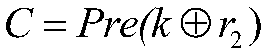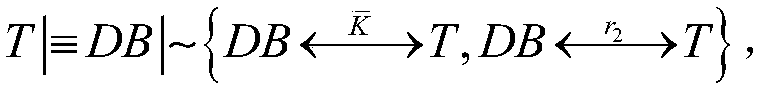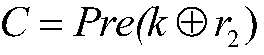Patents
Literature
272results about How to "Avoid security threats" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
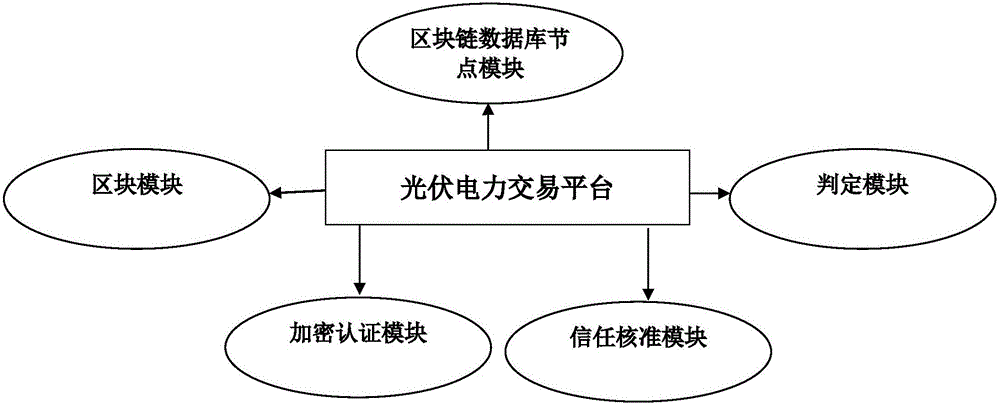
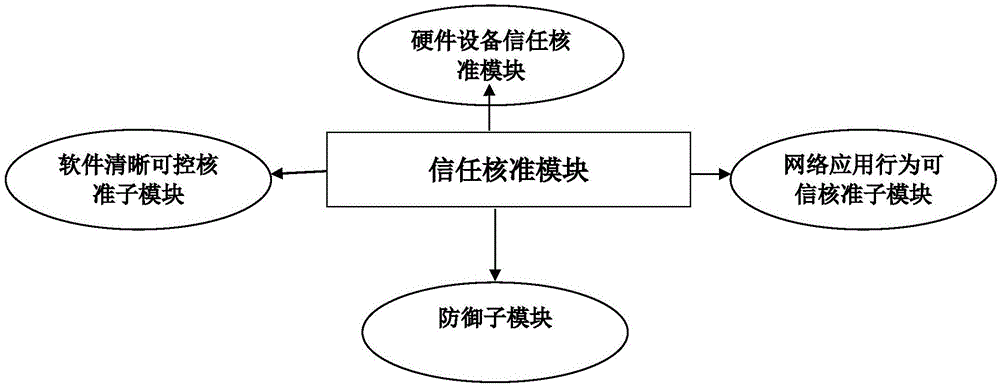
Trusted power grid transaction platform based on block chain technology
InactiveCN106296359AThe transaction is validConduct complianceBuying/selling/leasing transactionsSystems intergating technologiesElectric power transmissionPower grid
The invention provides a trusted power grid transaction platform based on block chain technology. The trusted power grid transaction platform comprises the components of (1), a power chain database node module which stores electric power transaction database copies at a plurality of nodes; (2), a block module, wherein the block chain database is divided into a plurality of blocks which are related with electric power transaction, wherein each block comprises detailed information of transaction; (3) an encryption authentication module which acquires whole-network authentication through combining and encrypting transaction details and signatures of two parties or signature of one party; (4), a trust approval module which is connected with the encryption authentication module and is used for establishing a trusted power grid transaction system of the block chain; and (5), a determining module which determines a fact that the transaction is effect on the condition that encryption records that correspond with all nodes are consistent, and adds the transaction into a historical transaction chain; and if the block is ineffective, the information of a role breaking node is modified through consistent option of the nodes. The trusted power grid transaction platform safely and reliably perform various kinds of power grid transactions and furthermore improves credibility of the block chain technology.
Owner:SHENZHEN FANXI ELECTRONICS CO LTD
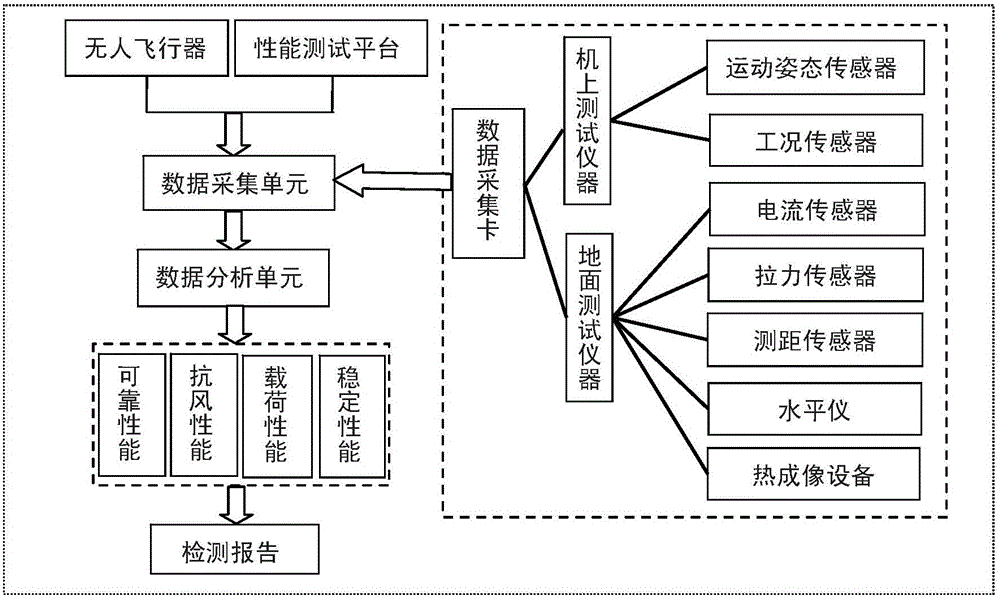
Performance test platform and method for multi-rotor unmanned aerial vehicle
ActiveCN105083588AFlexible swingAccurate and reliable performance indicatorsAircraft components testingFlight vehicleEngineering
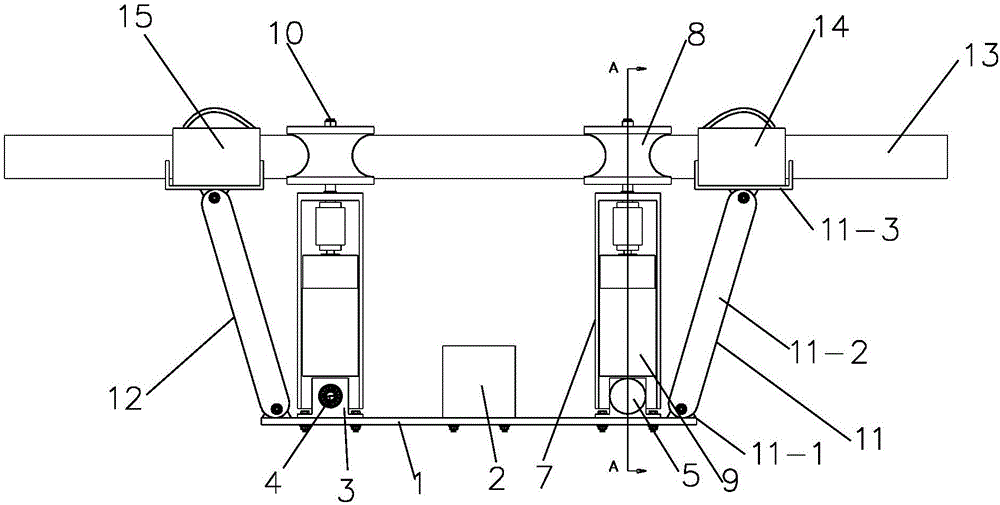
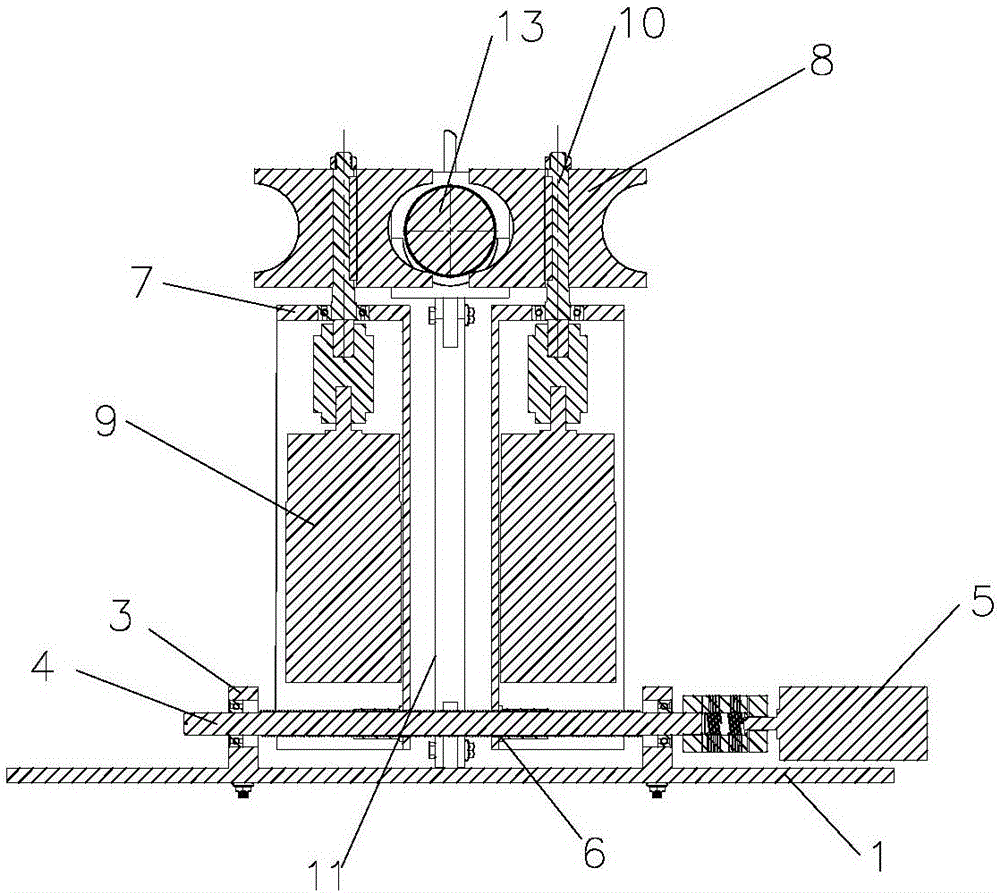
The invention discloses a performance test platform and method for a multi-rotor unmanned aerial vehicle. The test platform comprises a base, a stand column, a top frame, a performance test instrument and a calculation processing center; the bottom of the stand column is connected to the base through a ball-head universal bearing, and the top of the stand column is connected to the top frame through a ball-head universal bearing; the top frame is hung on an external rigid body through an elastic inhaul cable; a rack of the multi-rotor unmanned aerial vehicle is provided with a sleeving ring arranged on the stand column in a sleeving mode; the performance test instrument comprises an on-vehicle test instrument body which is arranged on the multi-rotor unmanned aerial vehicle and used for testing flight attitude information and work condition information of the multi-rotor unmanned aerial vehicle and a ground test instrument body which is arranged on the test platform and used for testing external response information of the multi-rotor unmanned aerial vehicle; the calculation processing center comprises a data collecting unit and a data analyzing unit. The test platform is simple in structure, good in flexibility and capable of accurately testing multiple performance indexes of the aerial vehicle.
Owner:SOUTH CHINA AGRI UNIV
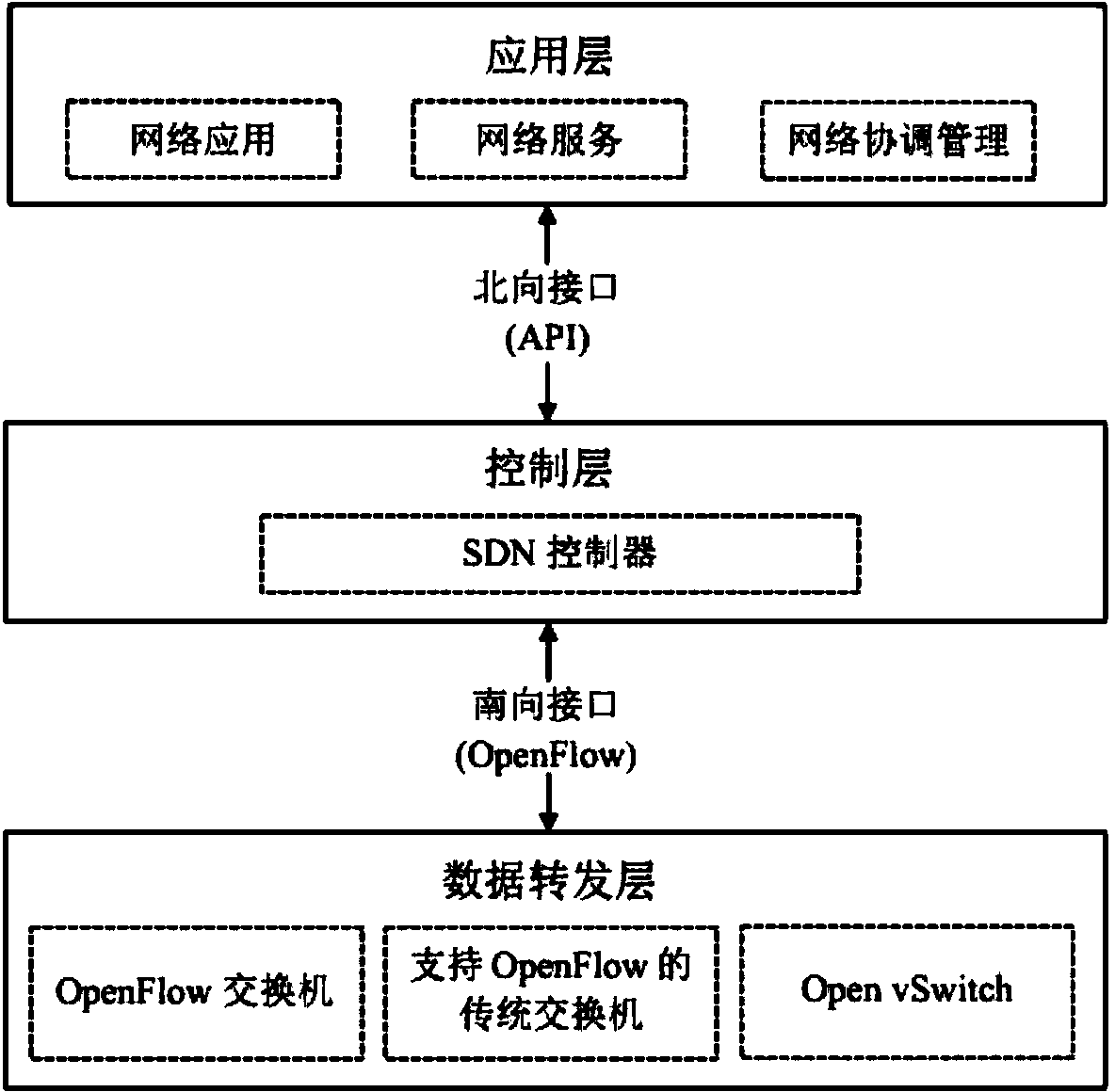
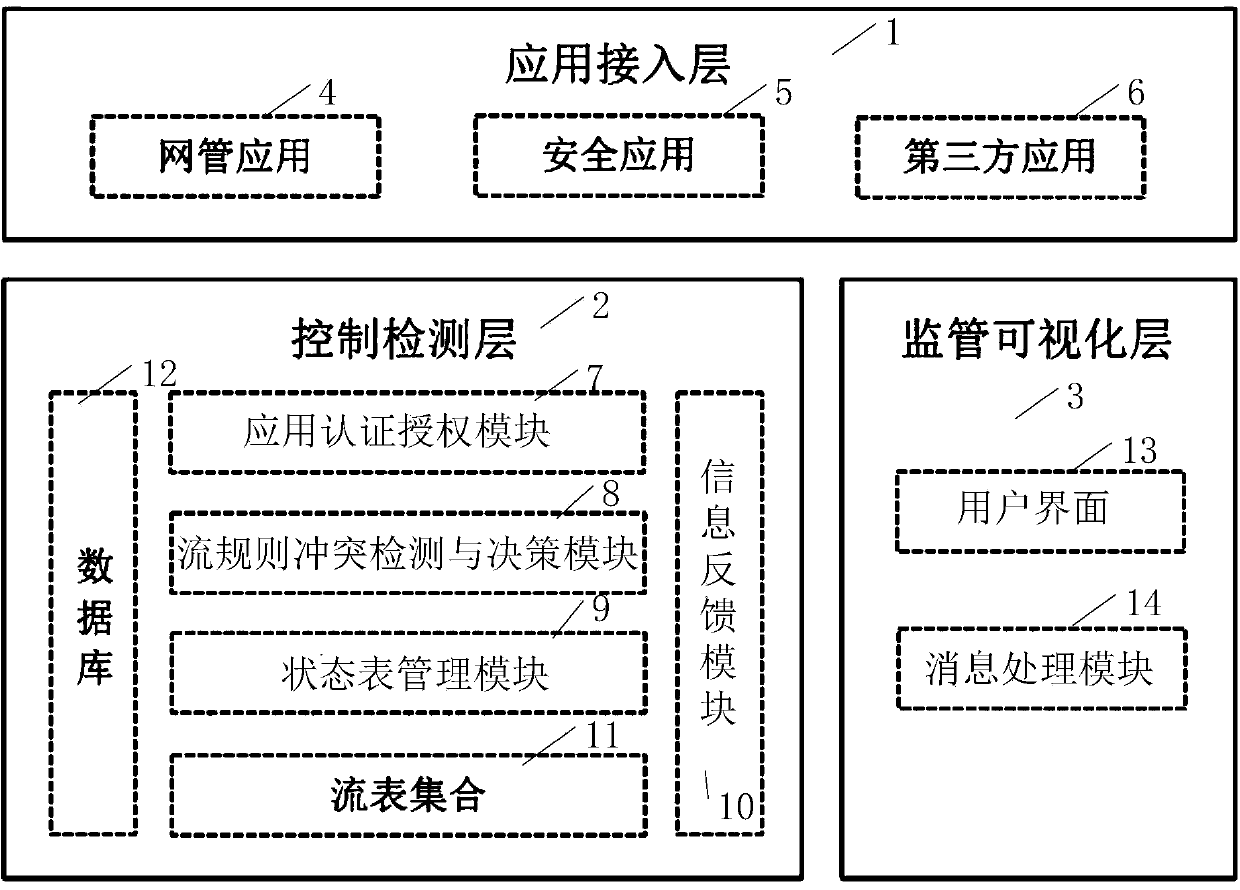
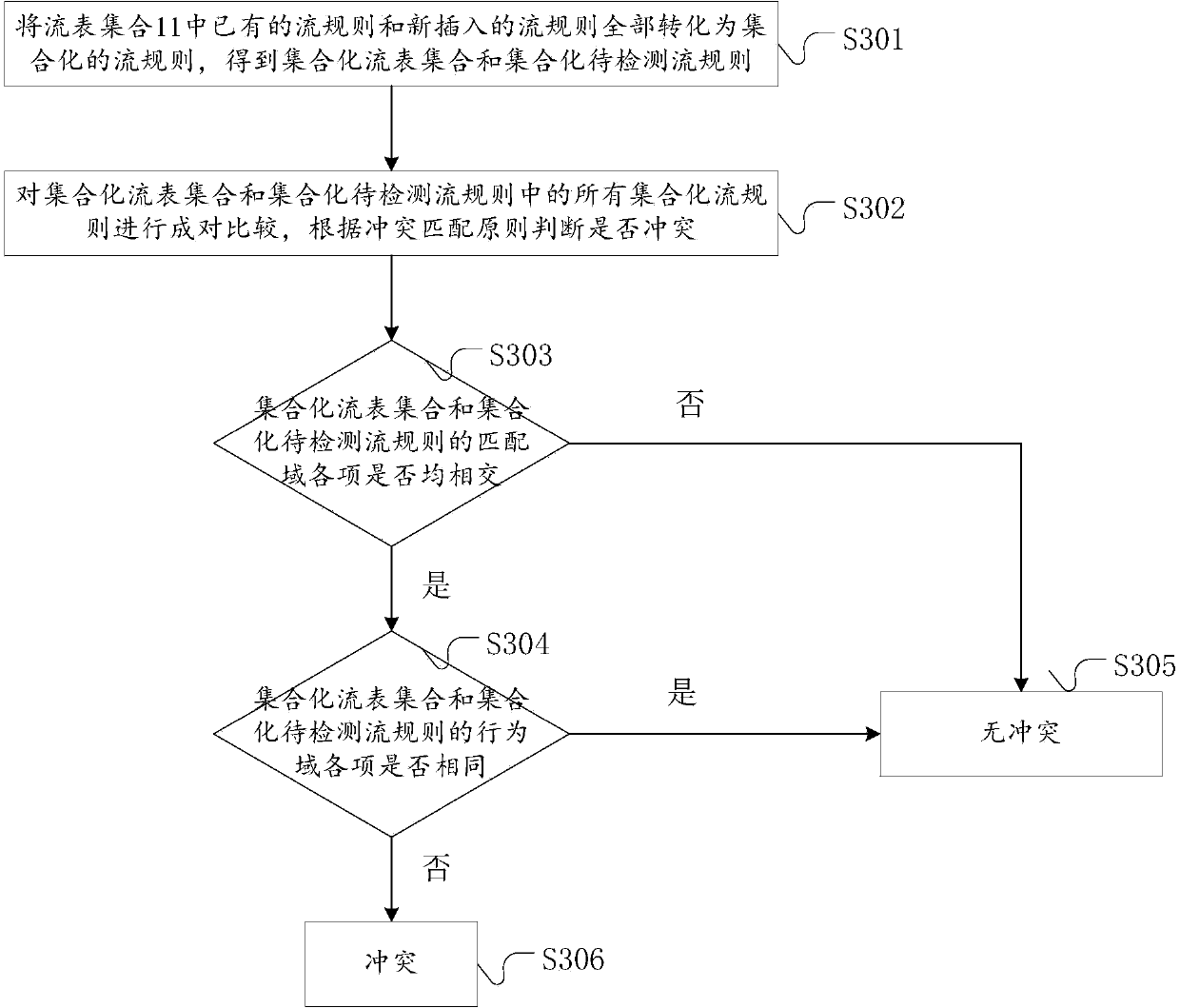
Policy conflict detection method and system for SDN (Software Defined Network) application
InactiveCN104202303AAvoid security threatsImprove scalabilityData switching networksAccess networkEngineering
The invention discloses a policy conflict detection method and system for an SDN (Software Defined Network) application. The method comprises the following steps: authenticating and authorizing an application waiting to access a network; giving a priority; performing conflict detection and reconciliation; feeding back a network state to network management personnel in real time; and establishing a comprehensive policy conflict detection framework specific to the SDN application in order to eliminate network security threats caused by an SDN. A set intersection-based flow rule policy conflict analysis algorithm adopted in the method is simple and stable, and is easy to extend, and policy conflict detection of intermediate behaviors such as Set in flow rules and policy conflict detection after the combination of the flow rules of different applications are realized. A flow rule policy conflict decision algorithm based on application priority comparison adopted in the method is simple and effective, and is easy to implement.
Owner:HUAZHONG UNIV OF SCI & TECH
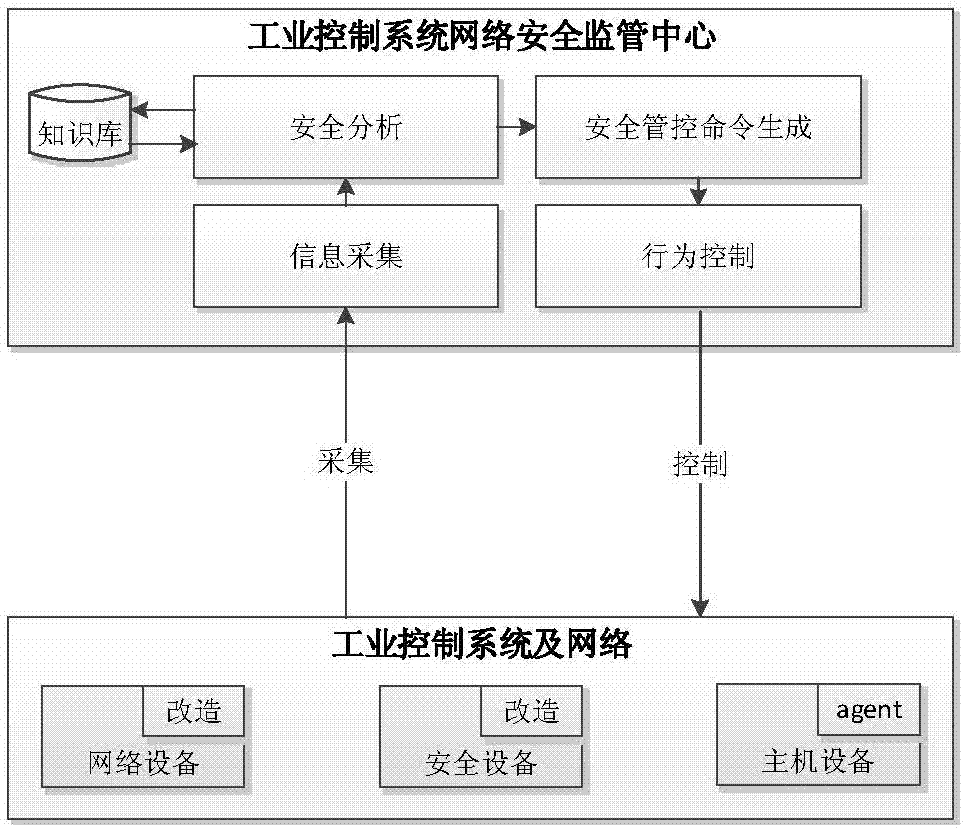
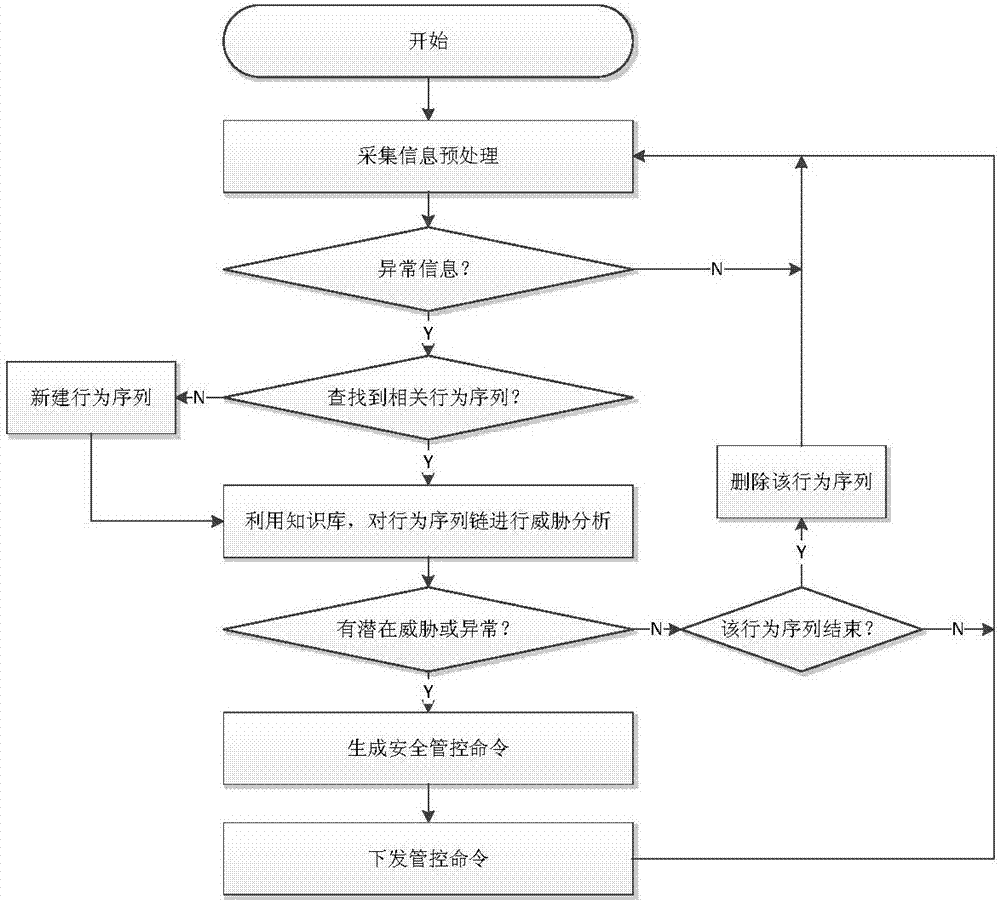
Network security monitoring method for industrial control system
ActiveCN107493265ARealize real-time monitoringRealize active defenseData switching networksRelevant informationIndustrial systems
The invention discloses a network security monitoring method for an industrial control system. The method comprises the following steps: collecting relevant information of an internal monitoring object of the industrial control system; performing security analysis on the collected relevant information; and when potential abnormal behavior is found through analysis, generating a relevant safety control order, and issuing the order to the relevant monitoring object for execution so as to block the abnormal behavior. According to the invention, real-time monitoring on major hidden security dangers of the industrial control system such as peripheral access, personnel operation, network external connection and the like is realized through abundant data acquisition of core networking equipment of the industrial control system. At the same time, through analysis processing on various behavior, the abnormal behavior is found and blocked timely, and thus real active defense of the industrial system is realized. For the current difficulty of effectively applying traditional security protection measures to the industrial control system, the major security threats to the industrial control system at present are well solved from the perspective of monitoring early warning.
Owner:NANJING NARI GROUP CORP +2
Warm knitted fabrics with one-way moisture conduction and rapid drying function and production process thereof
The invention discloses warm knitted fabrics with the one-way moisture conduction and rapid drying function and the production process thereof and belongs to the field of functional knitted fabrics. The warm knitted fabrics and the production process aim at solving the problems of the poor one-way moisture conduction function and the like of the existing fabrics. The warm knitted fabrics comprise a basic layer; the front side of the basic layer is a plain surface and a plurality of projections are distributed on the back side of the basic layer; a concaved sweat-absorbing groove is formed between every two adjacent projections; every projection is formed by polypropylene materials. According to the production process, a group of polypropylene yarns and a group of plain surface yarns are looped in order, circulated and alternated and intermeshed with each other along the weft direction of the fabrics to form a double-layer manufacturing structure; the front side of the basic layer of the obtained fabrics is the plain surface and the plurality of projections are distributed on the back side of the basic layer; every concaved sweat-absorbing groove is formed between the corresponding two adjacent projections; every projection is formed by the polypropylene materials. According to the warm knitted fabrics with the one-way moisture conduction and rapid drying function and the production process thereof, the one-way moisture conduction property of the fabrics is implemented.
Owner:TOREAD HOLDING GROUP CO LTD +1
Desynchronization resistant lightweight RFID bidirectional authentication protocol
ActiveCN103595525AFew rounds of interactionShorten the lengthKey distribution for secure communicationComputer hardwareThe Internet
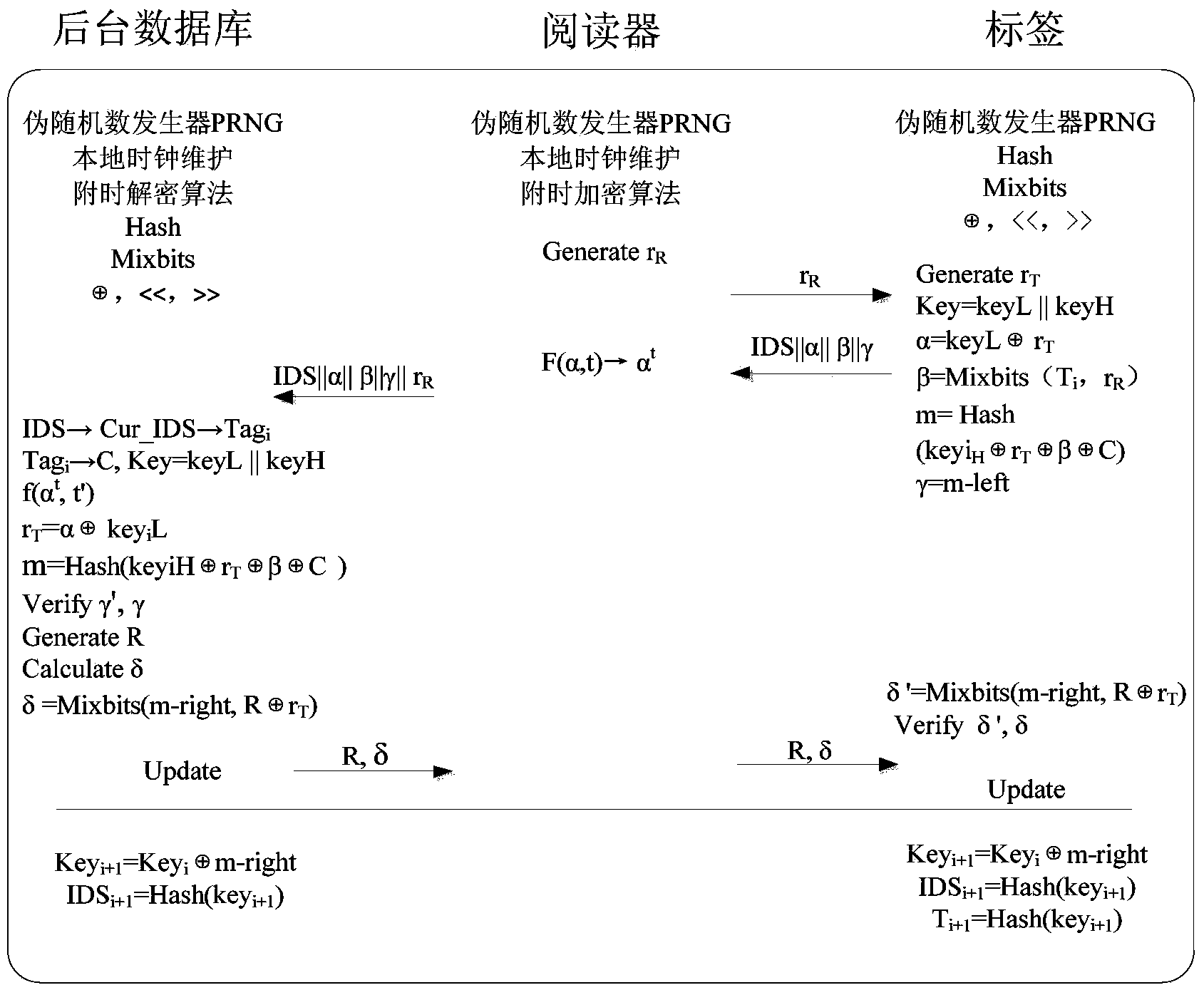
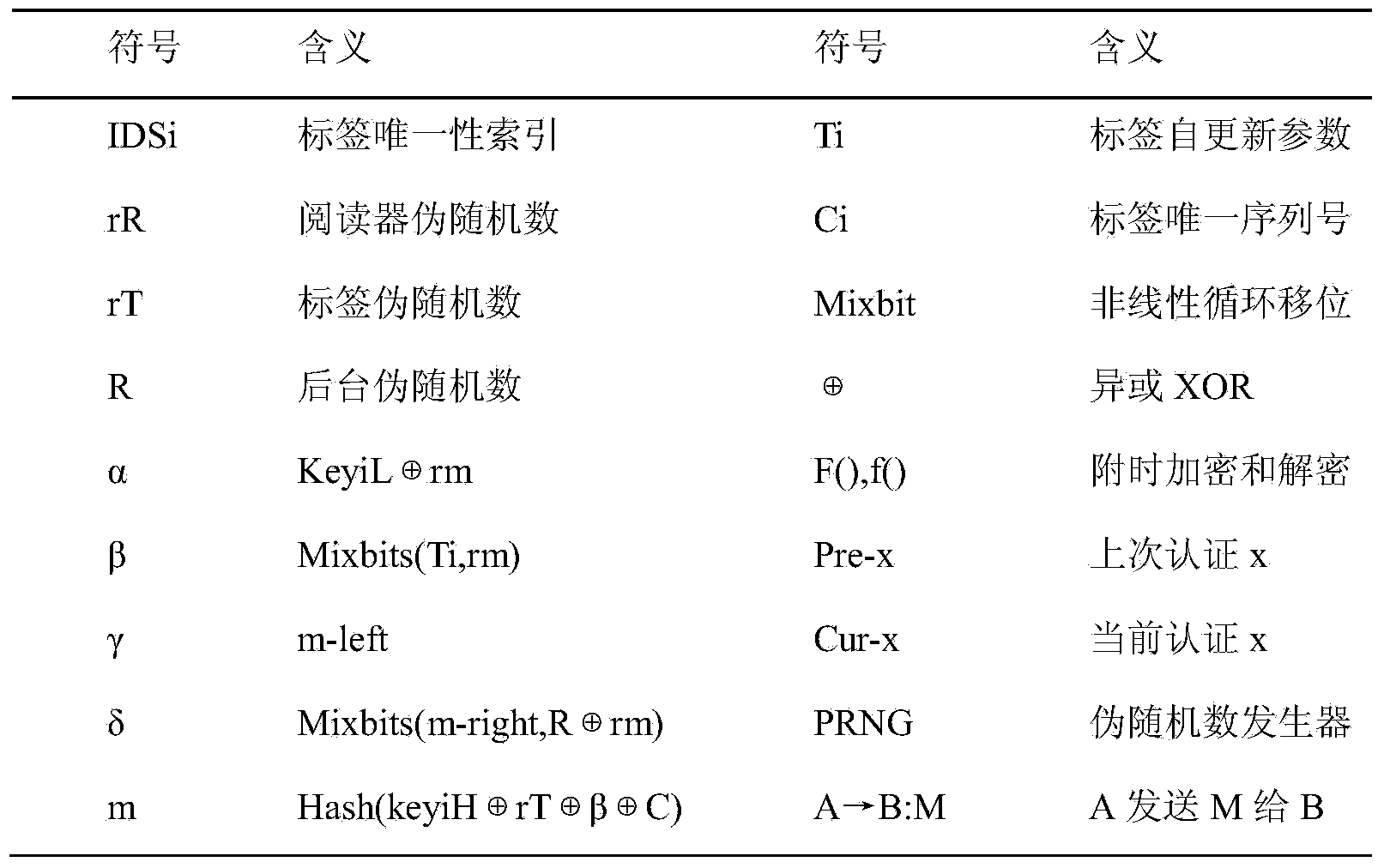
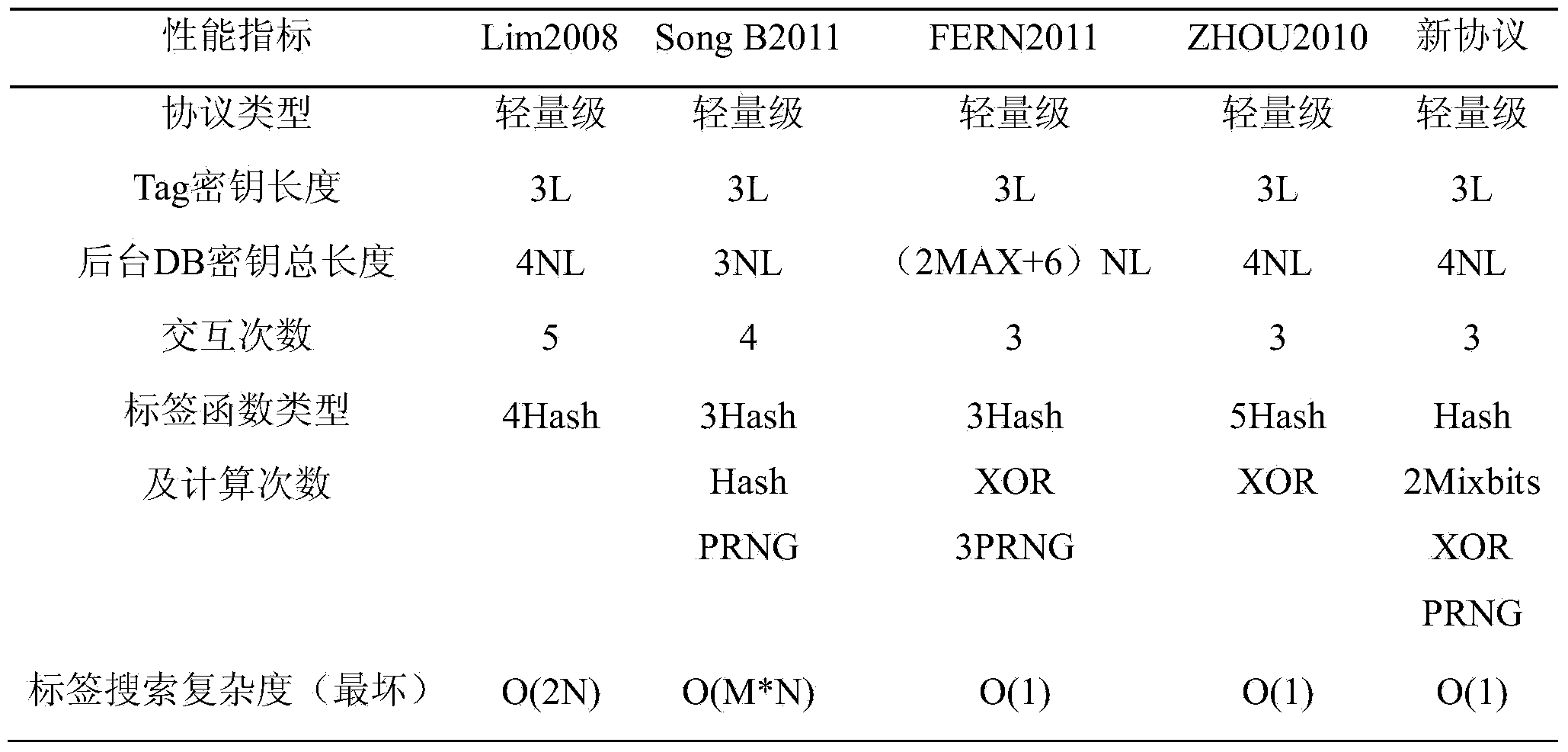
The invention relates to a lightweight bidirectional authentication protocol which can be used in an RFID system of the Internet of Things. The bidirectional challenging response of a backstage and an RFID label is achieved based on a dual authentication mechanism of 'bidirectional random number-new and old key pair, the pseudo random number and the clock parameter are bound through the time attachment encryption, and the trust worthiness of the freshness amount of the protocol can be improved. The protocol participates in authentication through the new and old key pair preset by a backstage database to resist the desynchronizatio excluding the RFID system, and the unbalance between the backstage and a label key is avoided. A reader and the backstage resist the desynchronization from the interior of a system through the time attachment encryption / decryption, and the occurrence that the backstage refuses an authentication label perpetually due to the fact that a malicious reader releases information again is avoided. In addition, the key is updated through the Hash operation, the parameter is corrected by alternately adopting the ultra-lightweight Mixbits function, and the tracking prevention and forward direction safety of the protocol are guaranteed on the basis of reducing the protocol calculating expenditure. The protocol has the advantages of being safe, efficient, flexible and suitable for the fields of identifying the low-cost RFID system, updating the key and the like.
Owner:BEIJING UNIV OF POSTS & TELECOMM
System and method for secured communication
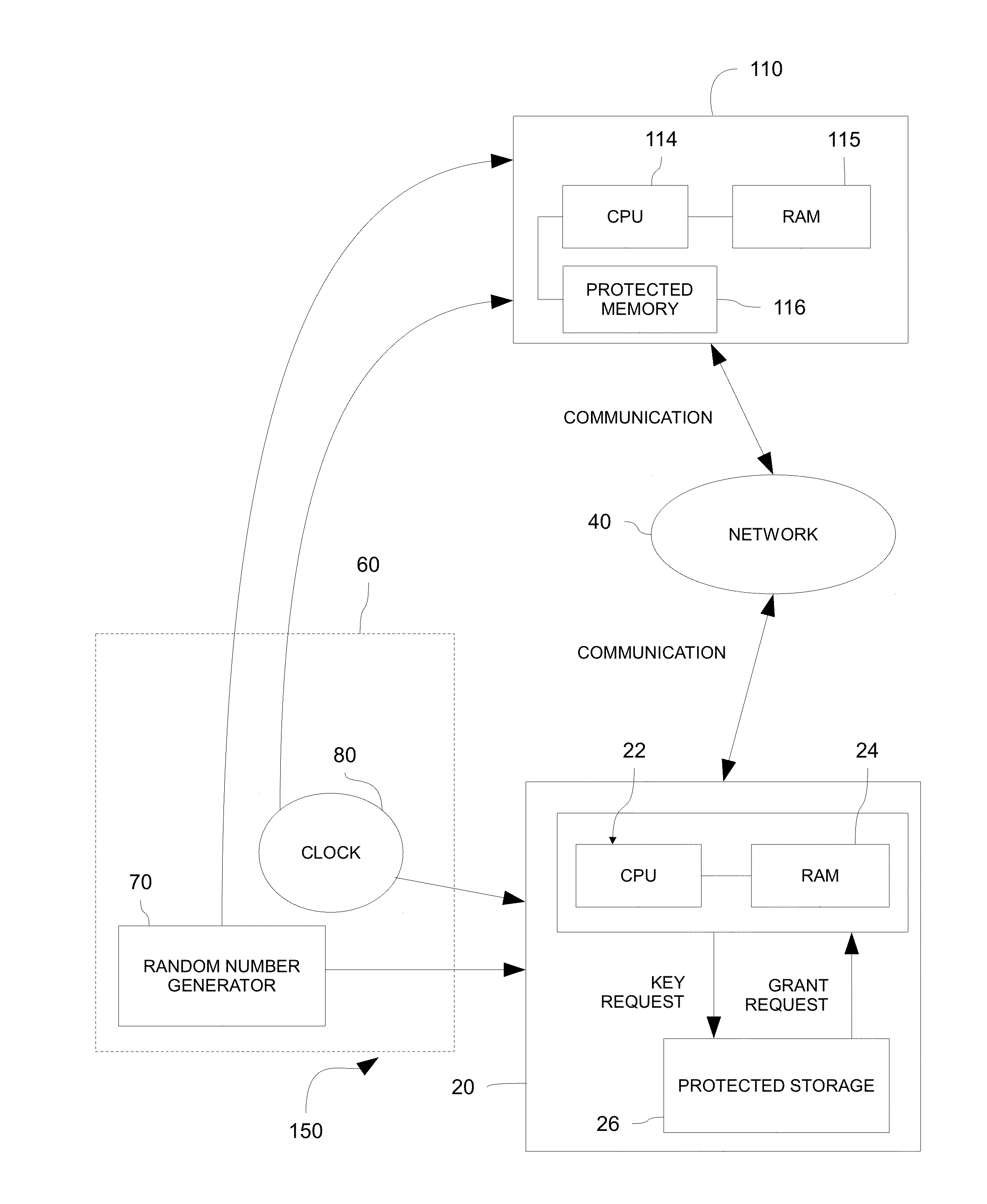
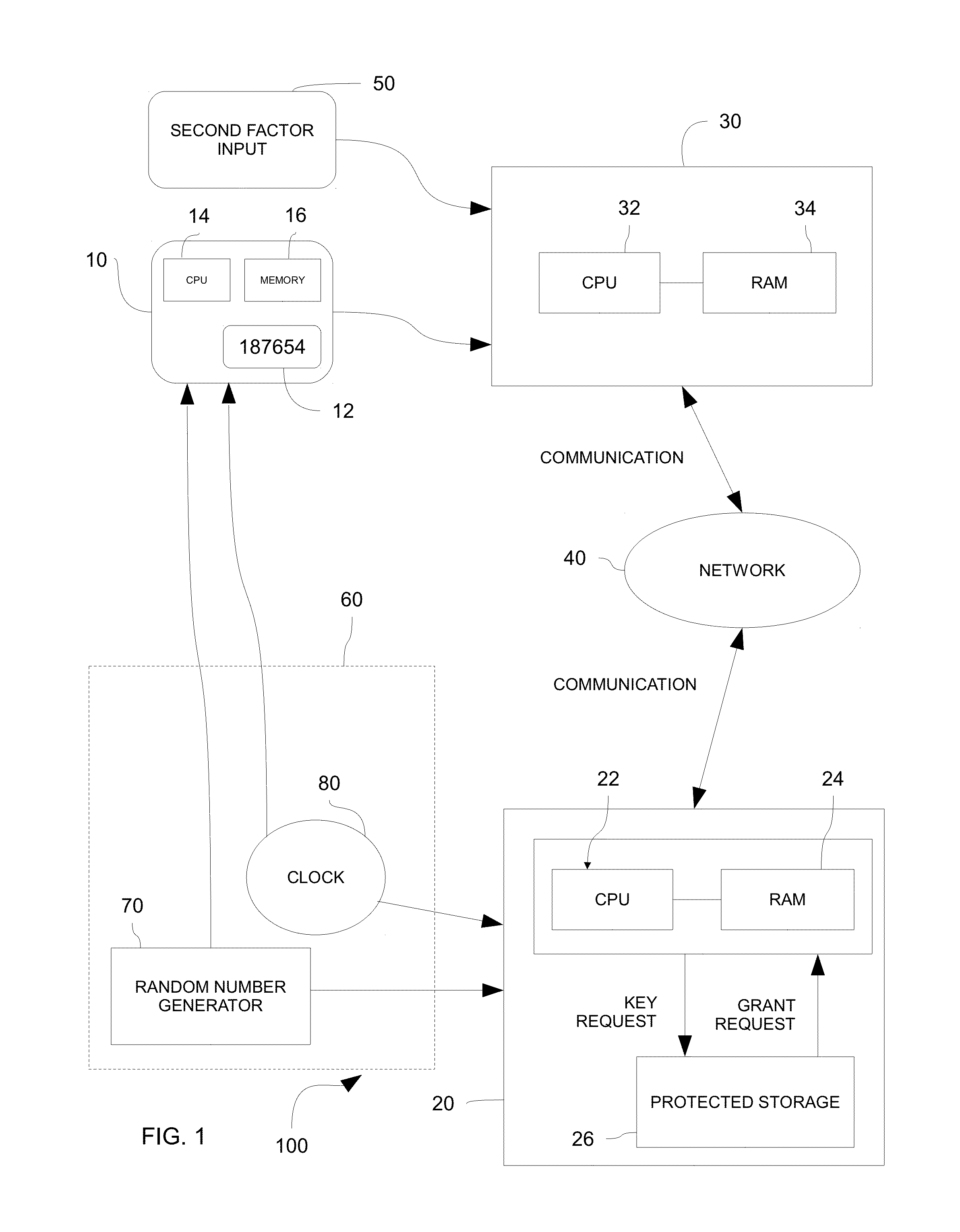
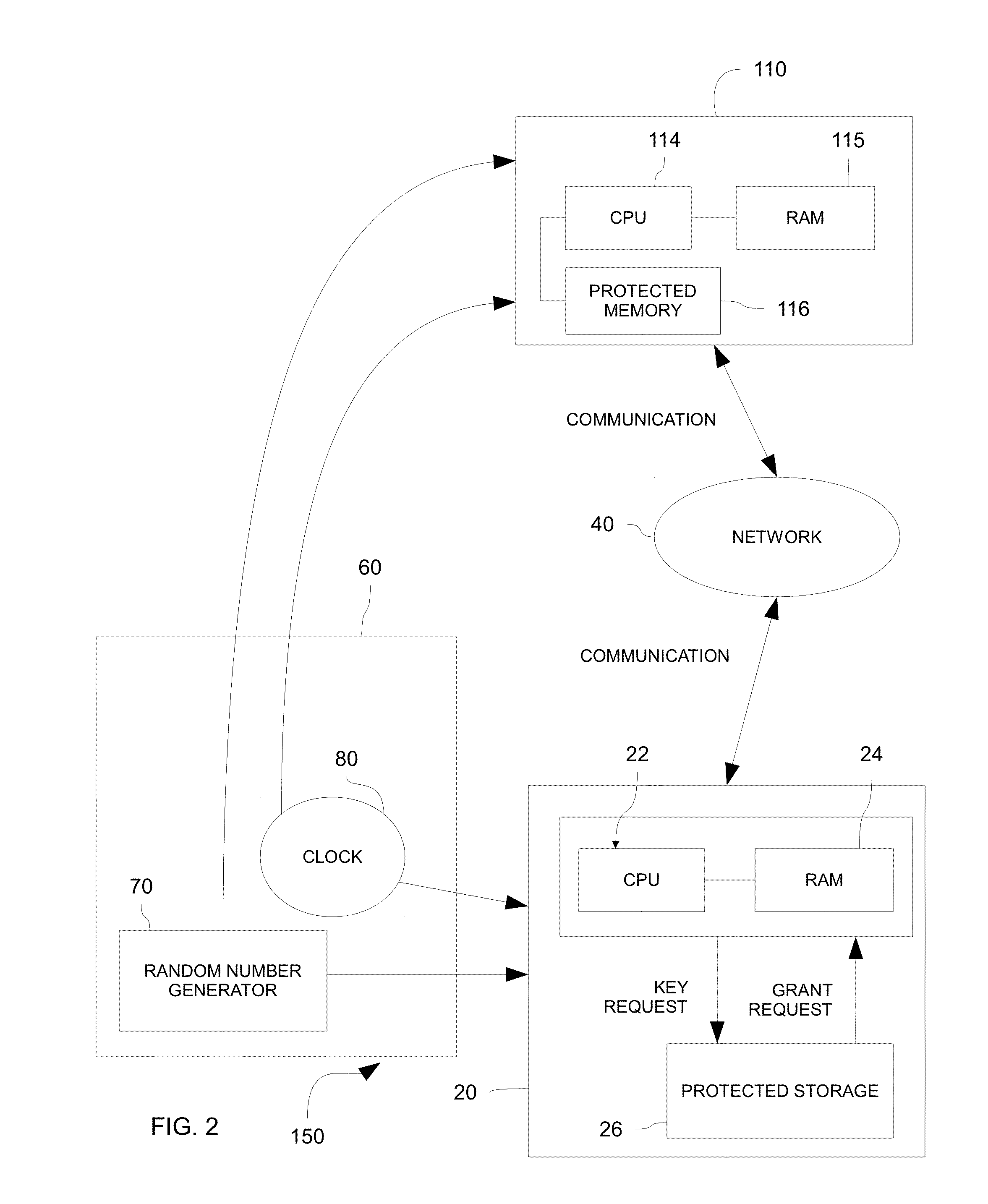
InactiveUS20150288517A1Avoid security threatsKey distribution for secure communicationSynchronising transmission/receiving encryption devicesSecure communicationCommunications system
Systems and methods for securely communicating with a server device are provided. Both the server device and a client device may be provided pre-shared keys, which may be based on a stream of random digits generated by a quantum random number generator. The client device may promote a new client-side key from among the pre-shared keys for use in secure communication with the server device in response to an event, such as a time-based event (e.g., passage of 30 seconds). The server device may be substantially synchronized with the client device such that a server-side key matches a client-side key being used to communicate securely with the server device.
Owner:UT BATTELLE LLC
Intelligent home Internet of Things safety protection method and system
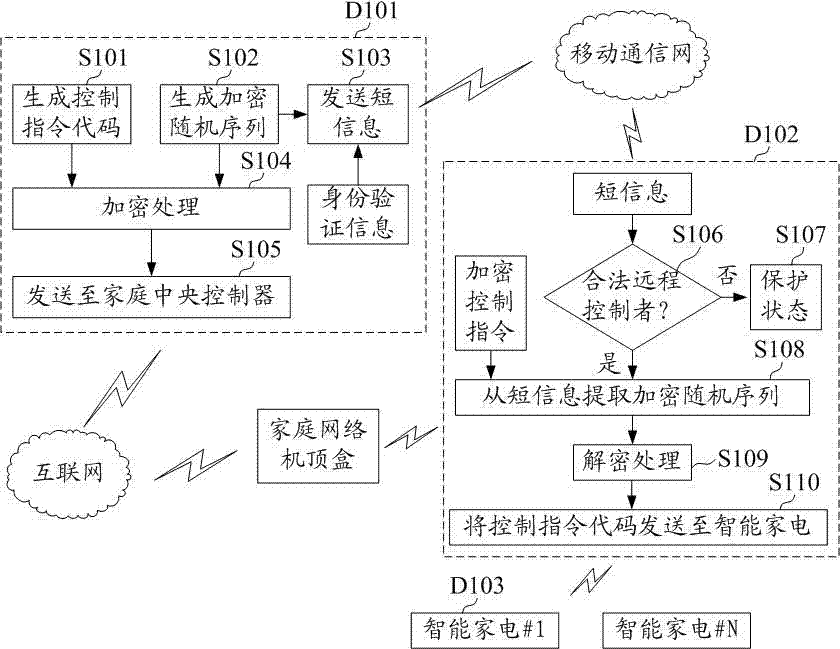
ActiveCN104301303AAvoid security threatsBlock controlUser identity/authority verificationHome automation networksIdentity recognitionRemote control
The embodiment of the invention discloses an intelligent home Internet of Things safety protection method which includes the following steps that, a remote control terminal generates a control instruction code and generates a corresponding encryption random sequence to encrypt the control instruction code; an encrypt control instruction is sent to a home central controller through the Internet; the identity authentication information of the remote control terminal and the encryption random sequence are sent to the home central controller through a mobile communication network; the home central controller is used for conducting identity recognition on the remote control terminal, and the received encryption random sequence is used for decrypting the encrypted control instruction and obtaining the control instruction code; the control instruction code is sent to an intelligent appliance to be executed. The embodiment of the invention further discloses an intelligent home Internet of Things safety protection system. By means of the intelligent home Internet of Things safety protection method and the intelligent home Internet of Things safety protection system, safety protection outside the route is added after the safety protection in the existing route is achieved, a hacker is prevented from invading a home gateway to generate safety threats to the intelligent appliance, even if the hacker invades into the home gateway, the hacker can be prevented from controlling the central controller, and the safety protection capability of the intelligent home is further improved.
Owner:SHANTOU UNIV
Zero-trust network architecture and construction method
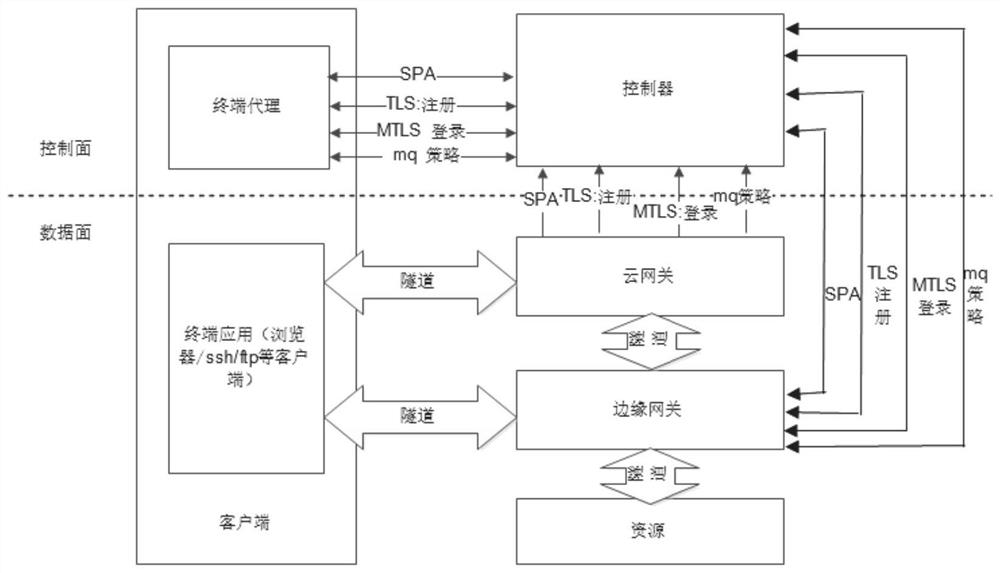
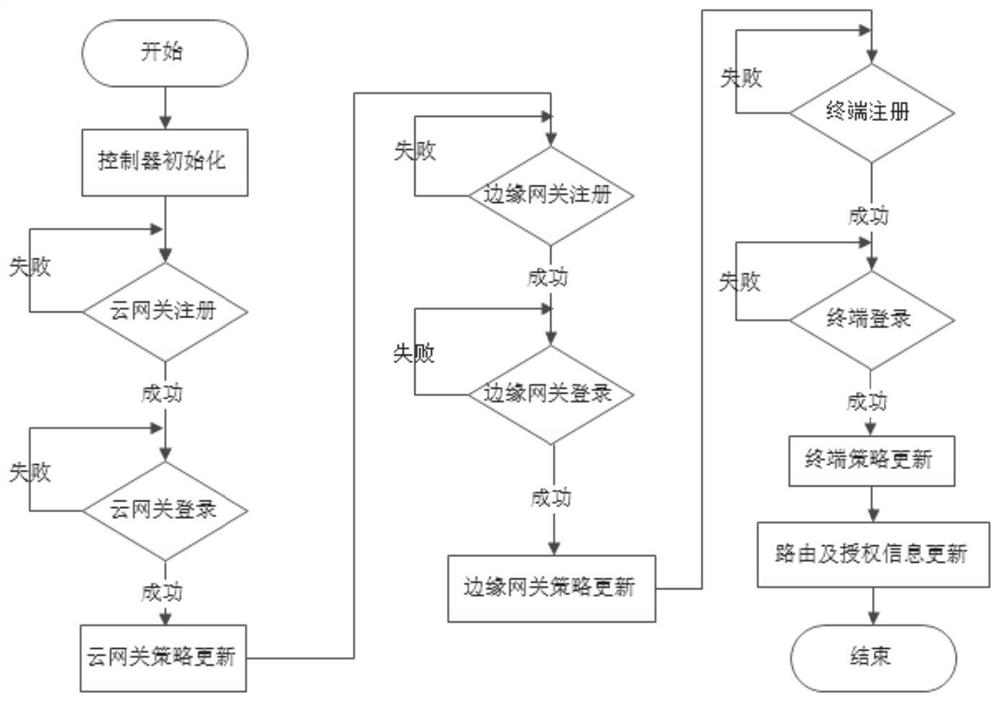
ActiveCN113572738AAvoid security threatsBlock network attacksData switching networksHigh level techniquesBusiness enterpriseNetwork architecture
The invention provides a zero-trust network architecture and a construction method. The zero-trust network architecture comprises a controller, a cloud gateway, an edge gateway and a terminal agent, the edge gateway is in communication connection with the cloud gateway, the cloud gateway, the edge gateway and the terminal agent are respectively in communication connection with the controller, and the cloud gateway and the edge gateway are respectively in communication connection with the client; the controller is used for controlling registration and login processes of the client, the cloud gateway and the edge gateway and issuing a routing strategy and an authorized access control strategy; the edge gateway is used for controlling resource security access, and the cloud gateway is used for routing when a client accesses resources across regions; the terminal agent is deployed at a client, establishes a tunnel with the cloud gateway and the edge gateway, and performs secure access on authorized resources; the network position boundary no longer determines the access authority, all access subjects need to be subjected to identity authentication and authorization before access is allowed, and the security threat brought by the enterprise network architecture with the fuzzy boundary at present is solved.
Owner:中孚安全技术有限公司
Secure and trusted capability opening platform
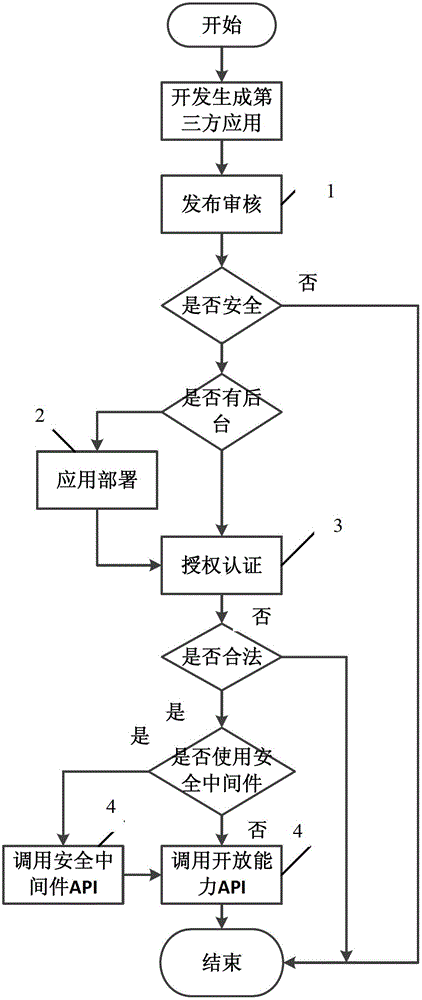
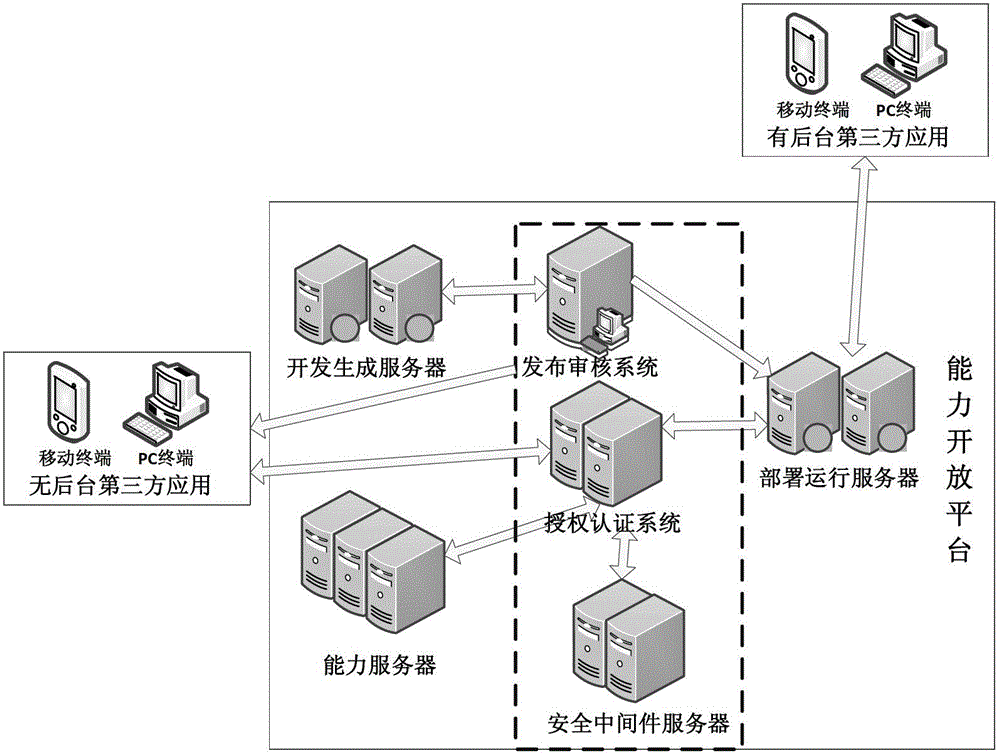
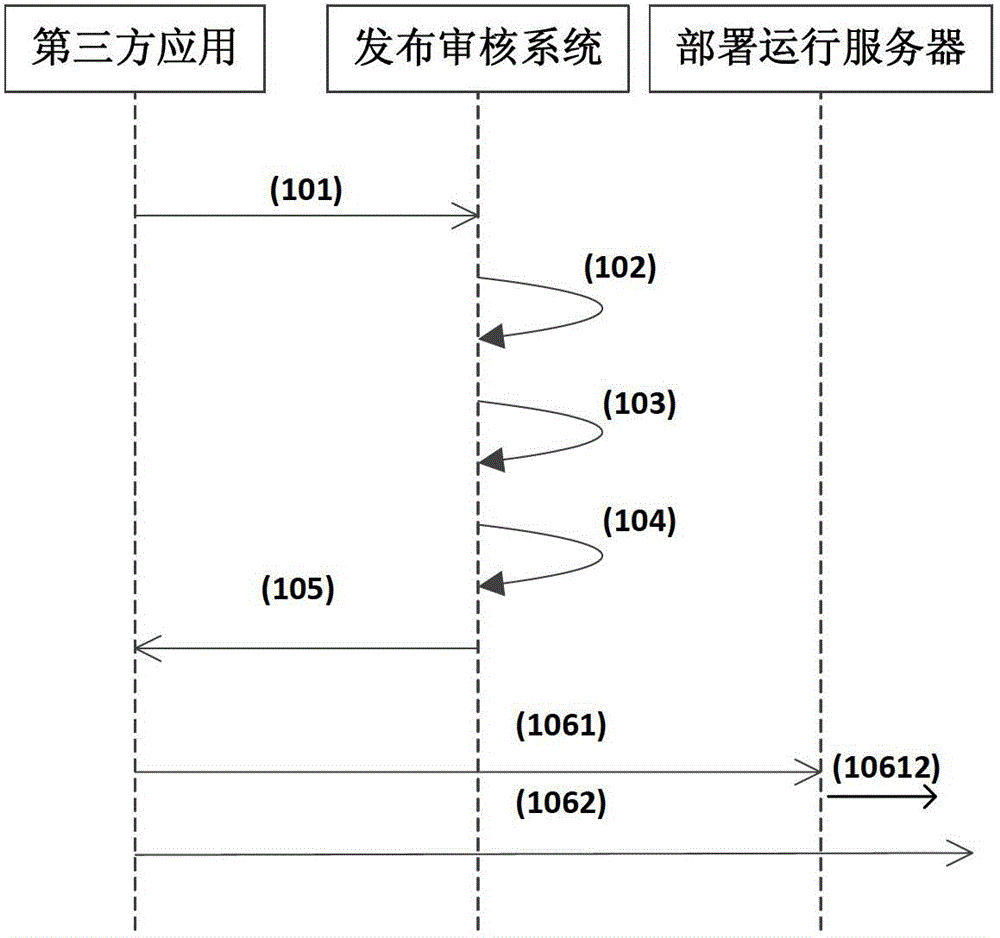
The invention discloses a secure and trusted capability opening platform, which comprises a publication auditing system, an authorization and authentication system and a secure middleware server, wherein the publication auditing system performs publication auditing on third-party application to ensure that the third-party application accessing the capability opening platform is secure and trusted, so that security threats caused by own bugs of the third-party application to the platform are avoided or the third-party application is prevented from becoming the attack backdoor of the whole capability opening platform; the authorization and authentication system authorizes and authenticates the access of the third-party application to resources provided by the capability opening platform to ensure legal access to the resources, so that economic loss caused by unauthorized access can be avoided; and open secure middleware service is provided for the third-party application to improve own security of the third-party application, maximally reduce development difficulty and development cost and improve the development efficiency of the third-party application, so that the practicability, convenience and flexibility of the whole capability opening platform are improved.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Certifying method and its device for radio network end-to-end communication
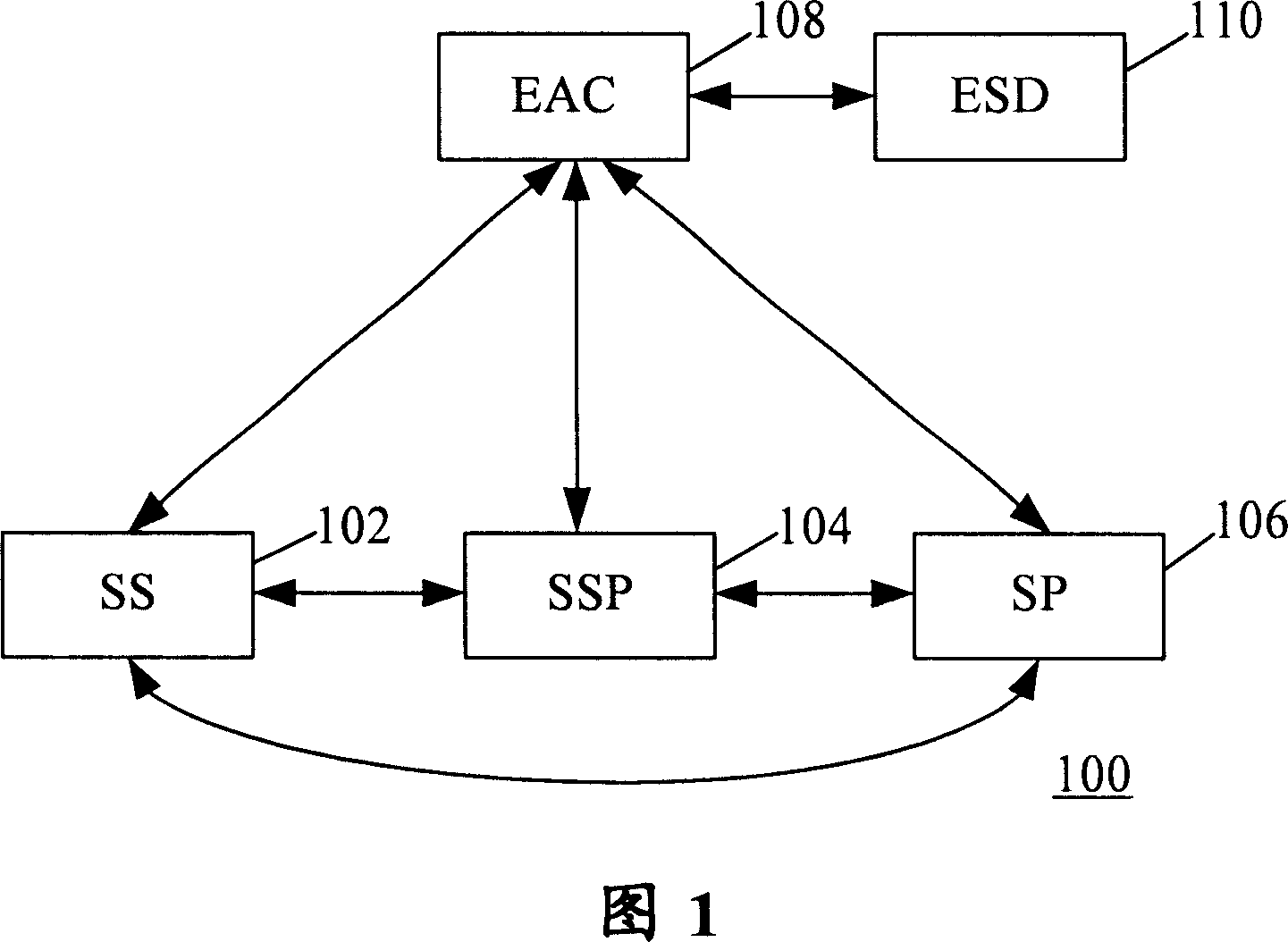
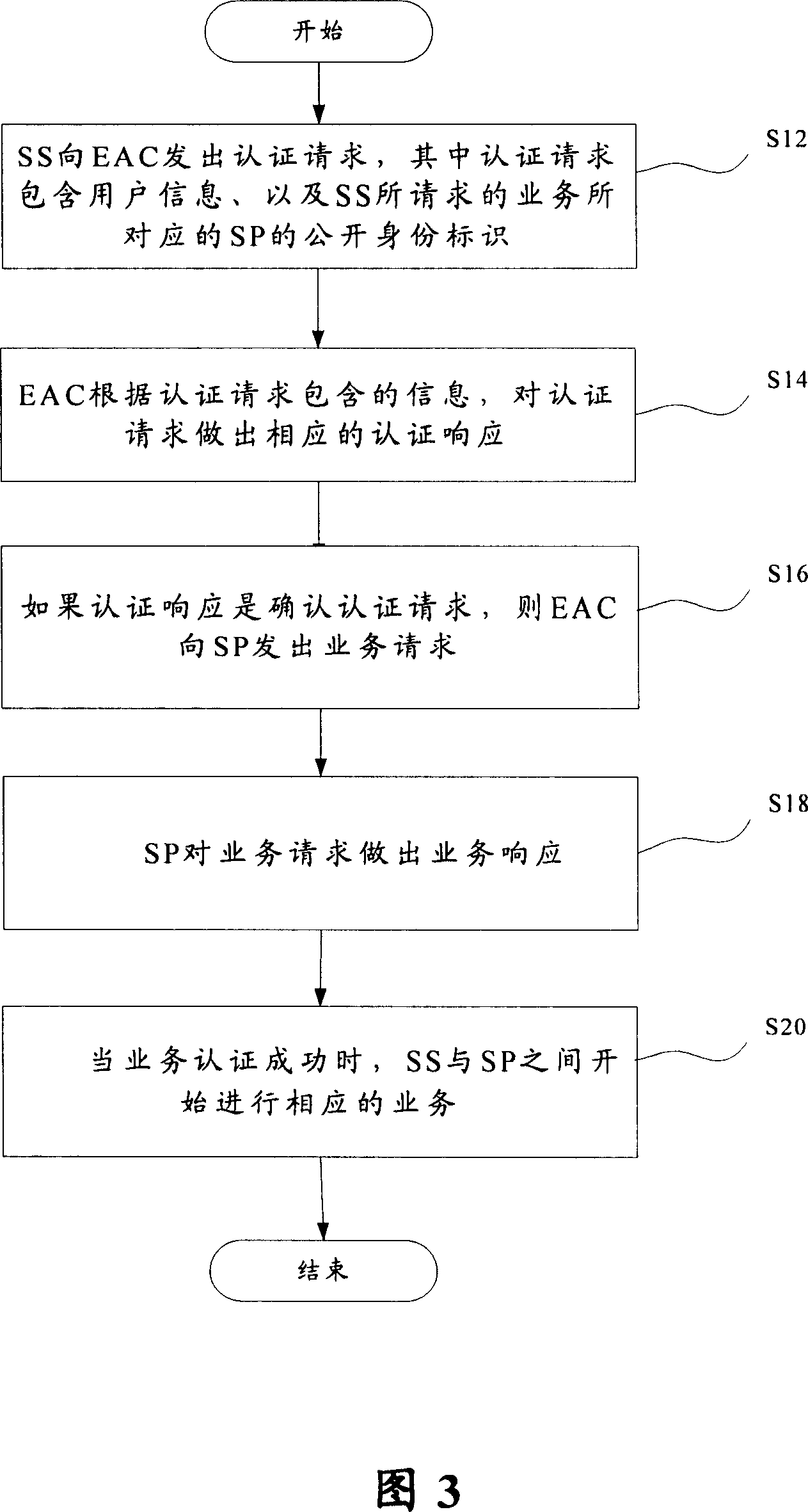
ActiveCN101051898ASolve the problem of password attackAvoid security threatsUser identity/authority verificationRadio networksAuthentication
Being in use to implement authentication end-to-end in Kerberos model of wireless network, the method includes following steps: (1) the party to a contract of service sends authentication request (AR) to entity authentication center (EAC); AR includes id of public identity of service provider corresponding to services requested by the party to a contract; (2) EAC makes out authentication response corresponding to AR based on information contained in AR; (3) if authentication response validates AR, then EAC sends out service request carrying certification that the party to a contract of service has passed authentication, and credence entitled to the use the service; (4) the party to a contract of service makes out service response to the service request; (5) if service response is successful, corresponding service starts to carry out between the party to a contract of service and the service provider.
Owner:HUAWEI TECH CO LTD
Authenticated encryption method and encryption system based on symmetric encryption
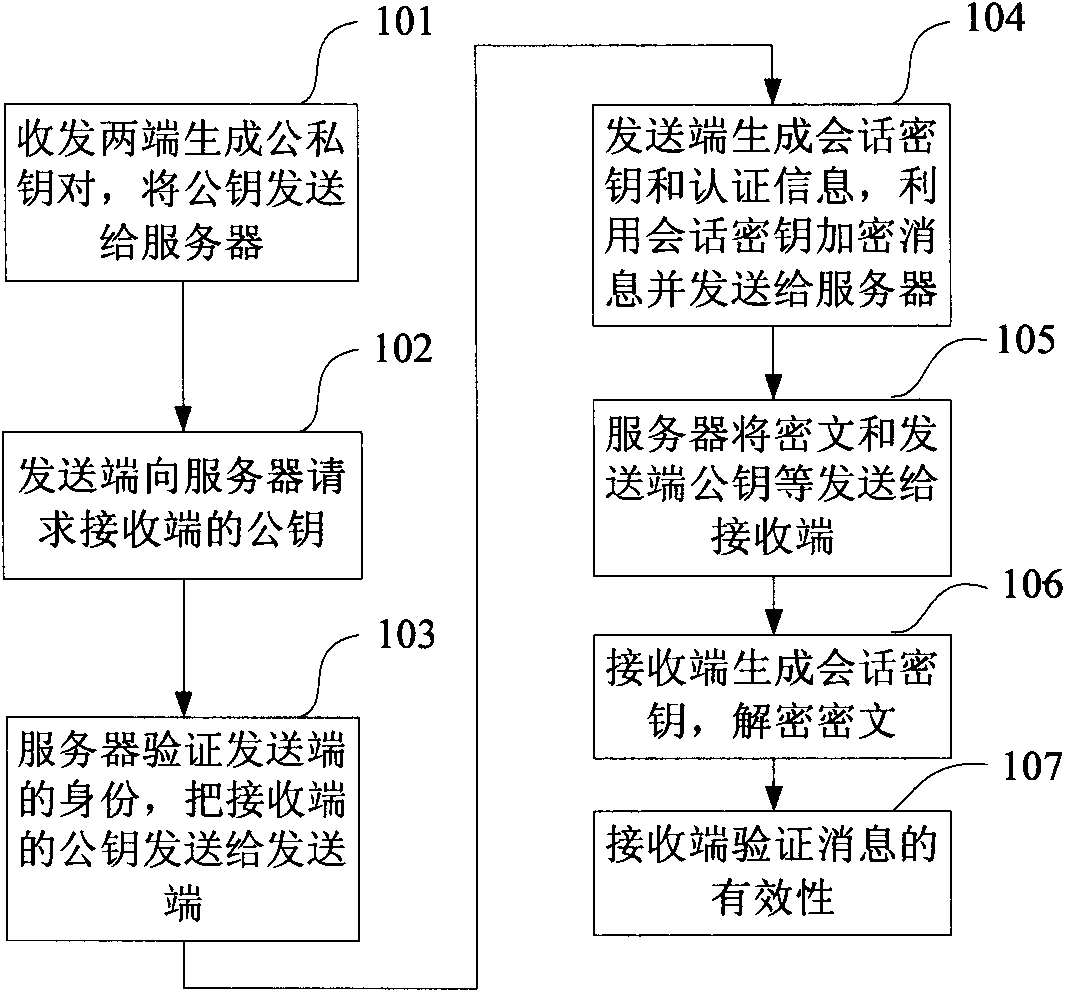
InactiveCN101667913AAchieve authenticationImplement encryptionKey distribution for secure communicationUser identity/authority verificationThird partyCommunications security
The invention discloses an authenticated encryption method and a system, relating to the field of communication security. The restorable signature of a message and the symmetric encryption technologyare combined; a commitment value which only can be calculated by a designated message receiving end is used as a session key encryption message; and the message receiving end validates the validity ofthe message by the restorable signature, thus realizing encryption and authentication in one logical step. A key generation unit of a sending end generates a session key of the sending end; an encryption unit encrypts a message to be sent; the receiving end generates a session key of the receiving end; a decryption unit utilizes the session key of the receiving end to decrypts the encrypted message; and the authentication and confirmation message is generated according to the decrypted message, thus validating the validity of the message. When disputes occur, the message receiving end transforms the authenticated and encrypted message signature into a common signature so as to lead a third party to validate the validity of the signature. The invention has the advantages of high security,low calculated amount and transmission cost, and the like.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
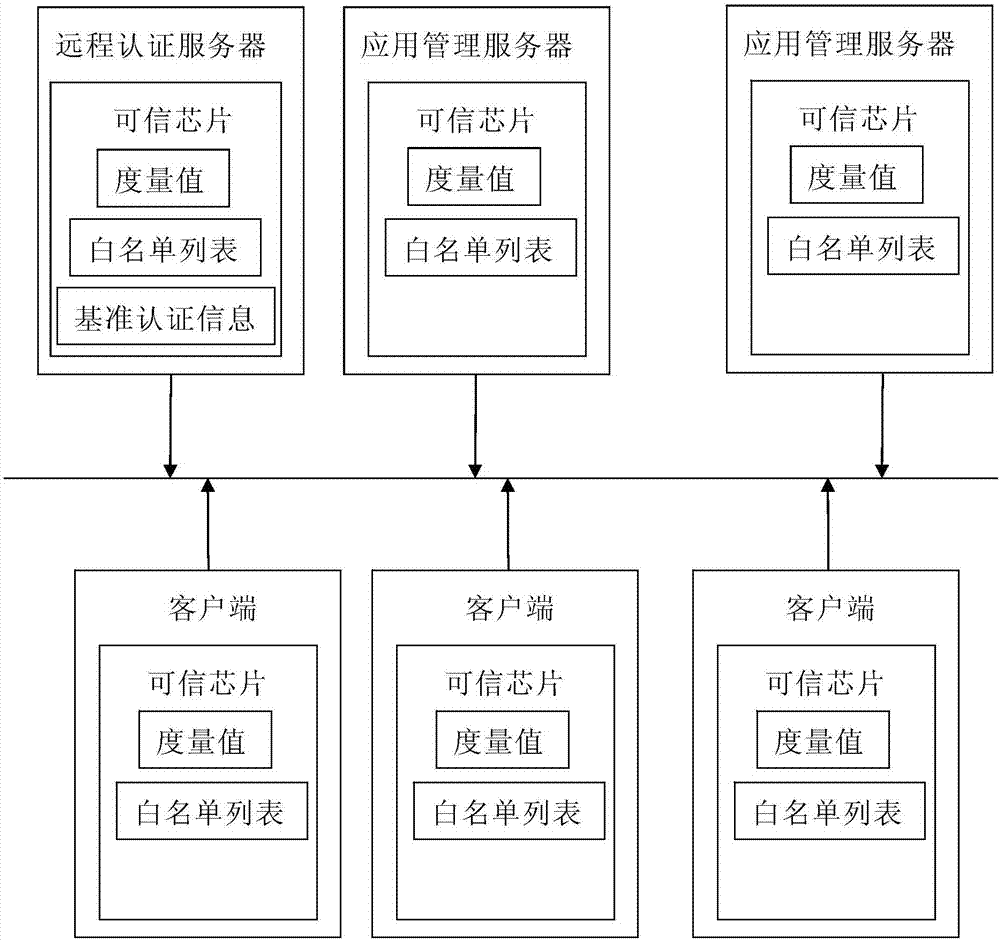
Trusted safety network system
InactiveCN107493271AImprove safety and reliabilityVerify integrityKey distribution for secure communicationUser identity/authority verificationNetworked systemAuthentication server
The invention discloses a trusted safety network system which is implemented on the basis of a client-server architecture, wherein each network node is a trusted host provided with a trusted chip, and each network node carries out a trusted starting process on the basis of the trusted chip; a white list is stored in the trusted chip of each network chip, the white list comprises application software allowed to be executed and a measured value of a key code of the application software, and when the application software is operated, the integrity of the application software is verified by the white list; a remote authentication server is configured, and datum authentication information for carrying out identity authentication and integrity verification is stored in a trusted chip of the remote authentication server; and an application management server is configured and used for carrying out deployment and management of application on each network node. The invention constructs the trusted safety network system implemented on the basis of the trusted chip, and safety reliability of the network system can be improved.
Owner:DATANG GAOHONG XINAN ZHEJIANG INFORMATION TECH CO LTD
Method for realizing dependable SSH based on dependable computing
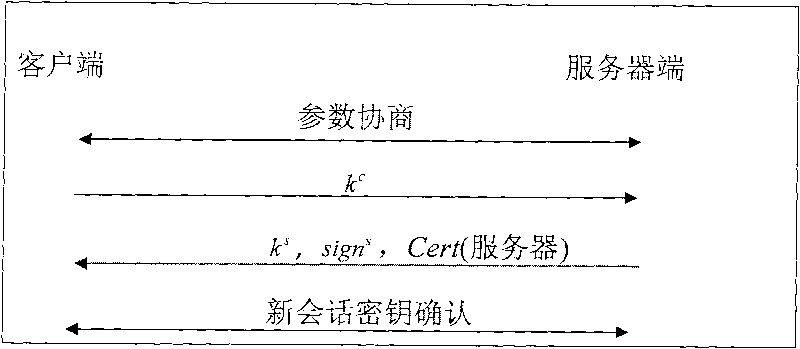
InactiveCN101741842AAvoid security threatsProtection against replay attacksKey distribution for secure communicationUser identity/authority verificationKey exchangeMan-in-the-middle attack
The invention provides a method for realizing dependable SSH based on dependable computing. The method integrates remote authentication of the dependable computing with key exchange of an SSH protocol so as to closely combine platform status information verification with session key negotiation; and the method enhances the security of data at a communication end point on the premise that safe transmission of the data is ensured. The method requires that both a server and a client are provided with dependable security chips; and the platform status can be measured by a measurement module and a dependable operating system. The method can not only effectively prevent the security threat that the communication with an unknown end point by using a security channel may undergo various attacks in the SSH protocol, but also effectively protect against replay attack, impersonation attack and man-in-the-middle attack.
Owner:BEIJING JIAOTONG UNIV
On-line underground temperature measurement system
ActiveCN101942990AAvoid short circuit problemsHigh strengthSurveyConstructionsThermocouple WireEngineering
The invention relates to an underground temperature measurement system. The system comprises a thermocouple, a compensating lead and a heavy hammer, wherein the compensating lead is positioned above the thermocouple, and the lower end of the compensating lead is connected with the upper end of the thermocouple; the heavy hammer is positioned below the thermocouple, connected with the lower end of the thermocouple and used for guiding the thermocouple to advance in a temperature measurement passage; and the thermocouple is a sheathed thermocouple manufactured by combined assembly of a thermocouple wire, an insulating material and a metal protective sleeve and stretching, and the length of the sheathed thermocouple corresponds to the thickness of a highest temperature interval in an underground high temperature layer to be measured. The temperature measurement system can greatly reduce the manufacturing cost of the thermocouple, effectively prolong the service life of the thermocouple and improve the automation degree of temperature measurement, and is convenient for repair and maintenance of the system per se.
Owner:ENN SCI & TECH DEV
Suspension bridge steel wire rope damage patrolling robot
ActiveCN107175665AJudging the degree of damageEasy for daily maintenanceProgramme-controlled manipulatorMaterial magnetic variablesRemote controlEngineering
The invention discloses a suspension bridge steel wire rope damage patrolling robot. The suspension bridge steel wire rope damage patrolling robot comprises a base, a patrolling device arranged on the base and conducting patrolling on suspension bridge steel wire rope damage, and a control device controlling the patrolling device. The process for patrolling a steel wire rope includes the steps that firstly, the patrolling device is installed; secondly, the patrolling robot conducts patrolling on the suspension bridge steel wire rope; thirdly, after the robot finish patrolling, the robot returns to the initial end of the suspension bridge steel wire rope; fourthly, the first step, the second step and the third step are repeatedly conducted many times; and fifthly, damage state data are obtained. The suspension bridge steel wire rope damage patrolling robot is novel and reasonable in design, low in using cost, easy to operate, good in safety and capable of conveniently and rapidly finishing the suspension bridge steel wire rope damage patrolling operation; through the arrangement of the control device, a user remotely controls the patrolling robot to conduct high-altitude detection through a wireless remote control transmitter, and safety hidden danger of workers during high-altitude operation is avoided; and design is ingenious and reasonable, reliability and stability are achieved, the size is small, and practicability is high.
Owner:XIAN UNIV OF SCI & TECH
Method and apparatus for filtrating data content, finite state automata and conformation apparatus
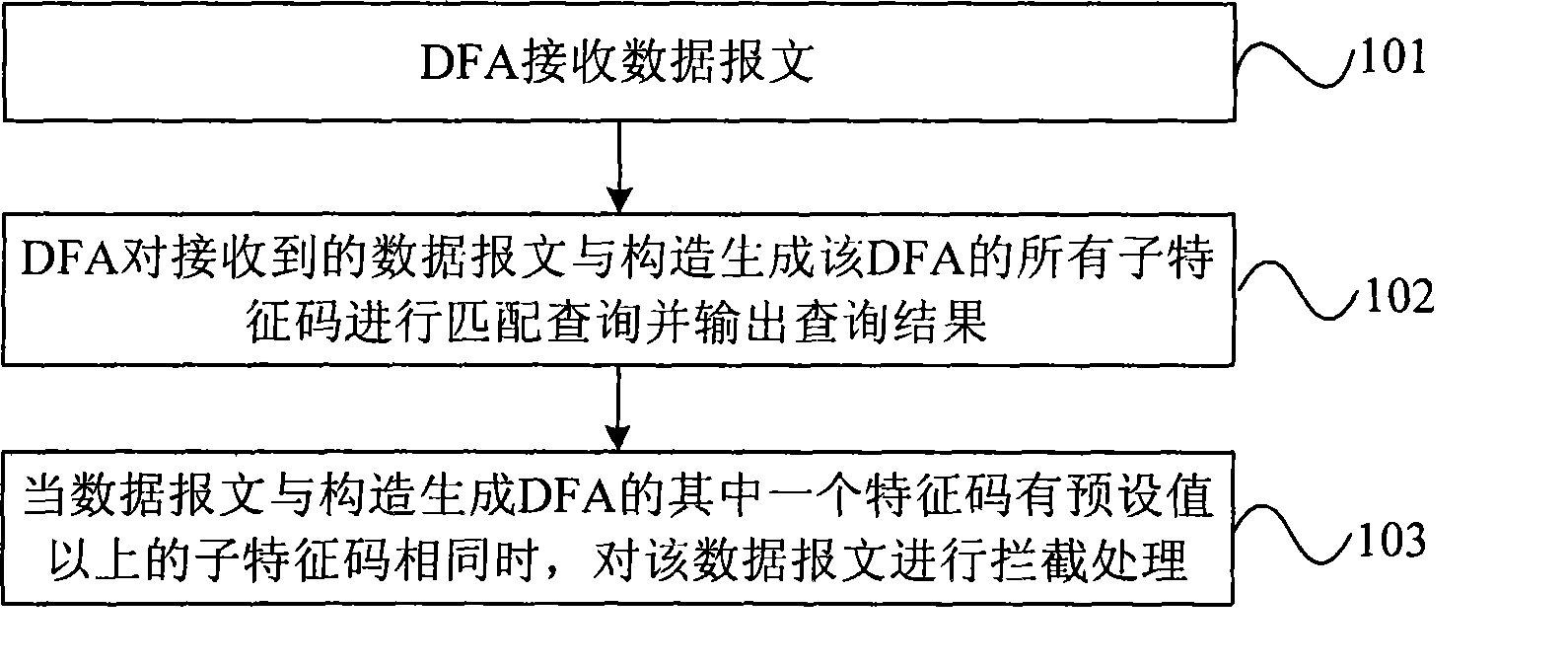
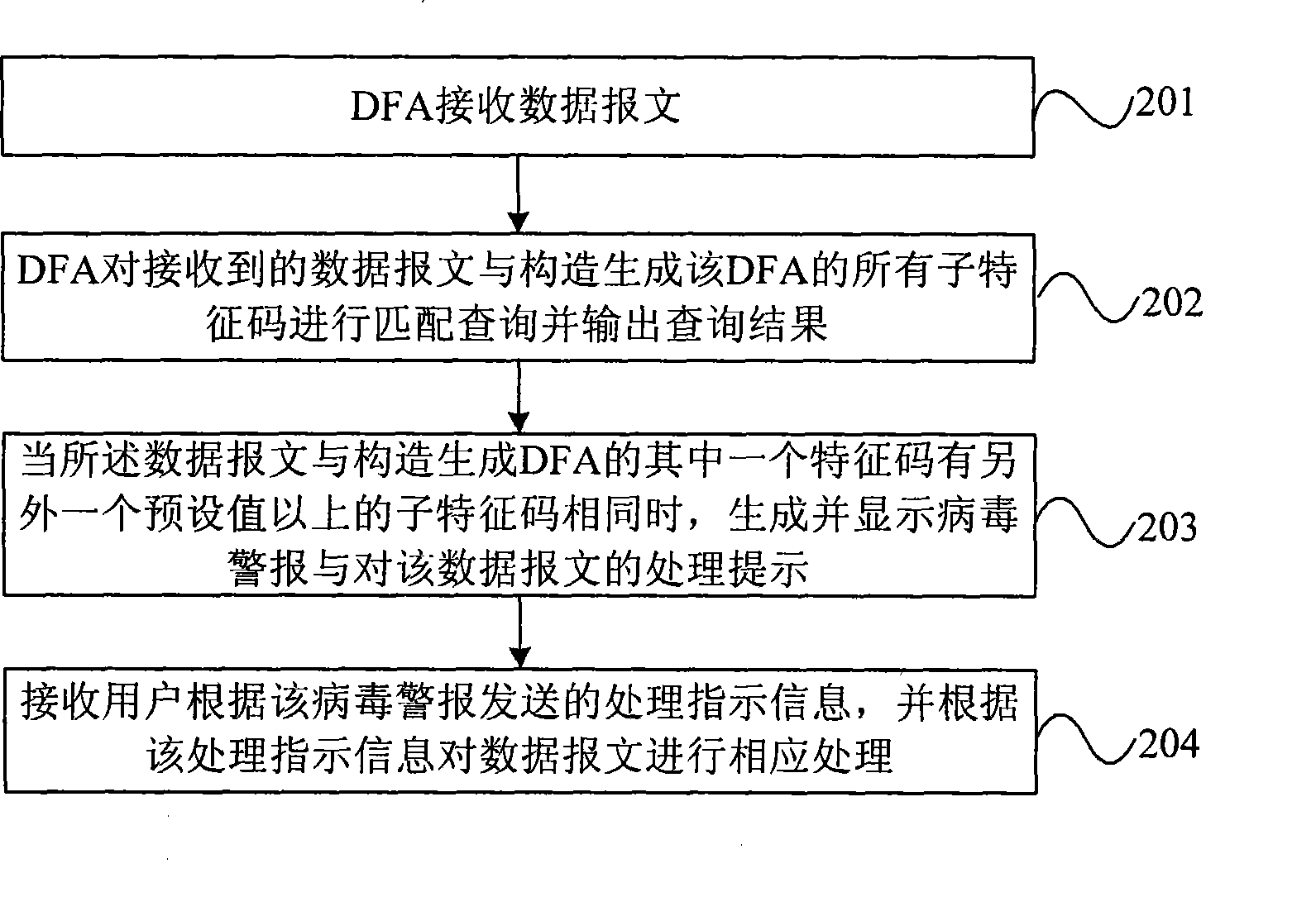
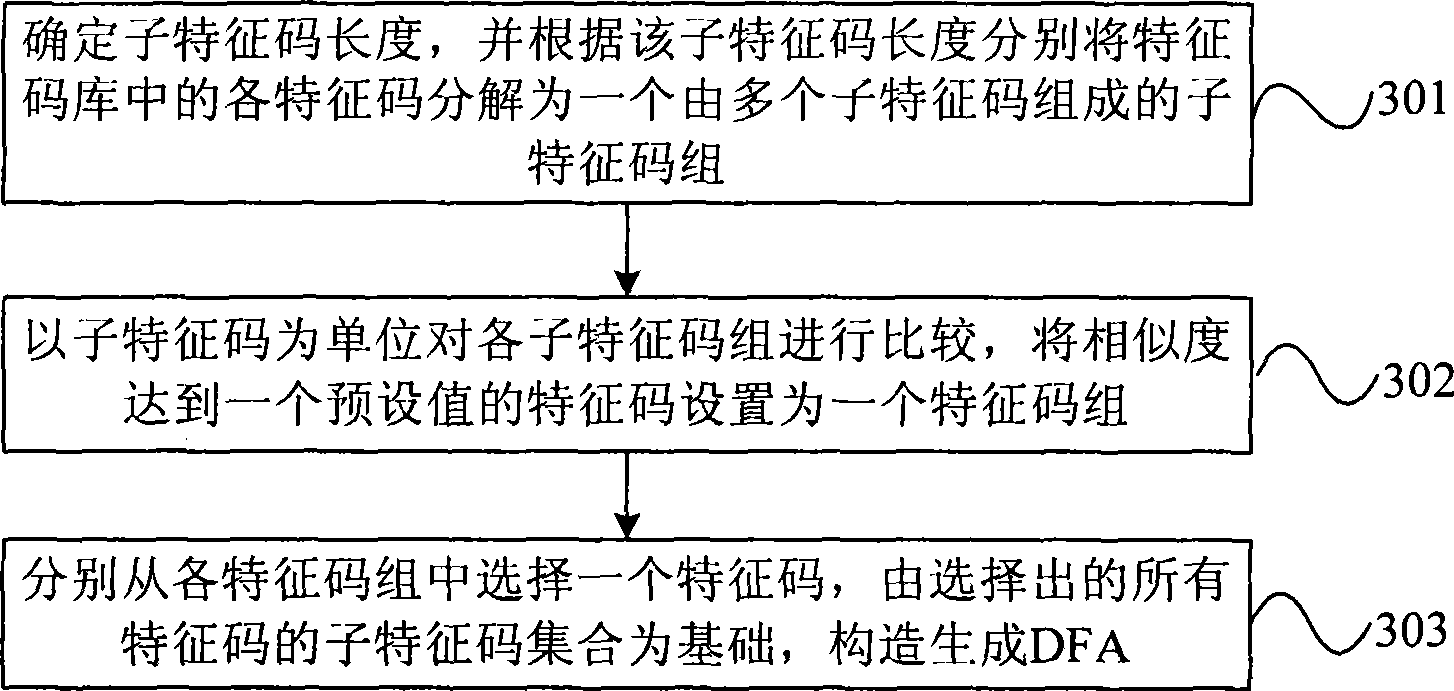
ActiveCN101414914AImplement filteringAvoid security threatsSecuring communicationData contentCondition Code
The invention discloses a method for filtering data content and a device thereof, a finite state automata and a structure device thereof, wherein, the method comprises the steps as follows: the finite state automate receives a data message; the finite state automata is constructed and generated by subcharacter codes which are obtained by decomposing condition codes; the finite state automata processes the received data message and all subcharacter codes used for constructing and generating the finite state automata for match query and outputs the query result; and according to the query result, when the data message is the same as one subcharacter code with the condition code being more than the preset value, wherein, the subcharacter code is used for forming and generating the finite state automata, the data message is intercepted. The embodiment of the invention can filter suspected virus and avoids the network safety threat from the suspected virus under the condition of not increasing the storage capacity of a condition code base and the spending and time required for searching the condition code base.
Owner:BEIJING ZHIGU TECH SERVICE
program non-control data attack protection method based on an LLVM compiler
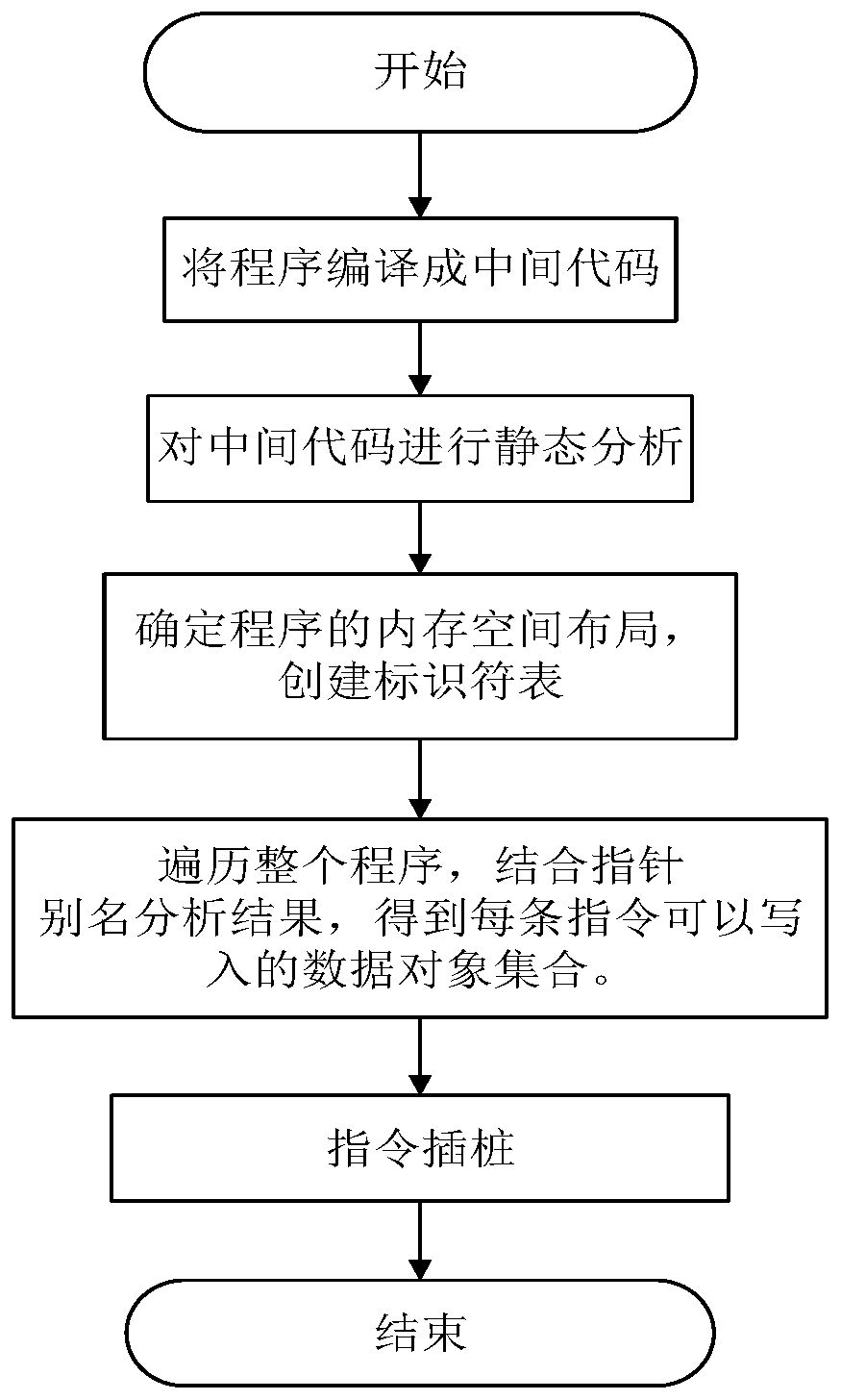
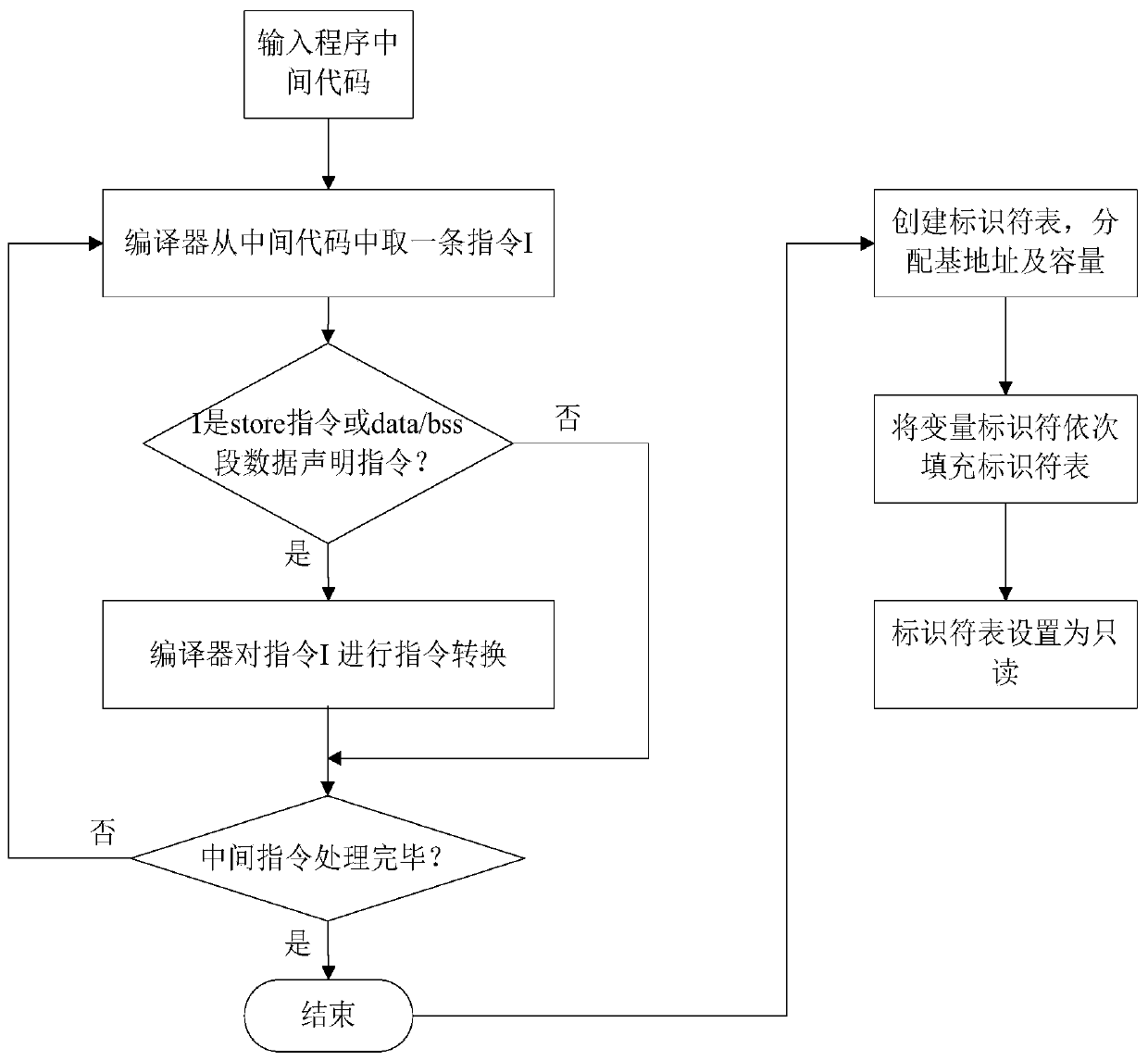
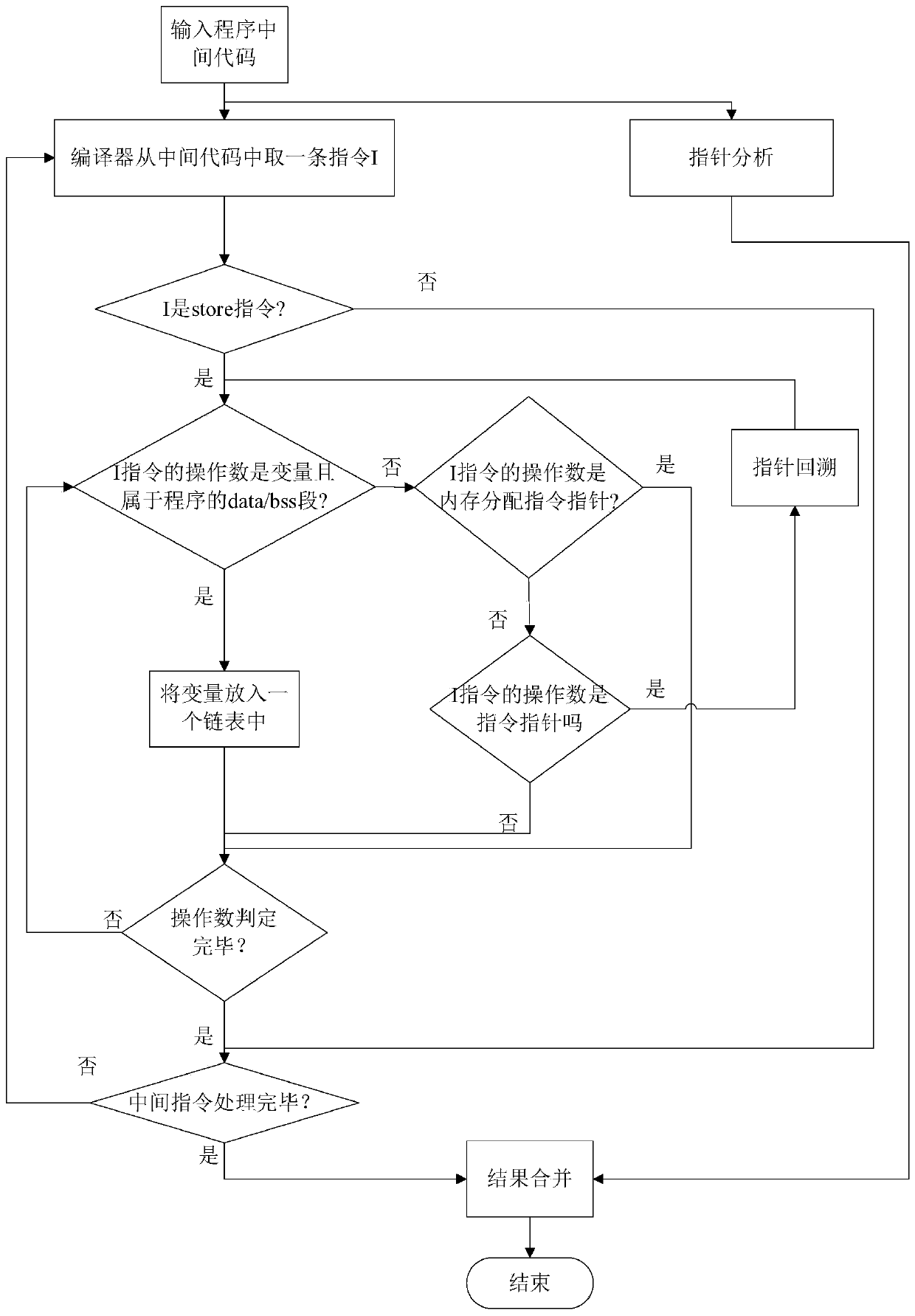
ActiveCN109918903AWill not affect the running processImprove accuracyPlatform integrity maintainanceCode compilationAttackSoftware engineering
The invention provides a program non-control data attack protection method based on an LLVM compiler, and the method comprises the steps: compiling a program source code into an intermediate code fora 64-bit application program which is widely applied at present, carrying out the static analysis of the intermediate code, obtaining a directivity analysis result, and obtaining non-control data which needs to be protected; meanwhile, carrying out instruction instrumentation on the basis of the intermediate code, so that non-control data of the program are prevented from being maliciously tampered. According to the method, the defects of an original static analysis method are overcome, the analysis accuracy is improved, and the security threat caused by malicious tampering of program non-control data by an attacker is solved by utilizing relatively low space and time complexity.
Owner:陕西数图行信息科技有限公司
Security protection performance evaluation method applicable to core network of wireless power private network
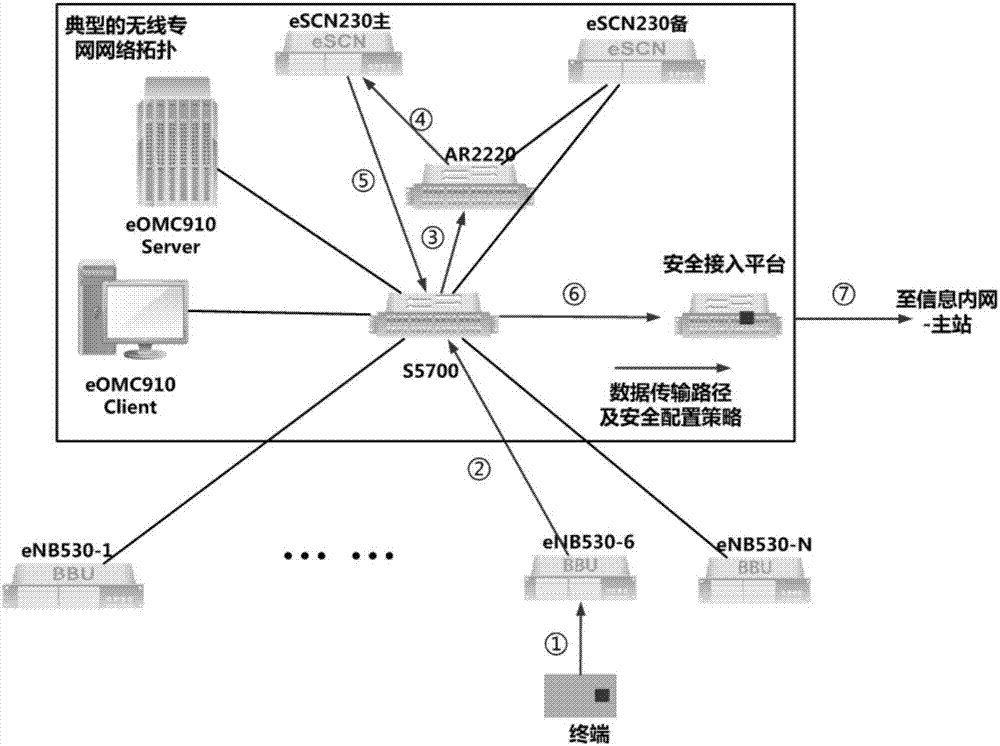
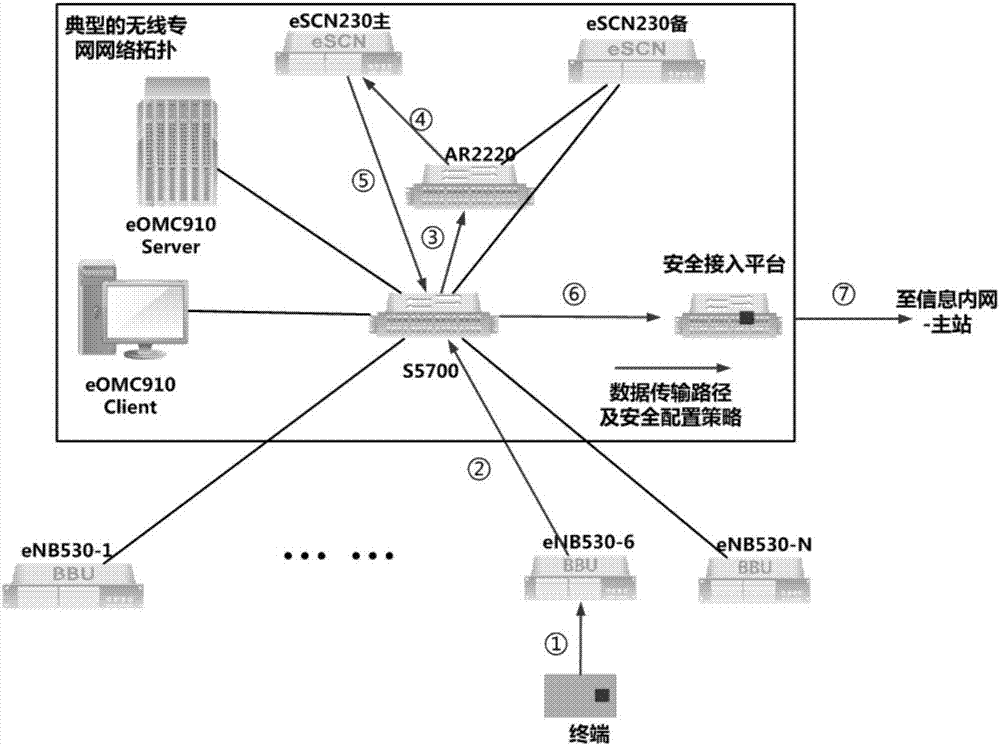
ActiveCN107071781AImprove the protective effectAvoid security threatsSecurity arrangementHigh level techniquesPrivate networkNetwork management
The invention discloses a security protection performance evaluation method applicable to a core network of a wireless power private network. The security protection performance evaluation method comprises the steps of firstly building a core network security protection performance evaluation system which comprises a terminal, multiple base stations, a switch, a secure encryption gateway, a core network, a network management server, a network management client and a secure access platform; then carrying out a data transmission security protection test of an S1 interface; carrying out a test for an HSS authorization server to refuse a service attack; carrying out a security controllability test for the core network; and carrying out a security test for the network management system of the wireless private network. By adopting the method, the security risk of the core network of the wireless power private network can be evaluated comprehensively, attack behaviors from malicious hosts to the core network of the wireless private network can be prevented efficiently, and the security robustness of the core network of the wireless power private network can be enhanced.
Owner:STATE GRID JIANGSU ELECTRIC POWER CO ELECTRIC POWER RES INST +2
Network access control method for comprehensive safety management of inner network
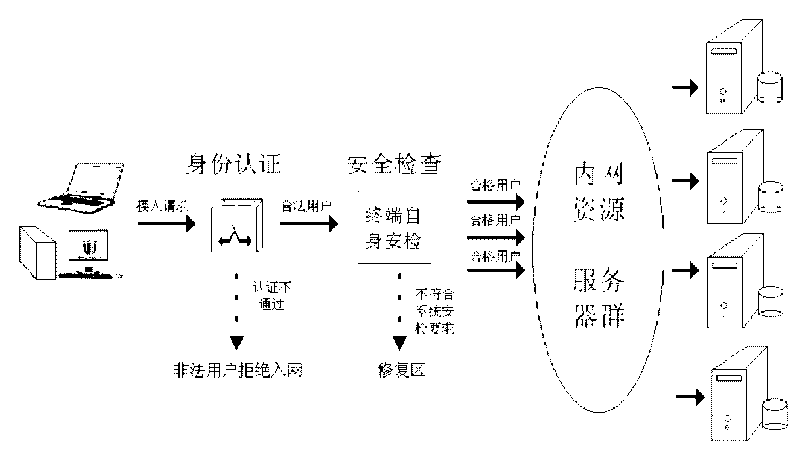
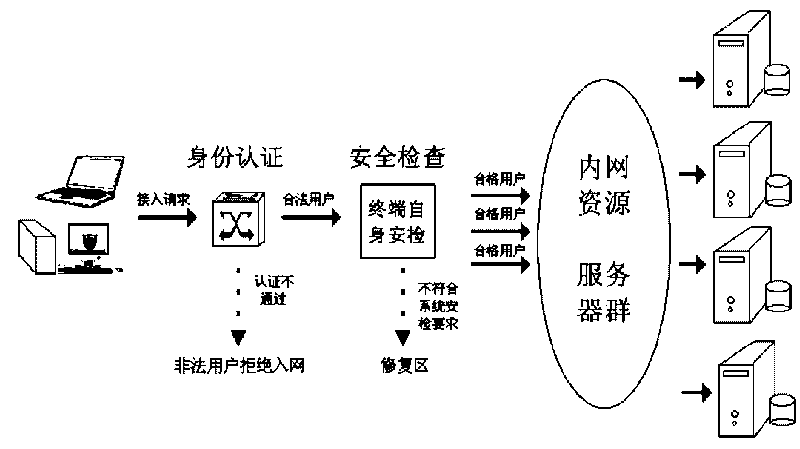
ActiveCN101714927AAvoid security threatsForbidden accessData switching networksContinuous scanningSafety management systems
The invention relates to a network access control method for the comprehensive safety management of an inner network. The network access control method is characterized in that the safety control of a network access terminal is realized by the linkage among a comprehensive inner network safety management system, a switch and a Radius server. The network access control method is realized by the following steps: firstly, pointing an 802.1 X authentication server to the Radius server and dividing into three vlans of a working area, an access area and a repairing area by a switch with the 802.1X access authentication function; and then, configuring the access control strategies of the vlans on the Radius server and the linkage configuration with the comprehensive inner network safety management. The invention can manage and control the terminal safety and saves network resources by freeing detection in a continuous scanning mode.
Owner:FUJIAN ETIM INFORMATION & TECH
Device for detecting circuit opening of secondary circuit of current transformer
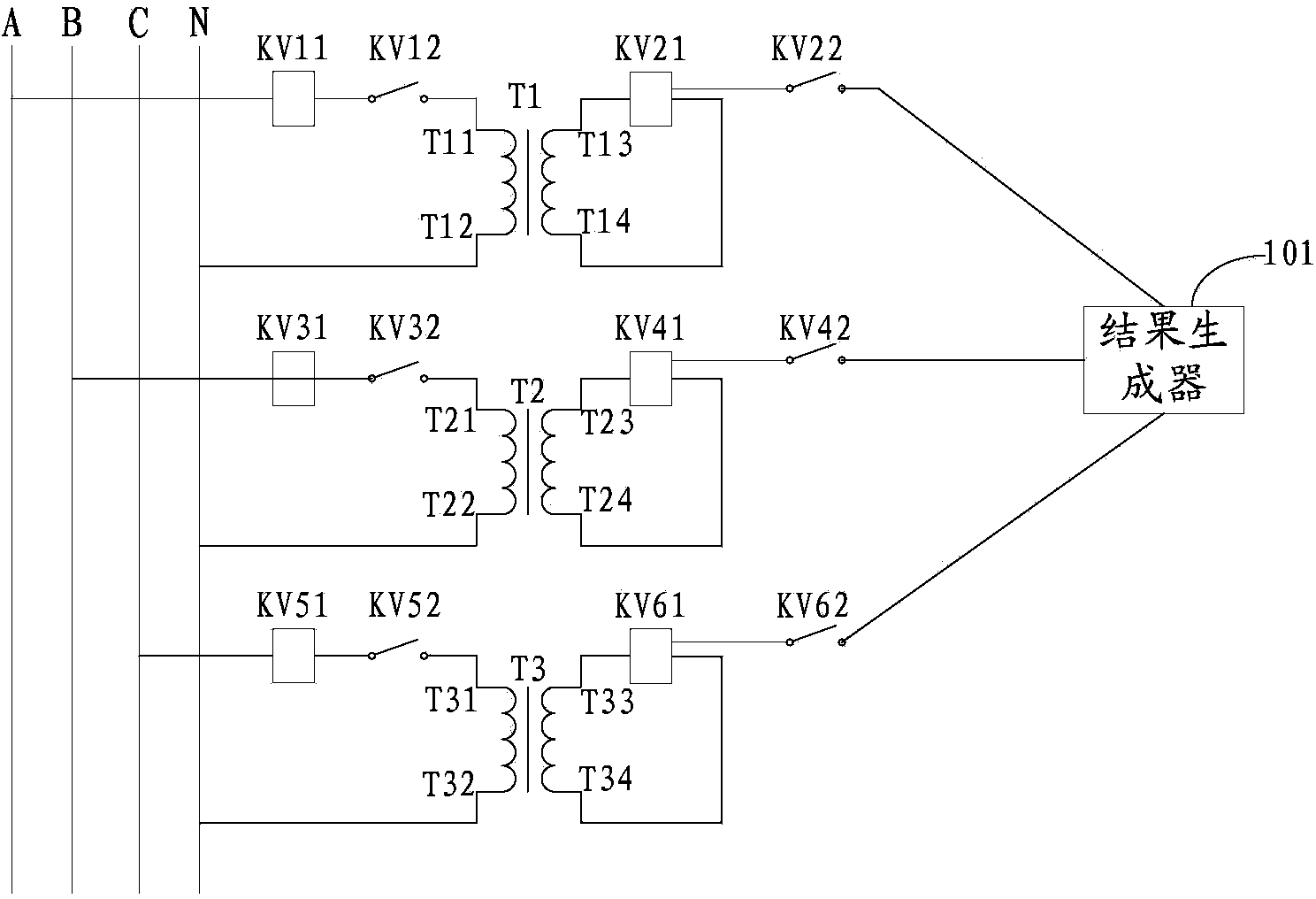
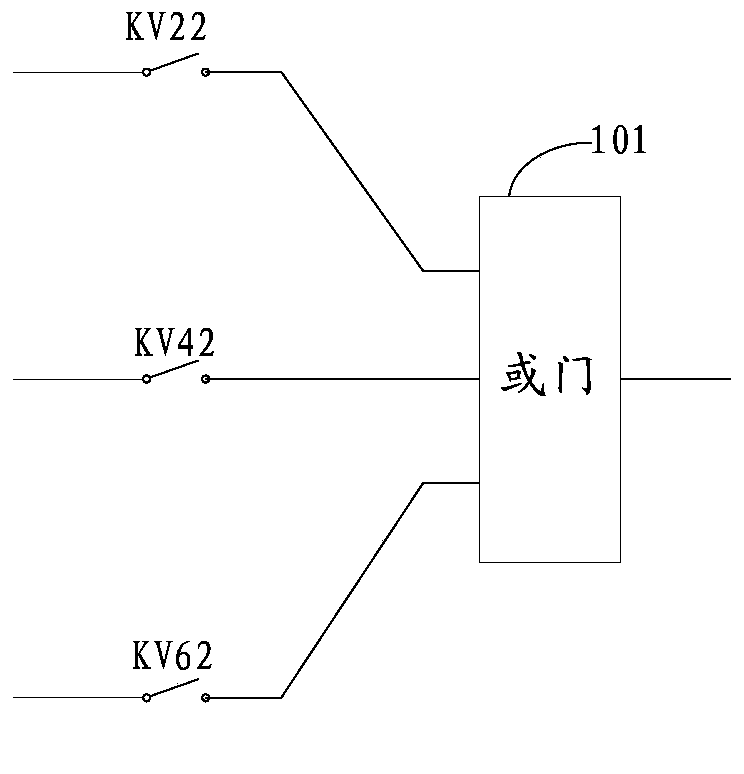
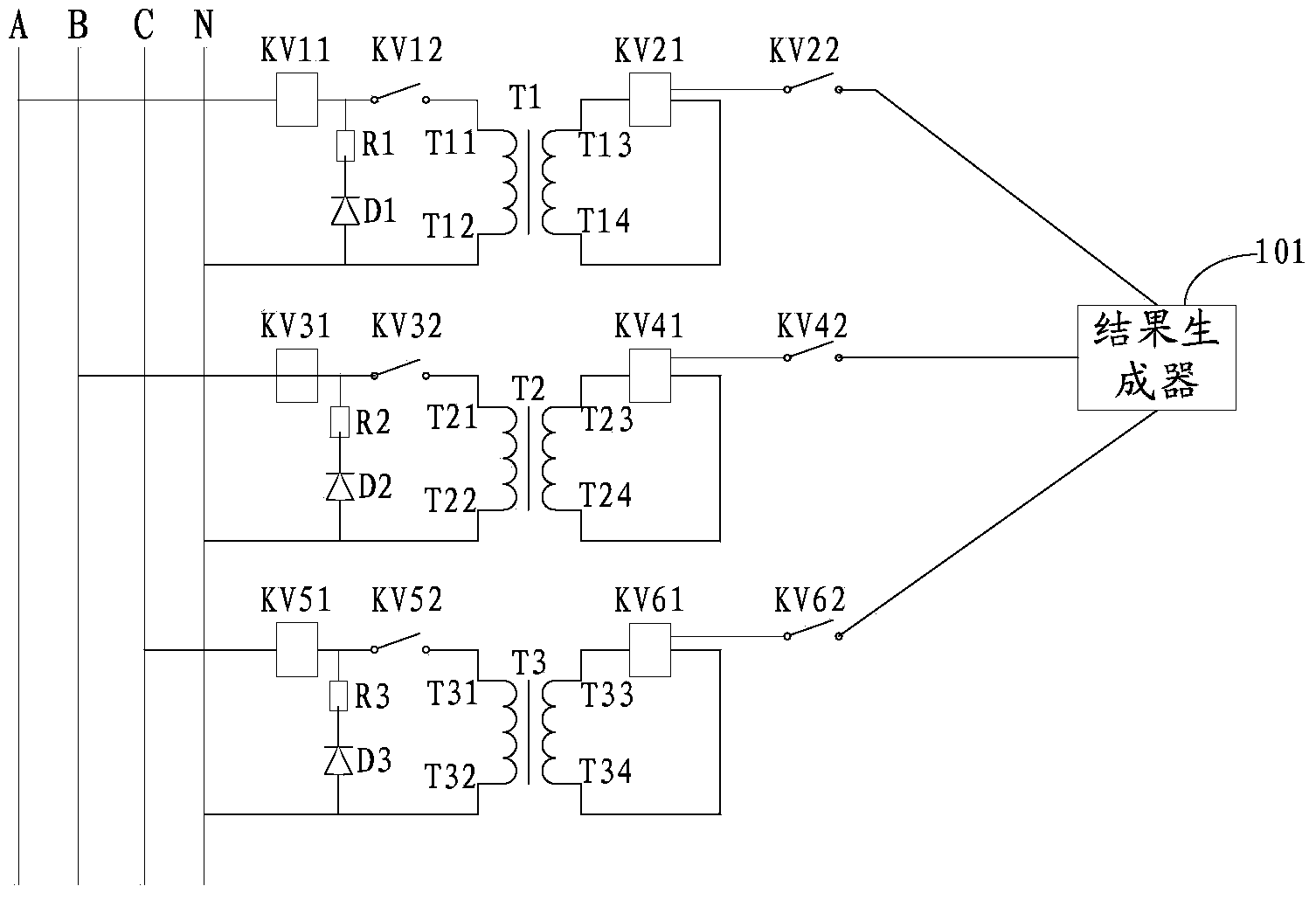
ActiveCN103399253AAvoid security threatsRealize real-time monitoringElectrical testingLow voltageSecondary loop
The invention discloses a device for detecting circuit opening of a secondary circuit of a current transformer. The device comprises relays, normally open contacts of the relays, high-voltage converters and result generators, wherein the relays and the normally open contacts of the relays are connected with a first output end, a second output end, a third output end and a grounding end of the secondary circuit of the current transformer respectively, and the result generators are connected with the normally open contacts. According to the device, one relay and one high-voltage converter are arranged on each phase circuit of the secondary circuit of the current transformer for monitoring voltage of each phase circuit, high voltage on the circuit is timely obtained and converted into lower voltage when the secondary circuit of the current transformer is in an open circuit state, and further, a first detecting result which shows that the secondary circuit is in an open circuit state or a second detecting result which shows that the secondary circuit of the current transformer operates normally is generated, so that whether the secondary circuit of the current transformer is in an open circuit state is detected in real time.
Owner:STATE GRID CORP OF CHINA +1
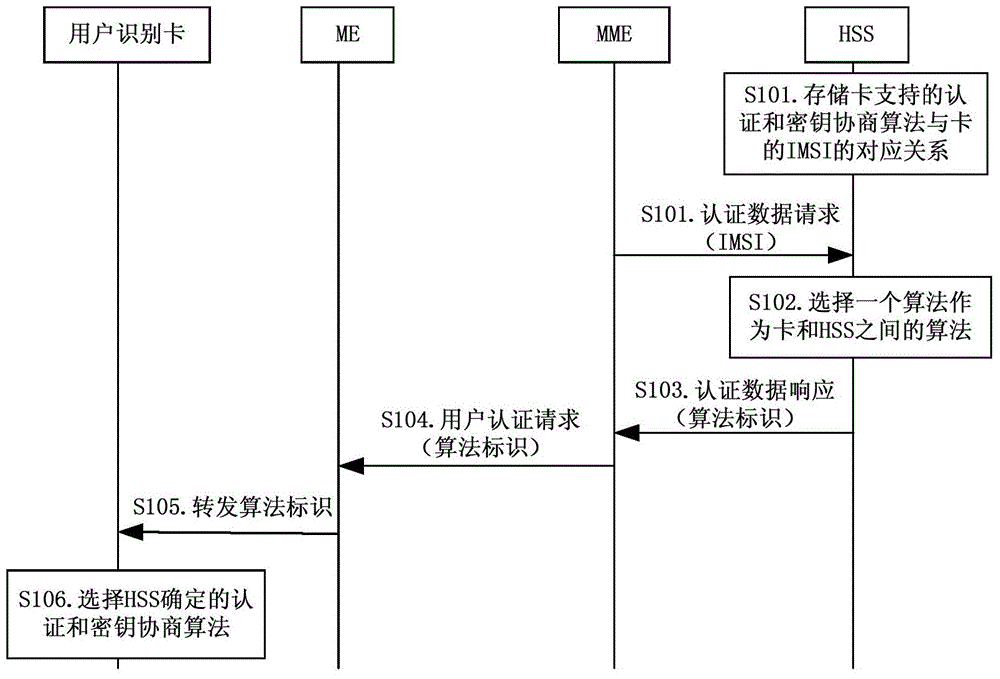
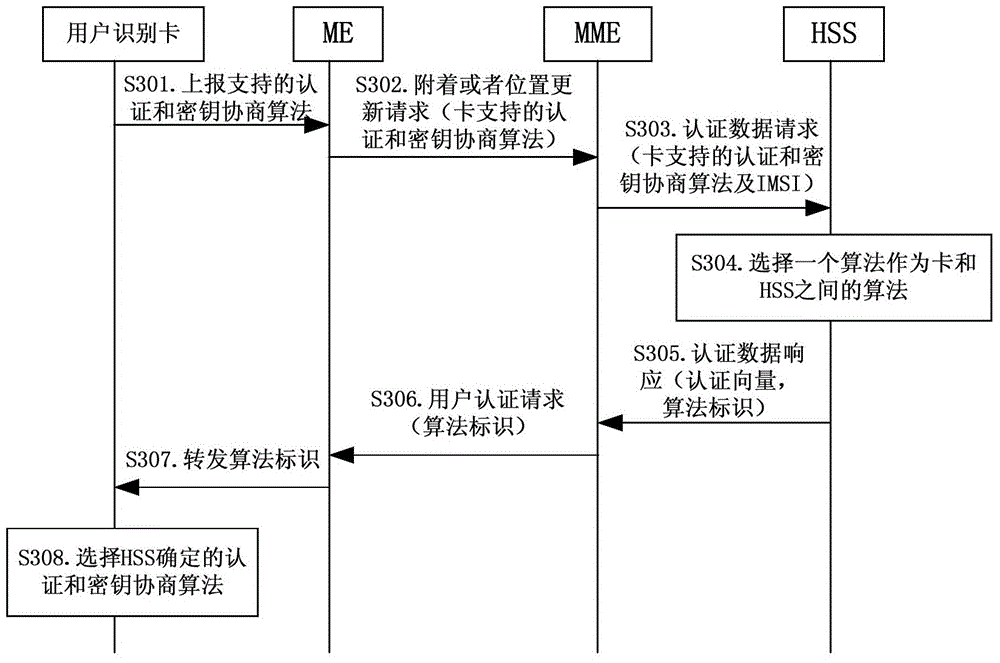
Negotiation method of authentication and key negotiation algorithm, network side equipment and user equipment
PendingCN105306406AAvoid security threatsEnsure safetyKey distribution for secure communicationComputer hardwareAuthentication
The invention provides a negotiation method of an authentication and key negotiation algorithm, network side equipment and user equipment. The method comprises the following steps: acquiring information of the authentication and key negotiation algorithm that a user identification card can support by the network side equipment; selecting an authentication and key negotiation algorithm that the user identification card and an HSS (Home Subscriber Server) can both support by the network side equipment according to the authentication and key negotiation algorithm that the user identification card and the Home Subscriber Server HSS can support; and taking the selected algorithm as the authentication and key negotiation algorithm between the user identification card and the HSS by the network side equipment. By adopting the negotiation method of the authentication and key negotiation algorithm, the network side equipment and the user equipment provided by the invention, the HSS and the user identification card can negotiate the authentication and key negotiation algorithm used by the HSS and the user identification card.
Owner:CHINA MOBILE COMM GRP CO LTD
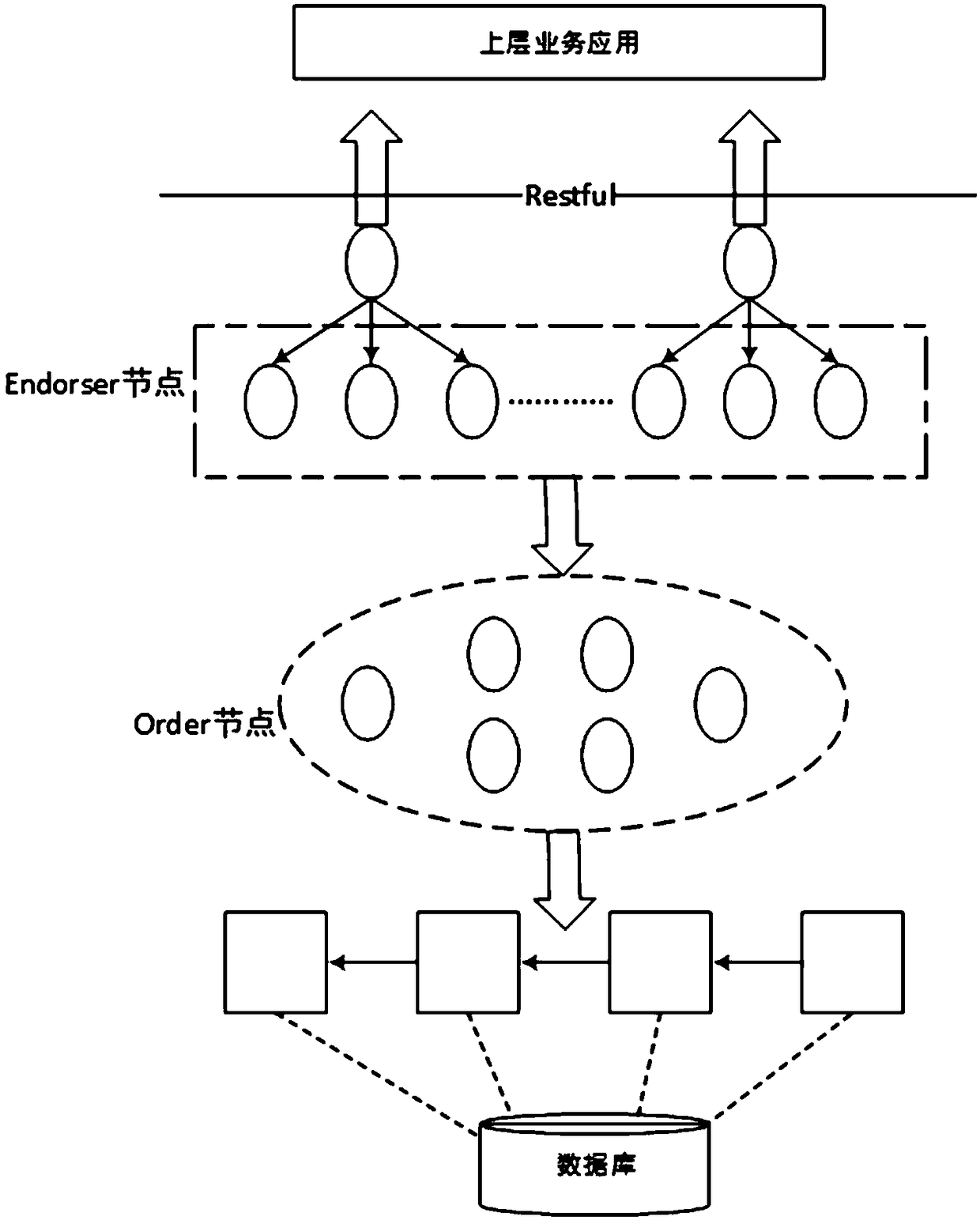
Blockchain-based power data security information system
The invention relates to a blockchain-based power data security information system. The system includes a database, a bottom-layer blockchain subsystem, and an upper-layer service application subsystem which are distributed sequentially from bottom to top; the database is used for storing data corresponding to a blockchain ledger; the bottom-layer blockchain subsystem is used for providing messagequery, message feedback and log query functions to the upper-layer service application subsystem in the form of interfaces, and includes a plurality of peer nodes, a consensus node, and a blockchainledger, wherein the peer nodes generate the blockchain ledger corresponding to the consensus node according to the content of the consensus node; and the upper-layer service application subsystem provides a data access interface by using a Restful-based unified interface mode, and communicates with the peer nodes of the bottom-layer blockchain subsystem through the access interface. Compared withthe prior art, the system of the invention has the advantages of no central data management, non-tampering property, audit fairness, port security shielding and the like.
Owner:SHANGHAI MUNICIPAL ELECTRIC POWER CO +1
Security protection performance evaluation method applicable to power wireless private network base stations
ActiveCN107172621AImprove the effect of early warningAvoid security threatsTransmissionSecurity arrangementPhysical securityPrivate network
The invention discloses a security protection performance evaluation method applicable to power wireless private network base stations. The method comprises the steps of establishing a base station security protection performance evaluation system which comprises a terminal, a plurality of base stations, a switch, a security encryption gateway, a core network, a network management server, a network management client and a security access platform; performing a base station remote or local malicious control security test and checking device remote connection condition, manager information, user lists and sensitive operation records; performing a base station physical security protection security test, testing whether a plurality of terminals with the same USIM card are connected with the same base station or not, and testing whether the terminals access each other or not; performing an illegal base station interference test; and performing a pseudo base station attack test and testing whether the terminals are hijacked by a pseudo base station or not. According to the method, the information security threat for the base stations can be reduced, and the base station security protection control capability can be improved.
Owner:STATE GRID JIANGSU ELECTRIC POWER CO ELECTRIC POWER RES INST +2
Key IP address safety alarm association analysis method based on fuzzy scene
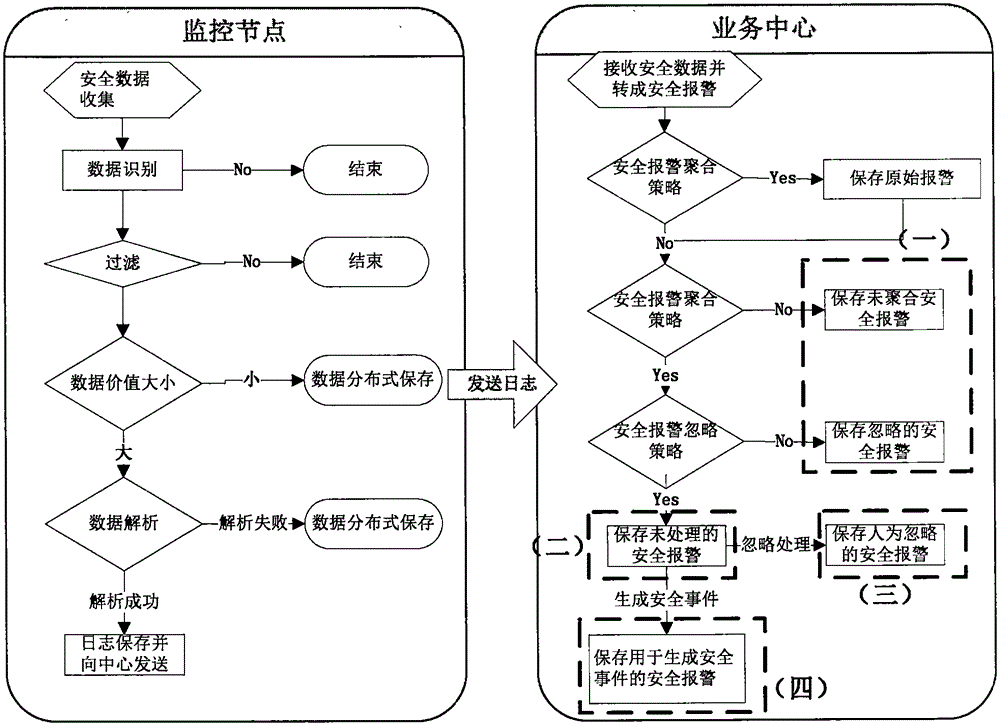
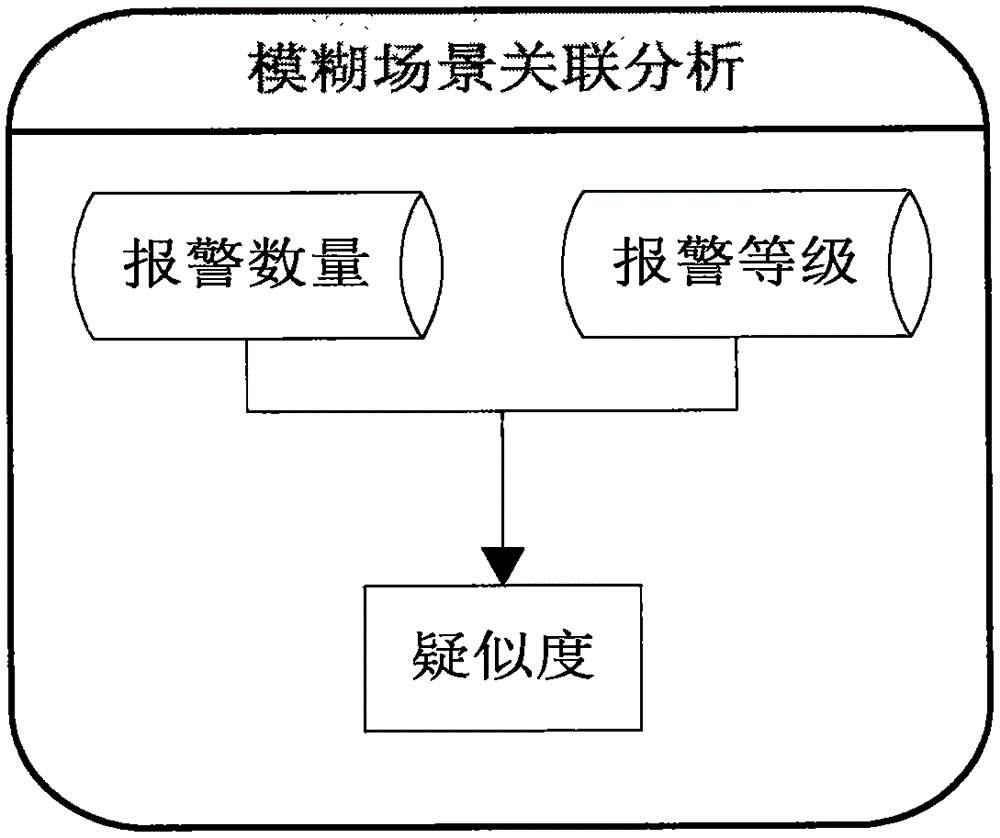
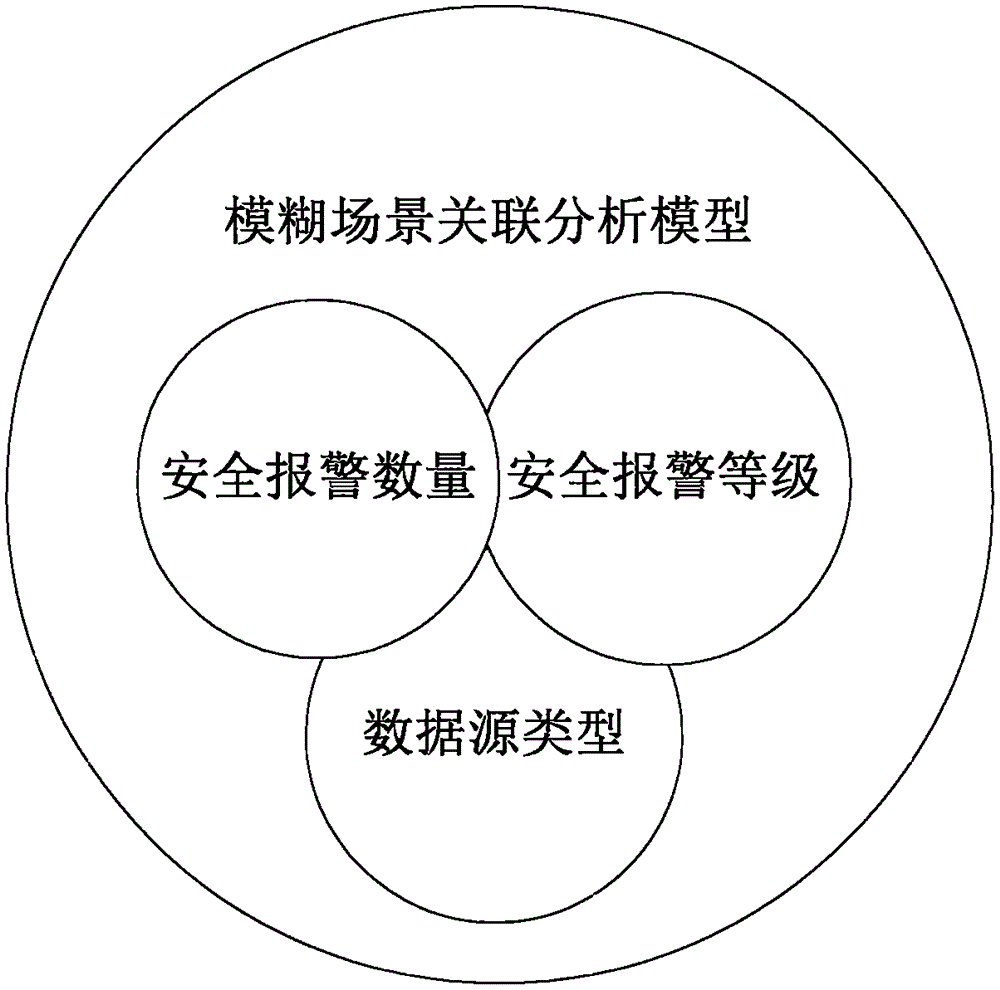
InactiveCN105471623ASolve expert knowledge buildingSolve the problem of difficult knowledge updateData switching networksIp addressAnalysis method
The invention discloses a key IP address safety alarm association analysis method based on a fuzzy scene. The method comprises the steps of: firstly, utilizing a statistic method to aggregate alarms, then utilizing a strategy to neglecting and filtering the alarms, finally utilizing an association analysis algorithm based on the fuzzy scene to calculate an event suspected degree corresponding to a source IP, and utilizing a big data analysis method to carry out statistic querying on alarm logs related to a suspected IP. According to the invention, the concept of fuzzy scene is innovatively provided, and a conventional analysis mode by constructing an attack scene is broken through, wherein the association analysis mode of the fuzzy scene is characterized in that deep excavation and association analysis are carried out on a large number of related safety alarm events with the IP address serving as the core. Related factors of the alarms, which may influence the IP safety, are analyzed, the factors are analyzed in an integrated manner, and a suspected degree value reflecting the safety condition of the IP is obtained by an event suspected degree calculation formula.
Owner:中国烟草总公司江苏省公司
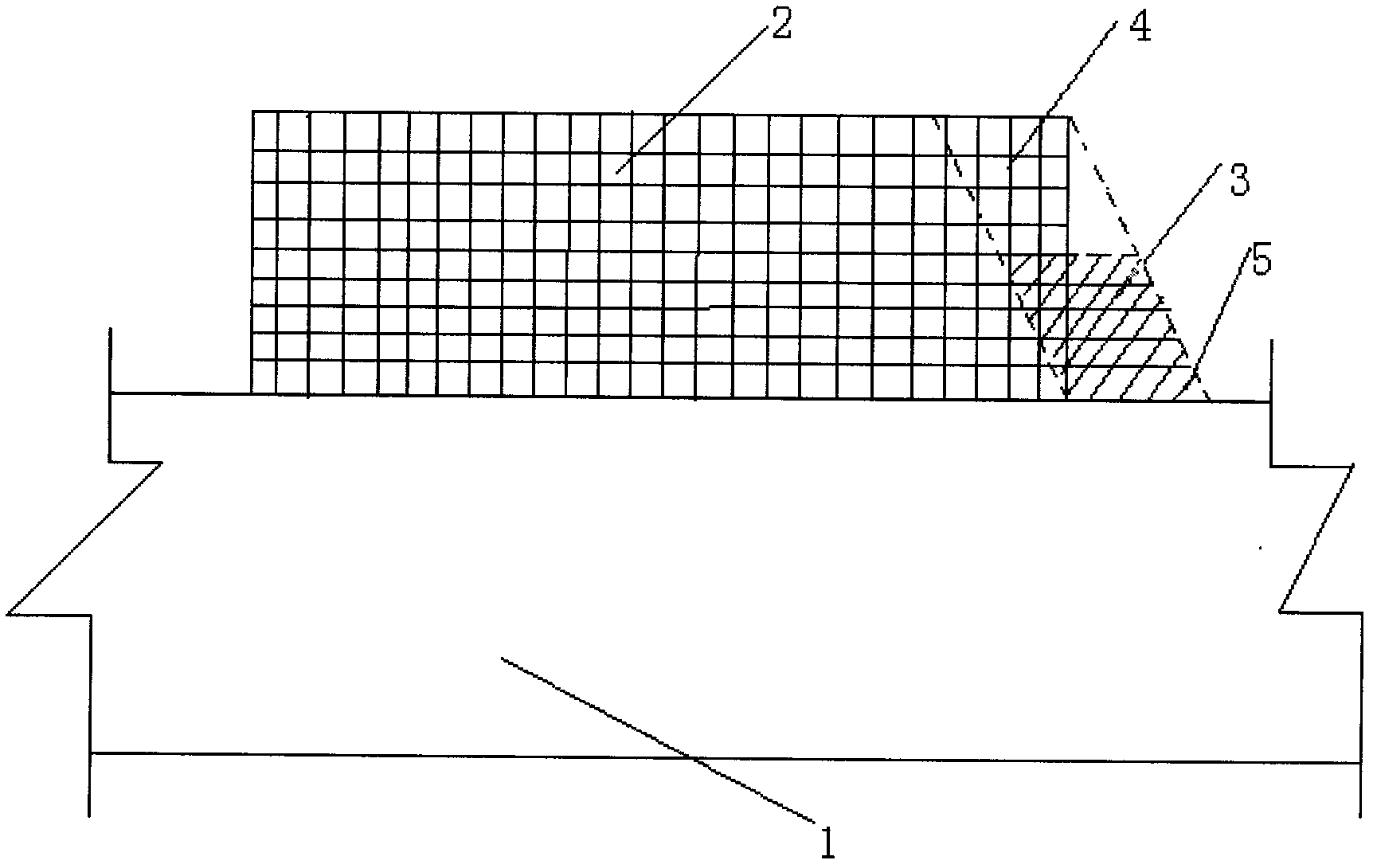
Construction method for opening off small-section underground chamber of coal mine rock roadway into large-section underground chamber
The invention relates to a construction method for opening off a small-section underground chamber of a coal mine rock roadway into a large-section underground chamber. The construction method comprises the following steps of: drilling and blasting on the top of the rock roadway at a design starting position of the underground chamber at an angle of 70 degrees tilting relative to the longitudinal direction; layering and roof-ripping; clearing by using a scraper loader; brushing the wall while spraying slurry; and the like. The construction method has the advantages of optimizing construction processes, greatly increasing the production efficiency, reducing the labor intensity of workers and increasing the safety coefficient during construction. The construction has high adaptability; the small-section underground chamber can be opened off into the large-section underground chamber on the basis of the conventional small-section rock roadway; the time is saved; and the resource waste is also avoided.
Owner:李菊菊
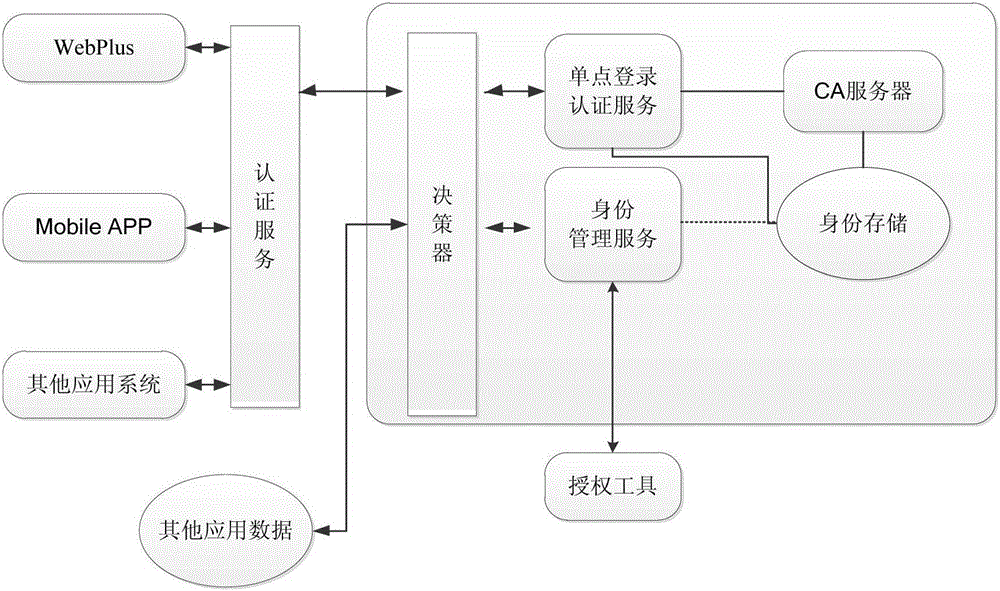
Context awareness type dynamic unified authentication method and system
InactiveCN105827641AImprove experienceEnsure application securityTransmissionPersonalizationServer-side
The present invention proposes a context-aware dynamic unified authentication method and system. By collecting personalized information of users when using the Internet and mobile Internet, the server log files stored in the client, Web server and proxy server can be verified. , Cookies, user registration information, and data explicitly entered by users, etc., for machine learning and data mining, and dynamically verify the user's identity. Learn the user's usage habits, and dynamically adjust the authentication level according to the status of the user's current terminal device and access method. In the environment that the user is familiar with, the authentication is mainly convenient and fast. When the user is in an unfamiliar environment, the authentication level is automatically increased. The implementation of the present invention can effectively solve the security threats that may exist in the increasingly popular mobile Internet applications, and through appropriate comprehensive protection measures, overcome the vulnerability of the mobile Internet system itself, control and reduce its security risks, and ensure people's daily work, Mobile Internet applications in life are safe, and at the same time, improve user experience.
Owner:WOSIGN CA LTD +1
Online earth fault positioning system for power distribution network
InactiveCN103558511AAvoid security threatsImprove power supply reliabilityFault locationInformation technology support systemSingle phaseTransformer
The invention discloses an online earth fault positioning system for a power distribution network. The online earth fault positioning system comprises a monitoring center, a transformer substation signal injection unit, a feeder line branch positioning unit and a distribution transformation monitoring terminal, wherein the monitoring center conducts data exchange with the transformer substation signal injection unit and the feeder line branch positioning unit to achieve the functions of operating data management, logical judgment and fault removal control; the transformer substation signal injection unit achieves the functions of earth fault detection, fault phase distinguishing, special signal injection, fed-out line signal detection and line selection; the feeder line branch positioning unit and the distribution transformation monitoring terminal achieve the functions of branch data acquisition, data exchange with the monitoring center, branch earth fault removal and accurate positioning of an earth point. By means of the online earth fault positioning system for the power distribution network, accurate positioning of an online single-phase earth fault can be realized, a fault section can be removed an isolated as quickly as possible after the earth fault occurs, as a result, security threats to electrical equipment and personnel due to the earth fault are avoided, and power supply reliability is improved.
Owner:STATE GRID CORP OF CHINA +1
Treatment method for upper corner suspension roof of heavy pitch fully mechanized mining coalface
InactiveCN107269220AEasy constructionReduce the possibilityDrilling using explosivesDisloding machinesDrill holeBuilding construction
The invention discloses a method for controlling the corner suspended roof of a steeply inclined fully mechanized mining face, which is mainly composed of forced caving drilling, hydraulic fracturing drilling, and advanced pre-splitting blasting drilling. Two rows of forced caving drill holes are arranged along the direction of the support, and a row of advanced pre-splitting blasting drill holes are arranged along the strike direction in the wind tunnel advance support of the coal mining face. Hydraulic fracturing boreholes are arranged in between. The structure is easy to construct, which destroys the integrity of the roof of the goaf in the coal mining face, releases and weakens the pressure of the roof in the advance support section, and can timely collapse the suspended roof of the goaf in the upper corner, reducing the risk of large-scale collapse of the suspended roof. The possibility of gas exceeding the limit is eliminated, and the safety threat caused by the large overhanging area of the upper corner of the steeply inclined fully mechanized mining face to mine gas control and roof management is very effective.
Owner:LYUSHUIDONG COAL MINE OF SICHUAN HUAYINGSHAN COALIND
Lightweight class RFID safety certification method based on Present algorithm
ActiveCN107171811AShorten the lengthAvoid security threatsKey distribution for secure communicationUser identity/authority verificationPrivacy protectionEavesdropping
The invention discloses a lightweight class RFID safety certification method based on a Present algorithm. The lightweight class RFID safety certification method based on a Present algorithm comprises steps of realizing identity mutual certification between a label and a database through sharing an old cipher key and new cipher key and secretes information between the back end database and the label, adopting a two-way random number as a fresh quantity during a protocol execution process and performing encryption calculation, wherein certification information of a label end on the database is encrypted by producing the random number from a database end and the certification information of database end on the label is encrypted by the random number generated by the label end, and executing a Present encryption algorithm to verify identities of two parties in each verification process. The lightweight class RFID safety certification method based on the Present algorithm has characteristics of safety and privacy protection, can better resist various attacks coming from the outside of the RFID system, can protect content privacy, position privacy and front and back safety and resists replay attacks, eavesdropping attacks, etc.
Owner:BEIJING UNIV OF POSTS & TELECOMM +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com