Instruction modification virtual platform execution method for kernel stack overflow defense
A virtual platform and instruction modification technology, which is applied in the field of computer security, can solve problems such as the proliferation of stack overflow attacks, single defense technology, and program operation failure, and achieve the effects of reducing reuse, saving memory resources, and improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] The present invention will be further described below with examples in conjunction with the accompanying drawings.
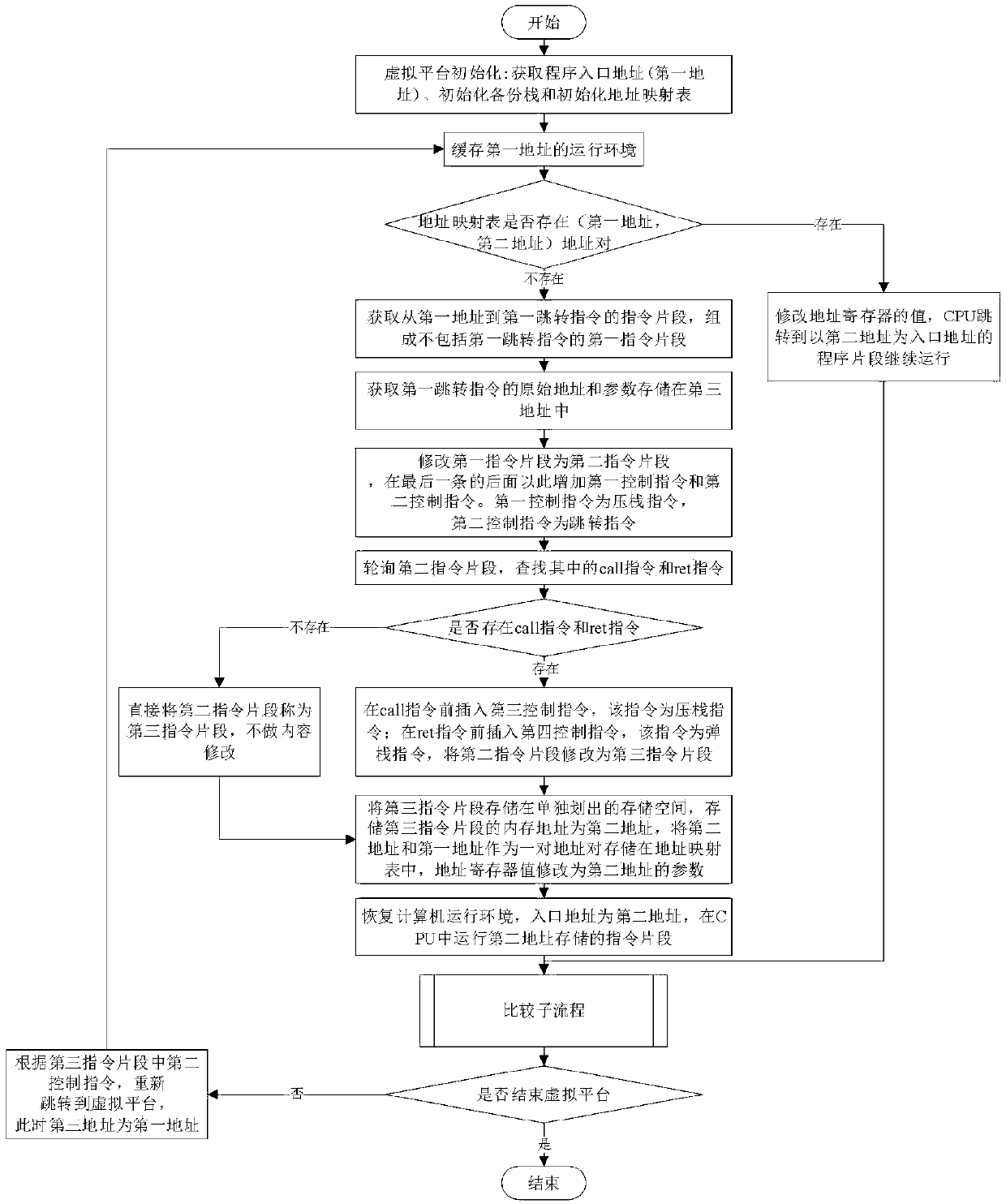
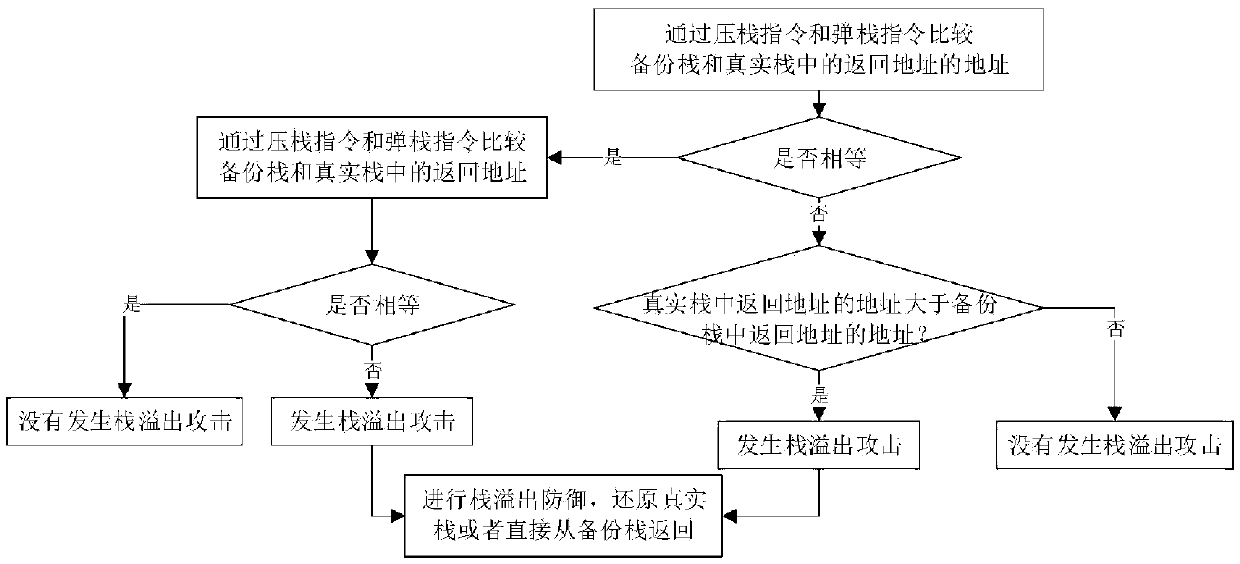
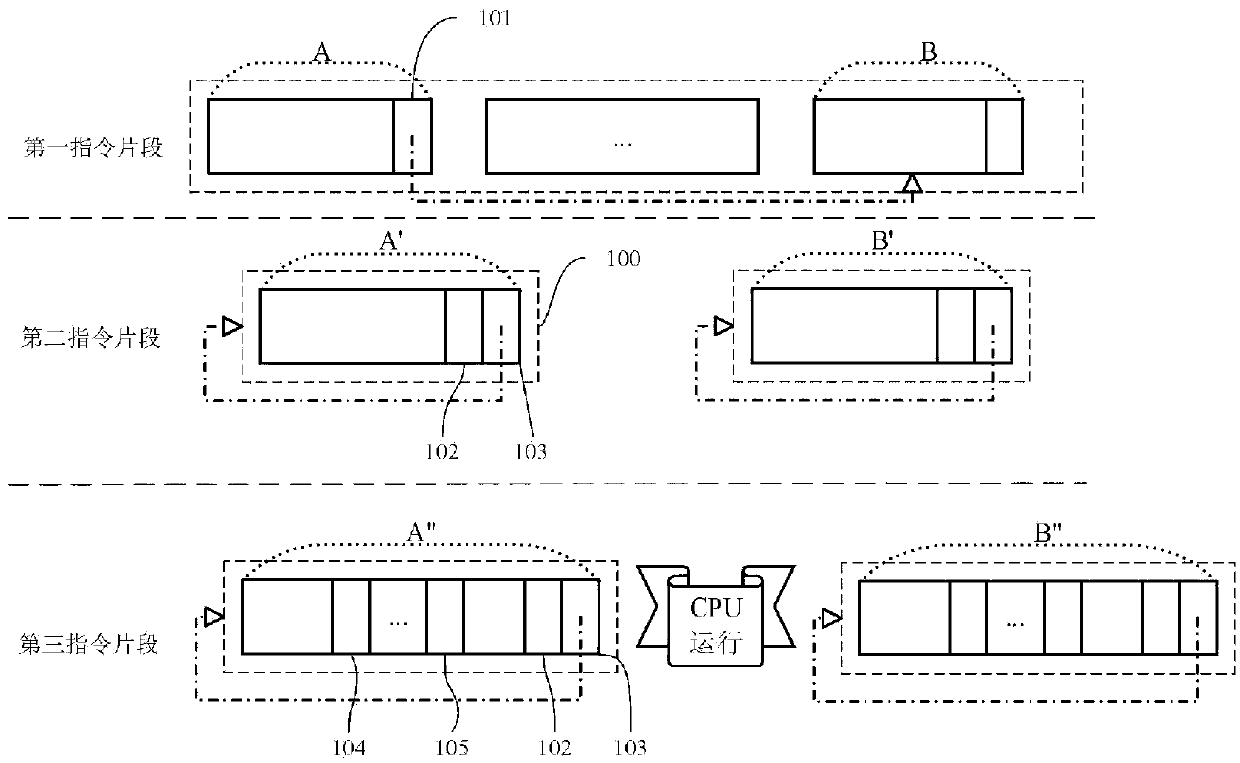
[0036] figure 1 with figure 2 It is a flowchart and a comparison sub-flowchart of an instruction modification virtual platform execution method oriented to kernel stack overflow defense provided by an embodiment of the present invention. The present invention is applied to the kernel stack overflow detection in Windows system, comprises the following steps:
[0037]Step 1. The virtual platform is loaded when the computer terminal is started. The initialization of the virtual platform includes obtaining the program entry address, initializing the backup stack and initializing the address mapping table. The program entry address is the first address, and the address mapping table is the first address and the second address stored in the form of address pairs in the storage space. The backup stack is to back up the push instruction in the original progra...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com