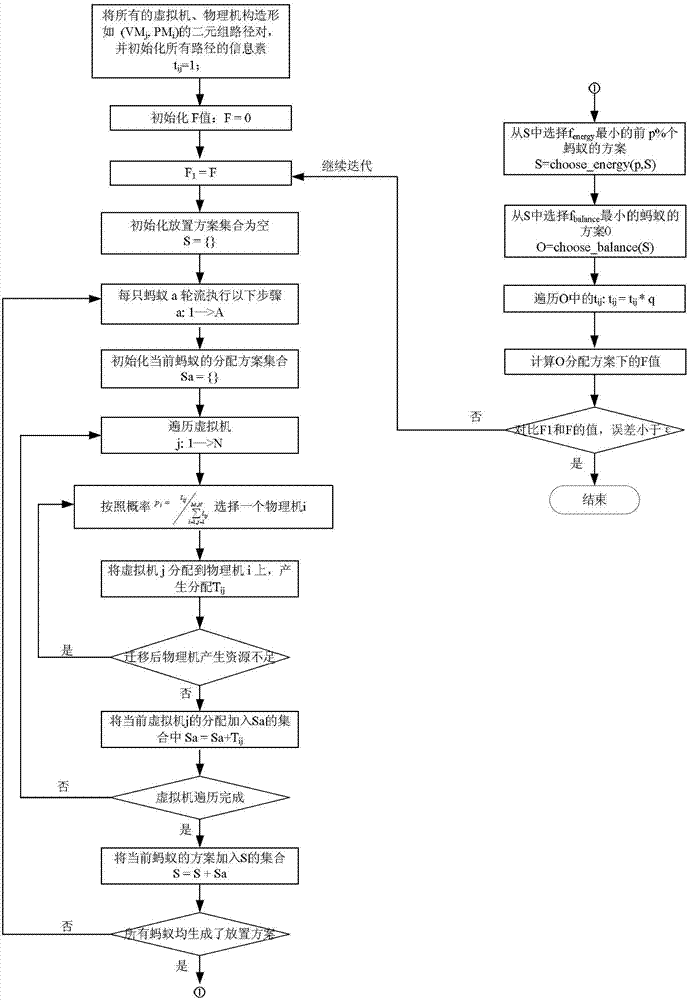
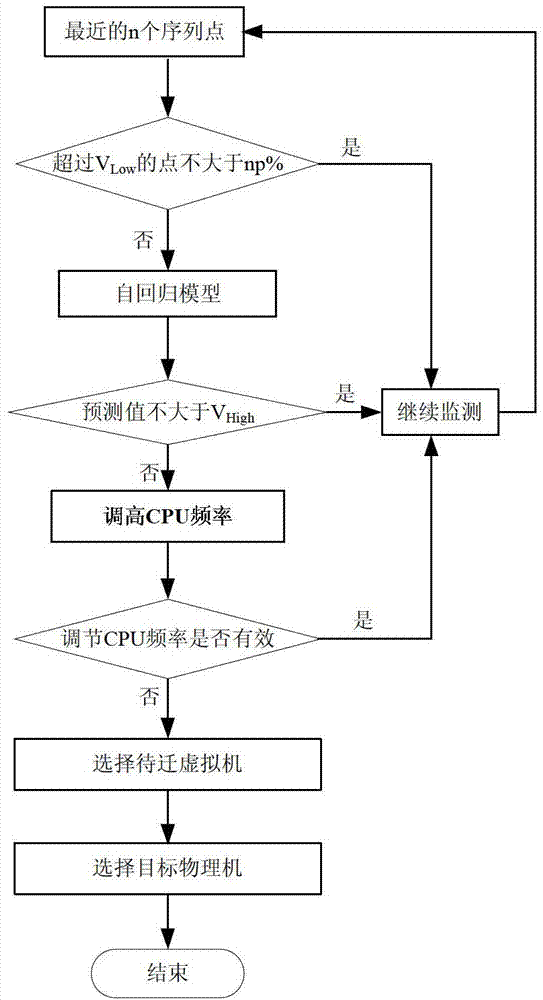
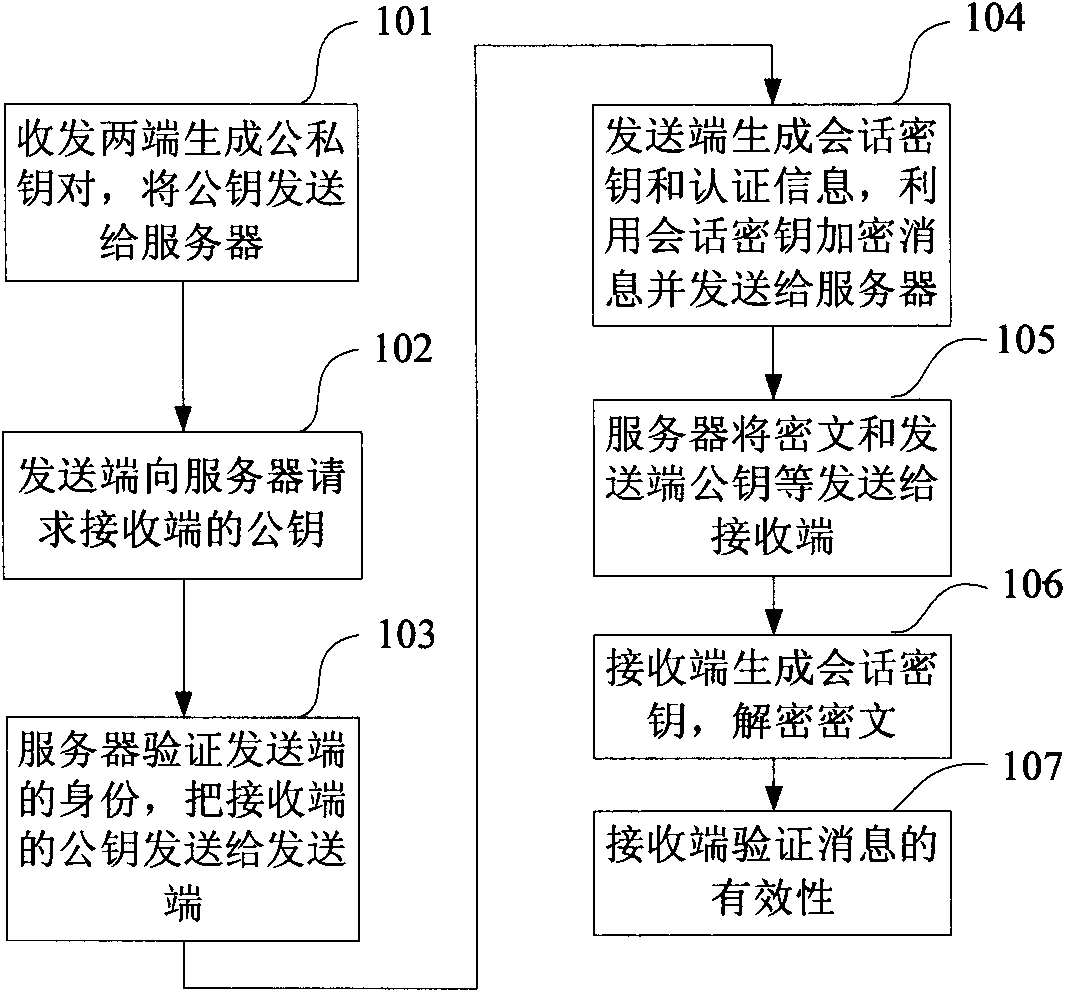
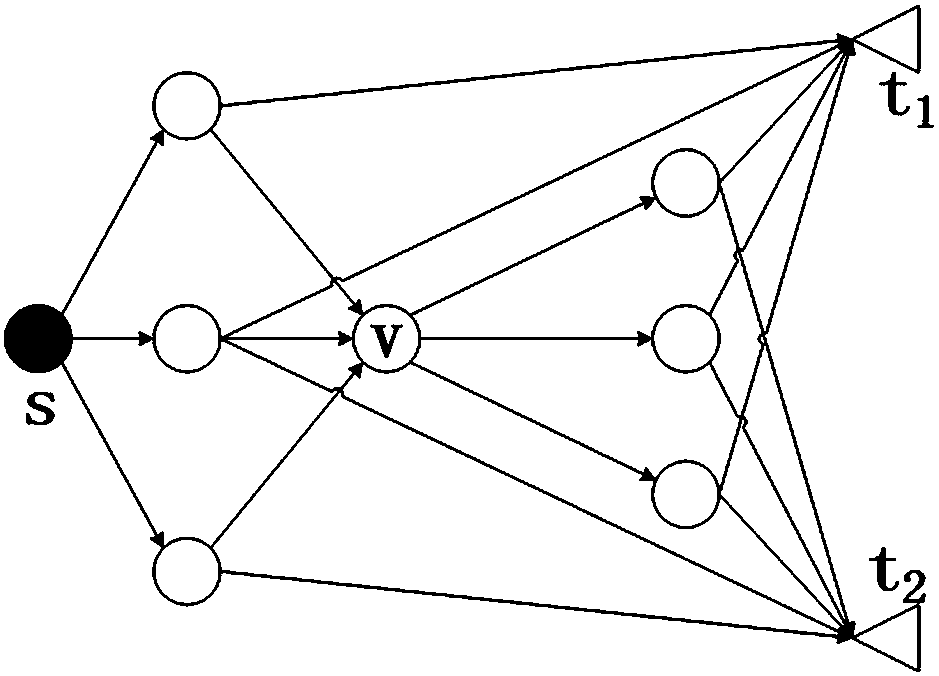
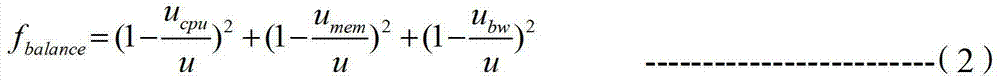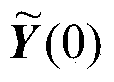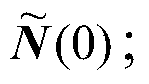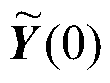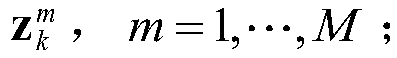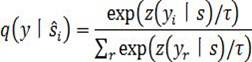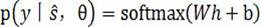Patents
Literature
70results about How to "Reduce transmission cost" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Data center energy saving method based on central processing unit (CPU) dynamic frequency modulation technology
ActiveCN103488539AGuaranteed real-timeReduce operational overheadEnergy efficient ICTResource allocationData centerDynamic management
The invention relates to a data center energy saving method based on a central processing unit (CPU) dynamic frequency modulation technology. The method includes two stages of initialization arrangement and dynamic management of a virtual machine. The method is different from methods in the prior art, a virtual machine arrangement technology used by energy saving of a data center is divided into the two stages of initialization arrangement and dynamic management. The initialization arrangement is applicable to the occasions of operation beginning and regular integral adjustment of the data center. The adopted method achieves the overall effect and the long-term effect due to time permission. The dynamic management is used for local management or moving facing different tasks during data center operation. The adopted method relates to local resource and ensures real-time performance.
Owner:BEIJING JIAOTONG UNIV
Authenticated encryption method and encryption system based on symmetric encryption
InactiveCN101667913AAchieve authenticationImplement encryptionKey distribution for secure communicationUser identity/authority verificationThird partyCommunications security
The invention discloses an authenticated encryption method and a system, relating to the field of communication security. The restorable signature of a message and the symmetric encryption technologyare combined; a commitment value which only can be calculated by a designated message receiving end is used as a session key encryption message; and the message receiving end validates the validity ofthe message by the restorable signature, thus realizing encryption and authentication in one logical step. A key generation unit of a sending end generates a session key of the sending end; an encryption unit encrypts a message to be sent; the receiving end generates a session key of the receiving end; a decryption unit utilizes the session key of the receiving end to decrypts the encrypted message; and the authentication and confirmation message is generated according to the decrypted message, thus validating the validity of the message. When disputes occur, the message receiving end transforms the authenticated and encrypted message signature into a common signature so as to lead a third party to validate the validity of the signature. The invention has the advantages of high security,low calculated amount and transmission cost, and the like.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
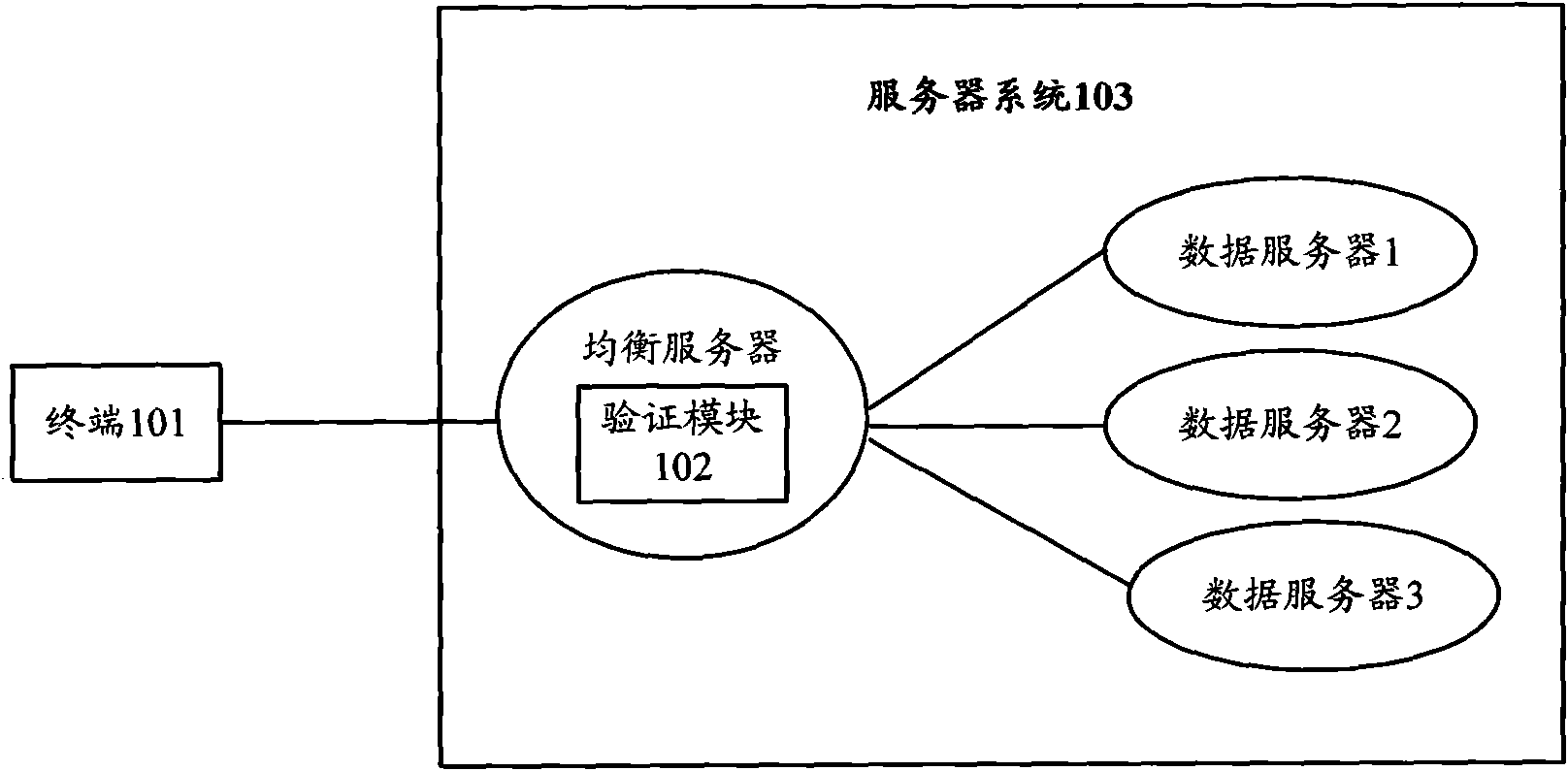
Communication system, equalization server and data verification method
InactiveCN101651719AImprove transmission efficiencyReduce transmission costTransmissionCommunications systemSource Data Verification
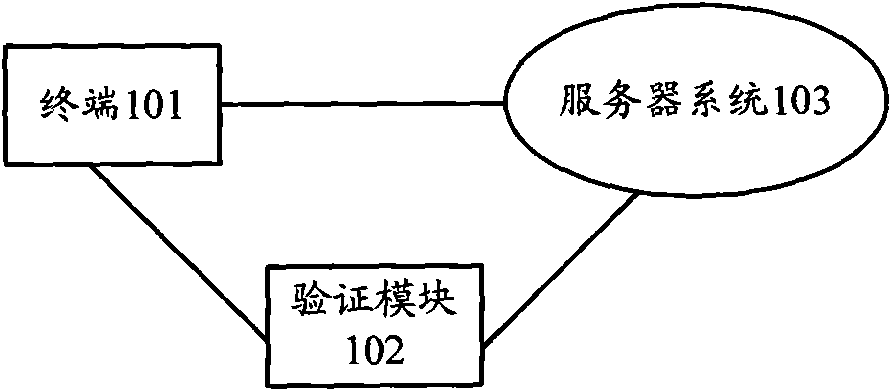
The invention provides a communication system, an equalization server and a data verification method. The method comprises the following steps: after a server system receives a file downloading request transmitted by a terminal, the description information of files is returned to the terminal; the terminal obtains each data block forming the files from the server system according to a file downloading address provided by the received description information; and a verification module obtains an algorithm parameter from the terminal and the server system and calculates the verification code ofeach data block according to a preset algorithm. The description information comprises a verification reference code which is used for verifying the effectiveness of each data block; the verificationmodule is used for comparing the verification code with the verification reference code; if the verification code is identical with the verification reference code, the data block is effective, and otherwise, the data block is ineffective. The technical scheme can effectively reduce information quantity carried by the description information, save the transmitting resources and reduce the transmitting cost for checking the files.
Owner:GUANGDONG YUTIAN TECH +1
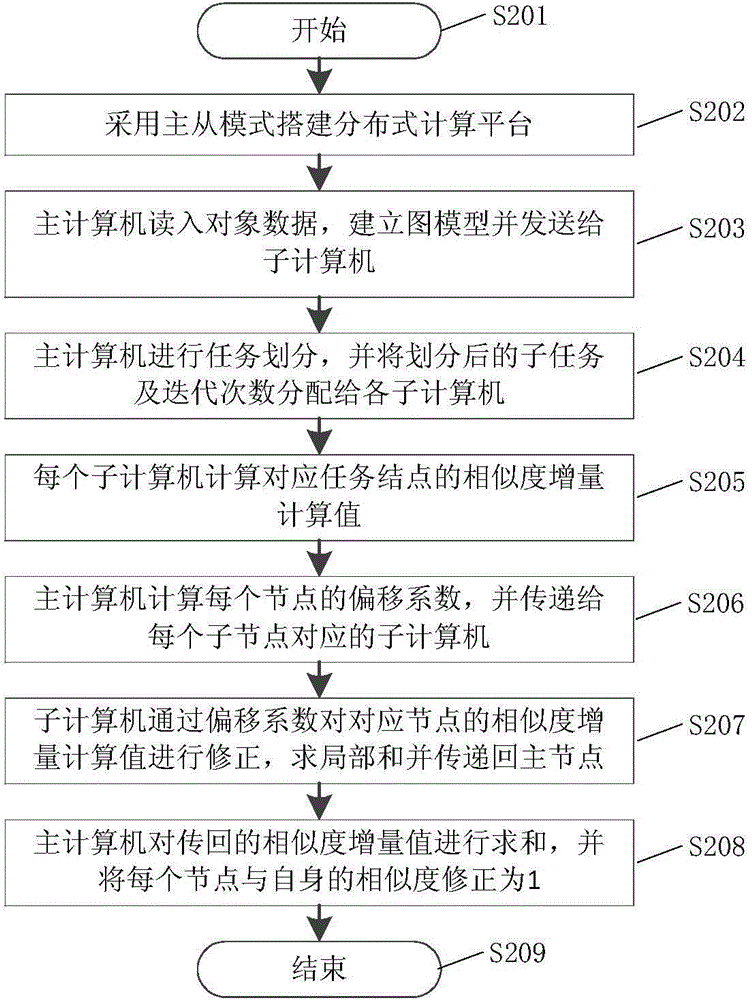
Method for calculating node similarity of chart in distributing manner
ActiveCN104158840AReduce transmission costShort calculation timeData switching networksSpecial data processing applicationsAlgorithmMaster/slave
The invention discloses a method for calculating node similarity of a chart in a distributing manner and belongs to the field of computer data mining. The method comprises the following steps: a distributed calculating platform is built by adopting a master / slave mode, object data is read by a master computer, a graph model is built and sent to slave computers, tasks are divided by the master computer, slave tasks are assigned to the slave computers, the slave computers calculate task nodes and send the calculating results to the similarity incremental calculation values of the node pairs of the graph model respectively, the master computer calculates a deviation ratio and sends the calculating results to corresponding slave computers, the slave computers amend the similarity incremental calculation values of the nodes of local tasks, sum the similarity incremental calculation values and send the calculating results to the master computer, the master computer integrates the similarities of the nodes of the graph model to obtain the similarity of the nodes of the graph model finally. According to the invention, compared with the traditional SimRank calculating method, the transmission cost is low, the calculating time is short, and the efficiency is obviously improved.
Owner:NORTHEASTERN UNIV
Equipment fault three-level bidirectional early warning method and system based on edge computing
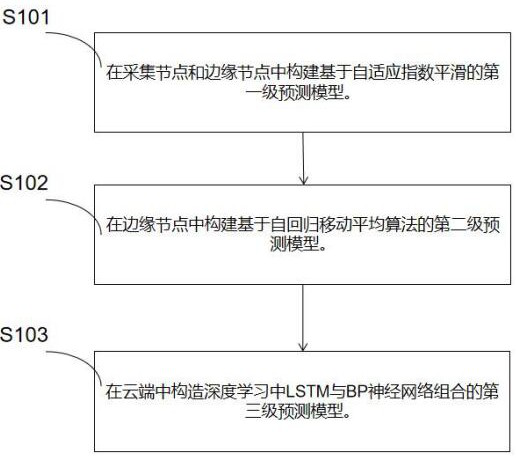
ActiveCN111651312AReduce communication costsReduce false alarm rateDetecting faulty hardware using neural networksHardware monitoringMoving averageAlgorithm
The invention provides an equipment fault three-level bidirectional early warning method and system based on edge computing, and the method comprises the steps: building a first-level bidirectional data sensing prediction model based on an adaptive exponential smoothing algorithm, predicting the data of a collection node, carrying out preliminary screening of a fault signal, uploading the fault signal, and reducing the cost of normal signal transmission; a second-stage bidirectional data perception prediction model of an autoregressive moving average algorithm based on extended Kalman filtering is constructed, and is used for further confirming the accuracy of a fault signal, reducing the false alarm rate and reducing the communication cost between a side end and a cloud end; creating a third-stage bidirectional data perception prediction model based on LSTM and BP neural network combination so that strong computing power is achieved based on edge equipment, he accuracy of data is enhanced, underlying requirements are timely responded, thus reducing time delay of cloud layer transmission. According to the invention, bandwidth and time delay consumed in a data acoustic wave communication transmission process are greatly reduced, and early warning is effectively carried out on a fault signal.
Owner:杭州雪沉科技信息有限公司
Compressed-sensing-based de-artifact fusion method of high-dynamic-range image
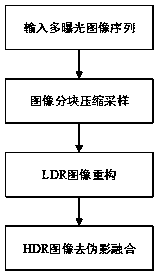
ActiveCN107730479AResolve ArtifactsSolver ambiguityImage enhancementImage analysisDictionary learningComputation complexity
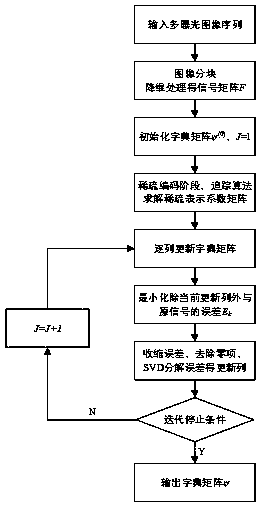
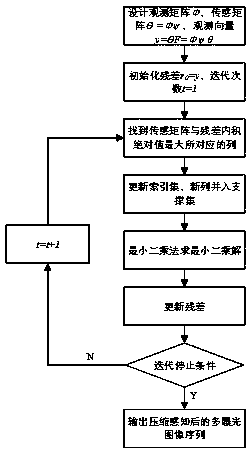
The invention discloses a compressed-sensing-based de-artifact fusion method of a high-dynamic-range image. Compressed sampling is carried out on an inputted multi-exposure image sequence; reconstruction is carried out by using a reconstruction method to obtain multi-exposure image sequence after compressed sensing; and then an image set after compressed sensing is normalized, multi-exposure imagede-artifact fusion based on PatchMatch and a rank minimization algorithm is carried out on the image set to obtain a high-dynamic-range (HDR) image of a target. According to the invention, on the basis of latest research results of K-SVD dictionary learning, compressed sensing and de-artifact fusion, the sampling rate, the storage space and the computational complexity are reduced effectively; and a de-artifact de-blurring HDR image is obtained.
Owner:SUN YAT SEN UNIV +2
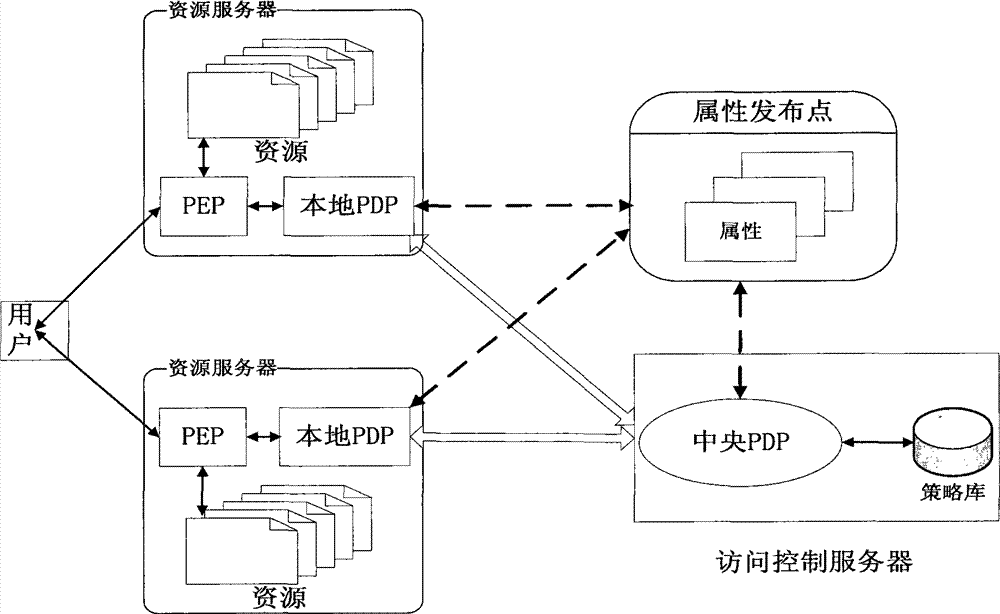
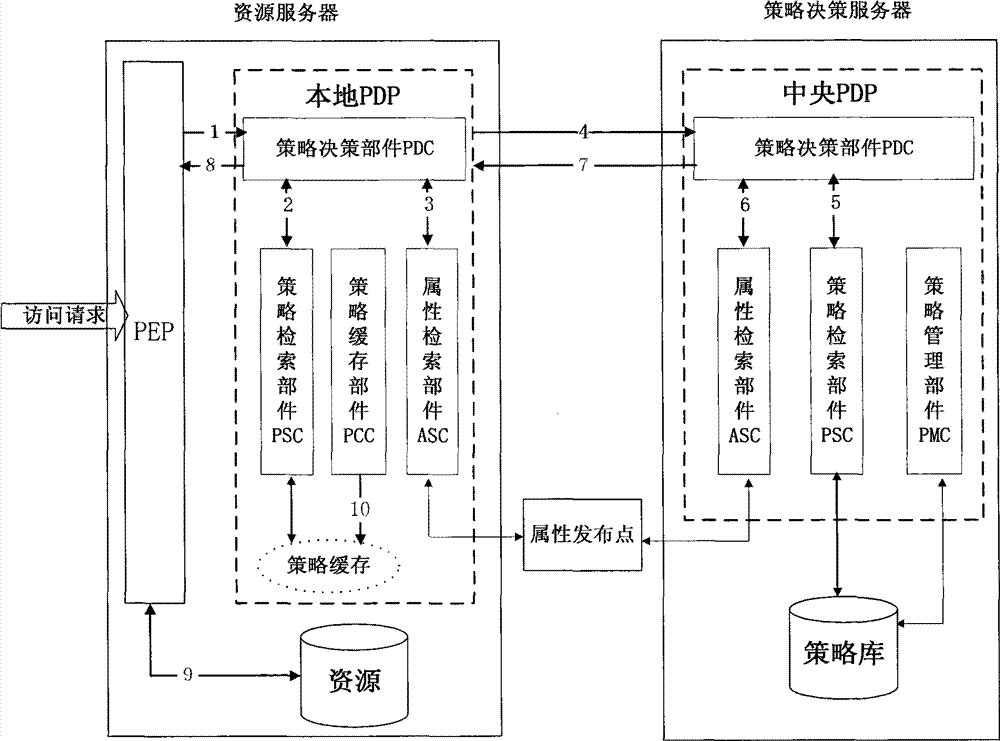
Two-level policy decision-based access control method and system
ActiveCN102006297AGuaranteed versatilityReduce the burden onTransmissionPolicy decisionAccess control matrix
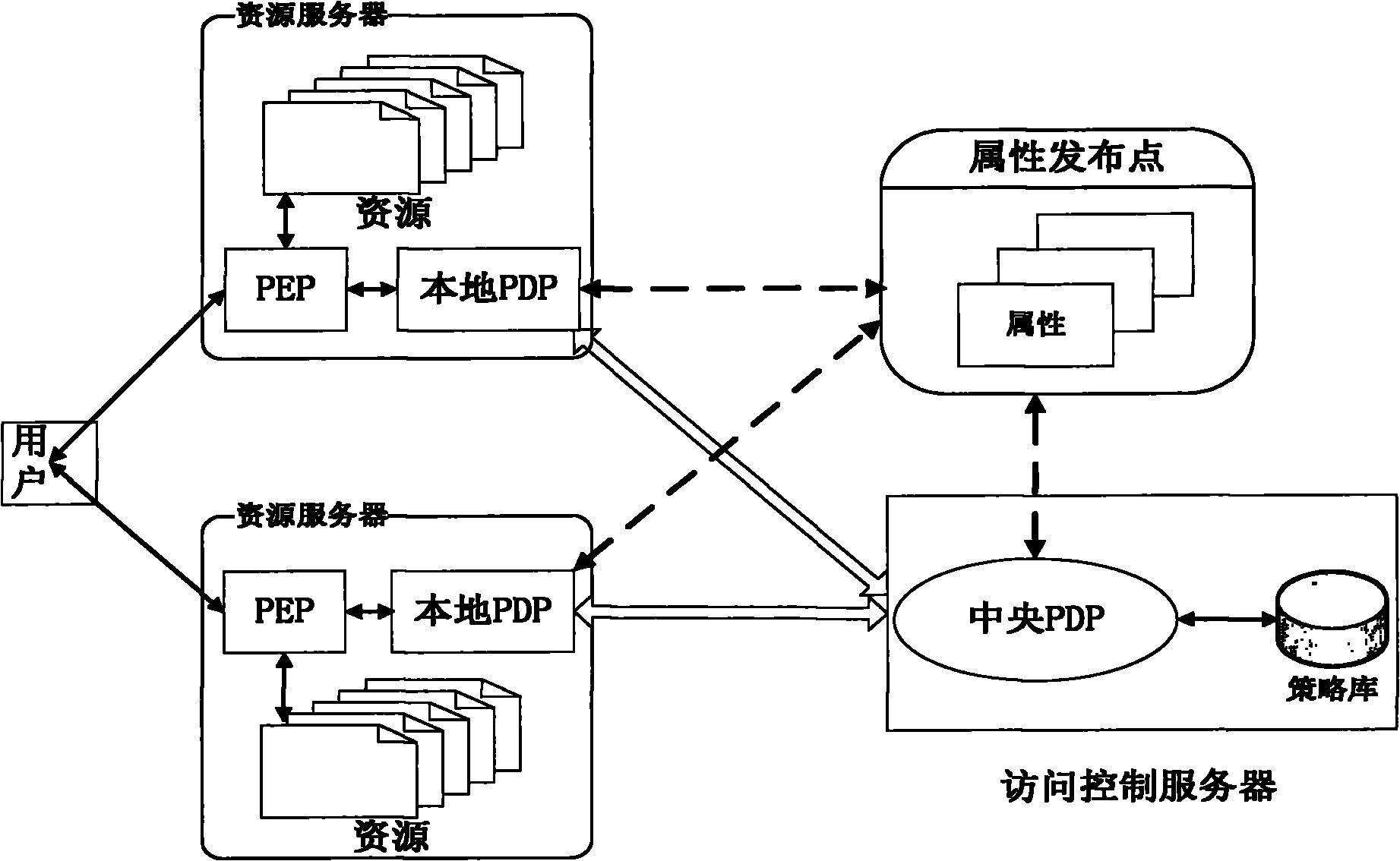
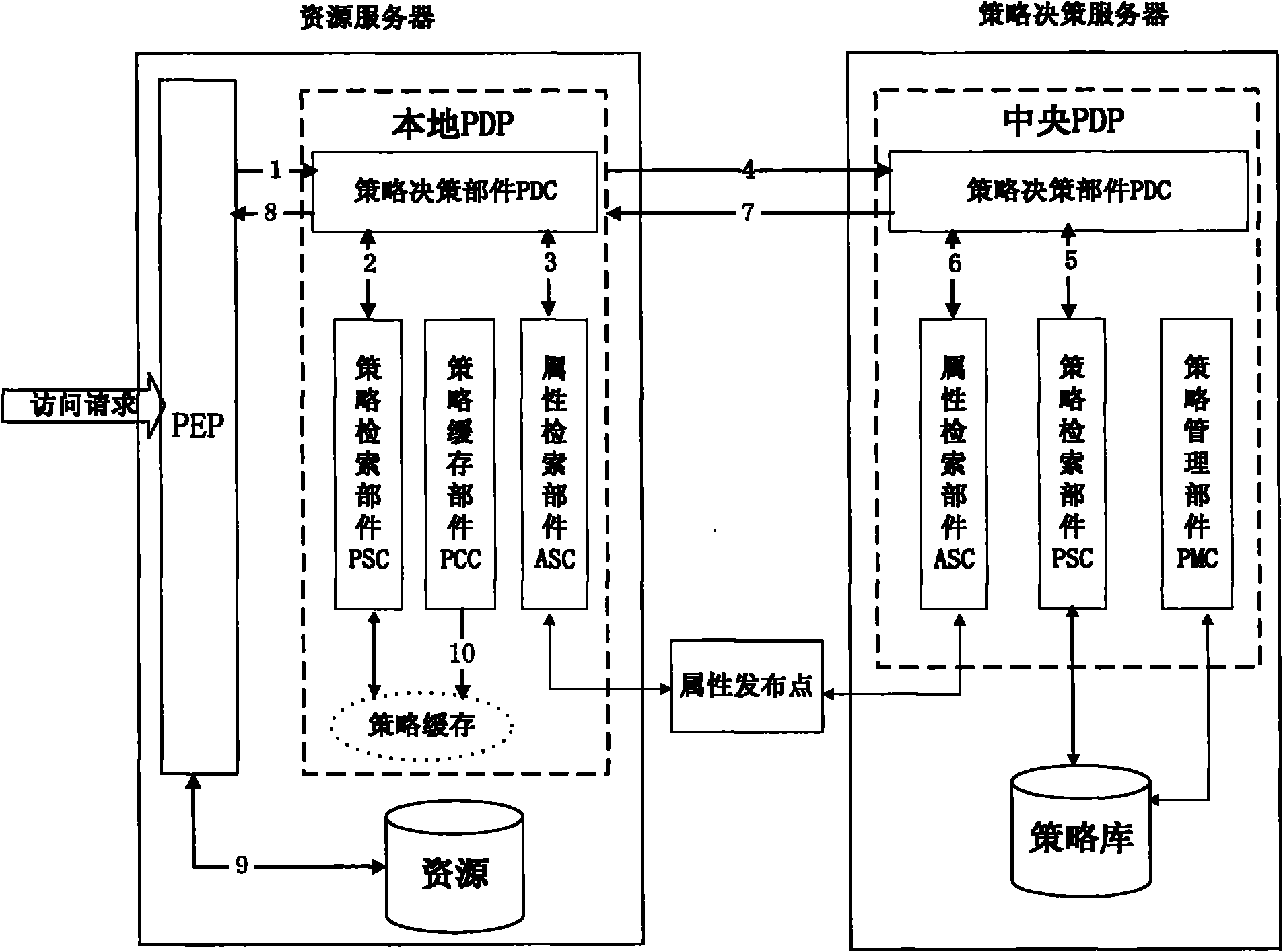
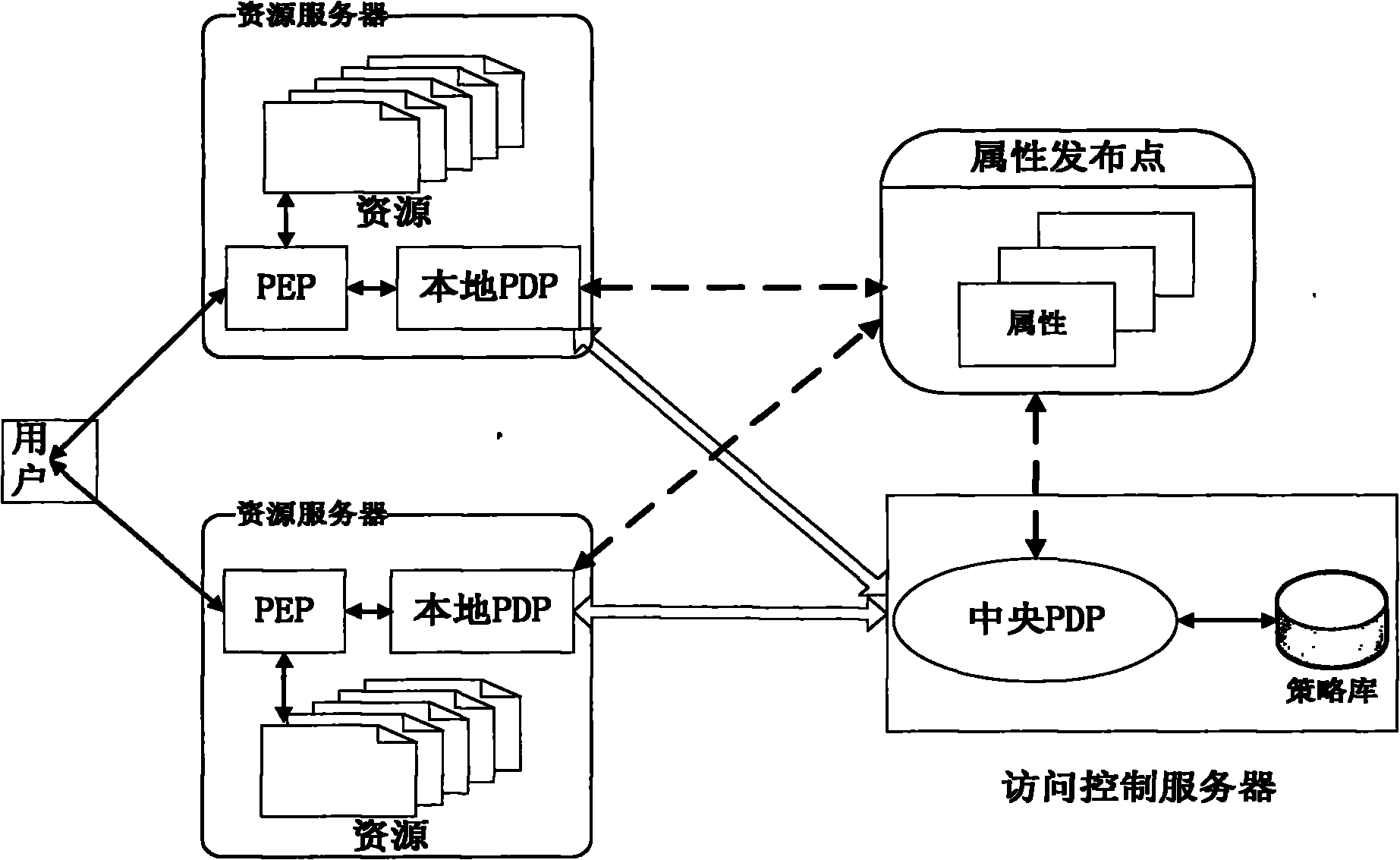
The invention discloses a two-level policy decision-based access control method and a two-level policy decision-based access control system, and belongs to the field of access control in information safety. In the method, a local policy decision point (PDP) is deployed at a policy enforcement point (PEP) end, and the local PDP makes a decision for an access request according to a local policy cache, and if the local PDP cannot determine that the decision is a deterministic decision, a central PDP finally finishes the decision according to a system policy library. The system comprises a policydecision server, an attribute publishing point and a plurality of resource servers, wherein a policy enforcement point (PEP) and a local policy decision point (PDP) are deployed on each resource server; and a central policy decision point (PDP) is deployed on the policy decision server. The invention has a good dynamically adjusted elastic system framework, fully utilizes the computing resources of the PEP end, lightens the burden of the central PDP, reduces the network transmission overhead and effectively improves the access control efficiency at extremely low policy update cost.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
Link selection method of P2P video living broadcast system data scheduling
ActiveCN101272404AEfficient use ofReduce transmission costStore-and-forward switching systemsData schedulingTransmission system
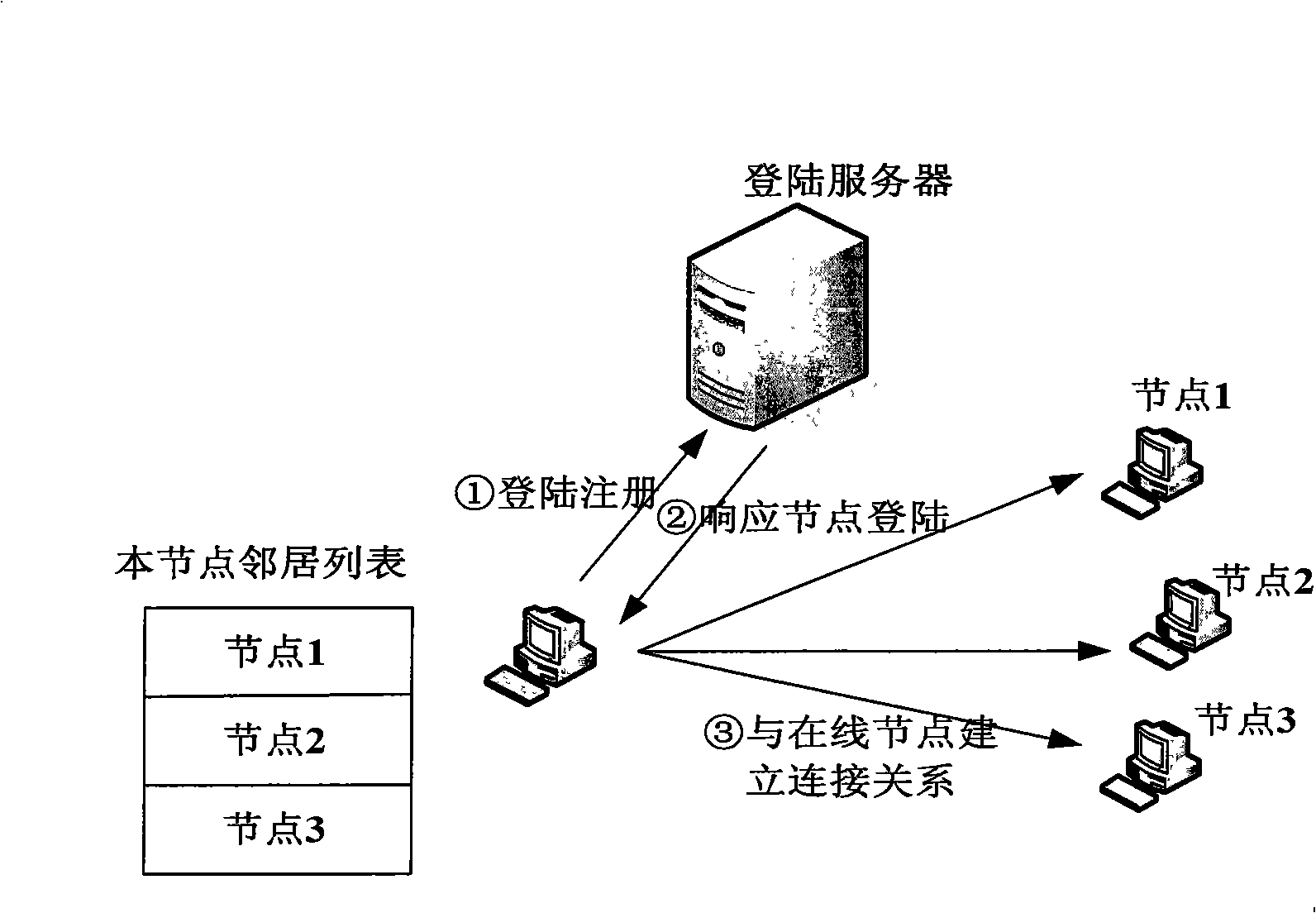
The invention discloses a link selection method for data scheduling of a P2P video living transmission system, which comprises the steps that: the data request nodes registers to a login server, and the login server distributes neighbor nodes to the request nodes; the request nodes establish connections with the distributed neighbor nodes, and the neighbor nodes are graded into different levels according to the link-cost; the request nodes acquire the request data from the neighbor nodes according to the different levels of the neighbor nodes and based on the information of data content and data transmitting performance. In the same data scheduling order, the method can make better use of network resources, thereby remarkably reducing the flux of going through NAT and the flux of stepping over autonomous system and backbone network of internet service providers.
Owner:ALIBABA (CHINA) CO LTD
Method for designing compression imaging system based on coded aperture lens array
InactiveCN102891956AReduce the sampling frequencyReduce data storageTelevision system detailsColor television detailsImage signalCoded aperture
The invention discloses a method for designing a compression imaging system based on a coded aperture lens array. The compression imaging system comprises a field stop array, a coded aperture template array, a sub-aperture splicing lens array, a coded sampling template array and a detector image surface array, wherein the field stop array partitions a large scene; the coded aperture template array performs spatial light modulation on rays from a scene target; the modulated rays are converged by the sub-aperture splicing lens array; the converged rays are spatially sampled by the coded sampling template array which is positioned at the front end of a focal plane; and the detector image surface array is used for compression imaging. The compression imaging system based on the coded aperture lens array can synchronously compress and sample the target scene, the sampling frequency of an image signal and data storage and transmission cost can be greatly reduced, a storage space required by a measurement matrix can be greatly reduced by partitioning and imaging the large scene through the sub-aperture splicing lens array, and the calibration working amount of an optical system is greatly reduced.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Multi-network coverage apparatus and method having network selection function
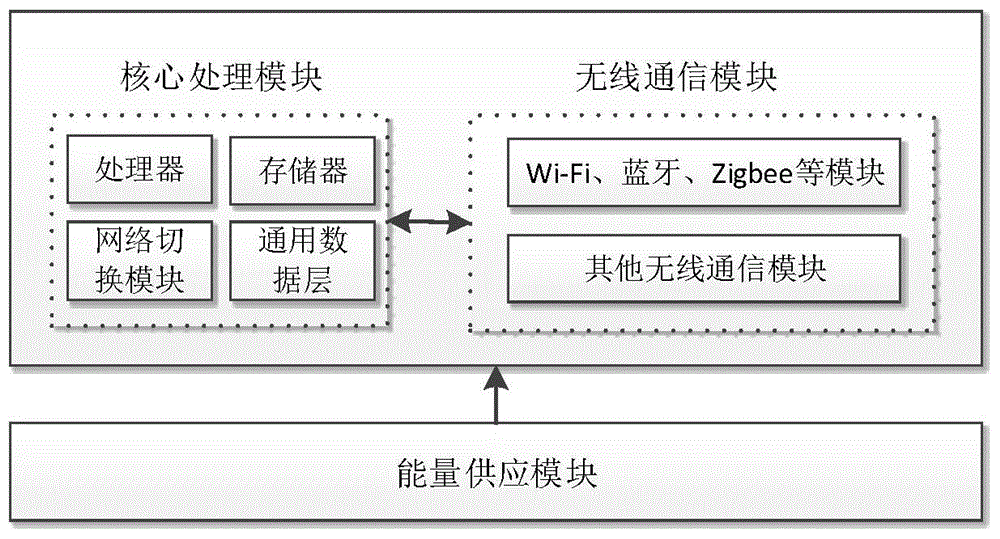
ActiveCN105007587AImprove survivabilityImprove acceleration performanceNetwork topologiesNetwork planningSurvivabilityComputer module
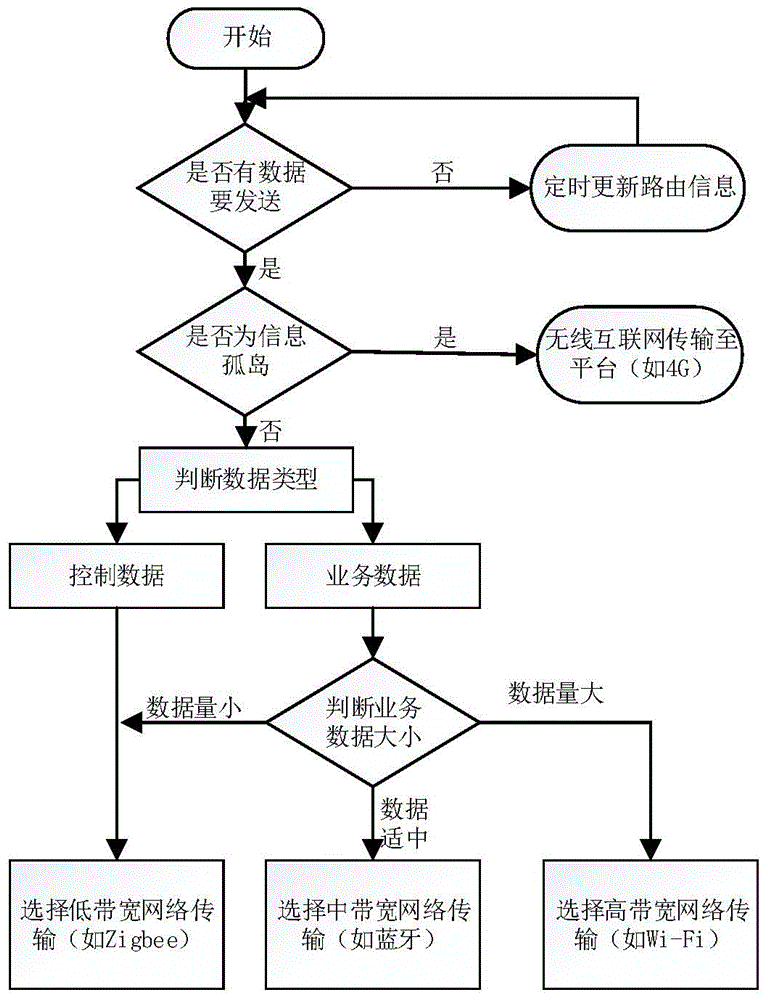
The present invention relates to a multi-network coverage apparatus and a multi-network coverage method having a network selection function. The multi-network coverage apparatus comprises a core processing module, a wireless communication module and an energy supply module; wherein the core processing module is used for controlling the multi-network coverage apparatus to achieve self-organized networking with other network apparatuses, and selecting a corresponding communication mode for performing data transmission according to attributes of data to be transmitted when there is data needing to be transmitted after the networking; the wireless communication module is used for providing a plurality of wireless communication modes for the core processing module to select during networking and data transmission; and the energy supply module is used for providing energy supply for the multi-network coverage apparatus. The multi-network coverage apparatus and the multi-network coverage method of the present invention improve a survival capability, an expansion capability and reliability of a network in a complex environment, reduce the number of various apparatuses in the network, facilitate management of the network, and reduce investment cost of the apparatuses.
Owner:INST OF INFORMATION ENG CAS
Online measurement node selection method for wireless network
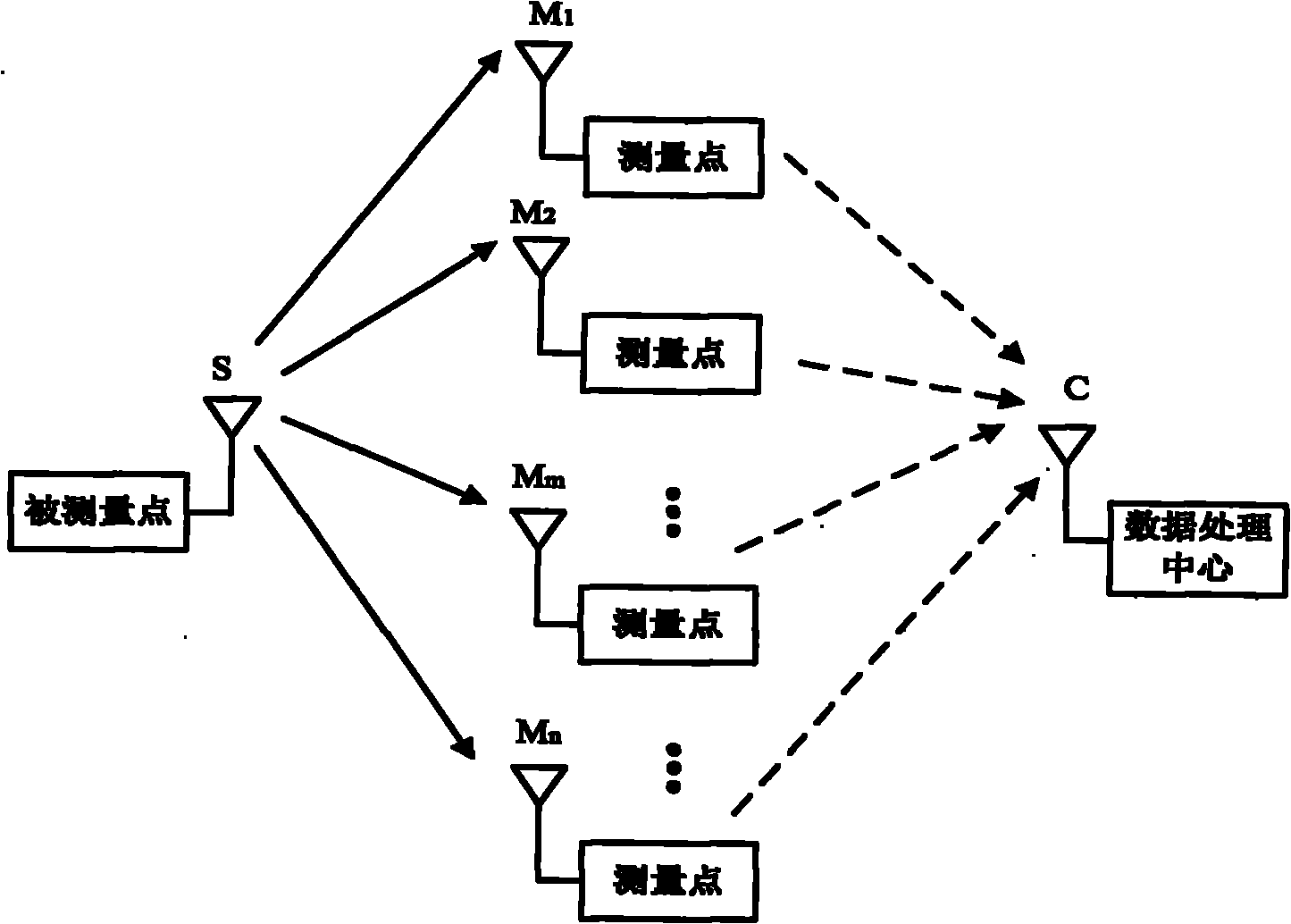
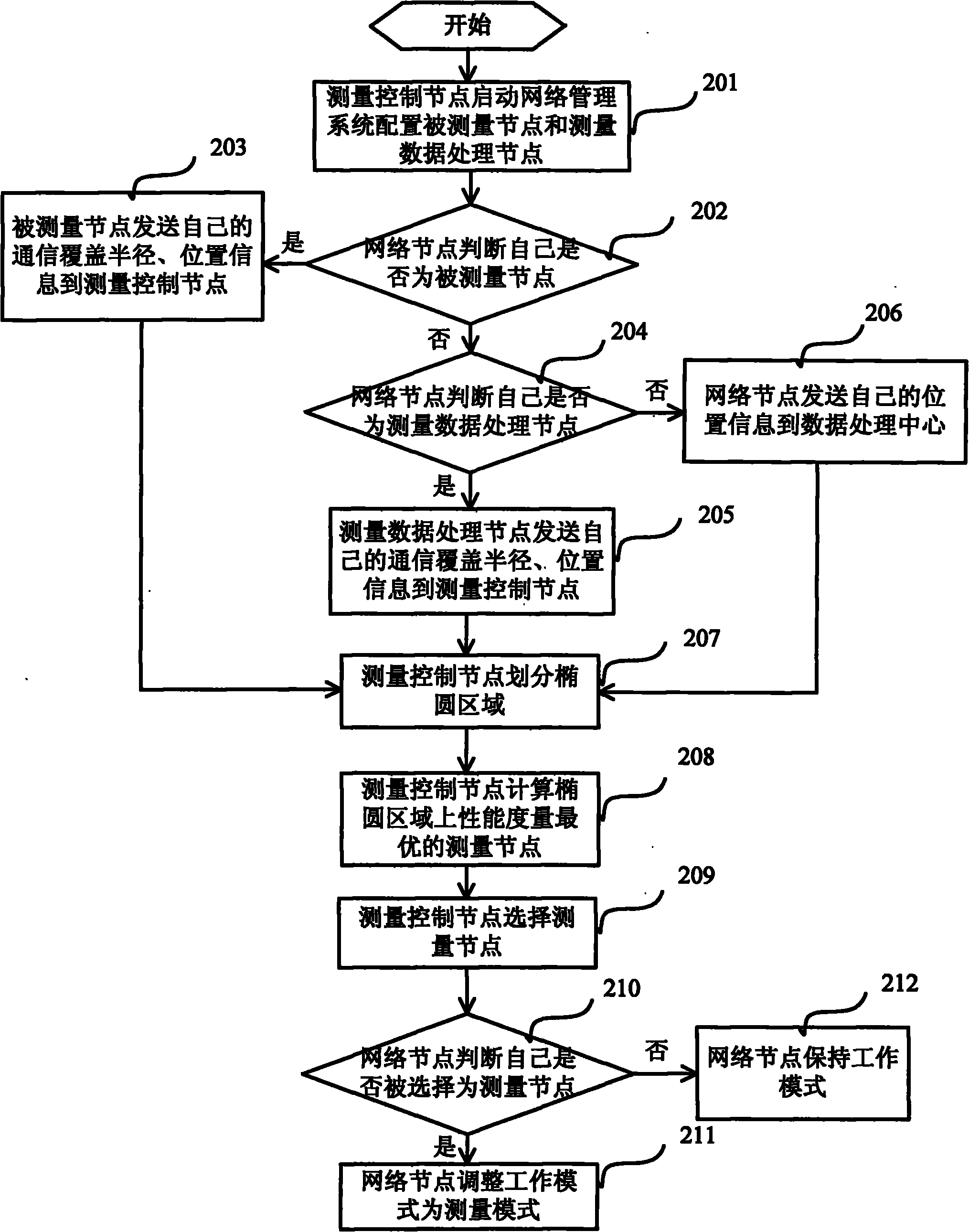
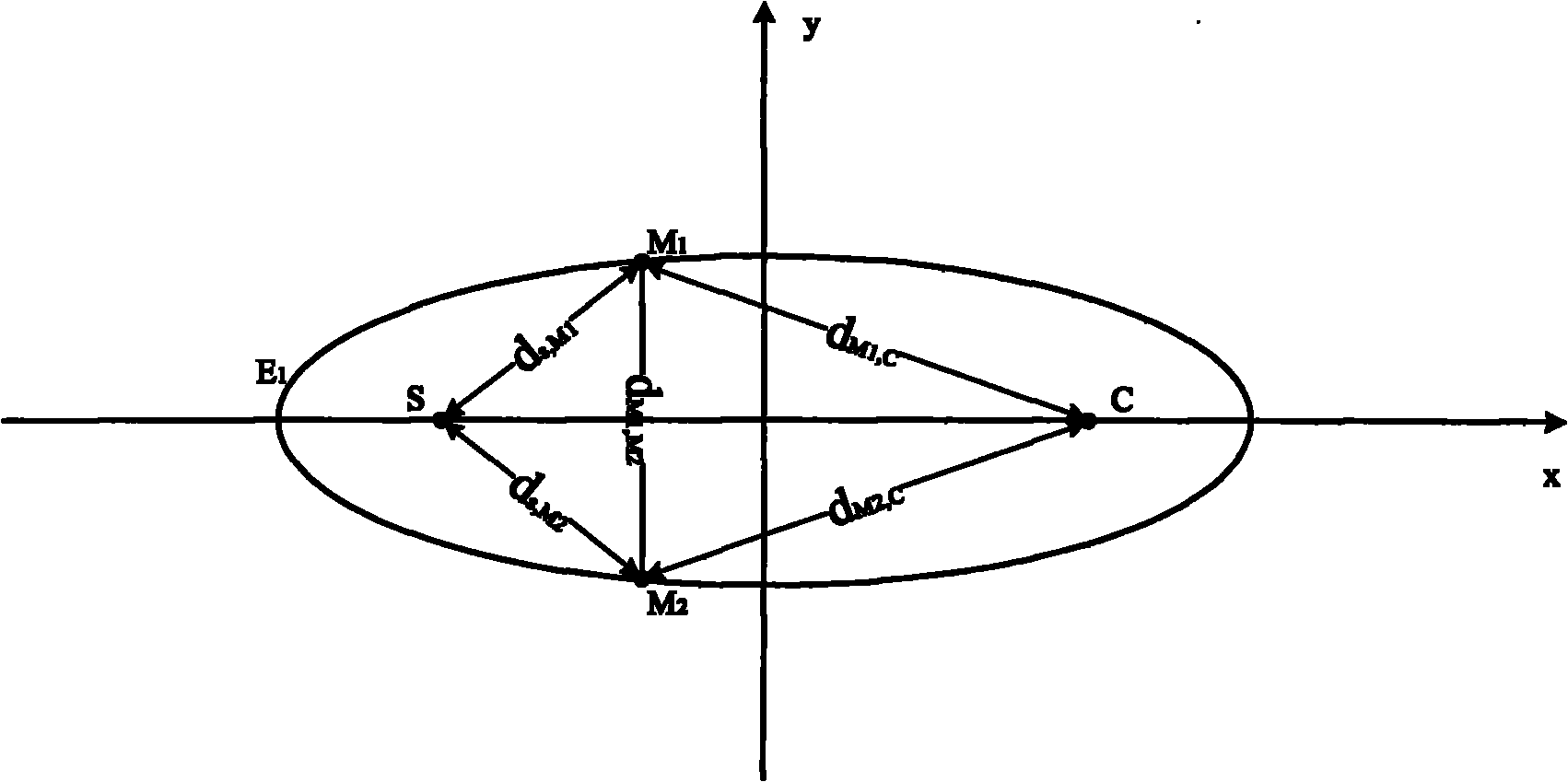
InactiveCN101917738AReduce computational complexityReduce transmission costAssess restrictionHigh level techniquesNetwork managementEllipsometry
The invention provides an online measurement node selection method for a wireless network. The method comprises that: a measurement control node starts a network management system to configure a measured node and a measurement data processing node; the measured node and the measurement data processing data transmit communication covered radius and position information to the measurement control node; other network nodes transmit position information to the measurement control node; the measurement control node divides an ellipsometry region according to an online measurement task, the position information of the measurement node, the communication covered radius and position information of the measured node and the measurement data processing node; and the measurement control node calculates the position of the measurement node with the best performance metric, and selects an actual measurement node which is closest to the measurement node with the best performance metric. The method can reduce the cost for transmitting a measurement report on the premise of meeting the detection probability required by the wireless network.
Owner:CHONGQING UNIV
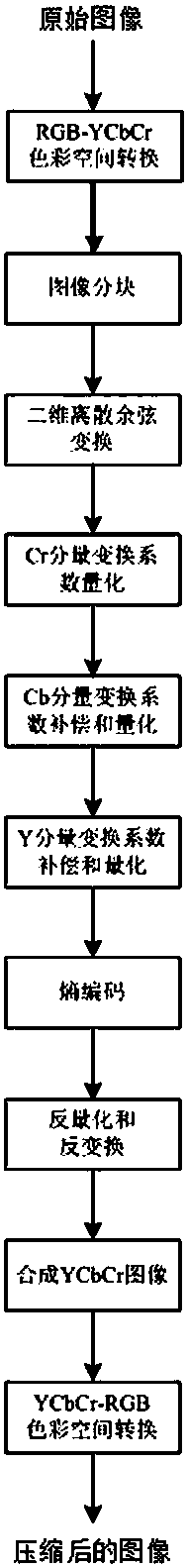
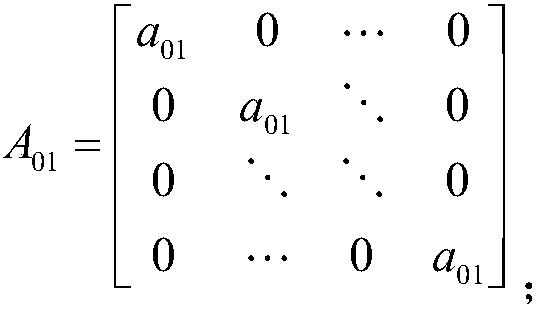
Color image compression method
ActiveCN107645662AReduce encoding distortionQuality improvementDigital video signal modificationRgb imageLightness
The invention, which relates to the technical field of image compression, discloses a color image compression method. An RGB color image is converted into a YCbCr image in a 4-to-4-to-4 format by an image color space conversion method; changing, quantification, sorting, and coding are carried out on a brightness Y component and chrominance Cb component and Cr components in the YCbCr image; and then the compressed RGB color image is synthesized again. On the premise that the encoding rate is controlled effectively, the quantization error of the YCbCr image is adjusted by processing the brightness Y component and chrominance Cb component and Cr components, thereby reducing the encoding distortion of the RGB image and guaranteeing the optimal quality of the RGB image after compression; and the encoding rate of directional quantification processing is low, the storage space is small, and the transmission cost is low.
Owner:UNIV OF ELECTRONIC SCI & TECH OF CHINA
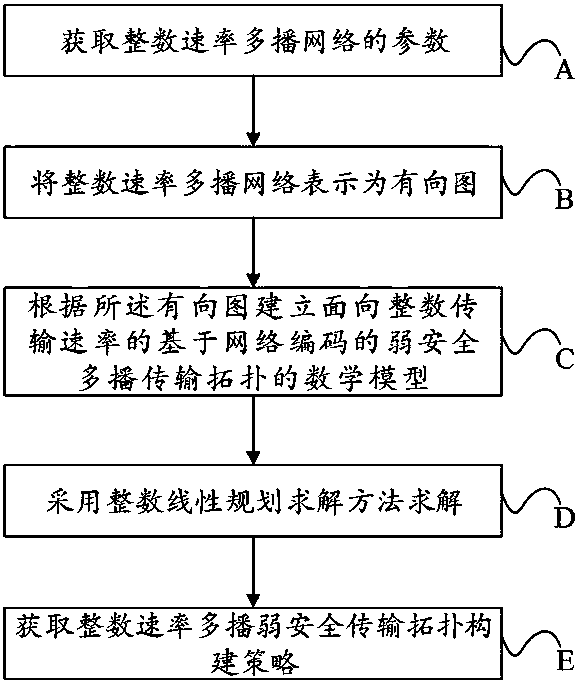
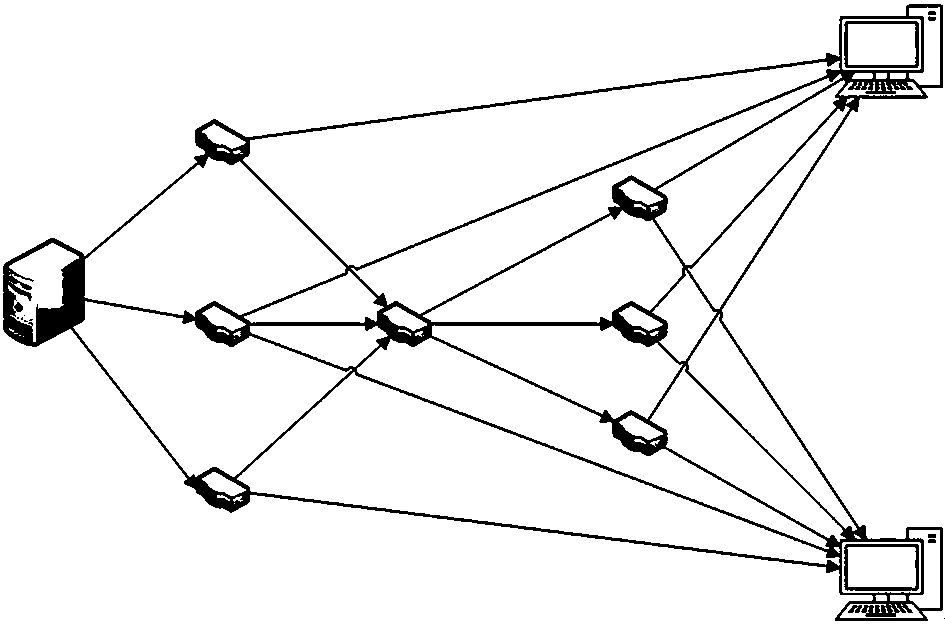
Network coding based weak security multicast transmission topology construction method facing integer transmission rates
ActiveCN108462643AGuaranteed Weak SecurityReduce transmission costData switching networksTelecommunications linkMathematical model
The invention discloses a network coding based weak security multicast transmission topology construction method facing integer transmission rates. The method includes the following steps: parametersof the network can be obtained; the network is expressed as a digraph, the digraph consists of nodes and edges, the nodes include source nodes, intermediate nodes and destination nodes, if a communication link exists between two nodes, an edge is connected between the two nodes in the communication link direction, the capacity of each directed edge is equal to the capacity of the corresponding communication link, and the cost of each directed edge is equal to the cost of the corresponding communication link; a mathematical model of the network coding based weak security multicast transmissiontopology of the integer transmission rates can be built according to the digraph; solving can be performed by adopting an integer linear programming solution; and a network coding based weak securitymulticast transmission topology construction plan of the integer transmission rates can be obtained. The construction of transmission topology can be achieved under the condition that the network coding based weak security multicast of the integer transmission rates meets weak security needs, secure transmission throughput in network can be reached to maximum, and at the same time, minimum transmission cost at the maximum throughput can be guaranteed, and efficiency and cost optimization of the network can be achieved.
Owner:SUZHOU UNIV
Distributed speech enhancement method based on distributed uniformity and MVDR (minimum variance distortionless response) beam forming
The invention discloses a distributed speech enhancement method based on distributed uniformity and MVDR (minimum variance distortionless response) beam forming. The distributed speech enhancement method includes S1, generating coordinates of sensor network nodes according to an improved random acoustic sensor network generation algorithm, and calculating connection matrixes, degrees and adjacent node collections of the nodes; S2, receiving noise-containing speech signals by a sensor network generated in the S1, performing MVDR preprocessing on the noise-containing speech signals received by the nodes to acquire a speech preprocessing matrix (0) and a noise preprocessing matrix (0); S3, performing distributed uniformity iteration according to the connection matrixes, the degrees and the adjacent node collections, which are acquired in the S1, of the nodes and the speech preprocessing matrix (0) and the noise preprocessing matrix (0) which are acquired in the S2 to enable the nodes to acquire uniform speech signals zi(t) of an MVDR speech enhancement time domain.
Owner:DALIAN UNIV OF TECH
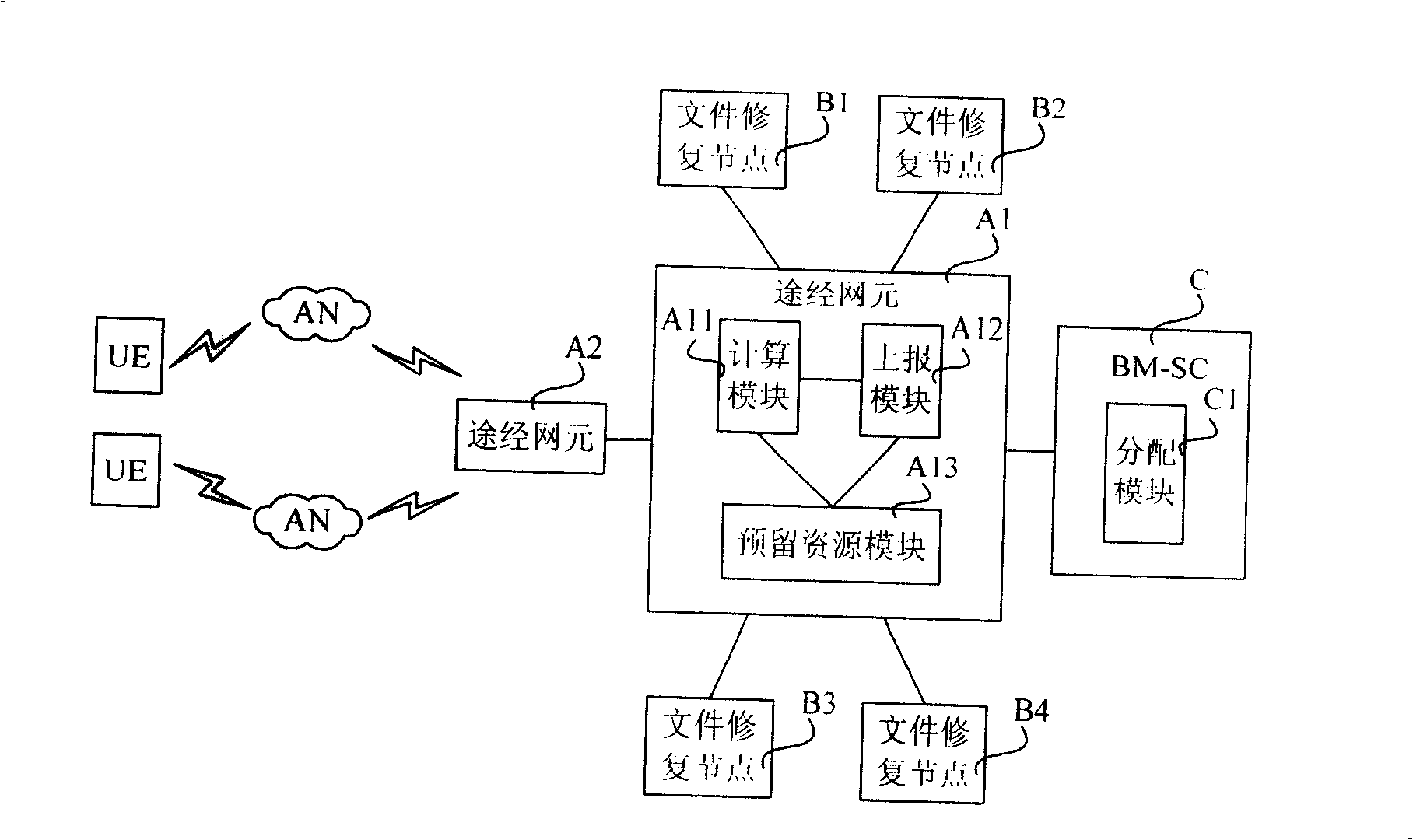
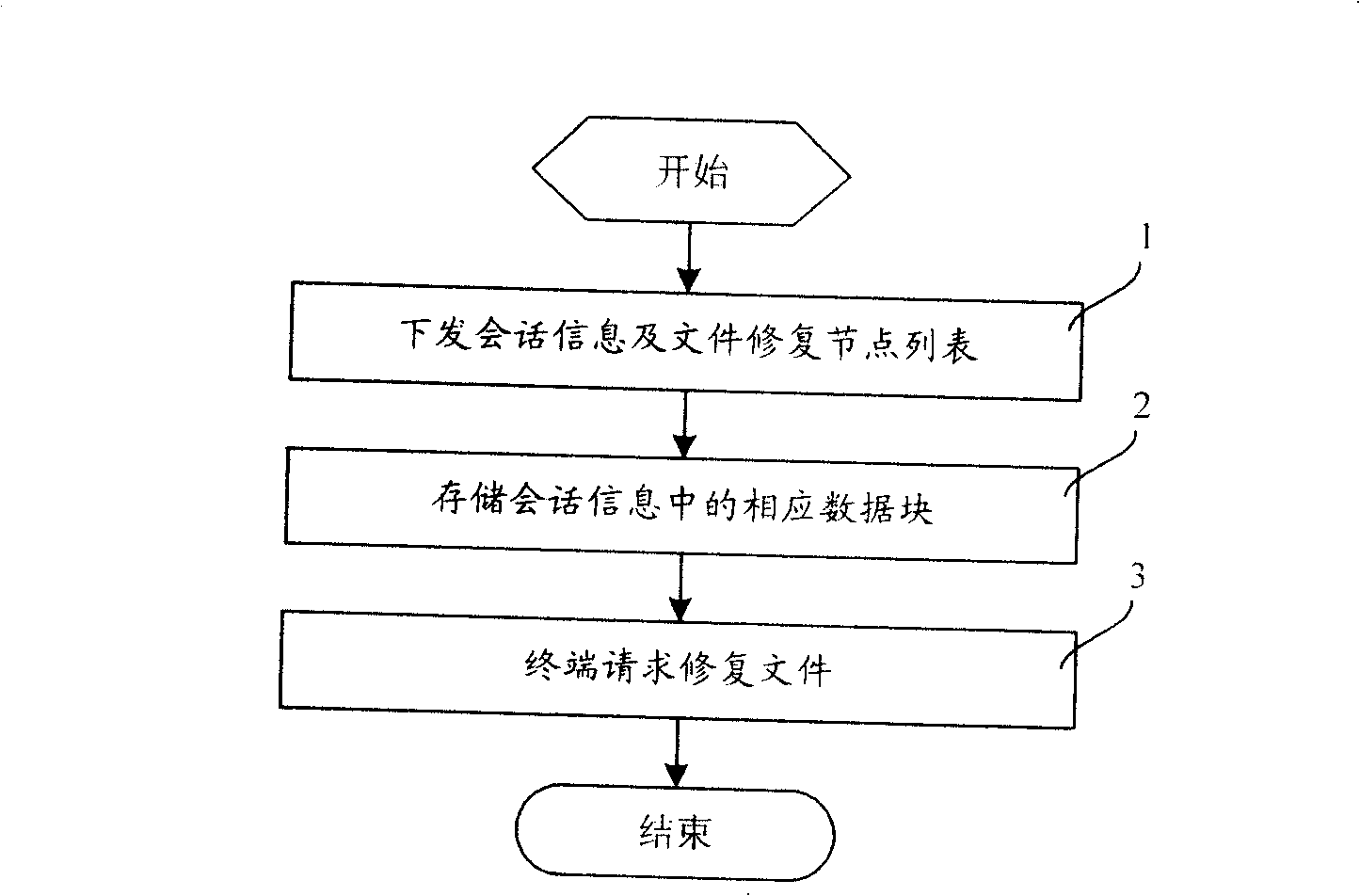
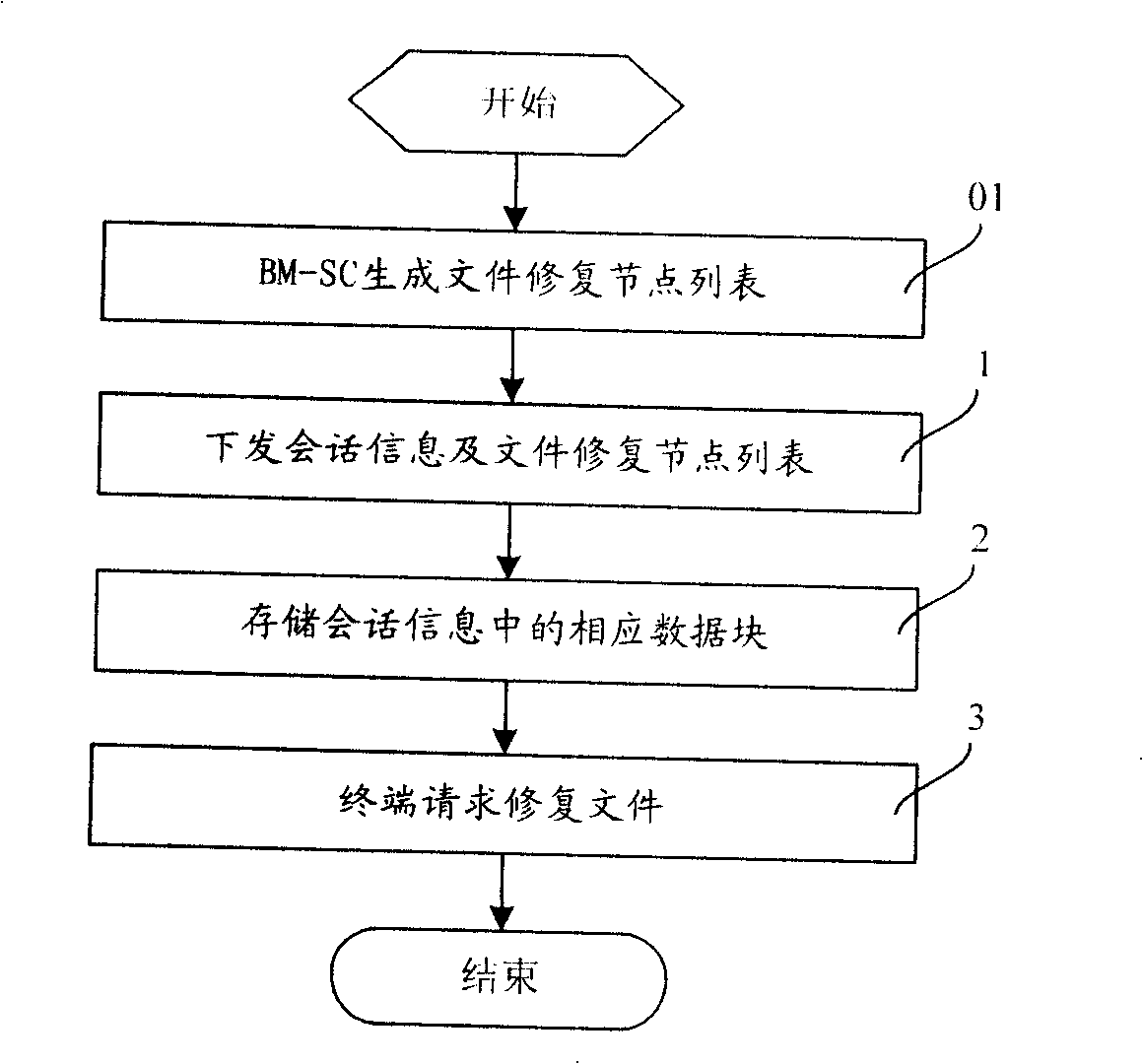
File repair system and method
ActiveCN101262627AReduce trafficReduce transmission costSpecial service provision for substationError preventionNetwork elementResource information
The invention relates to a file recovery system. The system comprises a BM-SC and a via network element, wherein, the system is also provided with a file recovery node which is connected with the via network element which controls the file recovery node, and the file recovery node is used for storing corresponding data block in dialog information forwarded by the via network element for realizing file recovery; the via network element which controls the file recovery node also comprises a calculation module which is used for calculating the usable resource information of the file recovery nodes and a report module which is connected with the calculation module and used for reporting the status information of the file recovery node to the BM-SC; the BM-SC also comprises a distribution module which is used for generating the list of the file recovery node. The invention also relates to a file recovery method which comprises the steps of distributing dialog information and the file recovery node list by the BM-SC, storing the corresponding data block by the file recovery node and requesting file recovery from a terminal. The file recovery system reduces communication traffic when data is distributed and downloaded to the file recovery node and avoids the overload of the file recovery node.
Owner:CHINA MOBILE COMM GRP CO LTD
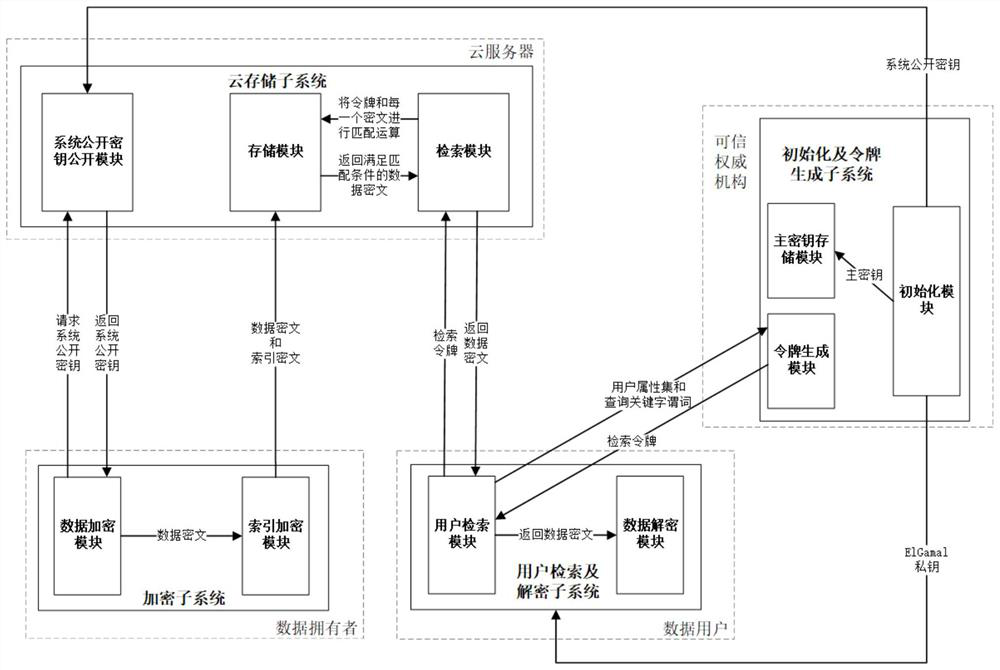
Multi-keyword searchable encryption method and system supporting Boolean access control strategy
ActiveCN112100649AFlexible controlImplement access controlDigital data protectionEngineeringTrusted authority
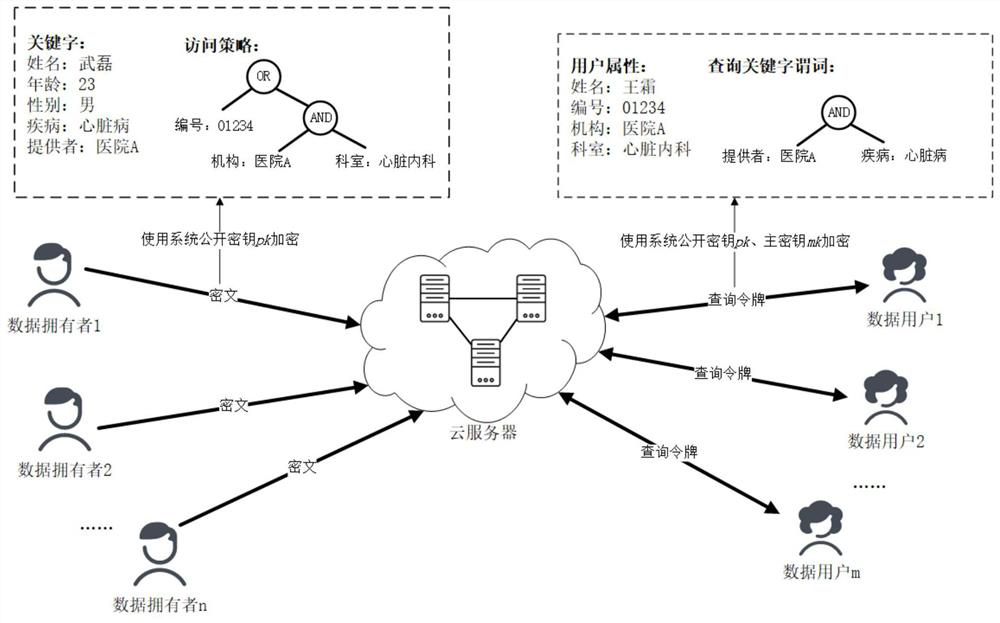
The invention discloses a multi-keyword searchable encryption method and system supporting a Boolean access control strategy, and the method comprises the steps of firstly enabling a trusted authorityto generate a system public key, a main key and an IlGamal private key, carrying out the cloud disclosure of the system public key, and transmitting the private key to a data user; then enabling thedata owner to generate an index ciphertext and a data ciphertext for the document and upload the index ciphertext and the data ciphertext to the cloud; uploading the attribute set and the query keyword predicate of the data user to a credible authority to verify whether the identity of the user is legal or not during data user retrieval, and generating a retrieval token and sending the retrieval token to the data user if the identity of the user is legal; enabling the data user to receive the retrieval token and upload the retrieval token to the cloud; after receiving the token, enabling the cloud server to check whether each index ciphertext is matched with the retrieval token or not by using a system public key, and send the matched data ciphertext to a data user; and enabling the data user to recover the data ciphertext into plaintext content by using the private key. According to the invention, fine-grained Boolean access control, Brillouin keyword search and constant-level systemkey length can be realized.
Owner:SOUTH CHINA UNIV OF TECH
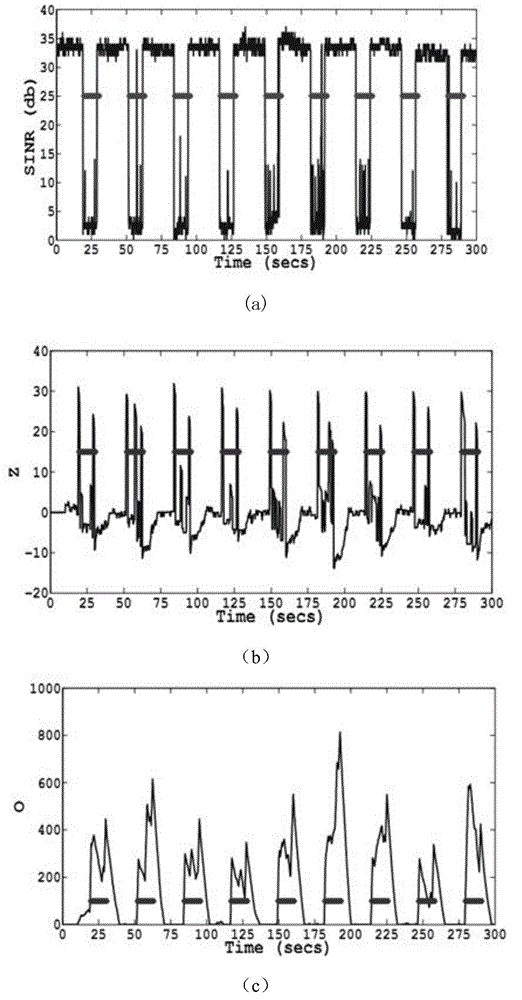
Intrusion detection method of physical layer of wireless network based on compressed sensing
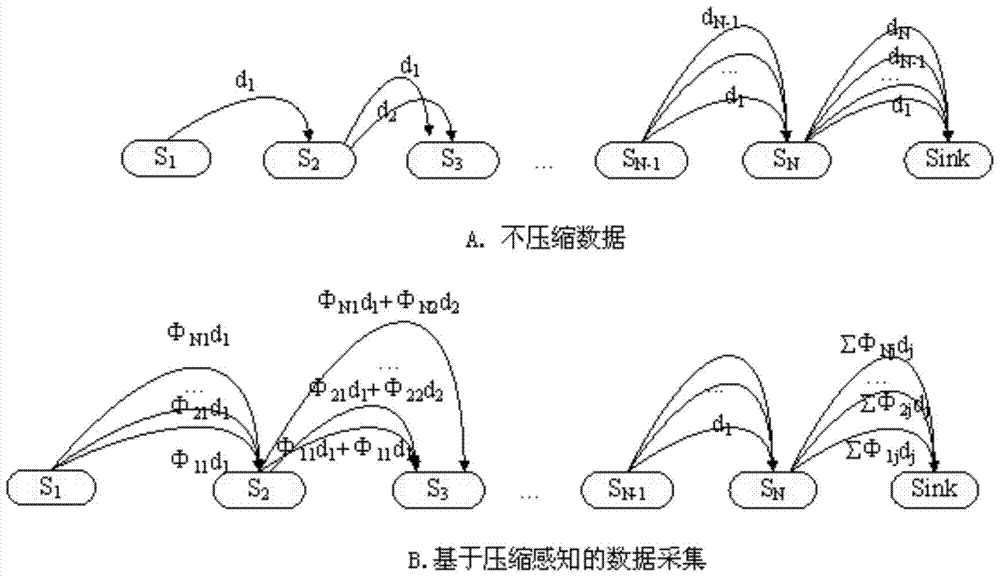
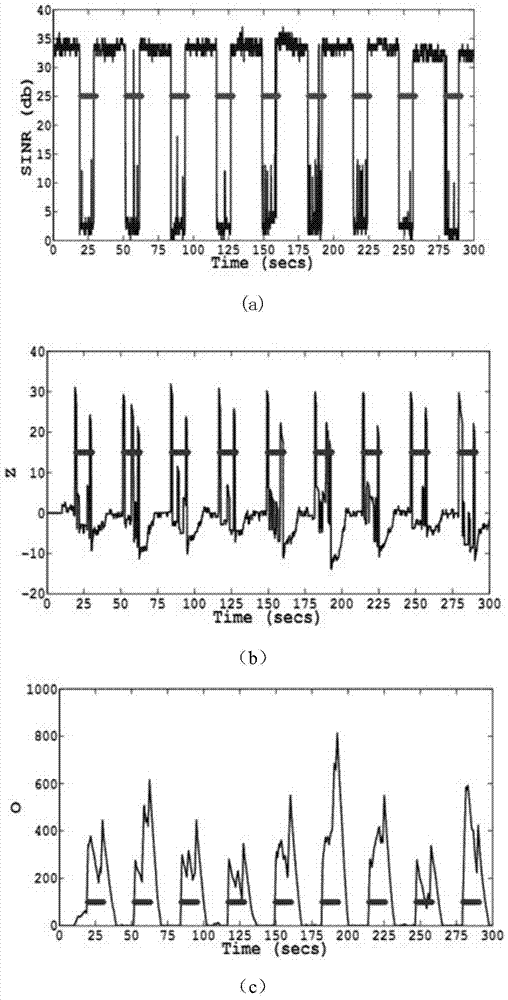
InactiveCN104135730ASmall scaleReduce transmission costTransmissionSecurity arrangementPattern recognitionWireless mesh network
The invention discloses an intrusion detection method of a physical layer of a wireless network based on compressed sensing. The intrusion detection method comprises the following steps that: a sensor node detects an event signal; an SINR (Signal to Interference plus Noise Ratio) signal x is subjected to sparse transform to obtain a sparse representation form x' of the signal; y (y belongs to RM) is obtained by the sparse representation form x' (x' belongs to RN) of the SINR signal through a projection on a matrix phi; y is transmitted through the wireless network, and reaches a central aggregation node after passing a plurality of nodes; and sampling in the central aggregation node is detected by utilizing a CUSUM algorithm, and a detected result is reconstructed and reduced to obtain abnormal behavior data, and then subsequent processing is carried out. The intrusion detection method has the advantages that: through compressed signal sampling, data scale is reduced, and transmission cost is reduced, so that the abnormal condition of the physical layer can be quickly judged.
Owner:SOUTHWEST UNIV
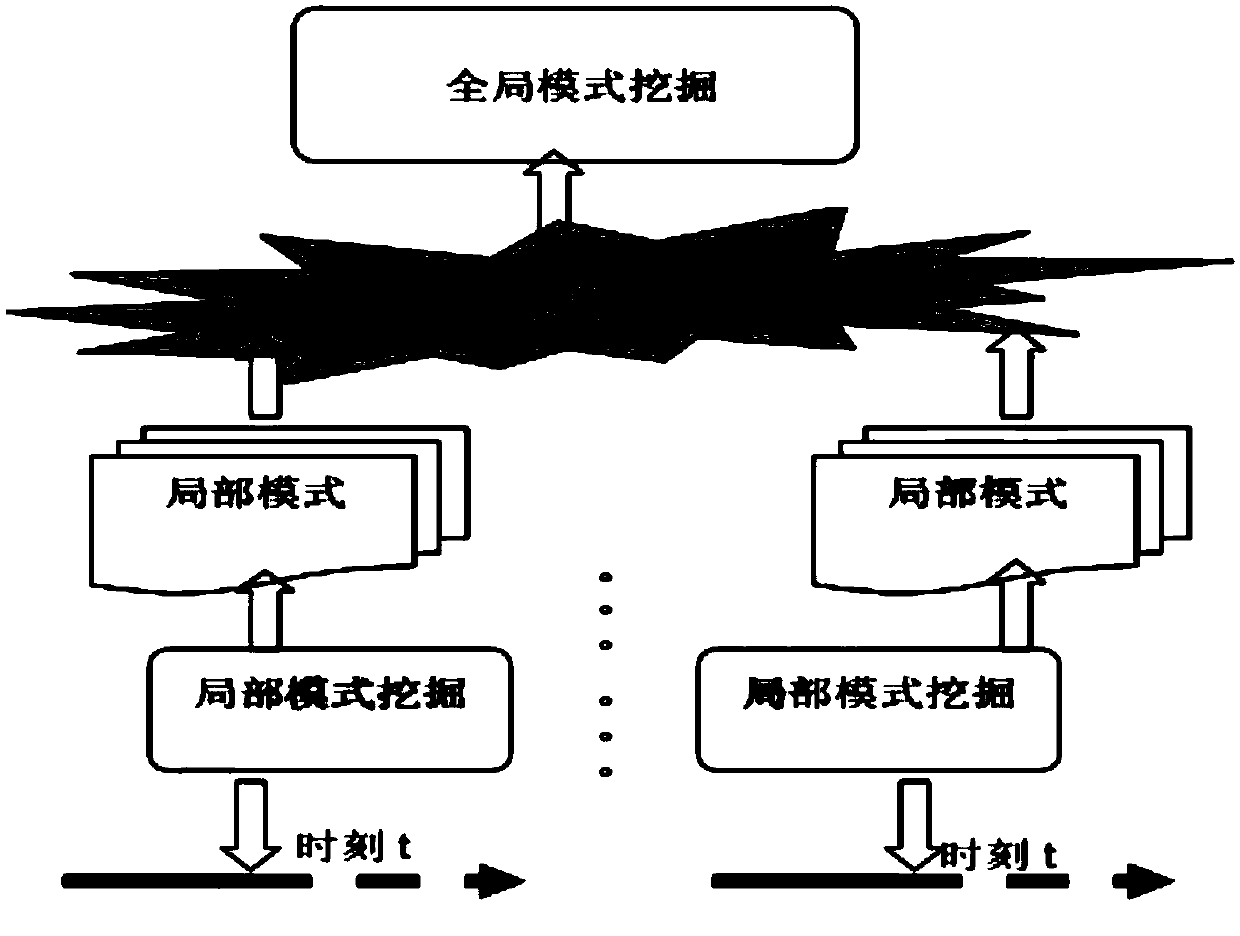
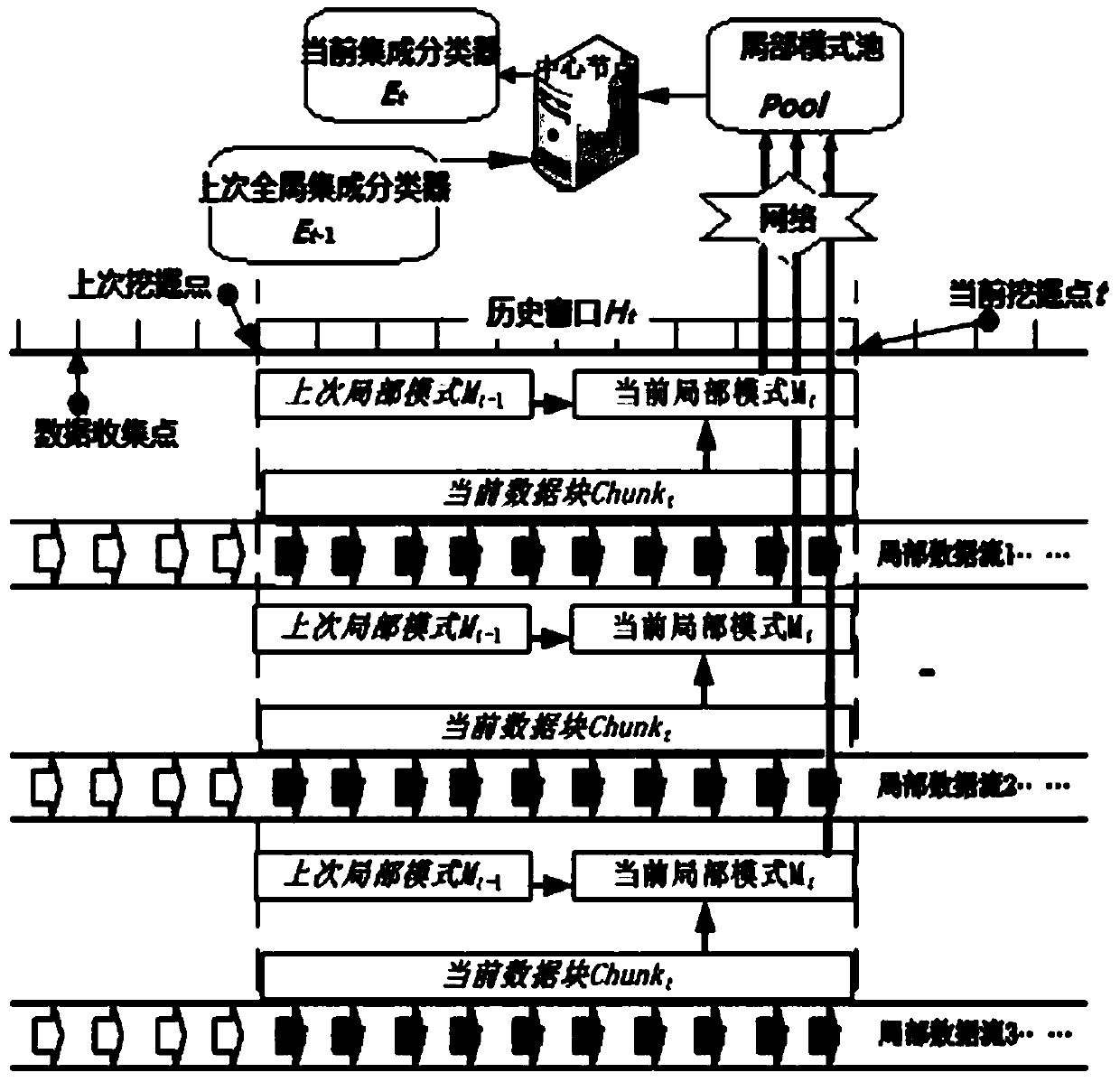
Dynamic mining method for distributed data streaming
InactiveCN109672729AReduce discardingSolve the problem of occupying network bandwidthCharacter and pattern recognitionData switching networksData streamData set
The invention discloses a dynamic mining method for distributed data streaming, which comprises the following steps of: S1, by each local node, collecting current data blocks at a current t moment andcarrying out micro cluster processing; S2, by each local node, carrying out incremental micro cluster updating of a local mode; S3, executing a local mode transmission stage, i.e., uploading the local mode of each local node at the t moment to a central node; S4, by the central node, after receiving the local modes of all the local nodes at the t moment, reconstructing a global sample data set onthe basis of a micro cluster; and S5, by the central node, executing a basic learner for new learning on the basis of the global sample data set, and carrying out incremental updating of a global mode in a current state on the basic learner for new learning. According to the invention, in a local mining mode, data can be processed locally to the greatest extent, so as to reduce the probability that the data is discarded.
Owner:FUJIAN UNIV OF TECH
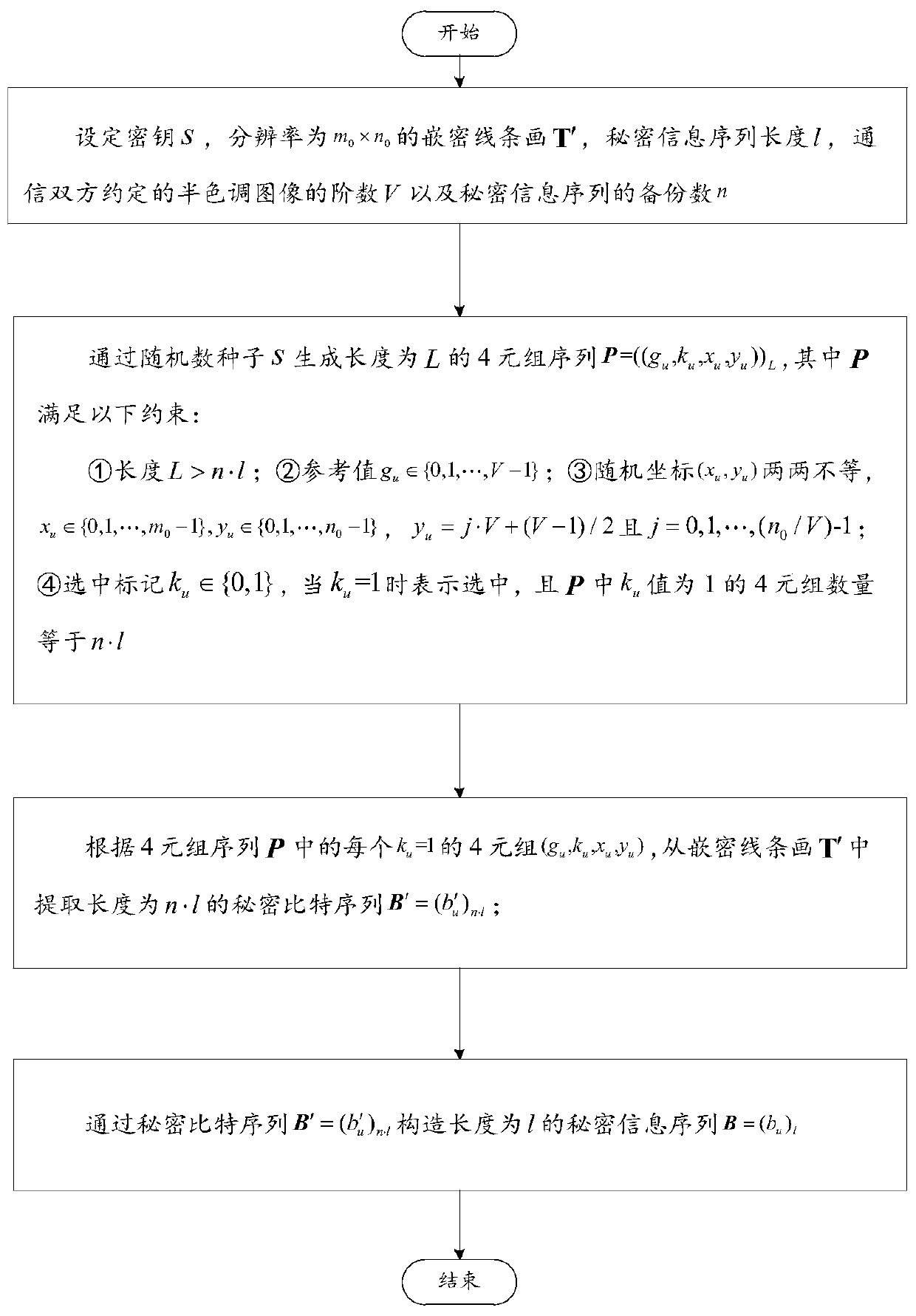
Line art picture hiding and recovering method and equipment, and storage medium
ActiveCN110475039AImprove reliabilityImprove accuracyPictoral communicationInformation embeddingSignal processing
The invention belongs to the crossing field of image information security and digital image signal processing, and discloses a line art picture hiding and recovering method and equipment, and a storage medium. A blindage image is converted into a multi-order halftone image, secret information is subjected to multiple backups, a secret information embedding position is positioned according to a user secret key, the secret information and blindage pixels are coded in combination with the thickness of a line graph, and a secret-containing line graph is generated. The secret information is decodedaccording to the key, and the accuracy of secret information recovery is improved through a secret information recovery strategy based on multiple backups. Compared with the existing method, the method according to the invention is advantageous in that the hiding and recovering process strictly depends on a user secret key, the certain attack tolerance capacity and recovering capacity are achieved, the secret embedding capacity is high, the transmission cost is low, the generated secret embedding shelter is a special carrier, an original shelter is not transmitted in a channel, detection of asecret analyzer based on natural image statistical characteristics can be resisted, and high safety is achieved.
Owner:SHAANXI NORMAL UNIV
Multi-sensor multi-frame joint detection algorithm based on posteriori information fusion
ActiveCN108845299AImprove detection tracking performanceReduce transmission costRadio wave reradiation/reflectionAcoustic wave reradiationApproximate computingPosterior probability density
The invention discloses a multi-sensor multi-frame joint detection algorithm based on posteriori information fusion. The method comprises steps that S1, system parameters are initialized, including the number M of sensors included in a system, the size Nx*Ny of a sensor echo data plane and the number K of algorithm joint processing cycles, and a variable k=1 is initialized; S2, echo data is received; S3, local posteriori probability density function calculation is performed; S4, a posterior probability density function represents approximate calculation of parameters; S5, information transmission is performed; S6, global posteriori probability density calculation is performed; and S7, target track estimation is performed. The algorithm is advantaged in that advantages of both multi-sensorinformation fusion technology and the multi-frame joint detection technology can be performed, detection and tracking performance of the algorithm for weak targets is further improved, transmission cost of the algorithm is reduced through Gaussian mixture approximation, algorithm implementation efficiency is improved while algorithm performance is guaranteed, and the algorithm can be widely applied to the networking radar, MIMO radar, array sonar and other fields.
Owner:UNIV OF ELECTRONIC SCI & TECH OF CHINA
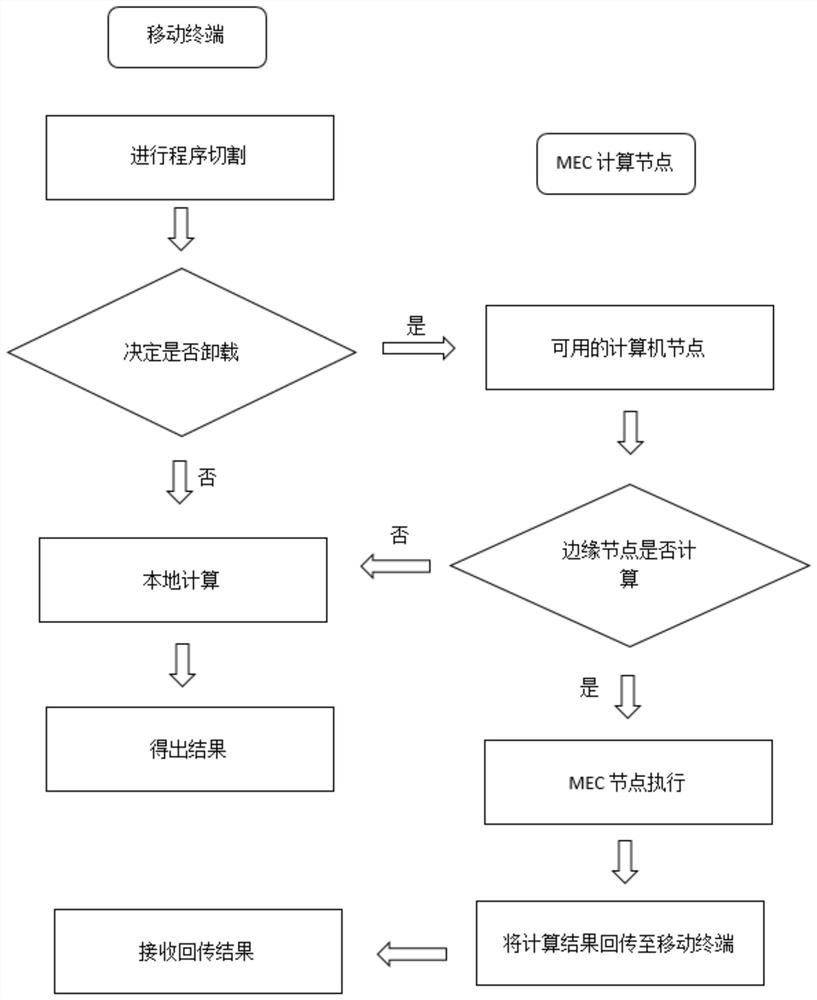
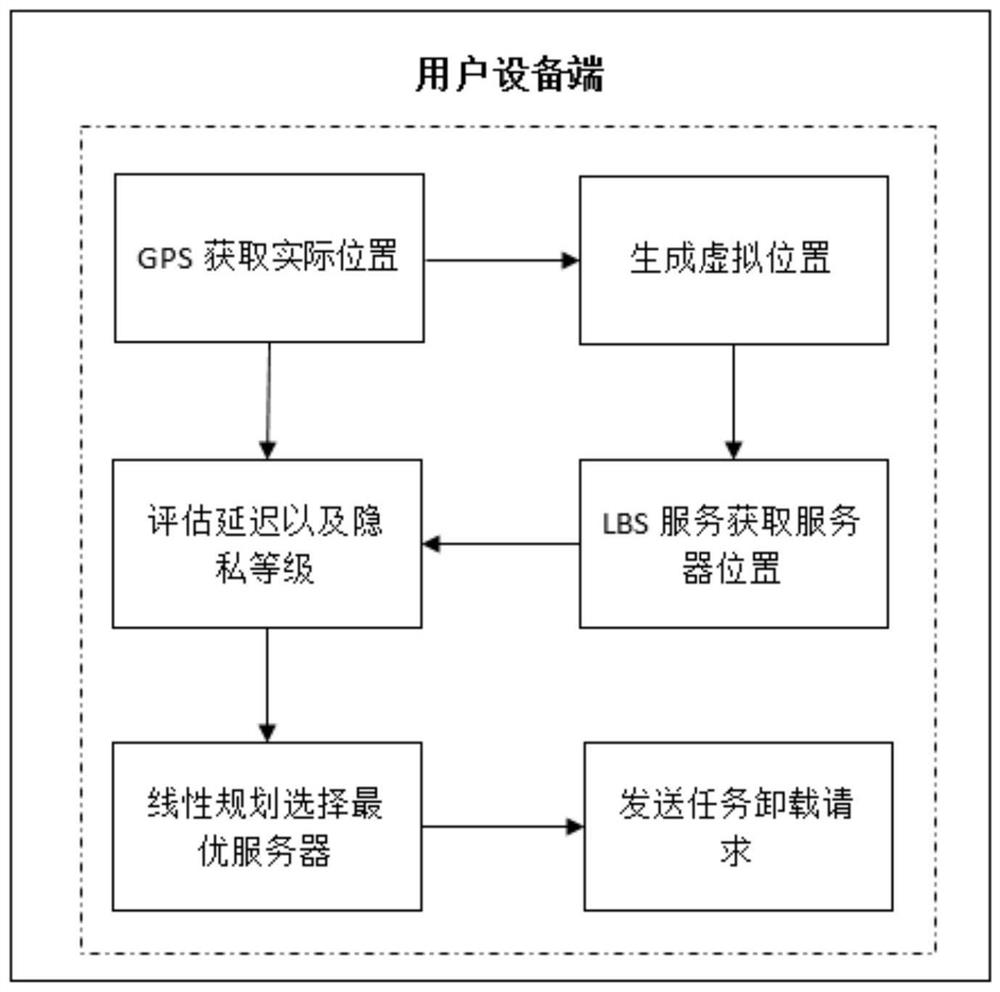
Task unloading method for location privacy protection
ActiveCN113407249AReduce transmission costReduce the risk of perceived locationResource allocationInterprogram communicationQuality of serviceSimulation
The invention discloses a task unloading method for location privacy protection. The method comprises the following steps: S1, generating an annular virtual position space by taking a real position of a user as a circle center, and selecting a virtual position according to an initial random probability; S2, acquiring a position of a base station deployed with an edge server nearby by using the virtual position, and constructing a server selection matrix; S3, according to the server selection matrix, preferentially selecting a server to send a task unloading request; S4, allocating bandwidth, and calculating related parameters of task processing; and S5, selecting a task which can be processed within task tolerance time, saves the most energy and time and has the maximum income and unloading the task to an edge node to be executed. According to the method, a task is unloaded by considering the location privacy problem of a user, the location privacy of the user can be effectively protected, the service quality can be obtained as much as possible, a task unloading decision is made by using a reinforcement learning algorithm, and an unloading strategy is dynamically adjusted through online learning.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Compressed data collection method for mobile wireless sensor network
ActiveCN110012488AImprove performance indicatorsImprove energy efficiency of collectionPower managementNetwork topologiesMobile wireless sensor networkSensor node
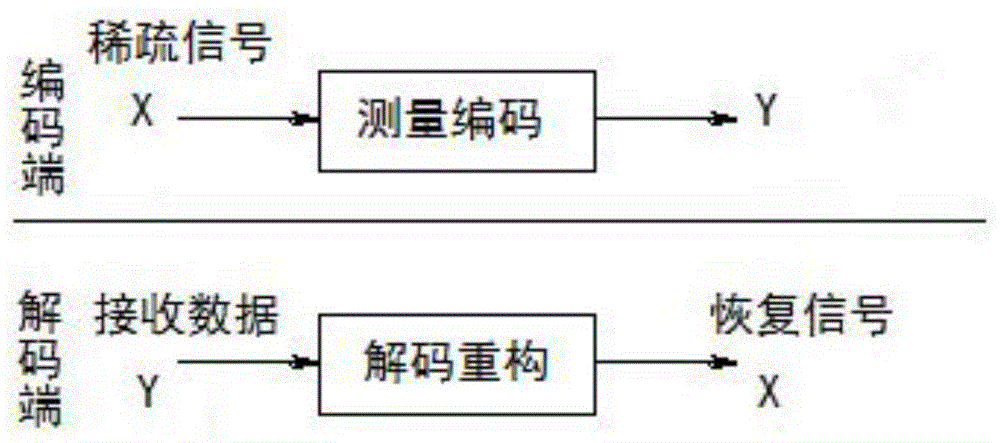
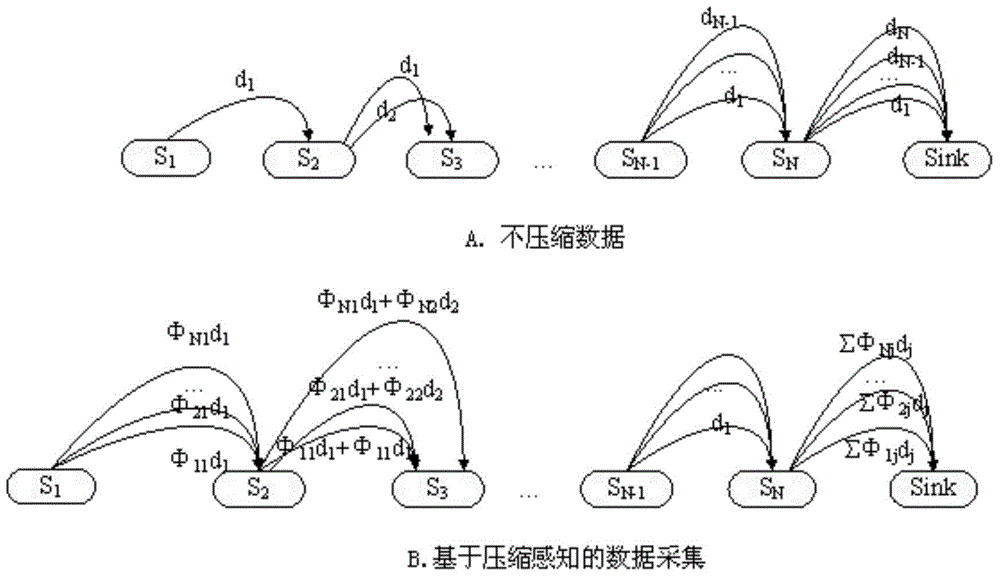
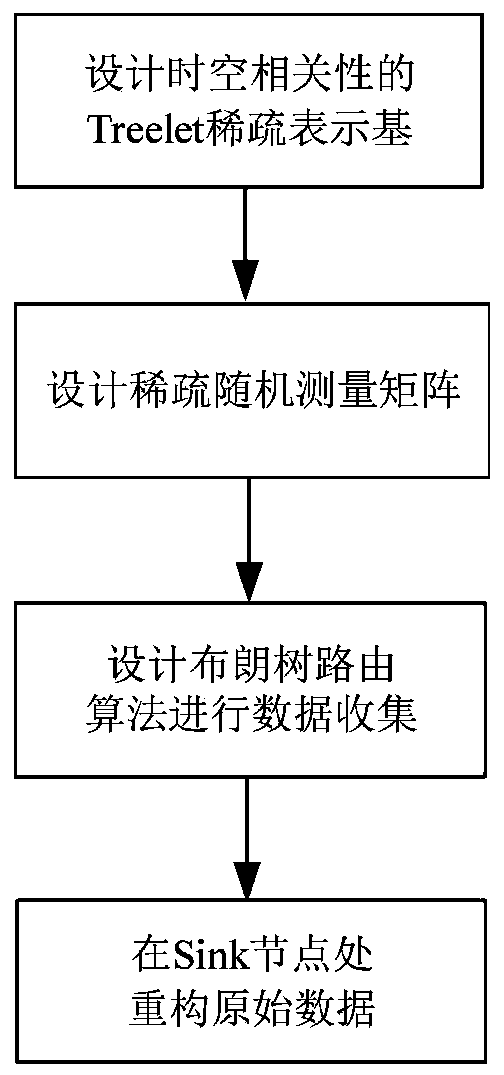
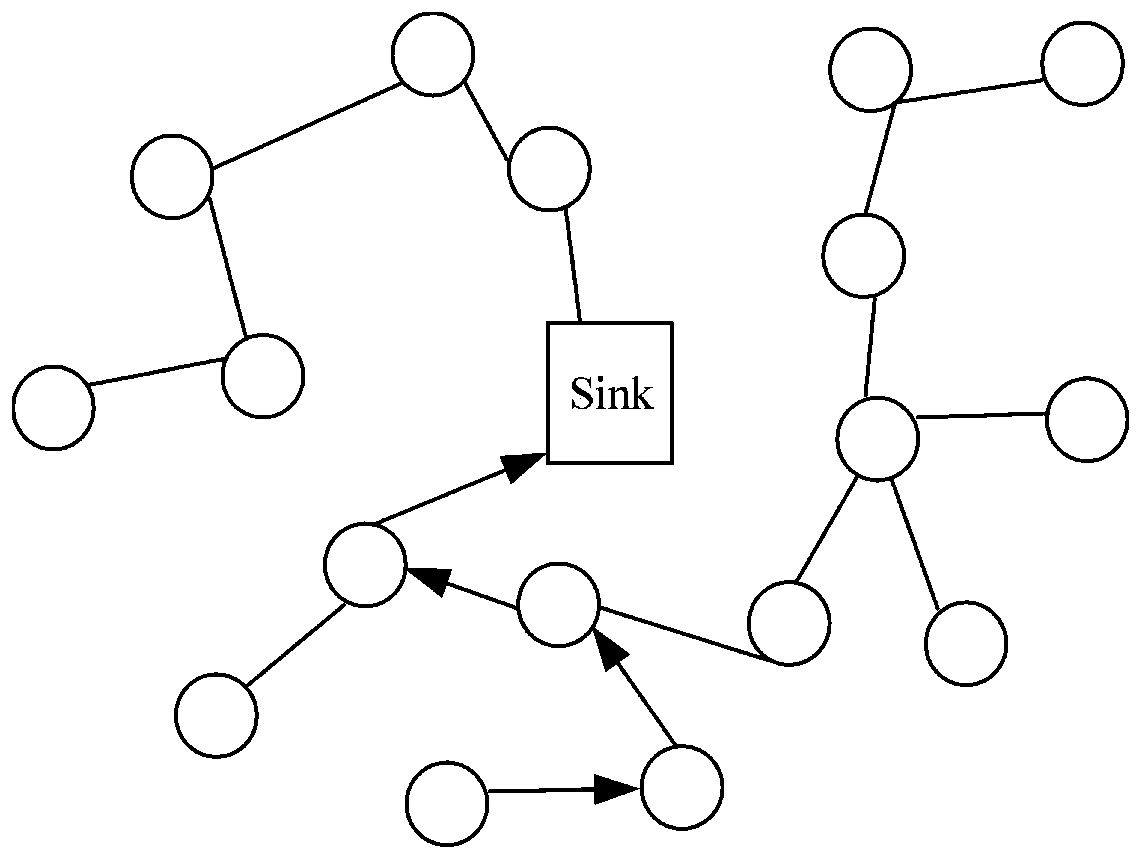
The invention discloses a compressed data collection method for a mobile wireless sensor network, which comprises the following steps of: firstly, designing a Treelet-based sparse representation baseby utilizing the space-time correlation of sensor node perception data; secondly, designing a sparse random measurement matrix; then, designing a Brown tree routing algorithm for data collection; andfinally, carrying out compressed data reconstruction at the Sink node according to the sparse representation base, the sparse random measurement matrix and the Brown tree route. By adopting the method, the data collection efficiency of the sensor network can be improved, the total cost of the nodes of the sensor network is reduced, and the life cycle of the network is prolonged to a certain extent.
Owner:HUAIYIN INSTITUTE OF TECHNOLOGY
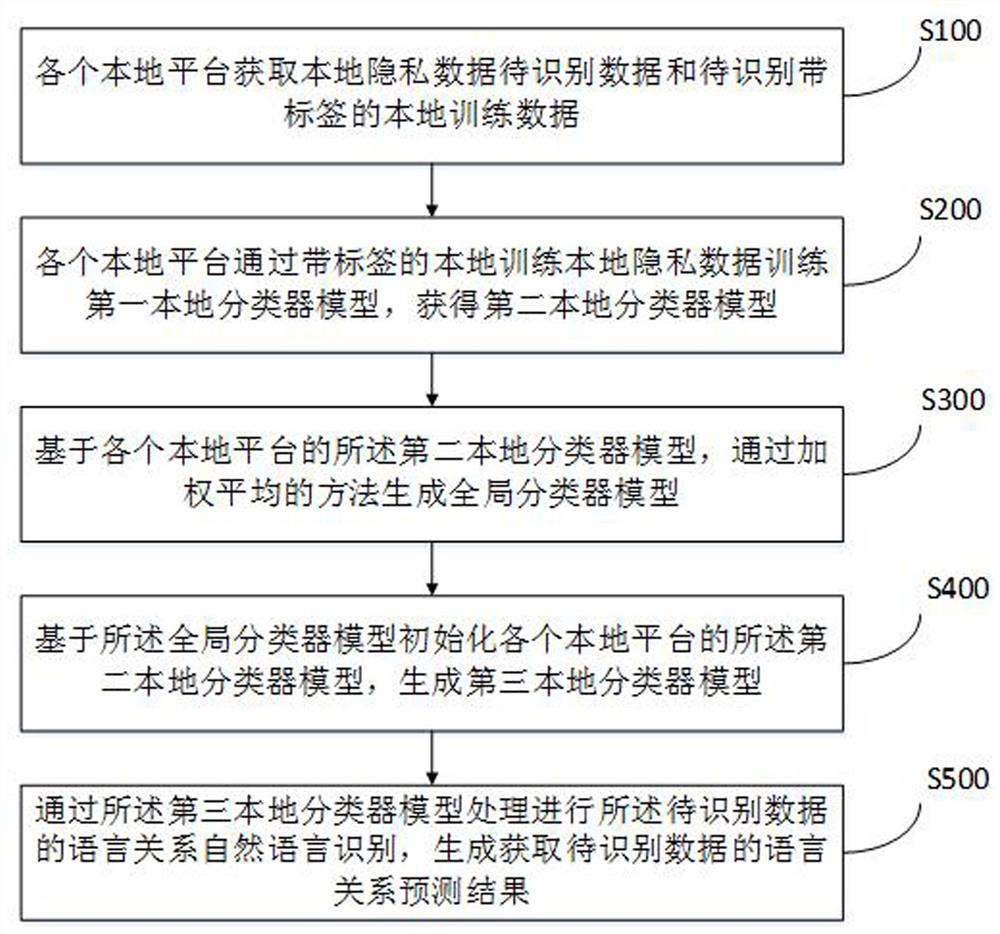
Federal learning-based distributed language relationship identification method, system and device
ActiveCN112101578AImprove collaborationSolve data silosEnsemble learningCharacter and pattern recognitionCategorical modelsEngineering
The invention belongs to the field of data identification, particularly relates to a distributed language relationship identification method, system and device based on federated learning, and aims tosolve the problem that a plurality of participants are difficult to perform joint modeling on the basis of not sharing data. The method comprises the steps that each local platform obtains to-be-recognized data and local training data with labels, a local classifier model is trained according to the local training data, the trained classifier models are integrated into a global classifier model,the local classifier model is initialized through the global classifier model, and to-be-identified data is identified by using the initialized local classification model to obtain a language relationship prediction result. According to the method, the local platform is combined with other platforms to perform data use and machine learning modeling on the basis of not sharing data, so that the training collaboration of the natural language recognition model is improved, the problem of data islands is solved, and the total amount and requirements of training data required for training the modelby each platform are reduced.
Owner:INST OF AUTOMATION CHINESE ACAD OF SCI
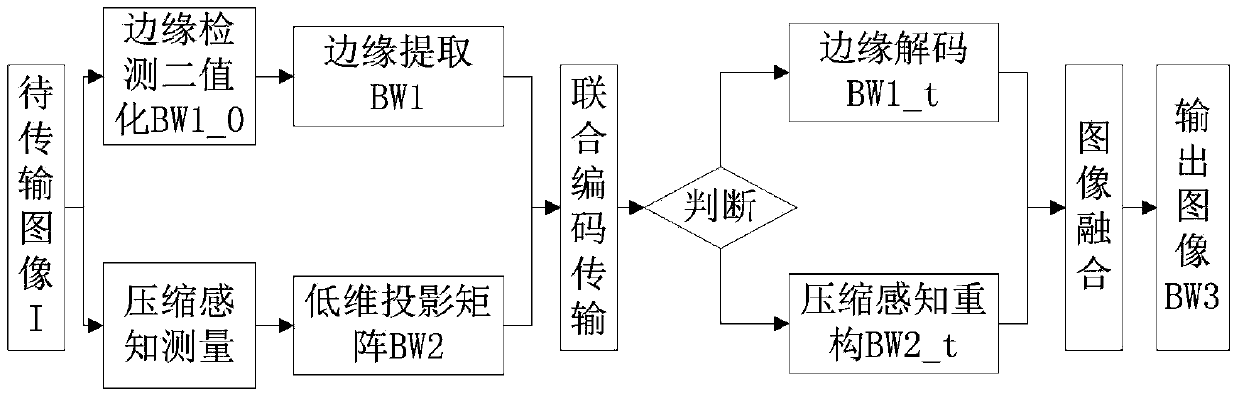
A compressed sensing compensation method based on an edge extraction and image fusion technology
InactiveCN104217431ARich image detail displayAccurate image detail displayImage enhancementImage analysisHat matrixEdge extraction
The invention relates to a compressed sensing compensation method based on an edge extraction and image fusion technology. The compressed sensing compensation method based on an edge extraction and image fusion technology comprises the following steps: at a sending end, inputting an original image I to be transmitted, extracting in advance an edge feature of the original image I in two stages, and obtaining a sparse matrix BW1 containing edge information of the original image; executing space-domain random sampling on the original image I by adopting a compressed sensing measurement method, and obtaining a low-dimensional projection matrix BW2 of the original image; integrating element information in the sparse matrix BW1 containing edge information of the original image and in the low-dimensional projection matrix BW2 of the original image, and transmitting the integrated element information; at a receiving end, executing edge decoding on transmission data, and reconstructing the low-dimensional projection matrix of the original image; executing registration on two images obtained, executing fusion on them by using a space-domain fusion principle, and outputting a final result BW3. The compressed sensing compensation method based on an edge extraction and image fusion technology has the advantages of the lower transmission cost and better ability of noise resistance.
Owner:TIANJIN UNIV
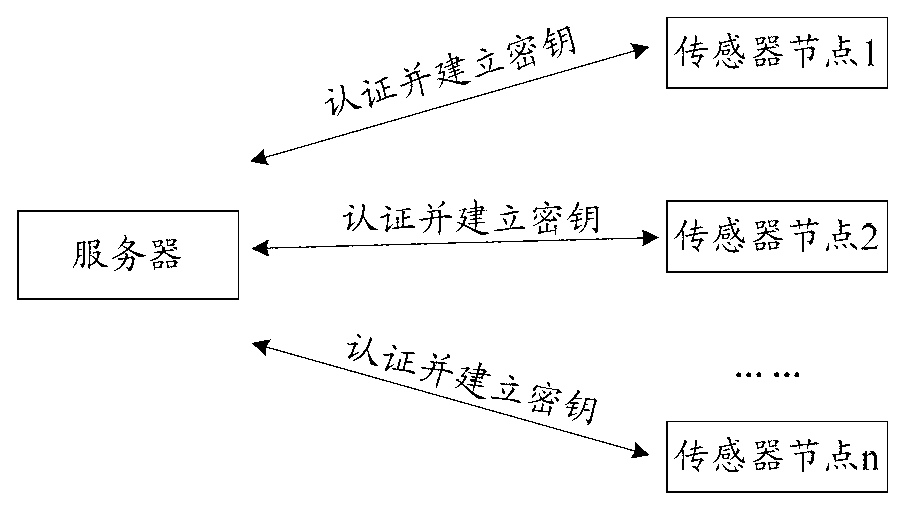
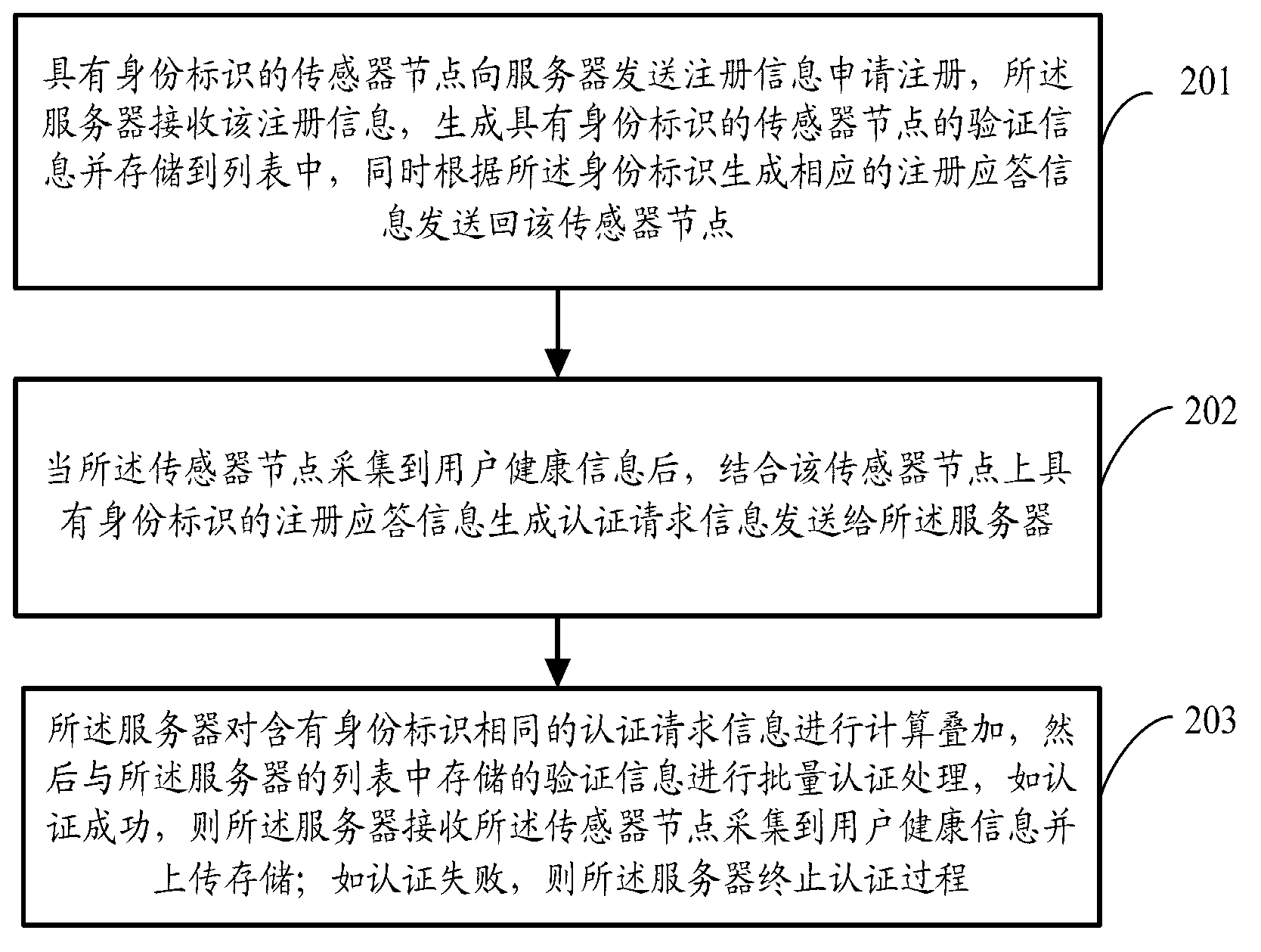
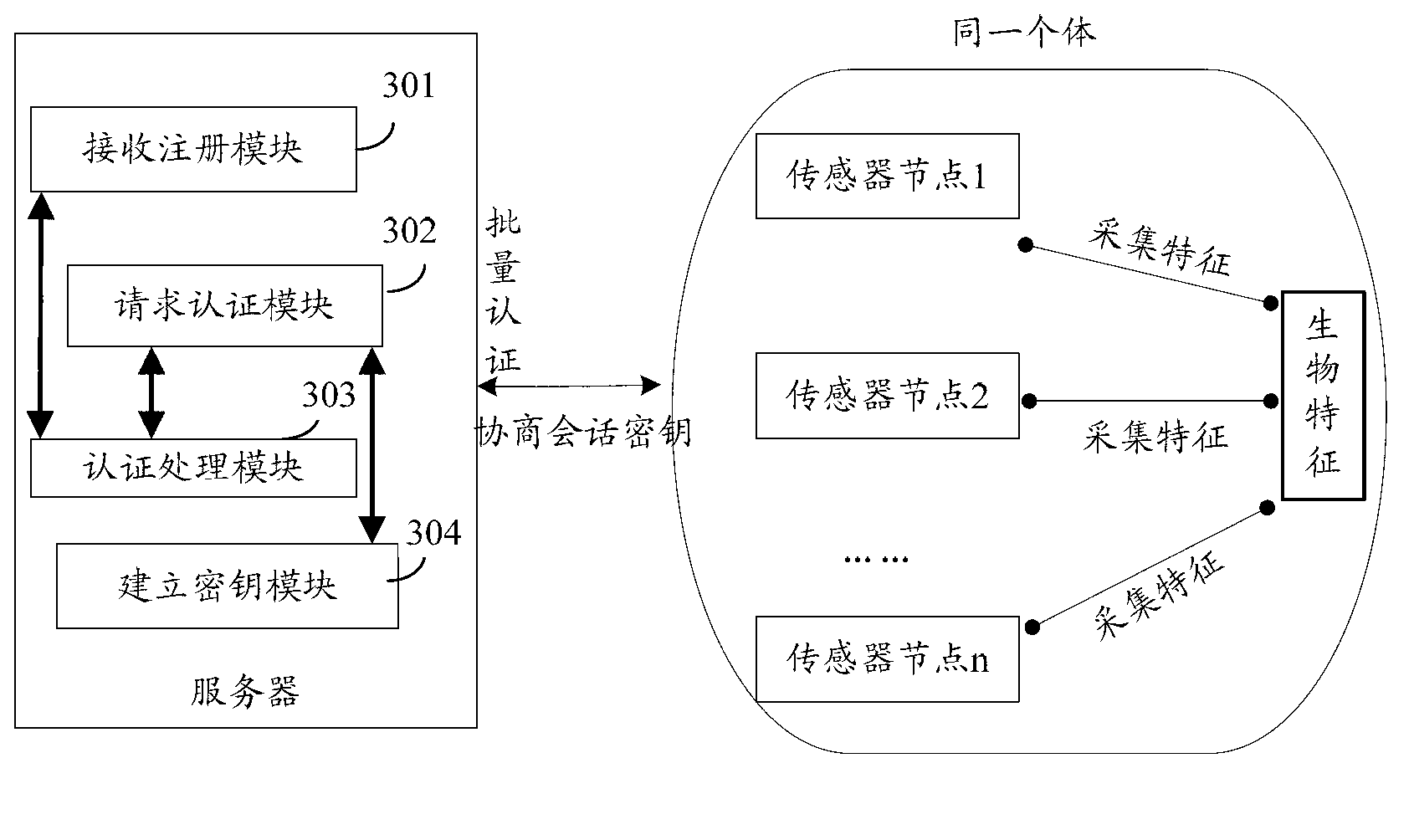
Method and server for identification in batches based on biological characteristics
InactiveCN103297235ARealize batch authenticationReduce consumptionUser identity/authority verificationDigital data authenticationPasswordSensor node
The invention discloses a method and server for identification in batches based on biological characteristics. The method comprises the steps that registration information is sent to the server by a sensor node with identity identification, verification information of the sensor node with the identity identification is generated by the server and stored in a list, and meanwhile corresponding registration response information is generated according to the identity identification and sent back to the sensor node; when user health information is collected by the sensor node, verification request information is generated with combination of the registration response information with the identity identification of the sensor node and sent to the server, calculation and superposition are conducted on verification request information with the same identity identification, identification processing in batches is conducted on the verification information stored in the list, and if verification is successful, the user health information collected by the sensor node is received by the server, uploaded and stored; and if verification is failed, the process of verification is stopped. According to the method and service for identification in batches based on the biological characteristics, the problems that verification cost is high in a personal health management system and a verification token or a password can be lost and forgotten easily are solved.
Owner:BEIJING UNIV OF POSTS & TELECOMM +2
Two-level policy decision-based access control method and system
The invention discloses a two-level policy decision-based access control method and a two-level policy decision-based access control system, and belongs to the field of access control in information safety. In the method, a local policy decision point (PDP) is deployed at a policy enforcement point (PEP) end, and the local PDP makes a decision for an access request according to a local policy cache, and if the local PDP cannot determine that the decision is a deterministic decision, a central PDP finally finishes the decision according to a system policy library. The system comprises a policydecision server, an attribute publishing point and a plurality of resource servers, wherein a policy enforcement point (PEP) and a local policy decision point (PDP) are deployed on each resource server; and a central policy decision point (PDP) is deployed on the policy decision server. The invention has a good dynamically adjusted elastic system framework, fully utilizes the computing resources of the PEP end, lightens the burden of the central PDP, reduces the network transmission overhead and effectively improves the access control efficiency at extremely low policy update cost.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
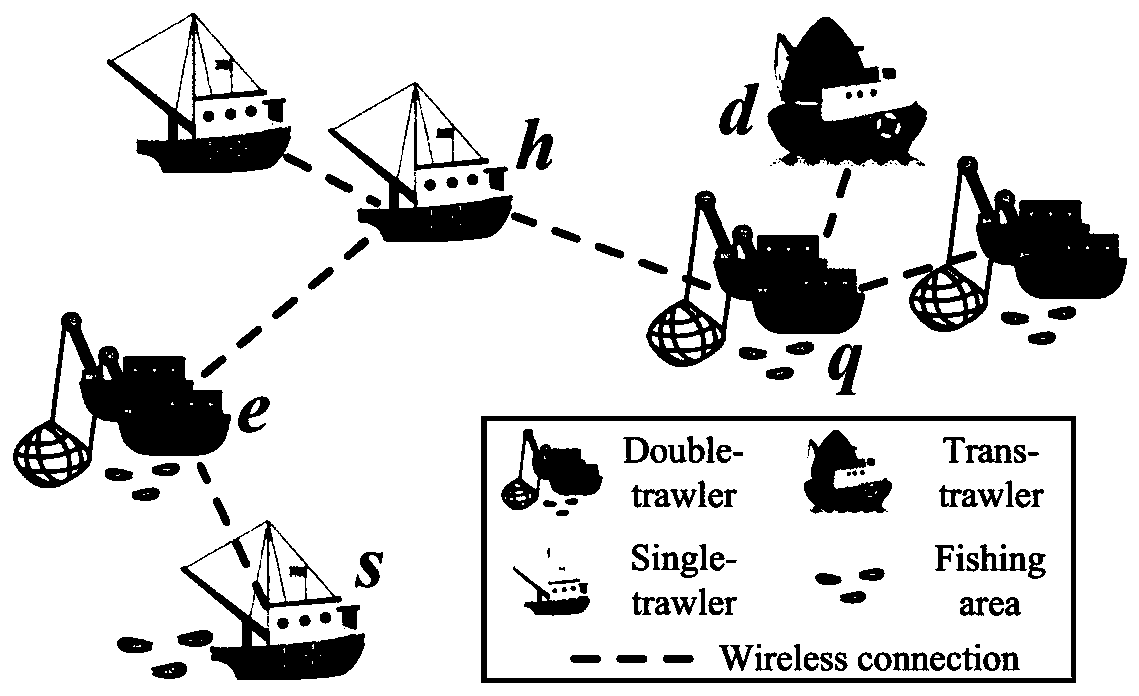
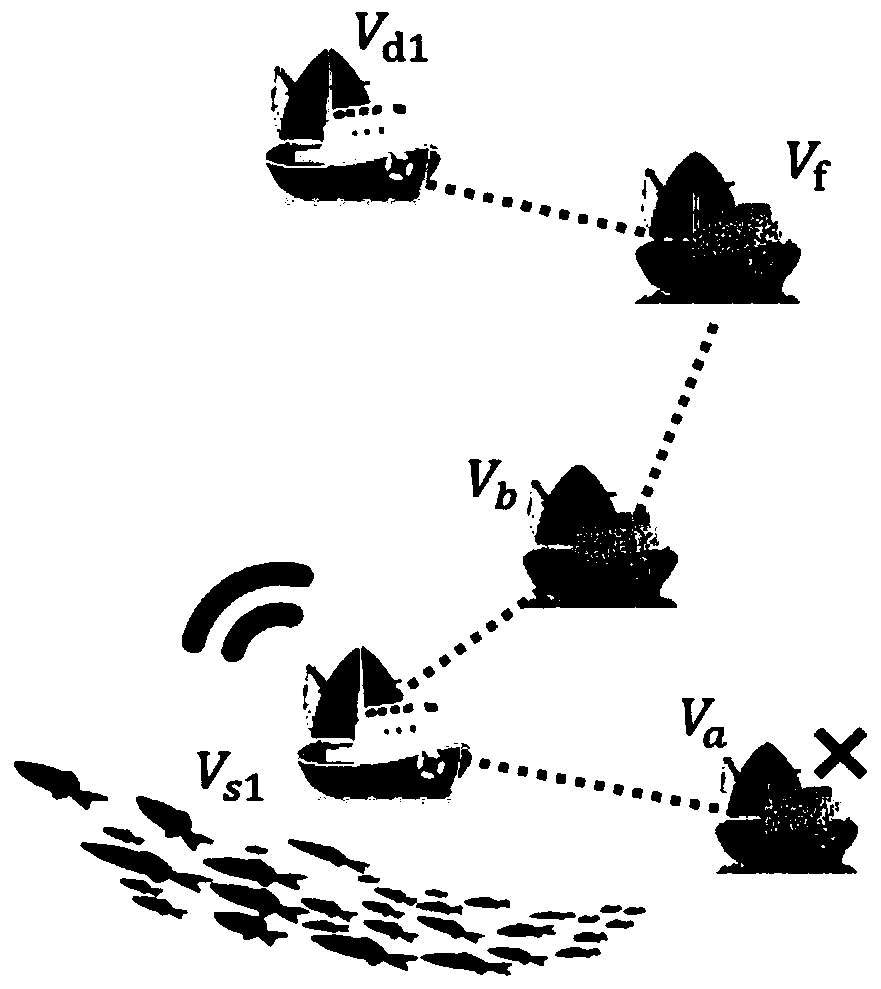
Ship network routing algorithm based on social familiarity
ActiveCN110691395AEliminate maintenance costsReduce transmission costNetwork topologiesAlgorithmSocial graph
The invention discloses a ship network routing algorithm based on social familiarity, and particularly relates to the technical field of data transmission of marine ship ad hoc networks. The defect that existing research is not based on real ship trajectory data, most simulators are adopted to simulate the motion of ships, and only simple route simulation can be achieved is overcome. According tothe ship network routing algorithm based on the social familiarity, the social relation between ships is calculated according to historical navigation information of the ships, so that a ship social network is constructed, and the next hop selection of routing is guided according to the encountering probability between the ships reflected in the ship social network information. The algorithm mainly comprises the following steps that: firstly, ships upload historical and real-time navigation information to the Internet of ships to generate a ship social network formed by social familiarity among the ships; secondly, the probability of meeting between ships is calculated according to the ship social network graph; and finally, the ship with the highest meeting probability with the target ship in the nearby ships is selected as the next hop.
Owner:OCEAN UNIV OF CHINA
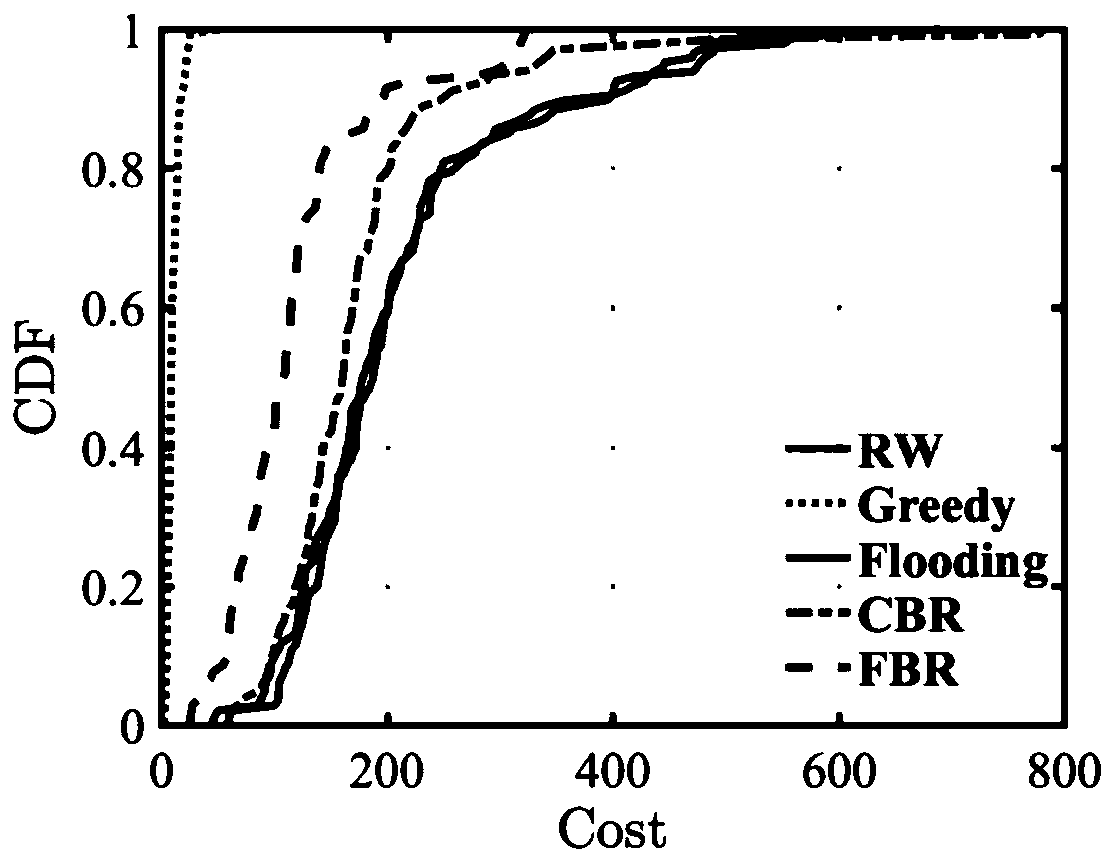
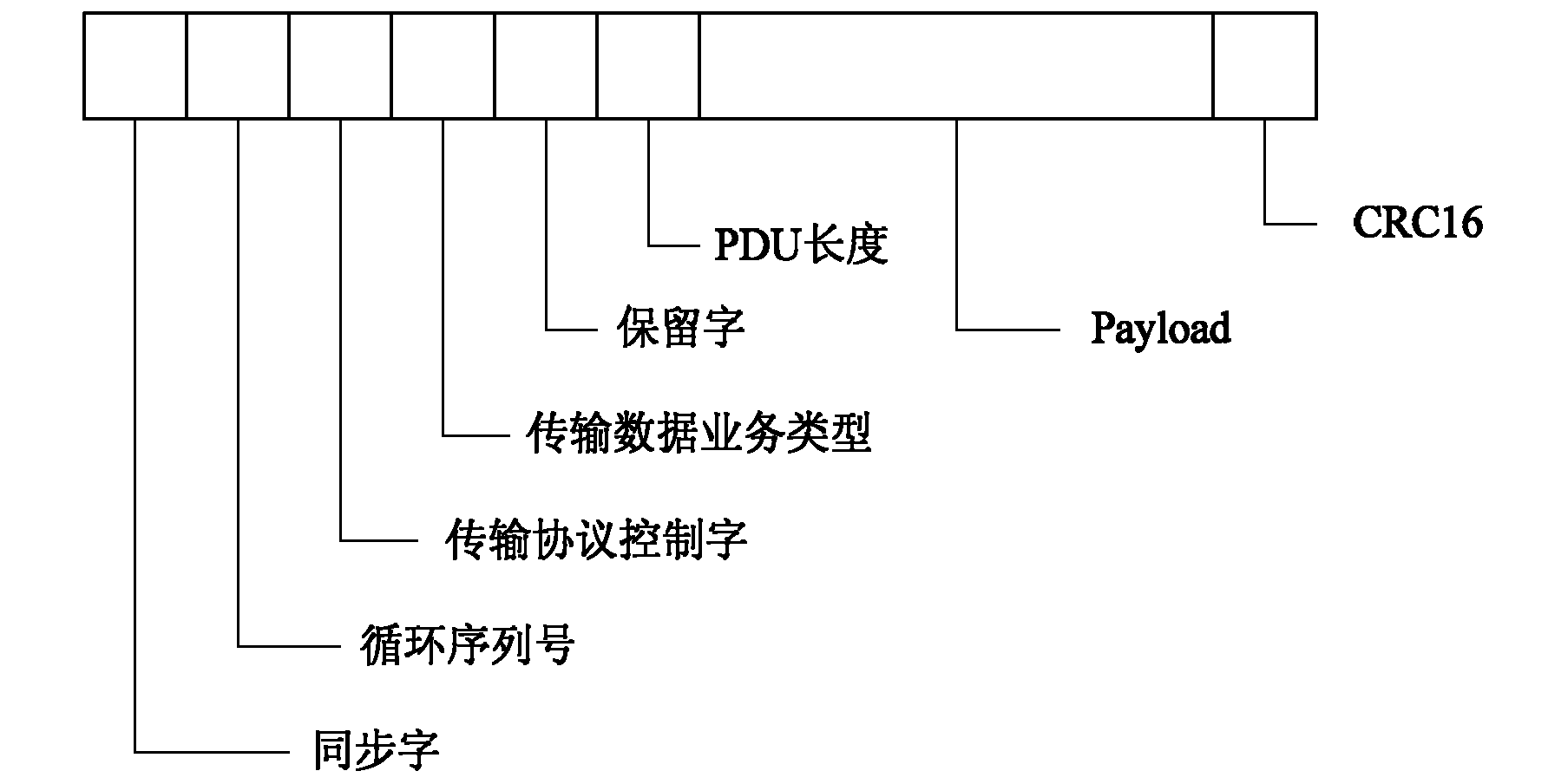
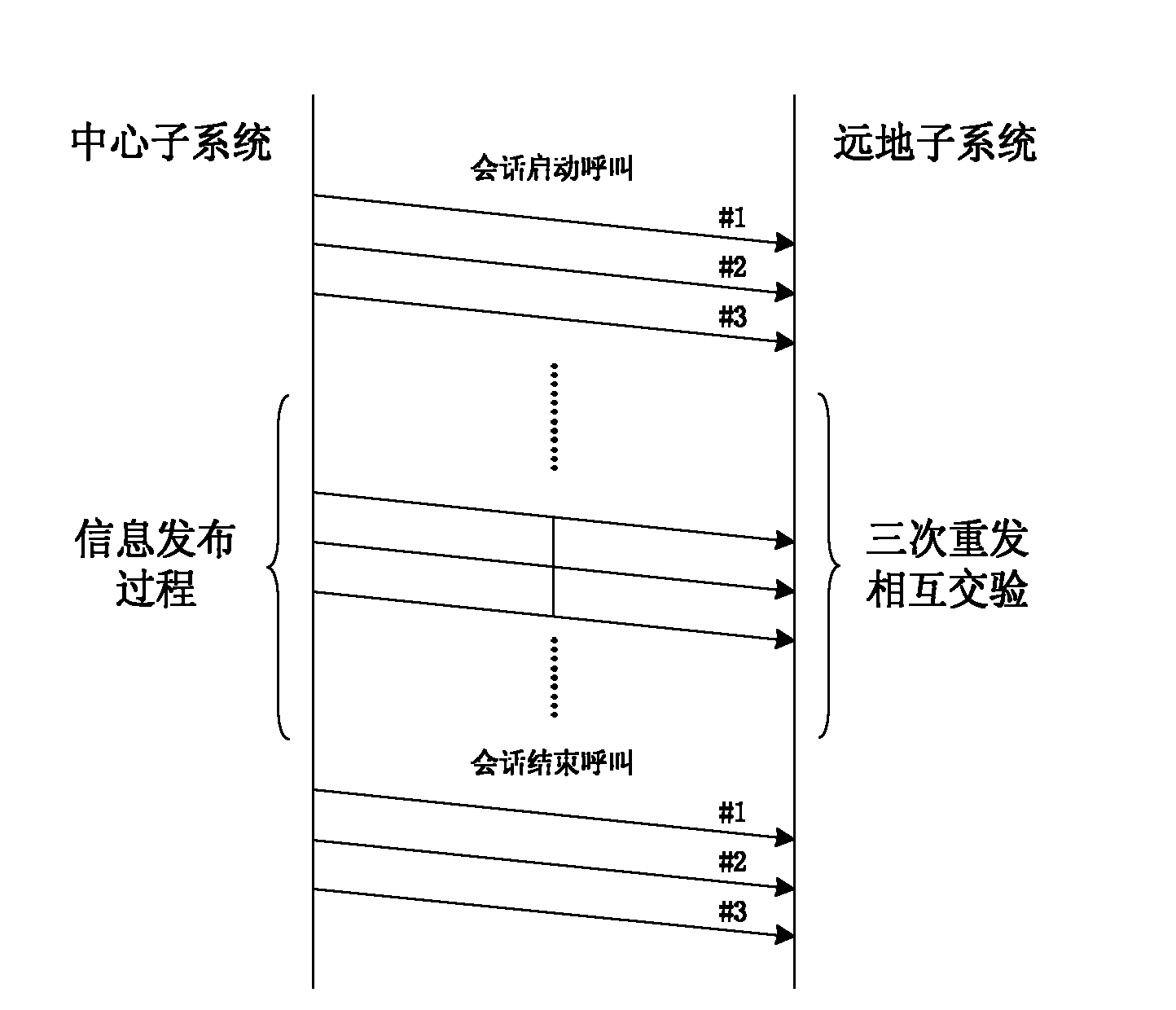
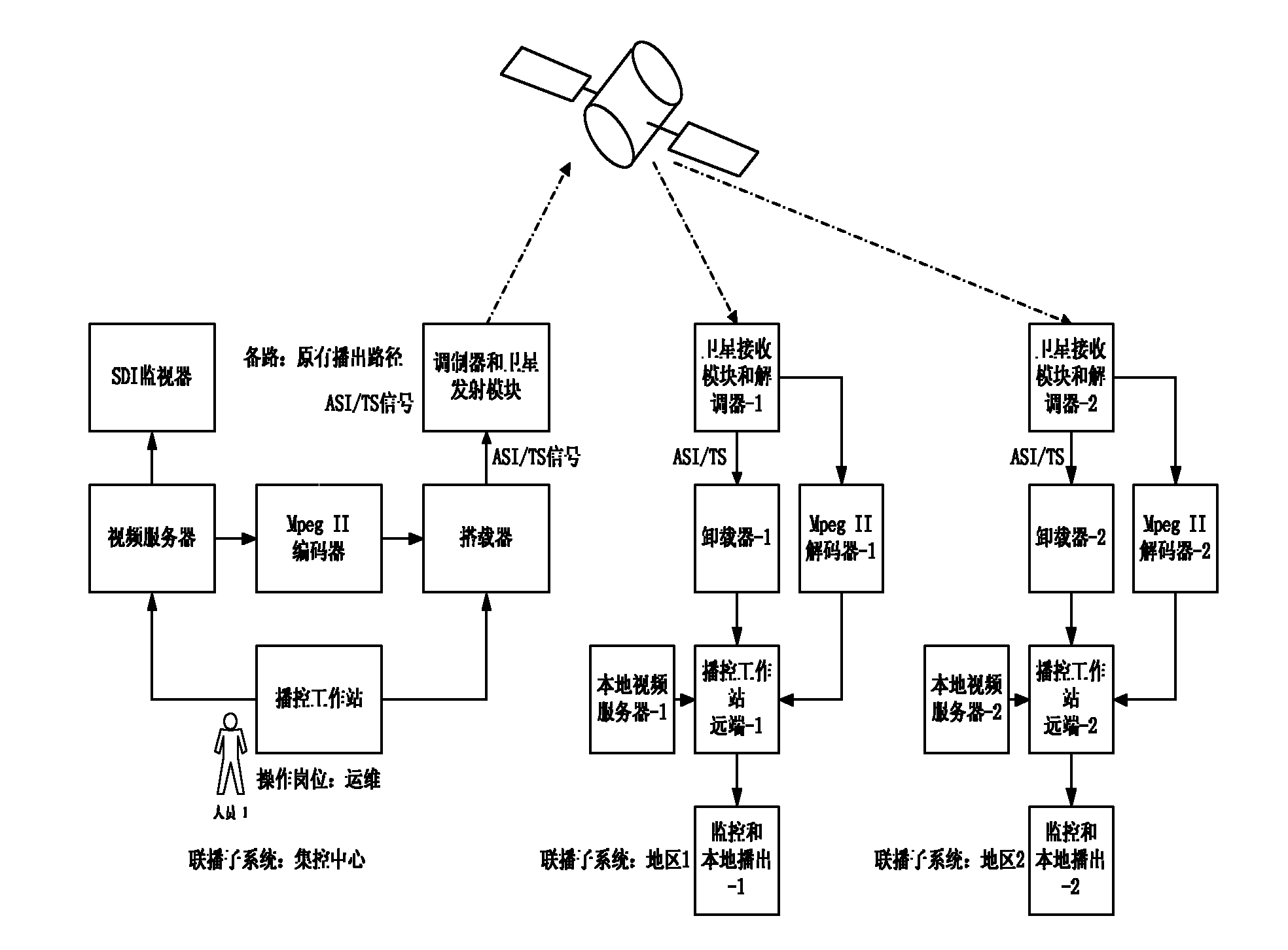
Method using information loaded by Mpeg II video stream to establish reliable transmission channel
InactiveCN101860742AImprove usabilityImprove stabilityPulse modulation television signal transmissionTransmissionTransmission protocolComputer hardware
The invention discloses a method using information loaded by Mpeg II video stream to establish a reliable transmission channel. A loader and an unloader are respectively arranged in a centralized control type simulcast system architecture, and the technical scheme utilized by the method is as follows: (1) constituting scattered bits obtained during a video loading process into a bit stream; (2) designing a protocol data unit on the basis of the bit stream; and (3) establishing a transport protocol to realize a reliable and stable transport channel through data unit synchronization and various error control. The invention has the advantages that the transmission channel can cover and transmit to areas capable of being covered by satellite signals along with television signals and satellites, which has wide obtained coverage, small transmission cost and good synchronization, thus facilitating a center emitting signals to centrally control the subsystems to load important information and realizing the control on far simulcast subsystems within the coverage area of satellite signals.
Owner:上海东方传媒集团有限公司
Data generation method and device, equipment and storage medium
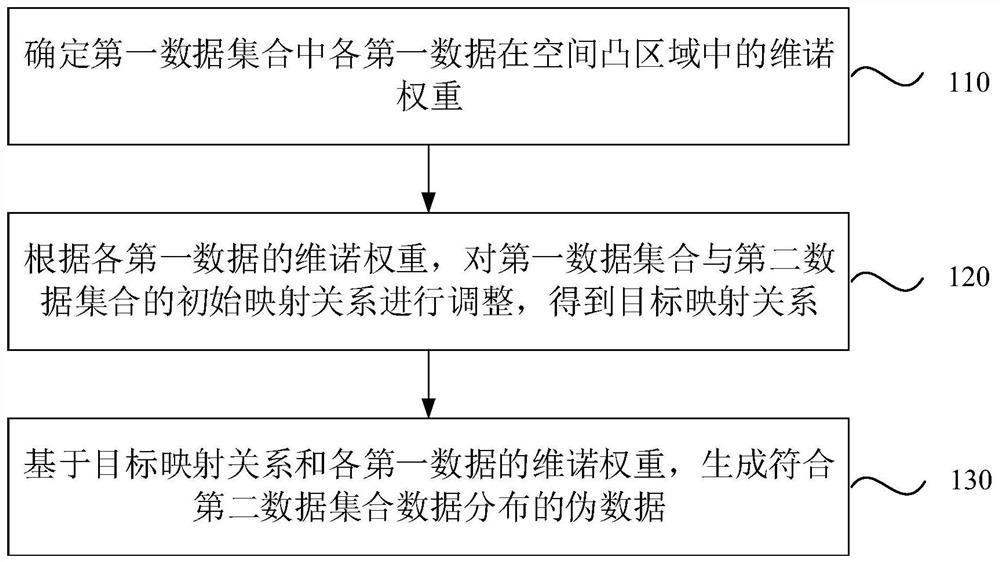
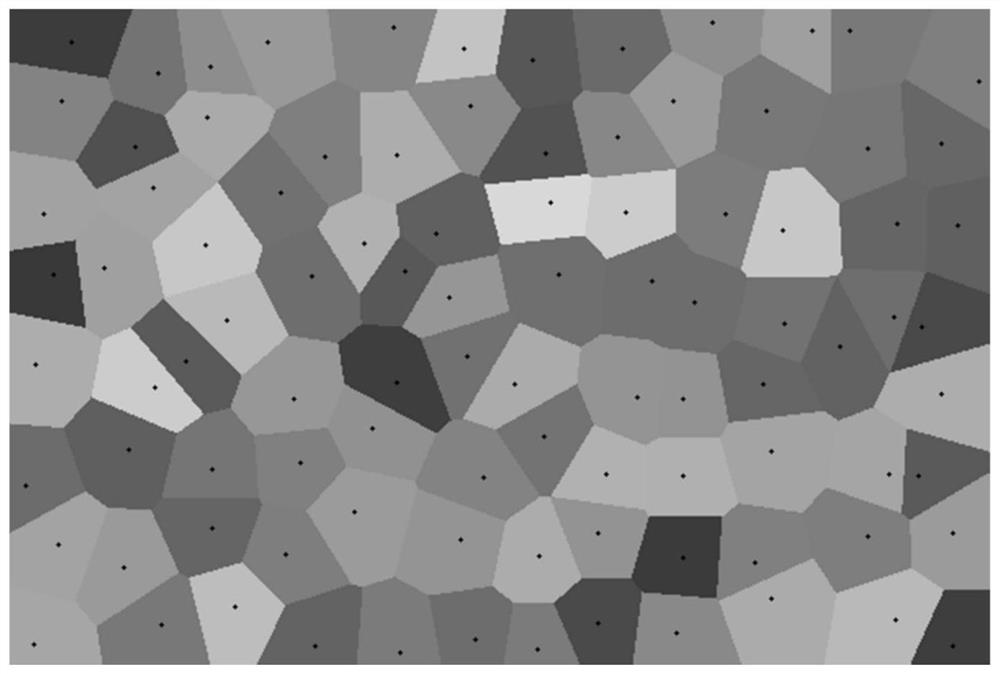
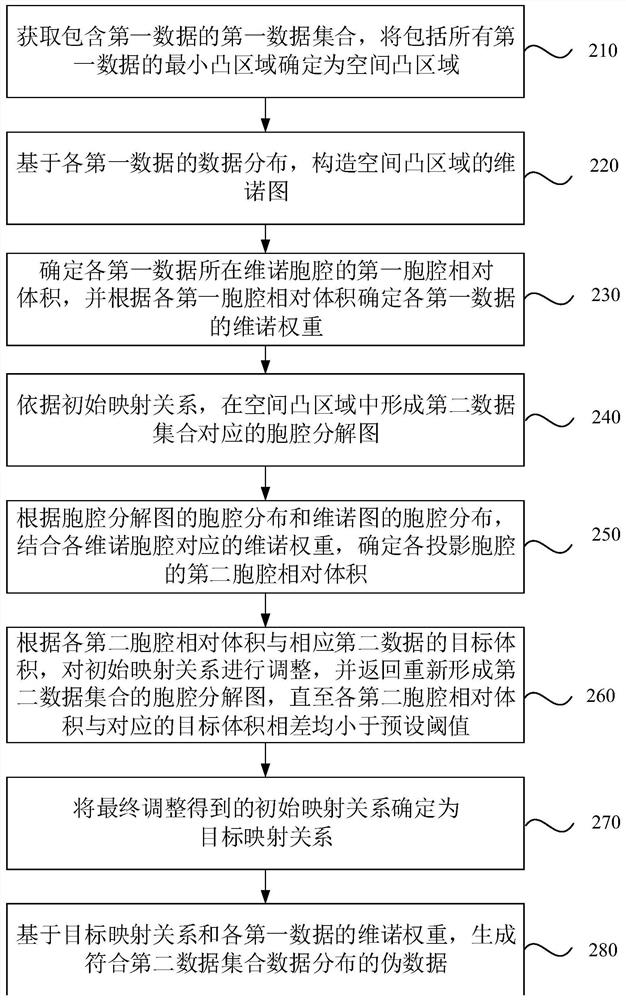
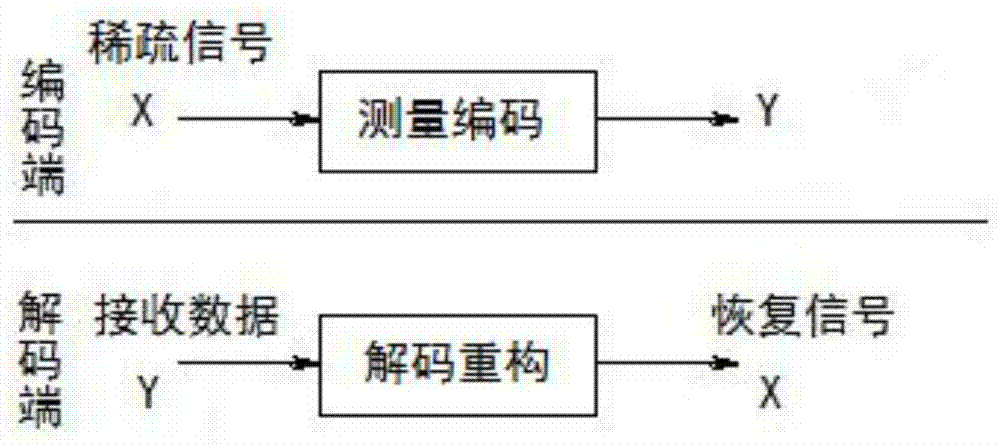
PendingCN112884162AReduce transmission costImprove accuracyCharacter and pattern recognitionMachine learningData setAlgorithm
The invention discloses a data generation method and device, equipment and a storage medium. The method comprises the following steps: determining a Voronoi weight of each piece of first data in a first data set in a spatial convex region; according to the Voronoi weight of each first data, adjusting an initial mapping relation between the first data set and a second data set to obtain a target mapping relation, wherein in the mapping relation satisfied by the data distribution of the first data set and the data distribution of the second data set, the transmission cost of the target mapping relation is minimum; and on the basis of the target mapping relationship and the Voronoi weight of each piece of first data, generating pseudo data conforming to the data distribution of the second data set. According to the method, the problems that the generated pseudo data is inaccurate and more singular points exist are solved, and the pseudo data is accurately generated, so that the effect of improving the accuracy of the generated model in machine learning is achieved.
Owner:SHANGSHANG TECH INC
A Physical Layer Intrusion Detection Method for Wireless Networks Based on Compressed Sensing
InactiveCN104135730BSmall scaleReduce transmission costTransmissionSecurity arrangementSignal-to-interference-plus-noise ratioPhysical layer
The invention discloses an intrusion detection method of a physical layer of a wireless network based on compressed sensing. The intrusion detection method comprises the following steps that: a sensor node detects an event signal; an SINR (Signal to Interference plus Noise Ratio) signal x is subjected to sparse transform to obtain a sparse representation form x' of the signal; y (y belongs to RM) is obtained by the sparse representation form x' (x' belongs to RN) of the SINR signal through a projection on a matrix phi; y is transmitted through the wireless network, and reaches a central aggregation node after passing a plurality of nodes; and sampling in the central aggregation node is detected by utilizing a CUSUM algorithm, and a detected result is reconstructed and reduced to obtain abnormal behavior data, and then subsequent processing is carried out. The intrusion detection method has the advantages that: through compressed signal sampling, data scale is reduced, and transmission cost is reduced, so that the abnormal condition of the physical layer can be quickly judged.
Owner:SOUTHWEST UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com