Detection method for security flaws in loop write-only memory of binary program
A binary program and memory writing technology, applied in computer security devices, software testing/debugging, instruments, etc., can solve the problems of huge number of paths and expensive loop unrolling, and achieve the effect of reducing computing cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
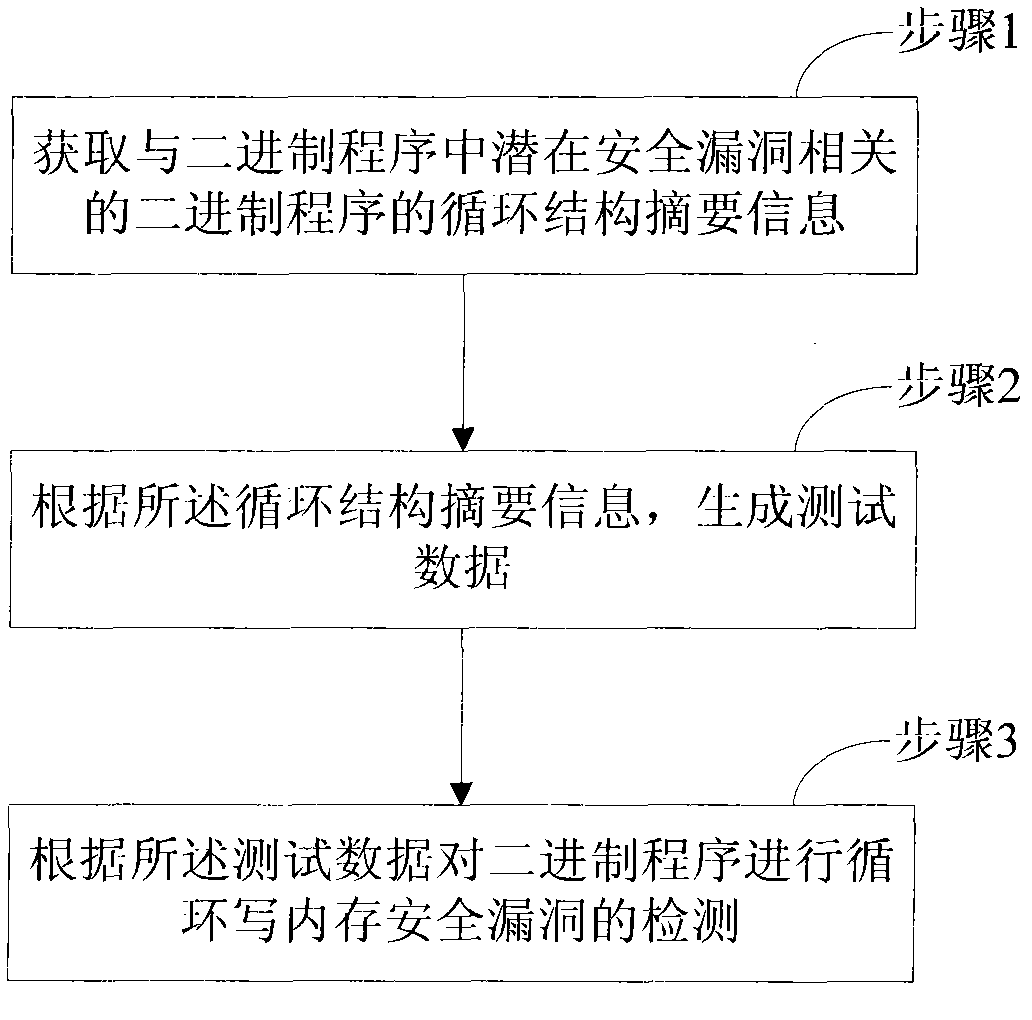
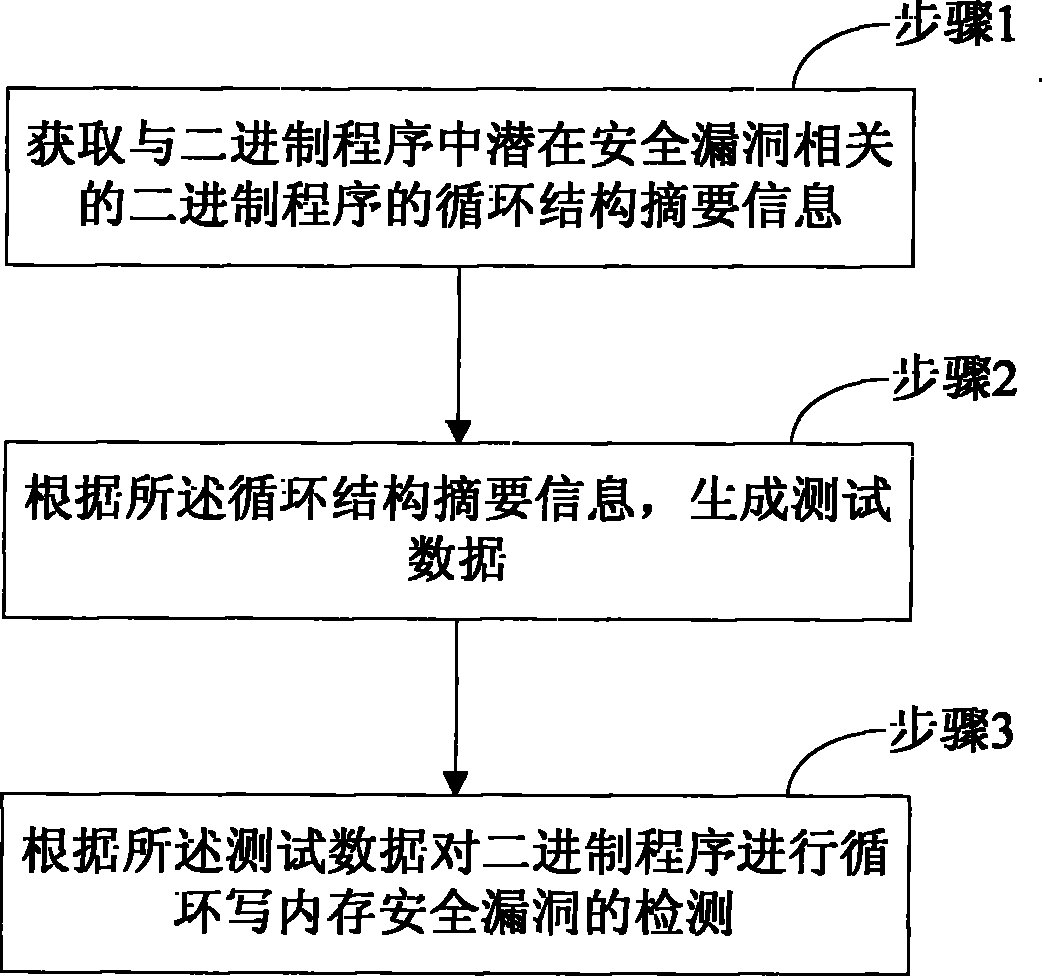
[0015] The present invention provides a detection method for a binary program loop write memory safety loophole, the implementation of which is as follows figure 1 As shown, including the following operations:
[0016] Step 1, obtaining the summary information of the loop structure of the binary program related to the potential security holes in the binary program;
[0017] Step 2, generating test data according to the summary information of the loop structure;
[0018] Step 3. According to the test data, the binary program is tested for loop write memory security vulnerabilities.
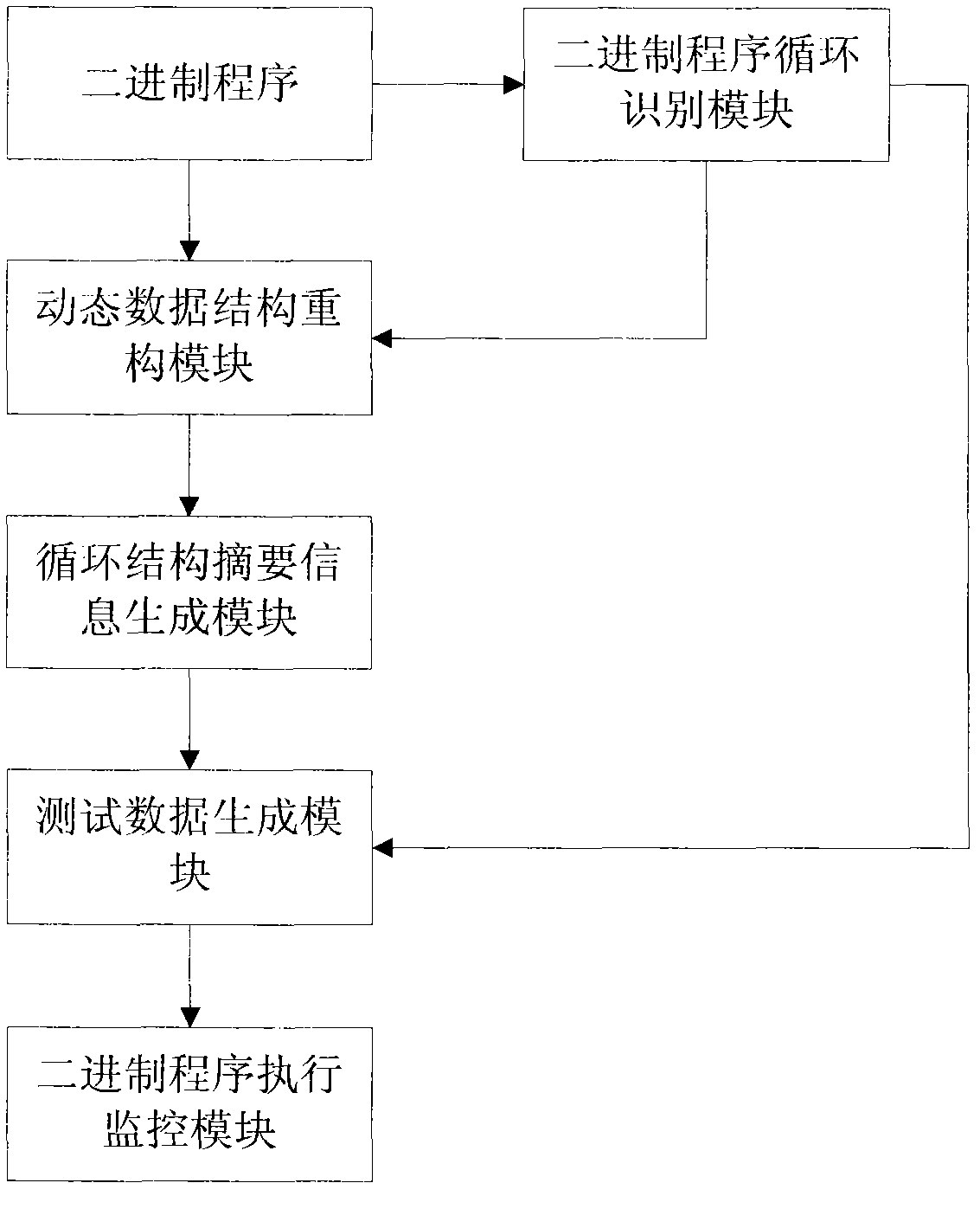
[0019] The method provided by the embodiment of the present invention does not need to traverse all paths of the loop structure of the binary program when generating the test data, but only needs to obtain the test data according to the generated summary information of the loop structure. Since the loop structure summary information is related to the potential security vulnerabilities of the bina...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com