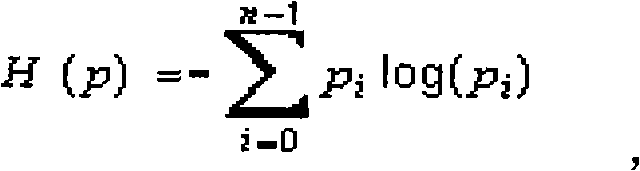Patents
Literature
49 results about "Shellcode" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In hacking, a shellcode is a small piece of code used as the payload in the exploitation of a software vulnerability. It is called "shellcode" because it typically starts a command shell from which the attacker can control the compromised machine, but any piece of code that performs a similar task can be called shellcode. Because the function of a payload is not limited to merely spawning a shell, some have suggested that the name shellcode is insufficient. However, attempts at replacing the term have not gained wide acceptance. Shellcode is commonly written in machine code.
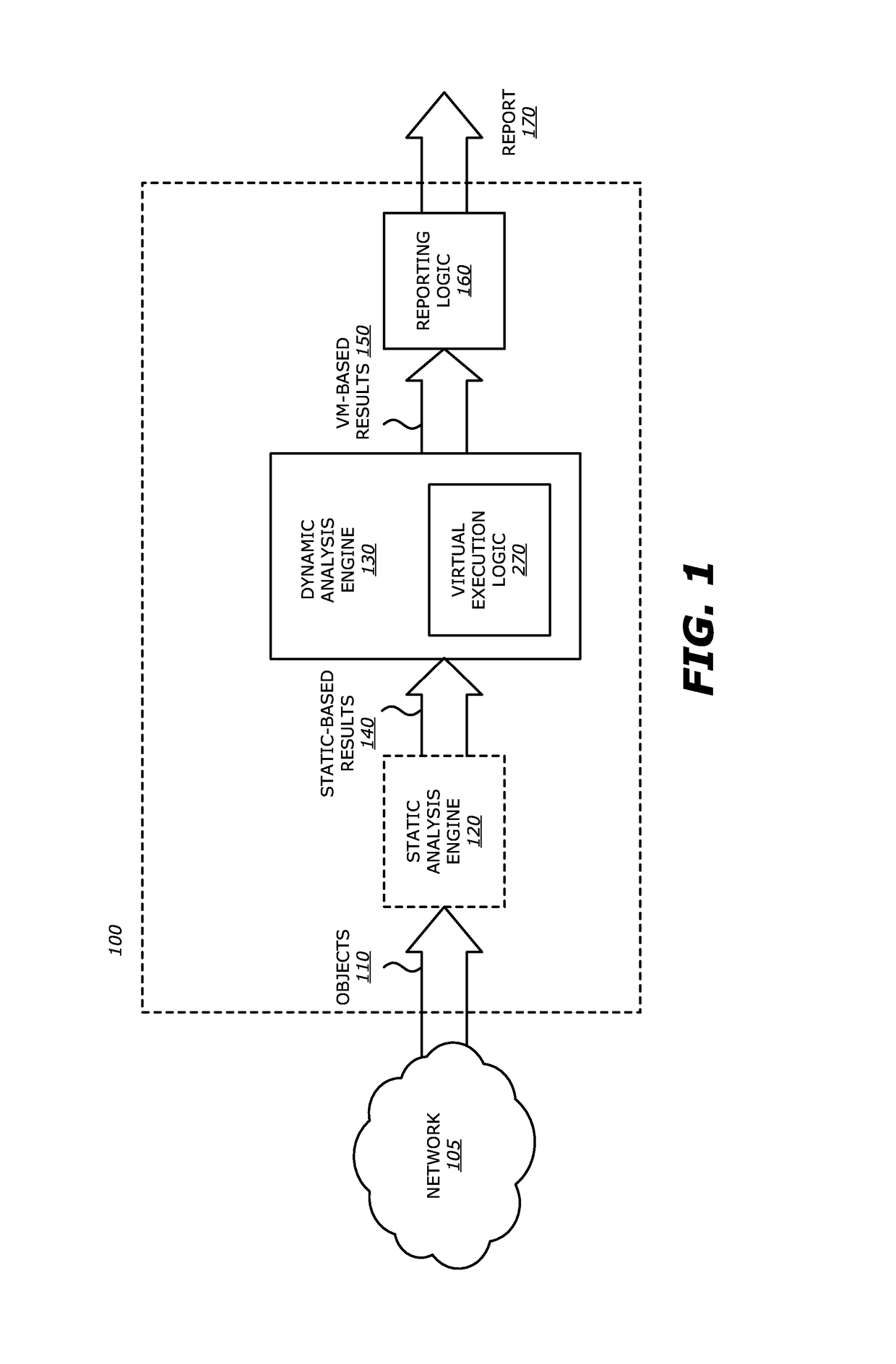
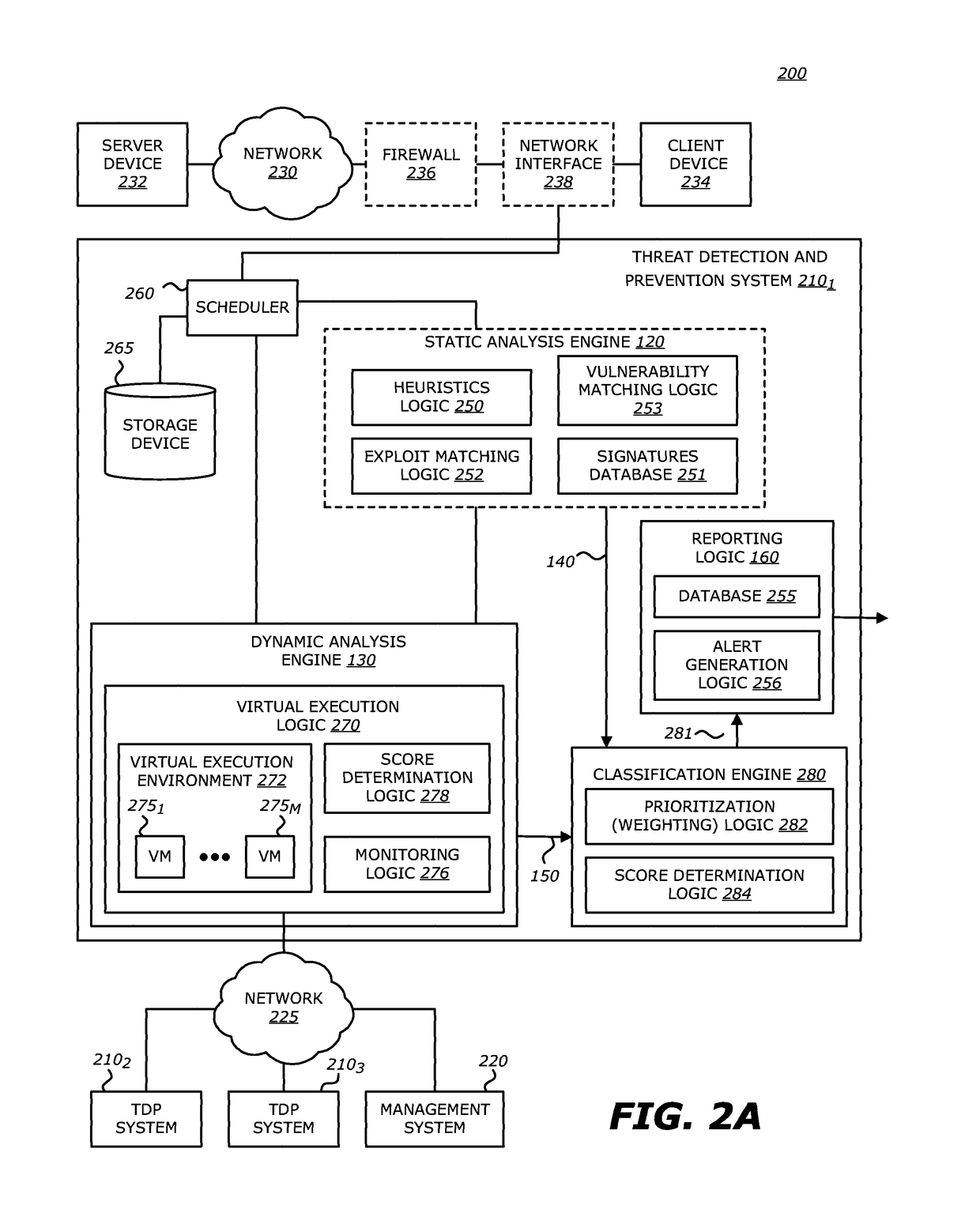
Computer exploit detection using heap spray pattern matching
ActiveUS9438623B1Analogue secracy/subscription systemsPlatform integrity maintainancePattern matchingTheoretical computer science
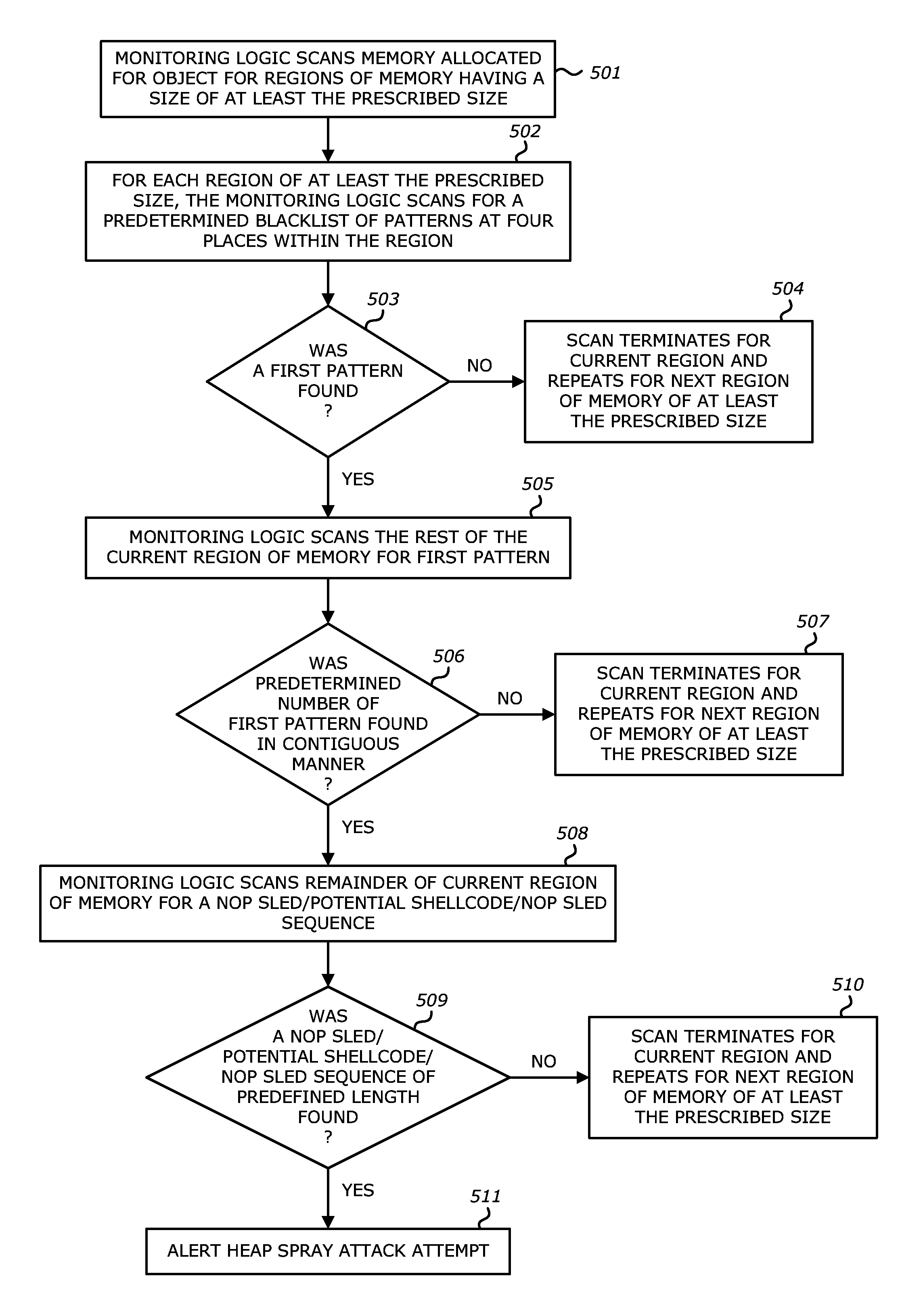
According to one embodiment, a threat detection system is integrated with at least a dynamic analysis engine. The dynamic analysis engine is configured to automatically to detect potential shellcode at a first storage location within a region of memory allocated for an application, conduct a first search at one or more storage locations prior to the first storage location within the region of allocated memory for at least one or more patterns, conduct a second search at one or more storage locations subsequent to the first storage location within the region of allocated memory for at least one or more patterns, detect a first pattern at one or more storage locations prior to the first storage location within the region of allocated memory, and detect a second pattern at one or more storage locations subsequent to the first storage location with the region of allocated memory, wherein at least one of the first pattern or the second pattern is absent from a predefined list of patterns.
Owner:FIREEYE SECURITY HLDG US LLC
Shellcode detection
According to one embodiment, a threat detection system is integrated with at least a dynamic analysis engine. The dynamic analysis engine is configured to automatically determine whether one or more objects included in received network traffic contains a heap spray attack. Upon detection of a potential heap spray attack, the dynamic analysis engine may copy potential shellcode within an object included in the received network traffic, insert the copy of the potential shellcode into a second region of allocated memory and analyze the execution of the potential shellcode to determine whether characteristics associated with an exploit are present.
Owner:FIREEYE SECURITY HLDG US LLC
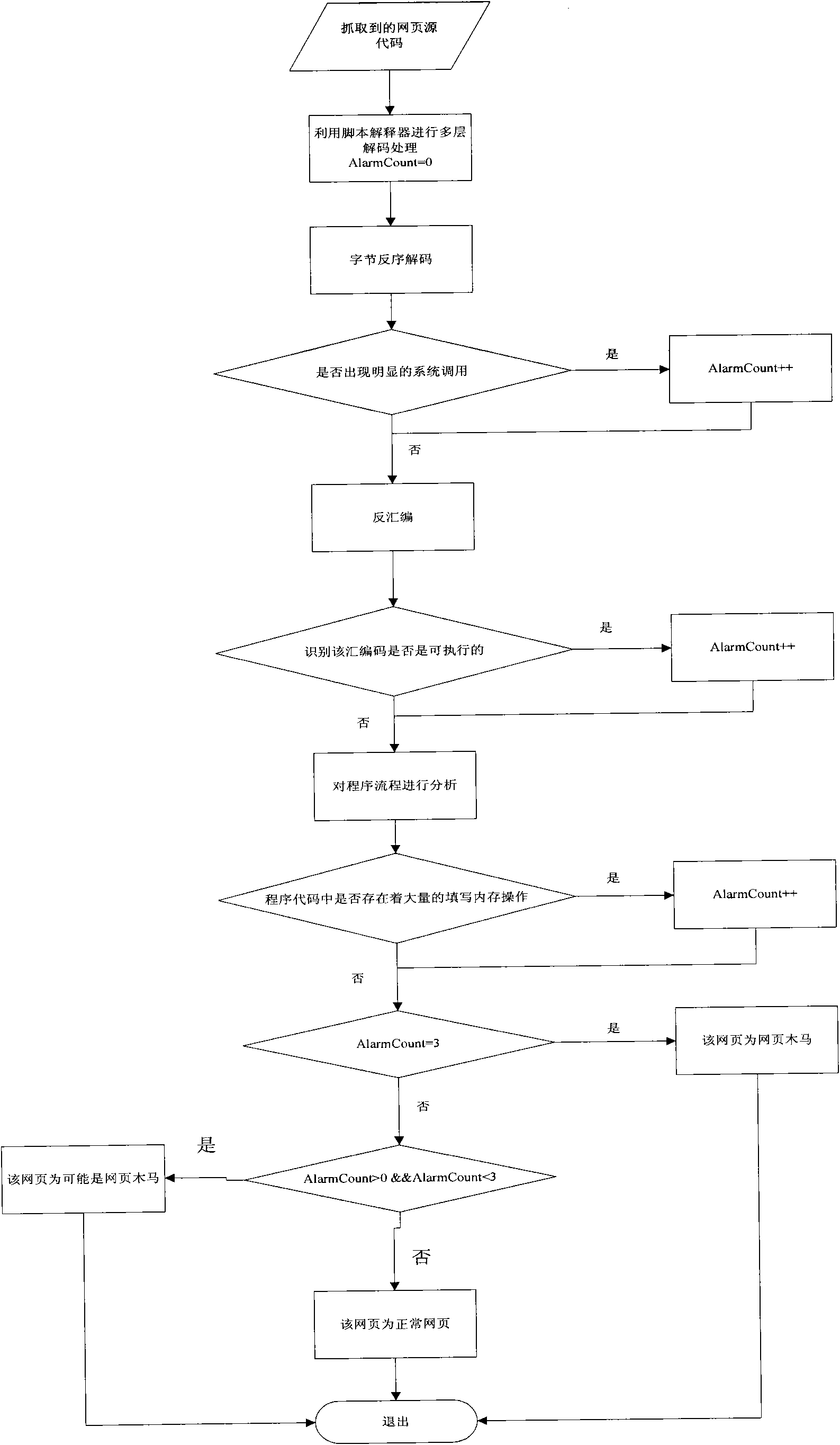
Method for detecting web page Trojan horse based on program execution characteristics
InactiveCN101673326AReduce missed detection rateReduce false detection ratePlatform integrity maintainanceSpecial data processing applicationsWeb siteBuffer overflow
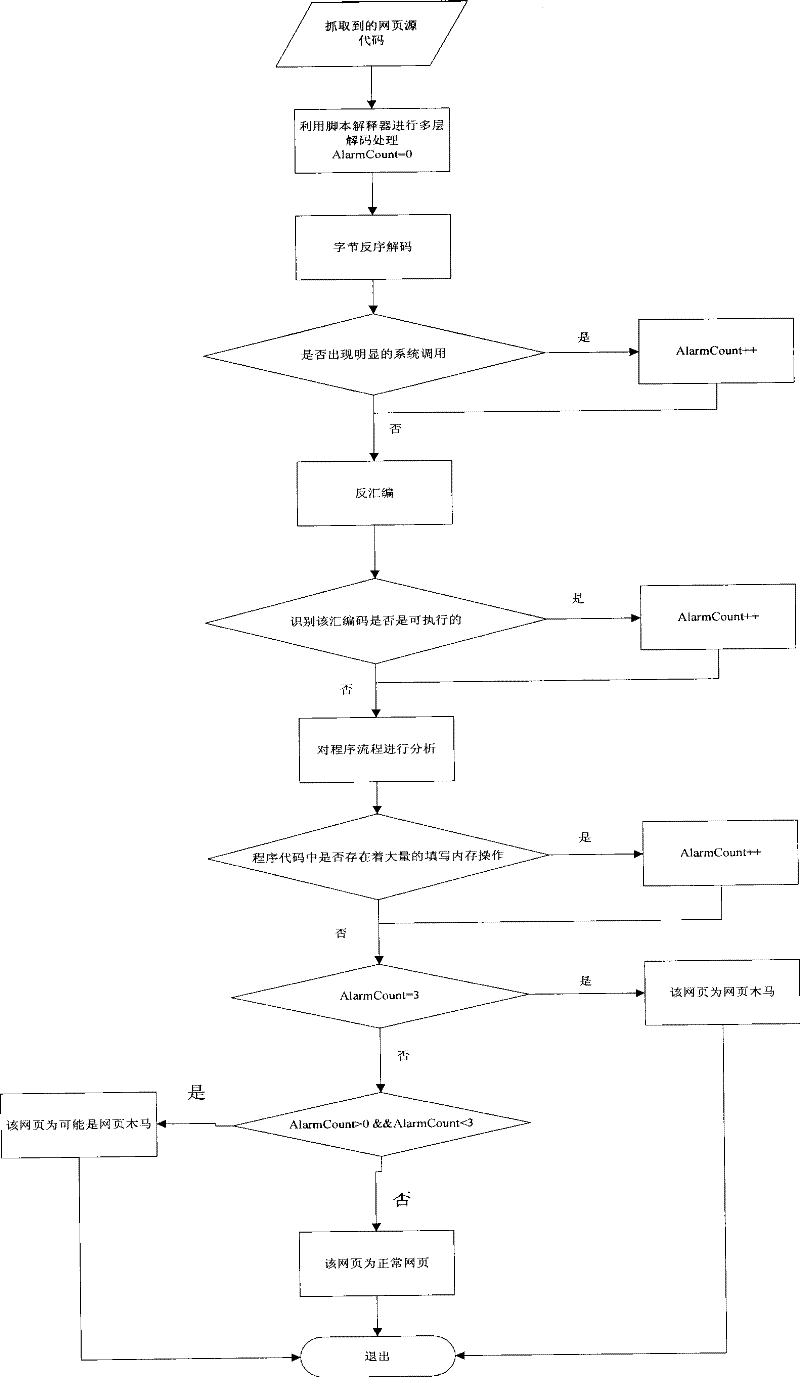
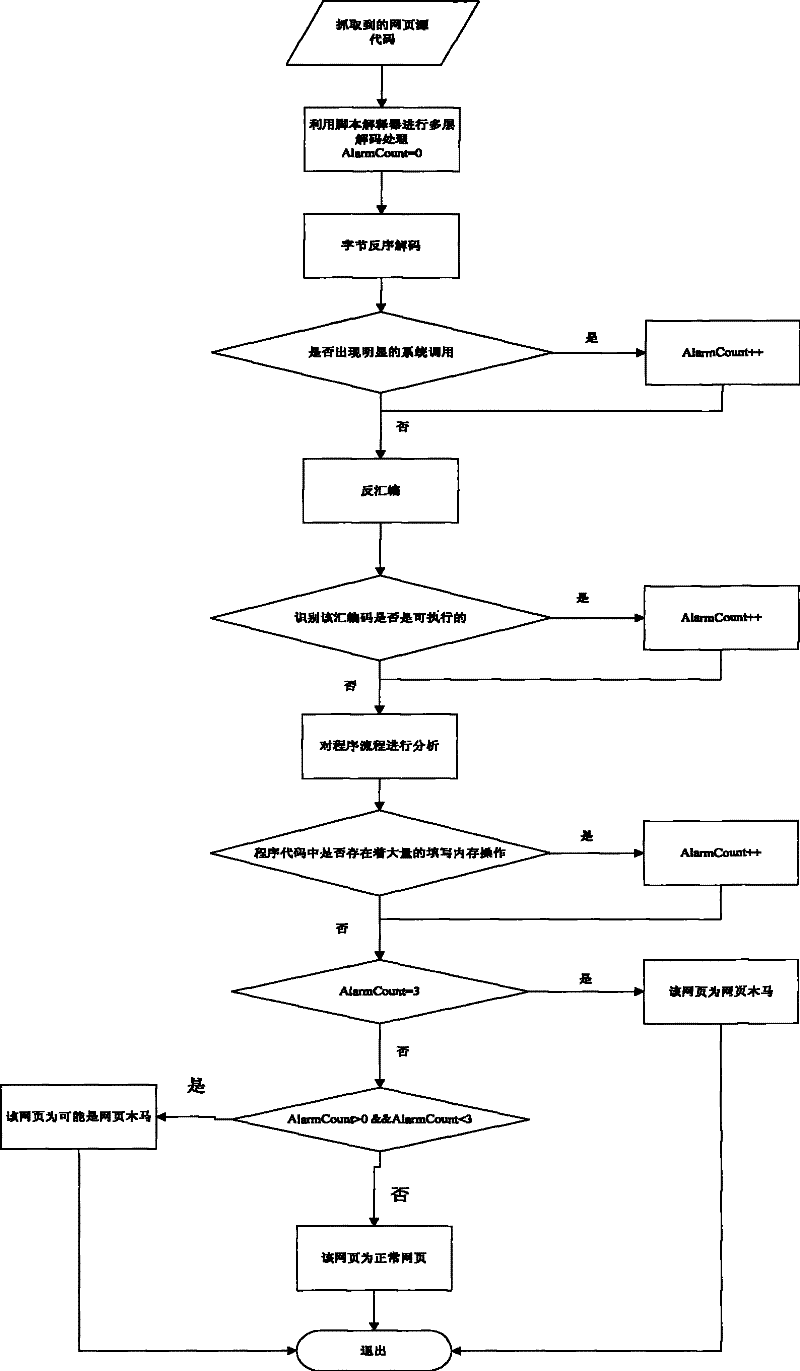
The invention belongs to the field of computer security, and relates to a method for detecting web page Trojan horse based on program execution characteristics, which comprises the following steps: using web crawlers to capture source codes of a web page; then obtaining a recognizable script program through multilevel decoding; carrying out disassembling processing on the script program to obtainassembled source codes while reserving the script program; then, judging whether a large number of filled invalid instructions, calling system level functions and obvious URL links exist in the sourcecodes; and finally detecting whether the Trojan horse exists in the web page through the assembled source codes in a deep level. Because most of the prior web pages with the Trojan horse are embeddedwith ShellCode, to execute the ShellCode in the web pages in a local computer, system vulnerability is needed to realize buffer overflow and enable the program to skip onto the ShellCode code segment. Thus, only by analyzing the condition of executing the ShellCode, and analyzing the source codes according to the execution characteristics, whether the web page to be detected is the web page Trojan horse can be quickly detected.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
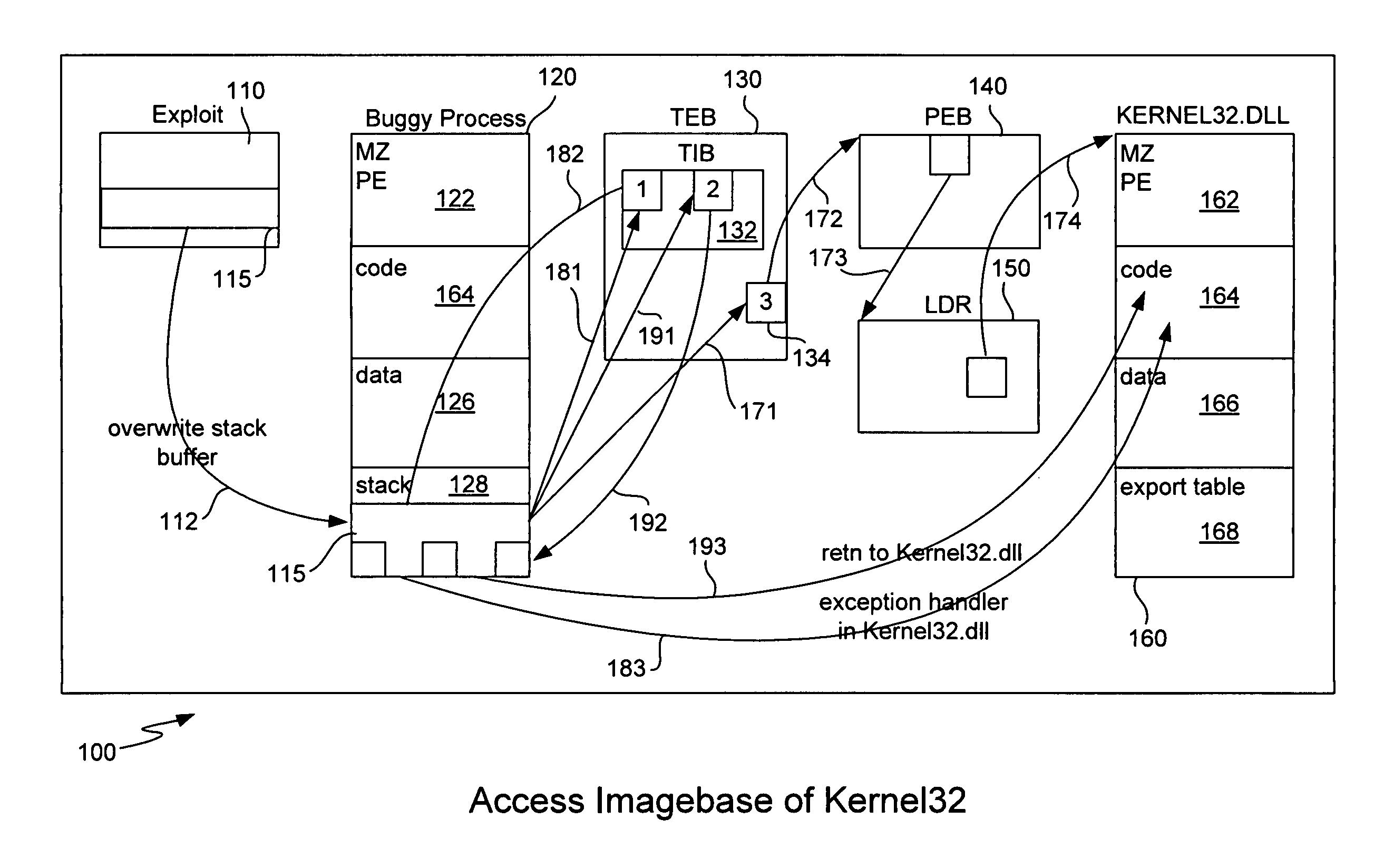
Generic shellcode detection
ActiveUS8307432B1Quick analysisImprove the detection rateMemory loss protectionError detection/correctionBuffer overflowShellcode
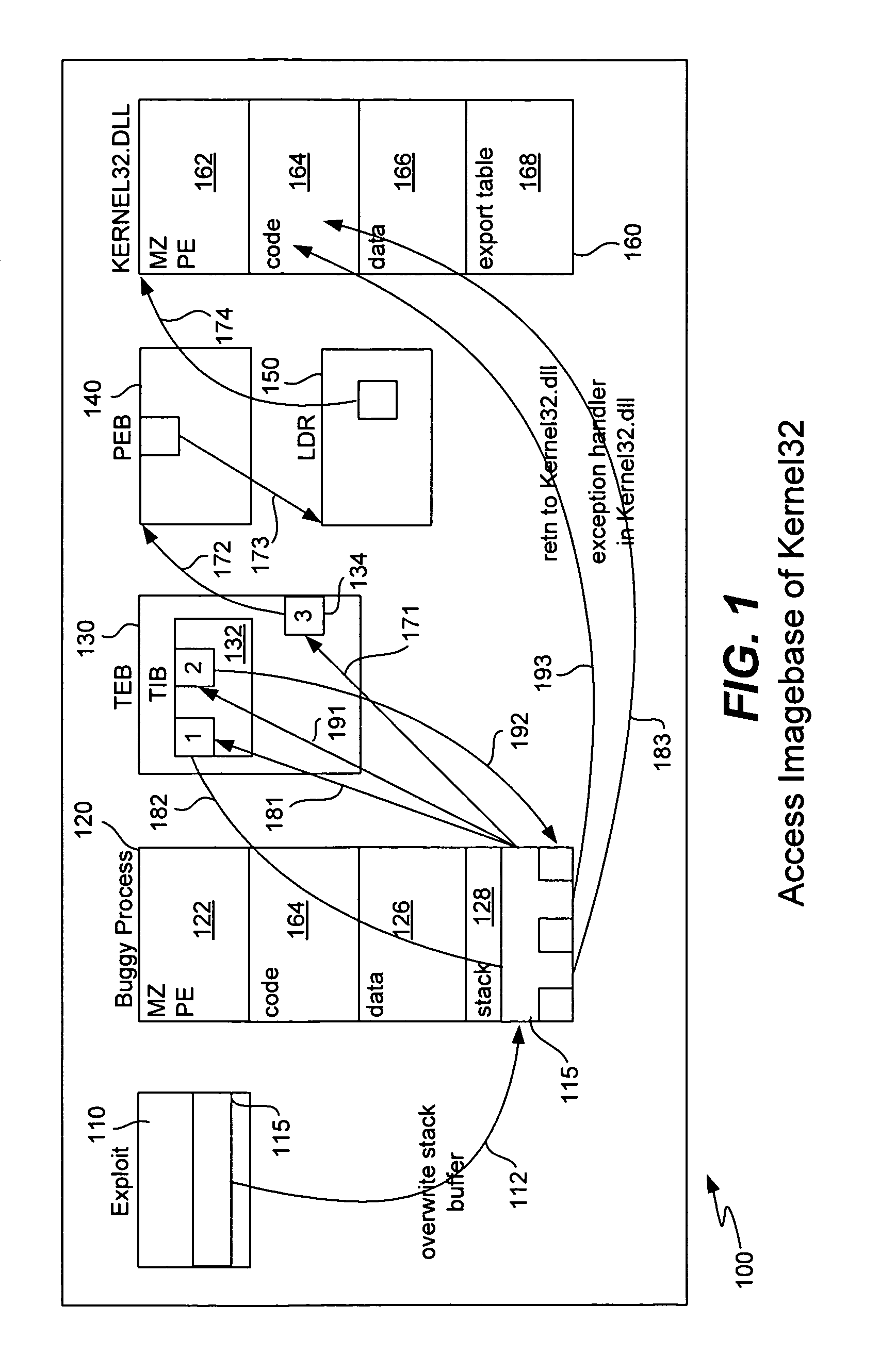
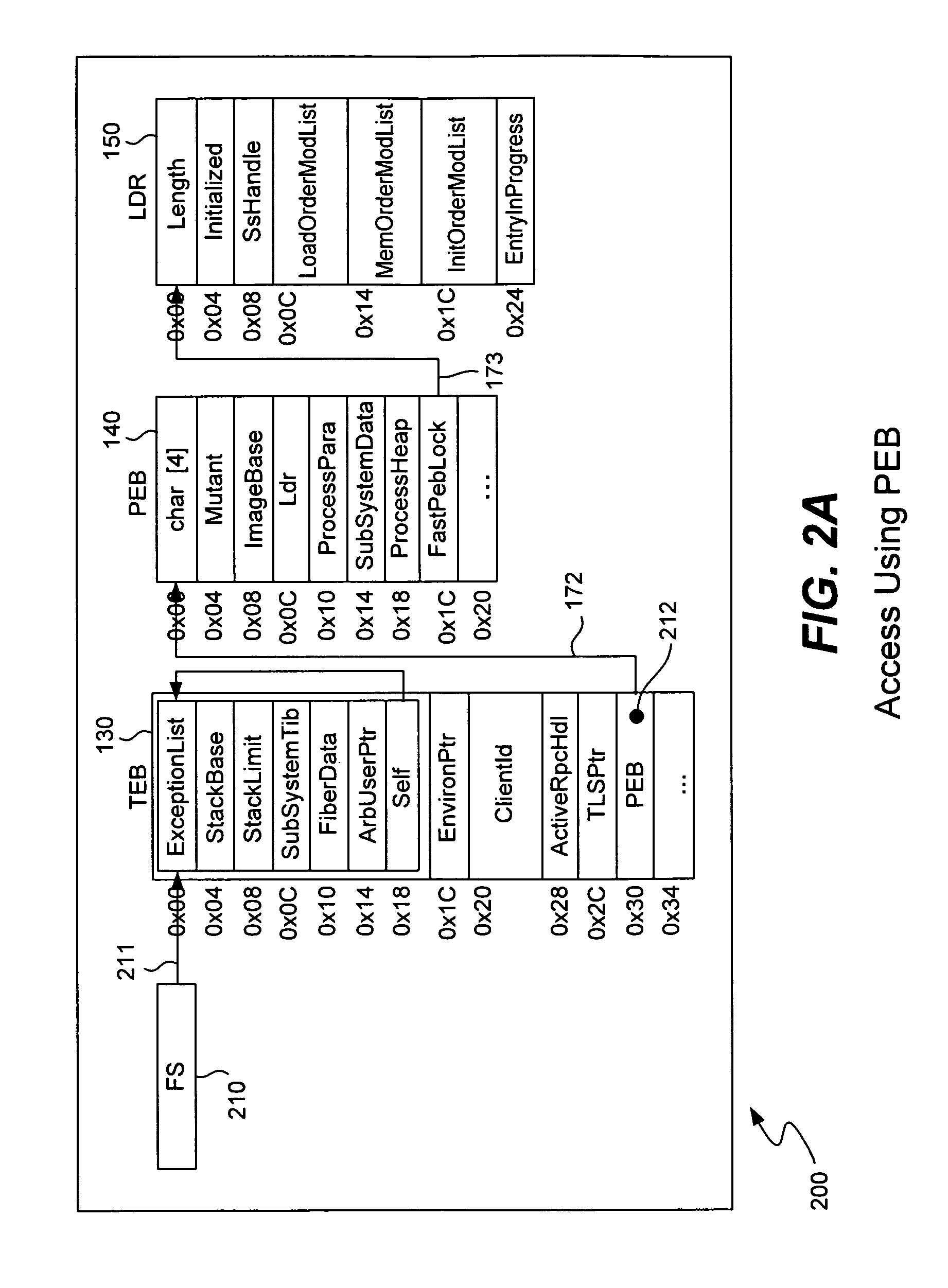
Detecting buffer-overflow exploits scans generically for shellcode without using virus signatures and maintains close to a zero false-positive rate. Shellcode is detected generically without determining specifically which buffer-overflow exploit is being used. Protection is offered against unknown buffer-overflow exploits. A file is scanned to determine if a vulnerable buffer in that file includes suspect code that has characteristics of shellcode. Next, it is determined if the suspect code contains a routine to find the imagebase of Kernel32.dll using any of the techniques of PEB, TOS or SEH (process environment block, top of stack or structured exception handling). It is next determined if the suspect code contains a routine to search for APIs in the export table of kernel32.dll. Techniques for analyzing the suspect code include static analysis and executing the code in an emulator. A high sensitivity setting determines that shellcode is present when any of the techniques of PEB, TOS or SEH are found.
Owner:TREND MICRO INC
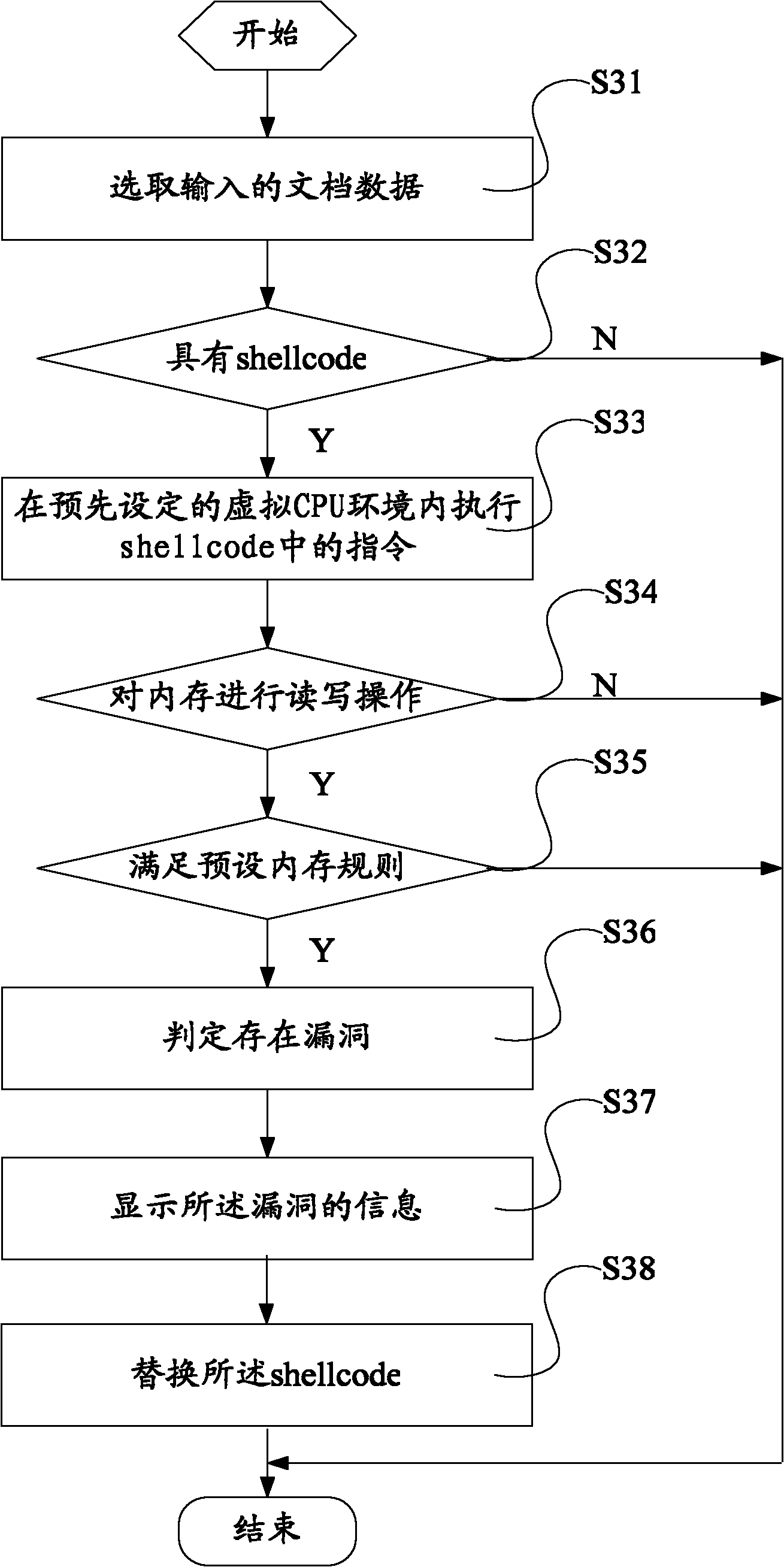
Leak detection method and device
ActiveCN101964036AImprove completenessImprove detection accuracyPlatform integrity maintainanceParallel computingShellcode
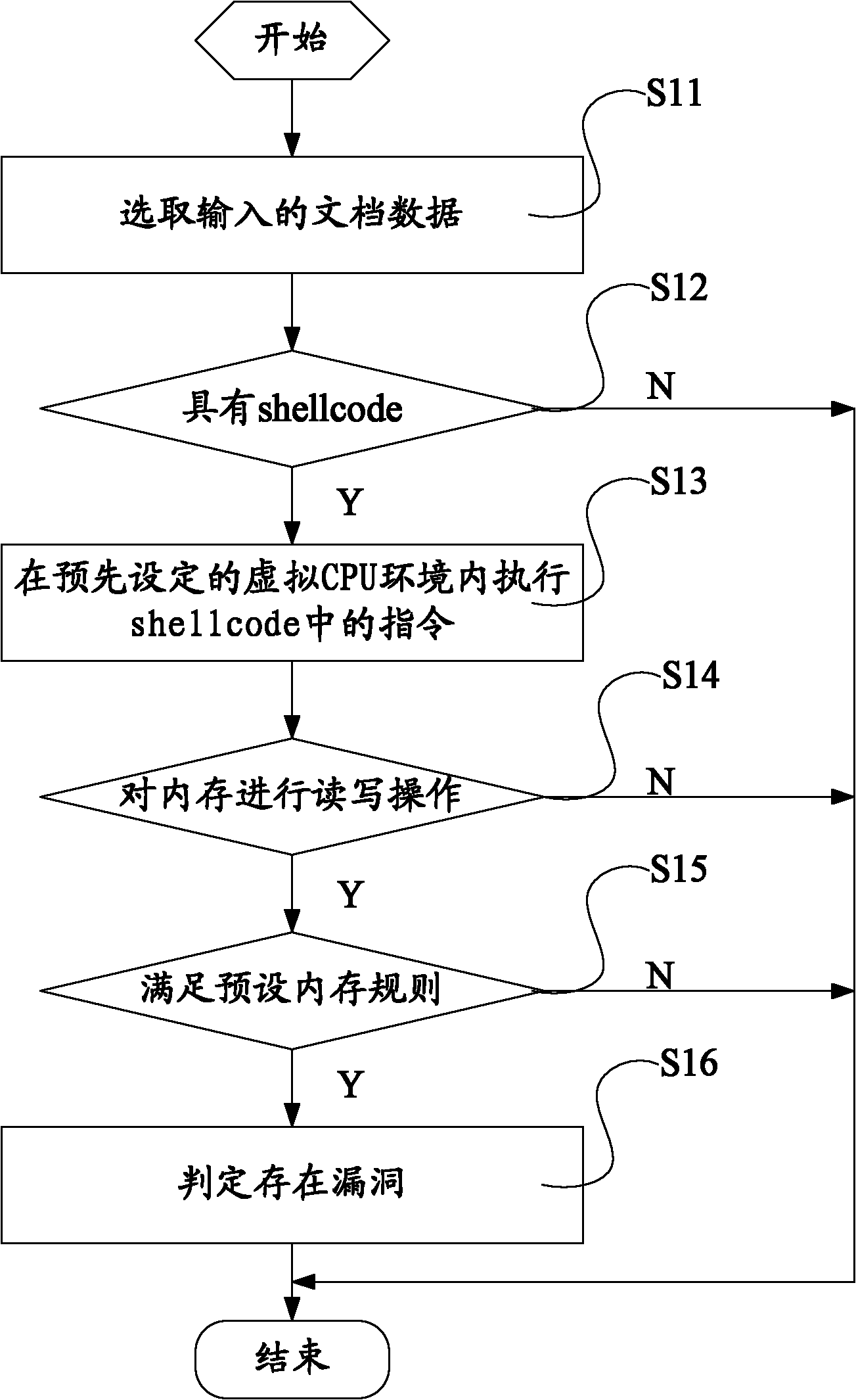
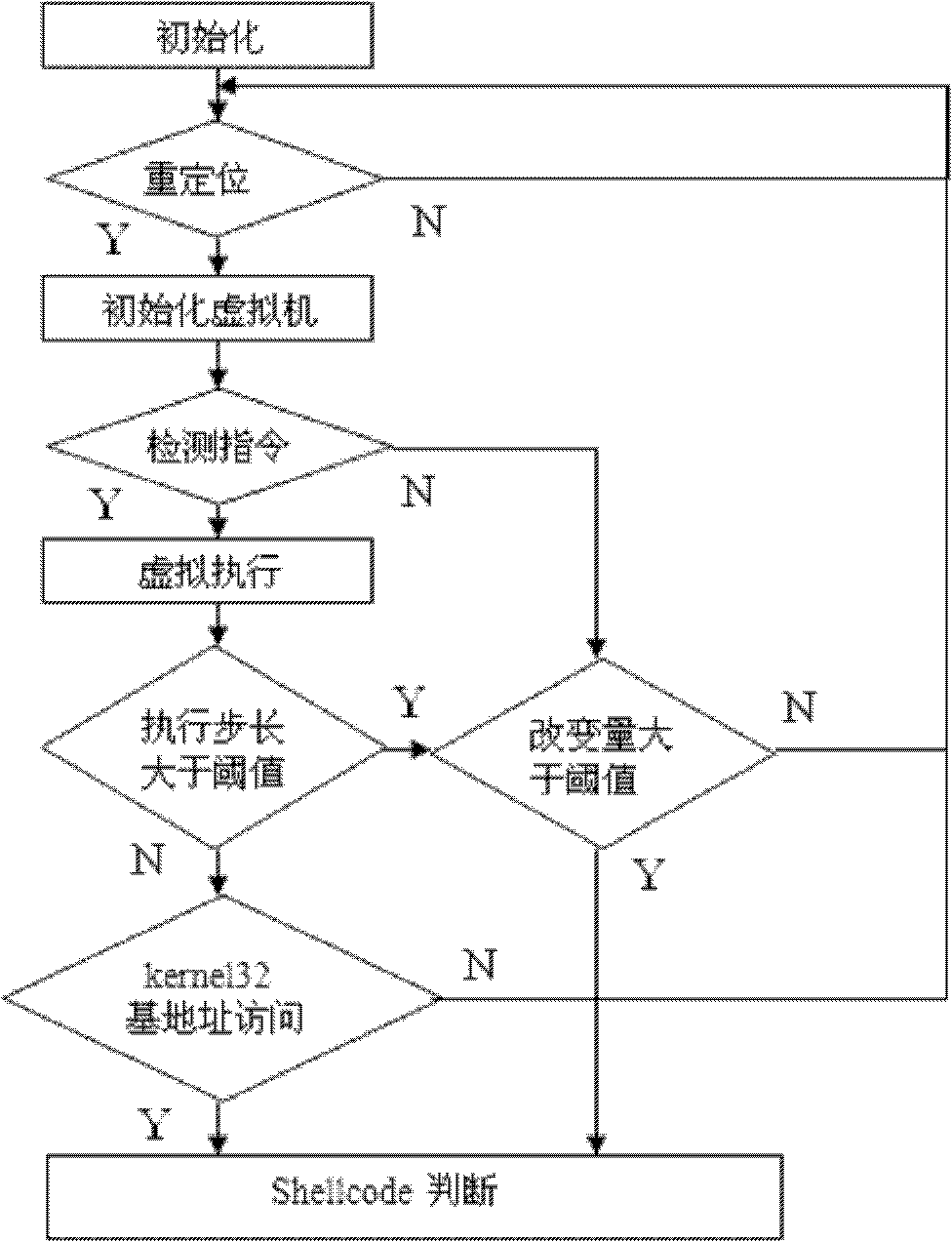
The invention discloses lead detection method and device. The method comprises the steps of: selecting input file data; detecting whether the file data has a shellcode or not; when the data has the shellcode, executing a command in the shellcode in a virtual CPU environment; when a memory is subjected to read and write operation in a process of executing the command in the shellcode, judging whether the read memory meets a preset memory rule or not; and when the read memory meets the memory rule, judging that a leak exists. Through adopting the method of detecting whether the received data has the shellcode using special leak under the virtual environment, and simulating the detected shellcode to judge whether the memory operation matched with the preset memory rule exists in the operation process or not so as to judge whether the leak exists, the integrity of the leak detection is improved, the detection accuracy is enhanced and the application range is further enlarged.
Owner:深圳市安盾椒图科技有限公司
Probabilistic shellcode detection
ActiveUS20100031359A1Memory loss protectionDigital data processing detailsParallel computingShellcode
Various embodiments include a method of detecting shell code in an arbitrary file comprising determining where one or more candidate areas exist within an arbitrary file, searching at least one nearby area surrounding each of the one or more candidate areas within the arbitrary file for an instruction candidate, and calculating for any such instruction candidate a statistical probability based on a disassembly of instructions starting at a found offset for the instruction candidate that the disassembled instructions are shellcode.
Owner:MCAFEE LLC
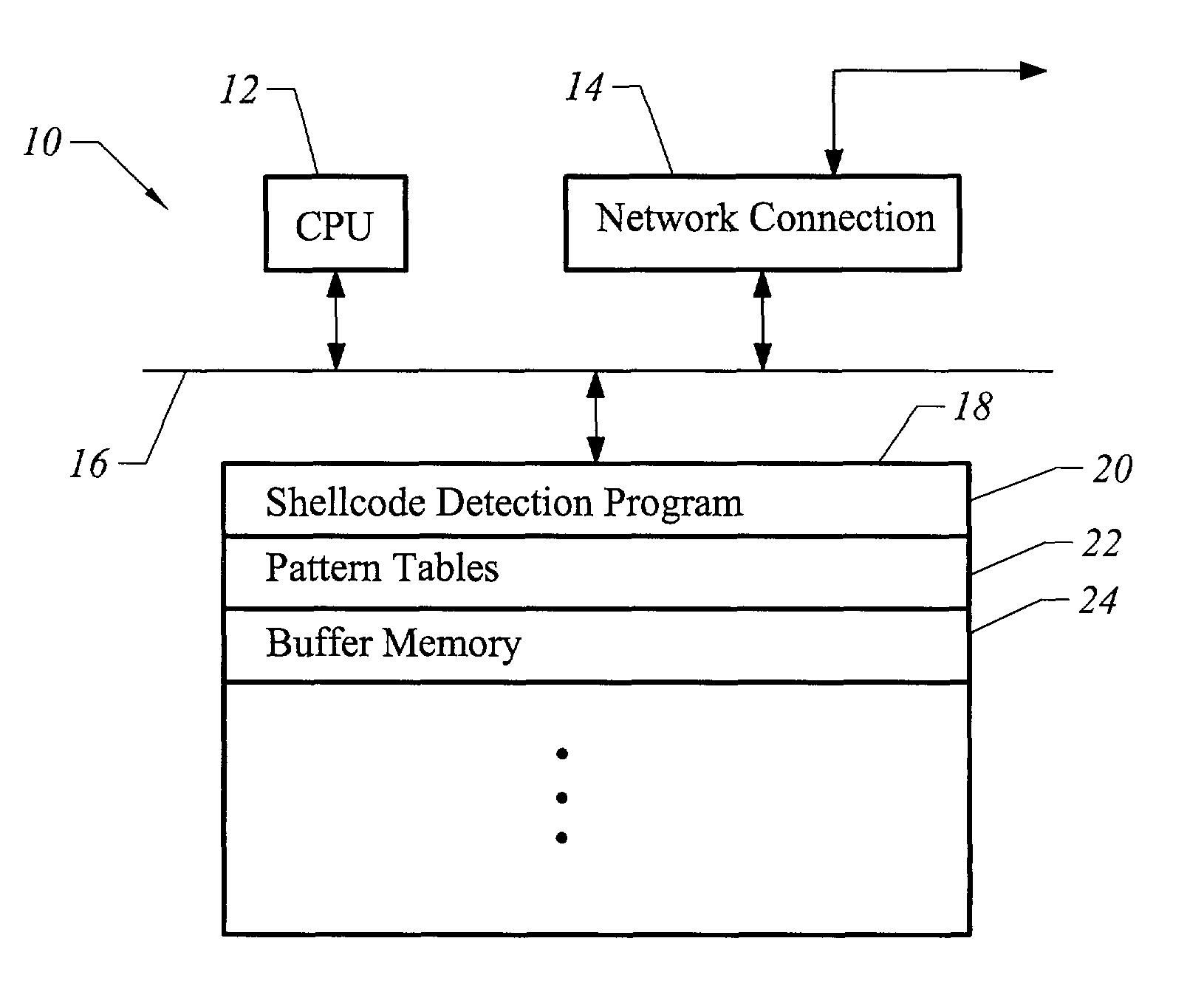
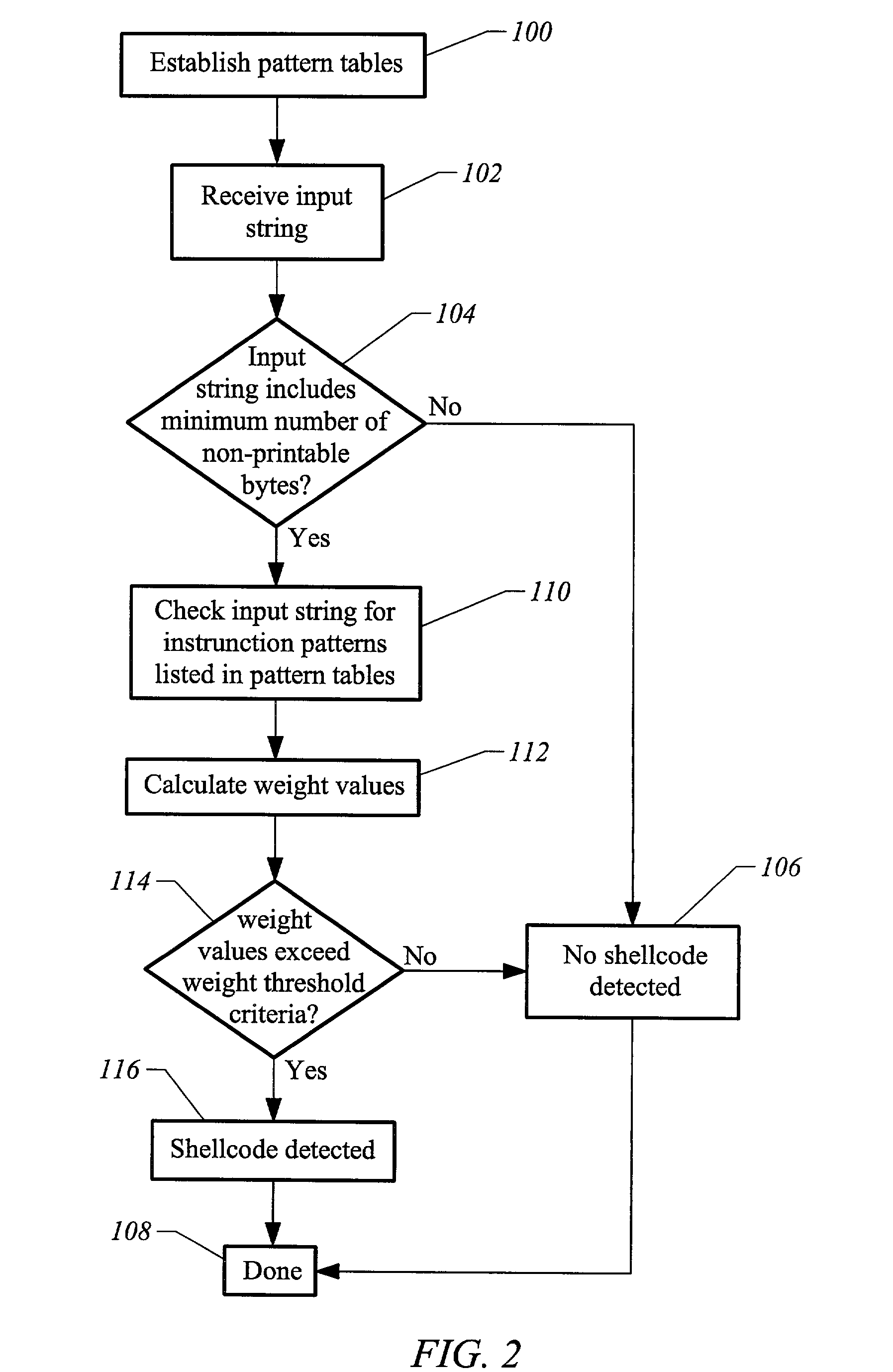
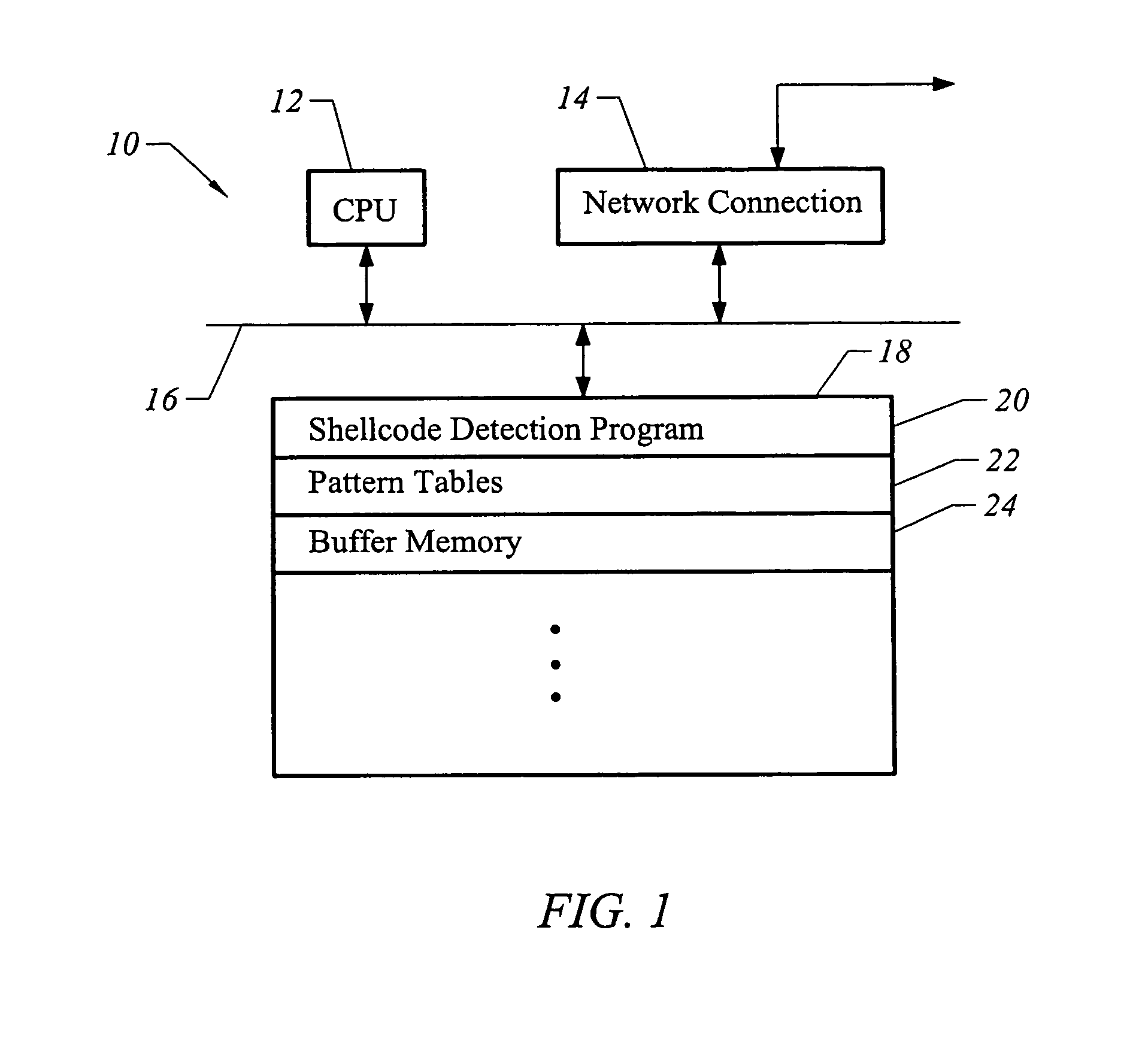
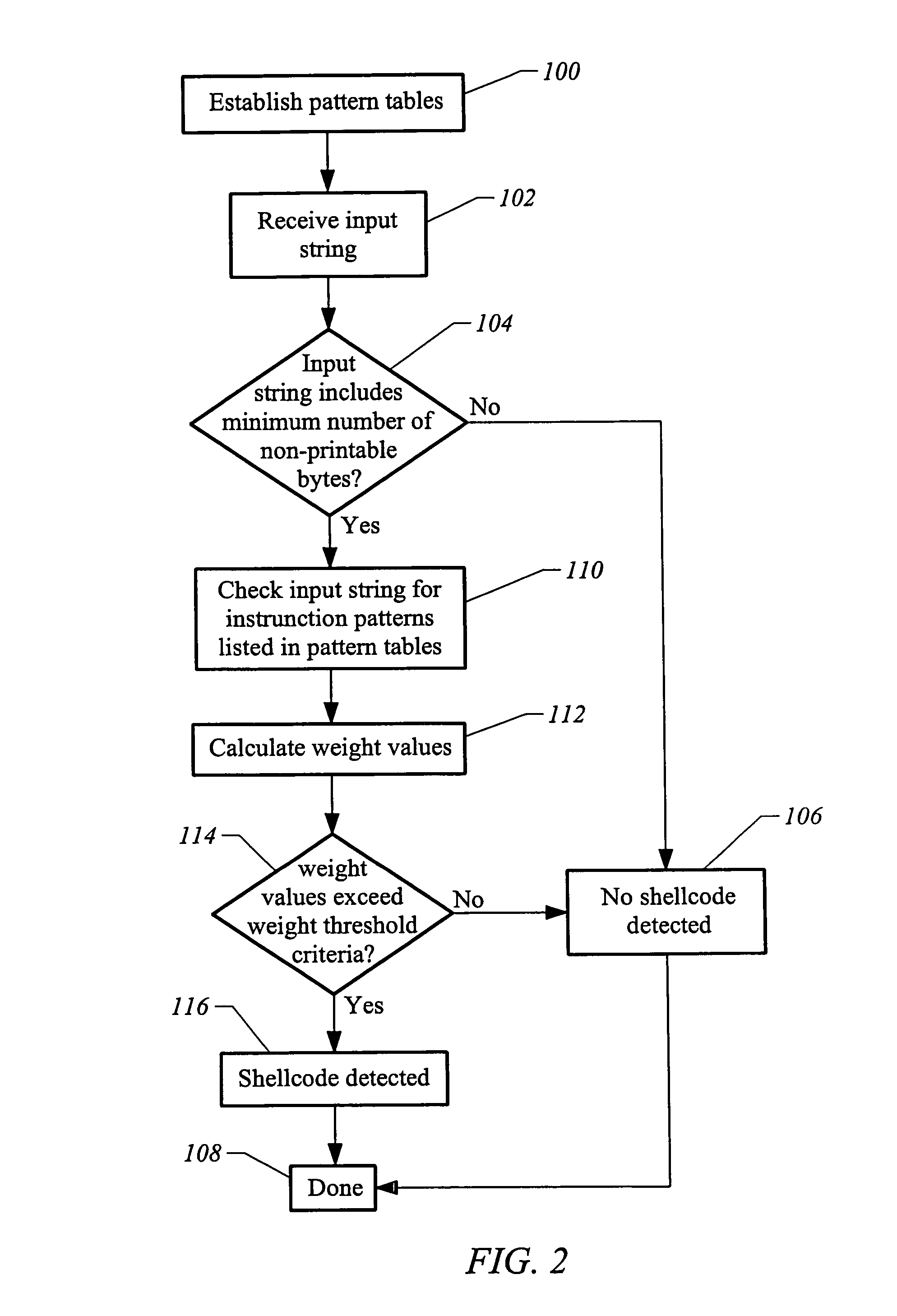
Method and apparatus for detecting shellcode
InactiveUS7904955B1Accurate detectionImprove abilitiesMemory loss protectionError detection/correctionShellcodeSystem call
The invention is a method and apparatus for detecting shellcode such that a set of computer instructions is scanned for the presence of a null operation instruction. The computer instructions are also examined for the presence of a system call instruction, and reviewed for the presence of a decoder instruction set. A null operation weight value is then determined corresponding to the null operation instruction. Also assessed is a system call weight value corresponding to the system call instruction. In addition, a decoder weight value is calculated corresponding to the decoder instruction set. The null operation weight value, the system call weight value, and the decoder weight value are then analyzed to identify a shellcode.
Owner:MCAFEE LLC
Method and apparatus for detecting shellcode
ActiveUS8051479B1Accurate detectionImprove abilitiesMemory loss protectionError detection/correctionShellcodeSystem call
Owner:MCAFEE LLC
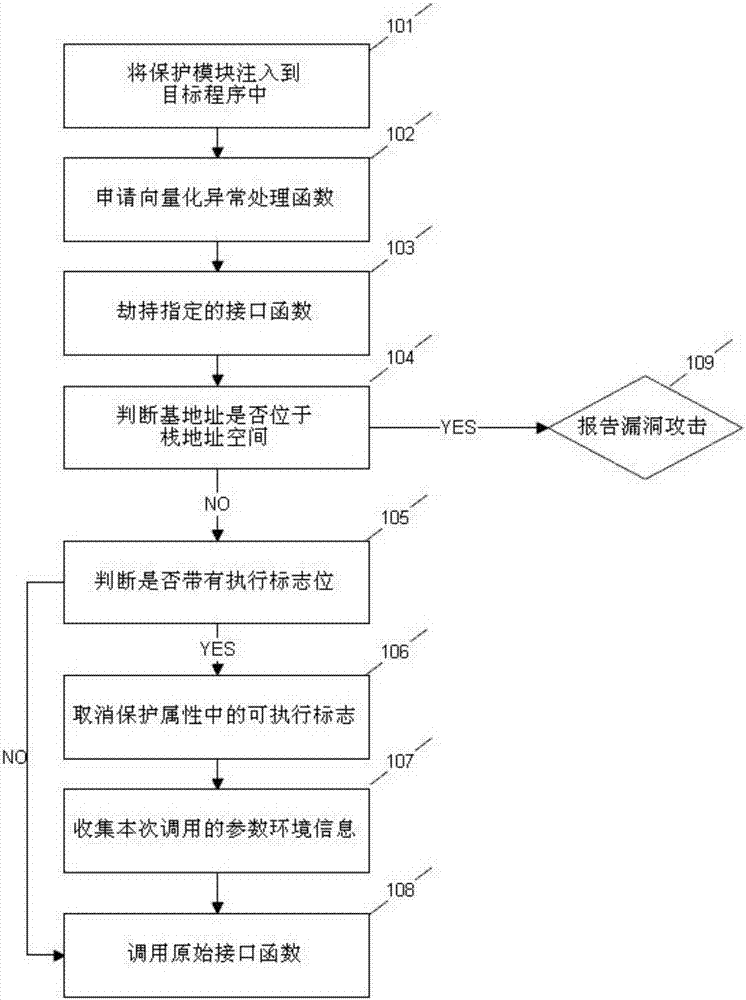
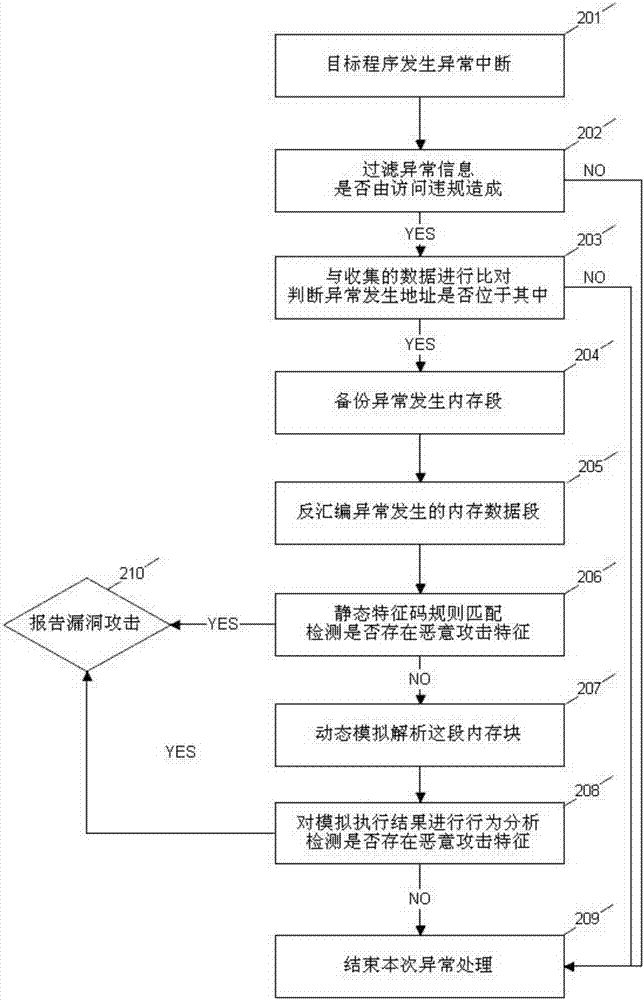
Malicious code tracking and recognizing method based on memory protection type monitoring
ActiveCN106991324ASolve the problem of small protection coverage area and low compatibilityProtection covers a wide areaPlatform integrity maintainanceShellcodeComputer compatibility
A malicious code tracking and recognizing method based on memory protection type monitoring includes the following steps that 1, a developed dynamic link library is injected into a target process; 2, vectorization manipulation function take-over anomaly is applied and used for conducting abnormal segment static analysis and dynamic analysis; 3, the interface function of memory protection attribute is hijacked and modified; 4, whether each call is located in stack space or not is detected; 5, whether the parameter of each call includes an attribute tag or not is judged; 6, for the interface function call of modifying the memory protection attribute into an executable attribute, the executable protection tag location is eliminated; 7, the parameter environment called by the interface function this time is recorded; 8, the original interface function is called so that the program can operate normally; 9, vulnerability attack finding is reported. By means of the steps, the effect of recognizing malicious code (shellcode) in the vulnerability attack process is achieved, and the problems that in the prior art, protection coverage area is small, and compatibility is low are solved.
Owner:XINGHUA YONGHENG BEIJING TECH CO LTD
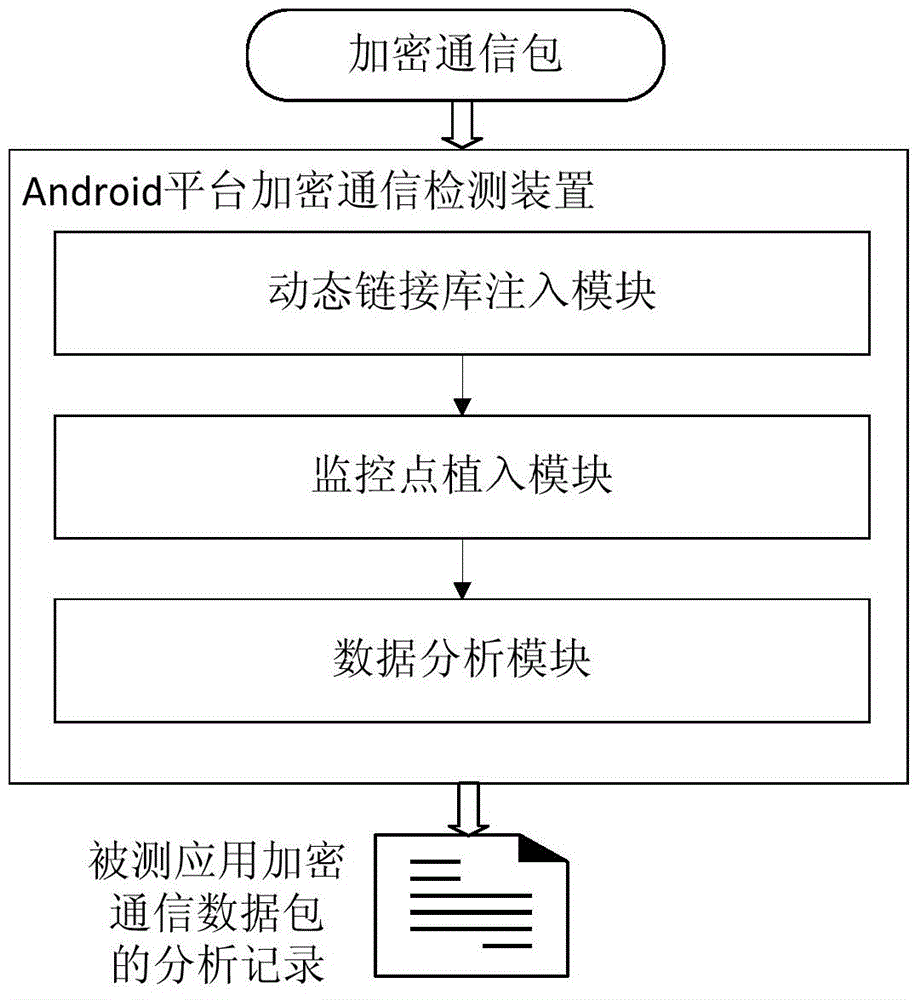
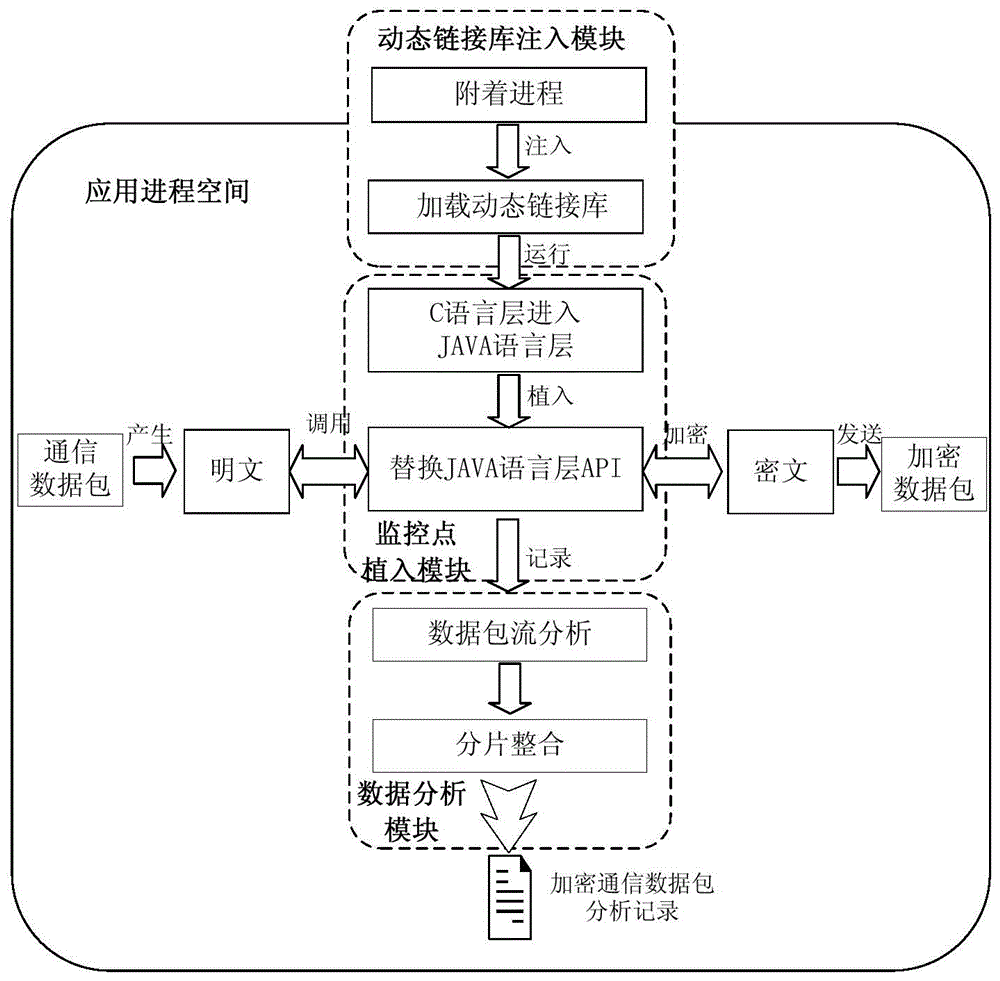
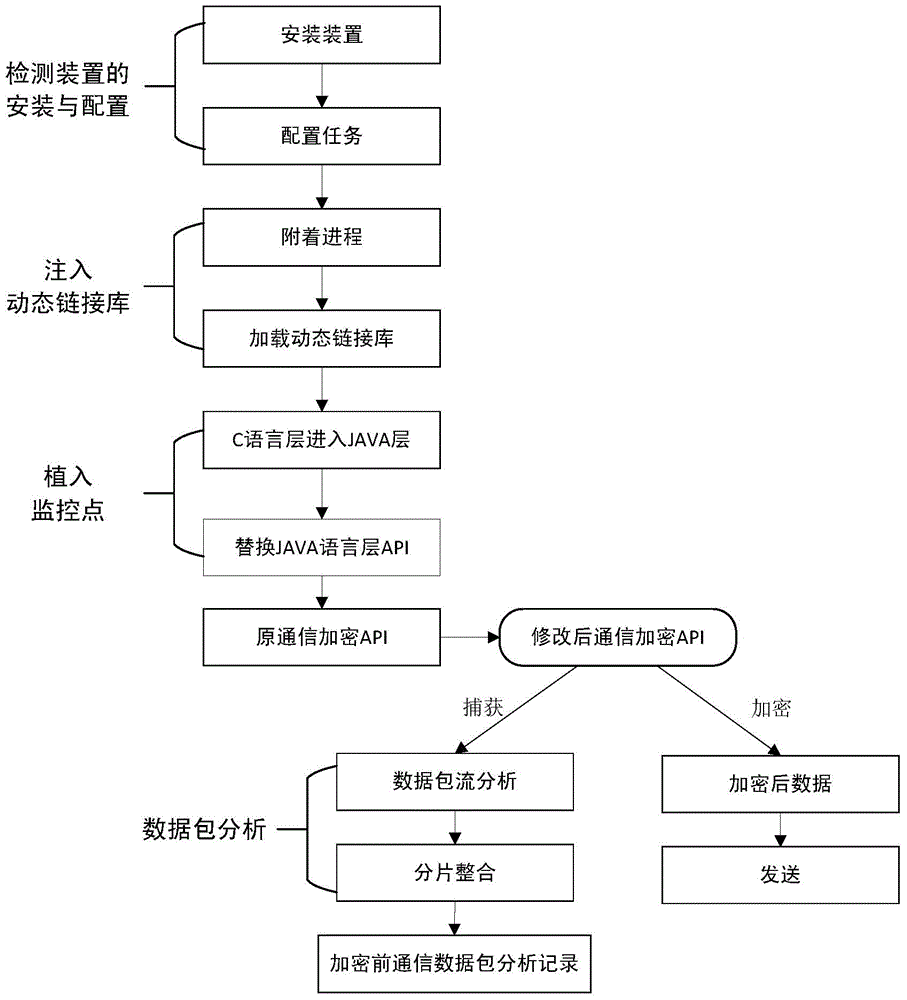
Android encryption communication detection device and method based on dynamic linking library injection
InactiveCN104156481AAvoid security issuesImprove applicabilityComputer security arrangementsTransmissionNetwork packetShellcode
The invention discloses an Android encryption communication detection device and method based on dynamic linking library injection. The detection device is provided with a dynamic linking library injection module, a monitoring point implantation module and a data packet analysis module. The detection device and method are used for detecting and analyzing terminal encryption communication on the conditions that the system ROM is not changed and the system is not in the debugging state. The detection method comprises the steps that the dynamic linking library injection mode is adopted, a shellcode is injected into the set process space of an intelligent terminal, the shellcode is searched for an API used by system encryption communication, the API is used as a monitoring point set and implanted at the Android system encryption communication position, unencrypted communication data packets sent and received by an Android intelligent terminal are captured and recorded, and the unencrypted communication data packets are detected and analyzed based on an Android platform, so that the safety problem caused by encryption communication for stealing user or enterprise privacy information and spreading illegal information is solved. The Android encryption communication detection device and method based on dynamic linking library injection have the advantages that the applicability is good, the monitoring point is extensible and comprehensive, data packet analysis and analysis cost are small, and therefore the Android encryption communication detection device and method have good application and popularization prospects.
Owner:BEIJING SOFTSEC TECH
Method for recognizing malicious file
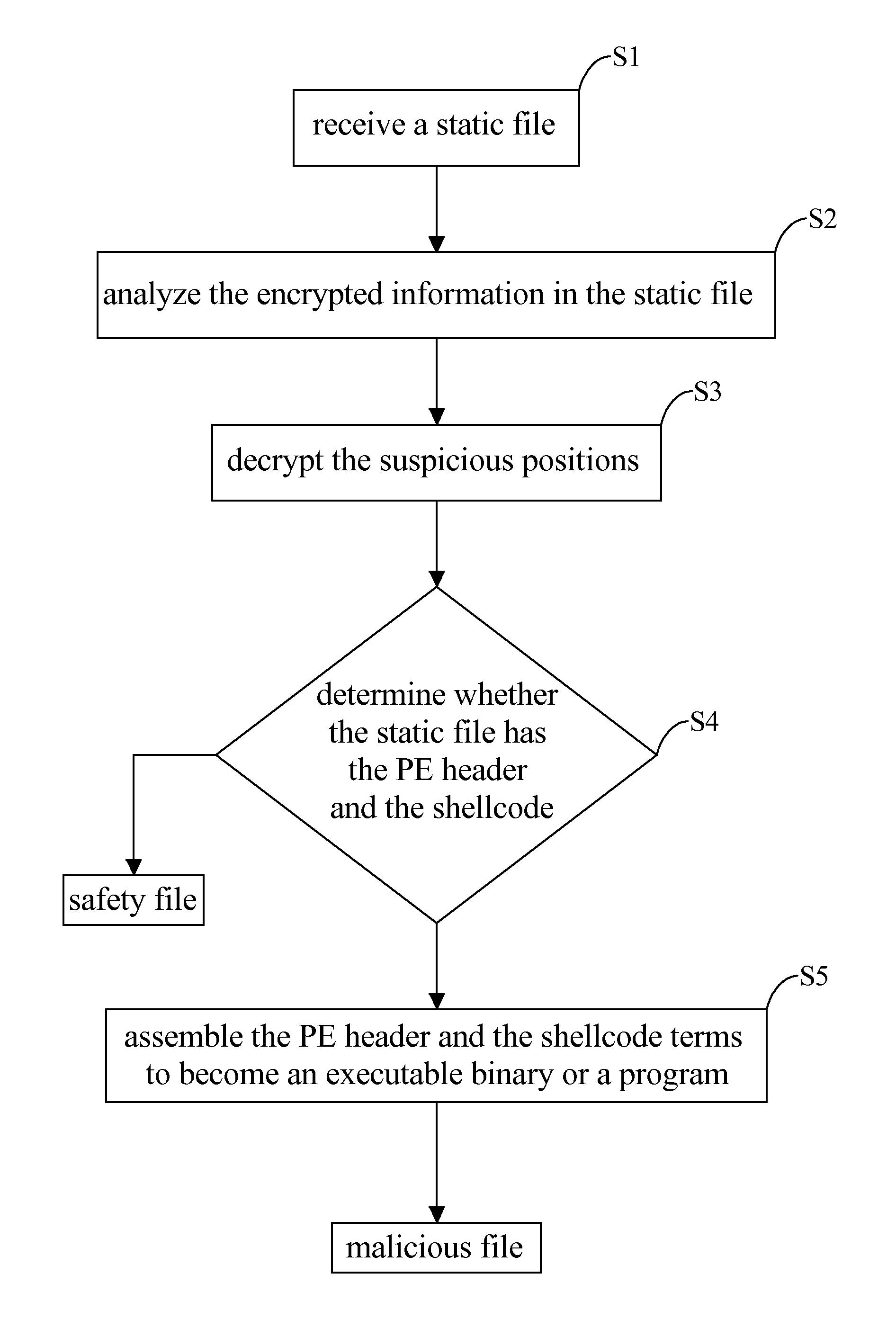
InactiveUS20140150101A1Avoiding the malicious software or malwareMemory loss protectionError detection/correctionShellcodeMalware
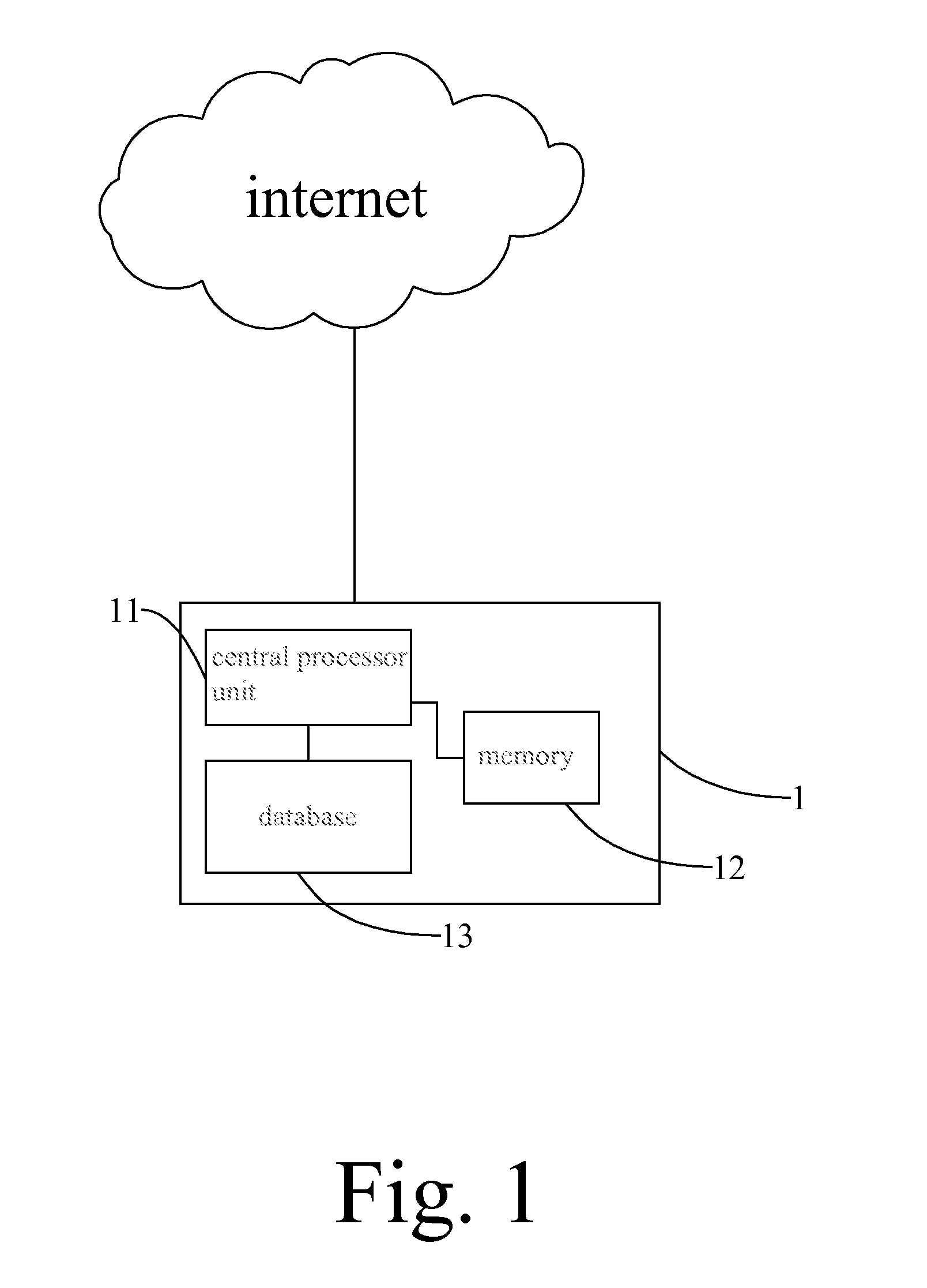
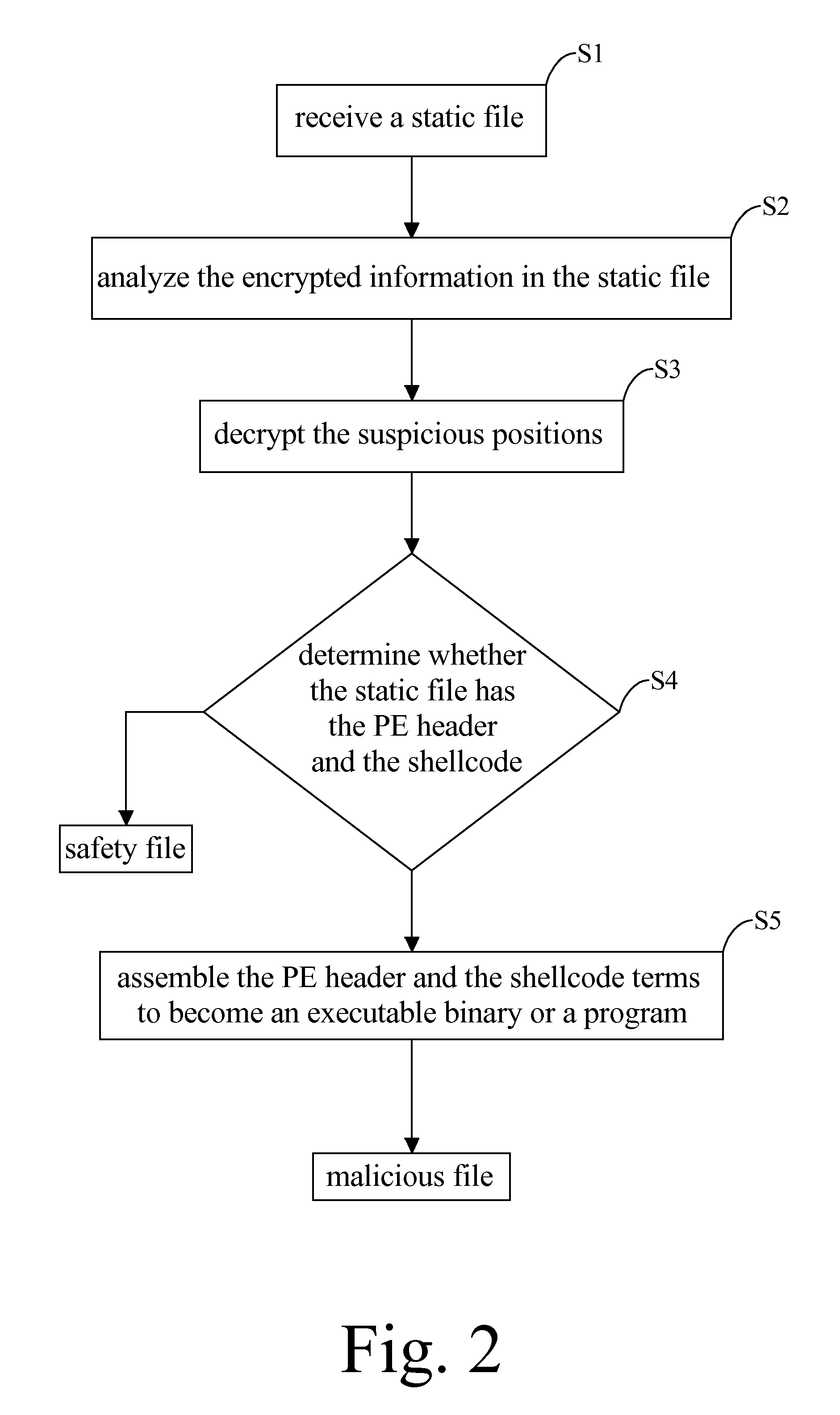
A method for recognizing malicious file has steps: receiving a static file through a network or an input / out interface to be stored in the memory; defining suspicious positions where components of a malware are possibly encrypted in the static file; decrypting the suspicious positions to identify a PE header and a shellcode; extracting the PE header and the shellcode terms in segments; and determining whether the PE header and the shellcode terms can be assembled into an executable binary which indicates a recognition of the malicious file.
Owner:VERINT SYST LTD
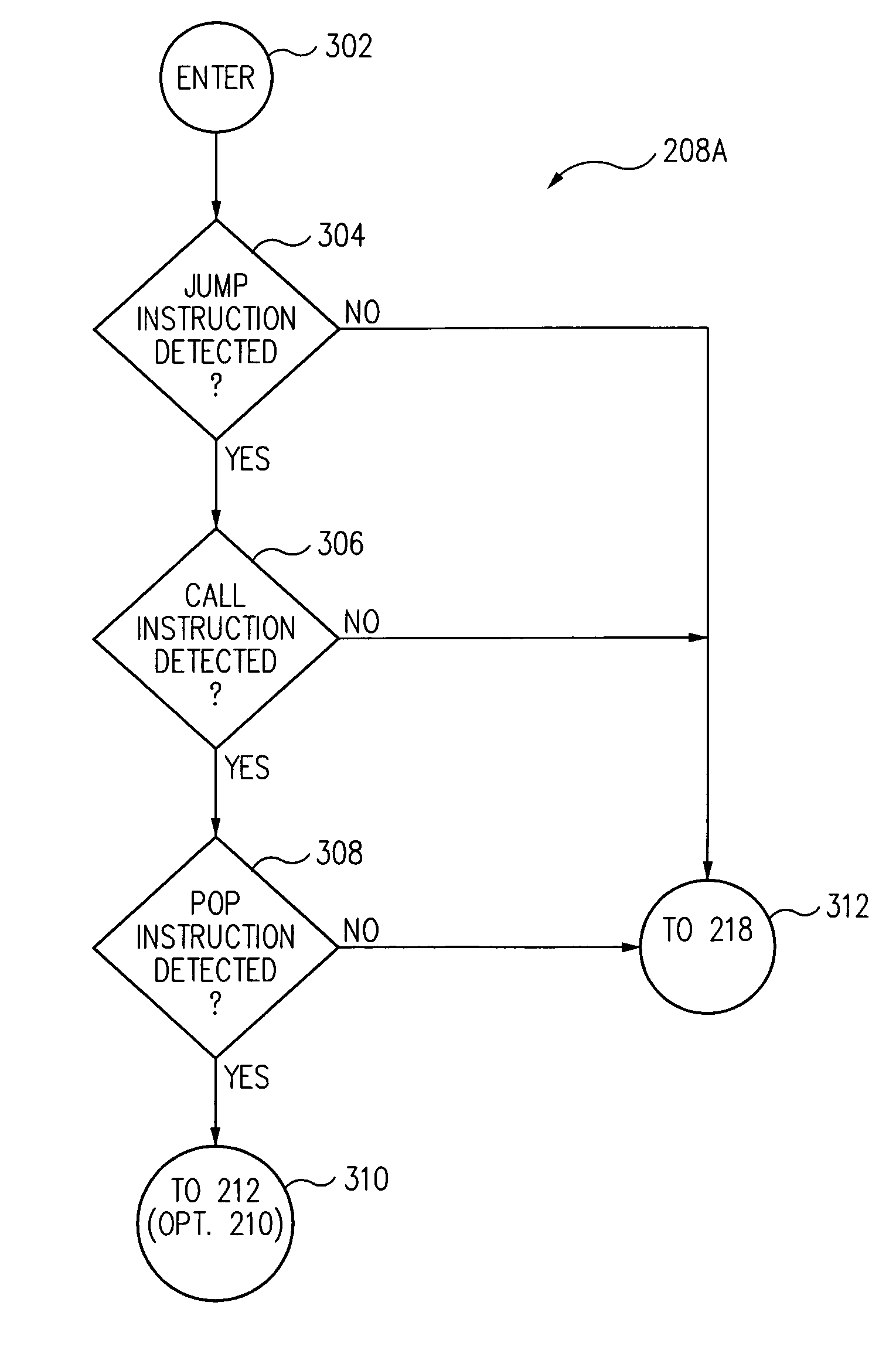
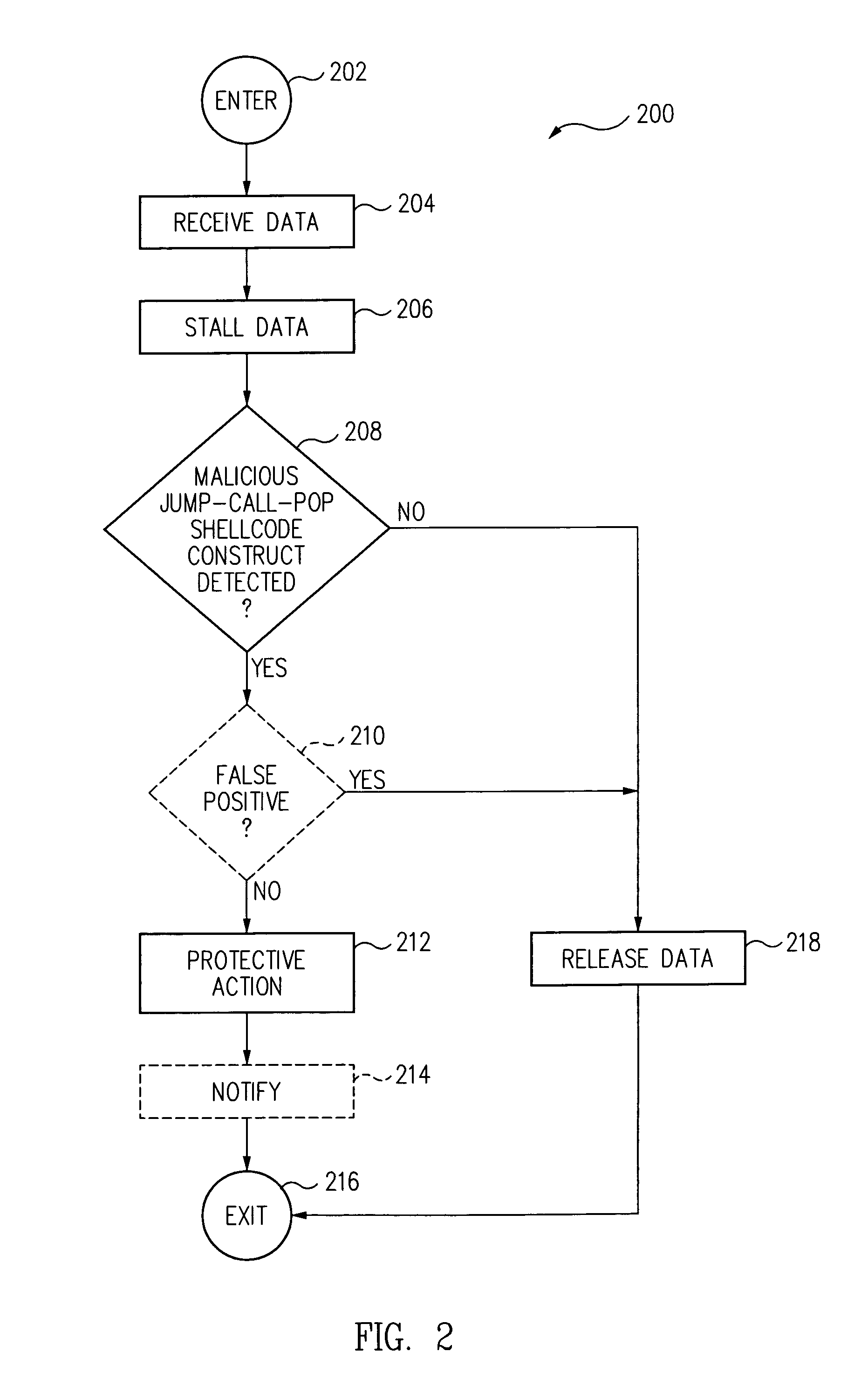
Method and system for detecting IA32 targeted buffer overflow attacks
Data streams are scanned to detect malicious jump-call-pop shellcode constructs used in attacks against stack-based buffer overflow vulnerabilities on software executing in the IA32 architecture prior to execution. Upon a detection of a malicious jump-call-pop shellcode construct, protective action is taken, such as preventing the malicious shellcode from executing.
Owner:GEN DIGITAL INC
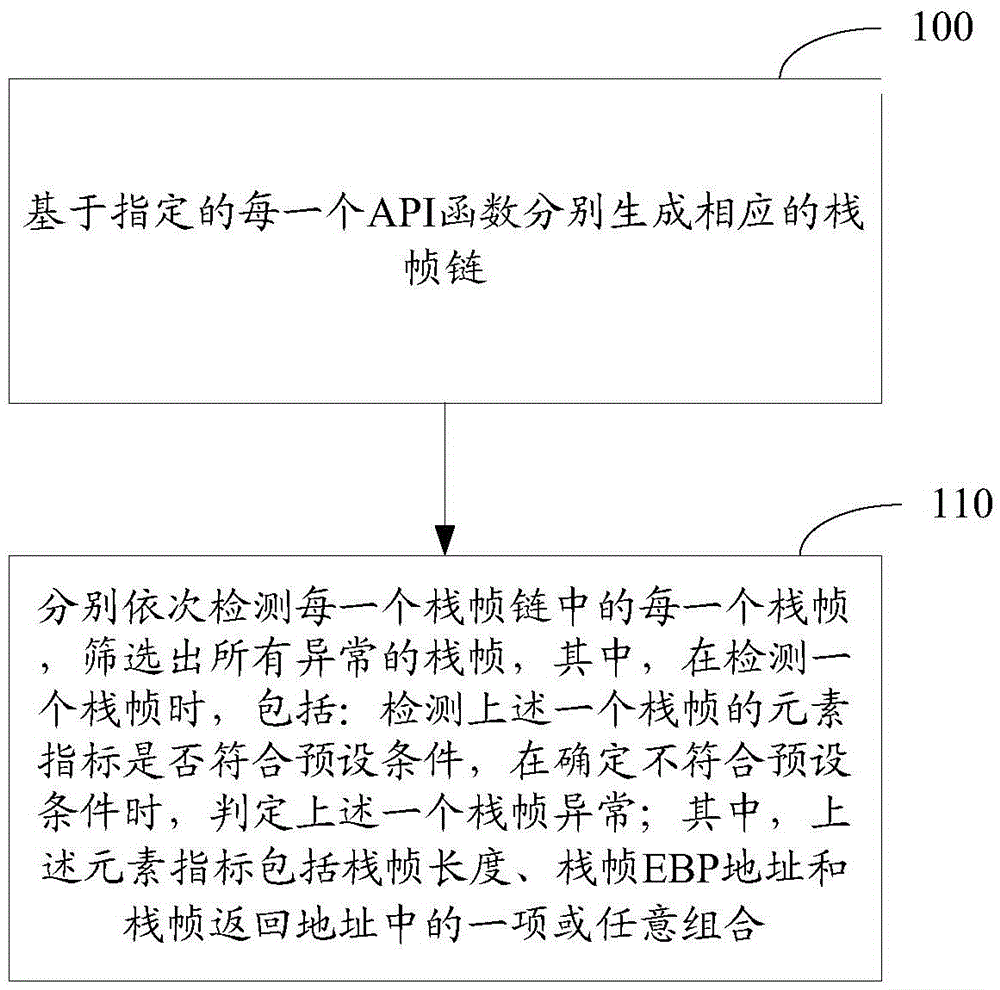
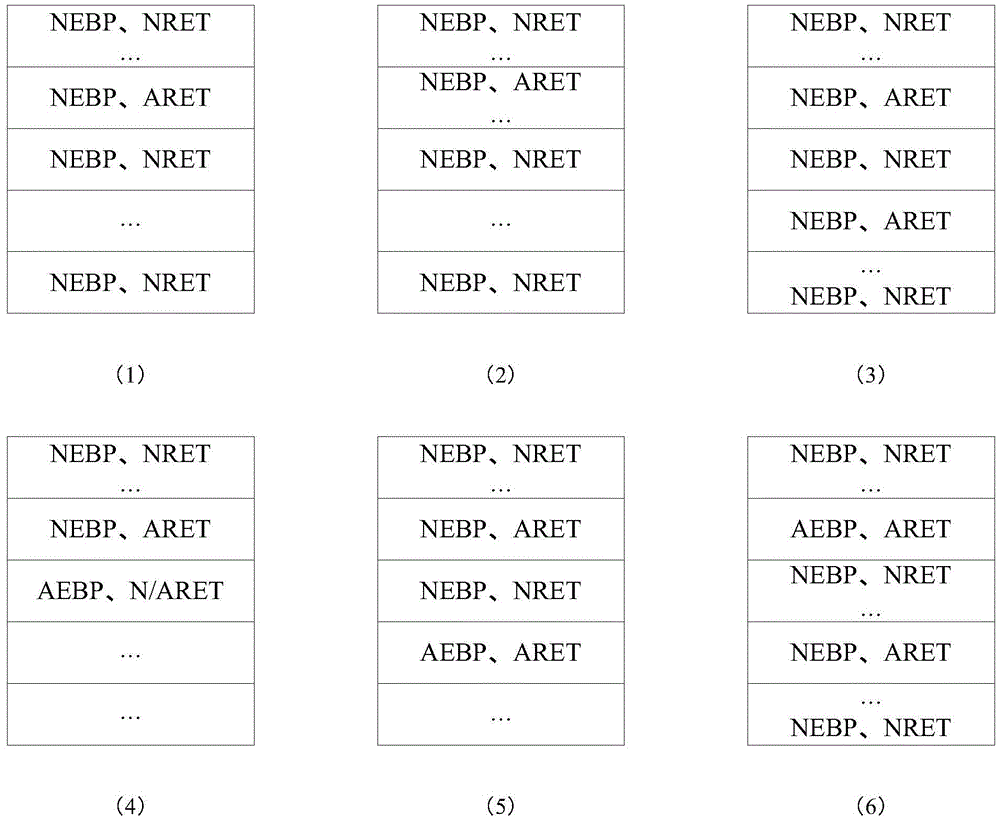
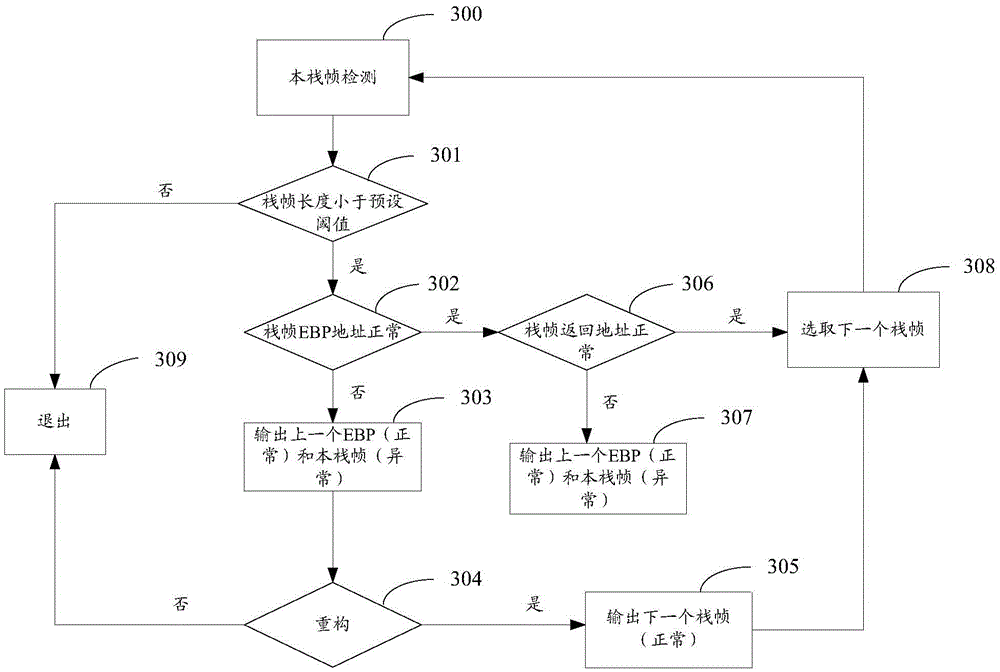
Method and apparatus for detecting Shellcode based on stack frame abnormity
InactiveCN105678168AAvoid blind detectionReduce false alarm ratePlatform integrity maintainanceComputer hardwareFrame based
The invention relates to the field of computers, and in particular to a method and an apparatus for detecting Shellcode based on stack frame abnormity. The method comprises the following steps: based on each designated API function, separately generating a corresponding stack frame chain, and separately detecting each stack frame of each stack frame chain in order, selecting all stack frames with abnormities, wherein the detection of one stack frame includes the following steps: detecting whether an element indicator of the one stack frame suits a preset condition, and if the element indicator is determined not to meet the preset condition, determining the one stack frame is abnormal; and the element indicator including one or a combination of stack frame length, stack frame EBP address and stack frame returning address. The mere detection of the stack frame chain which corresponds to a designated API function can avoid blind detection on all functions, and reduces system performance spending. And the method selects abnormal stack frames based on the element indicator of the stack frame, which increases the system detection performance and reduce rate of false alarm.
Owner:NSFOCUS INFORMATION TECHNOLOGY CO LTD +1
Malicious code sample extraction method and system based on document type bug
ActiveCN103294951AEasy extractionHigh speedPlatform integrity maintainanceDocument Type CodeShellcode
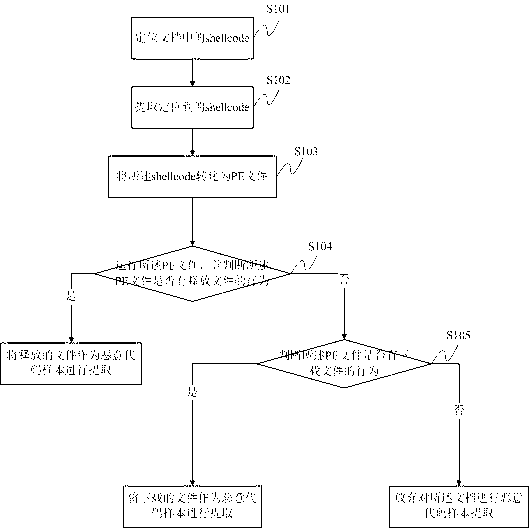
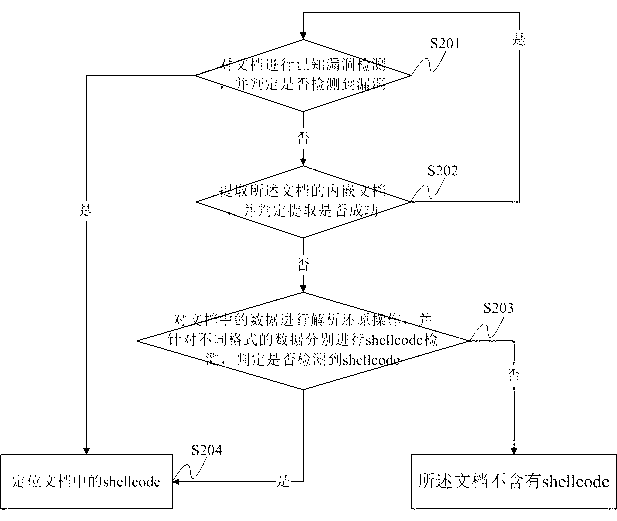
The invention discloses a malicious code sample extraction method and a system based on a document type bug. The method comprises the steps that a shellcode in a document is positioned; the positioned shellcode is extracted, and then converted into a PE (Portable Executable) file; the PE file is operated; whether the PE file releases a file is judged; if so, the released file serves as a malicious code sample to be extracted; if not, whether the PE file downloads a file is judged; if so, the downloaded file serves as a malicious code sample to be extracted; and if not, malicious code sample extraction on the document is abandoned. Compared with the traditional culture method, the method extracts more accurately, quickly and conveniently.
Owner:BEIJING ANTIY NETWORK SAFETY TECH CO LTD
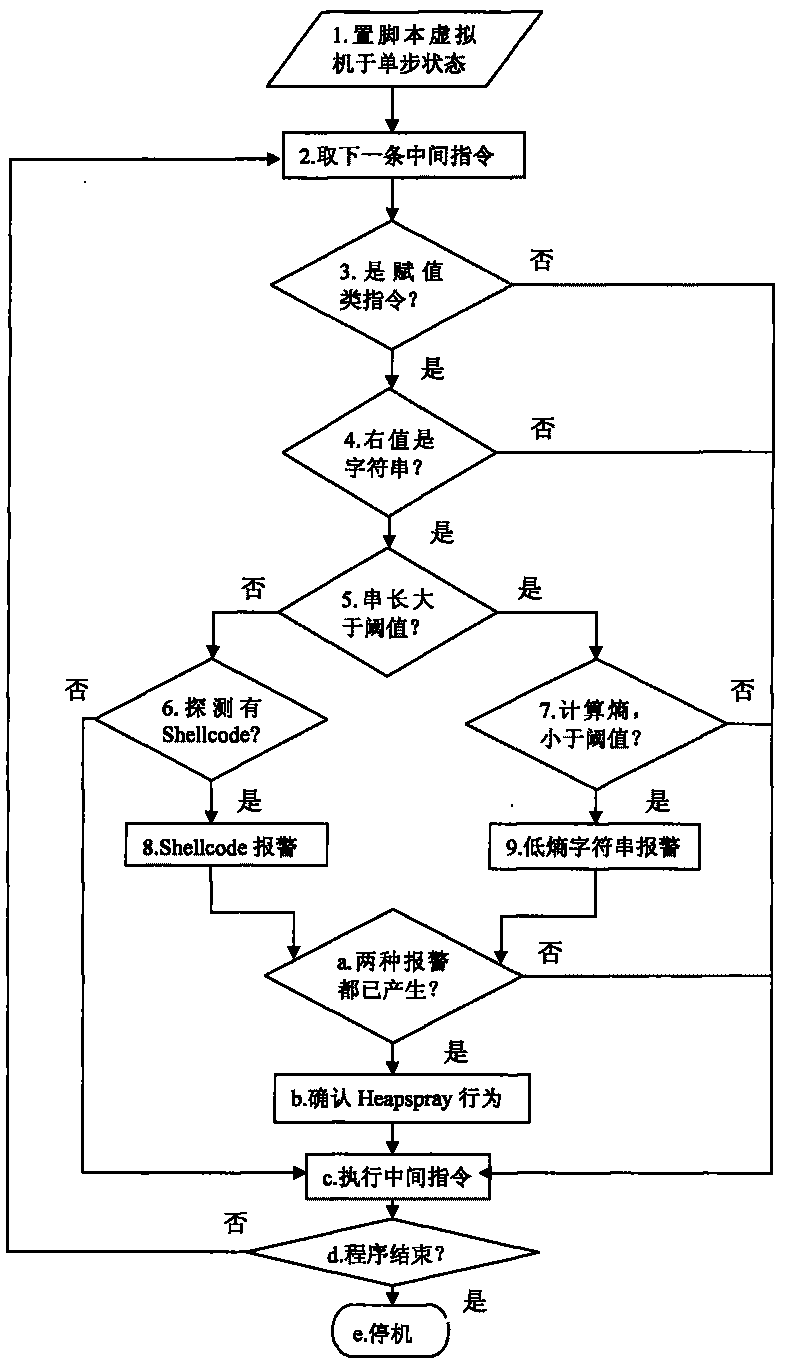
Heapspray detection method based on intermediate command dynamic instrumentation
InactiveCN101719204AAccurately determine the semanticsAccurately determine behaviorPlatform integrity maintainanceAlgorithmDynamic instrumentation
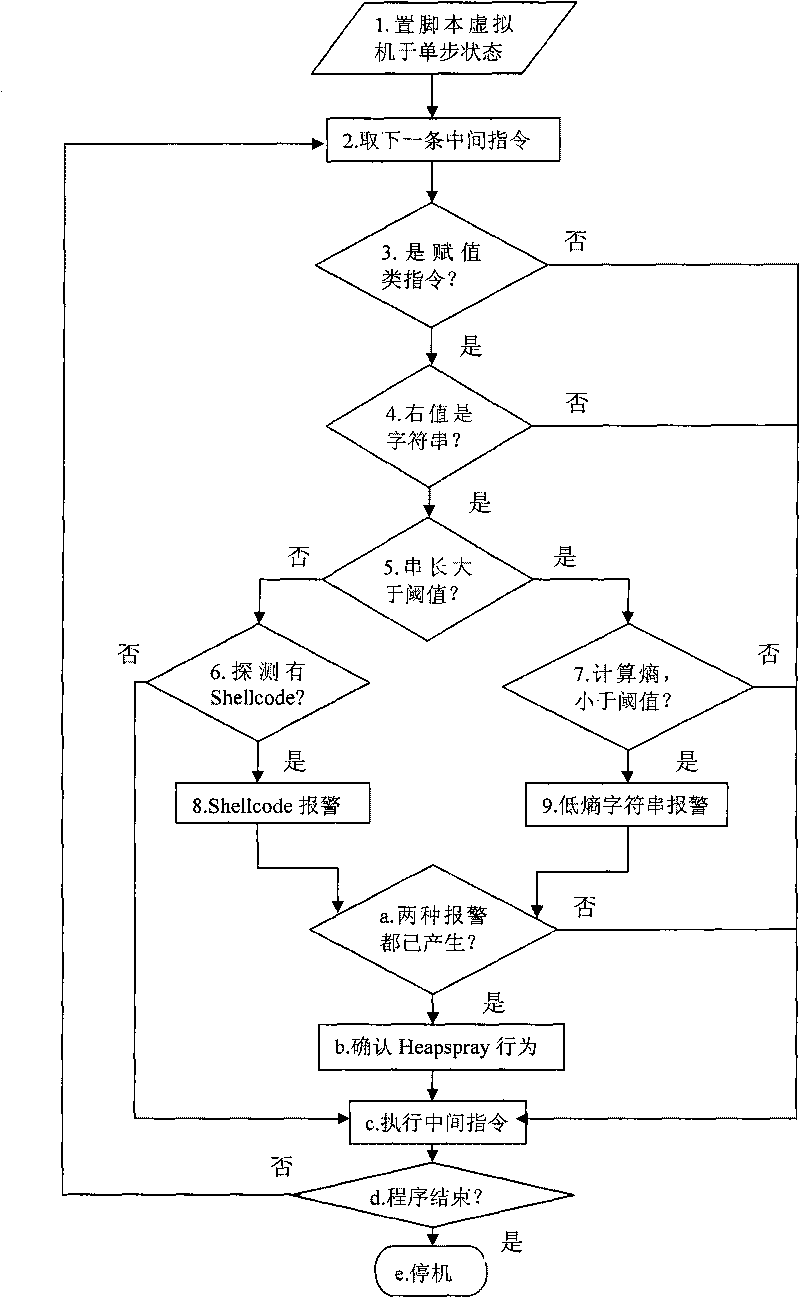
The invention discloses a Heapspray detection method based on intermediate command dynamic instrumentation, belonging to the technical field of computer security. The method comprises the following steps of: (1) setting a virtual machine used for explaining and implementing webpage dynamic script into a single-step operating state; (2) judging whether an intermediate command to be implemented currently is an assignment type intermediate command or not; (3) if so, then judging whether a rvalue parameter type in command parameters is a alphabetic string type or not; if the rvalue parameter is the alphabetic string type and a value thereof is less than a set threshold value P, then checking whether shellcode exists or not; if the rvalue parameter is larger than the set threshold value P, then calculating an information entropy value thereof; and (4) taking a next intermediate command and repeating the step (2) and the step (3); if a rvalue parameter of an assignment type intermediate command has the shellcode and an entropy value of a rvalue parameter of the other assignment type intermediate command is less than the set threshold value, then judging the script to have a Heapspray action. The invention can reduce system overhead and improve the accuracy rate of detection.
Owner:PEKING UNIV
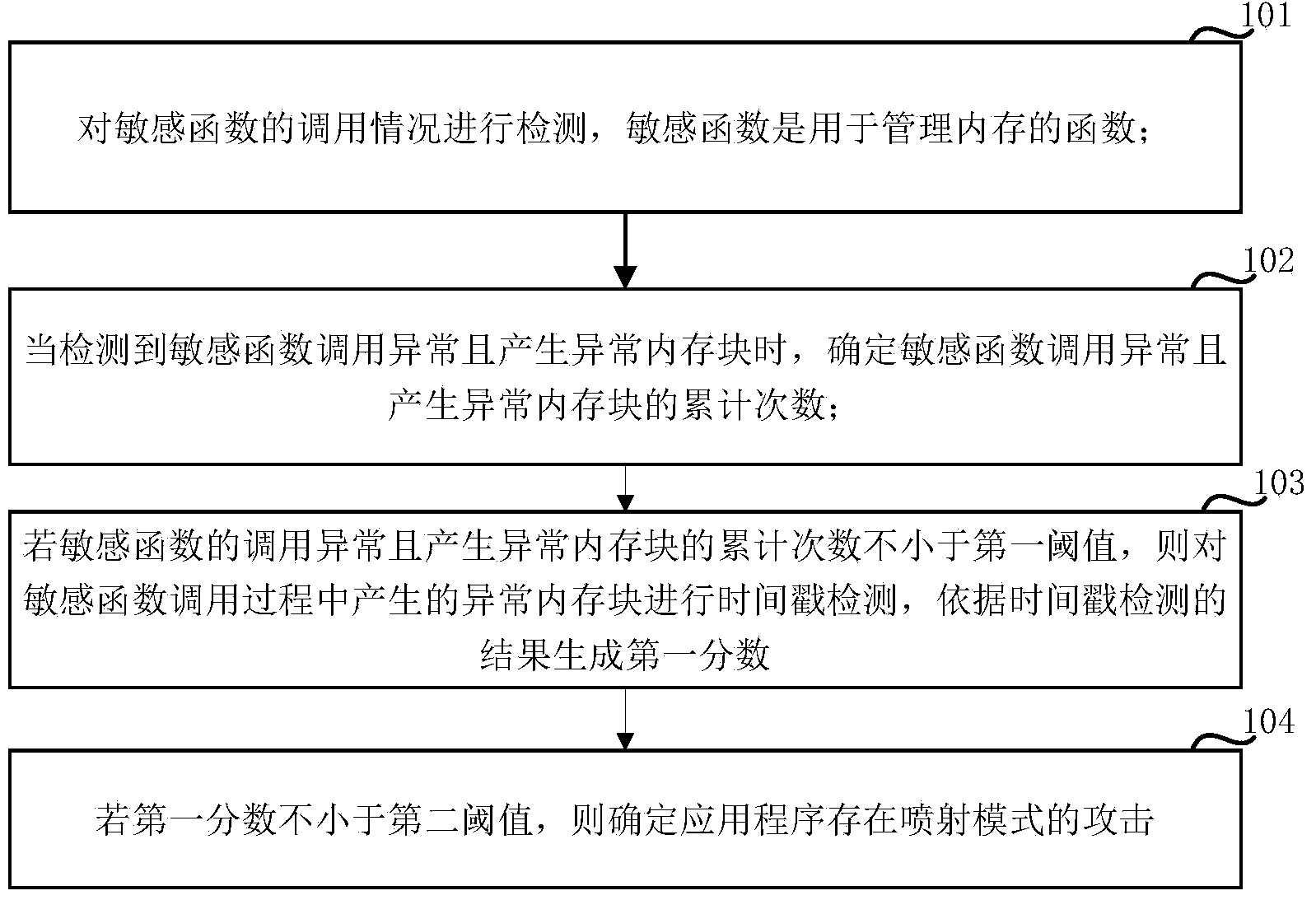
Detection method and detection device for attack in spray pattern
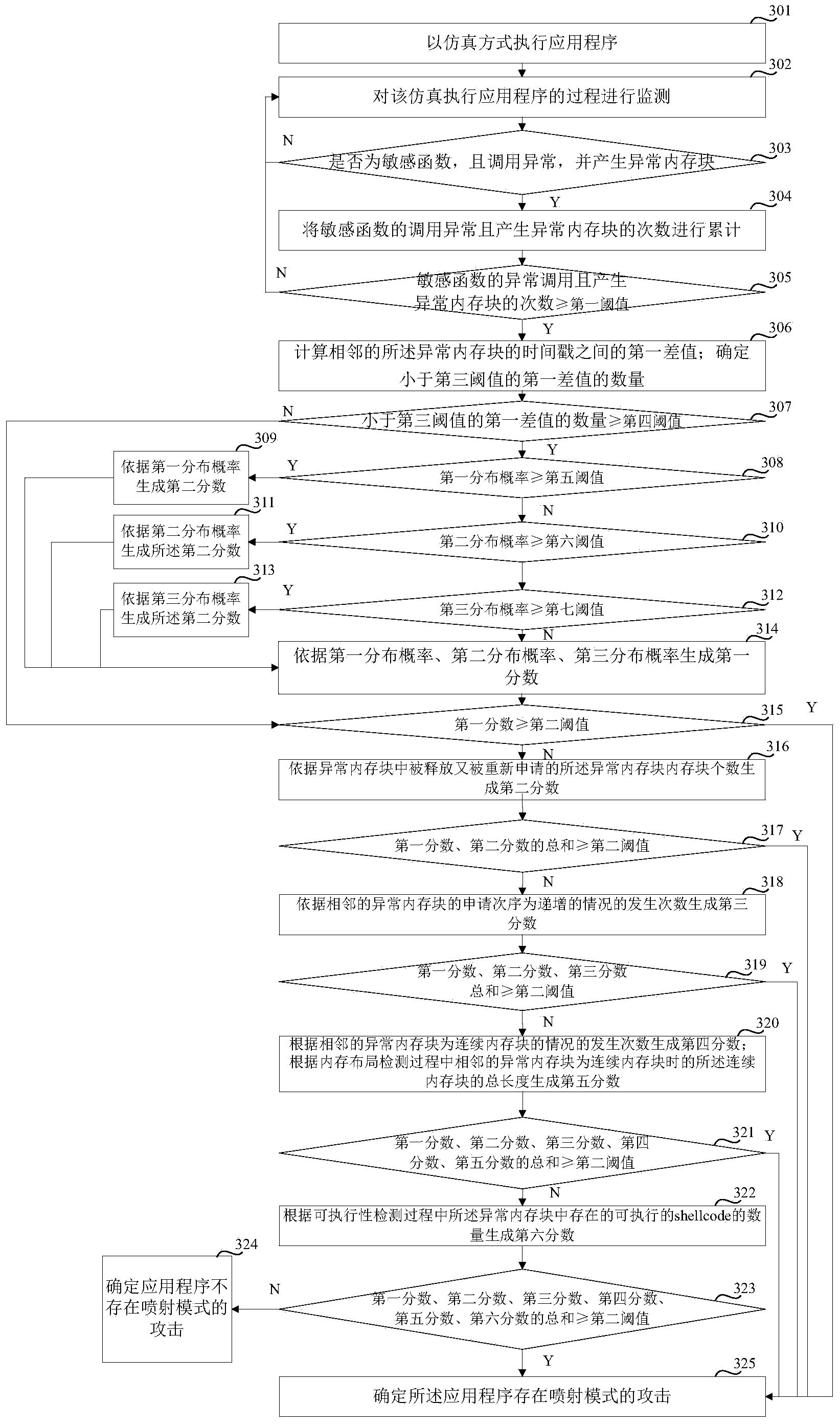
ActiveCN103984898AAvoid detection failureImprove timelinessPlatform integrity maintainanceShellcodeComputer science
An embodiment of the invention relates to the technical field of computer security, in particular to a detection method and a detection device for an attack in a spray pattern, which are used to solve a problem that a method judging whether the attack in the spray pattern exists simply by detecting whether a shellcode can be executed is possible to be subjected to detection failure. The method disclosed by the embodiment of the invention comprises the steps of: detecting a calling situation of a sensitive function; if calling of the sensitive function is abnormal and an accumulative number of memory blocks that are abnormal is not less than a first threshold value, performing time stamp detection upon the memory blocks that are abnormal during a calling progress of the sensitive function, generating a first fraction according to a result of the time stamp detection; if the first fraction is not less than a second threshold value, determining that an application is subjected to attach in the spray pattern. Whether the attack in the spray pattern exists can be judged simply by detecting time stamps of the abnormal memory blocks, so that occurrences of detection failure are reduced.
Owner:NSFOCUS INFORMATION TECHNOLOGY CO LTD +1
Similarity match based rapid detection method for malicious shellcode
InactiveCN105245495AImprove unified and effective detectionImprove throughputTransmissionShellcodeThroughput
Owner:HARBIN ENG UNIV
Network threat analysis method and system
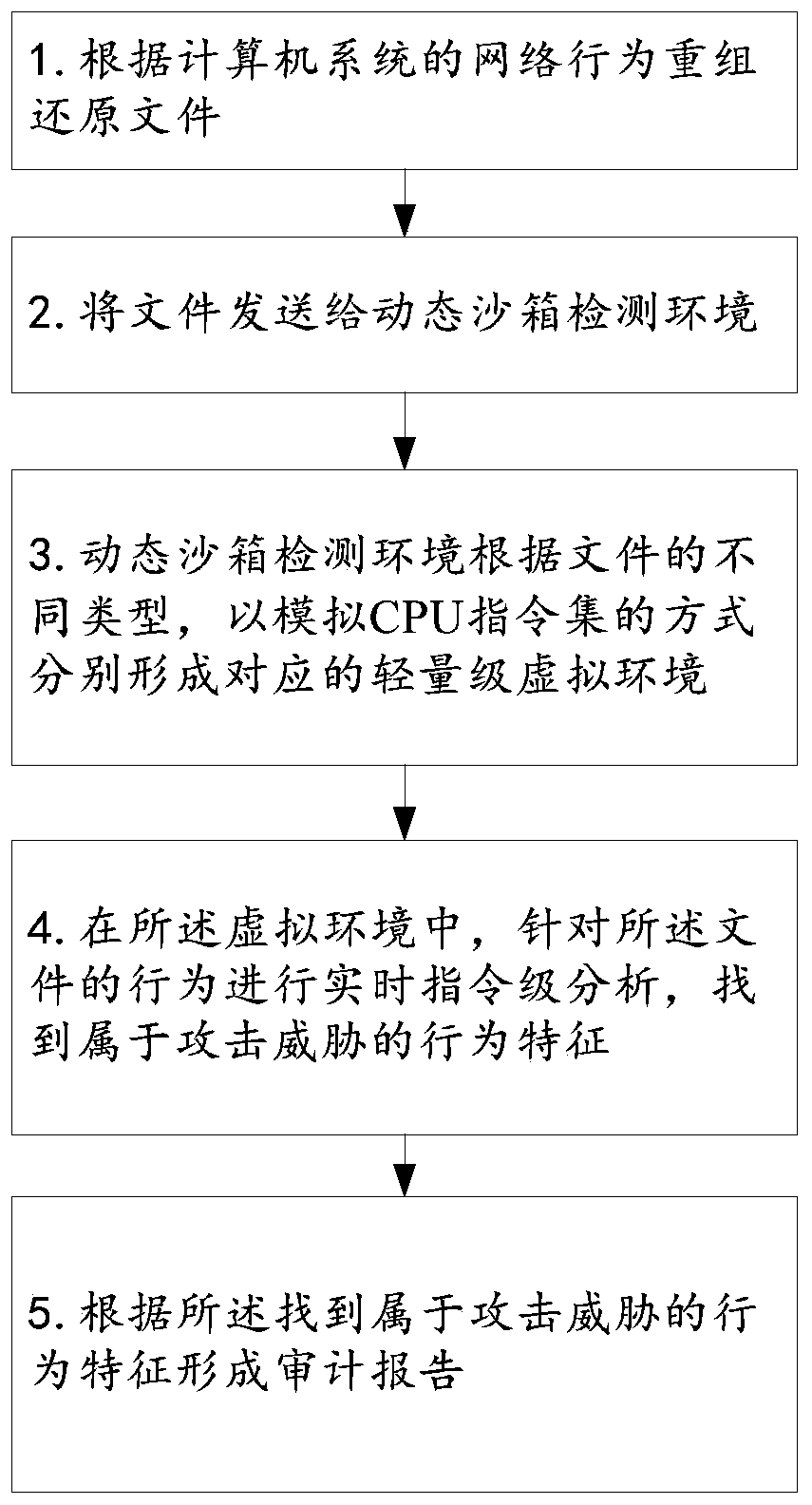
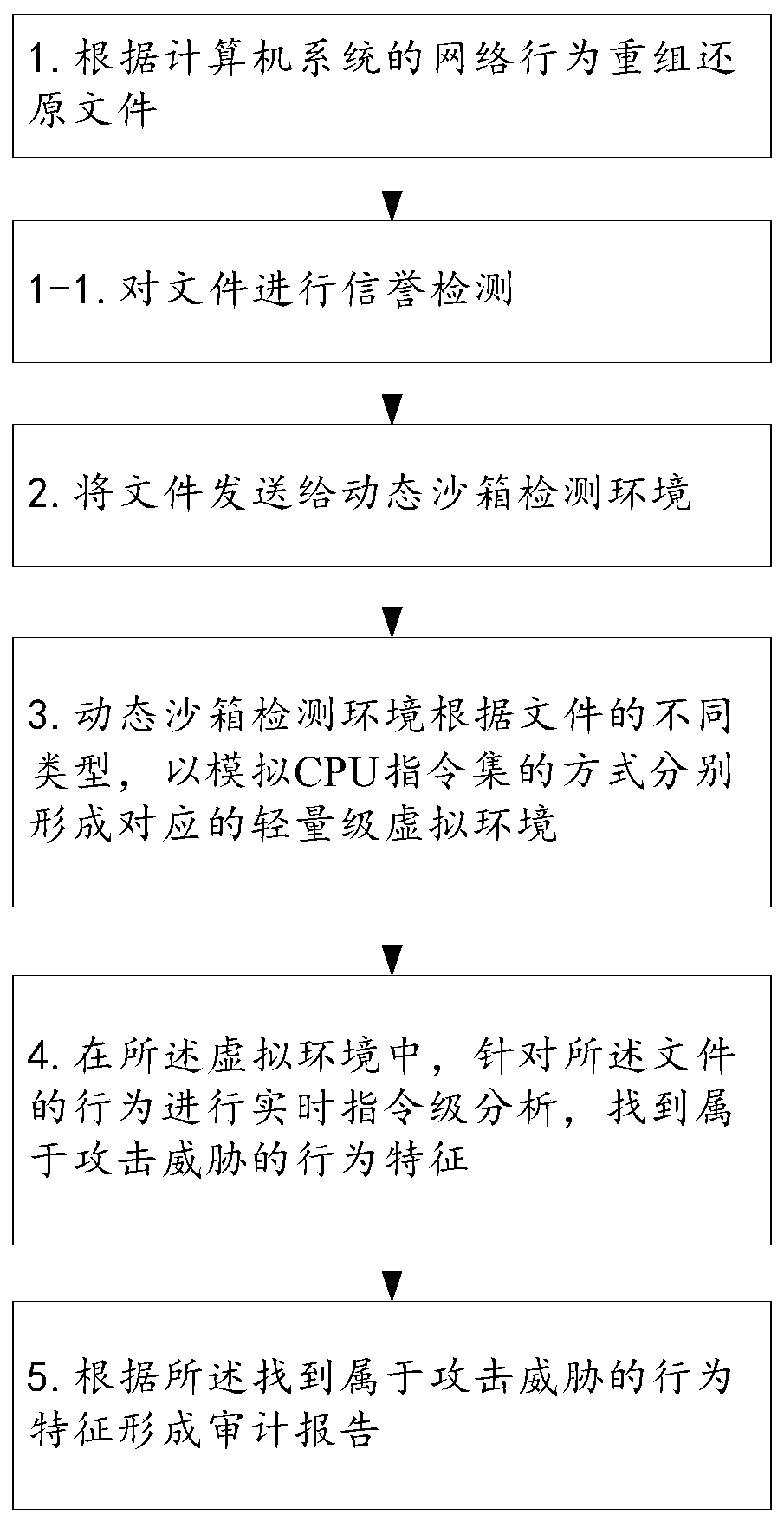
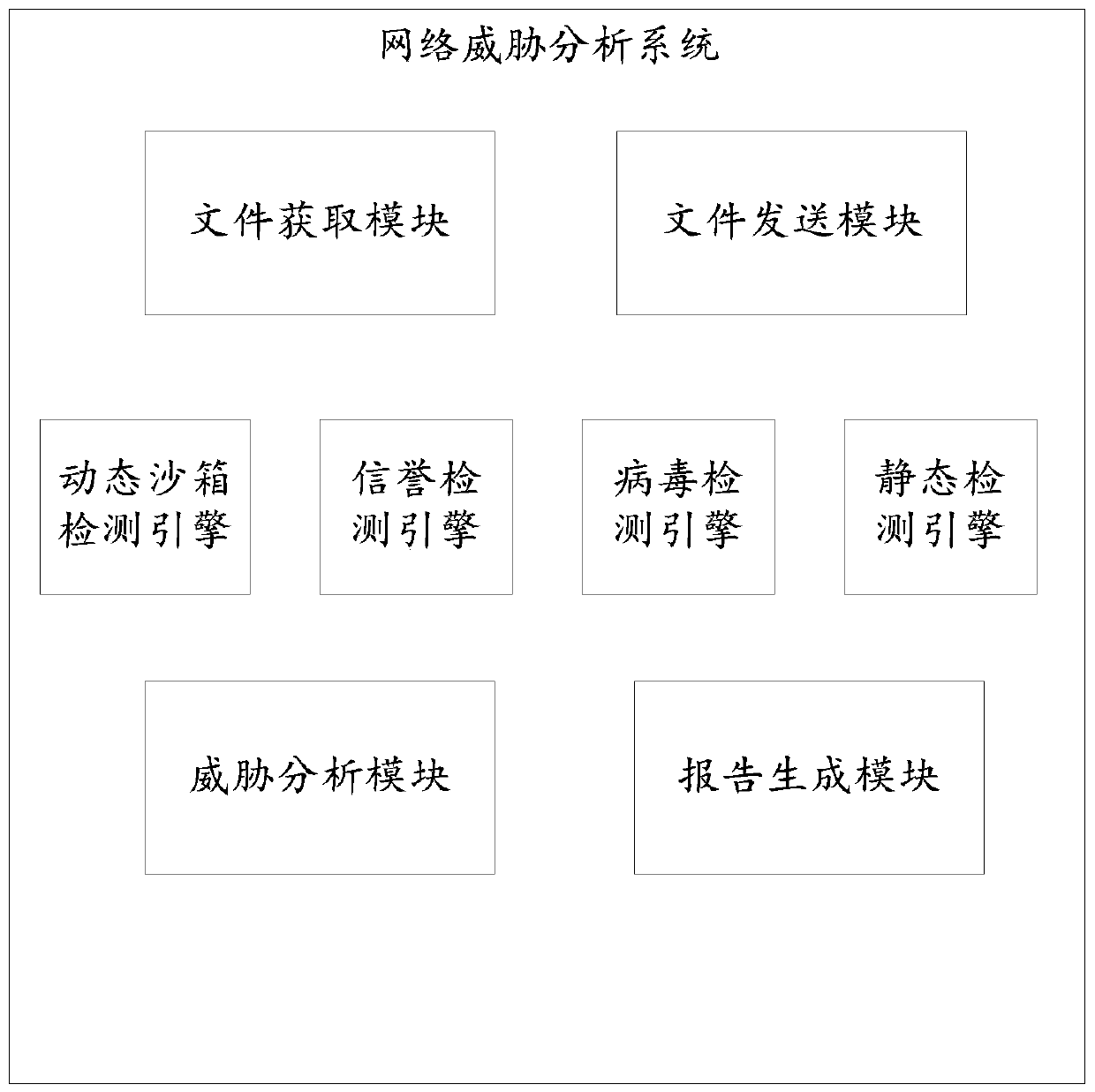
InactiveCN110602044AEffective detection of 0day attacksEffective detection of unknown attacksTransmissionShellcodeVirus detection
The invention discloses a network threat analysis method and system. The English name of the network threat analysis system is ThreatAnalysis Center (hereinafter referred to as TAC for short). Known and unknown malicious software and files entering a network through a webpage, an e-mail or other online file sharing modes can be effectively detected, APT attack behaviors utilizing 0day vulnerabilities are discovered, and a client network is protected from various risks caused by attacks such as 0day. According to the TAC system, a multi-core virtualization platform is adopted, and higher performance and higher detection rate are achieved through a parallel virtual environment detection and stream processing mode. The system comprises four core detection assemblies: a reputation detection engine, a virus detection engine, a static detection engine (including vulnerability detection and shellcode detection) and a dynamic sandbox detection engine, through parallel detection of multiple detection technologies, a 0day attack and an unknown attack can be effectively detected while a known threat is detected, so that an advanced sustainable threat can be effectively monitored.
Owner:GUIZHOU POWER GRID CO LTD
Dynamic detection method of Shellcode
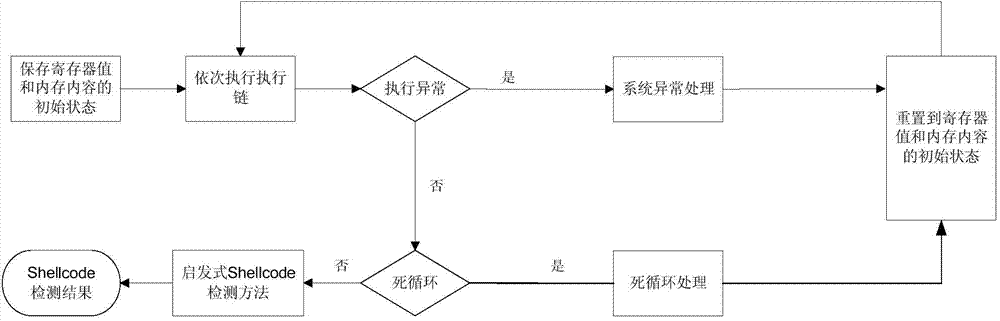
InactiveCN104731708AOvercome the defects of failureEasy to deploySoftware testing/debuggingPlatform integrity maintainanceVirtualizationShellcode
Disclosed is a dynamic detection method of a Shellcode. The method comprises the steps that network data flow is firstly grabbed and divided, and a plurality of execution links are obtained; then an operating system breakpoint is triggered to be abnormal, and the register value and internal storage content in the abnormality triggering process are used as an initial register value and internal storage content to be stored; finally, the execution links are executed in sequence, meanwhile, whether an endless loop or operating system abnormality occurs or not is detected in the execution process of each execution link, the current execution link has no Shellcode if the endless loop or operating system abnormality occurs, and otherwise whether the current execution link has the Shellcode or not is detected in a starting method, and detection is completed. According to the method, the Shellcode with the code obfuscation technology can be detected, the virtualization technology is not adopted, deployment is easy, the Shellcode capable of finding virtualization environment can be detected effectively, and the probability of Shellcode detection exposure is greatly reduced.
Owner:北京信息控制研究所 +1
Memory malicious code detection method based on processor tracking
ActiveCN113569244AEasy to detectImprove universalityPlatform integrity maintainanceIntel processorAttack
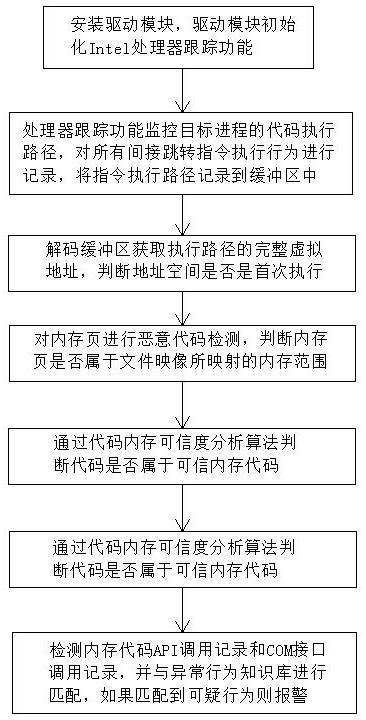
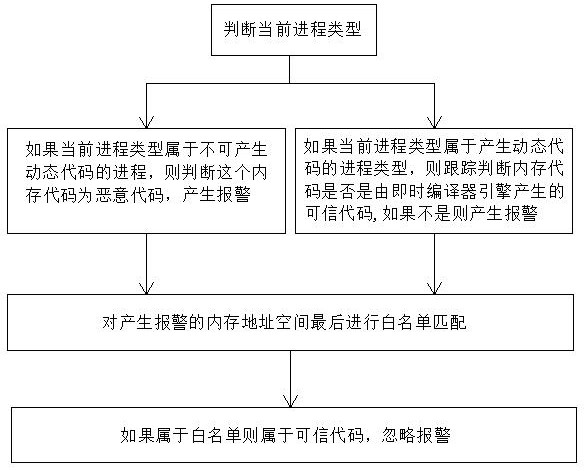
The invention discloses a memory malicious code detection method based on processor tracking, which belongs to the technical field of information security, and is characterized by comprising the following steps that: a, a driving module initializes an Intel processor tracking function; b, monitoring a code execution path of a target process; c, decoding a buffer area to obtain a complete virtual address of the execution path; d, carrying out malicious code detection on a memory page; e, judging whether the code belongs to a trusted memory code or not; and f, detecting a memory code API calling record and a COM interface calling record, and matching the memory code API calling record and the COM interface calling record with an abnormal behavior knowledge base. Common scenes such as memory codes, shelled malicious codes, encrypted malicious code viruses and Trojan horses used in file-free attacks can be detected, meanwhile, the method also has a detection effect on execution of shellcode codes in the vulnerability utilization process, the detection effect is good, and good universality is achieved.
Owner:COLASOFT
Shellcode detection method based on virtual execution
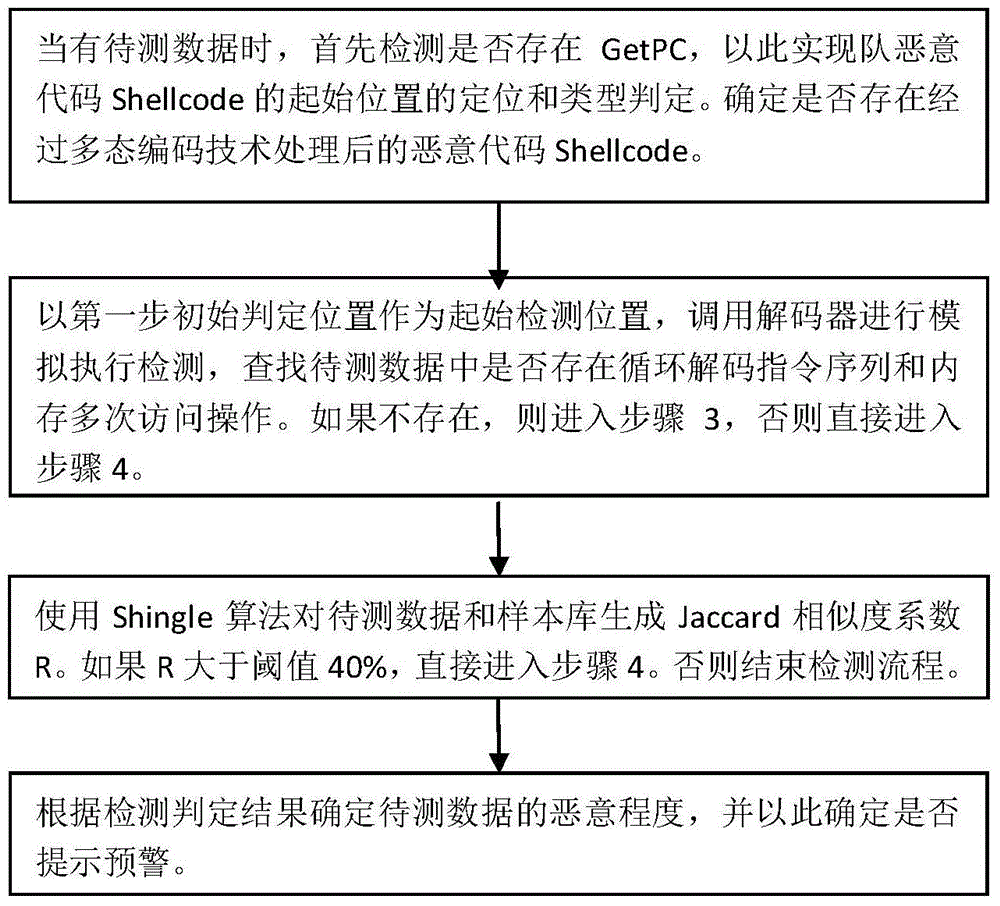
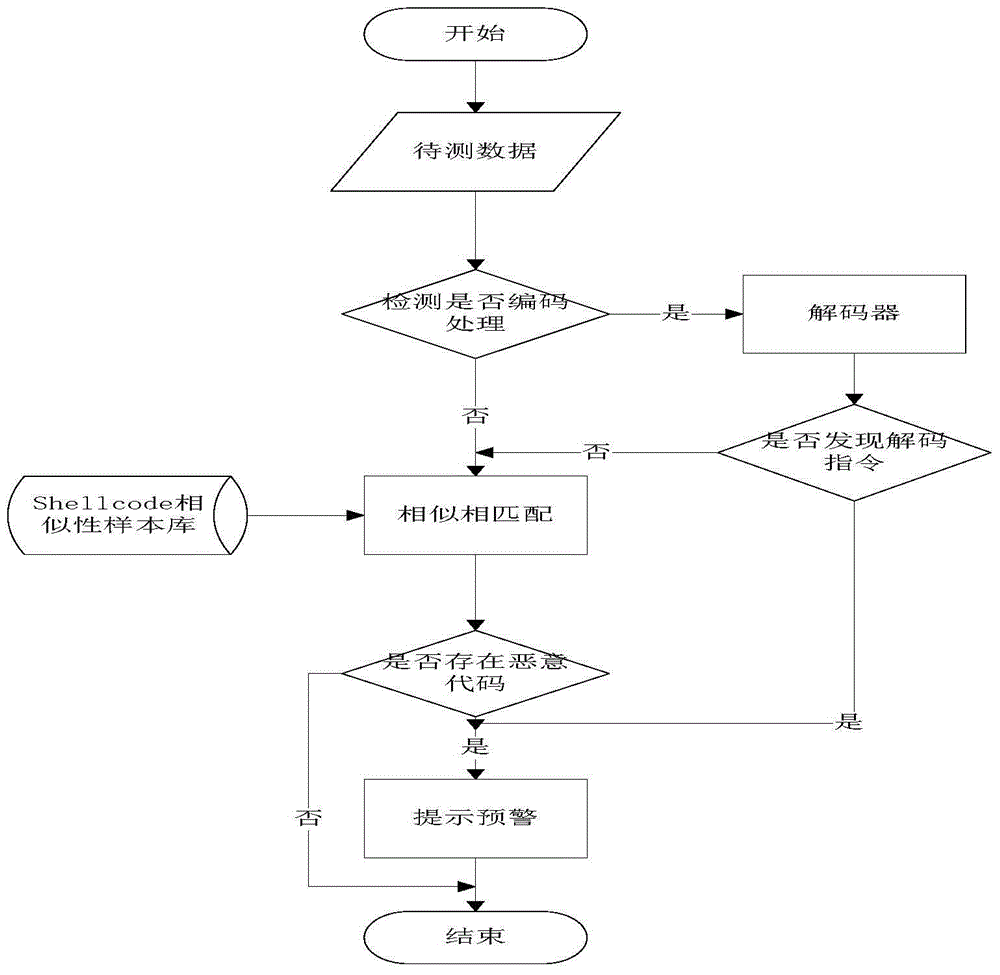
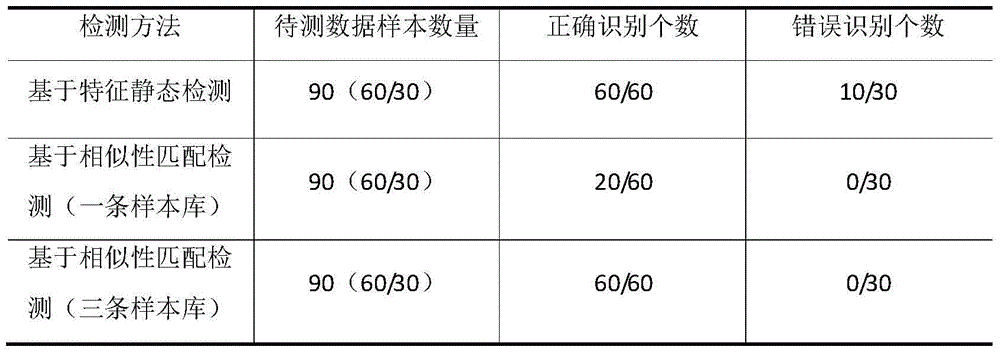
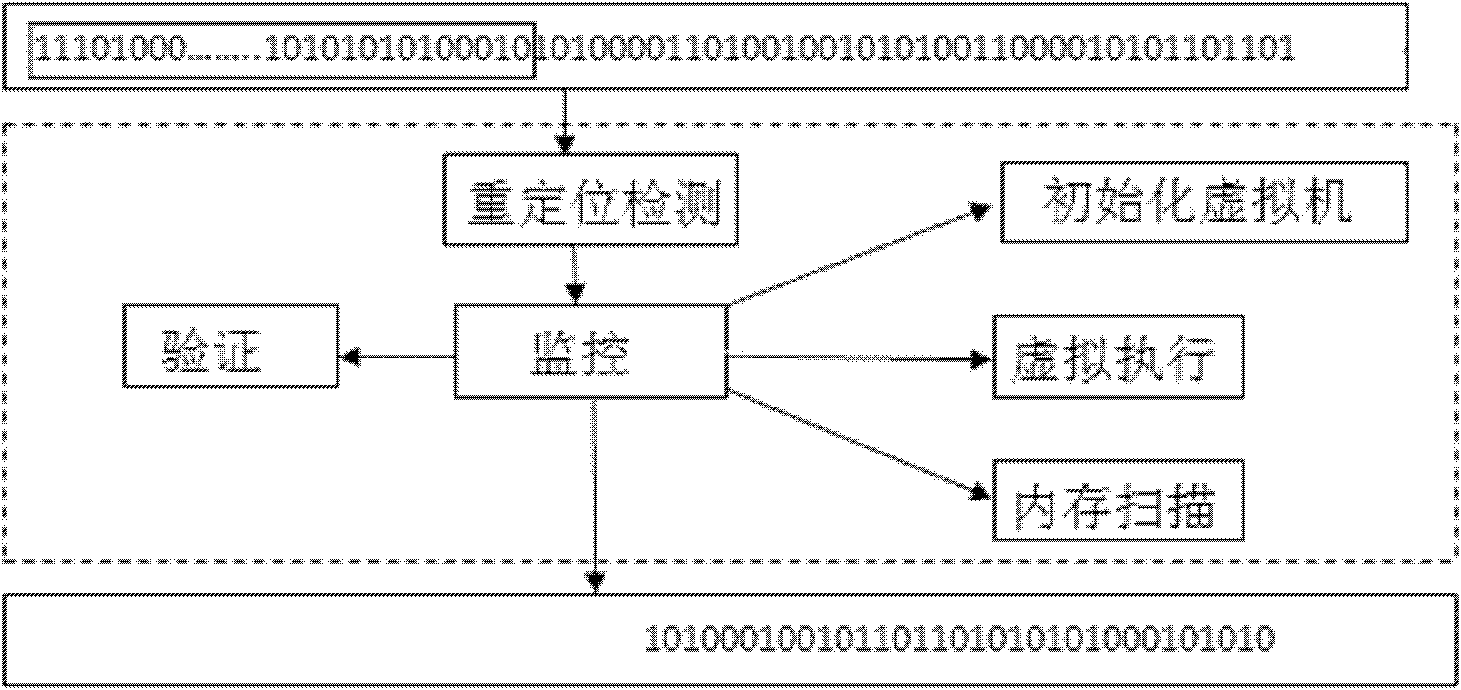
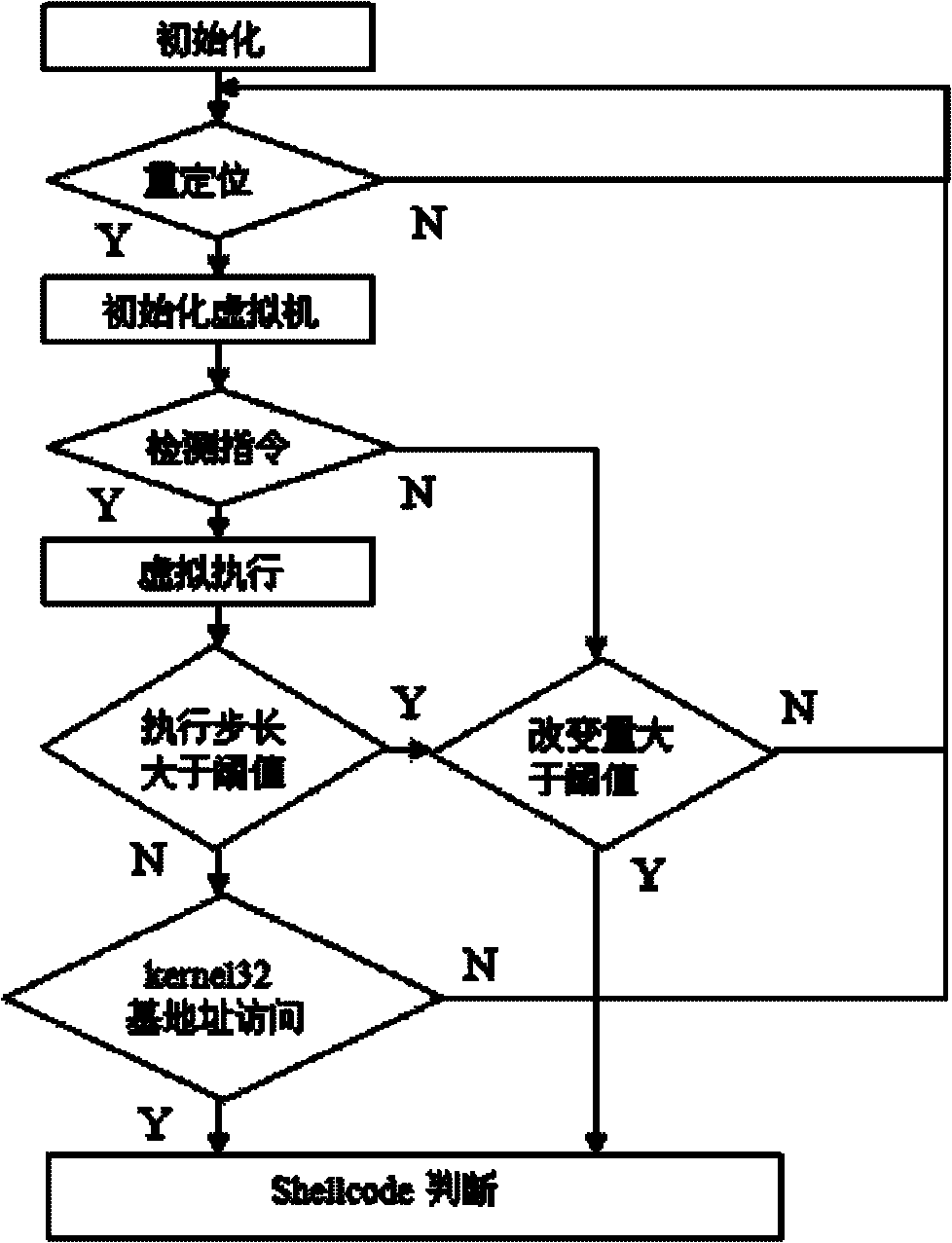
InactiveCN102223384AQuick checkTo achieve the purpose of overflow attack defensePlatform integrity maintainanceTransmissionShellcodeByte
The invention discloses a Shellcode detection method based on virtual execution, which comprises the following steps of putting a network byte stream in a virtual machine to be subject to controlled execution, monitoring the execution process, and judging whether the Shellcode exists or not according to the characteristics existing in the execution process. For the Shellcode using polymorphic technology, a user can get good detection effect by using the method, and the information safety of the user can be ensured.
Owner:THE THIRD RES INST OF MIN OF PUBLIC SECURITY
ShellCode detecting method and device
ActiveCN104008336AAvoid influencePrevent malicious tamperingPlatform integrity maintainanceShellcodeInstruction sequence
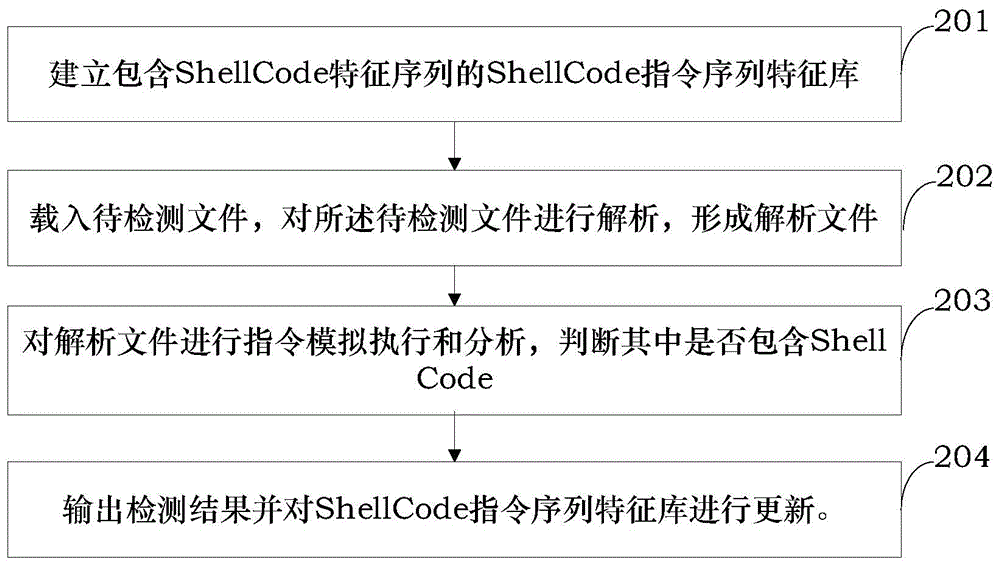
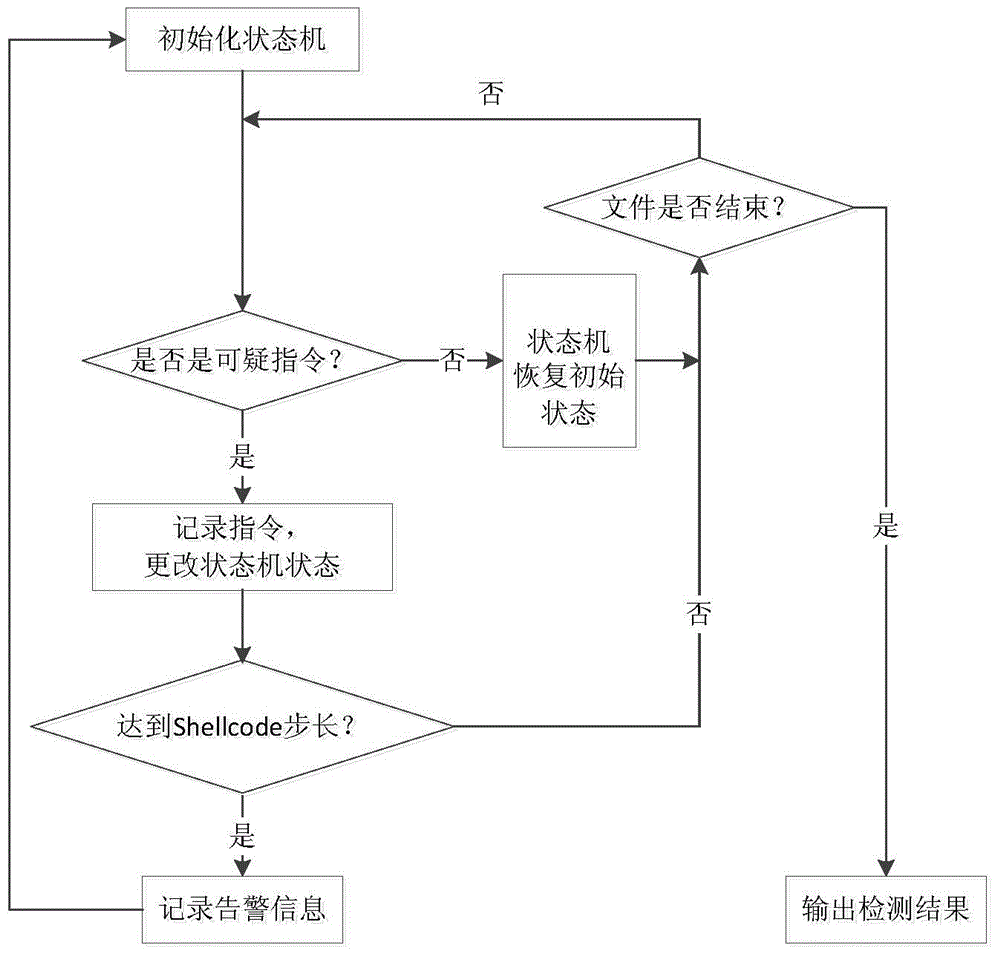
The invention provides a ShellCode detecting method and device. The method comprises the steps of establishing a ShellCode instruction sequence feature library containing a ShellCode feature sequence; loading a file to be detected and analyzing the file to be detected to obtain an analyzed file; conducting simulated instruction execution and analysis on the analyzed file, recording suspicious instruction sequences, comparing the suspicious instruction sequences with the ShellCode feature sequence in the ShellCode instruction sequence feature library, and judging whether the analyzed file contains the ShellCode; outputting a detection result. According to the ShellCode detecting method and device, detection can be conducted before ShellCode execution, the influence of the ShellCode on a system is prevented, and malicious tampering is prevented in time.
Owner:INST OF INFORMATION ENG CAS
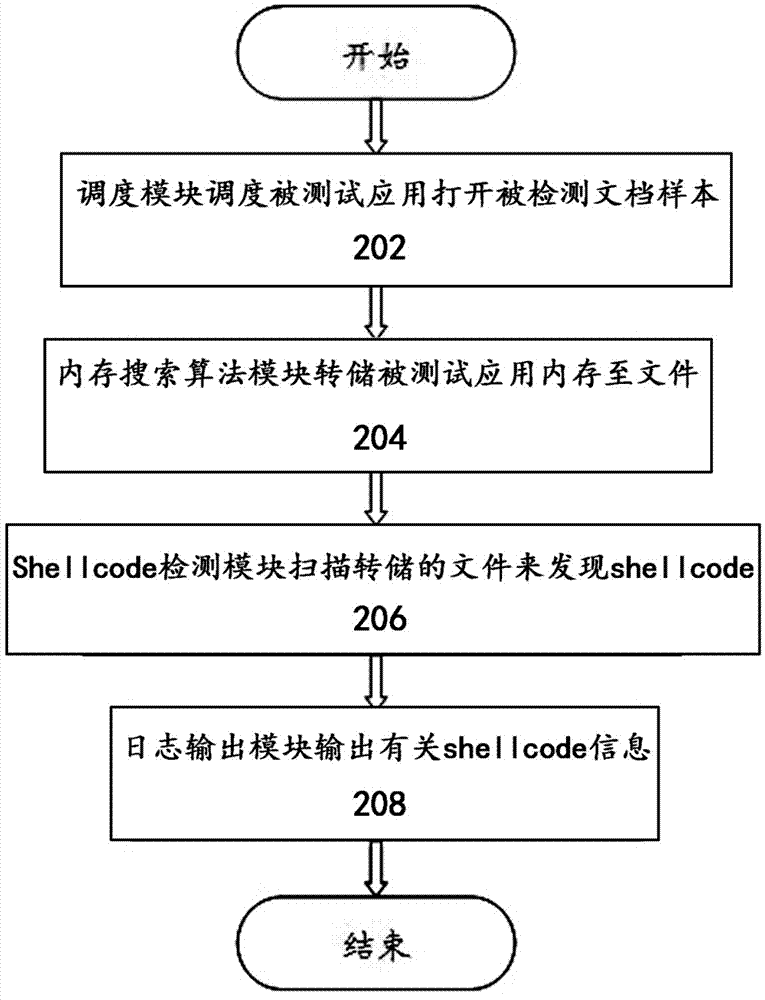
Detecting system and method for shellcode based on memory searching
InactiveCN103049701AImprove detection rateNo confrontation problemPlatform integrity maintainanceShellcodeDetection rate
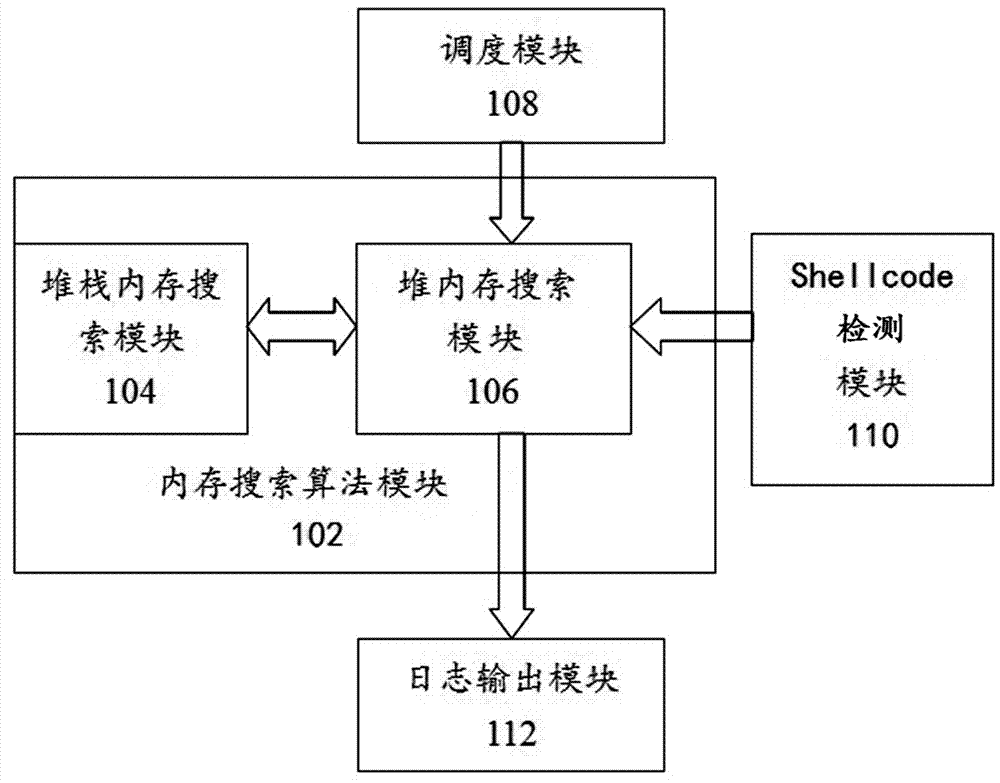
The invention discloses a detecting system for shellcode based on memory searching. The detecting system for shellcode includes a detected sample scheduling module, a memory searching algorithm module, a shellcode detecting module and a log module. A detecting method for shellcode includes the following steps: (1) the scheduling module schedules a tested application to open a detected document sample, (2) the memory searching algorithm module dumps memory of detected application to a file or performing memory searching directly, (3) shellcode detecting module scans the dumped file to find shellcode, and (4) the log output module outputs information related to shellcode. The detecting system and method for shellcode has the advantages of performing shellcode detection after being based on memory searching, being capable of detecting codes and encrypted and hidden shellcode of complicated application file formats so that a detection rate of malicious attack samples is raised greatly and an false positive rate and an false negative rate of malicious attack samples are lowered effectively.
Owner:ALIBABA (CHINA) CO LTD
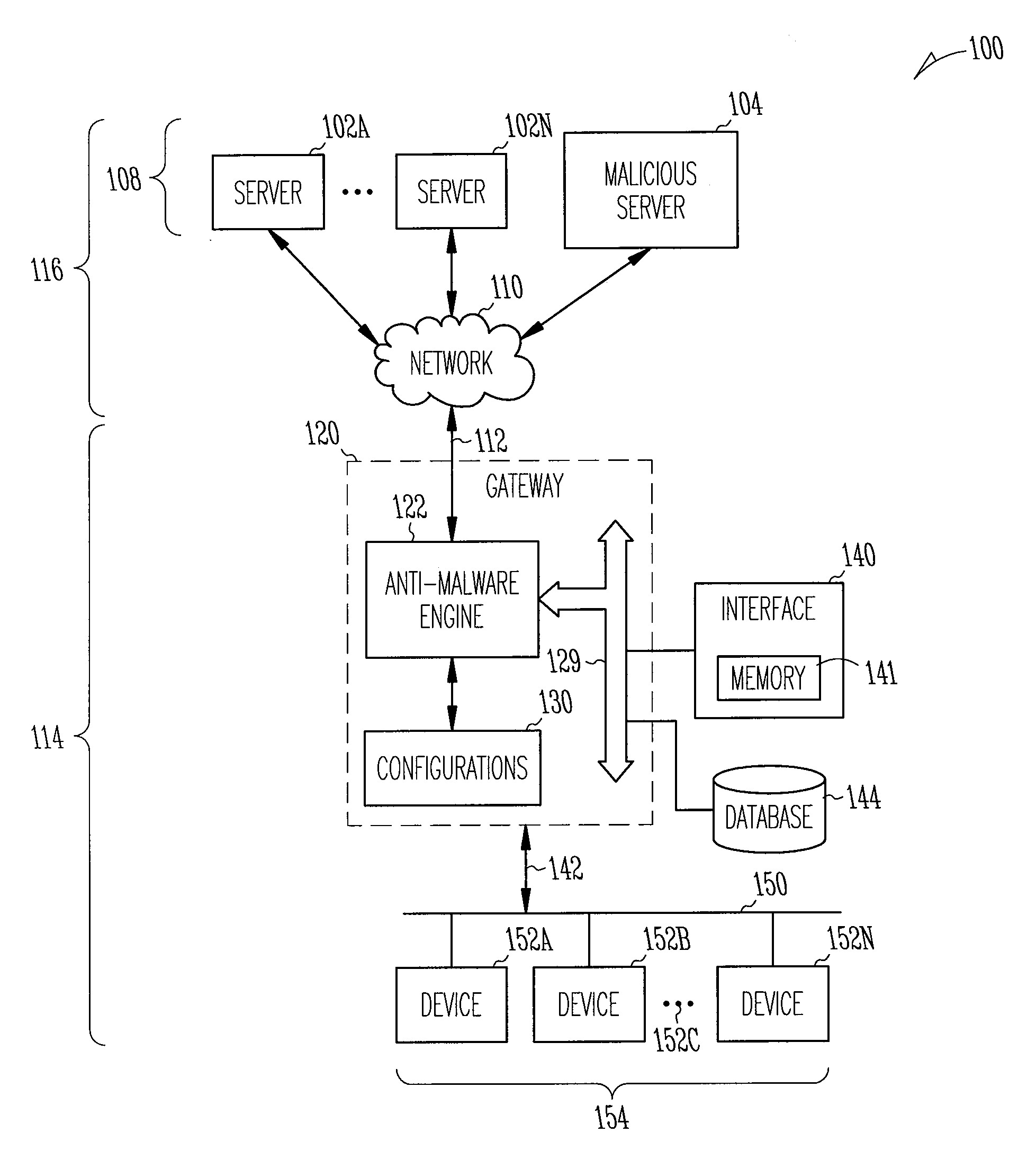
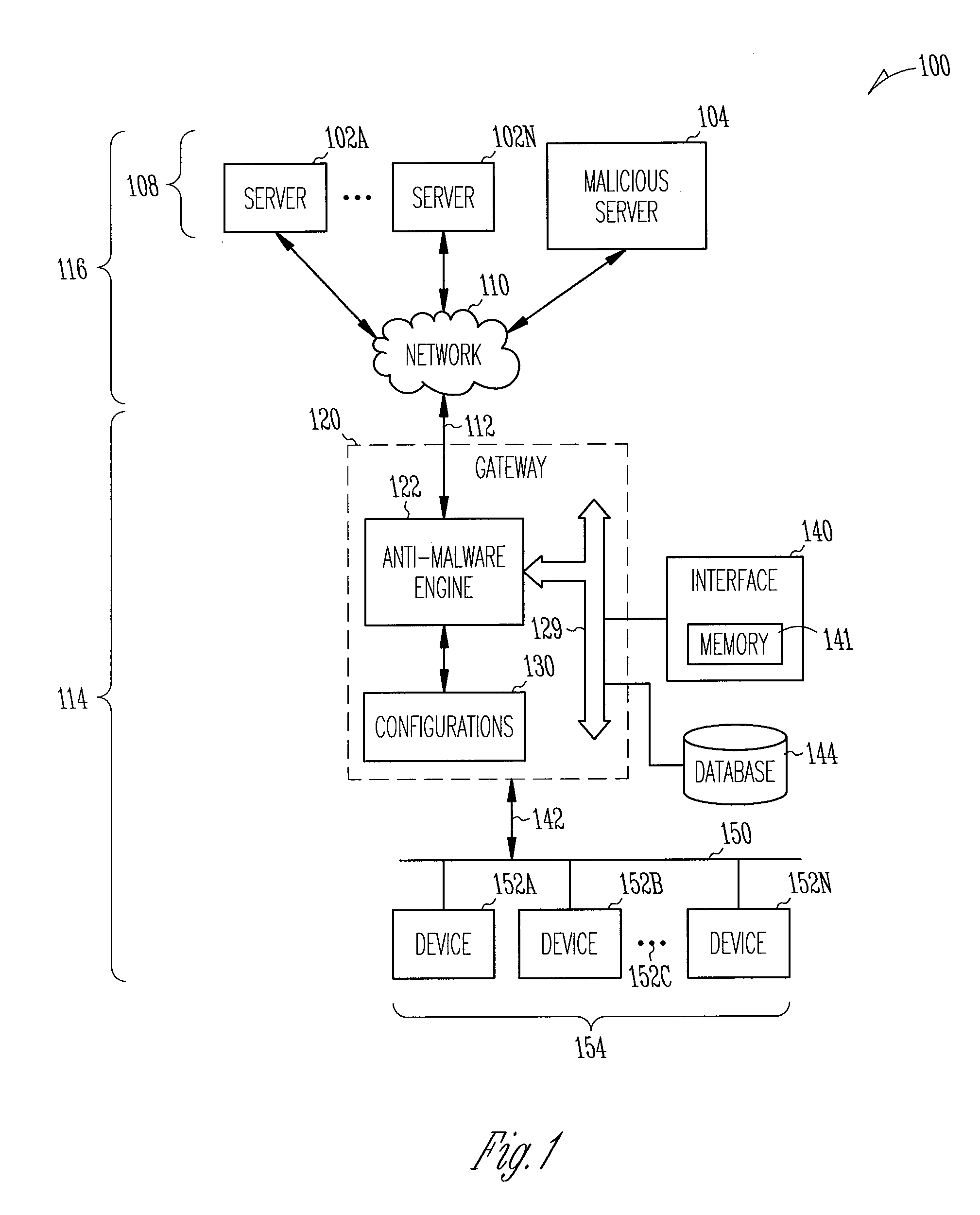
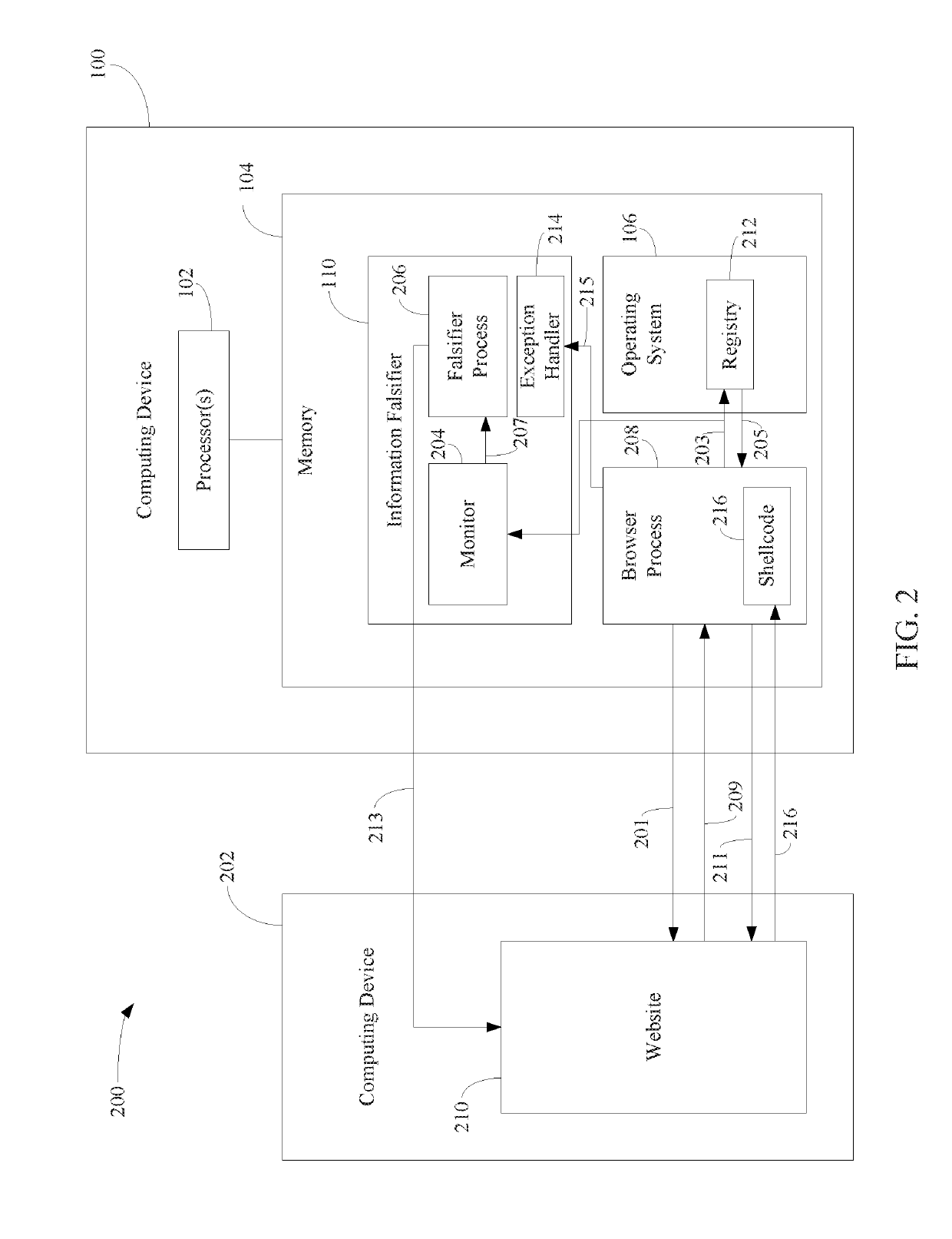
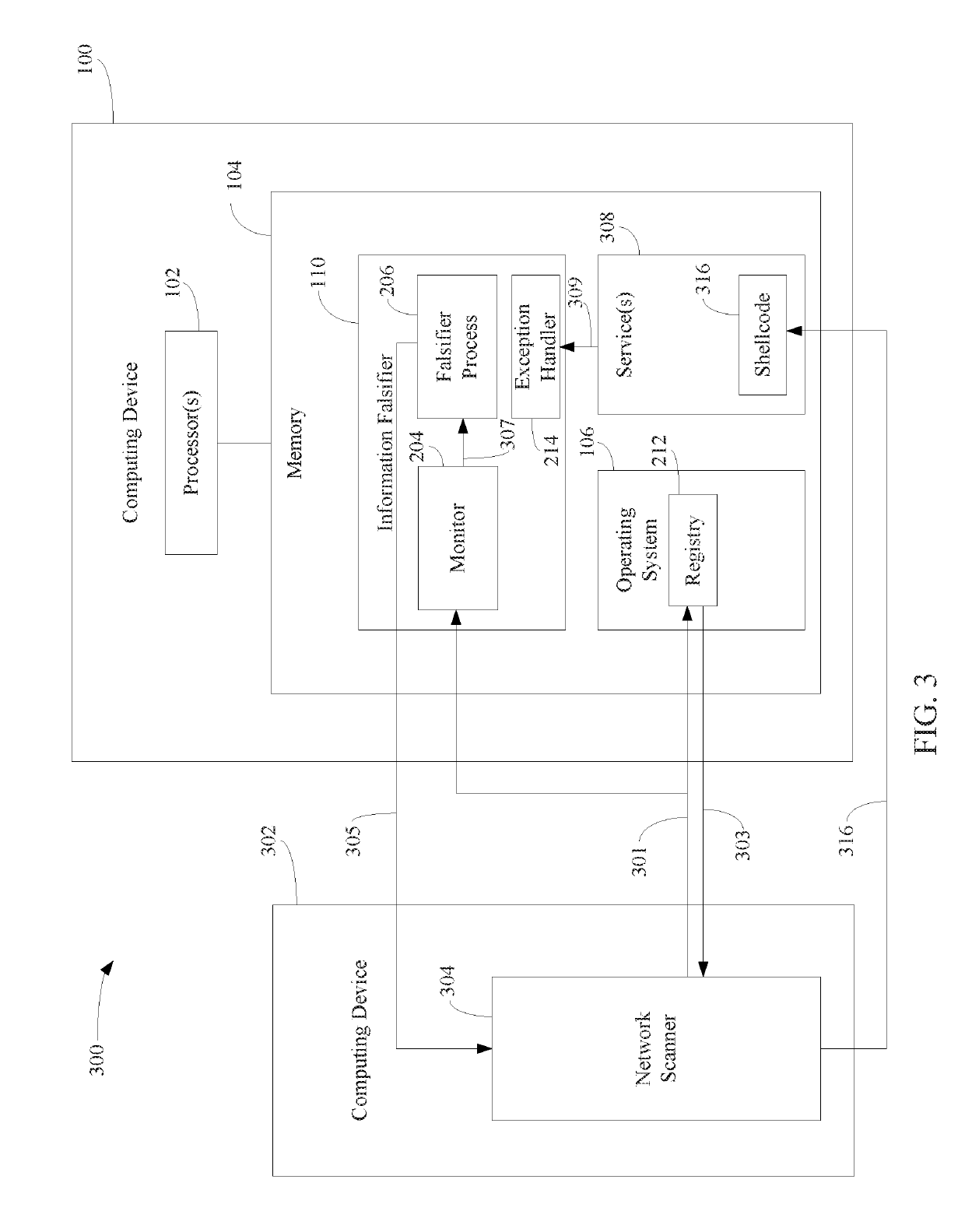
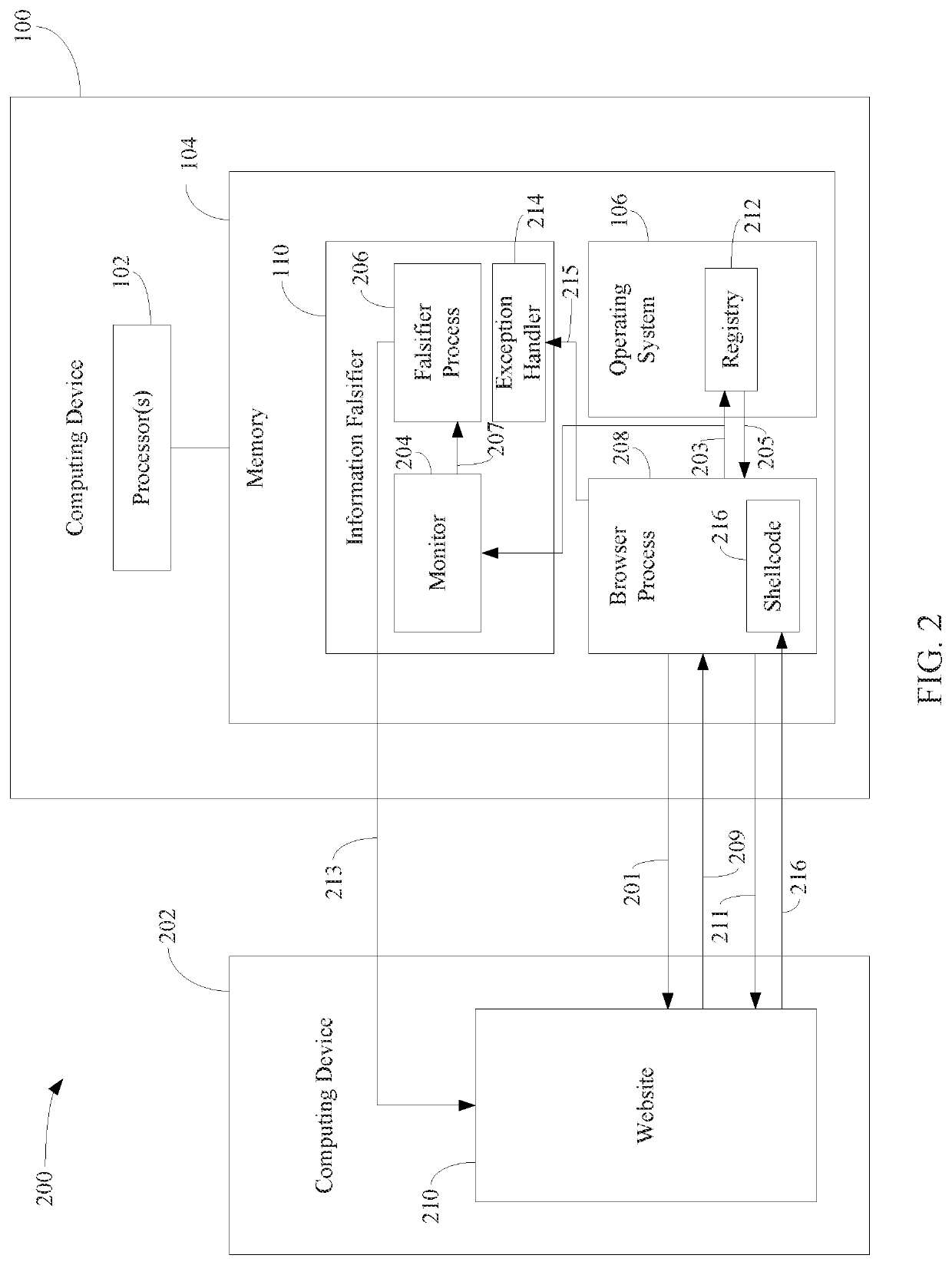
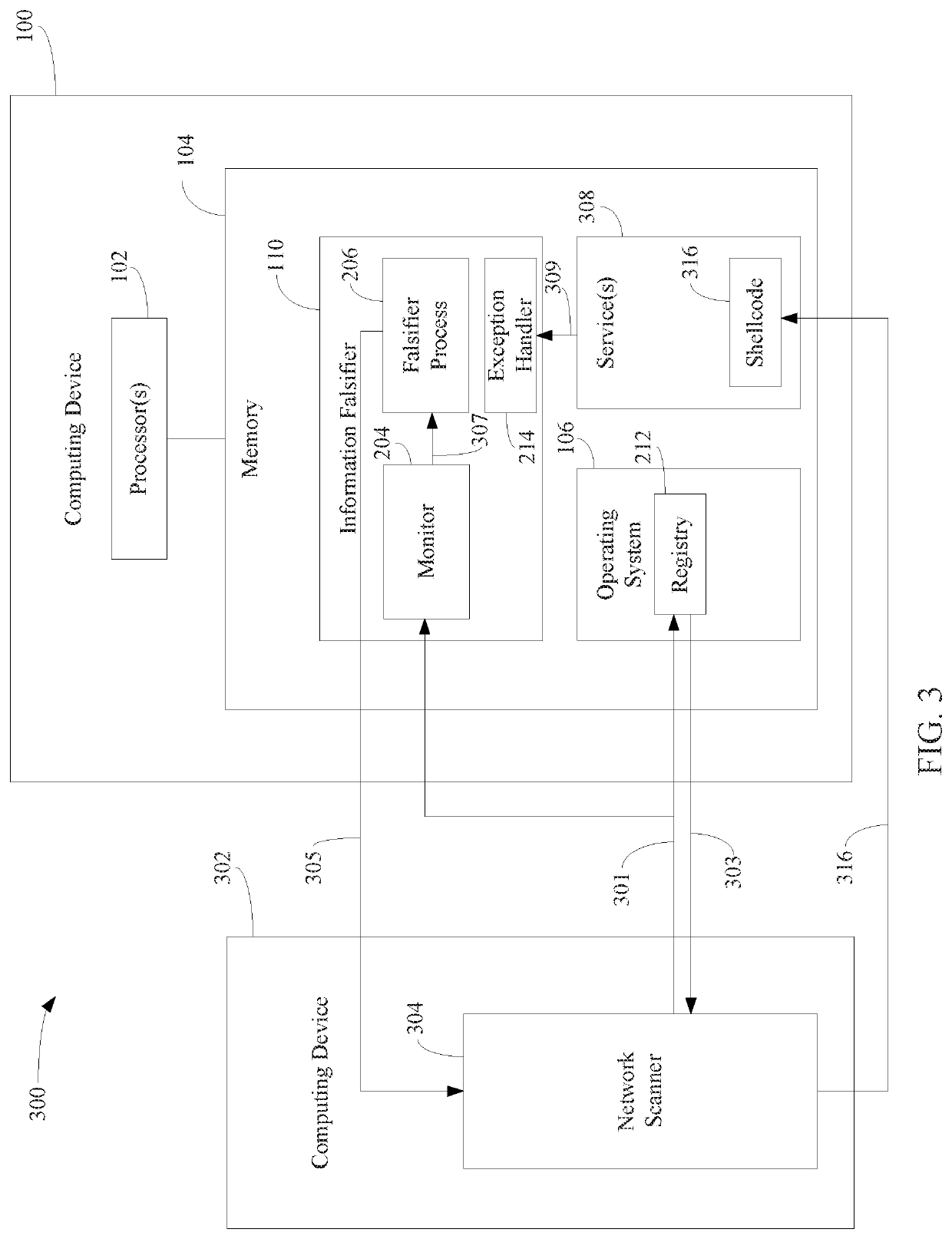
Protecting computing devices from a malicious process by exposing false information
Various automated techniques are described herein for protecting computing devices from malicious code injection and execution by providing a malicious process with incorrect information regarding the type and / or version and / or other characteristics of the operating system and / or the targeted program and / or the targeted computing device. The falsified information tricks the malicious process into injecting shellcode that is incompatible with the targeted operating system, program and / or computing device. When the incompatible, injected shellcode attempts to execute, it fails as a result of the incompatibility, thereby protecting the computing device.
Owner:MORPHISEC INFORMATION SECURITY 2014
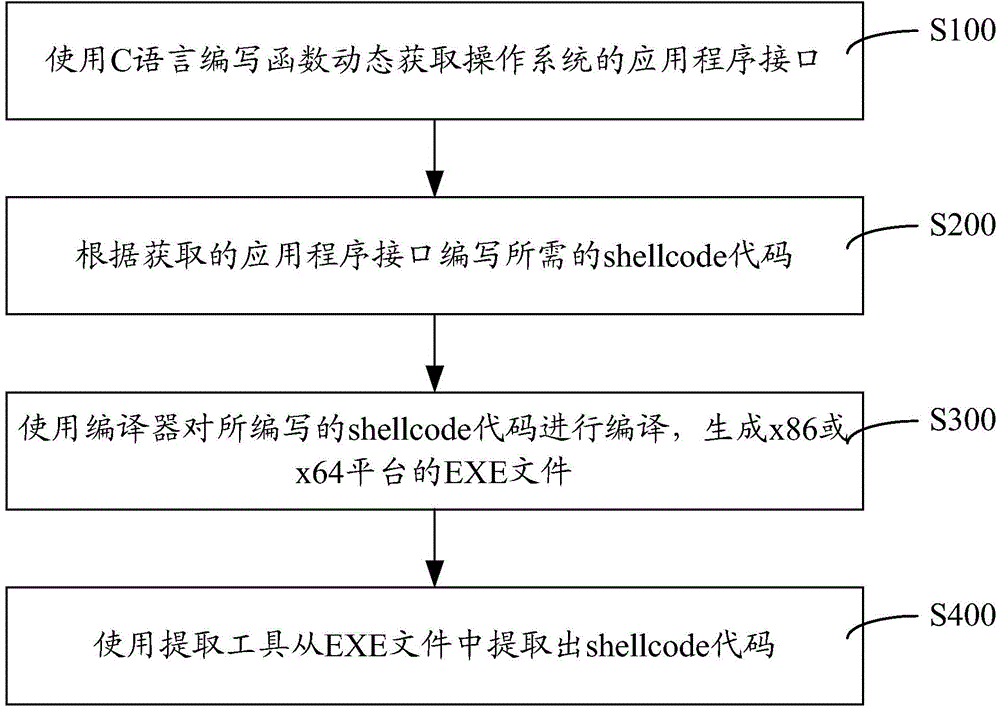
Method and system for developing shellcode of *86 platform or *64 platform fast
InactiveCN105487846AFast writing speedUnified maintenance is easyPlatform integrity maintainanceSpecific program execution arrangementsApplication programming interfaceShellcode
The invention discloses a method and a system for developing a shellcode of a *86 platform or a *64 platform fast. The method comprises the following steps: writing a function according to C language, and dynamically acquiring an application programming interface (API); writing the shellcode according to the acquired API; compiling the written shellcode with a compiler, so as to generate an EXE file of the *86 platform or the *64 platform; and extracting the shellcode from a code section of the EXE file with an extracting tool. As the writing of the shellcode is based on C language which is relatively high in level, the code developing speed is fast; and the API is acquired dynamically based on the function written according to C language, so as to adopt to the *86 platform or the *64 platform automatically. Therefore, a developing personnel can maintain shellcodes of the *86 platform and the *64 platform in a unified manner; and the shellcodes are easy to develop and maintain, and are unified, while complex functions can be realized easily.
Owner:STATE GRID CORP OF CHINA +1
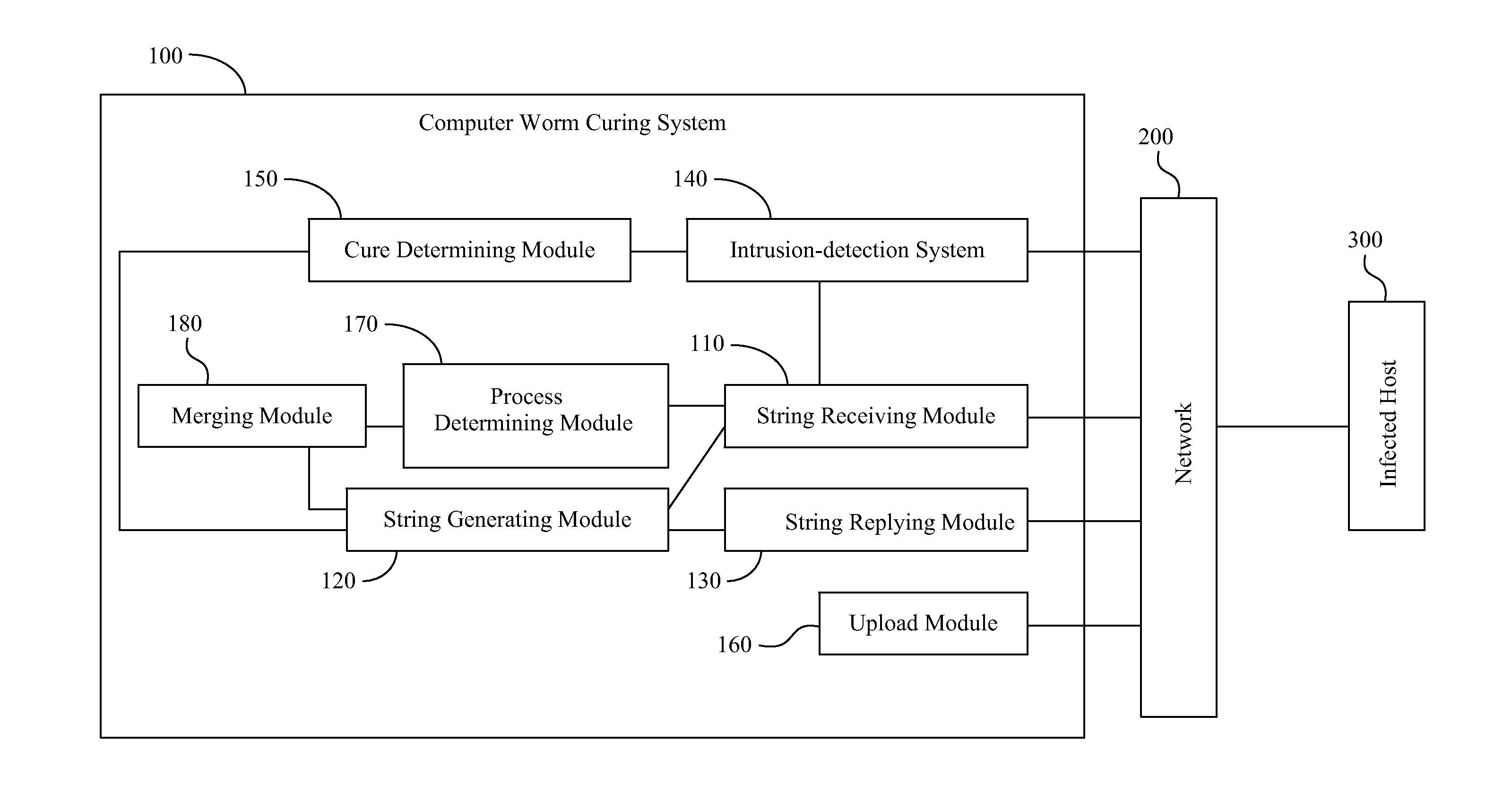
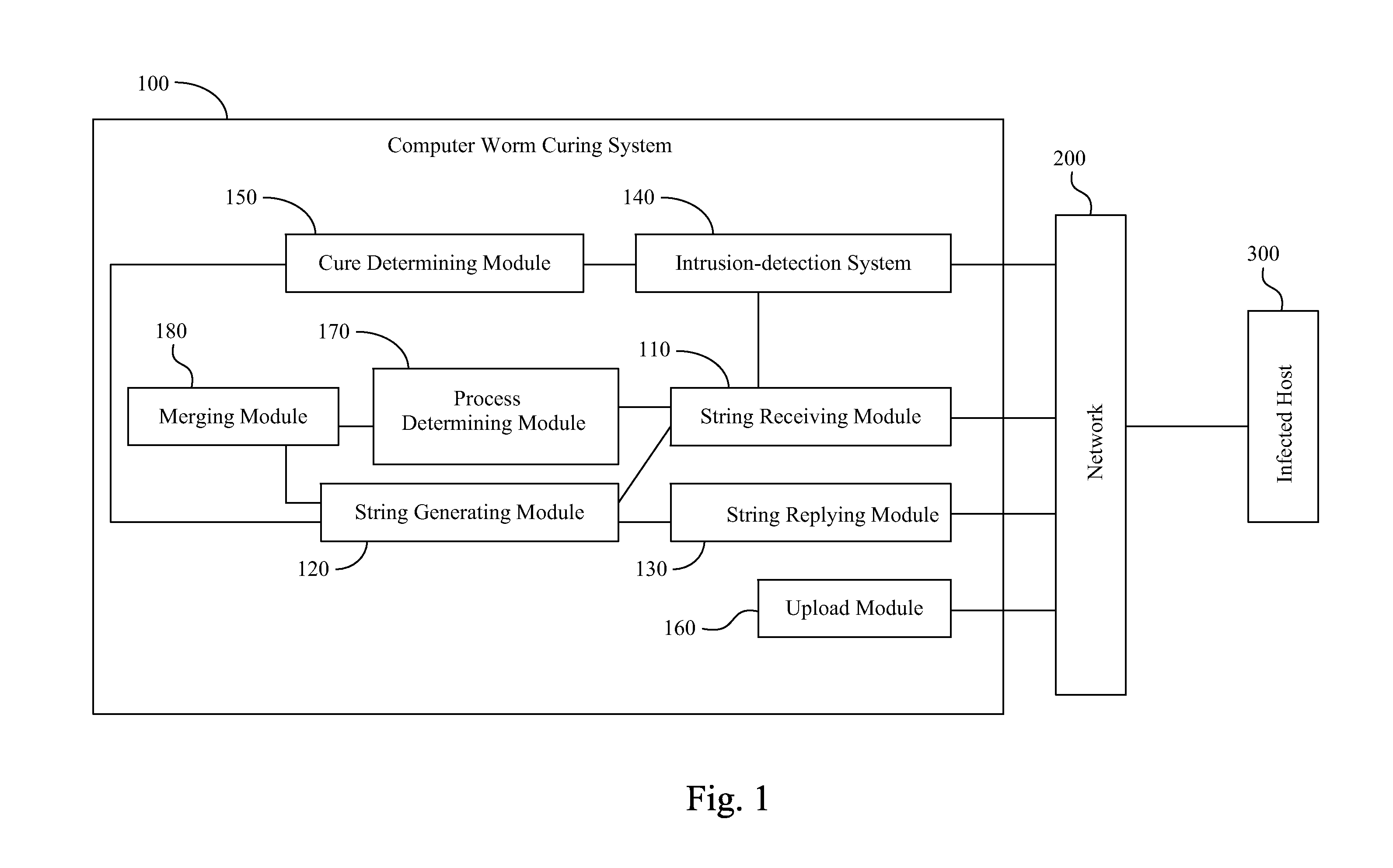
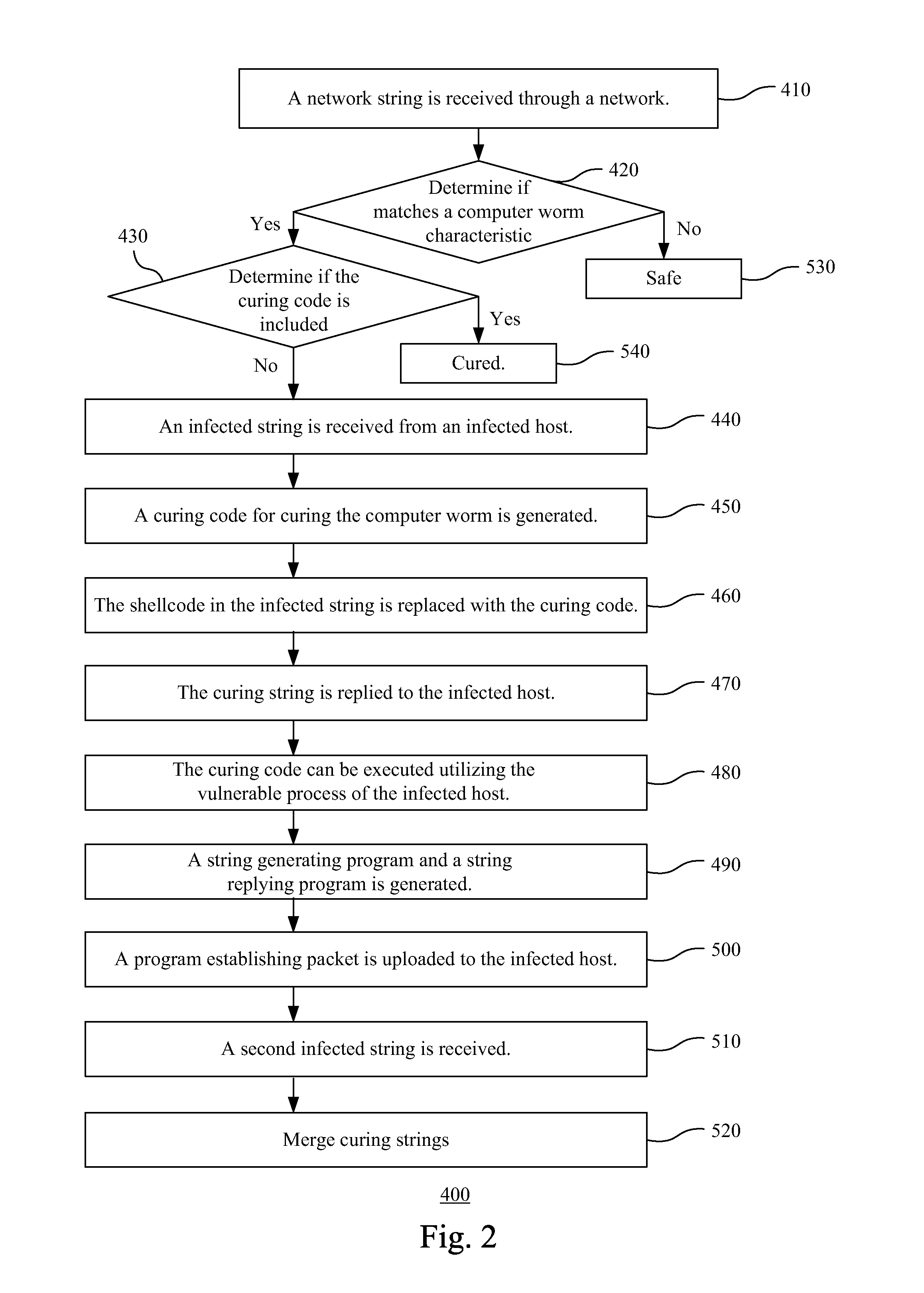
Computer Worm Curing System and Method and Computer Readable Storage Medium for Storing Computer Worm Curing Method
InactiveUS20120117647A1Save resourcesReduce bandwidth for transmittingMemory loss protectionError detection/correctionComputer wormTheoretical computer science
A computer worm curing system includes a string receiving module, a string generating module and a string replying module. The string receiving module receives an infected string, which is generated by a computer worm, from an infected host, which is infected by the computer worm, through a network. The infected string includes a shellcode, and the shellcode is executed utilizing a vulnerable process. The string generating module generates a curing code for curing the computer worm, and replaces the shellcode in the infected string with the curing code to generate a curing string, such that the curing string can be executed utilizing the vulnerable process. The string replying module replies the curing string to the infected host, such that the curing code of the curing string can be executed utilizing the vulnerable process of the infected host to cure the infected host of the computer worm.
Owner:INSTITUTE FOR INFORMATION INDUSTRY
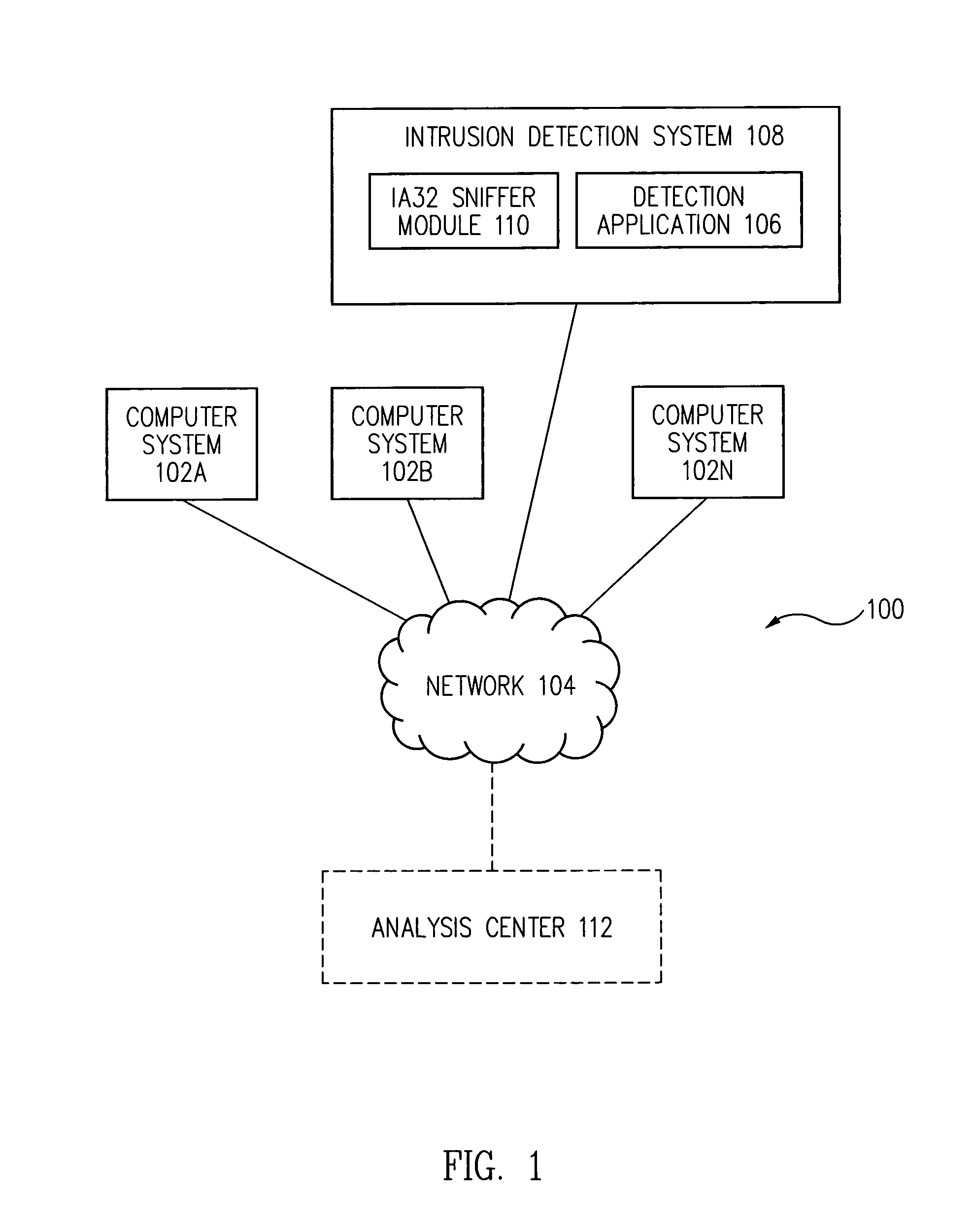
Communication monitoring system, communication monitoring apparatus and communication control apparatus
InactiveUS20080215721A1Early detectionIncrease probabilityDigital computer detailsPlatform integrity maintainanceShellcodeMonitoring system
A communication monitoring apparatus for monitoring communication data which are transmitted among a plurality of nodes on a network, includes a detecting section for detecting whether or not a shellcode is included in communication data transmitted and received between at least two nodes within the plurality of nodes and a storing section for storing communication data transmitted from the two nodes as being starting points during a predetermined time, when the detecting section detected the shellcode in communication data.
Owner:SECUREWARE INC
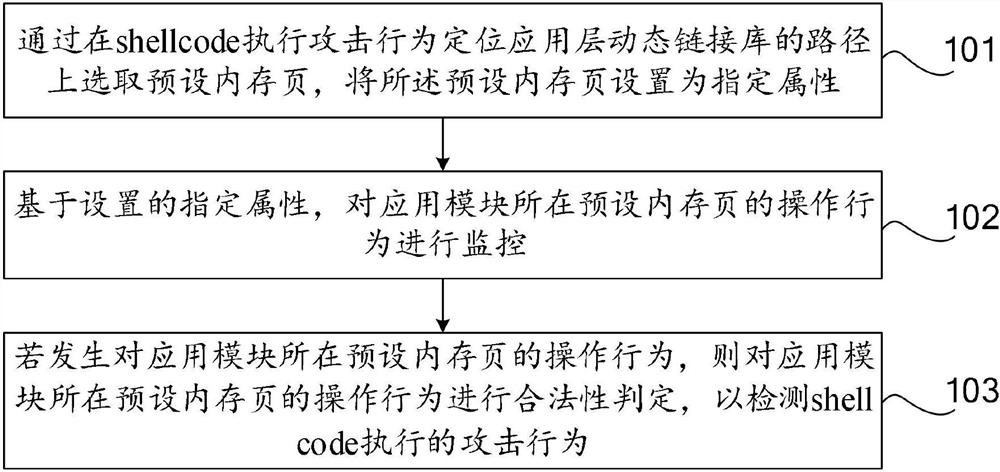
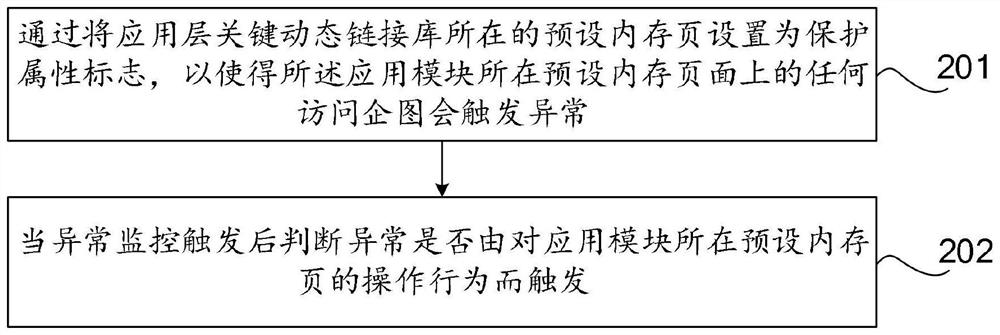
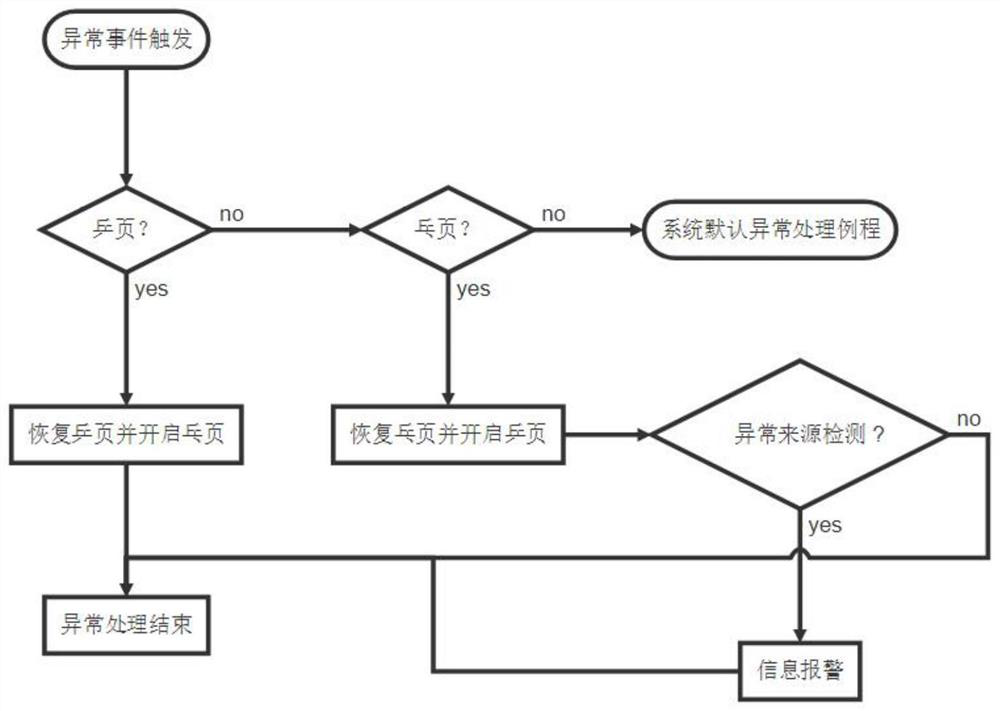
An application layer shellcode detection method and device
ActiveCN112395609AAttack Behavior DiscoveryPerform discoveryPlatform integrity maintainanceTransmissionPathPingOperational system
The invention discloses an application layer shellcode detection method and device, computer equipment and a computer storage medium, relates to the technical field of information network security, and aims to monitor a specific memory page of an application layer of an operating system, detect abnormal operation behaviors in time and effectively discover application layer shellcode attack behaviors. The method comprises the following steps: selecting a preset memory page on a path of a key dynamic link library of a shellcode execution attack behavior positioning application layer, and settingthe preset memory page as a specified attribute; monitoring an operation behavior of a preset memory page where the application module is located based on the set specified attribute; and if the access attempt to the preset memory page where the application module is located occurs, performing legality judgment on the access behavior to detect an attack behavior executed by the shellcode.
Owner:QI AN XIN SECURITY TECH ZHUHAI CO LTD +1
Method for detecting web page Trojan horse based on program execution characteristics
InactiveCN101673326BReduce missed detection rateReduce false detection ratePlatform integrity maintainanceSpecial data processing applicationsShellcodeBuffer overflow
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Protecting computing devices from a malicious process by exposing false information
Various automated techniques are described herein for protecting computing devices from malicious code injection and execution by providing a malicious process with incorrect information regarding the type and / or version and / or other characteristics of the operating system and / or the targeted program and / or the targeted computing device. The falsified information tricks the malicious process into injecting shellcode that is incompatible with the targeted operating system, program and / or computing device. When the incompatible, injected shellcode attempts to execute, it fails as a result of the incompatibility, thereby protecting the computing device.
Owner:MORPHISEC INFORMATION SECURITY 2014
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com