Boolean keyword searchable encryption method supporting large-scale user groups
An encryption method and keyword technology, applied in the field of cryptography, to achieve the effects of strong security, good practicability, and flexible access policy expression
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
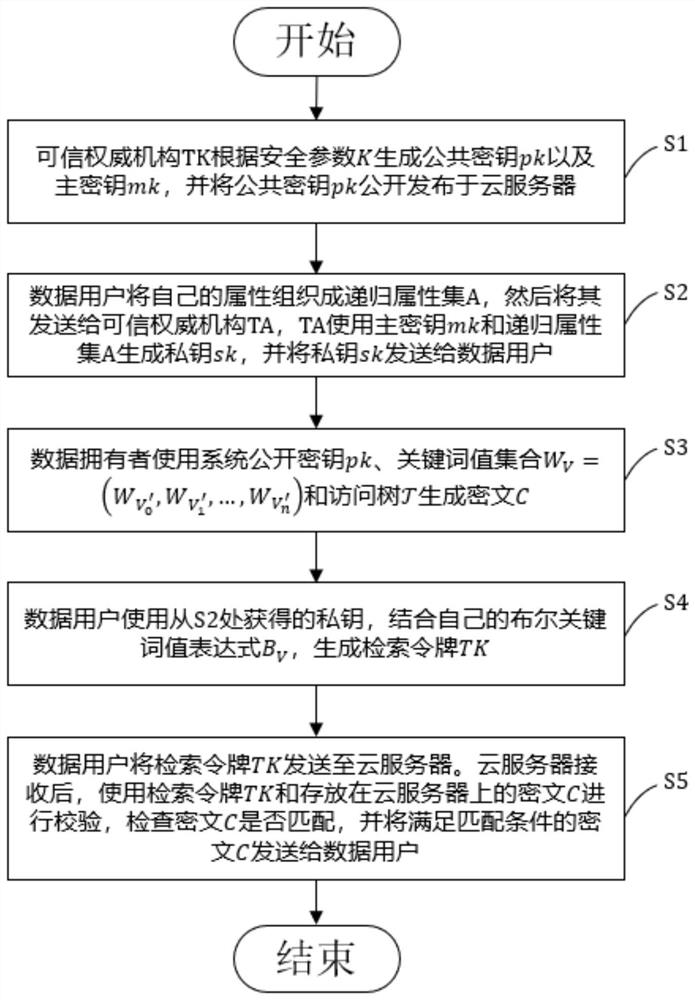
[0060]Flexible access policy matching can help data owners to manage data flexibly. Most of the existing work adopts access policies represented by Access Tree or Linear Secret Sharing Schemes (LSSS for short); users The expression of attributes can support more fine-grained access control. Most of the existing work combines user attributes in the form of strings, or combines attributes into a single attribute set or recursive attribute set structure; flexible keyword search It can bring flexible choices to the search of data users. The existing solutions mainly support one of the following three search methods: matching search, connection keyword search and Boolean keyword search. Among them, the flexibility of matching search is the worst, and Boolean keyword search is the most flexible. Keyword search flexibility is the best.
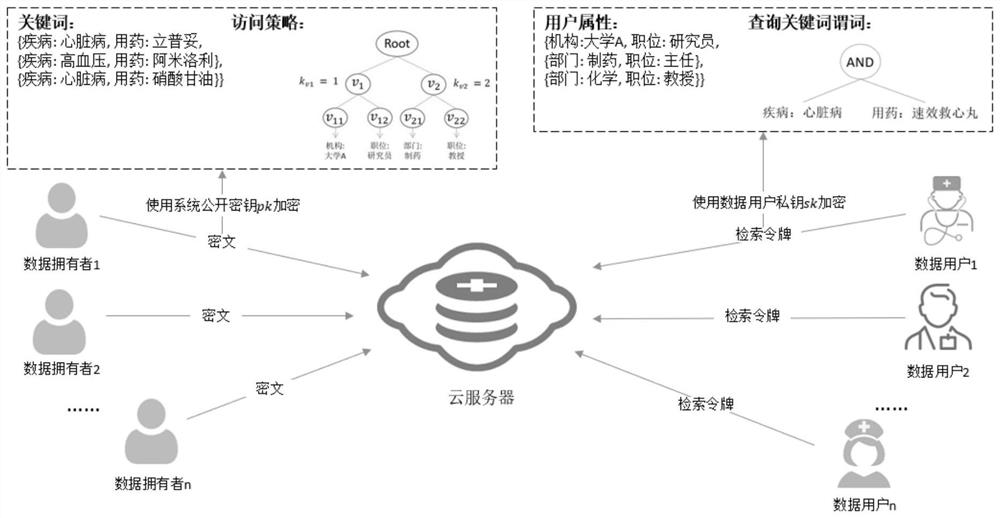
[0061] In actual application scenarios, the attributes of data users are very complex. For example, data user A can be a researcher at university A,...
Embodiment 2
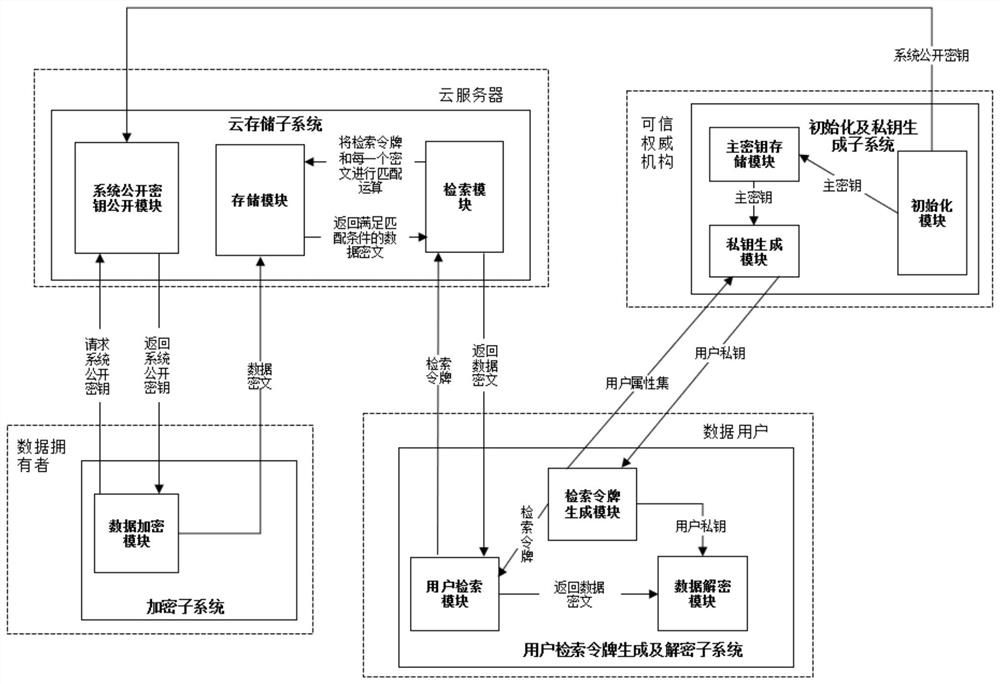
[0122] like image 3 As shown, the present embodiment continues to provide a large-scale user-oriented Boolean keyword ciphertext retrieval system, including the following four parts: the cloud storage subsystem running on the cloud server; the encryption subsystem running on the data owner; The user retrieval token generation and decryption subsystem at the data client end; the initialization and private key generation subsystem running on the trusted authority TA.
[0123] Wherein, the initialization and private key generation subsystem running on the trusted authority TA includes the following modules: an initialization module, a master key storage module and a private key generation module. Among them, the initialization module is used to generate the system public key and the master key, and publish the system public key to the cloud server, save the master key to the master key storage module, and the master key storage module is used to store the master key key, which ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com