program non-control data attack protection method based on an LLVM compiler
A compiler, non-controlling technology, applied in the direction of code compilation, program code conversion, platform integrity maintenance, etc., can solve the problems of high performance overhead, affecting the effect of protection, poor portability, etc., and achieve low space and time complexity. , Improve the accuracy and prevent the effect of related attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0074] The present invention will be further described in detail below in conjunction with specific embodiments, which are explanations of the present invention rather than limitations.
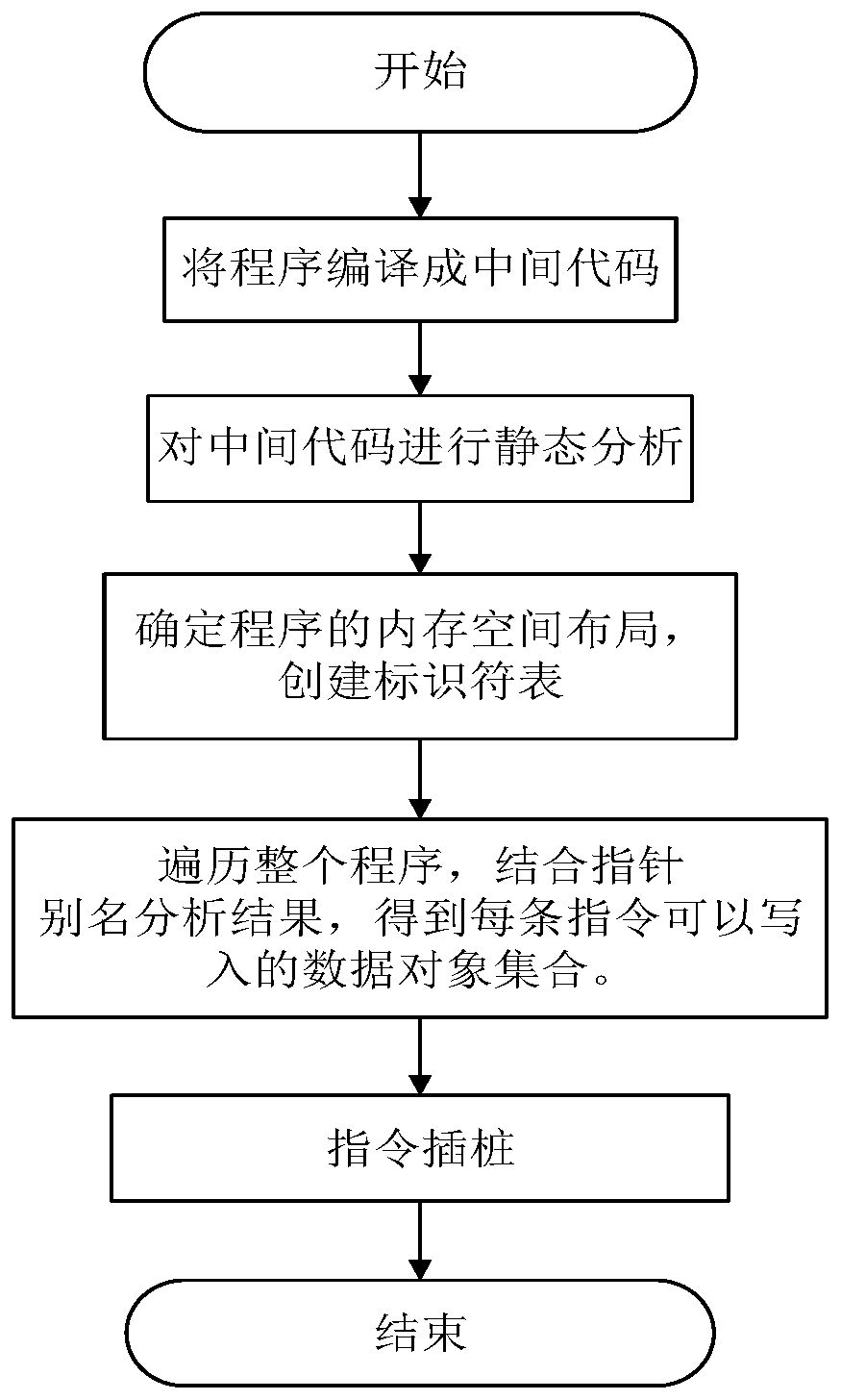
[0075] The present invention is proposed based on such an observation: no matter what type of attack on data tampering, if they want to tamper with data, they must pass unsafe data writing operations. If all data writing operations can be protected , it can fundamentally resist attacks against data tampering.
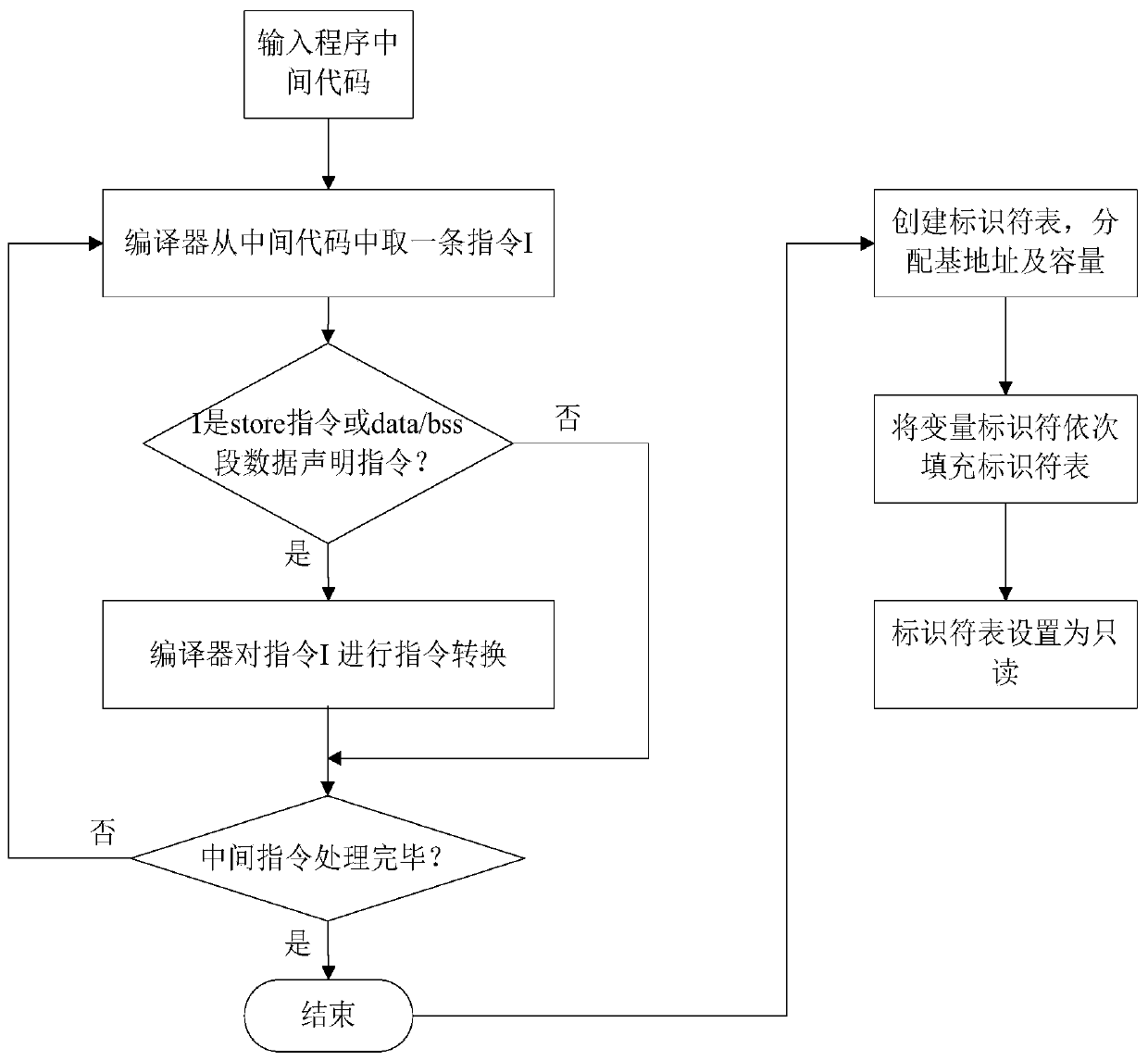
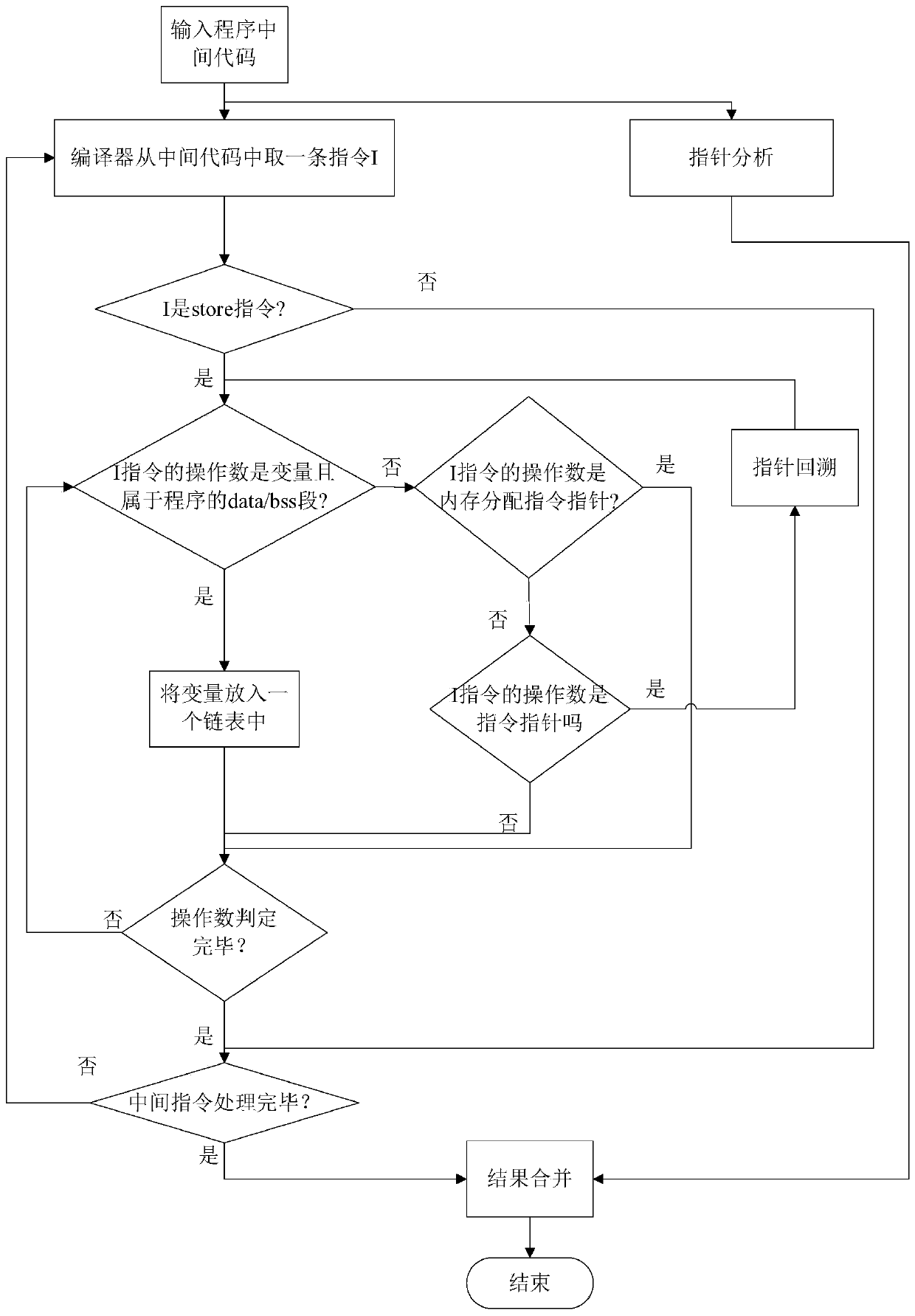
[0076] The core idea of the present invention is to design and implement a writing protection technology for non-control data. This mechanism assigns an identifier to each data write instruction, and at the same time, in the program compilation stage, assigns an identifier to the data in the data / bss segment of the program to form an identifier table; through compiler-based instruction conversion, the program is performing data When writing, do not write directly, but first compare ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com