Malicious code tracking and recognizing method based on memory protection type monitoring
A malicious code and protection type technology, which is applied in the field of information security, can solve the problems that the application program cannot use the protection scheme, low compatibility, and small protection coverage area, and achieve wide protection coverage area, high compatibility, and guaranteed accuracy Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0044] The present invention hijacks and modifies the system interface function of the memory protection attribute, collects and records call parameters including the executable attribute, clears the executable flag bit, intercepts the execution of the target code by monitoring exceptions, and executes it through static rules and dynamic simulation Efficient and accurate identification of vulnerability attacks and malicious codes.
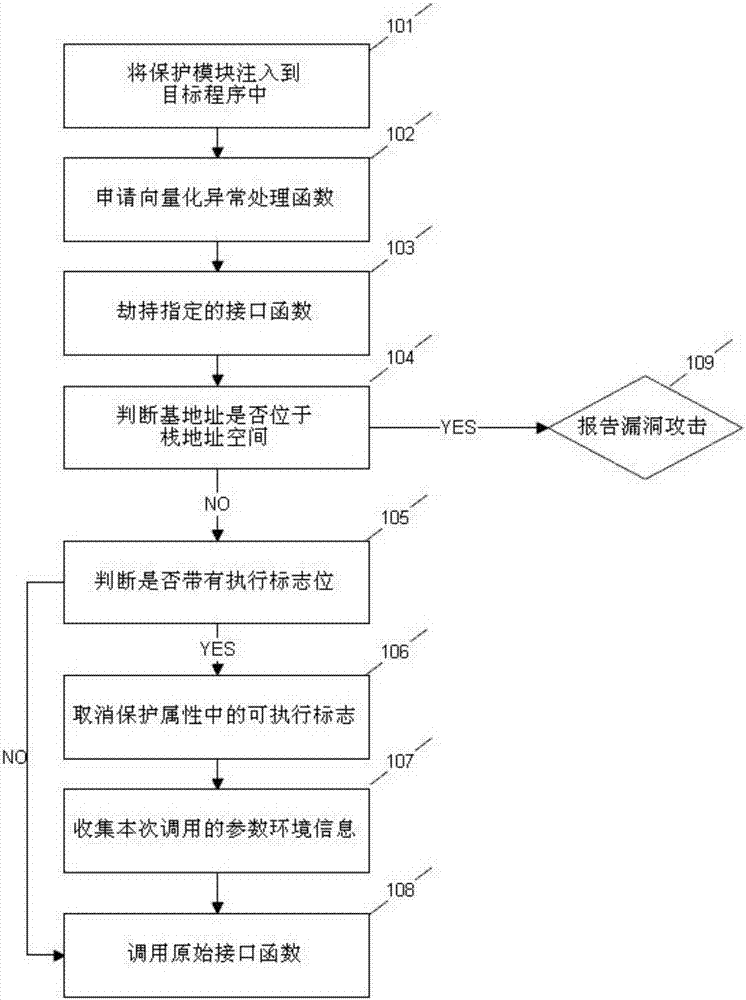
[0045] see figure 1 , is a schematic flow chart of the method of the present invention, and the specific process includes:
[0046] Step S101: Inject the protection module of the present invention into the target process.
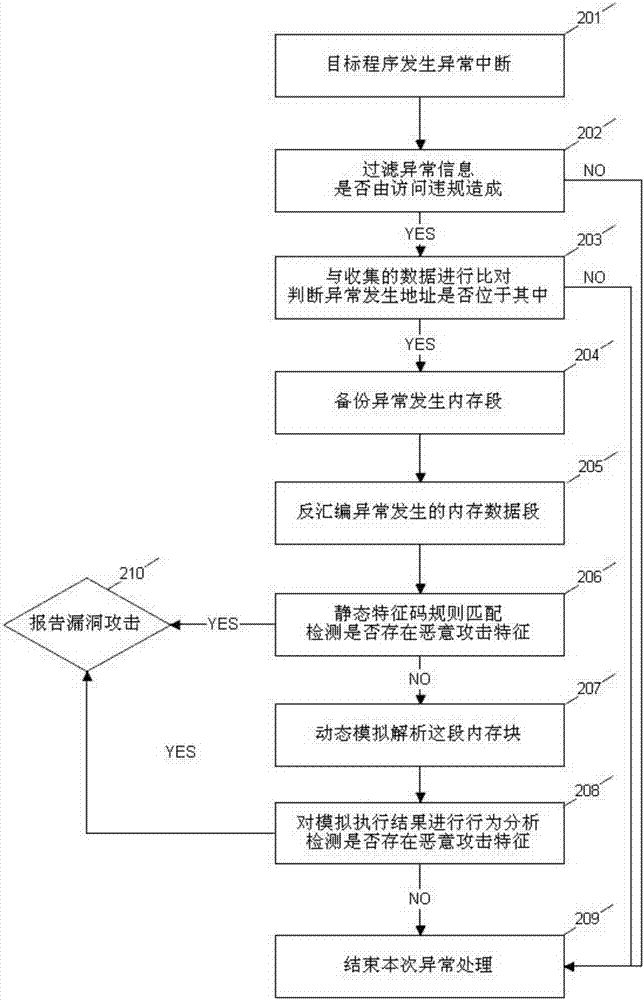
[0047]Step S102: Apply for a vectorized exception handling function in the protected target process, which is used to take over the abnormal interruption caused by the process during operation, and handle and analyze the abnormal environment. For the processing process, see reference figure 2 , divided into 10 steps S201-S210...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com