Patents
Literature
72 results about "Memory code" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
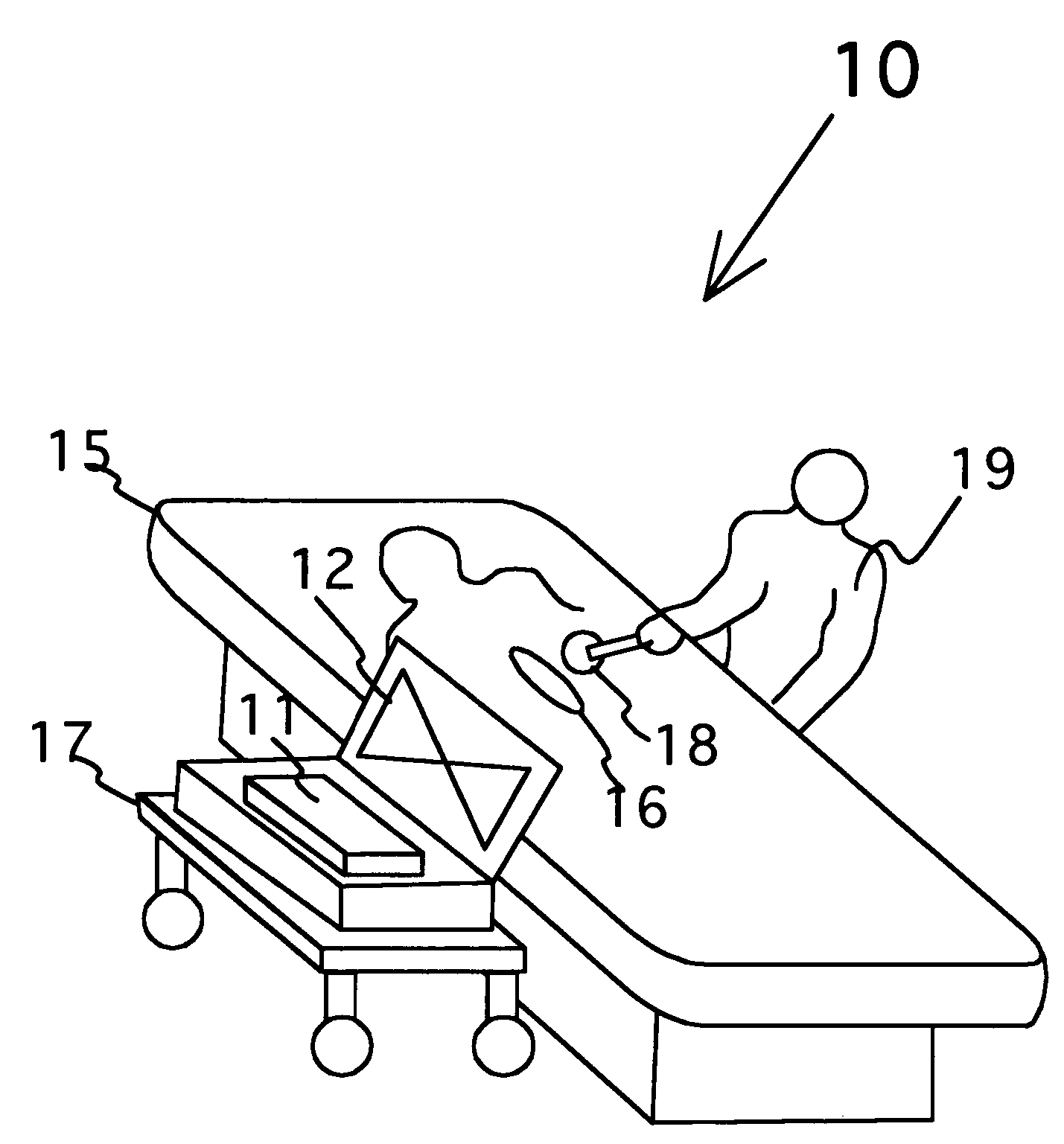
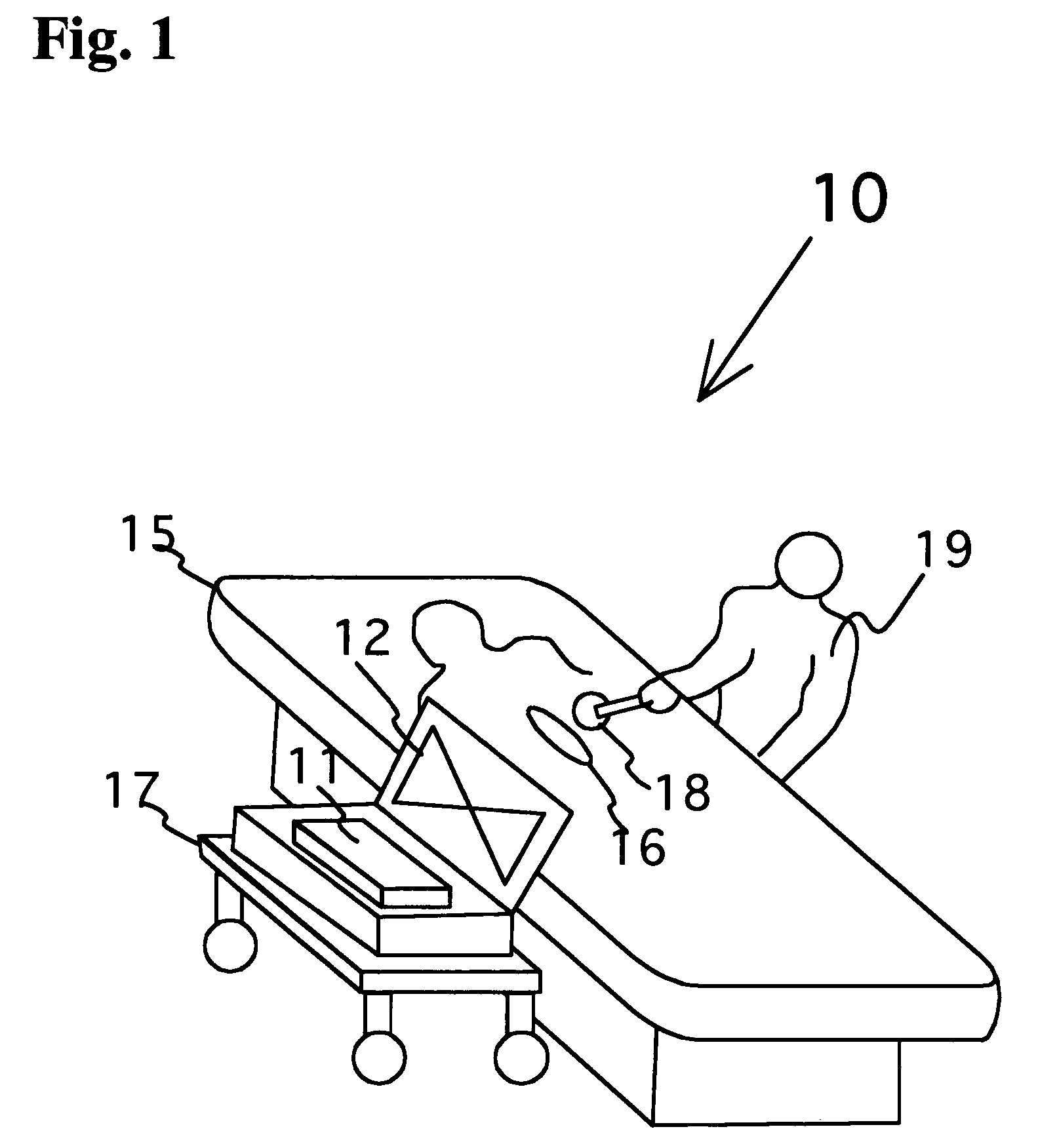
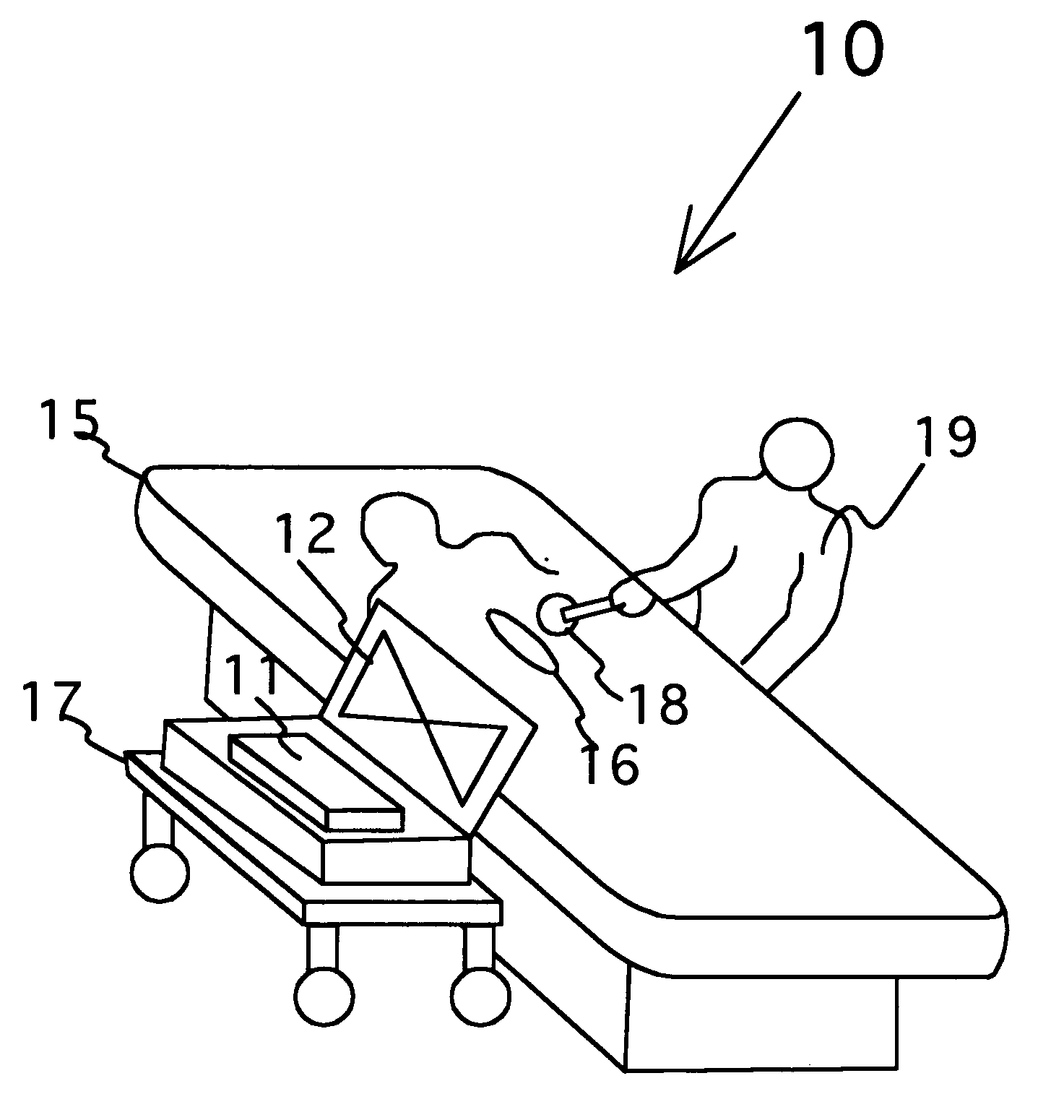
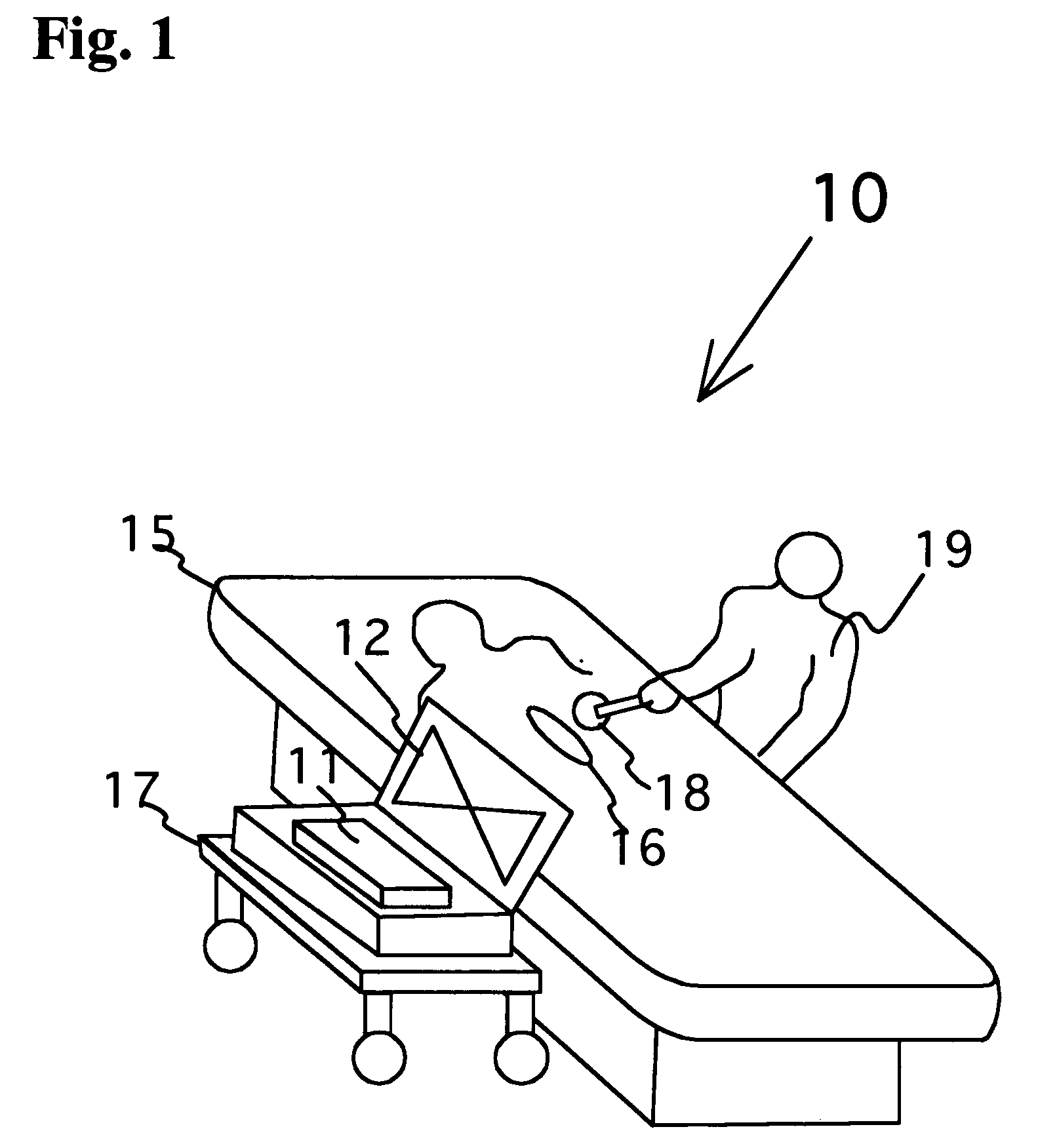
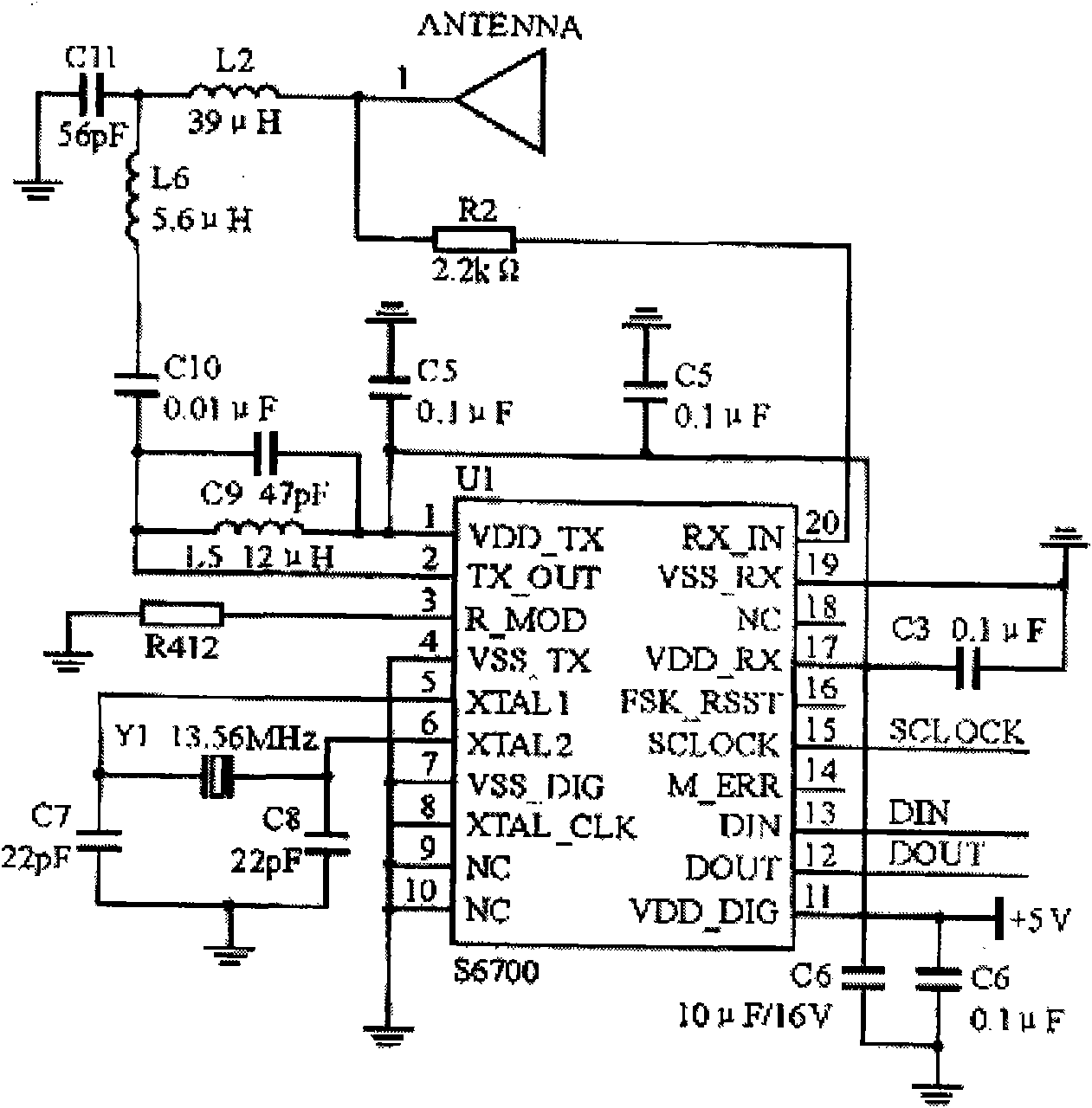
Surgical implement detector utilizing a radio-frequency identification marker
InactiveUS7307530B2Control moreSevere possibilitySurgeryElectric/electromagnetic visible signallingModulation functionEngineering
A radio-frequency surgical implement detection system detects surgical implements in a surgical wound during and at the completion of a surgical procedure. Surgical implements, including surgical sponges or laparotomy pads, gauze pads and metallic surgical instruments, are individually attached to a non battery-powered, encapsulated radio-frequency marker. The marker comprises an integrated chip having a burnt-in memory code, which is broadcast through an antenna using a modulated carrier frequency. The code is received by an interrogating antenna of a detector. The interrogating antenna provides a power pulse, which is received by the antenna of the radio-frequency marker. The power pulse charges a capacitor, which proves power for the read function, carrier frequency modulation function and broadcast function of the integrated chip, permitting each marker-containing implement to be specifically identified.
Owner:FABIAN CARL E
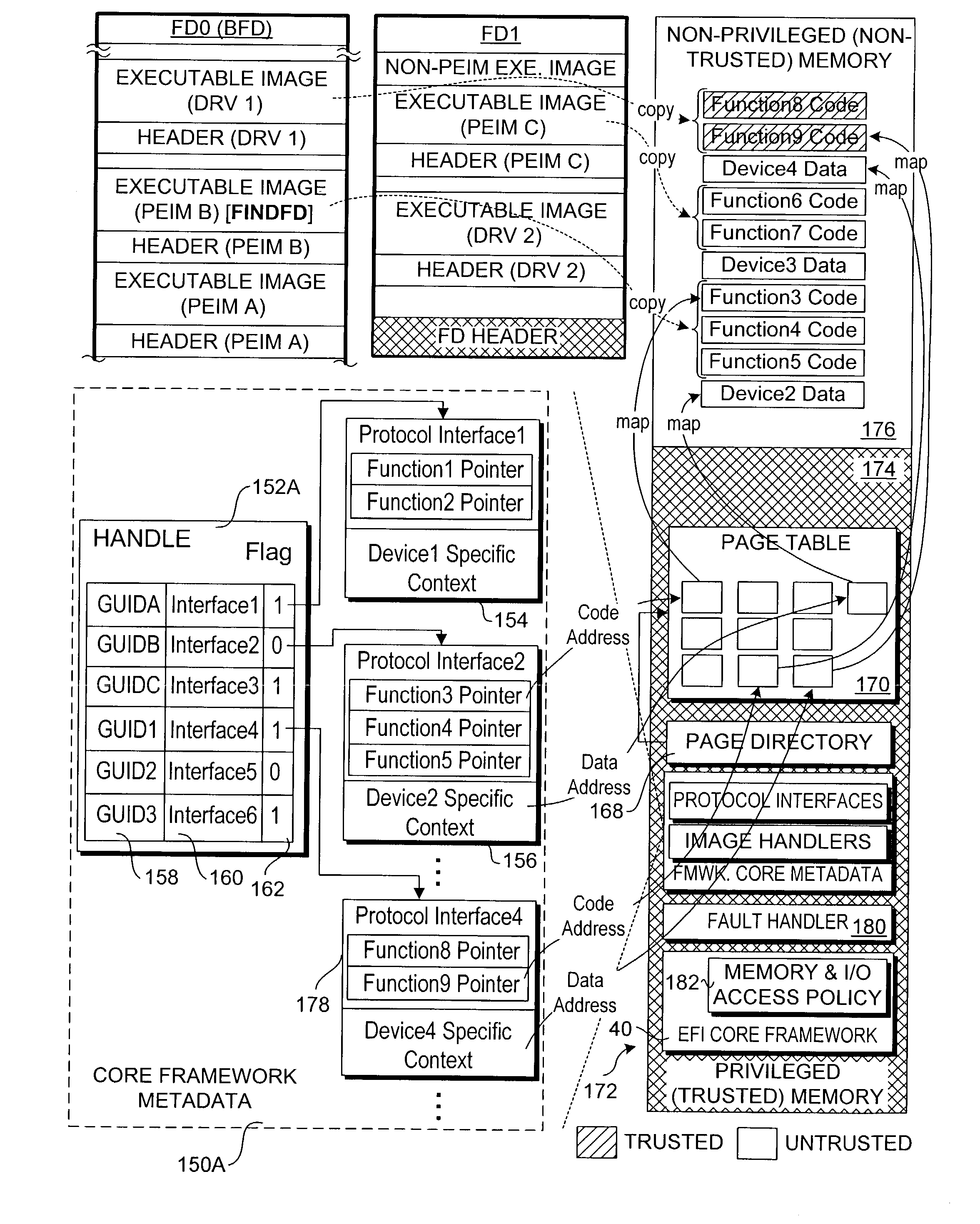
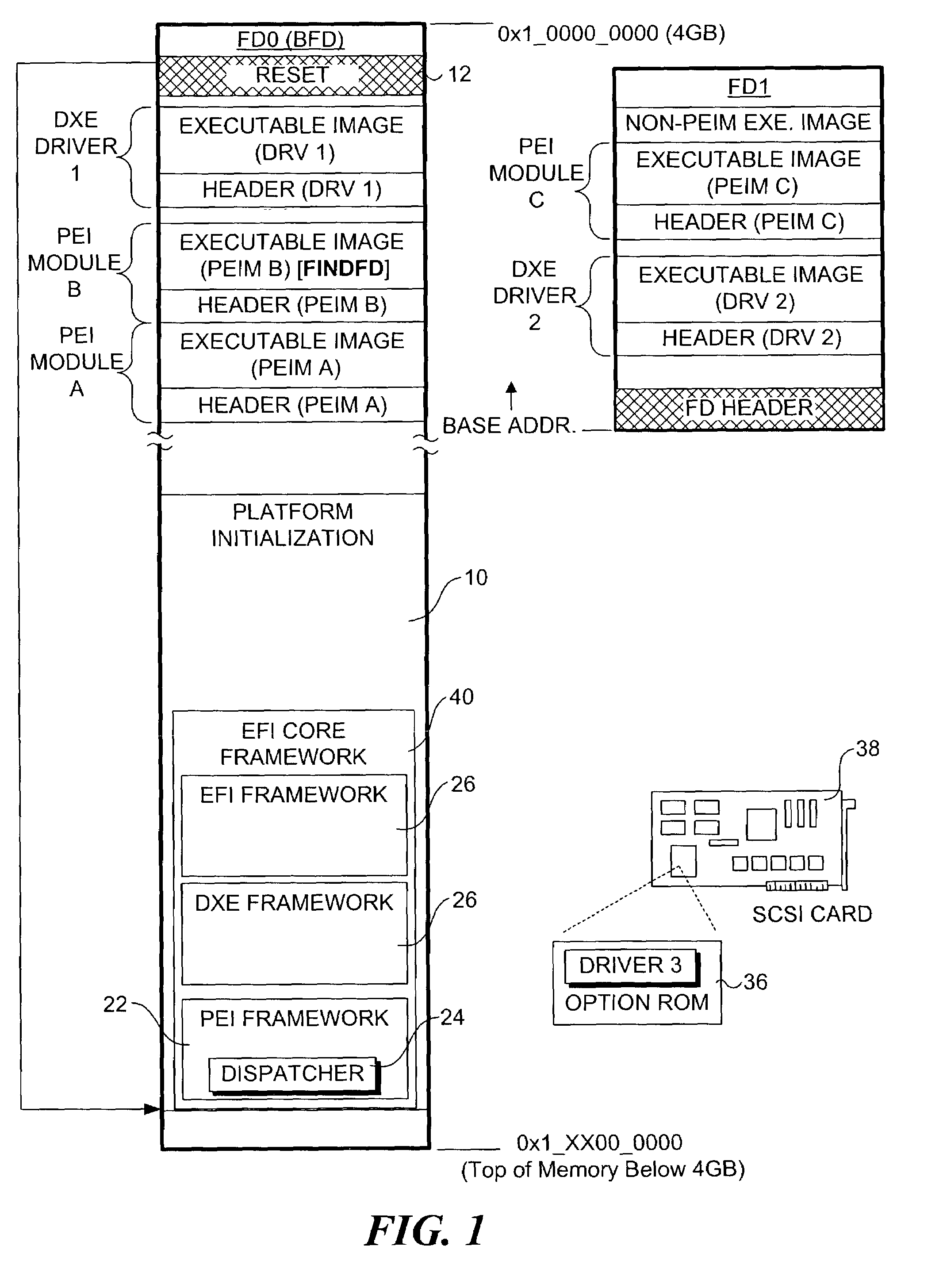
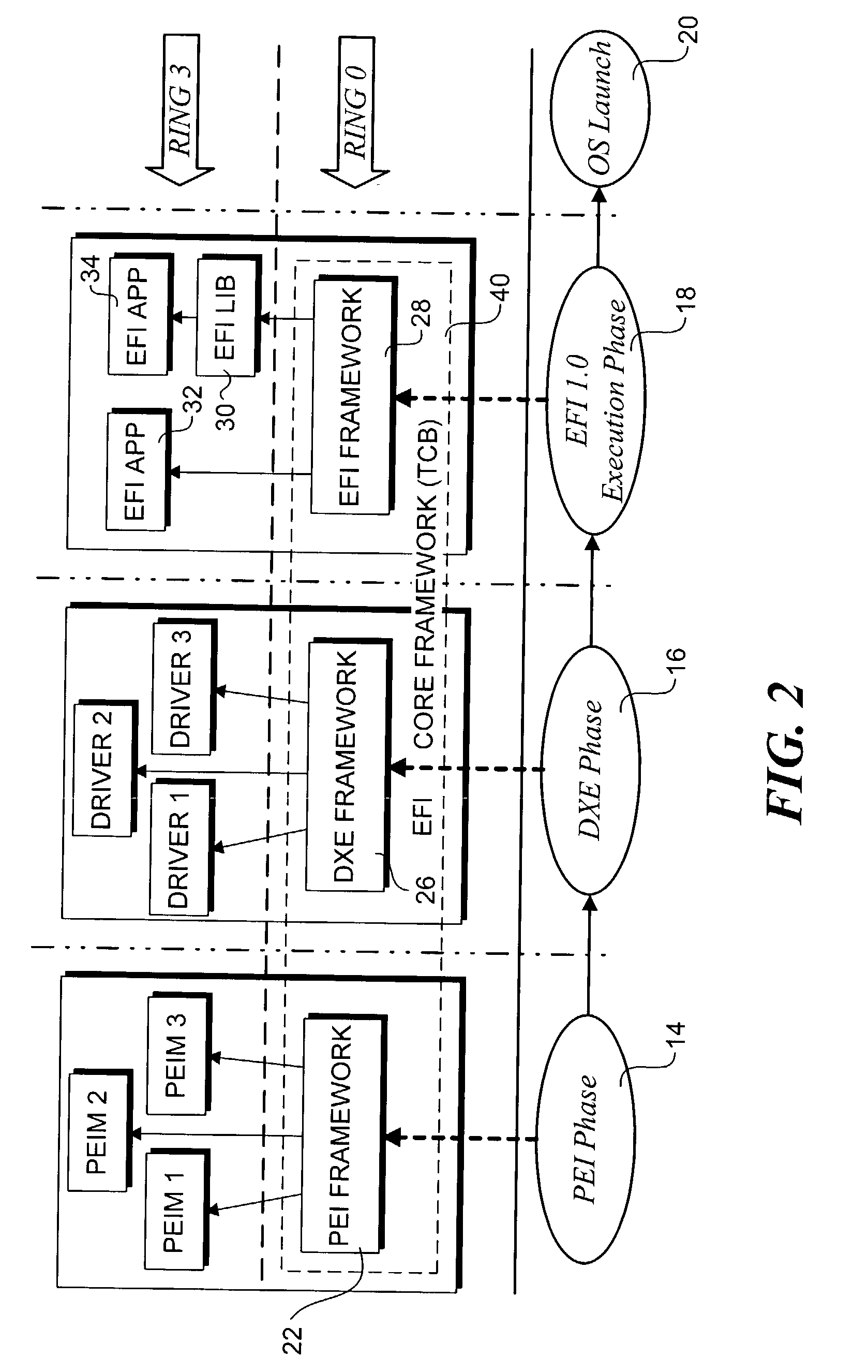
Hardened extended firmware interface framework
A method of system for hardening a firmware environment. A trusted core framework of firmware components are segregated from initially non-trustworthy extended firmware components such that the trusted core components are executed in a privileged processor mode, while the extended firmware components are executed in a non-privileged processor mode. An authentication of each extended firmware component is made to determine whether it is secure or non-secure. Through a memory code fault mechanism, memory accesses made by the extended firmware components are trapped, and a determination is made to whether the memory accesses should be allowed based on whether the extended firmware component is secure or non-secure and whether the requested memory page was allocated by the trusted core or a secure extended firmware component. This segregation scheme prevents non-trusted firmware from accessing privileged memory, thereby preventing rogue, errant, or malicious firmware from damaging the trusted core framework.
Owner:INTEL CORP
Surgical implement detector utilizing a radio-frequency identification marker
InactiveUS20060187059A1High bandwidthControl moreSurgeryElectric/electromagnetic visible signallingEngineeringFrequency modulation
A radio-frequency surgical implement detection system detects surgical implements in a surgical wound during and at the completion of a surgical procedure. Surgical implements, including surgical sponges or laparotomy pads, gauze pads and metallic surgical instruments, are individually attached to a non battery-powered, encapsulated radio-frequency marker. The marker comprises an integrated chip having a burnt-in memory code, which is broadcast through an antenna using a modulated carrier frequency. The code is received by an interrogating antenna of a detector. The interrogating antenna provides a power pulse, which is received by the antenna of the radio-frequency marker. The power pulse charges a capacitor, which proves power for the read function, carrier frequency modulation function and broadcast function of the integrated chip, permitting each marker-containing implement to be specifically identified.
Owner:FABIAN CARL E
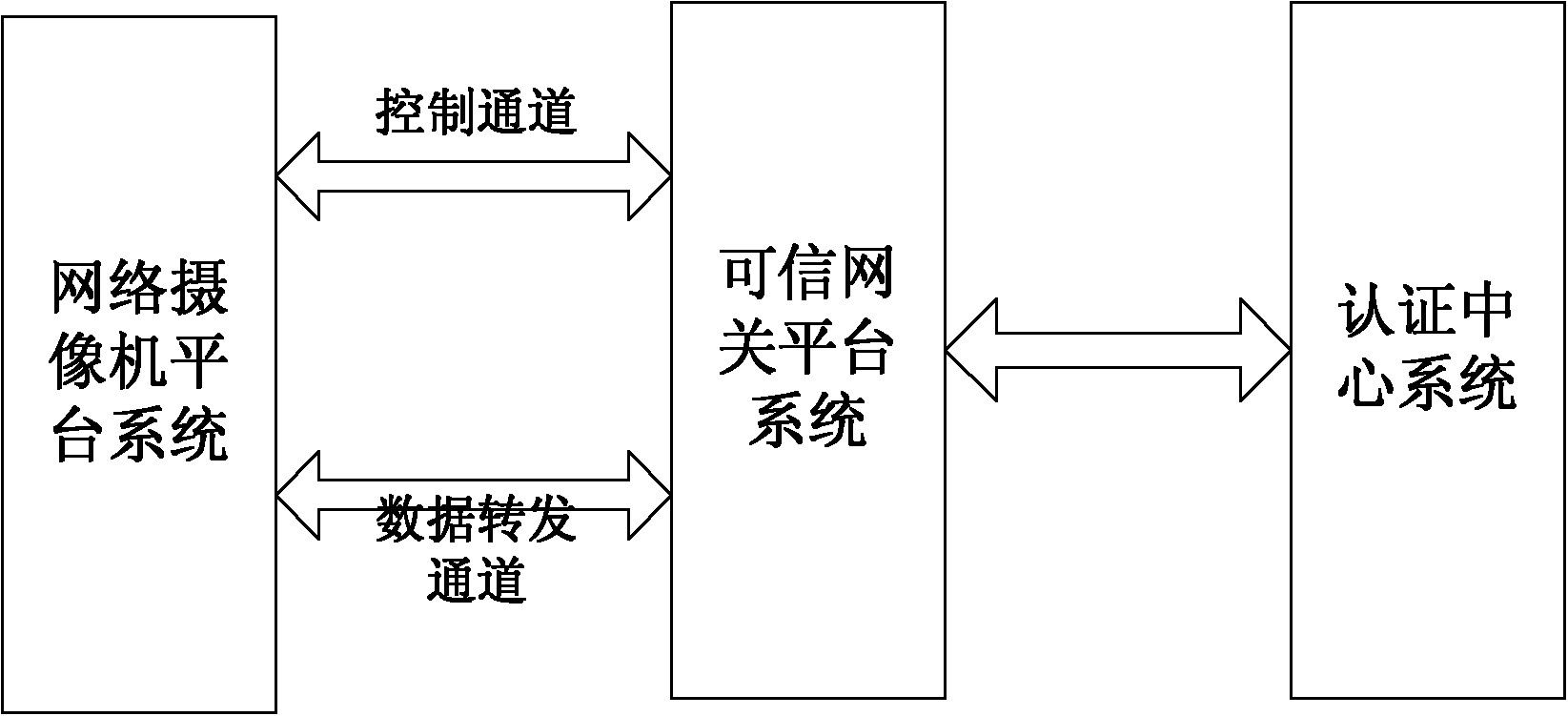
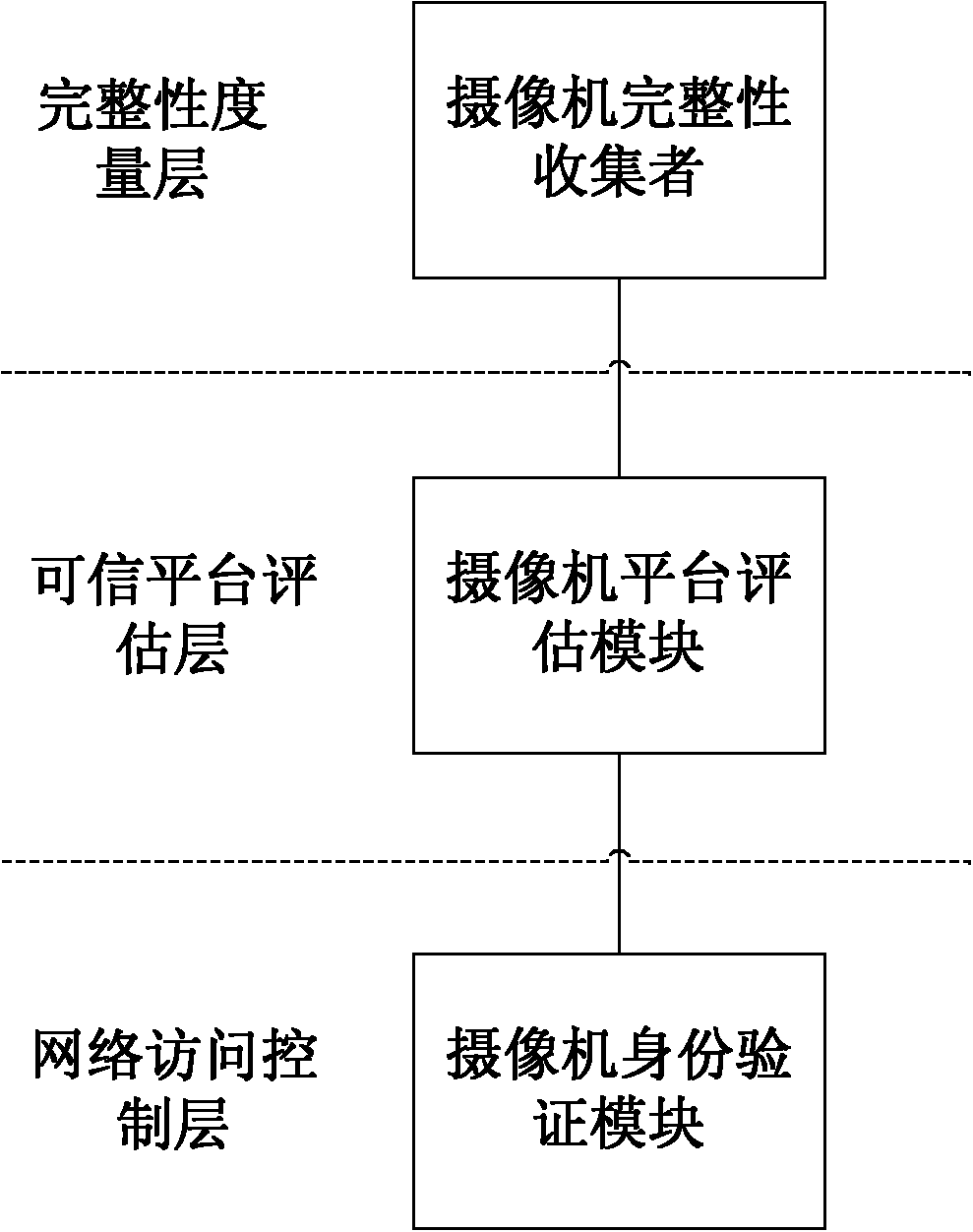
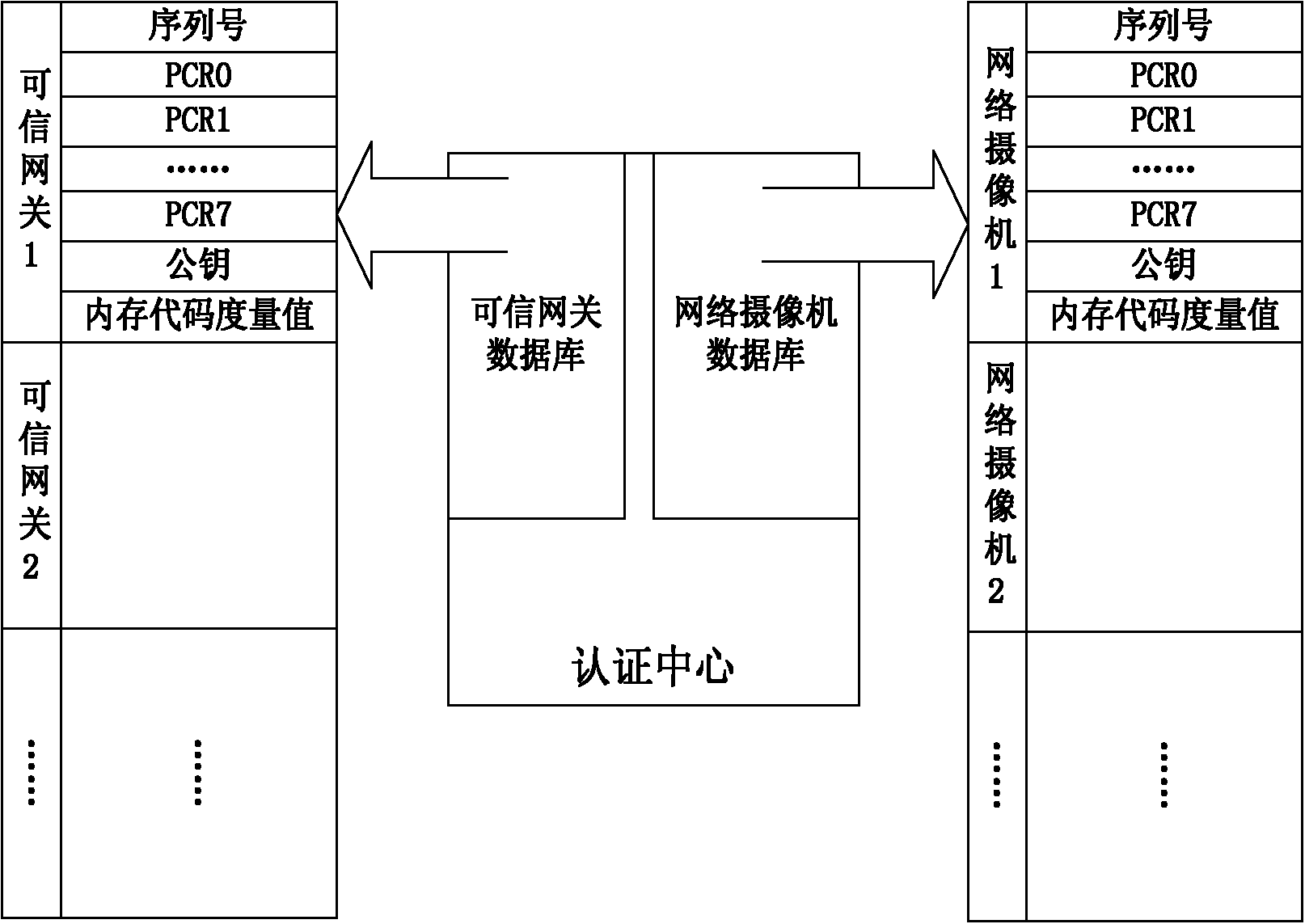
Network camera identity authentication method based on TPCM
ActiveCN103888257AImplement identity authenticationReduced authenticationUser identity/authority verificationClosed circuit television systemsProcessor registerMemory code
The invention provides a network camera identity authentication method based on a TPCM. The method is characterized in that a network camera and a reliable gateway adopt a self-signing mode to generate a digital certificate which comprises a value of a platform configuration register and a measurement result of a memory code segment in operation. An authentication center verifies validity of the digital certificate and confirms identity of the verified party. Advantages are that a measurement value in the starting process of equipment is stored in the platform configuration register so that hardware of the network camera and the reliable gateway is ensured to be unchanged. Reliability of equipment identity is ensured from the aspect of software via measurement of the memory code segment. Besides, a signature secret key is generated by a TPCM chip and bound with the hardware platform state of the equipment so that the digital certificate is difficult to forge.
Owner:BEIJING UNIV OF TECH
Processing method and apparatus for application not responding
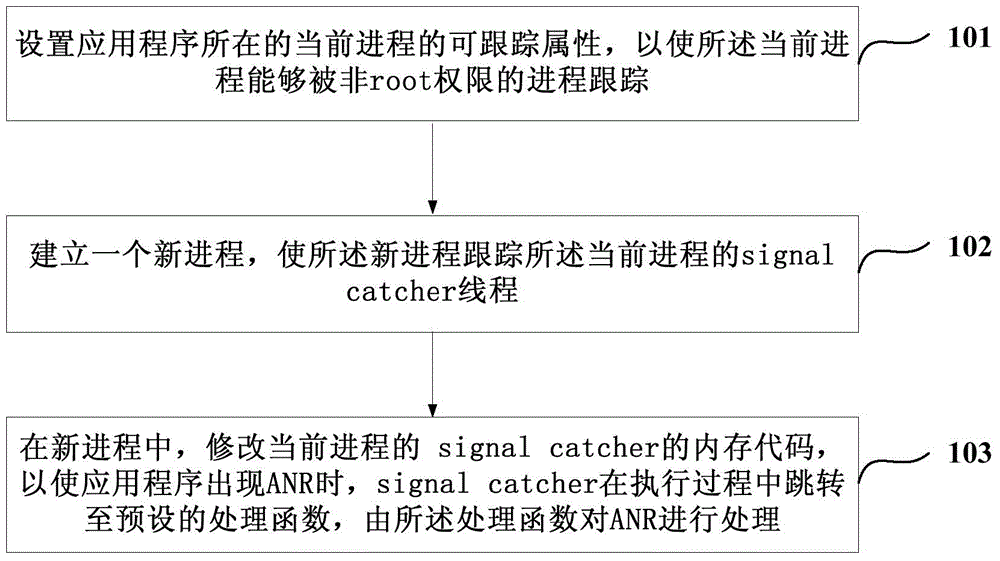
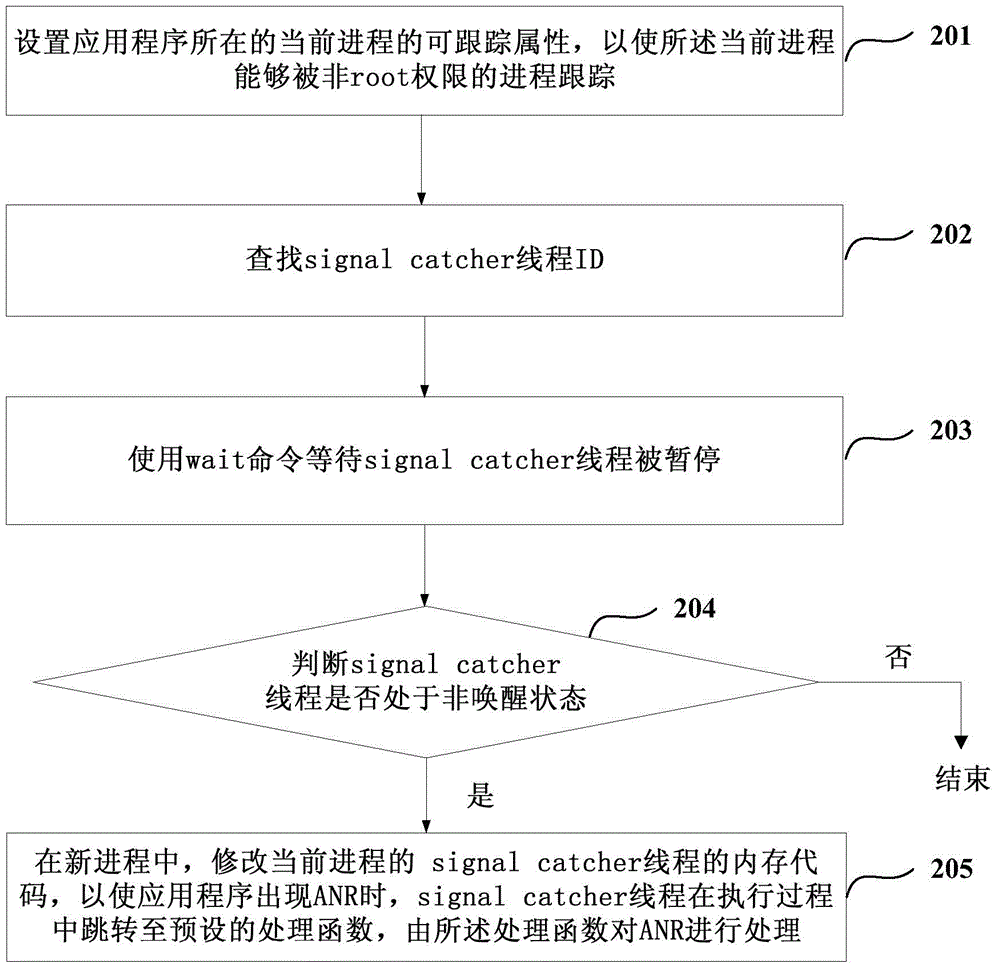
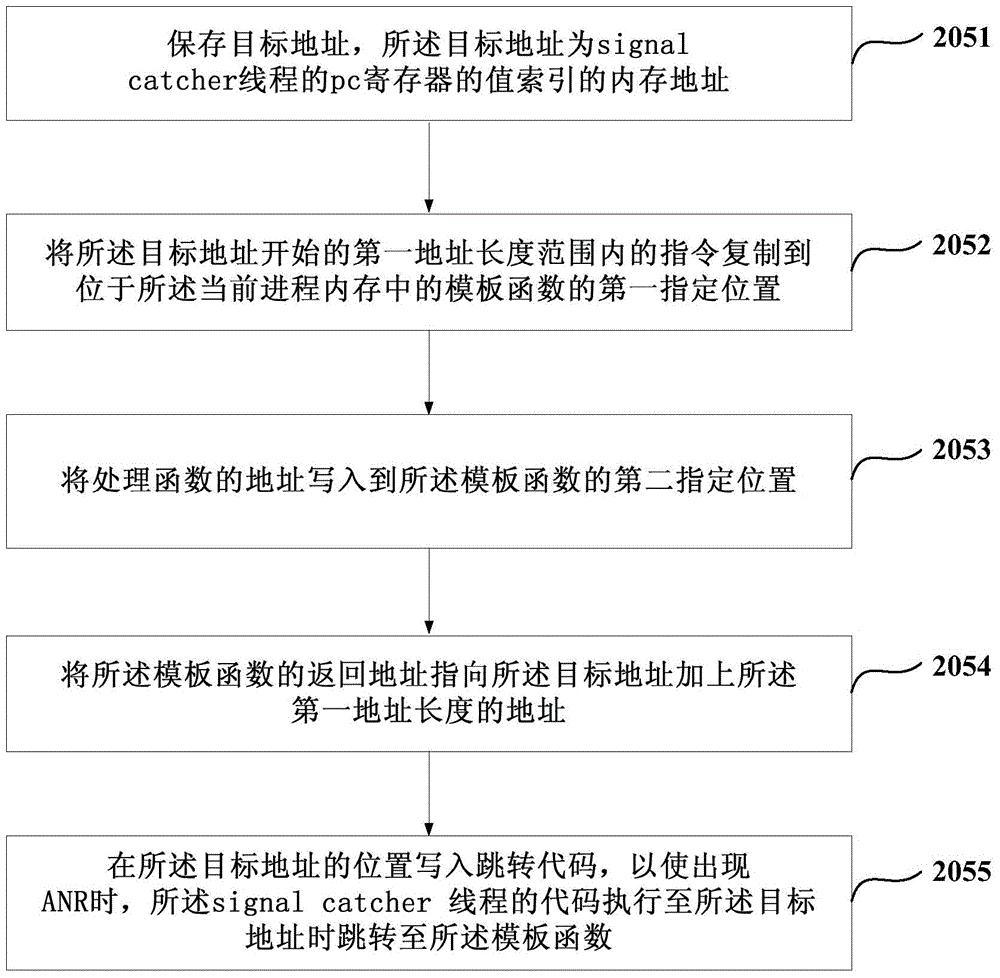
Embodiments of the invention disclose a processing method and apparatus for application not responding. A newly established process tracks a signal catcher thread of a current process in which an application is, and a memory code of the signal catcher thread is modified in the new process, so that when application not responding (ANR) occurs, the signal catcher thread can skip to a processing function preprogramed by a developer of the application; and the processing function processes the ANR, so that the application has a chance to interrupt time-consuming threads, stops input / output (I / O) operation, and records detail information of the ANR so as to improve the application.
Owner:ALIBABA (CHINA) CO LTD
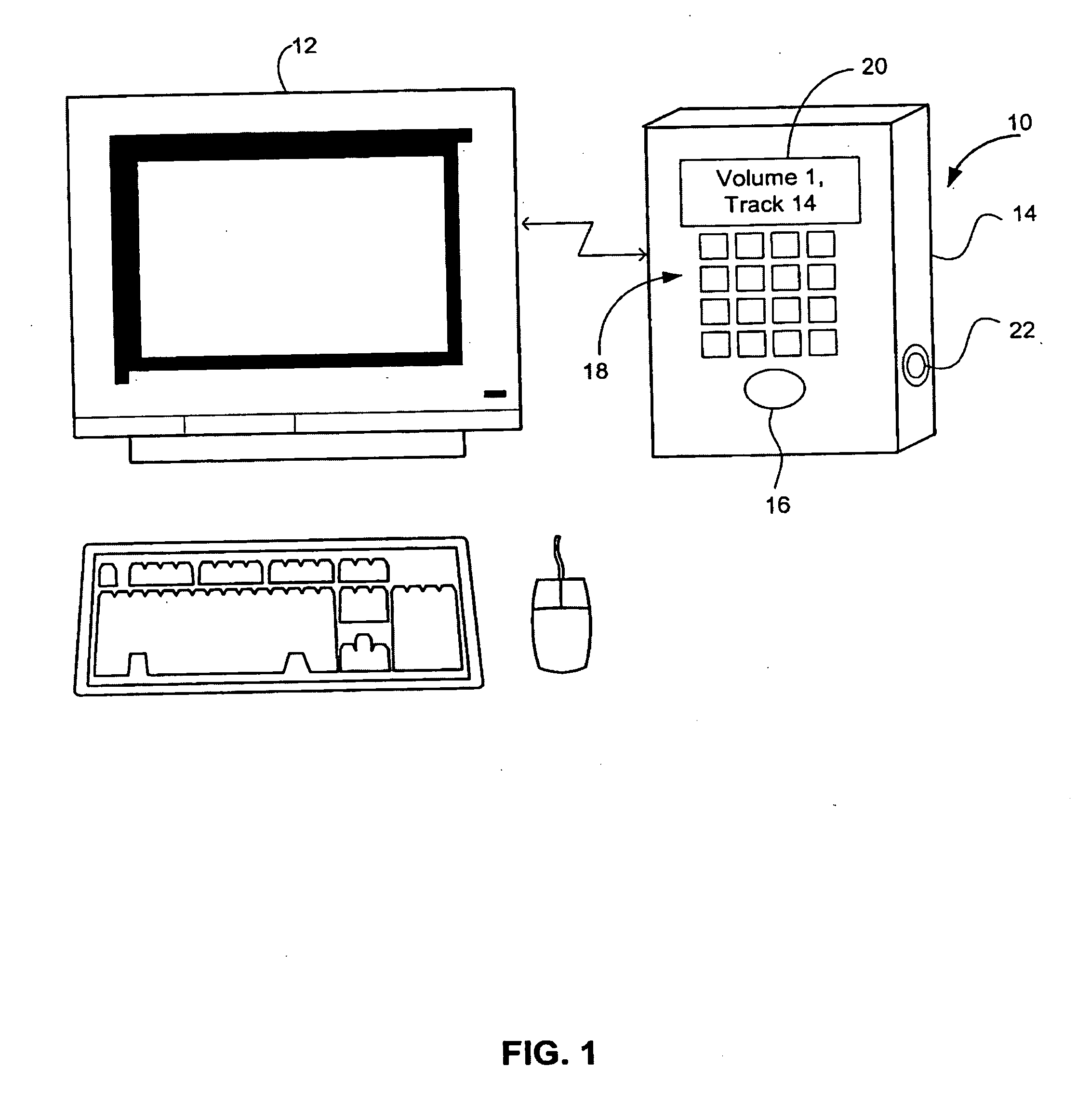
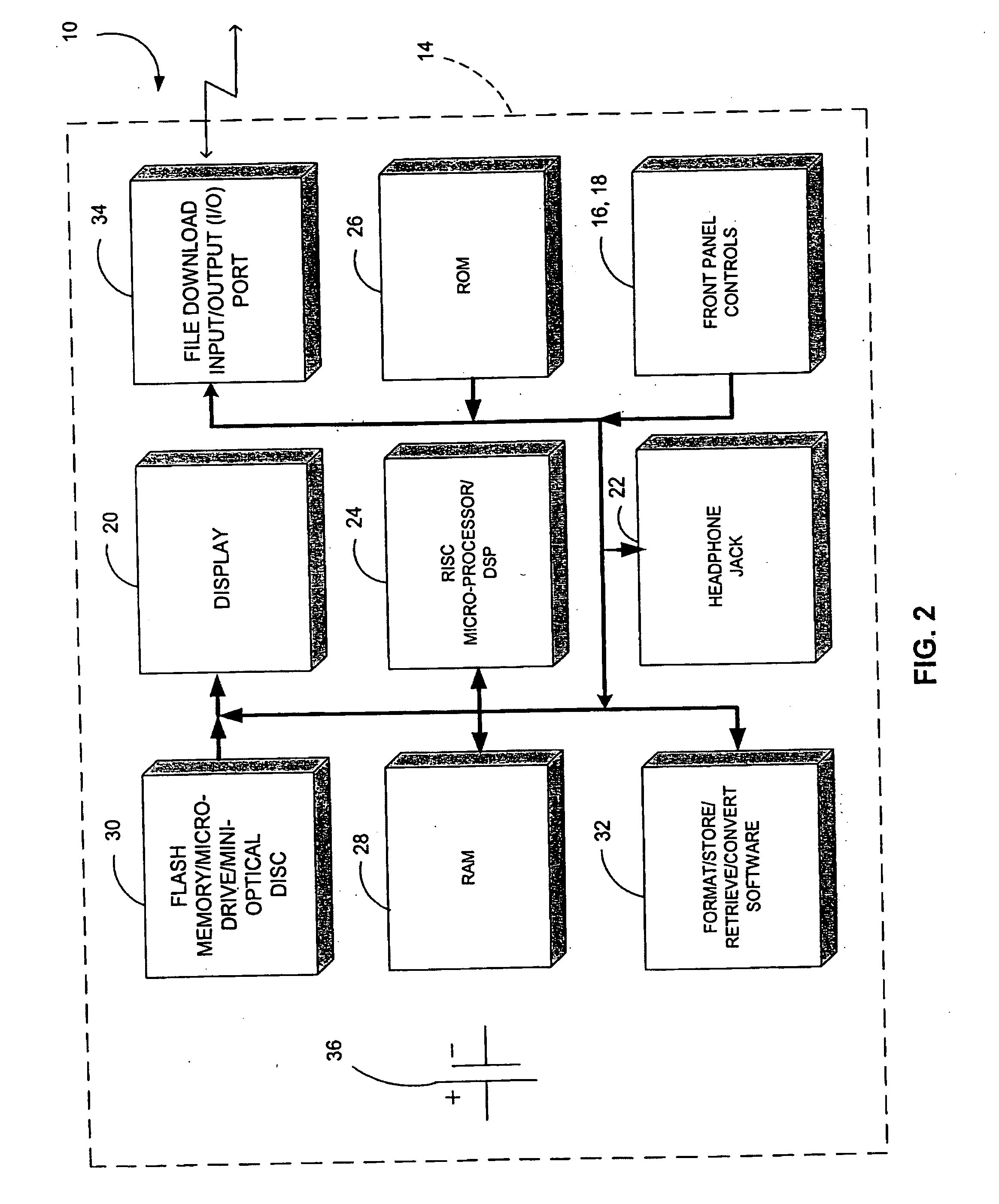
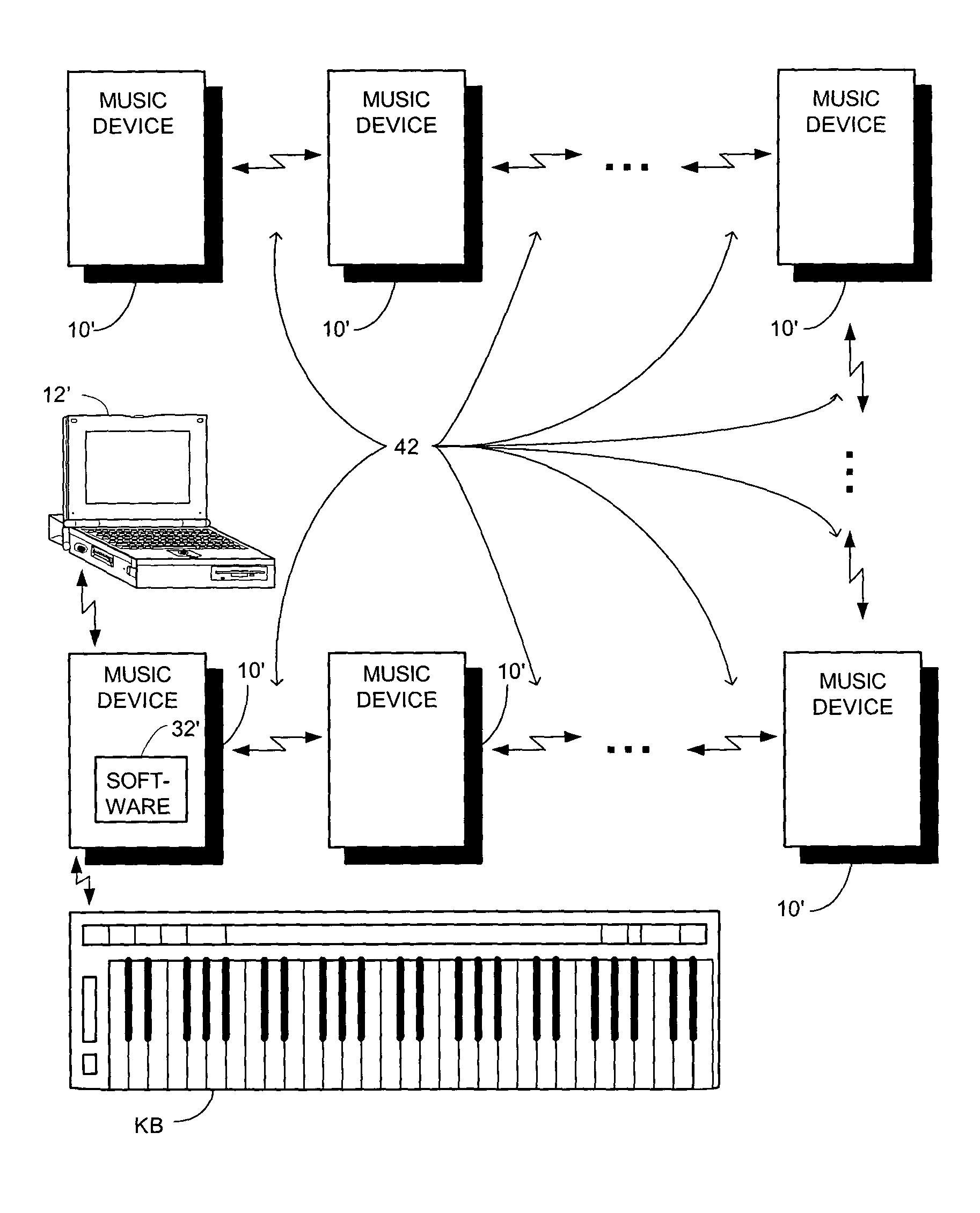
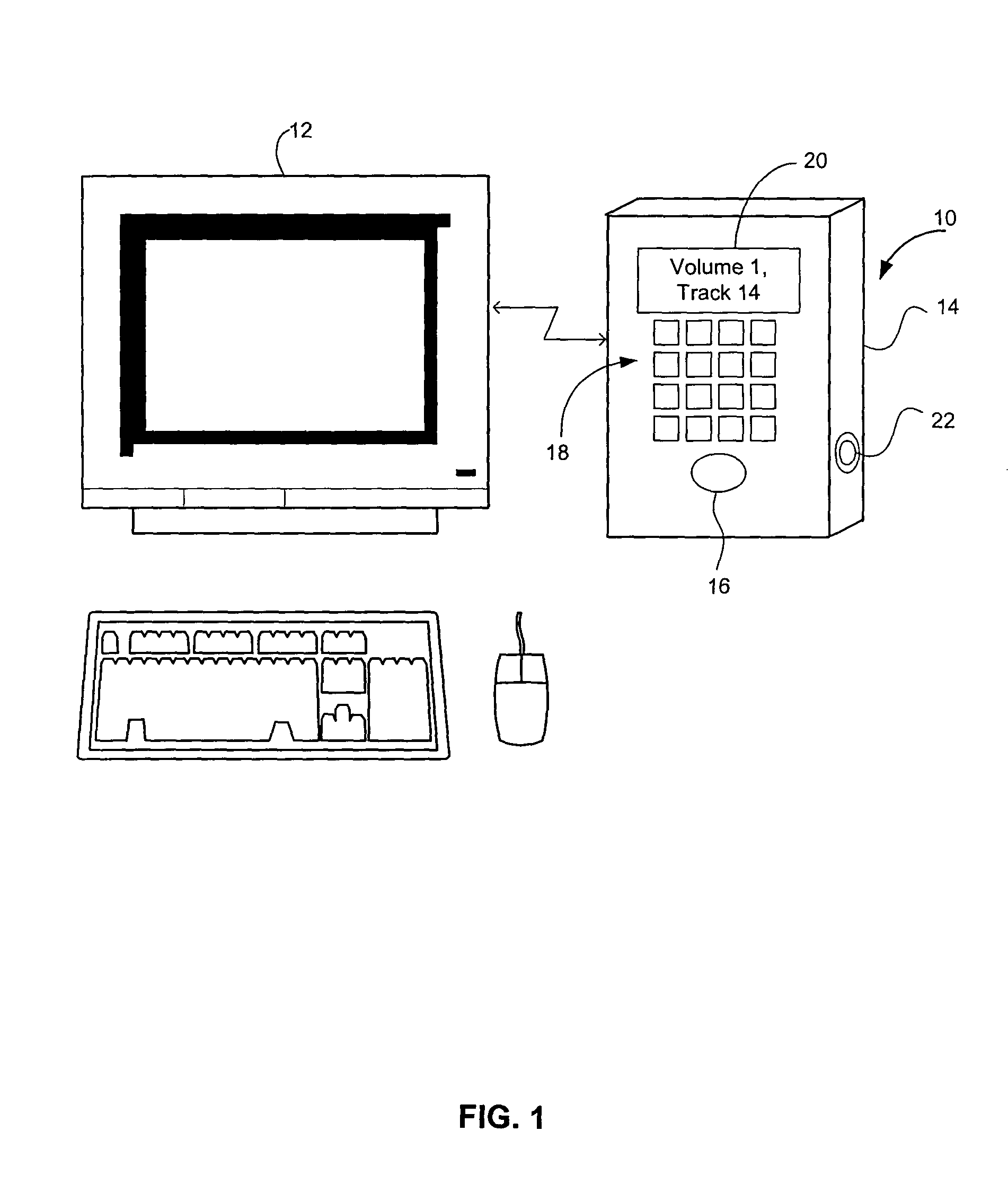
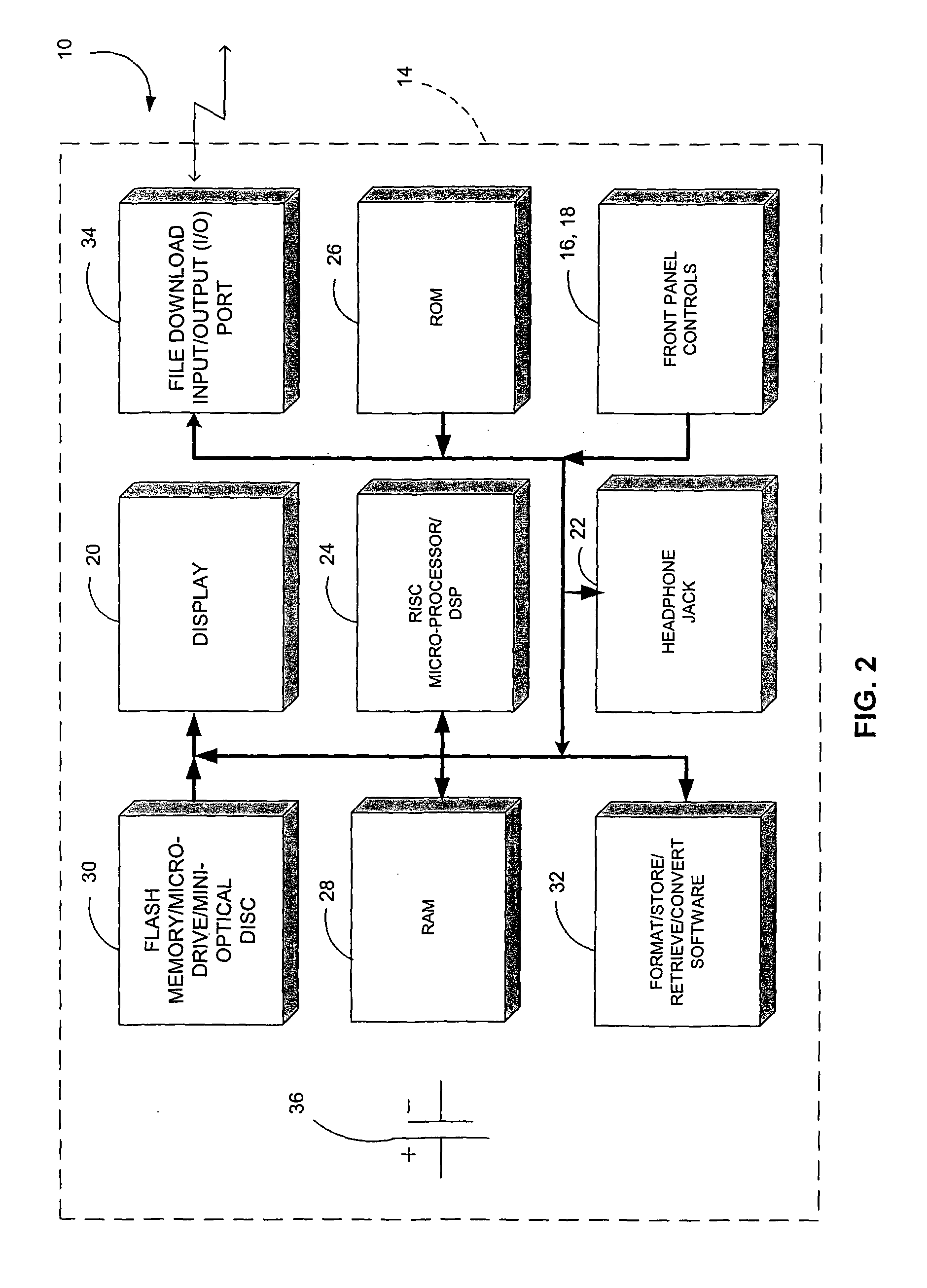
Hand-held music player with wireless peer-to-peer music sharing
The apparatus involves a hand-held housing with a memory for storing coded audio event data, a mechanism for downloading into the memory coded audio event data and digital-audio electronics for retrieving coded audio event data from memory, converting it to an audio signal and playing it out. In one disclosed embodiment of the invention, the data are stored in accordance with a musical instrument digital interface (MIDI) standard, and may be created on an appropriately equipped personal computer (PC). The capacity of such a hand-held device is far greater than if the data were conventionally digitized or coded. A wirelessly networked system of such music devices in physical proximity is disclosed that enables audio score synthesis and mixing by at least one such device of a synthesized score and an inputted score for outplay to others in a real-time musical jam or music-sharing session.
Owner:INTEL CORP
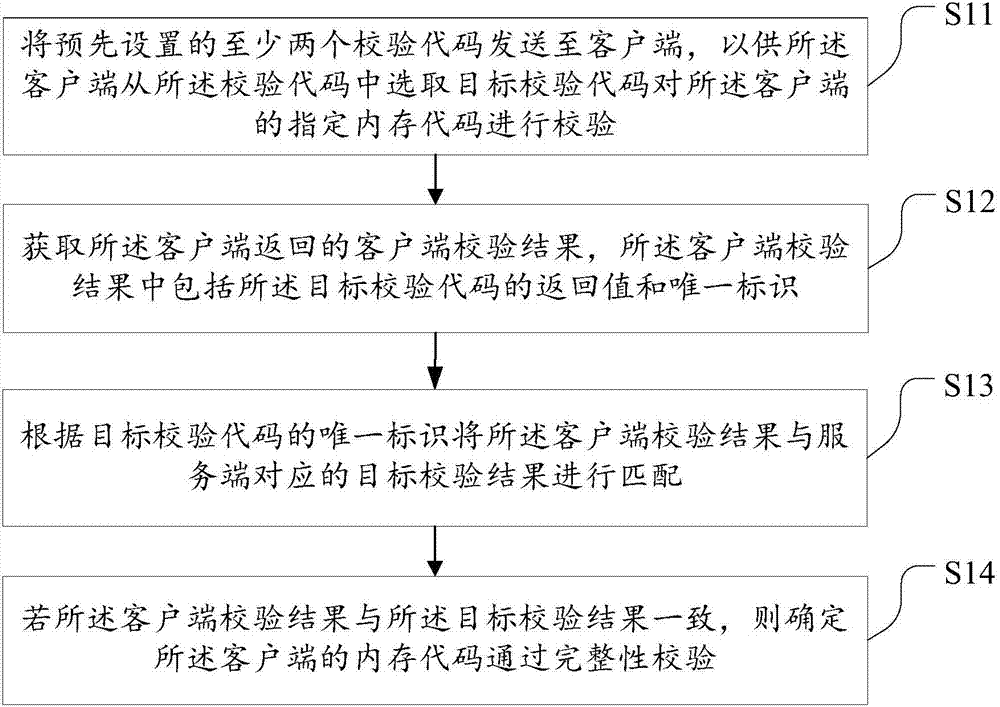
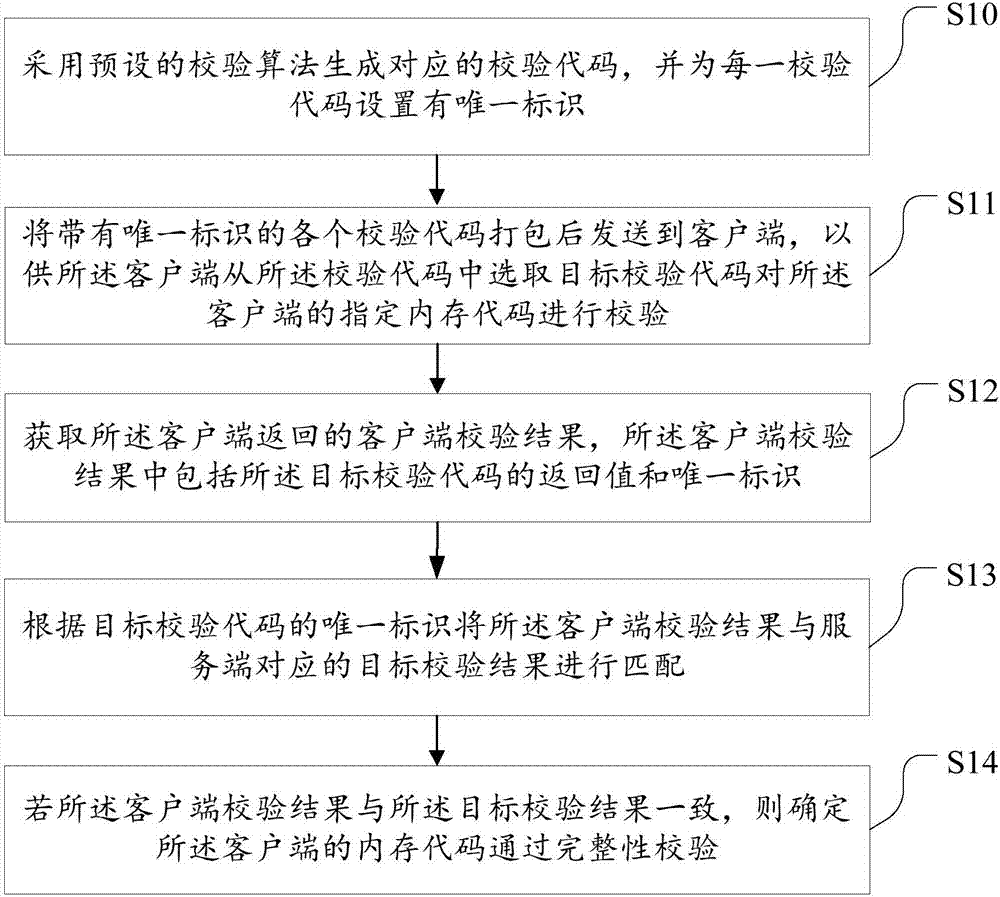
Memory code integrity verification method and device
InactiveCN107194250AGuaranteed accuracyRaise the barPlatform integrity maintainanceUnique identifierMemory code
The embodiment of the invention discloses a memory code integrity verification method and device. The method comprises the following steps: sending at least two preset verification codes to a client, so that the client can select a target verification code from the verification codes to verify a designated memory code of the client; acquiring a client verification result returned by the client, wherein the client verification result comprises a returned value and an unique identifier of the target verification code; according to the unique identifier of the target verification code, carrying out matching between the client verification result and a target verification result corresponding to a server; and if the client verification result is identical to the target verification result, determining that integrity verification for the memory code of the client is successful. The method and device provided by the invention has the advantages that a threshold for memory code modification by HACK can be greatly raised, so that the integrity verification accuracy rate for the memory code of the client can be guaranteed, and the safety can be improved.
Owner:WUHAN DOUYU NETWORK TECH CO LTD
Multiple fake-proof print oil with memory code and its checking method
The invention provides a multiple fake-proof print oil with memory code and its checking method, wherein the fake-proof print oil comprises stamp-pad ink, magnetic memory material and encrypted message therein, infrared fluorescent material and ultraviolet fluorescent material.
Owner:熊春宁
Video snapshot method based on memory coding mechanism and video snapshot device thereof
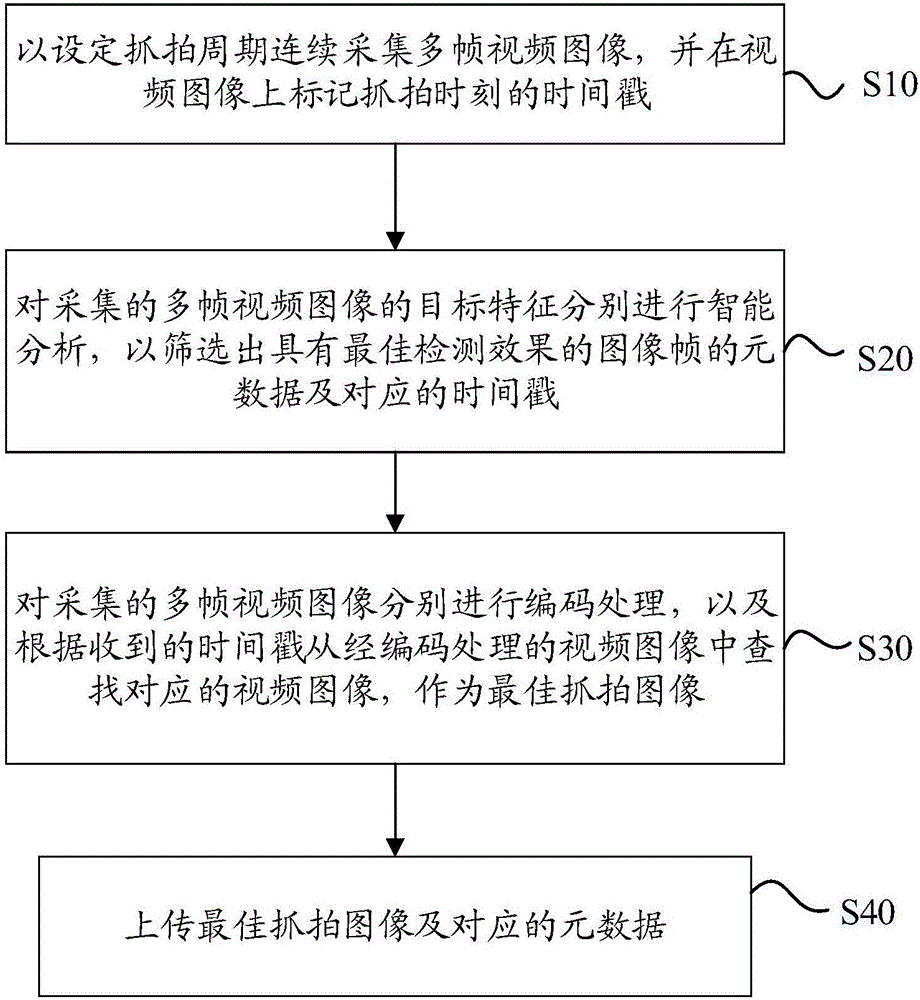
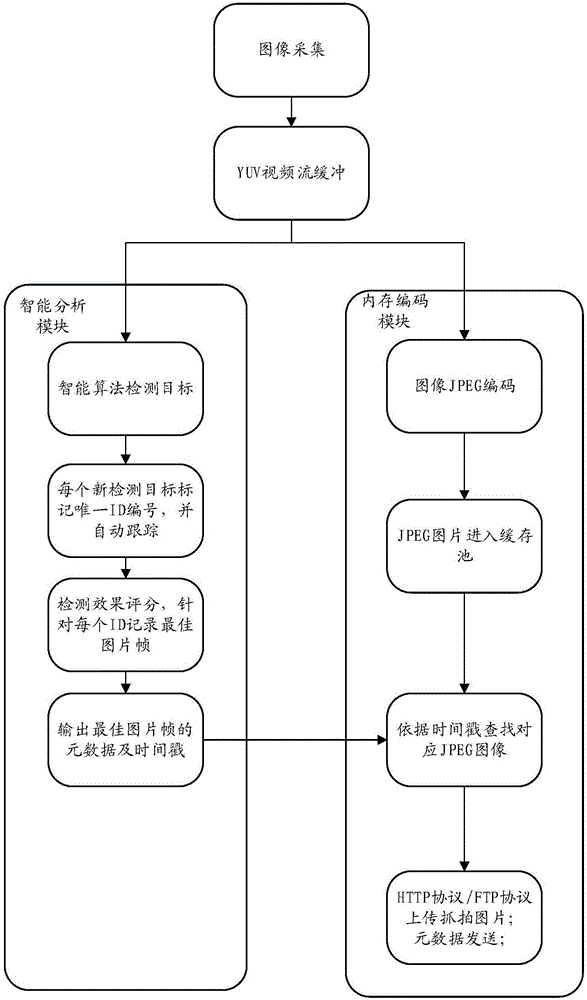
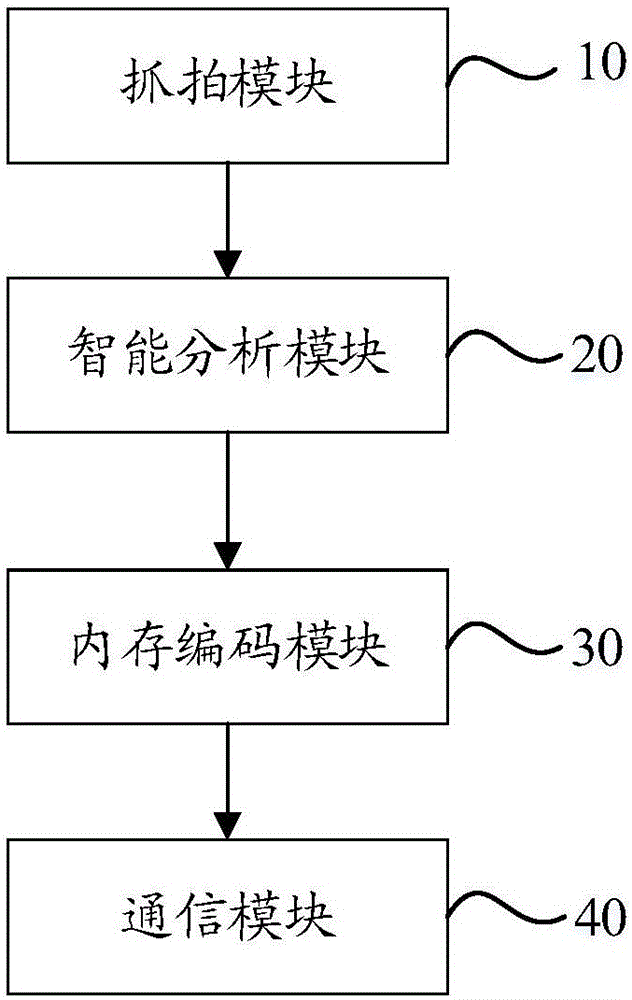
ActiveCN106803936ABest capture effectSave bandwidth resourcesTelevision system detailsColor television detailsTimestampMultiple frame
The invention discloses a video snapshot method based on a memory coding mechanism and a video snapshot device thereof. The method comprises the following steps that multiple frames of video images are continuously acquired according to a set snapshot period, and the timestamp of the snapshot moment is marked on the video images, wherein the video images include target characteristics; the target characteristics of the acquired multiple frames of video images are intelligently analyzed so as to select the metadata of the image frames having the optimal detection effect and the corresponding timestamp in a screening way; the acquired multiple frames of video images are coded, and the corresponding video images are searched from the coded video images according to the received timestamp to act as the optimal snapshot images; and the optimal snapshot images and the corresponding metadata are uploaded. According to the technical scheme, ineffective snapshot can be avoided, the images having the optimal snapshot effect can be acquired, the snapshot accuracy can be enhanced and the network bandwidth resource can also be saved.
Owner:SHENZHEN INFINOVA
Method for sorting and looking up telephone book of hand held
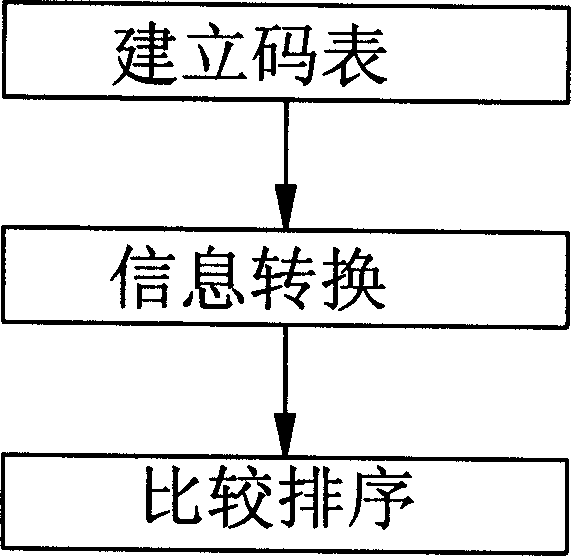
ActiveCN1728735AReasonably arrangedFind intuitiveSubscriber signalling identity devicesSpecial data processing applicationsTelecommunicationsHand held
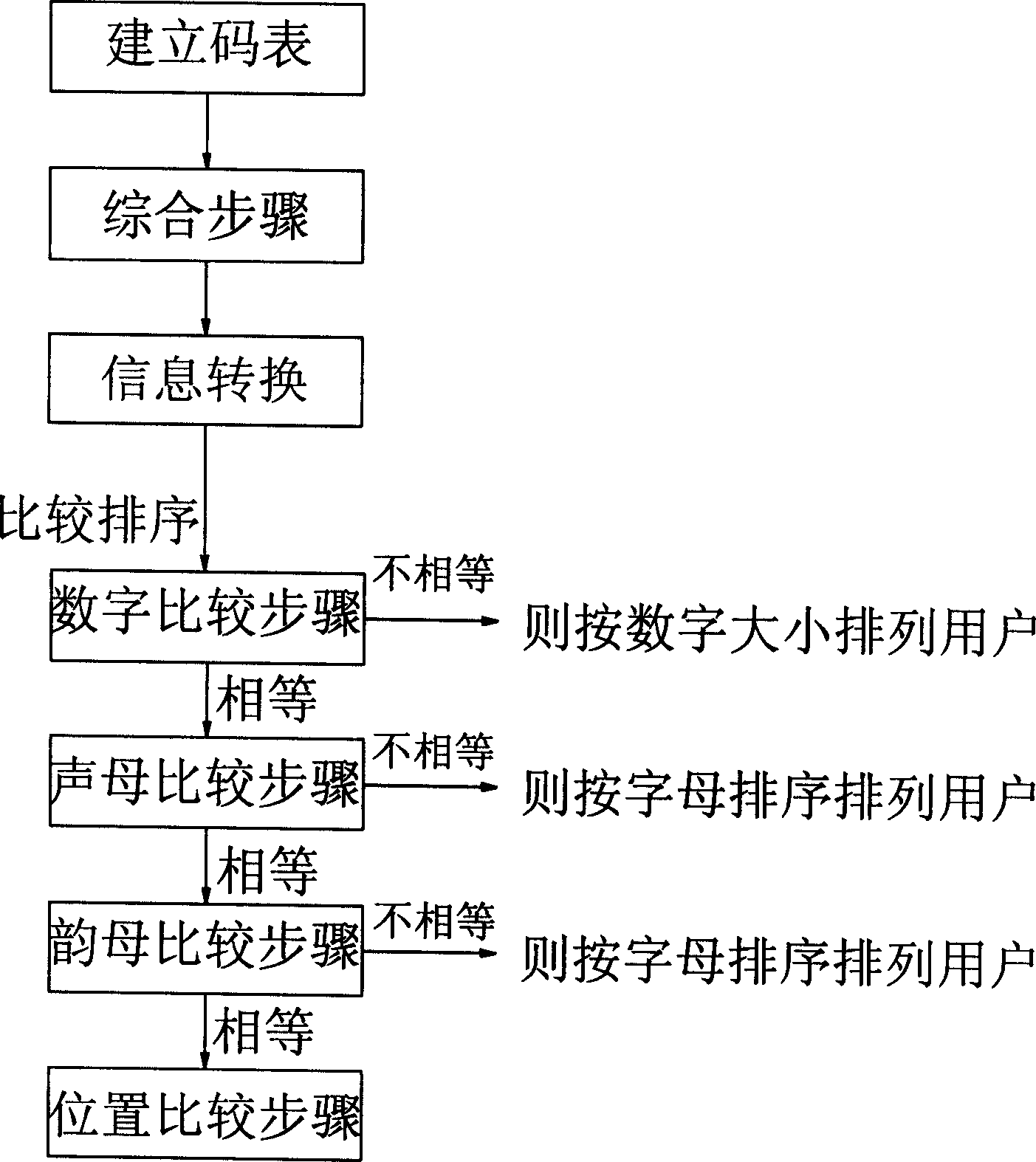
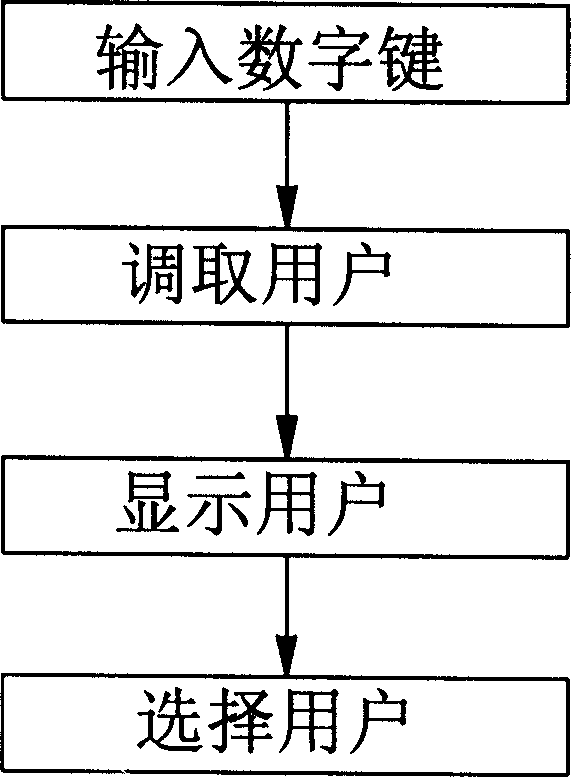
The method includes steps: first, building code table; then, information conversion; finally, carrying out comparison sort. Being converted to corresponding number, memory code of name (Unicode) of each user is arranged on phone book according to big and small. Keyboard of number converted from memory code of name (Unicode) is the keyboard the Unicode located at. Method for looking-up phone book of hand held device includes steps: first inputting number key; second, calling and obtaining user; third displaying user, finally, selecting user. Features are: convenience for looking up phone book, and quick.
Owner:AMOI TECH
Detection device and method for quickly positioning failure memory bank
InactiveCN105095032ARapid positioningNovel ideaDetecting faulty computer hardwareProduction lineMemory bank
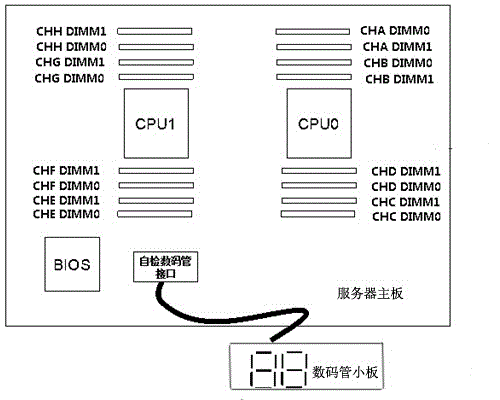
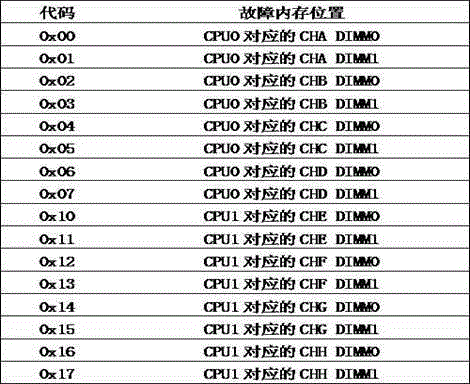
The invention discloses a detection device and method for quickly positioning a failure memory bank, and relates to a memory detection technology. The detection device mainly comprises a server mainboard and an external nixie tube small board; the server mainboard is provided with CPUs, a BIOS chip, a self-detection nixie tube interface and multiple memory banks expanded by the CPUs, and the nixie tube small board is connected to the self-detection nixie tube interface through a patch cord. According to the detection device and method for quickly positioning the failure memory bank, a memory failure code table is built, and when memory failure detection is performed, failure memory codes are displayed through the nixie tube small board and compared with the memory failure code table to quickly position the position of the failure memory bank; the time of server operators for excluding the failure memory bank can be saved, the workloads of the operators are reduced, the debugging efficiency of a server production line is improved, and the server productivity is improved.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
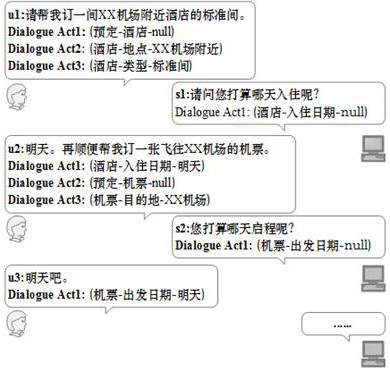
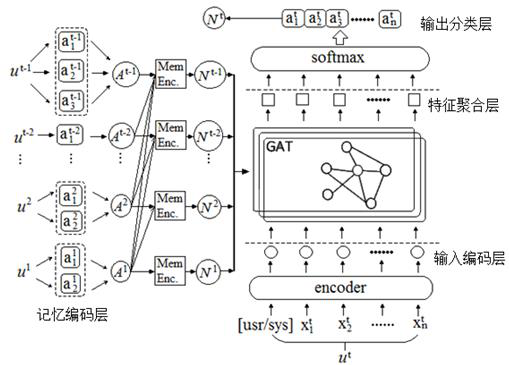
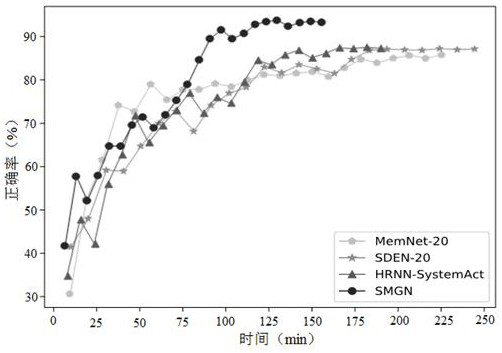
Structured memory graph network model for multiple rounds of spoken language understanding
ActiveCN112182191AImprove computing efficiencySolve the noiseSemantic analysisOther databases indexingSpoken languageTheoretical computer science
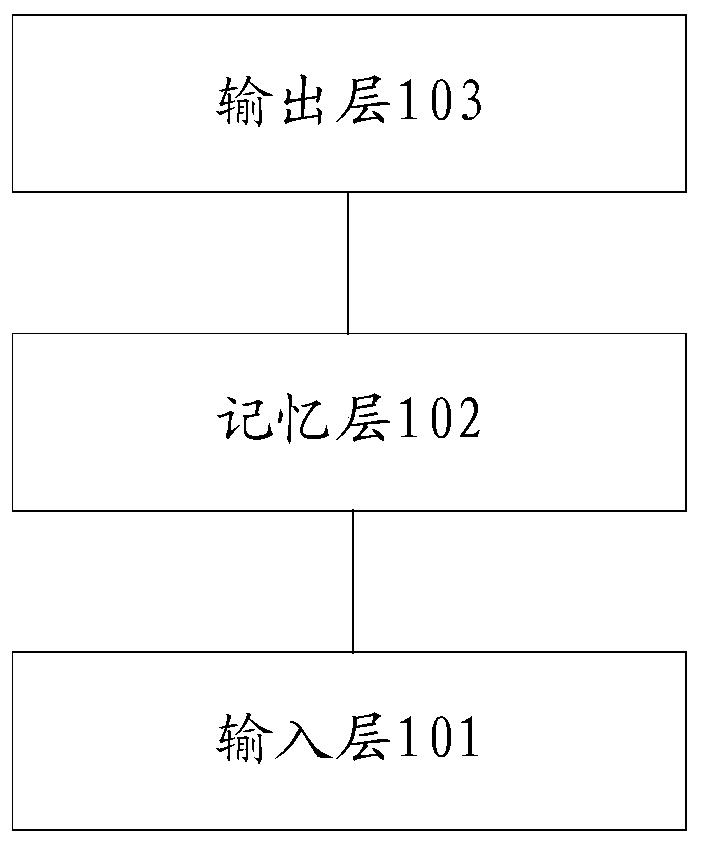
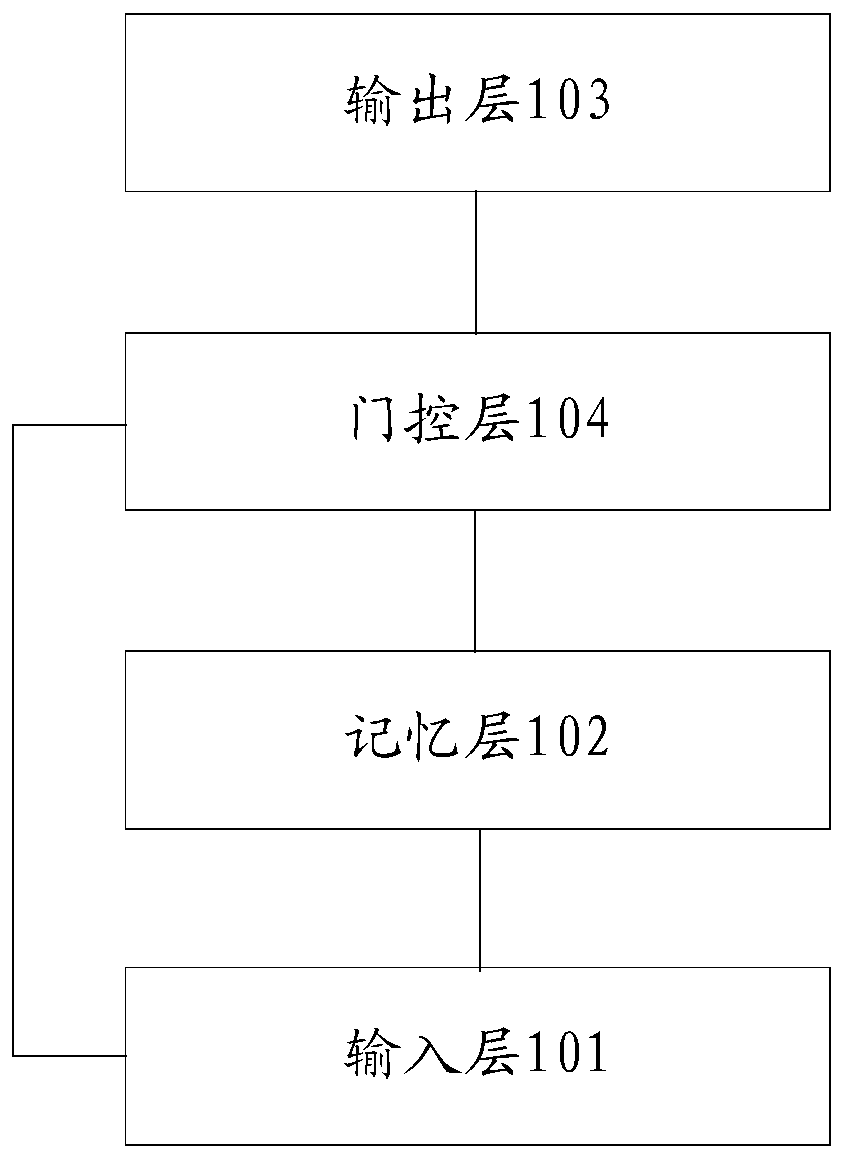
The invention discloses a structured memory graph network model for multiple rounds of spoken language understanding, which is composed of an input coding layer, a memory coding layer, a feature aggregation layer and an output classification layer, dialogue behaviors generated by spoken language understanding tasks are used to replace texts as memory nodes for coding, and the dialogue behaviors are formatted representations containing semantic framework information. And the unstructured characters are converted into a structured triple. A graph attention network is used for replacing a recurrent neural network and an attention mechanism to achieve feature aggregation, sequence information between the attention mechanism and dialogue nodes is reserved, and model learning how to effectivelyutilize structured memory nodes is facilitated. According to the network model, the encoding dialogue behavior replaces a historical dialogue text to serve as a memory unit, original information of asemantic framework is reserved to the maximum extent, and the problems that in the prior art, noise is generated in complex occasions due to the fact that text information depends on a model, and operation efficiency is low are solved.
Owner:NORTHWEST NORMAL UNIVERSITY
Portable hand-held music synthesizer and networking method and apparatus
The apparatus involves a hand-held housing with a memory for storing coded audio event data, a mechanism for downloading into the memory coded audio event data and digital-audio electronics for retrieving coded audio event data from memory, converting it to an audio signal and playing it out. In one disclosed embodiment of the invention, the data are stored in accordance with a musical instrument digital interface (MIDI) standard, and may be created on an appropriately equipped personal computer (PC). The capacity of such a hand-held device is far greater than if the data were conventionally digitized or coded. A wirelessly networked system of such music devices in physical proximity is disclosed that enables audio score synthesis and mixing by at least one such device of a synthesized score and an inputted score for outplay to others in a real-time musical jam or music-sharing session.
Owner:INTEL CORP
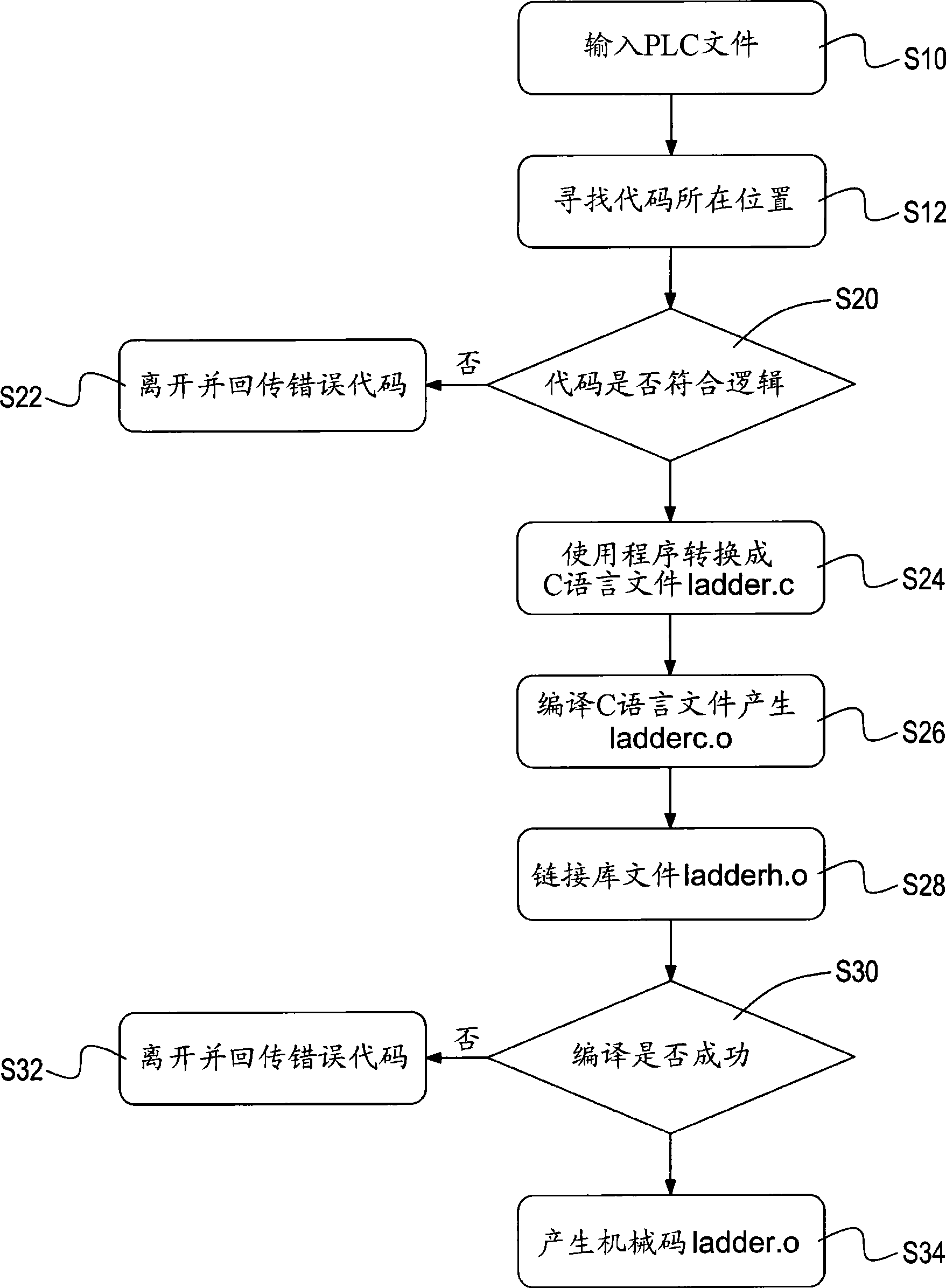
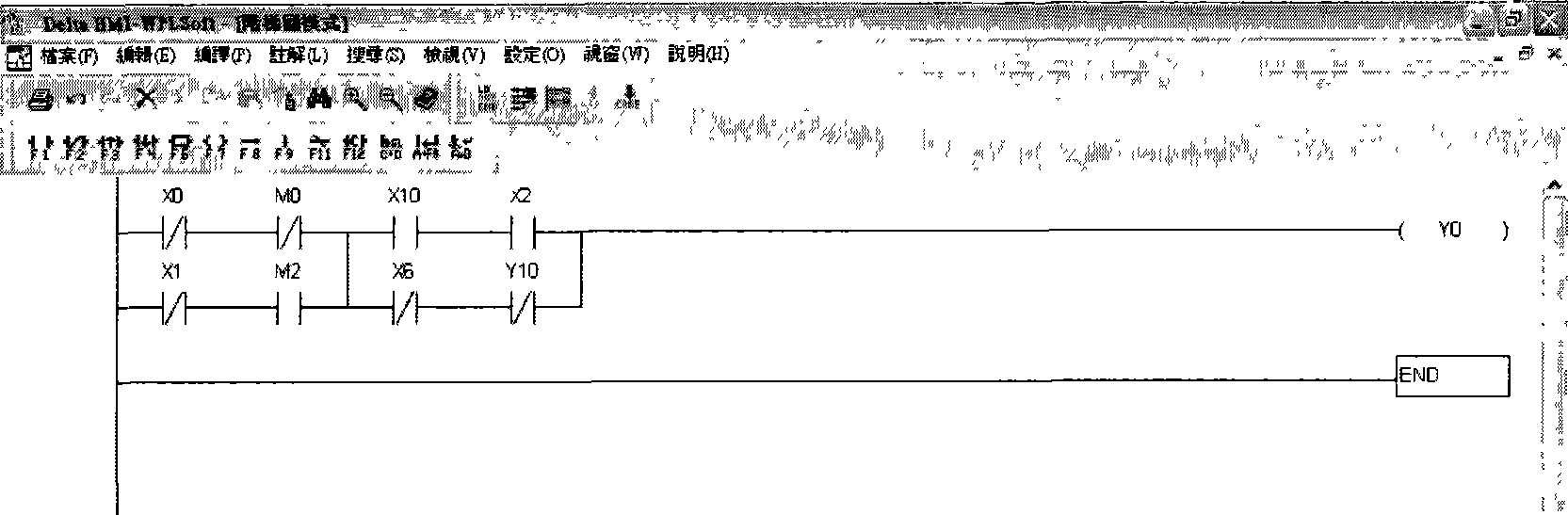
Program mechanical code compiling method for programmable logic controller
InactiveCN101382783AImprove conversion efficiencyProgramme control in sequence/logic controllersHuman–machine interfaceProgrammable logic controller
The invention relates to a program machine code compilation method of a programmable logic controller (PLC). After reading a PLC program, mnemonics codes in the program are searched. Provided that all the syntaxes of the mnemonics codes in the PLC program are logical, the PLC program is converted into a C Language file. And then the C language file is converted into a C Language target file which is linked with a library file. If the link is successful, a link file is converted into a machine code for being directly operated by the PLC so as to control external input and output connection points (EXIO) on a human-computer interface.
Owner:DELTA ELECTRONICS INC
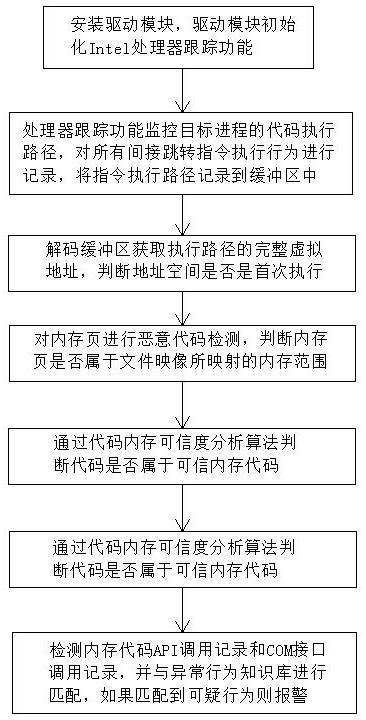
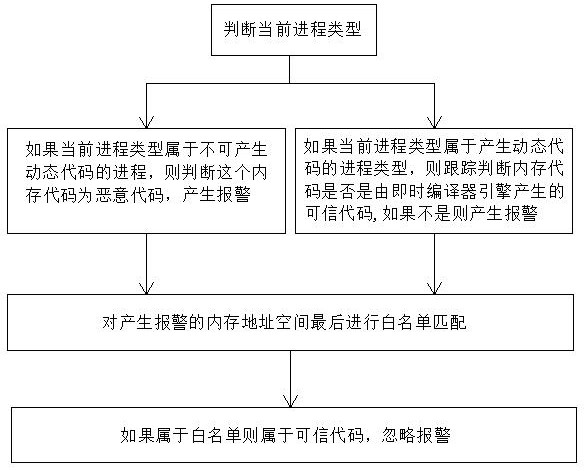
Memory malicious code detection method based on processor tracking
ActiveCN113569244AEasy to detectImprove universalityPlatform integrity maintainanceIntel processorAttack
The invention discloses a memory malicious code detection method based on processor tracking, which belongs to the technical field of information security, and is characterized by comprising the following steps that: a, a driving module initializes an Intel processor tracking function; b, monitoring a code execution path of a target process; c, decoding a buffer area to obtain a complete virtual address of the execution path; d, carrying out malicious code detection on a memory page; e, judging whether the code belongs to a trusted memory code or not; and f, detecting a memory code API calling record and a COM interface calling record, and matching the memory code API calling record and the COM interface calling record with an abnormal behavior knowledge base. Common scenes such as memory codes, shelled malicious codes, encrypted malicious code viruses and Trojan horses used in file-free attacks can be detected, meanwhile, the method also has a detection effect on execution of shellcode codes in the vulnerability utilization process, the detection effect is good, and good universality is achieved.
Owner:COLASOFT
RFID security system
InactiveCN101561892ASensing record carriersRecord carriers used with machinesMemory codeSecurity system
In order to solve the potential security hazard problem existing in RFID, the invention provides a security system applied to an electronic tag. The security system comprises an RFID chip, a reader and an unsymmetrical cryptographic algorithm, wherein the RFID chip is provided with tag memory codes of a Faraday cup and a memory switching key; the reader is provided with a detector; and the unsymmetrical cryptographic algorithm with the following improvement is arranged between the RFID chip and the reader. The algorithm comprises the steps of initially permuting, inversely permuting, transmitting a Query authentication request to the electronic tag by the electronic tag reader, generating H(IDkIIR), putting forward a request for obtaining all electronic tag marks to a backend database by the electronic tag reader, automatically marking the electronic tag reader by the backend database, authenticating the electronic tag reader, verifying the electronic tag, and the like.
Owner:BEIJING ZHONGSHI XINHUA TECH
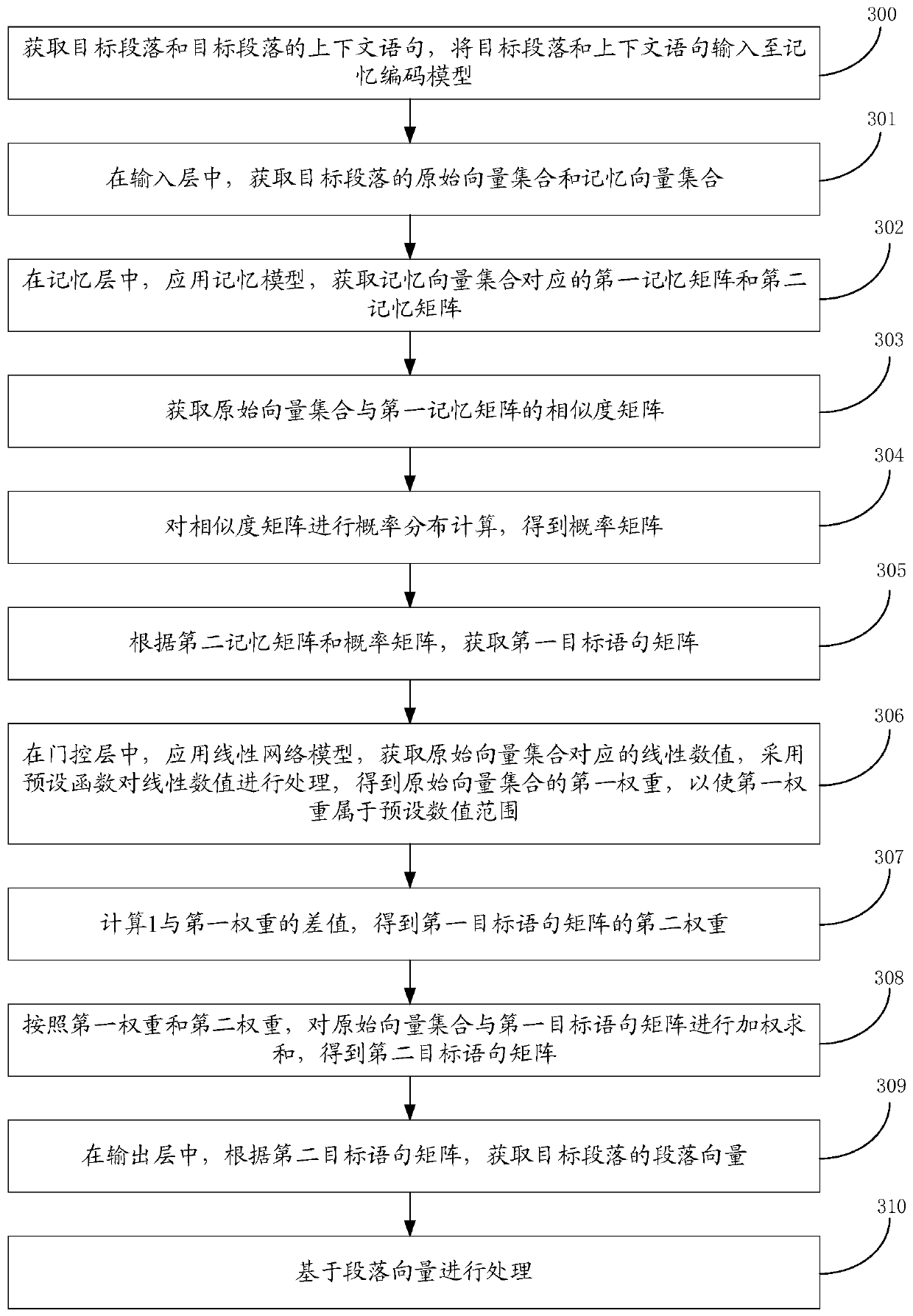
Coding method, device and equipment, and storage medium
ActiveCN110147533AImprove encoding speedImprove coding accuracyDigital data information retrievalSemantic analysisAlgorithmMemory code
The embodiment of the invention discloses coding method, device and equipment, and a storage medium, and belongs to the field of natural language processing. The coding method comprises the steps: obtaining a target paragraph and a context statement of the target paragraph, and inputting the target paragraph and the context statement into a memory coding model; and obtaining an original vector setand a memory vector set in an input layer, obtaining a first target statement matrix of the original vector set in a memory layer according to the original vector set and the memory vector set, obtaining a paragraph vector of a target paragraph according to the first target statement matrix in an output layer, and carrying out processing based on the paragraph vector. And each statement is codedby taking the target paragraph as a unit, so that the coding speed is increased. Moreover, in the coding process, the target paragraph itself is considered; the context statement of the target paragraph is also considered; the paragraph vector for accurately describing the target paragraph can be obtained according to the association relationship between the statement in the target paragraph and the context statement; and the coding accuracy is improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
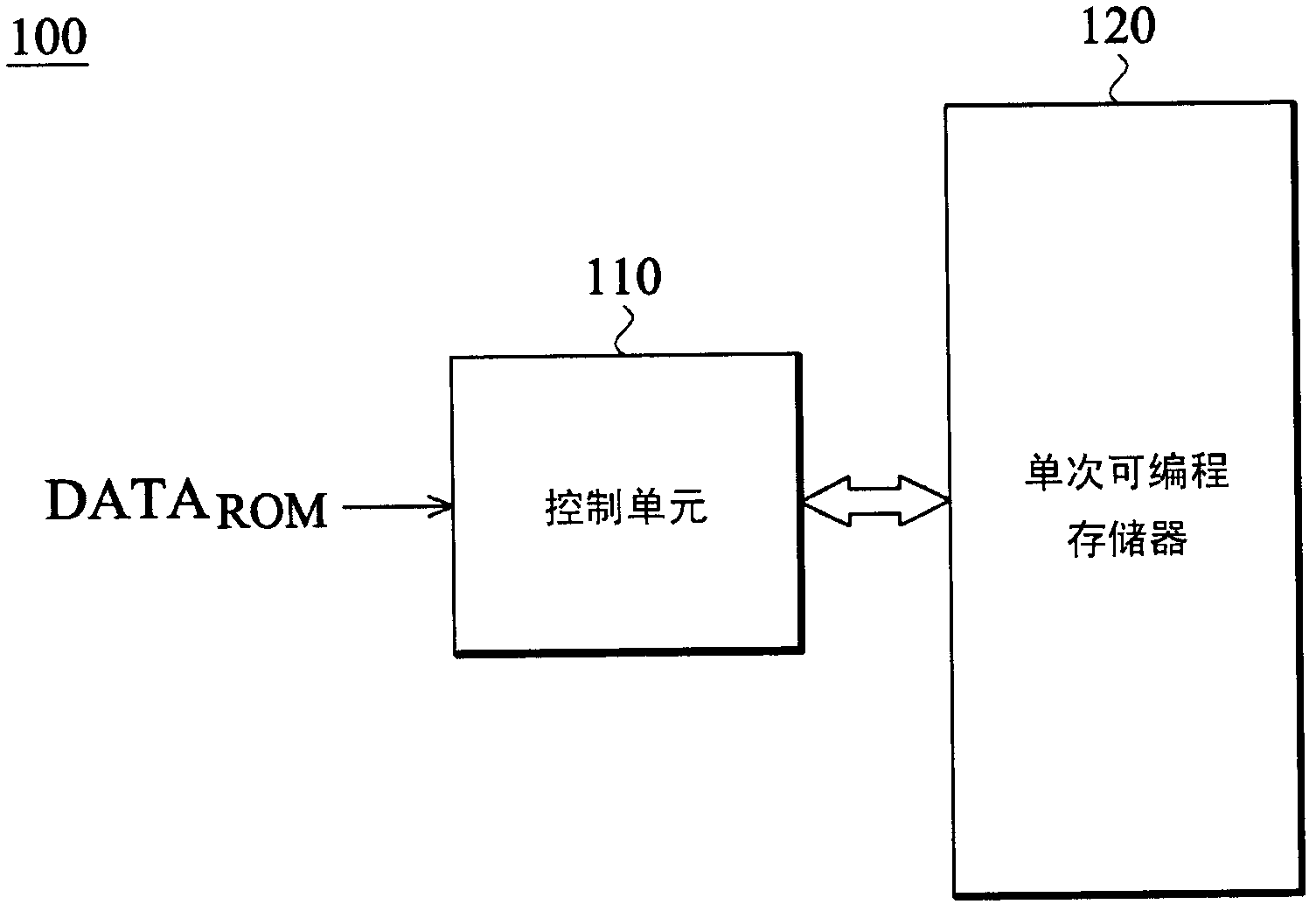
Datum programming circuit for one-time programmable memory and method thereof
The invention relates to a datum programming circuit for a one-time programmable memory and a method thereof. The datum programming circuit comprises a one-time programmable memory and a control unit. The control unit stores multiple segments of a reading only memory code to an unused space in the one-time programmable memory, and corresponds with same content segments in the multiple segments. The control unit stores a specific address to the one-time programmable memory.
Owner:SILICON MOTION INC (CN)
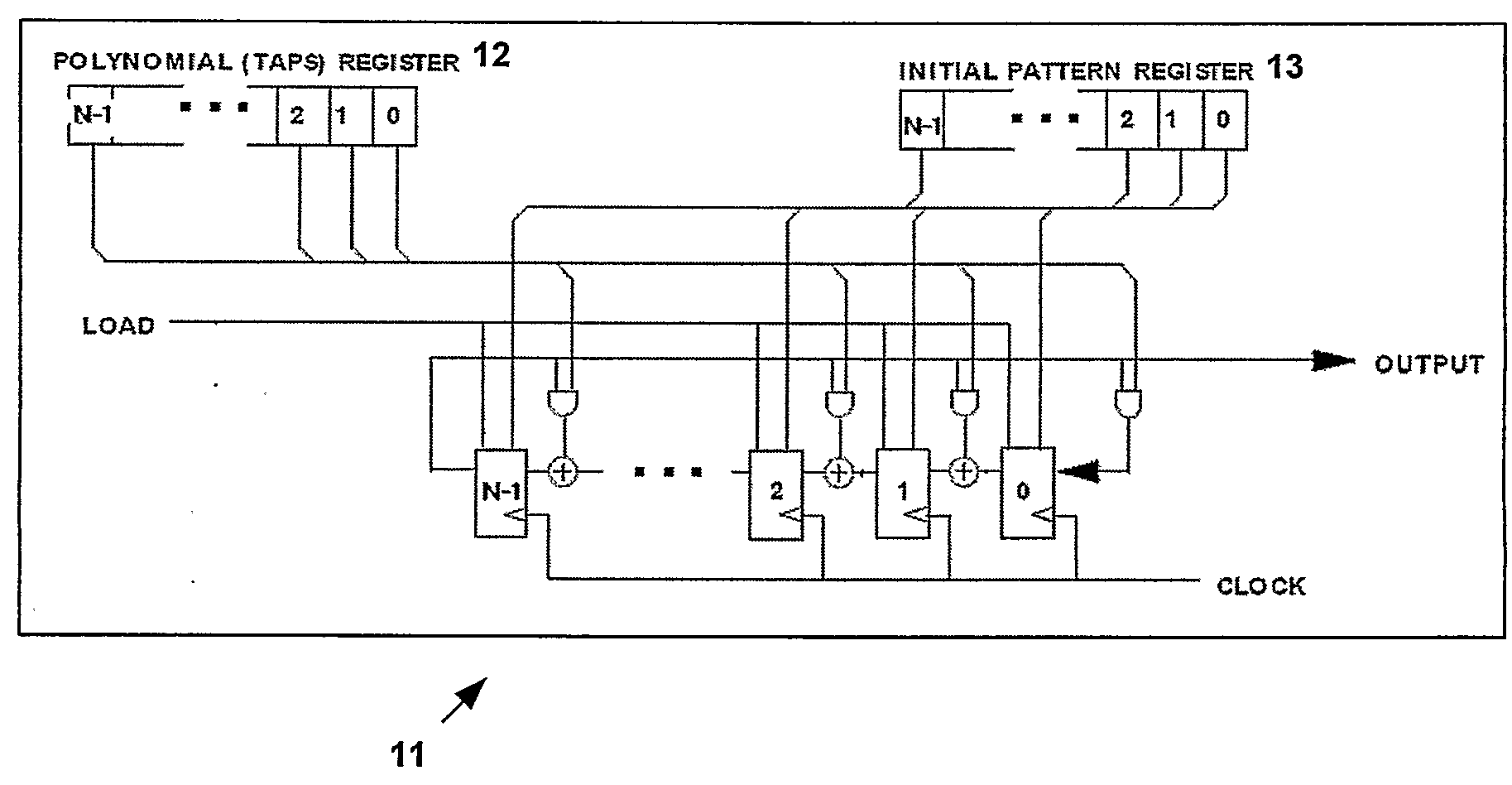
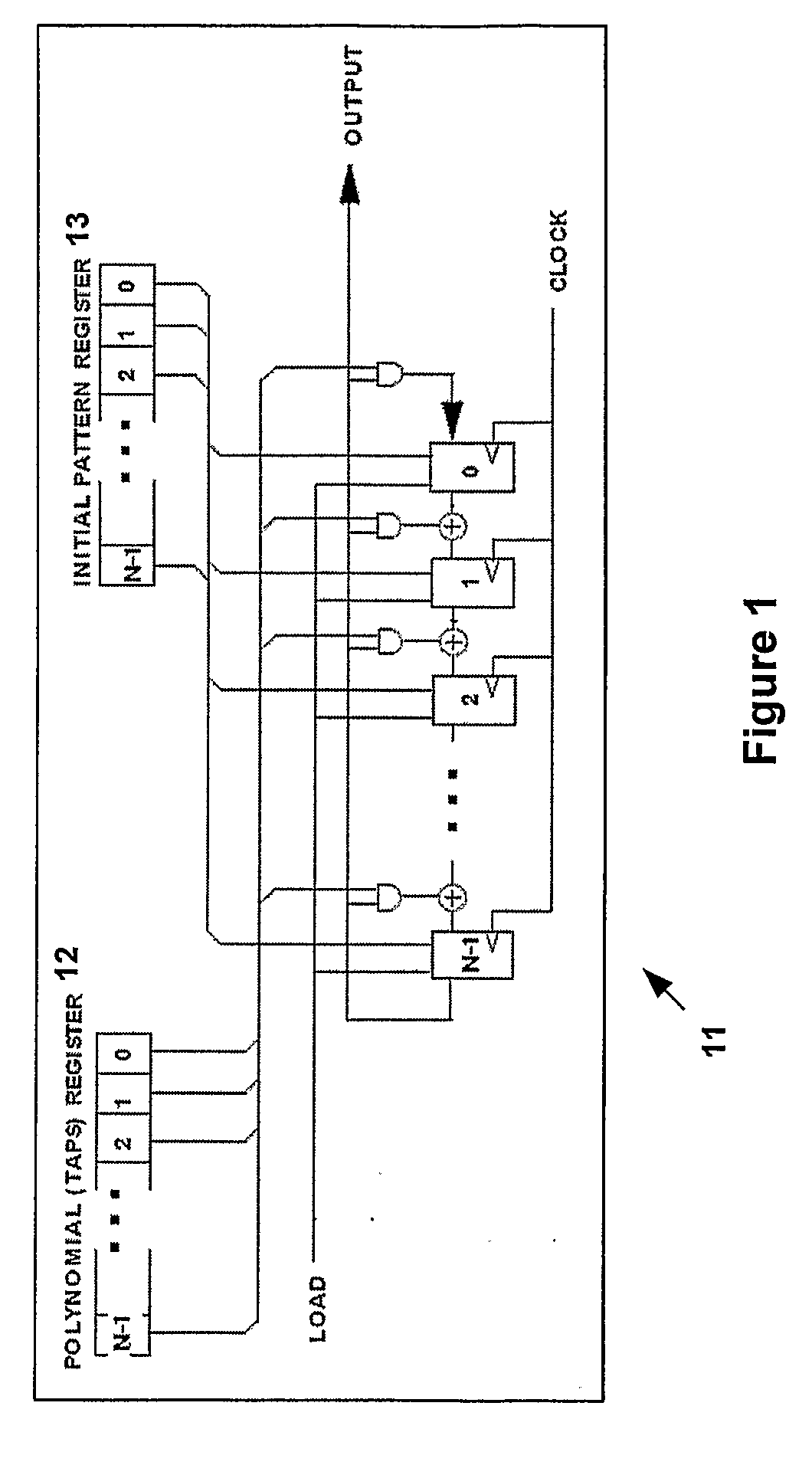
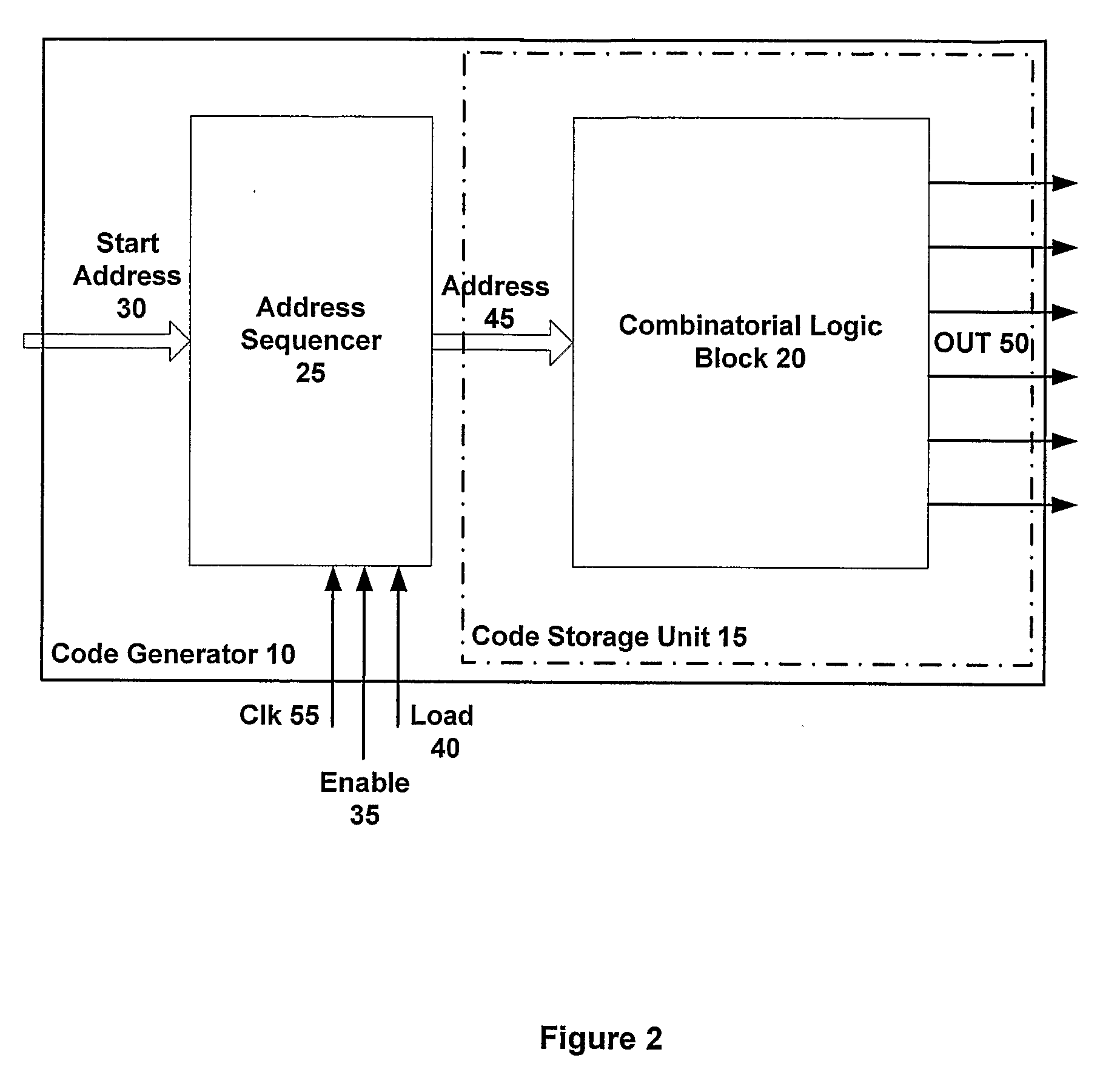
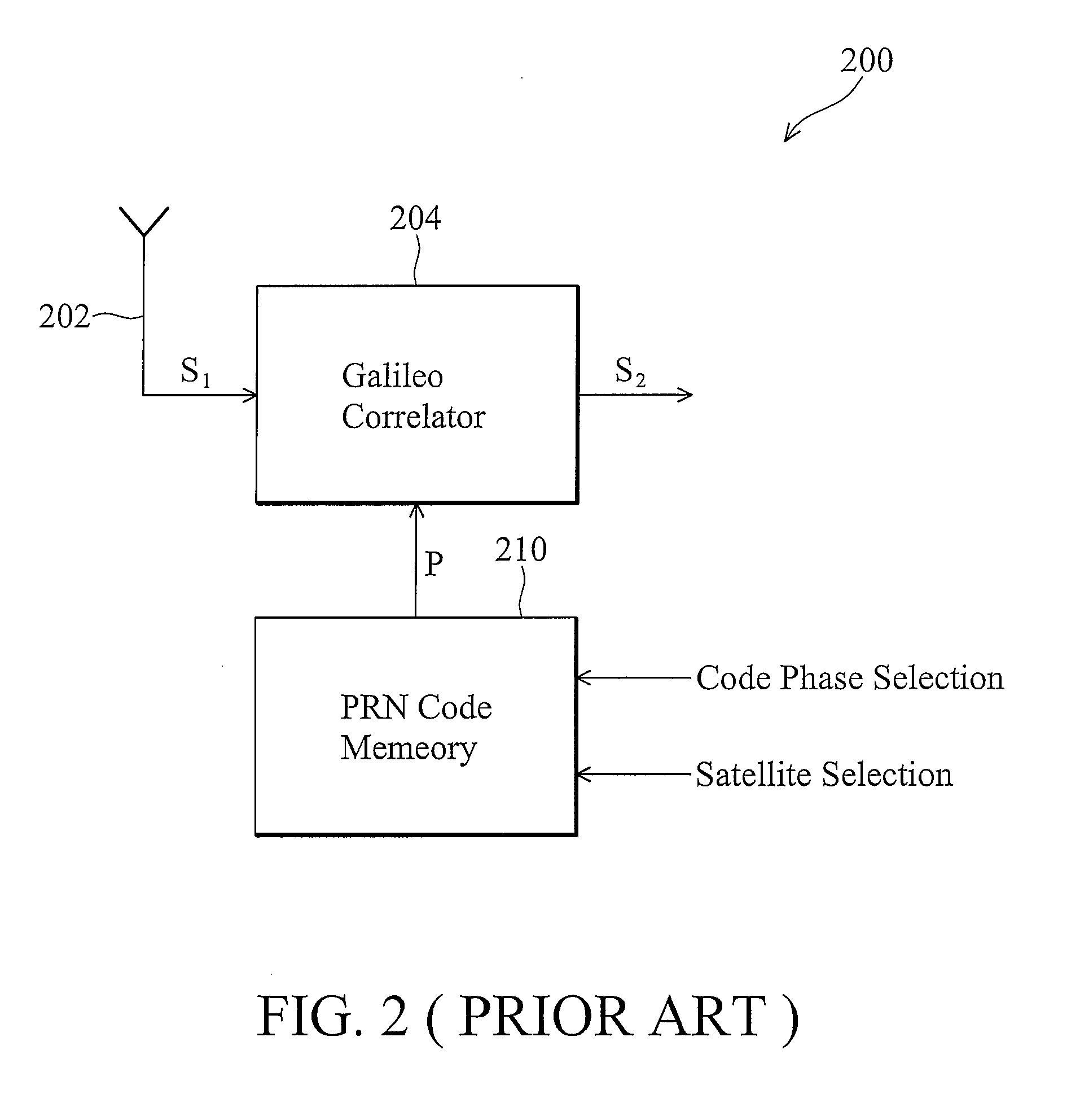
Receiver and transmitter for use in a satellite navigation system
ActiveUS20090147835A1Increase speedAvoid the needPosition fixationBeacon systemsMemory codeTransmitter
A receiver is provided for use with a satellite navigation system comprising a constellation of multiple satellites. Each satellite transmits a signal incorporating a spreading code. The receiver includes at least one code storage unit that includes combinatorial logic for storing a memory code comprising a fixed pattern of bits including address decoding, wherein the stored memory code corresponds to a spreading code incorporated into a signal transmitted from a satellite. The receiver further includes a correlator for performing a correlation between an incoming signal and the stored spreading code from the one code storage unit.
Owner:EUROON SPACE AGENCY
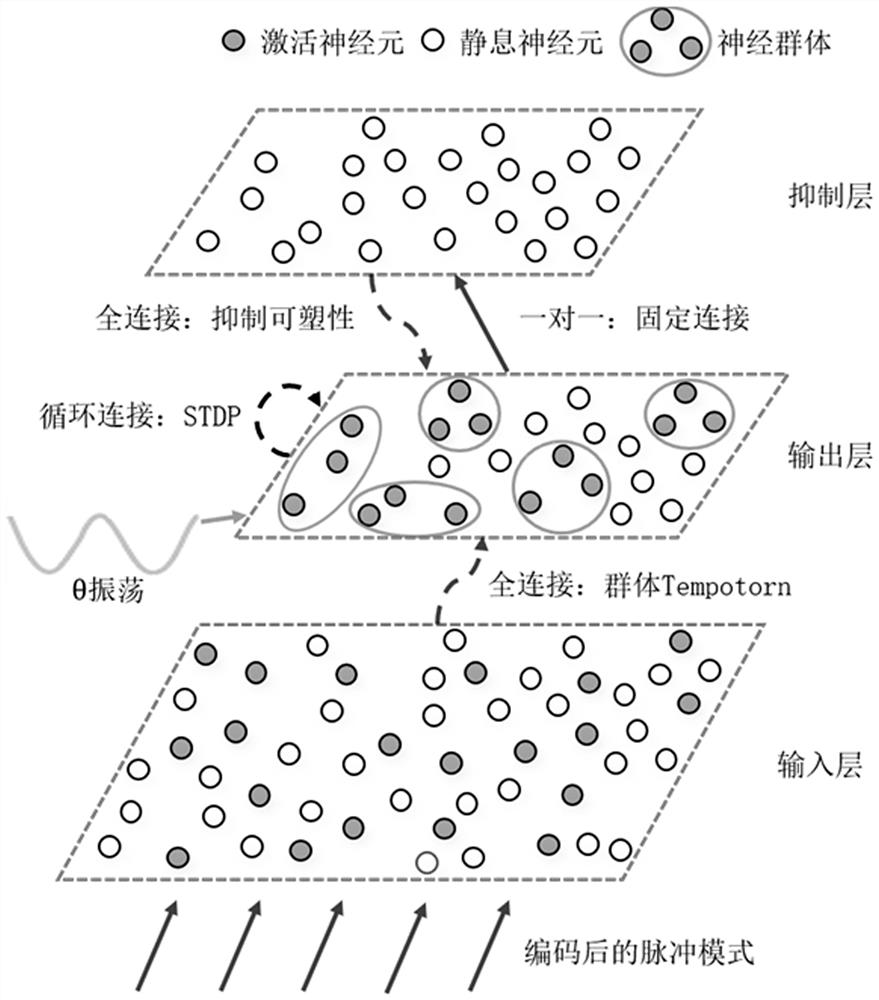
Fast memory coding method and device based on multi-synaptic plasticity spiking neural network
PendingCN114118383AImprove encoding speedImprove stabilityNeural architecturesPhysical realisationSynaptic weightPulse sequence
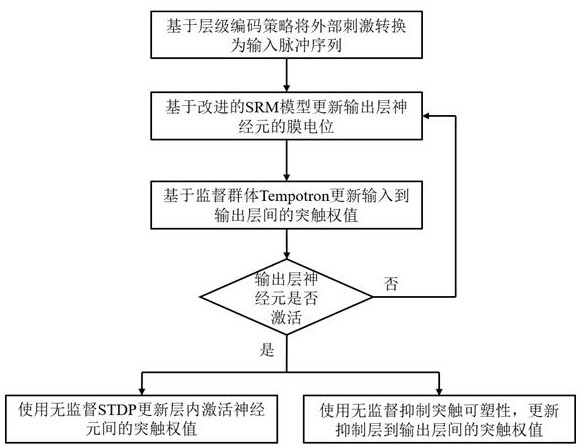
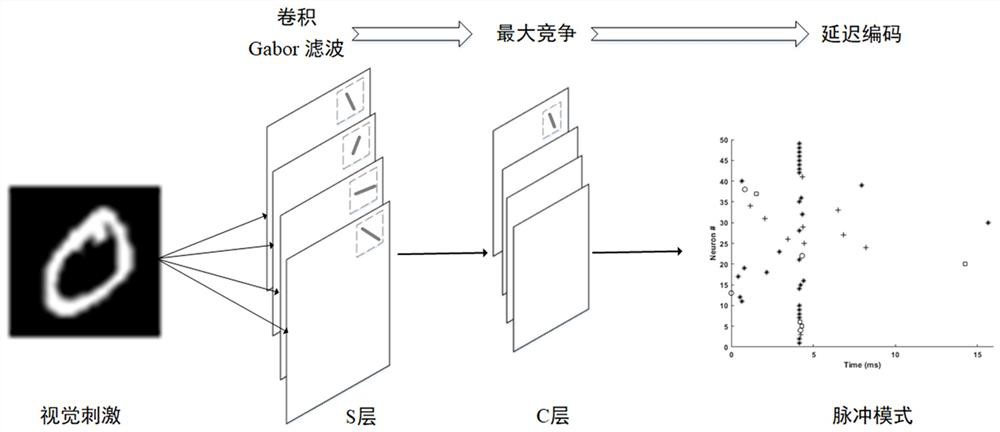
The invention provides a fast memory coding method based on a multi-synaptic plasticity pulse neural network. The fast memory coding method comprises the steps of 1, converting external stimulation into an input pulse sequence based on a hierarchical coding strategy; 2, after the pulse neural network receives an input pulse, updating a membrane potential of neurons of an output layer based on an improved SRM model; 3, updating a synaptic weight input to an output layer by using a supervisory group Tempotron, and activating neuron memory input of the output layer; step 4, after the neurons of the output layer are activated, using the unsupervised STDP to update synaptic weights among the activated neurons in the layer, and forming an enhanced cyclic sub-network storage memory; and step 5, while executing the step 4, using unsupervised inhibition synaptic plasticity, updating a synaptic weight between an inhibition layer and an output layer, and inhibiting separation of distribution time of neural populations with different inputs of feedback guarantee memories. The invention further provides a fast memory coding device based on the multi-synaptic plastic spiking neural network. According to the invention, the coding speed and stability of memory are effectively improved.
Owner:ZHEJIANG LAB +1
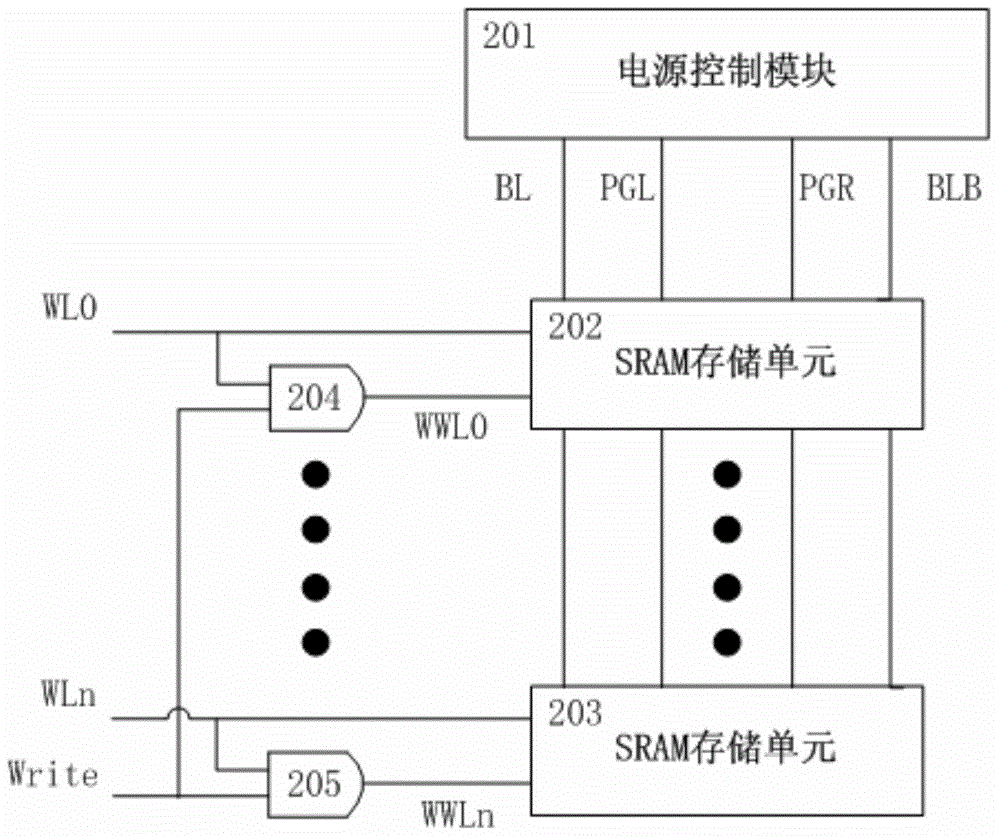
SRAM memory cell and circuit for improving read/write stability of SRAM memory cell
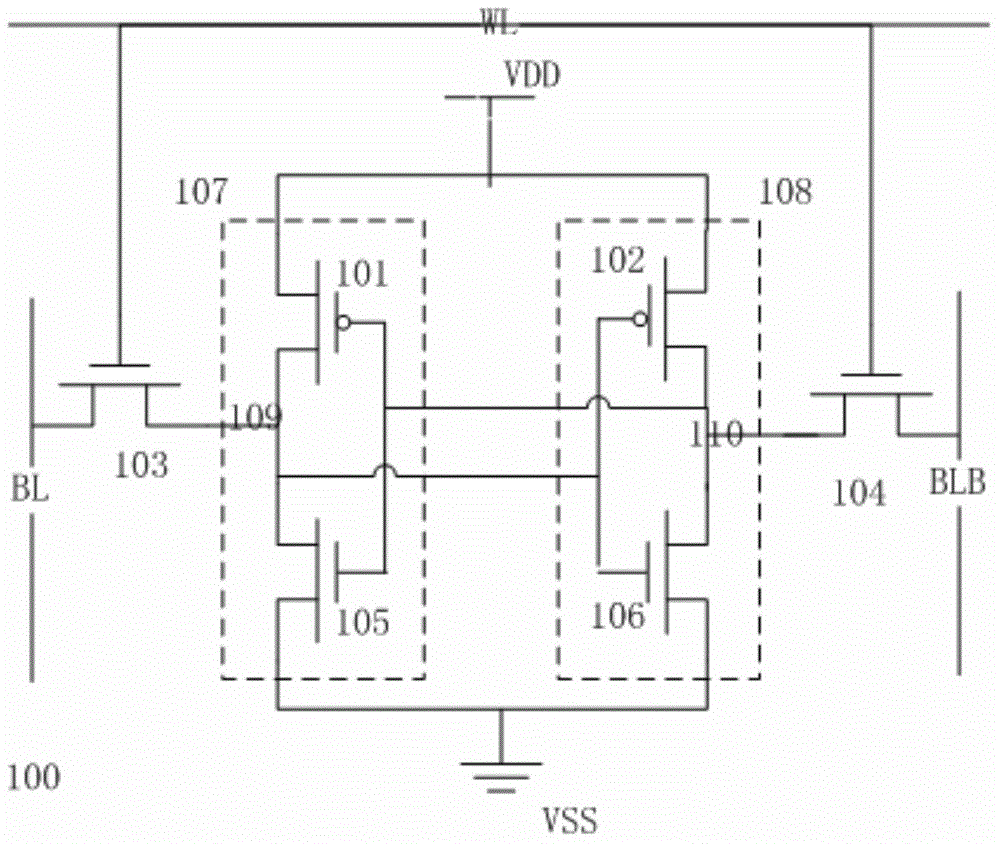
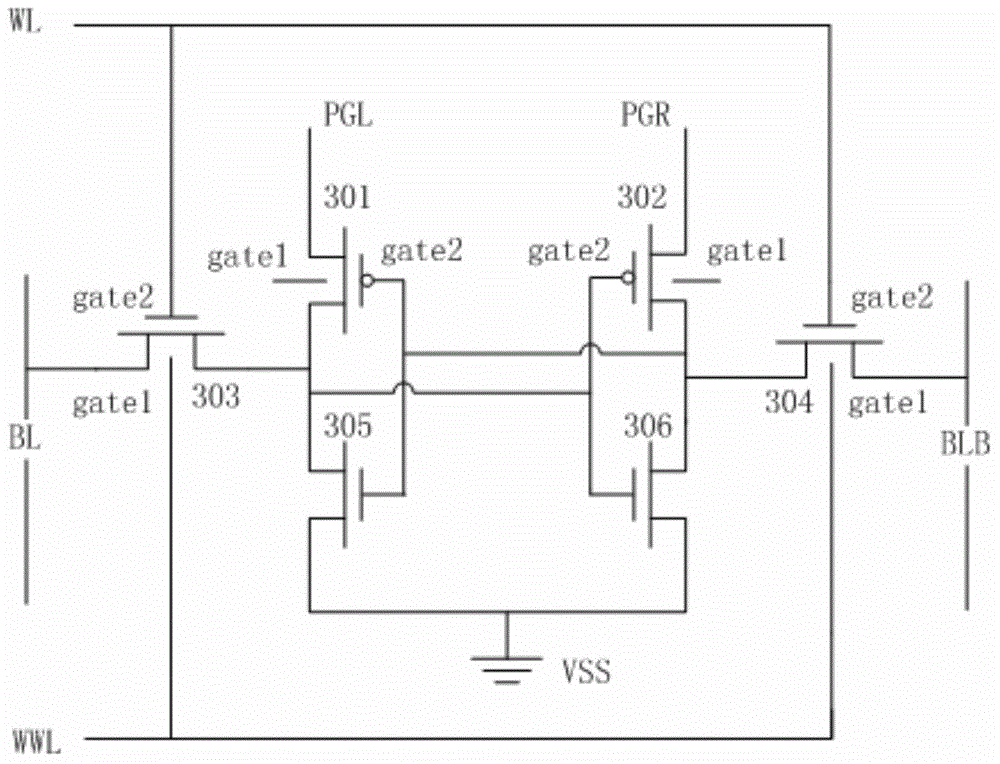
The invention relates to the technical field of electronic communication, in particular to an SRAM memory cell and a circuit for improving the read / write stability of the SRAM memory cell. The SRAM memory cell comprises a first switch device, a second switch device, a first inverse unit and a second inverse unit, wherein the first switch device is controllably connected with a first bit line to a first memory code; the second switch device is controllably connected with a second bit line to a second memory code; the first inverse unit is connected between the first switch device and the second switch device in series; the first inverse unit is provided with a first input end and a first output end; the first memory code is defined at the first output end; the second inverse unit is connected between the first switch device and the second switch device in series; a second input end of the second inverse unit is connected with the first output end; a second output end of the second inverse unit is connected with the first input end; and the second memory code is defined at the second output end. According to the SRAM memory cell and the circuit, better read / write ability is provided, the reliability of the SRAM memory cell is improved without adding overmuch extra circuits, the complexity of circuit design is reduced and the area is saved.
Owner:SPREADTRUM COMM (SHANGHAI) CO LTD
Memory coding method and apparatus
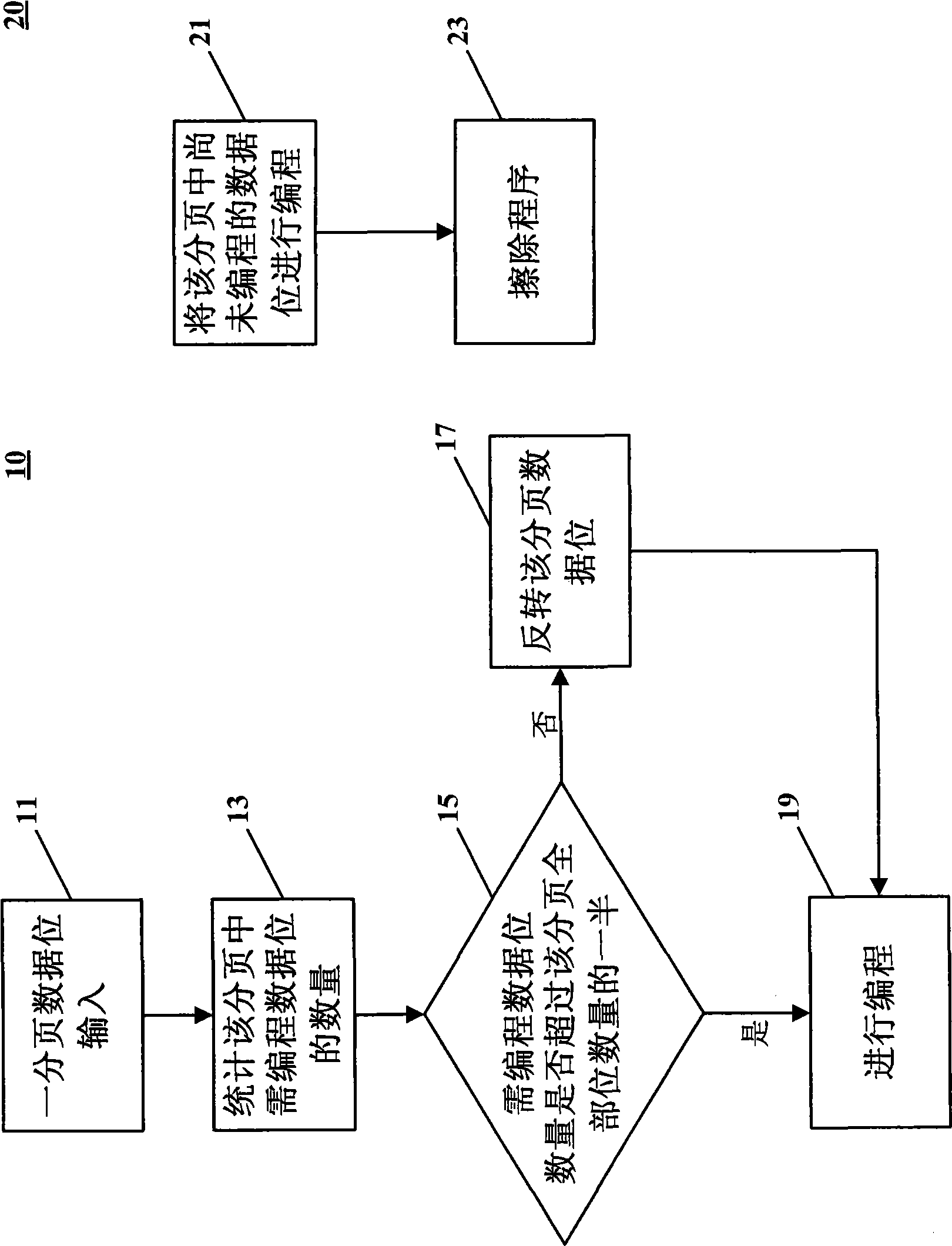
The invention of an open coding method, a memory which can be used to reduce memory loss and extend the storage life, the approach involves the following steps: A. receiving a number of binary code, which includes the binary code that need to be one of the first binary programming code with that program do not need a second binary code; B. Statistics of the number of binary code binary code in the first and the second binary code the number of at least one; C. When the second binary code the number exceeds the total number of binary code more than half, the reversal of the number of binary code; and D. The memory storage unit corresponding to the first part of binary code to program, and programming with a to check in to read bits of the inversion.
Owner:MACRONIX INT CO LTD
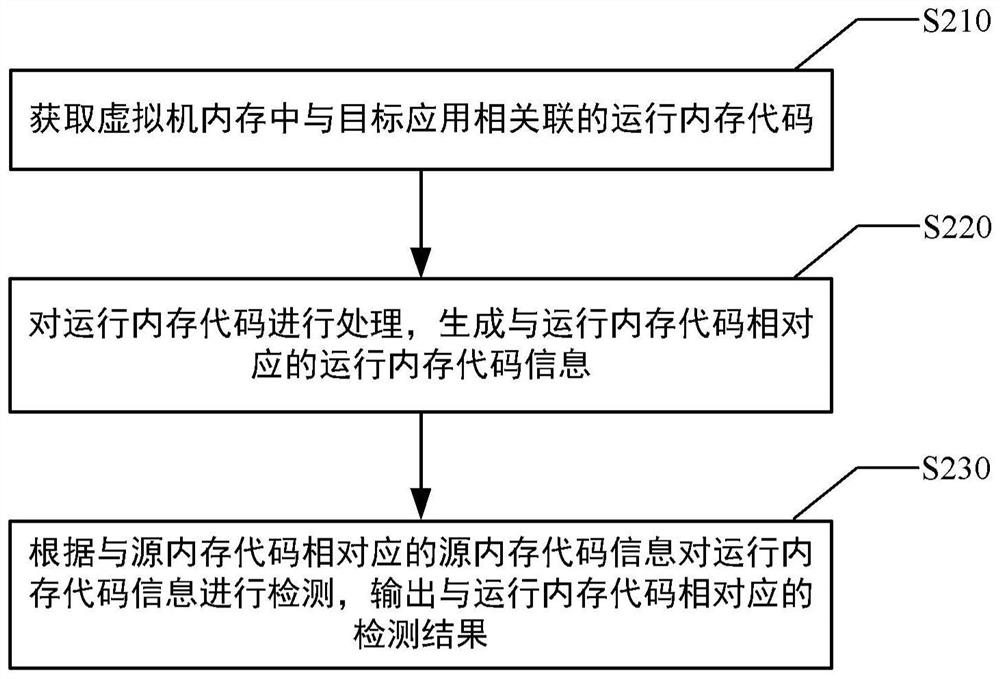
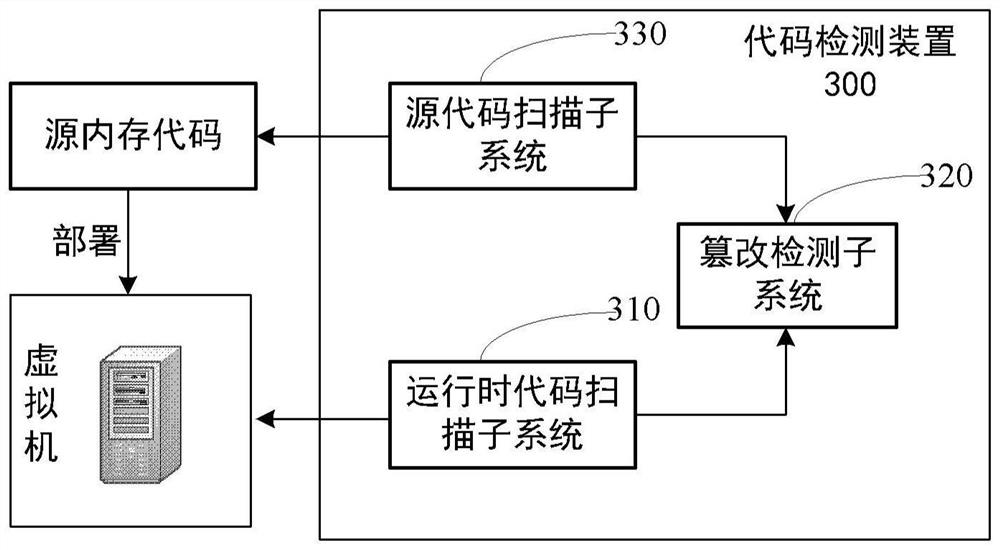
Code detection method, device, system and equipment and storage medium
The invention provides a code detection method, device, system and equipment and a storage medium, and can be applied to the fields of finance, computer technology and information security. The method comprises the steps that a running memory code associated with a target application in a virtual machine memory is obtained, and the target application runs based on the running memory code; the running memory code is processed, running memory code information corresponding to the running memory code is generated, and the running memory code information comprises a first hash value of each first byte code file in the running memory code; the running memory code information is detected according to source memory code information corresponding to the source memory code, a detection result corresponding to the running memory code is output, where the source memory code information comprises a second hash value of each second byte code file in the source memory code, and the source memory code comprises an initial running memory code of the target application.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
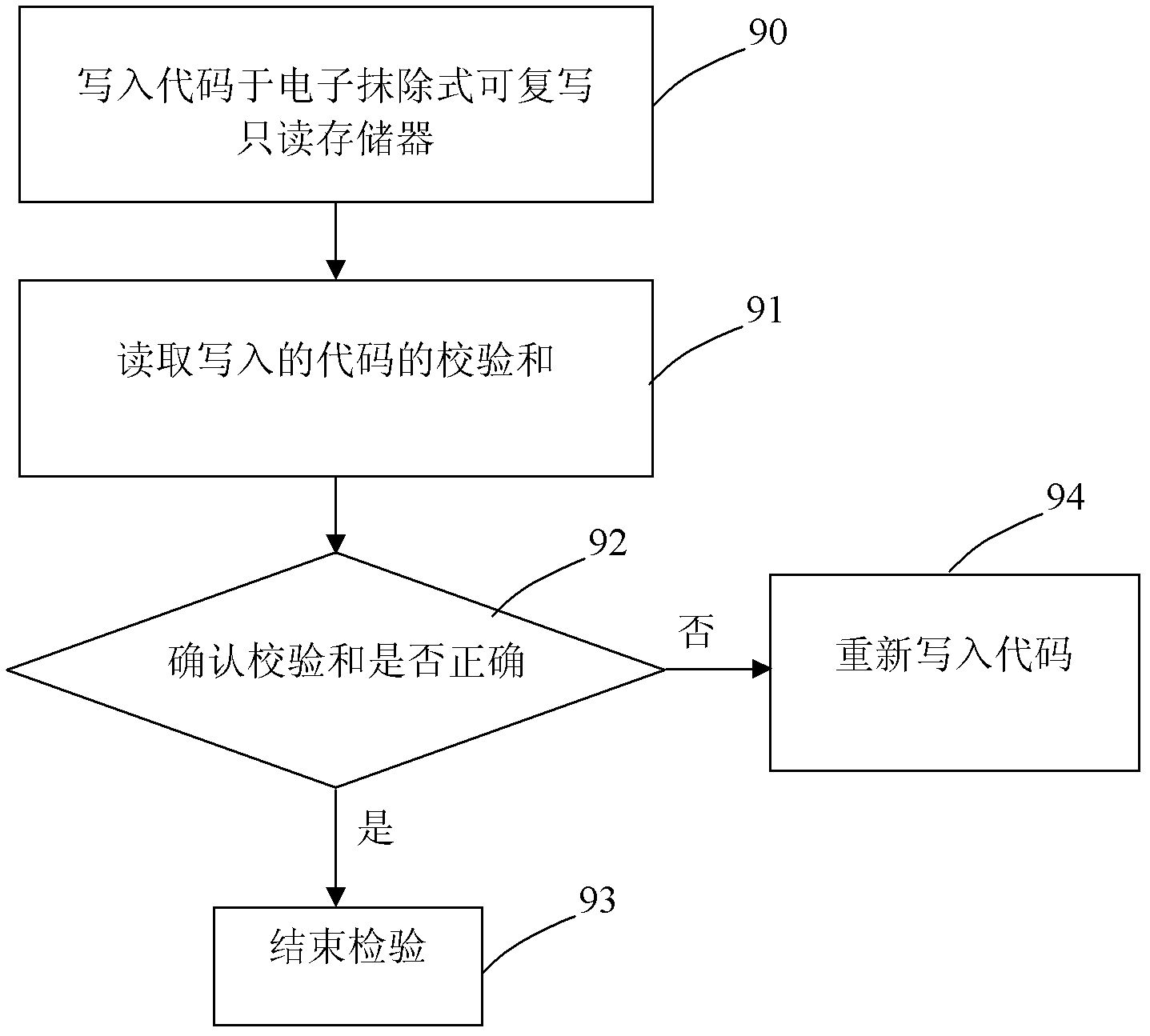
Method for examining memory code of printed circuit board
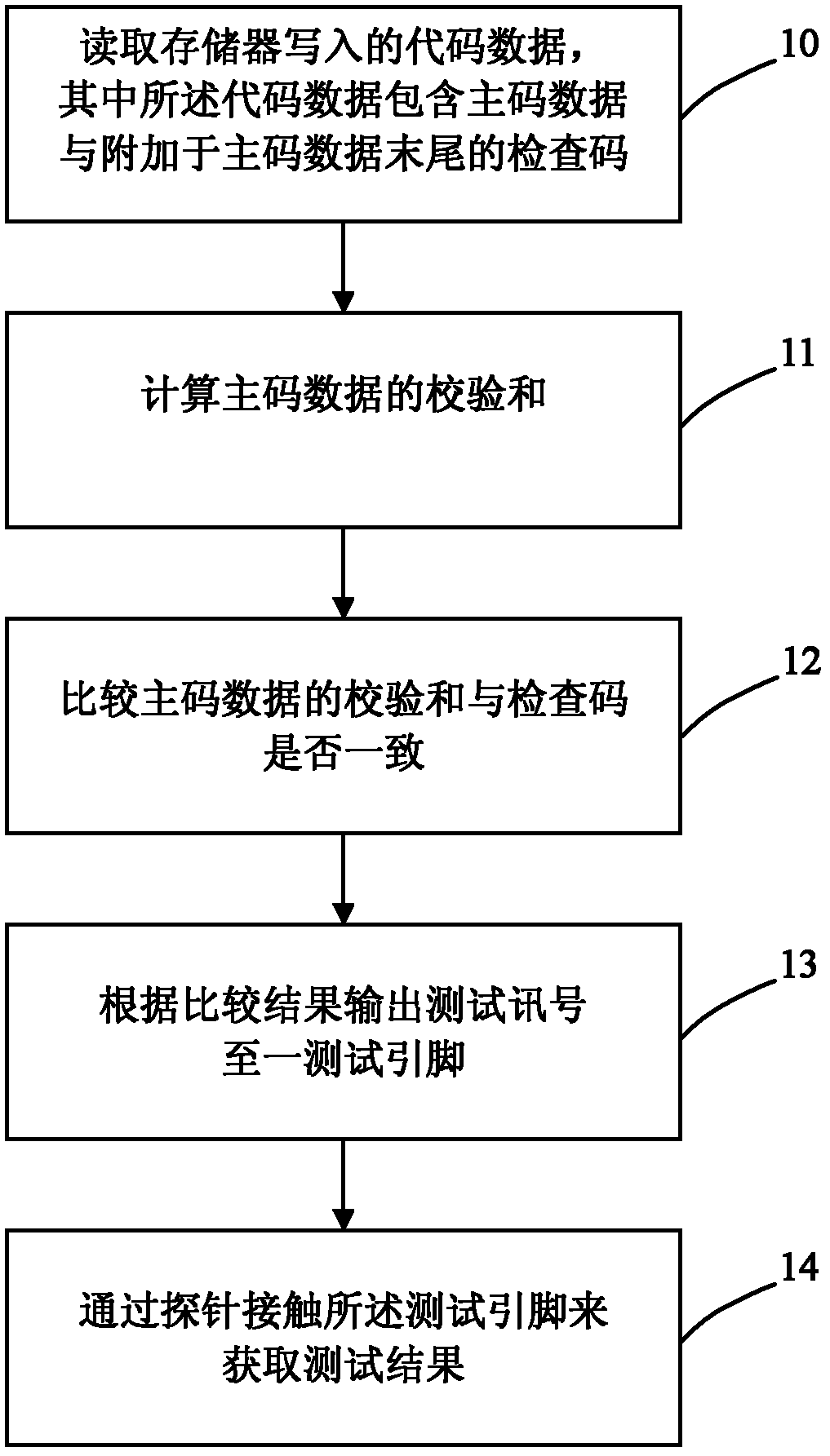
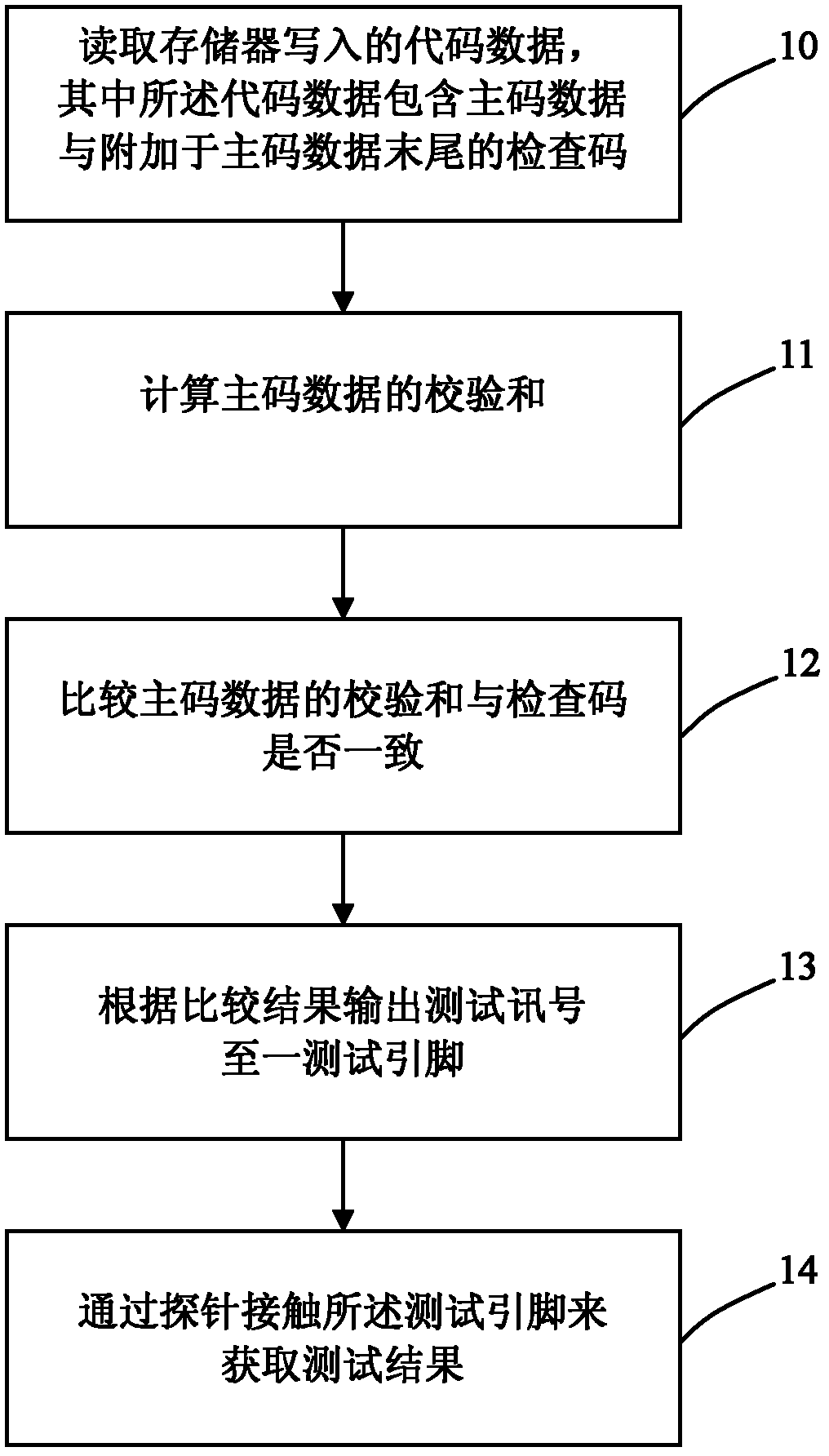
The invention discloses a method for examining a memory code of a printed circuit board, which comprises the following steps: adding a checking code at data end of the code, after writeing in a memory, calculating a checksum of the data of a main code part by a timing controller, comparing the calculated checksum and the checking code, outputting a test pin to a probe for displaying the comparison result to reach the purpose of examining whether the write-in code is correct or not. The method of the invention is capable of enhancing the work efficiency of the write-in code examination in the memory.
Owner:SHENZHEN CHINA STAR OPTOELECTRONICS TECH CO LTD
Multiple anti-forge ink with memory code and testing method thereof
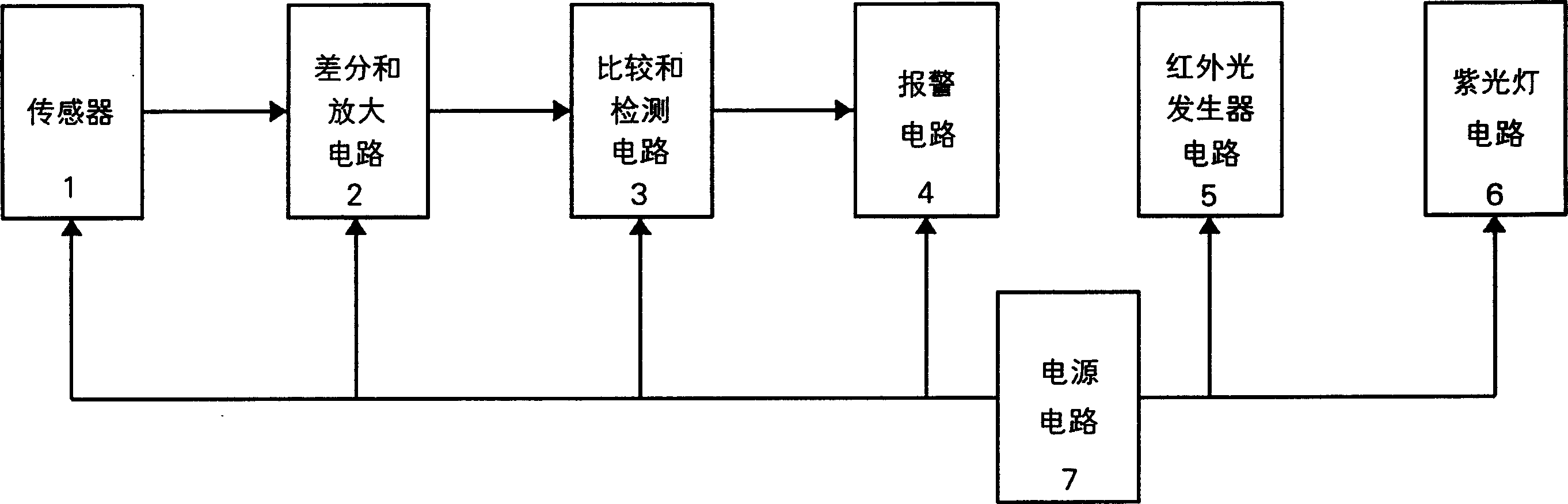
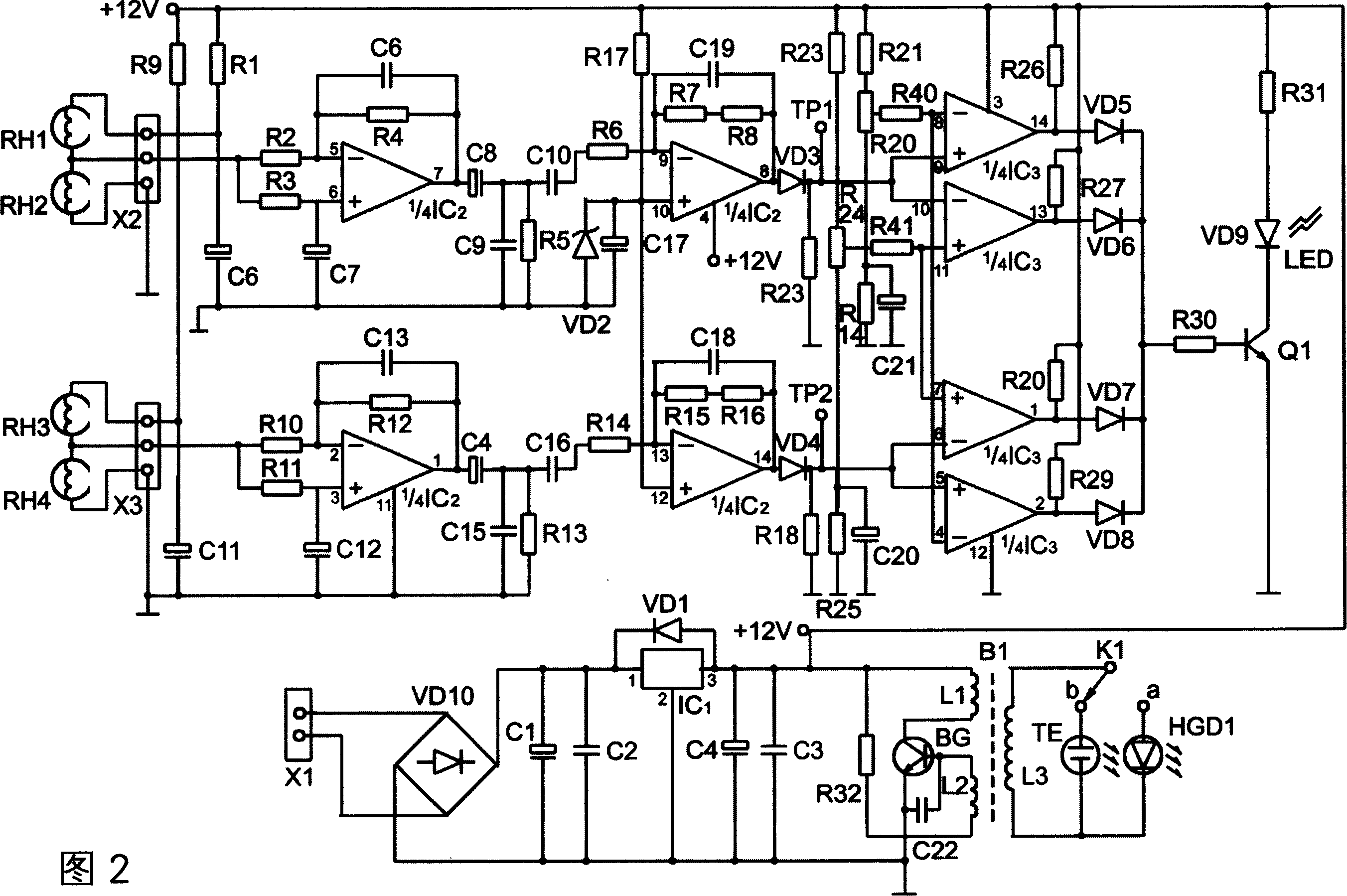
The invention is a multiple anti-falsification ink with a memory code and a method of detecting the ink marks of writing with it, synthesized of general ink, magnetic memory material, infrared fluorescent material and UV fluorescent material, etc. and the detecting method: making magnetic-electric conversion on the code information in the magnetic material in the ink marks and detecting, identifying the code information, and the infrared light generator excites infrared fluorescent information in the ink marks and the UV light of the UV lamp excites long-short wavelength UV fluorescent information in the ink marks. It has good anti-falsification effect, and the handwriting contains an electromagnetic code, infrared fluorescent information and UV fluorescent information, detected by special apparatuses and the code has uniqueness, so that the falsifier is difficult to simulate, thus able to effectively the occurrence of forging signatures, altering, forging written pledges, and other illegal activities. It is applied to important bills of documents and notes, signature, contracts and documents, etc.
Owner:熊春宁
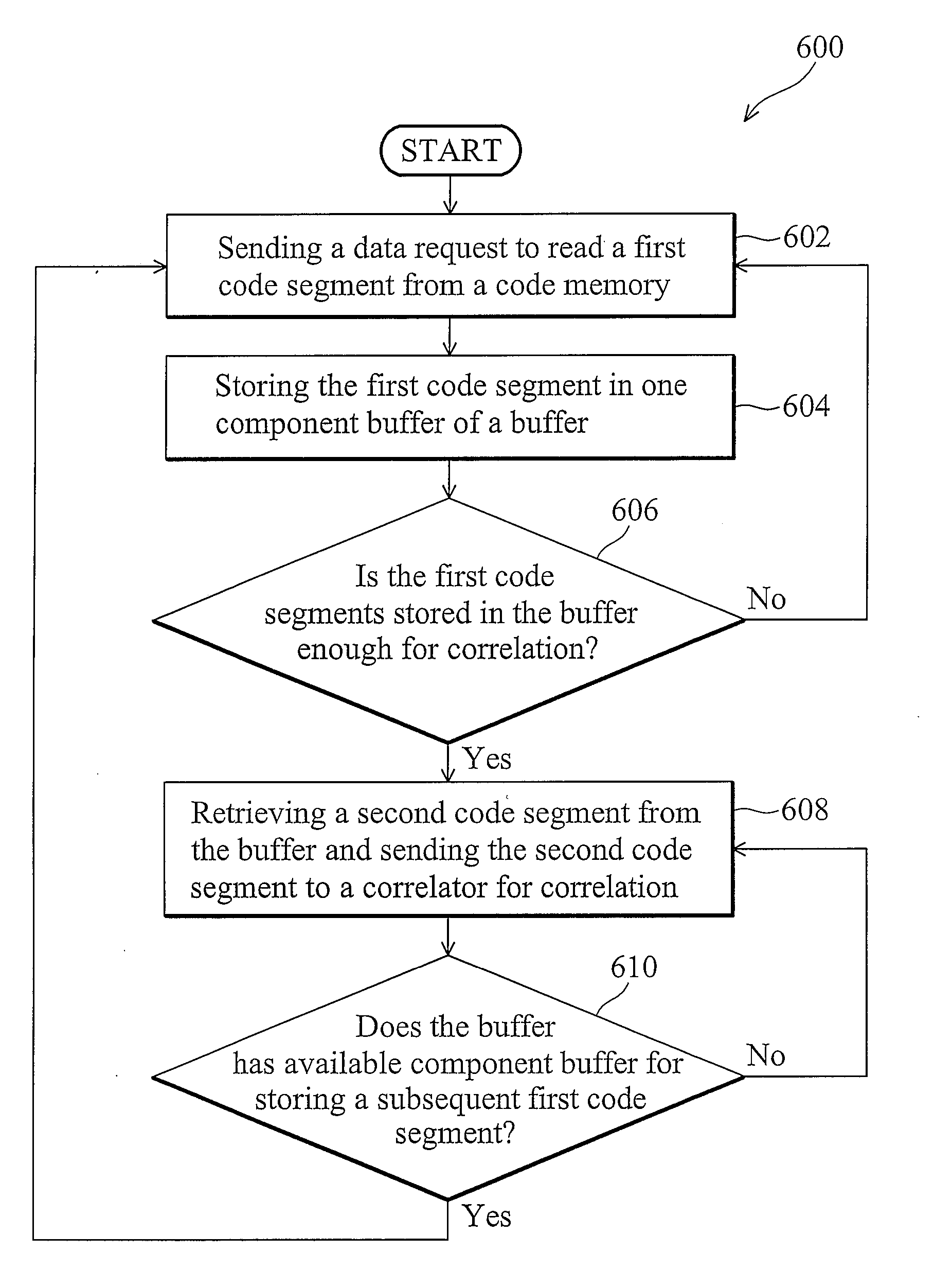
GNSS receiver and method for GNSS memory code generation
The invention provides a Global Navigation Satellite System (GNSS) receiver. In one embodiment, the GNSS receiver comprises a memory, a buffer, a correlator, and a selector. The memory stores a memory code and outputs a portion of the memory code as a first code segment. The buffer comprises a plurality of component buffers and stores the first code segment into one of the component buffers in order. The selector selects a portion of the first code segments stored in the buffer as a second code segment output to the correlator according to the code phase selection signal, wherein the data length of the second code segment is equal to a correlation data length of the correlator. The correlator calculates a correlation between a received GNSS signal with the correlation data length and the second code segment.
Owner:MEDIATEK INC
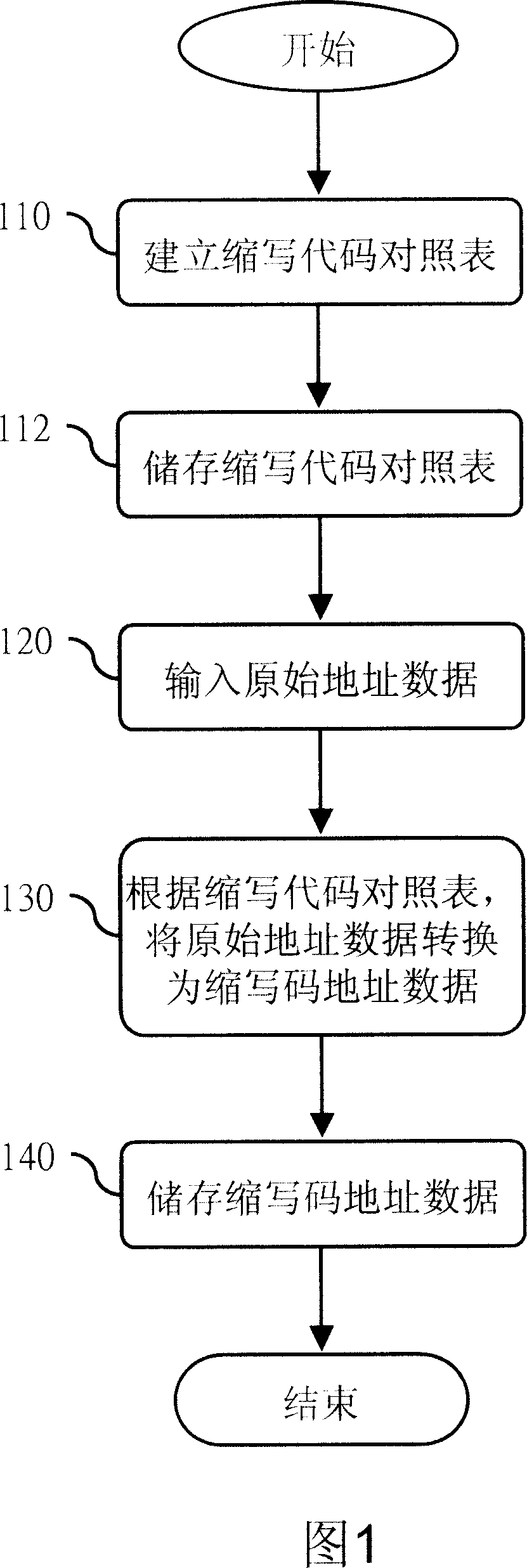
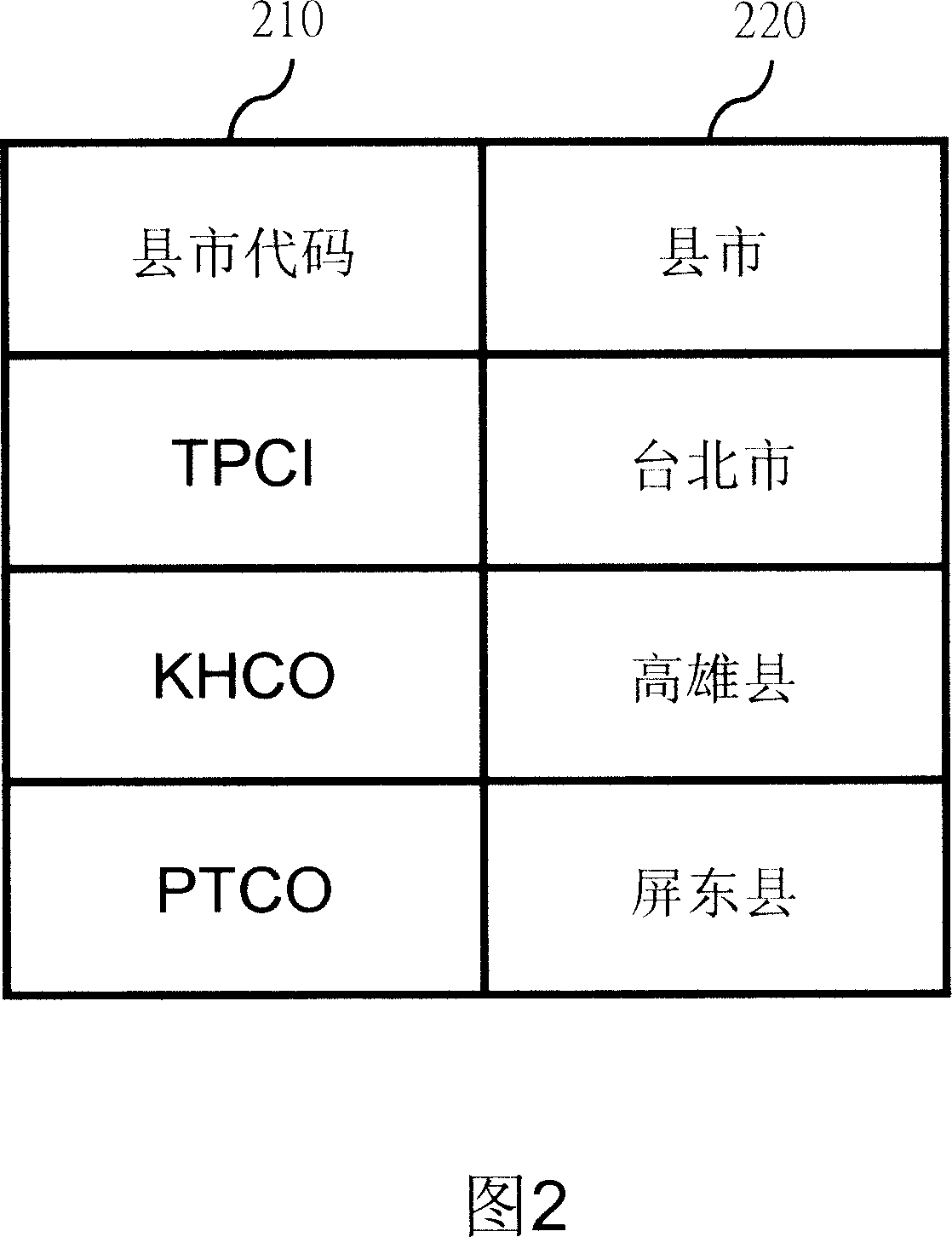
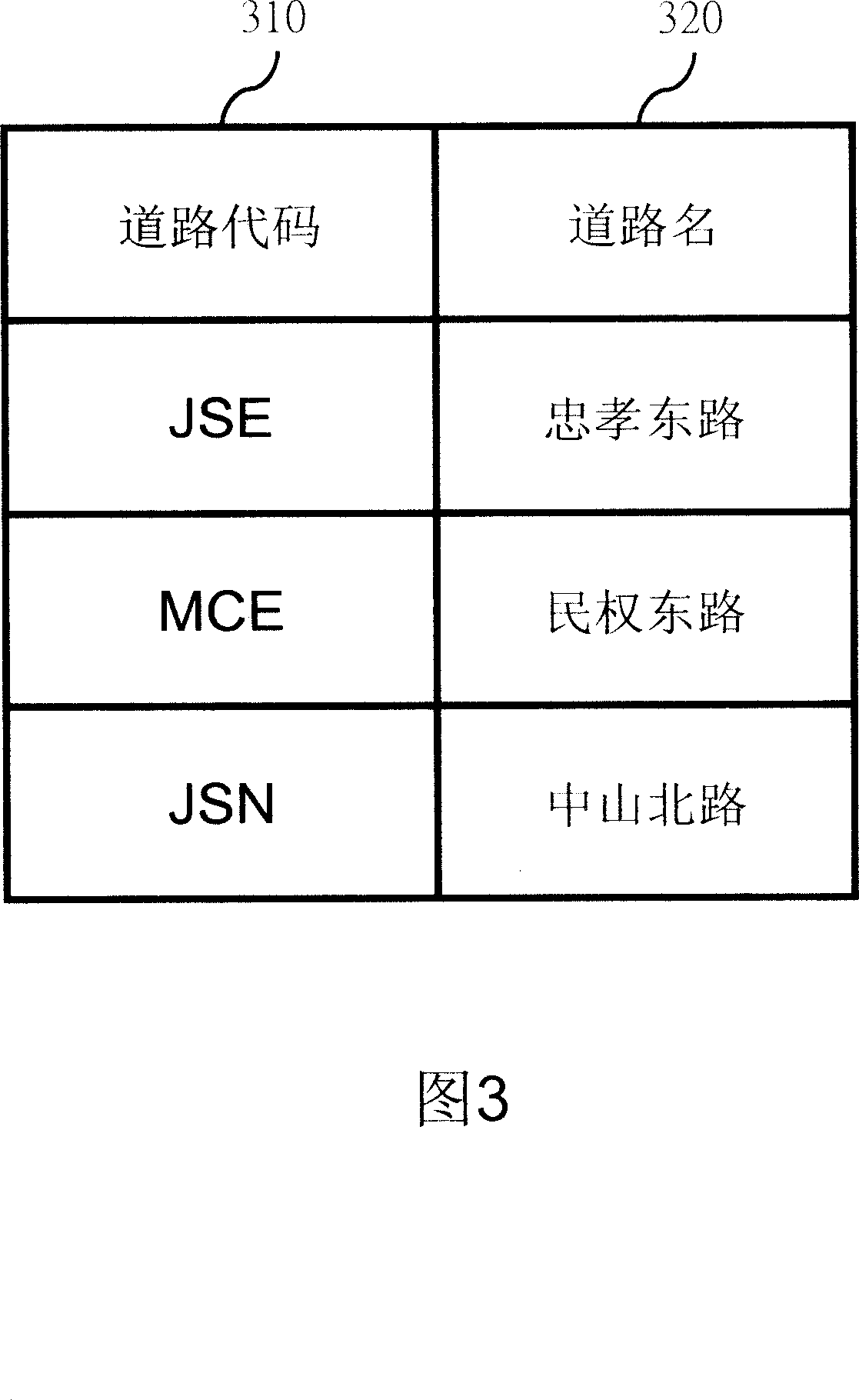
Method of transforming original address date for reducing address memory space with the code
InactiveCN101017487ASave storage spaceSpecial data processing applicationsMemory codeData conversion
This invention relates to one method to reduce address memory space by use of code type to convert original address applied in digital move device, which comprises the following steps: firstly, establishing compression codes list; then user inputting any detail complete address data; through compression code comparison list converting the original address data into compression codes address data; finally, converting the memory codes form address data to reduce address memory space.
Owner:HUANDA COMPUTER (SHANGHAI) CO LTD +1
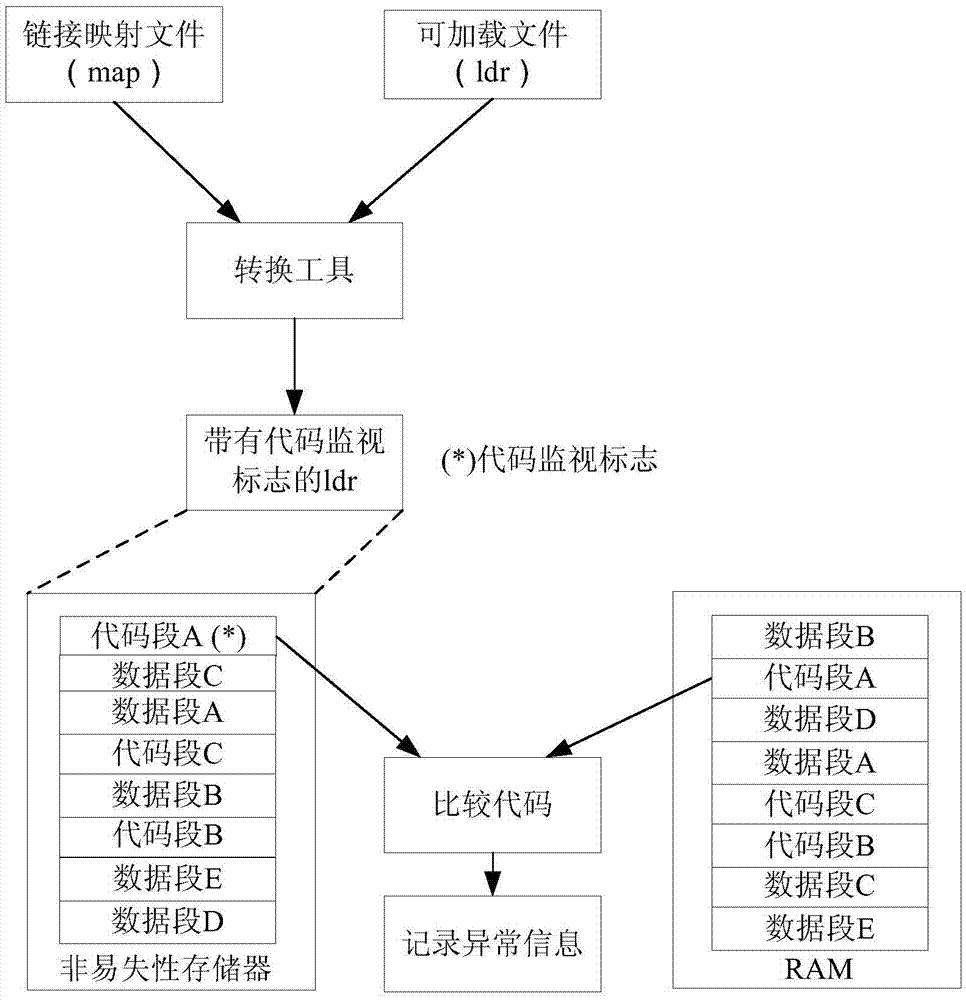
ADI DSP code online monitoring method
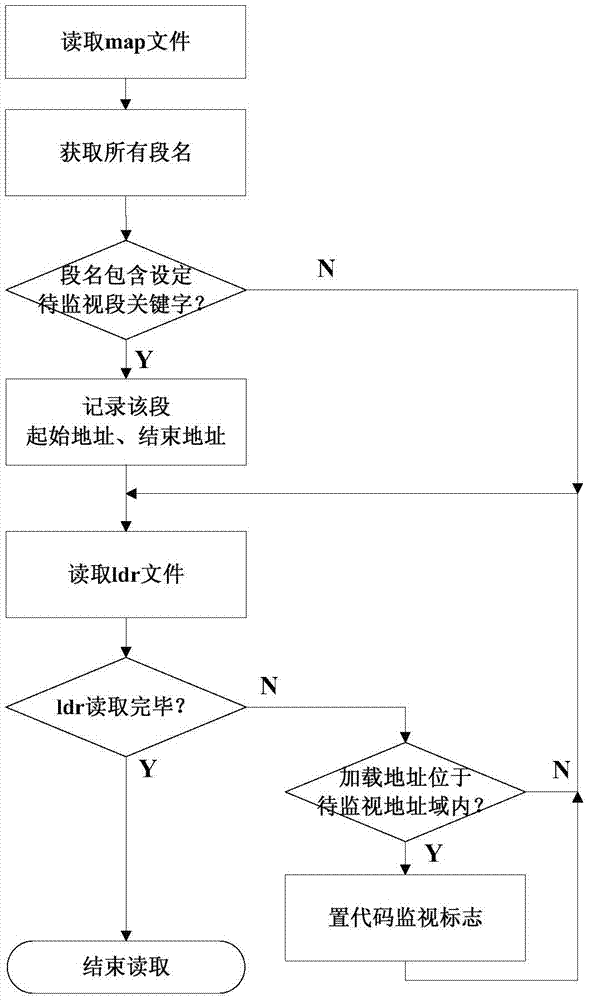
ActiveCN105446842ARealize online monitoringImprove securityDetecting faulty computer hardwareSoftware testing/debuggingParallel computingMemory code
The invention discloses an ADI DSP code online monitoring method. The method comprises: according to a DSP link mapping file, adding a code monitoring mark to a to-be-monitored code in a loadable file of a DSP; during operation, the DSP continuously reading an LDR in a nonvolatile memory, and if a code monitoring mark is discovered, comparing a nonvolatile memory code with a running code in an RAM; if the nonvolatile memory code is not consistent with the running code in the RAM, performing repeated check; and if it is determined that the nonvolatile memory code is consistent with the running code in the RAM, determining that the running code of the RAM has an error, instantly taking an alarming measure and recording error information into the nonvolatile memory for failure analysis. According to the method, the running code can be monitored online by simply modifying an LDR file.
Owner:NR ELECTRIC CO LTD +1
Integrity verification system using remote code execution and method thereof
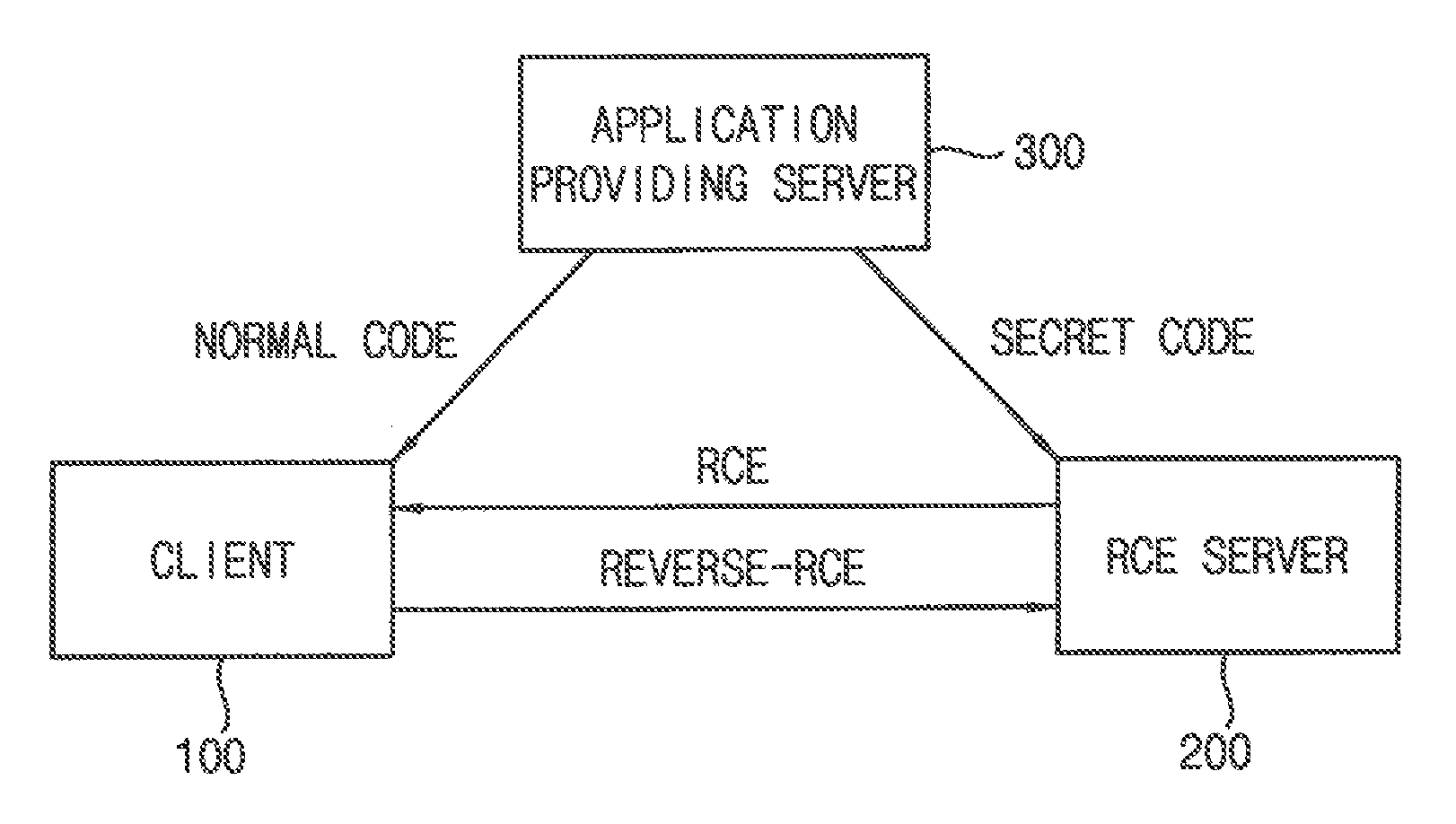
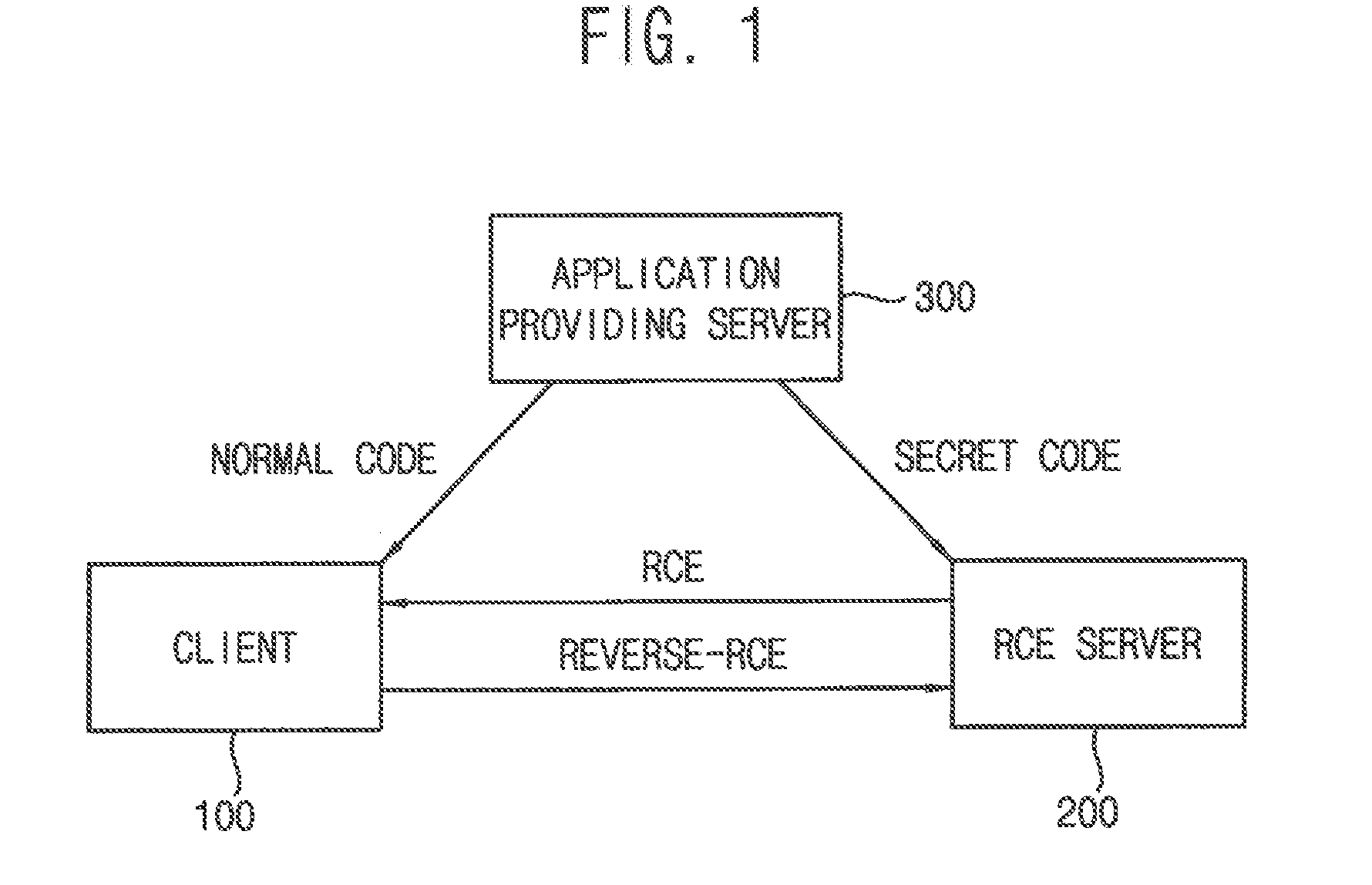
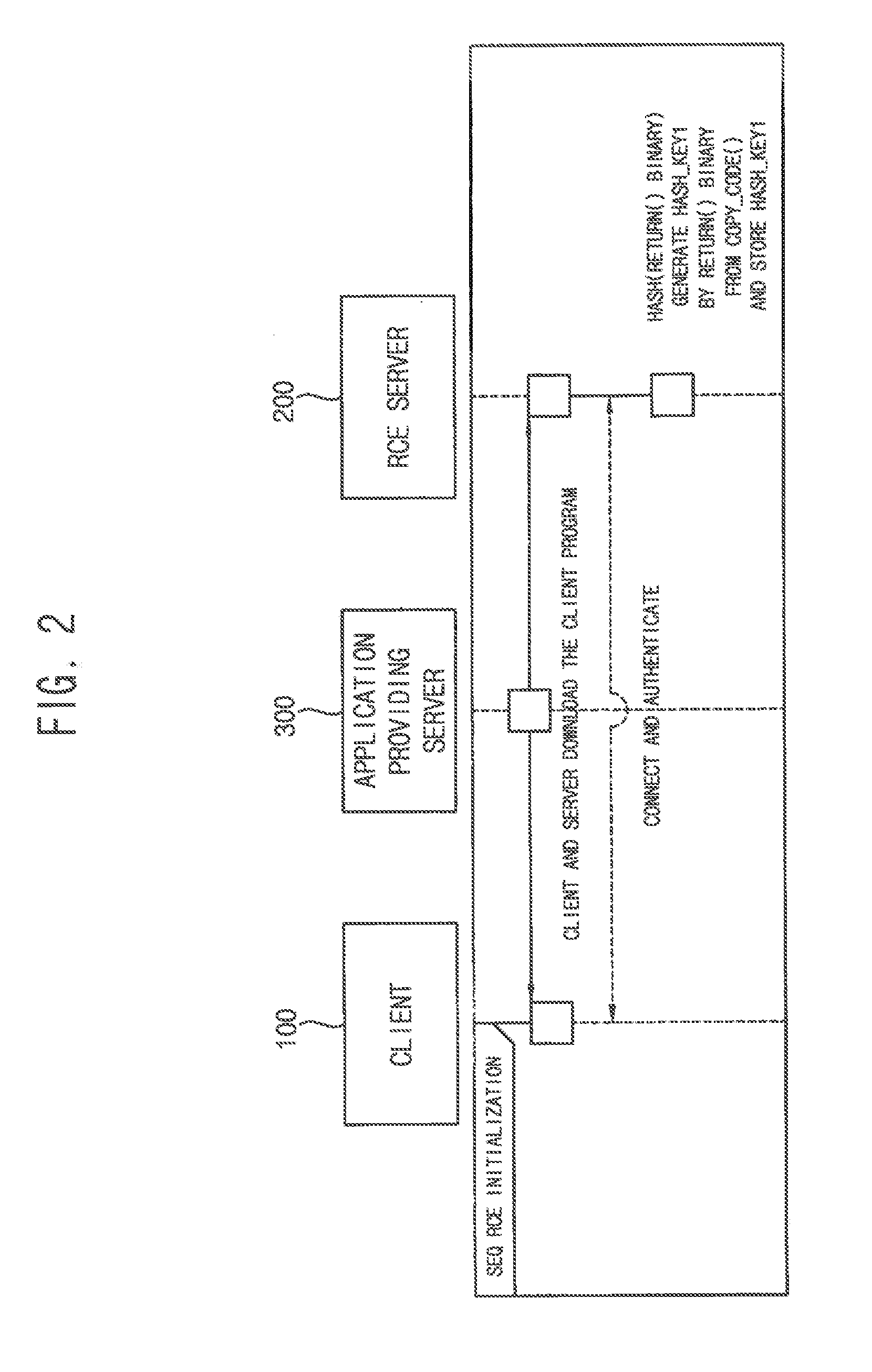
InactiveUS20170054693A1Resistibility can be improvedHigh resistivityDigital data protectionDigital data authenticationReturn functionClient-side
The integrity verification system includes a client and an RCE server. The client requests an RCE service to the RCE server using a pointer of a return function as a parameter of a service call function and transmits a memory code of the return function to the RCE server when Reverse-RCE for obtaining the memory code of the return function is requested from the RCE server. The RCE server generates a first hash key of the transmitted memory code, compares the first hash key to a stored second hash key of the memory code of an original return function, generates a return value according to a compared result between the first hash key and the second hash key and transmits the generated return value to the client using the generated return value as a parameter of the service call function. The client executes the return function using the return value as a parameter of the return function.
Owner:KSIGN +1
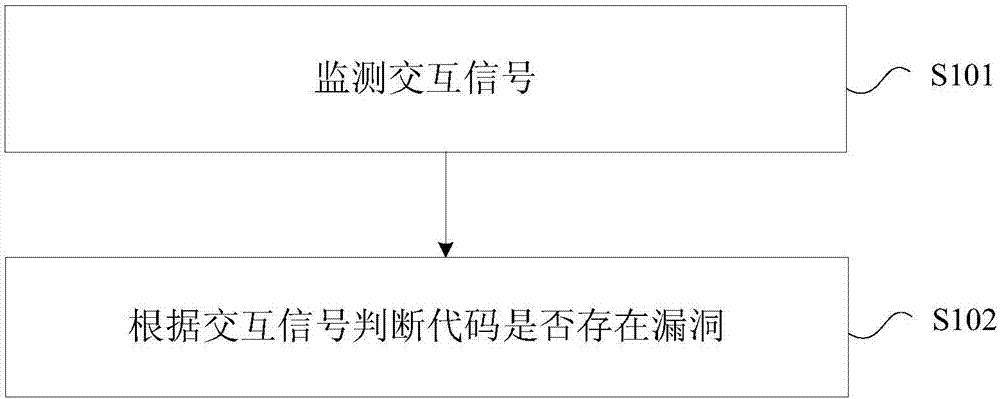
Method and device for monitoring code bugs, electronic equipment and storage media
ActiveCN107194258AImprove efficiencyImprove accuracyInternal/peripheral component protectionPlatform integrity maintainanceMemory chipMemory code
The invention provides a method and a device for monitoring code bugs, electronic equipment and storage media. The method comprises the following steps that: monitoring an interaction signal, wherein the interaction signal comprises an execution signal and a response signal when a processor receives an update signal for updating parameters, the execution signal is sent to a storage device to execute a write action, and the response signal is sent to the processor by the storage device; and according to the interaction signal, judging whether a code has bugs or not. Through the method, the problems in the prior art that a memory chip loses efficiency in advance since the code bug of the memory chip is difficult in manual monitoring can be solved, so that the automatic monitoring of a memory code is realized, memory code monitoring efficiency and accuracy can be improved, and the service life of the memory chip is guaranteed.
Owner:GREE ELECTRIC APPLIANCES INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com