A static authorization method for SQL analysis query
A static and query statement technology, applied in the database field, can solve problems such as large overhead, restrictions, and does not support simultaneous access to multiple columns, and achieve the effect of efficient and accurate authorization in the authorization process
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] The present invention proposes a static authorization method for SQL analysis and query, which is described as follows in conjunction with the accompanying drawings and embodiments.
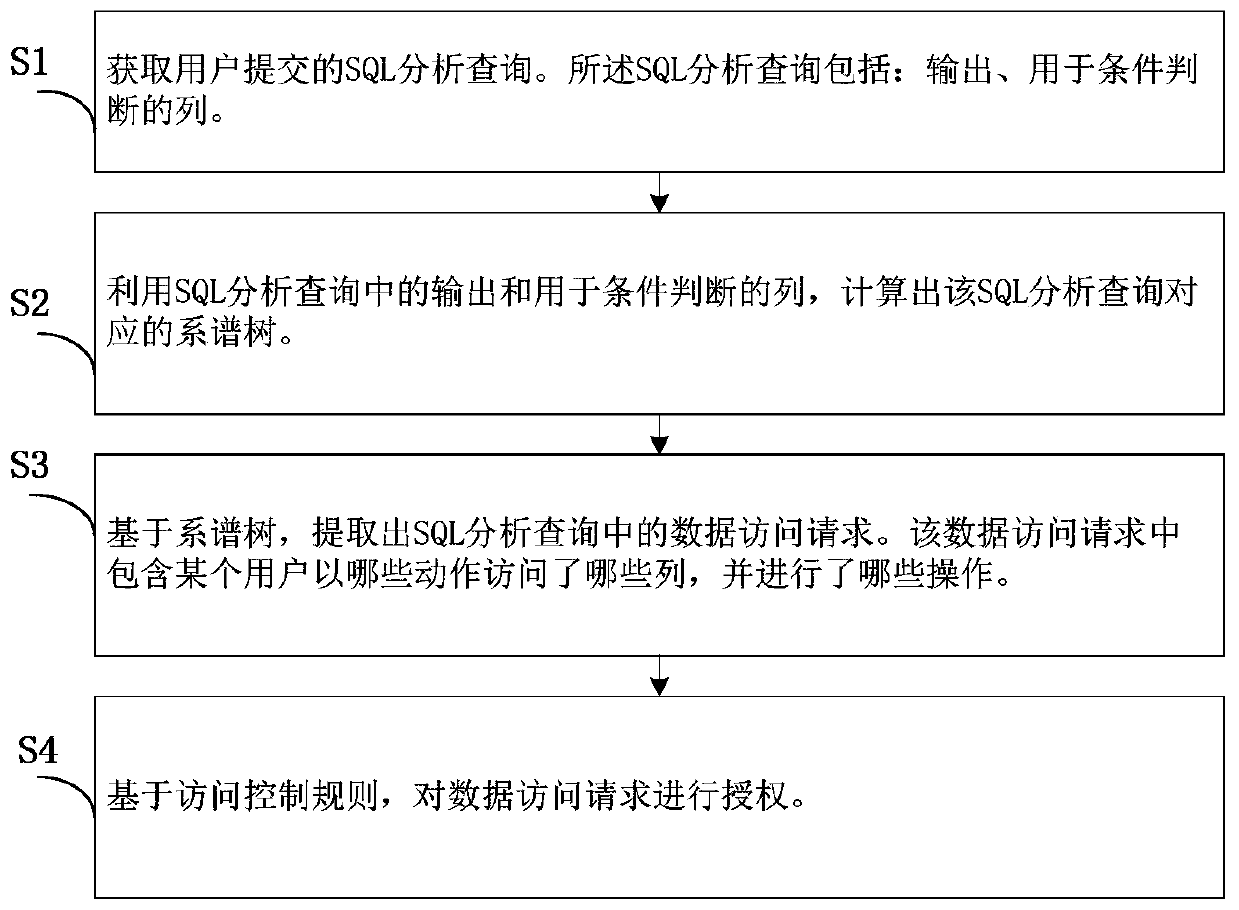
[0029] Such as figure 1 As shown, the method includes the following steps S1-S4.
[0030] S1: Get the SQL analysis query submitted by the user. The SQL analysis query includes: output and a column for condition judgment.
[0031] Intercept, analyze and authorize SQL analysis queries before they are executed. When the authorization is successful, the SQL analysis query continues to be executed; otherwise, the SQL analysis query will be blocked and returned to the user for modification.
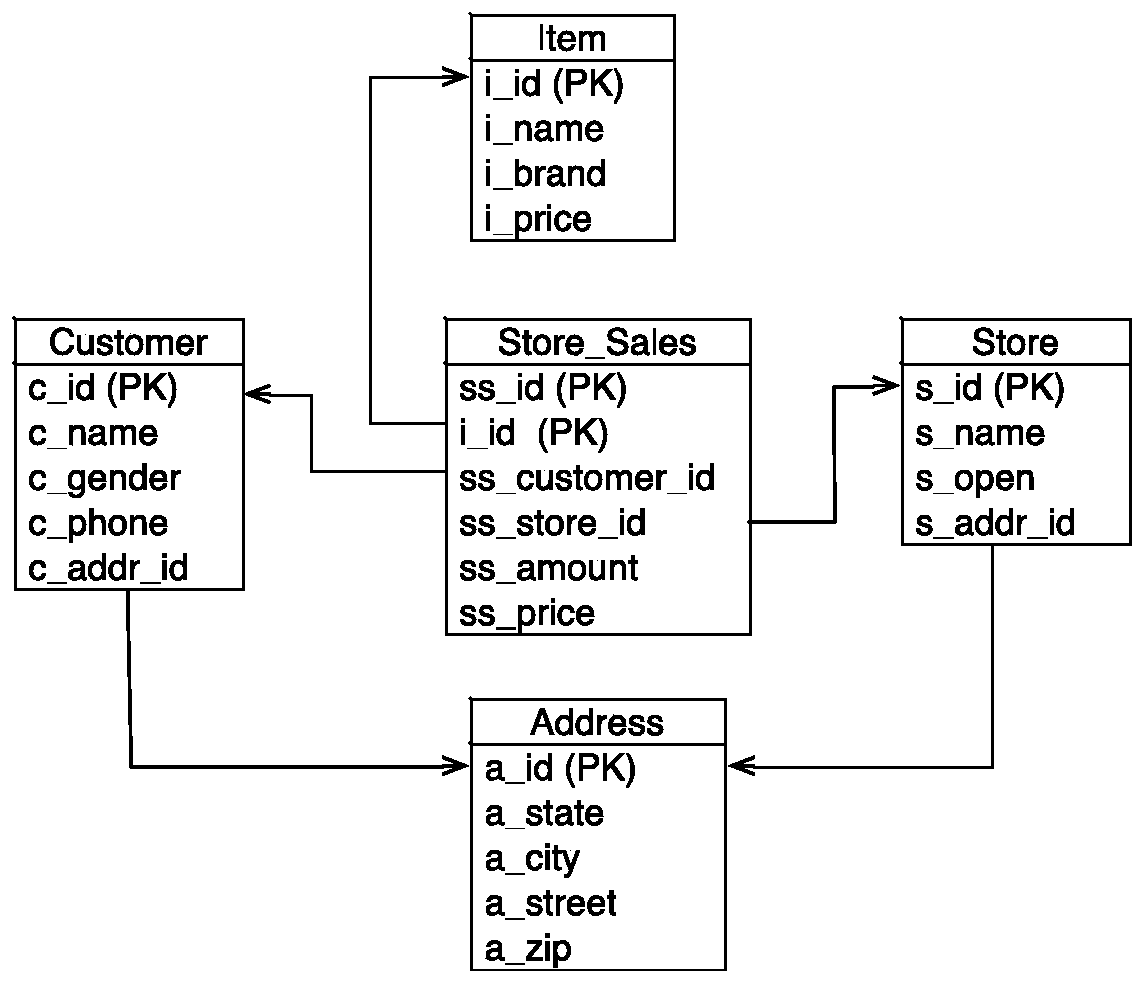
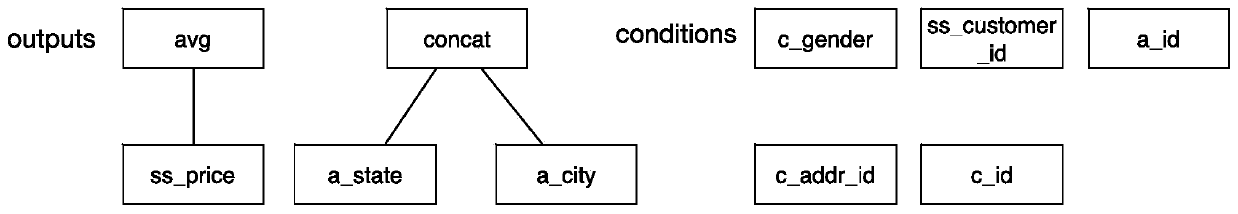
[0032] S2: Calculate the genealogy tree corresponding to the SQL analysis query by using the output in the SQL analysis query and the columns used for condition judgment. A genealogy tree is a tree consisting of columns and transformation operations in database tables, where leaf nodes are columns and n...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com