Patents
Literature
54 results about "Memory safety" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Memory safety is the state of being protected from various software bugs and security vulnerabilities when dealing with memory access, such as buffer overflows and dangling pointers. For example, Java is said to be memory-safe because its runtime error detection checks array bounds and pointer dereferences. In contrast, C and C++ allow arbitrary pointer arithmetic with pointers implemented as direct memory addresses with no provision for bounds checking, and thus are termed memory-unsafe.
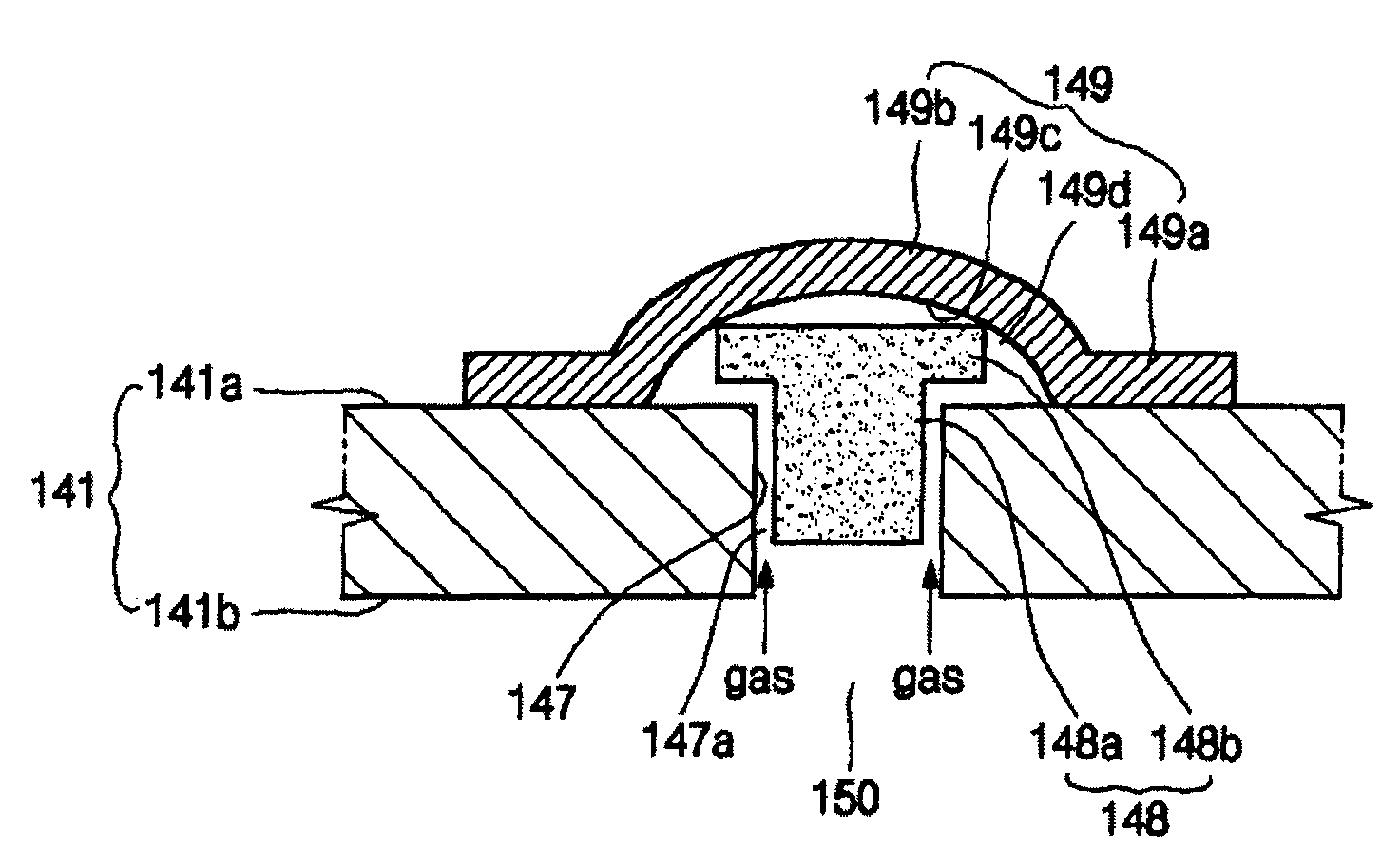
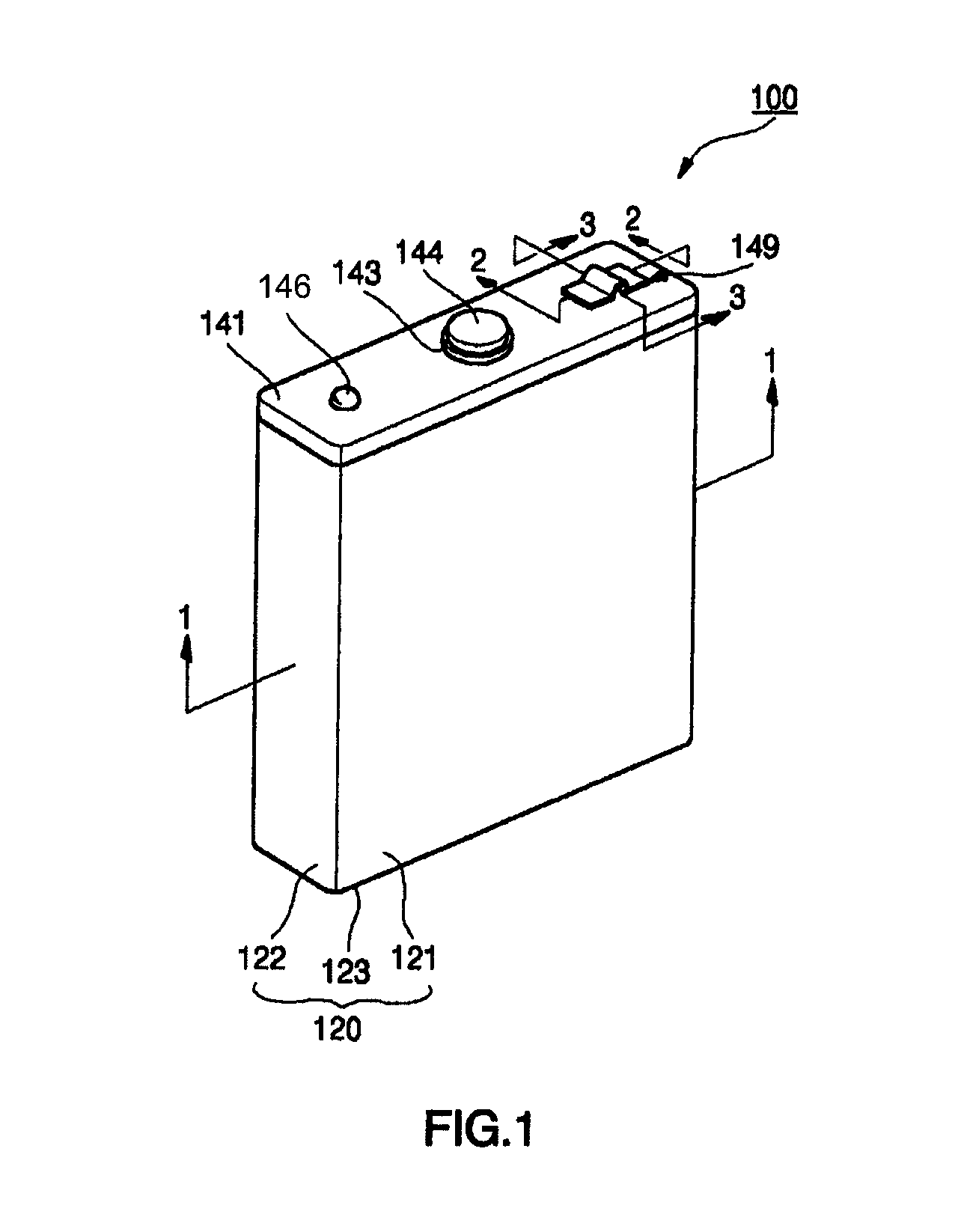
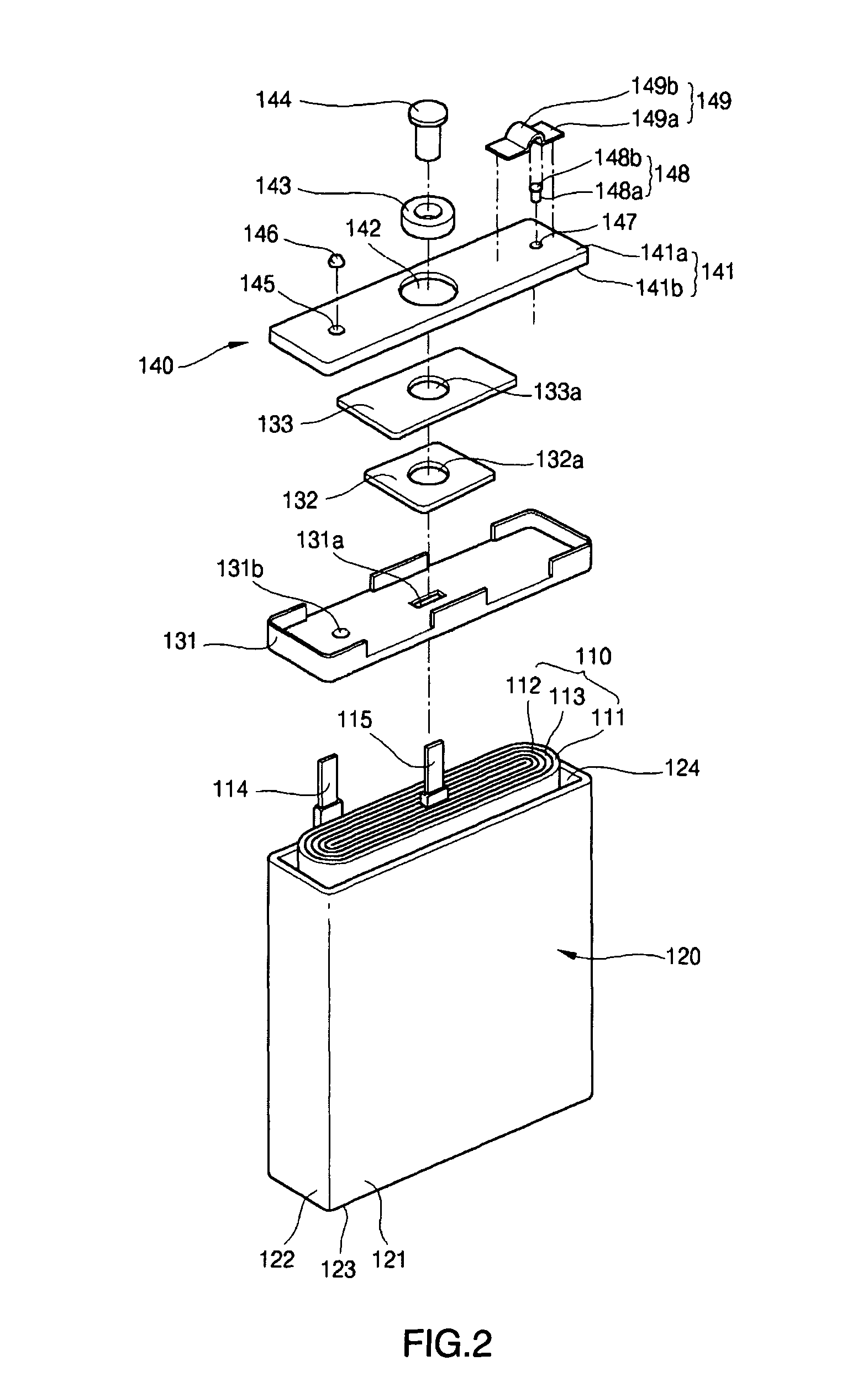
Lithium ion secondary battery having shape memory safety vent
InactiveUS20060073375A1Easy dischargeImprove securityFinal product manufactureCell temperature controlLithiumMemory safety
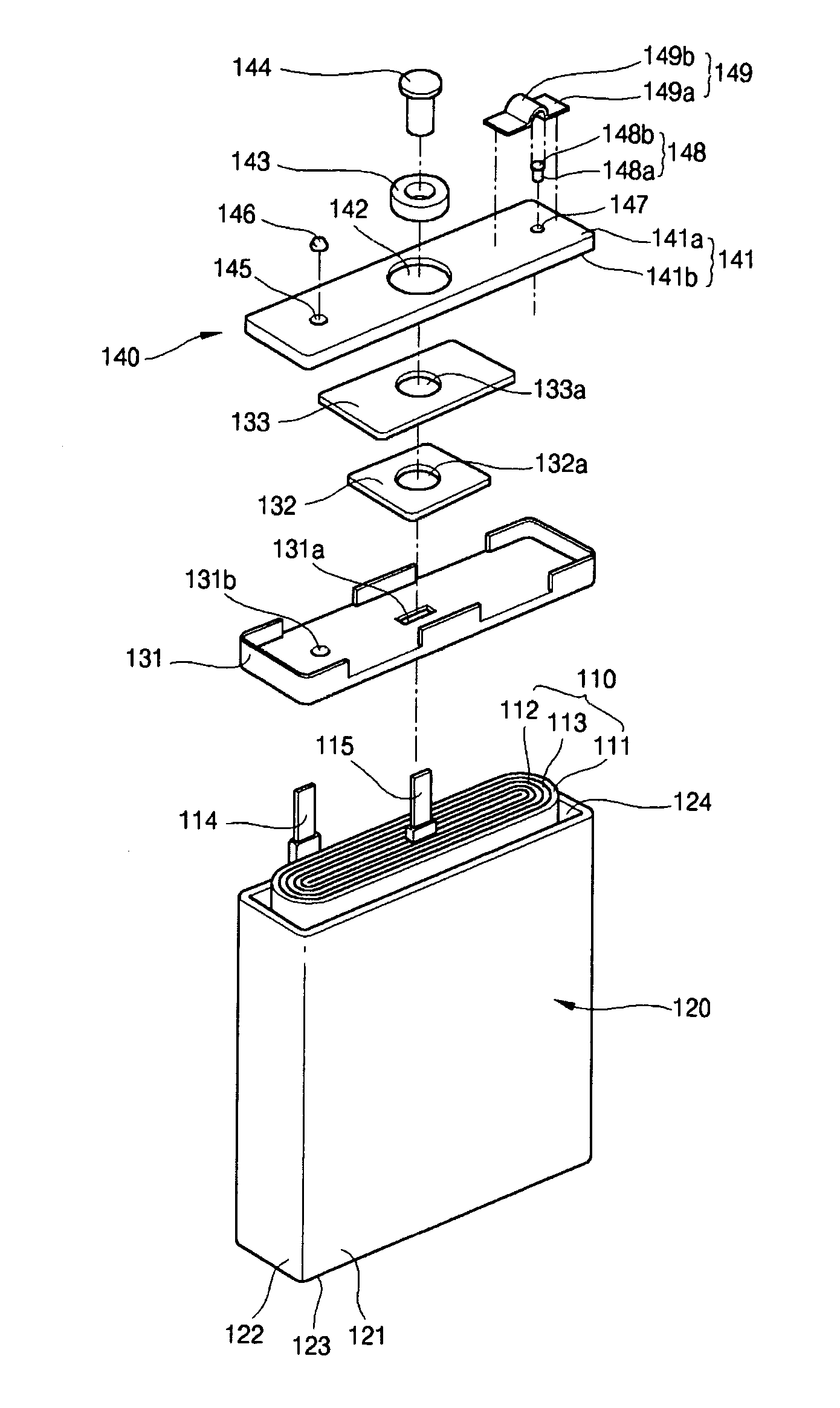
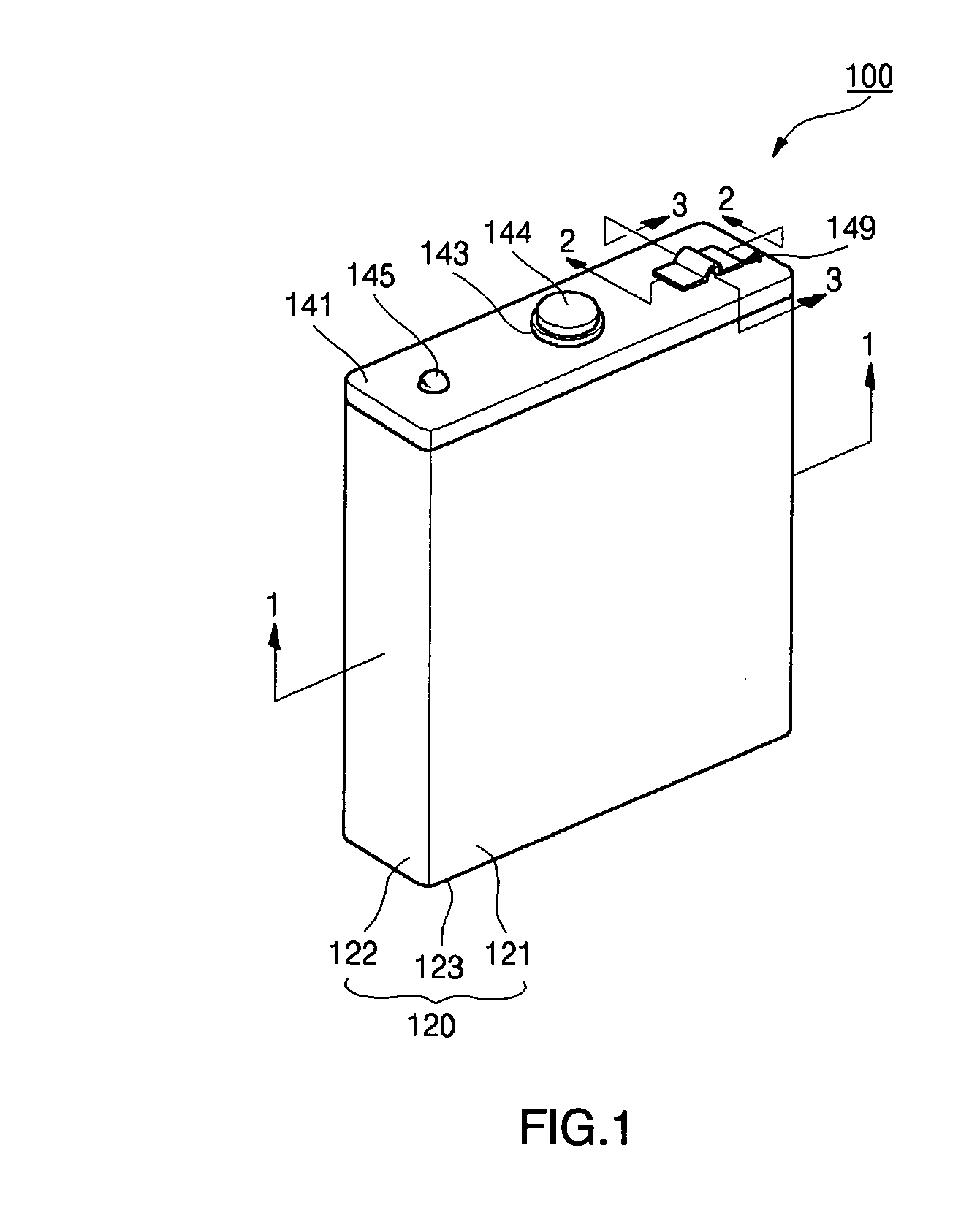
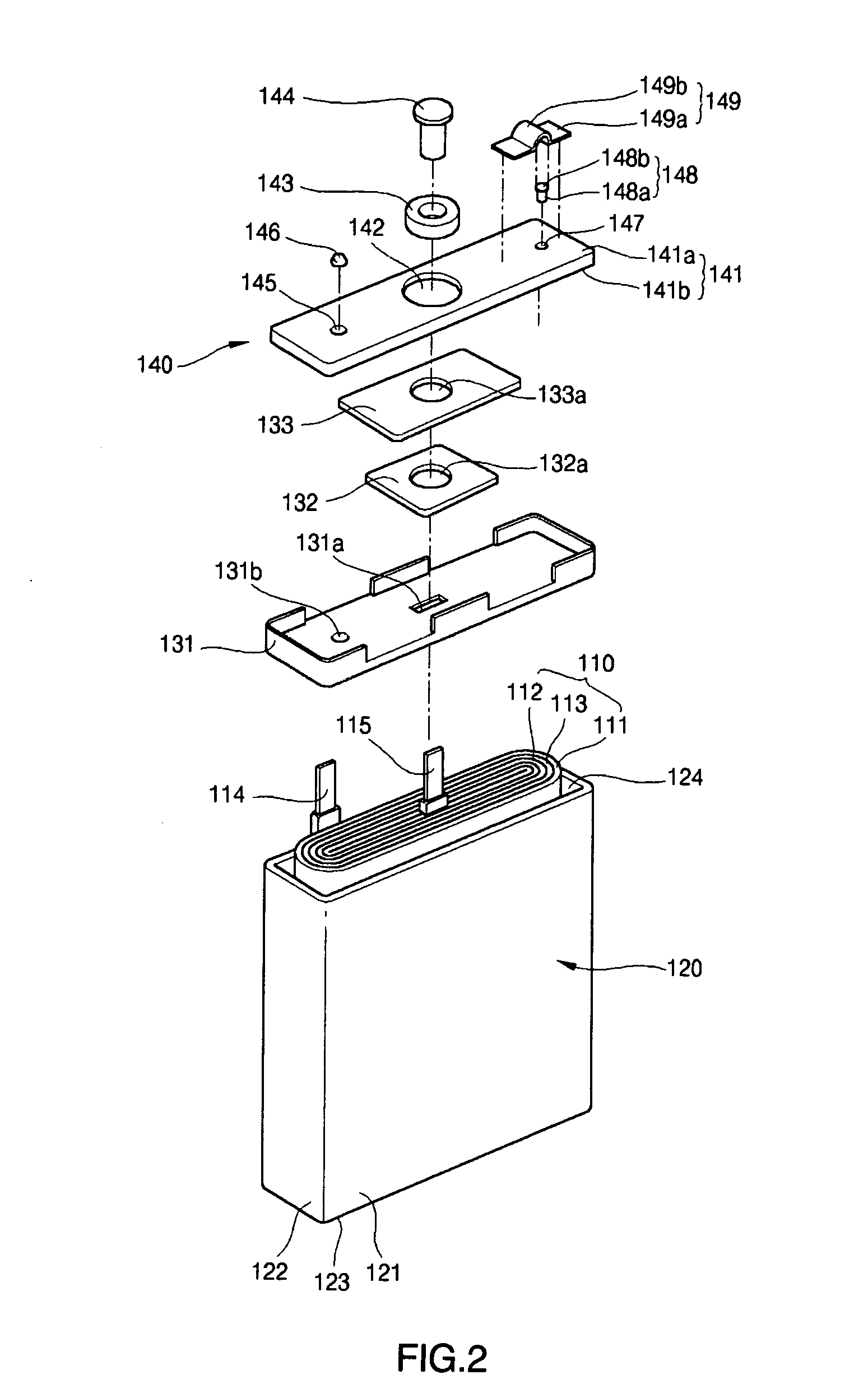
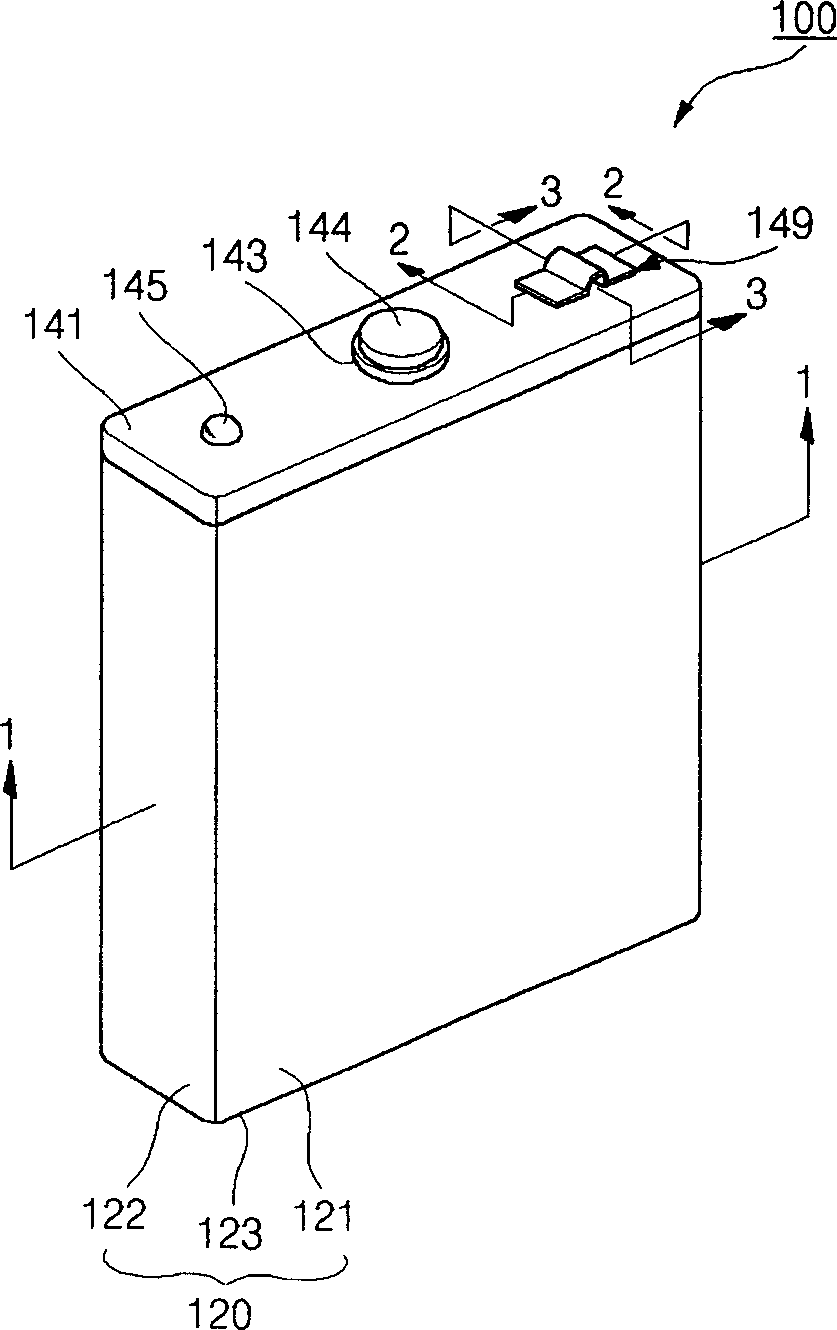
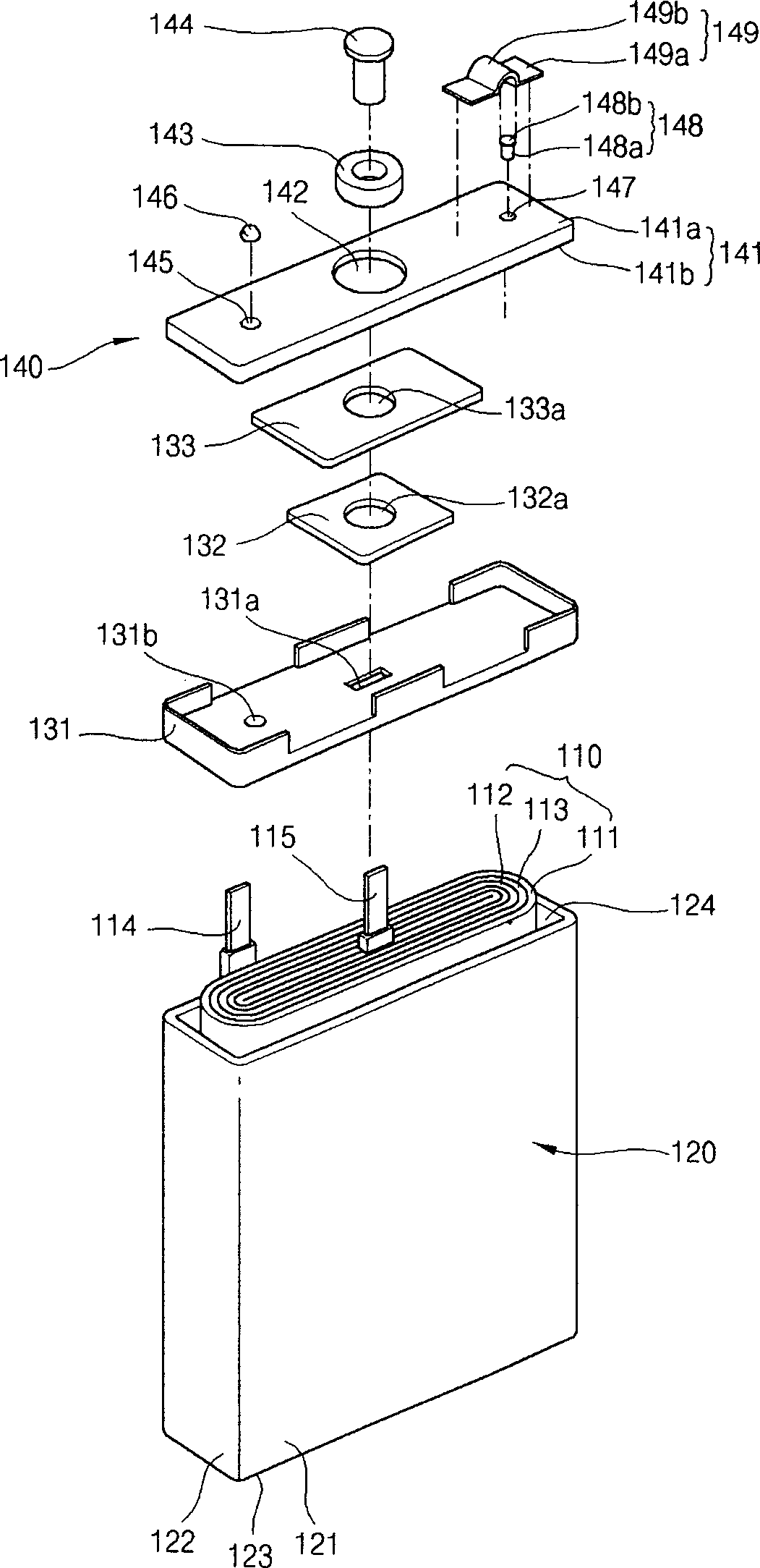
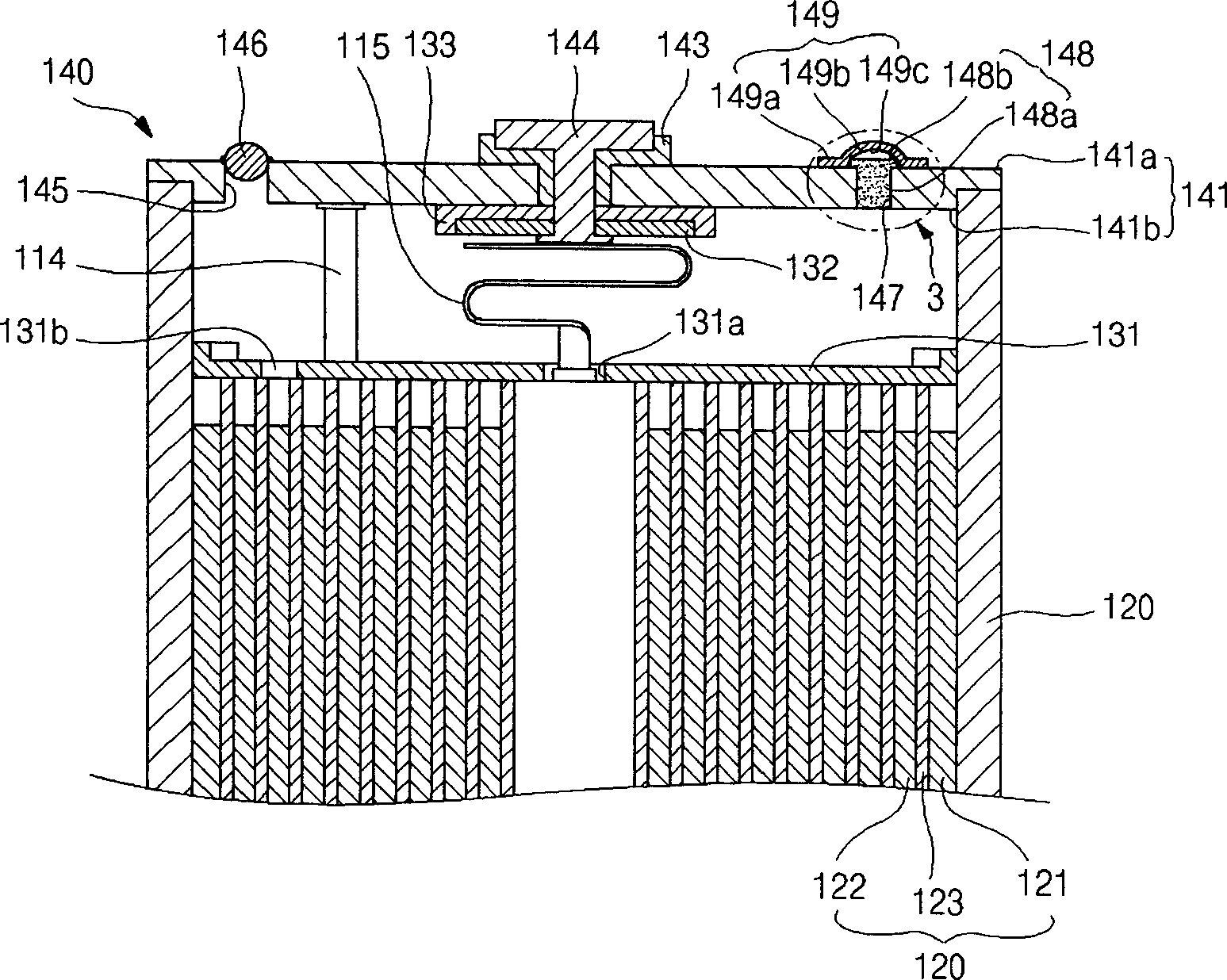
A lithium ion secondary battery has a shape memory safety vent adapted to discharge internal compressed gas by temporarily being opened when the temperature reaches a predetermined level to avoid a swelling phenomenon of the battery and improve safety. The lithium ion secondary battery includes an electrode assembly having first and second electrode plates wound a number of times with a separator interposed between them; a can having an opening formed on a side thereof to contain the electrode assembly; and a cap plate adapted to cover the can and provided with a vent hole on a side thereof, to which a safety vent adapted to deform at a predetermined temperature and discharge gas from inside the can to the exterior is coupled.
Owner:SAMSUNG SDI CO LTD
Method for technically controlling secure access to embedded system memory
ActiveCN105787360ARealize dynamic switchingEnsure legitimate accessInternal/peripheral component protectionPlatform integrity maintainanceWrite bufferOperational system
The invention discloses a method for technically controlling secure access to an embedded system memory. The method includes the following steps of initially designing a system of a memory secure access mechanism, wherein an MPU memory protection unit is introduced, domain attributes of different grades are distributed, and an access attribute and a system initiating progress are set; secondly, designing the secure access to the memory for switching of embedded operation system process context, wherein a domain control module is set, the system process context is set, and switching of the system process content is achieved in the domain control module. The illegal access of all address space resources are detected and limited through a processor MPU hardware mechanism, the boundary control and context switching of any task of the embedded real-time multi-task operation system for accessing resources of other tasks is achieved, distributing and designing of cache, writing buffer and MPU attributes of different storage spaces in the system are achieved, and the control over secure access to all background domains in the memory is ensured.
Owner:HANGZHOU BYTE INFORMATION TECH CO LTD
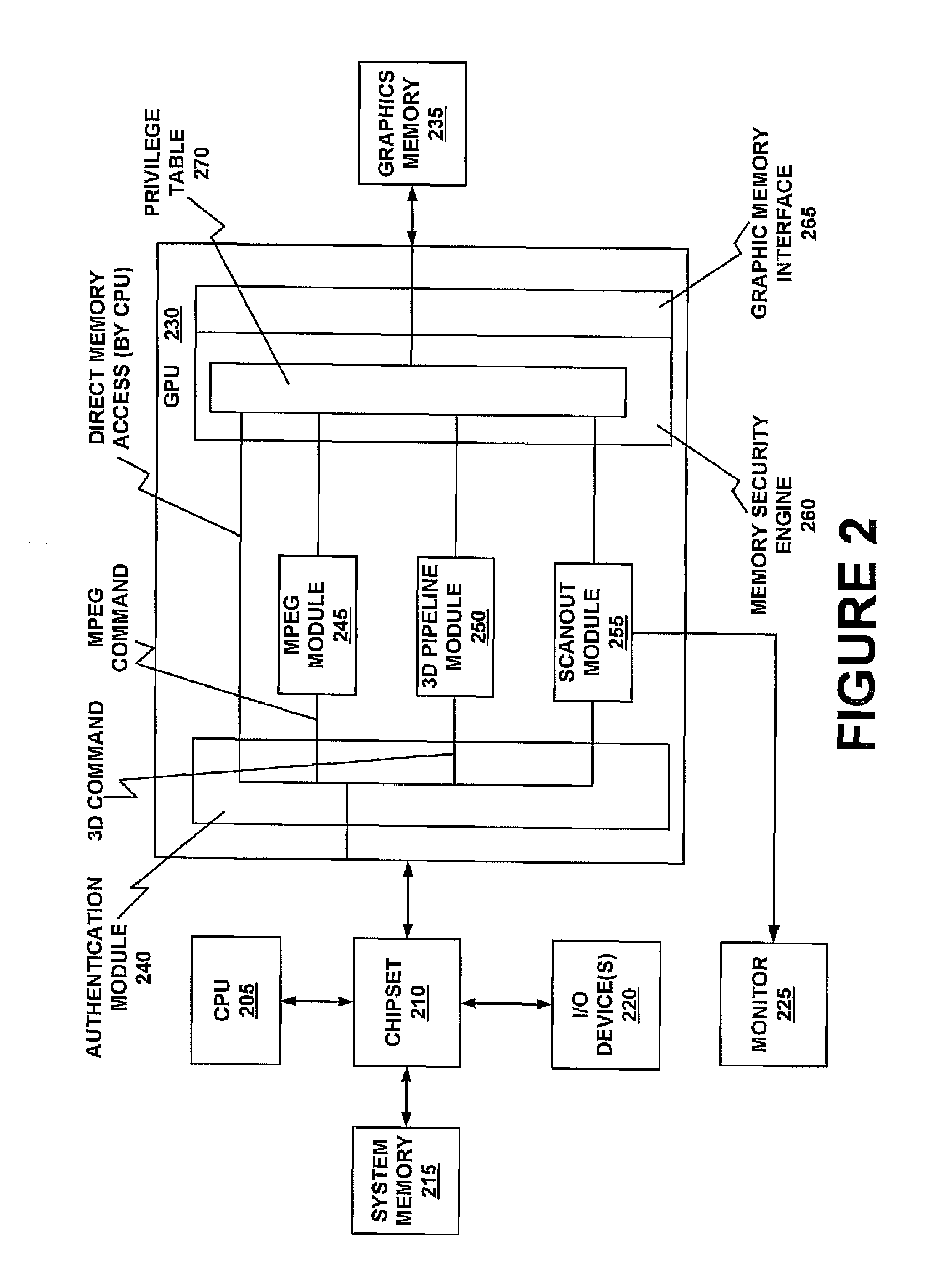
Memory redirect primitive for a secure graphics processing unit
InactiveUS7474312B1Increase image processing latencyNon-computationalImage memory managementCathode-ray tube indicatorsMemory addressGraphics
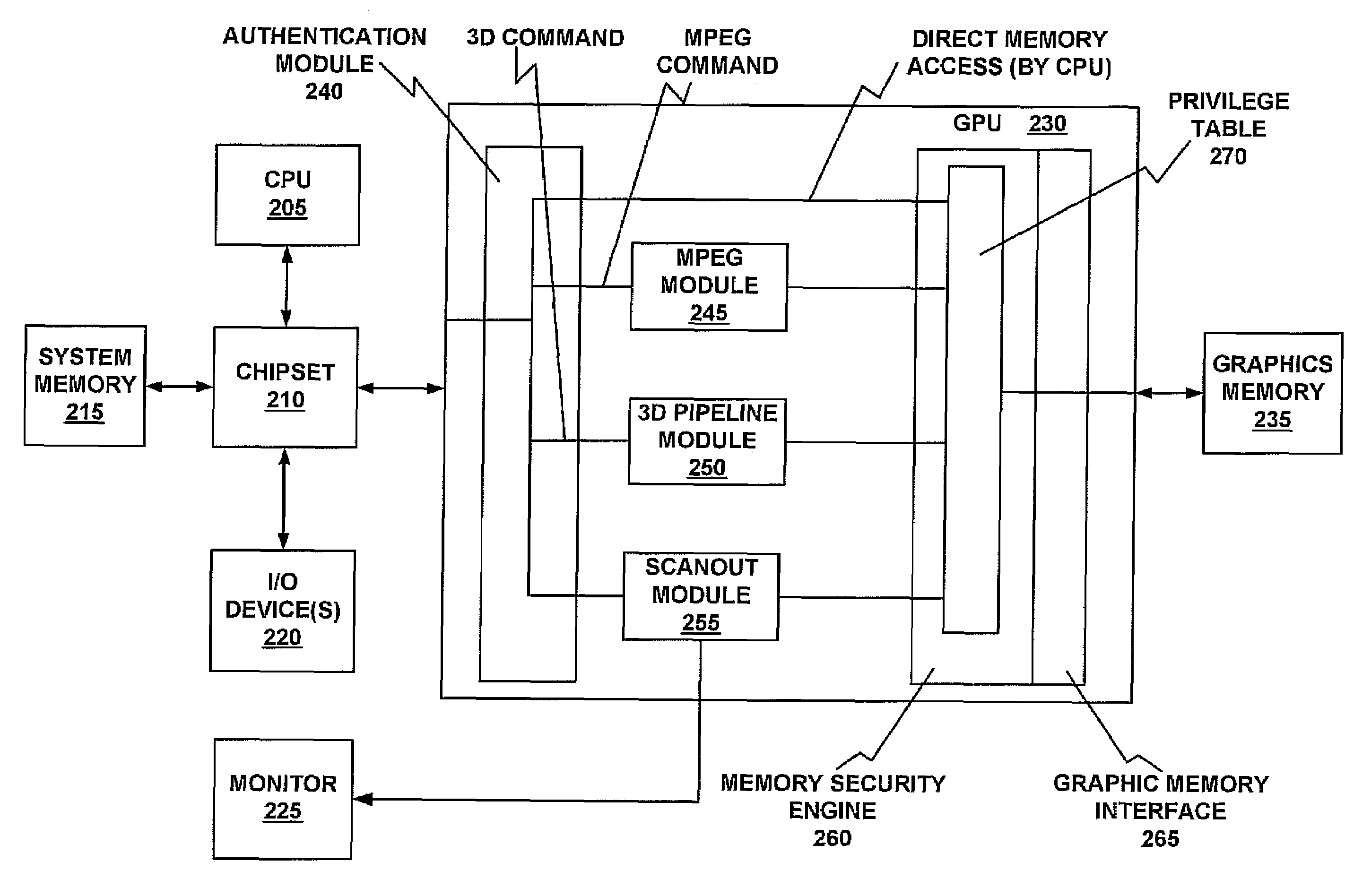
In one embodiment of the present invention, a GPU contains an authentication module at the front end, and a memory security engine and graphic memory interface at the backend. In one embodiment of the present invention, the memory security engine provides a privilege table. The programmable privilege table maps memory address ranges, and user IDs to privileges for accessing the memory address ranges. In one embodiment of the present invention, the memory security engine receives a memory access command along with an associated authenticated user ID. In one embodiment of the present invention, the memory security engine checks the authenticated user ID and address range against the privilege table. In one embodiment of the present invention, if the table indicates that the user has authorization for the particular read or write transaction to the graphic memory, the instruction is executed by the graphic memory interface. If the accessed address is not in the table, no special privileges are needed to access that address. If the table indicates that the user does not have authorization for the particular read or write transaction, the memory security engine provides a memory redirect.
Owner:NVIDIA CORP
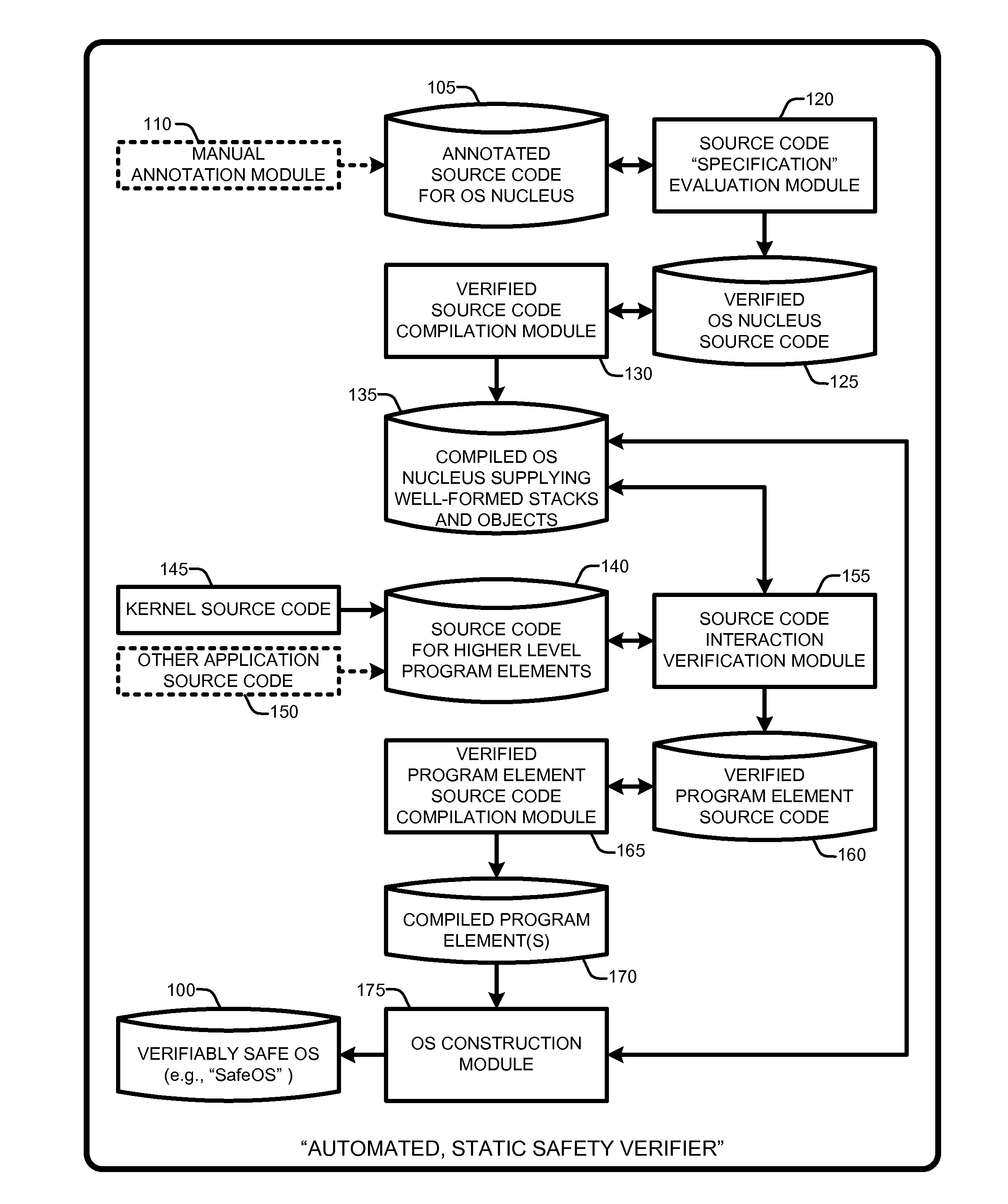
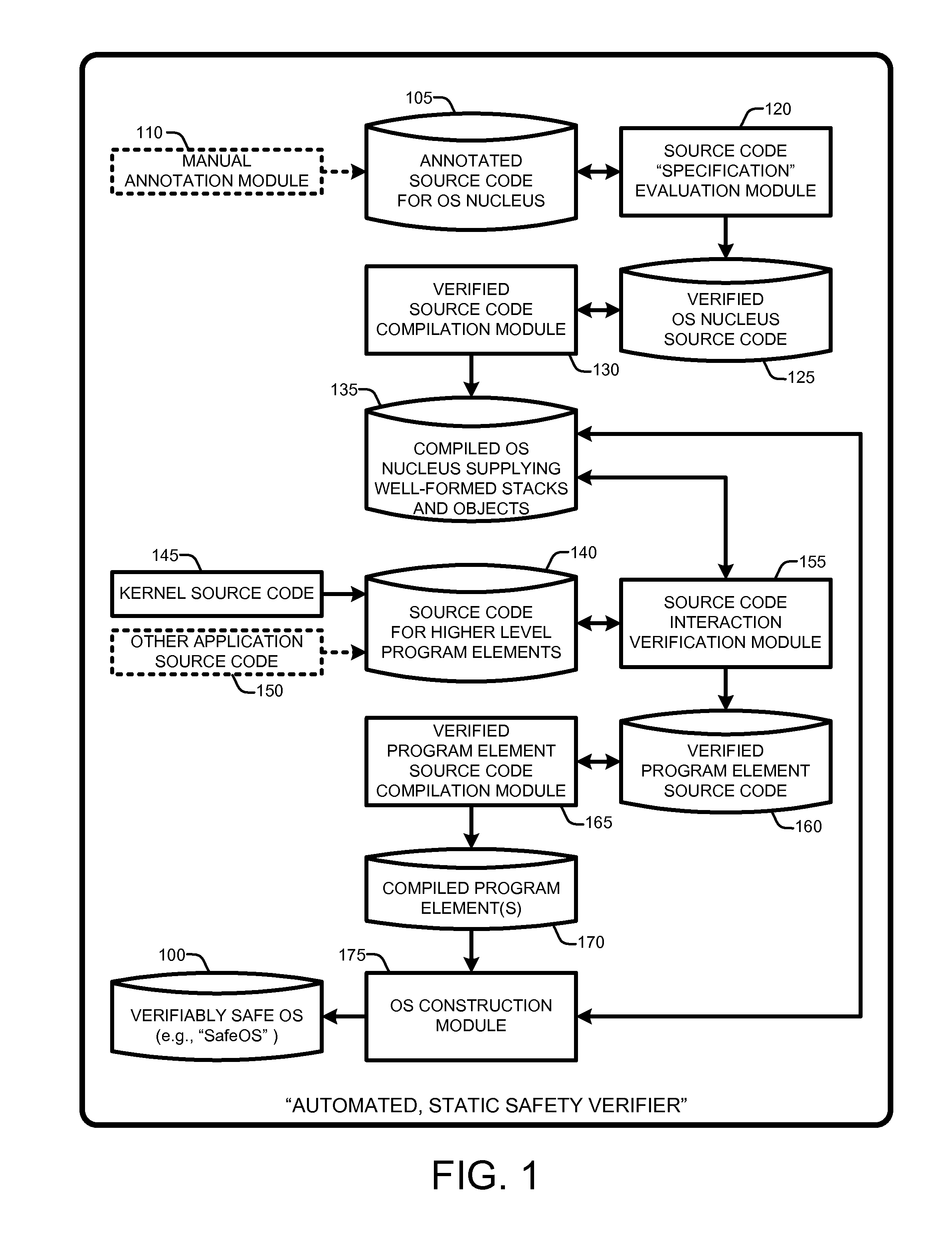
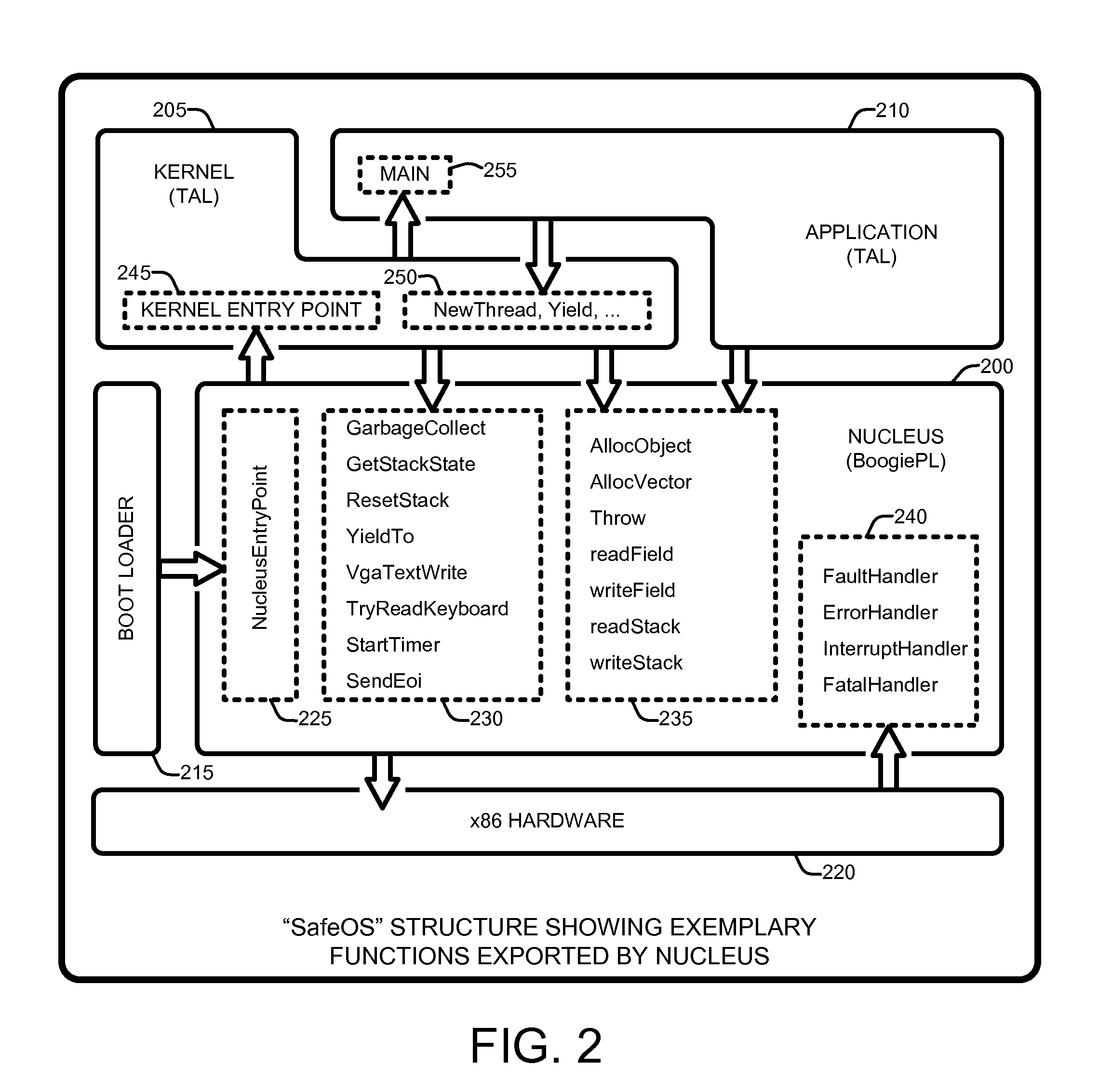
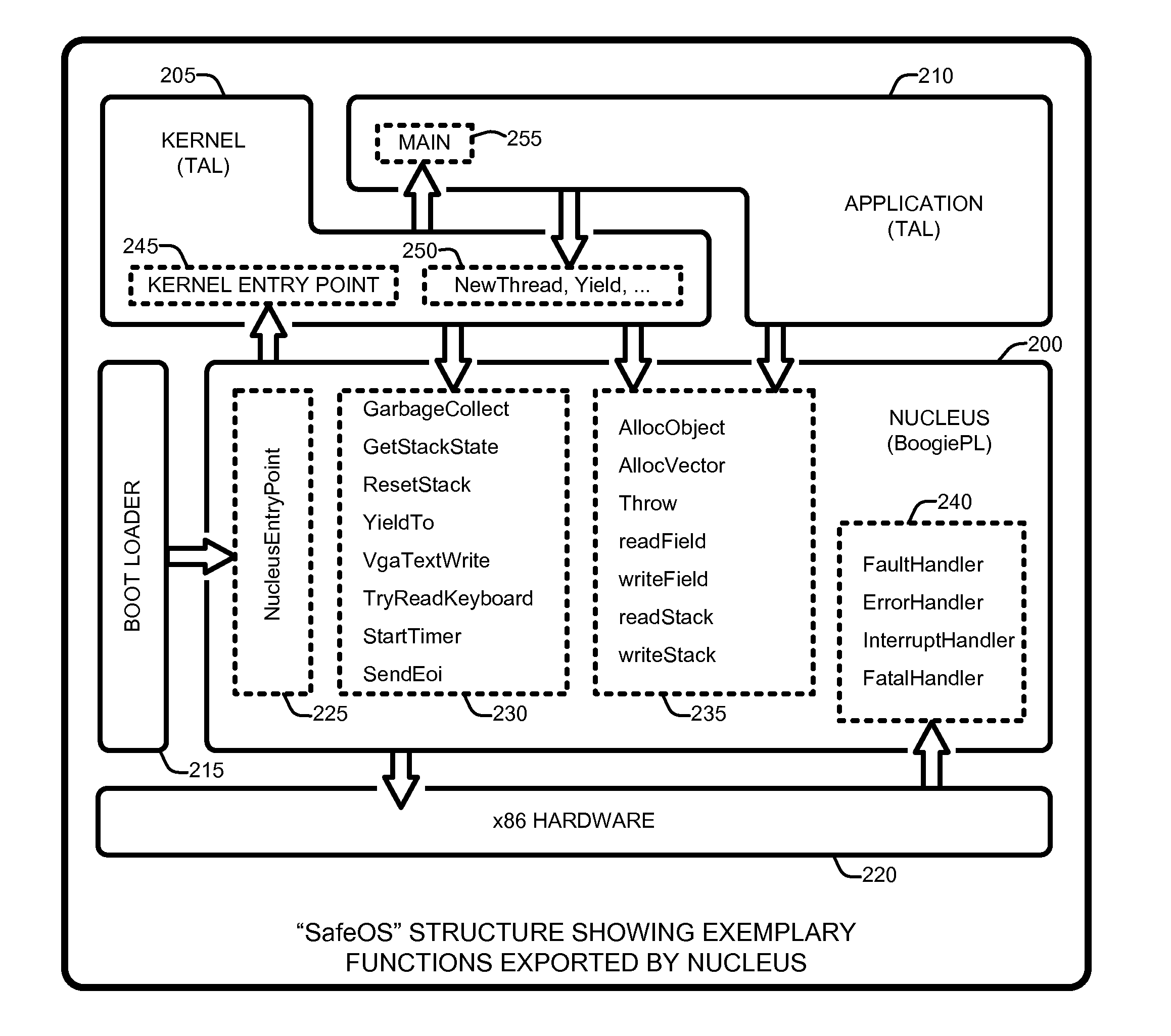
Automated verification of a type-safe operating system
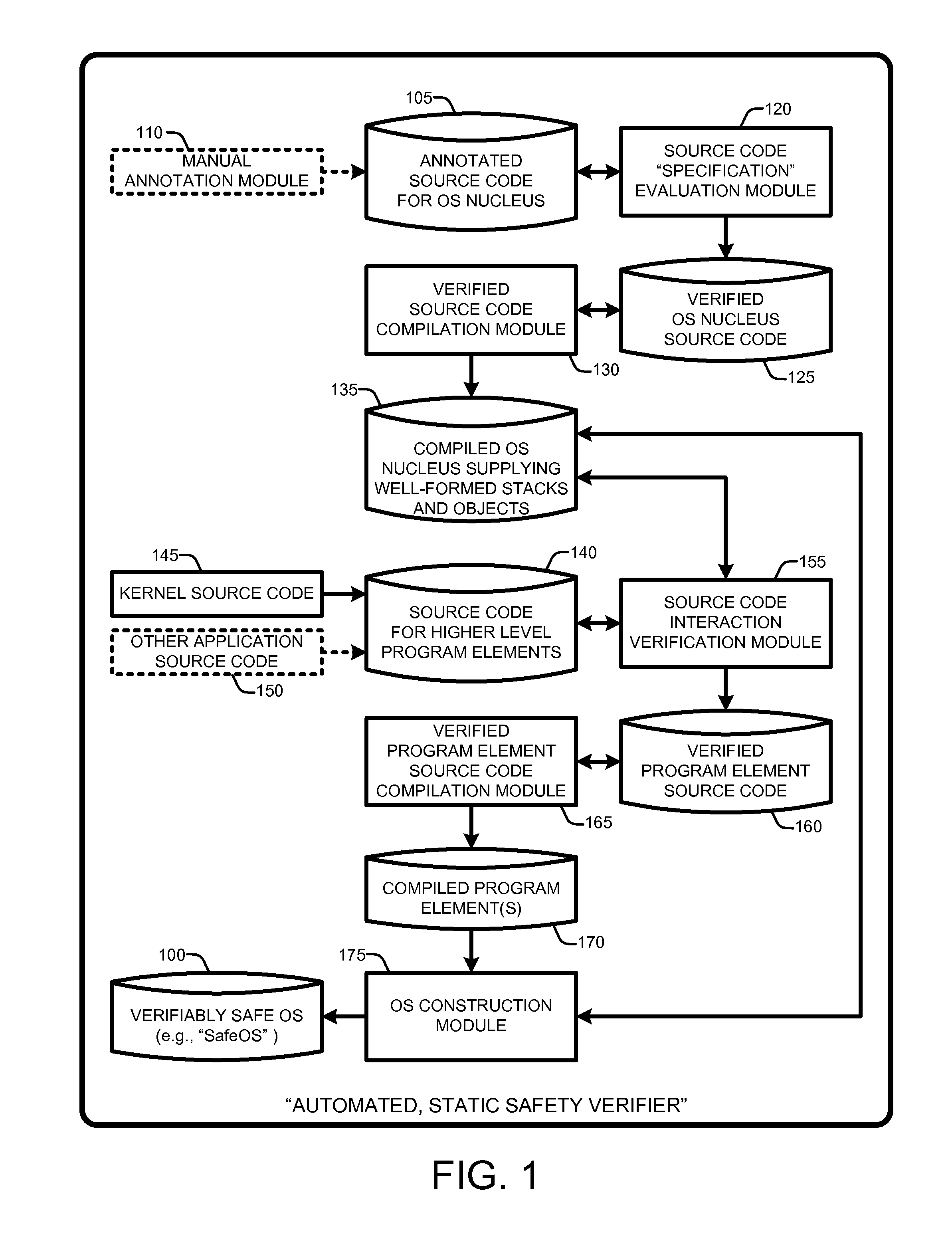
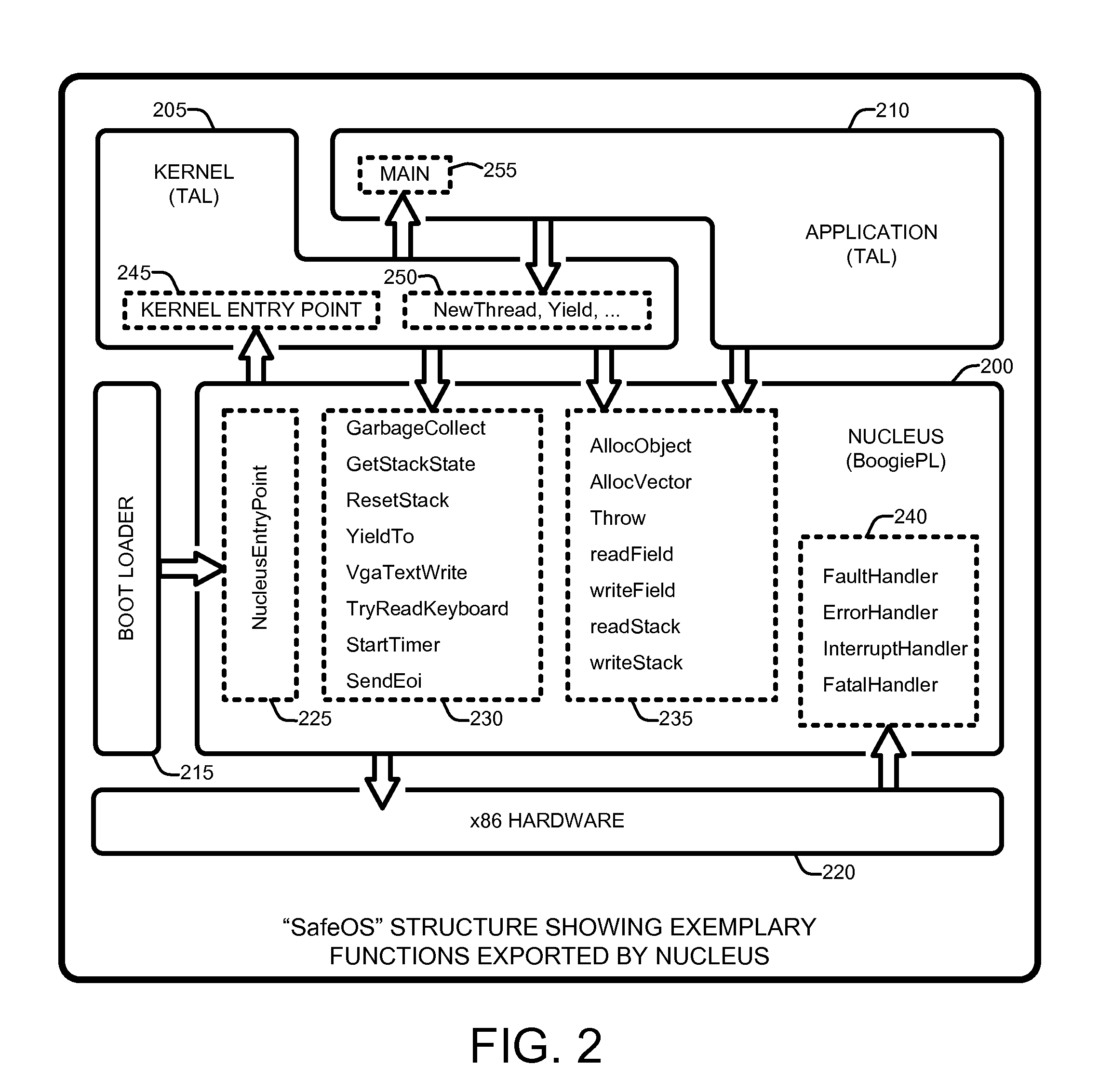
InactiveUS20100192130A1Verifies the safety of the kernel and applicationsSafety and correctness of the NucleusTransmissionSpecific program execution arrangementsOperational systemAutomated theorem provers
An “Automated, Static Safety Verifier” uses typed assembly language (TAL) and Hoare logic to achieve highly automated, static verification of type and memory safety of an operating system (OS). Various techniques and tools mechanically verify the safety of every assembly language instruction in the OS, run-time system, drivers, and applications, except the boot loader (which can be separately verified). The OS includes a “Nucleus” for accessing hardware and memory, a kernel that builds services running on the Nucleus, and applications that run on top of the kernel. The Nucleus, written in verified assembly language, implements allocation, garbage collection, multiple stacks, interrupt handling, and device access. The kernel, written in C# and compiled to TAL, builds higher-level services, such as preemptive threads, on top of the Nucleus. A Hoare-style verifier with automated theorem prover verifies safety and correctness of the Nucleus. A TAL checker verifies safety of the kernel and applications.
Owner:MICROSOFT TECH LICENSING LLC
Lithium ion secondary battery having shape memory safety vent
InactiveCN1747198AImprove securityAccurate operationFinal product manufactureCell lids/coversLithiumEngineering
A lithium ion secondary battery has a shape memory safety vent adapted to discharge internal compressed gas by temporarily being opened when the temperature reaches a predetermined level to avoid a swelling phenomenon of the battery and improve safety. The lithium ion secondary battery includes an electrode assembly having first and second electrode plates wound a number of times with a separator interposed between them; a can having an opening formed on a side thereof to contain the electrode assembly; and a cap plate adapted to cover the can and provided with a vent hole on a side thereof, to which a safety vent adapted to deform at a predetermined temperature and discharge gas from inside the can to the exterior is coupled.
Owner:SAMSUNG SDI CO LTD
Memory security device for flexible software environment
ActiveUS20050028004A1Cannot be hackedMemory loss protectionError detection/correctionTerm memoryMaster processor
A semiconductor integrated circuit includes a processor for executing application code from a memory and a verifier processor arranged to receive the application code via the same internal bus as the processor. The verifier processor performs a verification function to check that the application code is authentic. The verifier processor runs autonomously and cannot be spoofed as it receives the application code via the same internal bus as the main processor. An additional instruction monitor checks the code instructions from the CPU and also impairs the operation of the circuit unless the address of code requested is in a given range. The code is in the form of a linked list and the range is derived as a linked list table during a first check.
Owner:STMICROELECTRONICS (RES & DEV) LTD
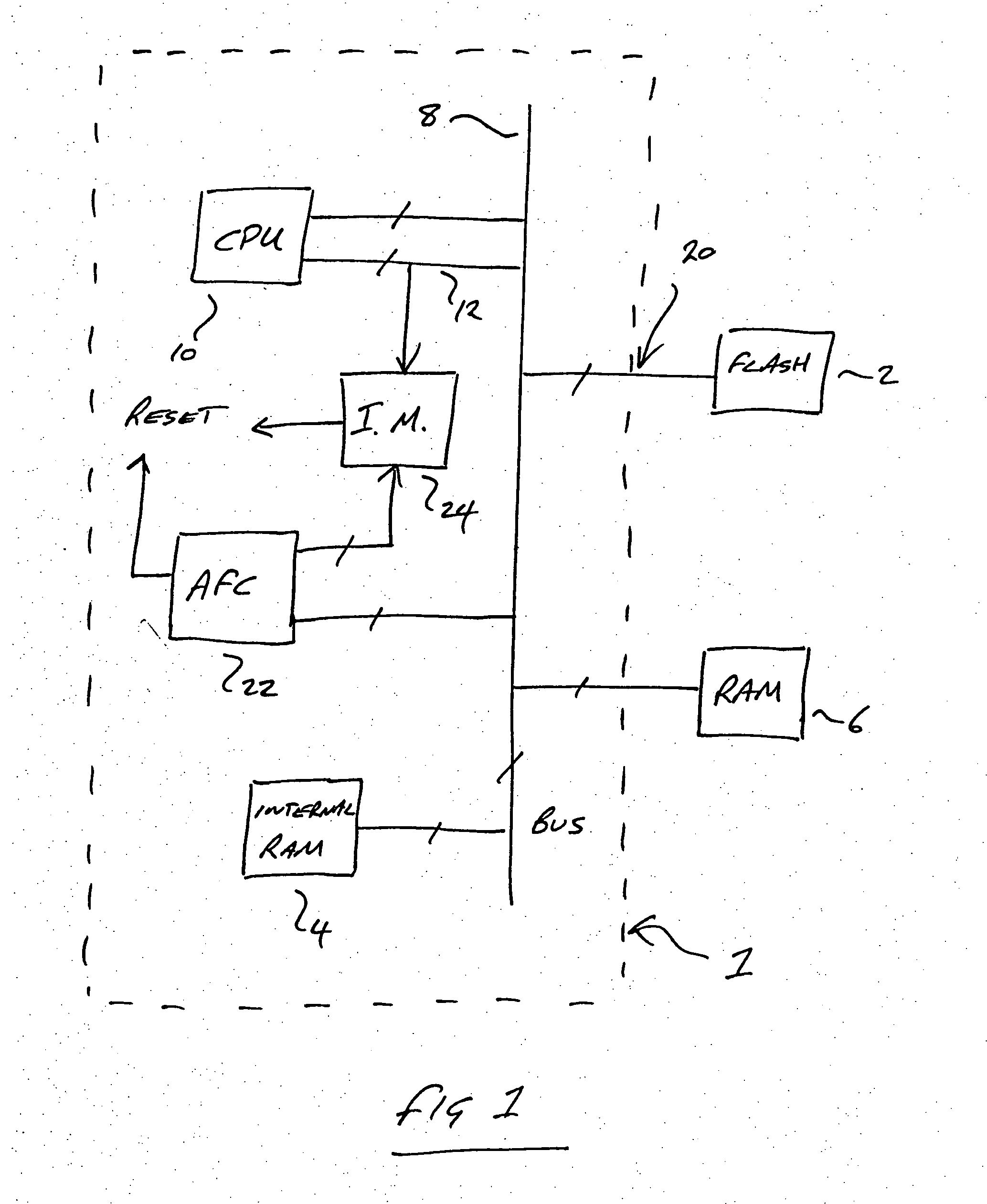
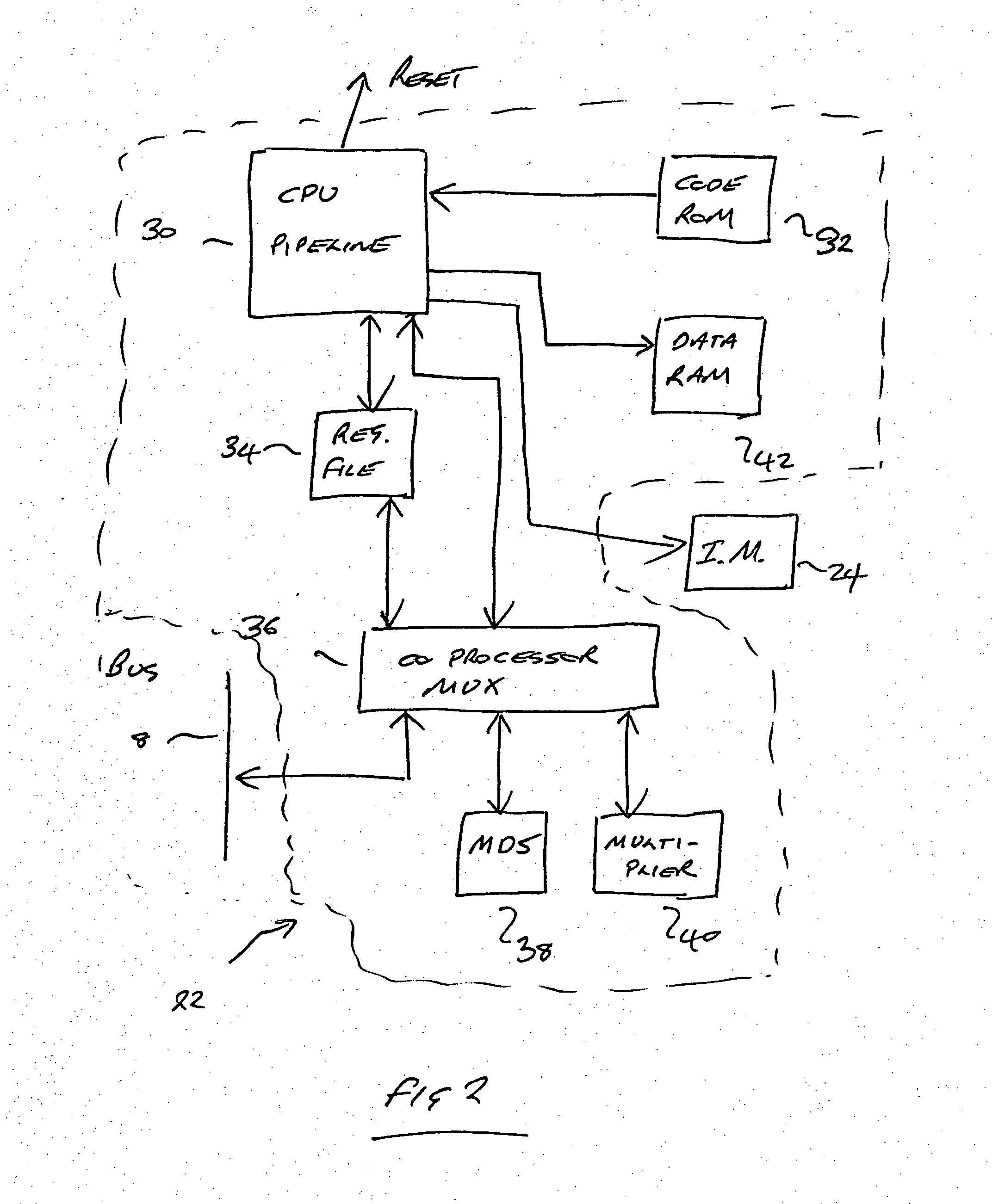
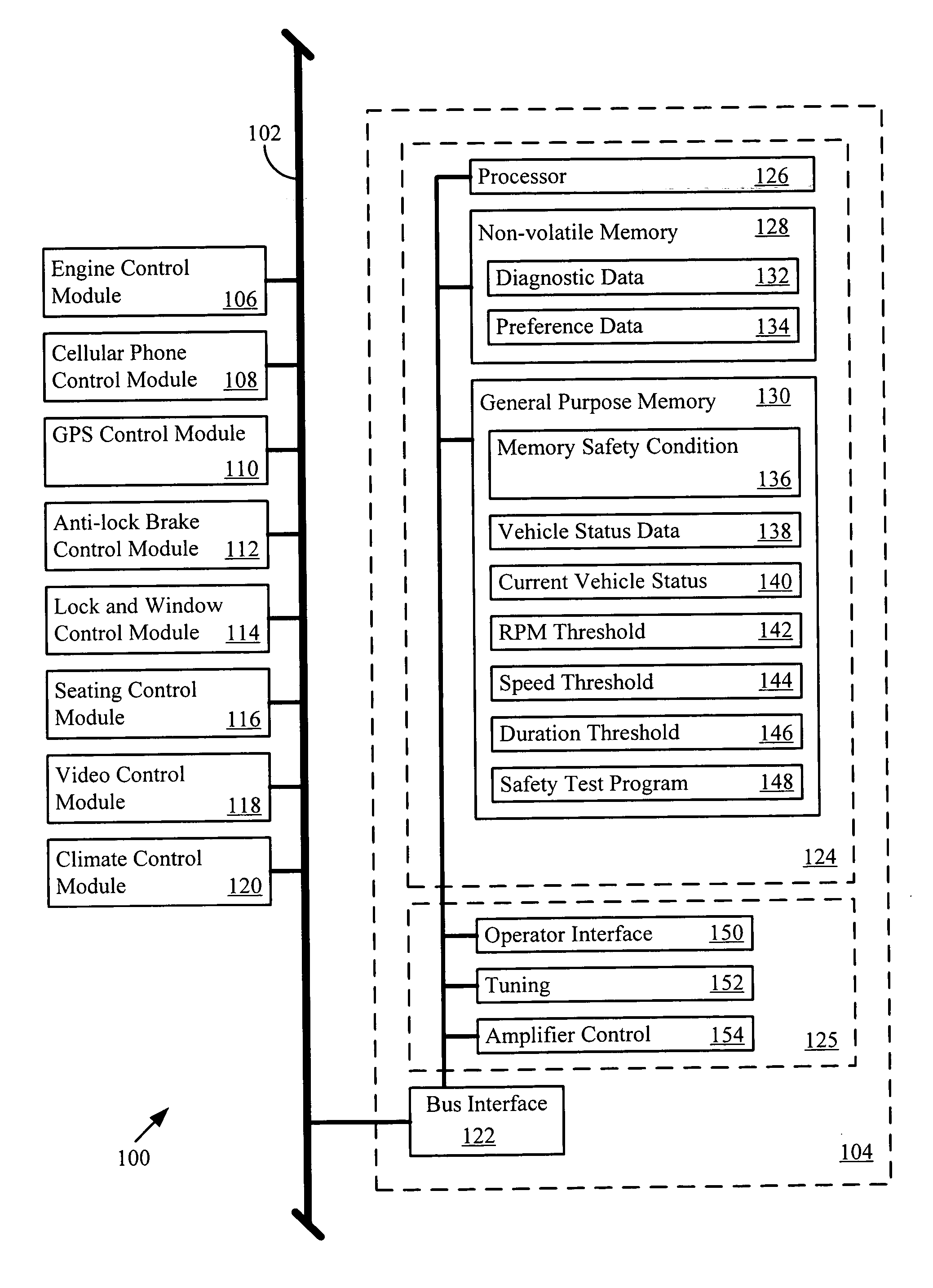
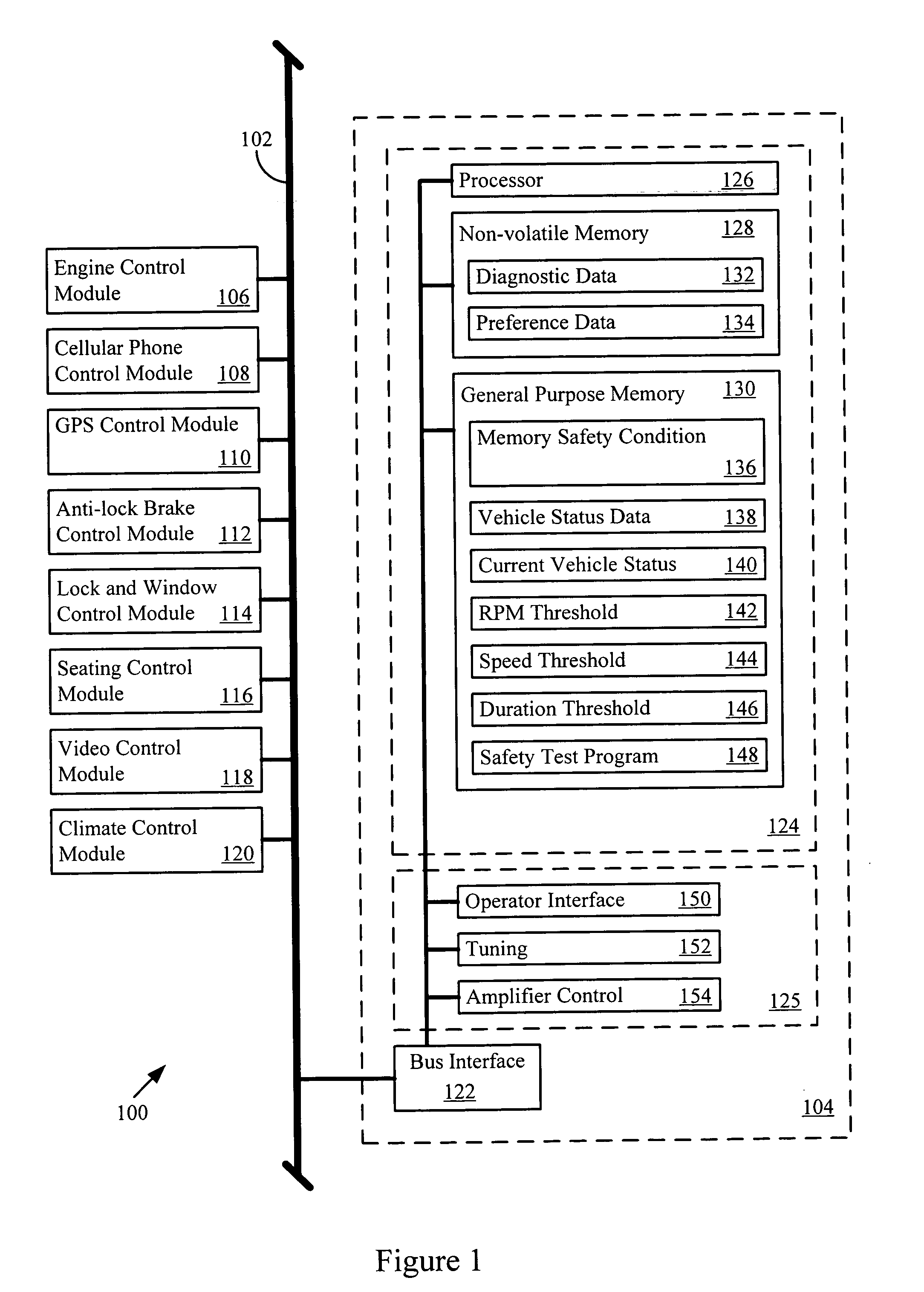
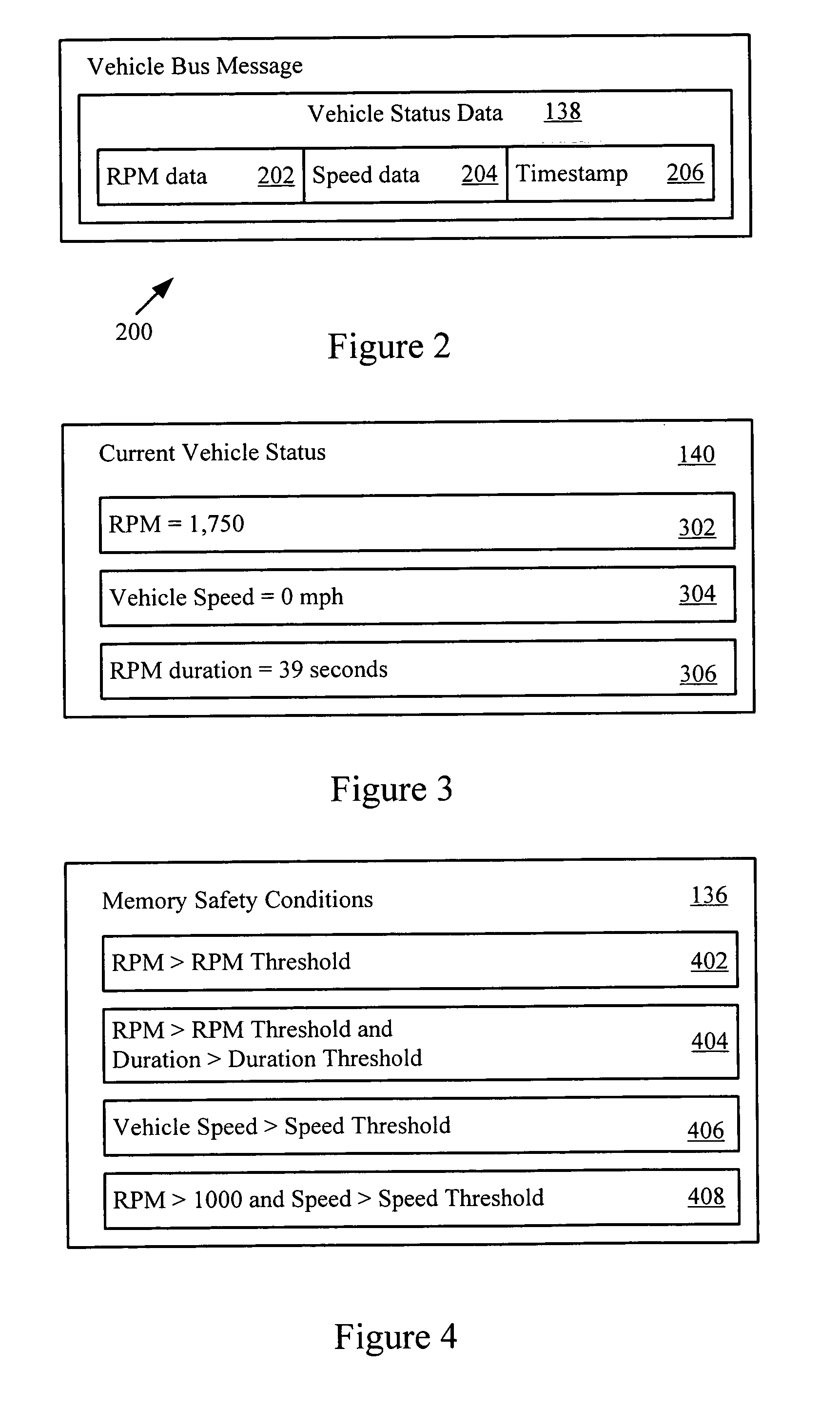
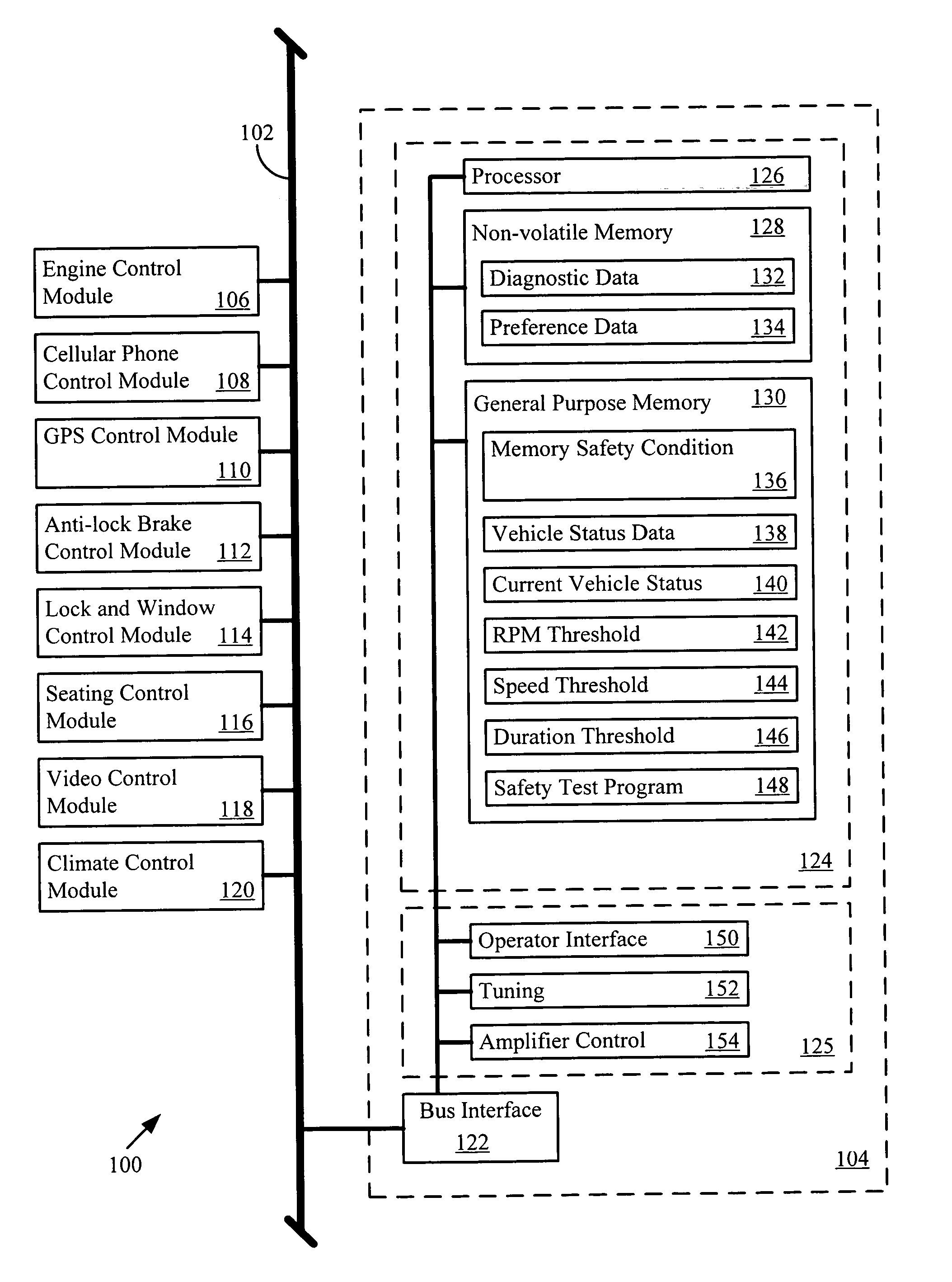
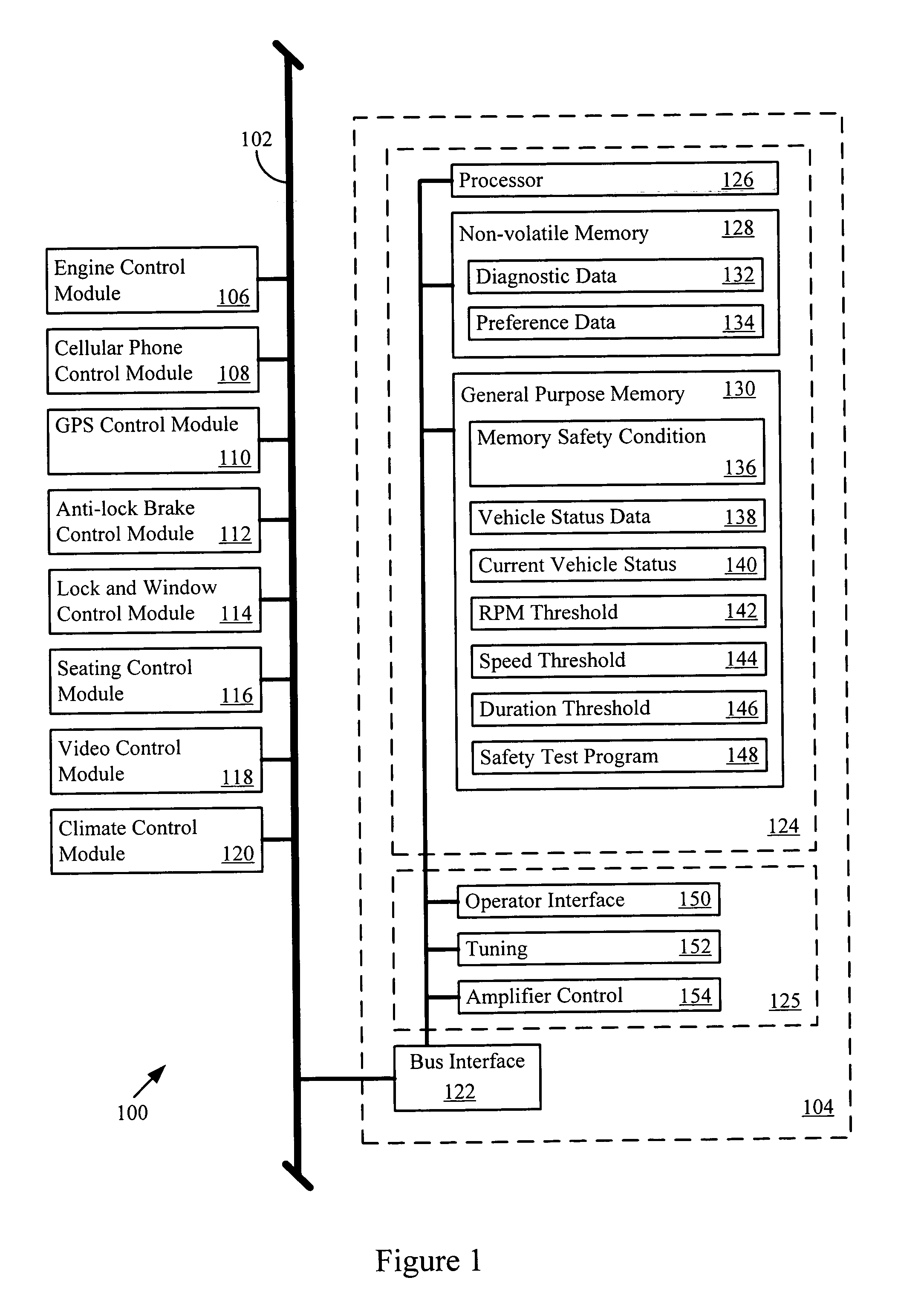
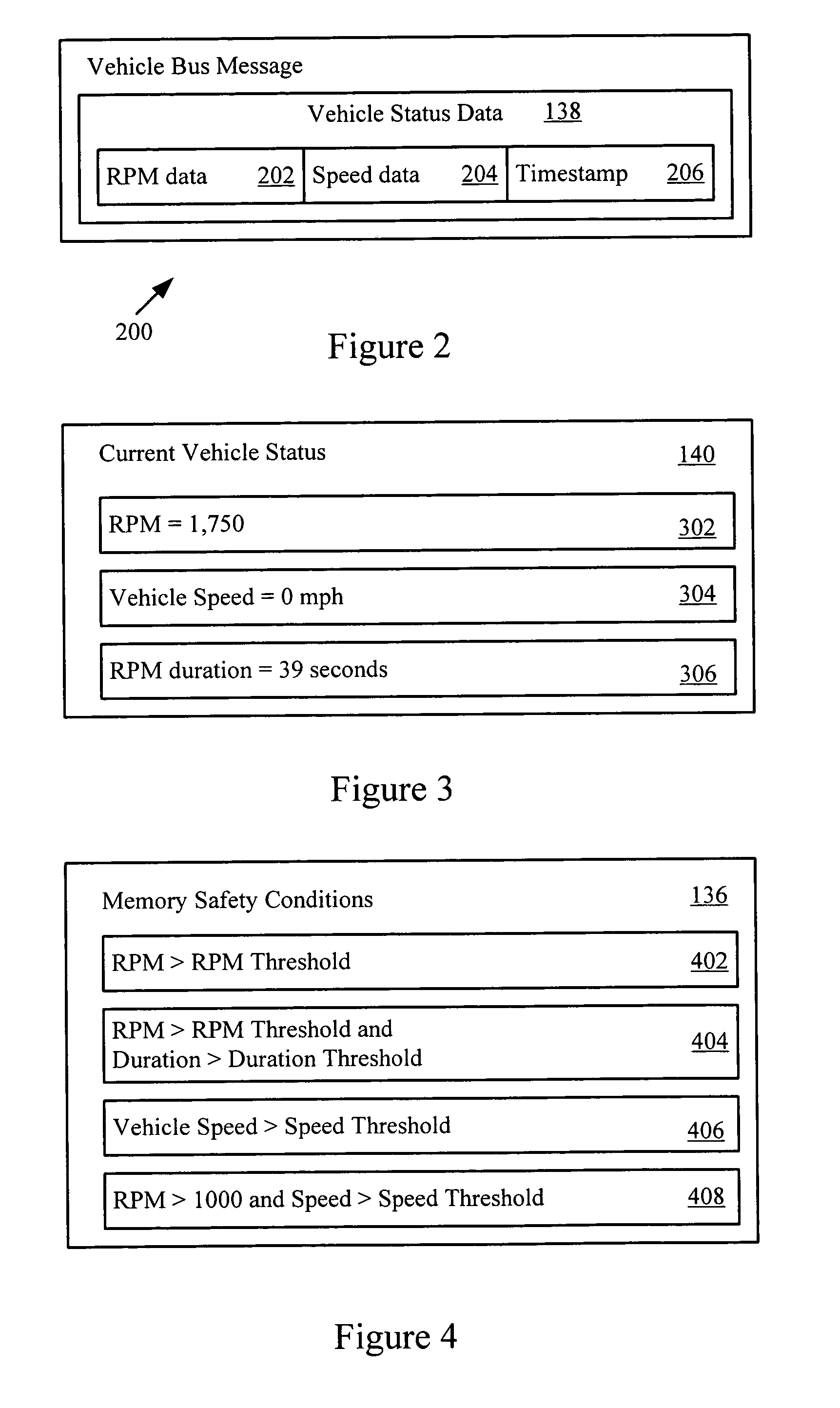
Informed memory access for vehicle electronic modules
ActiveUS20060041350A1Improve reliabilityVehicle testingRegistering/indicating working of vehiclesDiagnostic dataBus interface
A vehicle electronic module receives vehicle bus messages from a vehicle communication bus interface. The vehicle bus messages may include vehicle status data. The electronic module may determine whether a memory safety condition has been met based on the vehicle status data. The electronic module may delay reading or writing data, such as diagnostic data, into a non-volatile memory until the memory safety condition is reached. The data is read from or stored in the non-volatile memory with reduce risk of corrupted data.
Owner:HARMAN INT IND INC
Counter integrity tree for memory security
ActiveUS20190251275A1Increase in sizeInput/output to record carriersDigital data protectionComputer hardwareTerm memory
Owner:ARM LTD
Fault tolerant apparatus and method for elliptic curve cryptography
InactiveUS20150092941A1Public key for secure communicationUnauthorized memory use protectionData treatmentComputer science
A fault tolerant apparatus and method for elliptic curve cryptography. For example, one embodiment of a processor includes one or more cores to execute instructions and process data; and fault attack logic to ensure that the execution of the instructions and processing of the data is not vulnerable to memory safe-error attacks after a fault is injected by hiding any correlation between processor behavior and secret bits in a secret key.
Owner:INTEL CORP
Object-based programming method and object-based programming system in C language programming
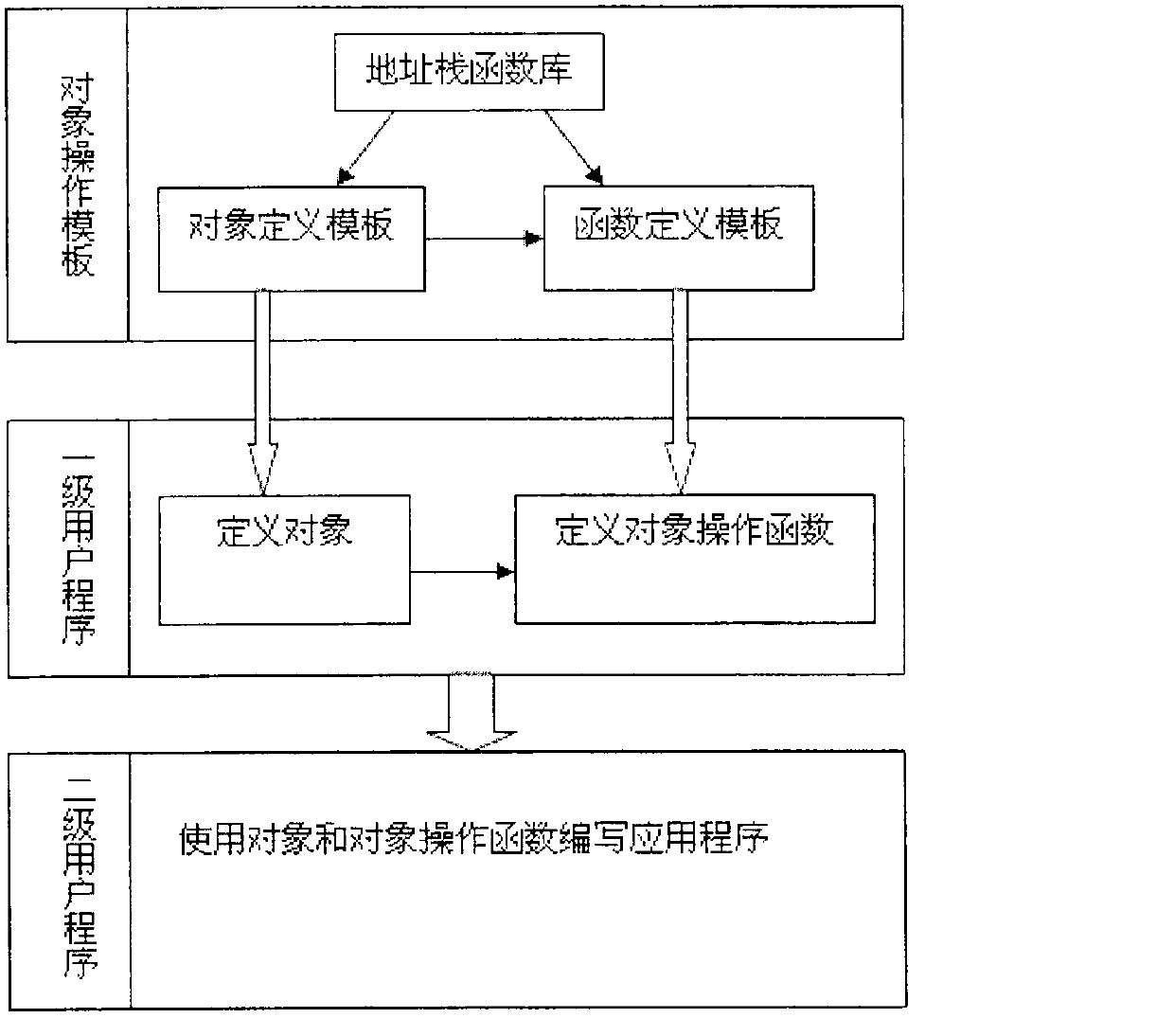
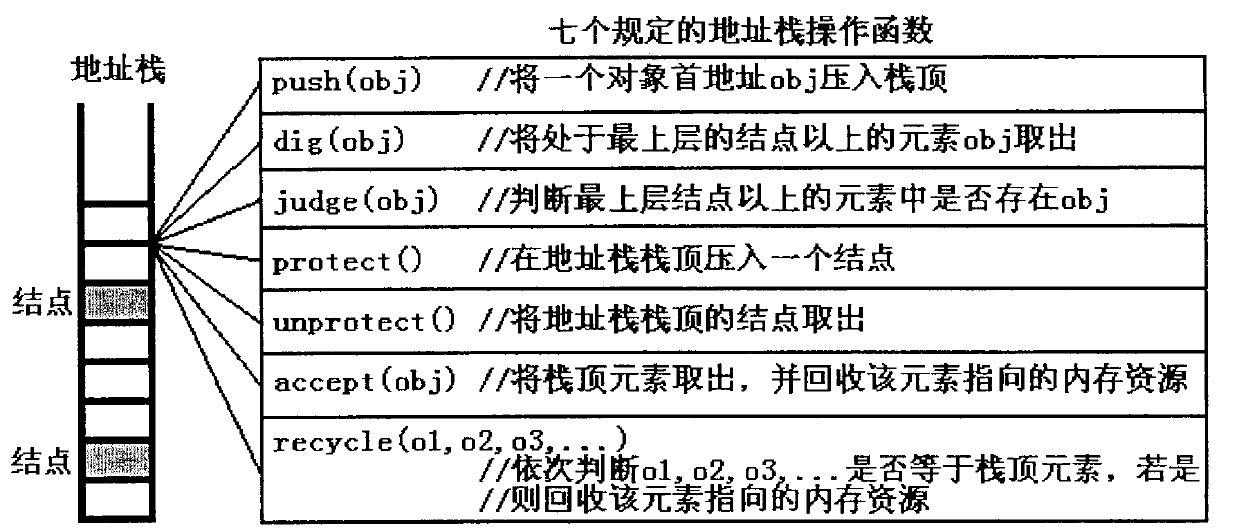
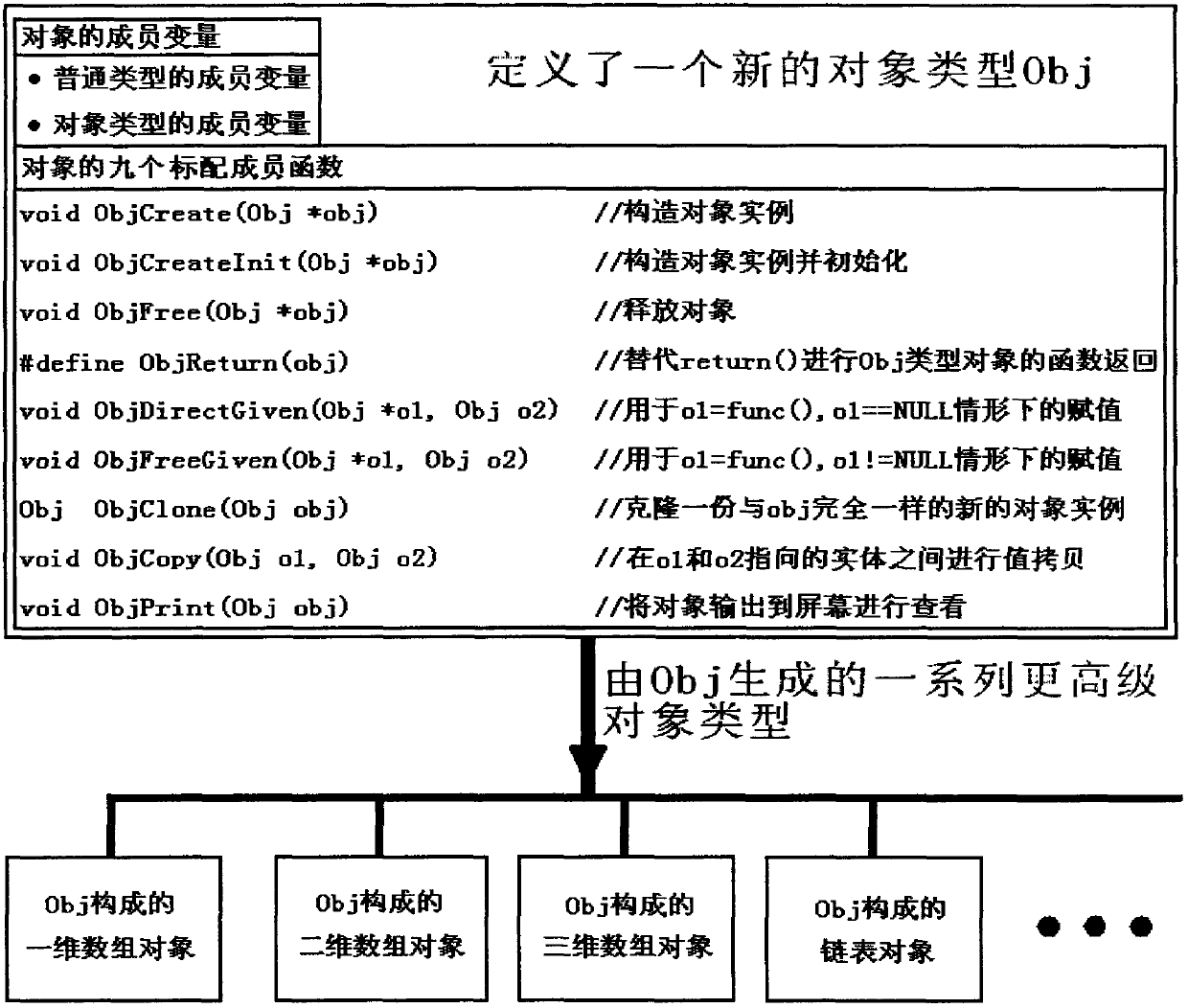
Certain currently popular programming languages (such as C++) are highly efficient but can easily bring about memory errors, and certain currently popular programming languages (such as Java) are safe in memories but lower in efficiency. The invention discloses an object-based programming method and an object-based programming system in C language programming, and the system is a convenient, safe and high-efficiency programming framework. The system utilizes the stack technique to efficiently judge the attribute of an 'object' (i.e. a non-generic type variable), also standardizes assignment and other operations on the object, and can release object resources and optimize the efficiency of object usage (or the efficiency of parameter transfer) simultaneously. The system provides defining templates for objects and object-operating functions, so that programmers can conveniently define the objects and the object-operating functions, the objects and functions defined by the defining templates can be conveniently subjected to recursionrecur and can be conveniently nested, invoked and operated in any other complex ways like generic type variables and functions, and the problems of memory safety and efficiency are automatically processed by the templates.
Owner:INST OF FLUID PHYSICS CHINA ACAD OF ENG PHYSICS
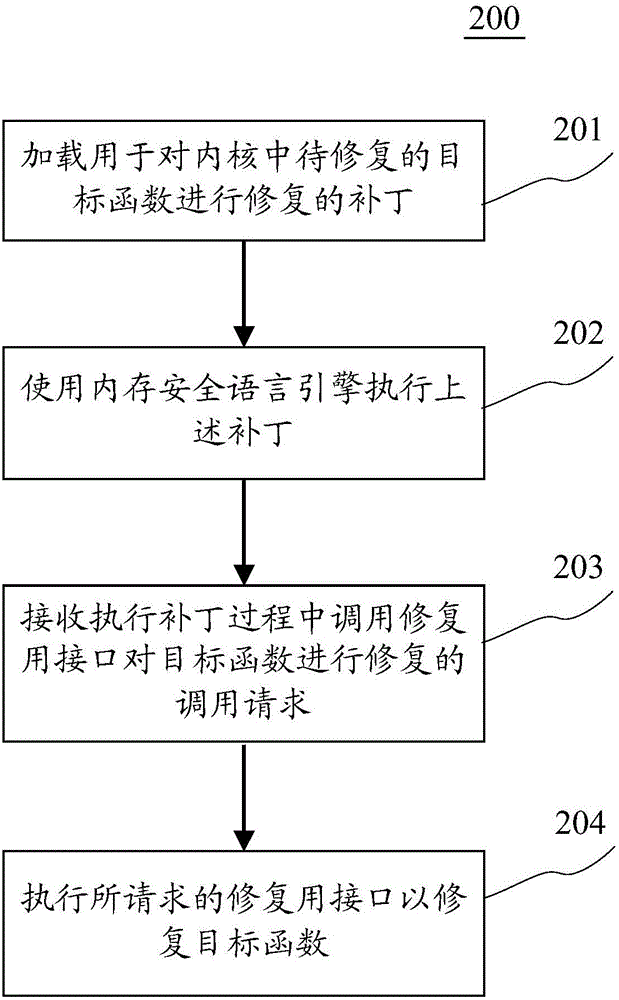
Kernel fixing method and apparatus
ActiveCN106055979ARestrict permissionsPrevent arbitrary tamperingSoftware engineeringPlatform integrity maintainanceObject functionMemory safety
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
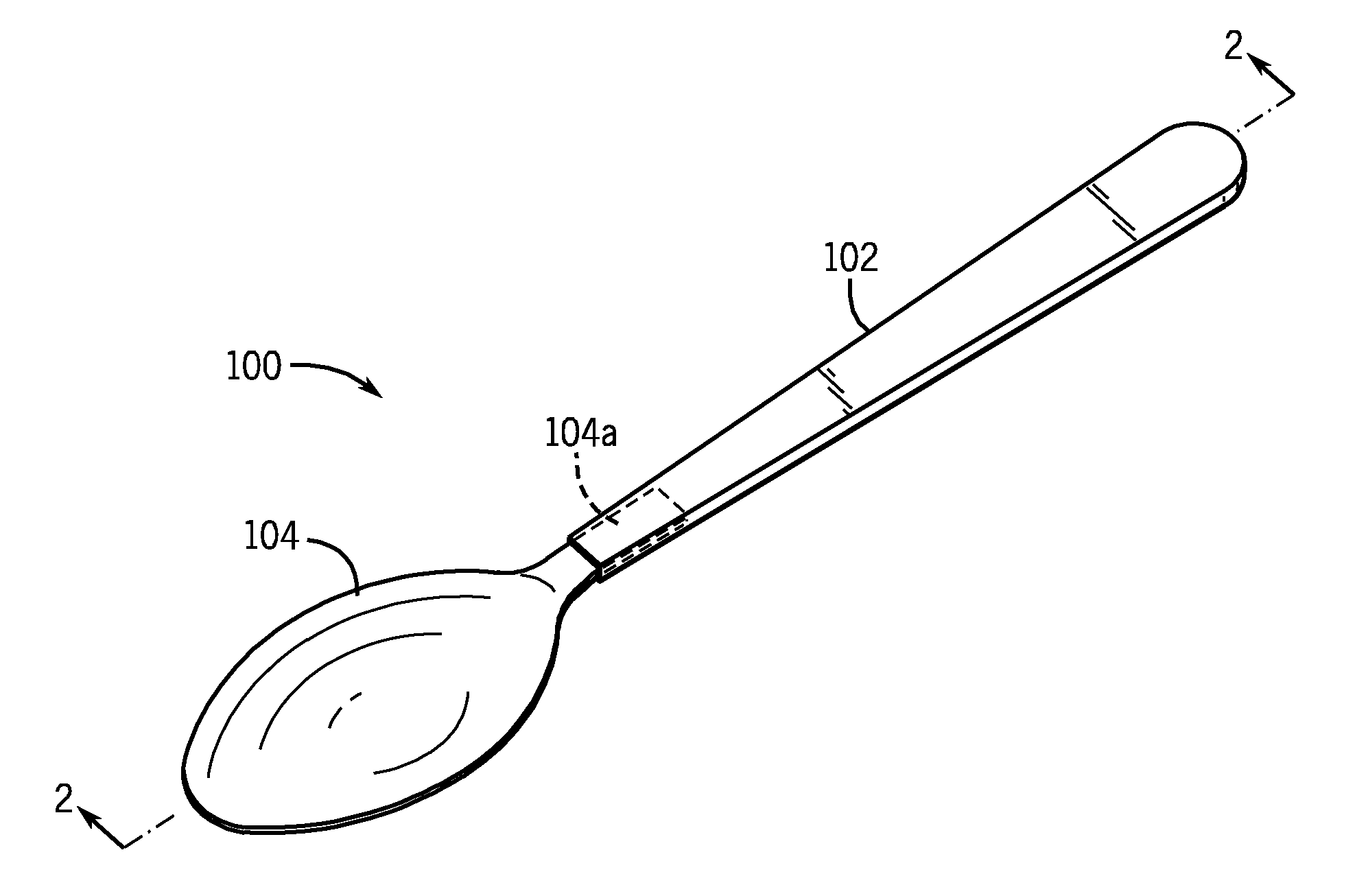
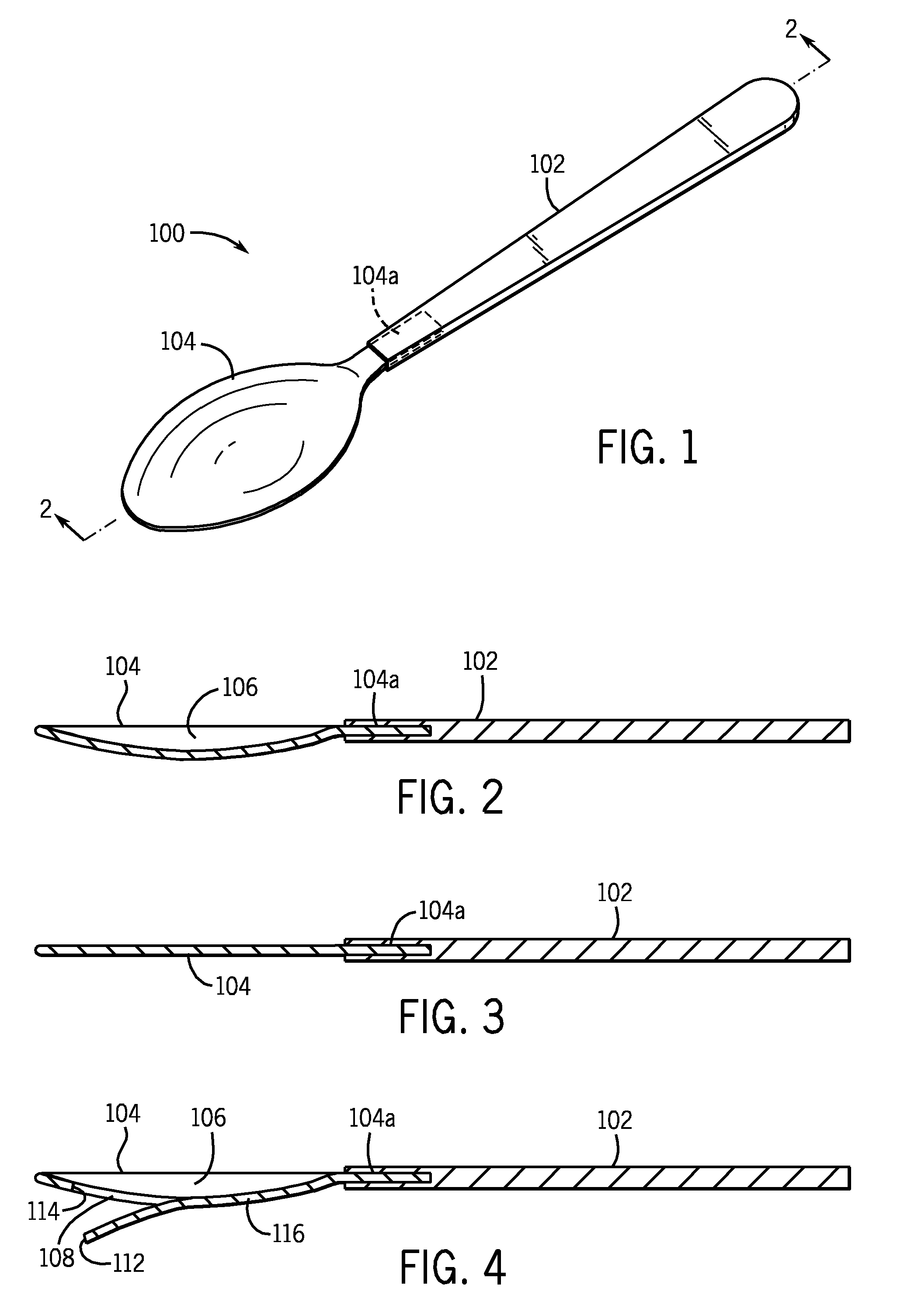
Shape Memory Safety Utensil
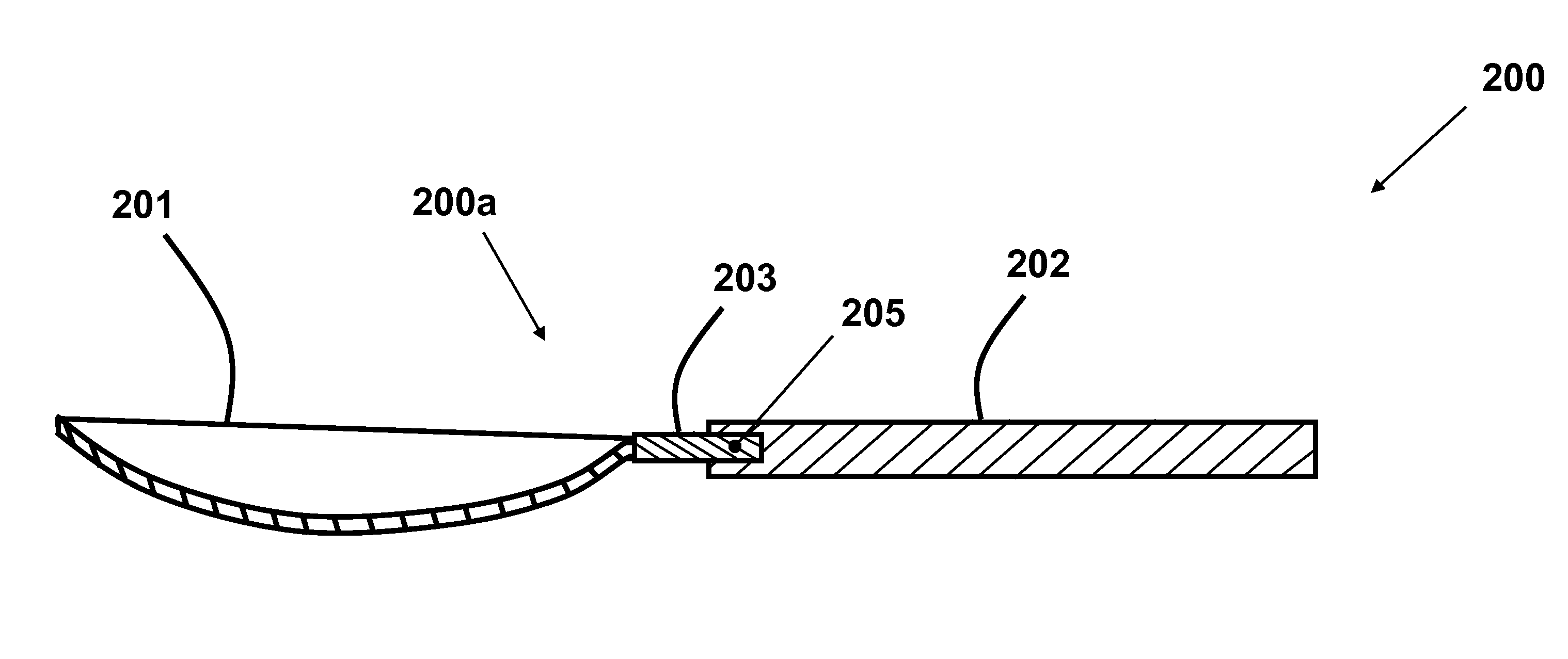
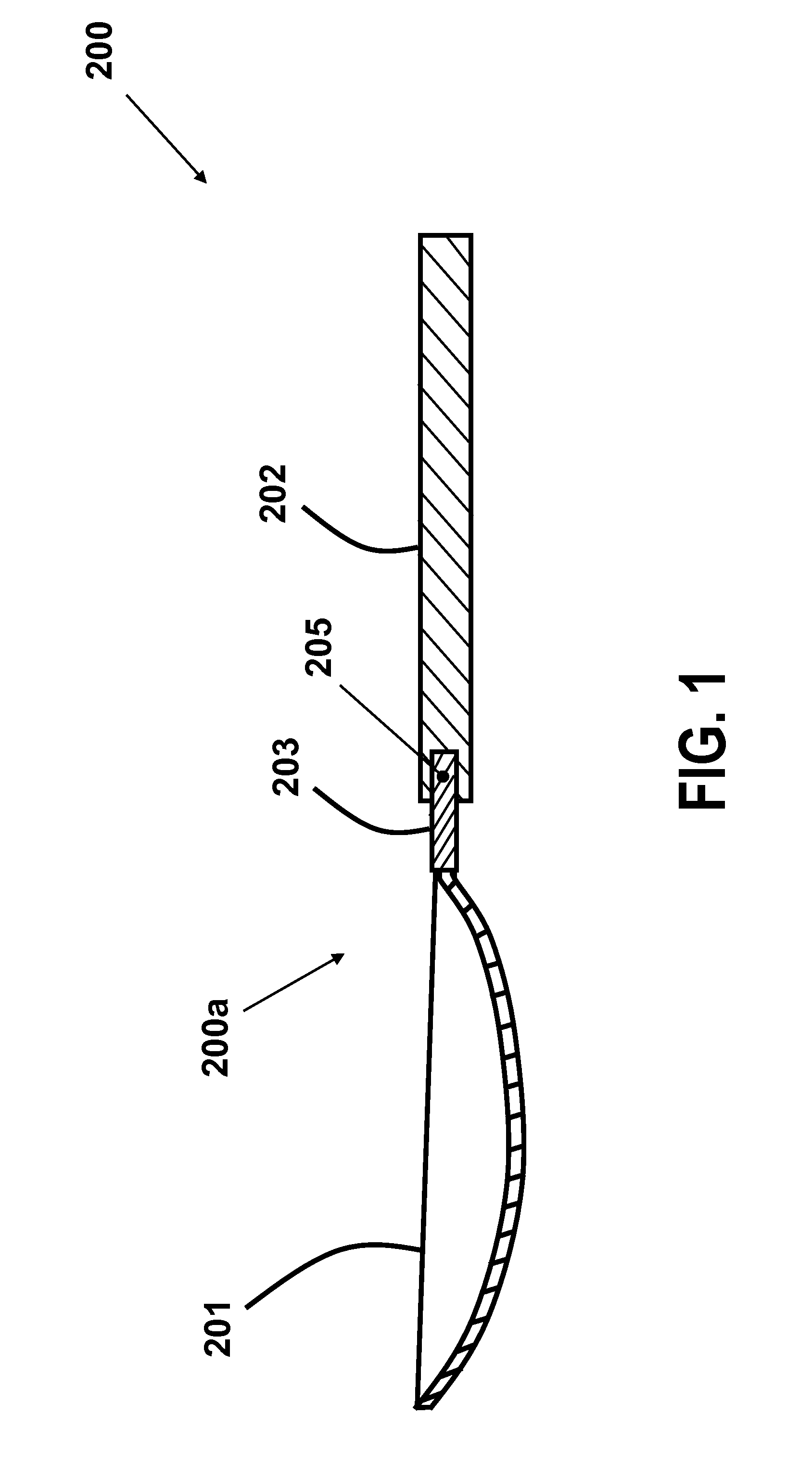
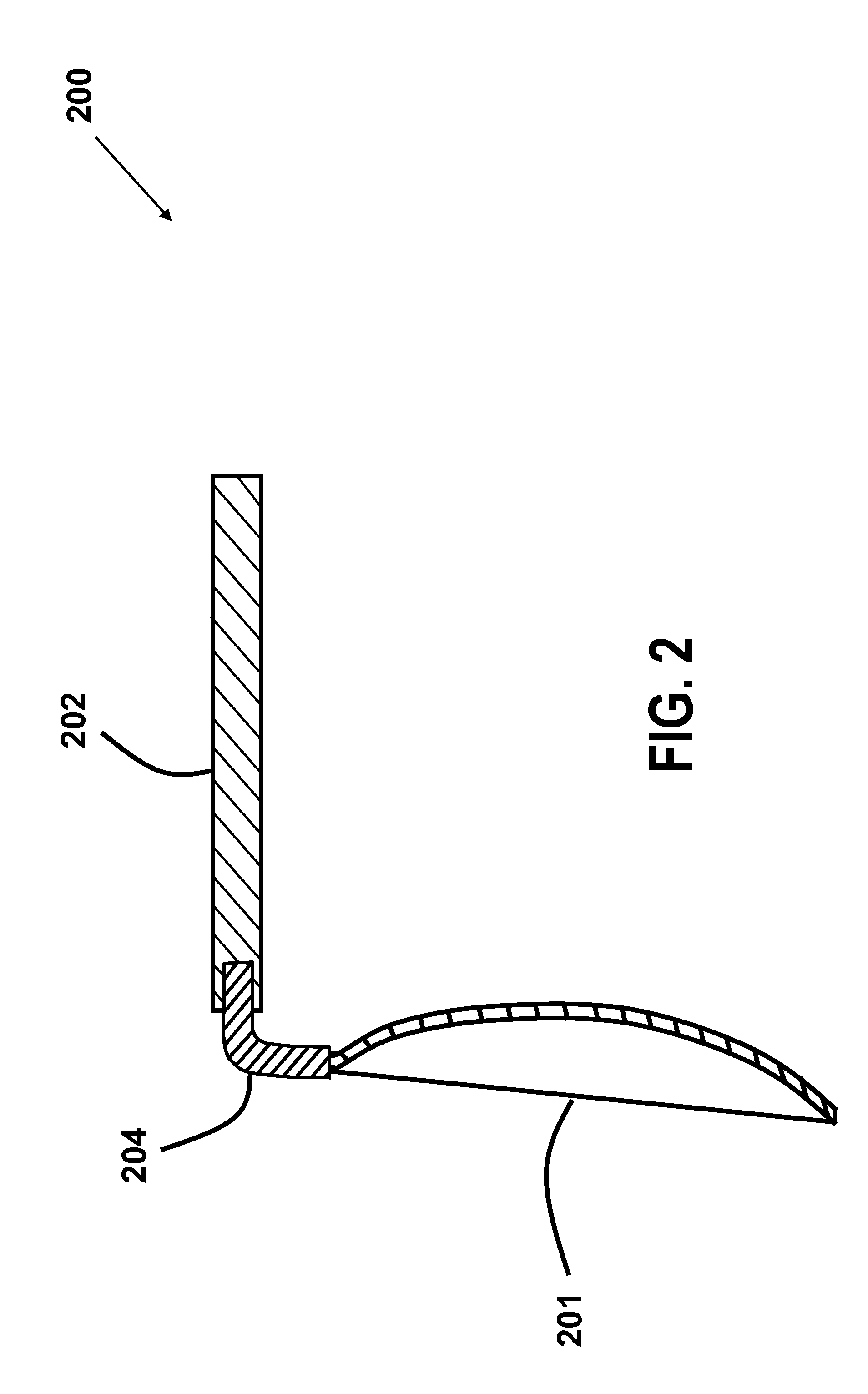
InactiveUS20160095455A1Simple and inexpensive configurationPortable power-driven toolsMetal working apparatusShape-memory alloyEngineering
A method for preventing holding of one or more of a hot liquid or hot food in a utensil. The method including: configuring a utensil portion for holding one or more of a liquid or food to have a first orientation relative to a handle portion when a temperature of a shape memory alloy neck portion connecting the utensil portion to the handle portion is below a transition temperature and changing the orientation of the utensil portion relative to the handle portion to a second orientation when the temperature of the shape memory alloy neck portion is greater than the transition temperature so as to not hold the liquid or food.
Owner:OMNITEK PARTNERS LLC
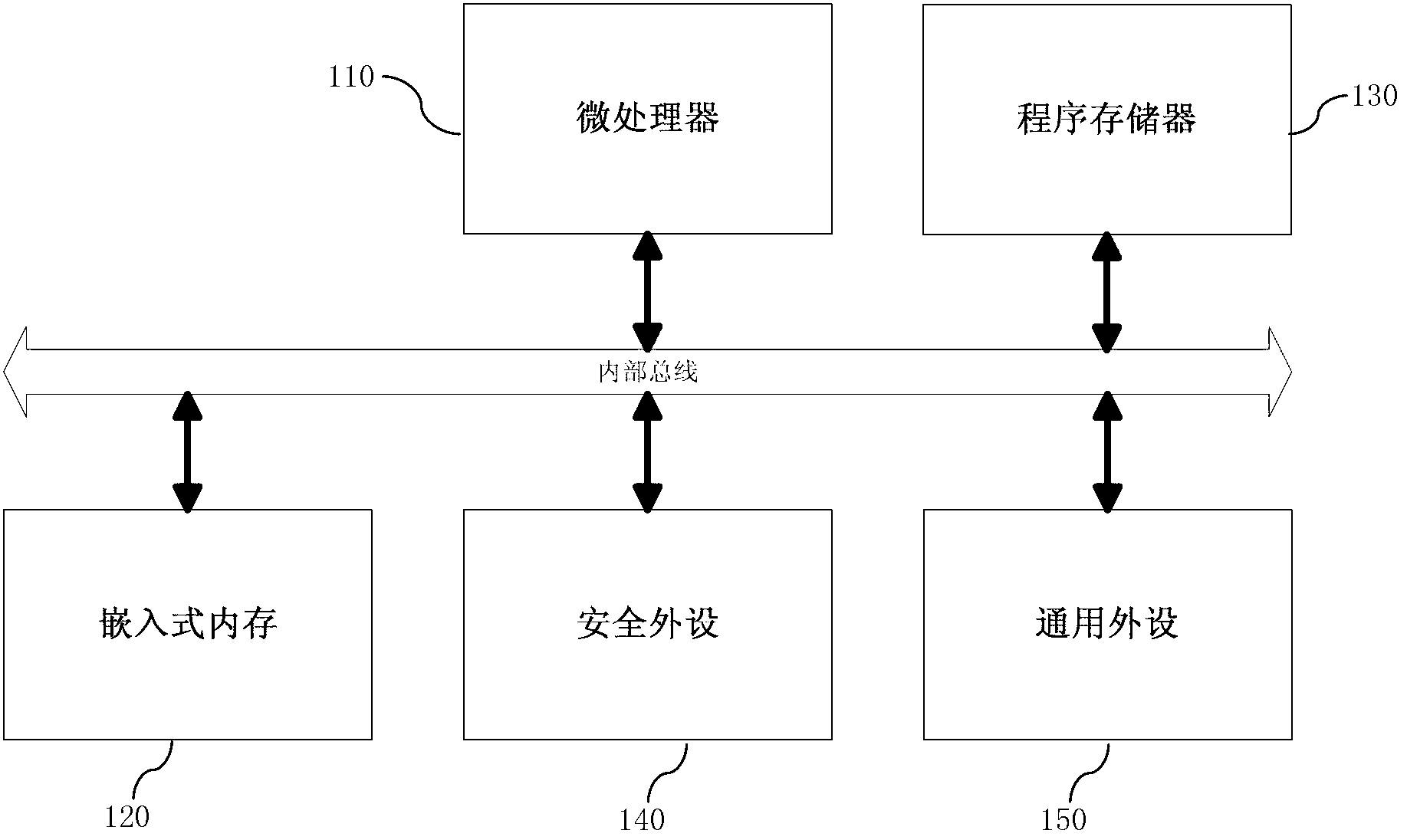
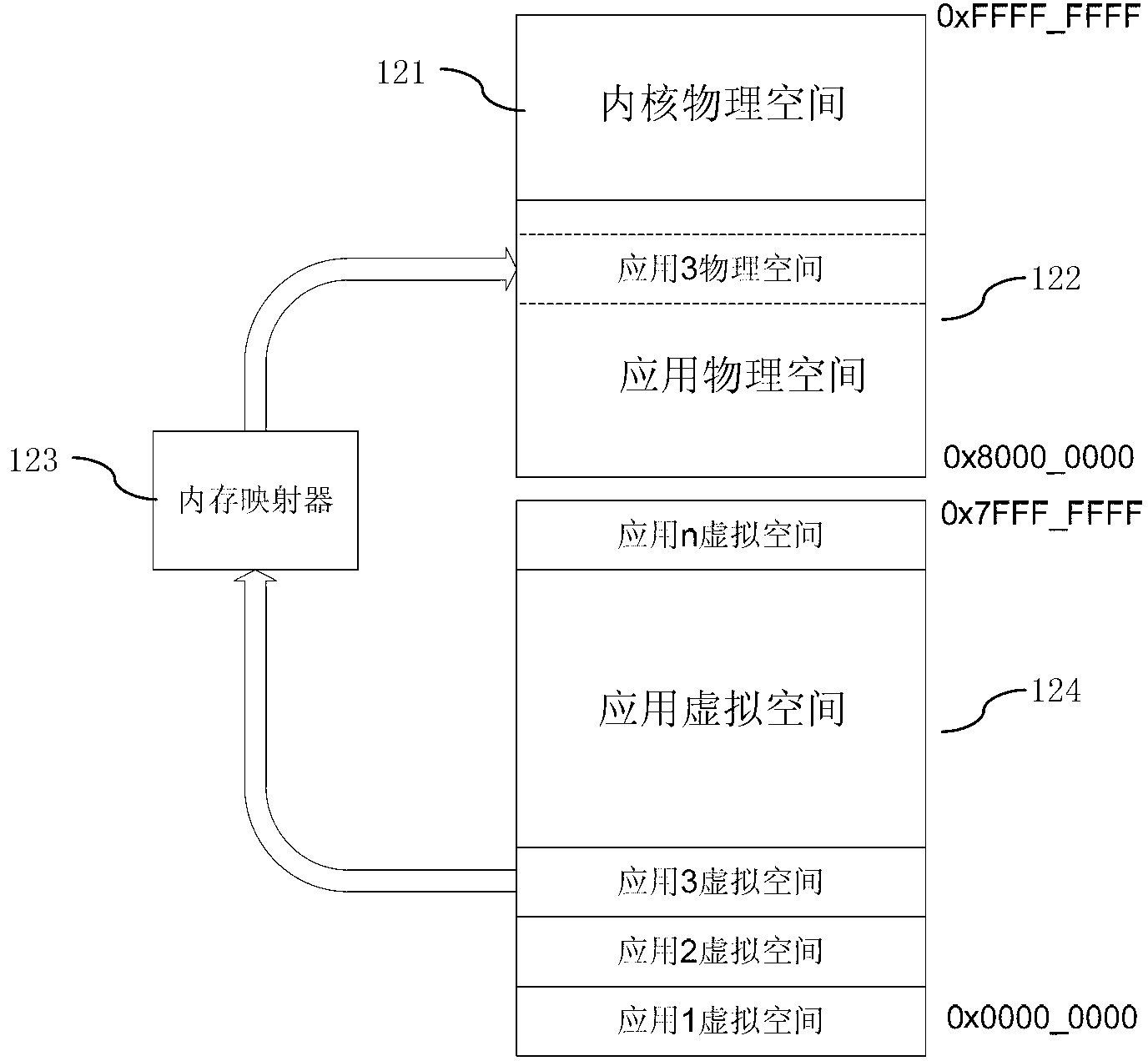
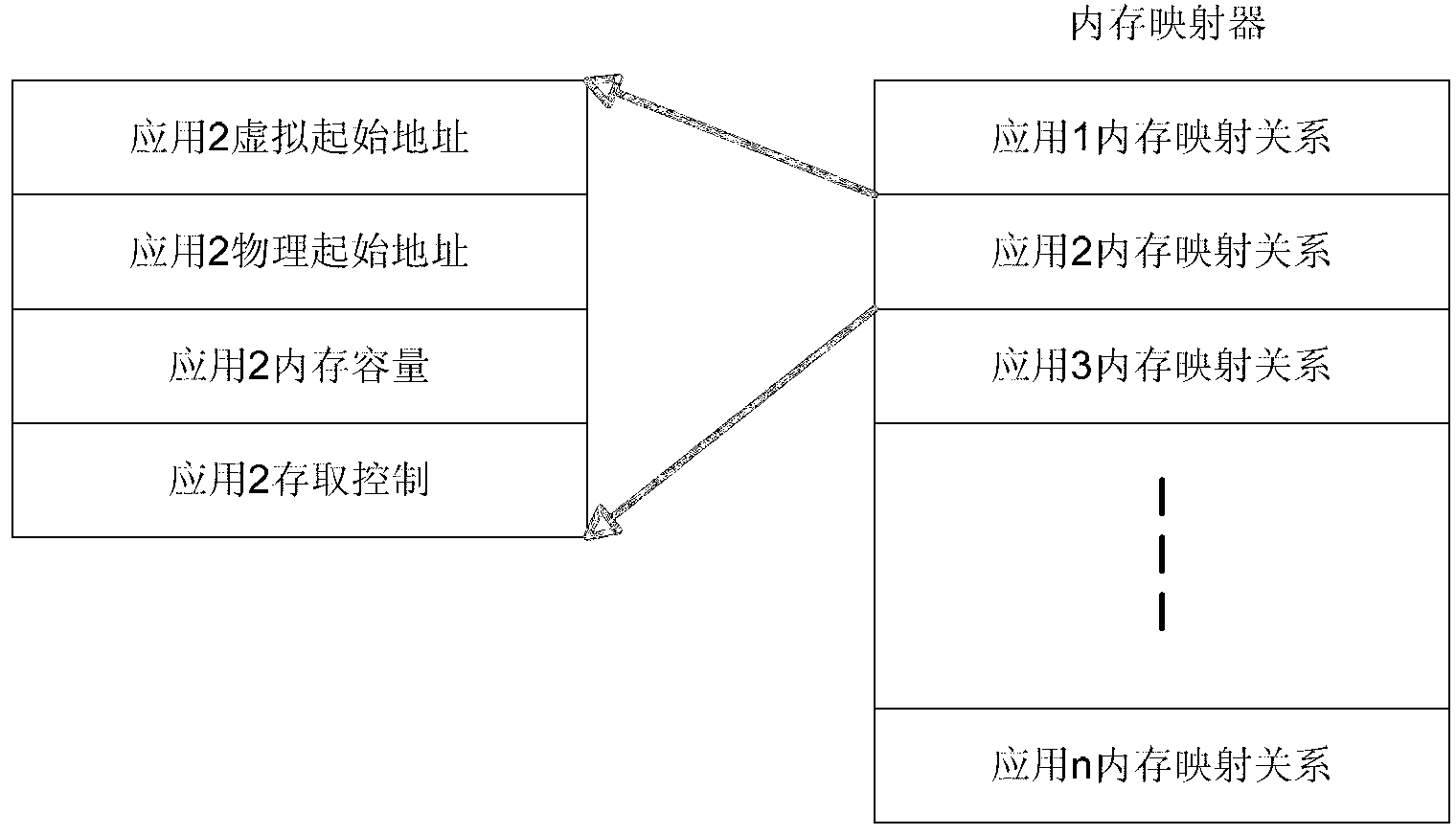
Embedded system and safety managing method for internal storage thereof
ActiveCN103309819AAvoid visitingPrivacy protectionMemory adressing/allocation/relocationUnauthorized memory use protectionVirtual memoryApplied physics
The invention discloses an embedded system and a safety managing method for internal storage thereof. The internal storage comprises a kernel physics space, an applied physics space, an applied virtual space mapped with the applied physics space, and a memory mapper. As for an application not configured in the memory mapper, an kernel program configures a mapping relation parameter in the memory mapper for the application, the mapping relation parameter comprises an application ID, an access authority, and an applied virtual space and an applied physics space assigned to the application; as for an application configured in the memory mapper, the application can visit an applied virtual space and an applied physics space assigned to the application through the kernel program and the memory mapper; and therefore, each application can visit an applied virtual space assigned to the application to prevent data of applications from being visited by an unauthorized person, so as to protect the privacy of each application.
Owner:BRITE SEMICON SHANGHAI CORP
Automated verification of a type-safe operating system
InactiveUS8341602B2Verifies the safety of the kernel and applicationsSafety and correctness of the NucleusTransmissionSpecific program execution arrangementsOperational systemAutomated theorem provers
An “Automated, Static Safety Verifier” uses typed assembly language (TAL) and Hoare logic to achieve highly automated, static verification of type and memory safety of an operating system (OS). Various techniques and tools mechanically verify the safety of every assembly language instruction in the OS, run-time system, drivers, and applications, except the boot loader (which can be separately verified). The OS includes a “Nucleus” for accessing hardware and memory, a kernel that builds services running on the Nucleus, and applications that run on top of the kernel. The Nucleus, written in verified assembly language, implements allocation, garbage collection, multiple stacks, interrupt handling, and device access. The kernel, written in C# and compiled to TAL, builds higher-level services, such as preemptive threads, on top of the Nucleus. A Hoare-style verifier with automated theorem prover verifies safety and correctness of the Nucleus. A TAL checker verifies safety of the kernel and applications.
Owner:MICROSOFT TECH LICENSING LLC
Memory security device for flexible software environment
ActiveUS7624442B2Cannot be hackedMemory loss protectionError detection/correctionApplication softwareMaster processor
Owner:STMICROELECTRONICS (RES & DEV) LTD
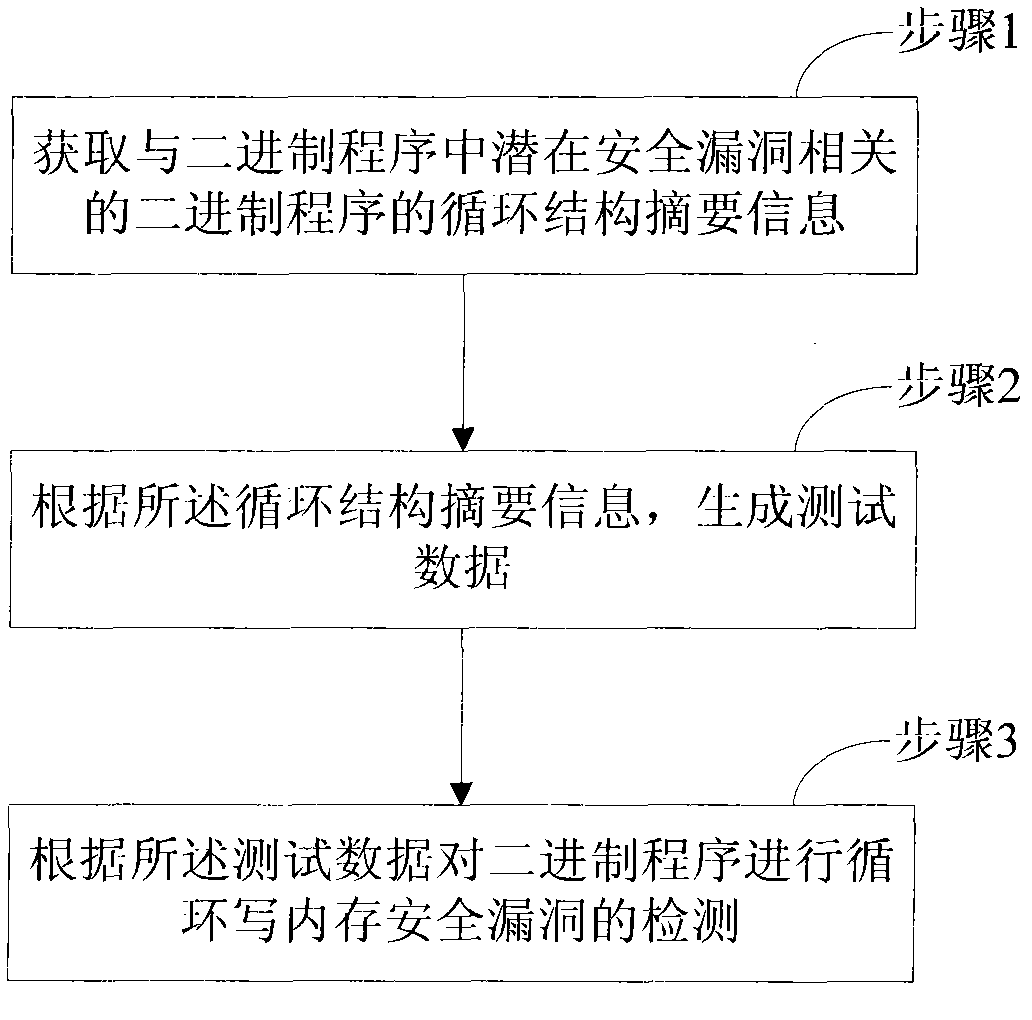
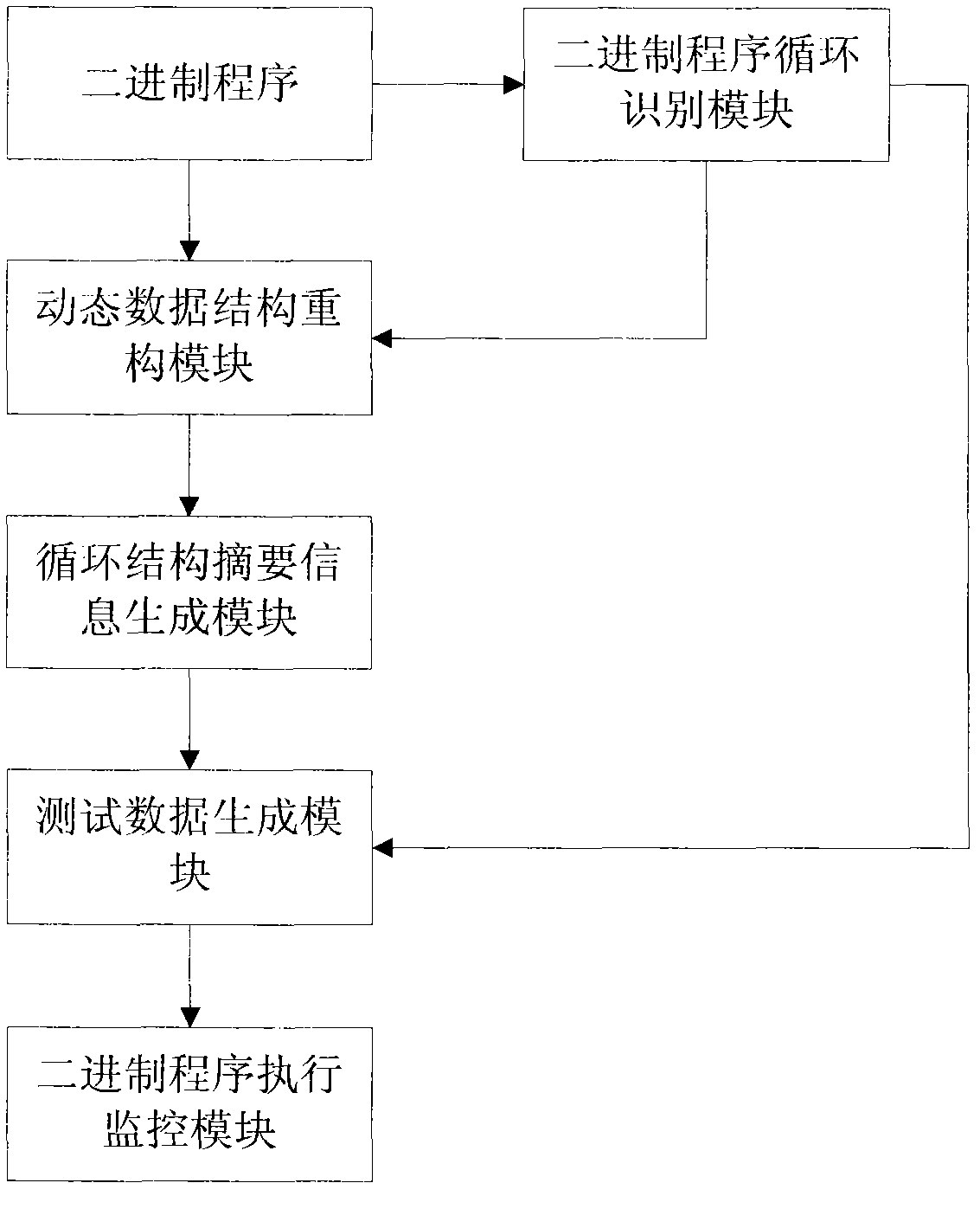
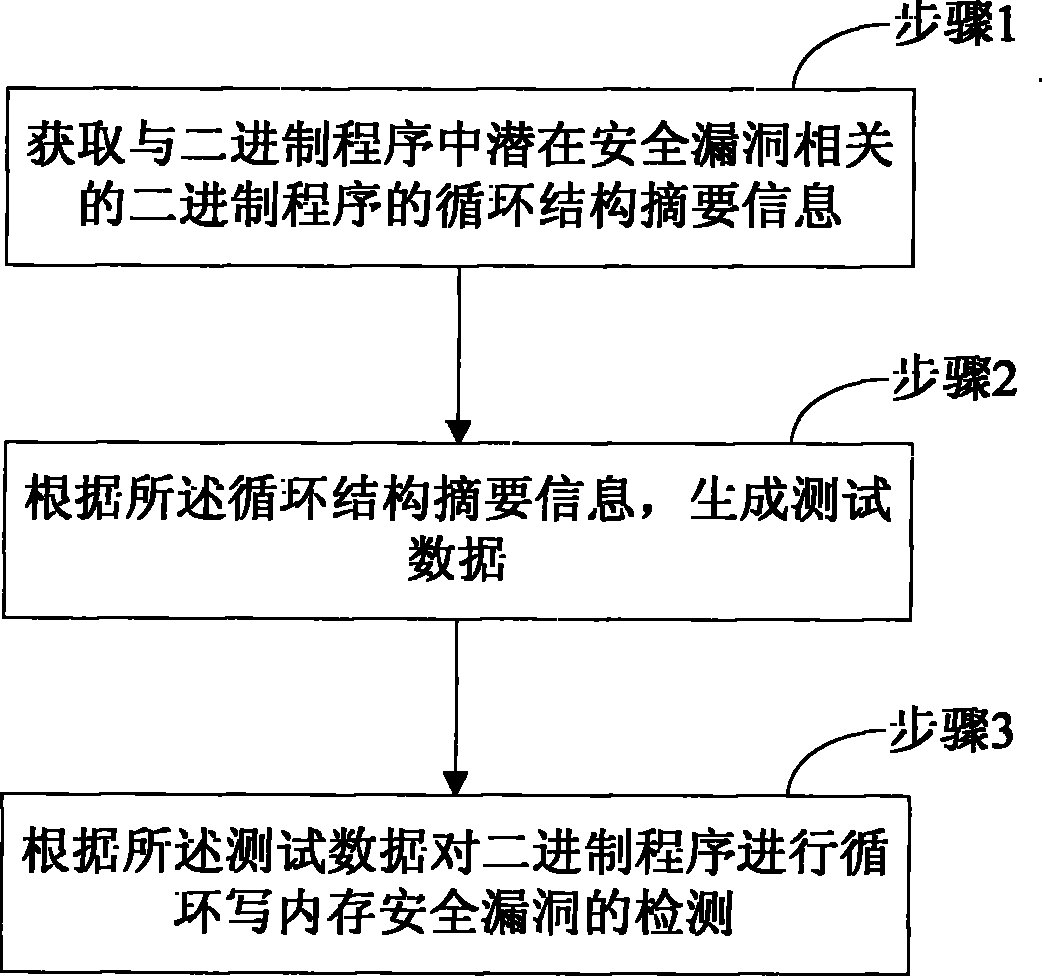
Detection method for security flaws in loop write-only memory of binary program
InactiveCN102708054AReduce computational costSoftware testing/debuggingPlatform integrity maintainanceParallel computingMemory safety
The invention aims at providing a detection method for security flaws in a loop write-only memory of a binary program, comprising the following steps of: step 1, obtaining loop structure abstract information of a binary program, related to the potential security flaws in the binary program; step 2, generating test data according to the loop structure abstract information; and step 3, performing loop write-only memory security flaw detection on the binary program according to the test data. According to the method provided by the embodiment of the invention, when generating the test data, a process of traversing all the paths of the binary program loop structure is not needed, and the test data can be obtained just according to the generated loop structure abstract information. Since the loop structure abstract information is related to the potential security flaws of the binary program, the generated test data are targeted more, and the calculation overhead for detecting the security flaws is reduced greatly.
Owner:CHINA INFORMATION TECH SECURITY EVALUATION CENT +1
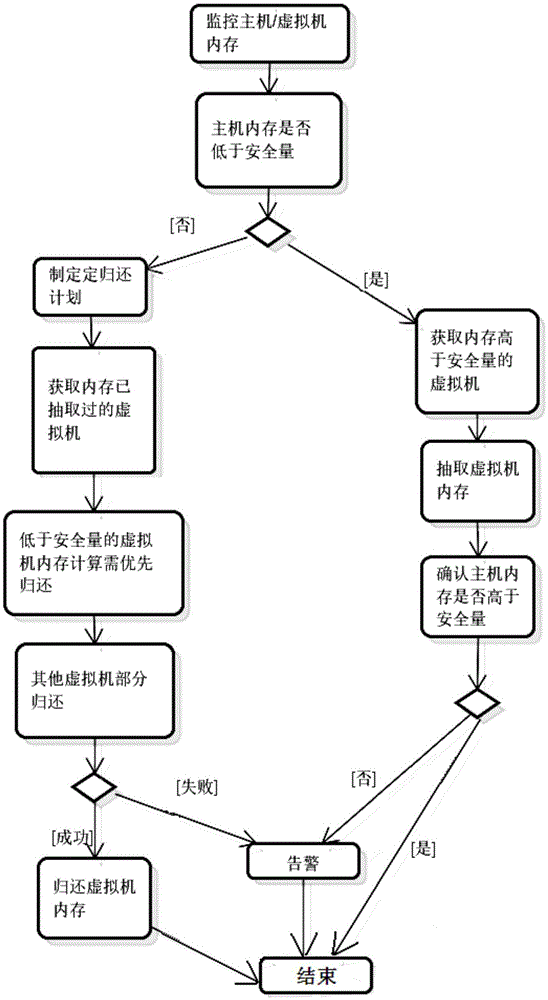
Memory dynamic adjusting method for cloud desktop host and virtual machine
ActiveCN105677485AGuaranteed uptimeReduce dynamic adjustment frequencyResource allocationAlarm messageHost memory
The invention provides a memory dynamic adjusting method for a cloud desktop host and a virtual machine. The method comprises the steps that 1, the memory is monitored, wherein the host memory and virtual machine idle memory condition is monitored; a the memory is adjusted, if the host idle memory is lower than the safety level, the idle memory of the virtual machine is extracted, if the host idle memory is higher than the safety level, the memory is returned to the virtual machine, and finally the host memory and the virtual machine memory are higher than the safety level; an alarm message is sent to a manager. The host memory is monitored, the dynamic adjusting frequency is reduced based on the safety level, and therefore the virtual machine has the sufficient memory to response to the emergency requests; normal running of the virtual machine can be ensured by setting the safety level of the virtual machine memory safety level.
Owner:CETC CHINACLOUD INFORMATION TECH CO LTD
Informed memory access for vehicle electronic modules
ActiveUS7454273B2Improve reliabilityVehicle testingRegistering/indicating working of vehiclesUniform memory accessDiagnostic data
A vehicle electronic module receives vehicle bus messages from a vehicle communication bus interface. The vehicle bus messages may include vehicle status data. The electronic module may determine whether a memory safety condition has been met based on the vehicle status data. The electronic module may delay reading or writing data, such as diagnostic data, into a non-volatile memory until the memory safety condition is reached. The data is read from or stored in the non-volatile memory with reduce risk of corrupted data.
Owner:HARMAN INT IND INC
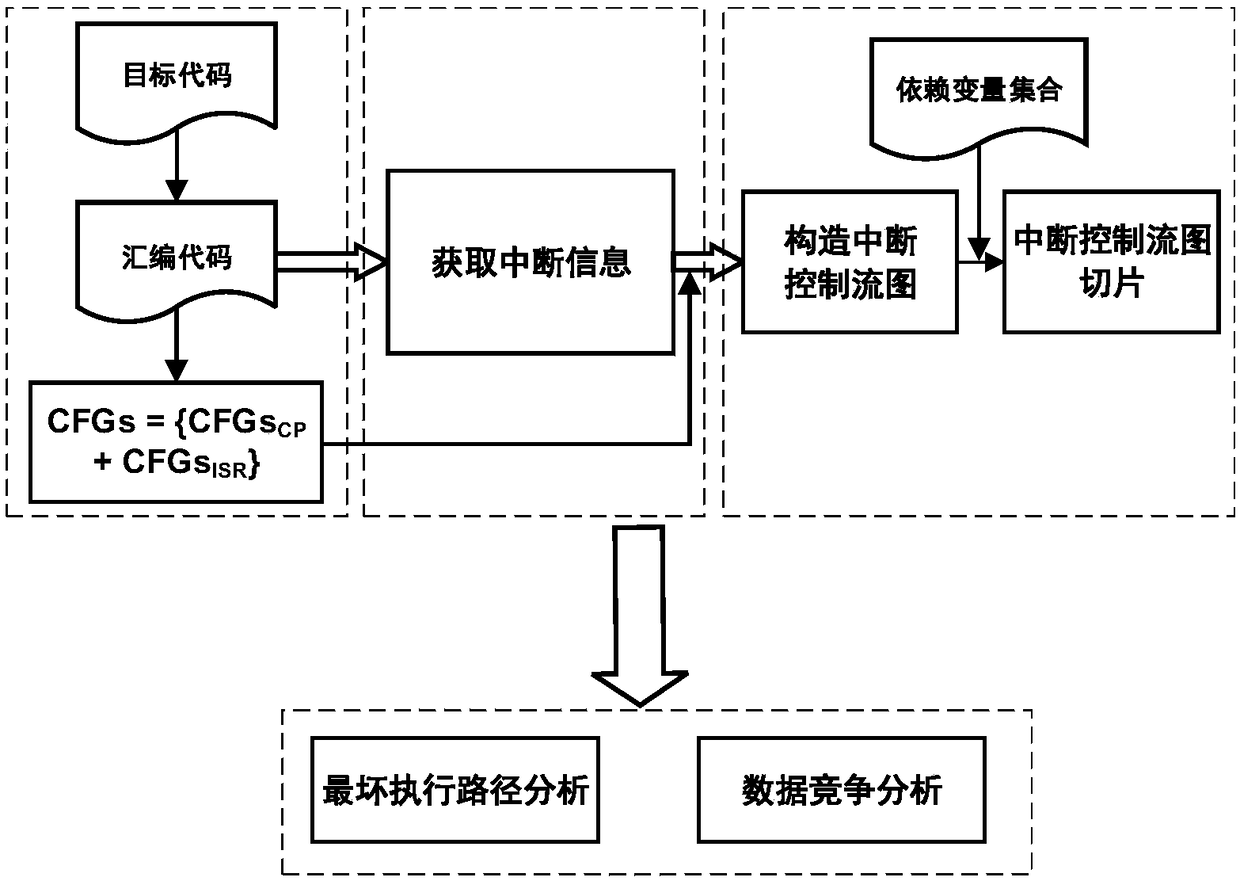
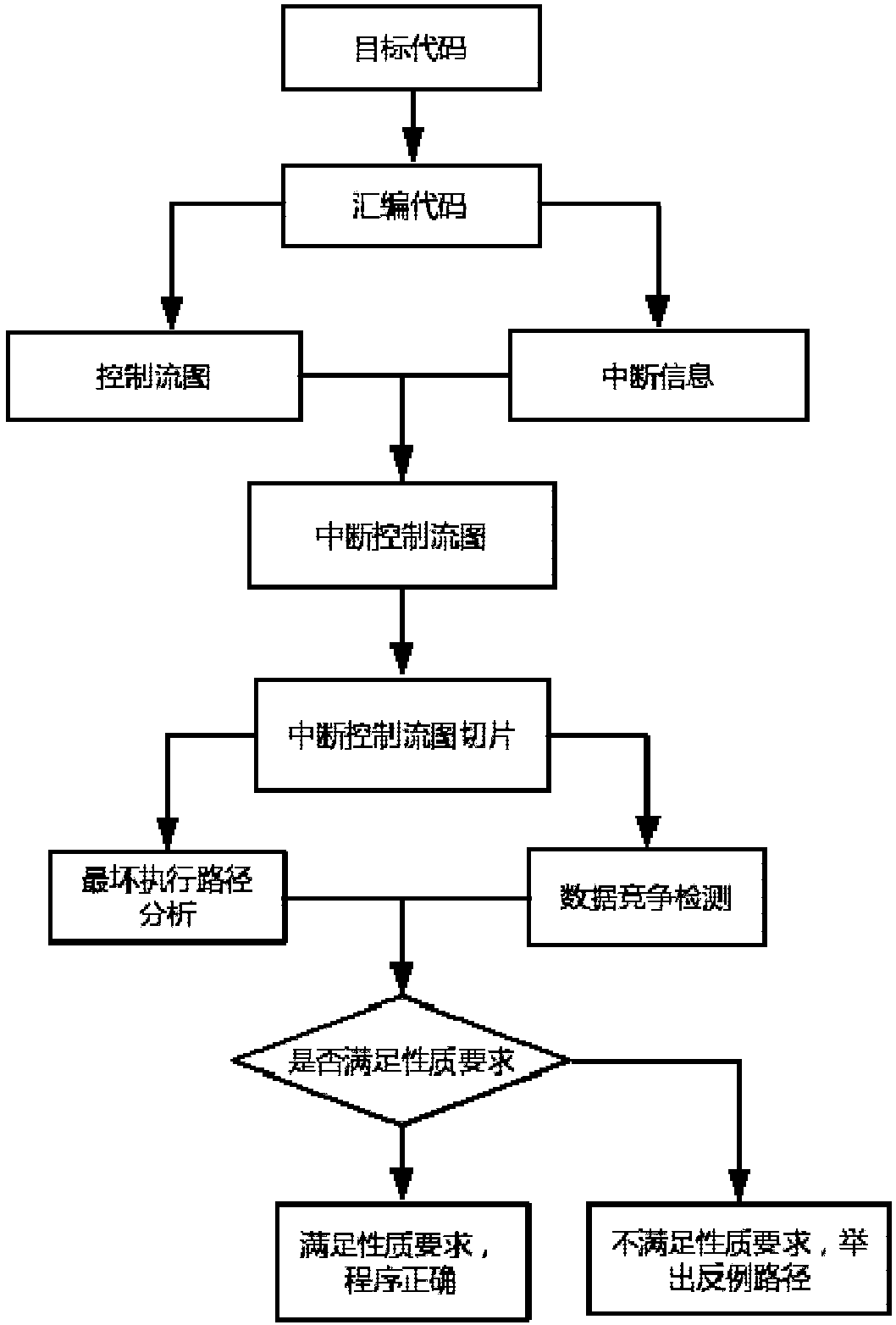
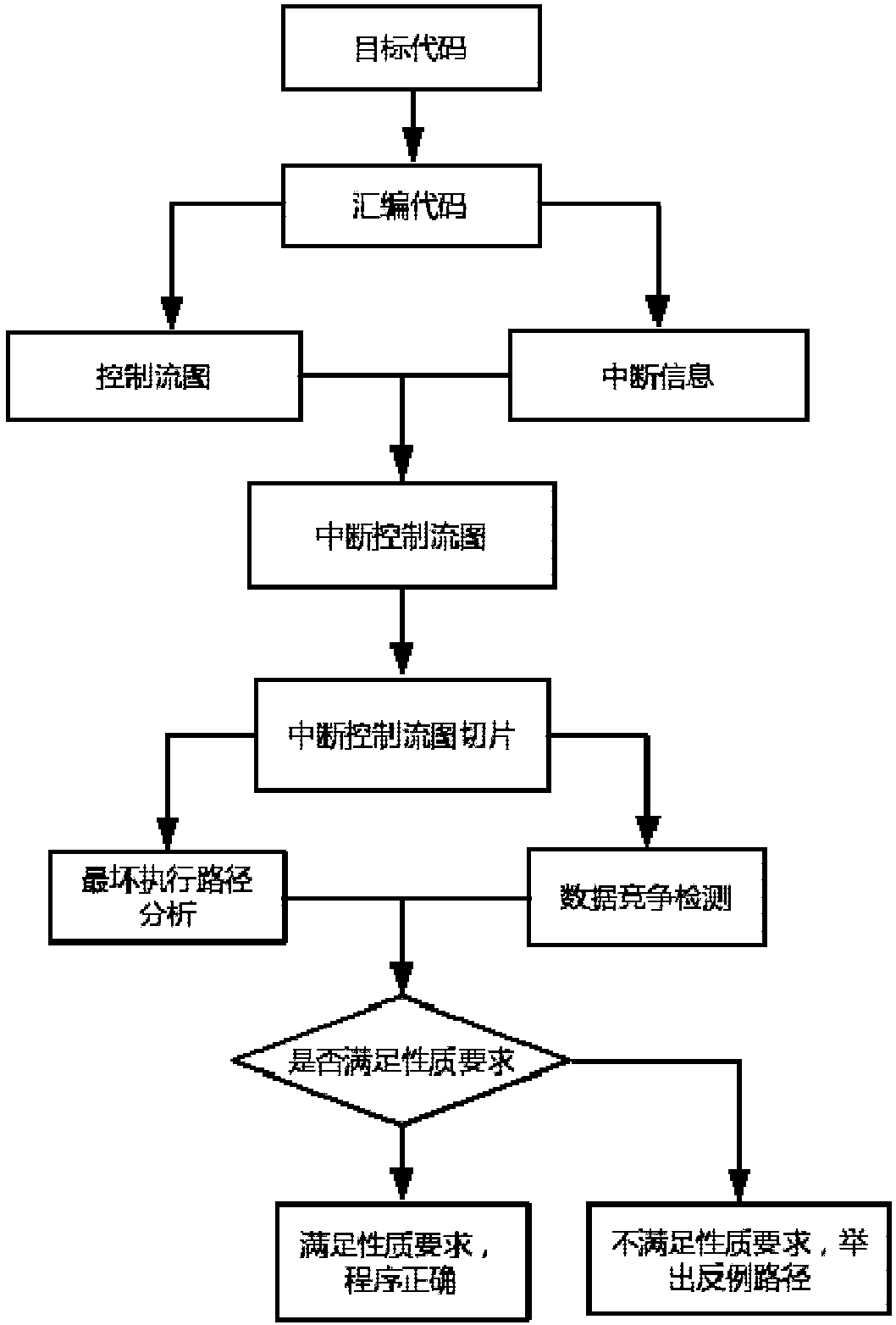
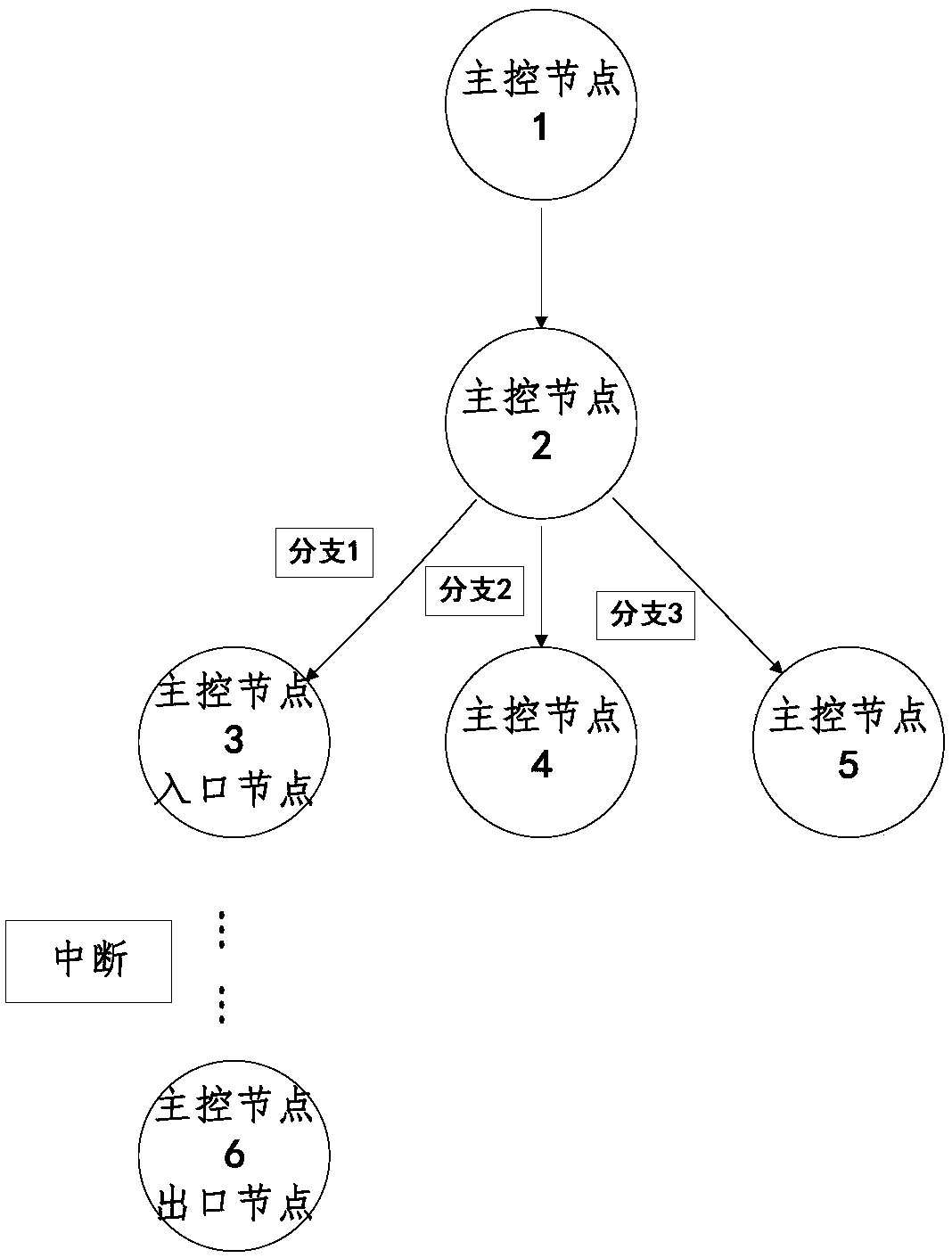
Interruption control flow diagram-based interruption verification method
ActiveCN108459963AImprove reliabilityImprove securitySoftware testing/debuggingControl flowProgram slicing
The invention discloses an interruption control flow diagram-based interruption verification method. The method comprises the following steps of: carrying out a disassembling operation on a target code of an interruption driving program so as to obtain an assembly code; constructing an interruption control flow diagram according to the assembly code; slicing the interruption control flow diagram to obtain interruption control flow diagram slices; and verifying time safety and memory safety of the interruption control flow diagram according to the interruption control flow diagram slices. According to the method, control flow information of the interruption driving program is described by adoption of the interruption control flow diagram, and the interruption control flow diagram is slicedby utilizing a program slicing technological thought so as to analyze and verify the time safety and memory safety of the target code. The method has the advantages of putting forward model-interruption control flow diagrams of interruption control flow structures, verifying two most common problems of the interruption driving program in a same model, and improving the reliability and safety of interruption driving program verification.
Owner:EAST CHINA NORMAL UNIVERSITY +1
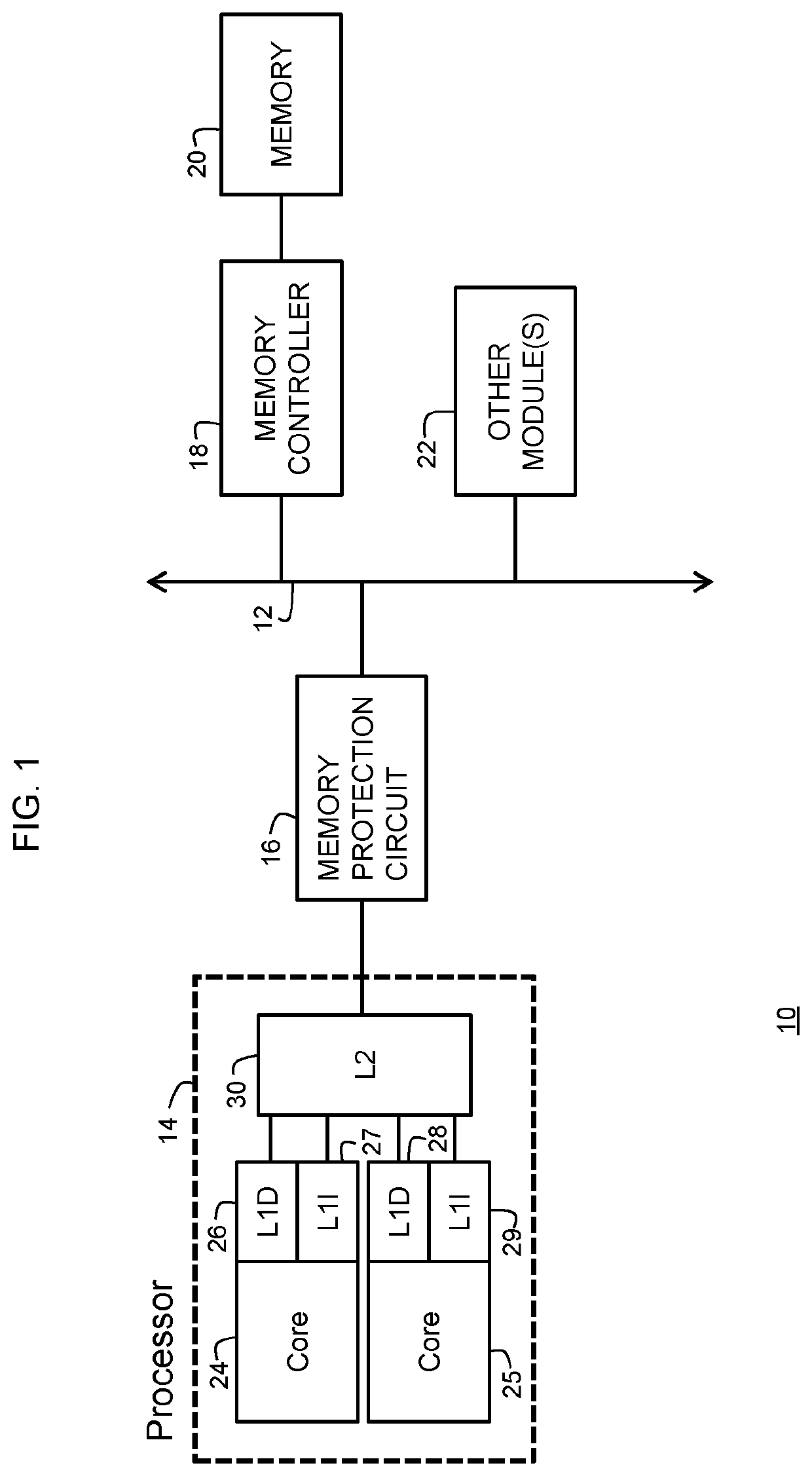
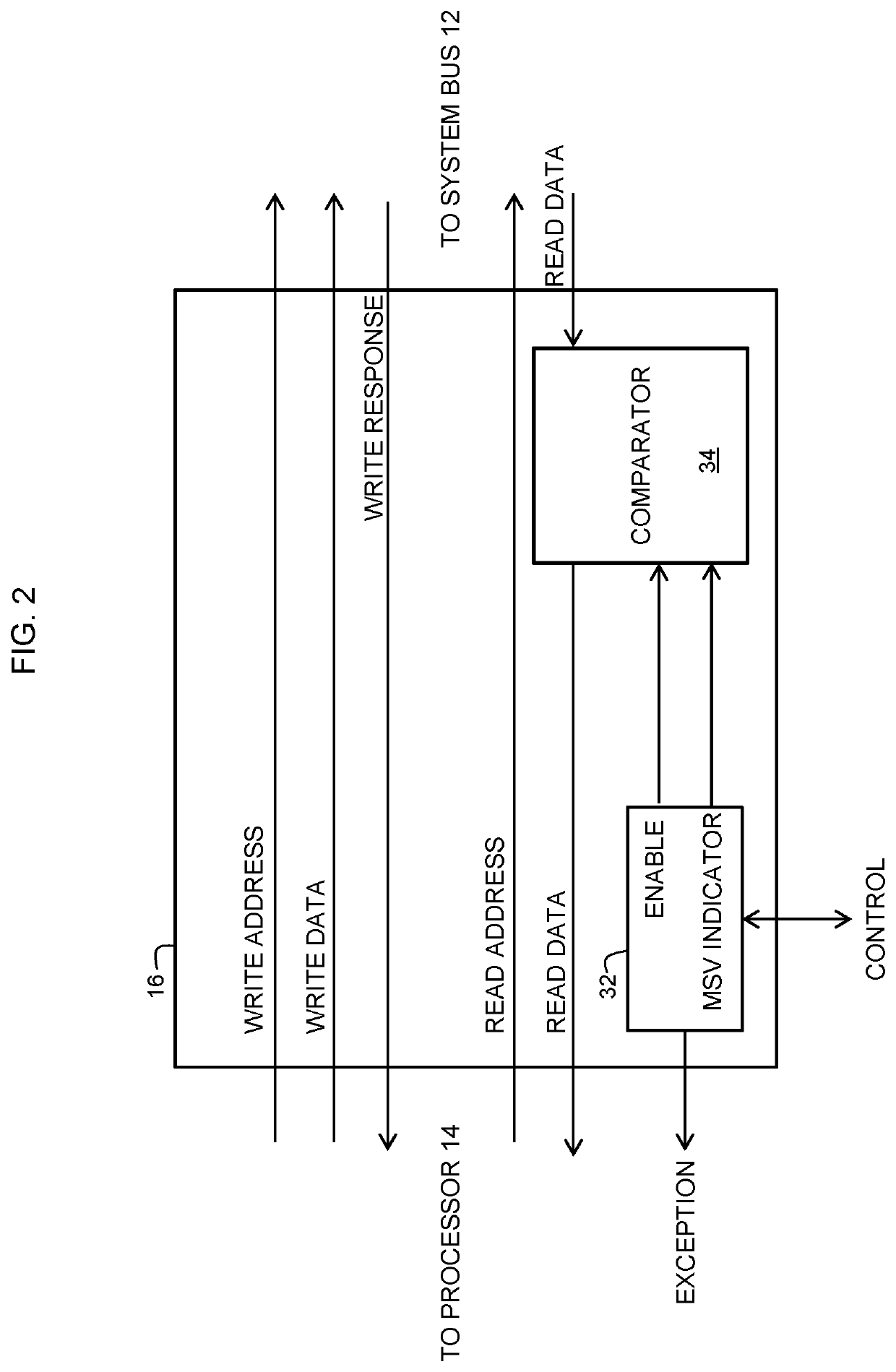
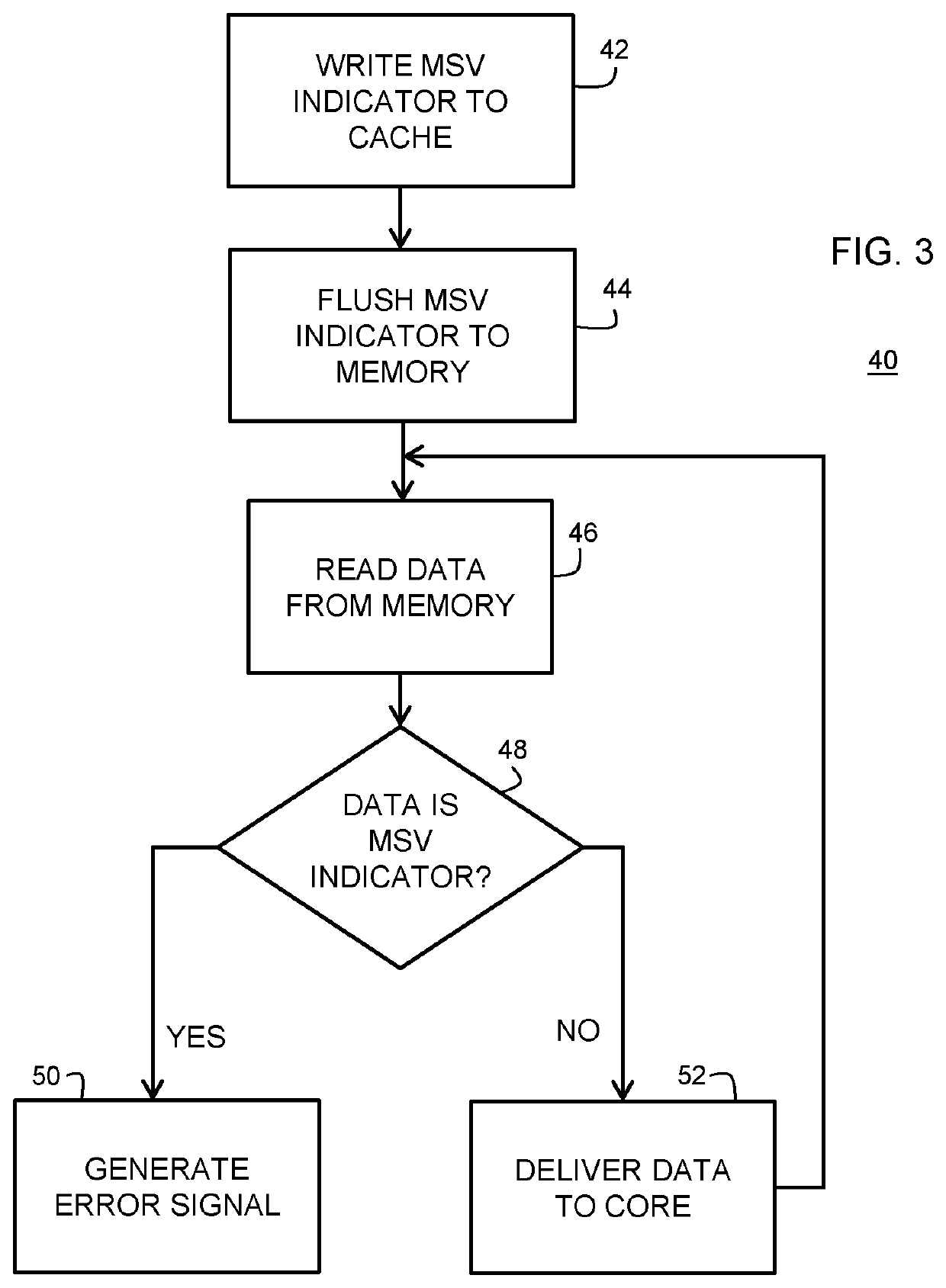
Data processing system having memory protection and method therefor
ActiveUS20200264976A1Memory architecture accessing/allocationMemory adressing/allocation/relocationData processing systemProcessing core
A data processing system and method for protecting a memory from unauthorized accesses are provided. The data processing system includes a system bus, a memory coupled to the system bus through a memory controller, and a processing core including a cache system. The memory controller is coupled to the system bus for controlling accesses to the memory that are requested by the processing core. A memory protection circuit is coupled to the system bus and to the processing core. The memory protection circuit uses one or more memory safety violation (MSV) indicators stored in out-of-bounds areas of the memory for detecting when the processing core attempts to access an out-of-bounds area of the memory. The processing core generates an error signal, such as an interrupt, when an attempt to access the out-of-bounds area is detected. The out-of-bounds area may be an unallocated area of the memory. The MSV indicator may be written to the memory by executing a flush instruction of the cache system and may include the same number of bits as a cache line of the cache system. A data value of the MSV indicator may be a secret data value.
Owner:NXP BV
Lithium ion secondary battery having shape memory safety vent
InactiveUS8084152B2Avoid a swelling phenomenon of the batteryImprove securityFinal product manufactureCell temperature controlLithiumMemory safety
A lithium ion secondary battery has a shape memory safety vent adapted to discharge internal compressed gas by temporarily being opened when the temperature reaches a predetermined level to avoid a swelling phenomenon of the battery and improve safety. The lithium ion secondary battery includes an electrode assembly having first and second electrode plates wound a number of times with a separator interposed between them; a can having an opening formed on a side thereof to contain the electrode assembly; and a cap plate adapted to cover the can and provided with a vent hole on a side thereof, to which a safety vent adapted to deform at a predetermined temperature and discharge gas from inside the can to the exterior is coupled.
Owner:SAMSUNG SDI CO LTD
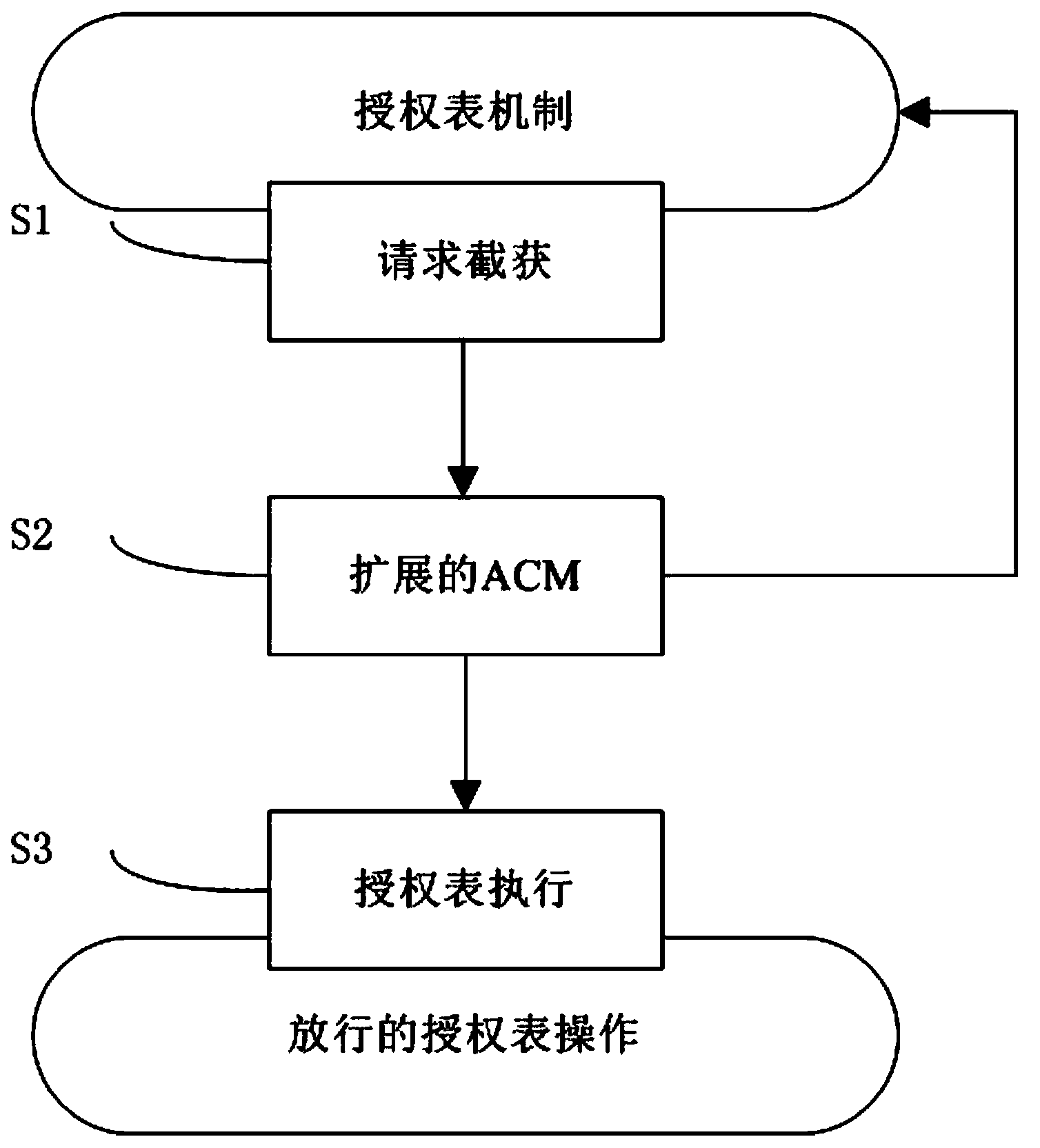
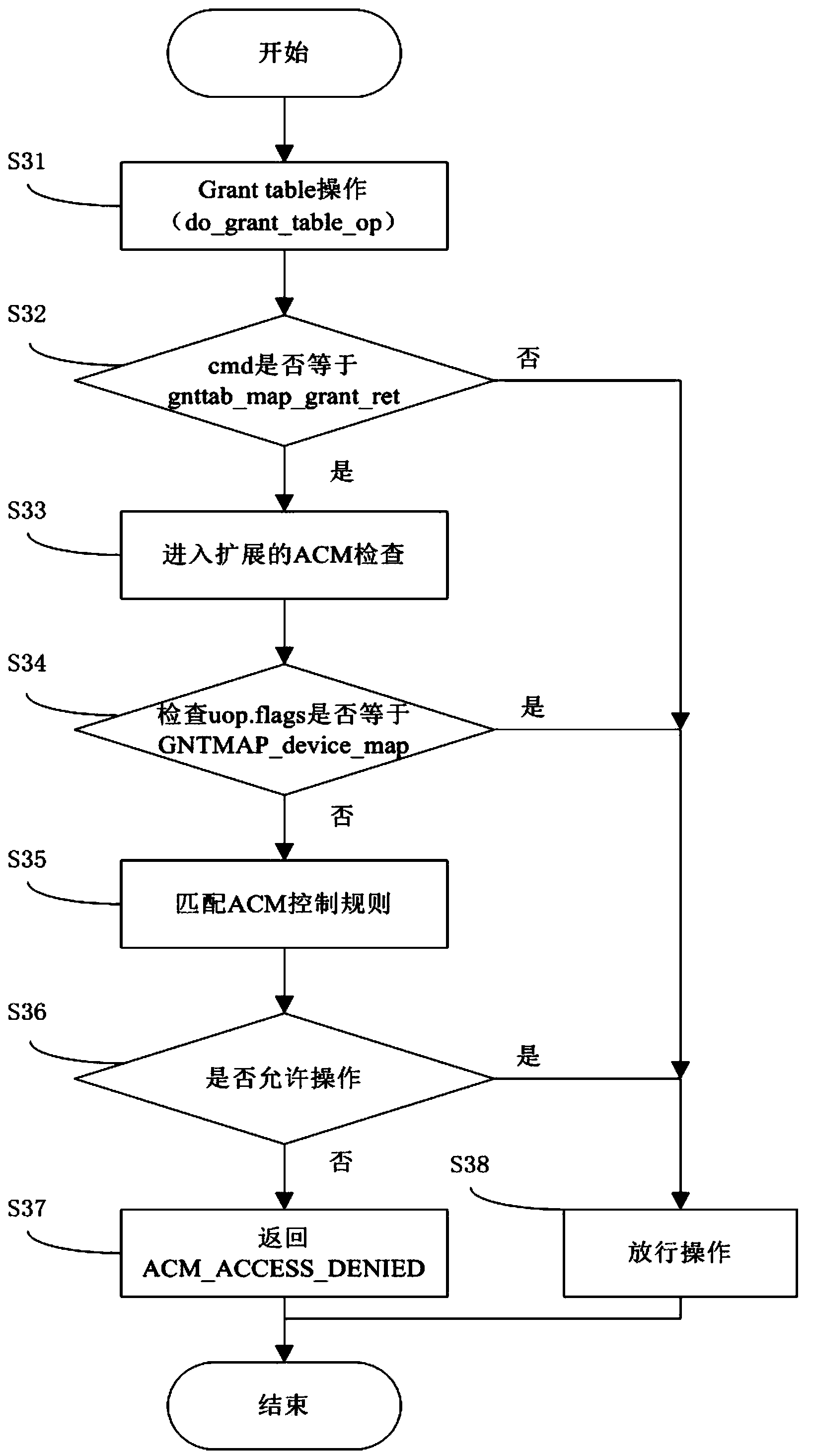
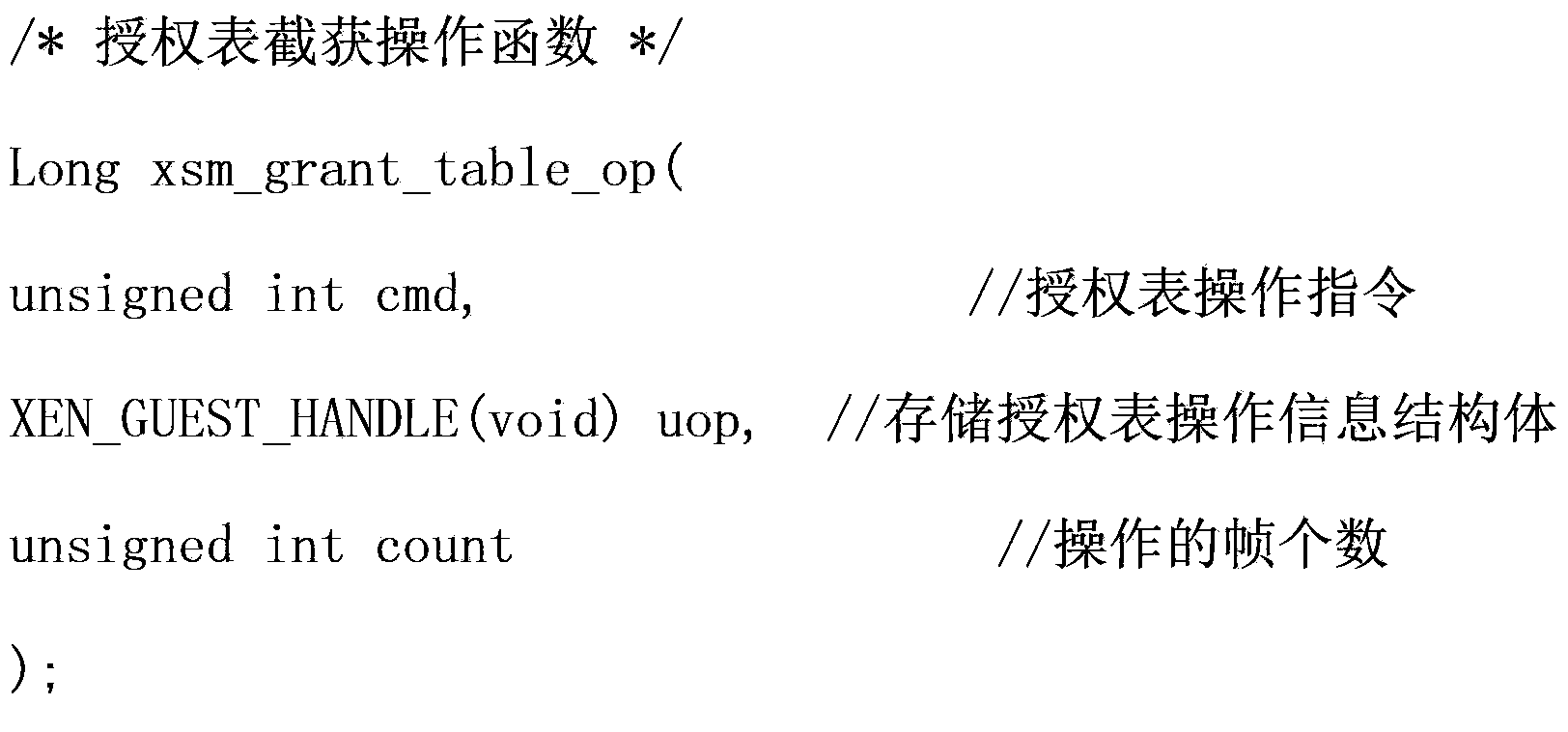
XEN cloud platform virtual machine isolation method based on memory isolation
InactiveCN103413093ASafety isolation is achievedImprove securityPlatform integrity maintainanceKnowledge FieldInformation security
The invention discloses an XEN cloud platform virtual machine isolation method based on memory isolation, and belongs to the field of information safety. The XEN cloud platform virtual machine isolation method based on memory isolation comprises the following steps of S1, carrying out interception on an authorization list operation, S2, extending the ACM mechanism, achieving validity verification of the authorization list operation, letting the authorization list operation pass when the validity verification of the authorization list operation gets through, and S3, carrying out control execution on the passed authorization list operation. The XEN cloud platform virtual machine isolation method based on memory isolation has the advantages that the authorization list operation of an XEN memory is intercepted to carry out analysis on the memory mapping relation between virtual machines, the validity verification of the authorization list operation is accomplished through an extended ACM, the authorization list operation is let pass after the validity verification of the authorization list operation gets through, memory safety isolation between the virtual machines is accomplished through control over an authorization list, and the XEN cloud platform virtual machine isolation method based on memory isolation belongs to the field of Hypervisor safety research, can achieve safe isolation of a memory resource, and improves safety of the XEN cloud environment.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Computer-implemented method and a system for encoding a stack application memory state using shadow memory
ActiveUS20180157442A1Memory architecture accessing/allocationInput/output to record carriersShadow memoryByte
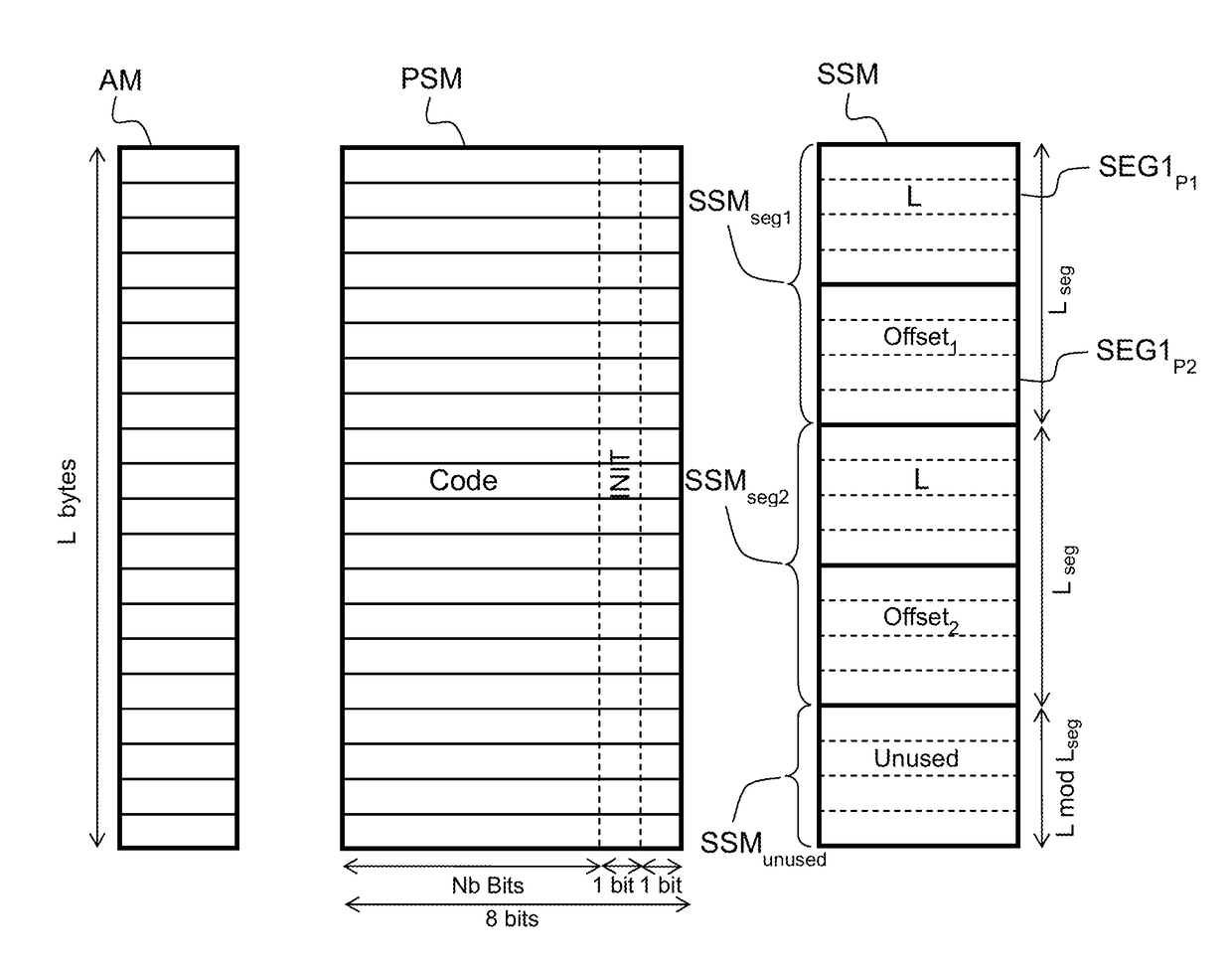
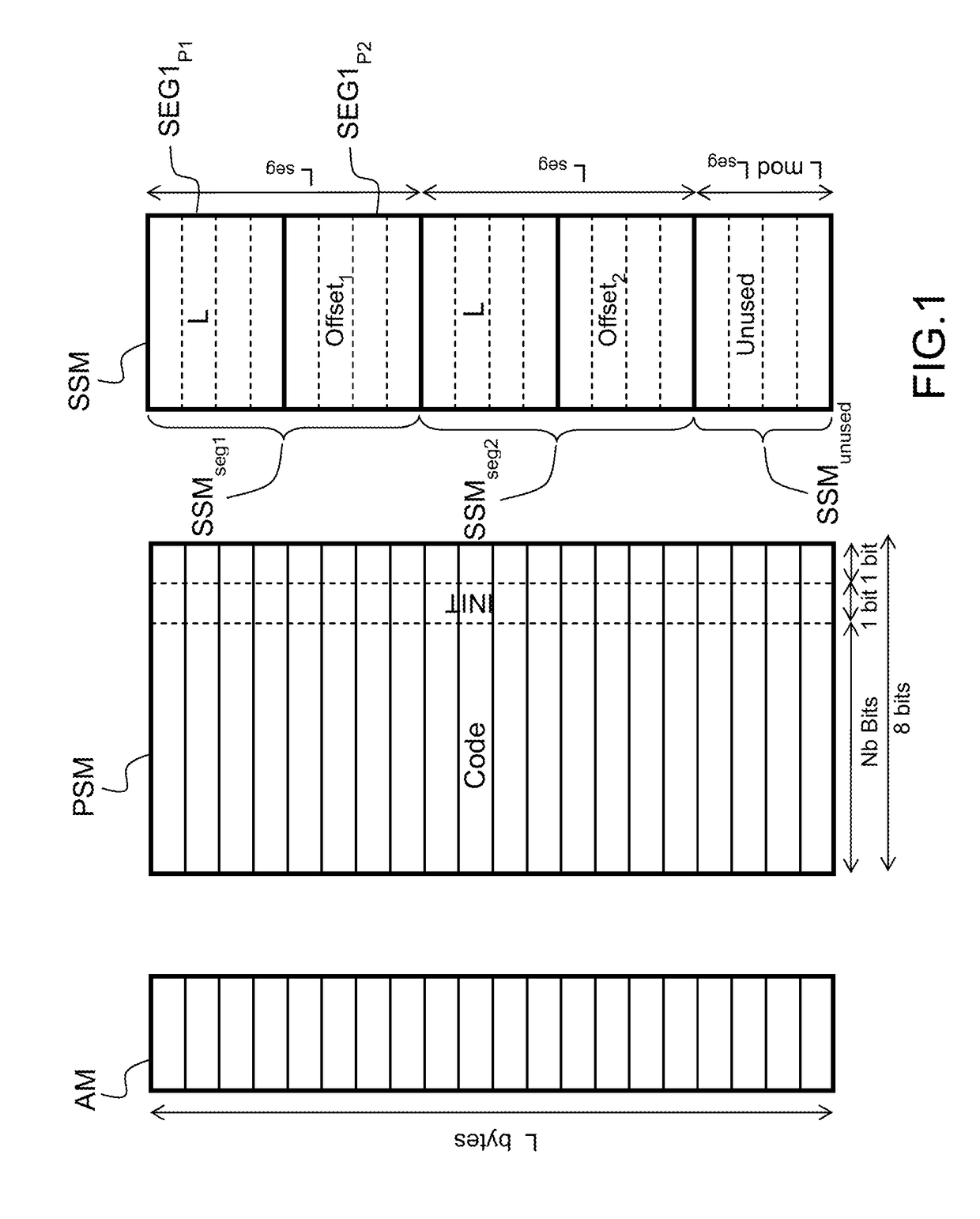
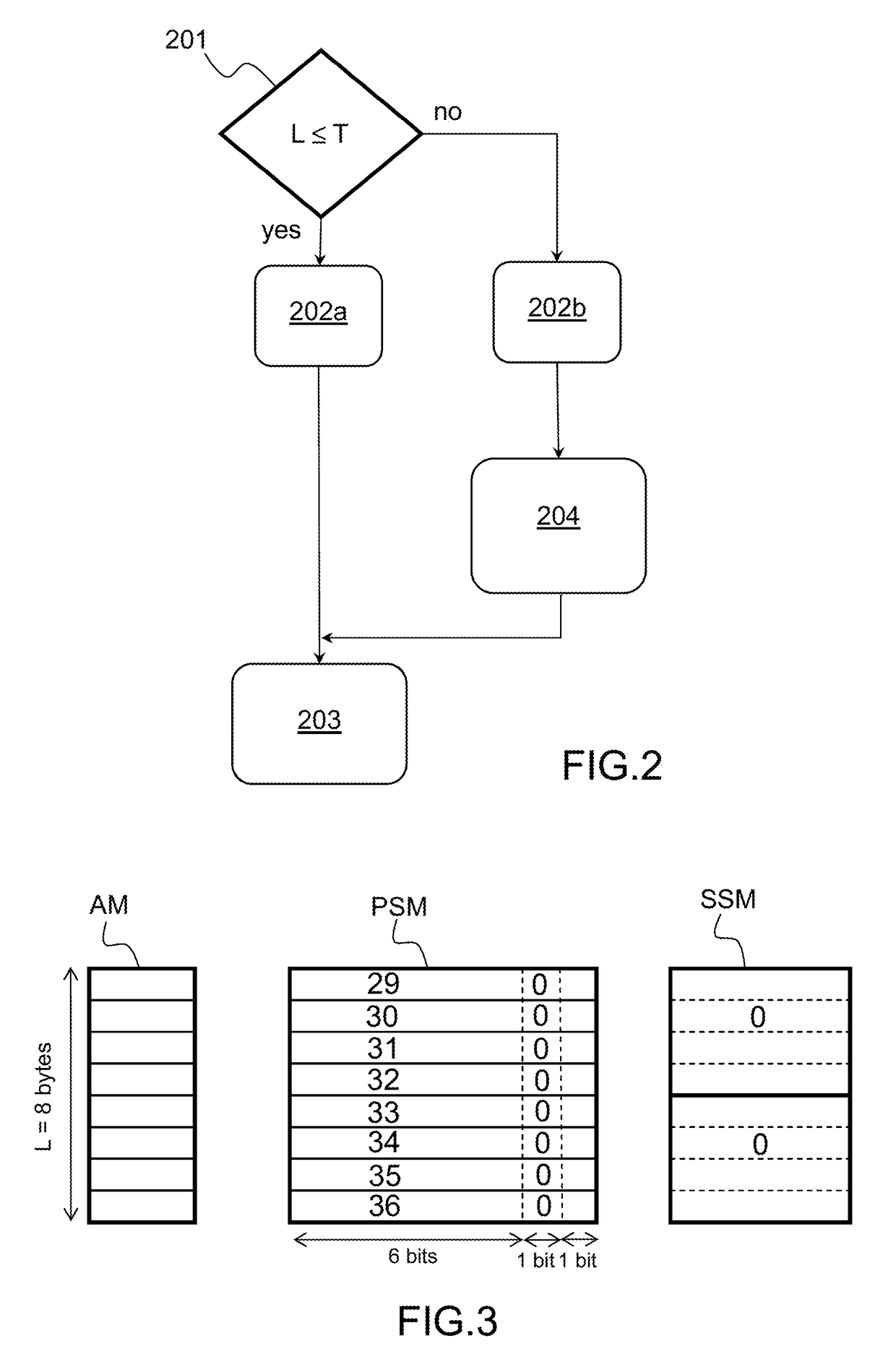
A method is provided that allows tracking boundaries of allocated memory blocks while still capturing byte-level properties. This is achieved with a particular shadow memory encoding scheme which captures boundaries and lengths of allocated memory blocks. Analyzing the shadow memory state allows detecting memory safety issues. In particular, for a memory location given by its address a, the proposed invention allows computing the following information: whether a has been allocated, whether a has been initialized, the start (base) address of the memory block a belongs to, the byte-length of the memory block a belongs to, the byte offset of a within its block. Such information allows for detection of specific memory safety issues at runtime.
Owner:COMMISSARIAT A LENERGIE ATOMIQUE ET AUX ENERGIES ALTERNATIVES
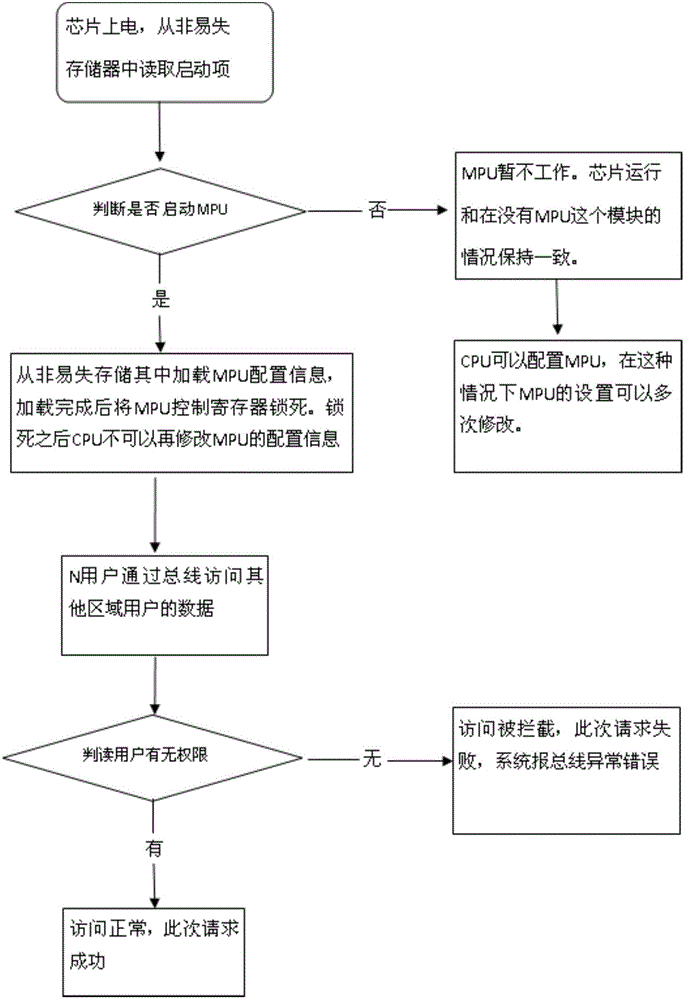
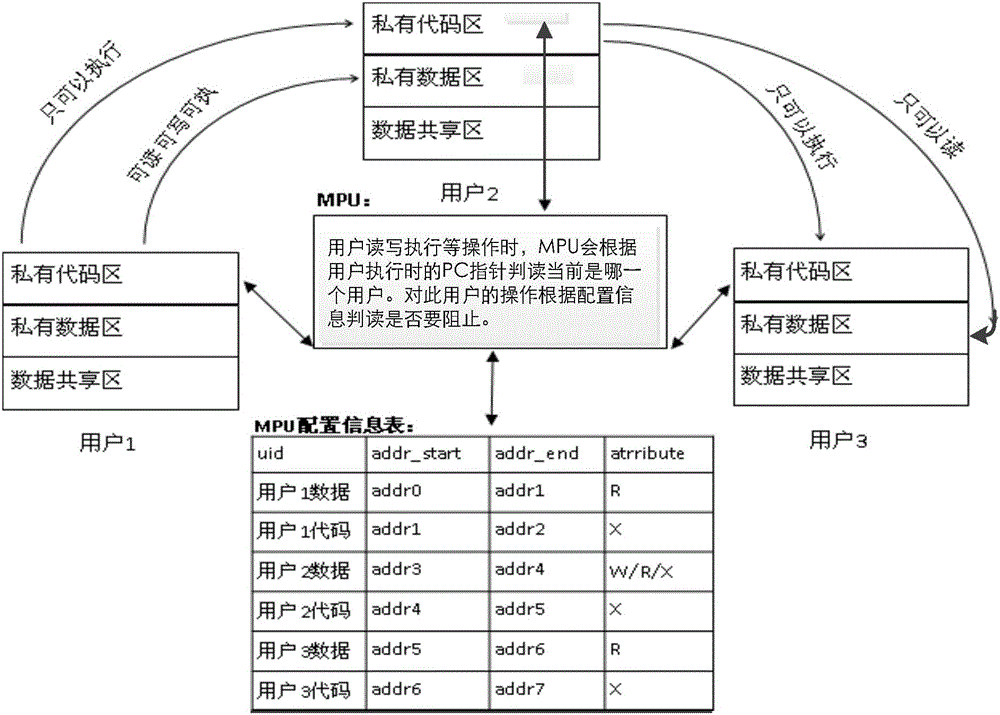
Nonvolatile memory safety protection method
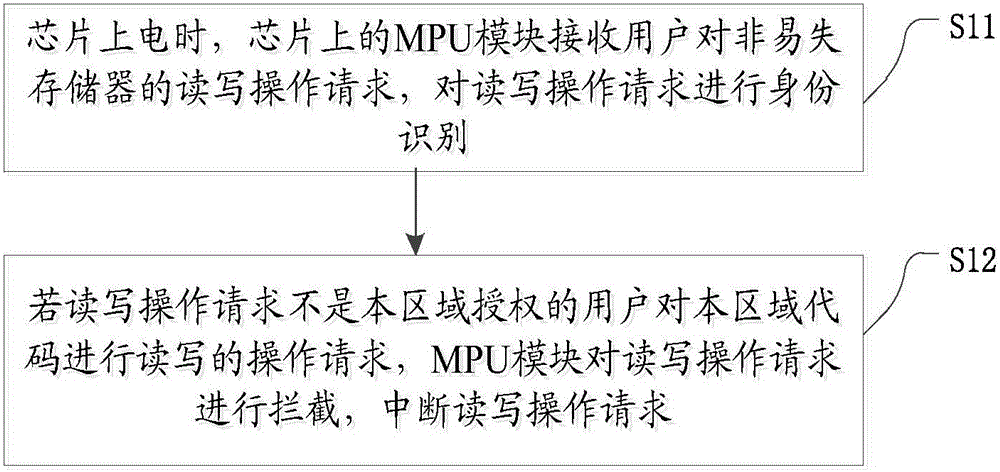
InactiveCN106228092AImprove securityInternal/peripheral component protectionComputer scienceEmbedded system
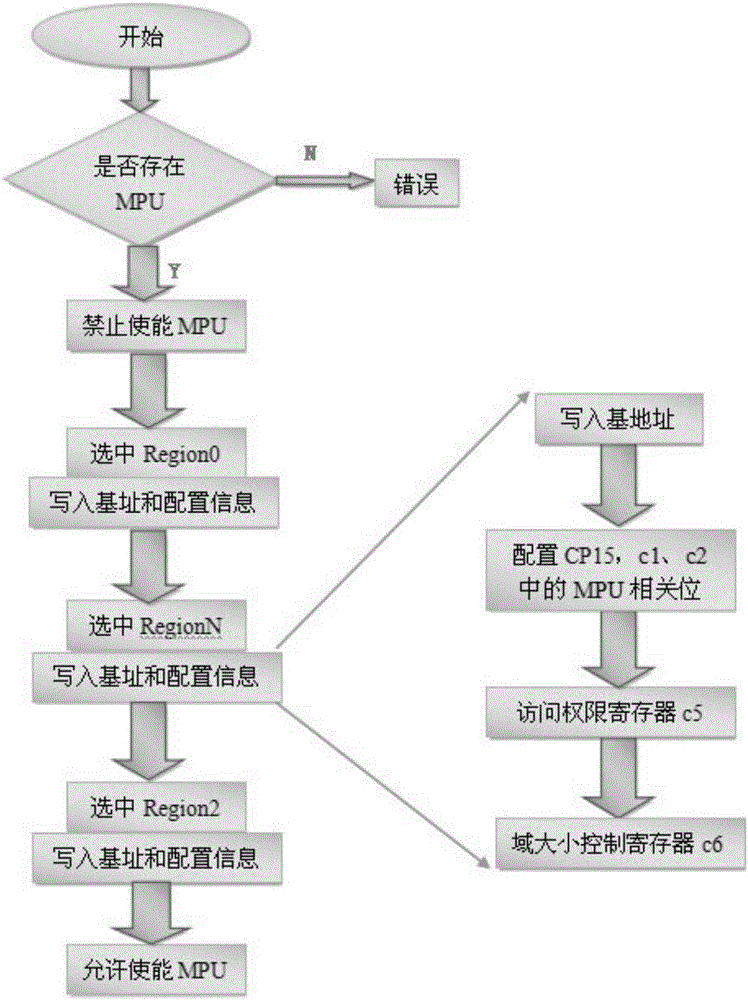
The invention discloses a nonvolatile memory safety protection method comprising the following steps: allowing a MPU module on a chip to receive a user read-write operation request on a nonvolatile memory when the chip is powered up, and carrying out identity identification of the read-write operation request; allowing the MPU module to intercept the read-write operation request if the read-write operation request is not a read-write operation request on local area codes by the local area authorized user, and interrupting the read-write operation request. The novel method can improve nonvolatile memory safety.
Owner:苏州国芯科技股份有限公司
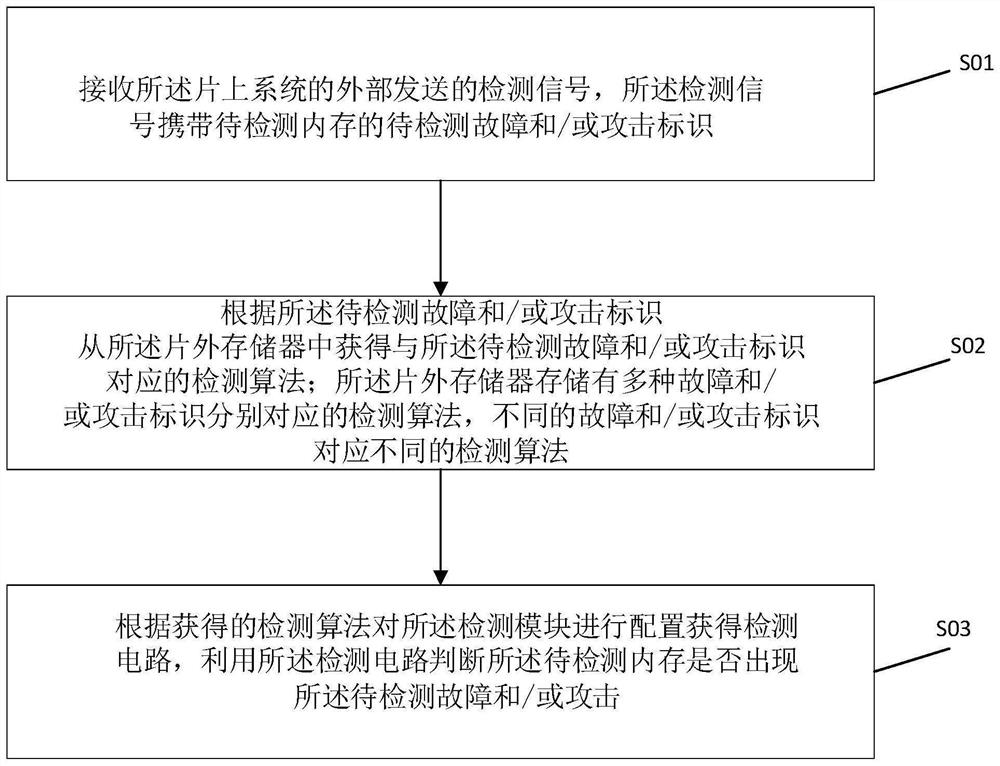
Memory security detection method and system on chip
PendingCN113157509AImplement security testingReduce power consumptionFaulty hardware testing methodsTerm memorySecurity policy
The invention provides a memory security detection method and a system on chip, the system on chip comprises a security policy controller and a memory to be detected, and the security policy controller comprises a detection module. The security policy controller receives a detection signal which carries a to-be-detected fault and / or an attack identifier of the to-be-detected memory, and obtains a detection algorithm corresponding to the to-be-detected fault and / or the attack identifier from the off-chip memory according to the to-be-detected fault and / or the attack identifier; and the off-chip memory stores detection algorithms corresponding to various fault and / or attack identifiers, the detection module is configured according to the obtained detection algorithms to obtain a detection circuit, and the detection circuit is utilized to judge whether the to-be-detected memory has a to-be-detected fault and / or attack. Security detection of corresponding faults and / or attacks of the to-be-detected memory is achieved, multiple complex detection circuits do not need to be deployed in the system at the same time, corresponding detection algorithms are called according to different detection signals to configure the corresponding detection circuits, power consumption is reduced, and efficiency is improved.
Owner:INST OF MICROELECTRONICS CHINESE ACAD OF SCI
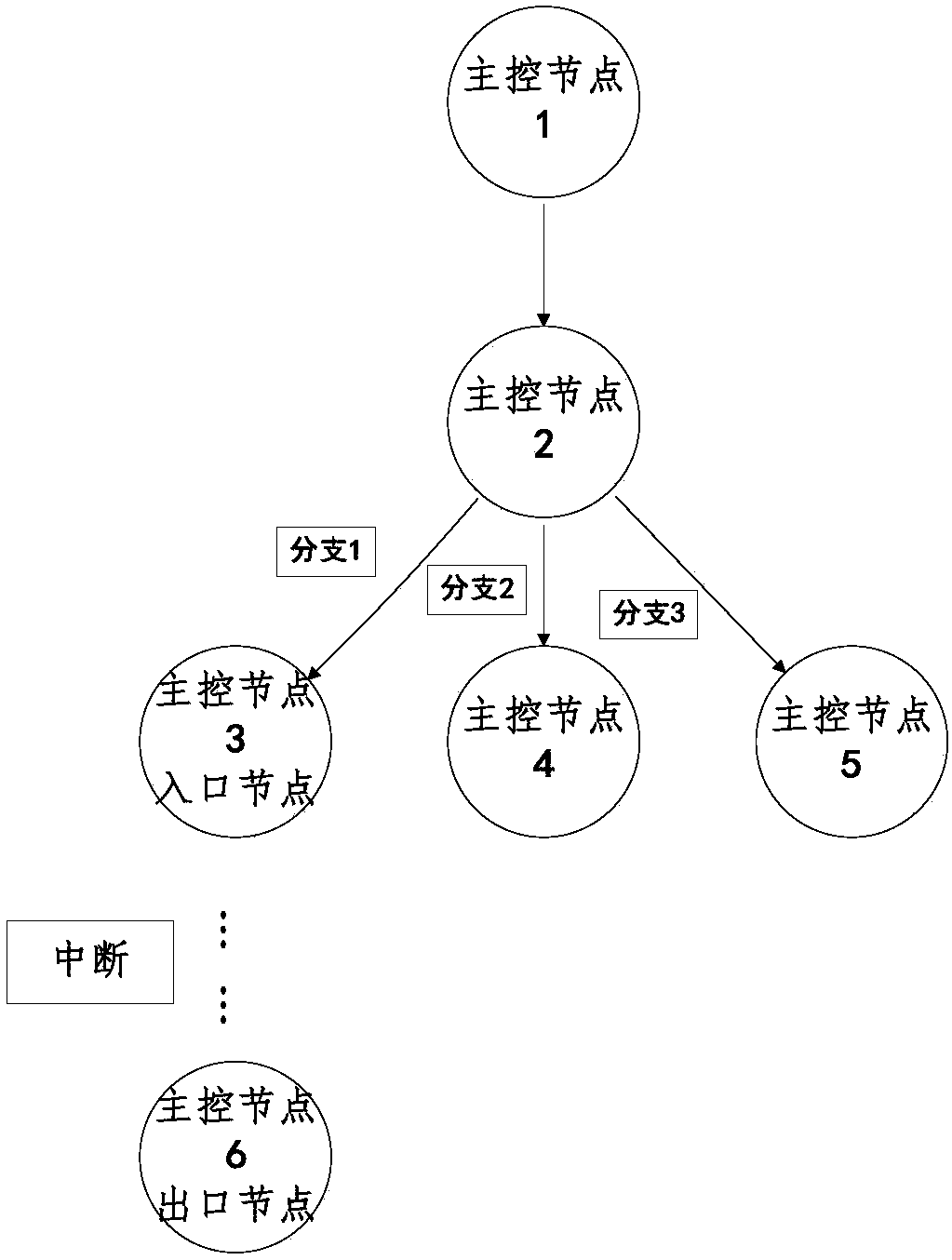
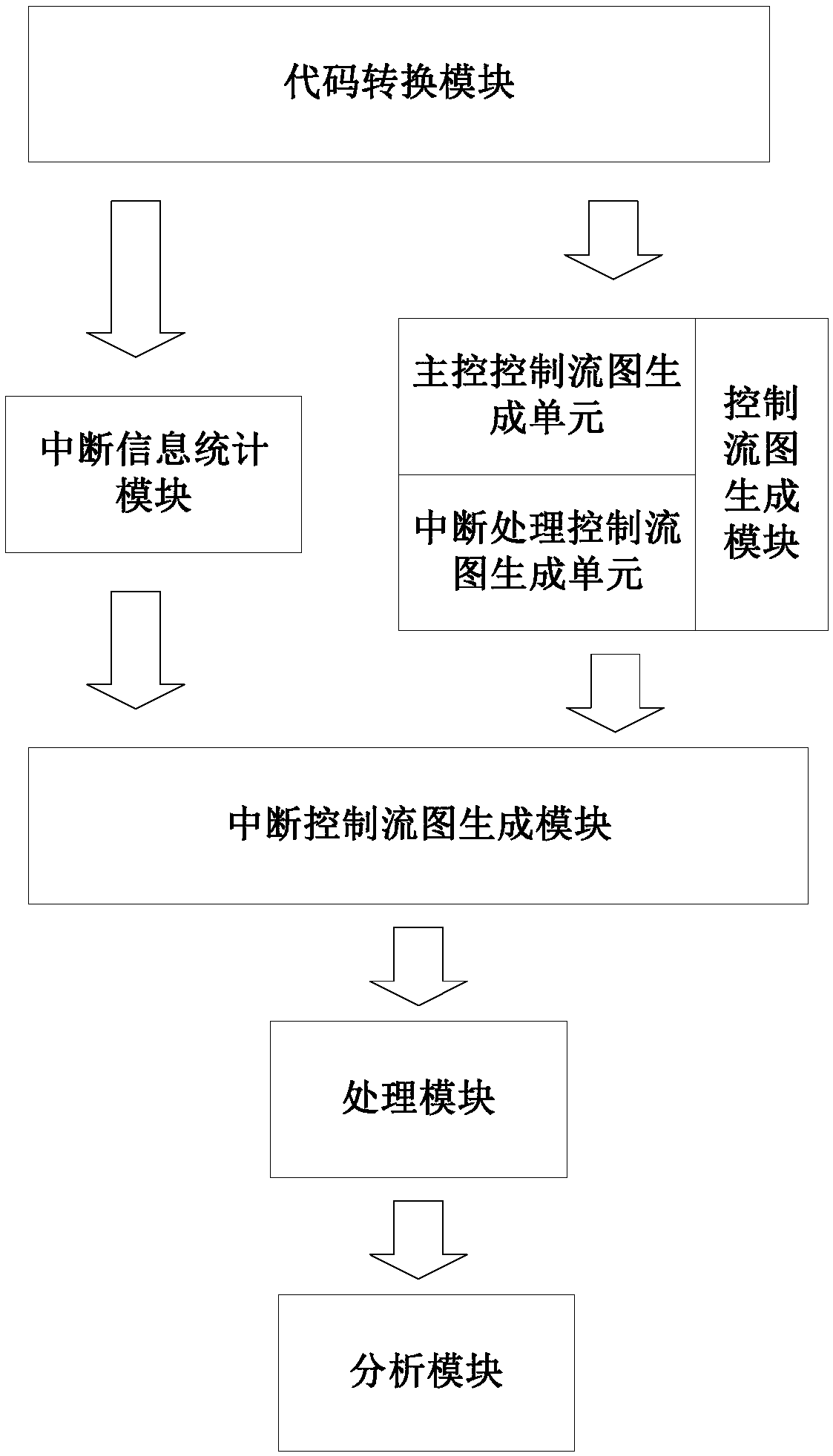
Interrupt verification system based on interrupt control flow graph
ActiveCN108469987AImprove reliabilityImprove securityProgram initiation/switchingControl flowGraph generation
The invention discloses an interrupt verification system based on an interrupt control flow graph. The system comprises a code conversion module, an interrupt information statistical module, a controlflow graph generation module, an interrupt control flow graph generation module, a processing module and an analysis module, wherein the code conversion module is used for obtaining an assembly codeaccording to an interrupt driving program; the interrupt information statistical module carries out statistics of interrupt information according to the assembly code; the control flow graph generation module generates the control flow graph according to the assembly code; the interrupt control flow graph generation module generates the interrupt control flow graph according to the control flow graph and the interrupt information; the processing module is used for carrying out slicing processing on the interrupt control flow graph; and the analysis module verifies the time safety and the memory safety of the interrupt driving program according to an interrupt control flow graph slice. The invention puts forward a new a model-interrupt control flow graph used for showing the control flow structure of the interrupt driving program and gives a method for cutting off the scale (slice) of the interrupt control flow graph, two categories of problems which appear most often in the interrupt driving program are verified in the same model, and the verification reliability and safety of the interrupt driving program is improved.
Owner:EAST CHINA NORMAL UNIV +1
Method for analyzing memory security in C code by using data stream analysis algorithm
The invention provides a method for analyzing memory security in a C code by using a data stream analysis algorithm. Defining an instruction into a formalized instruction set, and performing the following operations: statically analyzing a code demand and adding a mark to a pointer; codes are converted into an abstract syntax tree, type checking is carried out on each instruction, and related pointer permission transfer or borrowing statements are modified at the same time, so that the related pointer permission transfer or borrowing statements are distinguished in static single assignment; performing linearization on the abstract syntax tree to obtain a control flow graph in a static single assignment form, and performing data flow analysis to obtain a result of a convergent permission mapping table; and iterating the stabilized result by using a data flow analysis algorithm, and checking whether a memory security problem exists or not by using an error checking function. The method has the advantages that based on a series of common instructions related to the memory in the C language, the formalized instruction set is defined, a series of memory error detection methods are defined, and memory safety detection is facilitated.
Owner:上海那一科技有限公司
Shape memory safety utensil
ActiveUS8087174B2Simple and inexpensive configurationDwelling equipmentEqualizing valvesThreshold temperatureBiomedical engineering
A spoon having: a handle portion; and a head portion connected to the handle portion, the head portion being at least partially fabricated from a shape memory material, the head having a first shape to hold a liquid when the temperature of the liquid is less then a predetermined threshold temperature and a second shape so as to not hold the liquid when the temperature of the liquid is greater than the predetermined threshold. The first shape is preferably a concave shape and the second shape is a substantially flat shape. Alternatively, the first shape is a concave shape and the second shape is a concave shape having at least one opening in the concave shape. A fork is also disclosed having times that change shape when the temperature of food held thereon is greater than a predetermined threshold.
Owner:OMNITEK PARTNERS LLC
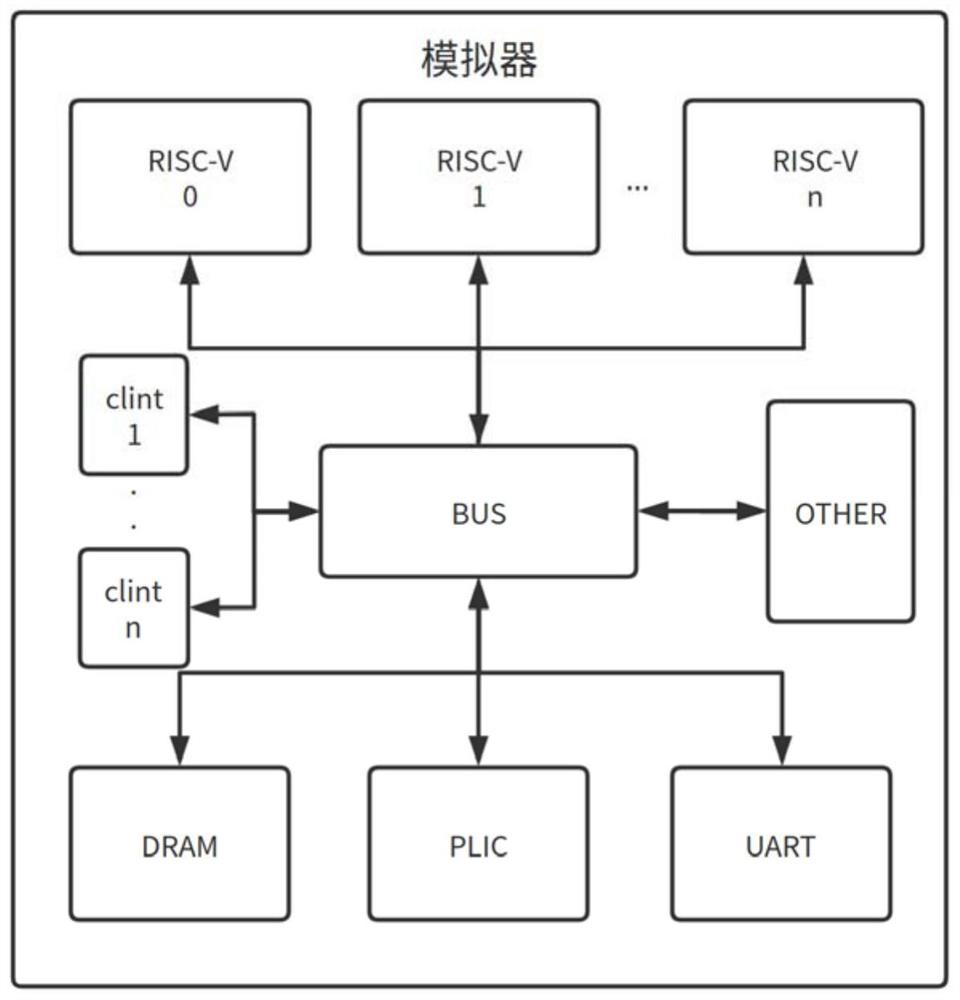
Multi-core RISV-CPU simulator based on Rust
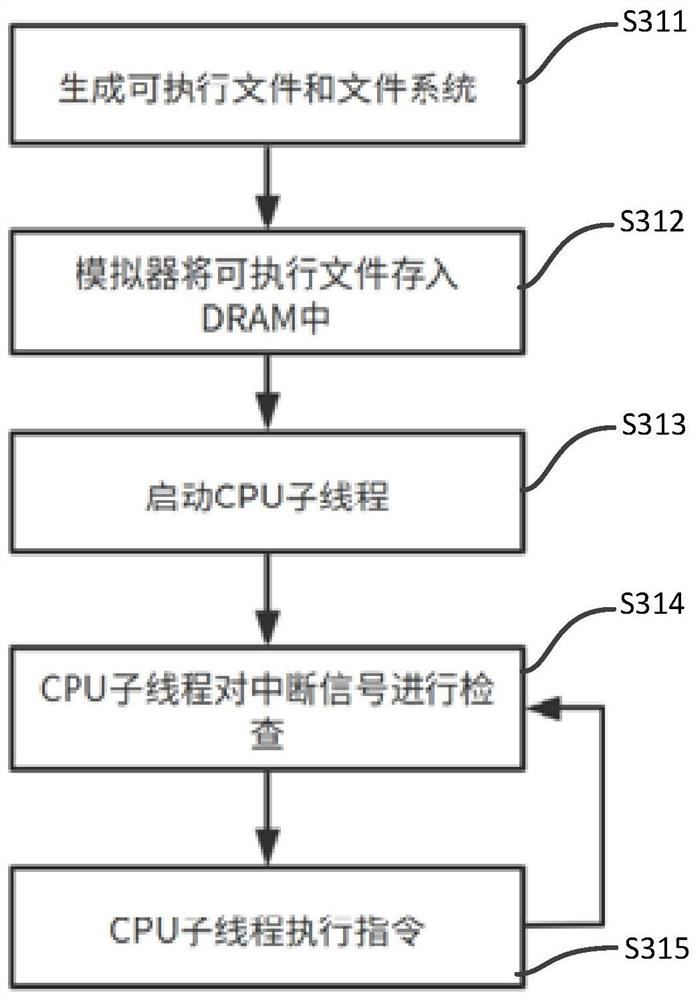
PendingCN113609066ASimple structureImprove robustnessMultiple digital computer combinationsMachine execution arrangementsTerm memoryMemory safety
The invention discloses a multi-core RISCV (Reduced International Standard Control Virtualization) simulator based on Rust. The simulator comprises a plurality of Risc-V processing core modules, a bus module, a DRAM module, a CLINT module, a PLIC module and a UART module, wherein the Risc-V processing core modules are constructed based on a Risc-V open source instruction set and used for achieving instruction fetching, decoding and execution functions. The DRAM module is used for simulating a memory; the PLIC module is used for simulating a hard disk; the UART module is used for simulating external interruption or local interruption; and the bus module is used for controlling information interaction among the Risc-V processing core module, the bus module, the DRAM module, the CLINT module, the PLIC module and the UART module so as to realize conflict-free communication. According to the simulator provided by the invention, the characteristics of security, memory layout control and concurrency are emphasized by using the Rust language, the memory security during the simulator operation is improved, and the robustness is strong.
Owner:SHENZHEN UNIV
Memory security detection system and method for cloud platform
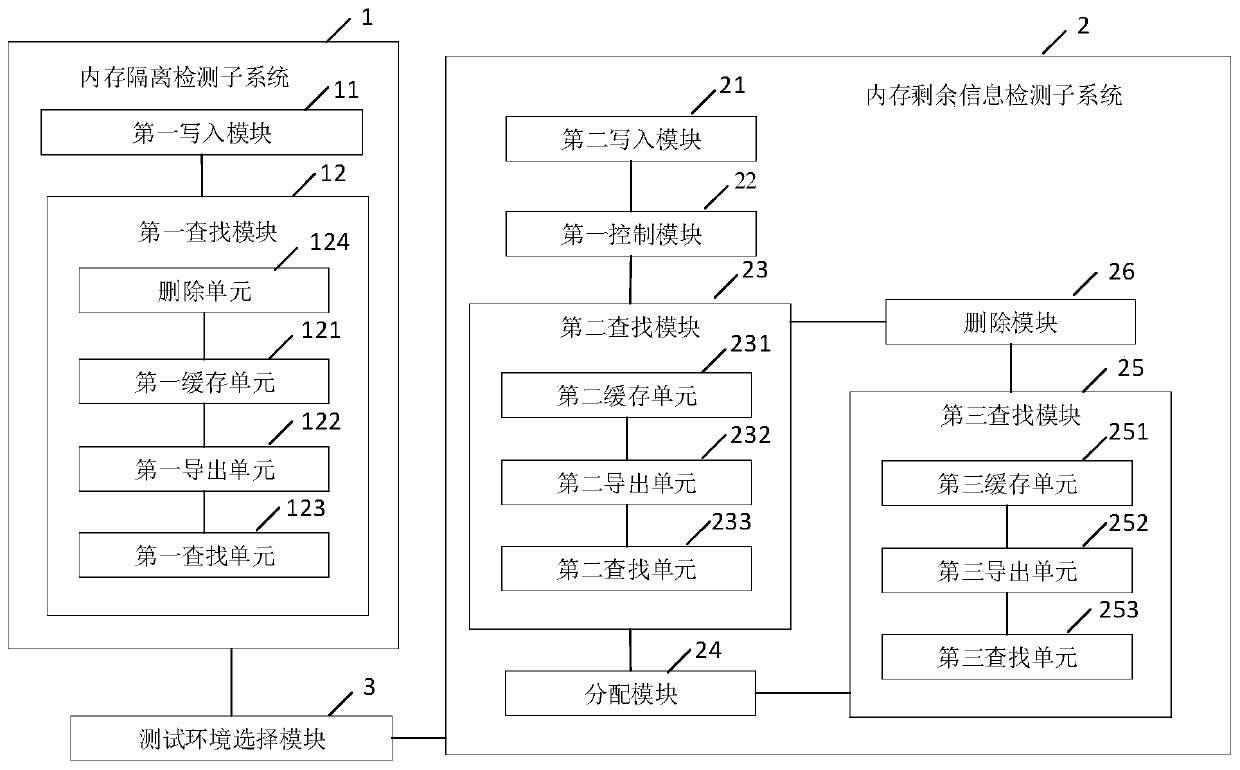
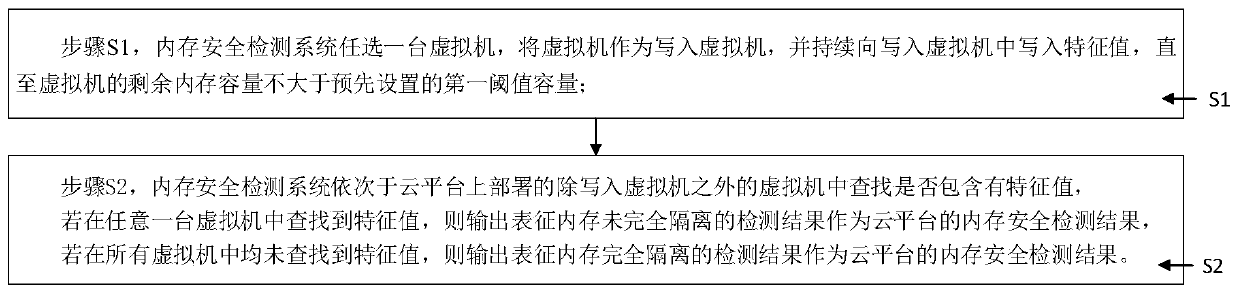
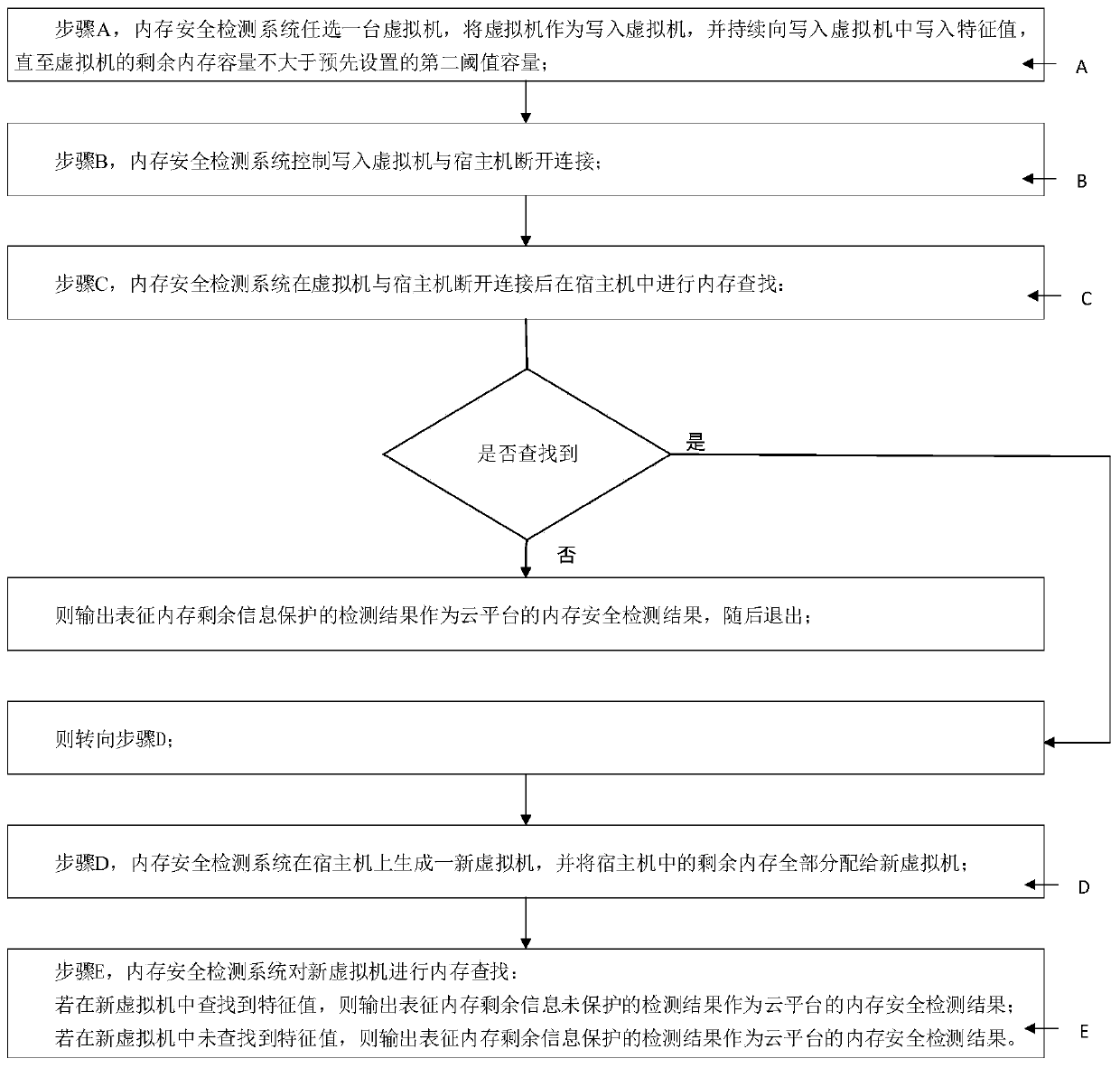
PendingCN111399988AIntuitive Memory Safety StatusIntuitive display of memory safety statusSoftware simulation/interpretation/emulationTerm memoryMemory safety
The invention discloses a memory security detection system and method for a cloud platform, and relates to the field of network security, wherein a plurality of virtual machines are deployed on the cloud platform and respectively run on the same host machine, and the host machine respectively provides memory for each virtual machine; the security detection system performs memory security detectionin a mode of writing a characteristic value into the virtual machine; the memory isolation detection subsystem comprises a first write-in module, a second write-in module, a third write-in module, afourth write-in module, a fifth write-in module, a sixth write-in module and a sixth write-in module, and the first searching module is used for searching whether the virtual machines except the virtual machines written in contain the characteristic values or not in sequence, outputting a detection result representing that the memory is not completely isolated when the characteristic values are searched in any virtual machine, and outputting a detection result representing that the memory is completely isolated when all the virtual machines are not searched. The invention has the beneficial effect of accurately and visually displaying the memory security state of the cloud platform.
Owner:THE THIRD RES INST OF MIN OF PUBLIC SECURITY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com