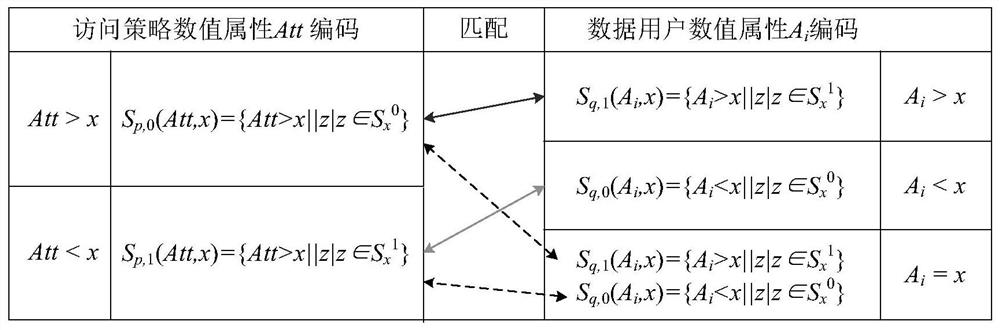
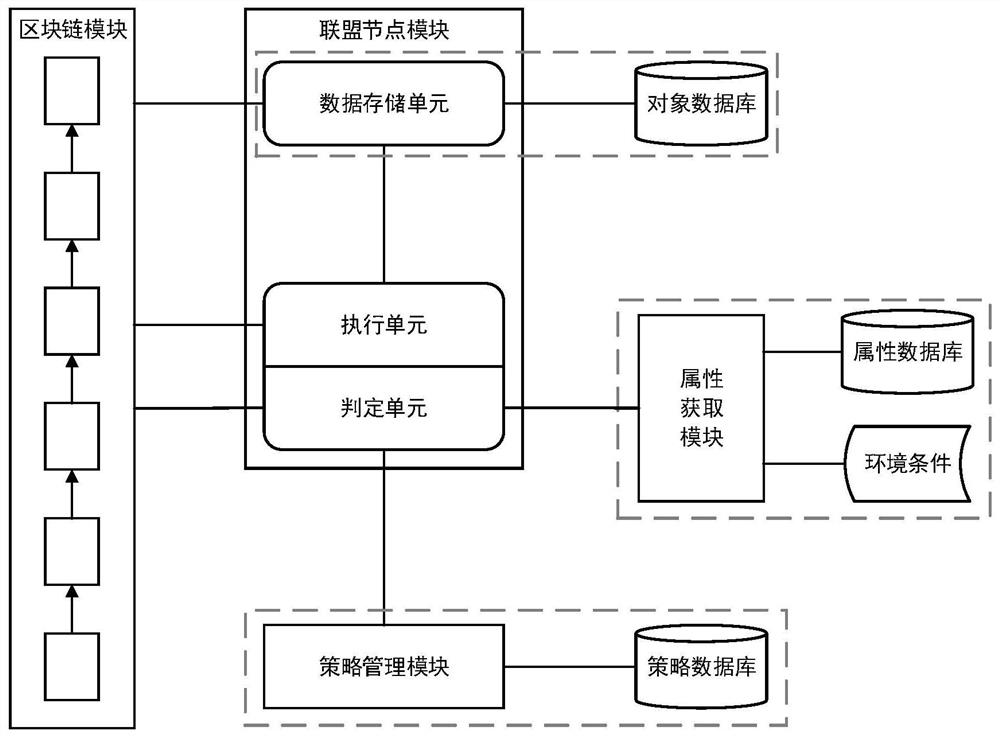
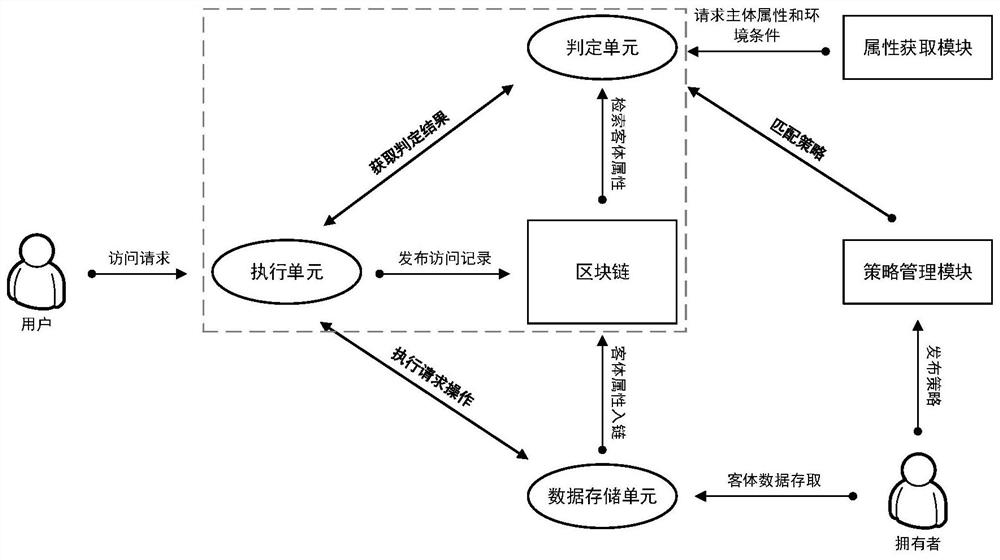
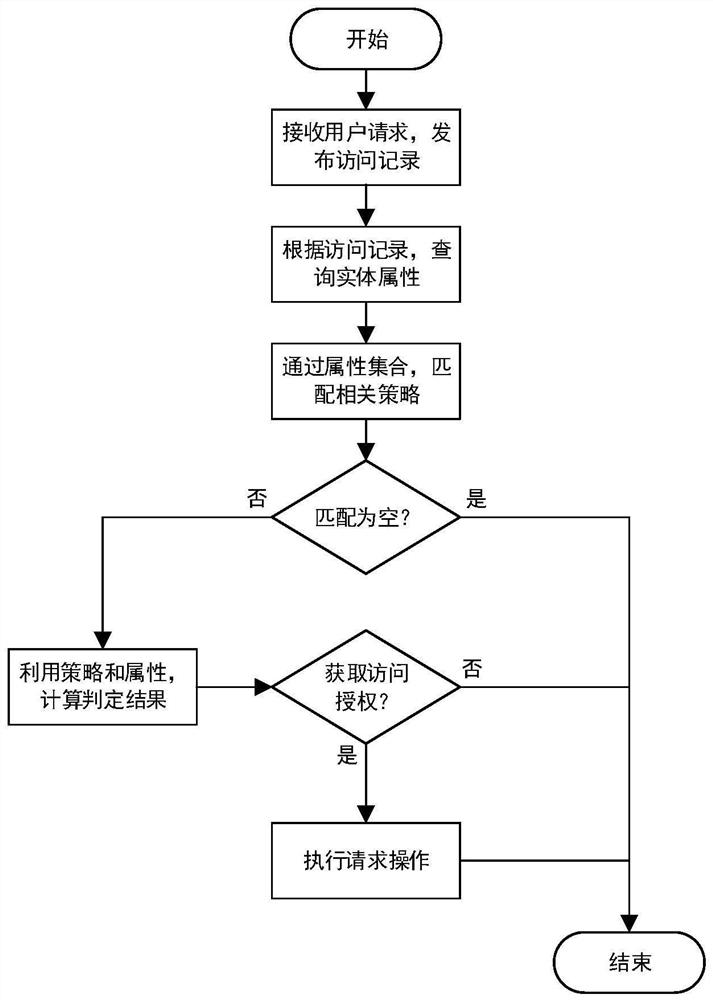
Patents
Literature
32results about How to "Flexible Authorization" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
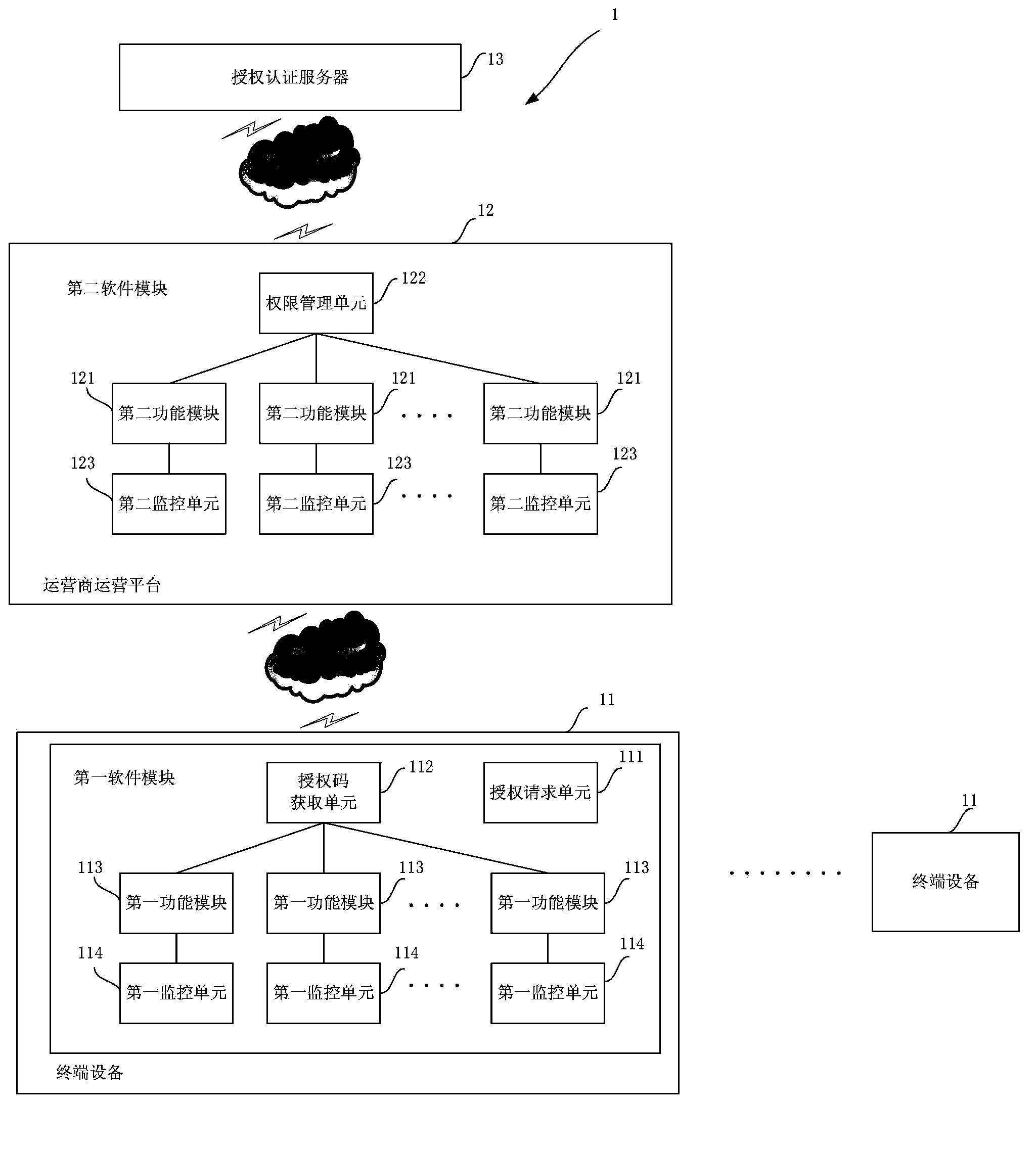
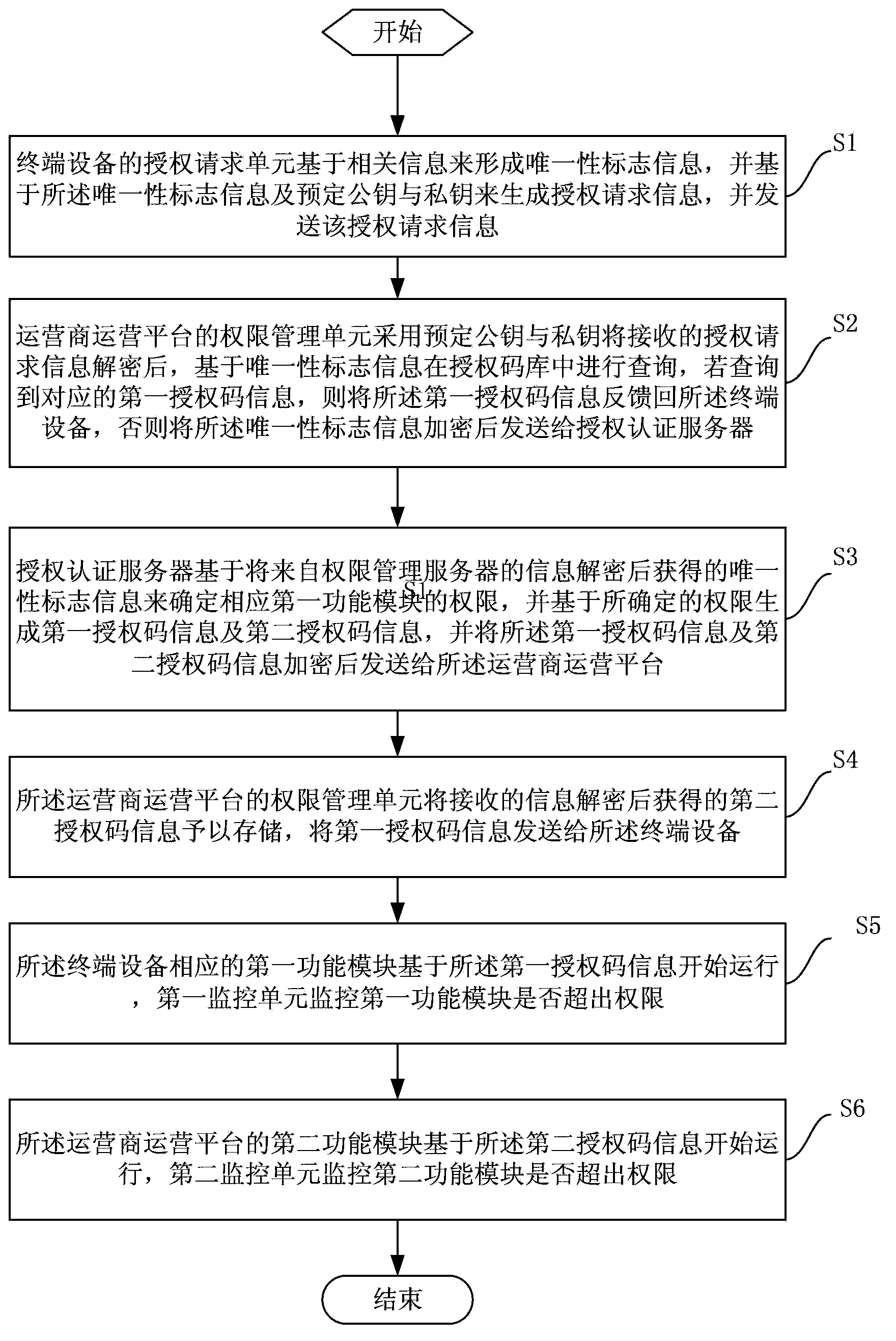
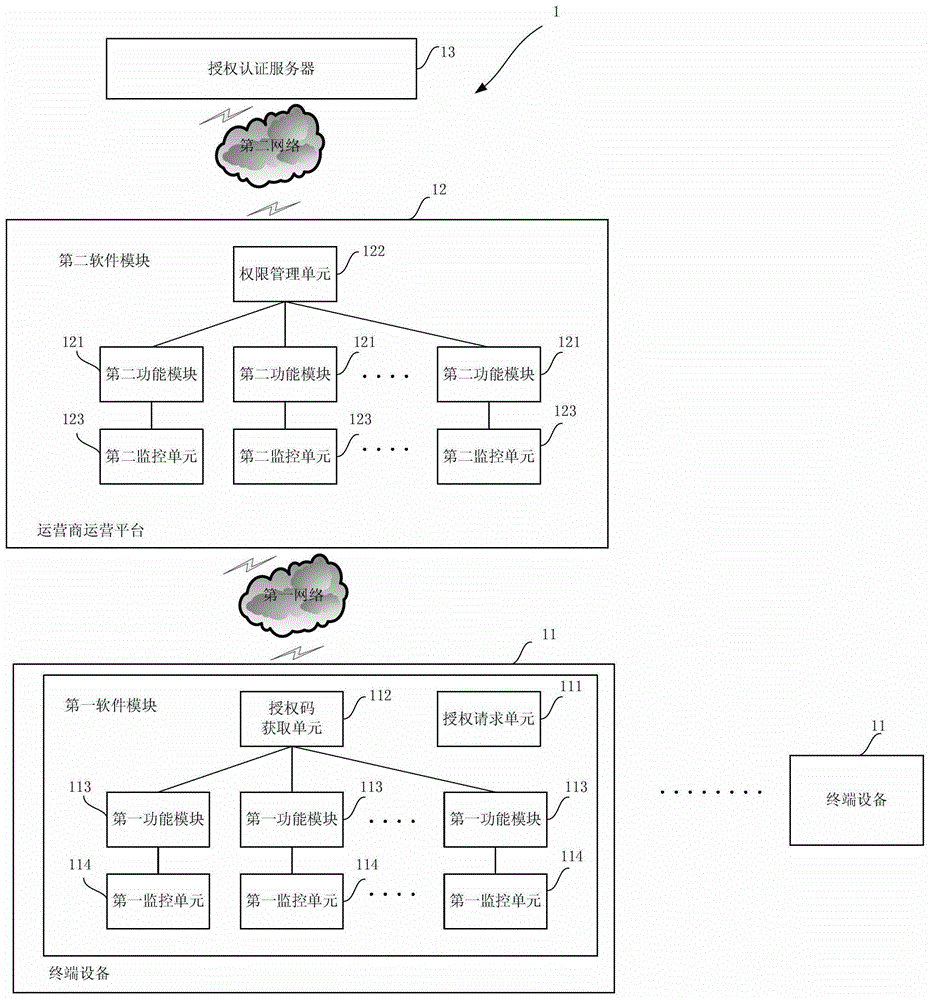
Method and system for authorization of software function modules of internet of things
ActiveCN103906054AFlexible authorizationAuthorization method securitySecurity arrangementRelevant informationThe Internet
The invention provides a method and system for authorization of software function modules of the internet of things. The system for authorization at least comprises at least one terminal device, an operator operation platform communicated with the terminal device through a first network and an authorization authentication server communicated with the operator operation platform through a second network. The terminal device is used for starting an authorization procedure and can form a uniqueness mark through acquisition of relevant information and authorize the corresponding function module according to returned first authorization code information. The operator operation platform is used for processing authorization requests and the like of the terminal device. The authorization authentication server is used for managing secret keys of the terminal device and the operator operation platform and automatically generating the first authorization code information, second authorization code information and the like according to the uniqueness mark. According to the method and system, independent authorization can be conducted according to functions and function points of software, the version safety of the software is guaranteed, authorization is achieved according to the requirements, version management conducted by an operator is facilitated, and the operator can know the application condition of the software so as to further improve the software.
Owner:上海农业信息有限公司 +2
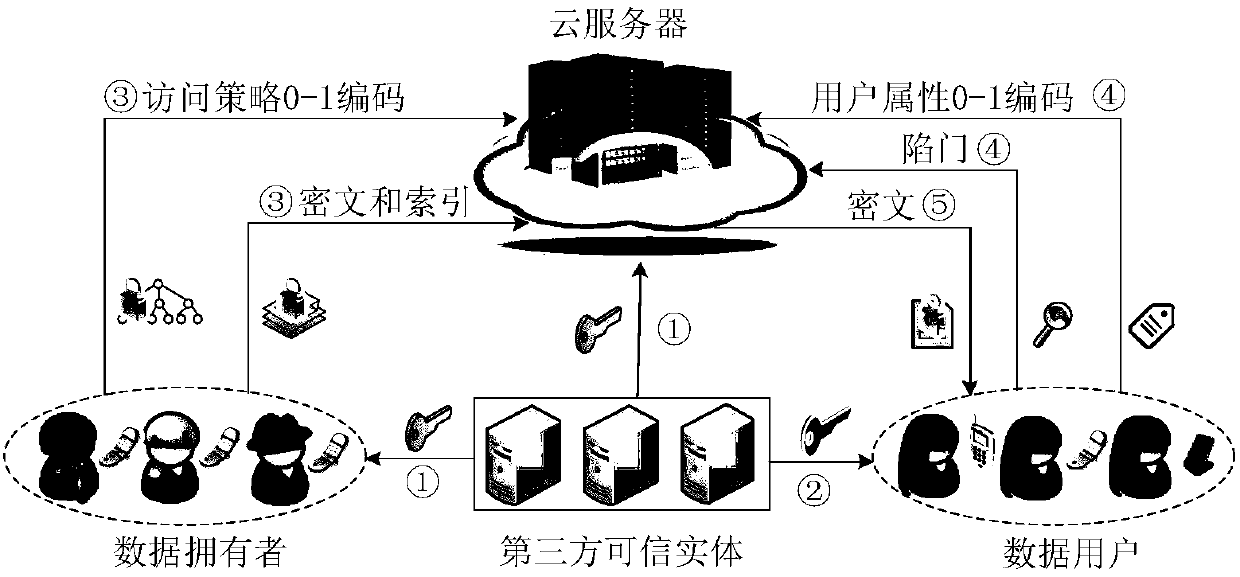
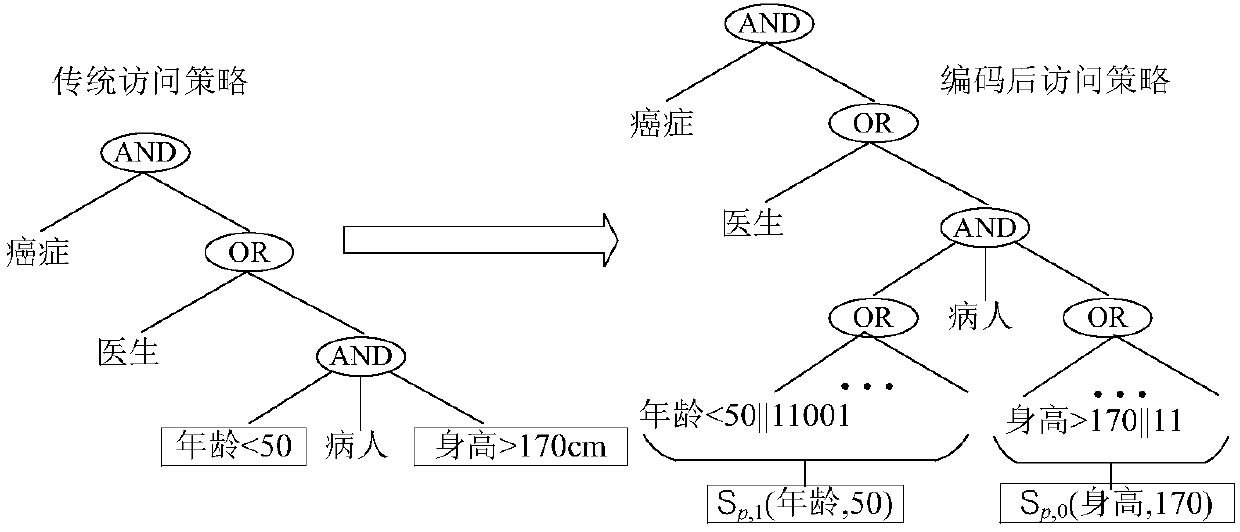
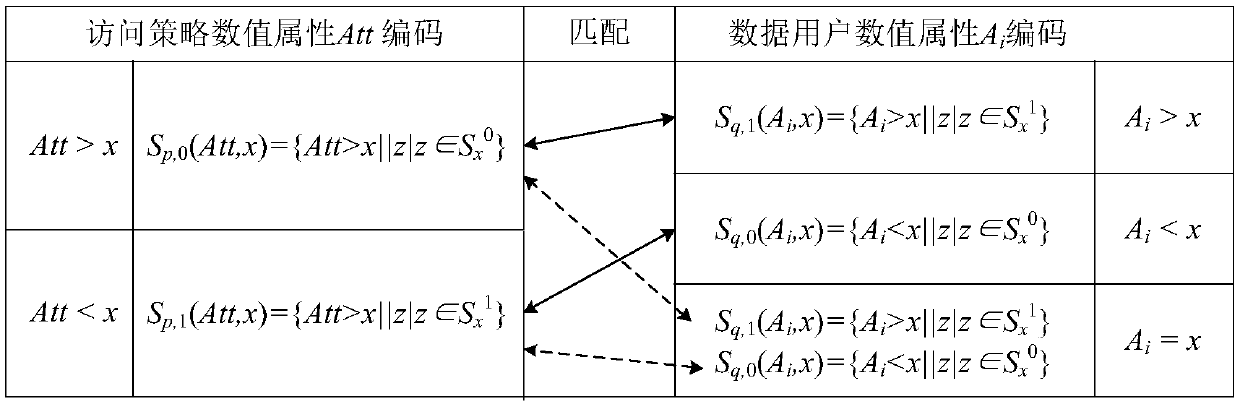
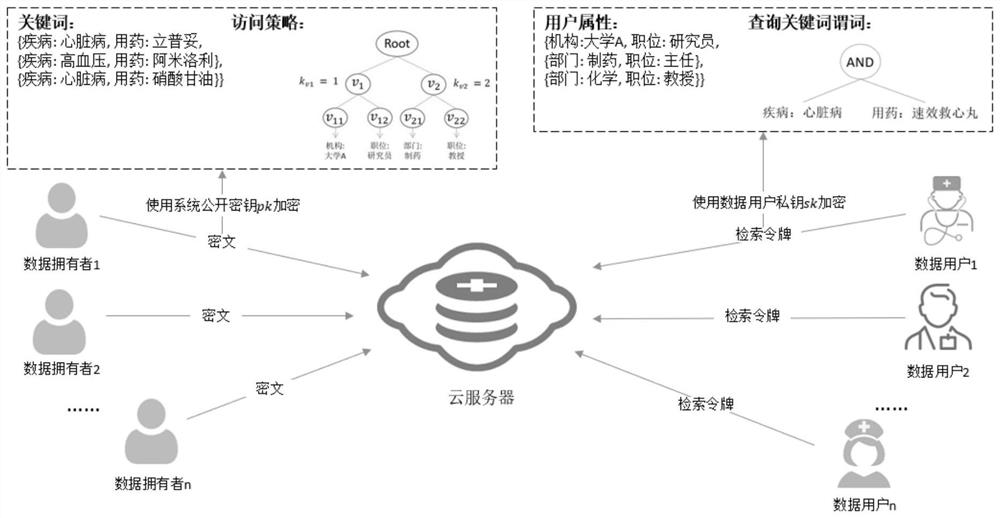
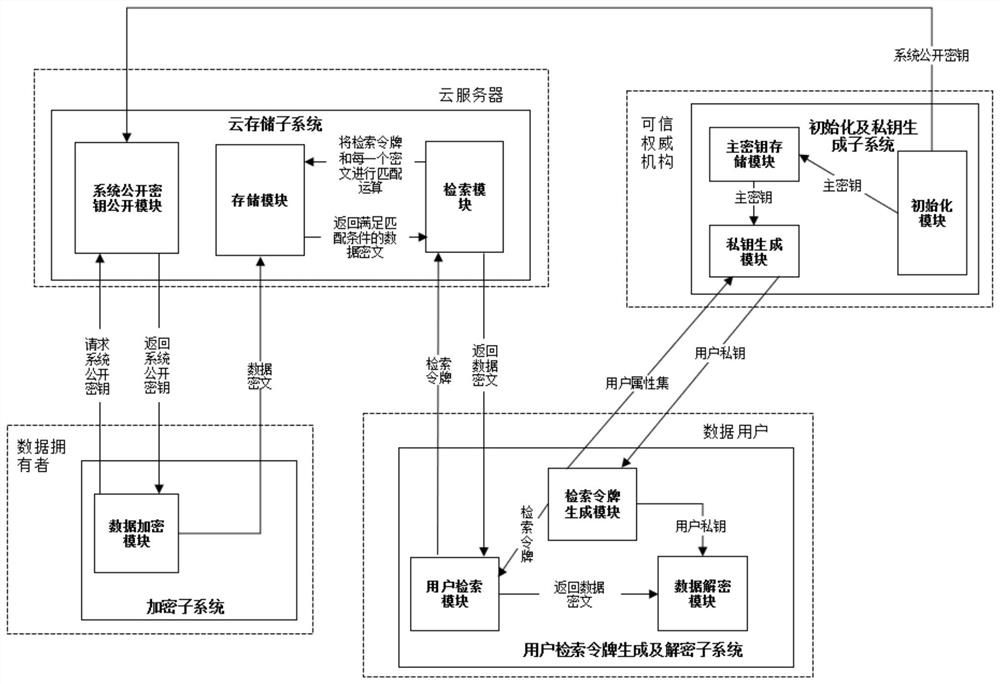
Multi-keyword searchable encryption method supporting numerical attribute comparison
ActiveCN108156140AFlexible AuthorizationRapid positioningKey distribution for secure communicationEncryption apparatus with shift registers/memoriesCiphertextDocumentation
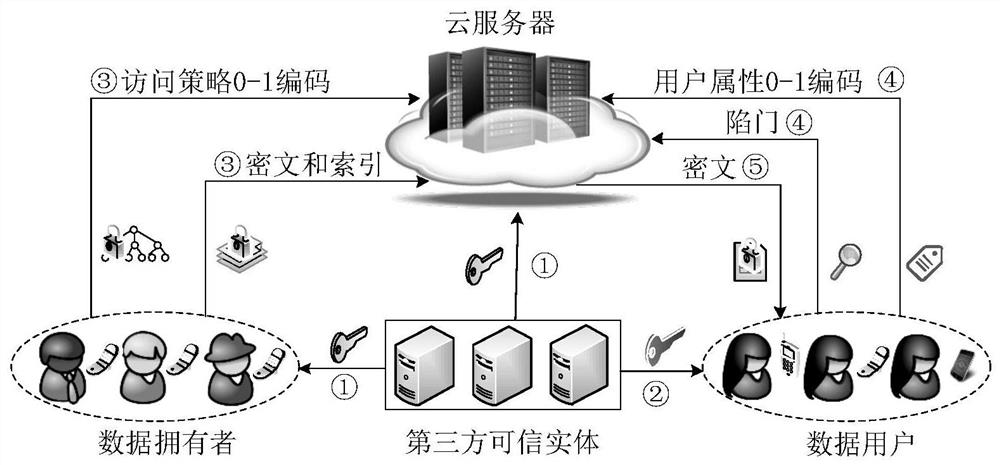
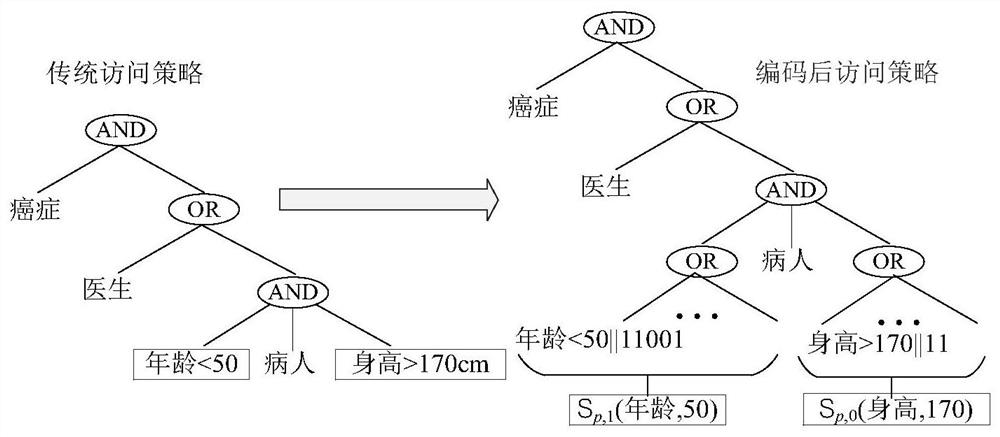
The invention discloses a multi-keyword searchable encryption method supporting numerical attribute comparison, the method is used for realizing multi-keyword searchable encryption of numerical attribute comparison under a cloud storage background, establishing an effective ciphertext index through a searchable encryption technology and realizing multi-keyword ciphertext retrieval; the method notonly can quickly locate a ciphertext document which a user is interested in, but also saves bandwidth resource and improves user experience; through an attribute encryption technology of a ciphertextstrategy, the method realizes fine-grained access control, the user can perform ciphertext retrieval only for legitimate data, and 0 coding and 1 coding are executed for a numerical attribute of an access control strategy; and the method can support numerical attribute comparison and has more wide application scenarios.
Owner:XIDIAN UNIV
Searchable encryption method based on wildcard character in cloud storage safety
ActiveCN107256248AFlexible AuthorizationFlexible revocationDigital data protectionSpecial data processing applicationsCiphertextCloud storage security
The invention relates to a searchable encryption method based on wildcard character in cloud storage safety. The method comprises the following steps that: setting a document to be uploaded; extracting a keyword set; encrypting the keyword set; selecting a random number as a document encryption key, and encrypting the document encryption key; encrypting the document to be uploaded to obtain a ciphertext, and sending the ciphertext to a cloud computing platform; input a query keyword set, generating a query trapdoor, carrying out signature, and sending the signature to the cloud computing platform; verifying a query signature by the cloud computing platform, and executing a search algorithm by the cloud computing platform; transmitting a keyword index and the query trapdoor into a keyword matching protocol to obtain an encryption matching result; carrying out decryption to obtain a search result; according to the search result, returning a corresponding ciphertext by the cloud computing platform; and recovering the document encryption key, and recovering the document. By use of the method, the keyword search of at most two wildcard characters can be supported, the wildcard character can appear on any position of the keyword, and a plurality of random characters can be represented.
Owner:FUZHOU UNIV
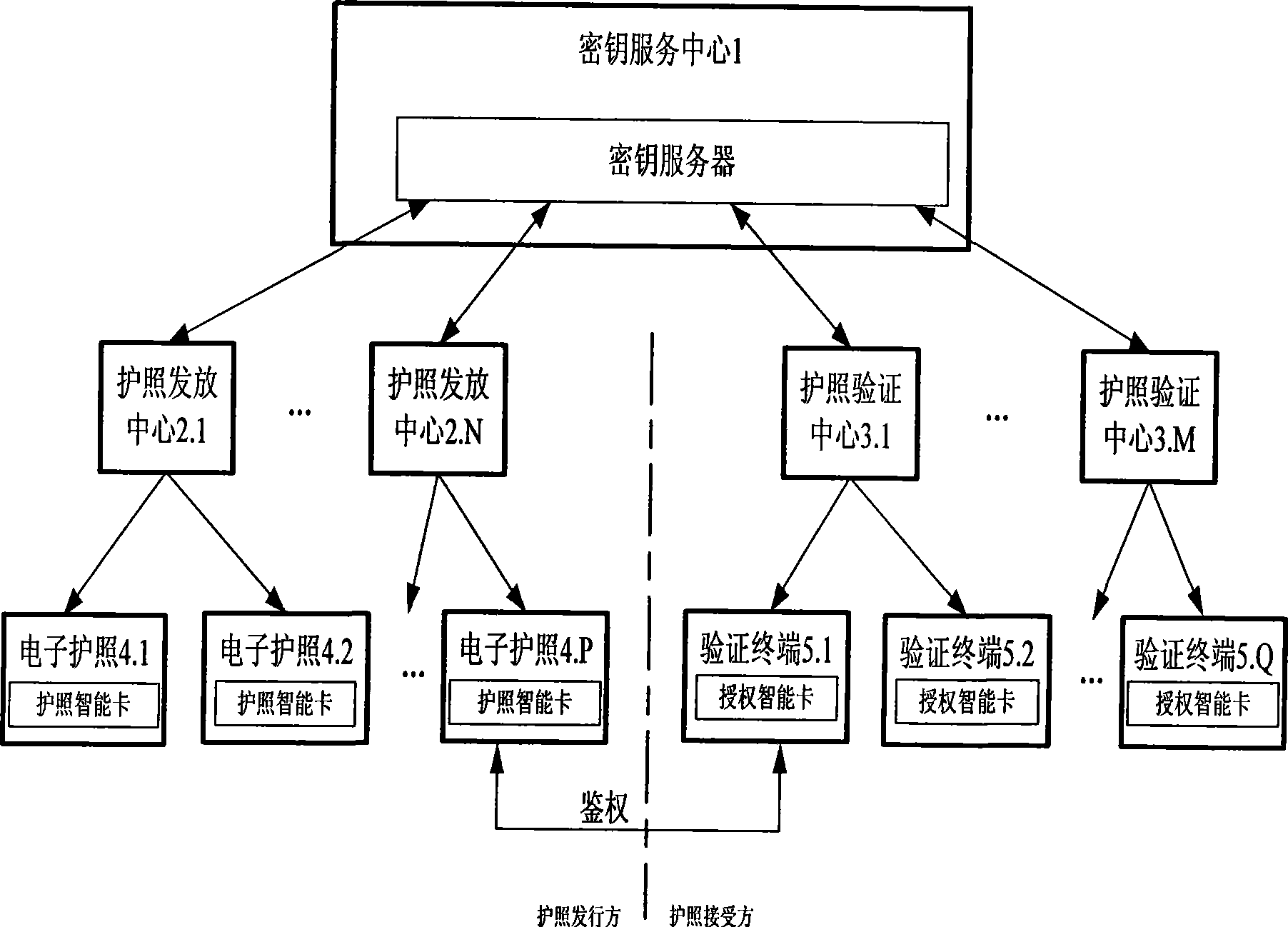
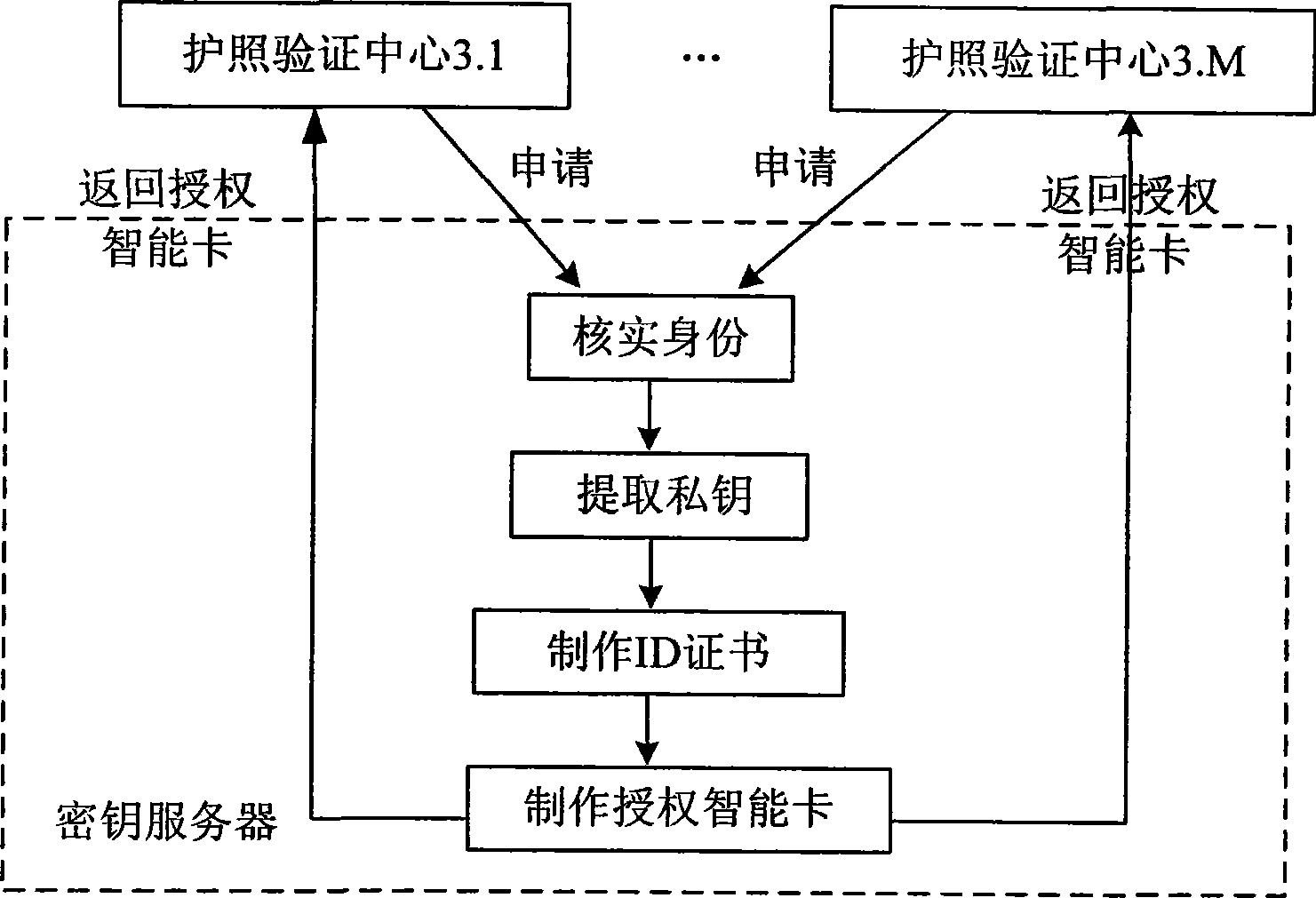
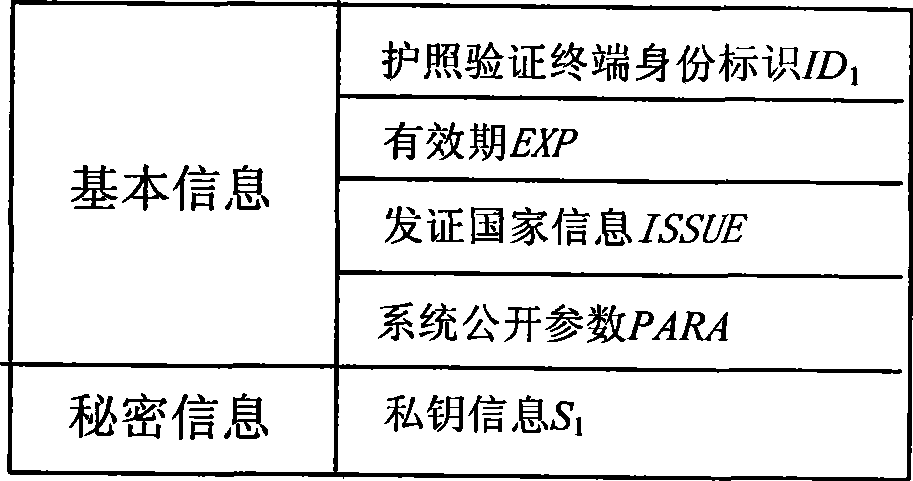
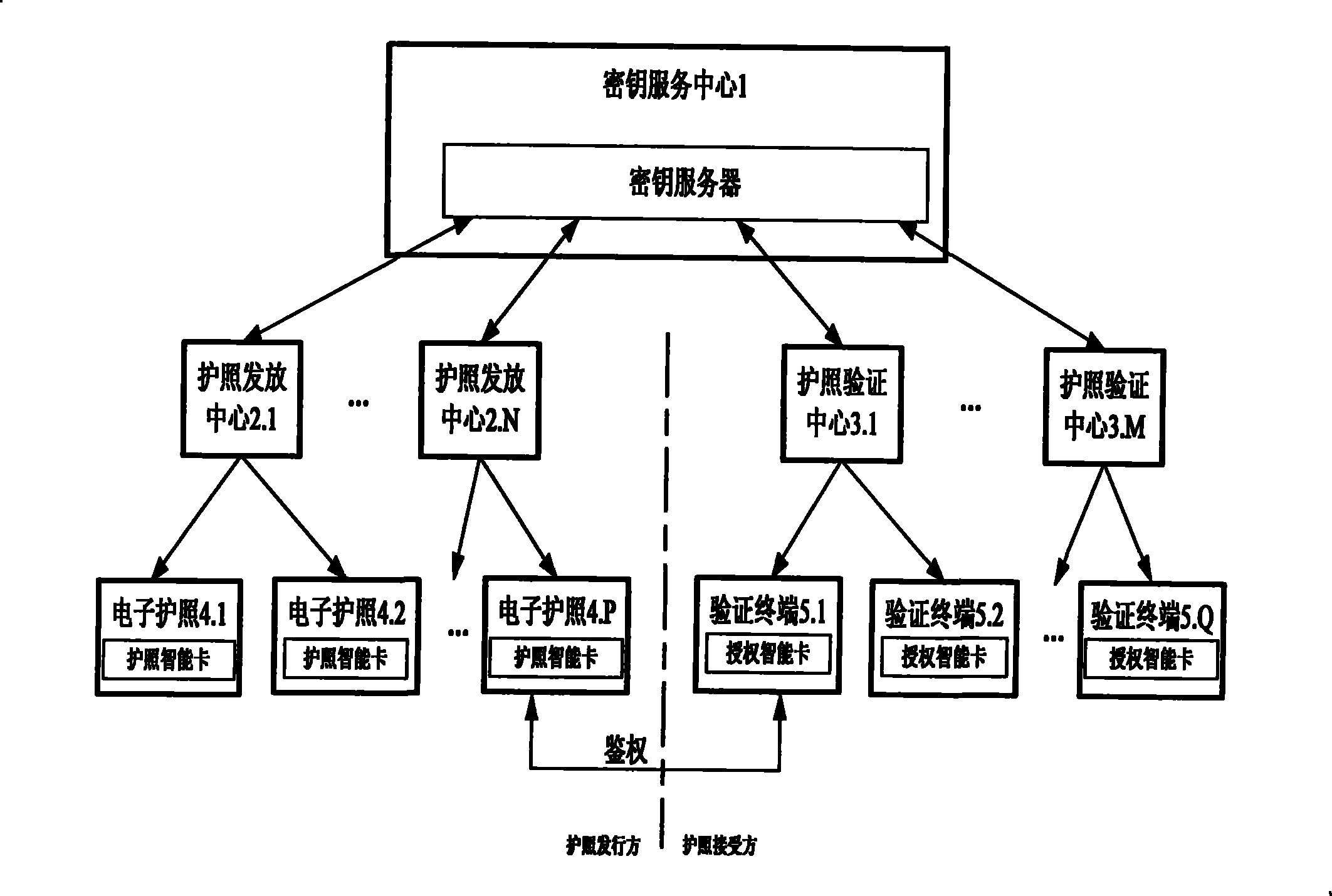
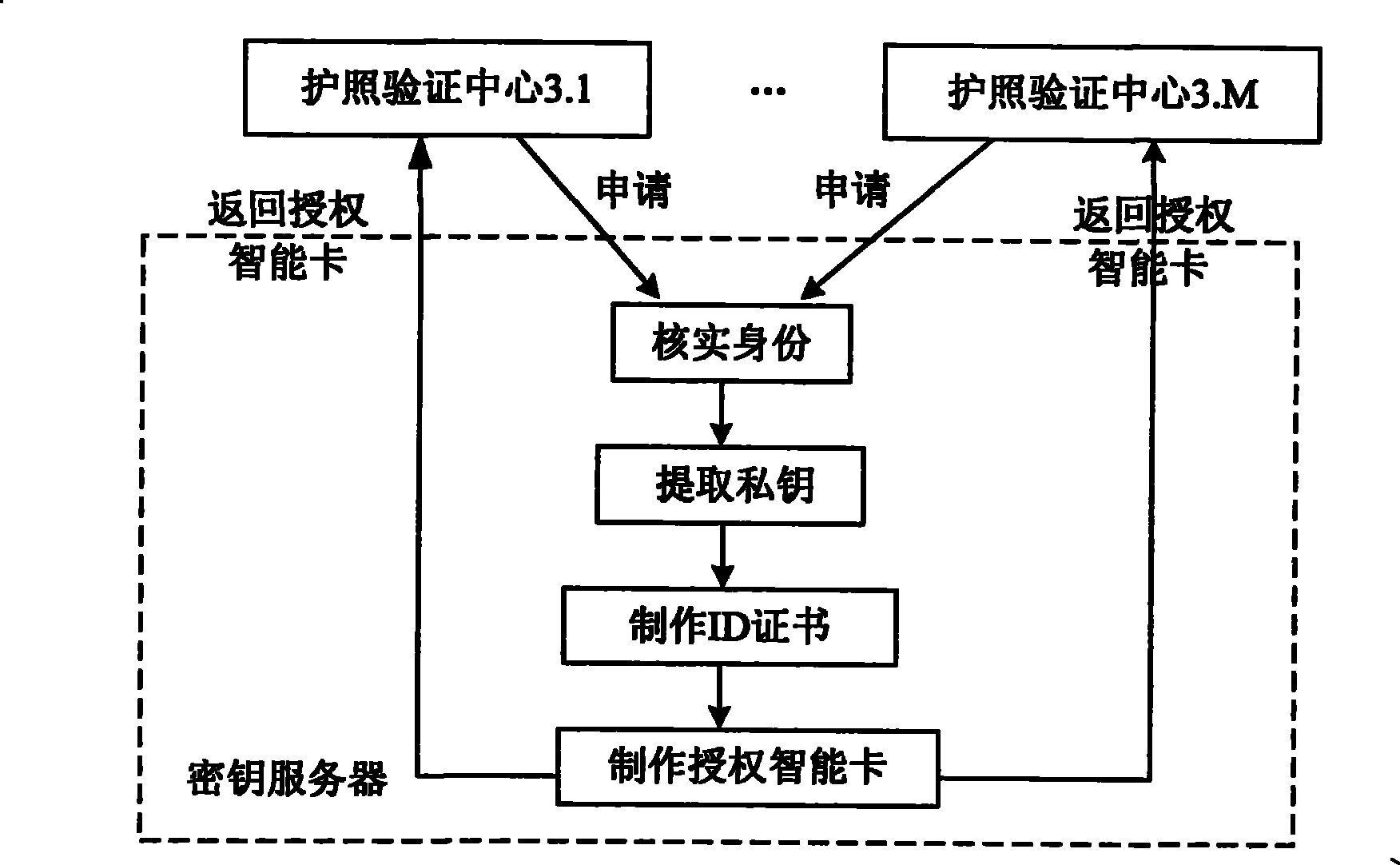
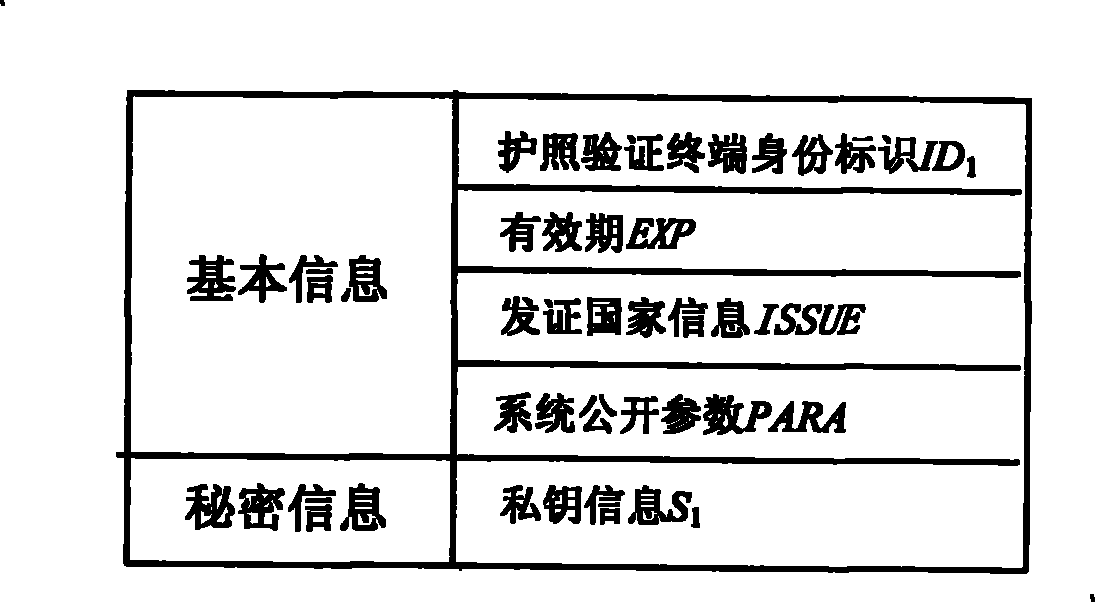
Electronic passport expansion access control system and authentication method based on identification cipher technology
ActiveCN101504732AFlexible AuthorizationOvercoming loopholes in authorization trust transferUser identity/authority verificationCo-operative working arrangementsAuthentication protocolExtended Access Control
The invention discloses an identification cryptographic technique-based electronic passport extended access control system and an identification cryptographic technique-based authentication method. The authentication method comprises the following steps that: a key service centre provides a key service; a passport verification center makes an application for sensitive biological characteristic information-reading authority, the key service center issues an authorization smart card to perform authorization, and the passport verification center distributes the authorization smart card to a verification terminal controlled thereby; and a passport issuing center applies the key service center for an authentication key and a public parameter for authentication and writes the authentication key and the public parameter into passport smart card of an electronic passport. During passport verification, the authorization smart card and the passport smart card implement an identification cryptographic algorithm-based authentication protocol to judge if the verification terminal has the authority to read sensitive biological characteristic data. The system and the method avoid loopholes in authentication trust transmission in a European proposal, save the establishment of a complicate PKI system, and allow for low system construction cost. Compared with Singaporean EAC, the method provides flexible authorization for a certifying organization, and can still authorize the certifying organization after the issue of a passport.
Owner:WUHAN TIANYU INFORMATION IND
Data authorization method for block chain
InactiveCN109977697AFlexible controlImplement authorization managementDigital data protectionConfidentialityCombined use
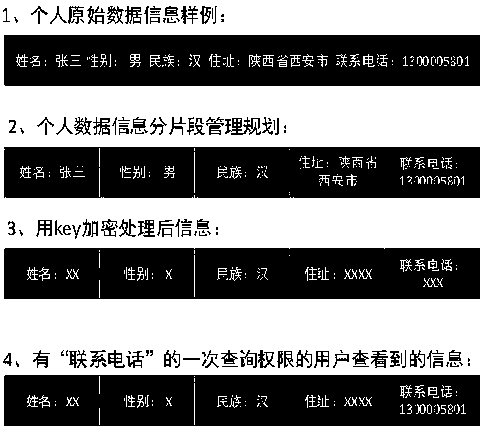
A data authorization method of a block chain comprises the steps of 1, enabling a user to carry out segmented encryption according to the confidentiality degree of a field and a displayable object; 2,storing the encrypted information on a block chain by the user; 3, according to the authorization request of the user to the field, decrypting the related field; and 4 for the use of the authority, using the authority according to the principle of applying once and using once, or according to the principle that after applying once, the authority can be checked in an unlimited manner within a period of time, or combining the two authorizations to use. According to the technical scheme, by dividing the fields of the data, a whole piece of information is divided into a plurality of independent fields to be managed, controlled and authorized, the authorization time control is increased, a user can truly and flexibly control the data, so that the authorization management of the personal data on the block chain is achieved, and the refined management and control of the personal data are achieved.
Owner:陕西医链区块链集团有限公司
Authorization processing method and device
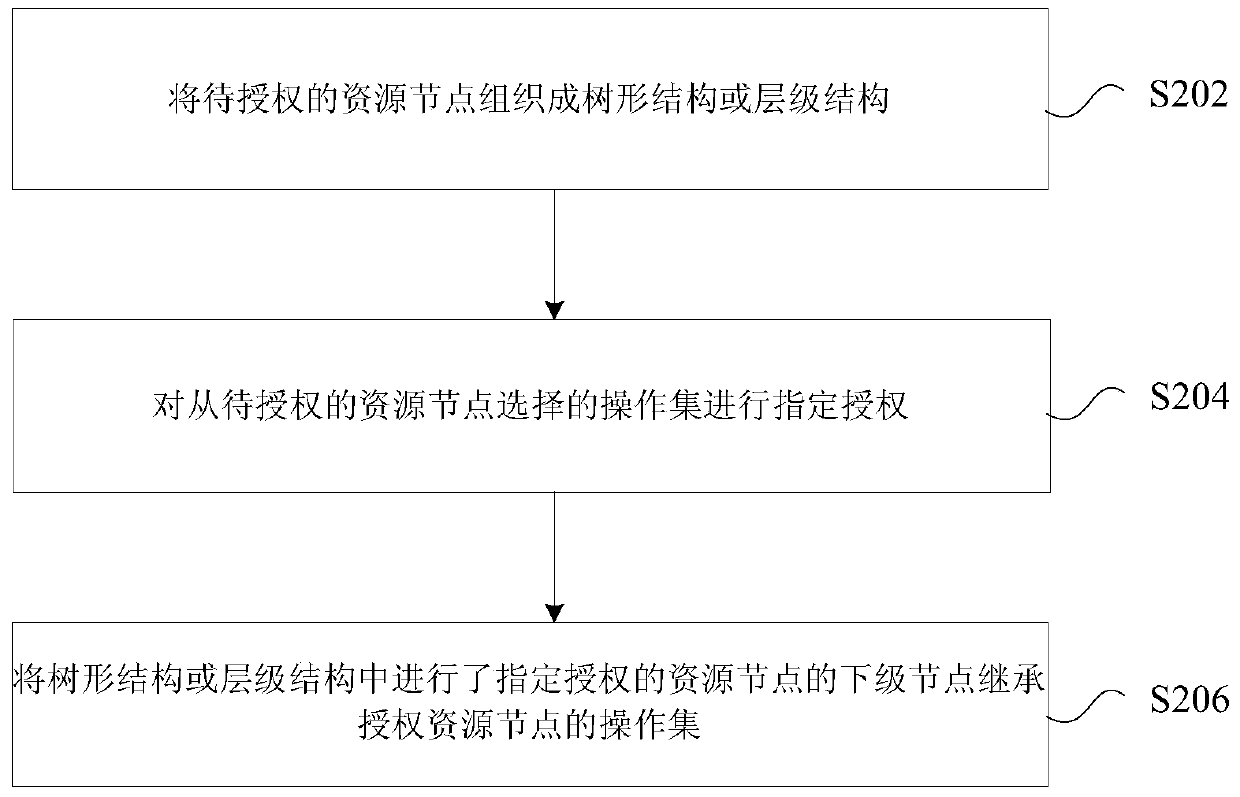
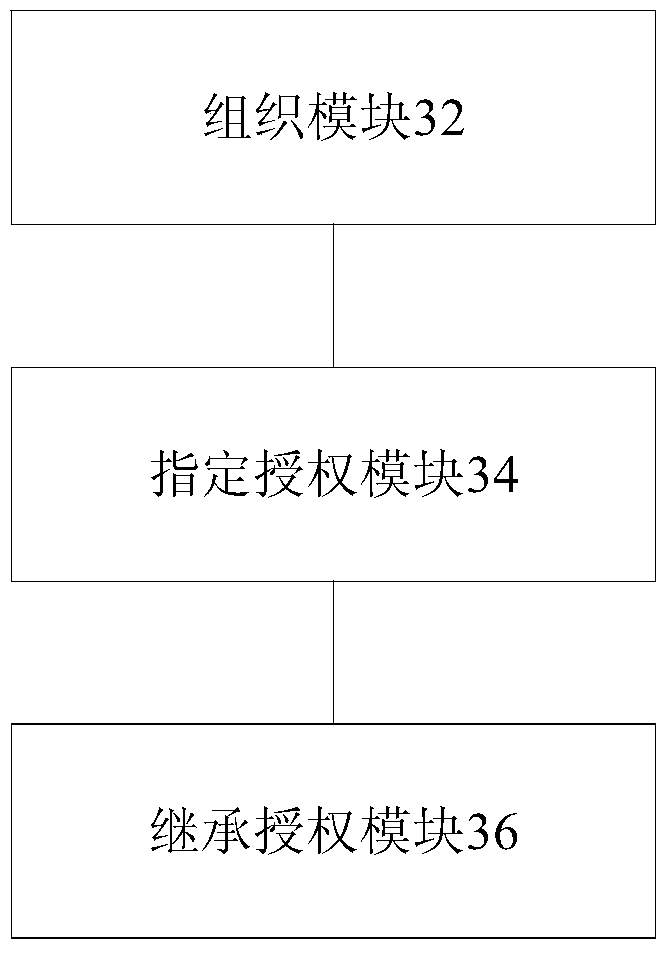
ActiveCN105763522AFlexible authorizationPermission display is not intuitiveDigital data authenticationTransmissionAuthorization ModeTree shaped
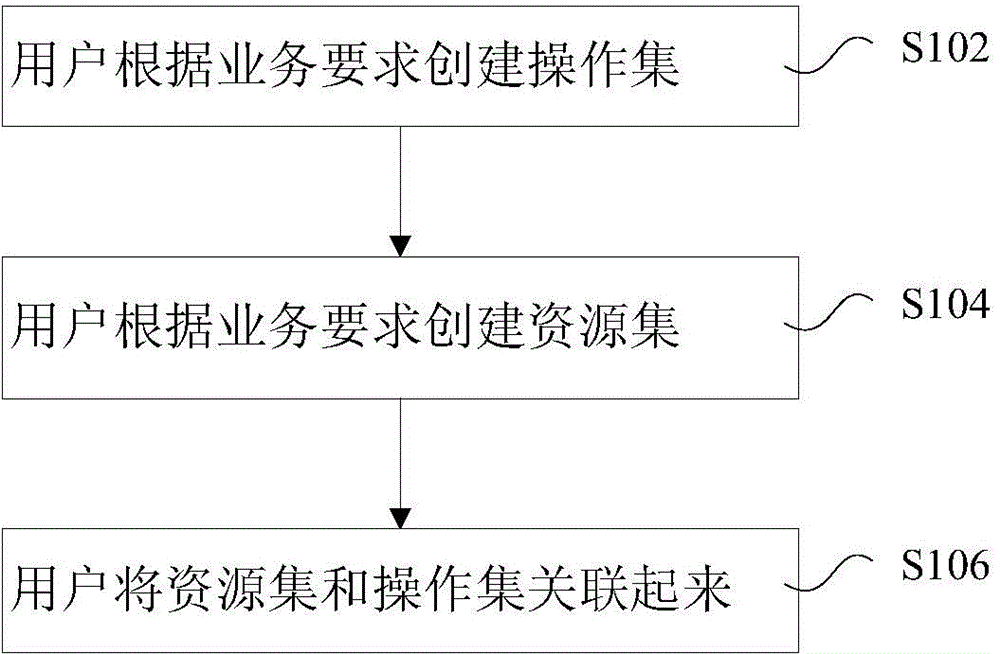
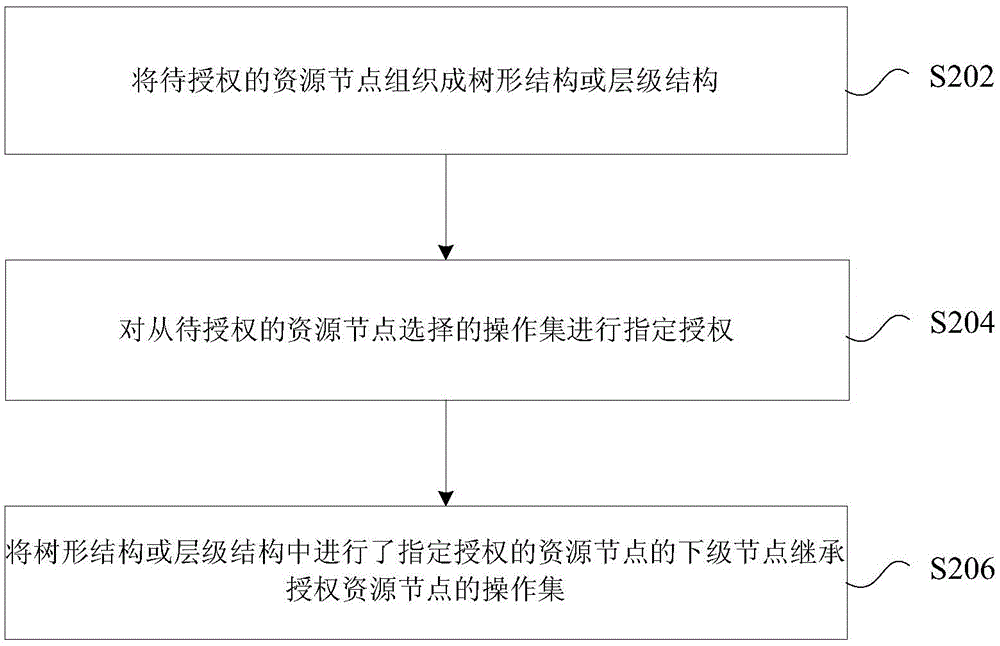
The invention discloses an authorization processing method and device. The method includes organizing to-be-authorized resource nodes into a tree-shaped structure or a hierarchy structure; performing appointed authorization on an operation set selected from the to-be-authorized resource nodes; letting subordinate nodes of the resource nodes subjected to appointed authorization in the tree-shaped structure or the hierarchy structure inherit the operation set of the authorization resource nodes. In related prior art, at least one among the problems of inflexible authorization method, indirection authority display and huge amount of authorization number exists in role authorization. The invention provides the flexible authorization method, provides direct authority display and achieves preferable authority storage.
Owner:ZTE CORP
A method and system for licensing software licenses
InactiveCN109086575AImprove securityIncrease flexibilityProgram/content distribution protectionThird partySoftware license
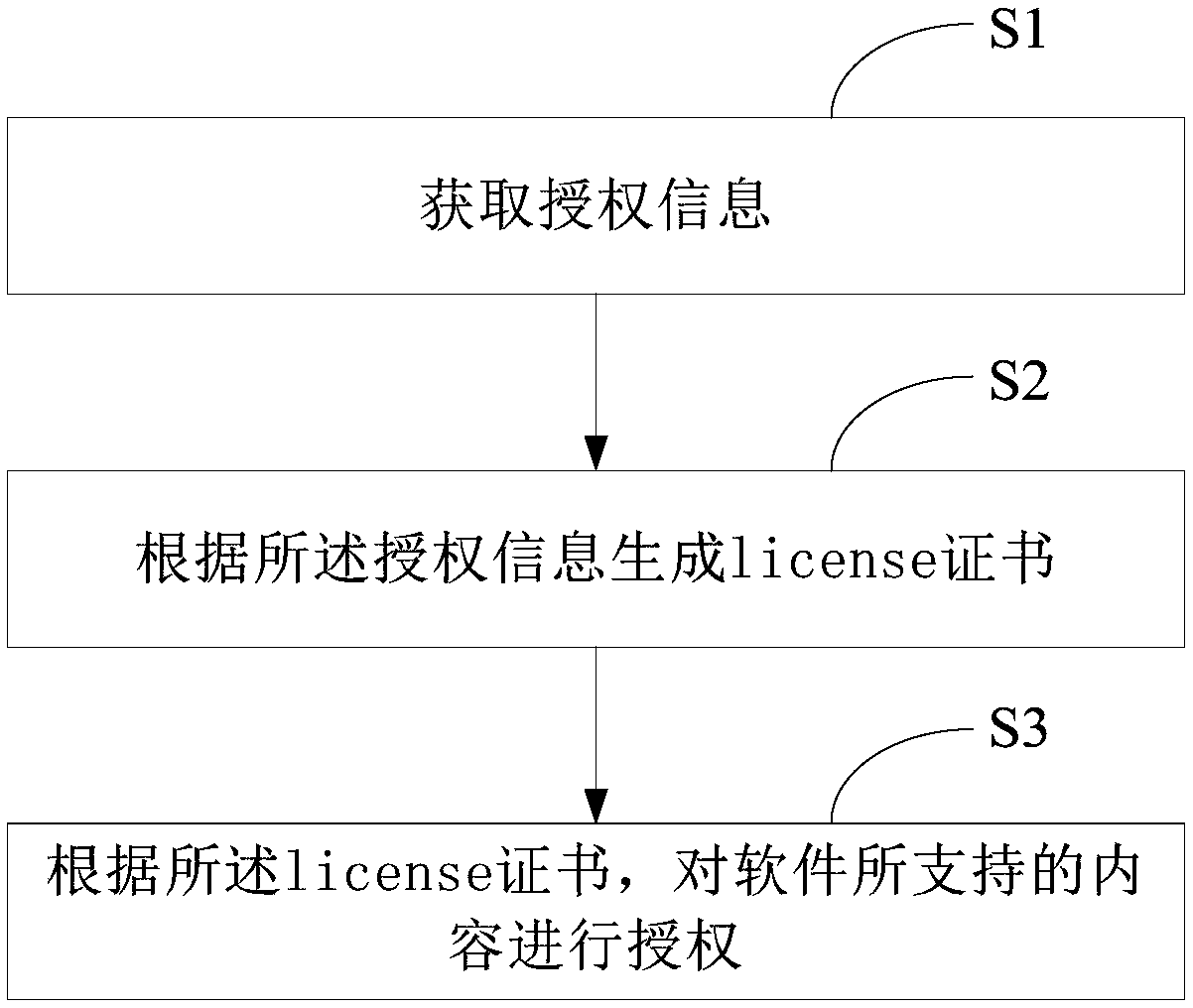
The present application discloses an authorization method and a system for a software license. The method includes obtaining authorization information, generating a license certificate according to the authorization information, and authorizing contents supported by the software according to the generated license certificate. The system includes: authorization information acquisition module, certificate generation module and authorization module. With the method and system for licensing software licenses in the present application, software licensing can be flexibly performed according to different machines to be licensed without having to rely on a fixed third party program for licensing. The software supported content can also be licensed according to the license certificate through theapplication, which is favorable for improving the flexibility and security of the software licensing.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
Low-power-consumption intelligent ticket selling and taking terminal and using method thereof
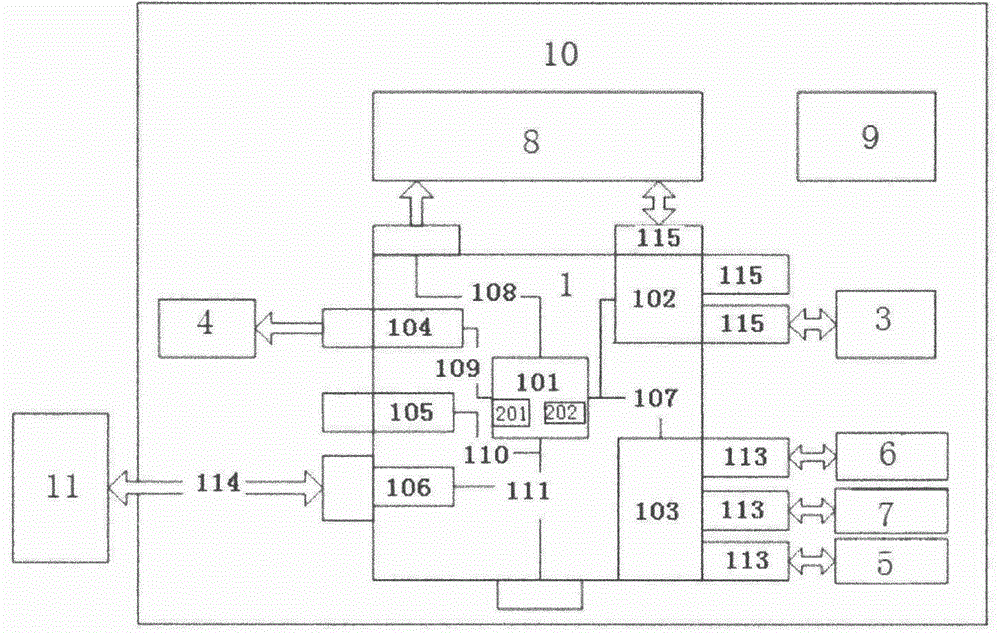
InactiveCN104392559AGood serviceService efficiencyApparatus for meter-controlled dispensingTransceiverData acquisition
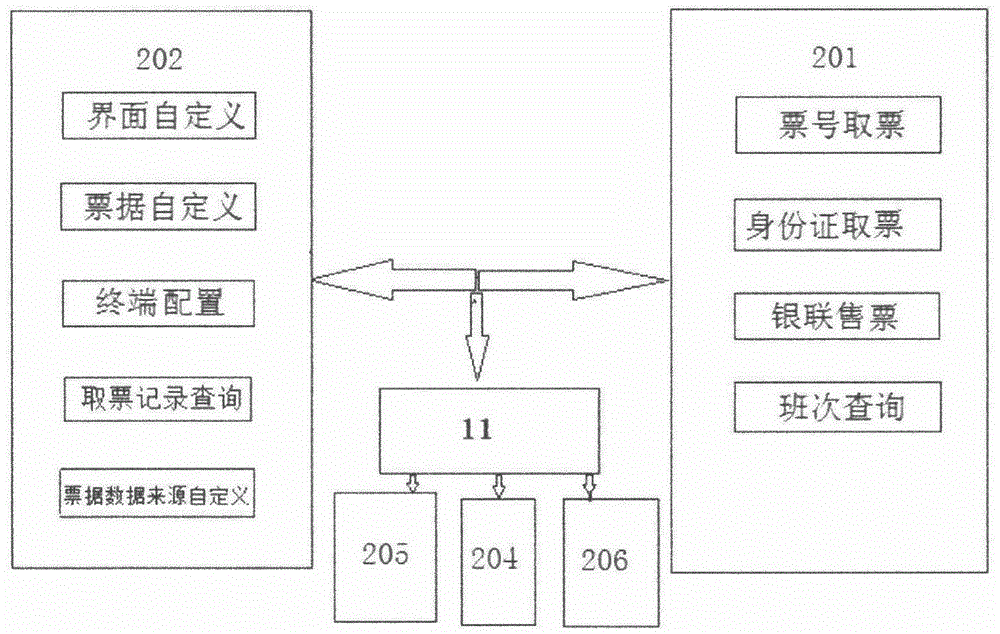
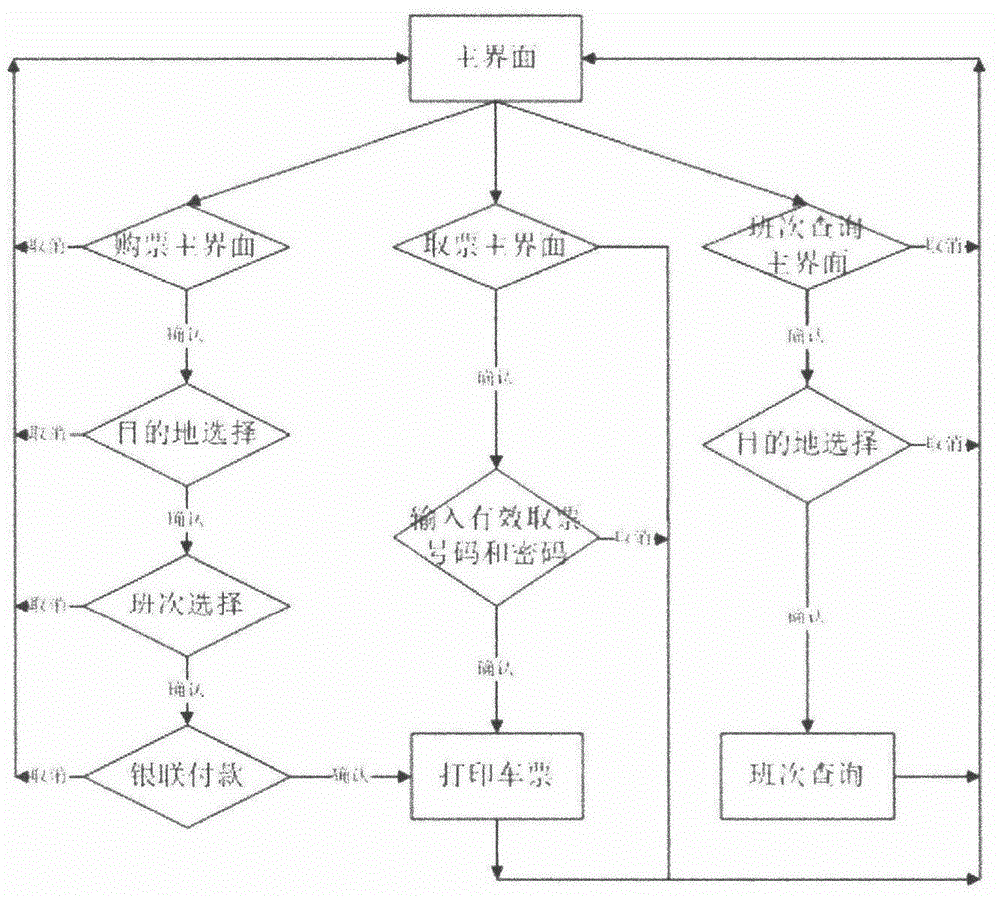
The invention discloses a low-power-consumption intelligent ticket selling and taking terminal and a using method thereof. The terminal comprises a main controller (1), a ticket taking system compact disc (2), a bill printer (3), sound equipment (4), an identity card reader (5), a metal encryption keyboard (6), a union pay card reader (7), a touch display (8), an AC-DC (alternating current-direct current) power supply (9), a shell (10), a background server (11) and various network interfaces, wherein the main controller (1) consists of a four-core ARM (advanced risc machine) processor (101), a USB (universal serial bus) HUB chip (102), an RS 232 transceiver (103), an audio DAC (data acquisition chassis ) circuit (104), a video decoder circuit (105) and an Ethernet controller circuit (106); and the ticket taking system compact disc (2) comprises foreground application software (201) and a management platform (202). The terminal is small in size, low in power consumption and free and flexible in authorization; a system runs stably; and an application range is quite wide.
Owner:无锡怡通智运科技发展有限公司
Copyright purchasing and using method and device, electronic equipment and readable storage medium
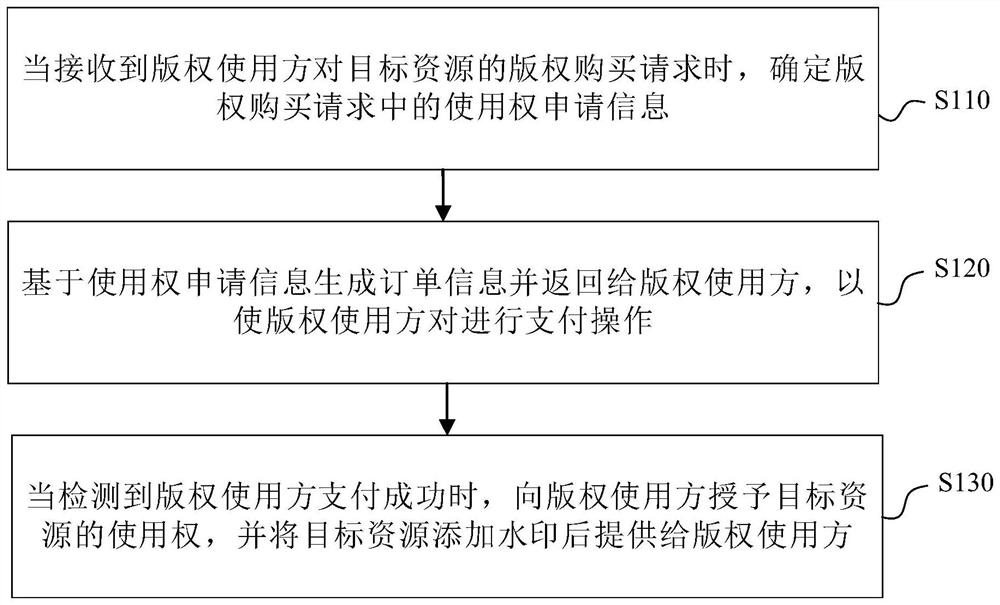
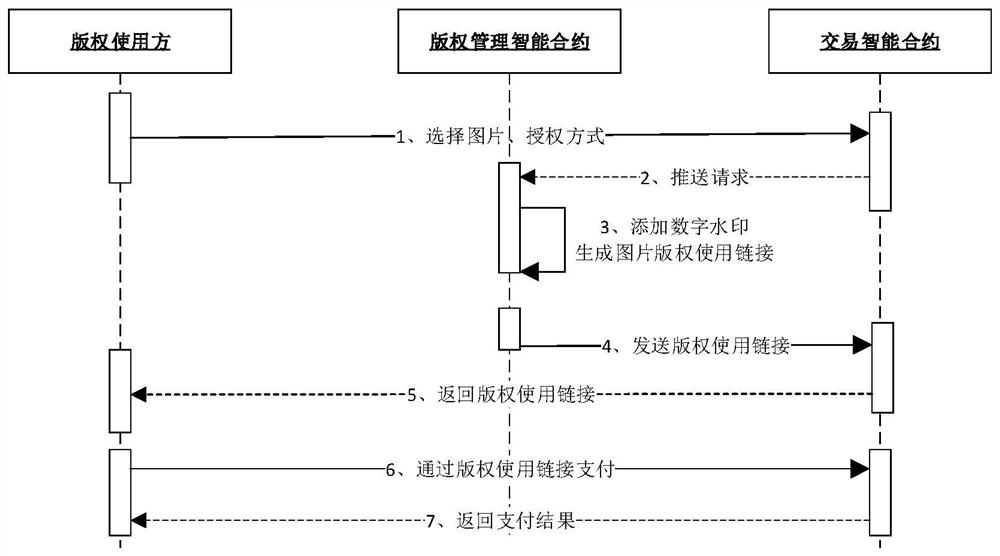
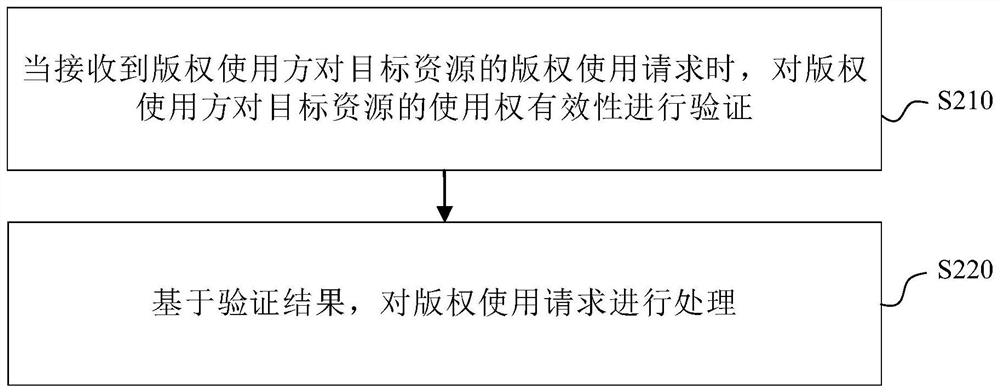
PendingCN111666541ARealize online transactionFlexible AuthorizationPayment architectureProgram/content distribution protectionEngineeringFinancial transaction
The embodiment of the invention provides a copyright purchasing and using method and device, electronic equipment and a readable storage medium. The method comprises the steps: when a copyright purchase request of a copyright user for target resources is received, determining use right application information in the copyright purchase request; generating order information based on the use right application information and returning the order information to the copyright user, so as to enable the copyright user to perform payment operation; and when it is detected that the copyright user pays successfully, granting the use right of the target resource to the copyright user, adding a watermark to the target resource, and providing the target resource to the copyright user. Based on the scheme, online transaction of the copyright is realized, flexible authorization of the copyright is realized, and actual use requirements can be met.
Owner:CHINA CITIC BANK
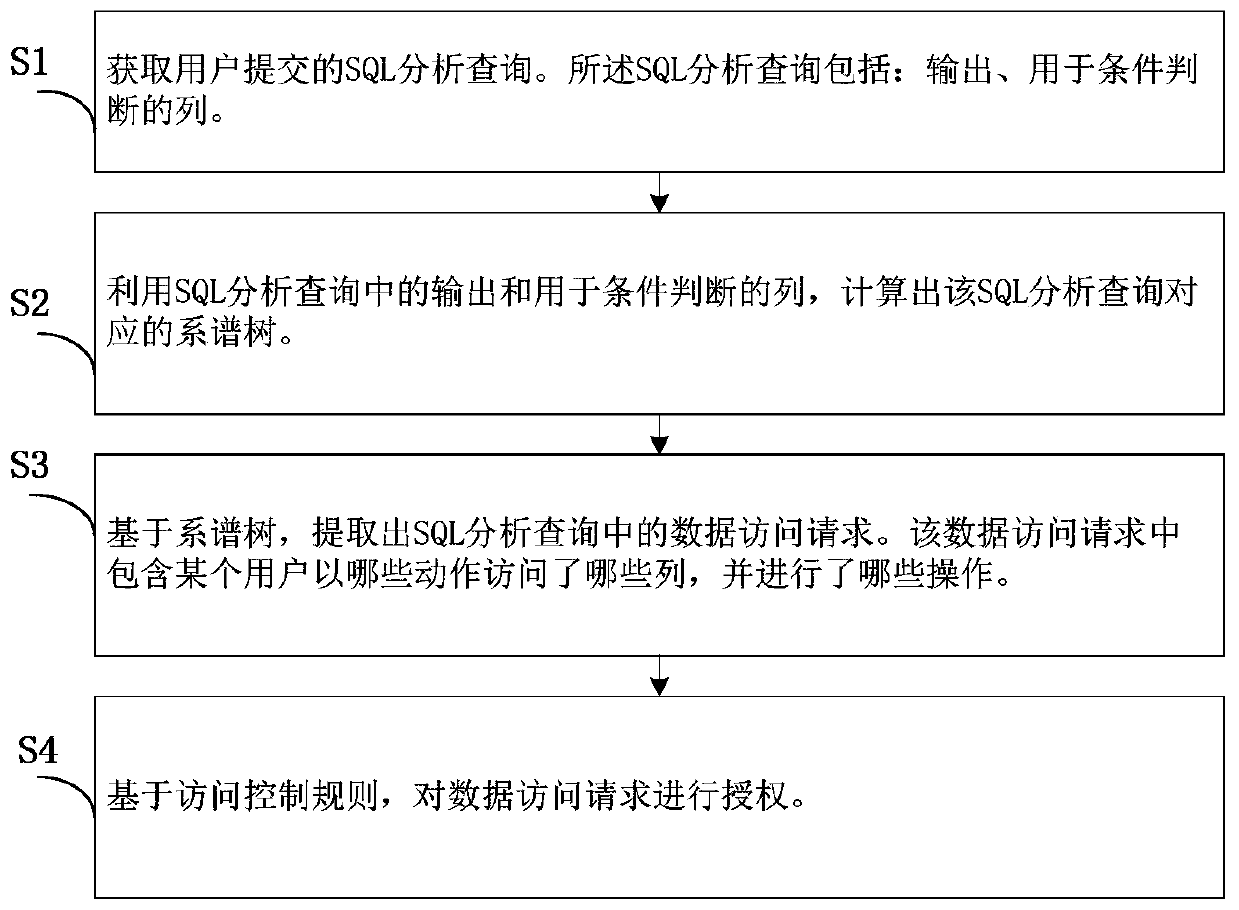
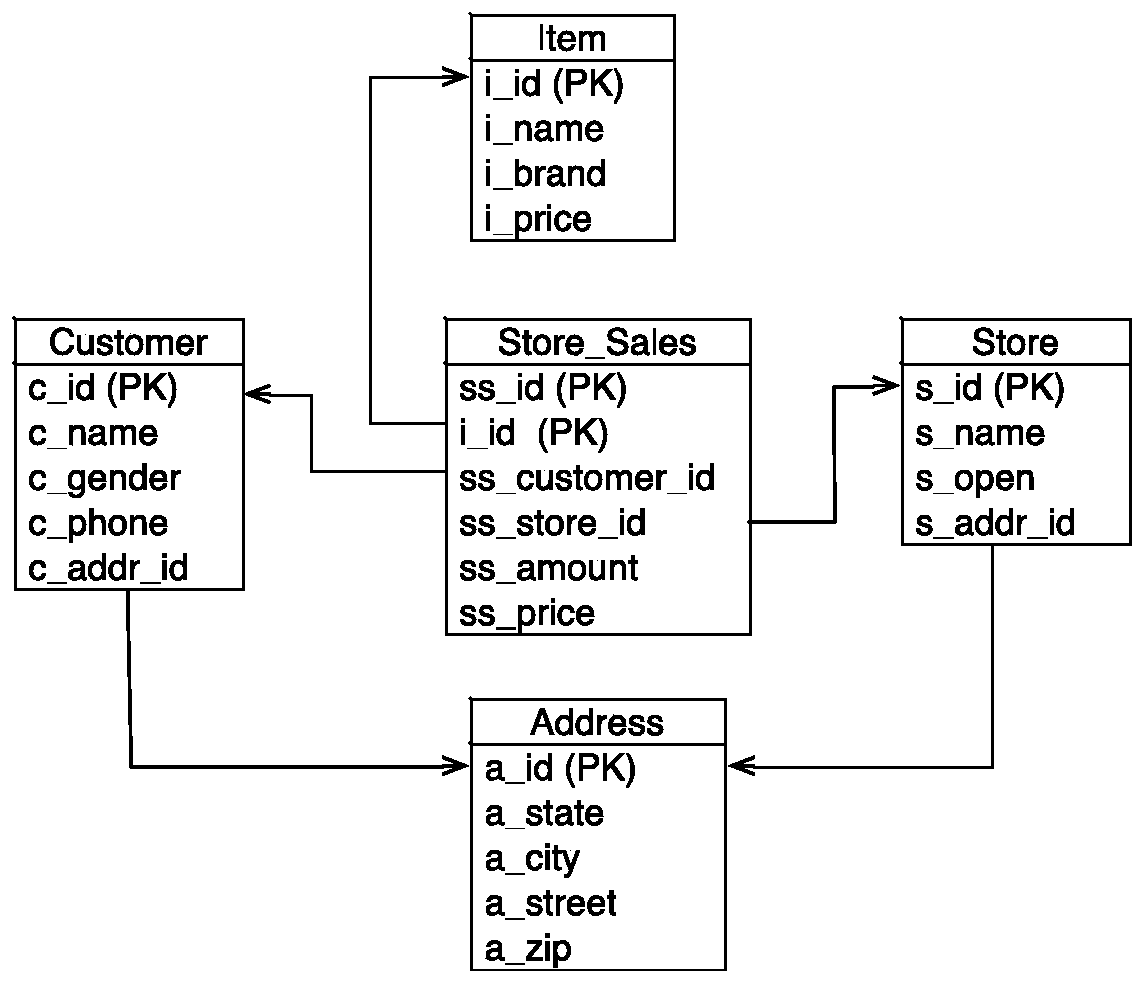
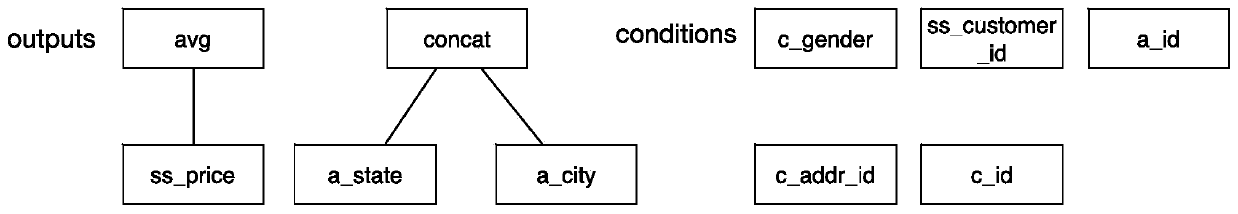
Static authentication method capable of aiming at SQL (Structured Query Language) analytical query
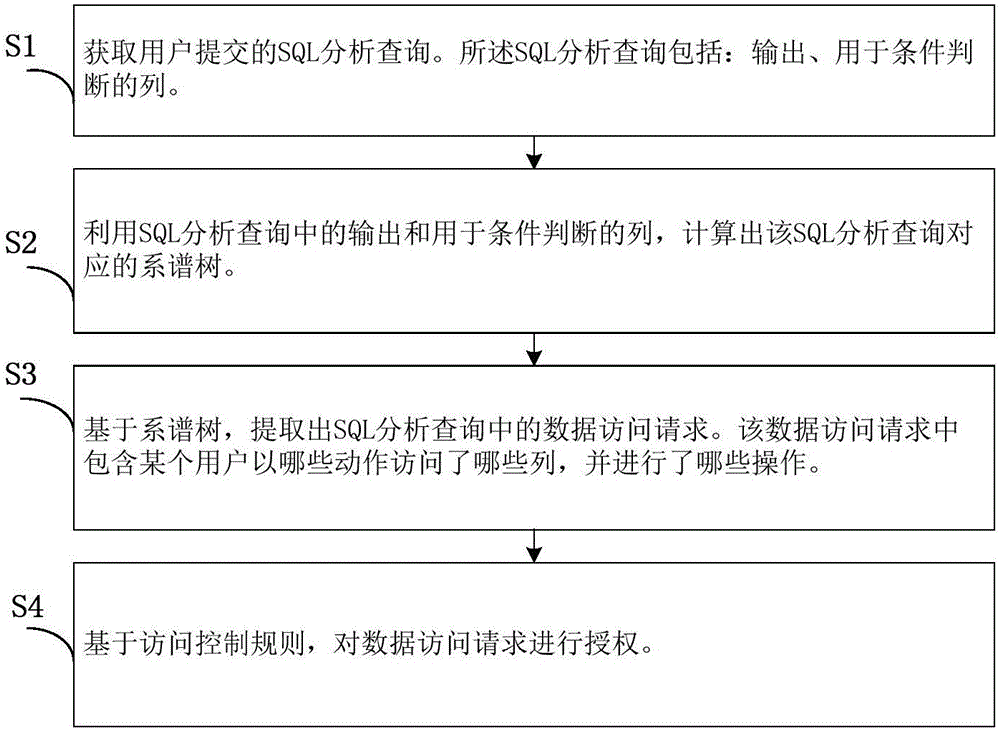
ActiveCN106383855AFlexible AuthorizationAccurate authorizationSpecial data processing applicationsData accessLarge scale data
The invention provides a static authentication method capable of aiming at SQL (Structured Query Language) analytical query. The method comprises the following steps of: S1: obtaining the SQL analytical query submitted by a user; S2: constructing a genealogical tree from the SQL analytical query; S3: on the basis of the genealogical tree, extracting a data access request of the SQL analytical query; and S4: on the basis of an access control rule, authenticating the data access request. Compared with an existing database access control technology, the static authentication method combines the characteristics of the analytical query to support simultaneous access to a plurality of columns and control for an operation. Therefore, by use of the method, the SQL analytical query can be more flexibly and accurately authenticated. Meanwhile, by use of the method, an administrator is permitted to carry out permission management through the compiling of the access control rule, in addition, no extra burdens are brought to users, and therefore, the static authentication method exhibits better availability. Finally, the method carries out authentication only on the basis of the SQL analytical query, so that an authentication process is more efficient, and the method is suitable for a large-scale data analysis scene.
Owner:TSINGHUA UNIV
Data authorization method and device based on ERP
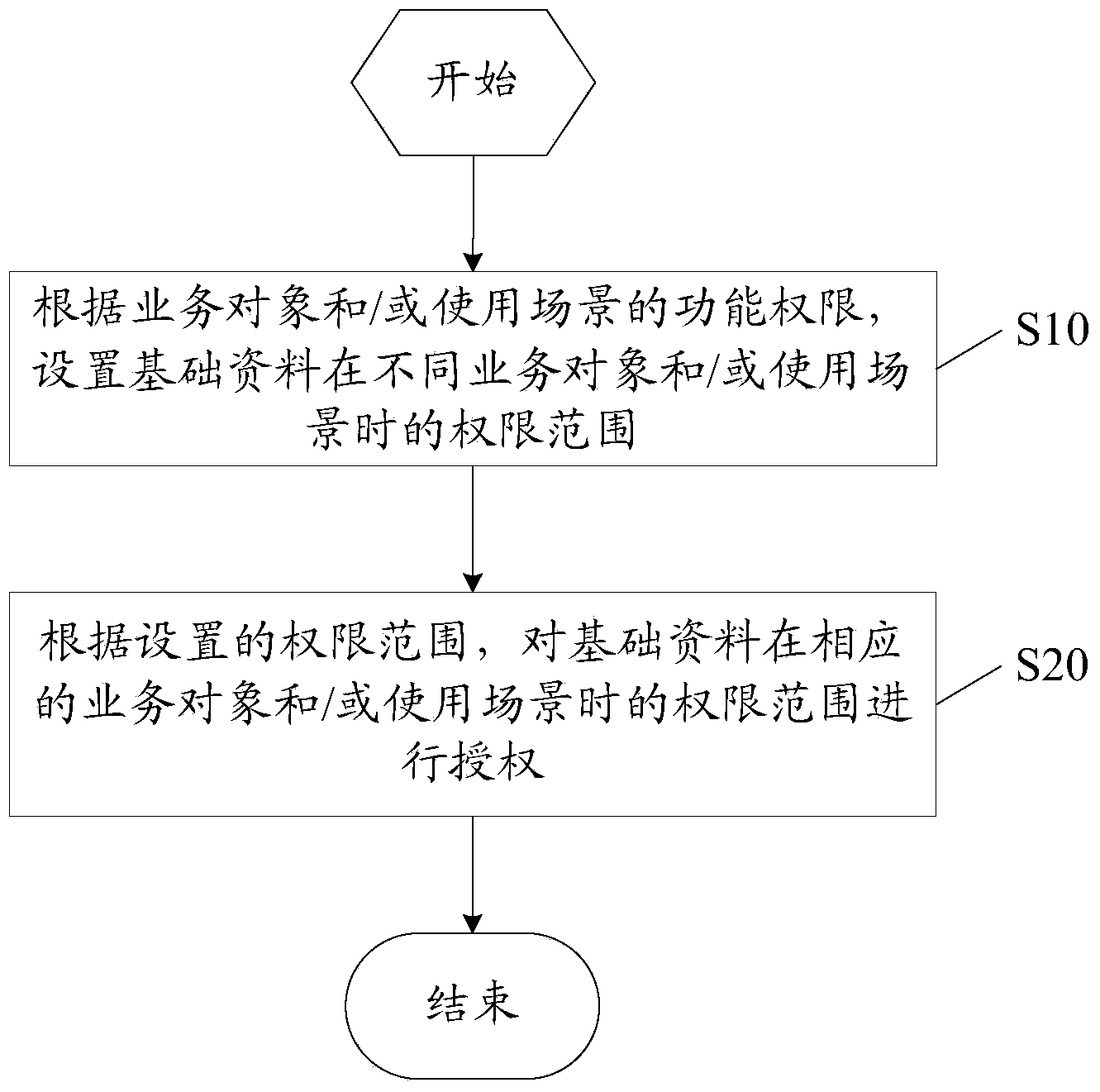
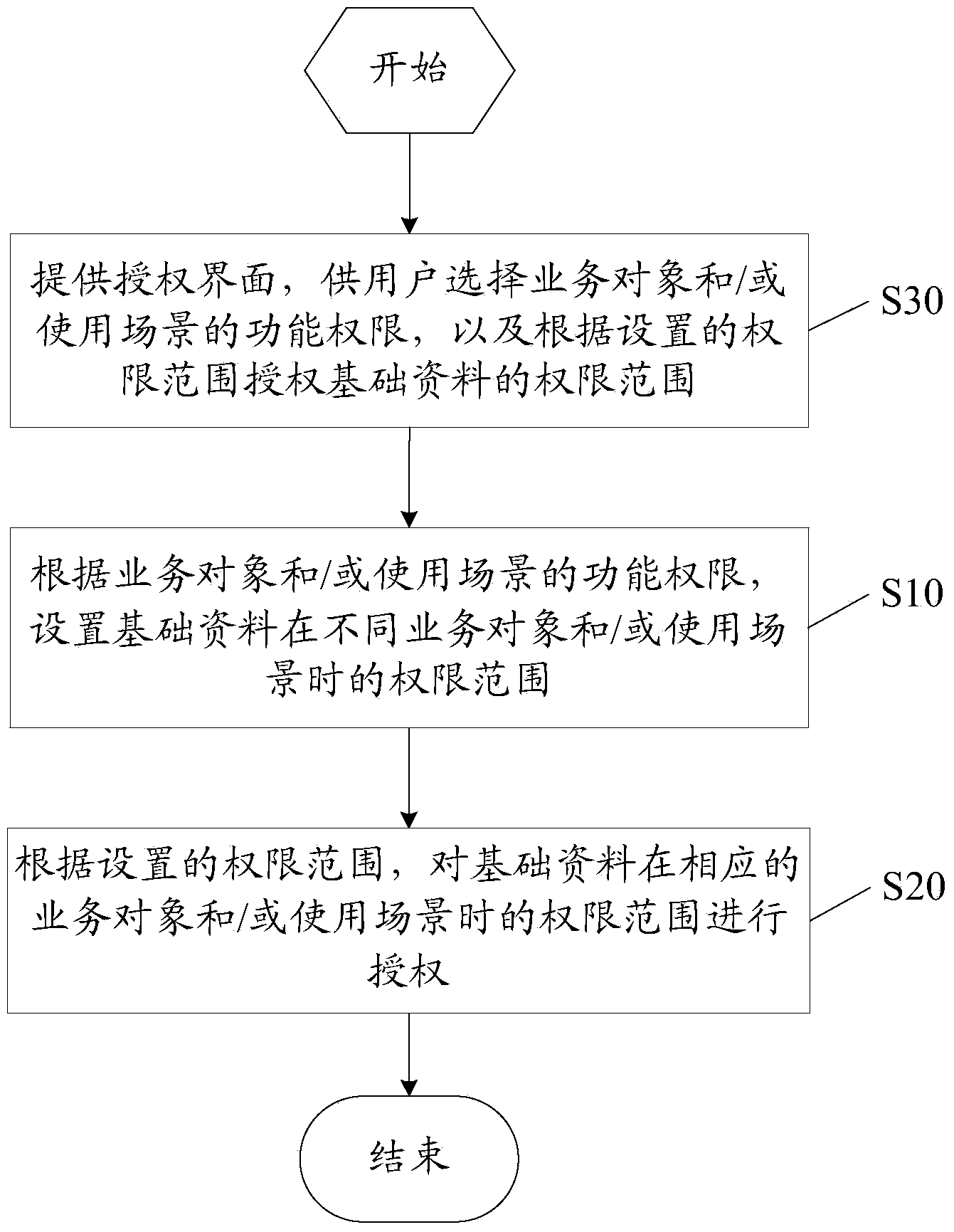
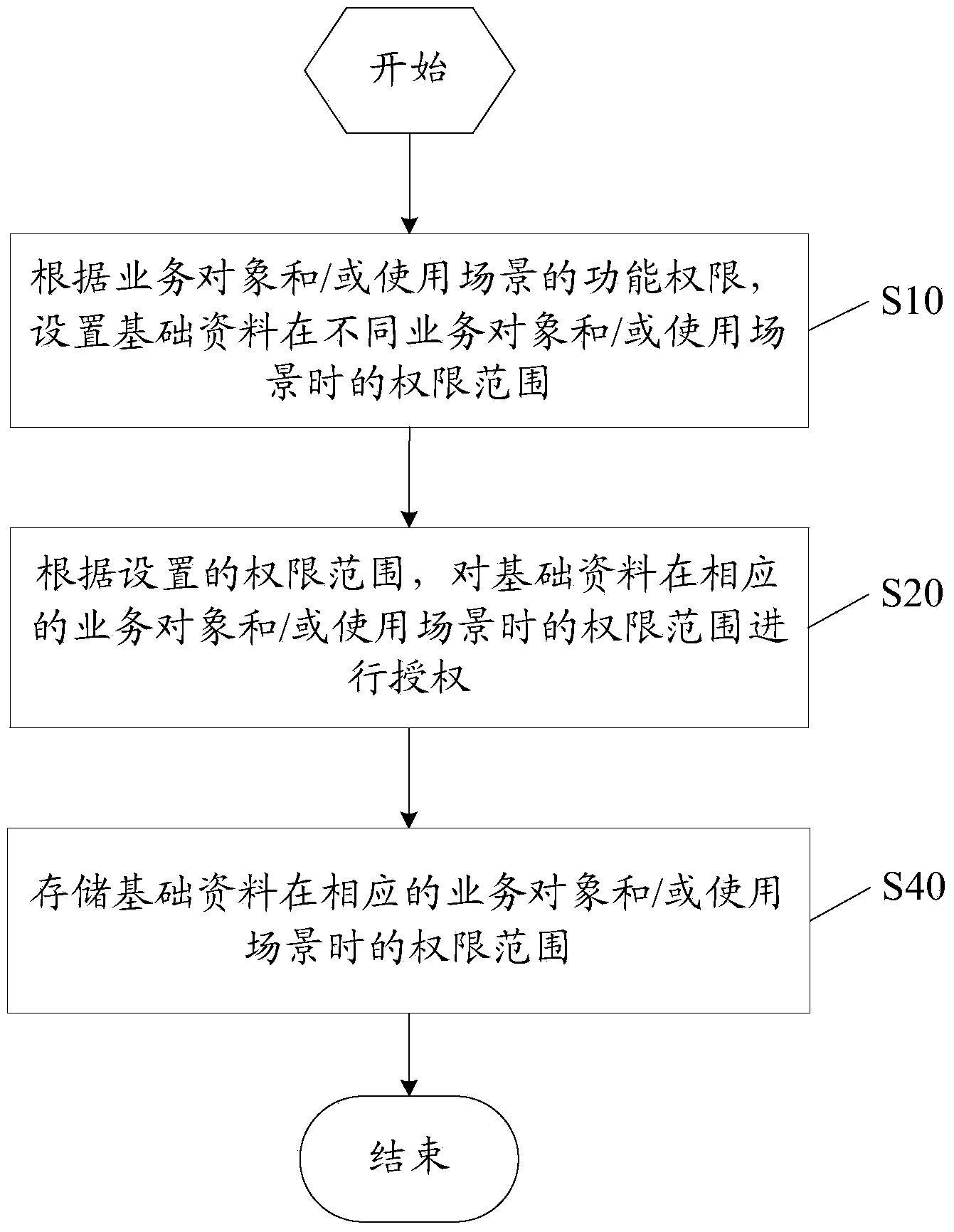
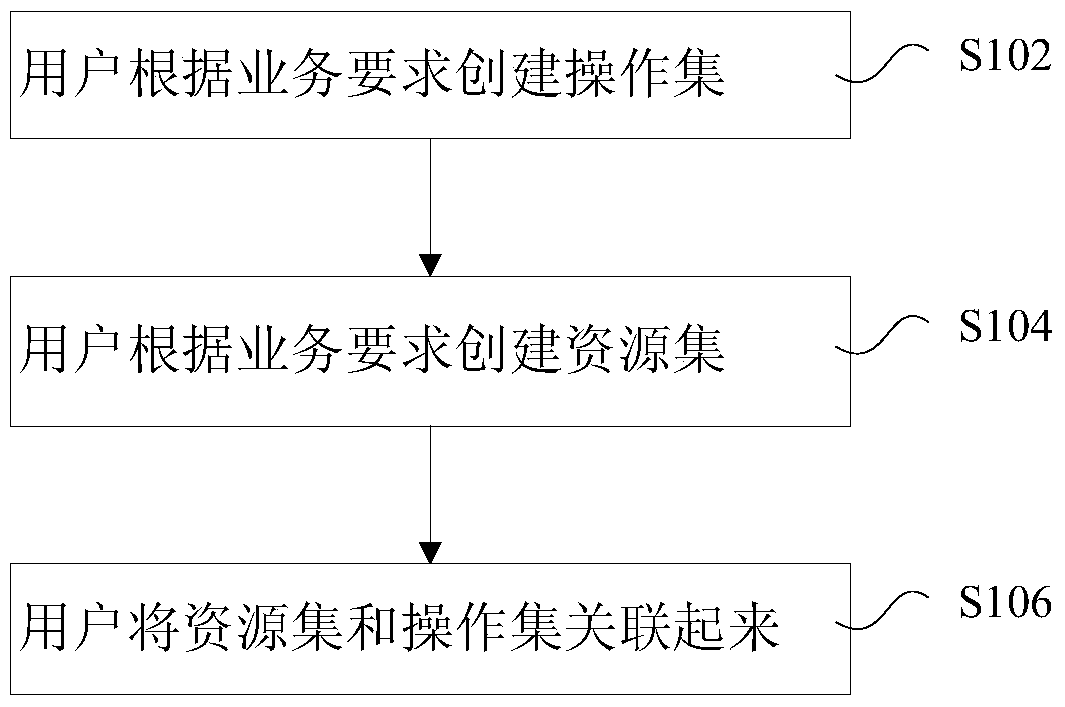
InactiveCN103530537AFlexible AuthorizationReduce stitchingDigital data authenticationAuthorizationBusiness object
The invention discloses a data authorization method based on an ERP. The method includes the steps of setting permission ranges of basic data of different service objects and / or in different use scenes according to the function permission of the service objects and / or the use scenes, and carrying out authorization in the permission ranges of the basic data of the corresponding service objects and / or in the corresponding use scenes according to the set permission range. The invention further discloses a corresponding device. When an ERP product operates, after the service object and / or the use scene under the current operation state is judged, according to the different permission ranges, different data are shown to a user, data range authorization is more flexible, and due to the fact that splicing of the permission ranges is reduced, performance of the ERP product is improved.
Owner:KINGDEE SOFTWARE(CHINA) CO LTD
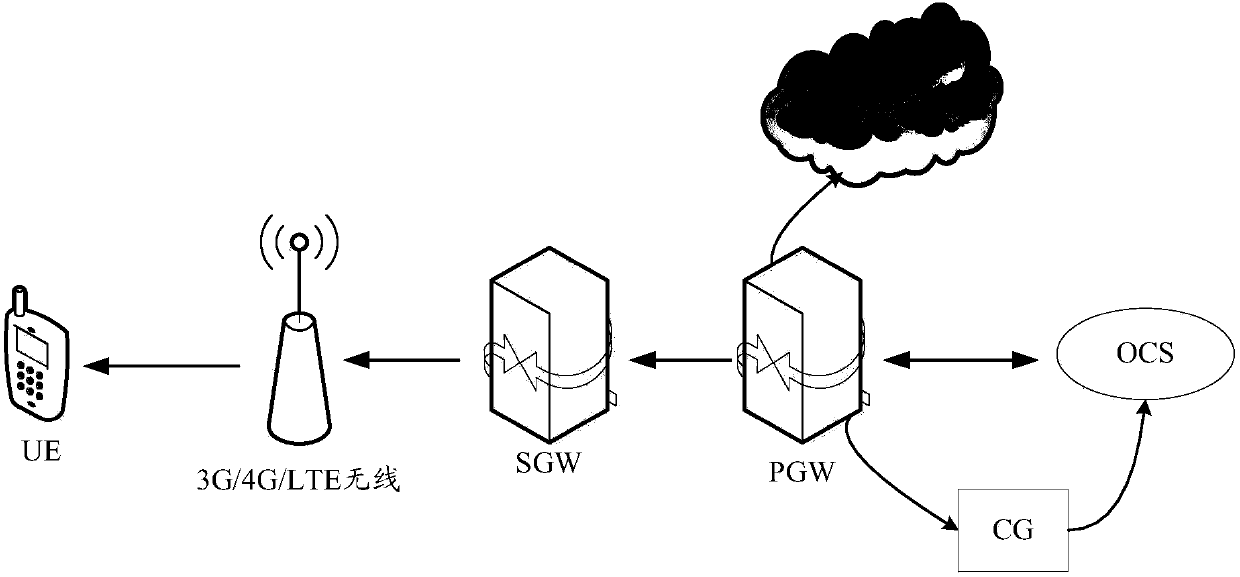
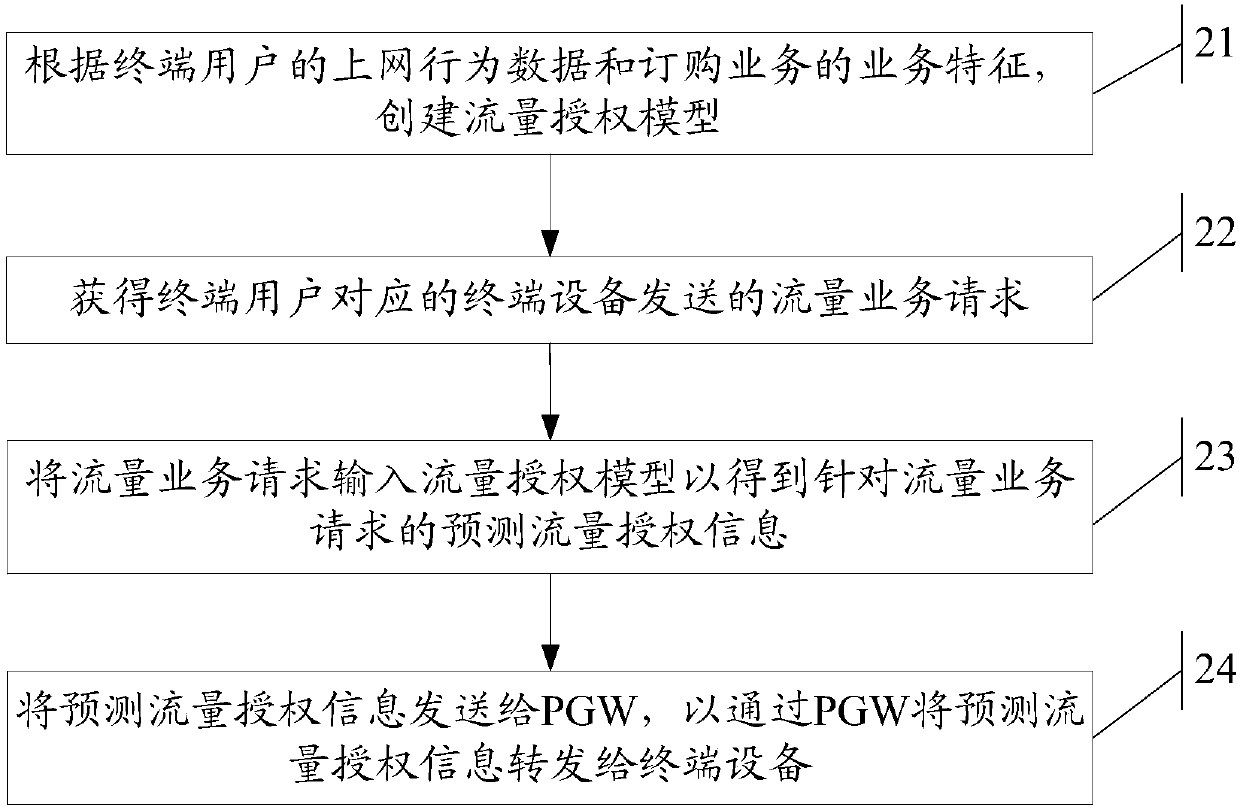
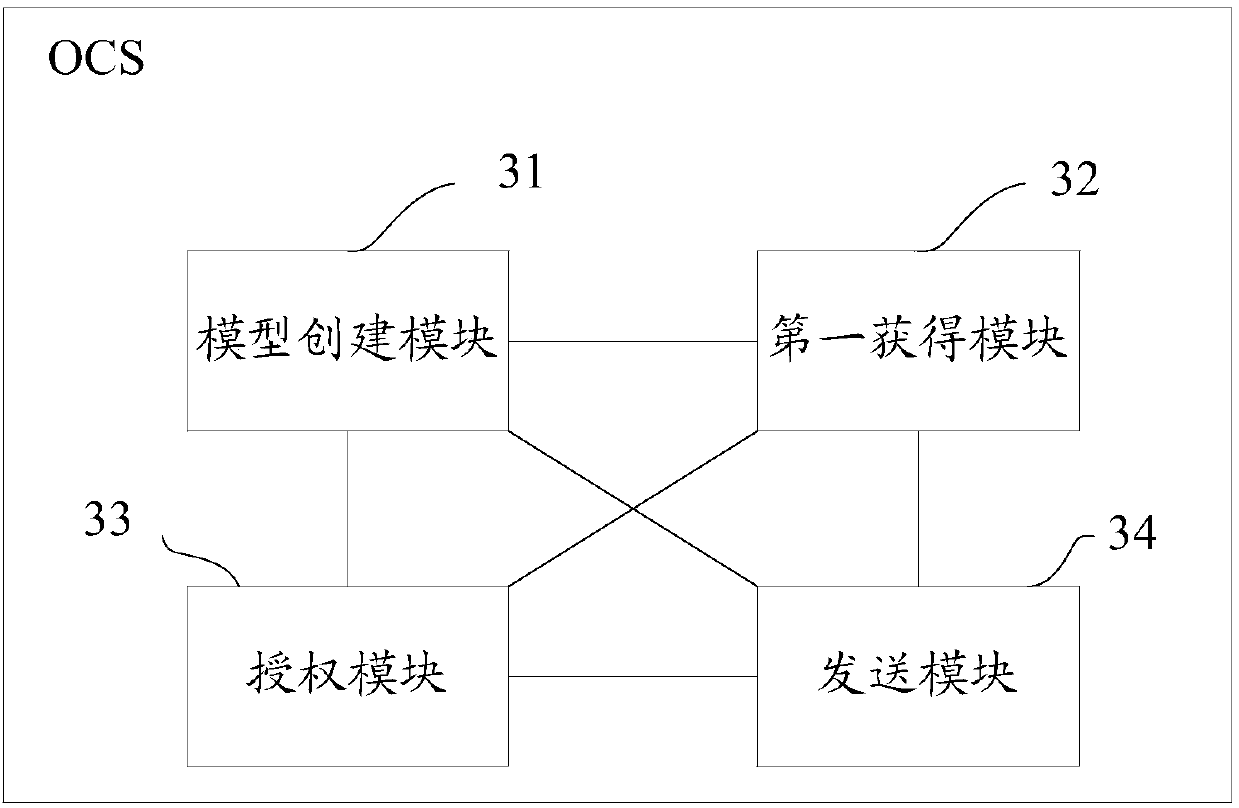
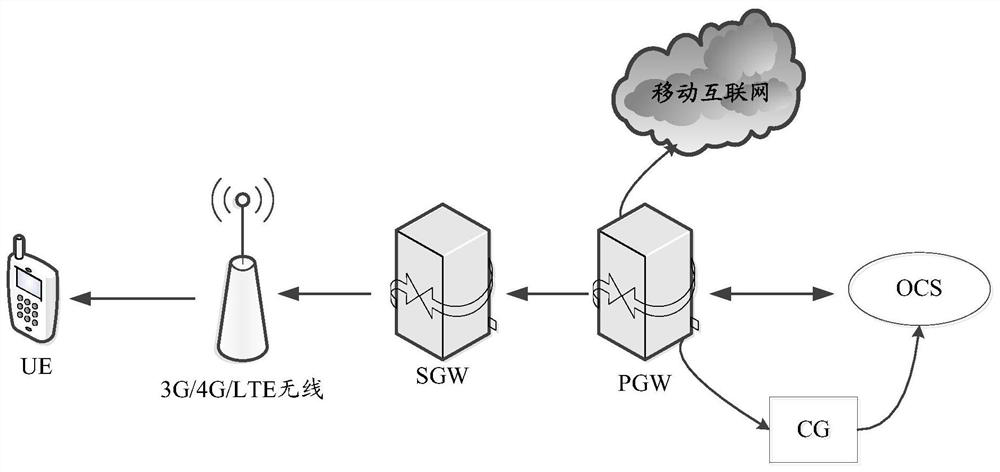
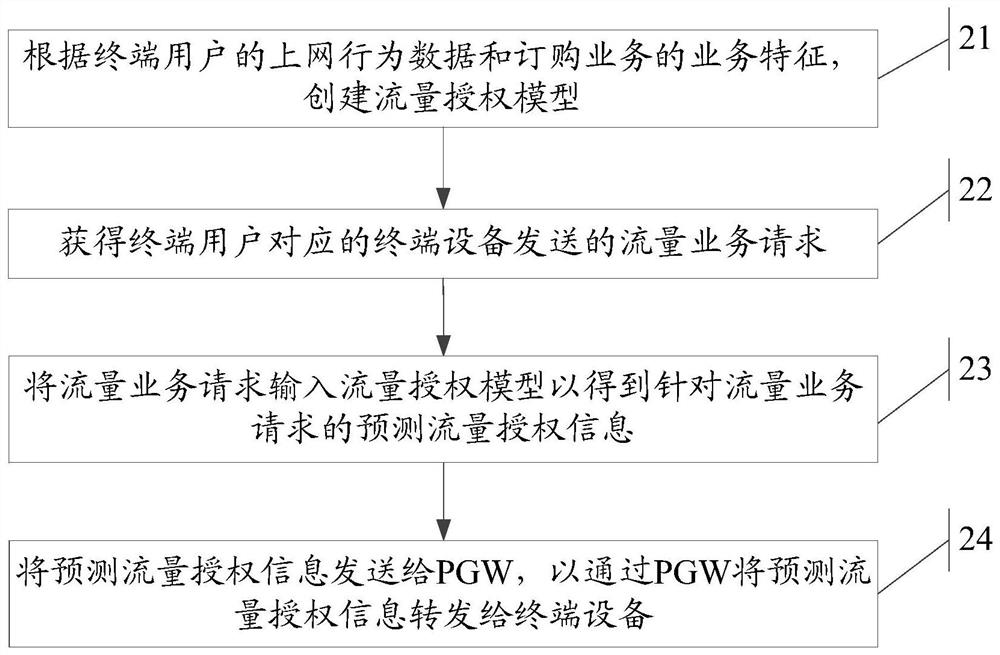
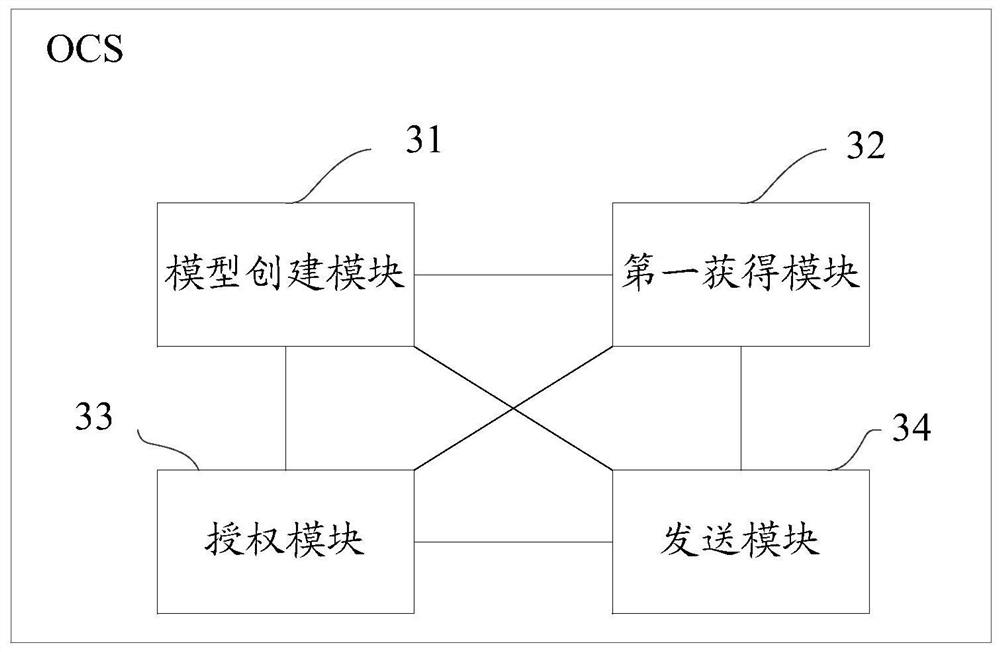
OCS traffic authorization method, OCS, server and readable storage medium
ActiveCN109995539AMeet actual traffic business needsEnhance traffic service experienceMetering/charging/biilling arrangementsTraffic capacityService experience
The invention discloses an OCS traffic authorization method, an OCS, a server and a readable storage medium. The method is used for solving the technical problem that in the prior art, the mode of carrying out dynamic authorization configuration by an OCS is not flexible enough, and consequently the authorization configuration accuracy of a user is low. Therefore, the flexibility of flow authorization configuration is improved, different flow authorizations can be realized for different users to meet the actual flow service requirements of the users as much as possible, and the flow service experience of the users is enhanced. The method comprises the following steps: creating a flow authorization model according to Internet behavior data of a terminal user and service characteristics of an ordering service; obtaining a traffic service request sent by a terminal device corresponding to the terminal user; inputting the traffic service request into the traffic authorization model to obtain predicted traffic authorization information for the traffic service request; and sending the predicted flow authorization information to a PGW, so that the predicted flow authorization informationis forwarded to the terminal equipment through the PGW.
Owner:CHINA MOBILE GROUP JILIN BRANCH +1
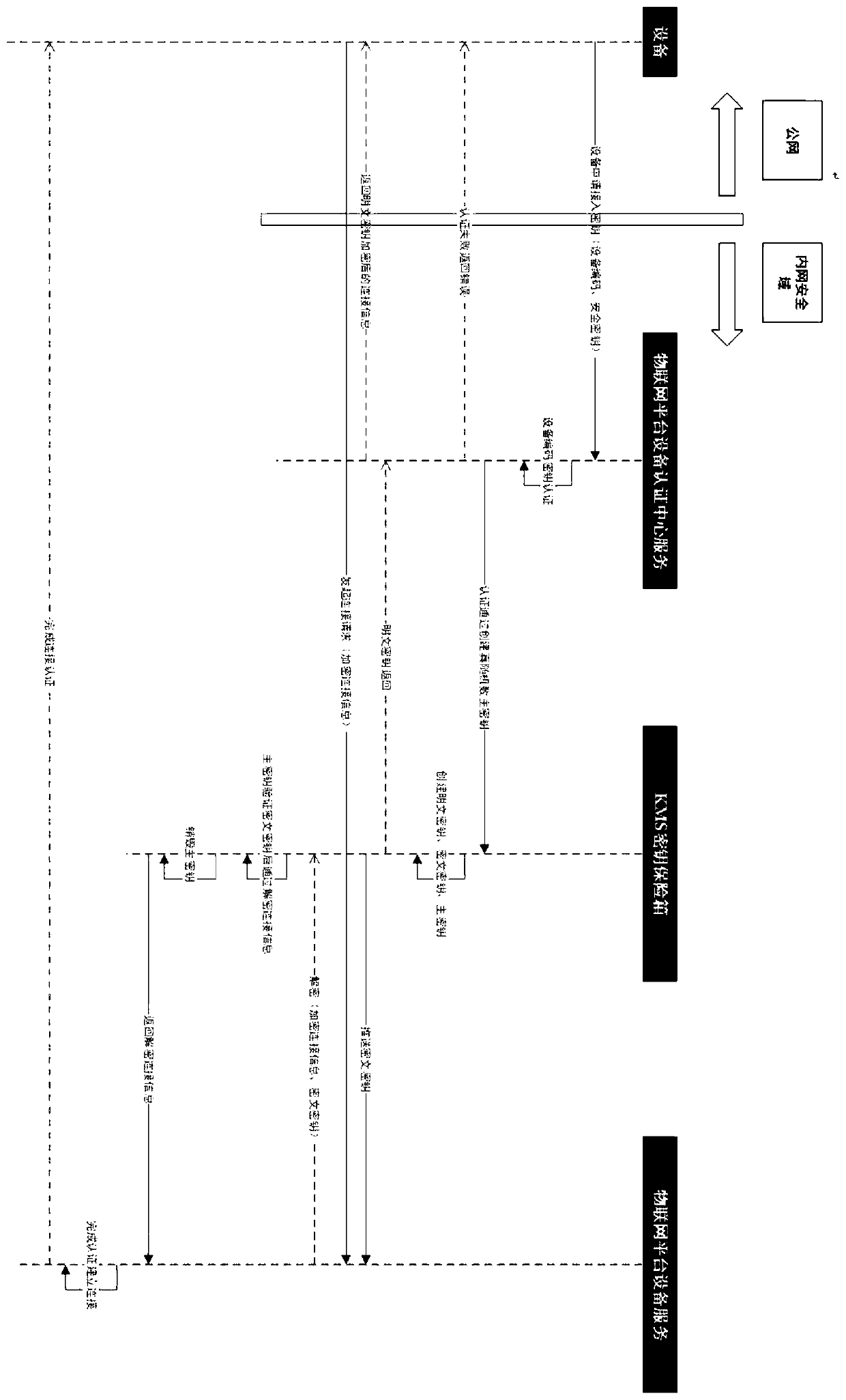
Device access authentication system and method based on KMS
The invention discloses a device access authentication system based on a KMS. The system comprises an equipment authentication center server, a KMS secret key safe box, an equipment server and an equipment terminal; the equipment authentication center server, the KMS secret key safe box and the equipment server are in communication connection through an intranet, and the equipment terminal is in communication connection with the equipment authentication center server and the equipment server through a public network. According to the invention, the equipment secret key separation management, flexible authorization, destruction after use, secret key management without external network transmission and a use mechanism can be realized, and better, safe and convenient operation can be providedfor equipment access and management.
Owner:UNICLOUD (NANJING) DIGITAL TECH CO LTD
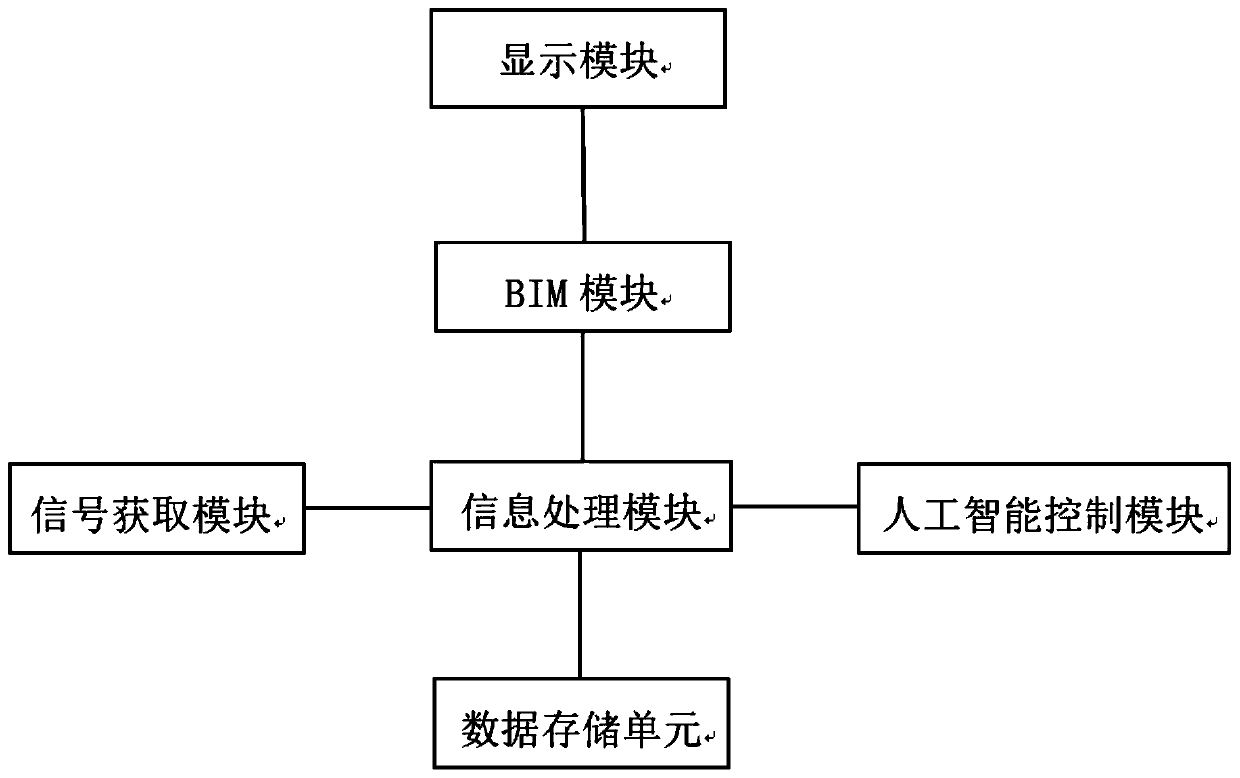
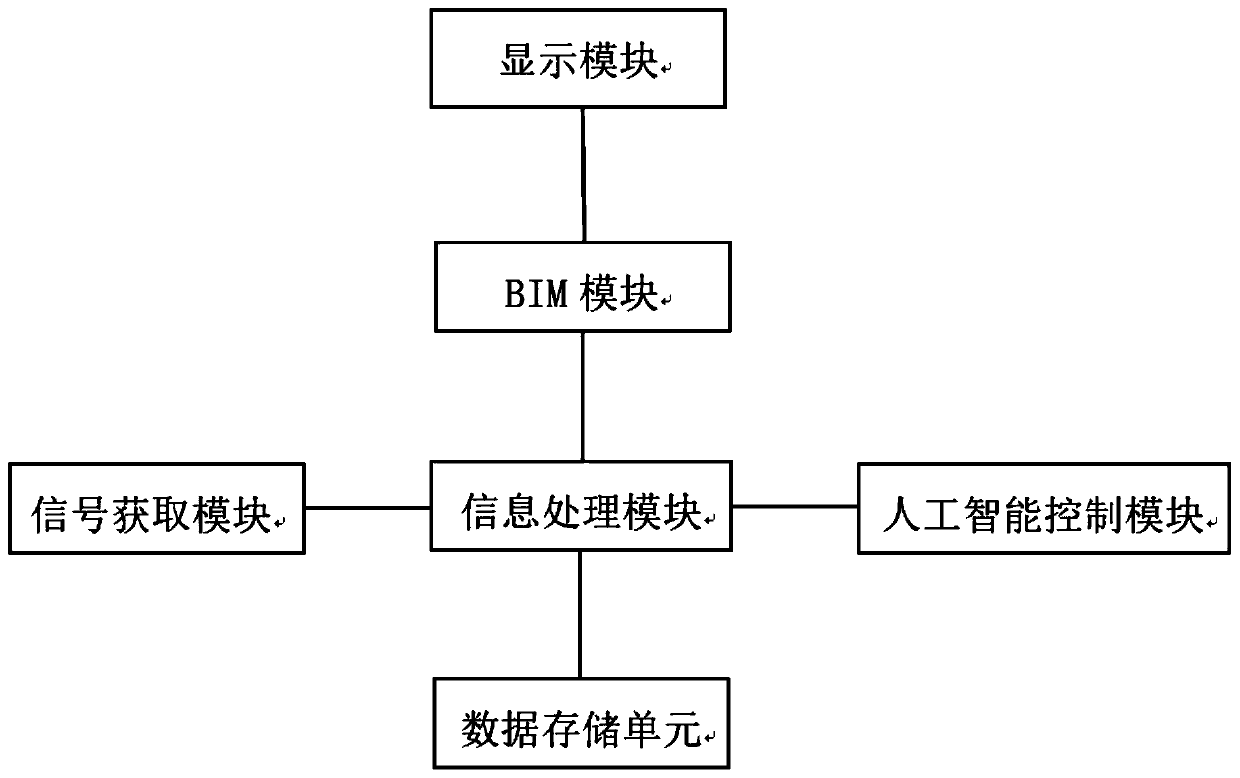
Method for realizing remote monitoring and authorization of tramcar based on BIM+AI
InactiveCN110032090ARealize remote monitoringGranular authorizationGeometric CADProgramme control in sequence/logic controllersData displayInformation processing
The invention provides a method for realizing remote monitoring and authorization of a tramcar based on BIM+AI. The method comprises the following steps of acquiring tramcar running related information in real time by adopting an information acquisition module; transmitting the acquired tramcar running related information to an information processing module, enabling the information processing module to carry out computational analysis on the information and storing corresponding data through a data storage module, and processing an analysis result through a BIM module and displaying the analysis result through a display module. According to the method, a building information model technology is adopted, and simulation and schematic equipment and data display modes in the traditional urbantramcar industry are broken, accurate display of tramcar running lines, vehicles, stations, equipment and the like on a three-dimensional comprehensive monitoring platform is realized, real-time on-spot remote monitoring of the tramcar is realized, an artificial intelligence technology is applied to a comprehensive management system of the tramcar, and fine and flexible authorization in a tramcaroperation and maintenance management process is realized.
Owner:深圳众维轨道交通科技发展有限公司
Method and system for acquiring service key, conditional access module and subscriber terminal
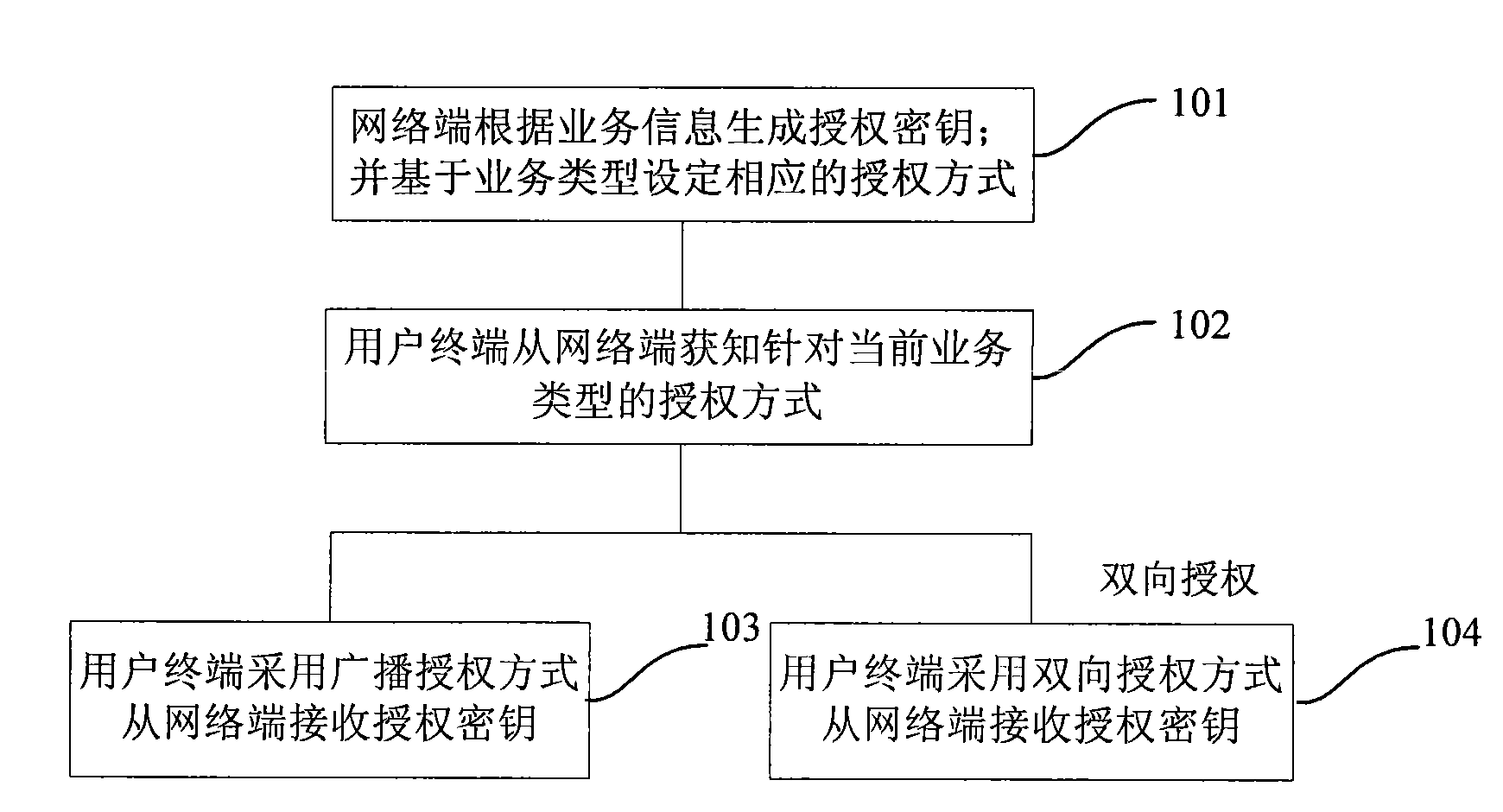
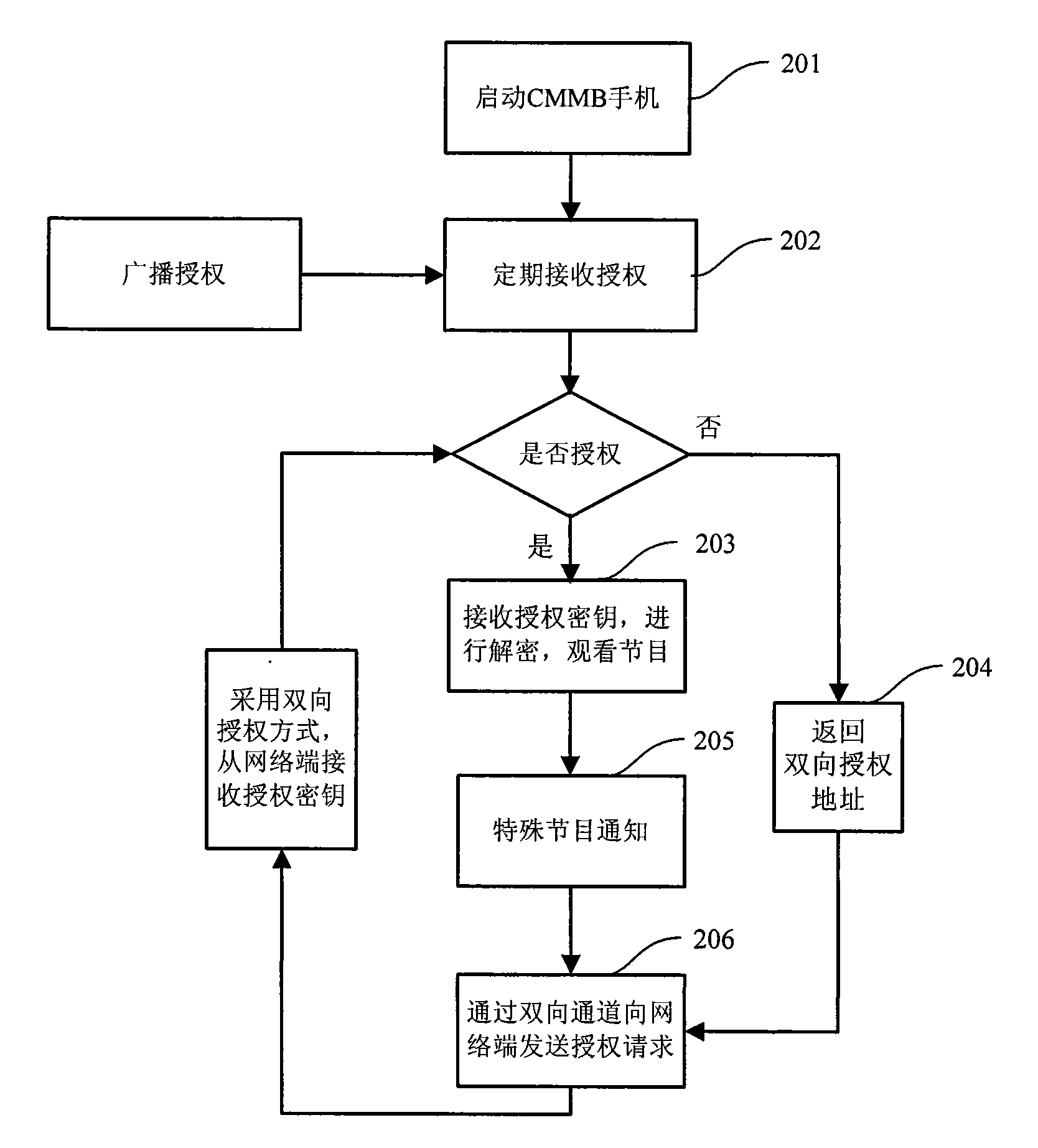
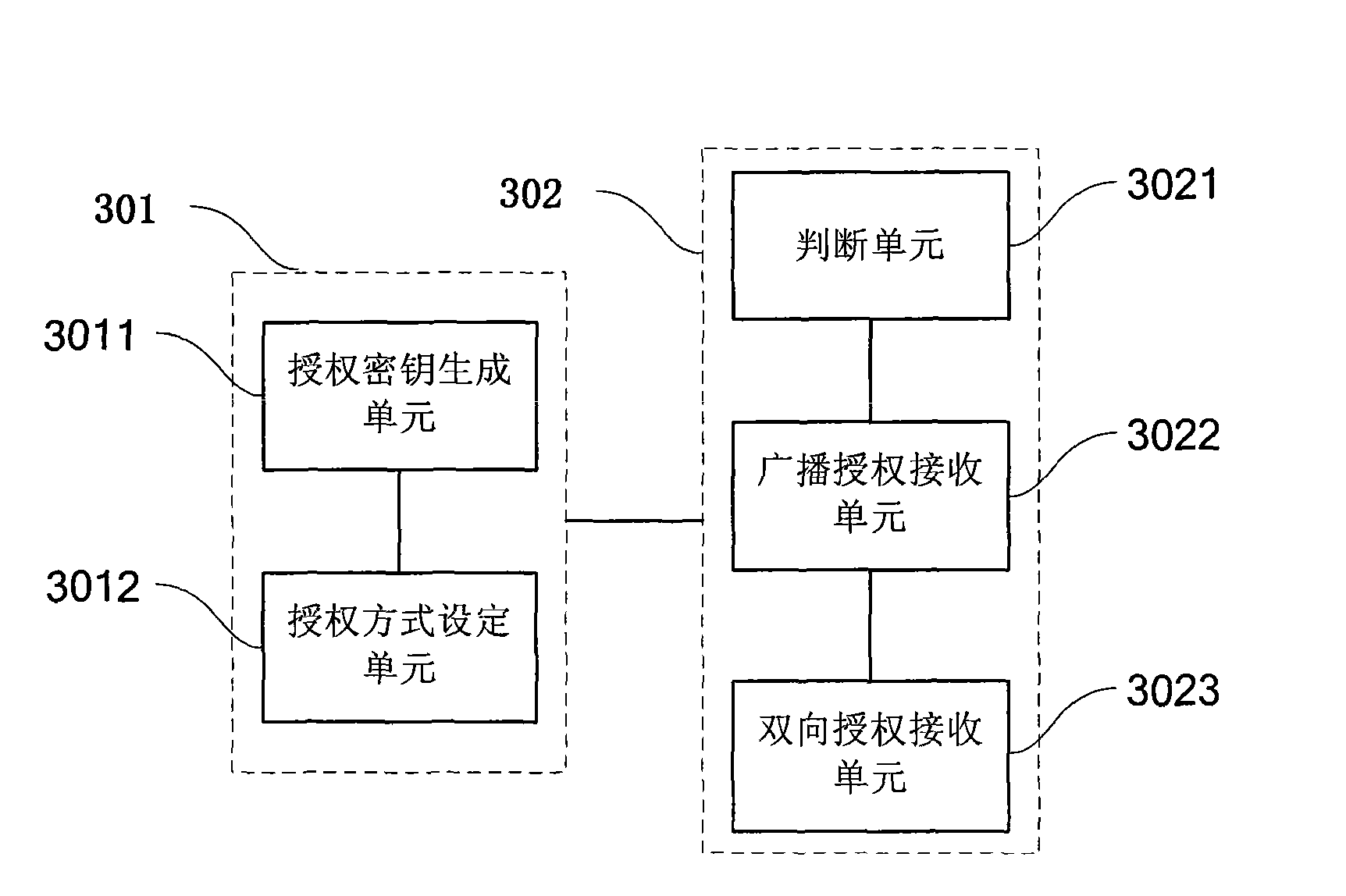
InactiveCN101582729AImprove authorization efficiencyImprove experienceHigh level techniquesBroadcast systems controlAuthorization ModeConditional access
The invention provides a method and a system for acquiring a service key. The method comprises the following steps: a subscriber terminal acquires authorization directing at the present type of service from the network terminal; the authorization is set based on the type of service; if the authorization is broadcasting authorization, the subscriber terminal receives an authorization key from the network terminal by means of broadcasting authorization; if the authorization is bidirectional authorization, the subscriber terminal receives the authorization key from the network terminal by means of bidirectional authorization; wherein, the authorization key is generated by the network terminal based on service information. The invention further provides a conditional access module and the subscriber terminal. In the invention, the subscriber terminal which has broadcasting authorization and bidirectional authorization combines the advantages of the two authorizations, satisfies the need of different subscribers flexibly, improves the subscriber authorization efficiency, promotes subscriber experience and saves resources and power dissipation.
Owner:新奇点智能科技集团有限公司
Boolean keyword searchable encryption method supporting large-scale user groups
PendingCN114357477AFlexible controlFlexible AuthorizationDigital data information retrievalDigital data protectionBoolean matchingEngineering
The invention discloses a Boolean keyword searchable encryption method supporting a large-scale user group, which realizes flexible access strategy matching and fine-grained access control on the premise of facing large-scale users based on a recursive attribute set structure, an access tree structure and a recursive keyword set structure. Firstly, a more flexible data user attribute organization mode and more flexible access strategy matching are supported, and more efficient access control is achieved. According to the method, the access tree is used for representing the access strategy, and the data user attributes are organized in a recursive collection structure, so that more efficient access strategy matching is realized. In addition, the method also supports a more flexible keyword organization mode and Boolean keyword retrieval. According to the method and the device, the keywords are organized into the recursive set, and flexible keyword organization and Boolean keyword search are realized through a Boolean matching operation method.
Owner:SOUTH CHINA UNIV OF TECH
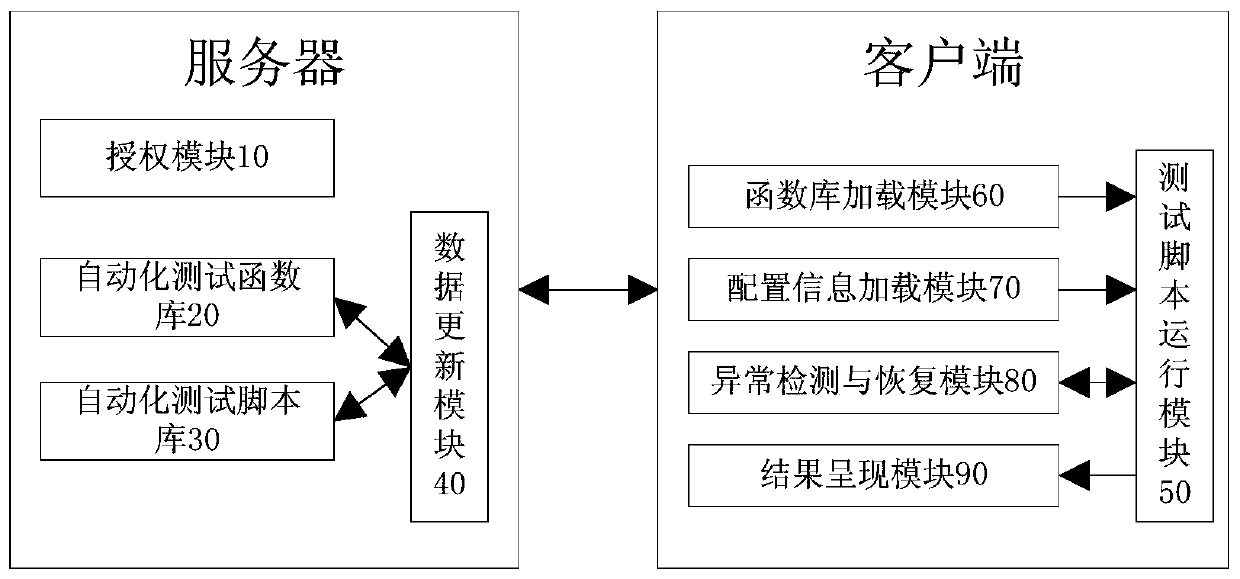
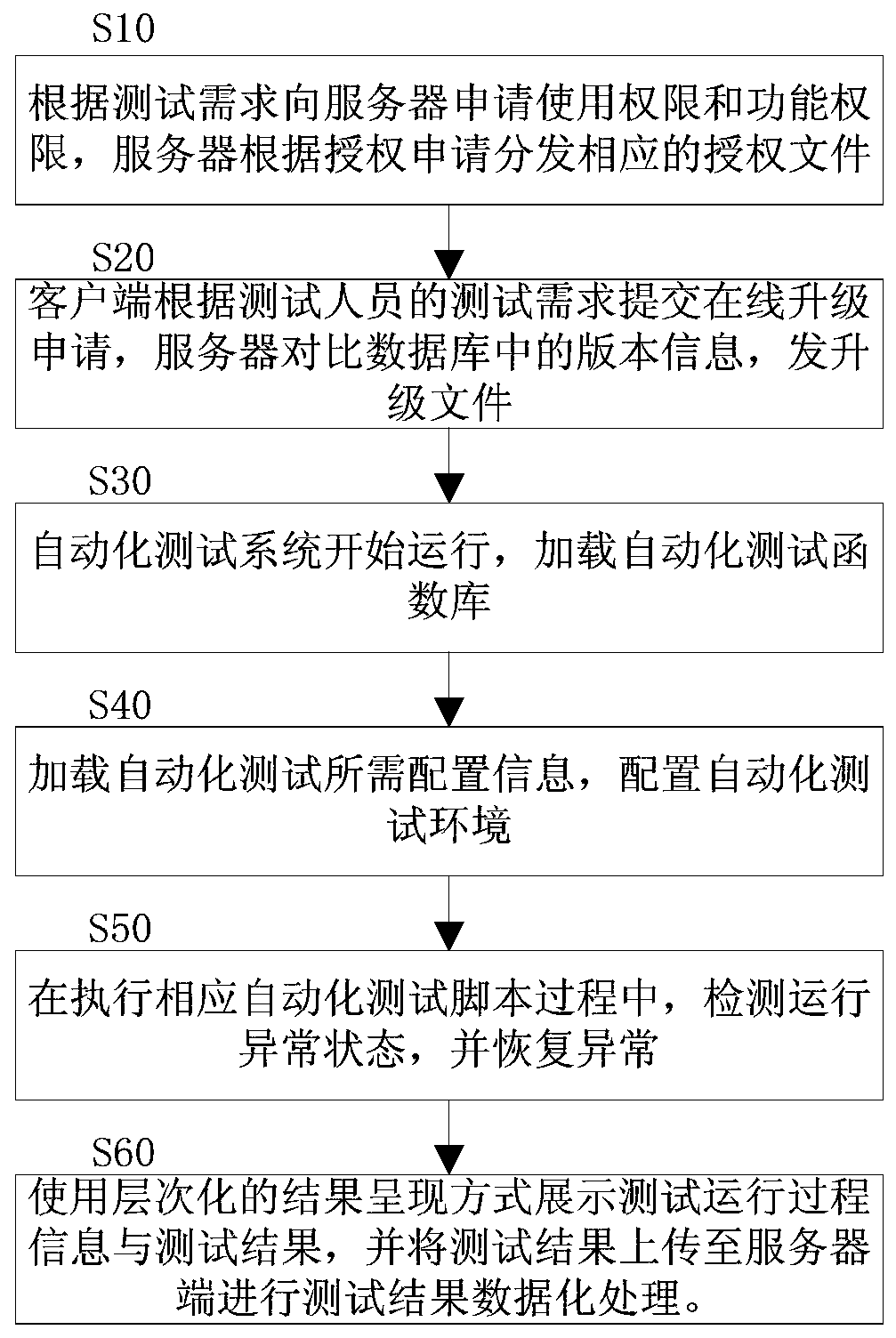
A kind of automatic test system and method for CS architecture communication equipment
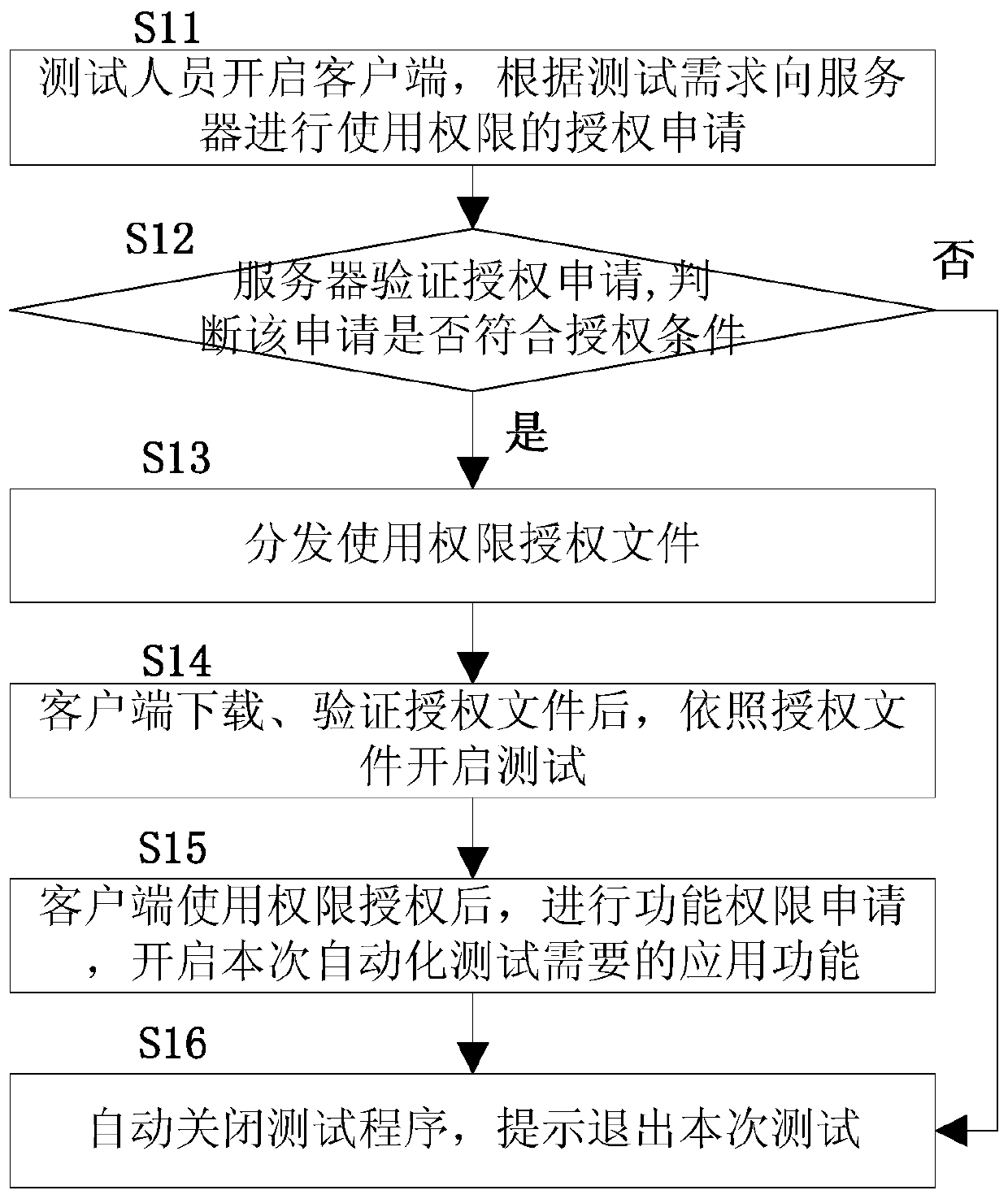
ActiveCN106789393BFlexible AuthorizationImprove convenienceData switching networksTest scriptTest requirements
The invention discloses a system and method for automated testing of CS architecture communication equipment. The method includes: testers apply for use authority and function authority to a server according to test requirements, and the server distributes corresponding authorization documents according to the authorization application; The test needs to submit an online upgrade application, the server compares the version information in the database, and sends the upgrade file; the automated test system starts running, loads the automated test function library; loads the configuration information required for the automated test, configures the automated test environment; executes the corresponding automated test script In the process, detect the abnormal state of operation and restore the abnormality; use the hierarchical result presentation method to display the test operation process information and test results, and upload the test results to the server and store them in the test result database. The invention effectively controls the use range of the automated test system, and greatly improves the convenience, timeliness and reliability of deployment.
Owner:FENGHUO COMM SCI & TECH CO LTD
Speaking right queuing queue user authorization method and device
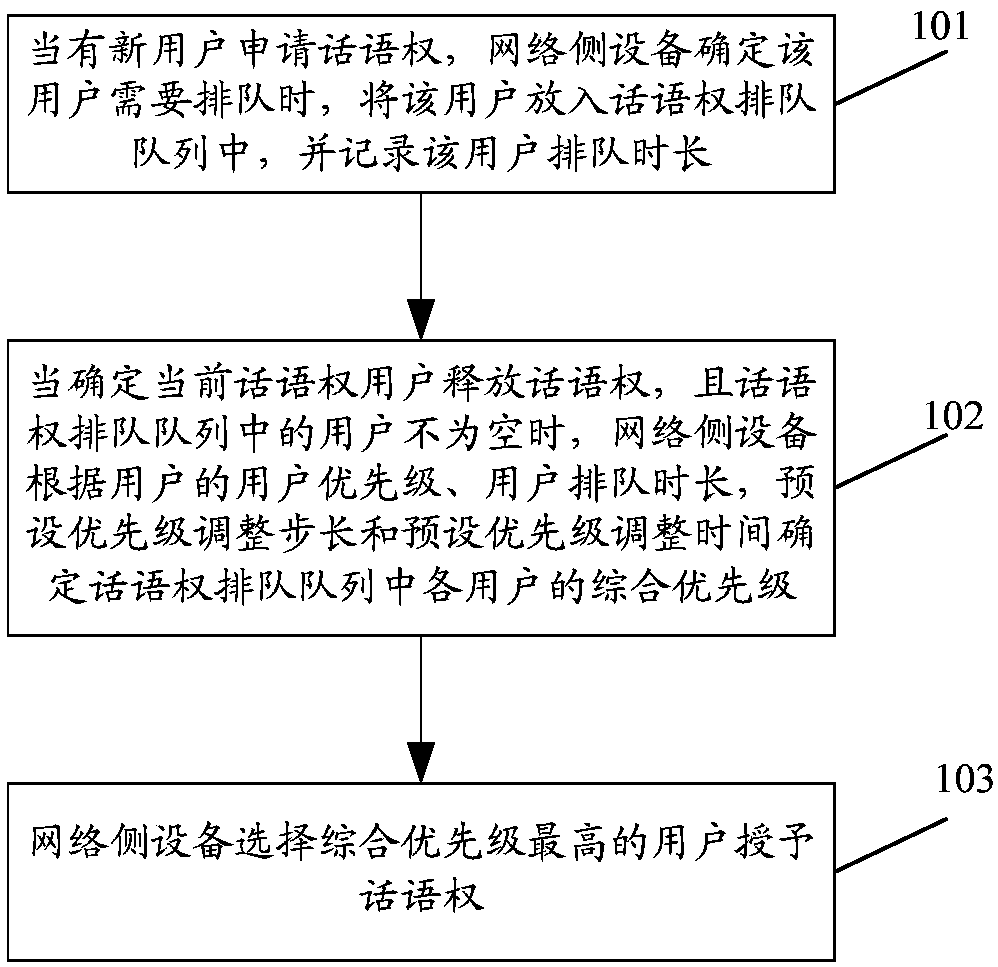
InactiveCN110049454AImprove experienceFlexible AuthorizationBroadcast service distributionUser needsBroadband
The invention provides a speaking right queuing queue user authorization method applied to a broadband cluster system, and the method comprises the steps: when a new user applies for a speaking rightand it is determines that the user needs to queue, putting the user into a speaking right queuing queue, and recording the queuing duration of the user; when it is determined that the current speakingright user releases the speaking right and the user in the speaking right queuing queue is not empty, determining the comprehensive priority of each user in the speaking right queuing queue accordingto the user priority, the user queuing duration, the preset priority adjustment step length and the preset priority adjustment time of the user; and selecting the user with the highest comprehensivepriority to grant the speaking right. The scheme can flexibly authorize the speaking right for users in different application scenarios, and the user experience is improved.
Owner:POTEVIO INFORMATION TECH
Blockchain-based data mutual-trust mutual-sharing intercommunication platform
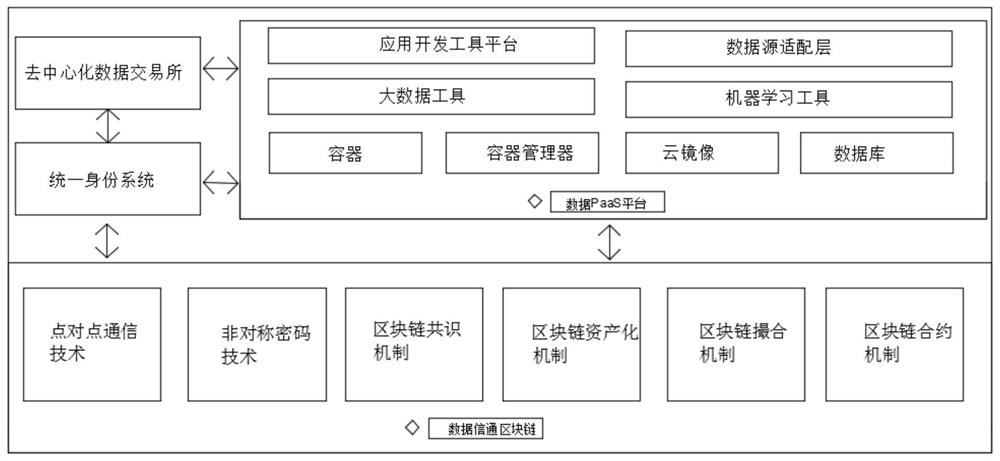
PendingCN112634058ASolve digital assetizationThe only realizationFinanceDatabase distribution/replicationData streamData platform
The invention relates to the technical field of data management platforms, and discloses a blockchain-based data mutual-trust mutual-sharing intercommunication platform, which comprises a blockchain module, a data PaaS platform module, a unified identity system module and a decentralized data exchange module. According to the blockchain-based data mutual-trust mutual-sharing intercommunication platform, based on the blockchain technology, the safety of data is guaranteed, meanwhile, benefit distribution of all parties in the data circulation process is guaranteed, dependence on the data format is reduced, the specification and quality of data opening are guaranteed, and therefore, existing investment is protected to the maximum extent, and the social value of the data is increased; the problems that existing data development and sharing are prone to information leakage, and data rights and interests cannot be effectively tracked and calculated during data circulation can be solved.
Owner:无锡井通网络科技有限公司
Multi-authority group inheritance management method and device based on distributed control
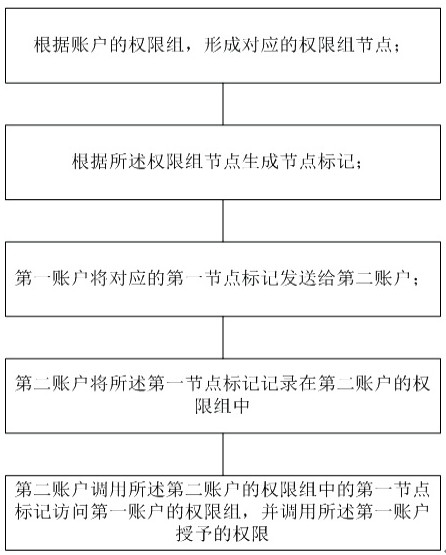
ActiveCN111967036BAvoid Duplicate Permission SituationsThere will be no problem of repeated configurationDigital data protectionTransmissionAuthorizationDistributed computing
The invention discloses a multi-weight group inheritance management method and device based on distributed control. The method comprises the following steps that a corresponding authority group node is formed according to an authority group of an account; node marks are generated according to the authority group nodes; the first account sends the corresponding first node mark to the second account; the second account records the first node mark in an authority group of the second account; the second account calls the first node mark in the second permission group to access the permission groupof the first account, and calls the permission granted by the first account. Authorization between accounts is carried out by using a permission group node mark form; during permission inheritance, an inherited permission can be called by recording a node mark corresponding to a permission group, and therefore the problems that a permission list formed by a traditional permission list recording mode is large in capacity and traditional authorization is inconvenient to manage are prevented; operations of authorization and permission inheritance can be carried out between any accounts through the method, and decentralized distributed operation is achieved.
Owner:成都掌控者网络科技有限公司
A Multi-Keyword Searchable Encryption Method Supporting Numerical Attribute Comparison
ActiveCN108156140BFlexible AuthorizationRapid positioningKey distribution for secure communicationEncryption apparatus with shift registers/memoriesCiphertextTheoretical computer science
The invention discloses a multi-keyword searchable encryption method supporting numerical attribute comparison, the method is used for realizing multi-keyword searchable encryption of numerical attribute comparison under a cloud storage background, establishing an effective ciphertext index through a searchable encryption technology and realizing multi-keyword ciphertext retrieval; the method notonly can quickly locate a ciphertext document which a user is interested in, but also saves bandwidth resource and improves user experience; through an attribute encryption technology of a ciphertextstrategy, the method realizes fine-grained access control, the user can perform ciphertext retrieval only for legitimate data, and 0 coding and 1 coding are executed for a numerical attribute of an access control strategy; and the method can support numerical attribute comparison and has more wide application scenarios.
Owner:XIDIAN UNIV
An access control method and system based on blockchain technology
ActiveCN108123936BImplement Consistency ChecksFlexible authorizationFinancePayment protocolsData privacy protectionAuthorization Mode
An access control method and system based on blockchain technology, which combines blockchain technology with attribute-based access control, including: object attributes are entered into the chain, and based on policies, the judgment process of attributes and policies is bound on all blockchain nodes. Change the access authorization from centralized to distributed, use the consensus mechanism of the block chain to realize the consistency check of the judgment results in the whole network, and permanently record the authorization operation of the access record transaction on the block chain. This method has the characteristics of anti-single point failure, flexible authorization mode, precise access boundary, and auditable records. The present invention is applicable to enterprises, governments, etc. that have data privacy protection requirements and realize multi-branch collaborative work environment based on the block chain platform, and can manage the access rights of users in the system in a dynamic and scalable manner, and realize it around policies and attributes Fine-grained authority management has important practical significance for protecting information system security in a distributed network environment.
Owner:UNIV OF SCI & TECH BEIJING
Electronic passport expansion access control system and authentication method based on identification cipher technology
ActiveCN101504732BFlexible AuthorizationOvercoming loopholes in authorization trust transferUser identity/authority verificationCo-operative working arrangementsBiometric dataControl system
Owner:WUHAN TIANYU INFORMATION IND
Internet printing security management system for U disk
InactiveCN108874329AStrict managementFlexible AuthorizationDigital output to print unitsSafety management systemsDatabase server
The invention discloses an internet printing security management system for a U disk, comprising a first client (1), a firewall (2), a first router (3), a database server (4), a central server (5), asecond client (6), a second router (7), and a management machine (8), wherein U disk protection walls (9) are provided in both the first client and the second client, the first client is in communication connection with the firewall via the internet (10), the firewall is in communication connection with the first router, the second client is in telecommunication connection with the second router,the second router is in telecommunication connection with the management machine, the second router is in communication connection with the firewall through a VPN gateway (11), the first router is incommunication connection with the database server and the central server respectively through an internal network (12). According to the internet printing security management system for the U disk, the system can achieve transparent encryption and high strength, and prevent data leakage and the loss and destruction of the U disk.
Owner:安徽心驰信息科技有限公司
A traffic authorization method for ocs, ocs, server and readable storage medium
ActiveCN109995539BMeet actual traffic business needsEnhance traffic service experienceMetering/charging/biilling arrangementsService experienceTerminal equipment
Owner:CHINA MOBILE GROUP JILIN BRANCH +1
An attribute reconstruction encryption method and system for permission chain data sharing and supervision
ActiveCN113127927BProtect privacy and securityEffective supervisionFinanceDigital data protectionPersonalizationCiphertext
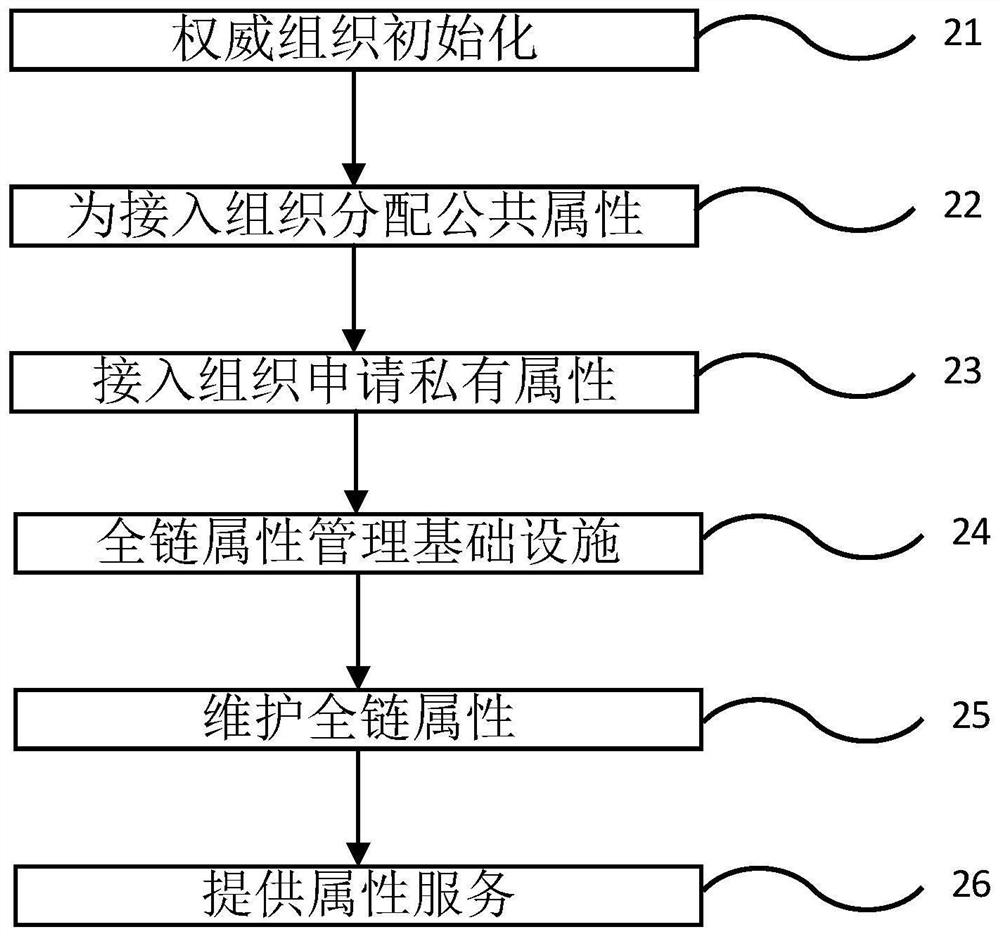
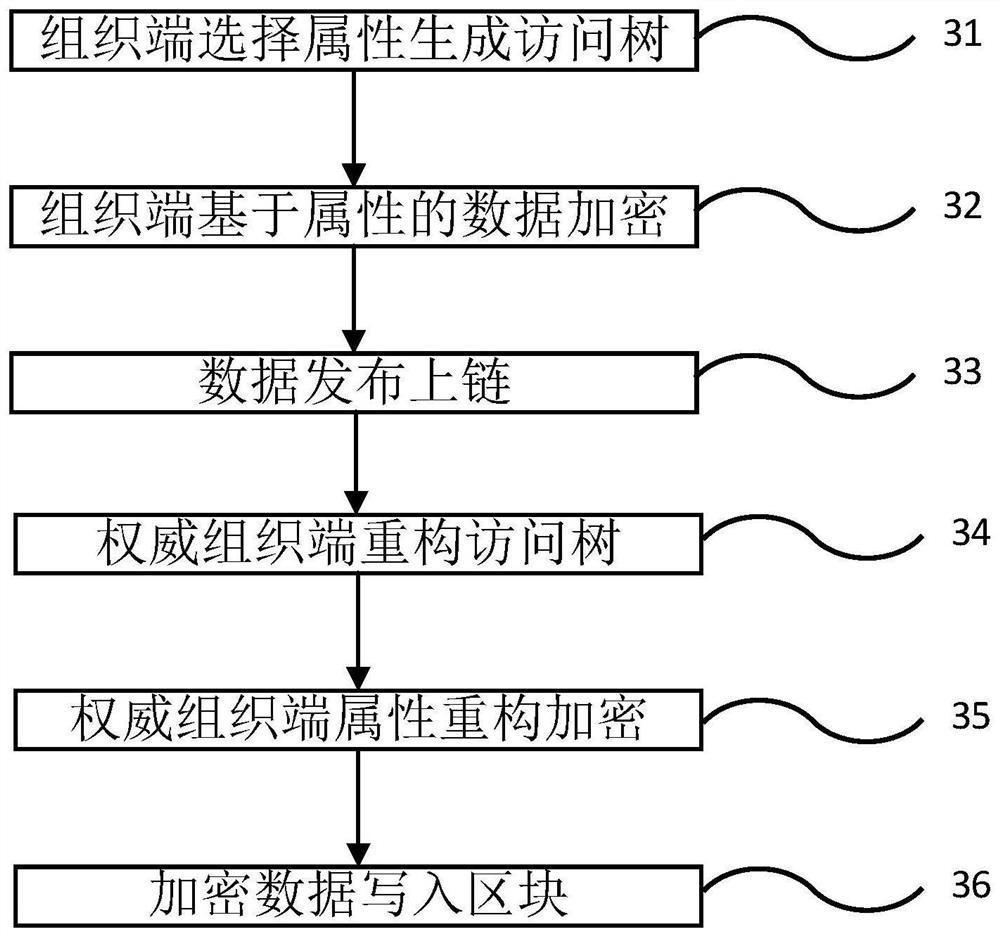
The invention belongs to the technical field of block chains, and discloses an attribute reconstruction encryption method and system for permission chain data sharing and supervision. Its characteristics include that the permission chain authoritative organization acts as a data supervision organization to build an attribute management infrastructure for managing the attributes of the entire chain; the access tree submitted by the data release organization is reconstructed into a standardized access tree under the attribute management infrastructure; The standardized standard access tree trans-encrypts the ciphertext submitted by the organization, and converts personalized encryption and access control into full-chain standardized encryption and access control. This application can protect the privacy and security of uplink data through the cryptographic algorithm and license chain technology based on attribute encryption, realize fine-grained and flexible authorization of data, and use the invented attribute reconstruction encryption method and system to realize efficient encryption of encrypted data Supervision.
Owner:TAISHAN UNIV
vsim authorization method, device and system
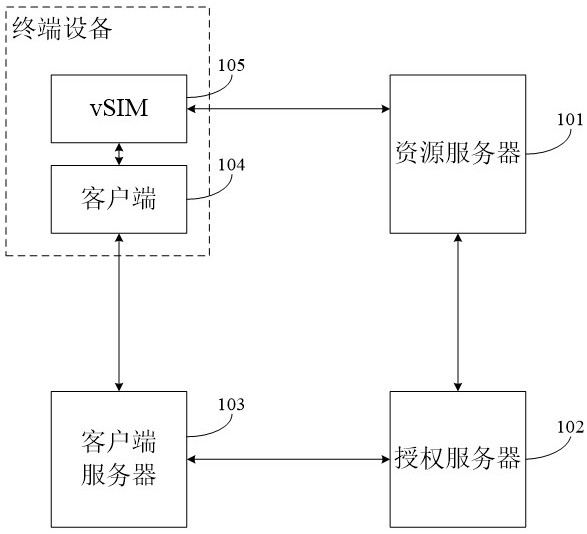
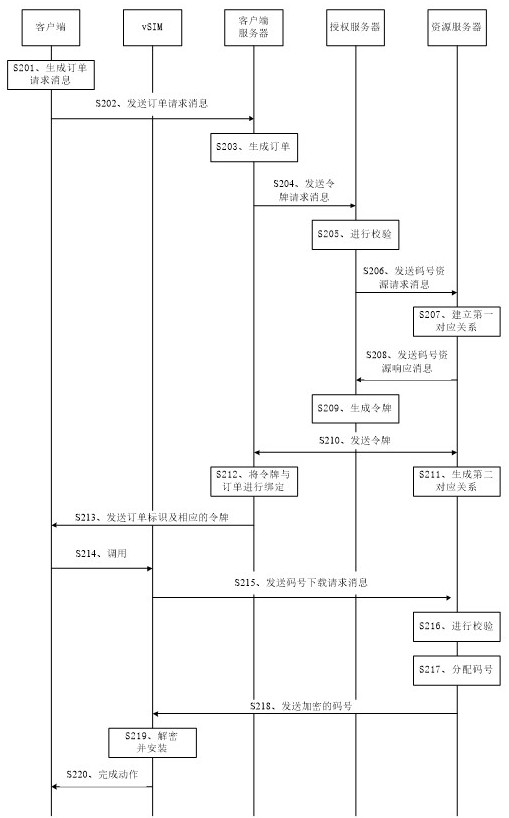
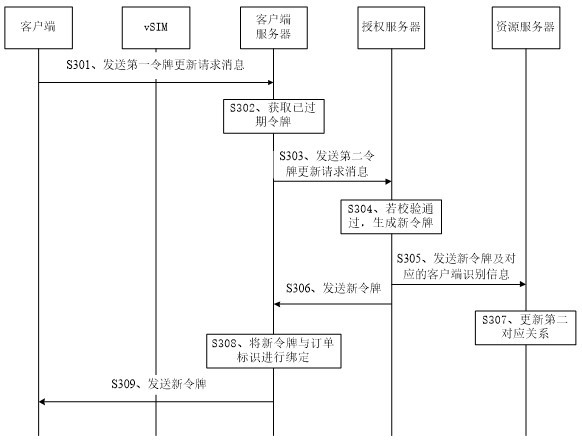
ActiveCN112153630BAuthorization securityFlexible AuthorizationSecurity arrangementNetwork data managementEngineeringAuthorization
Owner:SHENZHEN JETLINK TECH CO LTD
Authorization processing method and device
ActiveCN105763522BFlexible authorizationPermission display is not intuitiveDigital data authenticationTransmissionAuthorization ModeEngineering
Disclosed are an authorization processing method and apparatus. The method comprises: organizing resource nodes to be authorized into a tree structure or a hierarchical structure; performing appointed authorization on an operation set selected from the resource nodes to be authorized; and subordinate nodes of the resource nodes subjected to appointed authorization in the tree structure or the hierarchical structure inheriting the operation set of the authorized resource nodes. By the means of the present invention, at least one of the following problems, such as an inflexible authorization method, non-visual authority displaying and a large authority quantity during role authorization in the relevant art is solved, so that the effects of providing a flexible authorization method, visual authority displaying and better authority storage method are achieved.
Owner:ZTE CORP
A static authorization method for SQL analysis query
ActiveCN106383855BFlexible AuthorizationAccurate authorizationDigital data information retrievalSpecial data processing applicationsData accessData profiling
The invention provides a static authentication method capable of aiming at SQL (Structured Query Language) analytical query. The method comprises the following steps of: S1: obtaining the SQL analytical query submitted by a user; S2: constructing a genealogical tree from the SQL analytical query; S3: on the basis of the genealogical tree, extracting a data access request of the SQL analytical query; and S4: on the basis of an access control rule, authenticating the data access request. Compared with an existing database access control technology, the static authentication method combines the characteristics of the analytical query to support simultaneous access to a plurality of columns and control for an operation. Therefore, by use of the method, the SQL analytical query can be more flexibly and accurately authenticated. Meanwhile, by use of the method, an administrator is permitted to carry out permission management through the compiling of the access control rule, in addition, no extra burdens are brought to users, and therefore, the static authentication method exhibits better availability. Finally, the method carries out authentication only on the basis of the SQL analytical query, so that an authentication process is more efficient, and the method is suitable for a large-scale data analysis scene.
Owner:TSINGHUA UNIV
Internet of things software function module authorization method and system
ActiveCN103906054BFlexible authorizationAuthorization method securitySecurity arrangementRelevant informationThe Internet
The invention provides a method and system for authorization of software function modules of the internet of things. The system for authorization at least comprises at least one terminal device, an operator operation platform communicated with the terminal device through a first network and an authorization authentication server communicated with the operator operation platform through a second network. The terminal device is used for starting an authorization procedure and can form a uniqueness mark through acquisition of relevant information and authorize the corresponding function module according to returned first authorization code information. The operator operation platform is used for processing authorization requests and the like of the terminal device. The authorization authentication server is used for managing secret keys of the terminal device and the operator operation platform and automatically generating the first authorization code information, second authorization code information and the like according to the uniqueness mark. According to the method and system, independent authorization can be conducted according to functions and function points of software, the version safety of the software is guaranteed, authorization is achieved according to the requirements, version management conducted by an operator is facilitated, and the operator can know the application condition of the software so as to further improve the software.
Owner:上海农业信息有限公司 +2
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com