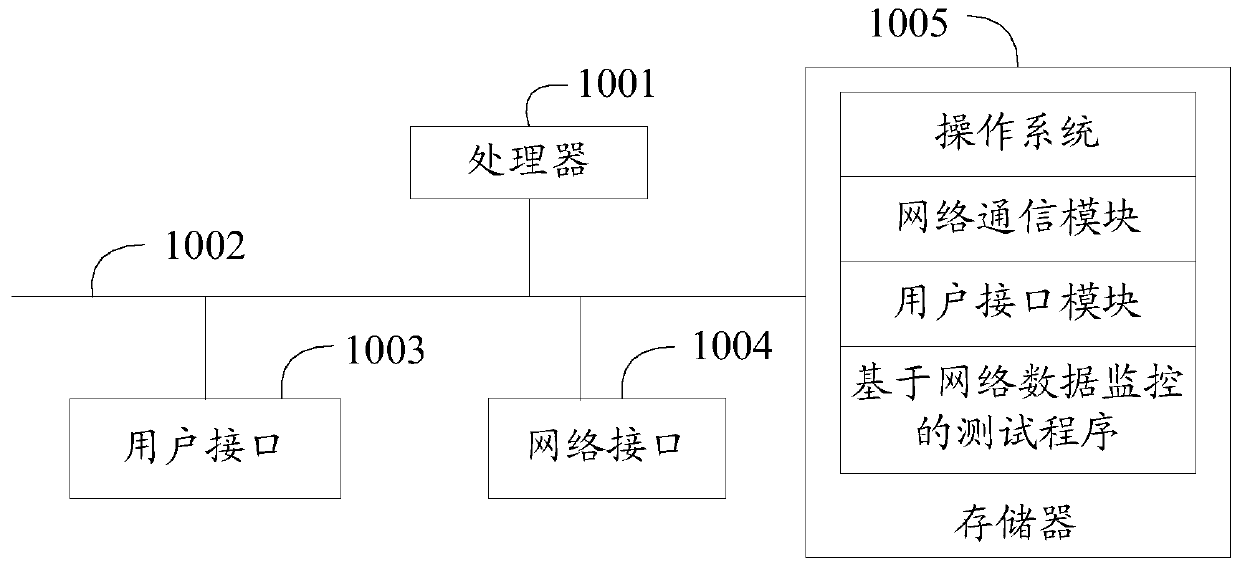
Patents
Literature
37results about How to "Implement security testing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
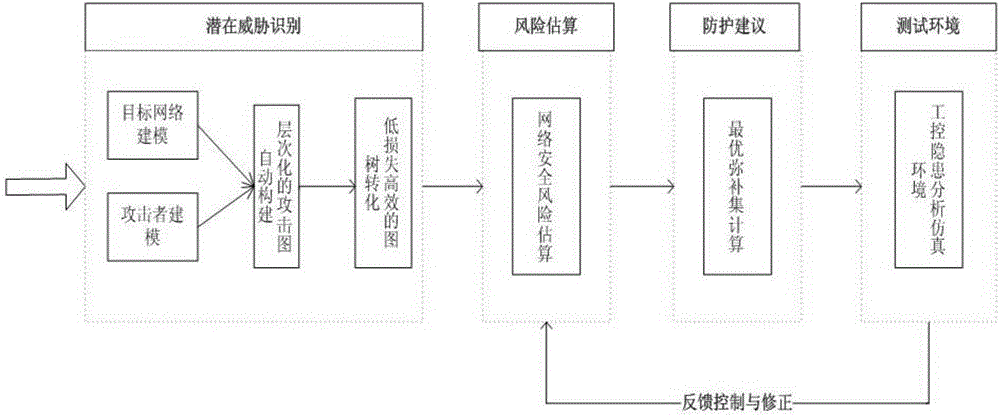
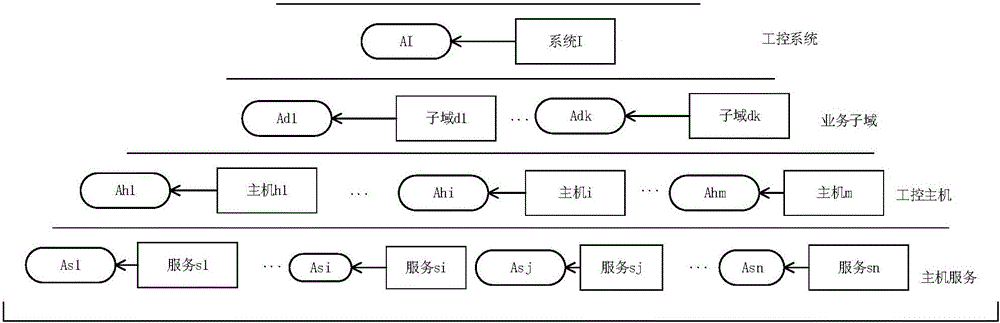
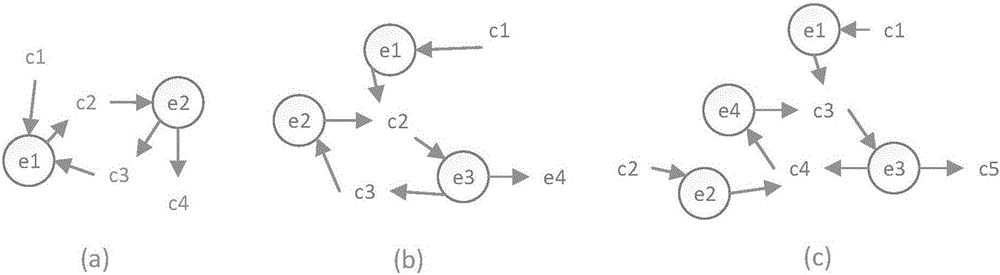
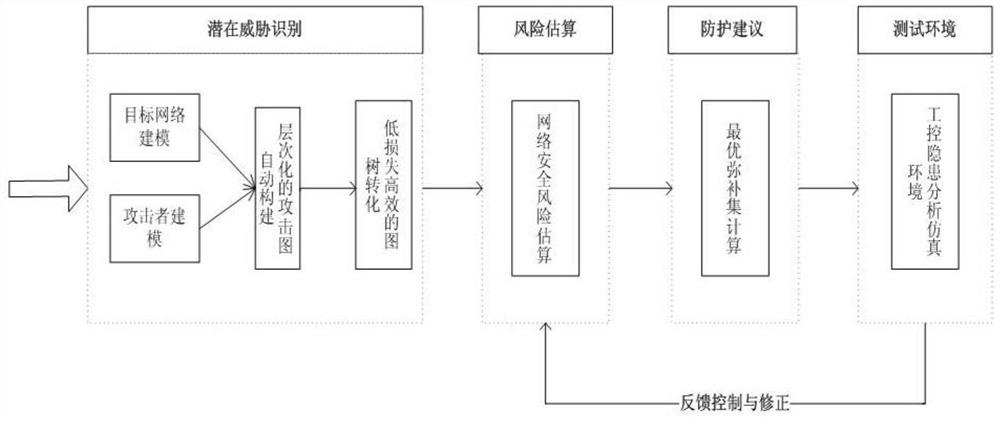
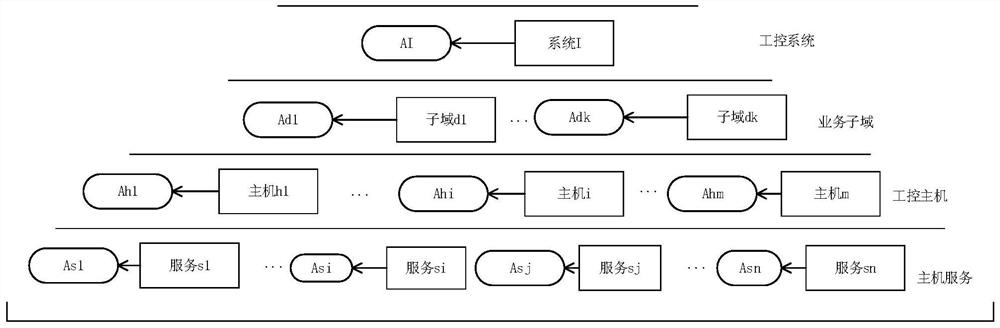
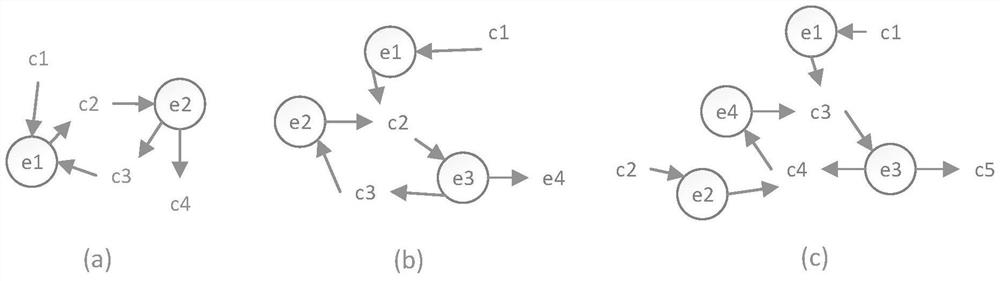
Risk assessment method suitable for industrial control system
ActiveCN106709613ARealize safety hazardDiscovery of potential safety hazardsResourcesSecurity assessmentIndex system
The invention relates to a risk assessment method suitable for an industrial control system. According to the method, modeling is performed on a target network by using a hierarchical modeling method based on the security attribute, and modeling is performed on the capacity of an attacker in the attack process by using an attack mode knowledge base; then a hierarchical attack graph is constructed according to the security model of the target network and the attacker, and the attack graph is converted into an attack tree; and then a hierarchical risk evaluation index system is constructed by using a hierarchical index analysis method, and comprehensive judgment is performed by using a layer-by-layer weighing method so that the risk assessment result of the industrial control system can be obtained. The system or equipment does not need to be offline in the analysis method, and the method is a risk assessment and management tool based on combination of qualitative and quantitative analysis of the model so that the security hidden trouble in the industrial control system can be discovered, and the security assessment level of the industrial control system can be enhanced.
Owner:INST OF INFORMATION ENG CAS
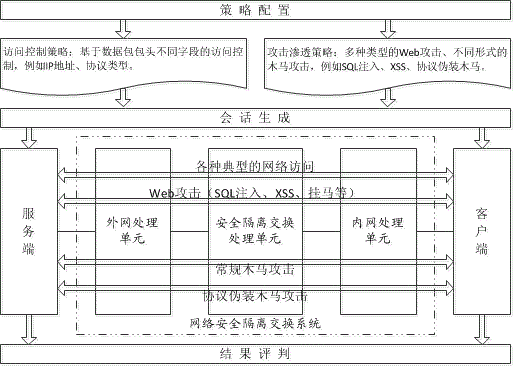
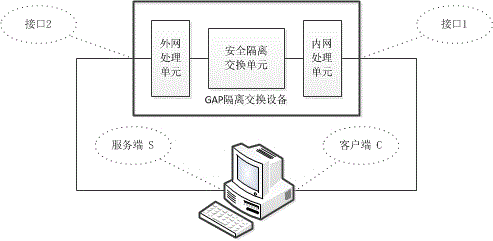
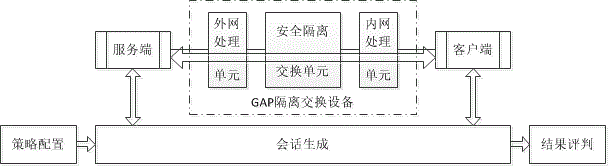
Penetration testing method for GAP isolation and exchange device
InactiveCN103916384AImplement security testingData switching networksComputer hardwareNetwork packet
The invention discloses a penetration testing method for a GAP isolation and exchange device. The method comprises the concrete steps that (a) policy configuration is tested, wherein according to the working principle, the function and the implementation mode of the tested device, applicable test cases are selected from a preset penetration testing rule base, and test environment parameters are configured; (b) a network attack session is generated, wherein an independent client program and an independent server program are established, hosts in networks at the two ends of the tested device are respectively simulated, afterwards, test plugins corresponding to the test cases are respectively called, and the test environment parameters configured in the step (a) are passed to the test plugins; the test plugins produce corresponding data packets in real time, the data packets are sent through a client or a server, and therefore the network attack session is generated; (c) test results are evaluated, wherein the test results of the test cases are evaluated according to the completion condition of the network attack session and the warning information of the tested device. By the application of the penetration testing method for the GAP isolation and exchange device, automated security testing for the GAP isolation and exchange device can be achieved.
Owner:中国人民解放军信息安全测评认证中心 +1
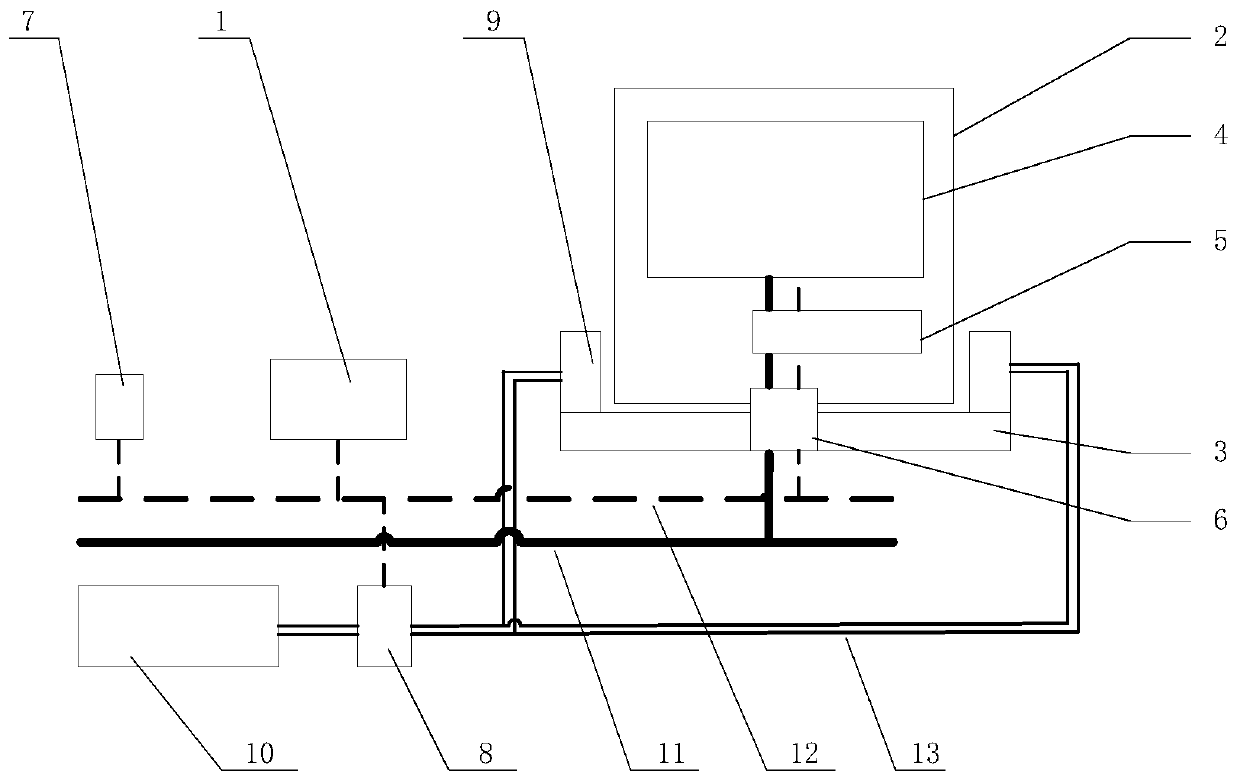
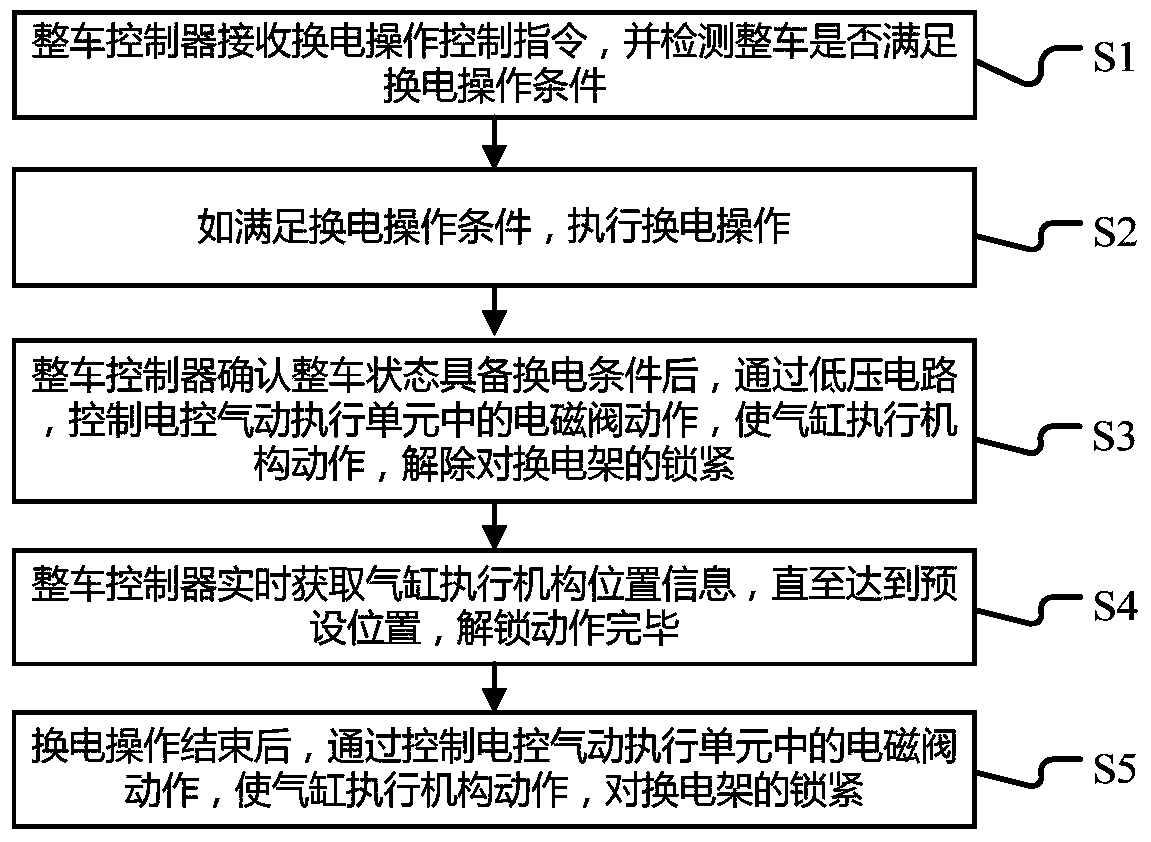
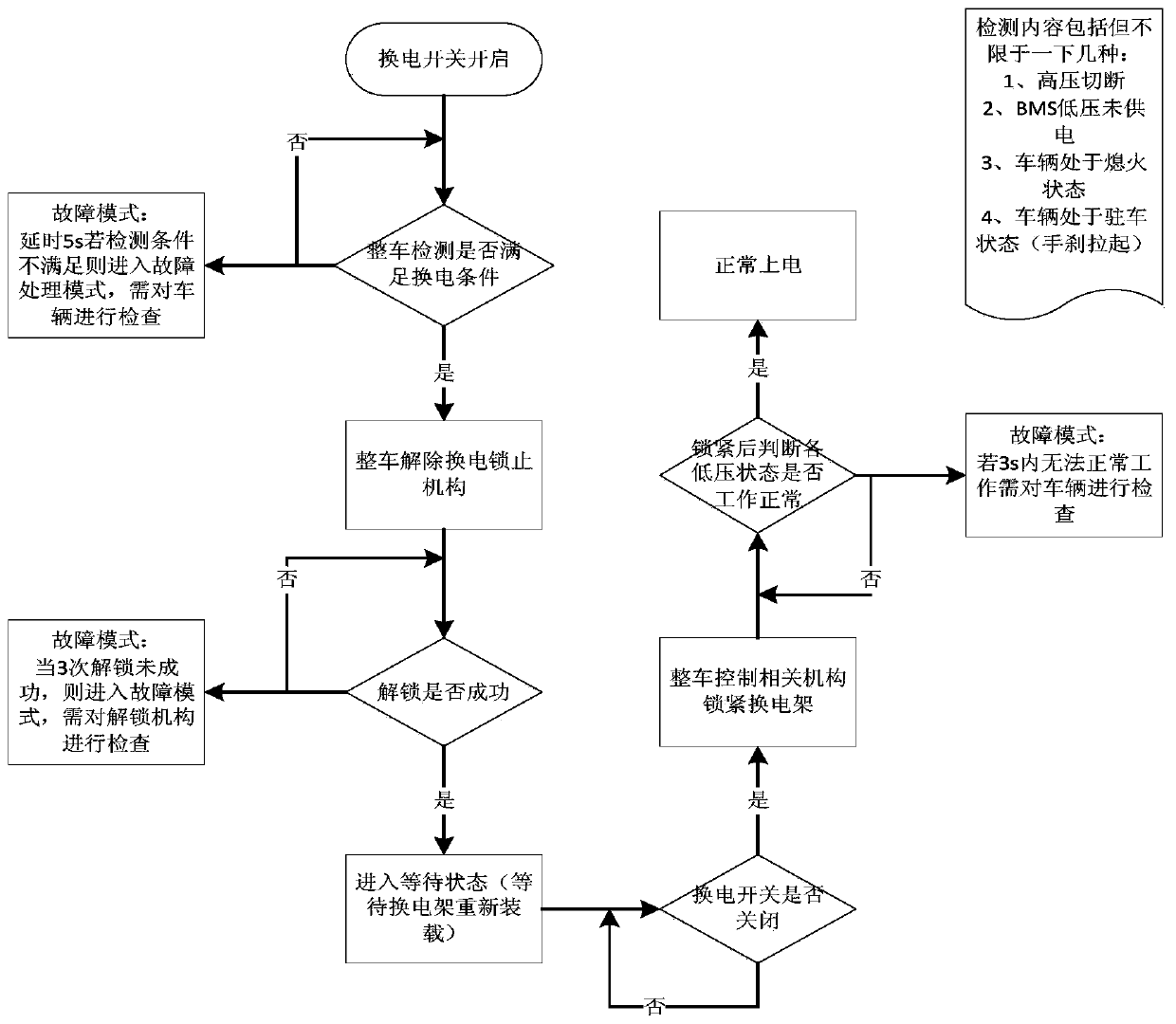
Electric-control pneumatic battery changing system and method for electric truck and load-carrying electric vehicle
PendingCN110834564AQuick battery change controlImplement security testingCharging stationsVehicular energy storageDriver/operatorElectrical battery
The invention provides an electric-control pneumatic battery changing system and method for an electric truck and a load-carrying electric vehicle. A power battery pack and a battery manager are arranged in a battery changing frame, a vehicle-mounted battery changing seat is used for bearing the battery changing frame, and the high-voltage and low-voltage electrical socket is used for connecting the battery changing frame with high-low voltage electric of a vehicle and a CAN communication network; and a vehicle control unit is used for receiving a driver control signal, a parking signal, a switching signal, a battery manager signal, a power battery main contactor status signal and the like, identifying the intention of a driver, and realizing control and monitoring of a vehicle battery changing system through a control strategy and logic judgment. The quick battery changing control of the electric truck is realized, the vehicle parking power supplementation time is favorably reduced, the vehicle battery changing efficiency is improved, the vehicle safety detection, and the reliability and the safety detection of the battery changing type electric truck in the using process before and after the battery changing operation are realized, so that the vehicle running safety is guaranteed.
Owner:SINO TRUK JINAN POWER
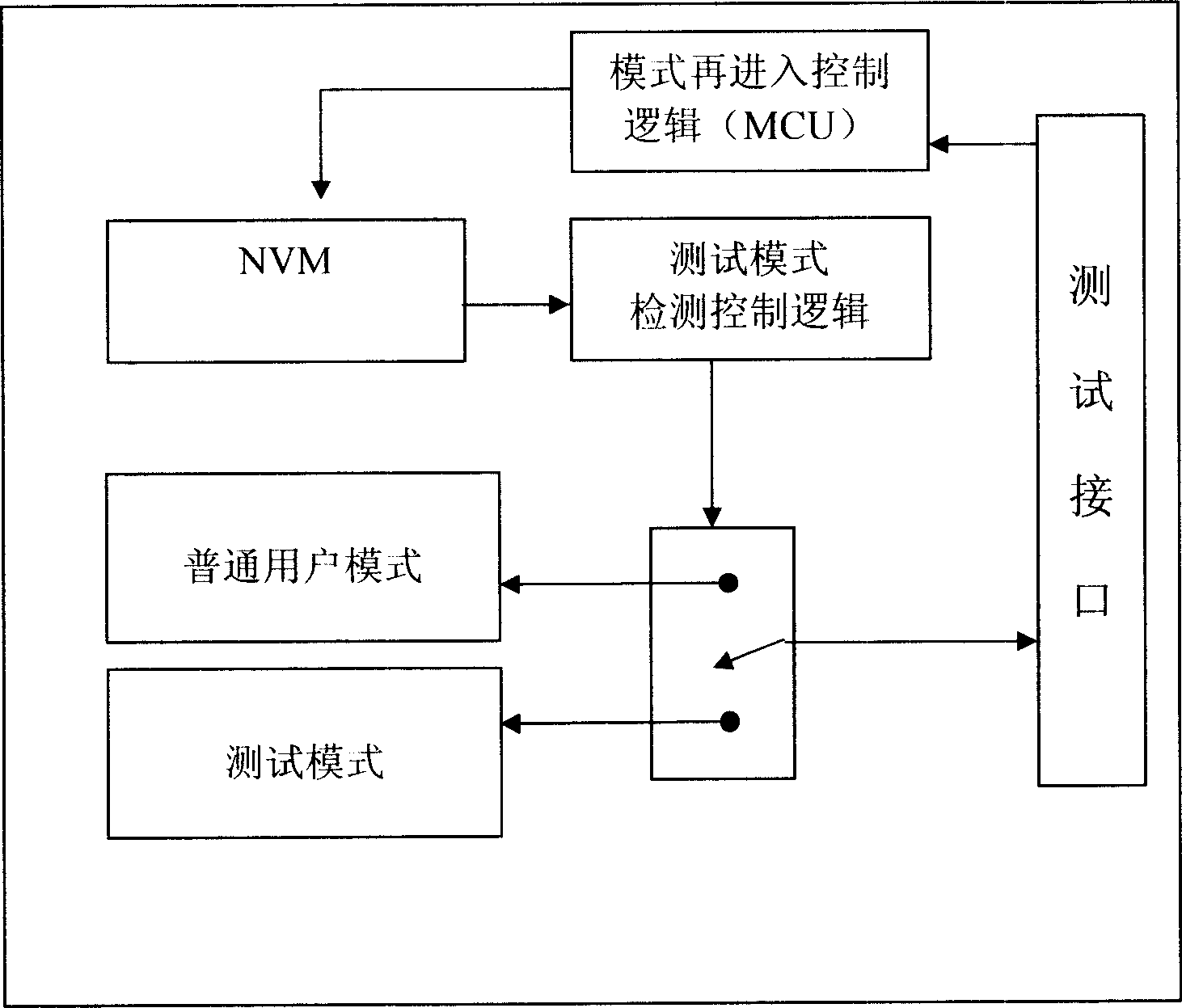
Safety detecting method for system integrated chip with built-in non-volatile memory
InactiveCN1979686AImplement access testingImplement security testingSemiconductor/solid-state device testing/measurementElectronic circuit testingProcessing InstructionComputer module
The invention discloses a safe test method for an SOC (system on chip) embedded with nonvolatile memory (NVM), detecting data at embedded NVM specific addresses by a test mode detecting logic so as to implement test mode switching, where the embedded NVM specific addresses can not be accessed in user mode, and when the test is finished, it writes the appointed mode setting data at the embedded NVM specific addresses, and after detecting the data, a test mode logic circuit of the SOC intermediately switches the chip to the user mode to cut off test circuits of internal modules so as to make the chip enter into common user mode, thus implementing access inhibition to the internal modules. For reentering into the chip test mode, the invention also erases the mode setting data in the NVM by a special microprocessing instruction and simultaneously erases all data in the NVM so as to protect data.
Owner:SHANGHAI HUA HONG NEC ELECTRONICS
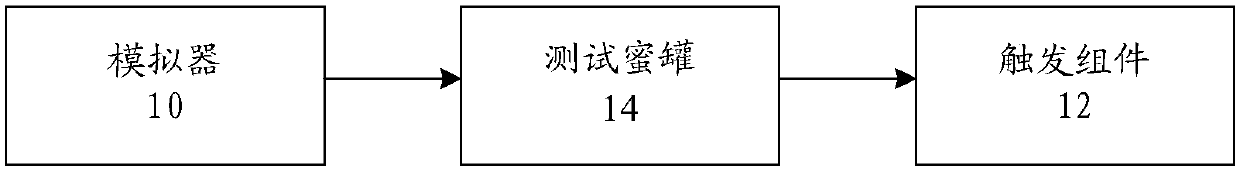
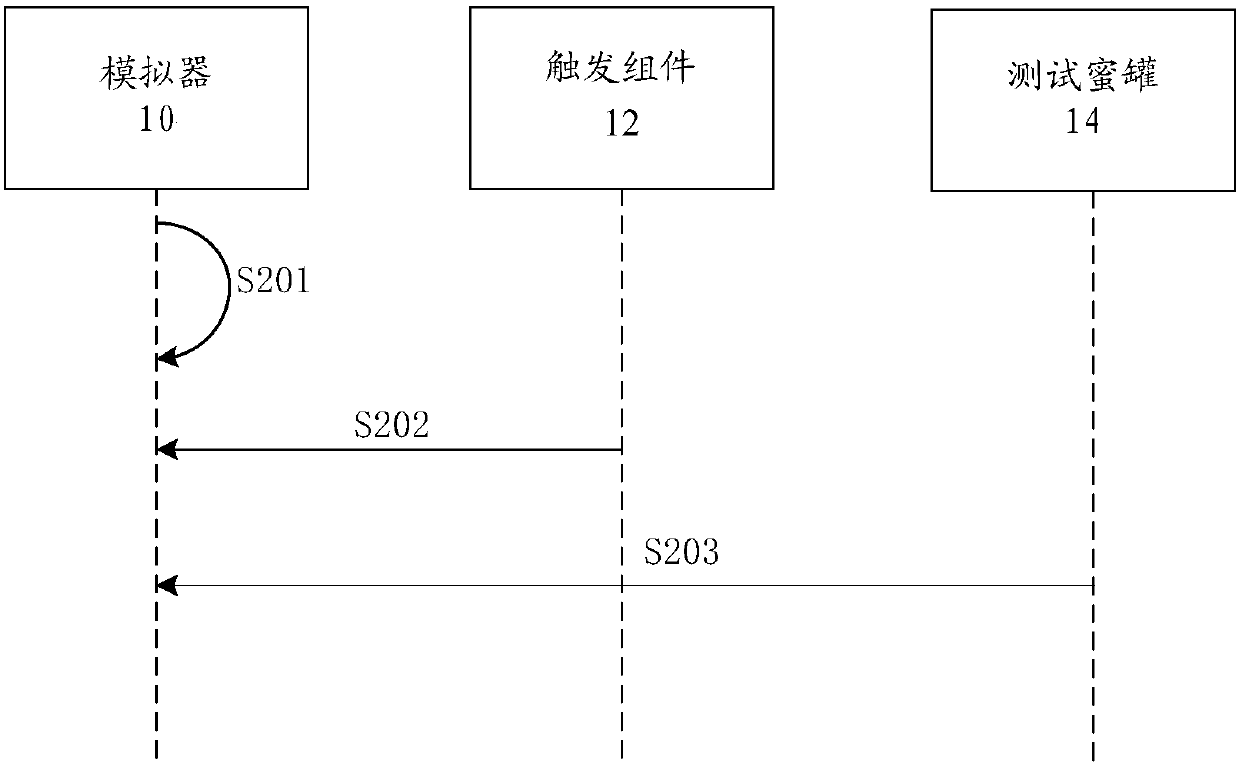
Sample security test method and device and equipment
InactiveCN107644161AImplement security testingPlatform integrity maintainanceTest sampleSafety testing
The invention discloses a sample security test method and device and equipment. The method comprises the steps that a pre-constructed honey pot system is acquired, a to-be-tested sample is run in a running environment determined by the honey pot system; the honey pot system is triggered to send test data to the running environment running the sample; and if sample interception test data is monitored and malicious operation is performed on the test data, it is determined that the sample has a security vulnerability, wherein the malicious operation comprises the behavior of executing Trojan horse operation on the test data. Through the sample security test method and device and the equipment, the technical problem that viruses in the prior art cannot be discovered in time due to ceaseless upgrade and variation is solved.
Owner:ALIBABA GRP HLDG LTD
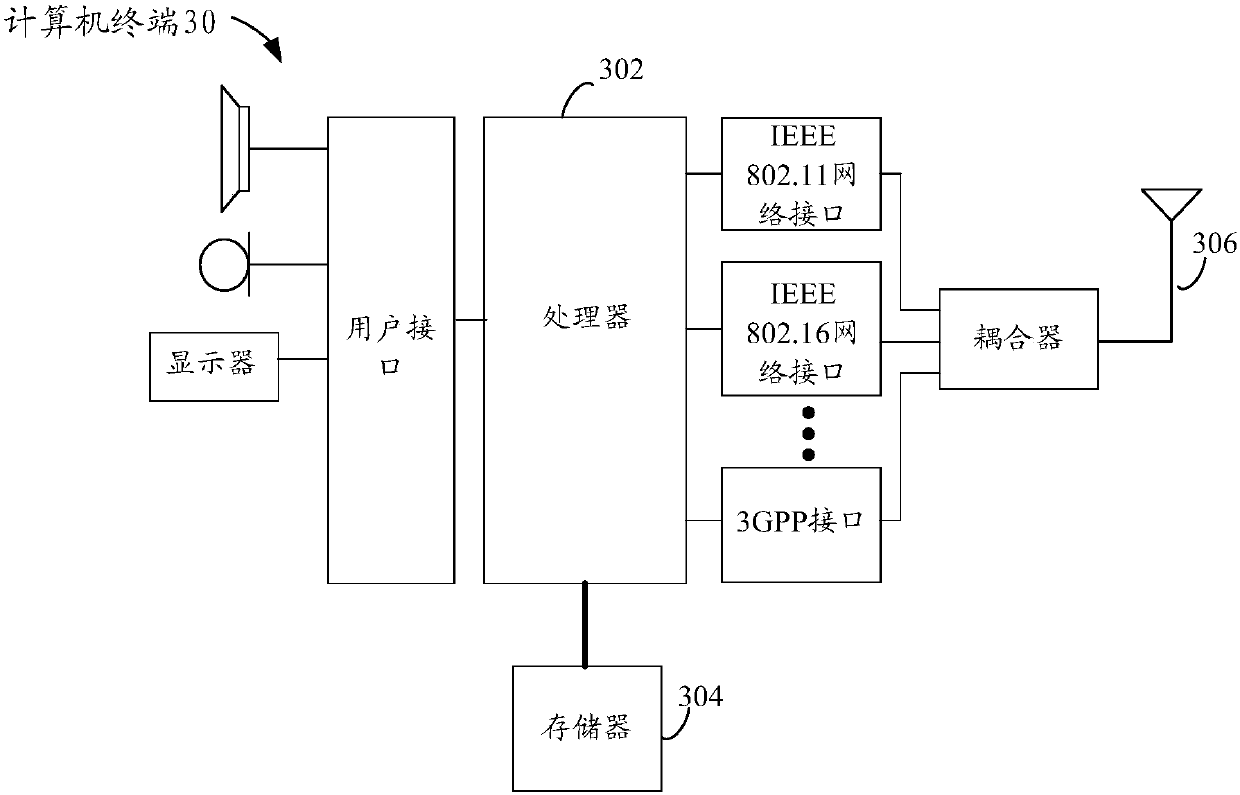
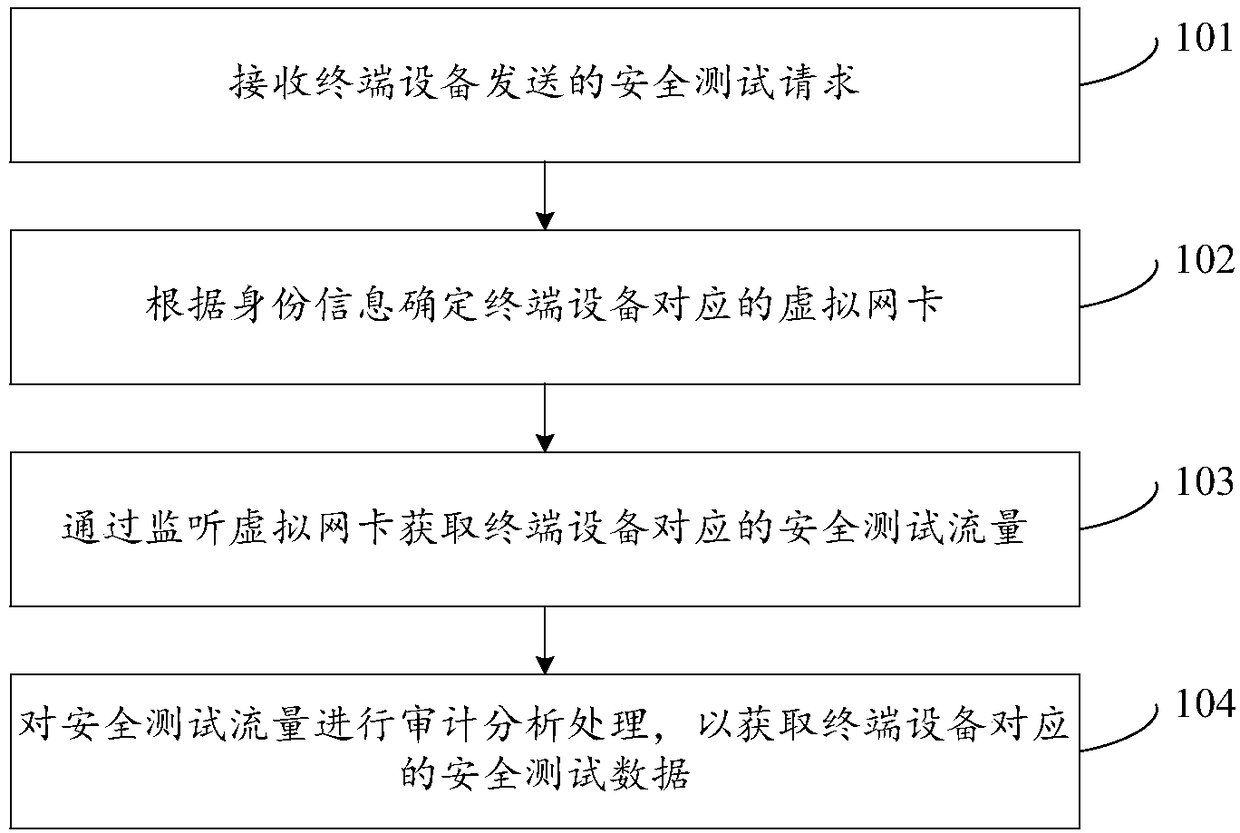
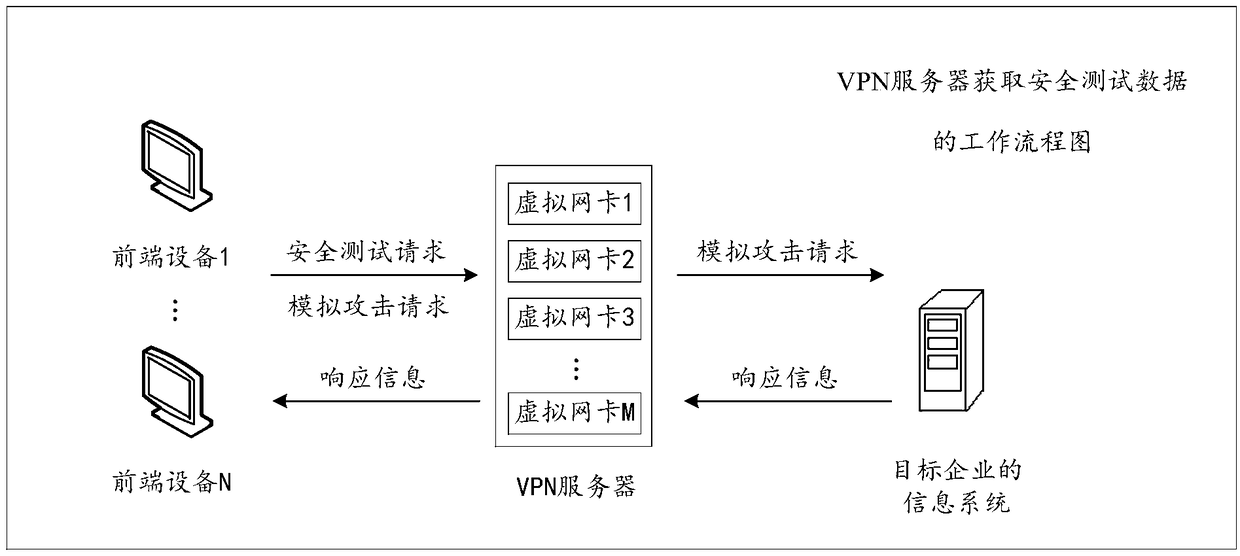
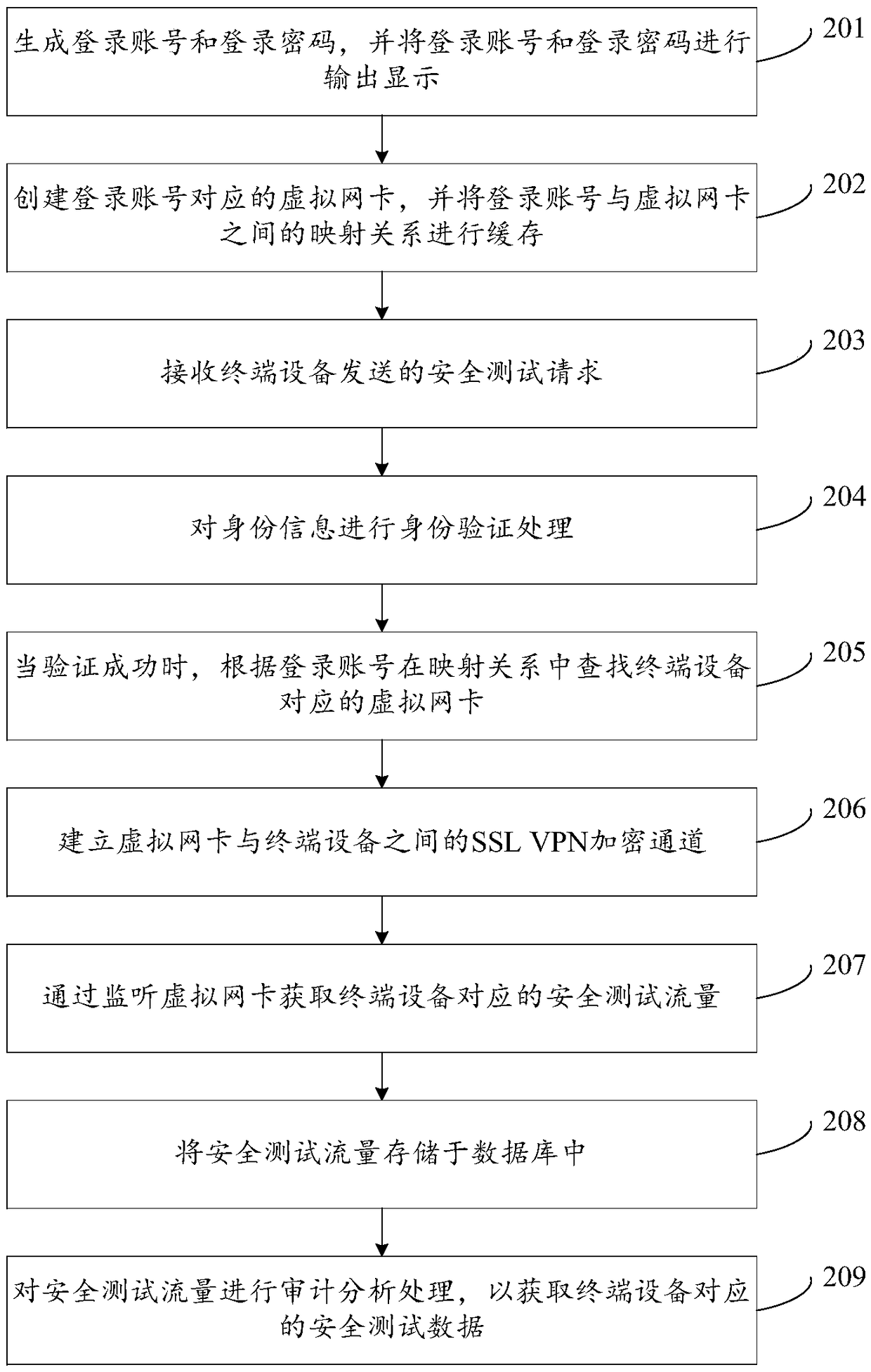
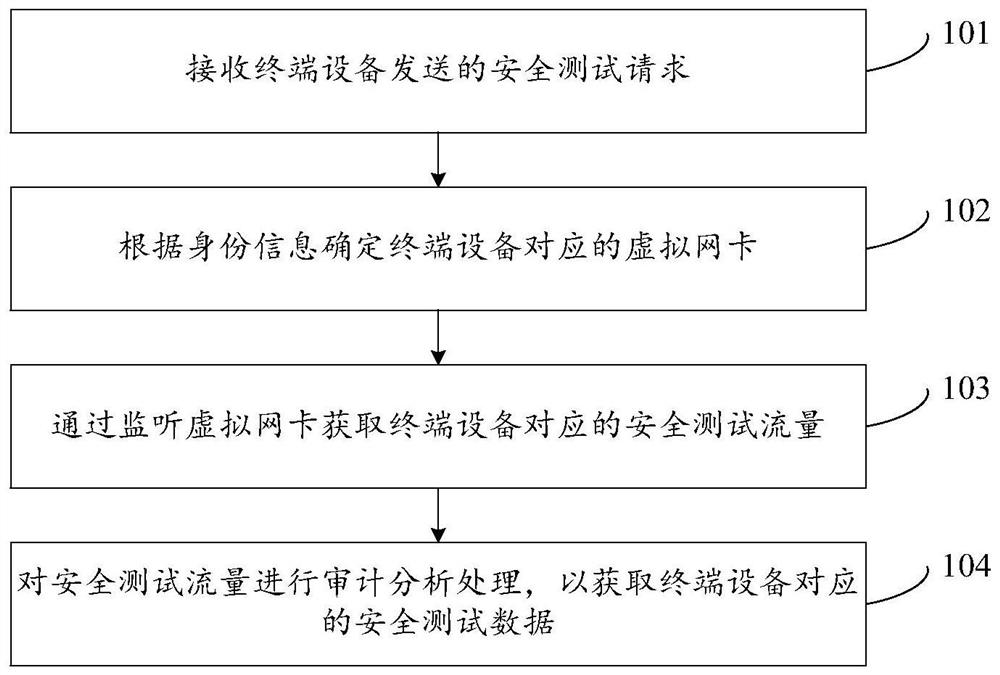
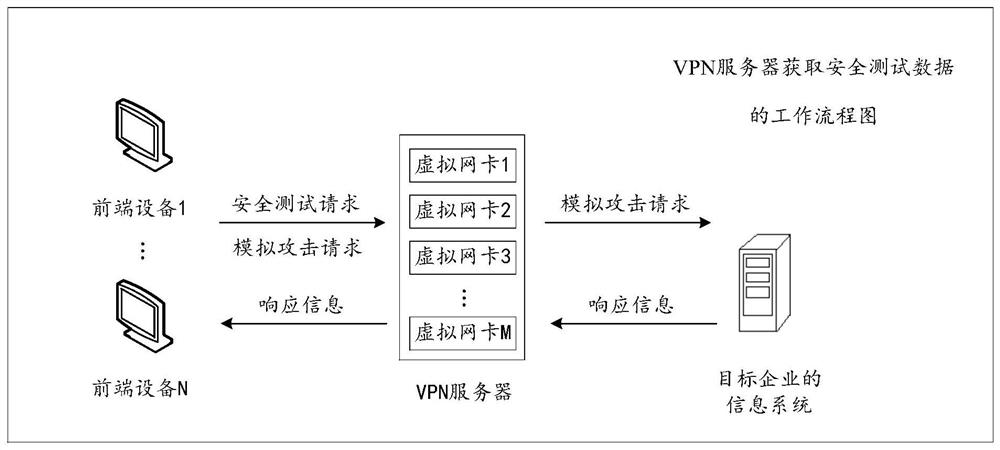
Acquisition and audit analysis method and device for safety test data
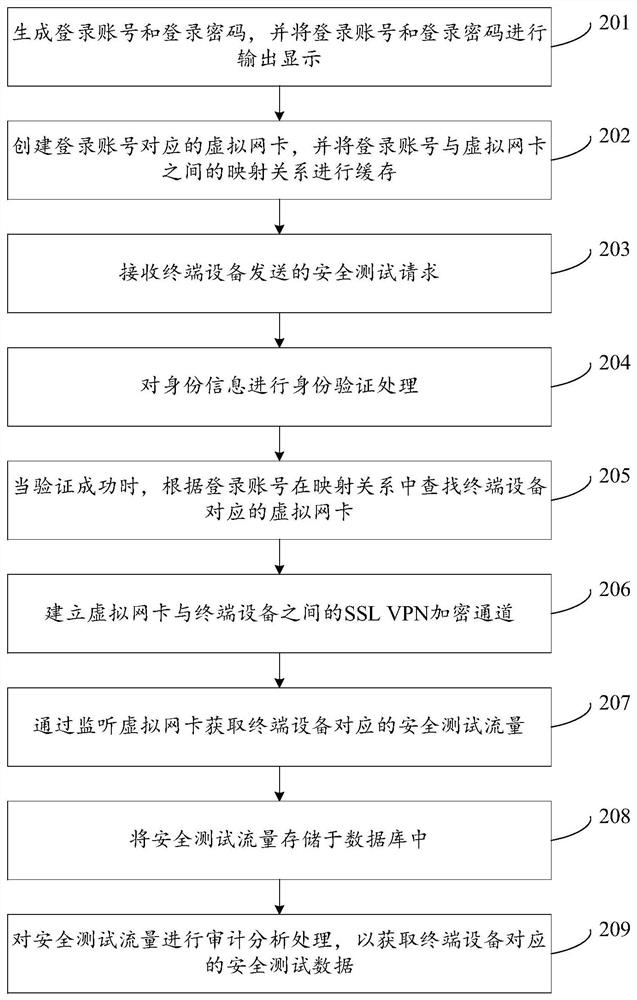
The invention discloses an acquisition and audit analysis method and device for safety test data, relates to the technical field of the internet, and improves safety of a process of carrying out a safety test on an information system of an enterprise. The method disclosed by the invention comprises the steps of: receiving a safety test request sent by terminal equipment, wherein the safety test request comprises identity information corresponding to the terminal equipment; according to the identity information, determining a virtual network card corresponding to the terminal equipment; by monitoring the virtual network card, acquiring safety test traffic corresponding to the terminal equipment; and carrying out audit analysis processing on the safety test traffic to acquire safety test data corresponding to the terminal equipment, wherein the safety test data is used for quantizing the safety test process corresponding to the terminal equipment and auditing a high-risk behavior operation corresponding to the terminal equipment. The acquisition and audit analysis method and device are applicable to the process that a third-party tester carries out the safety test on the informationsystem of the enterprise.
Owner:北京中金安服科技有限公司
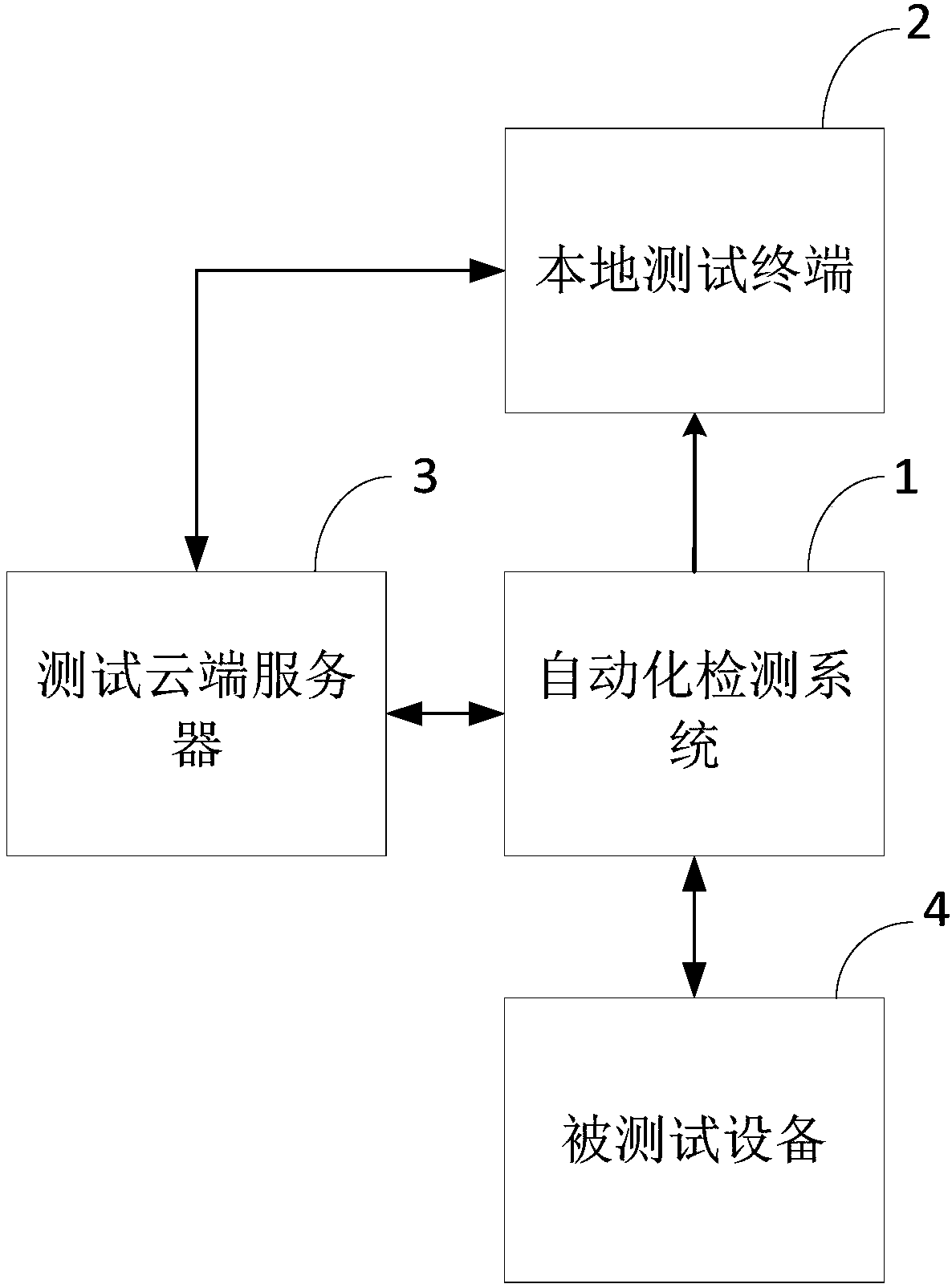
Vehicle information safety automated testing system and method
ActiveCN108415398AImplement security testingThreat fulfillmentElectric testing/monitoringTransmissionTest facilityTest report
The present invention provides a vehicle information safety automated testing system. The system comprises: an automated detection system connected with a tested device and configured to perform information safety testing of the tested device and upload test result data; a local test terminal configured to display a human-computer interaction interface; and a test cloud server configured to searchthe information safety test data flow corresponding to a test scene to analyze the received test result data, determine the information safety condition of the tested device and generate a test report. The testing method comprises the steps of: selecting a test scene; sending the information safety test data flow; performing vehicle information safety test of the tested device, and performing feedback of the test result data; and determining the vehicle information safety condition to generate a test analysis report. Compared to the prior art, a plurality of vehicle information safety test isemployed to achieve vehicle information safety test and reduce the threats caused by the safety risks.
Owner:上海辇联网络科技有限公司
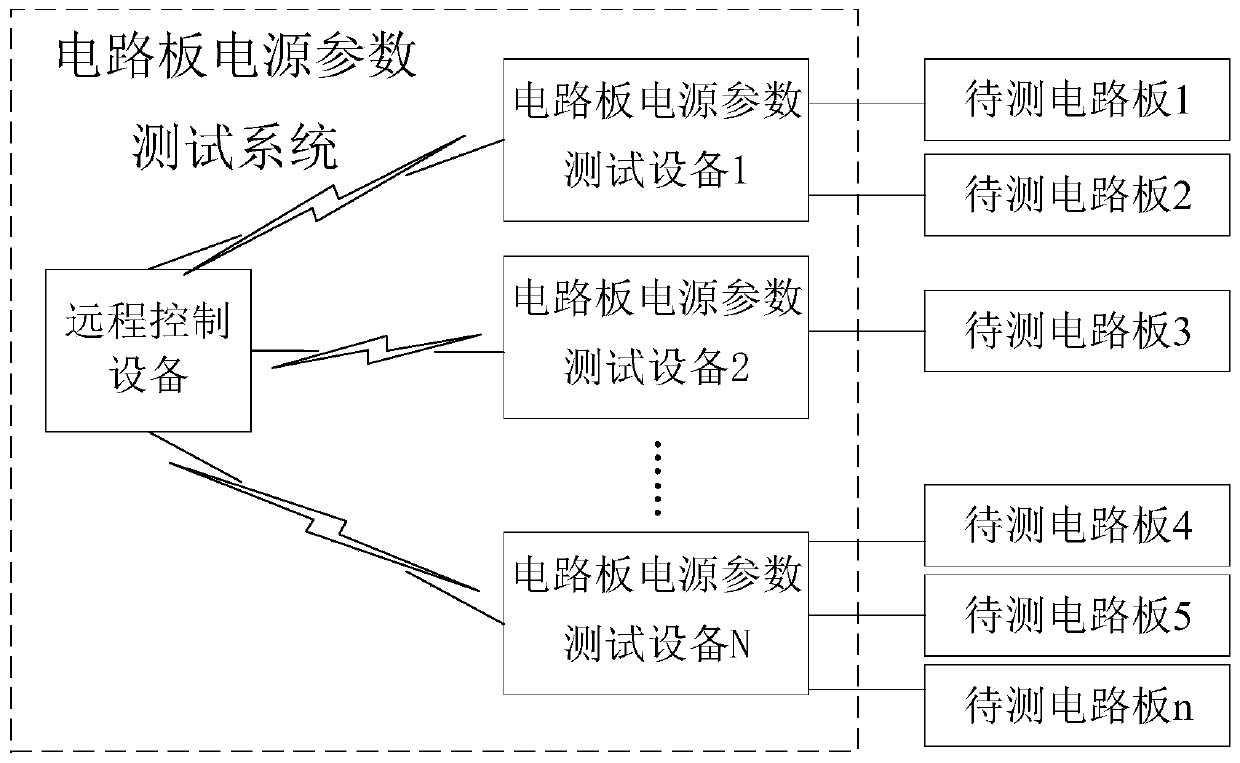
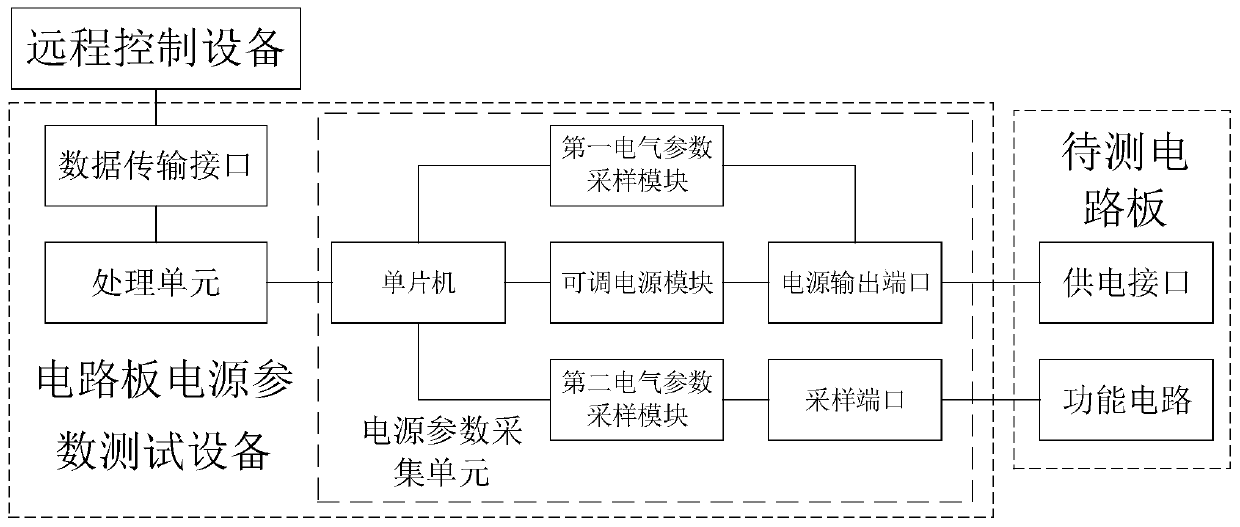
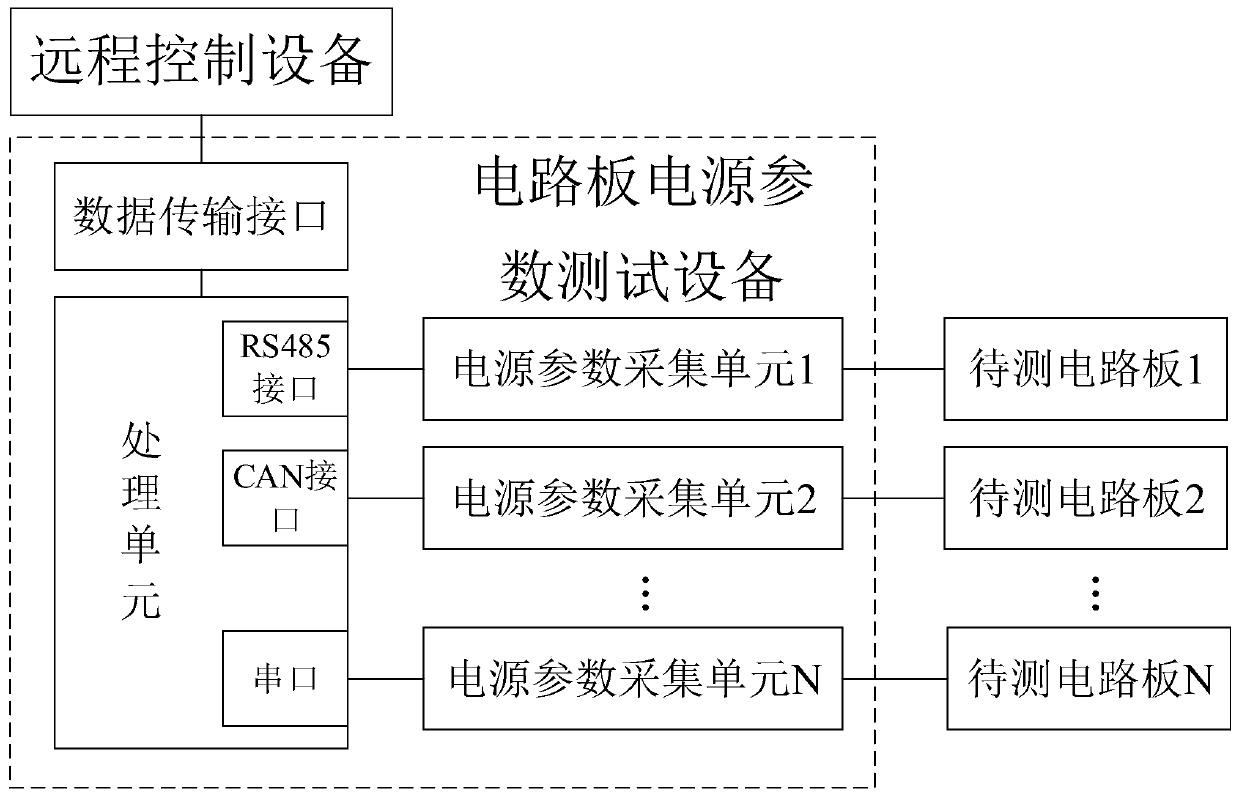
Circuit board power supply parameter test system and method
ActiveCN111142008AImplement automated testingMeasurement limitPrinted circuit testingTest efficiencyRemote control
The invention relates to a circuit board power supply parameter test system and method. In the circuit board power supply parameter test system, a remote control device can be connected with a plurality of circuit board power supply parameter test devices through a network; the circuit board power supply parameter testing device can test at least one circuit board to be tested. The processing unitis connected with the remote control device and is respectively connected with a power supply interface and a functional circuit of the circuit board to be tested through a power supply parameter acquisition unit; based on the above structure, the processing unit can obtain configuration parameters and test parameters transmitted by the remote control device, and then configure the power supply parameter acquisition unit, thereby realizing the automatic test of the power supply parameters of the circuit board to be tested, and improving the test efficiency and accuracy. Based on this, the number of the circuit board power supply parameter test devices can be flexibly set according to the number and requirements of the circuit boards to be tested, multi-channel remote testing is realized,the efficiency of remote control is improved, and the measurement number of the circuit boards to be tested is prevented from being limited by the number of device ports.
Owner:广州京信通信科技有限公司
Proximity switch testing arrangement in high temperature environment
ActiveCN105319498AEasy and safe operationImplement security testingCircuit interrupters testingMicrometerTest fixture
The present invention discloses a proximity switch testing arrangement in a high temperature environment. The proximity switch testing arrangement comprises a high temperature test mechanism and a normal temperature operation mechanism, the high temperature test mechanism includes a proximity switch, a proximity switch installing support, an induction sheet mobile device support and the like, and the normal temperature operation mechanism main includes a displacement regulation support, a micrometer and the like. The proximity switch installing support is provided with a proximity switch and the induction sheet capable of moving and rebounding under the action of tension; the displacement regulation support is provided with the micrometer with adjustable displacement; and one end of a steel wire is connected with the induction sheet in a high temperature oven, and the other end of the steel wire is connected with the micrometer. According to the invention, the safety test of a proximity switch may be performed in a high temperature environment; in the high temperature environment, the induction distance and the induction diameter of the proximity switch is adjustable; the proximity switch testing arrangement in the high temperature environment is applicable to the tests of proximity switches with different types in the high temperature environment, and is convenient for testing induction sheets with different materials; and the separation of the high temperature area and the normal temperature area is beneficial for safe operation.
Owner:BC P INC CHINA NAT PETROLEUM CORP +1
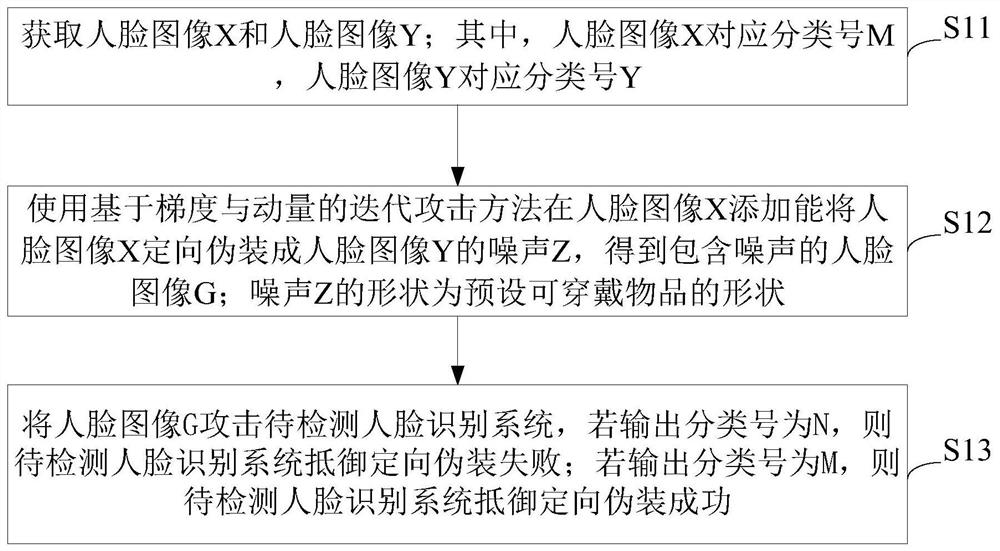
Method and system for detecting camouflage attack resistance of face recognition system
PendingCN112507811AImplement security testingTimely detection of face recognition detection vulnerabilitiesCharacter and pattern recognitionMedicineRadiology
The invention discloses a method and a system for detecting camouflage attack resistance of a face recognition system. The method comprises the following steps that a face image X and a face image Y are acquired; wherein the face image X corresponds to a classification number M, and the face image Y corresponds to a classification number N; noise Z is added to the face image X by using an iterative attack method based on gradient and momentum, the noise Z is masked into the shape of a wearable article, and a face image G containing noise is obtained; the face image G attacks the to-be-detectedface recognition system, and if the output classification number is N, it is indicated that the to-be-detected face recognition system fails to resist the directional camouflage attack; and if the output classification number is M, it is indicated that the to-be-detected face recognition system successfully resists the camouflage attack. The face recognition system is attacked by using the generated wearable decorative article with the camouflage characteristic, whether the face recognition system has the capacity of resisting the camouflage countermeasure sample can be detected, and the safety of the face recognition system is evaluated.
Owner:GUANGZHOU UNIVERSITY +1
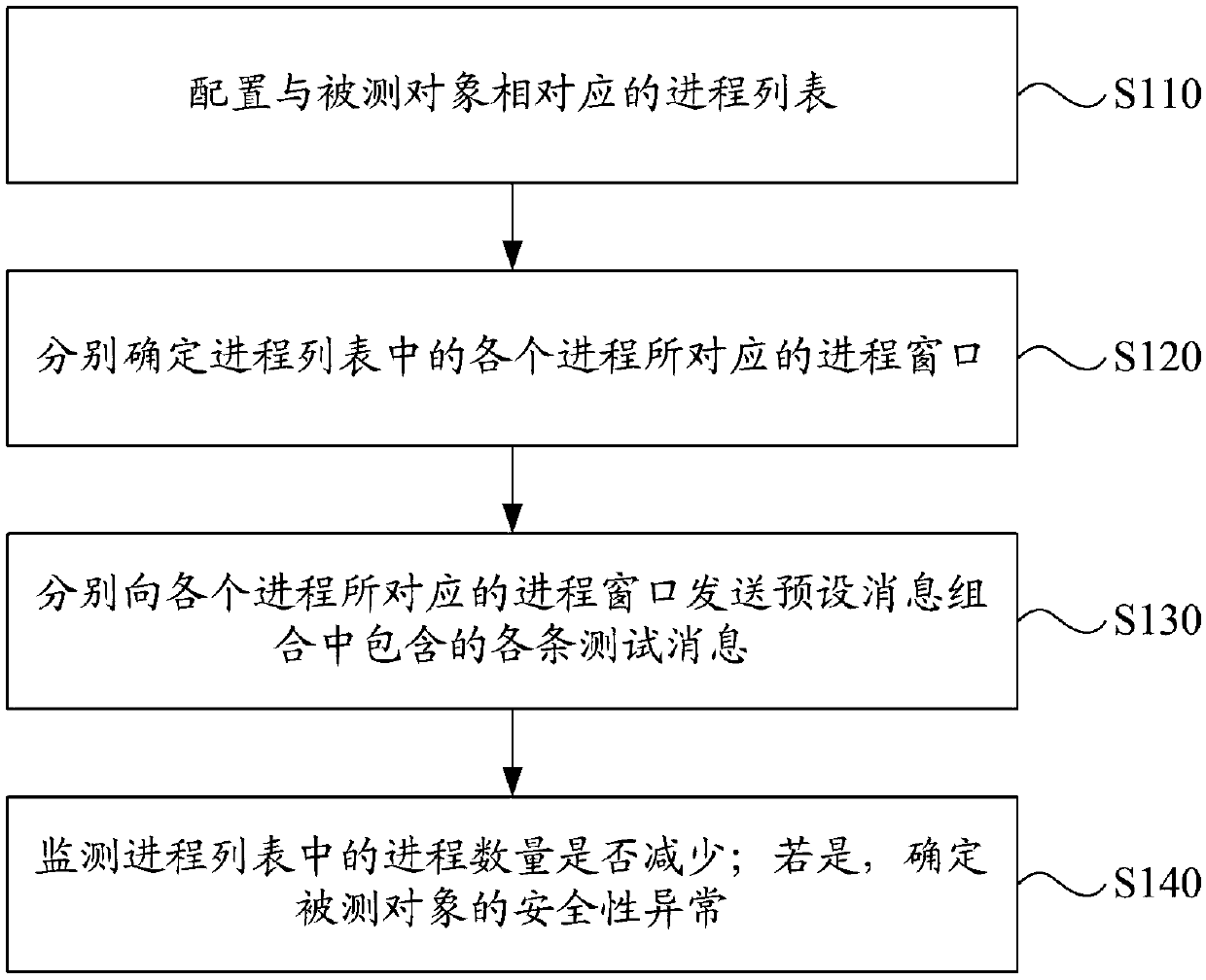
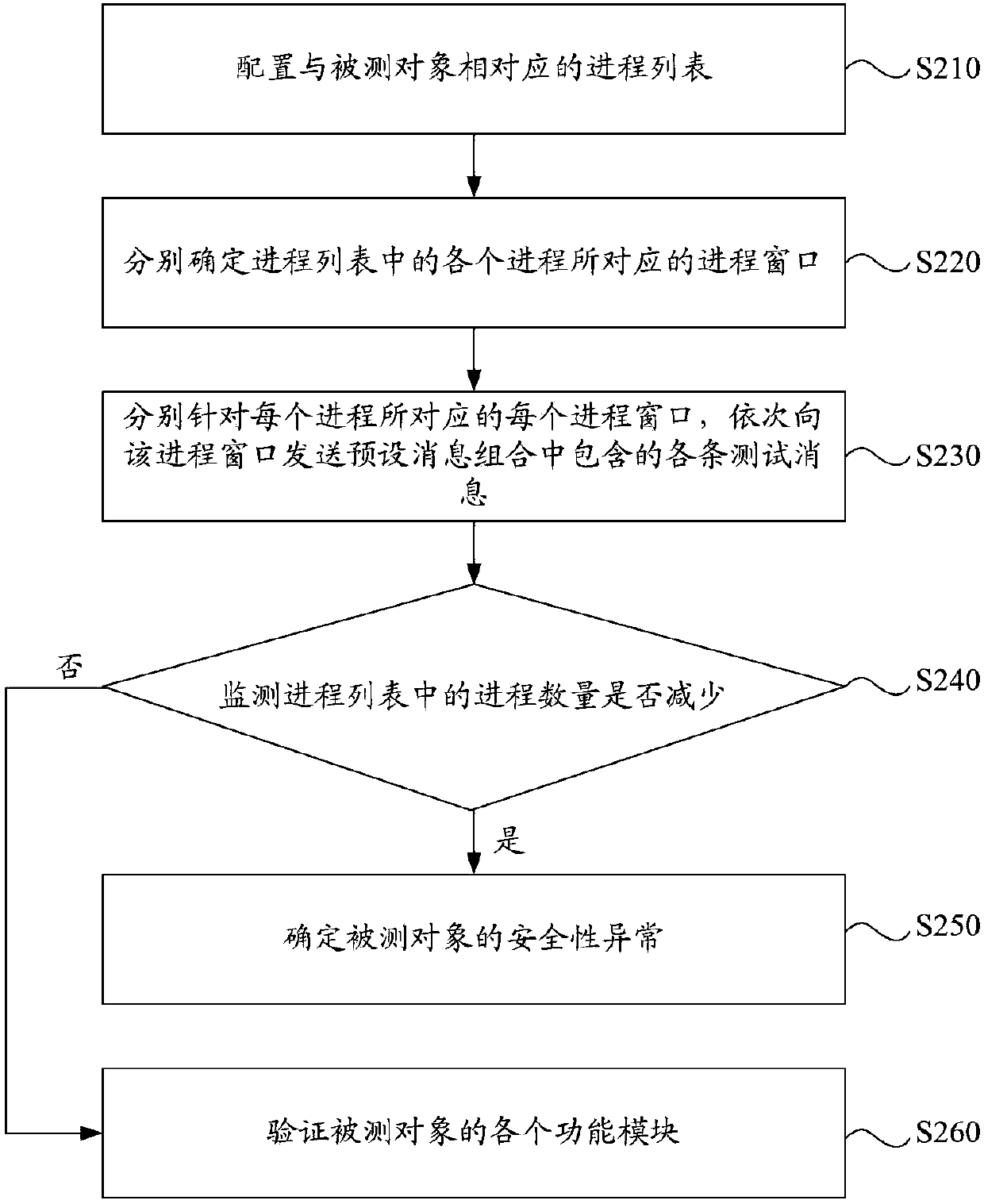
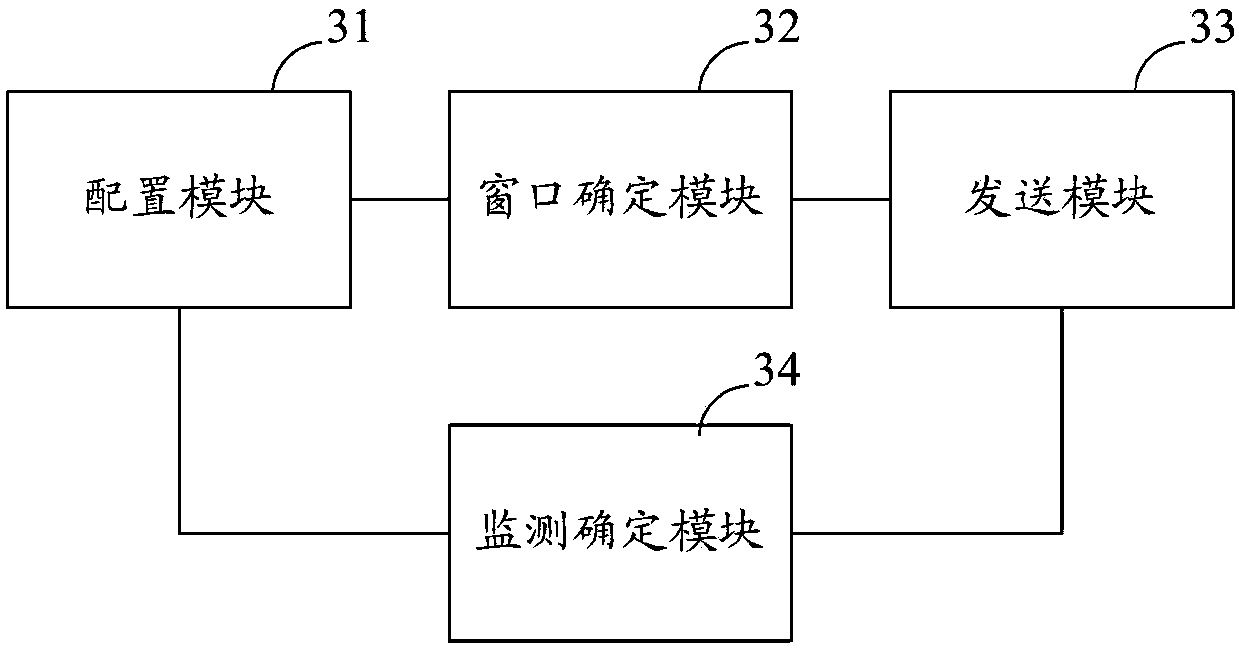
Safety testing method and device, electronic device and computer storage medium
ActiveCN107590389AFull accessComplete acquisitionSoftware testing/debuggingPlatform integrity maintainanceComputer hardwareSafety testing
The invention discloses a safety testing method and device, an electronic device and a computer storage medium. The safety testing method comprises the steps that a process list corresponding to a tested object is configured; process windows corresponding to processes in the process list are respectively determined; testing messages included in a preset message combination are sent to the processwindows corresponding to the processes; whether the number of the processes in the process list is decreased or not is monitored; if yes, the safety abnormity of the tested object is determined. By adopting the scheme, the safety vulnerability coverage rate is higher, the safety vulnerabilities of products can be comprehensively obtained, and product safety testing can be achieved. In addition, product safety testing results have lower dependency on the testing level of testing technicians.
Owner:BEIJING QIHOO TECH CO LTD
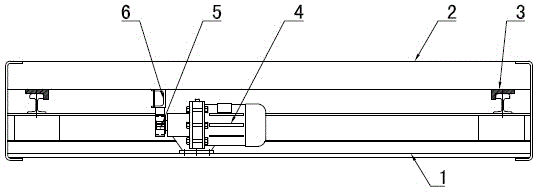
Fixed washboard type agricultural machinery braking performance detector
ActiveCN103604613AImplement security testingBest detection positionVehicle testingAgricultural engineeringMechanical property
The invention discloses a fixed washboard type agricultural machinery braking performance detector and belongs to the field of agricultural machinery performance detection devices. The fixed washboard type agricultural machinery braking performance detector comprises a fixed washboard table body (1) and a washboard detection table (2) arranged above the fixed washboard table body (1) in an embedded mode. The fixed washboard type agricultural machinery braking performance detector is characterized in that the lower portion of the washboard detection table (2) is installed above the fixed washboard table body (1) in a supporting mode through a slide (3), a driving device is installed in the gap between the fixed washboard table body (1) and the washboard detection table (2), an infrared sensor (7) capable of detecting a tire and transmitting signals is arranged on the upper portion of the washboard detection table (2), and the driving device receives the signals of the infrared sensor (7) to drive the washboard detection table (2) to slide left and right along the slide (3). The fixed washboard type agricultural machinery braking performance detector is wide in application range, easy to operate, and capable of automatically adjusting the distance between detection tables.
Owner:SHANDONG KEDA COMP APPL INST
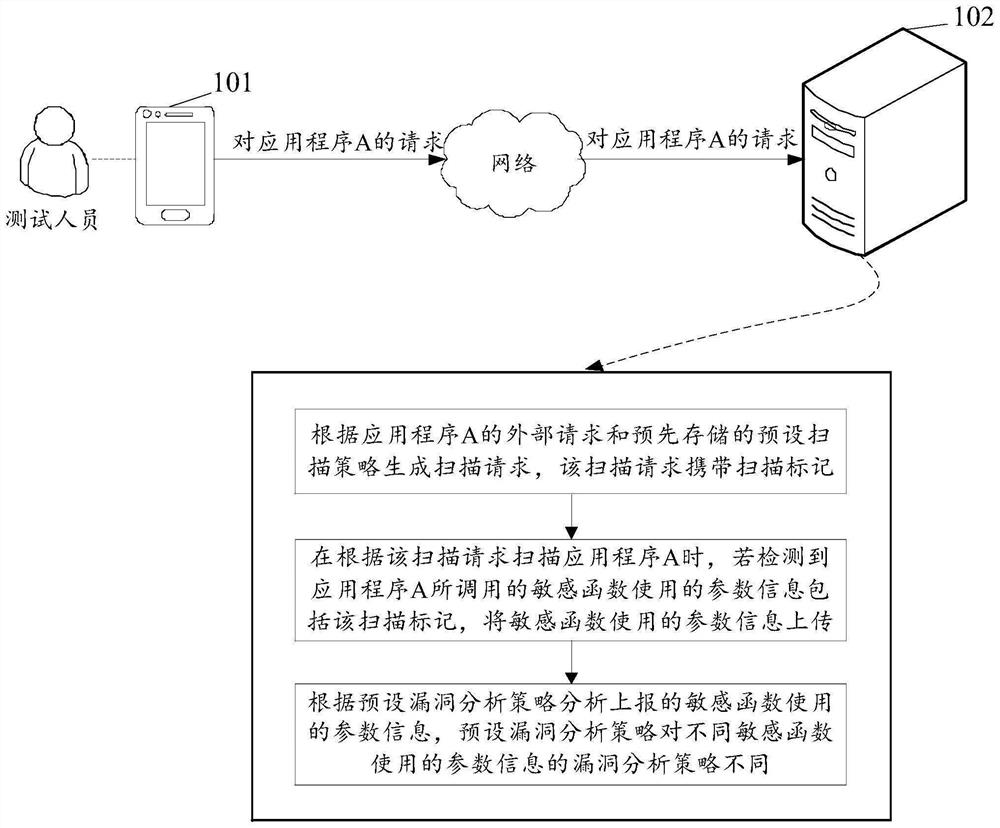
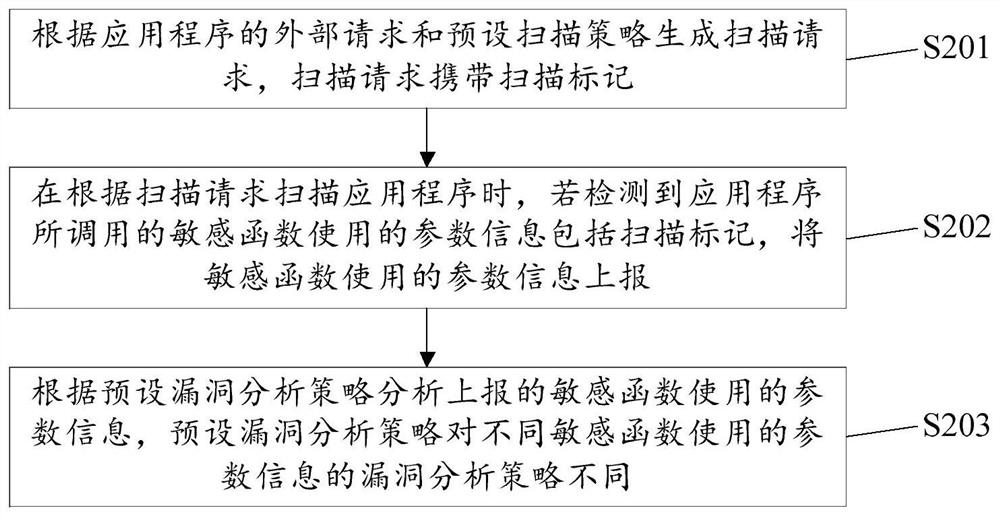
Application program security test method and related device
PendingCN113010898ALighten the dependency on request-responseImplement security testingSoftware testing/debuggingPlatform integrity maintainanceSecurity testingAlgorithm
The embodiment of the invention discloses an application program security test method and a related device, and the method comprises the steps: obtaining an external request of an application program, and generating a scanning request carrying a scanning mark through a preset scanning strategy; in the process of scanning the application program by using the scanning request, detecting whether the parameter information used by the sensitive function called by the application program comprises the scanning mark, and if so, reporting the parameter information used by the sensitive function; and analyzing the reported parameter information used by the sensitive function by using a preset vulnerability analysis strategy corresponding to the sensitive function. According to the method, the request response of the application program to the scanning request does not need to be waited, in the scanning process, it is detected that the parameter information used by the sensitive function called by the application program comprises the scanning mark which indicates that the sensitive function is the sensitive function possibly having the vulnerability, and vulnerability analysis is further performed on the parameter information used by the sensitive function; therefore, whether the application program has vulnerabilities or not is judged, and application program security testing is achieved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
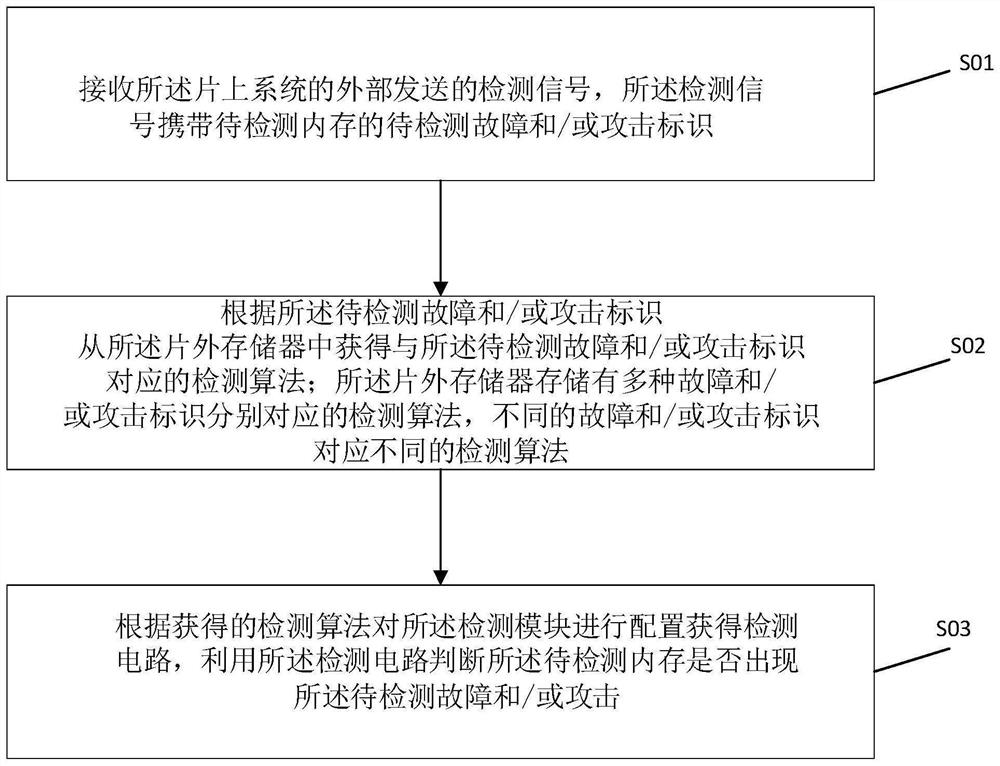
Memory security detection method and system on chip
PendingCN113157509AImplement security testingReduce power consumptionFaulty hardware testing methodsTerm memorySecurity policy
The invention provides a memory security detection method and a system on chip, the system on chip comprises a security policy controller and a memory to be detected, and the security policy controller comprises a detection module. The security policy controller receives a detection signal which carries a to-be-detected fault and / or an attack identifier of the to-be-detected memory, and obtains a detection algorithm corresponding to the to-be-detected fault and / or the attack identifier from the off-chip memory according to the to-be-detected fault and / or the attack identifier; and the off-chip memory stores detection algorithms corresponding to various fault and / or attack identifiers, the detection module is configured according to the obtained detection algorithms to obtain a detection circuit, and the detection circuit is utilized to judge whether the to-be-detected memory has a to-be-detected fault and / or attack. Security detection of corresponding faults and / or attacks of the to-be-detected memory is achieved, multiple complex detection circuits do not need to be deployed in the system at the same time, corresponding detection algorithms are called according to different detection signals to configure the corresponding detection circuits, power consumption is reduced, and efficiency is improved.
Owner:INST OF MICROELECTRONICS CHINESE ACAD OF SCI
Coal mine safety monitoring and inspection management device applied to coal mine safety management
PendingCN113137275AInnovative designImplement security testingMining devicesWithdrawing sample devicesAutomotive engineeringProcess engineering
The invention relates to a coal mine safety monitoring and inspection management device applied to coal mine safety management. The coal mine safety monitoring and inspection management device applied to coal mine safety management comprises a base, an air exhaust box and a reagent box which are mounted on the base, a rotating shaft rotationally mounted on the air exhaust box, and a camera rotationally mounted on the rotating shaft, wherein a driving assembly drives a spraying assembly to work when working, so that a stopping agent solution in the reagent box is sprayed to air, and meanwhile, the driving assembly drives the rotating shaft to rotate, the rotating shaft drives a reciprocating assembly to move, the reciprocating assembly is matched with a detection assembly, the detection assembly detects air components, a meshing assembly triggers work, a retracting and releasing assembly intermittently moves, the retracting and releasing assembly moves, the camera rotates clockwise, a torsional spring is compressed, the retracting and releasing assembly stops moving, and the torsional spring enables the camera to rotate anticlockwise, so that safety detection of the air, camera monitoring of the field environment and spraying prevention of the stopping agent solution are achieved.
Owner:YANAN UNIV
Safety test method and device for virtual engine application and storage medium
PendingCN110275836AImprove search efficiencyImprove accuracySoftware testing/debuggingTest efficiencySoftware engineering
The embodiment of the invention discloses a security test method and device for an unreal engine application and a storage medium, and belongs to the technical field of computers. The method comprises: when an application program developed on the basis of an unreal engine runs, generating a metadata link table according to elements with reflection marks in codes of the application program, wherein metadata in the metadata link table is used for describing information of the elements; obtaining data corresponding to the element according to the metadata of the element; and performing a security test on the element according to the element and the data corresponding to the element. According to the embodiment of the invention, the element and the data corresponding to the element can be determined through the metadata link table, so that the problems that the searching efficiency and accuracy are low and the safety test cannot be carried out on the element which is not contained in the symbol table when the element is searched through the symbol table are solved, and the testing efficiency and the testing range of the safety test are improved.
Owner:SHENZHEN TENCENT INFORMATION TECH CO LTD
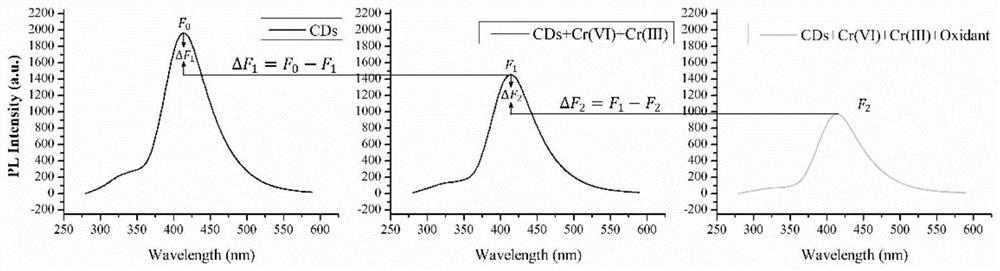
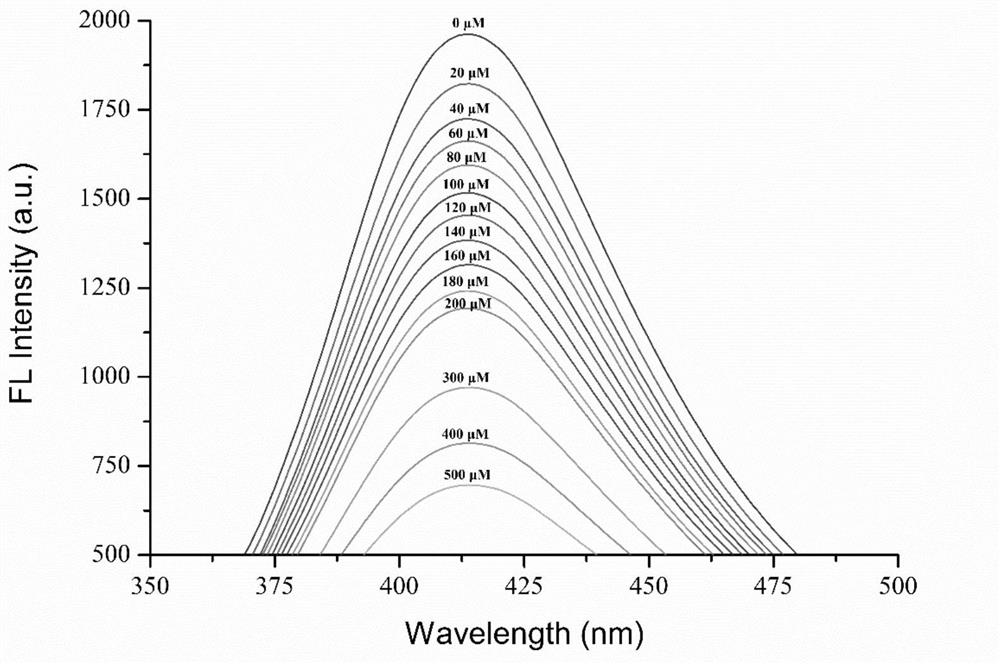
Method for stepwise detecting Cr(VI) and Cr(III) based on fluorescent carbon quantum dots
PendingCN111707650ATunable fluorescence emissionImplement security testingMaterial nanotechnologyNano-carbonFood safetyPotable water
The invention provides a method for stepwise detecting Cr(VI) and Cr(III) based on fluorescent carbon quantum dots, and belongs to the field of heavy metal detection. According to the method, the fluorescent carbon quantum dots are prepared firstly, then a fluorescent system is constructed to inspect the function relationship between the Cr(VI) content and the Cr(III) content and the fluorescenceintensity change value, and then the Cr(VI) content and the Cr(III) content are obtained by comparing the fluorescence intensity; the method is simple and convenient to operate, low in cost, wide in detection range and high in precision, can realize rapid stepped detection research on Cr (VI) and Cr (III), and has very important practical significance for detecting chromium elements with differentvalence states in drinking water and maintaining food safety.
Owner:JIANGSU UNIV
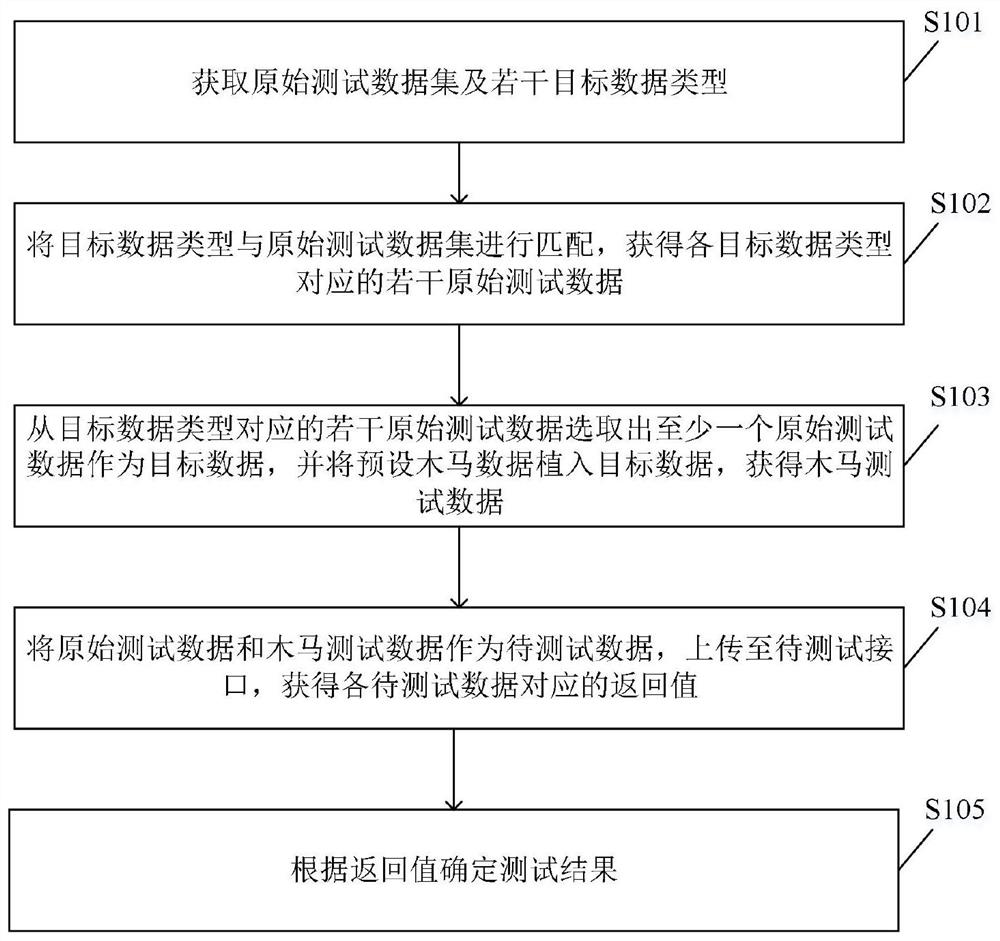
Data uploading interface test method and system, electronic equipment and readable storage medium
PendingCN113821800AImplement security testingReliable and reliableSoftware testing/debuggingPlatform integrity maintainanceData classData set
The invention relates to the technical field of interface testing, and discloses a data uploading interface testing method and system, electronic equipment and a readable storage medium. The method comprises the steps of obtaining an original testing data set and a plurality of target data types, and matching the target data types with the original testing data set; obtaining a plurality of original test data corresponding to each target data type, selecting at least one original test data from the plurality of original test data corresponding to the target data type as target data, implanting preset Trojan horse data into the target data to obtain Trojan horse test data, and taking the original test data and the Trojan horse test data as to-be-tested data; uploading the to-be-tested data to a testing interface, acquiring the return value corresponding to each to-be-tested data, and determining the test result according to the return value, so that Trojan safety test of the to-be-tested interface is realized, and the test result is more reliable.
Owner:重庆紫光华山智安科技有限公司
Security test method and device, computer equipment and storage medium
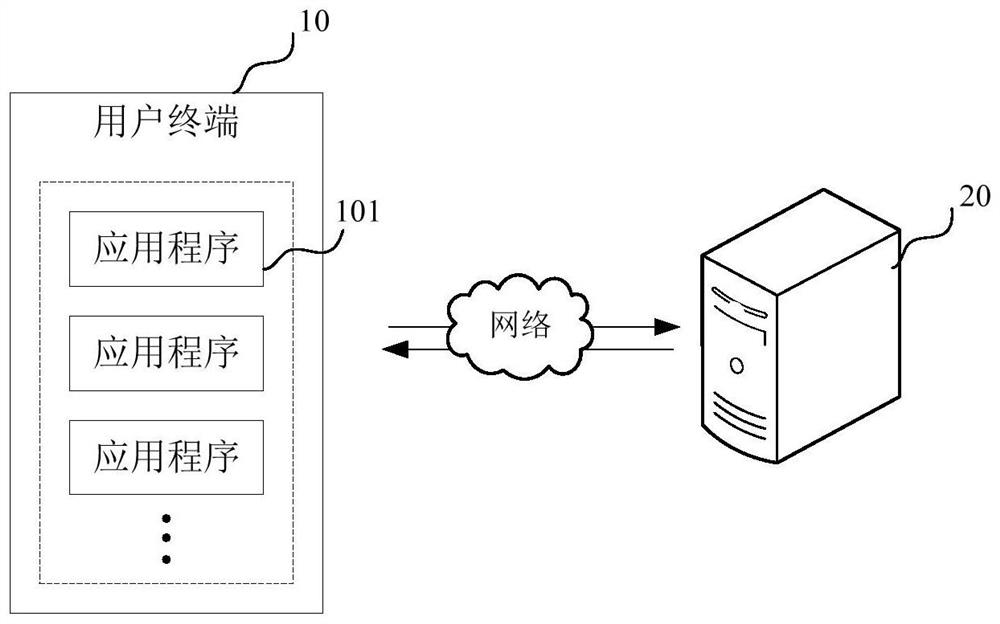
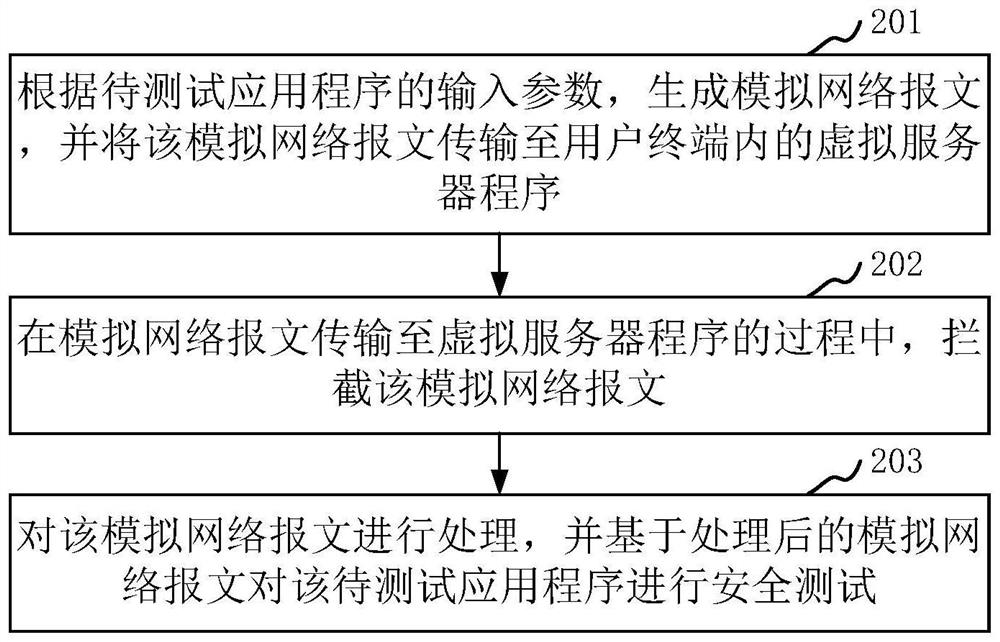
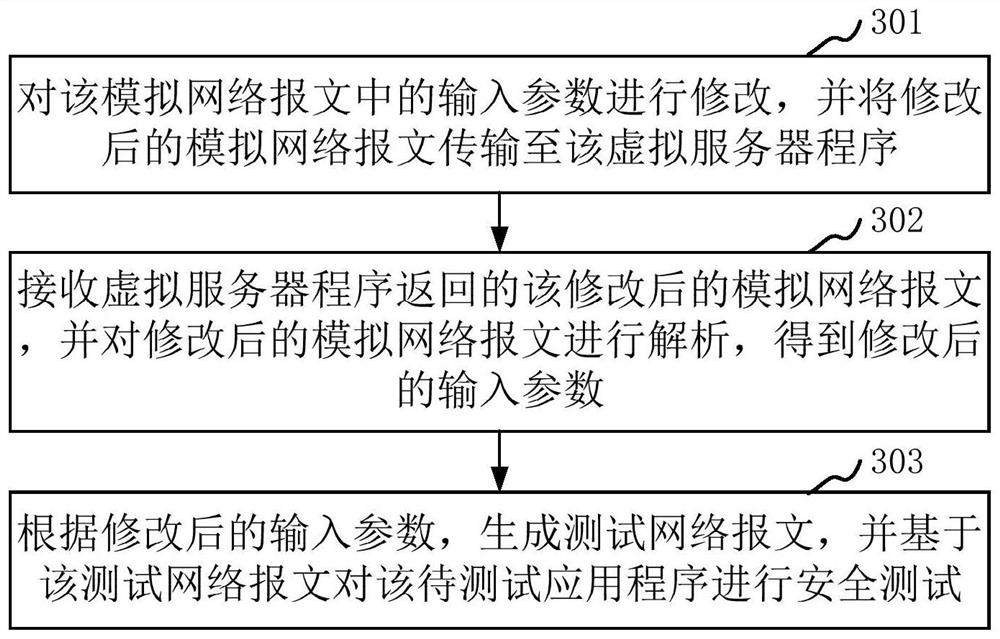
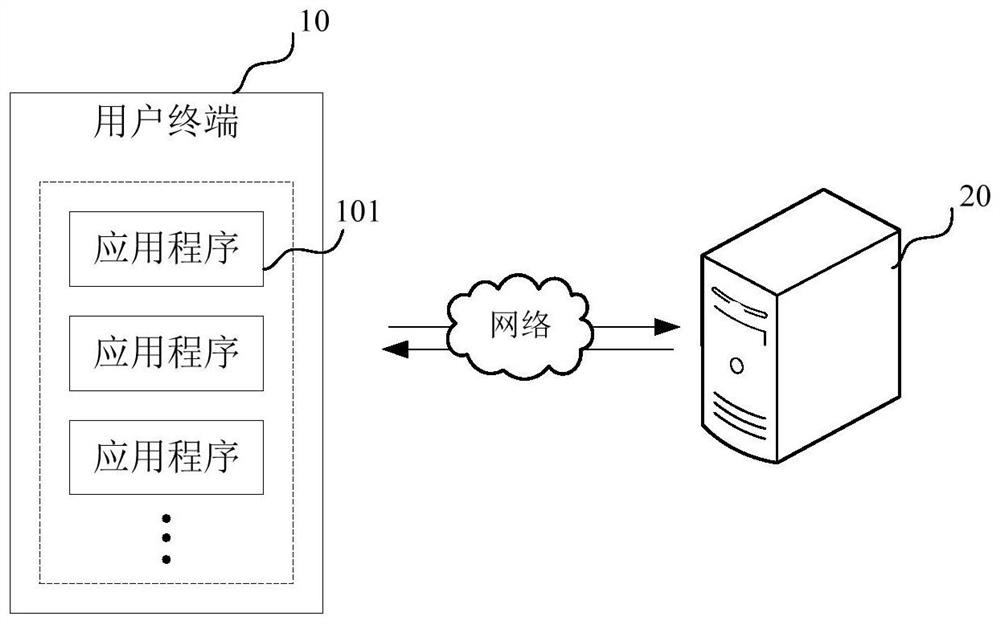
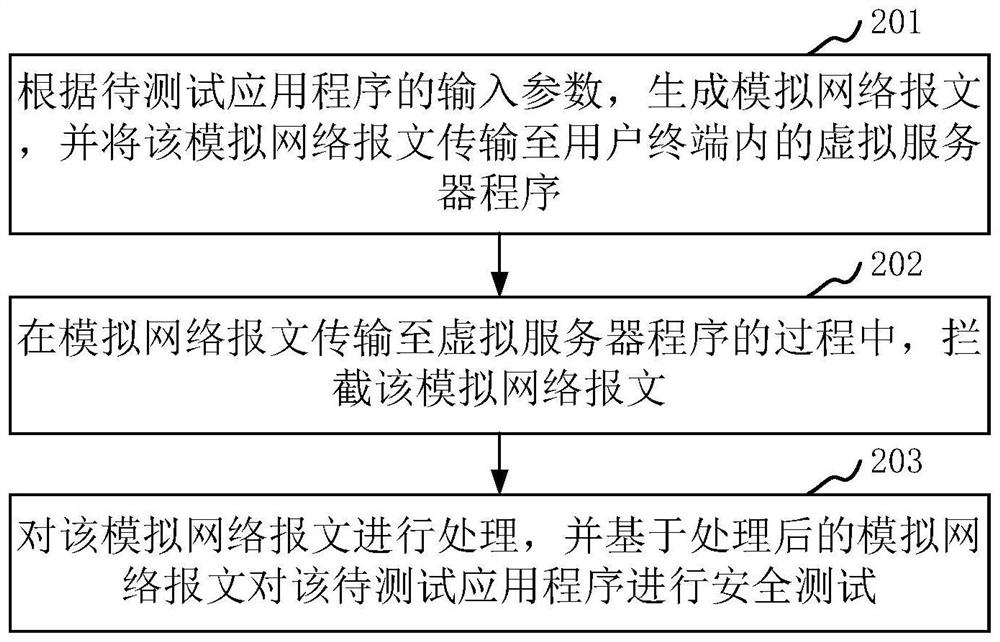
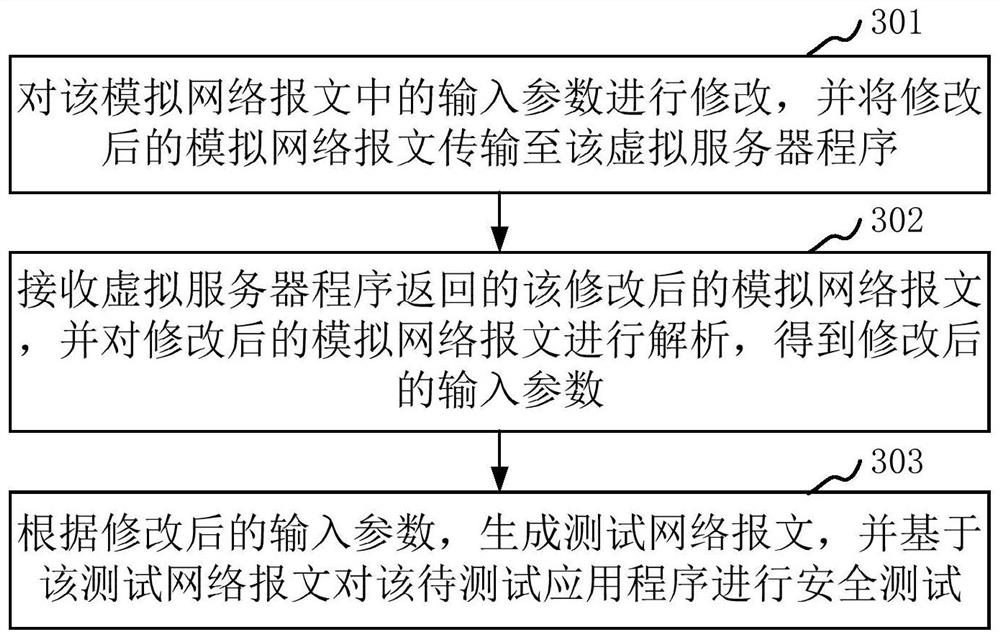
ActiveCN114039760AReduce difficultyReduce complexitySecuring communicationApplication procedureInformation security
The invention relates to a security test method and device, computer equipment and a storage medium. The method relates to the technical field of information security, and comprises the following steps: generating a simulation network message according to an input parameter of a to-be-tested application program, and transmitting the simulation network message to a virtual server program in a user terminal; intercepting the analog network message in the process of transmitting the analog network message to the virtual server program; processing the analog network message, and performing a security test based on the processed analog network message. That is, in the embodiment of the invention, the simulation network environment can be established locally at the user terminal, the problem that the security test cannot be carried out due to the fact that the man-in-the-middle test module cannot acquire the input parameters due to direct interaction between the application program and the server can be avoided, and the simulation network message is generated through the simulation network environment; and the security test on the to-be-tested application program is realized by processing the simulation network message, so that the security test efficiency is improved.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
Proximity switch test device under high temperature environment
ActiveCN105319498BImplement security testingEasy to testCircuit interrupters testingMicrometerRoom temperature
The present invention discloses a proximity switch testing arrangement in a high temperature environment. The proximity switch testing arrangement comprises a high temperature test mechanism and a normal temperature operation mechanism, the high temperature test mechanism includes a proximity switch, a proximity switch installing support, an induction sheet mobile device support and the like, and the normal temperature operation mechanism main includes a displacement regulation support, a micrometer and the like. The proximity switch installing support is provided with a proximity switch and the induction sheet capable of moving and rebounding under the action of tension; the displacement regulation support is provided with the micrometer with adjustable displacement; and one end of a steel wire is connected with the induction sheet in a high temperature oven, and the other end of the steel wire is connected with the micrometer. According to the invention, the safety test of a proximity switch may be performed in a high temperature environment; in the high temperature environment, the induction distance and the induction diameter of the proximity switch is adjustable; the proximity switch testing arrangement in the high temperature environment is applicable to the tests of proximity switches with different types in the high temperature environment, and is convenient for testing induction sheets with different materials; and the separation of the high temperature area and the normal temperature area is beneficial for safe operation.
Owner:BC P INC CHINA NAT PETROLEUM CORP +1
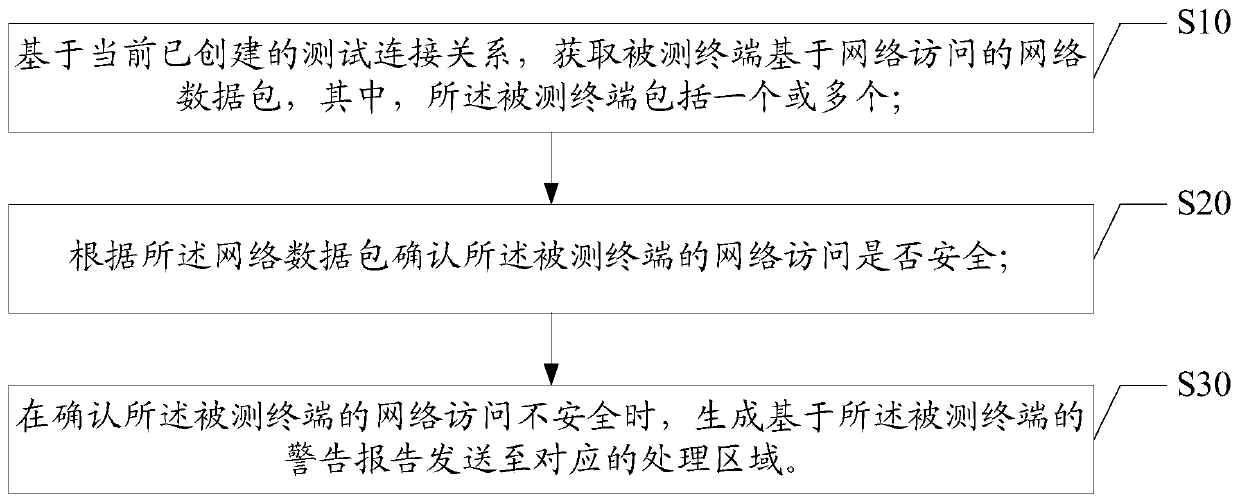
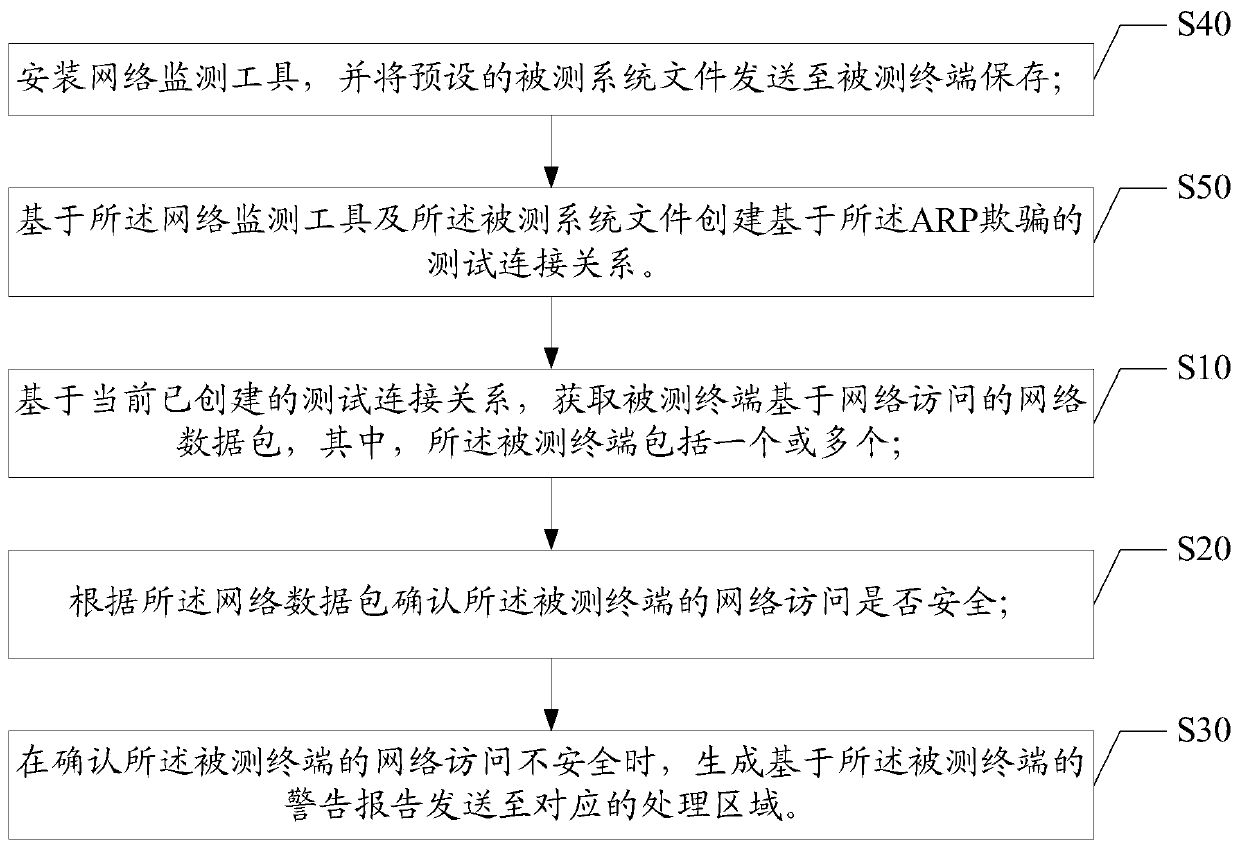
Testing method and device based on network data monitoring and readable storage medium
The invention discloses a test method based on network data monitoring, and the method comprises the steps: obtaining a network data packet, based on network access, of one or more tested terminals based on a currently created test connection relation; determining whether the network access of the tested terminal is safe or not according to the network data packet; and when it is confirmed that the network access of the tested terminal is unsafe, generating a warning report based on the tested terminal, and sending the warning report to a corresponding processing area. The invention further discloses a testing device based on network data monitoring and a readable storage medium. According to the invention, the network connection is established through the ARP spoofing technology, so thatthe data accessed by the television network connected in the network flows through the test terminal, the unsafe access data is determined by analyzing the data packet of the network access data through the test terminal, and the beneficial effect of safety detection of the television system in the network data access process is realized.
Owner:SHENZHEN TCL DIGITAL TECH CO LTD
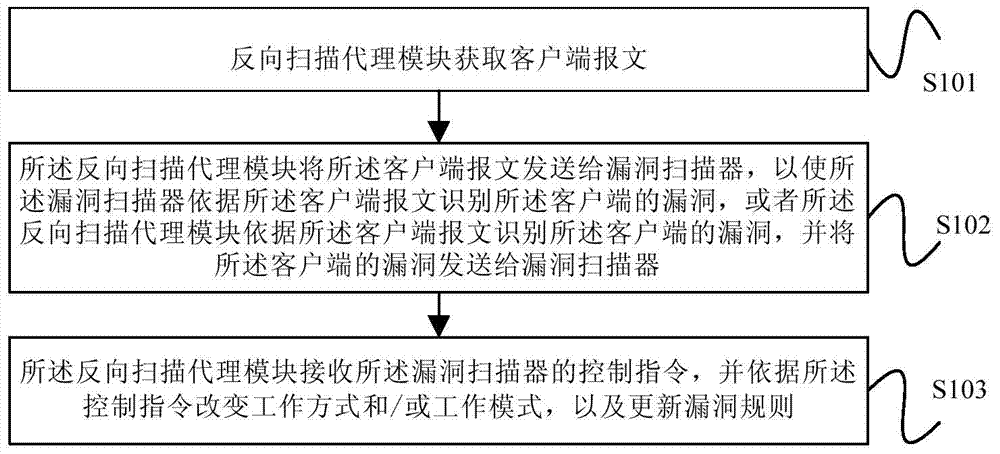
Vulnerability scanning method and device
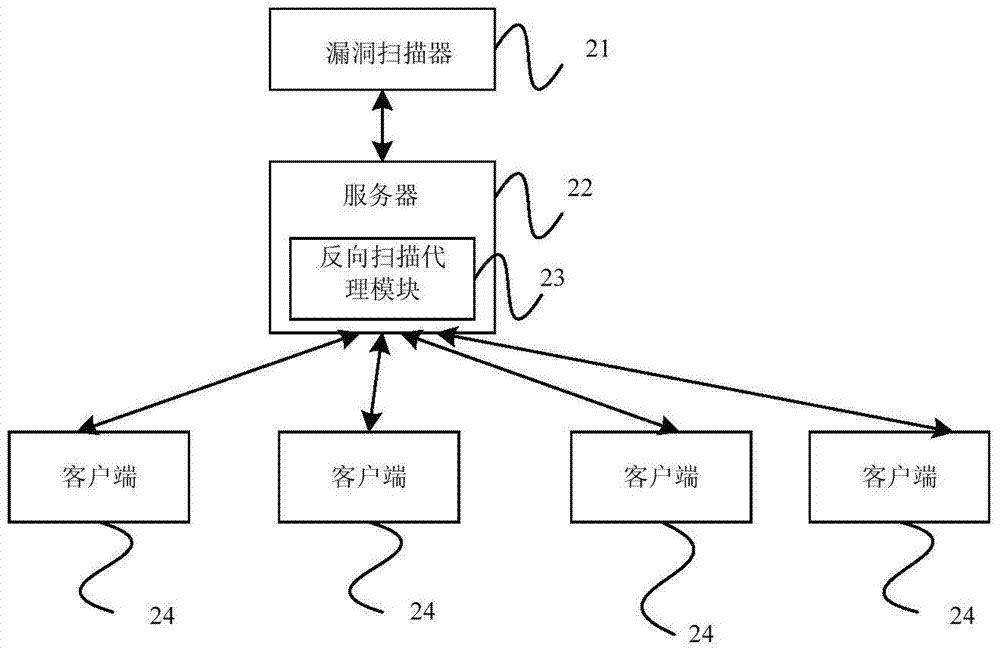
ActiveCN104506522BImprove analysisRaise security concernsComputer security arrangementsTransmissionClient-sideSecurity question
Embodiments of the present invention provide a vulnerability scanning method and device. The method includes: a reverse scanning agent module obtains a client message; the reverse scanning agent module sends the client message to a vulnerability scanner, so that the vulnerability scanner identifies the The vulnerability of the client; or the reverse scanning proxy module identifies the vulnerability of the client according to the client message, and sends the vulnerability of the client to the vulnerability scanner; the reverse scanning proxy module receives the vulnerability control instructions of the scanner, and change the working mode and / or working mode according to the control instructions, and update the vulnerability rules. The embodiment of the present invention obtains the client message through the reverse scanning proxy module, and analyzes the client message to identify the loopholes in the client. Analysis, thus realizing the security detection of the entire network environment.
Owner:NSFOCUS INFORMATION TECHNOLOGY CO LTD +1
Fixed washboard brake performance tester for agricultural machinery
ActiveCN103604613BImplement security testingBest detection positionVehicle testingAgricultural engineeringMechanical property
The invention discloses a fixed washboard type agricultural machinery braking performance detector and belongs to the field of agricultural machinery performance detection devices. The fixed washboard type agricultural machinery braking performance detector comprises a fixed washboard table body (1) and a washboard detection table (2) arranged above the fixed washboard table body (1) in an embedded mode. The fixed washboard type agricultural machinery braking performance detector is characterized in that the lower portion of the washboard detection table (2) is installed above the fixed washboard table body (1) in a supporting mode through a slide (3), a driving device is installed in the gap between the fixed washboard table body (1) and the washboard detection table (2), an infrared sensor (7) capable of detecting a tire and transmitting signals is arranged on the upper portion of the washboard detection table (2), and the driving device receives the signals of the infrared sensor (7) to drive the washboard detection table (2) to slide left and right along the slide (3). The fixed washboard type agricultural machinery braking performance detector is wide in application range, easy to operate, and capable of automatically adjusting the distance between detection tables.
Owner:SHANDONG KEDA COMP APPL INST
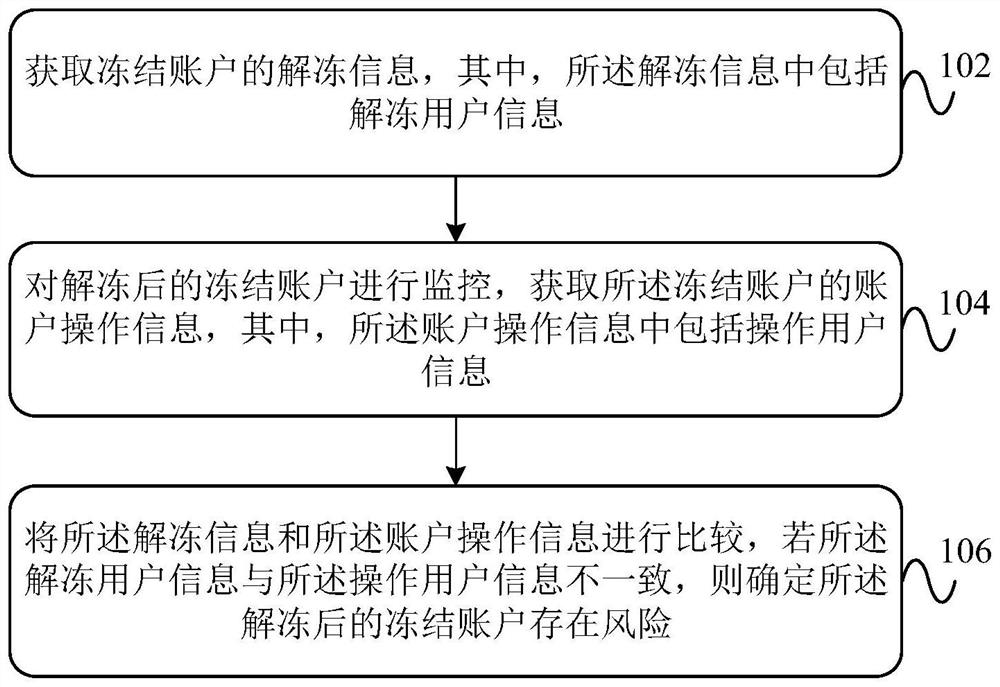
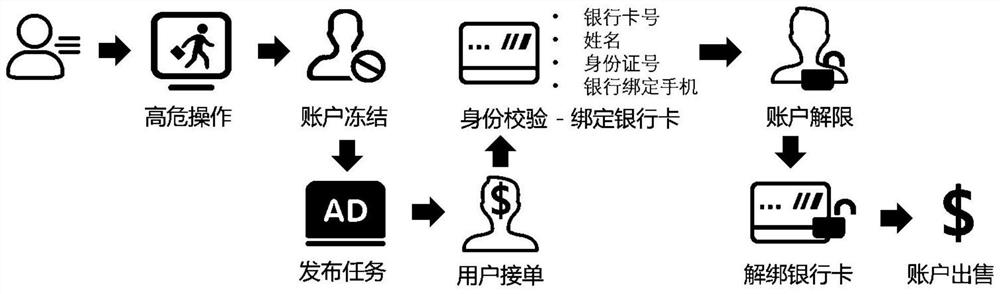
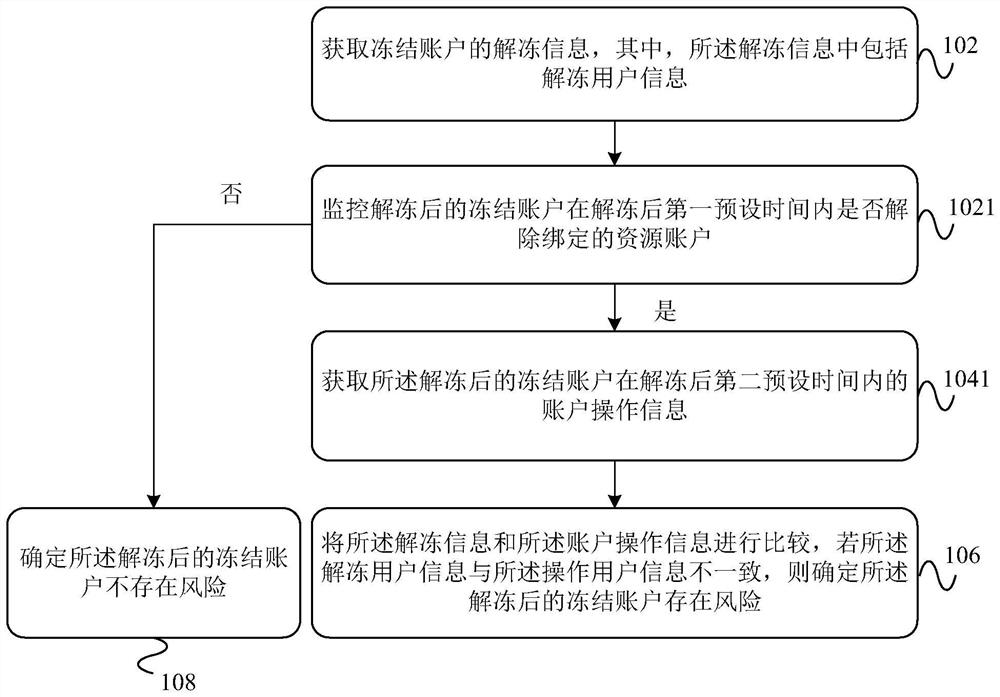
Data management method and device for frozen accounts, equipment and storage medium
ActiveCN112232809AAvoid the problem of unfreezing successImplement security testingProtocol authorisationData scienceSecurity management
The invention provides a data management method and device for frozen accounts, equipment and a storage medium, and the method comprises the steps: obtaining unfreezing information when a frozen account is unfrozen, and carrying out special monitoring of the unfrozen frozen account; acquiring account operation information of the frozen account after unfreezing, and comparing the unfrozen information and the account operation information to accurately determine whether unfreezing of the frozen account and the operation after unfreezing are performed by the same person, so that crowdsourcing unfreezing risk identification failure in the frozen account tunfreezing link through batch behaviors is avoided, and the risk of crowdsourcing unfreezing in the frozen account unfreezing link is reduced. so that the frozen account is not unfrozen. The account operation information and the unfreezing information of the unfrozen frozen account are recorded and compared, so that whether the unfreezingof the frozen account belongs to crowdsourcing unfreezing or not is determined more accurately, whether the unfrozen frozen account is used for doing illegal services or not is judged, the safety detection of the unfrozen frozen account is realized, and the safety of the unfrozen account is improved. Accuracy of account security management is improved.
Owner:ALIPAY (HANGZHOU) INFORMATION TECH CO LTD
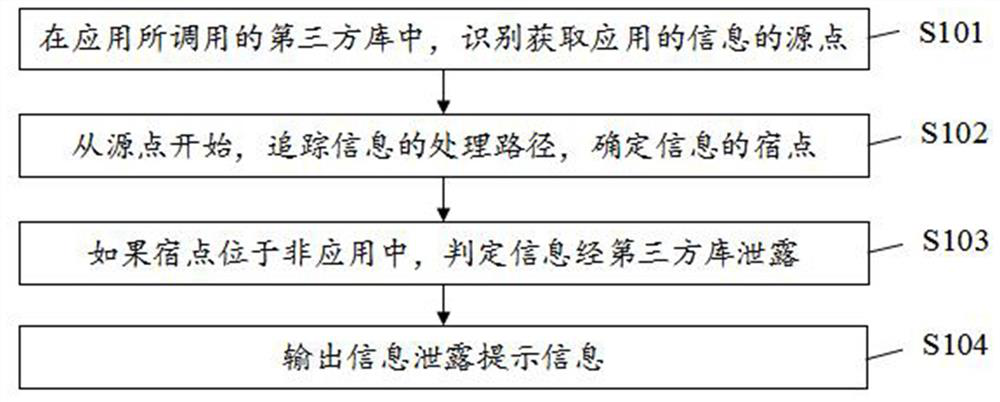
A third-party library information leakage detection method and device
ActiveCN112632551BImplement security testingDigital data protectionPlatform integrity maintainanceThird partyReliability engineering
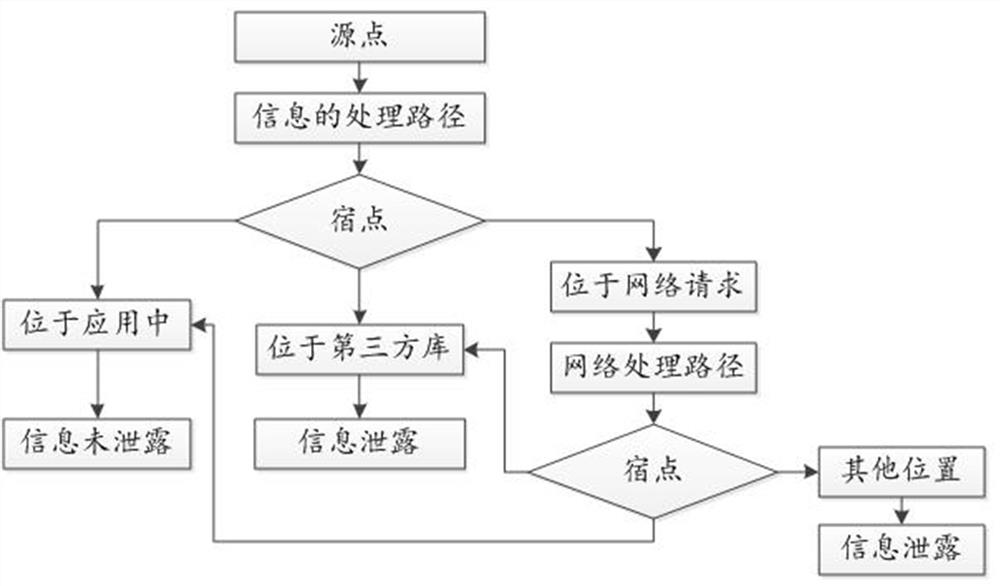
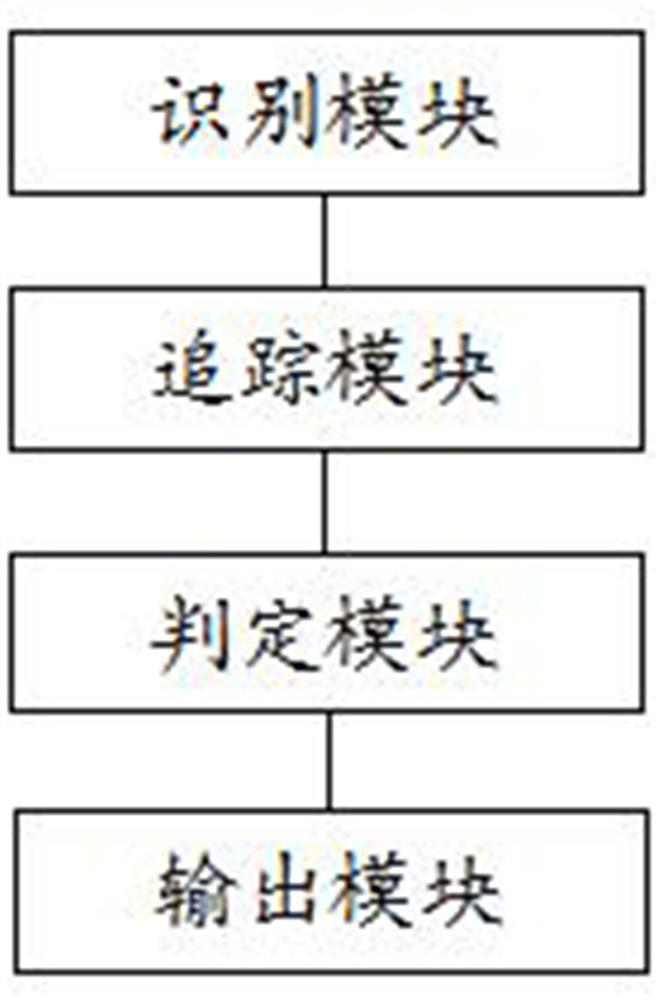
One or more embodiments of this specification provide a method and apparatus for detecting information leakage of a third-party library, including identifying a source point for acquiring information about an application in a third-party library called by an application; starting from the source point, tracking the processing of information Path, determine the sink point of the information; if the sink point is located in a non-application, determine that the information is leaked through a third-party library; output information leakage prompt information. According to the method in this specification, it is possible to detect whether there is information leakage in the third-party library, and realize the security detection of the third-party library.
Owner:BEIJING UNIV OF POSTS & TELECOMM +2
COB (Chip On Board) automatic sorting unit
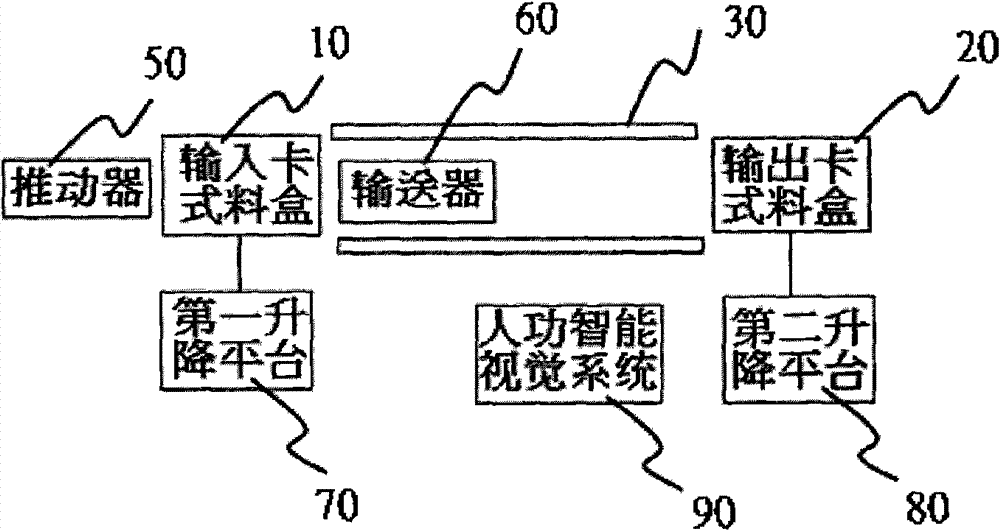
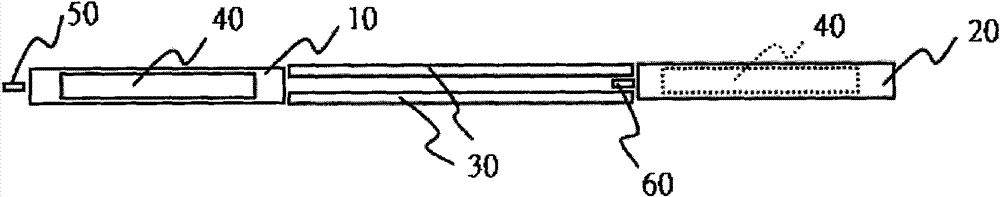
InactiveCN101941004BGuaranteed normal transmissionImplement security testingSortingOn boardControl system
The invention provides a COB (Chip On Board) automatic sorting unit, relating to an automatic chip testing device. The automatic sorting unit comprises a central control system, an input cassette system, a driving unit, a testing feed track and an output cassette system, wherein the input cassette system, the driving unit, the testing feed track and the output cassette system are respectively connected with the central control system. The input cassette system is positioned on one end of the testing feed track, and comprises a cassette system track, a locating rack, a feed bowl stand perpendicular to the locating rack, and an input cassette feed bowl vertically arranged on the feed bowl stand, wherein the input cassette feed bowl is provided with a plurality of input trenches. The output cassette system is positioned on the other end of the testing feed track, and comprises a cassette system track, a locating rack, a feed bowl stand perpendicular to the locating rack, and an output cassette feed bowl vertically arranged on the feed bowl stand, wherein the output cassette feed bowl is provided with a plurality of output trenches. The driving unit drives COB bar feed in the input trenches to move linearly so that the COB bar feed is delivered to the testing feed track from the input trenches, and the testing feed track drives COB bar feed in single layer to move linearly so that the COB bar feed is delivered to the output trenches.
Owner:杰西·吕
Security testing method, apparatus, computer equipment and storage medium
ActiveCN114039760BReduce difficultyReduce complexitySecuring communicationTest efficiencyInformation security
The present application relates to a security testing method, apparatus, computer equipment and storage medium. The method relates to the technical field of information security, and the method includes: generating a simulated network message according to input parameters of an application to be tested, and transmitting the simulated network message to a virtual server program in a user terminal; In the process of transmission to the virtual server program, the simulated network message is intercepted; the simulated network message is processed, and a security test is performed based on the processed simulated network message. That is, in the embodiment of the present application, a simulated network environment can be established locally on the user terminal, which can avoid the problem that the application program directly interacts with the server, so that the man-in-the-middle test module cannot obtain the input parameters and thus cannot perform the security test. The network message is processed, and the security test of the application to be tested is realized by processing the simulated network message, so as to improve the security test efficiency.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
A Risk Assessment Method Applicable to Industrial Control System
ActiveCN106709613BRealize safety hazardDiscovery of potential safety hazardsResourcesManagement toolAttack
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
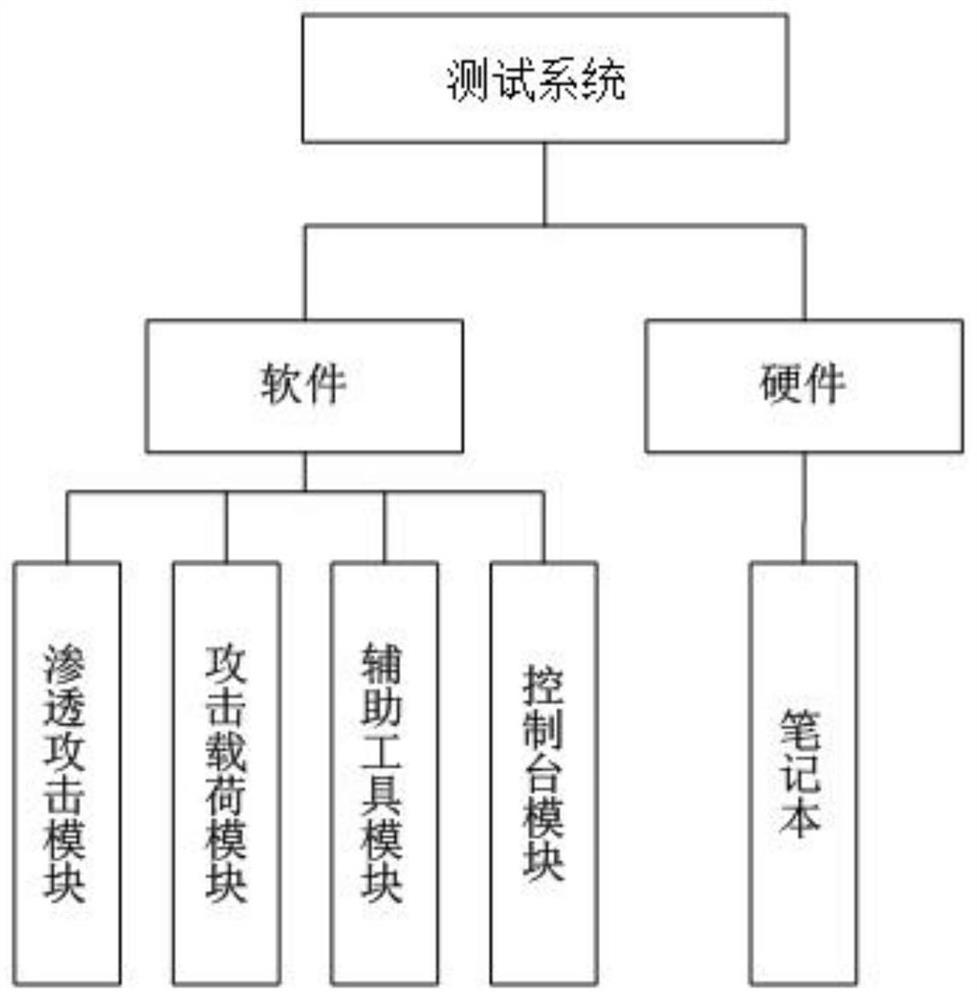
Test system based on metasploit framework and method to realize network security test
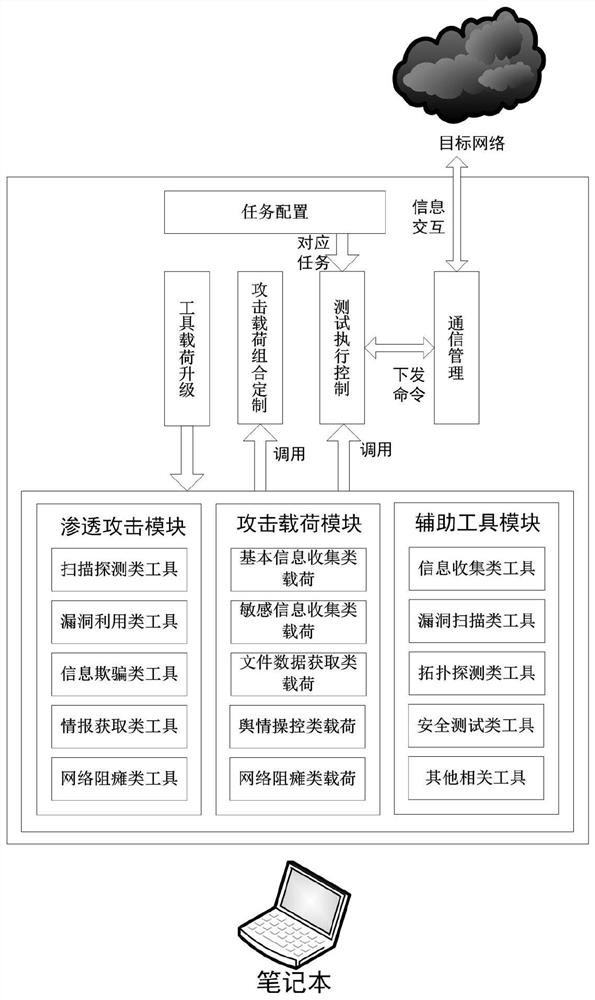
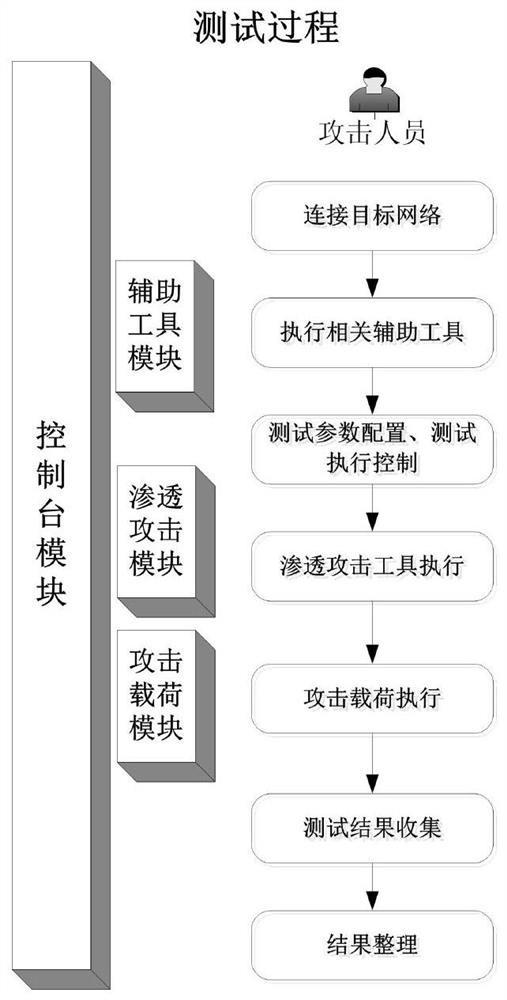
ActiveCN109284611BSimplify the configuration processImplement security testingPlatform integrity maintainanceAttackInformation security
The invention relates to a testing system based on a Metasploit framework and a method for realizing network security testing, and relates to the technical field of information security. The present invention realizes the test process by calling the penetration attack tool in the Metasploit framework in batches; and verifies the test effect of the penetration attack tool by selecting a specific typical attack load and the combination of the penetration attack tool. Through the present invention, a test system for target computer vulnerabilities and network security equipment is constructed, and a large number of penetration attack tools and attack loads integrated in the Metasploit framework are used to realize the security test of the target network in combination with other related test tools.
Owner:BEIJING INST OF COMP TECH & APPL
Safety test data acquisition and audit analysis method and device
Owner:北京中金安服科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com