Test system based on metasploit framework and method to realize network security test
A technology for testing systems and frameworks, applied in the field of information security to simplify the configuration process
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] In order to make the purpose, content, and advantages of the present invention clearer, the specific implementation manners of the present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments.
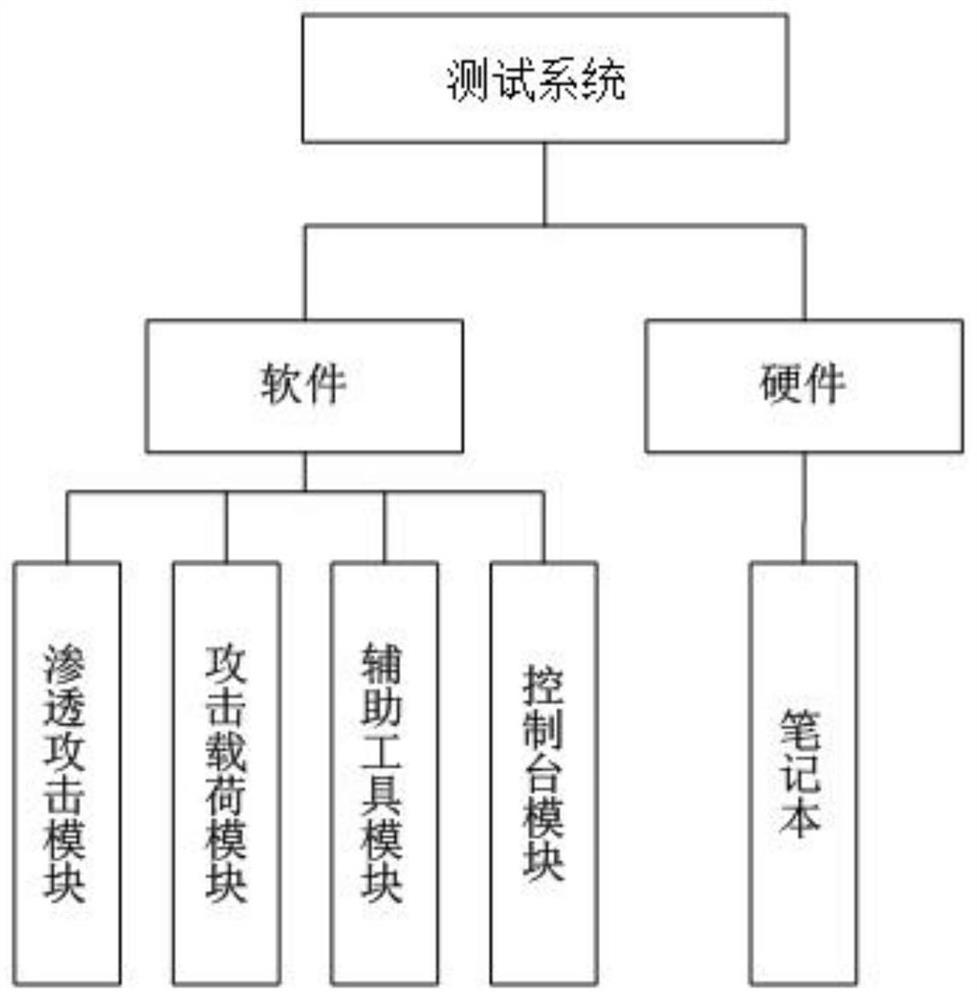
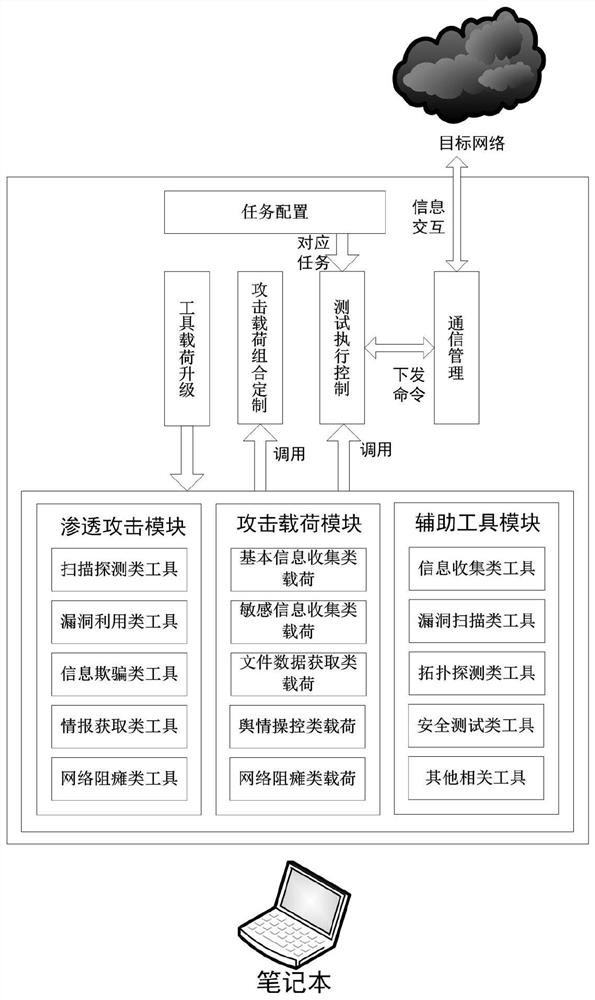
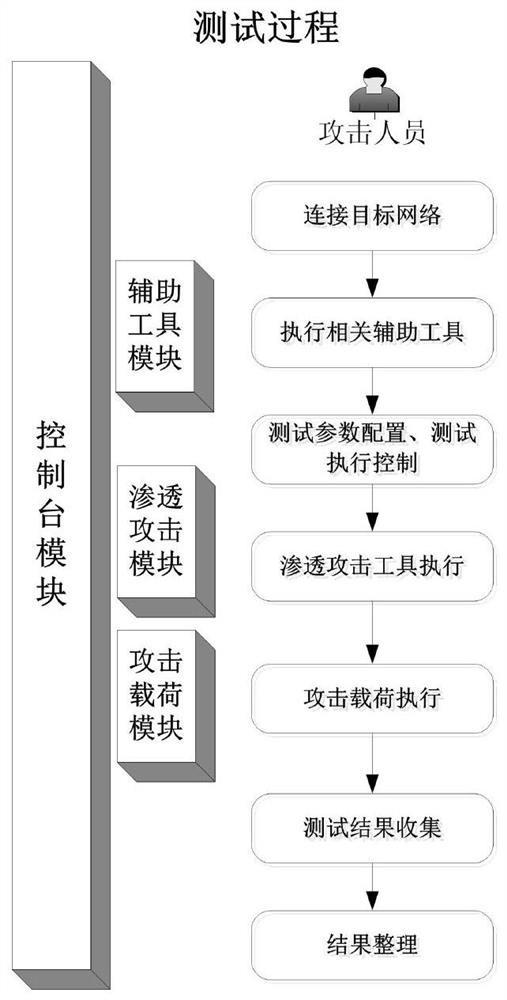
[0035] The test system of the present invention includes a penetration attack module, an attack load module, an auxiliary tool module and a console module, and is realized by integrating open source products such as Metasploit and self-developed methods, and its hardware carrier can be a notebook, such as figure 1 shown.
[0036] Wherein, the penetration attack module is a collection of various penetration attack tools, and the concept of the penetration attack tool in the present invention corresponds to the exploit in Metasploit (which is designed by attackers or testers for the loopholes in the system to destroy the security of the system. Attack code), which is a vulnerability exploit tool running in the test compu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com