Detection method for software vulnerability
A detection method and technology for software defects, applied in the field of information security, can solve problems such as integrity affecting the effect of fuzzing, increasing the difficulty of writing fuzzer tools, etc., to achieve the effect of comprehensive detection results, practical detection, and guaranteed effectiveness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
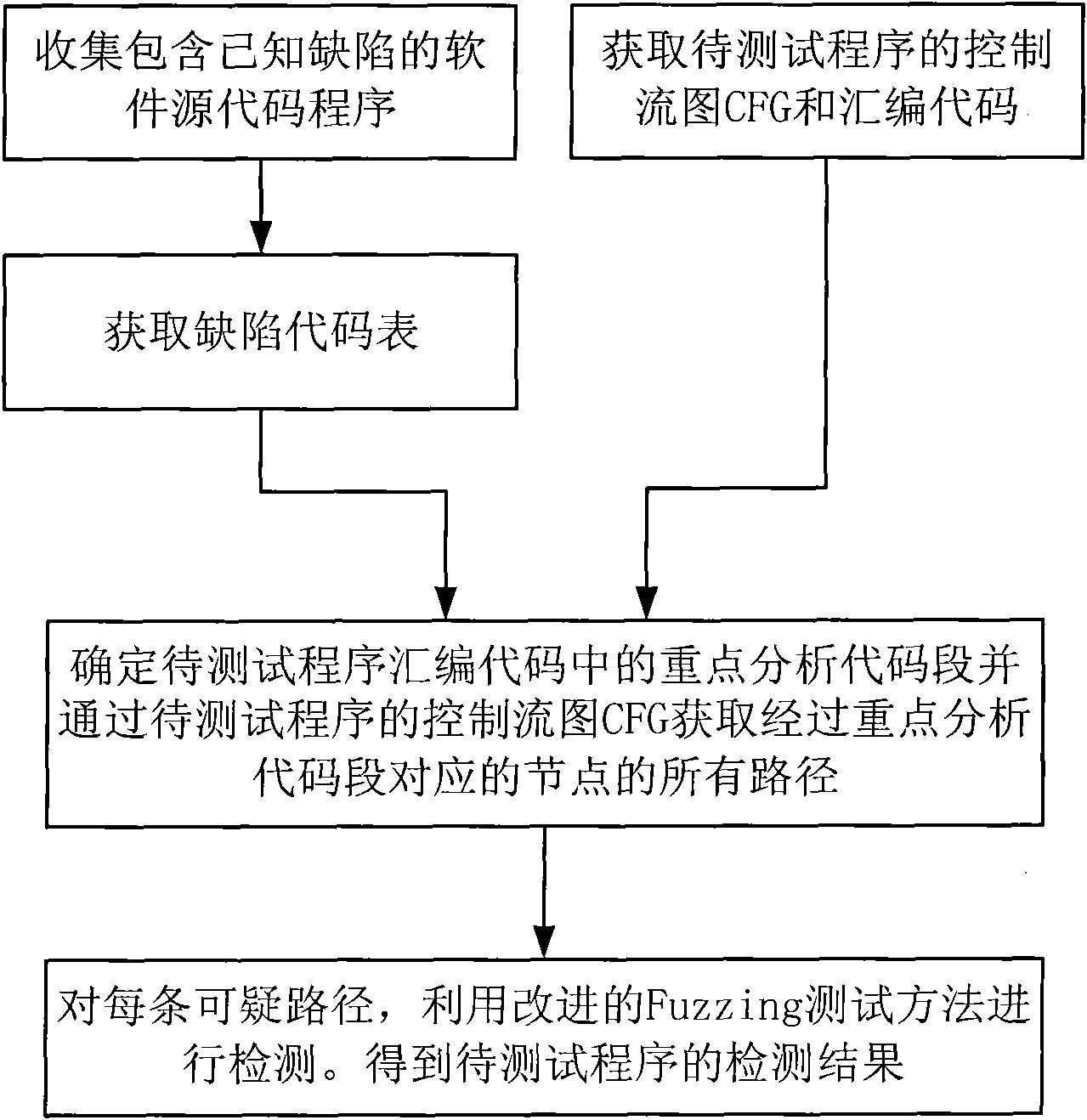
[0078] The technical solution of the present invention will be described in detail below in conjunction with the accompanying drawings and specific embodiments.
[0079] The present embodiment adopts the method of the present invention to test an executable program to be tested with a size of 172KB. The function of this executable program is to realize the verification of the password. If the verification result is correct, then output Access granted, if the verification result is wrong , then output Access denied.
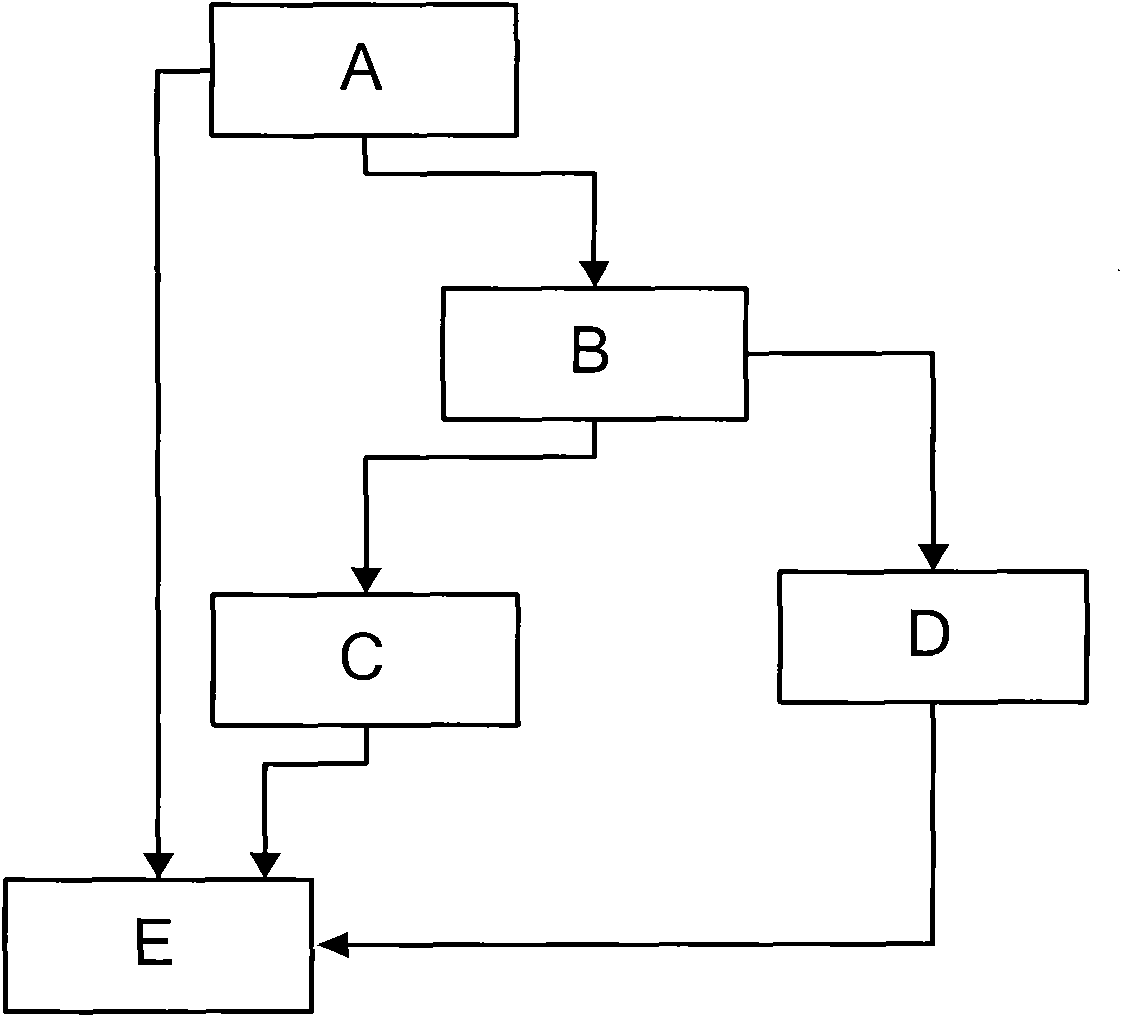
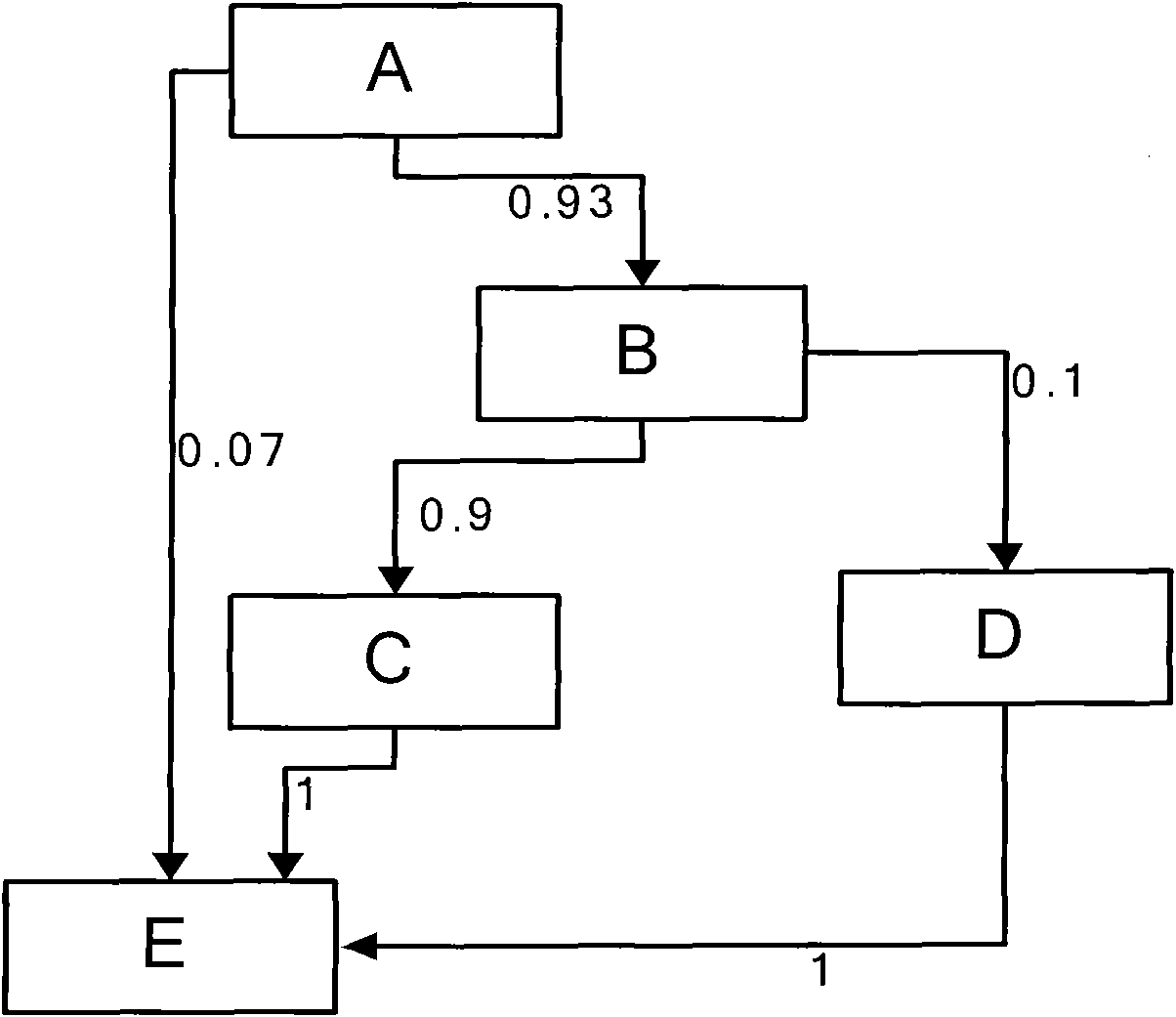
[0080] Its operation process is as figure 1 As shown, specifically:
[0081] Step 1. Collect software source code programs containing known defects.
[0082] A total of 32 software programs with known defects and their source codes were collected. These include buffer overflow, format string, integer overflow and other vulnerable programs and programs with known related defects.
[0083] Step 2. Obtain the defect code list.
[0084] Process the software progr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com