Method for detecting web page Trojan horse based on program execution characteristics
A web Trojan horse and program execution technology, applied in the field of computer security, can solve the problems of system detection speed drop, false detection, and failure to detect whether a web page is a Trojan web page, etc., so as to improve detection speed, reduce missed detection rate and false detection rate effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0036] In today's network environment, there are a large number of websites with Trojan horses. In order to avoid the detection of mainstream detectors, Trojan horse manufacturers have made a series of careful modifications to the code of web pages containing Trojan horses to realize the detection of the functional codes of Trojan horses. Hiding, such as source-level deformation avoidance, variable name replacement, etc.
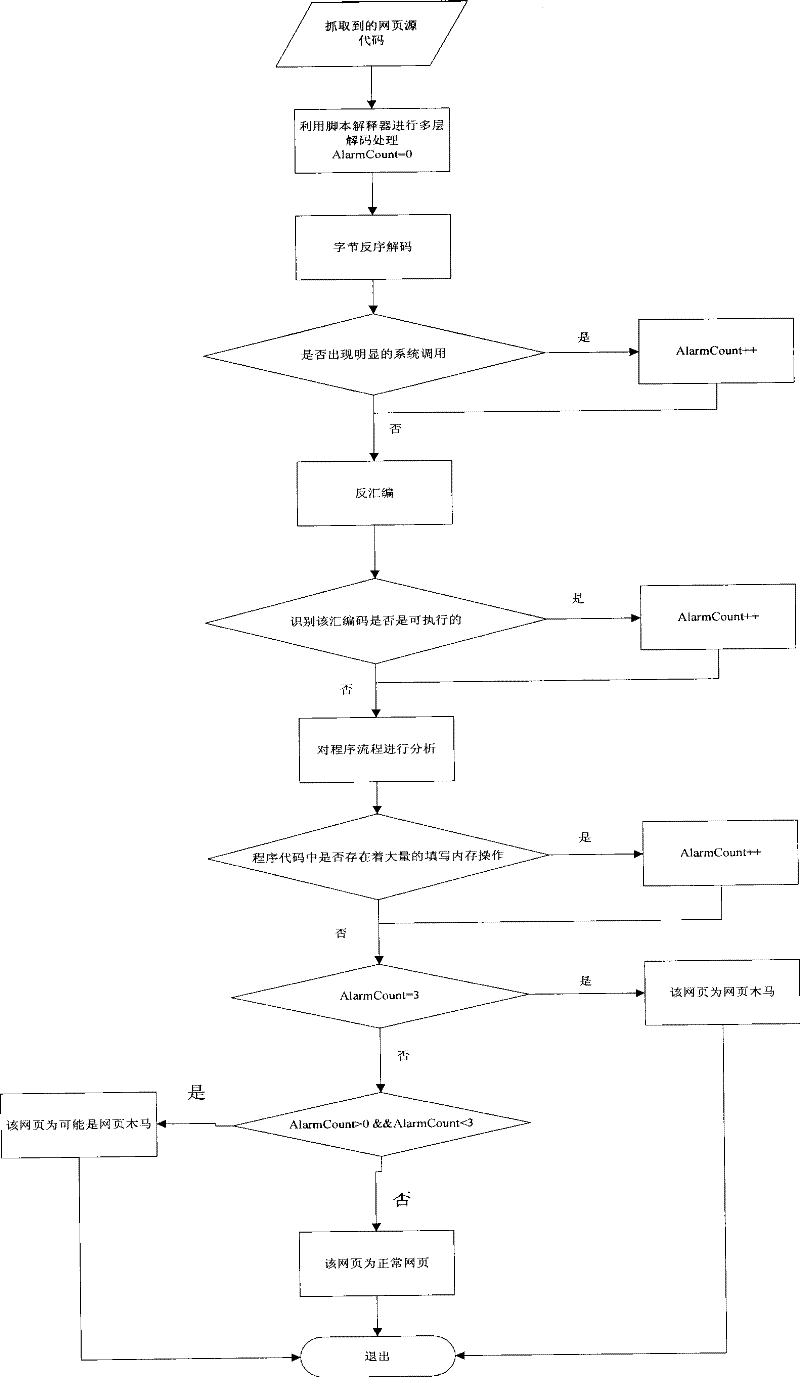
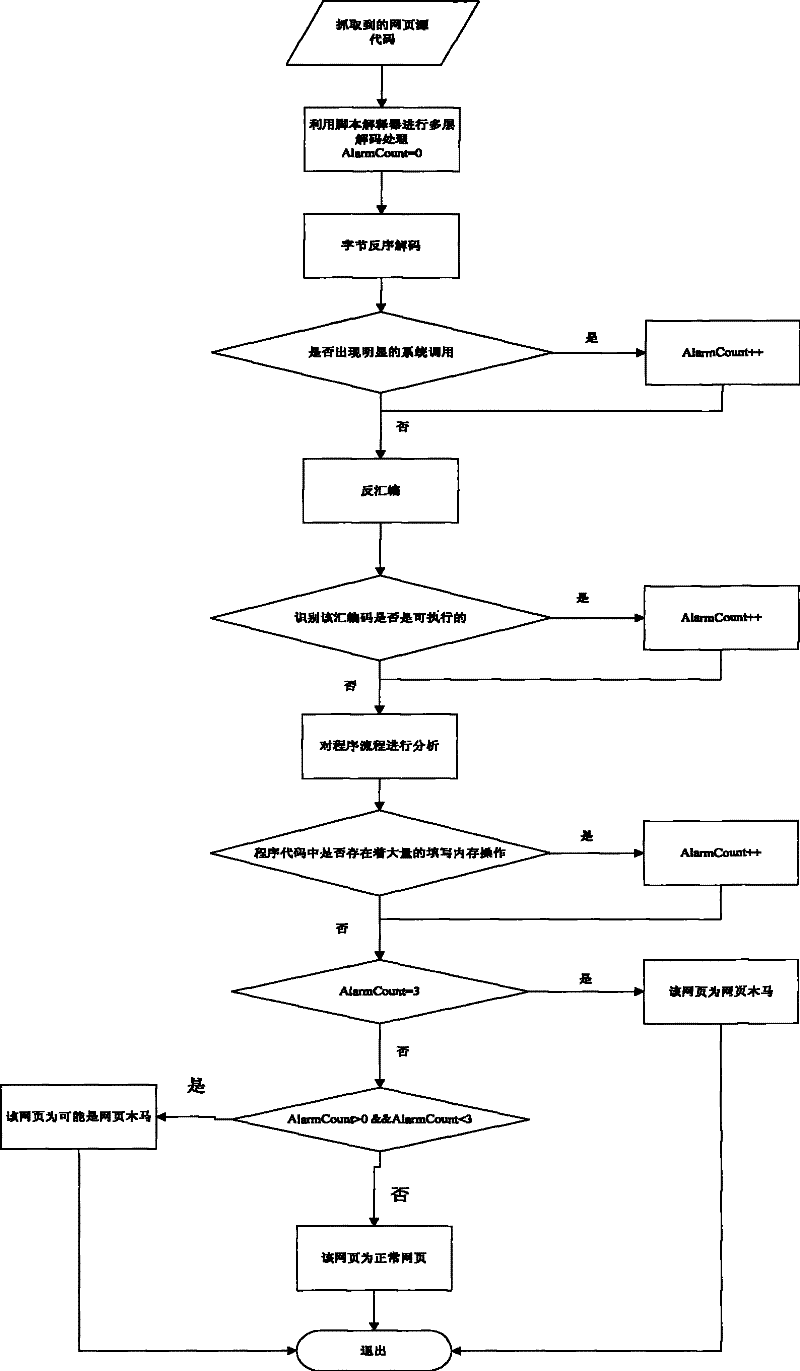
[0037] Therefore, at this time, simply relying on the feature library of the detector to detect web page Trojans will greatly increase the false negative rate. A webpage Trojan horse detection method based on program execution characteristics proposed by the present invention analyzes the webpage to be checked from the perspective of the operation mechanism of the webpage Trojan horse, rather than simple pattern matching, so it has certain intelligence. The specific implementation process is as follows figure 1 shown.
[0038] Specific embodiment: divided ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com