Patents
Literature
933results about How to "Save bandwidth resources" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
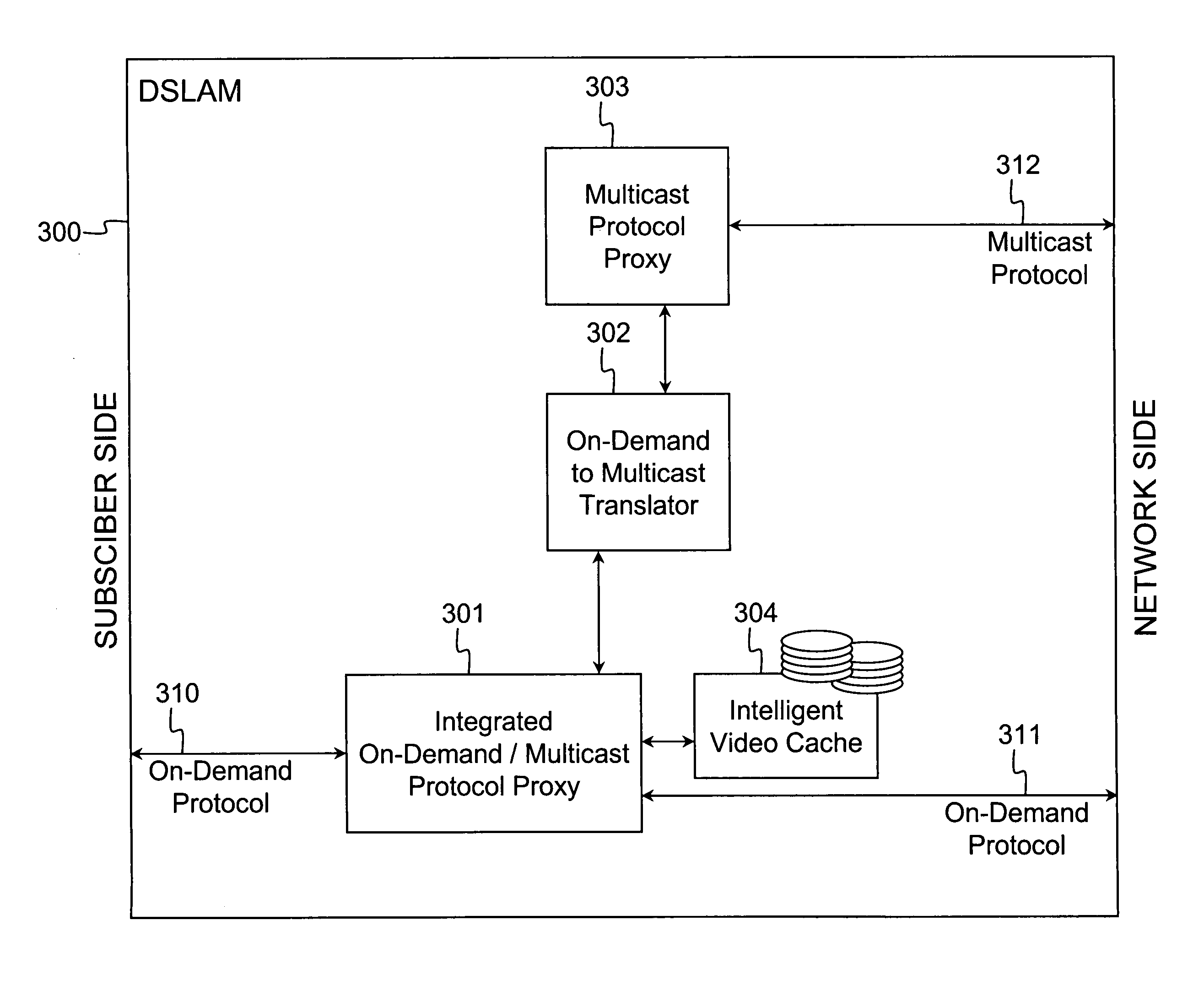
Access/edge node supporting multiple video streaming services using a single request protocol
ActiveUS20070101377A1Compact integrationReduce in quantityAnalogue secracy/subscription systemsClosed circuit television systemsEdge nodeService use
Owner:ALCATEL LUCENT SAS +2
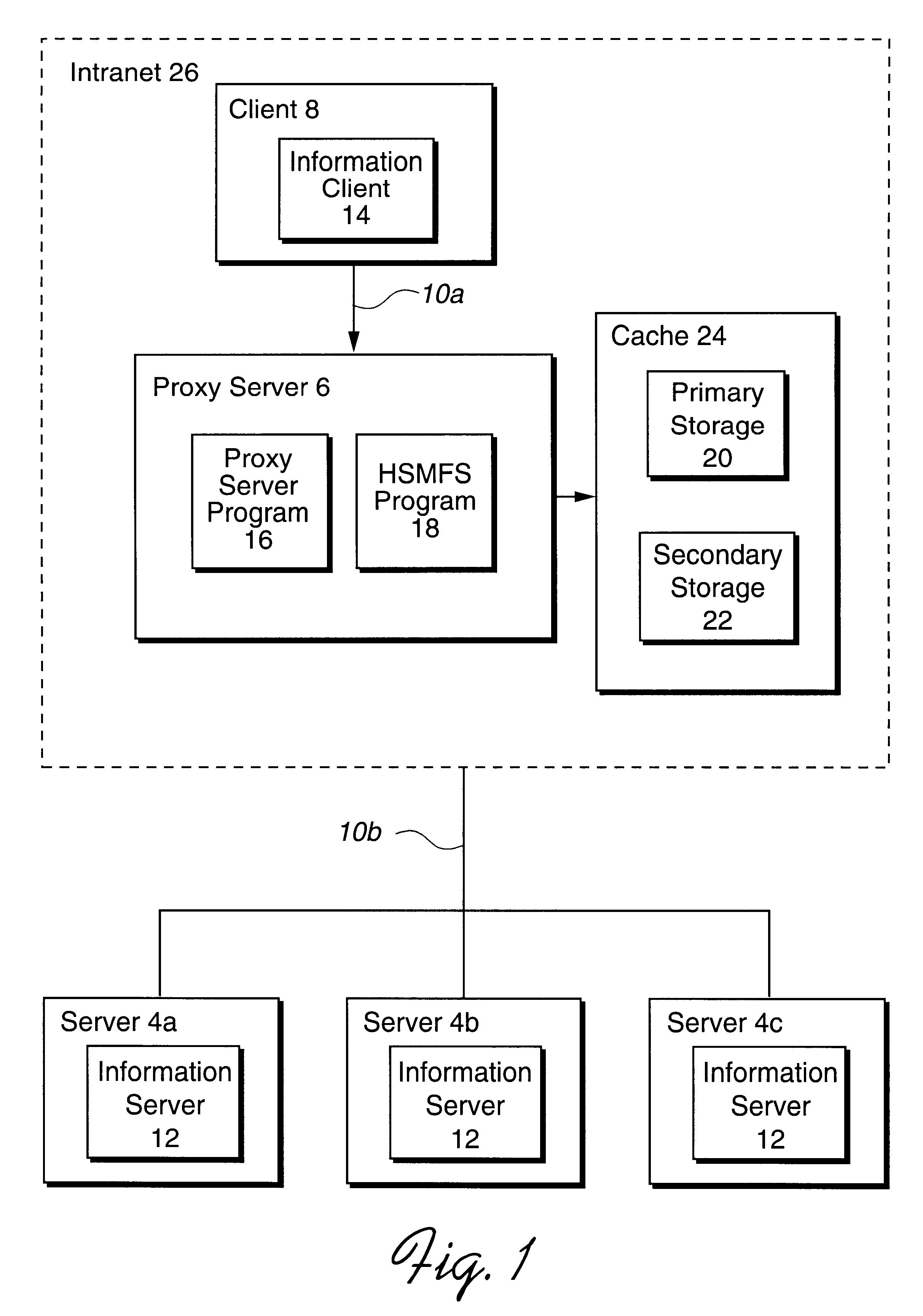
System, method and program for migrating files retrieved from over a network to secondary storage
InactiveUS6442601B1Save bandwidth resourcesIncrease speedMultiple digital computer combinationsSecuring communicationAuxiliary memoryUnit of time
Disclosed is a system, method, and program for caching files retrieved from a server over a network. A computer system receives a request from a requesting computer system for a file maintained on the server. The computer system is capable of communicating with the server via the network. The computer system retrieves the requested file from the server over the network and stores a copy of the requested file in a primary storage. The computer system further returns another copy of the requested file to the requesting computer system. The computer system determines retrieved files to migrate from the primary storage to a secondary storage and migrates the determined retrieved files from the primary storage to the secondary storage. To determine the files to migrate from primary storage to secondary storage, the computer system may determine a distribution of file requests per unit of time according to file size for files maintained in the primary storage and the secondary storage. The computer system then processes the determined distribution and a provided maximum number of file requests per unit of time to determine a minimum file size for migration. Files having a size greater than the minimum file size for migration are migrated from the primary storage device to the secondary storage device.
Owner:COMCAST IP HLDG I
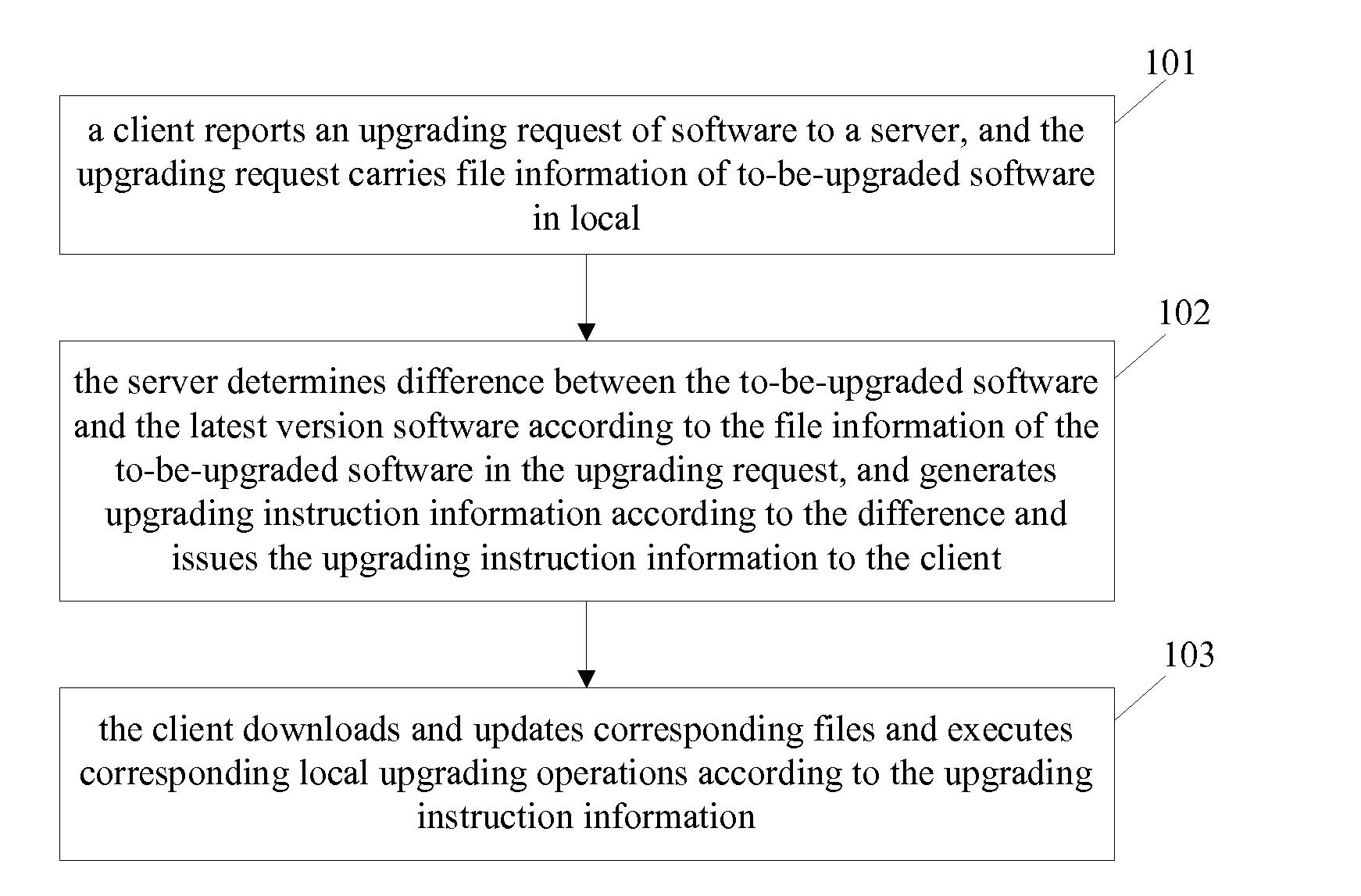
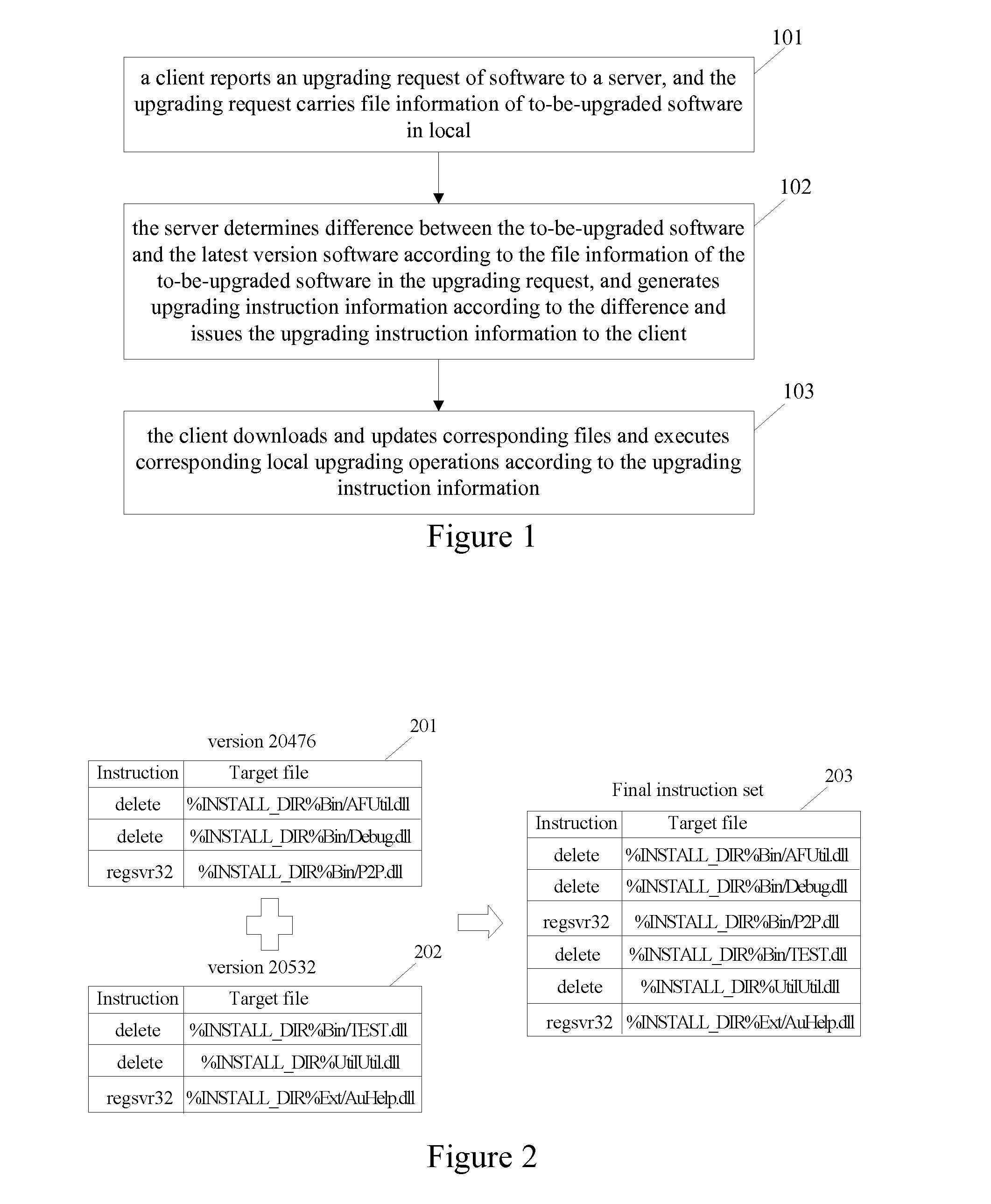
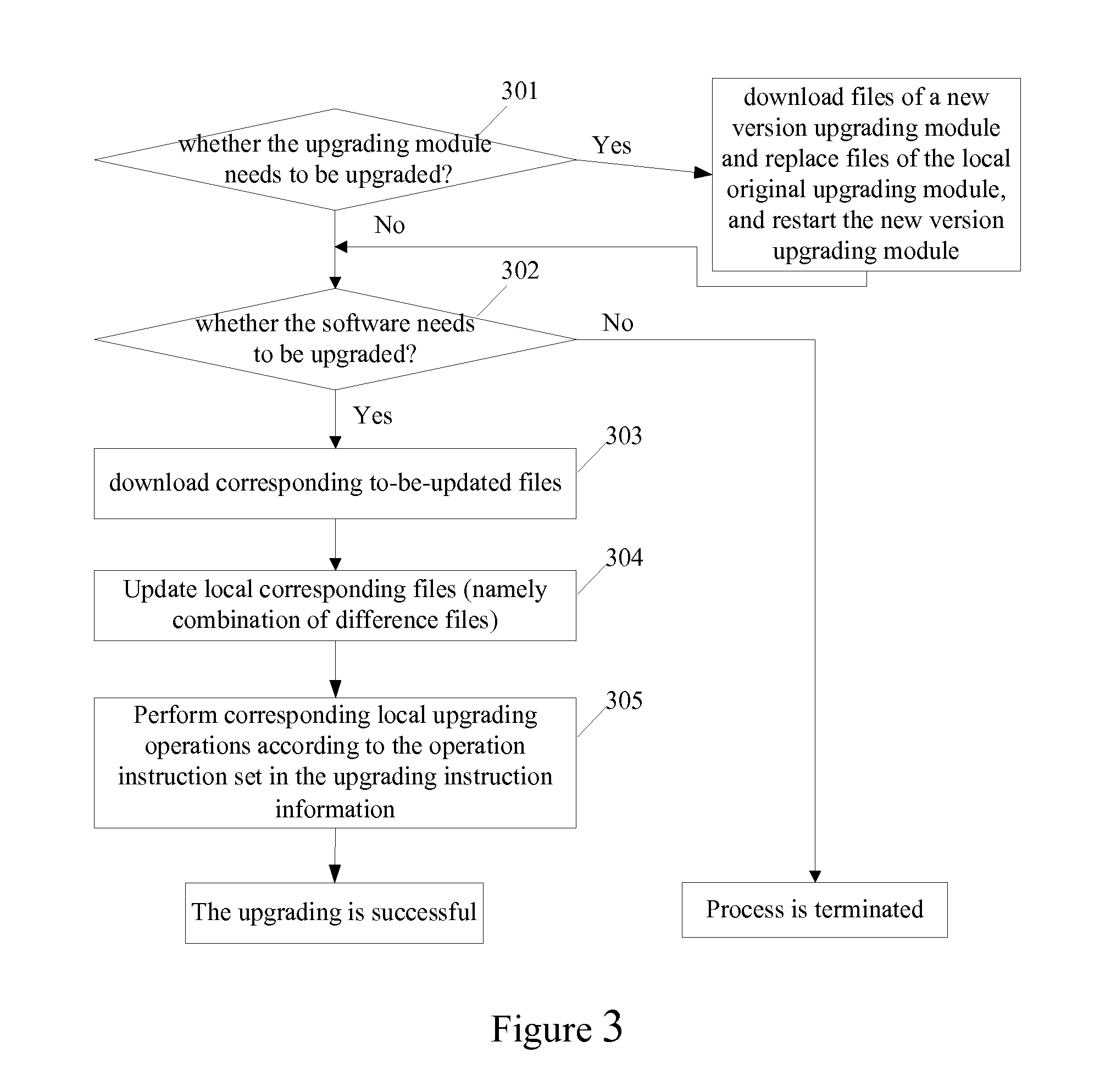
Method and system for upgrading software
ActiveUS20140304697A1Save bandwidth resourcesReduce software upgrading workloadDatabase updatingVersion controlSoftware engineeringWorkload
Embodiments of the present disclosure provide a method and a system for upgrading software. The method includes: a client reports a software upgrade request to a server, wherein the upgrade request carries file information of the local software to be upgraded; the server determines the difference with the latest version software according to the file information of the software to be upgraded in the upgrade request, and generates upgrade instruction information according to the difference and sends it to the client; the client downloads and updates the relevant files and performs the relevant local upgrade operations according to the instructions in received upgrade instruction information. Technical solutions of the present disclosure can save bandwidth resources and reduce the workload for upgrading software.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Method and system for displaying web page
InactiveCN101201827ASave bandwidth resourcesRelieve stressDigital data information retrievalSpecial data processing applicationsData displayClient-side
Owner:ALIBABA GRP HLDG LTD
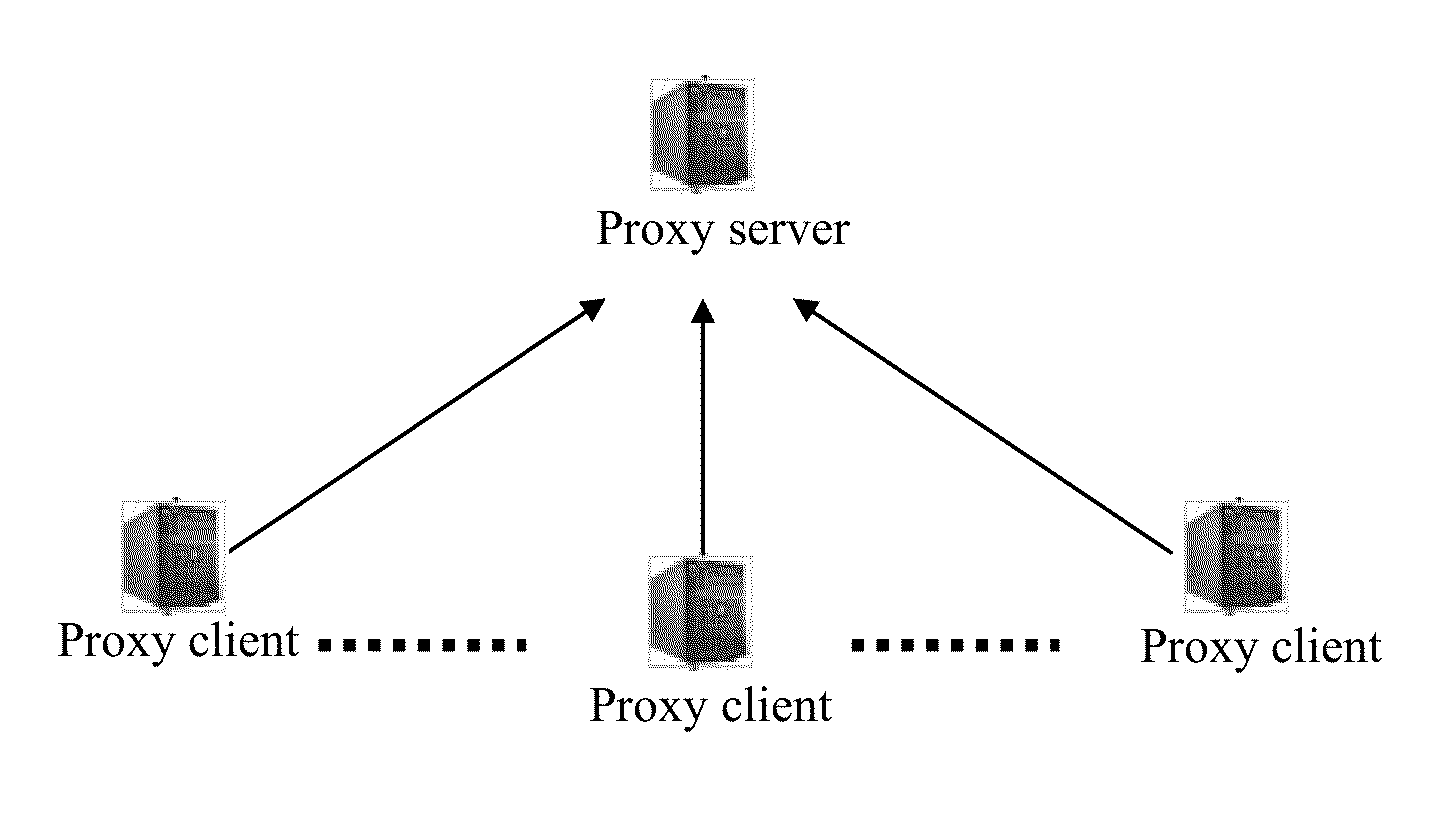
Data query method and system and storage medium
InactiveUS20150213134A1High cost of deploymentPoor service performanceWeb data indexingDigital data processing detailsData providerClient-side
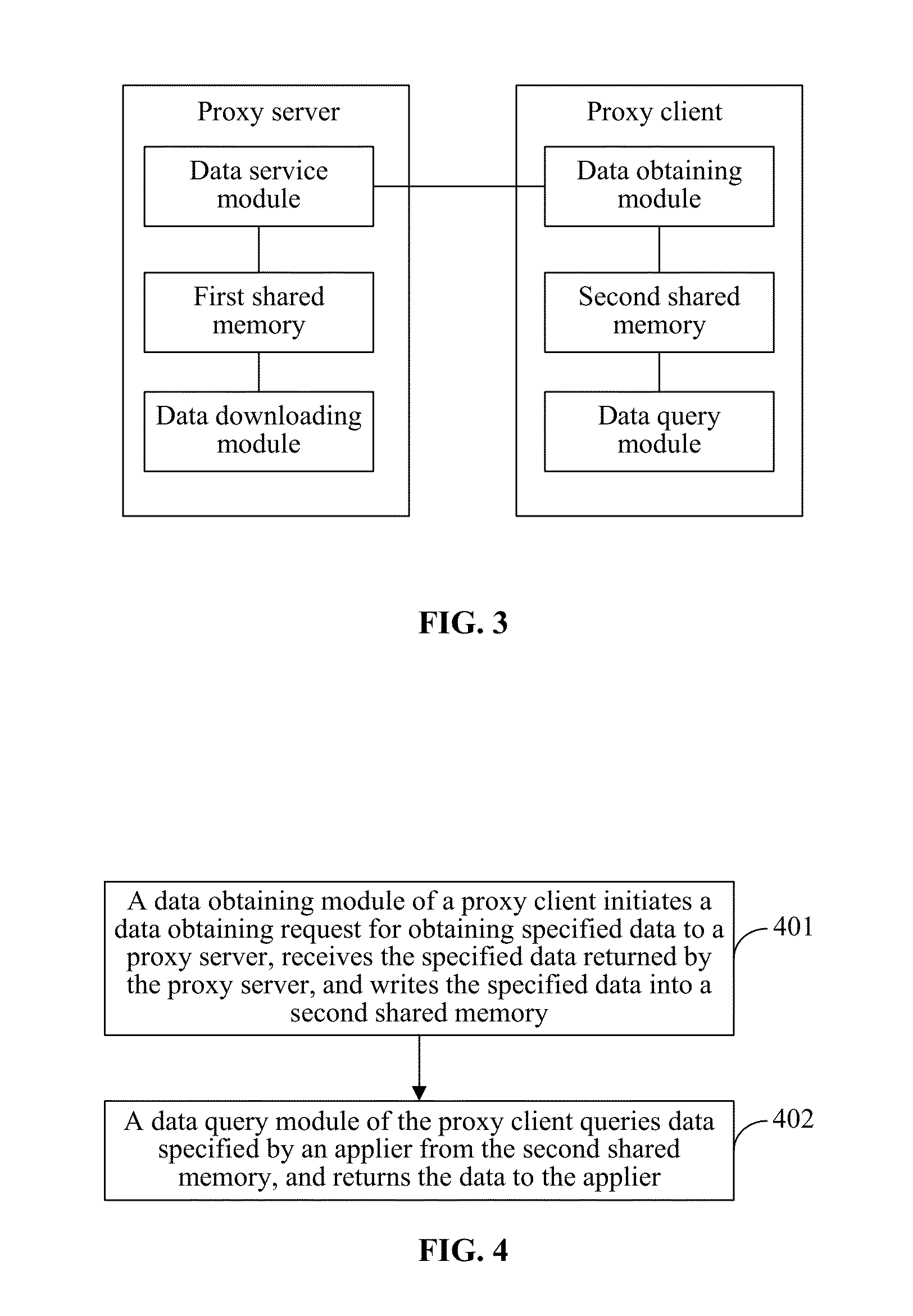
The present disclosure discloses a data query system, method, and storage medium. The data query system includes a proxy server and at least one proxy client. The proxy server is disposed on a server that serves as a data provider, and is configured to provide the proxy client with a data delivery service. The proxy client is disposed on a client that serves as a data user, and is configured to obtain data from the proxy server and save the data and provide a data query service. The proxy client thus includes a data obtaining module, a data query module, and a second shared memory. Accordingly, the present disclosure further discloses a data query method. The present disclosure has a simple structure, achieves fast data update, requires a low deployment cost, saves bandwidth resources, and achieves excellent service performance.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Wide area network-oriented decomposition support method for animation rendering task and implementation method
InactiveCN102088472AImprove efficiencySolve the problem of a large amount of transmitted data occupiedAnimationTransmissionDecompositionAnimation
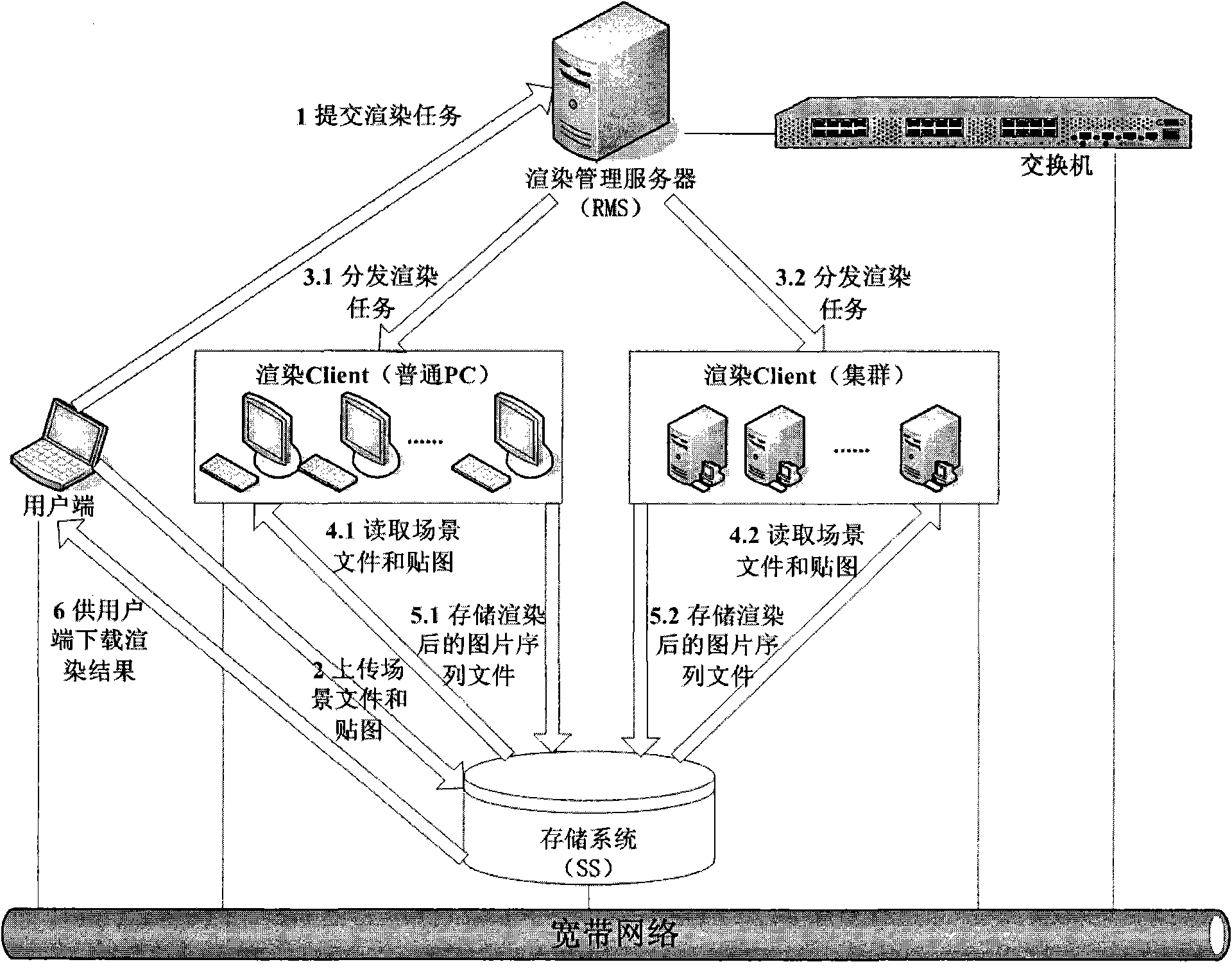
The invention discloses a wide area network-oriented decomposition support method for an animation rendering task and an implementation method, which belong to the field of computer networks. According to the intensive computation characteristic of the animation rendering task and the characteristic that the transmission rate in a wide area network environment is limited to a network bottleneck bandwidth, the method comprises a visible range-based scene file and picture set splitting method, a node performance assessment method, an operation distribution strategy and integration and process control of the methods. During composition of the rendering task of a user, the scene file and picture set splitting method related to the invention is used and a scene is optimized according to the analysis of objects and pictures which are visible and invisible for the current scene camera, so that the aim of reducing a final rendering file is fulfilled. In a simplified model scene, a transmission data volume in a network can be effectively decreased, equivalent splitting of a scene file and a calculated amount is realized, and the distribution and execution of the fineness of rendering operation are facilitated. By using the method, the computing efficiency of each rendering client is brought into full play, and very high expandability is achieved.
Owner:COMMUNICATION UNIVERSITY OF CHINA
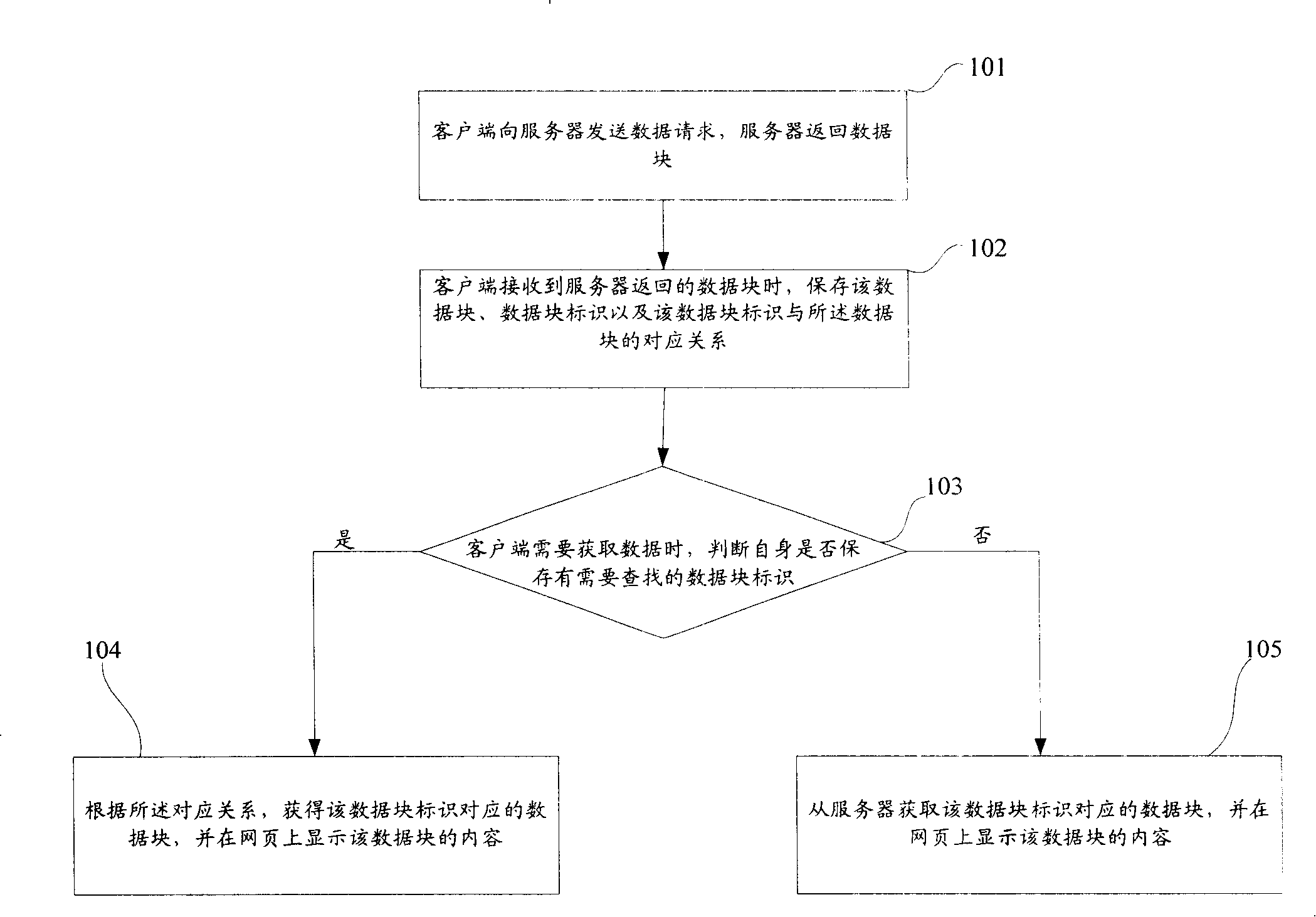
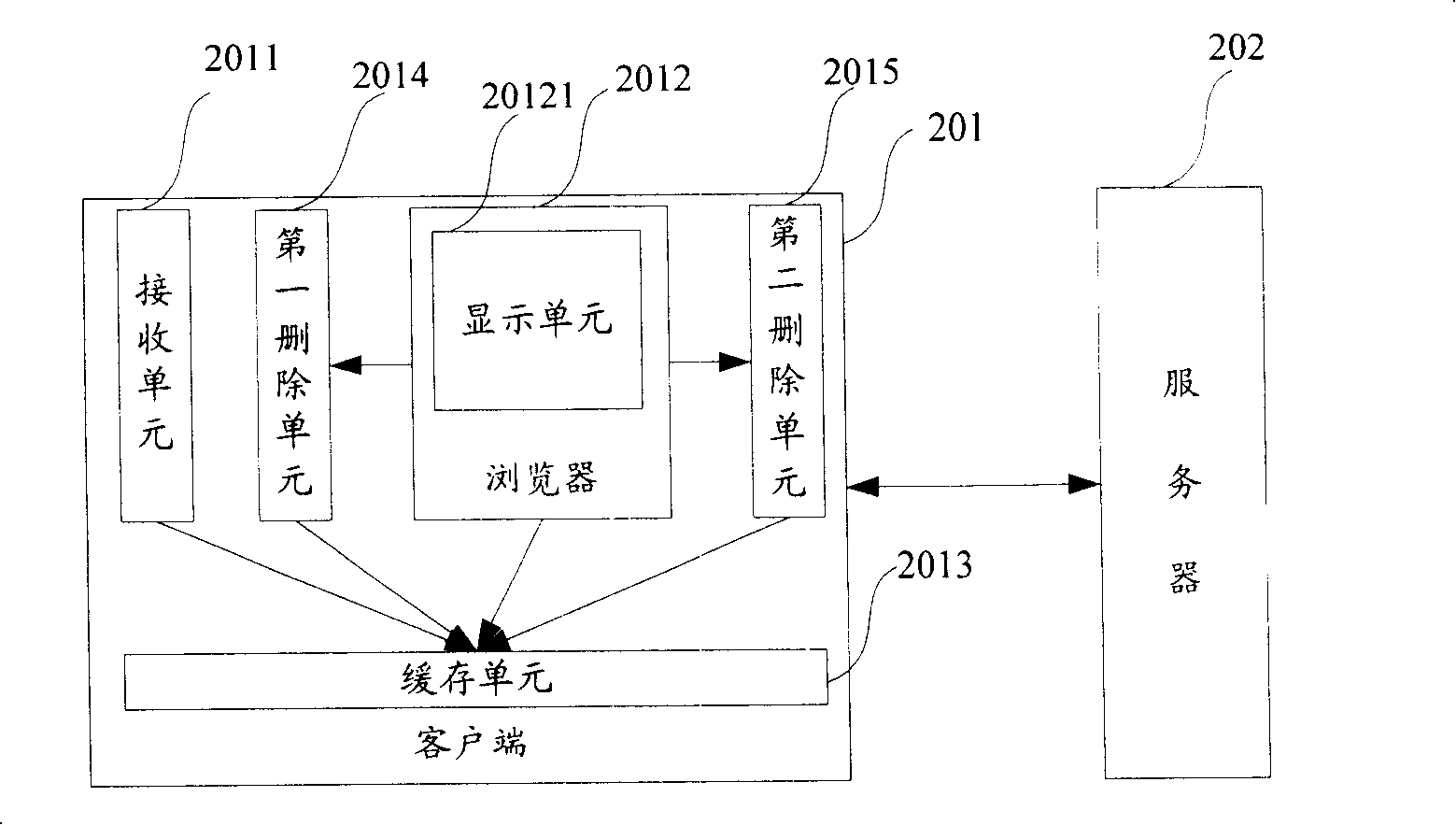
Method and System for Displaying Web Page
InactiveUS20100088612A1Relieve stressIncrease speedInput/output for user-computer interactionDigital data information retrievalClient-sideWeb page
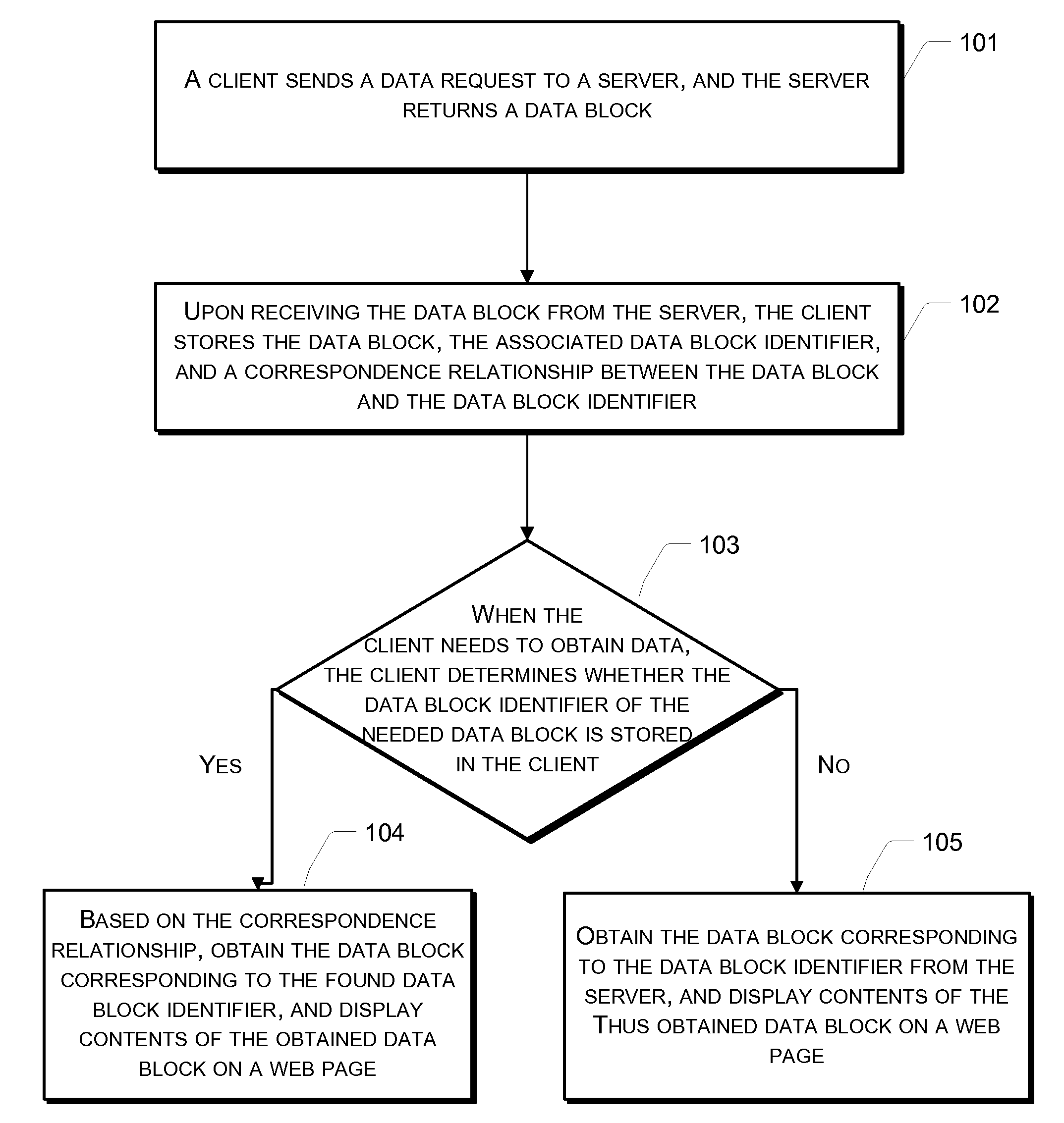
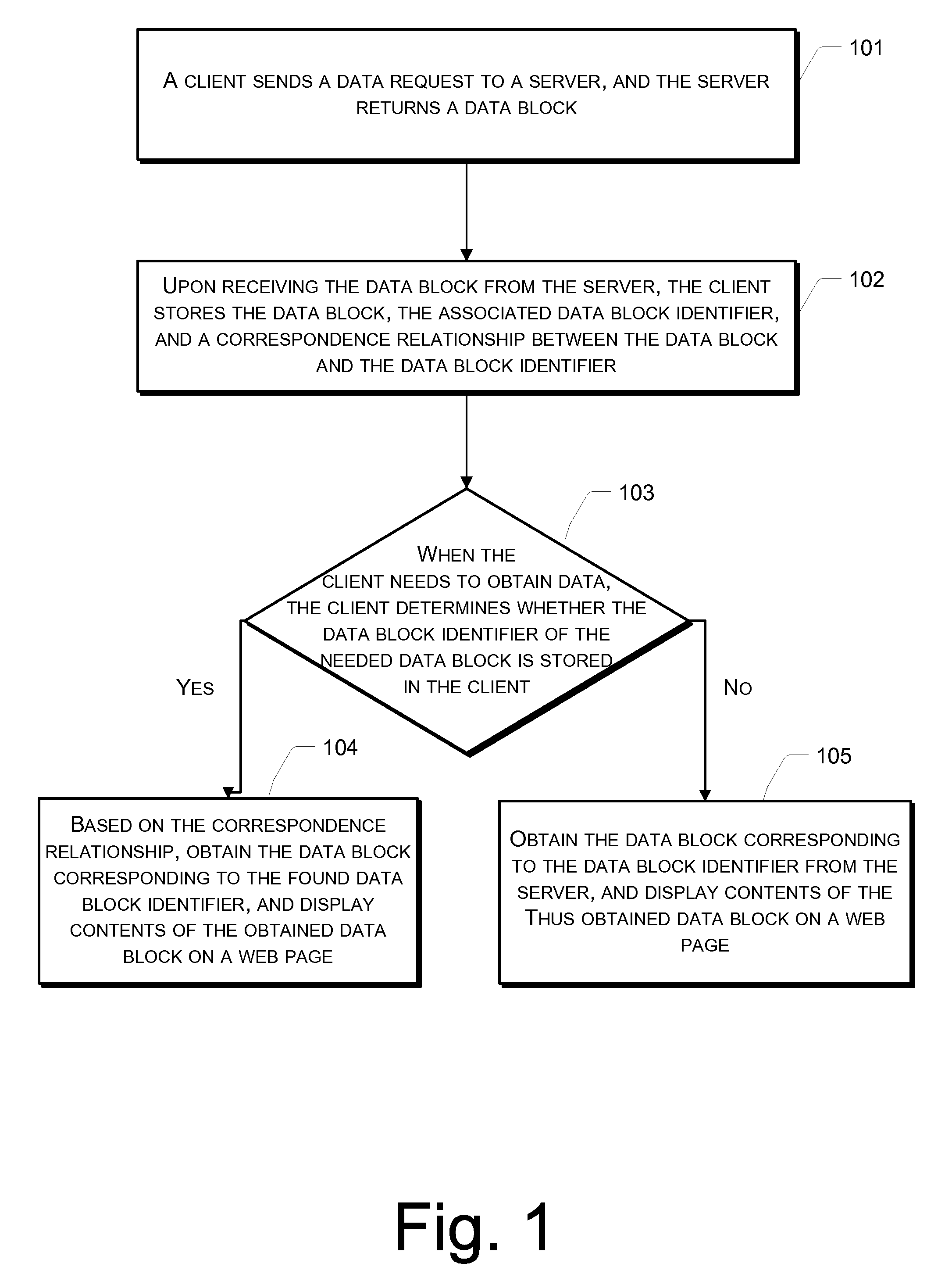
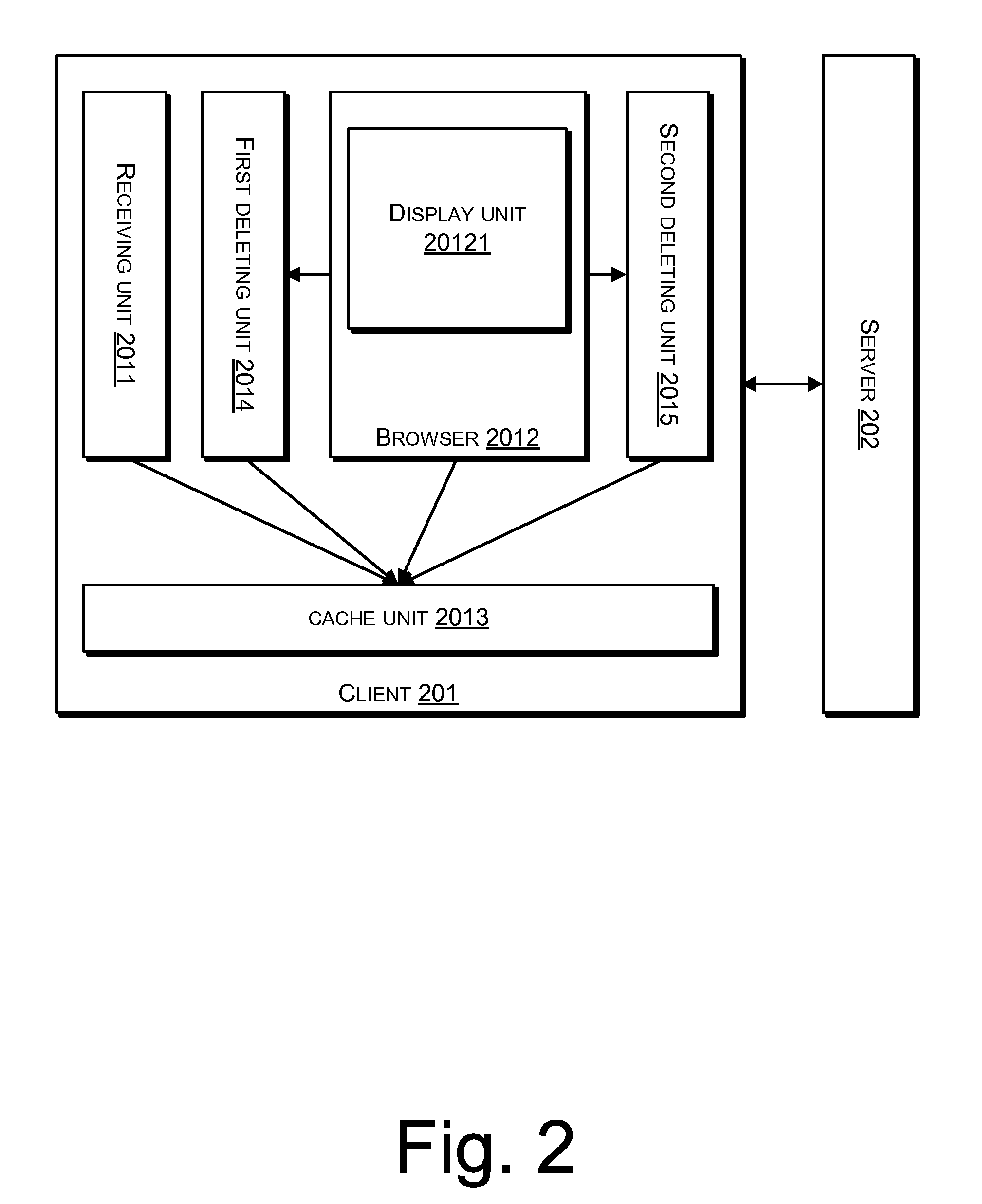
Disclosed is a method for displaying a web page. According to the method, upon receiving a data block including web page display data from a server, a client stores a data block identifier and a correspondence relationship between the data block identifier and the data block. The client then uses the identifier of the needed data block to determine whether the needed data block identifier is stored in the client, if affirmative, obtains the data block corresponding to the found data block identifier according to the correspondence relationship, and displays the web page display data of the obtained data block on a web page. Further discloses a system for displaying a web page. The disclosed method and system can be used to greatly reduce the pressure on a server end, save network bandwidth resources, and improve a client's speed for displaying a web page.
Owner:ALIBABA GRP HLDG LTD
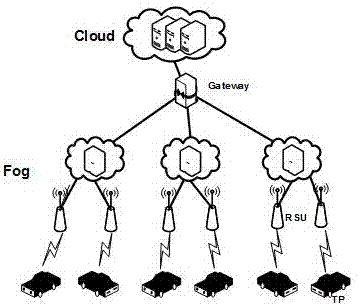
Internet of Vehicles deployment system based on fog computing
InactiveCN107071033AEasy accessEffective controlWireless commuication servicesTransmissionFog computingThe Internet
The invention discloses an Internet of Vehicles deployment system based on fog computing and relates to the field of Internet of Vehicles deployment and planning. A road side unit RSU collects vehicle traffic information and sends the information to fog equipment; the fog equipment processes and forwards the vehicle traffic information and temporarily stores the vehicle traffic information; and the fog equipment uploads the stored vehicle traffic information to a server cluster, and the server cluster controls the vehicle traffic information through computation and analysis of a big data result and makes a reasonable traffic strategy. According to the system, the fog equipment is introduced to the edge of the network, and meanwhile, the fog equipment temporarily computes and stores the vehicle traffic information, so that the bandwidth resources are saved and the data transfer rate is improved.
Owner:JINAN INSPUR HIGH TECH TECH DEV CO LTD
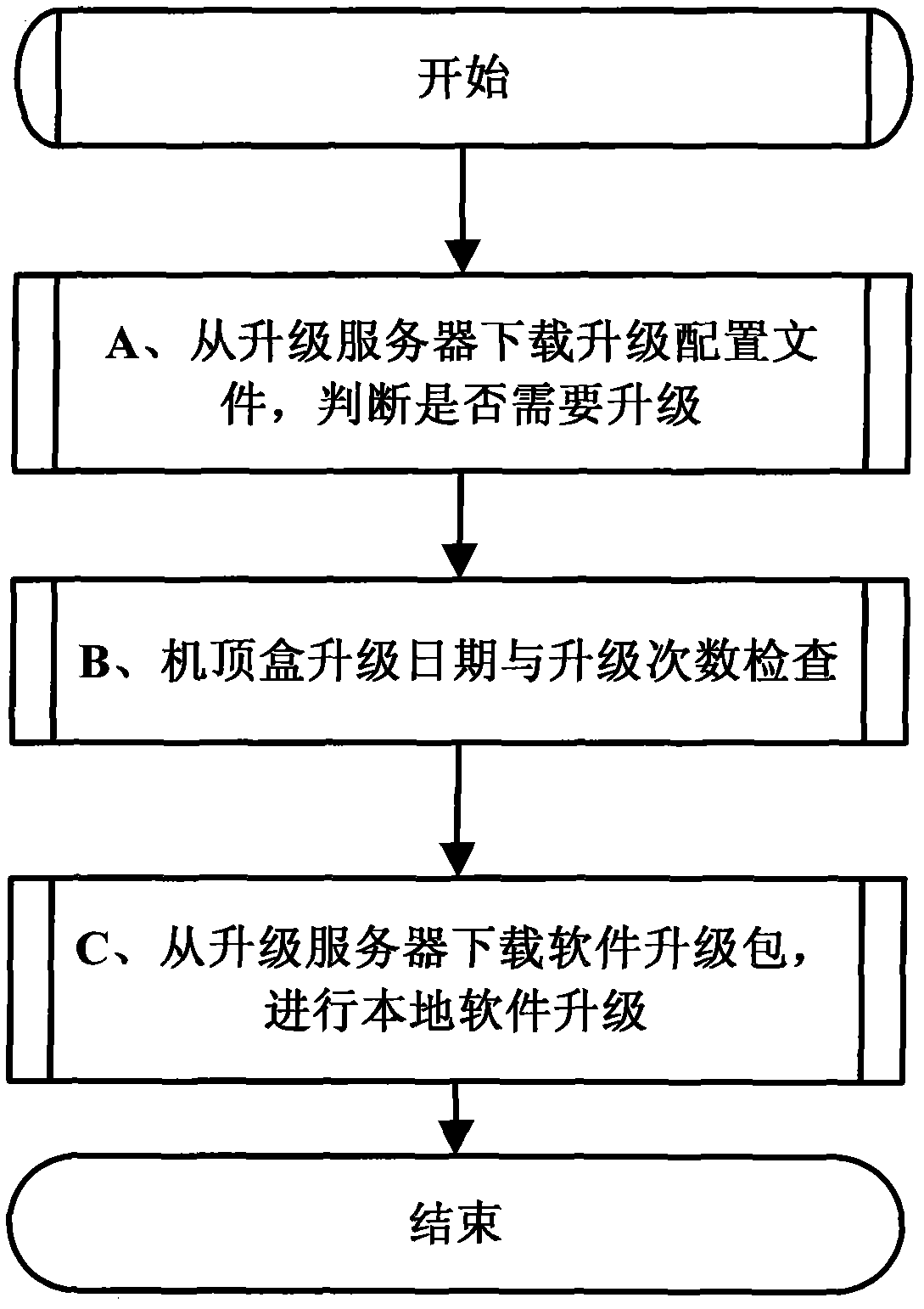
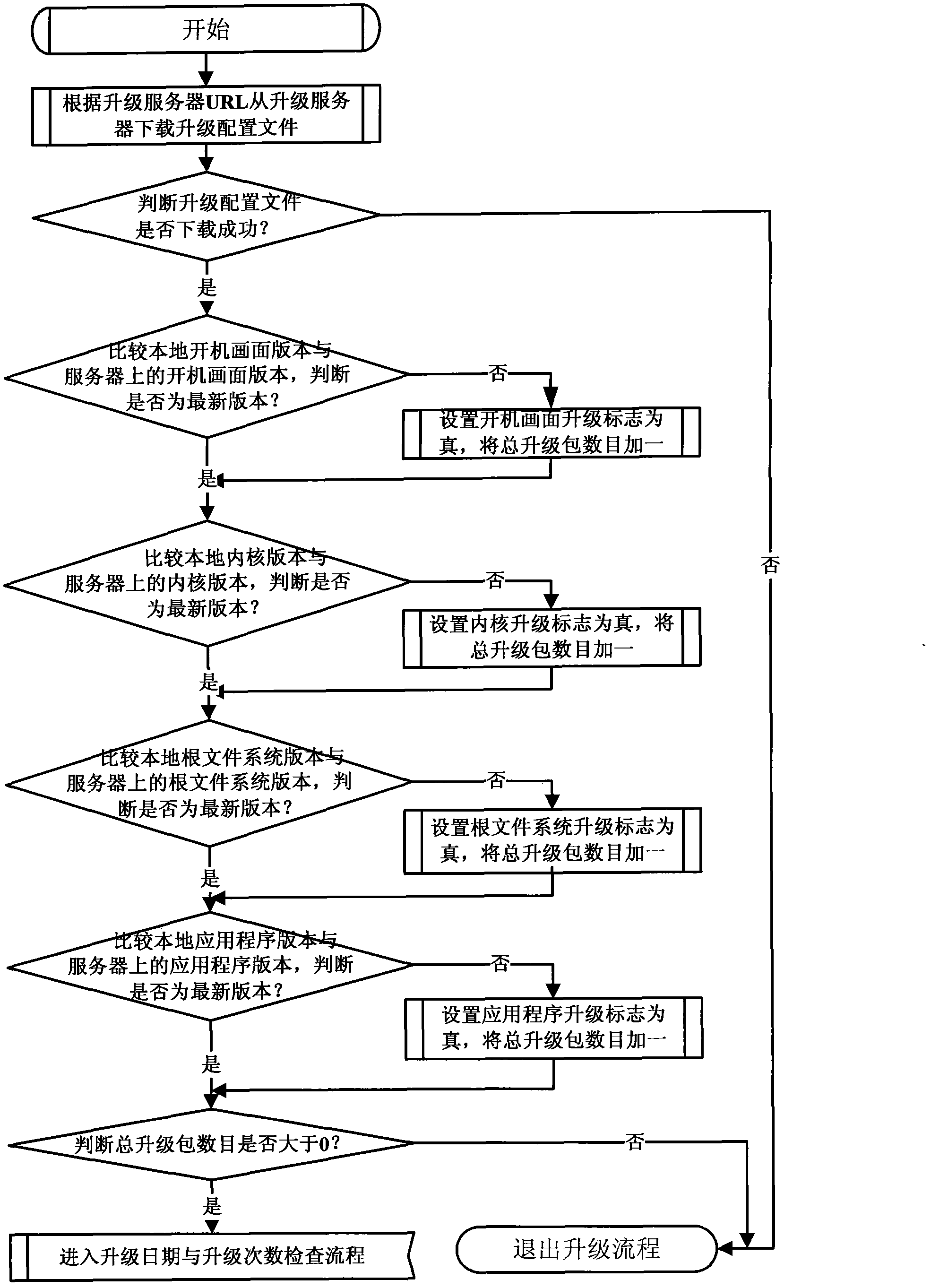
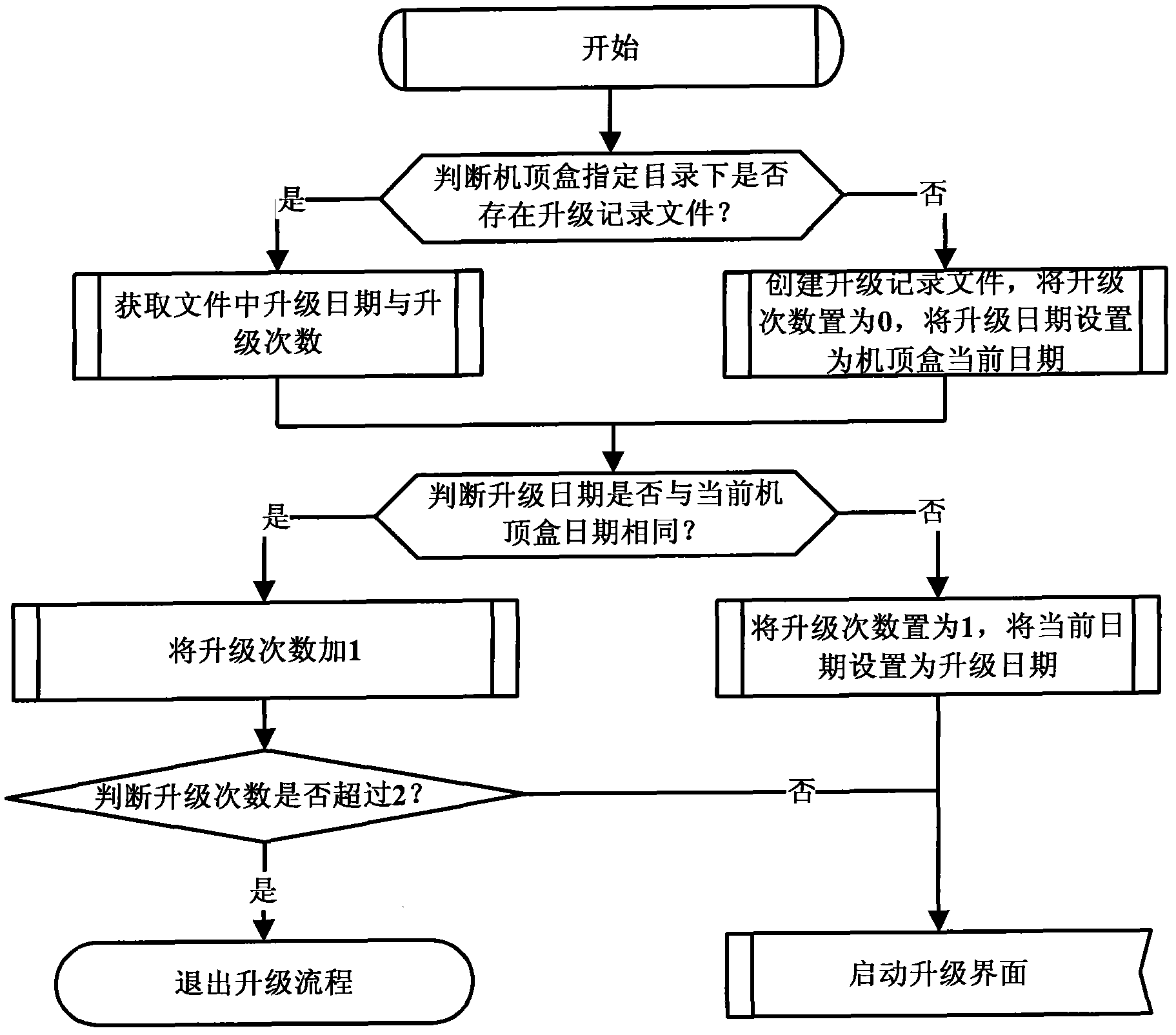
Incremental software updating method of internet protocol television (IPTV) set top box
InactiveCN102253850AImprove upgrade efficiencyImprove experienceProgram loading/initiatingSelective content distributionElectricitySoftware update
The invention discloses an incremental software updating method of an internet protocol television (IPTV) set top box. The method comprises the following steps of: A, when the set top box is started and powered on, performing updating detection, downloading an updating configuration file from an updating server according to an address of the updating server which is locally configured, judging whether updating is required according to contents of the configuration file and the current software version information of the set top box, if the updating is required, determining a software package to be updated and executing the step B, and if the updating is not required, normally starting; B, judging whether the number of day updating times of the set top box is greater than a preset threshold value, if the number of the day updating times of the set top box is greater than the preset threshold value, normally starting, and if the number of the day updating times of the set top box is not greater than the preset threshold value, executing the step C; and C, downloading the software package to be updated from the updating server, and performing local updating installation. The method has the advantages that: incremental updating is adopted, and only the software package to be updated is downloaded and updated, so bandwidth resources are saved, the updating efficiency of the IPTV set top box is improved, updating time is shortened, user experience is improved, and an updating mode is relatively flexible and easy to control.
Owner:FENGHUO COMM SCI & TECH CO LTD
Packaging method, device and equipment for software development kit and readable medium
InactiveCN107066291ASave bandwidth resourcesShorten the timeProgram loading/initiatingSoftware deploymentSoftware development processAgile software development
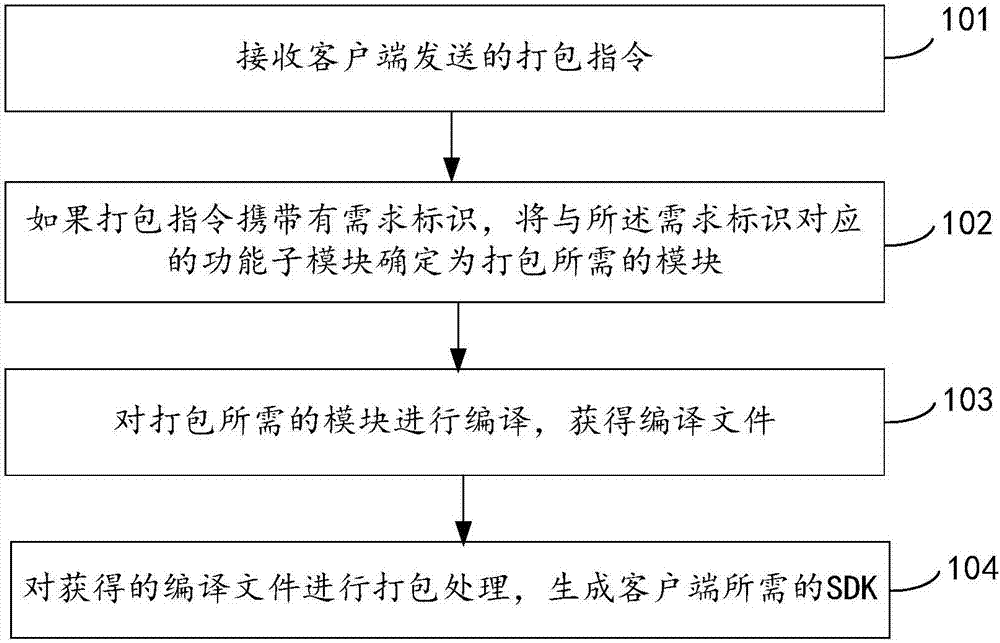
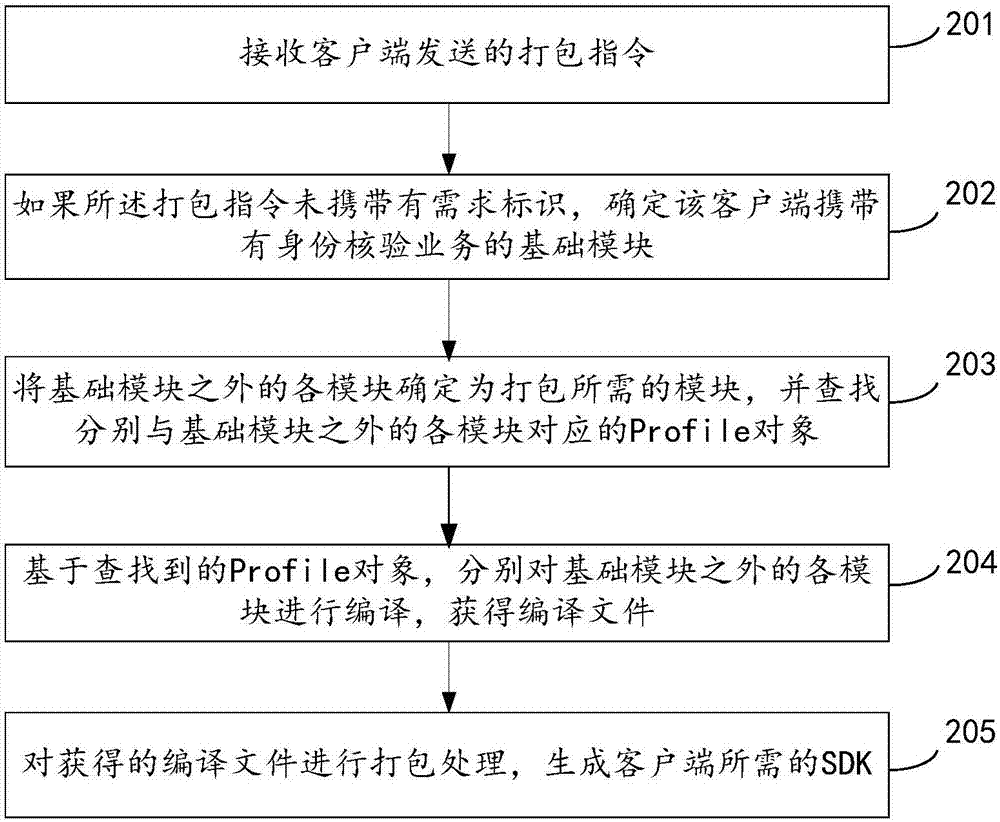
The invention provides a packaging method, device and equipment for a software development kit (SDK) and a readable medium. The method comprises the steps that a packaging instruction sent by a client is received; if the packaging instruction carries a demand identifier, a functional submodule corresponding to the demand identifier is determined as a module needed for packaging; a set of all the functional submodules is a functional module, wherein the functional module is used for supporting various business functions of target business at the same time, and the demand identifier corresponds to the business function needed by the client; the module needed for packaging is compiled to obtain a compiling file; and the obtained compiling file is packaged to generate the SDK needed by the client. By implementing the method, flexible packaging can be performed according to the demand of the client based on the same set of codes of the target business.
Owner:ADVANCED NEW TECH CO LTD
Method and device for updating application programs
ActiveCN103699410AReduce the number of responsesReduce resource consumptionProgram loading/initiatingTransmissionData differencingNetwork packet
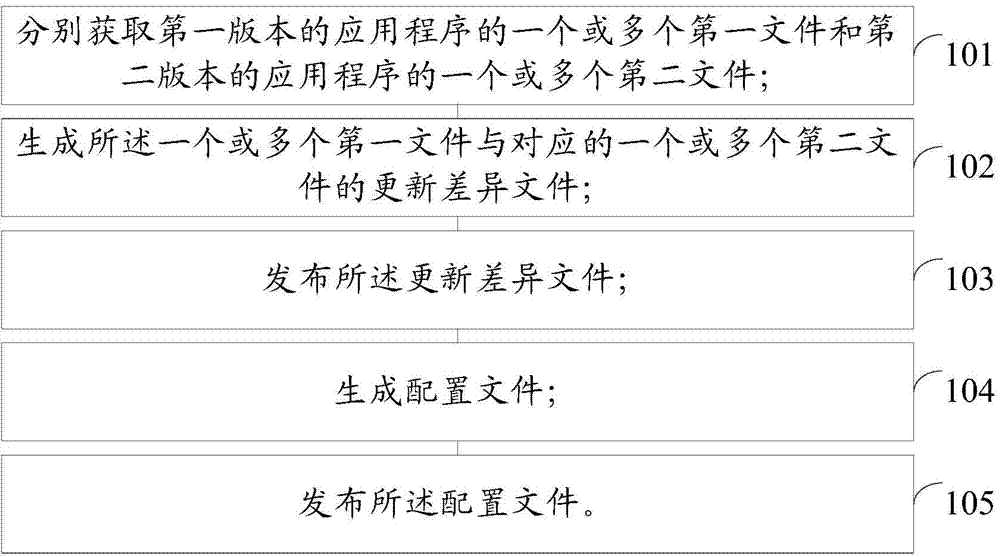
The invention discloses a method and a device for updating application programs. The method comprises the following steps of: acquiring one or more first files of a first version of the application programs, and one or more second files of a second version of the application programs; generating the update difference files of the one or more first files and the corresponding one or more second files; issuing the update difference files comprising download addresses; generating configuration files comprising the version information of the second version and the download addresses of the update difference files; issuing the configuration files. According to the method and the device disclosed by the invention, clients are prevented from blindly accessing a server to request to update service, thus reducing the response frequency of the server and decreasing the resource consumption of the server; meanwhile, the volume of each of the update difference files produced by data difference is greatly reduced compared with a complete version update data package, thus greatly reducing network bandwidth resources, and increasing download success rate and update success rate.
Owner:BEIJING QIHOO TECH CO LTD
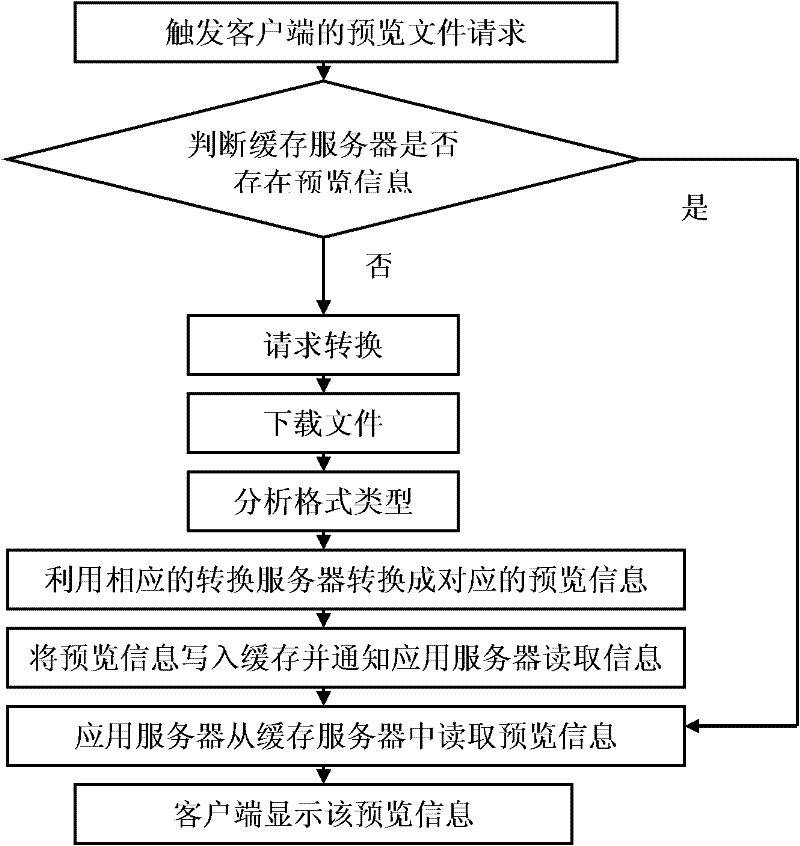
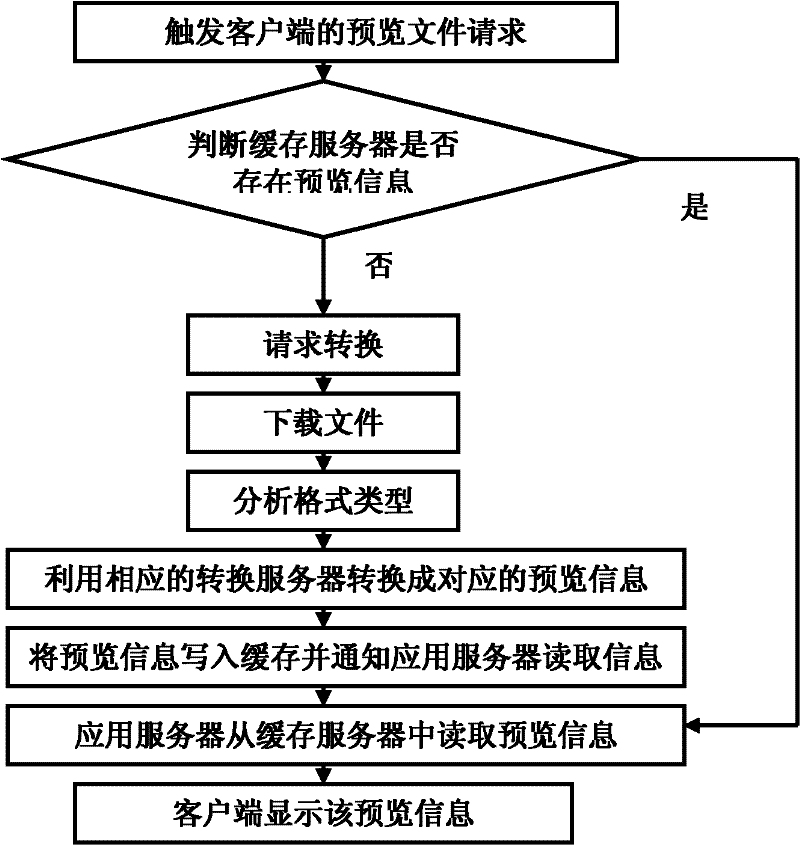
Method and system for previewing file
InactiveCN102184177AReduce blind lookup operationsSave search timeSpecial data processing applicationsCache serverWorld Wide Web
The invention discloses a method and a system for previewing a file. The method comprises the following steps that: 1, a user triggers a file-previewing request; 2, a conversion server downloads the file to be previewed from a storage device; 3, the downloaded file is converted into corresponding preview information and the corresponding preview information is sent to a cache server; and 4, the preview information is read from the cache server and displayed. In the invention, the file to be previewed is converted into the corresponding preview information by the conversion server and displayed to the user in a manner of the preview information, so that blind search operation of the user is reduced, a large amount of search time is saved for the user and a large quantity of precious bandwidth resources are saved for the servers in a network. According to statistics of a large amount of data, the size of general preview information is several K-bits, so that the storage space occupied by the original searched file is larger; therefore, by adoption of the invention, more bandwidth resources are saved for the servers in the network.
Owner:BEIJING PEOPLE HAPPY INFORMATION TECH
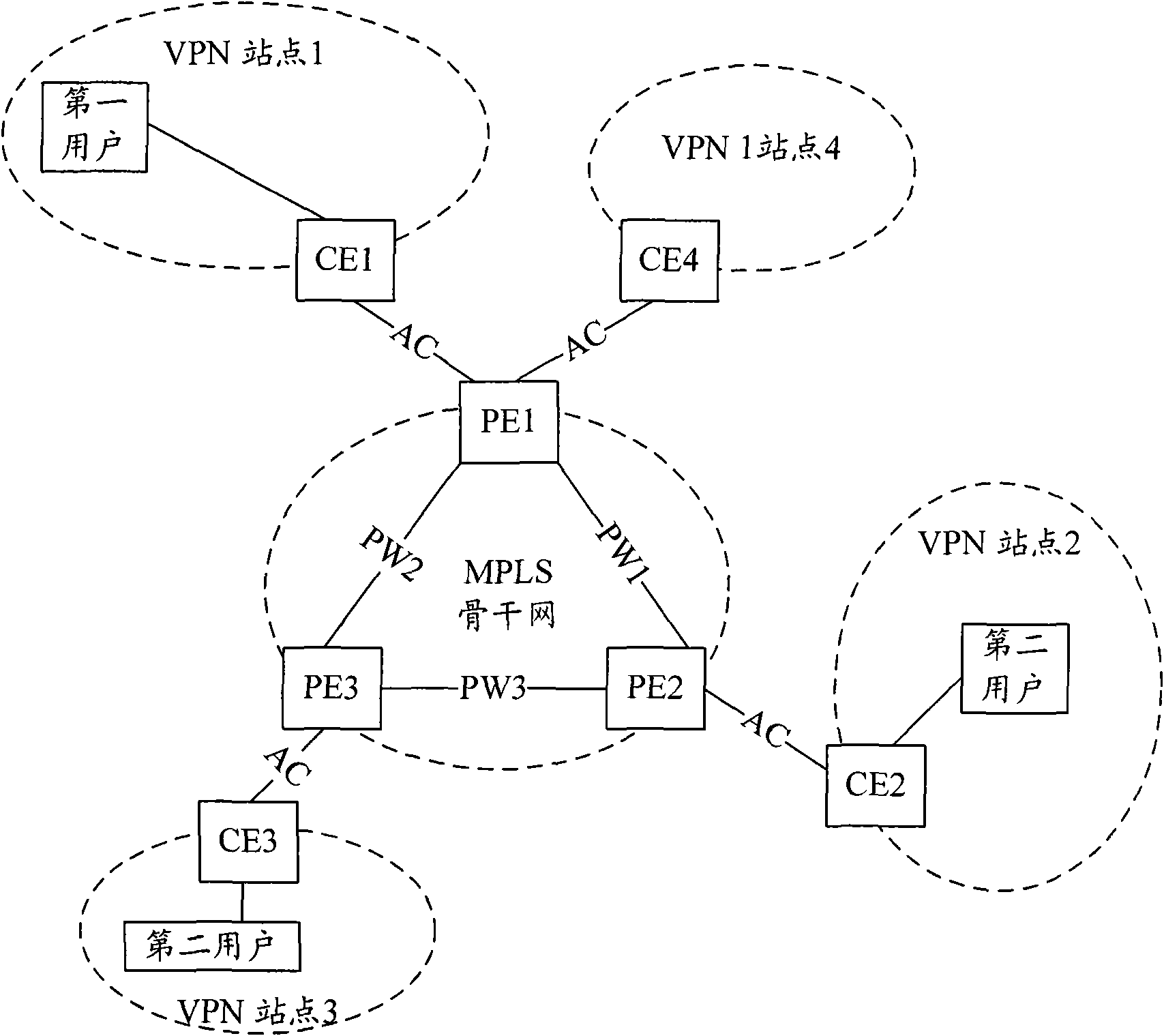
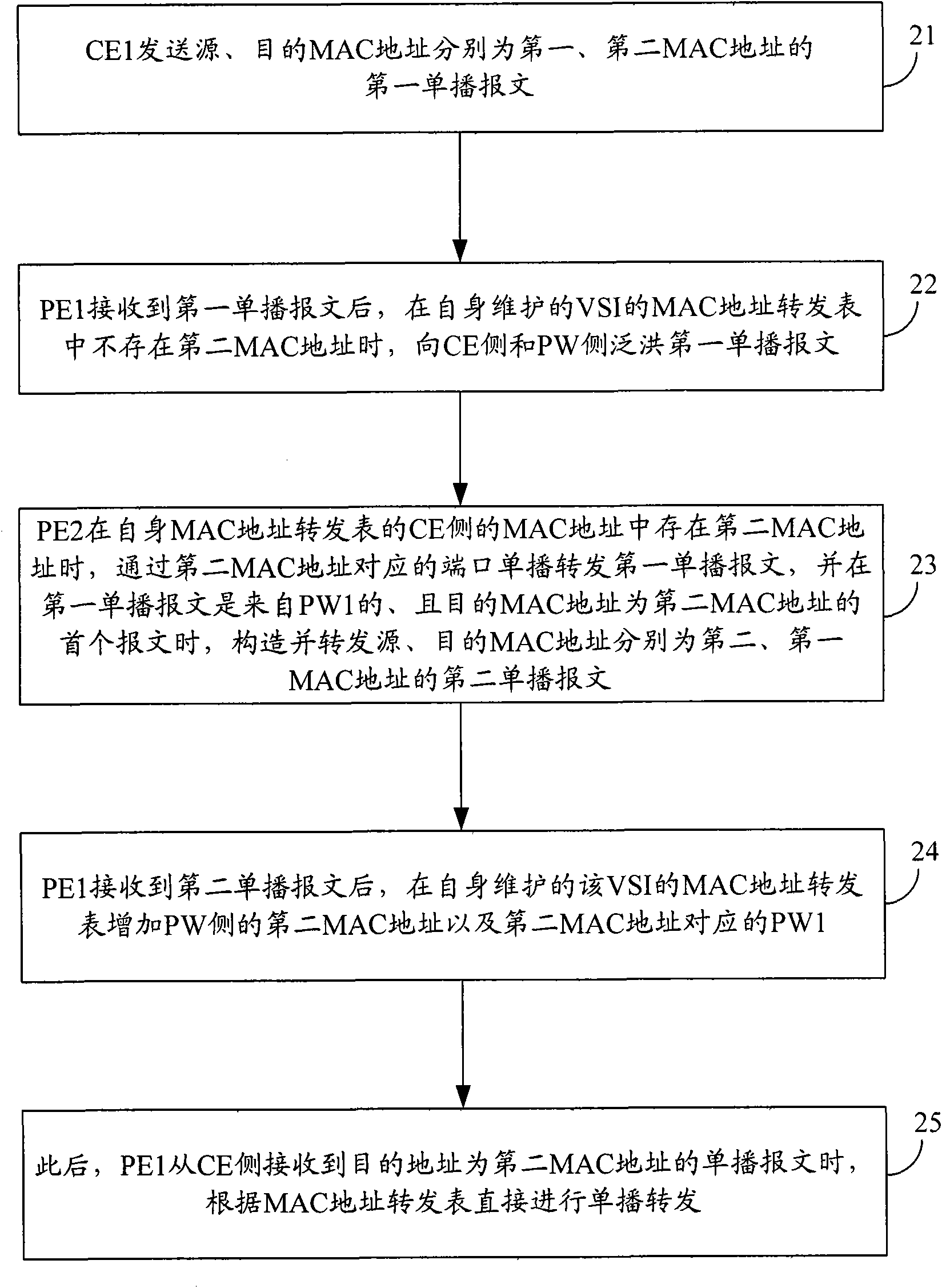
Method for message processing in VPLS service network and device
InactiveCN101616082AReduce trafficSave network bandwidth resourcesNetworks interconnectionTraffic volumeTraffic capacity
The invention provides a method for message processing in VPLS service network and a device. In the method, if monitoring a first message which comes form PW and has a target MAC address of a second MAC address, PE actively returns a unicast message whose MAC original address is a second MAC address to PW, so that PE on the opposite terminal of PW can quickly learn the second MAC address; thus, flow produced during flooding treatment to the unicast message in the VPLS network is greatly lowered so as to save network bandwidth resource.
Owner:NEW H3C TECH CO LTD
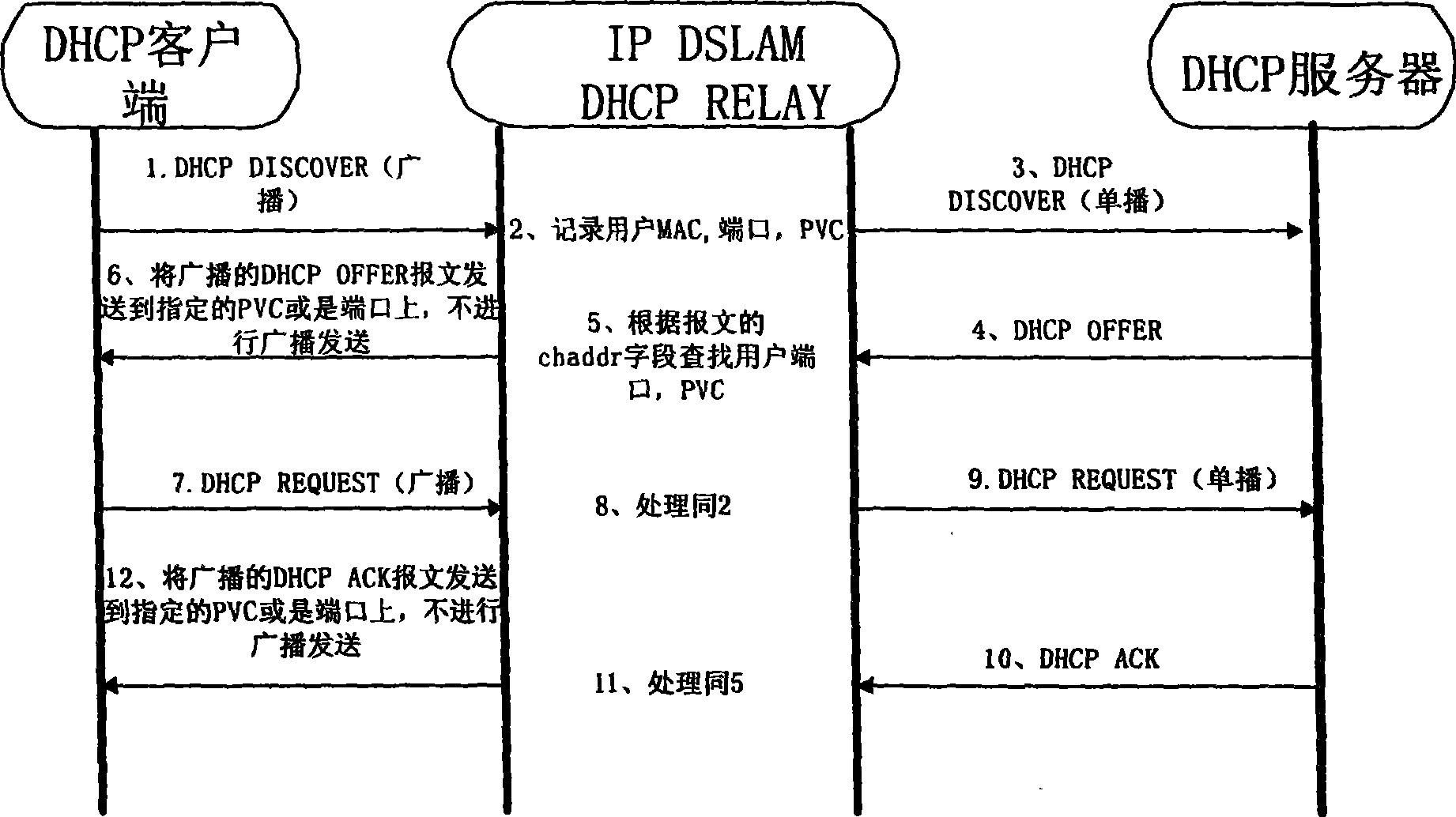
Method for preventing IP address from leakage
The invention discloses a method for preventing an IP address from being leaked, which comprises the following steps: recording a user port address for sending a message after a DHCP Relay acquires the DHCP message transmitted by a DHCP client; searching the MAC address of the DHCP client from the client hardware address field of the message; establishing corresponding relation between the MAC address and the user port address; searching the MAC address by using the DHCP Relay according to a client hardware address field in a response message after the response message transmitted by a DHCP server is received; searching the corresponding user port address according to the corresponding relation between the MAC address and the user port address; and then directly sending the response message to a user port determined by the user port address. The technical scheme provided by the invention effectively prevents the interception of a user, enhances the application safety of a DHCP protocol, simultaneously reduces the broadcast message transmission of a two-layer network, and saving the network bandwidth resources.
Owner:HUAWEI TECH CO LTD
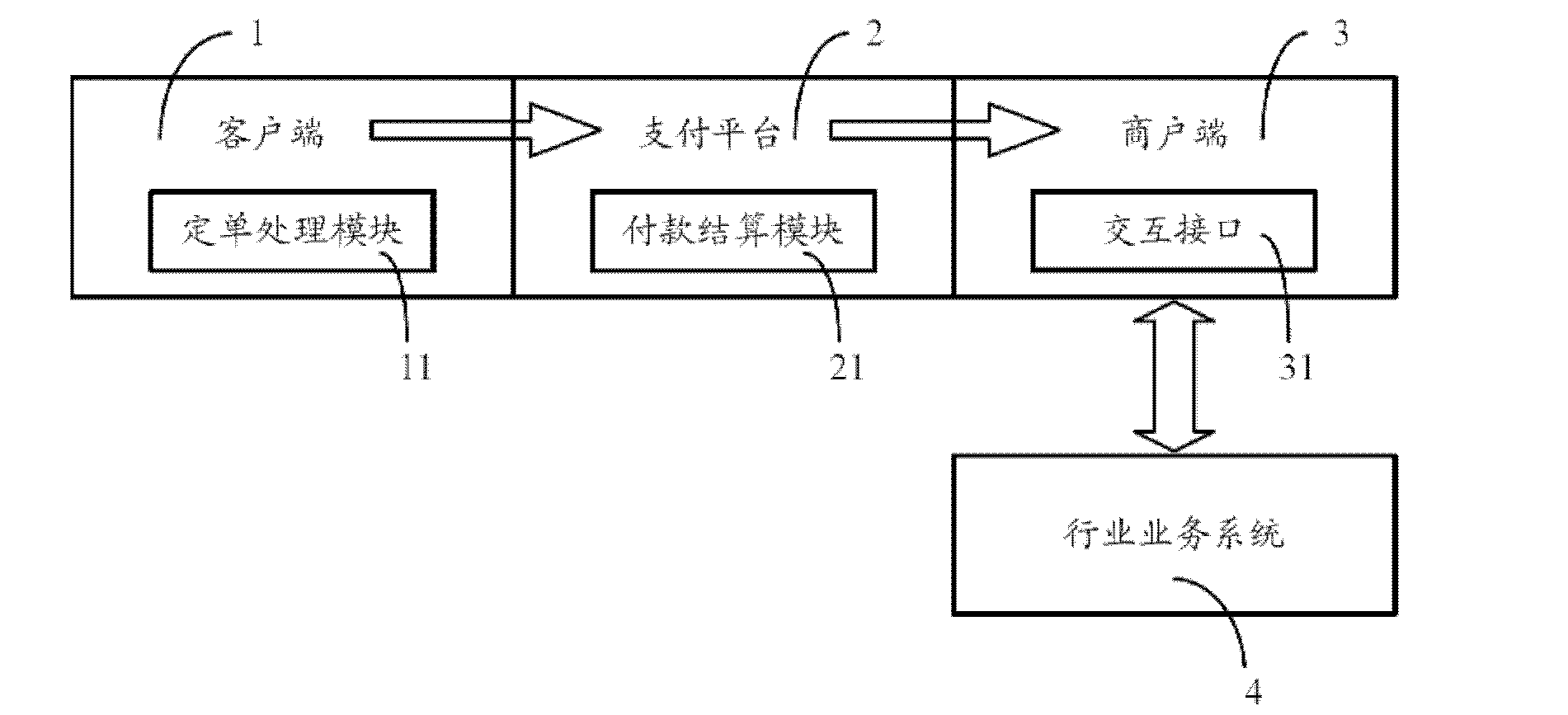
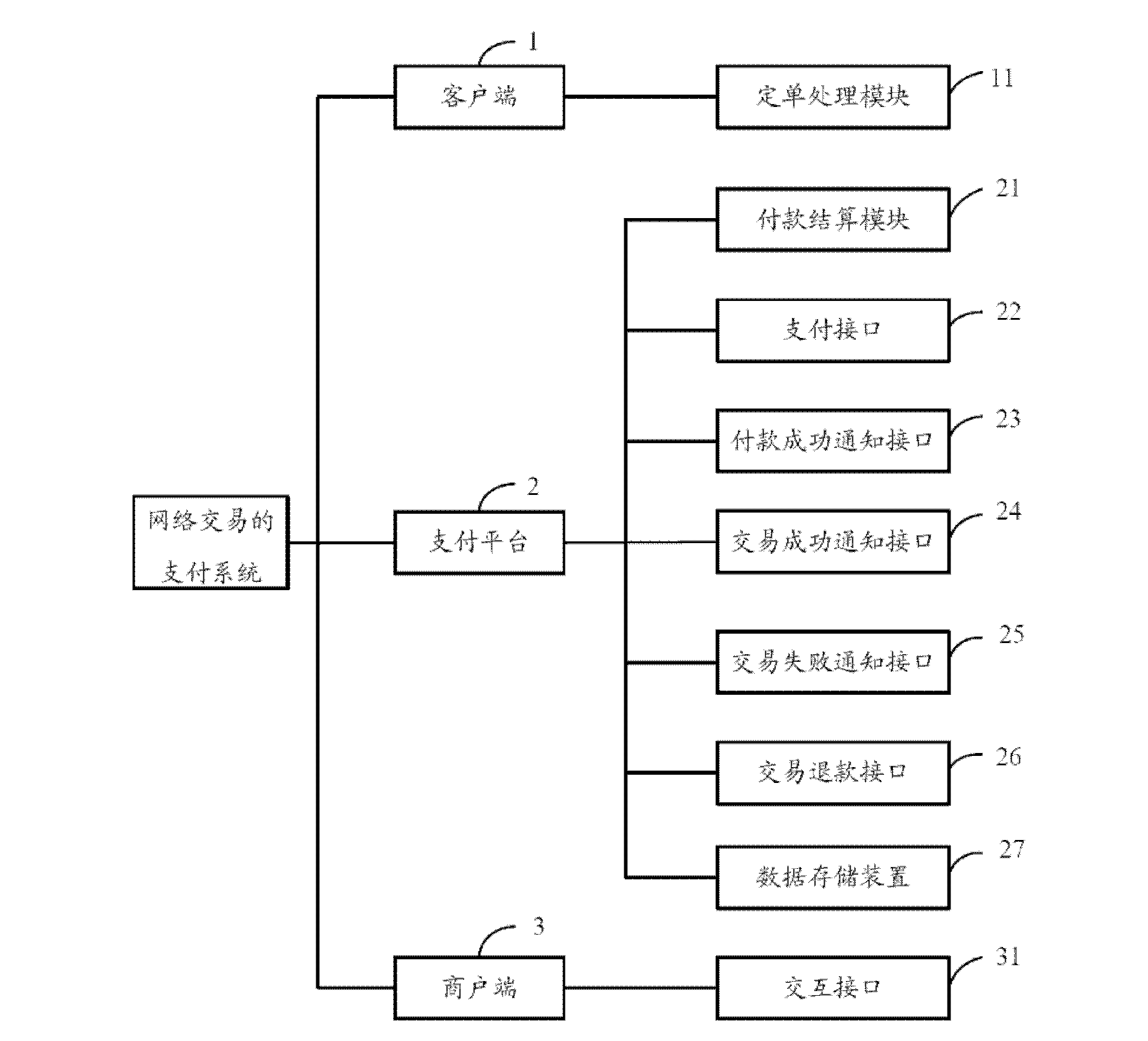
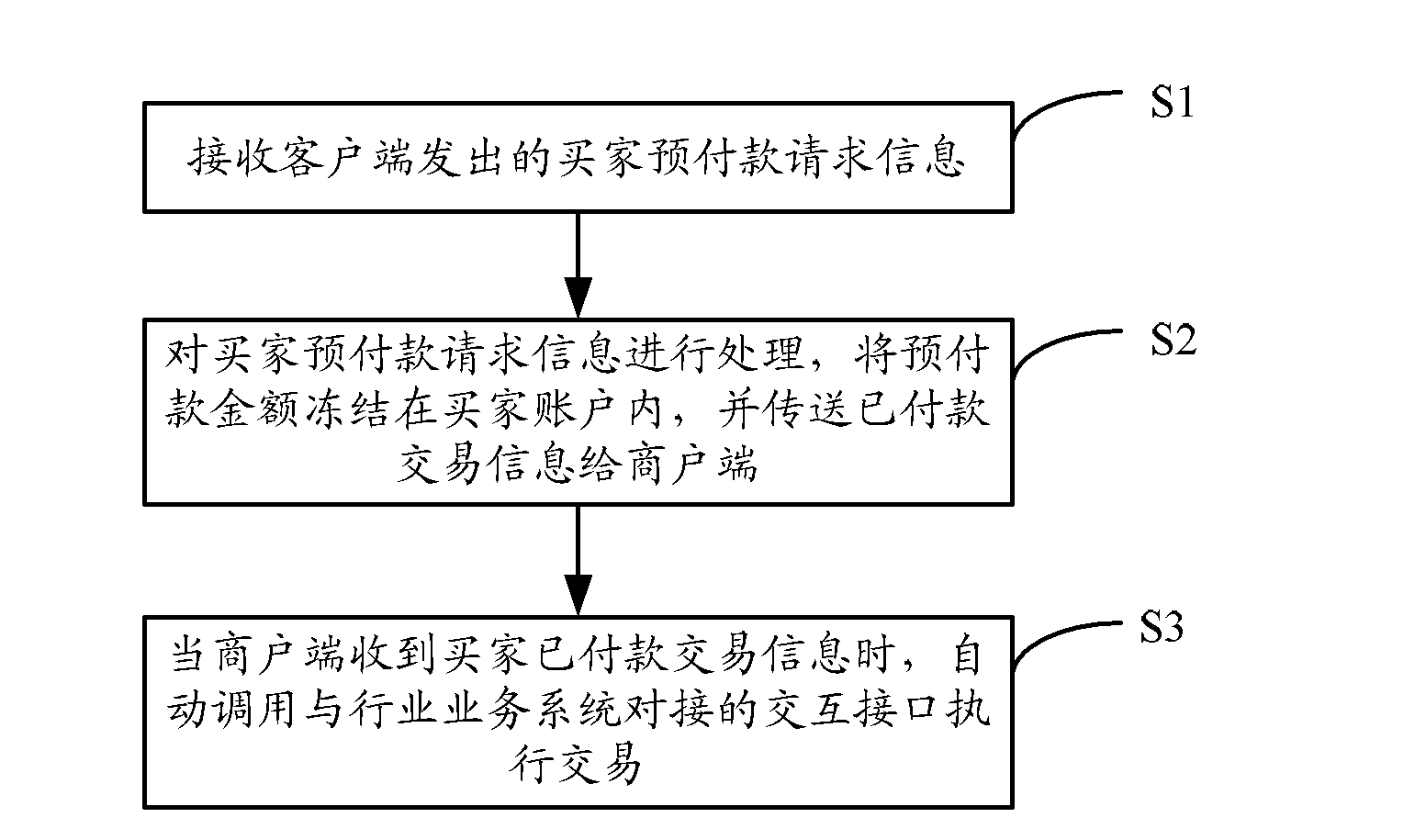
Payment method, payment device and payment system of networked transaction
InactiveCN103186852AReduce the amount of informationSave network bandwidth resourcesPayment architectureCommerceAdvance paymentPayment transaction
The invention discloses a payment method, a payment device and a payment system of networked transaction. The payment system comprises a client, a payment platform, a payment success informing interface and a commercial tenant end, wherein the client comprises a bill processing module which is used for receiving an ordered bill of a buyer and sending advance payment request information; the payment platform comprises a payment settlement module, and is used for processing the advance payment request information of the buyer and freezing advance payment account in an account of the buyer; the payment success informing interface is used for transmitting account paid transaction information to the commercial tenant end; and the commercial tenant end comprises an interactive interface used for being abutted against an industry business system. When the commercial tenant end receives the account paid transaction information of the buyer, the transaction is executed by calling the interactive interface. Compared with a prior agency secured transaction, the technical scheme is that the payment method, the payment device and the payment system of the networked transaction reduce the amount of information needing processing, save network bandwidth resources, and meanwhile reduce manual operations of the buyer and a seller.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
Method and system for realizing realtime transmission protocol message redundancy
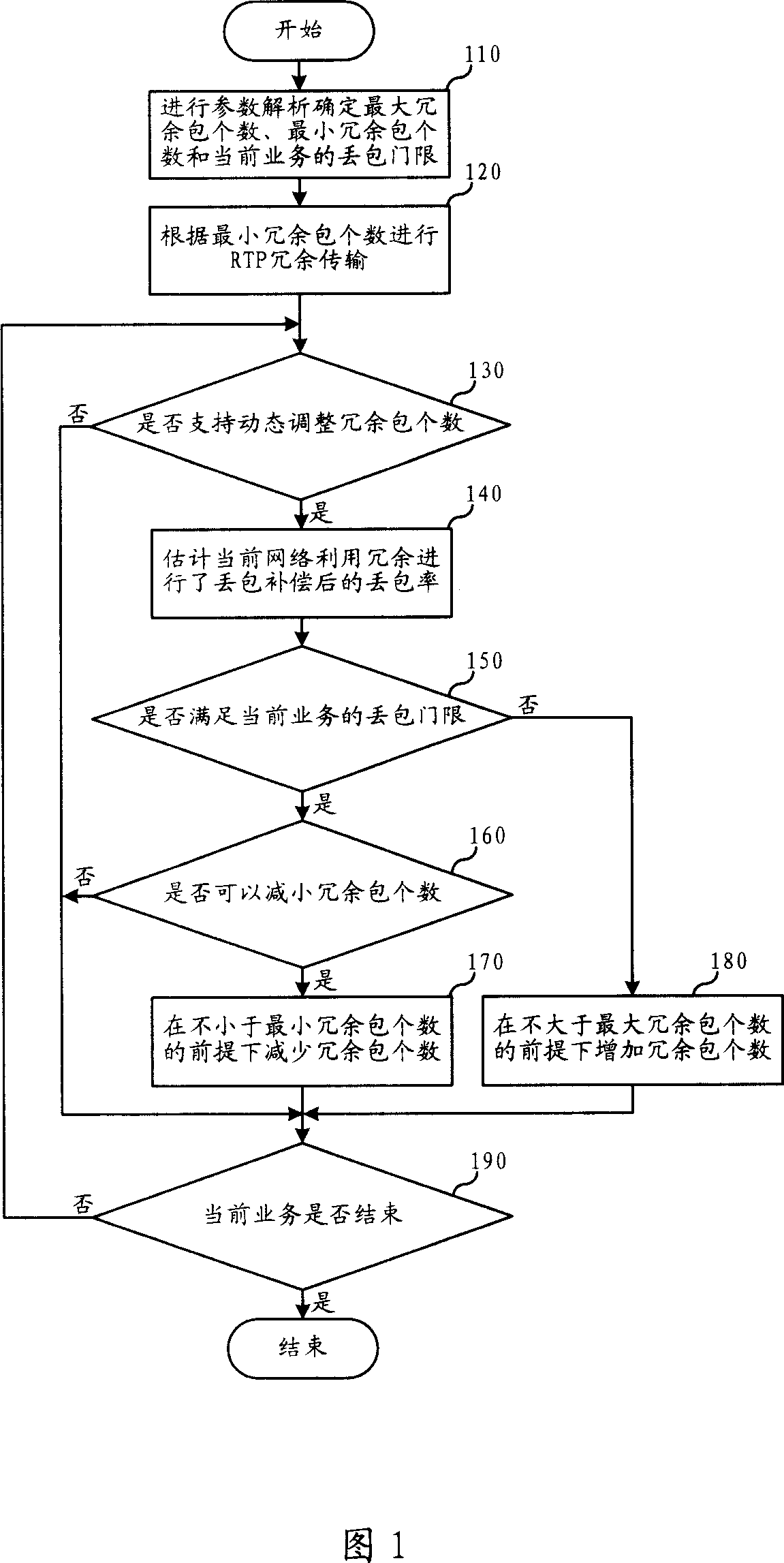
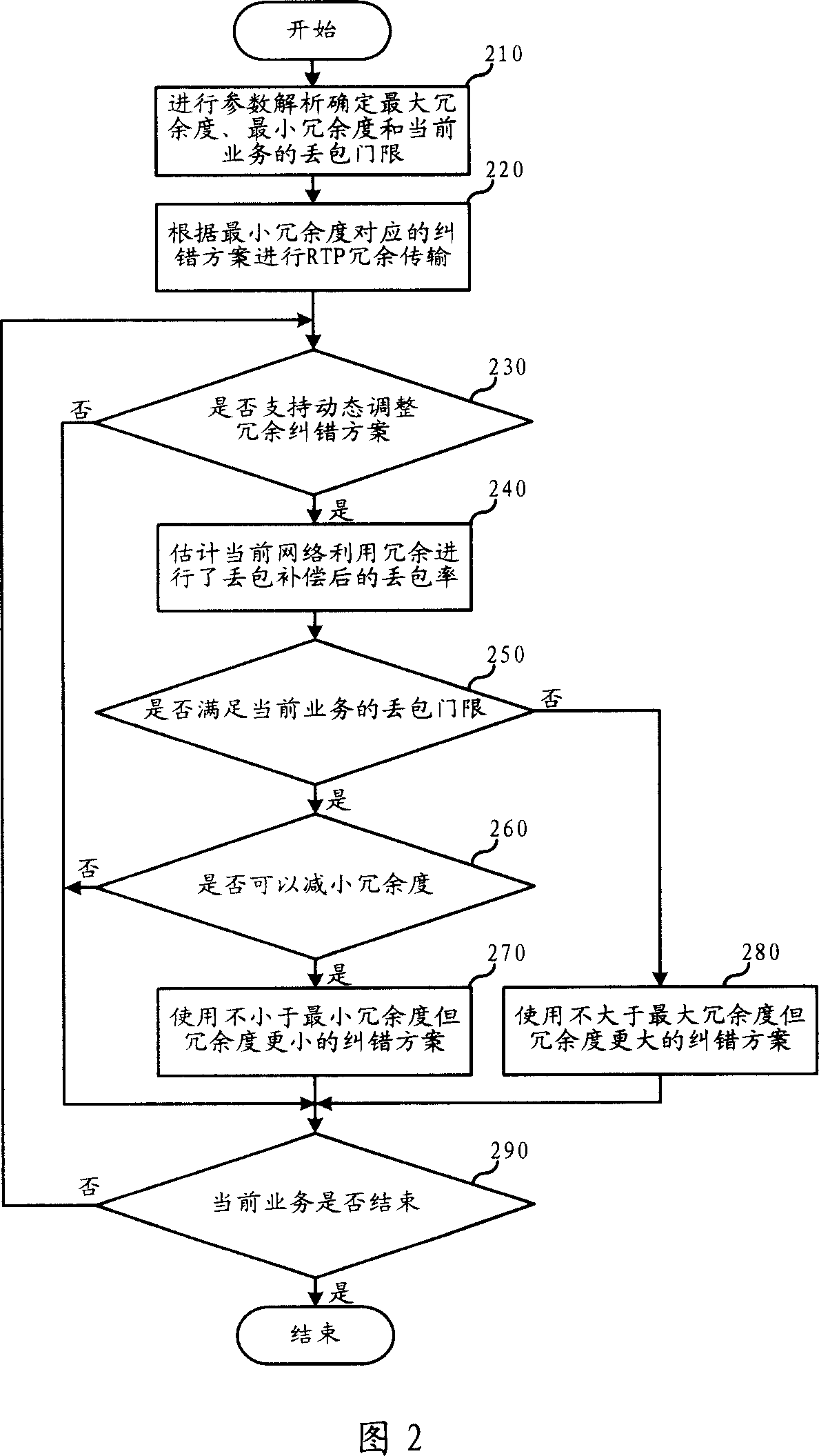
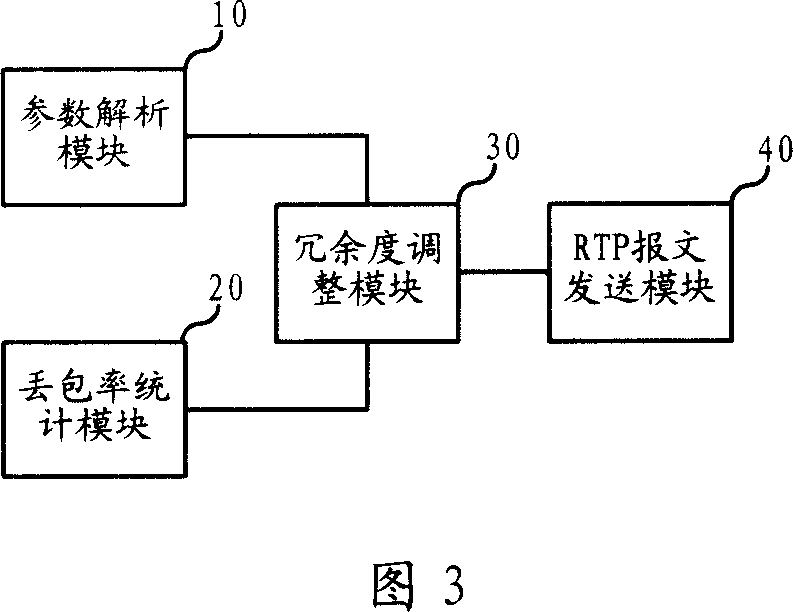
ActiveCN101030832ASave bandwidth resourcesGuaranteed service QoS requirementsError preventionReal-time Transport ProtocolReal-time computing
The invention is used for avoiding the waste of bandwidth and satisfying the requirement of packet loss rate when using RTP redundancy mechanism. In the invention, when making a calling, the redundancy degree can be dynamically adjusted according to the transmission environment of network.
Owner:HUAWEI TECH CO LTD
Method for deciding route at radio mesh network
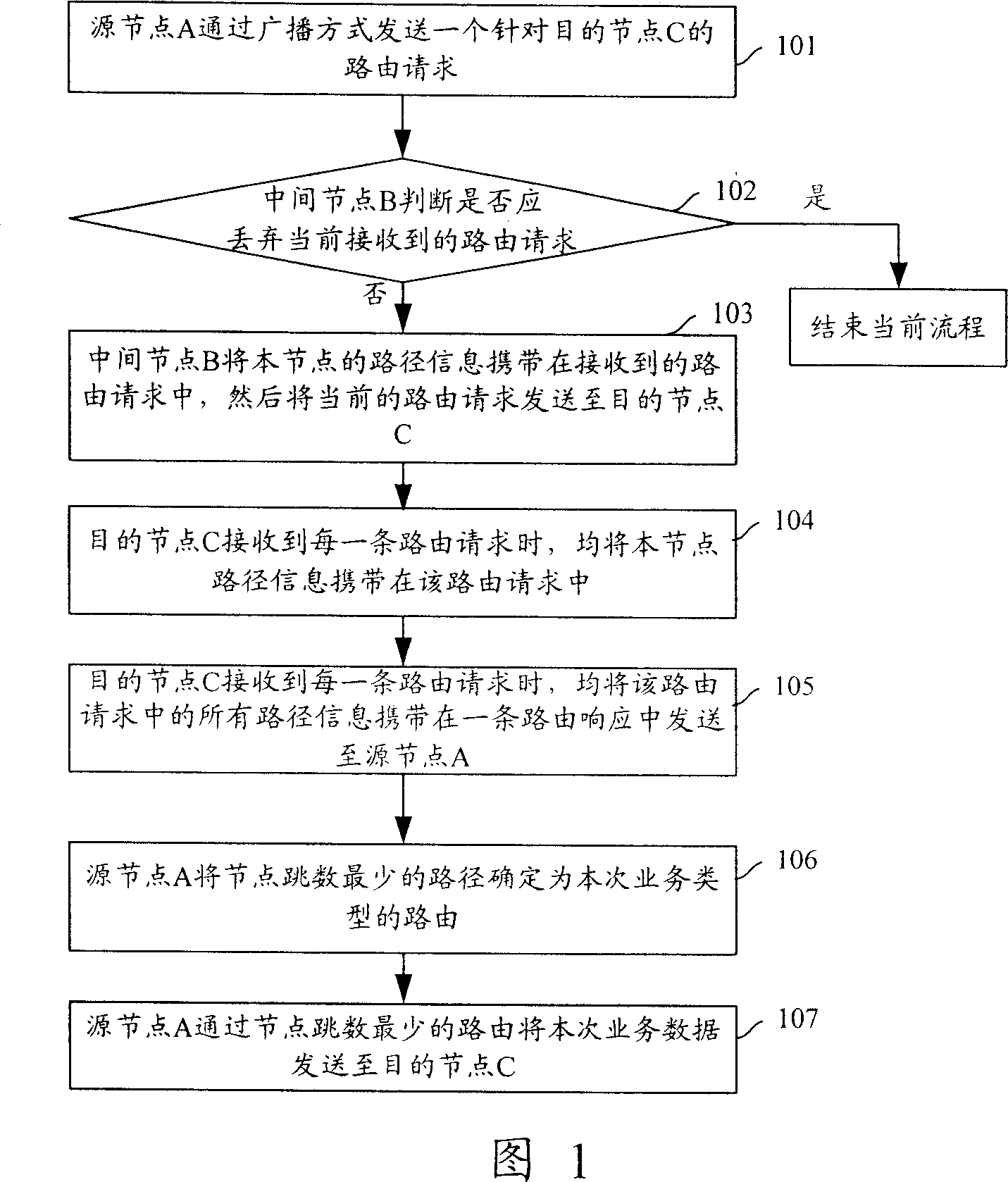
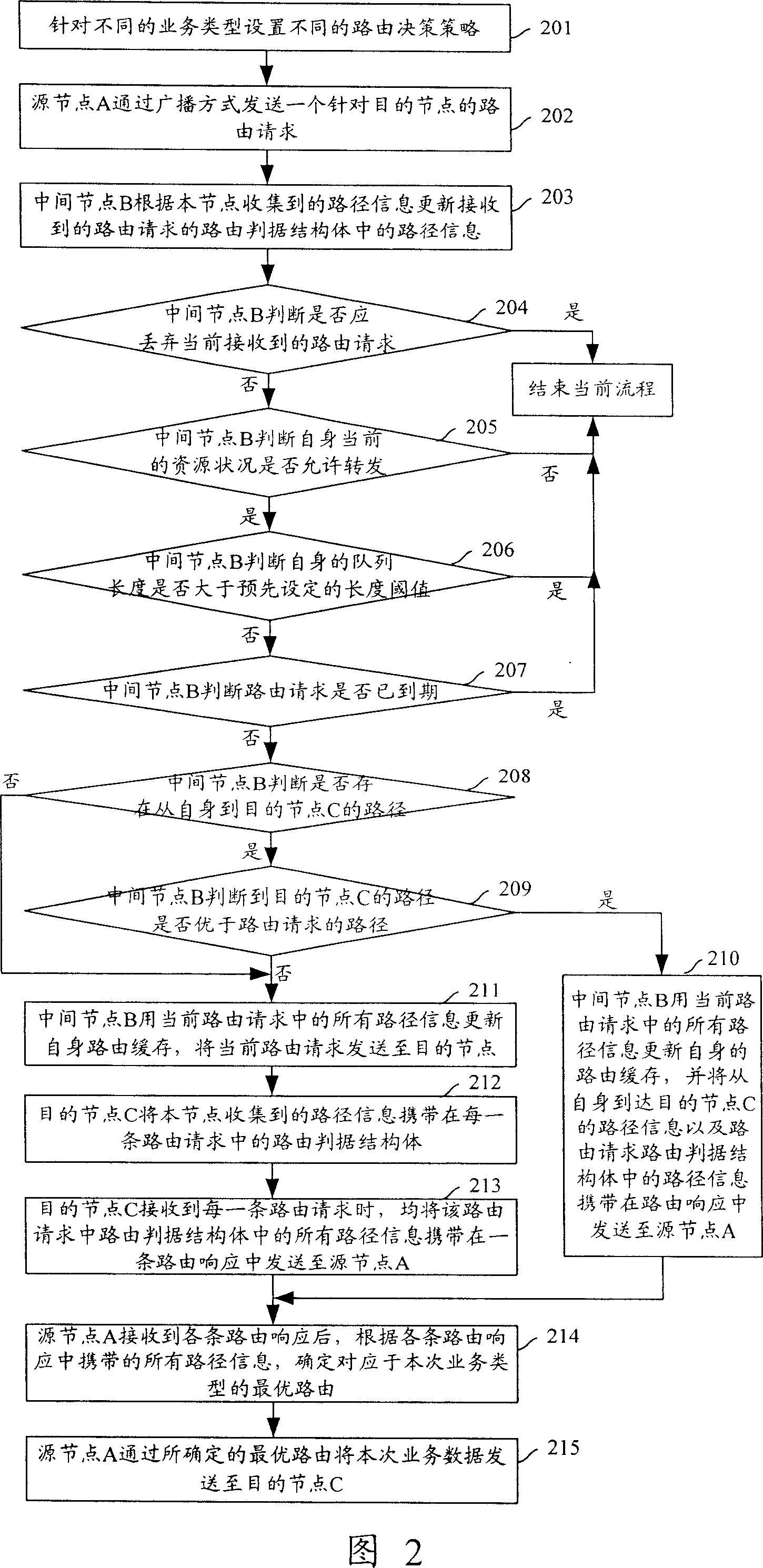
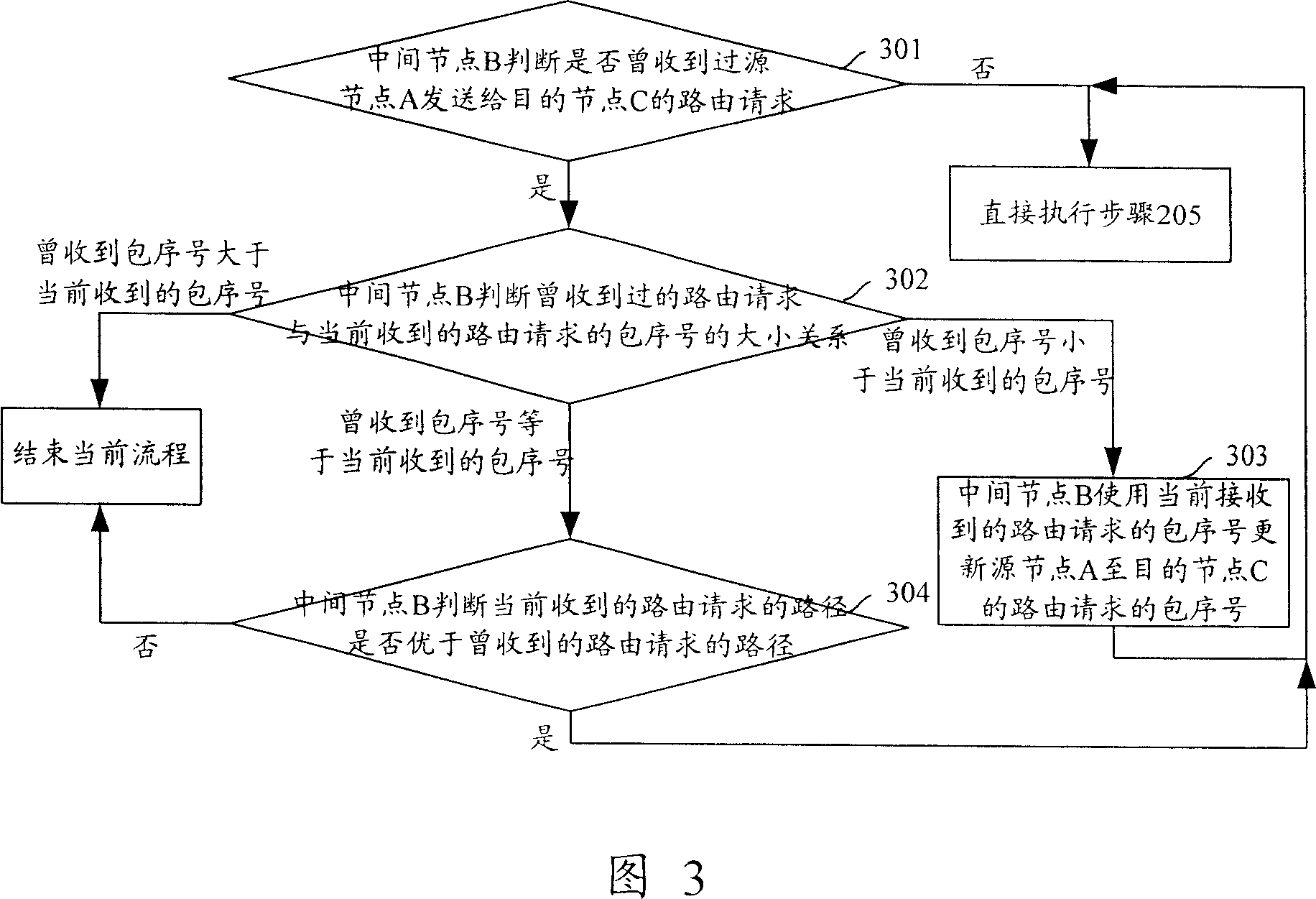
InactiveCN101048012AGuaranteed normal transmissionImprove performanceMultiplex system selection arrangementsData switching by path configurationQuality of serviceWireless mesh network
The invention discloses a method for route-identifying in a wireless mesh network, including: It set up different routing strategies for different types of business, and the source nodes receive multi-path routing response with routing information, then the source determines the related routing according to the strategy of the business and the routing information. The invention can ensure data transmission between the source node and the destination node, and greatly improves the network performance.
Owner:HUAWEI TECH CO LTD +1
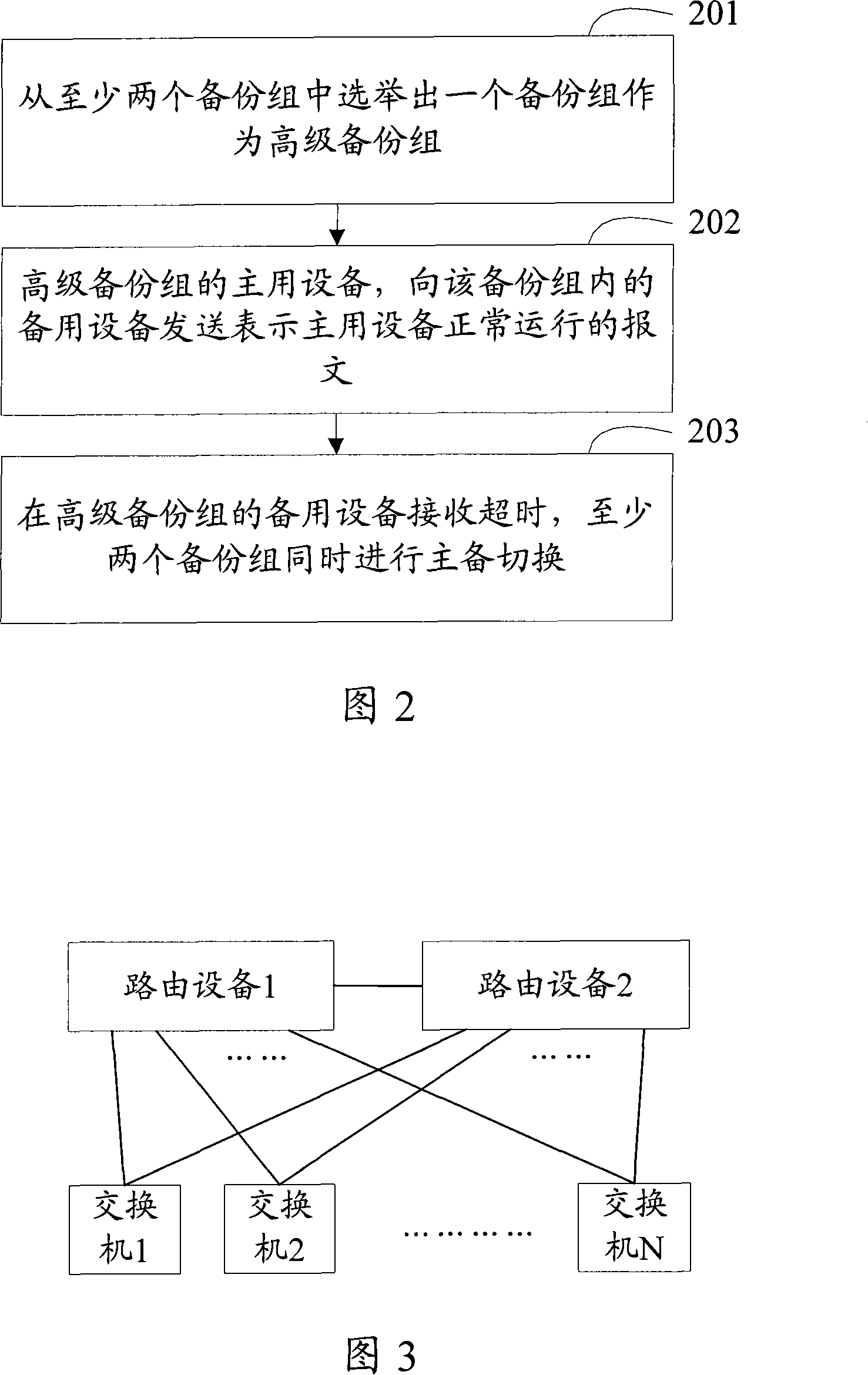
Main and standby switching method and route standby system for route device
ActiveCN101094102AIncrease the number ofWill not increase the burdenError detection/correctionData switching networksTelecommunicationsBackup
In the invention, the main equipment is a same route equipment, and the stand-by equipment is one of multi backup group in same route equipment; the main equipment only having one backup group sends a message for indicating the main equipment is in normal running state to the standby equipment in said backup group; if the receiving of message by the standby equipment in the standby group is over time, all standby groups simultaneously make man / standby switch. By the invention, the amounts of the messages between route devices will be not increased after the amount of backup group are increased.
Owner:NEW H3C TECH CO LTD
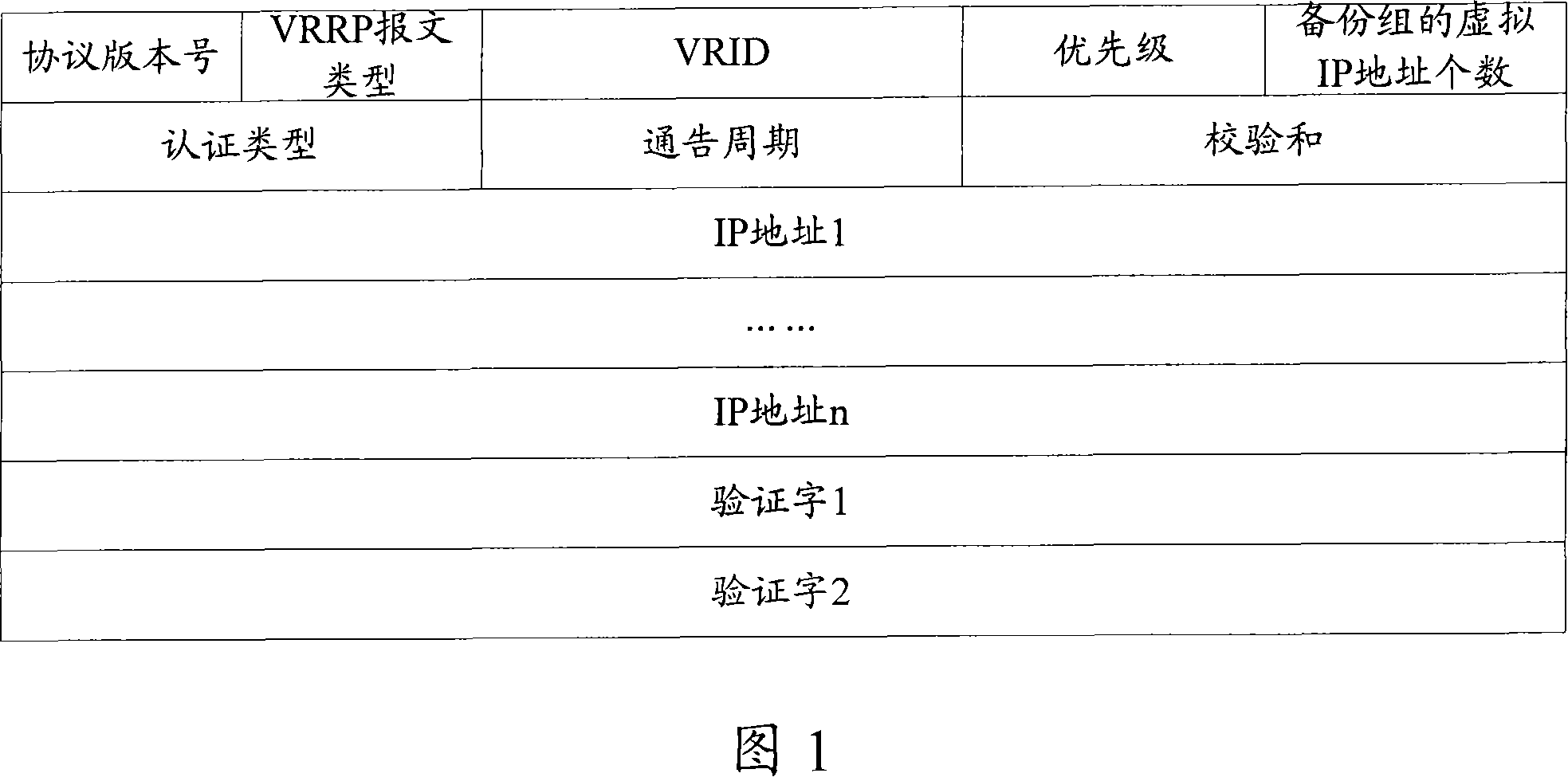
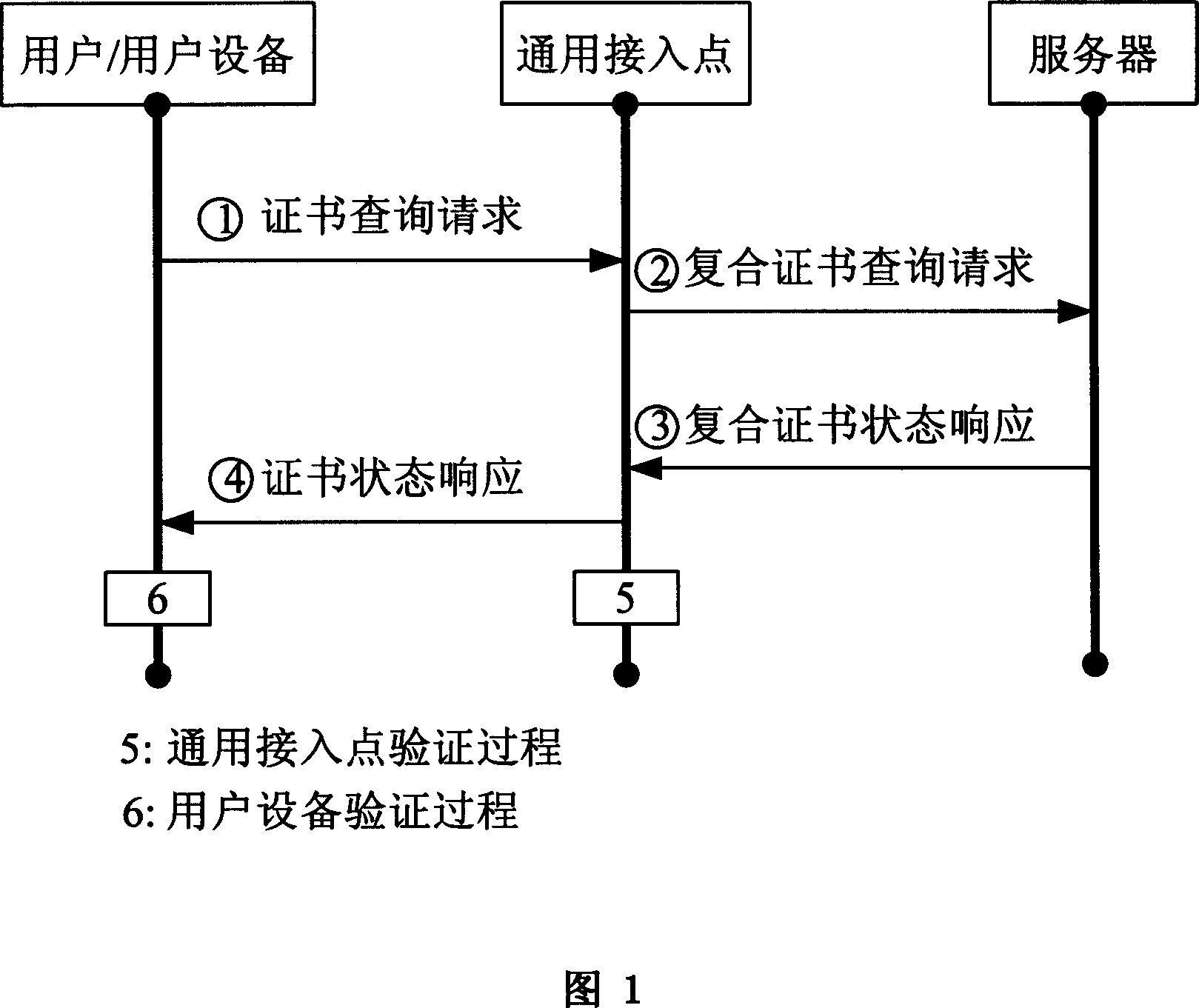
Public key certificate state obtaining and verification method
ActiveCN1929380AProcesses that reduce exchangesSave bandwidth resourcesPublic key for secure communicationUser identity/authority verificationUser deviceValidation methods
This invention relates to common key identification acquiring and test method, which comprises the following steps: forming and sending identification and index demands; forming and sending compound identification demands; forming and sending compound identification status responding; transferring identification status for interface test for user device testing. This invention adopts user identification catch method through interface to provide user or user device for common interface point.
Owner:CHINA IWNCOMM
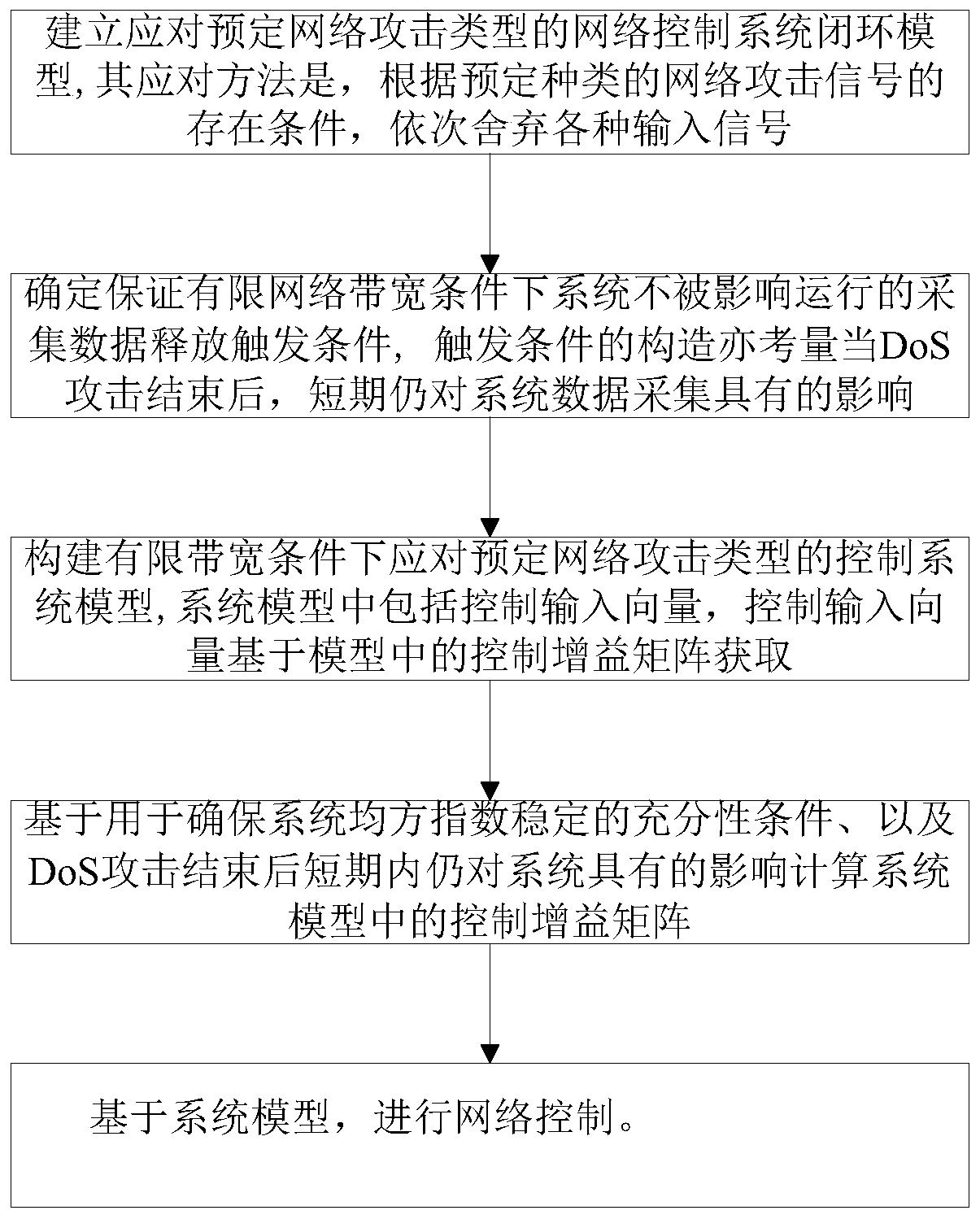
Security control method of event-driven network control system under multi-network attack
ActiveCN110213115AImprove stabilityReduce the number of transfersData switching networksLyapunov stabilityEvent trigger
The invention provides a security control method of an event-driven network control system under a multi-network attack. Considering the network transmission security problem, a random network spoofing attack, a replay attack and a DoS attack are sequentially introduced, and a system closed-loop model under the multi-network attack is established. Further considering the constraint of the limitednetwork bandwidth, an event trigger mechanism is introduced to screen and release sampling data meeting a preset event trigger condition to the network for transmission, thereby establishing a new switching system model on the basis of the system closed-loop model. Based on a switching system model, a Lyapunov stability theory is utilized to obtain a sufficiency condition for enabling the system to meet the stability of a mean square index, and a group of linear matrix inequalities is solved to obtain the gain of the state feedback controller. Compared with an existing controller design method, safe and stable operation of the network control system under the influence of multi-network attacks is guaranteed, meanwhile, the data transmission frequency is reduced, and limited network bandwidth resources are saved.
Owner:NANJING UNIV OF FINANCE & ECONOMICS
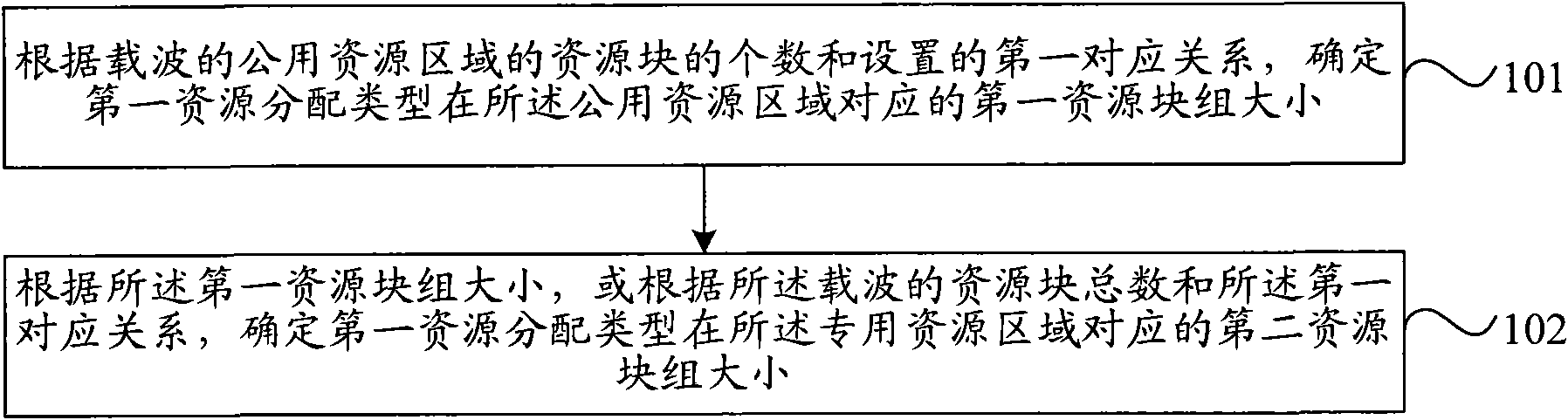
Method and device for allocating resources
ActiveCN102340875ASimplify the scheduling processLow reassignment rateMultiple modulation transmitter/receiver arrangementsNetwork traffic/resource managementResource blockCarrier signal
The invention discloses a method and device for allocating resources. The method comprises the steps of: determining the size of a first resource block group corresponding to a first resource allocation type in public resource regions according to the number of resource blocks of the public resource regions of carriers and a set first corresponding relationship; dividing the resource blocks of all the public resource regions of the carriers into one or more resource block groups according to the size of the first resource block group; determining the size of a second resource block group corresponding to the first resource allocation type in a special resource region according to the size of the first resource block group or the total number of the resource blocks of the carriers and the first corresponding relationship; and dividing the resource blocks of the special resource region of the carriers into one or more resource block groups according to the size of the second resource block group. According to the embodiment of the invention, the size of the resource block group is determined in accordance with the number of the resource blocks of the public resource regions, so that the scheduling process is simple, the resource repeated allocation rate is low, and the bandwidth resource is saved.
Owner:HUAWEI TECH CO LTD
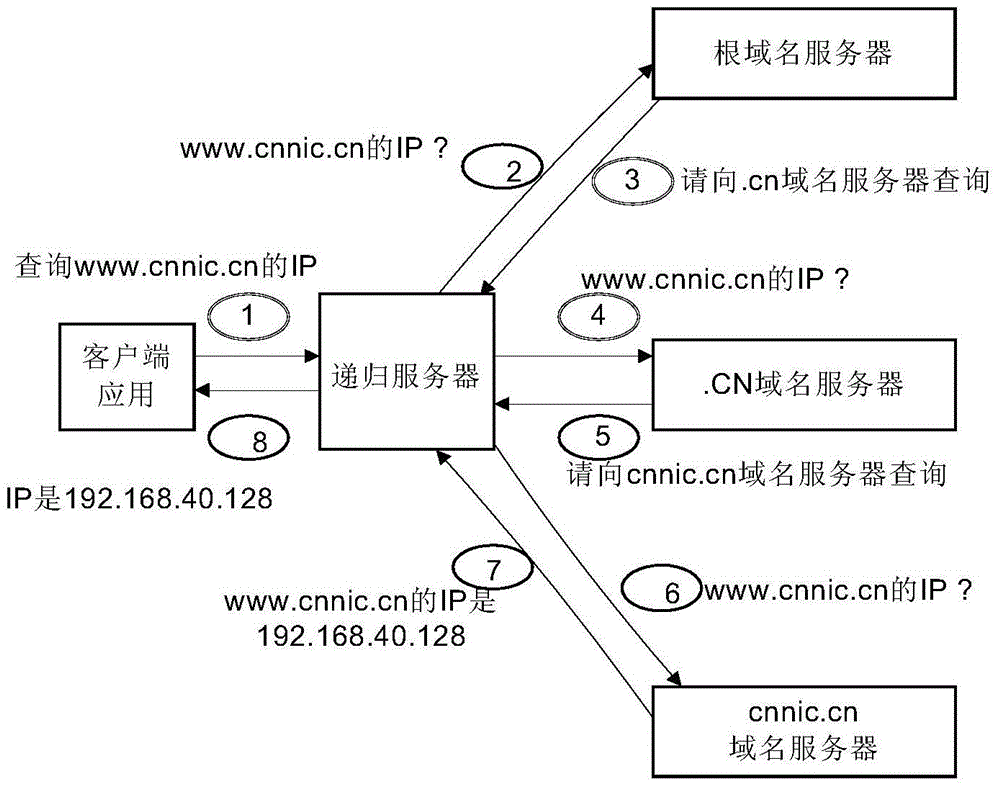
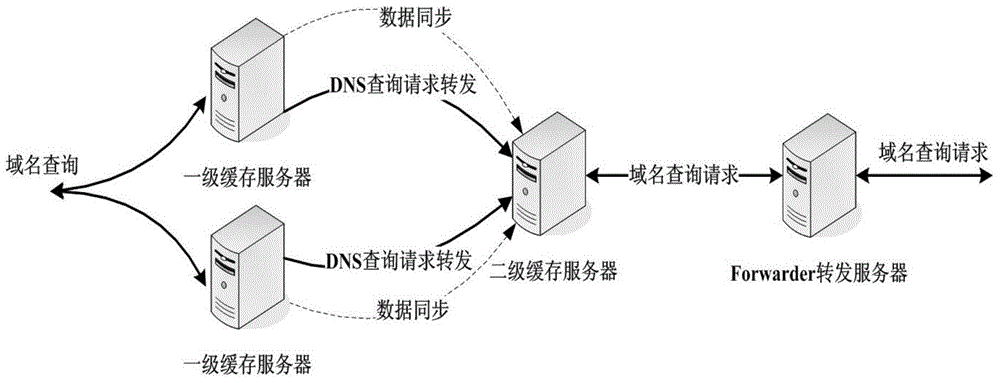
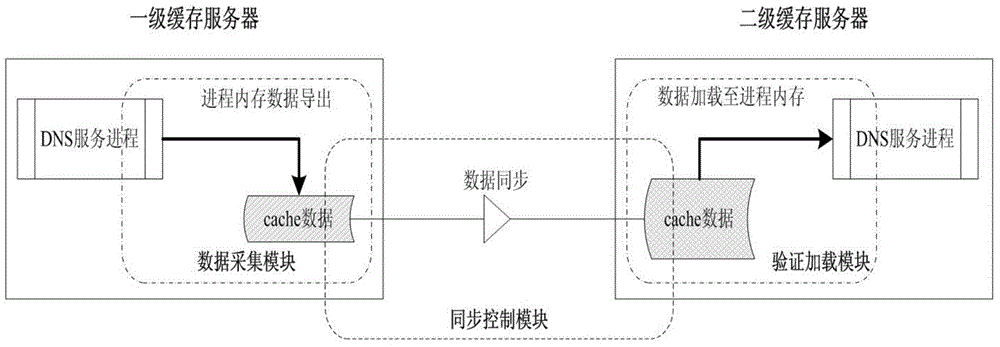
Recursive domain name service system and method of multi-level shared cache
The invention relates to a recursive domain name service system and method of multi-level shared cache. The system comprises first-level cache servers, a second-level cache server and a forward server. The second-level cache server is used for collecting cache records of all first-level cache servers at a front end through a consistency cache sharing mechanism, and establishing a relatively large cache region; and checking a local server cache region after receiving a domain name query request forwarded by the first-level cache server; and directly returning data to the first-level cache server if a requested resource record exists in the local cache region, or forwarding the domain name query name to the forward server; and then the forward server is used for iteratively querying to obtain a query result. Furthermore, the system comprises a data acquisition module, a synchronous control module and a verification loading module. The sharing of cache resource records between different cache servers can be realized, the domain name cache hit ratio is obviously improved, and the domain name analysis time delay is shortened.
Owner:CHINA INTERNET NETWORK INFORMATION CENTER
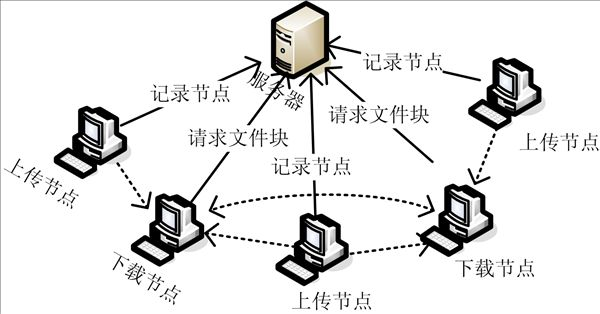
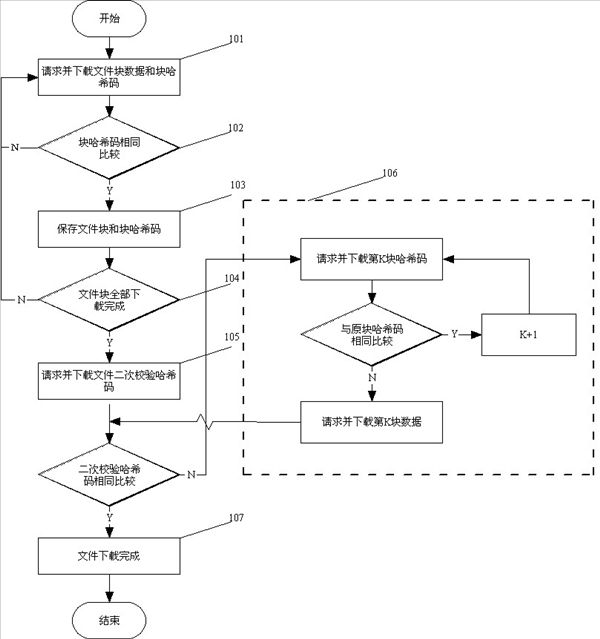
Verifying method for network file transmission
InactiveCN102325167AGuaranteed correctnessImprove reliabilityTransmissionComputer hardwareFile transmission
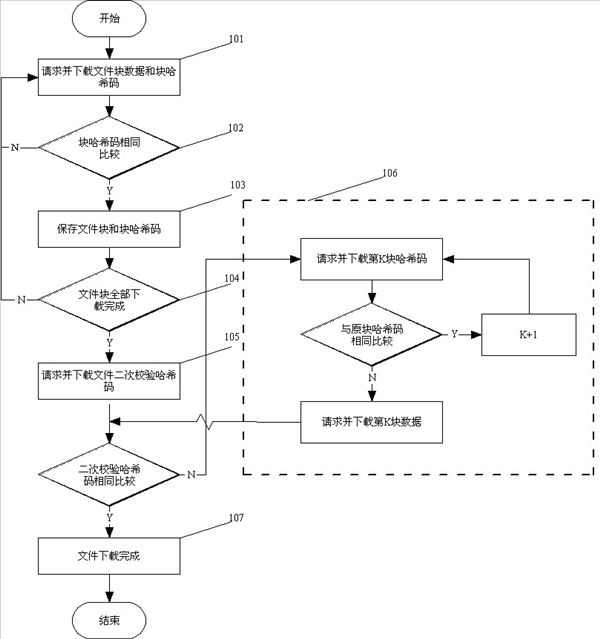
The invention provides a verifying method for network file transmission. File block transmission data and block hash codes are adopted in the method. The method comprises the following steps of: after block transmission finishes, extracting the block hash codes and comparing the extracted block hash codes with the value acquired by transmission, if an error happens, retransmitting the value from another data source, otherwise, preserving the block data and the block hash codes in a file; after the file is transmitted, acquiring secondary verification hash codes of file blocks from a server, performing secondary verification hash code extraction on the file preserving the block hash codes, comparing, if different, newly requesting the server for the addresses of other file servers, and retransmitting; and repeating the processes till the secondary verification hash codes of the file blocks are compared successfully. Compared with the prior art, the method has the advantages that: besides hash code verification of the file blocks, secondary verification of the hash codes of the file blocks is performed, so that the complete accuracy of file verification is ensured and the reliability of file transmission is improved. The secondary verified hash codes of the file blocks are acquired by secondary hash calculation of the hash codes of the file blocks, the number of the file blocks is limited, and the advantage is obvious compared with massive time consumption in hash calculation of the whole file. When the secondary verified hash codes of the file blocks are different, error file blocks of the file can be quickly found by using the block hash codes; and compared with a mode of directly downloading the file blocks, massive broadband resources are saved.
Owner:HANGZHOU MICORUNIT TECH
Method, node and system for establishing backup label switching path
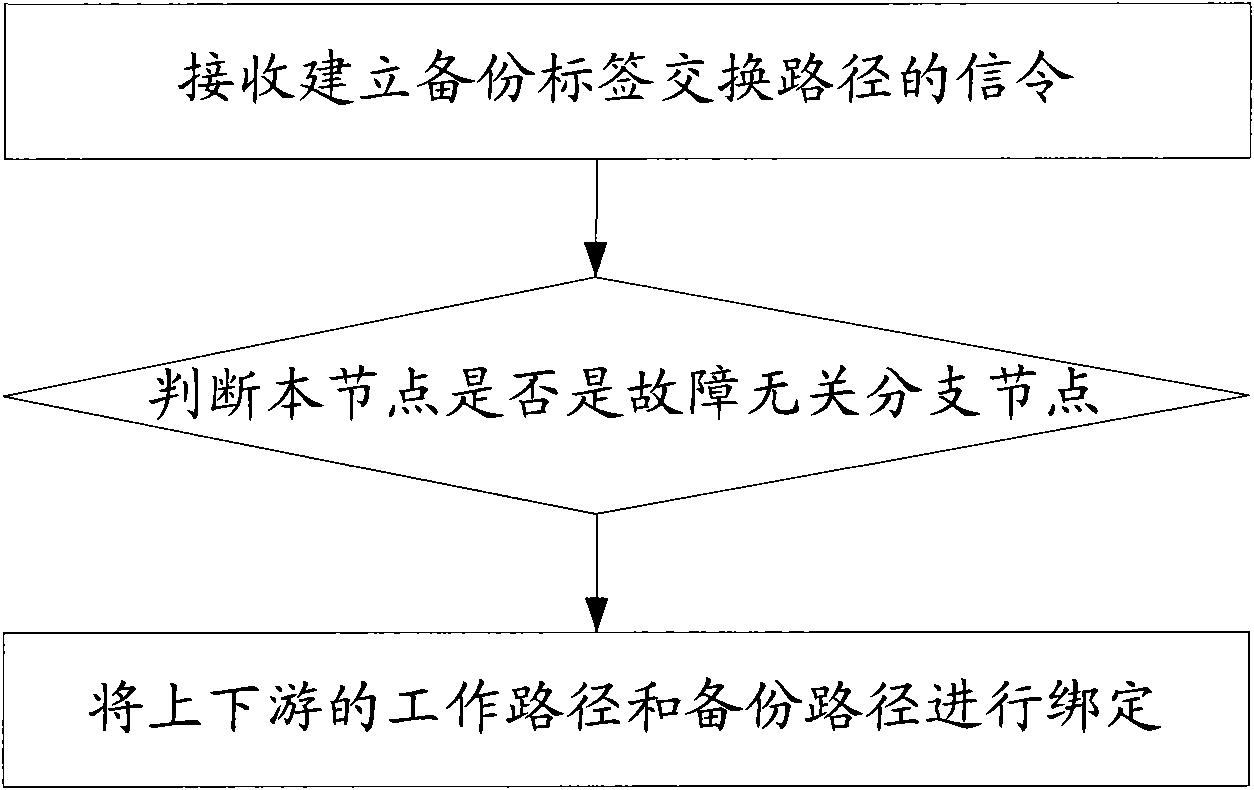
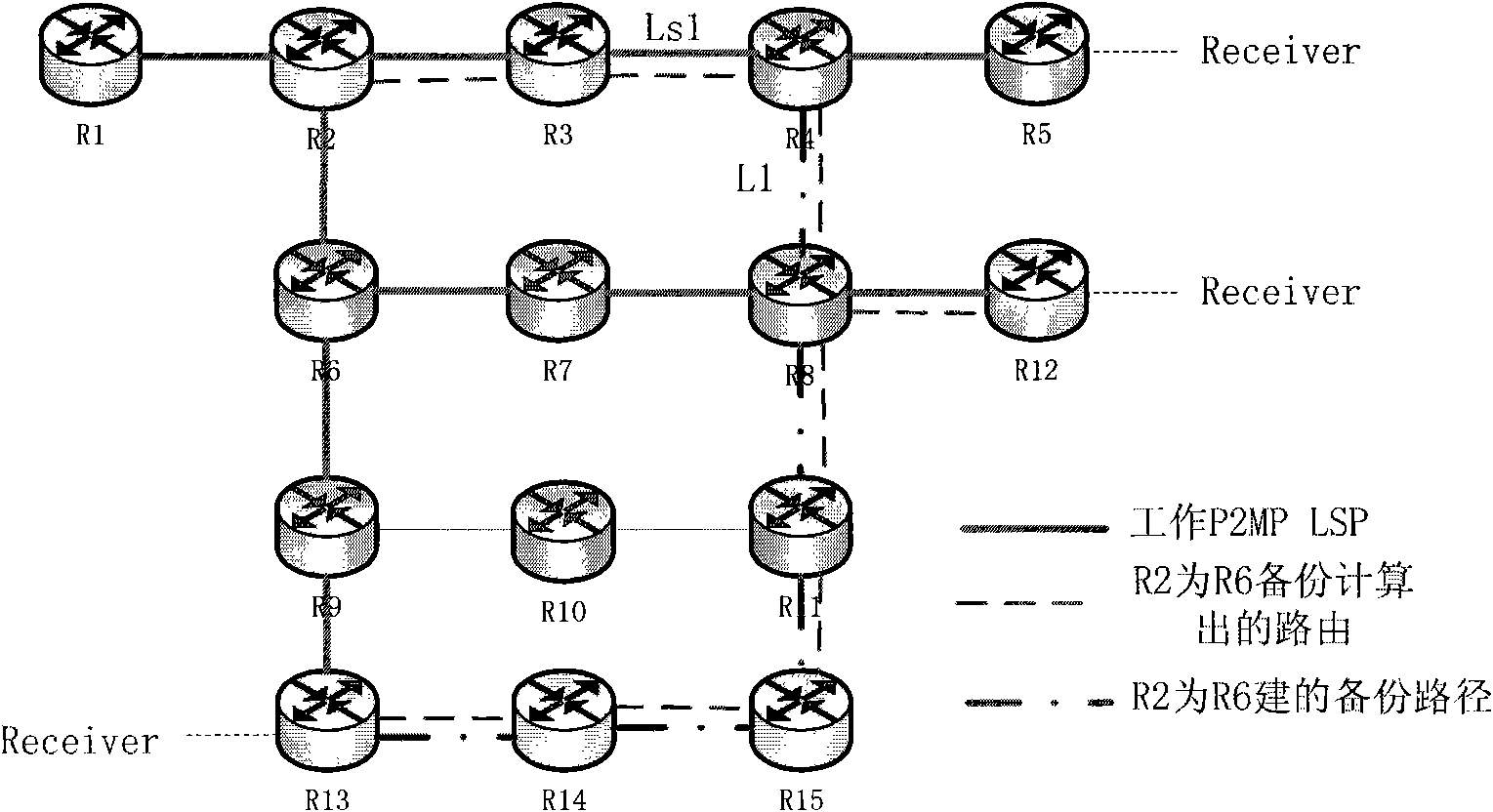
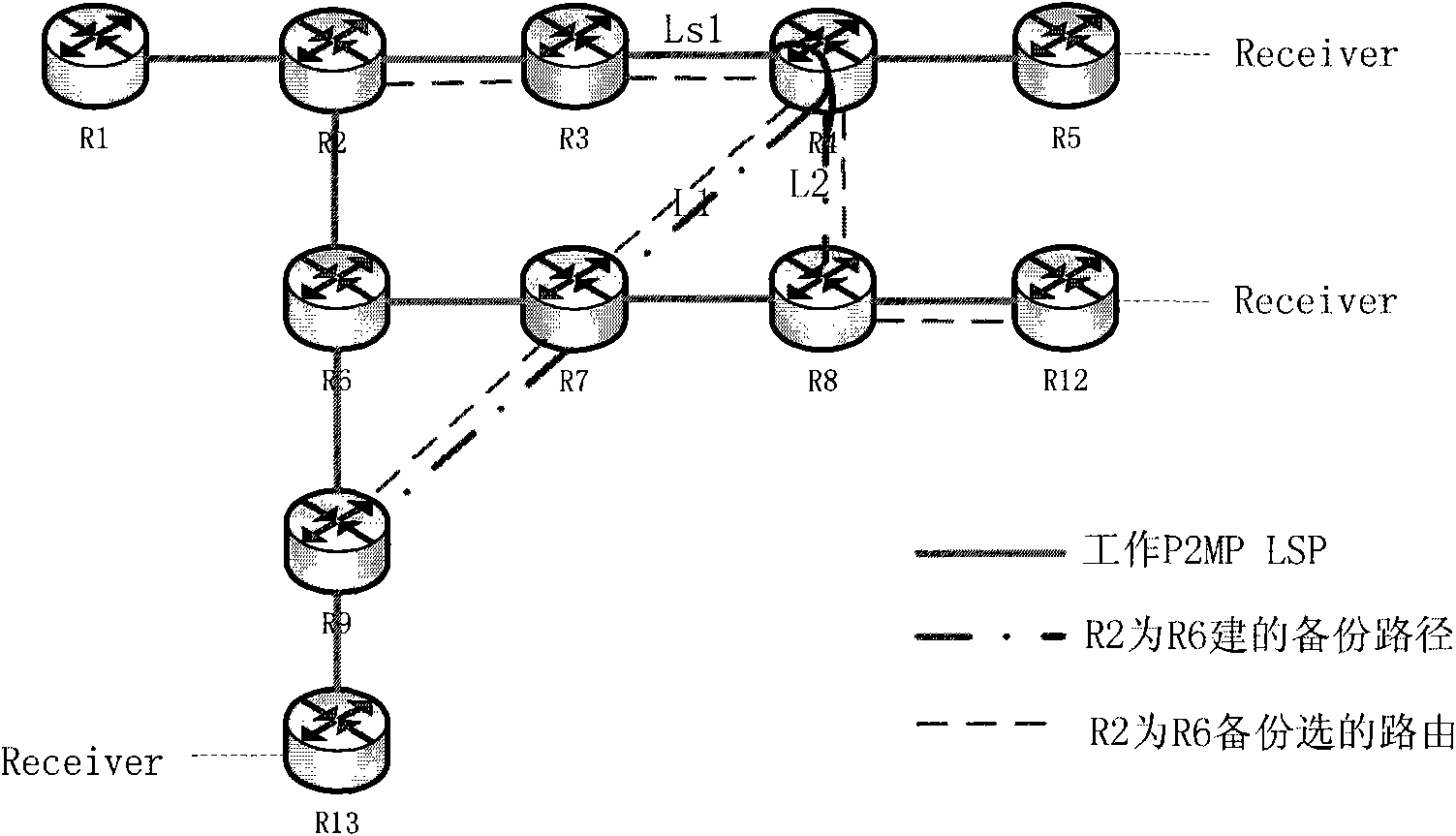
InactiveCN101552715AAvoid wastingAvoid double sendingData switching networksBackup pathLabel switching
The embodiment of the invention discloses a method for establishing a backup label switching path, and a method, a node and a system for protection and rearrangement of a fault. The method for establishing a backup label switching path comprises the following steps: receiving a command for establishing a backup label switching path; judging whether the node is a branch node unrelated to the fault or not, if the node is a branch node unrelated to the fault, binding an operating path and a backup path on the upper stream and the lower stream. By using the operating path unrelated to the fault, the superposition of the backup path and the operating path is avoided, the resource waste caused by a loop formed by the backup path and the operating path is avoided, and network resources and label resources are saved. A service message is sent to the superposed part of the backup path and the operating path to prevent the repeated sending of the service message, bandwidth resources are saved, and thus, effective multicast LSP protection is achieved by using least resources.
Owner:深圳市智通天下科技服务有限公司
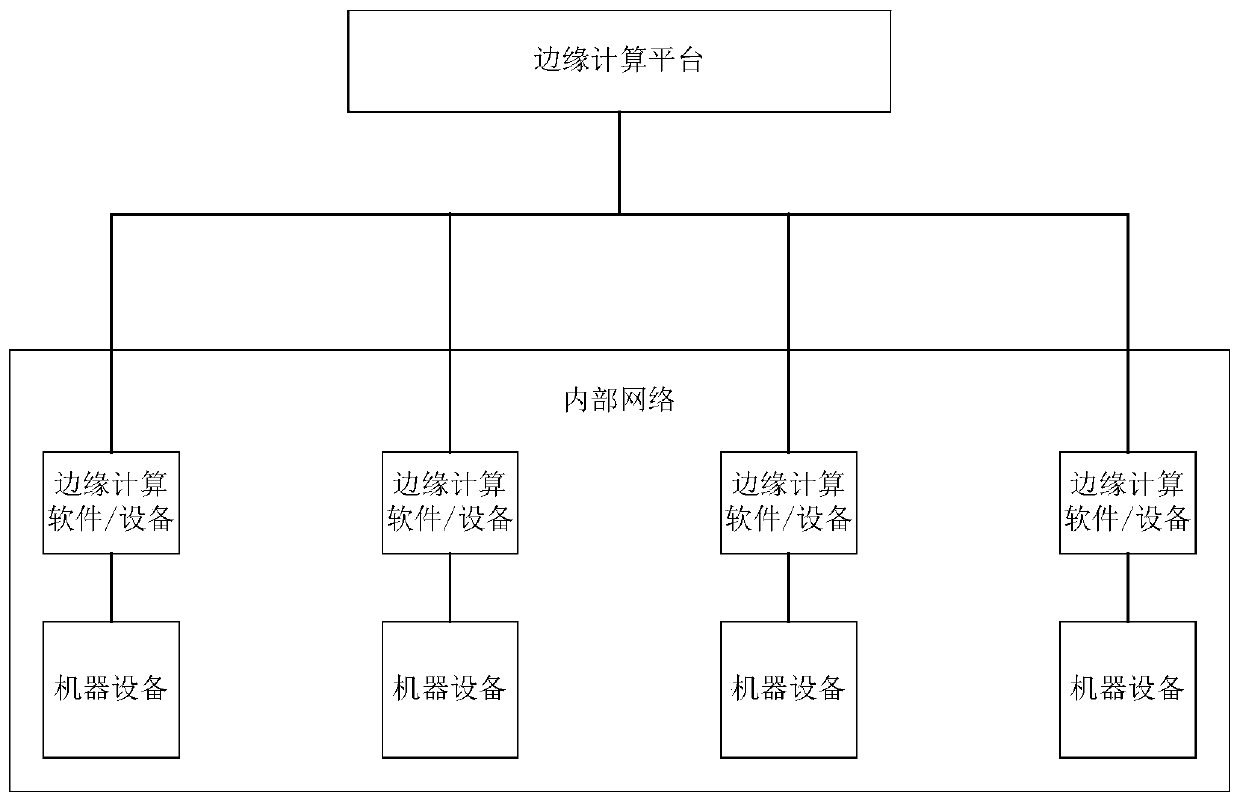
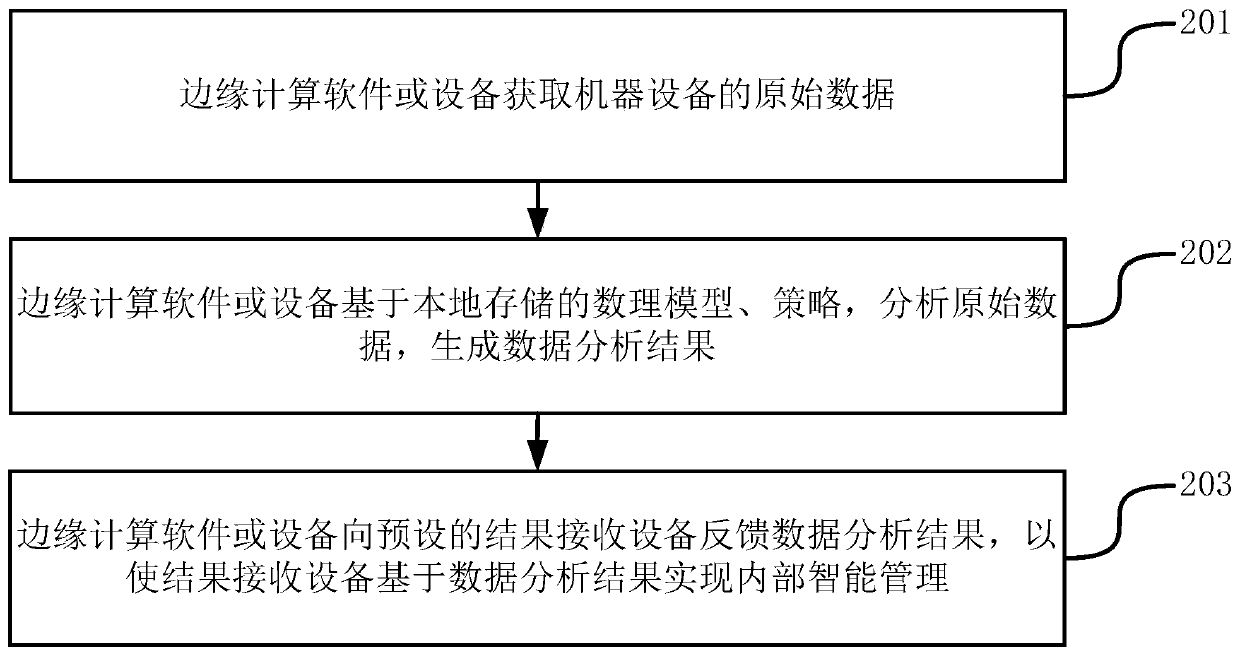
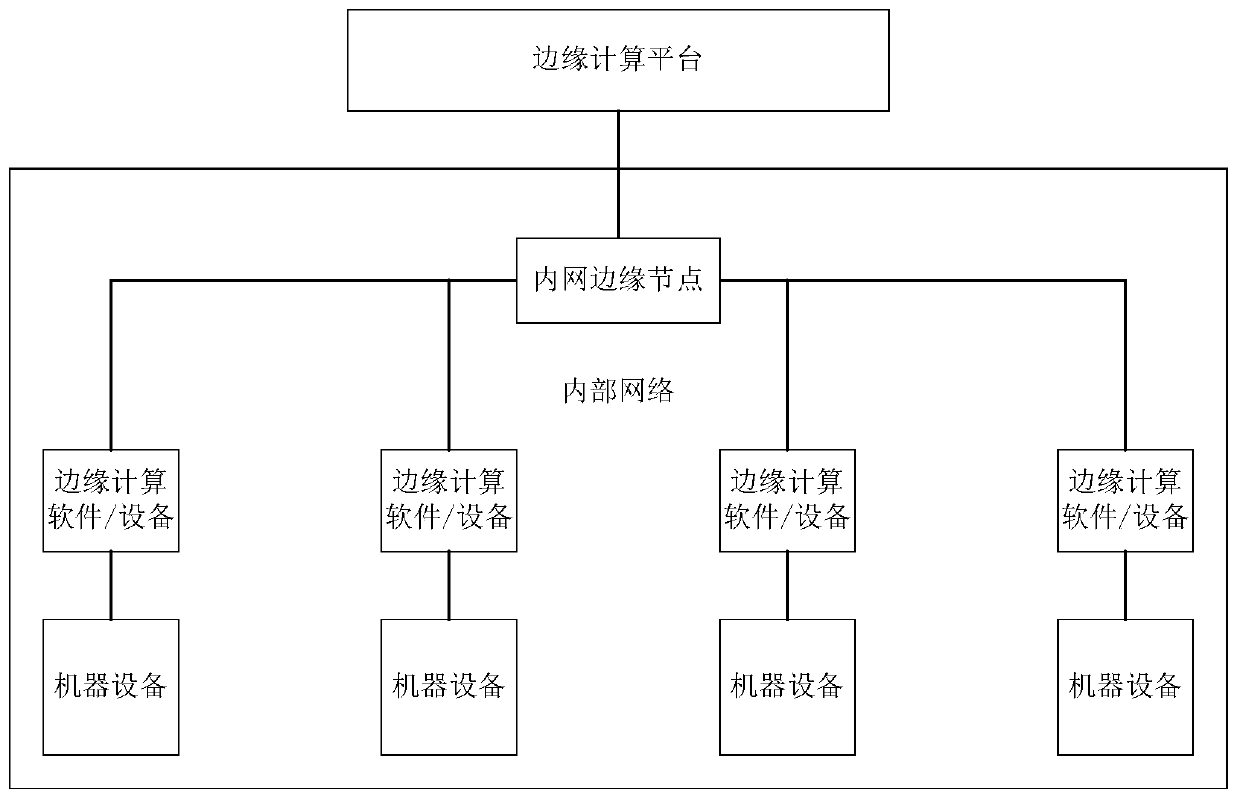
An intelligent management method and system based on edge computing
PendingCN109815733AImprove securityReduce latencyMathematical modelsDigital data protectionEdge computingMobile edge computing
The invention discloses an intelligent management method and system based on edge computing, and belongs to the technical field of edge computing. According to the invention,the data analysis and processing time can be shortened and the time delay is reduced; and when the network is interrupted and cloud crashes, it is guaranteed that edge computing can operate local computing software offline inan internal network; local autonomy is implemented, interconnection and intercommunication between the machine equipment can be realized through a local edge computing group which runs offline, so that a complete intelligent management network and system can be established; meanwhile, bandwidth resources for data transmission can be saved during networking, and the problems that data calculation and storage pressure is too high, flow is too high, application and development are difficult, and intelligence is insufficient during cloud on bottom-layer mechanical equipment are effectively relieved.
Owner:CHINANETCENT TECH
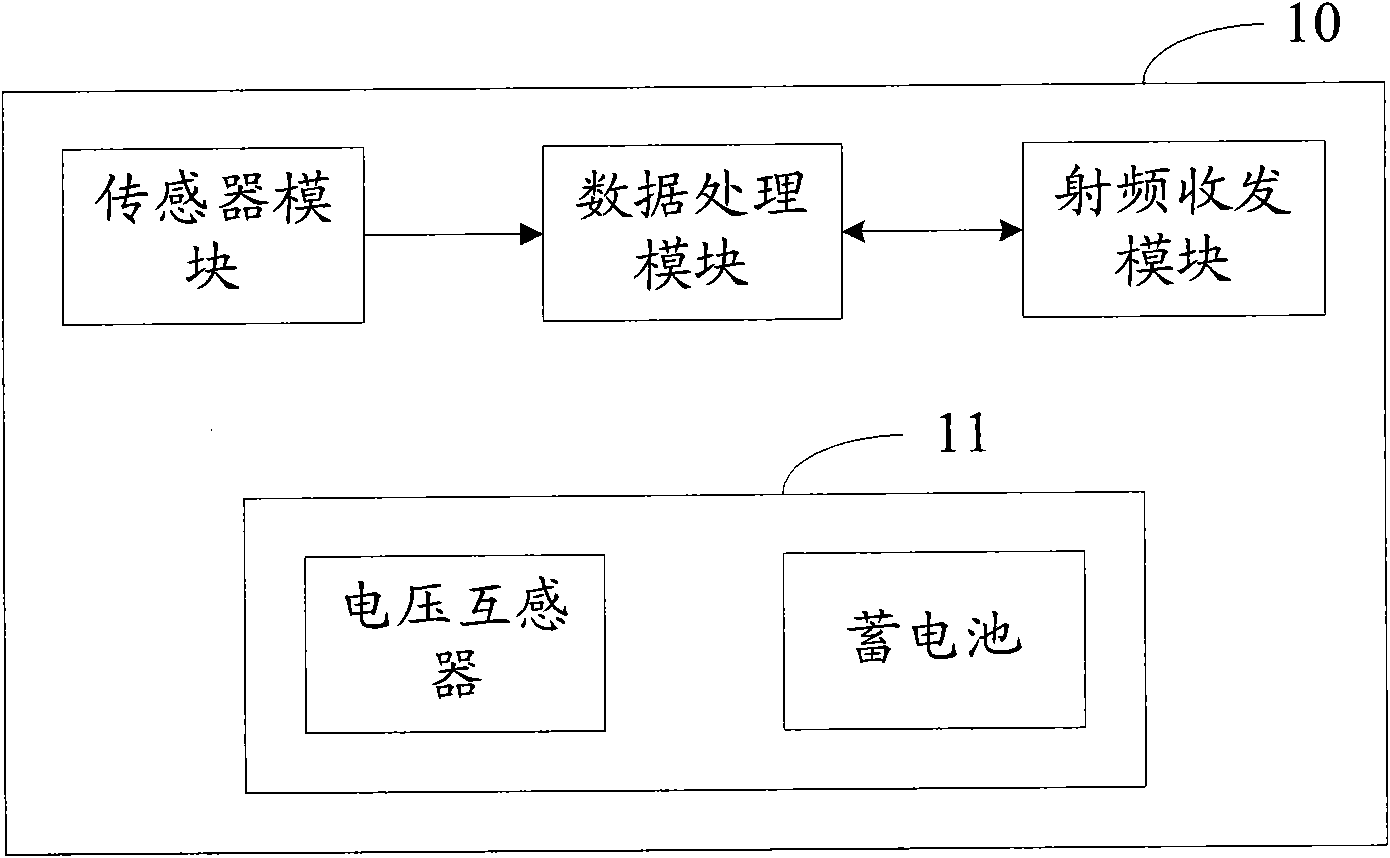
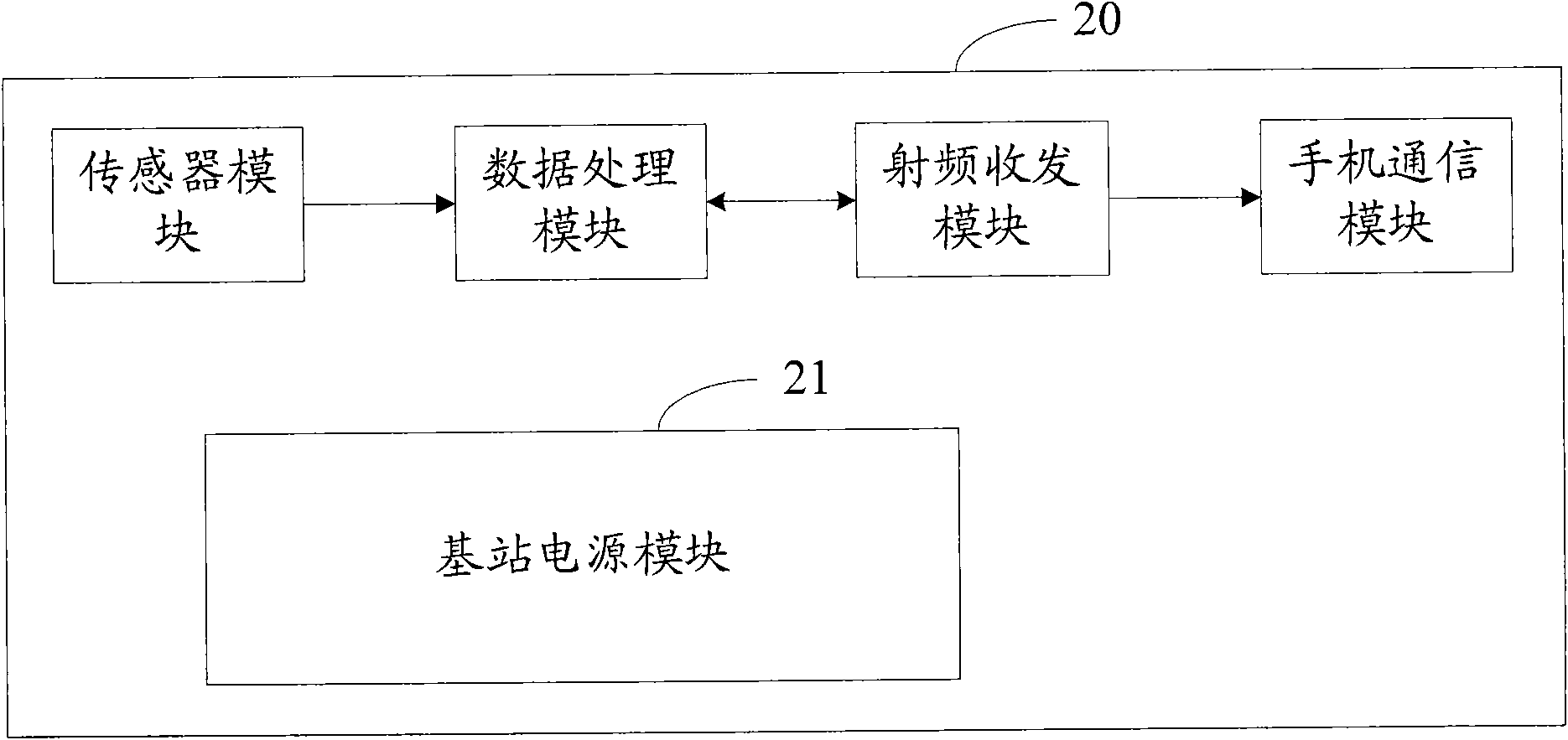
Monitoring device of overhead transmission lines and monitoring method
ActiveCN102118881AReduce data volumeSave bandwidth resourcesNetwork topologiesTension measurementMobile WebTransmission line
The invention relates to a monitoring device of overhead transmission lines, comprising nodes networked by a wireless sensor network multihop mode. The monitoring device is characterized in that the nodes comprise common nodes and base station nodes; the common nodes acquire and process parameter information of the transmission lines and transmit the processed parameter information to the base station nodes; the base station nodes receive and process the parameter information of the transmission lines and upload the processed parameter information of the transmission lines to the control center by a mobile network communication mode. In the monitoring device, related physical parameter values such as temperature, voltage, current and tension and the like of the overhead transmission lines can be monitored in real time, and are transmitted to the base station nodes by the wireless sensor network multihop manner, data is forwarded to the control center by a TD-SCDMA / GPRS / EDGE module on the base station nodes, and the bandwidth resource and the system cost are saved.
Owner:SHENZHEN INST OF ADVANCED TECH
Method and device for loading webpage in browser
ActiveCN104063460AImprove loading speedReduce the number of requestsSpecial data processing applicationsData informationNetwork switch
The embodiment of the invention provides a method and a device for loading a webpage in a browser. The method comprises the following steps of parsing a webpage requested to be downloaded by the browser to obtain the DOM (document object model) tree structure data information of the webpage; acquiring a text of a webpage element of a specified type from the DOM tree structure data information, wherein the text of the webpage element comprises a source address; requesting the downloading of contents of the webpage element of the specified type to a specified-type webpage element storage server corresponding to the browser according to the source address of the webpage element of the specified type; when the webpage is rendered and loaded, performing rendering by using the webpage element of the specified type downloaded from the specified-type webpage element storage server, and loading the webpage element of the specified type in the webpage. According to the embodiment of the invention, paths for requesting for downloading to a webpage server are reduced, the network switching capacity is reduced, bandwidth resources are effectively saved, the downloading time of the webpage element is reduced, and the loading speed of the webpage is further increased.
Owner:北京鸿享技术服务有限公司
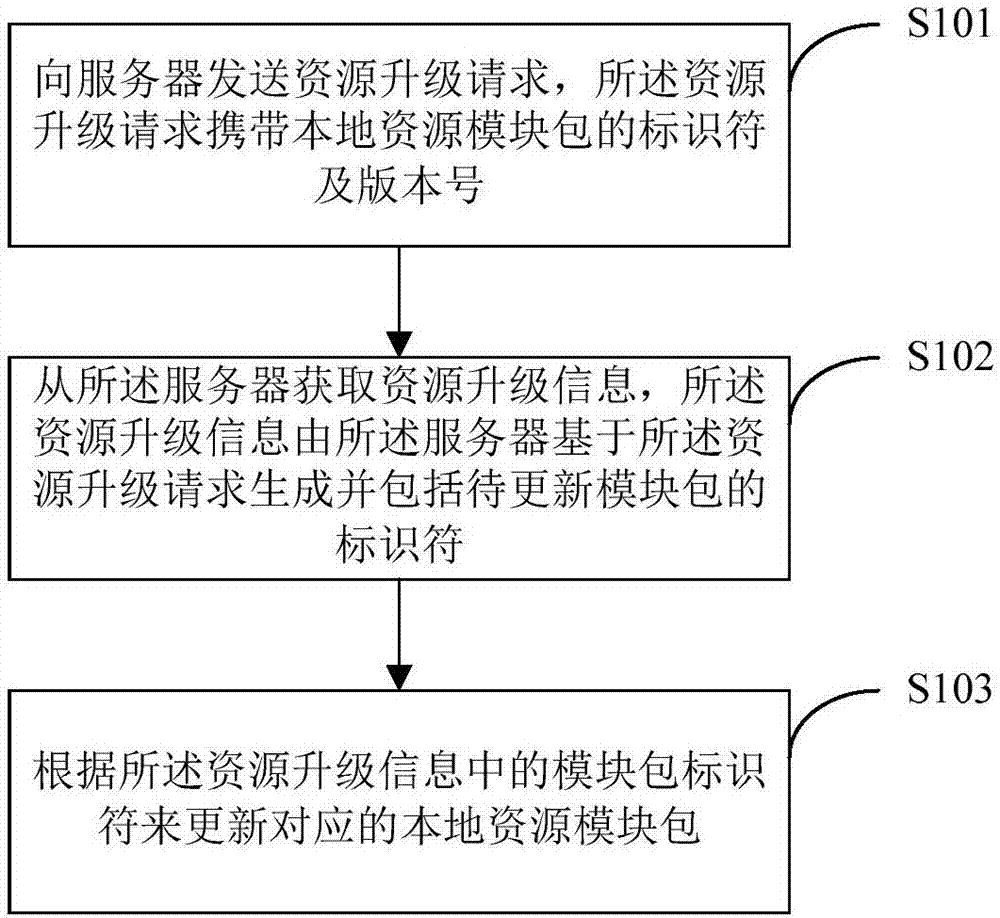
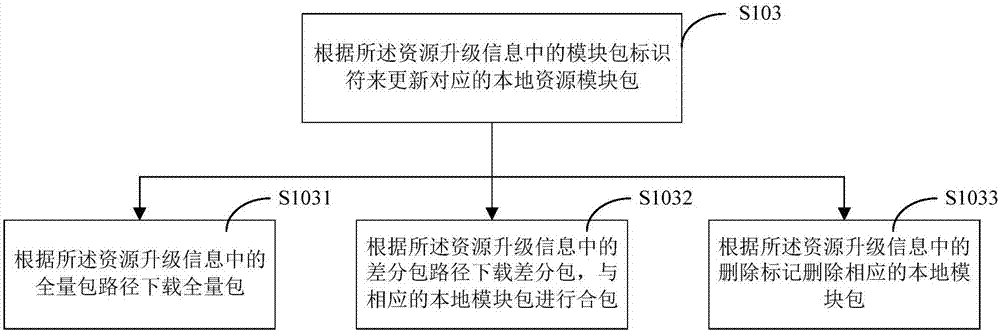
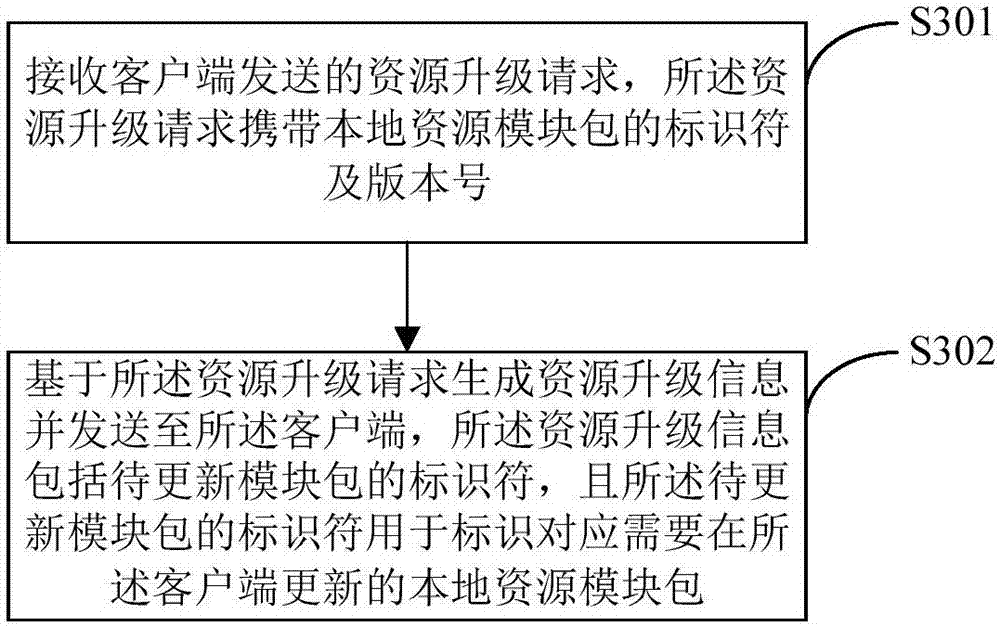
Resource upgrading method and device, computer readable memory medium and electronic equipment
InactiveCN107203395AReduce data volumeReduce complexityProgram loading/initiatingSoftware deploymentComputer moduleDistributed computing
The invention discloses a resource upgrading method and a resource upgrading device, a computer readable memory medium and electronic equipment. The method includes steps of sending a resource upgrading request to a server, wherein the resource upgrading request carries with a sign symbol and a version number of a local resource module packet; acquiring resource upgrading information from the server, wherein the resource upgrading information is generated by the server on the basis of the resource upgrading request and comprises a sign symbol of a to-be-updated module packet; updating the corresponding local resource module packet according to a module packet sign symbol in the resource upgrading information. According to the invention, the bandwidth resource and downloading time for the client upgrading can be saved.
Owner:BEIJING JINGDONG SHANGKE INFORMATION TECH CO LTD +1
Multi-keyword searchable encryption method supporting numerical attribute comparison
ActiveCN108156140AFlexible AuthorizationRapid positioningKey distribution for secure communicationEncryption apparatus with shift registers/memoriesCiphertextDocumentation
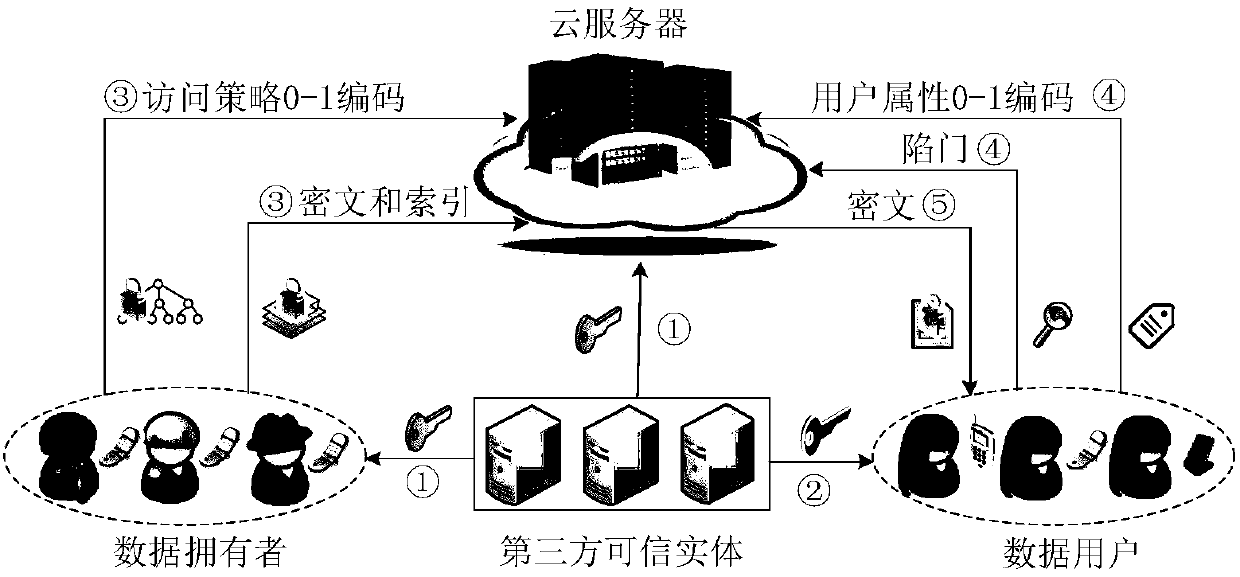
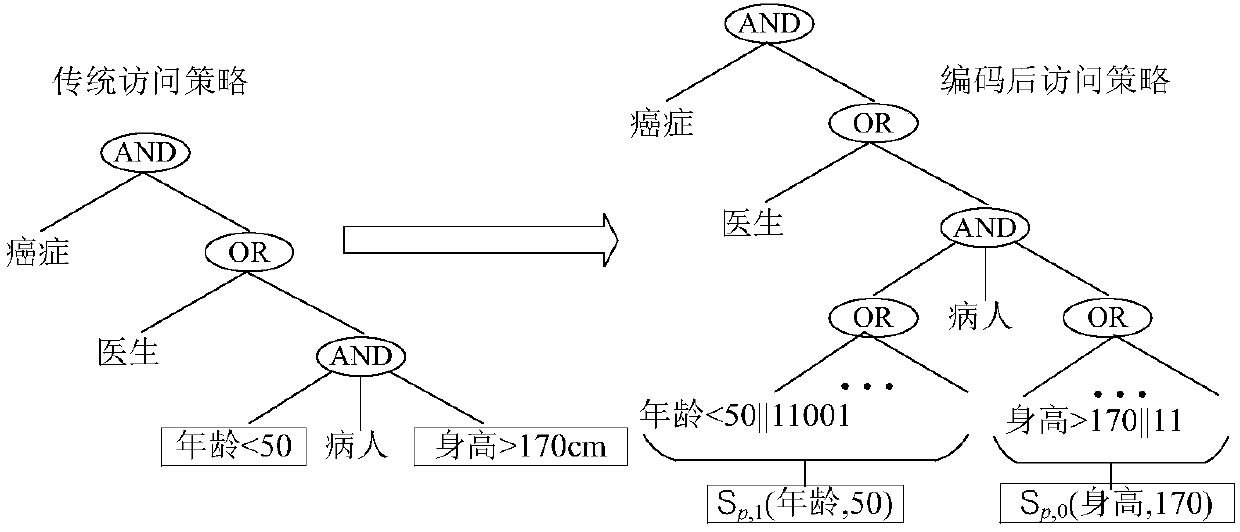
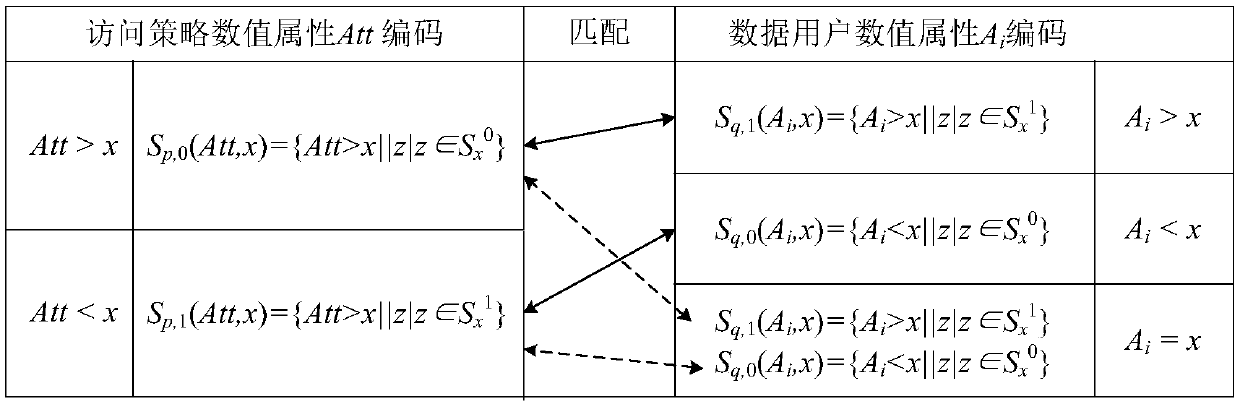
The invention discloses a multi-keyword searchable encryption method supporting numerical attribute comparison, the method is used for realizing multi-keyword searchable encryption of numerical attribute comparison under a cloud storage background, establishing an effective ciphertext index through a searchable encryption technology and realizing multi-keyword ciphertext retrieval; the method notonly can quickly locate a ciphertext document which a user is interested in, but also saves bandwidth resource and improves user experience; through an attribute encryption technology of a ciphertextstrategy, the method realizes fine-grained access control, the user can perform ciphertext retrieval only for legitimate data, and 0 coding and 1 coding are executed for a numerical attribute of an access control strategy; and the method can support numerical attribute comparison and has more wide application scenarios.
Owner:XIDIAN UNIV
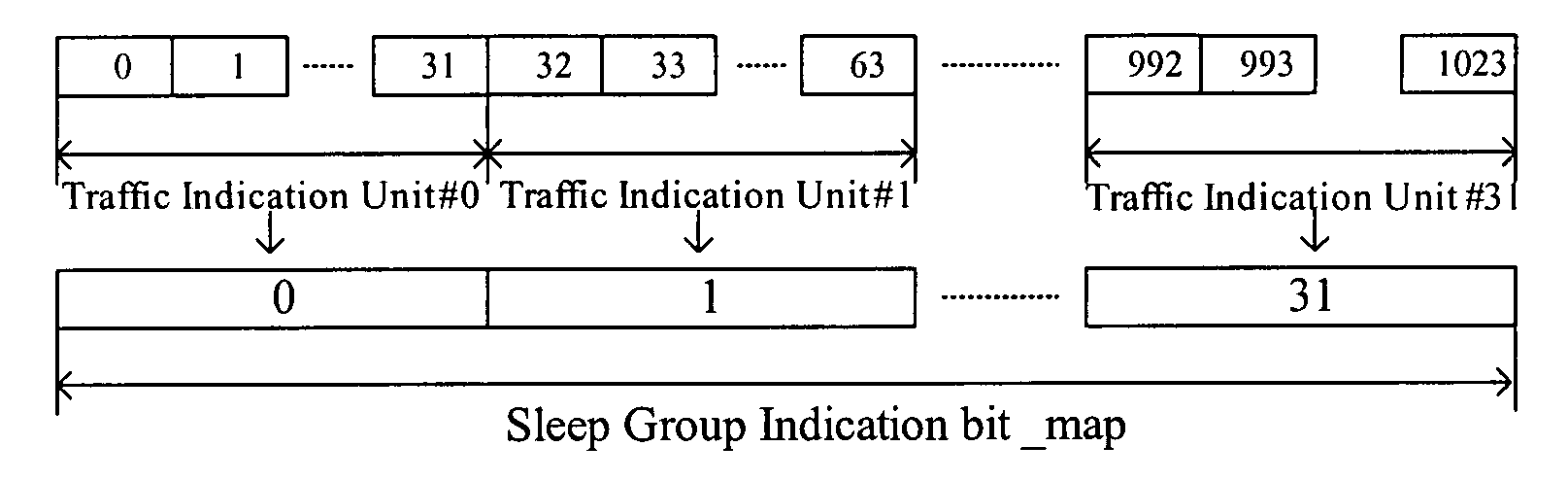
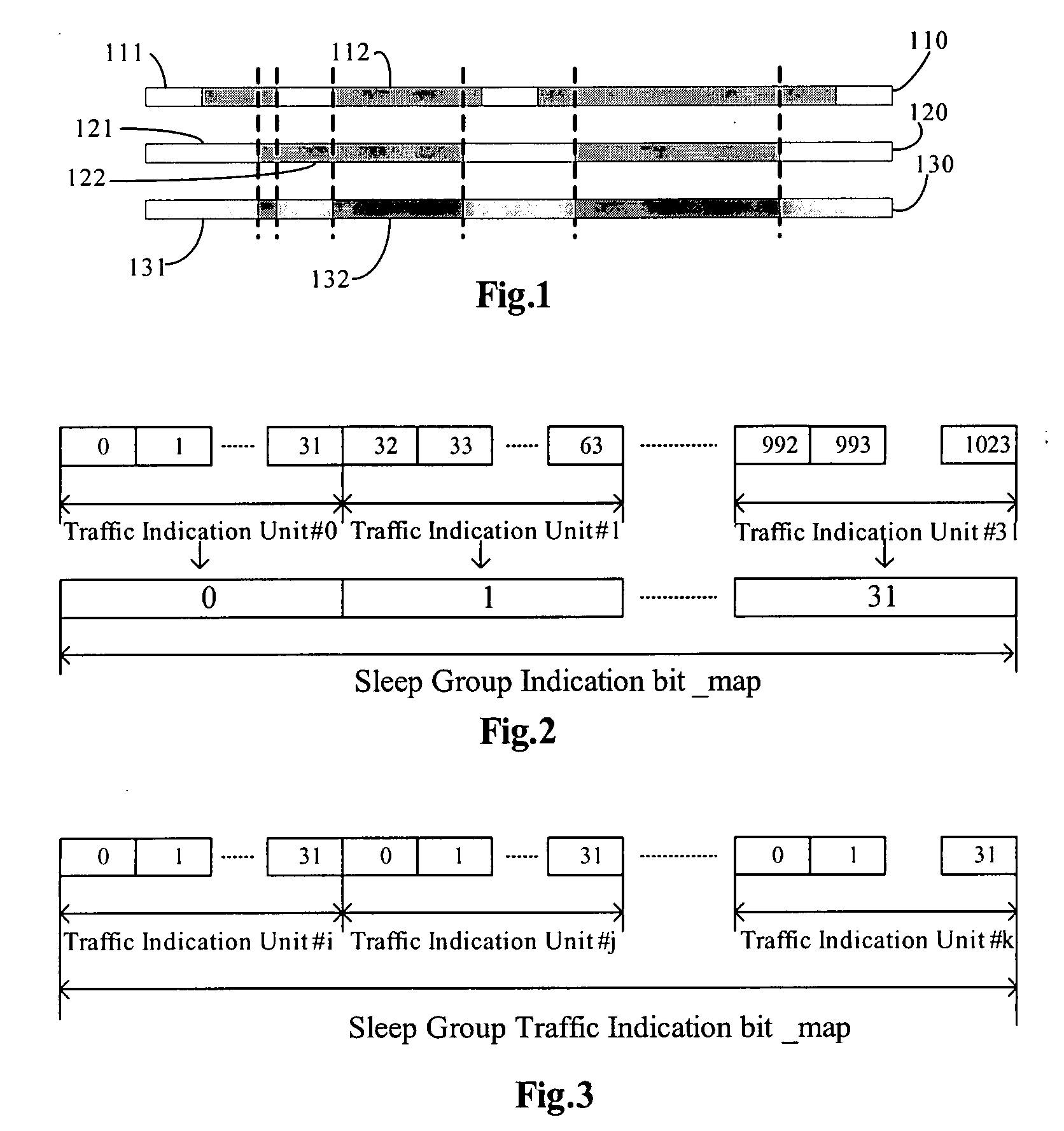
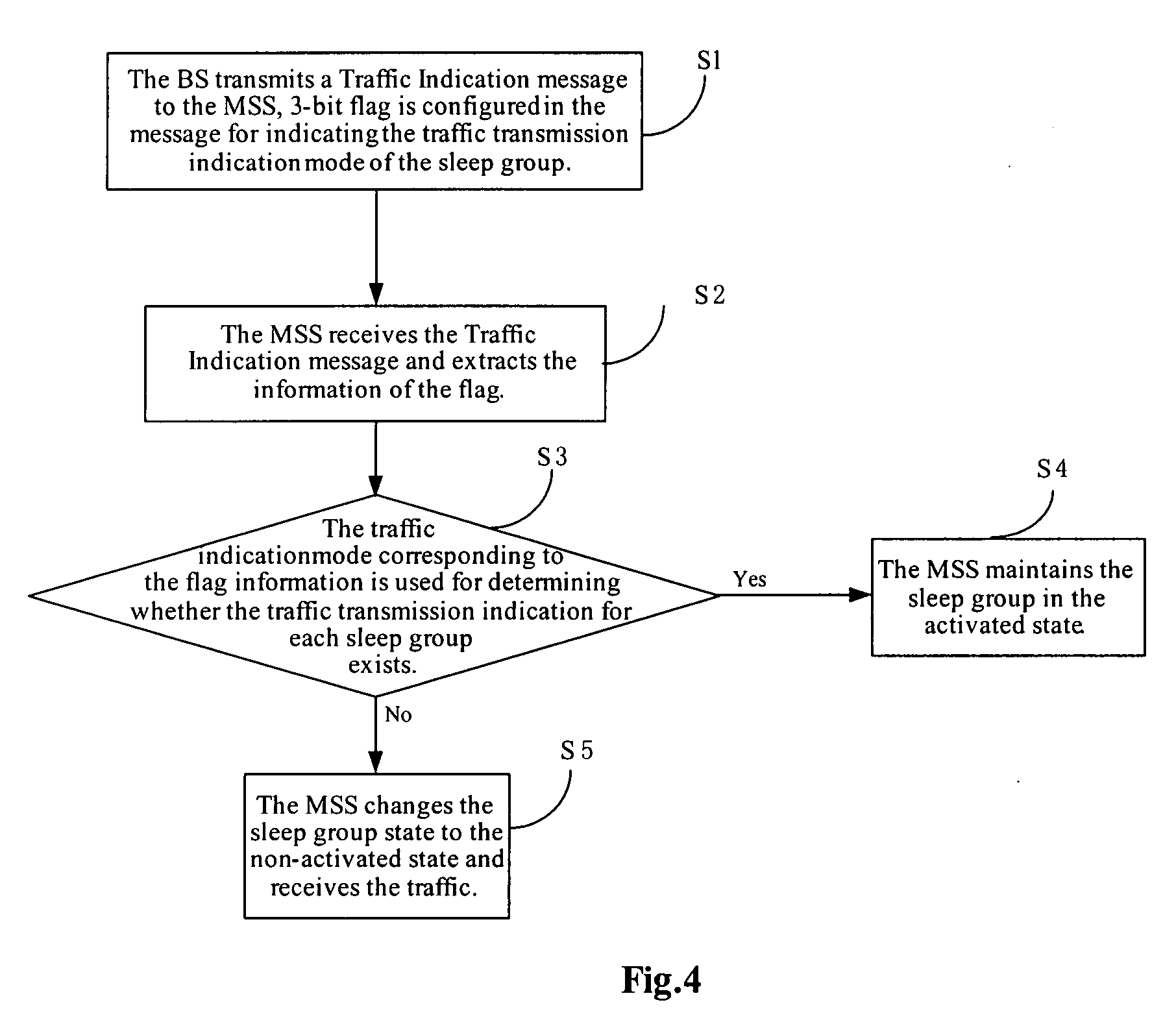
Method and apparatus for transmitting traffic indication message in sleep mode
InactiveUS20080031173A1Reduce overheadSave resourcePower managementTransmission systemsAir interfaceReal-time computing
A method and apparatus for transmitting a Traffic Indication message from a BS to a MSS in Sleep Mode is provided in embodiments of the present invention. The method includes: transmitting, by the BS, a Traffic Indication message to the MSS, and setting a flag in the Traffic Indication message for indicating the indication mode of the traffic transmission of a sleep group; receiving, by the Mobile Subscriber Station, the Traffic Indication message, and determining whether each sleep group has a traffic transmission indication according to the flag, if so, the Mobile Subscriber Station changes the corresponding state of the sleep group to non-activated and receives the traffic; otherwise, the Mobile Subscriber Station maintains the sleep group in the activated state. According to an embodiment of the present invention, any indication mode of the traffic transmission can be carried flexibly, thus the problem that only one indication mode of the traffic transmission can be selected is avoided, hence overhead of the Traffic Indication message is reduced and air interface resource is saved.
Owner:HUAWEI TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com