Penetration testing method for GAP isolation and exchange device
A technology of switching equipment and penetration testing, which is applied in the field of information security and can solve problems such as difficult and safe and controllable testing, complex environment configuration, and low efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0015] The present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
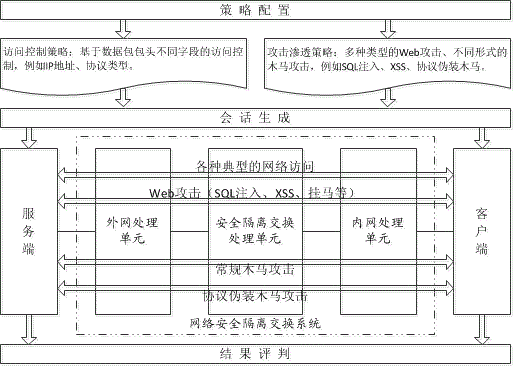
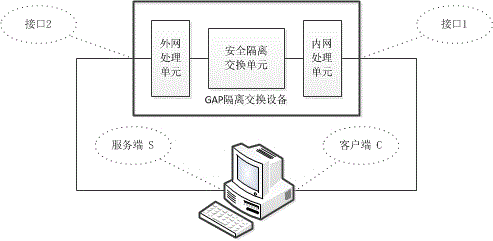
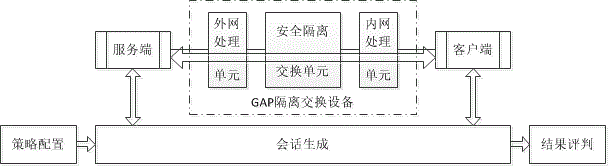
[0016] figure 1 It is a frame diagram of the technical principles of the present invention, and the penetration testing method for GAP isolation switching equipment consists of three parts: policy configuration, session generation and result evaluation. The policy configuration module is used to customize the network attack session strategy according to the security test requirements, mainly including access control, Web attack and Trojan horse attack; the session generation module simulates the host (client and server) connected to the internal and external network, , generate a precisely defined specific network attack session, and pass through the GAP isolation switching device under test; the result evaluation module checks the status of the network attack traffic traversal (passing, intercepted, modified, etc.), and combines the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com