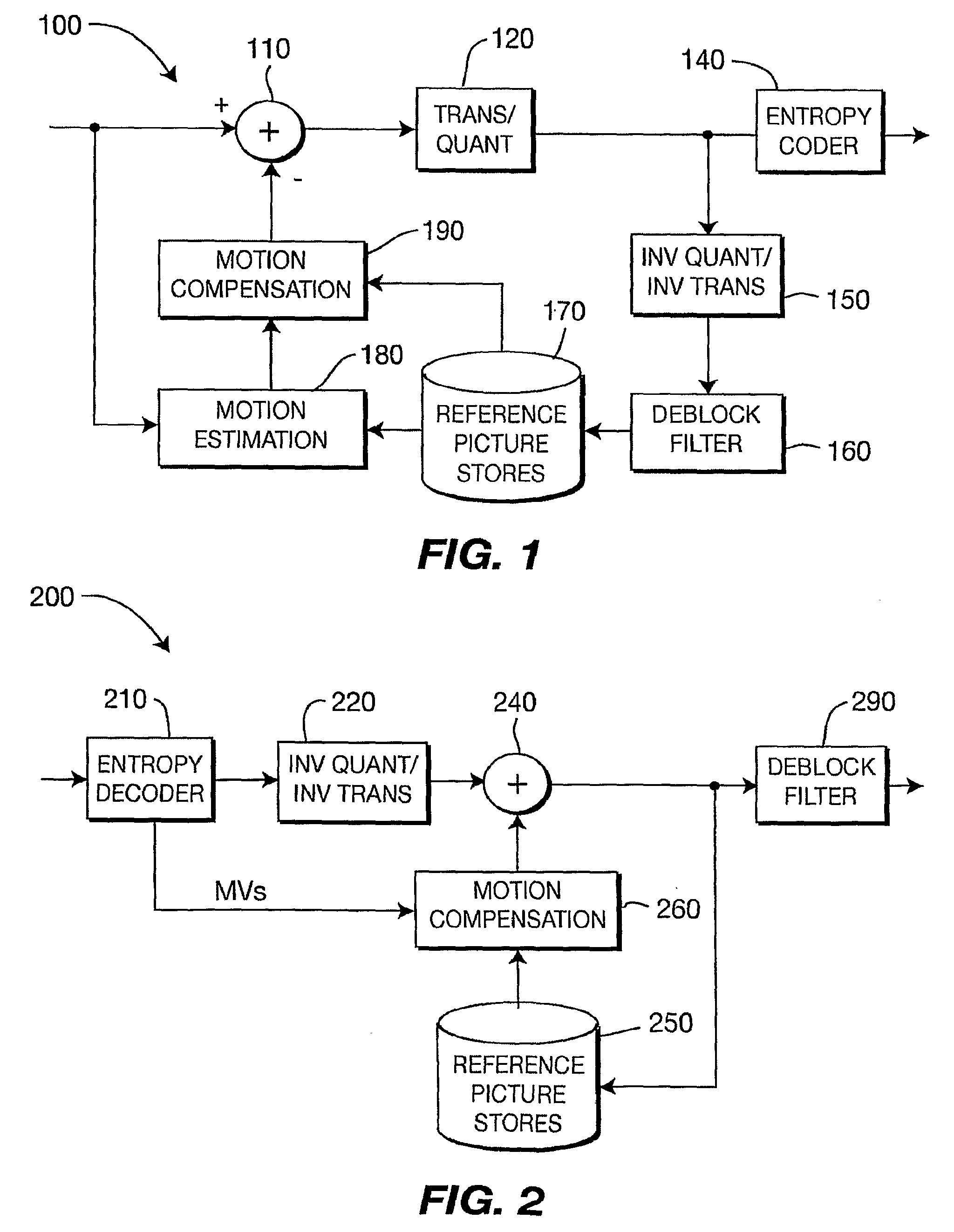
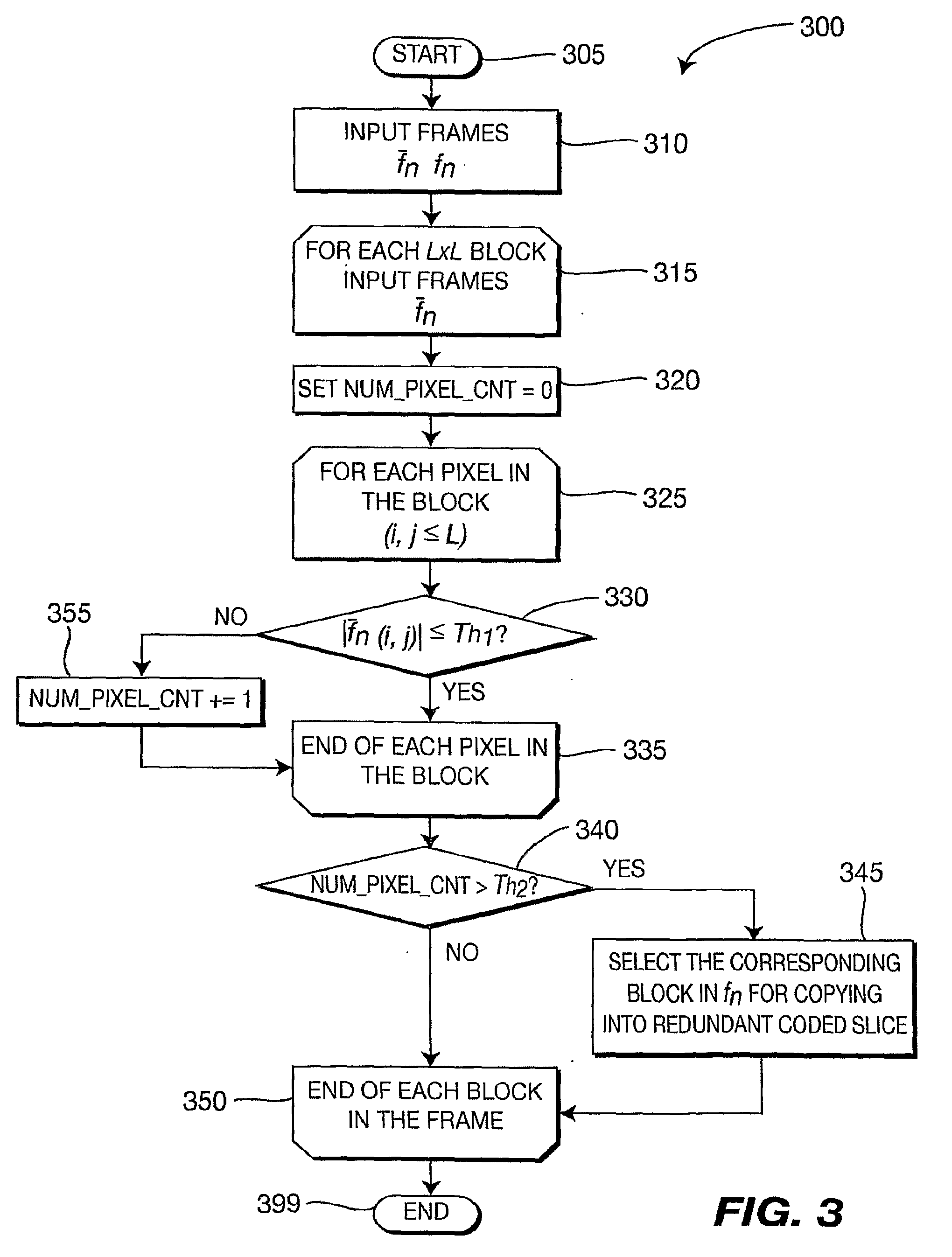
Method and Apparatus for Redundant Video Encoding
ActiveUS20090052543A1Color television with pulse code modulationColor television with bandwidth reductionVideo encodingRedundant code
A method and apparatus are provided for redundant video coding. The apparatus includes an encoder for encoding a redundant coded picture corresponding to a source picture by selecting individual blocks in the source picture for inclusion into the redundant coded picture.
Owner:INTERDIGITAL MADISON PATENT HLDG
Data structure for flash memory and data reading/writing method thereof
ActiveUS20080294935A1Effective protectionStatic storageRedundant data error correctionRedundant codeByte
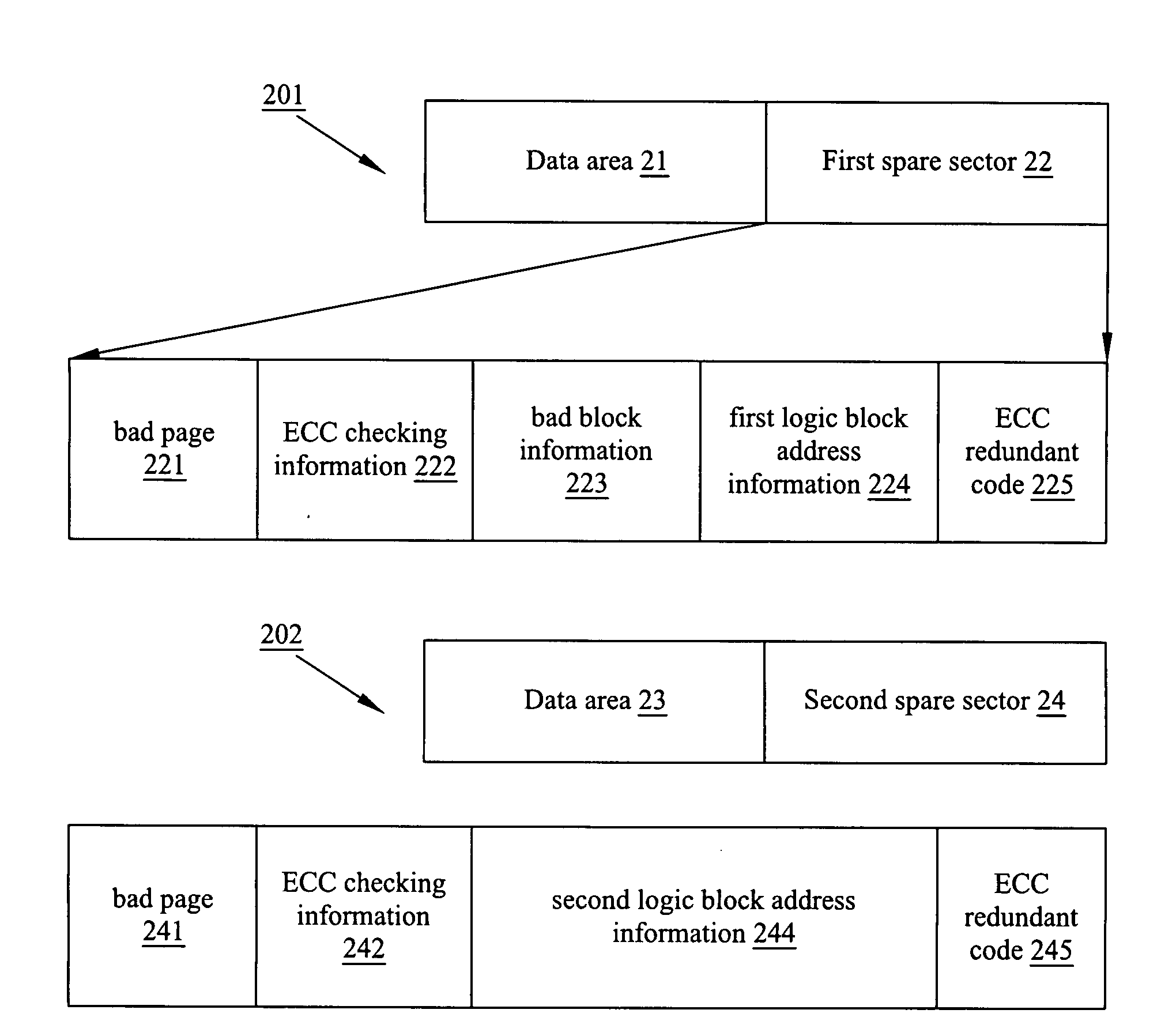
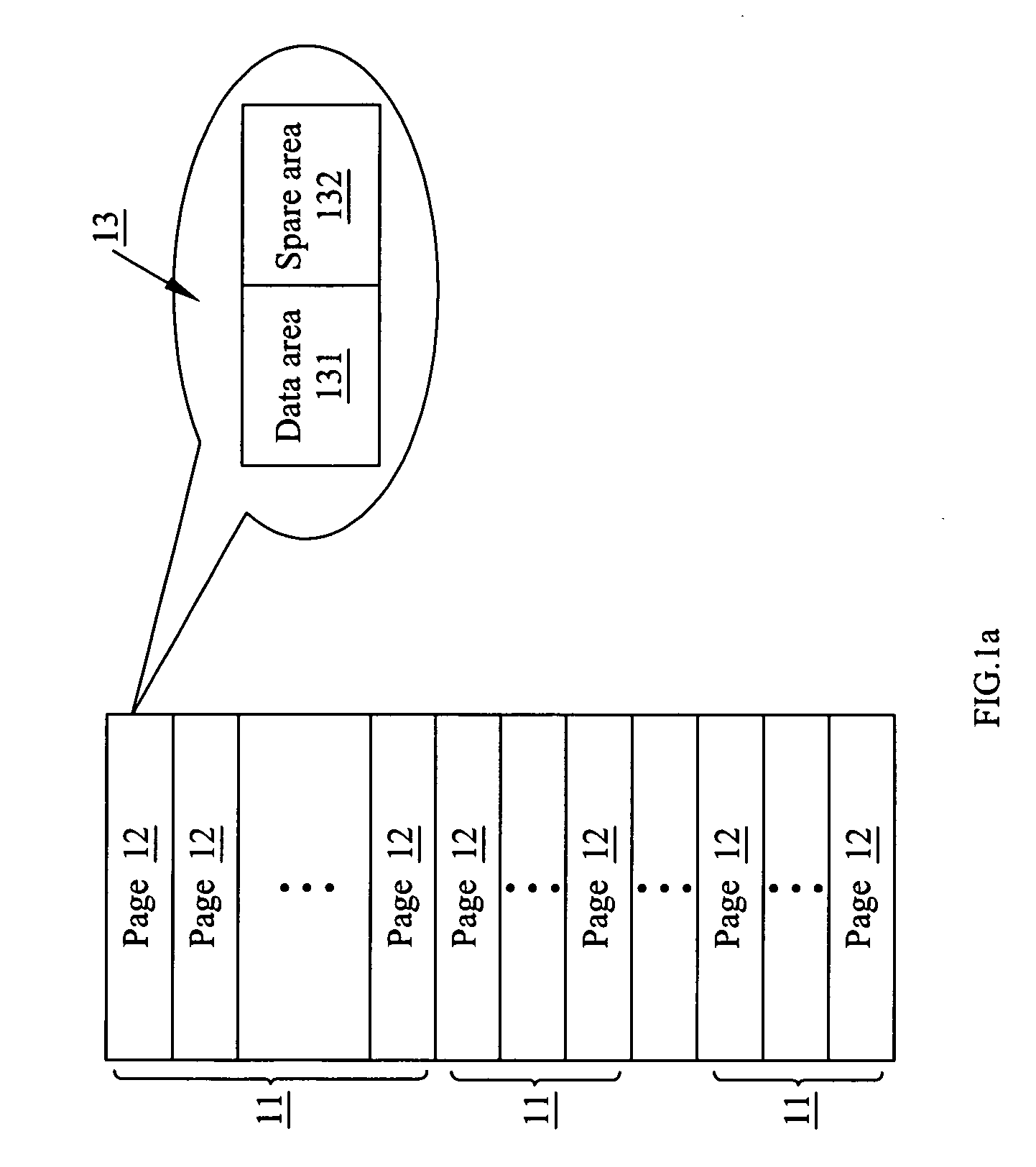
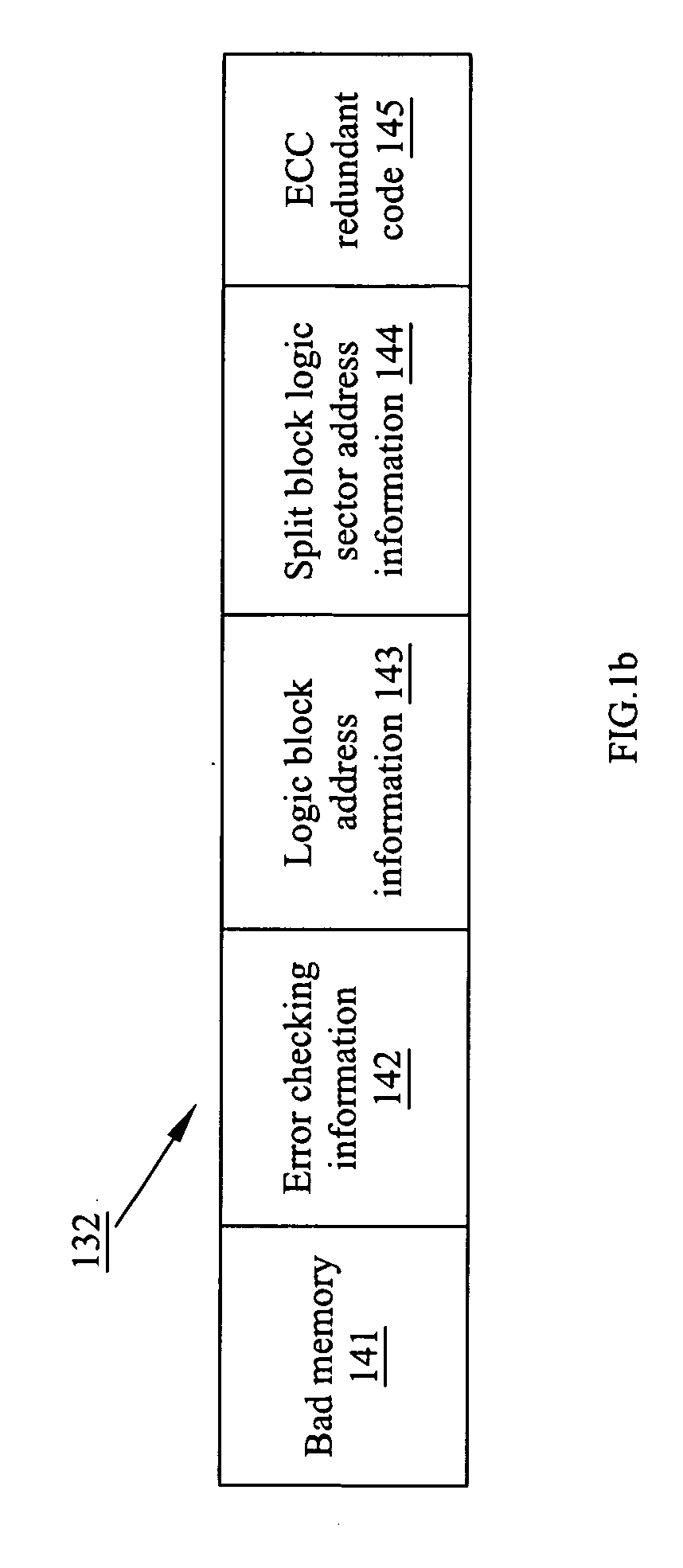
A data structure for a flash memory and data reading / writing method thereof are disclosed. A 512 bytes data and a redundant code derived from the data encoded with a 6-bit error correcting code scheme are stored in a first sector and a second sector with sequential address in a block of the flash memory respectively. A logic block address information of this block is divided into two parts that are stored in the first sector and the second sector respectively.
Owner:REALTEK SEMICON CORP
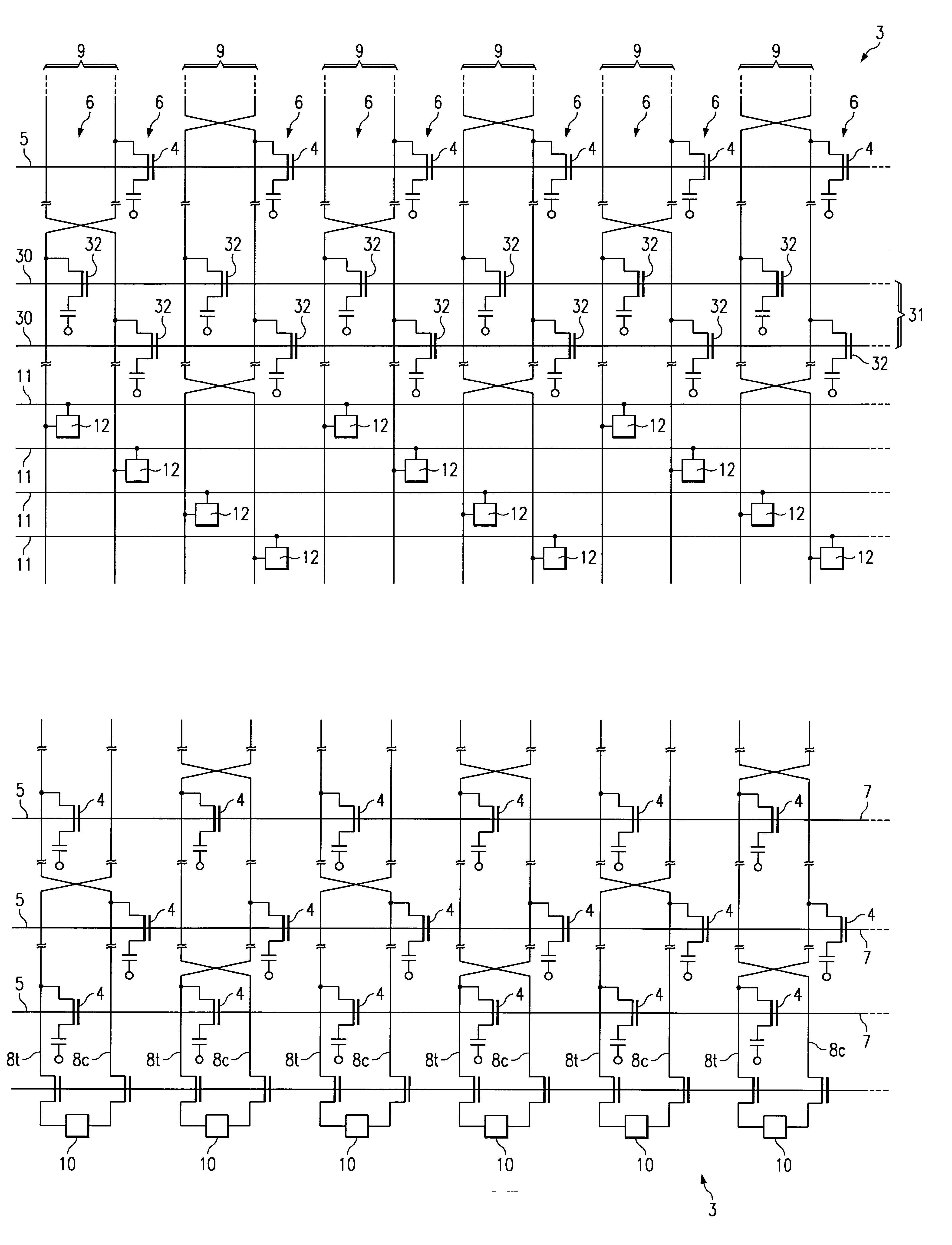
Redundant memory cell for dynamic random access memories having twisted bit line architectures
A dynamic random access memory (DRAM) device is disclosed. The DRAM device includes a memory cell array having a twisted bit line architecture. The memory cell array includes at least one pair of redundant rows of memory cells. Redundant row decode circuitry is capable of configuring the pair of redundant rows to replace any one row of memory cells having a defect. Each pair of bit lines is coupled to a distinct memory cell from each redundant row of the redundant row pair so that both the true and complement version of a data value is maintained by the redundant row pair. Rows of reference cells are disconnected and / or disabled during a memory access operation involving the redundant row pair. The use of a pair of redundant rows of memory cells to replace a single row of memory cells having a defect substantially reduces the complexity of decode circuitry for enabling the rows of reference cells.
Owner:STMICROELECTRONICS SRL
Radio communication apparatus, radio communication method, communication control apparatus, and program
InactiveUS20110182195A1Frequency-division multiplex detailsNetwork traffic/resource managementRedundant codeNetwork packet
There is provided a radio communication apparatus including a detection unit to detect first redundant information indicating redundancy at a physical / MAC layer of radio communication, a communication control unit to determine a second redundancy at an upper layer from the layer based on the first redundant information detected by the detection unit, a packetizing unit to generate a data packet by packetizing transmission data, and a redundant encoding unit to add a redundant packet to the data packet generated by the packetizing unit based on the second redundancy determined by the communication control unit.
Owner:SONY CORP
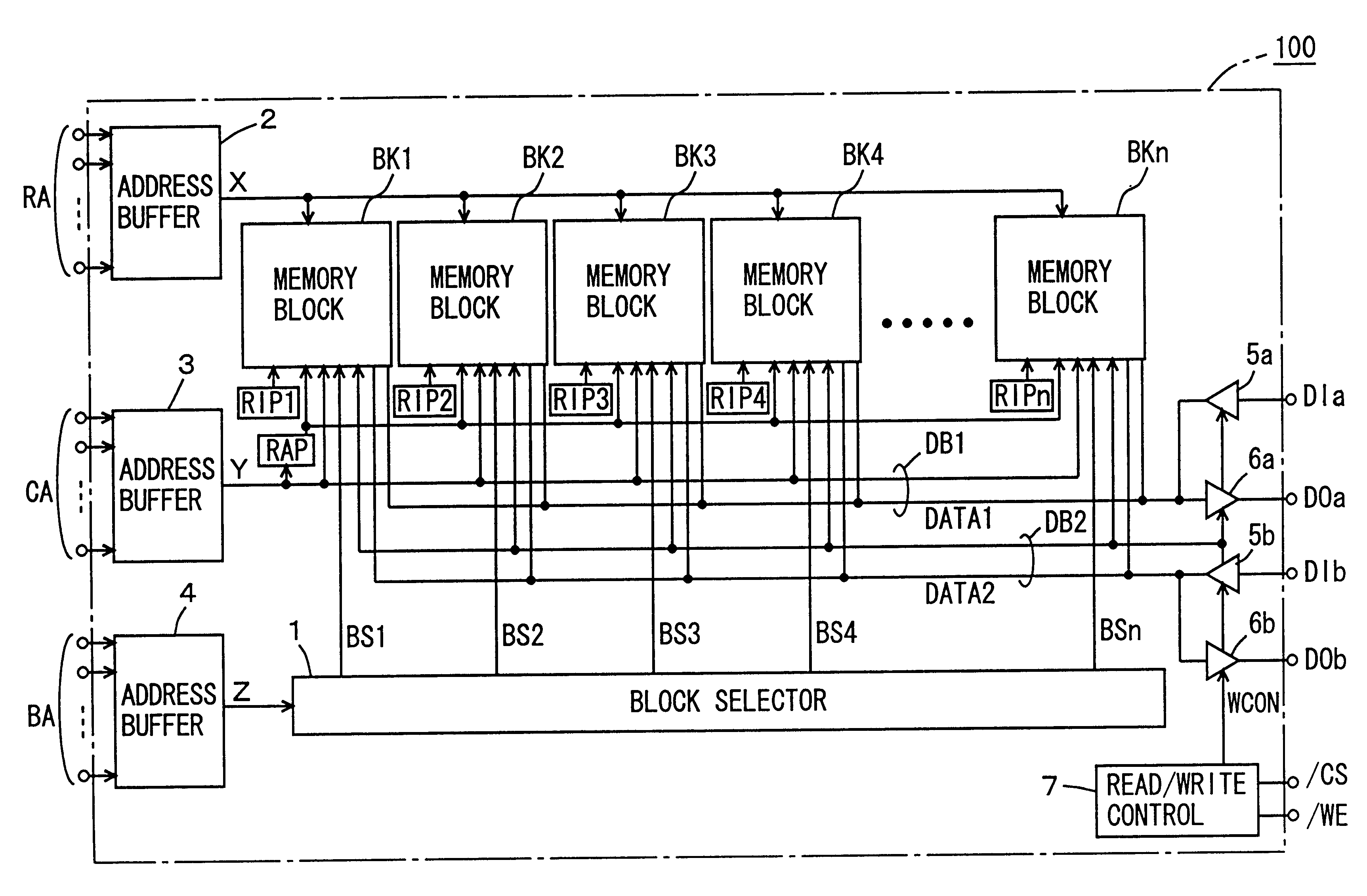
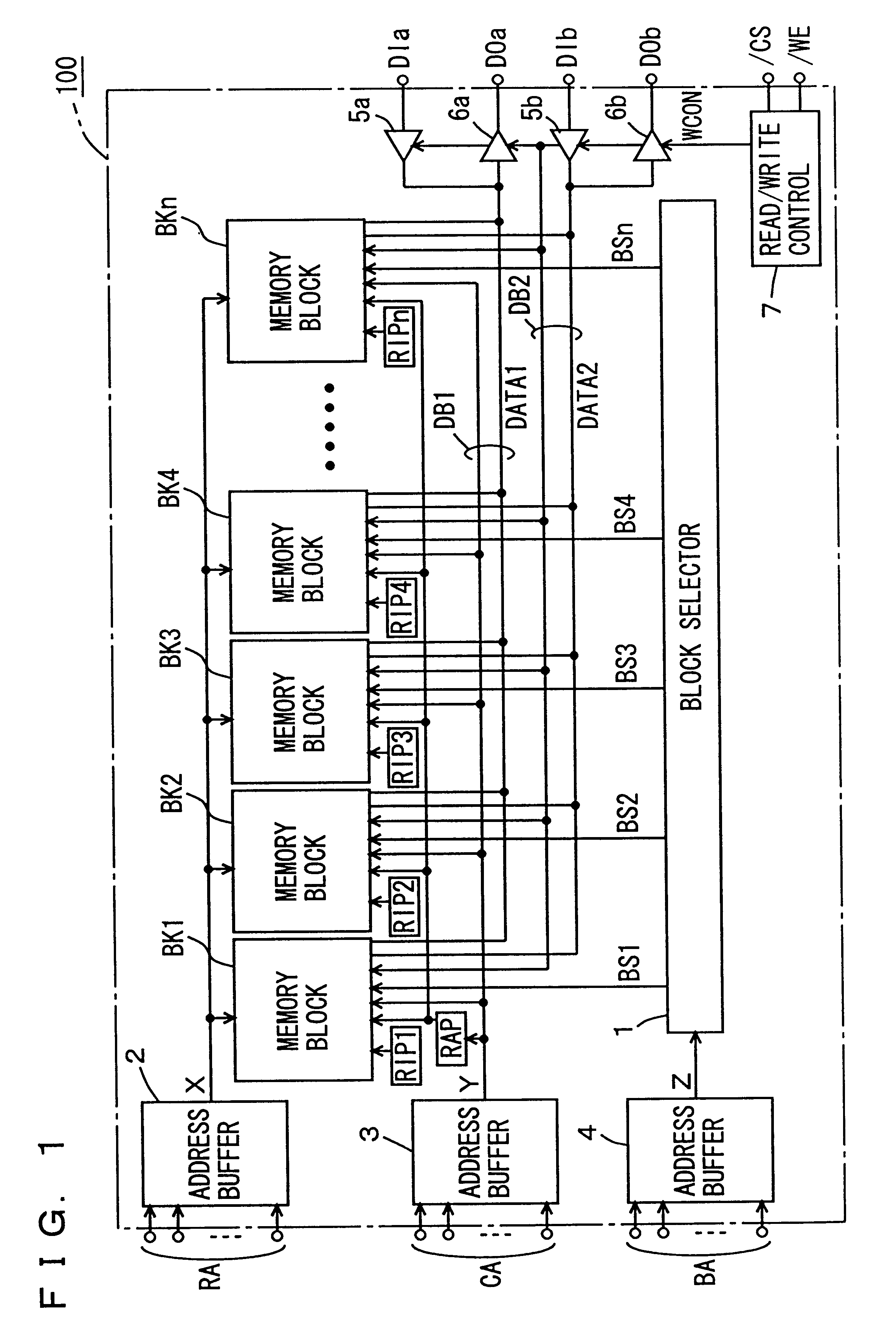
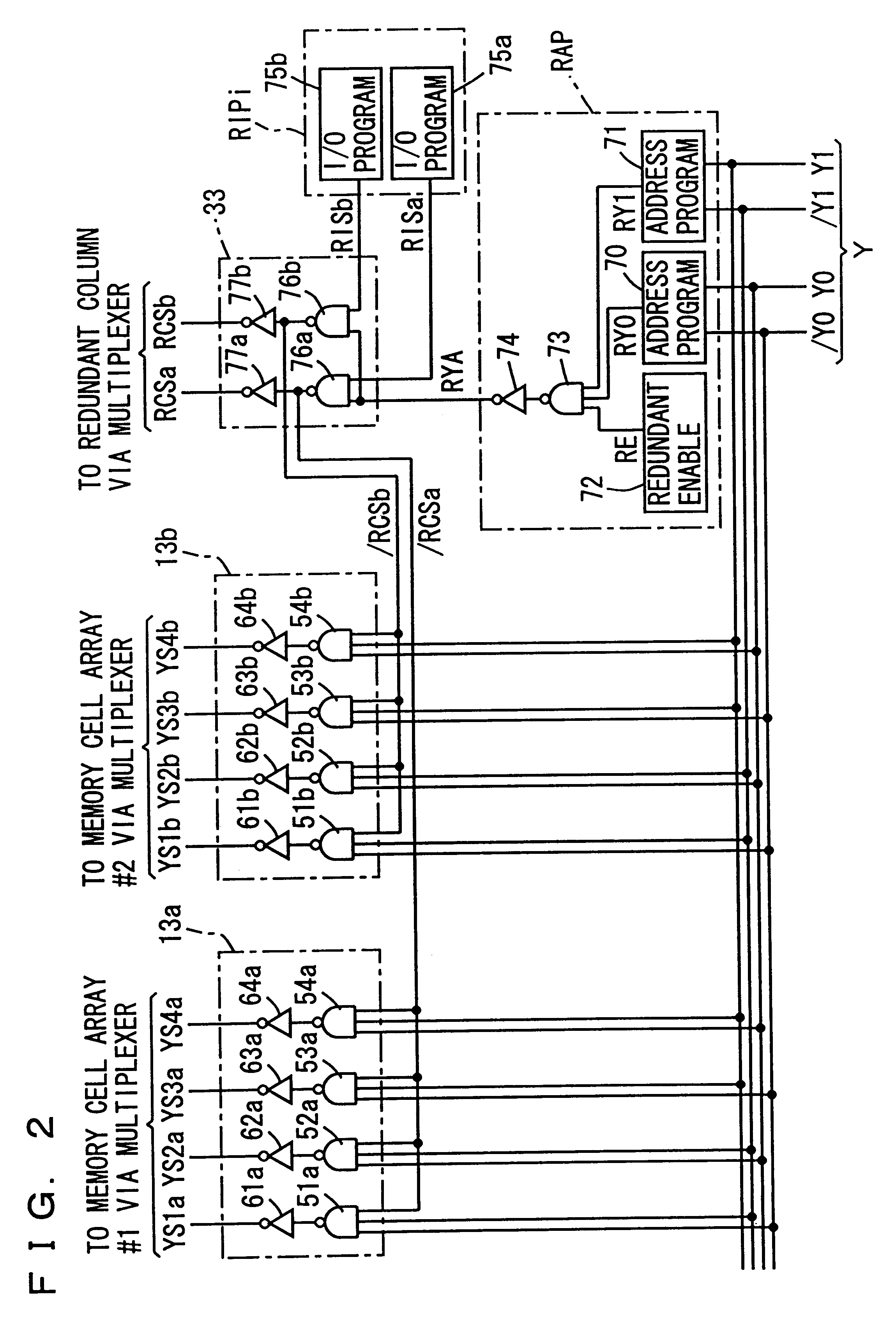
Semiconductor memory device allowing reliable repairing of a defective column
A replacement IO program circuit is provided for each of memory blocks coupled commonly to a data bus of multiple bits, and a replacement column address program circuit is provided for a predetermined number of memory blocks. The state of use of a redundant column can be independently determined in each memory block, and the number of program circuits and the area occupied by the circuits are reduced. A semiconductor memory device includes a defective column repairing circuit allowing efficient use of the redundant column without increasing a chip area.
Owner:MITSUBISHI ELECTRIC CORP
Security chip design method based on control flow detection and resistant to error injection attack
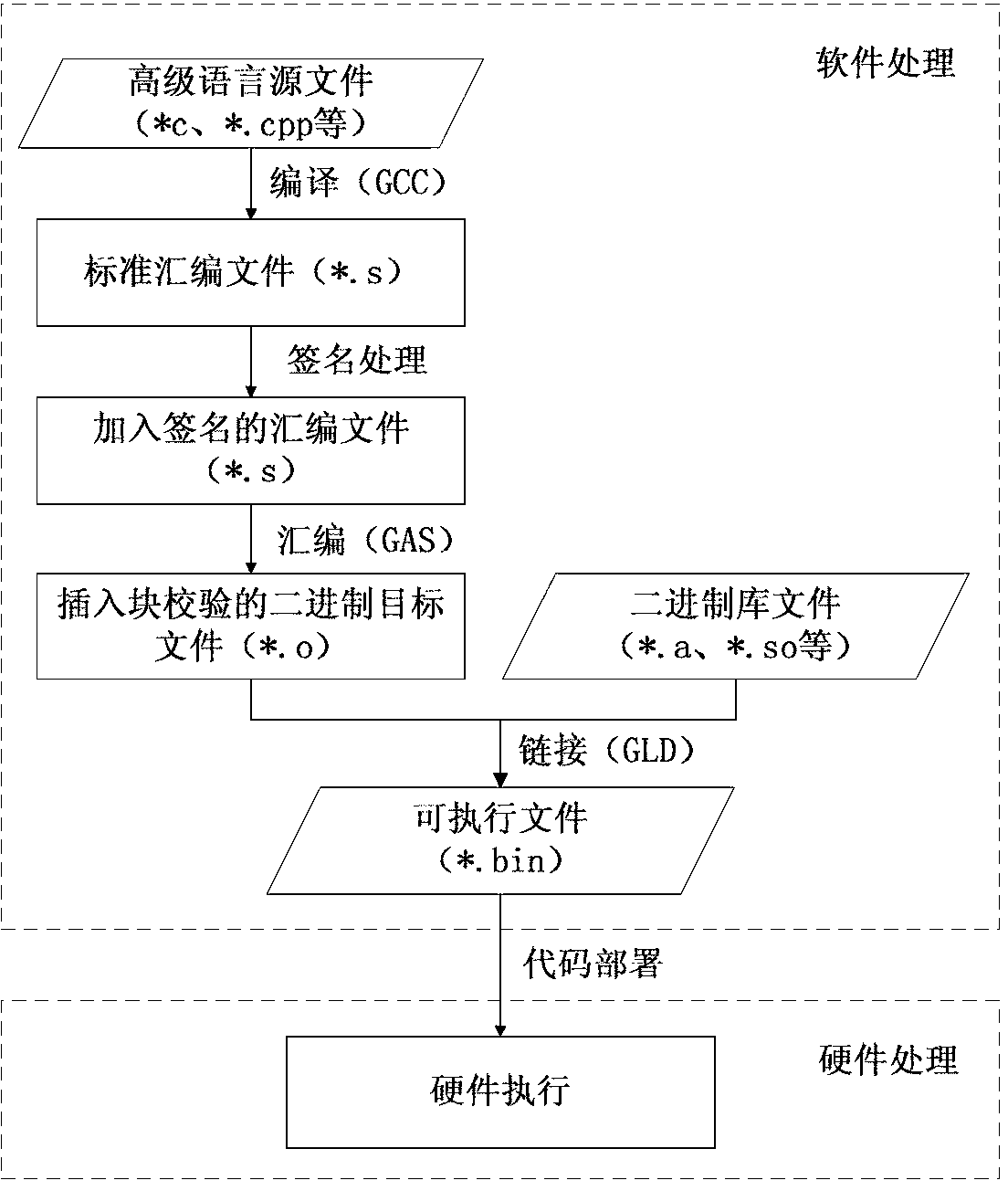
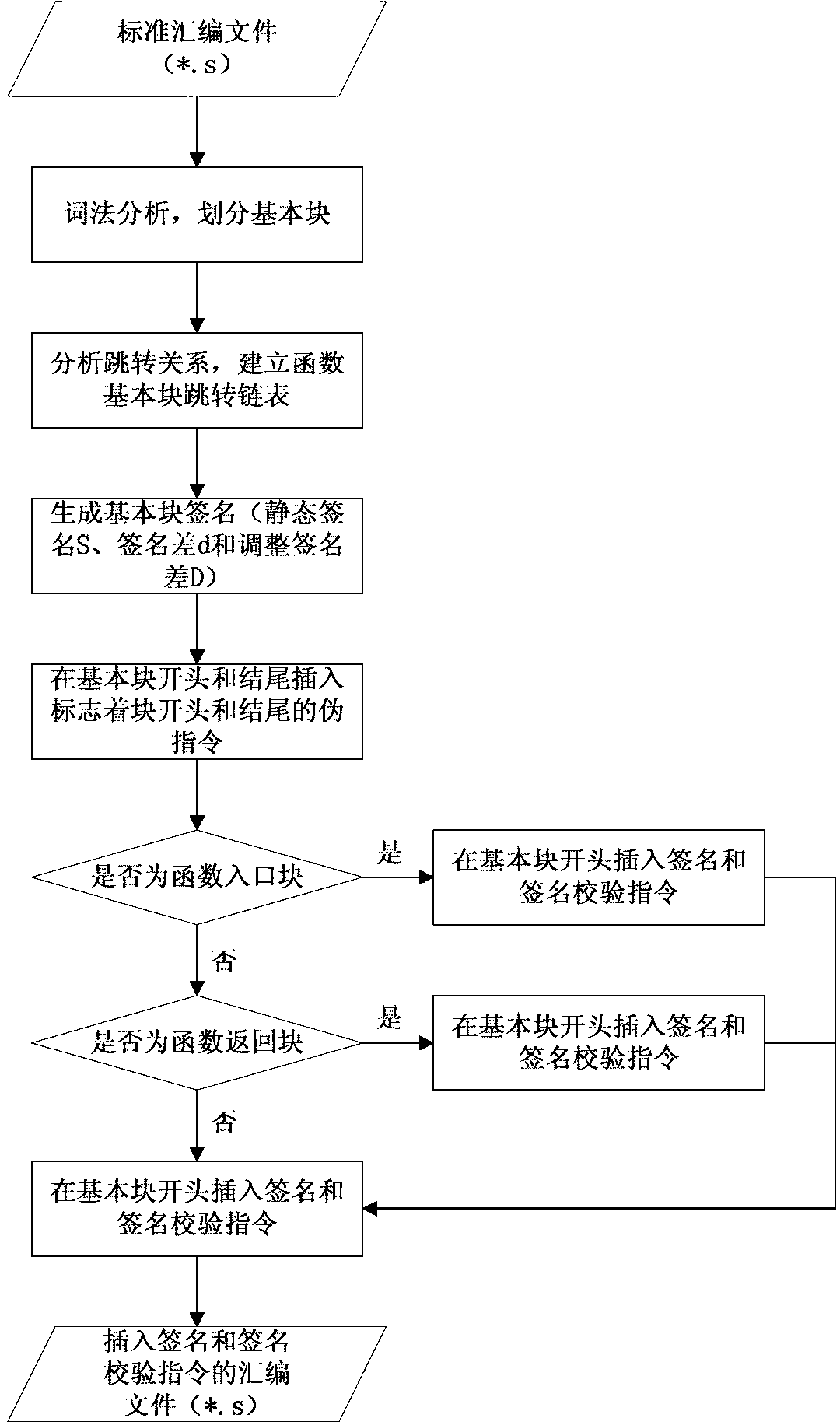
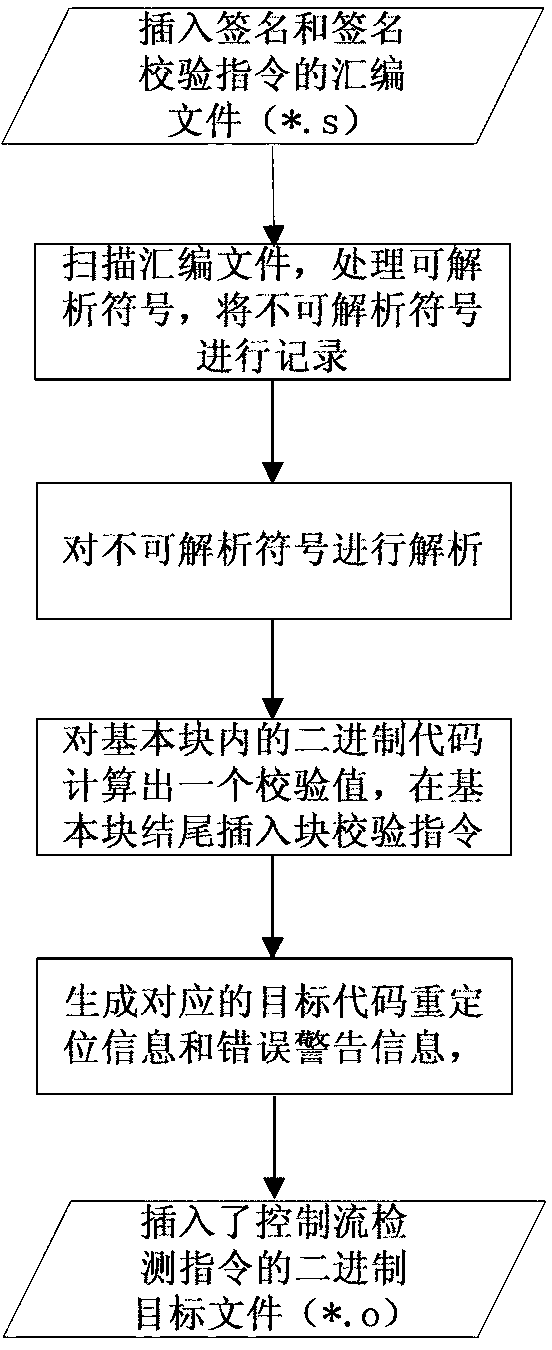
InactiveCN103345445AReduce overheadAvoid detecting blind spotsSoftware testing/debuggingControl flowLexical analysis
The invention relates to a security chip design method based on control flow detection and resistant to error injection attack. The security chip design method comprises a first step of compiling a standard assembling file which supports a security chip, a second step of dividing the standard assembling file into basic blocks by means of lexical analysis, a third step of generating basic block signature values and forming an assembling file with a control flow detection instruction, a fourth step of translating the assembling file into a target file, generating basic block checking values and inserting basic block checking instructions, and a fifth step of generating an executable file from the target file and a database file link and executing the executable file on hardware. The security chip design method based on control flow detection and resistant to error injection attack can effectively detect skip errors among the basic blocks and inside each basic block and non-skip errors of a command sequence, has the self checking function on the control flow detection instruction which is newly added, and is simple in implementation and low in redundancy code cost by the adoption of the mode of combination of software and hardware.
Owner:HUAZHONG UNIV OF SCI & TECH
Method and apparatus for encoding and decoding video
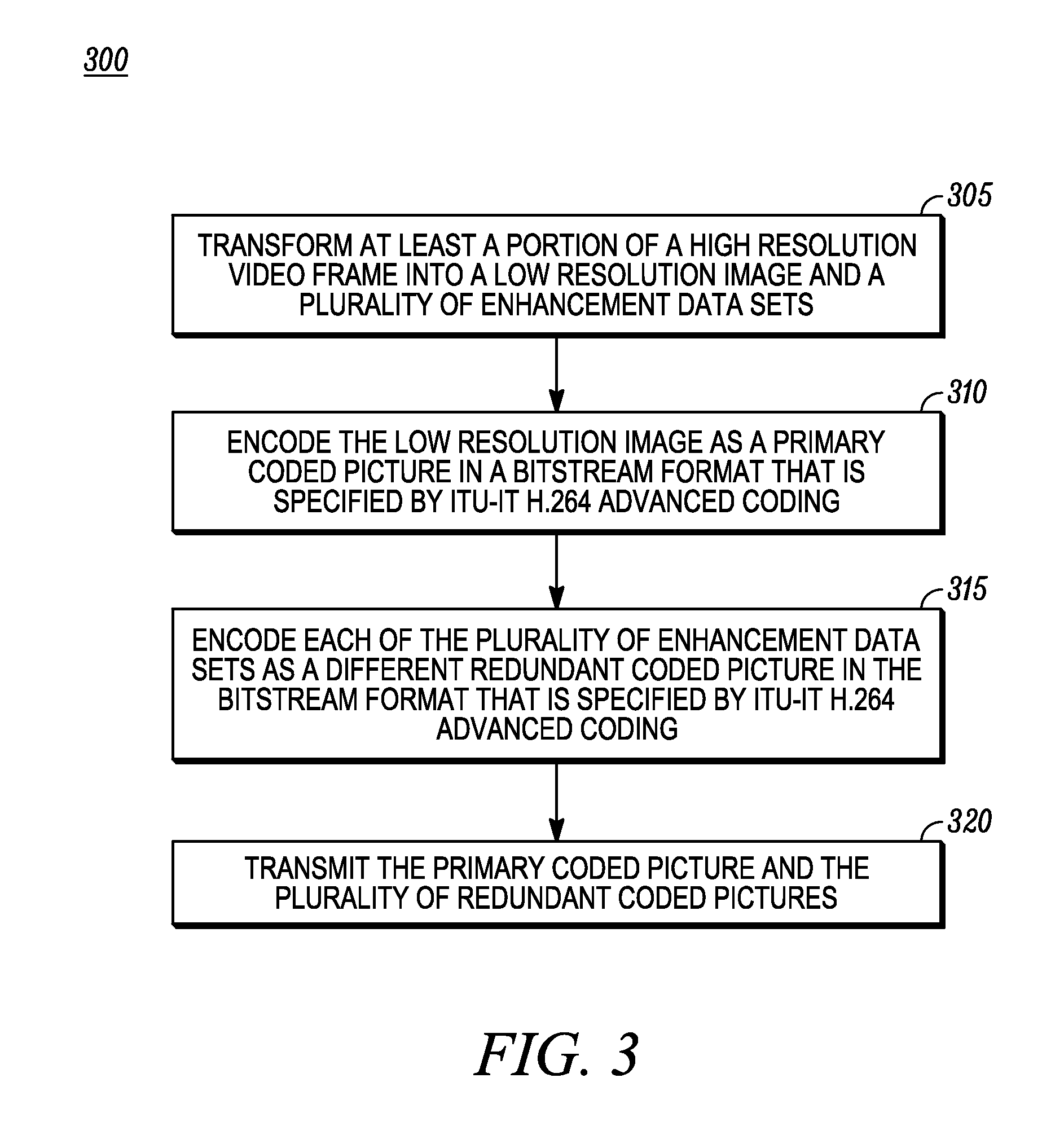
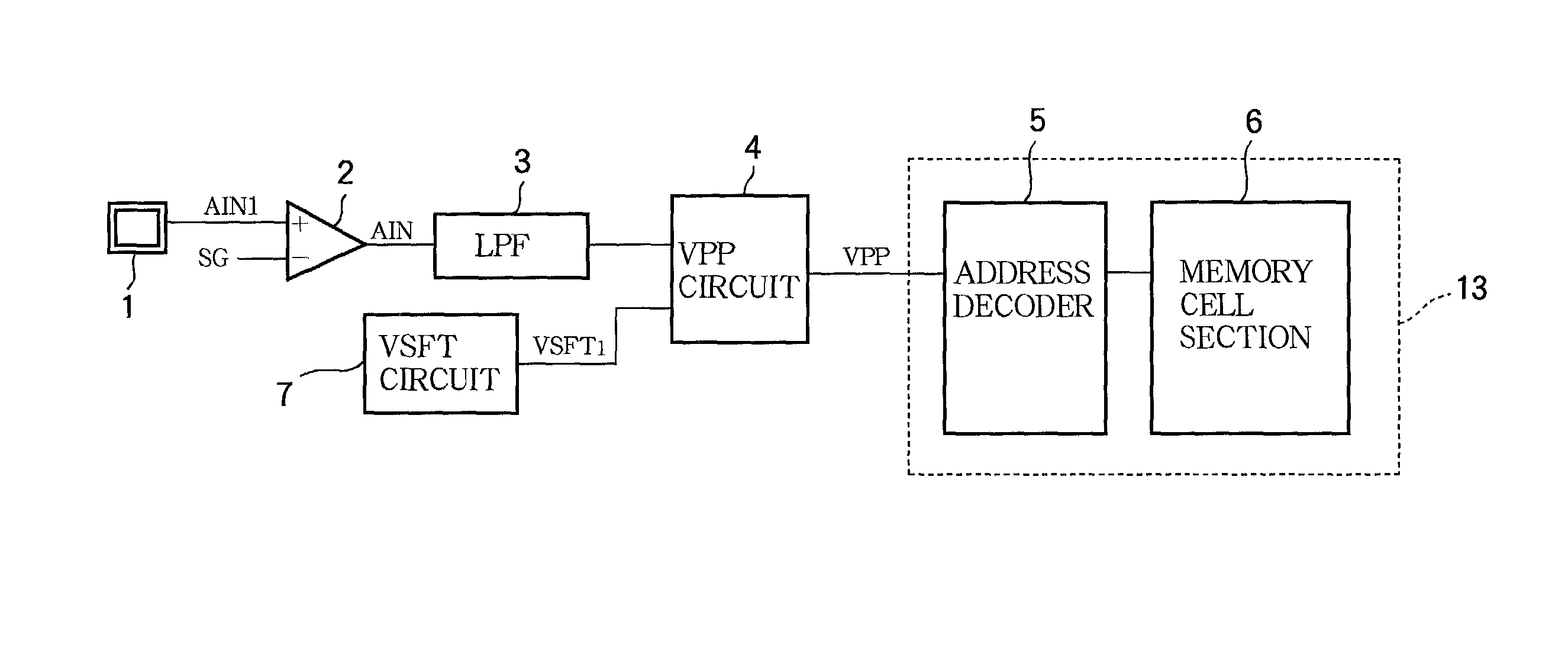
ActiveUS20090268805A1Color television with pulse code modulationColor television with bandwidth reductionData setImage resolution
A method and apparatus for encoding and decoding video performs transformation of at least a portion of a high-resolution video frame into a low resolution image and a plurality of enhancement data sets, encodes the low resolution image as a primary coded picture in a bitstream format and encodes each of the plurality of enhancement data sets as a different redundant coded picture in the bitstream format. For decoding, a decoded low resolution image and a plurality of decoded enhancement data sets are generated and an inverse transform is performed to construct a decoded high-resolution mage. The primary coded picture and a redundant coded picture may be formatted according to the ITU-T H.264 Advanced Coding specification. The transform may be a polyphase or a sub-band transform.
Owner:GOOGLE TECH HLDG LLC
Redundant memory circuit for analog semiconductor memory
A redundant memory circuit for use in an analog semiconductor memory has a cell array divided into sectors. To replace bad sectors, the cell array may include a pair of redundant sectors disposed at opposite ends of the cell array, or may have a centrally located redundant sector. Alternatively, the redundant memory circuit may have a sector selection circuit that selects the sectors and redundant sector in sequence from one end of the cell array to the other, or may have a word line selector located in the center of the cell array, or may have two cell arrays and a redundant sector selection circuit that enables a bad sector in one cell array to be replaced by a redundant sector in either of the two cell arrays. These arrangements improve the capability for redundancy replacement and the quality of the reproduced analog signal.
Owner:LAPIS SEMICON CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com