Device access authentication system and method based on KMS
A technology for device authentication and device access, which is applied in transmission systems, electrical components, etc., can solve problems such as spending a lot of time and cost, public keys are easy to leak, etc., and achieve the effect of convenient operation and flexible authorization
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] The present invention will be further illustrated below in conjunction with the accompanying drawings and specific embodiments.
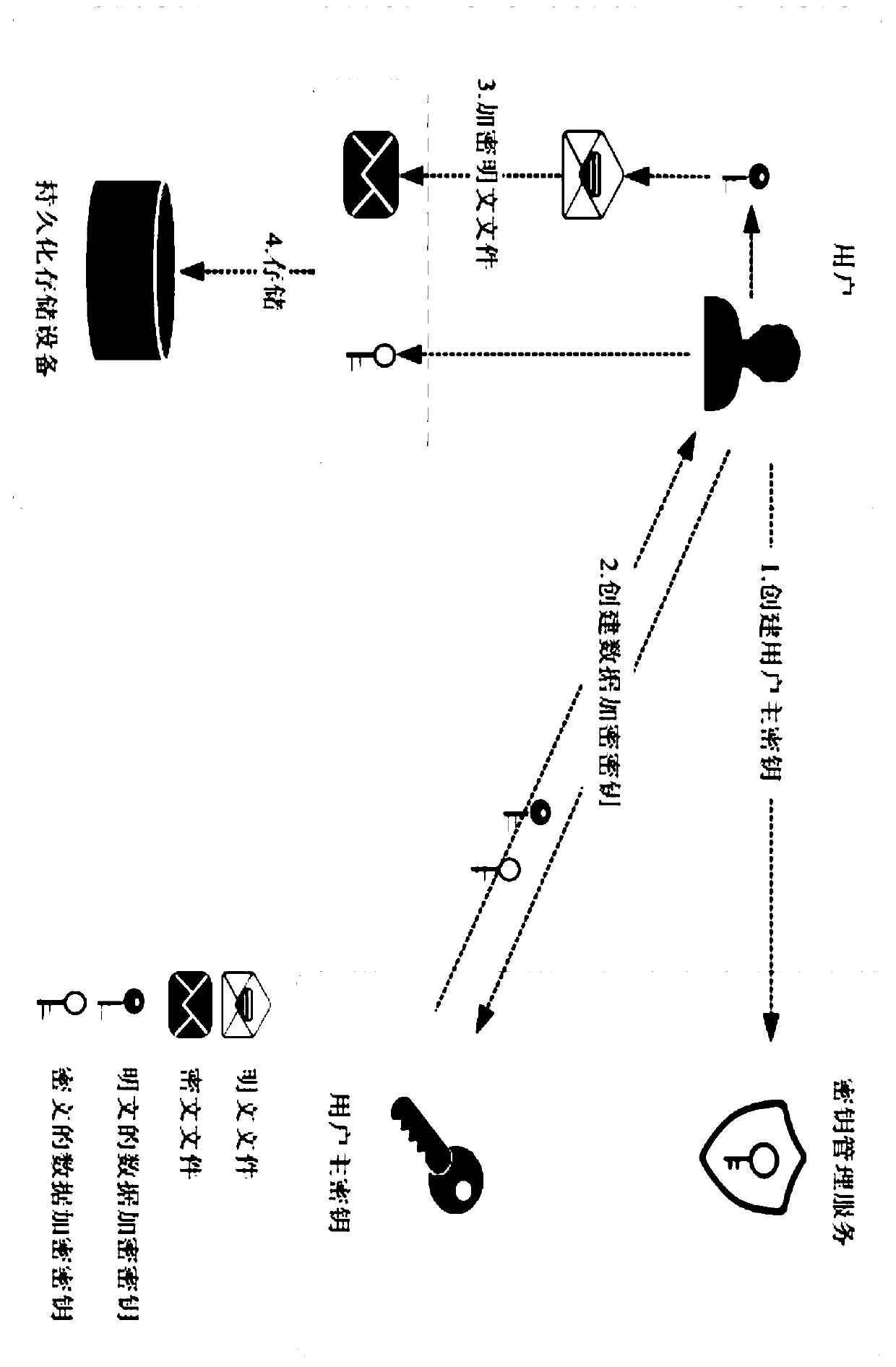
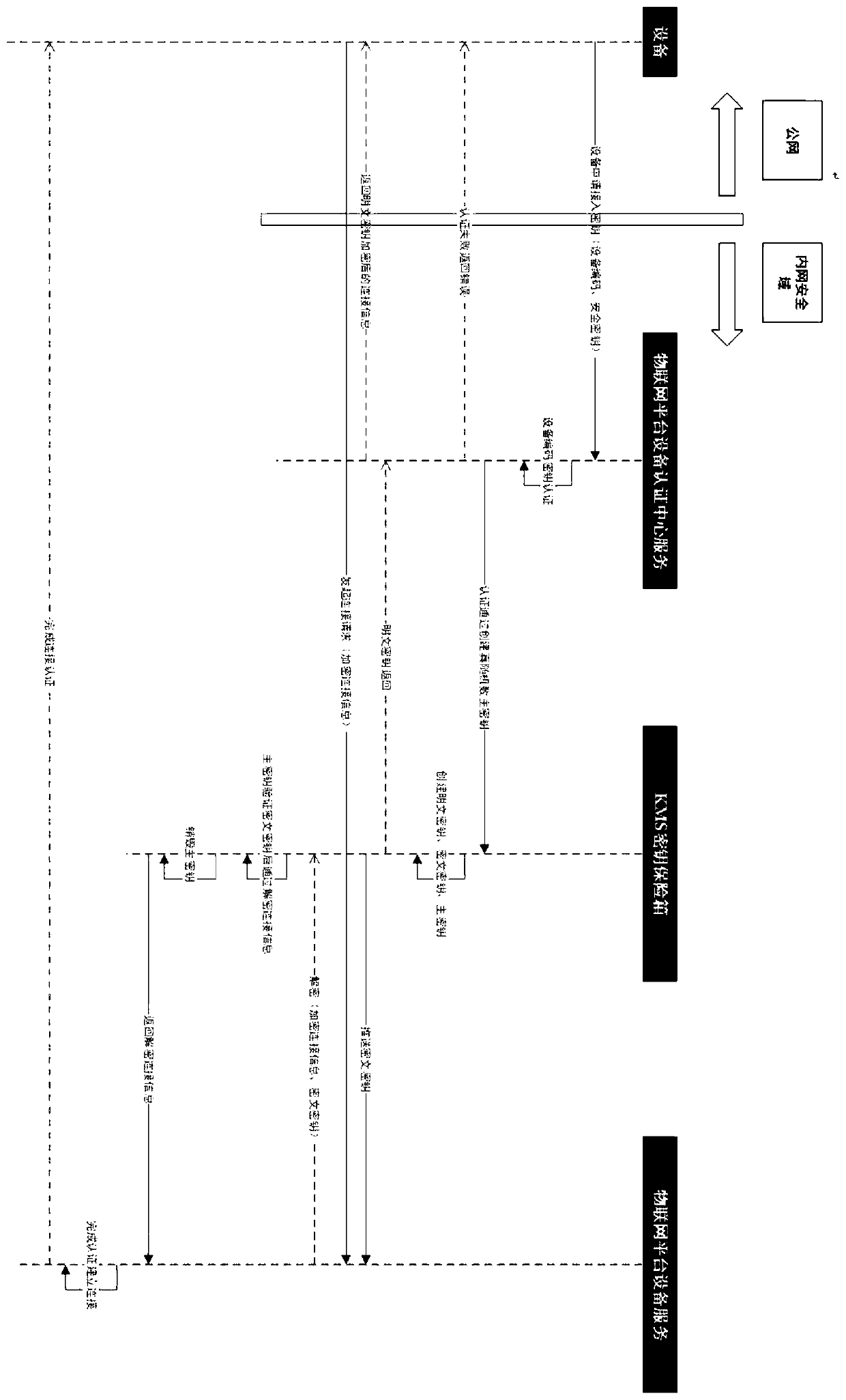
[0021] figure 1 It is a structure diagram of the present invention. like figure 1 As shown, the KMS-based device access authentication system of the present invention includes a device authentication center server, a KMS key safe, a device server, and a device terminal. The device authentication center server, the KMS key safe, and the device server communicate through an intranet connected, and the device end communicates with the device authentication center server and the device server through the public network respectively.
[0022] The device authentication center server creates an AK key and distributes it to the device; the device carries the AK key request to access the device authentication center server, and the device authentication center server authenticates the AK key of the device, and if the authentication passes, the devic...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com