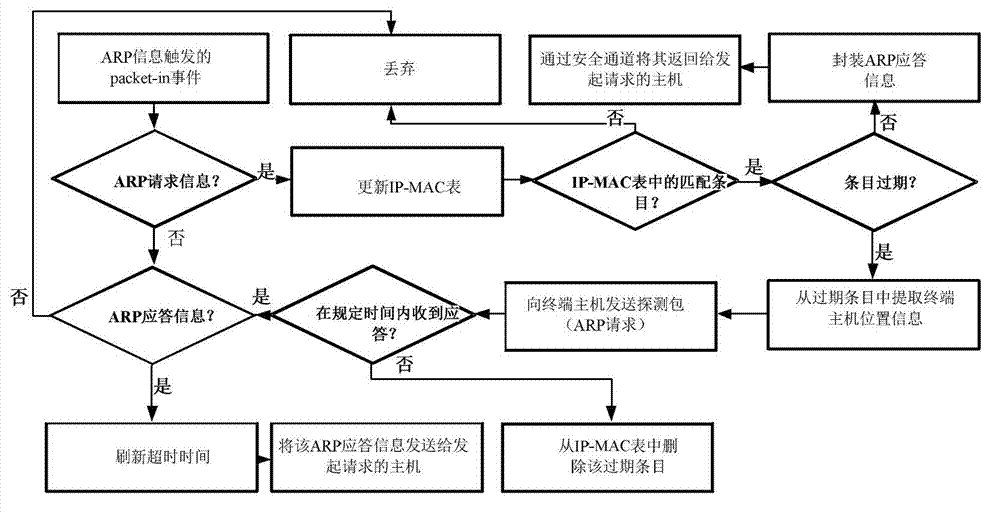
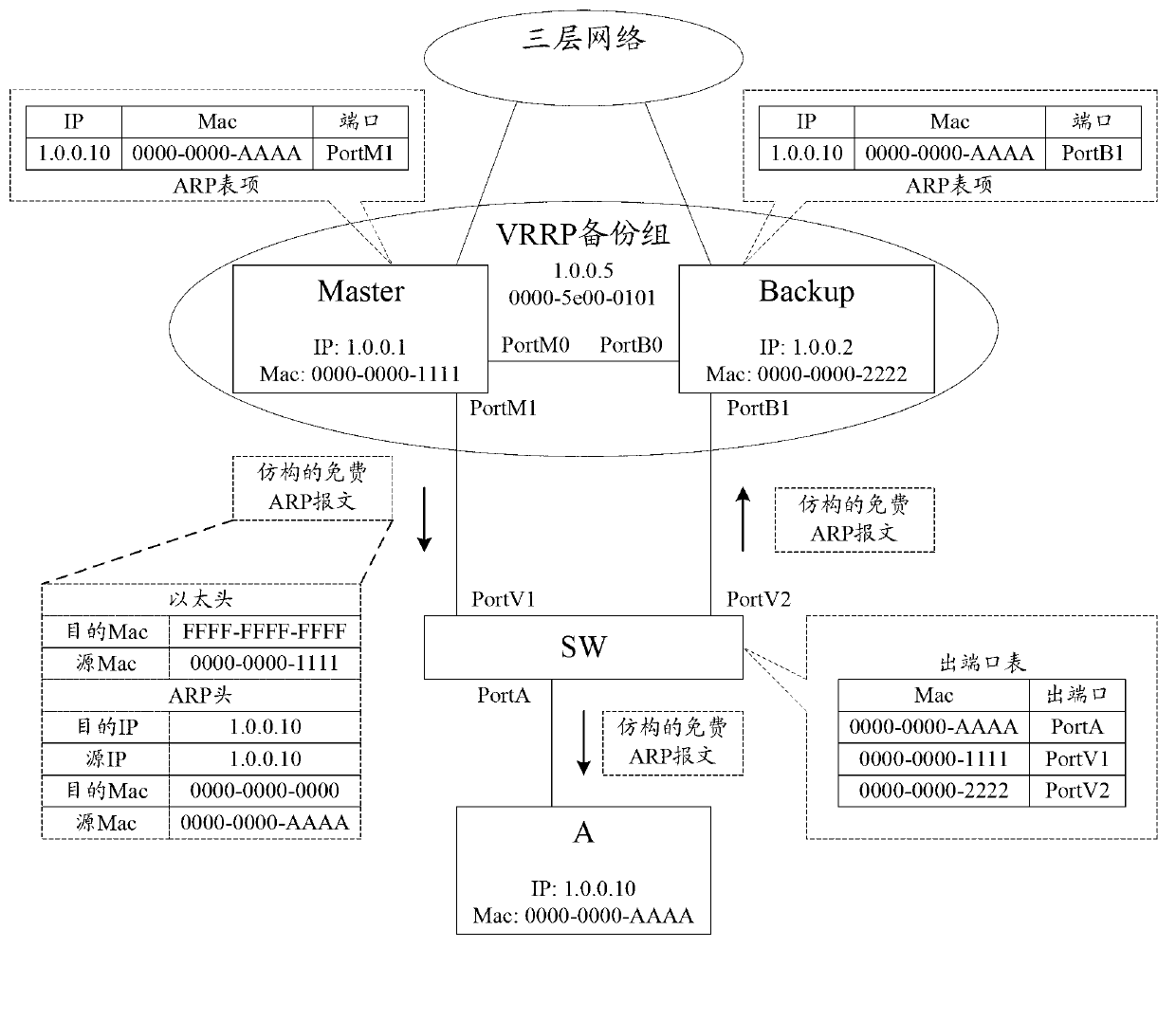
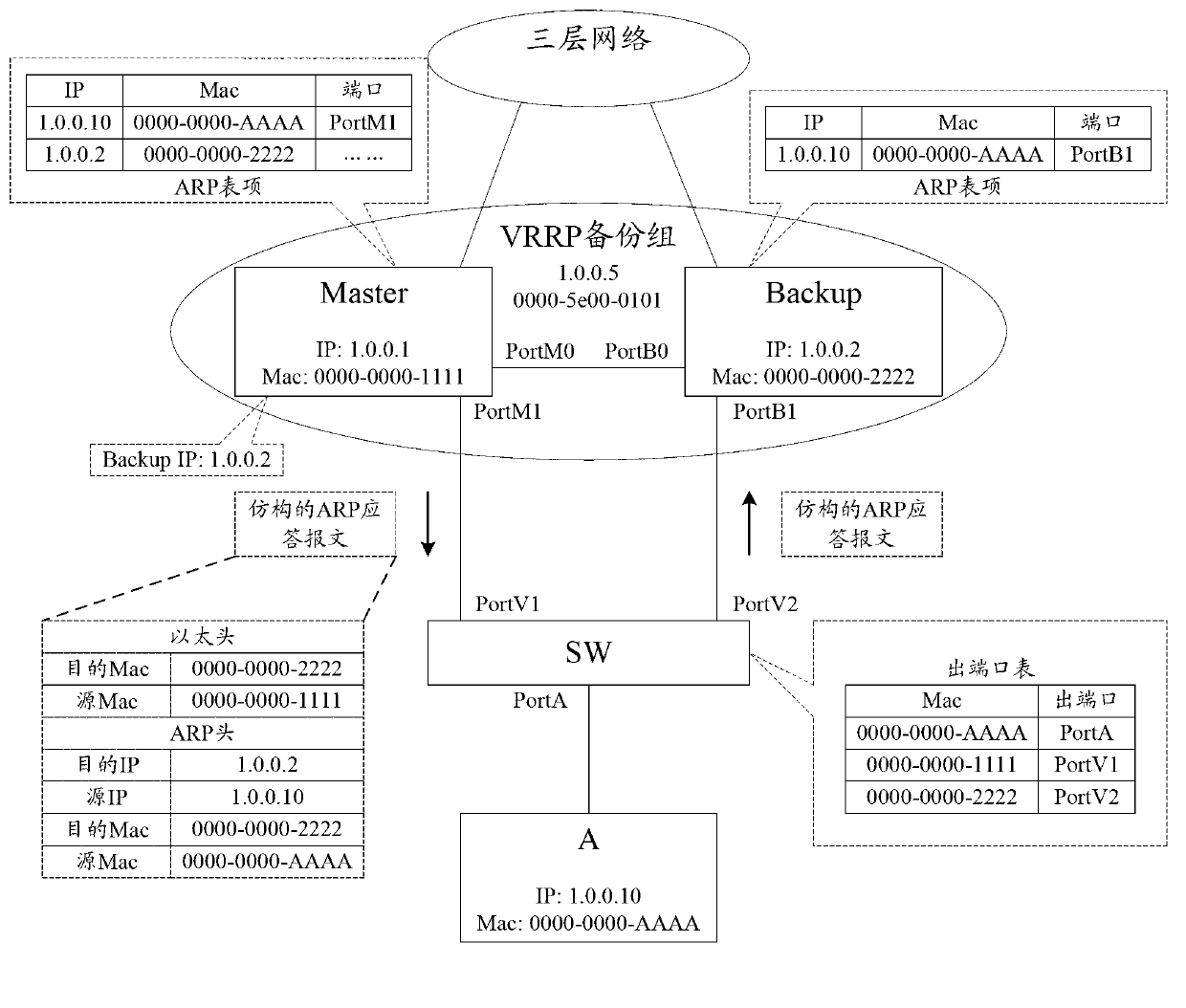
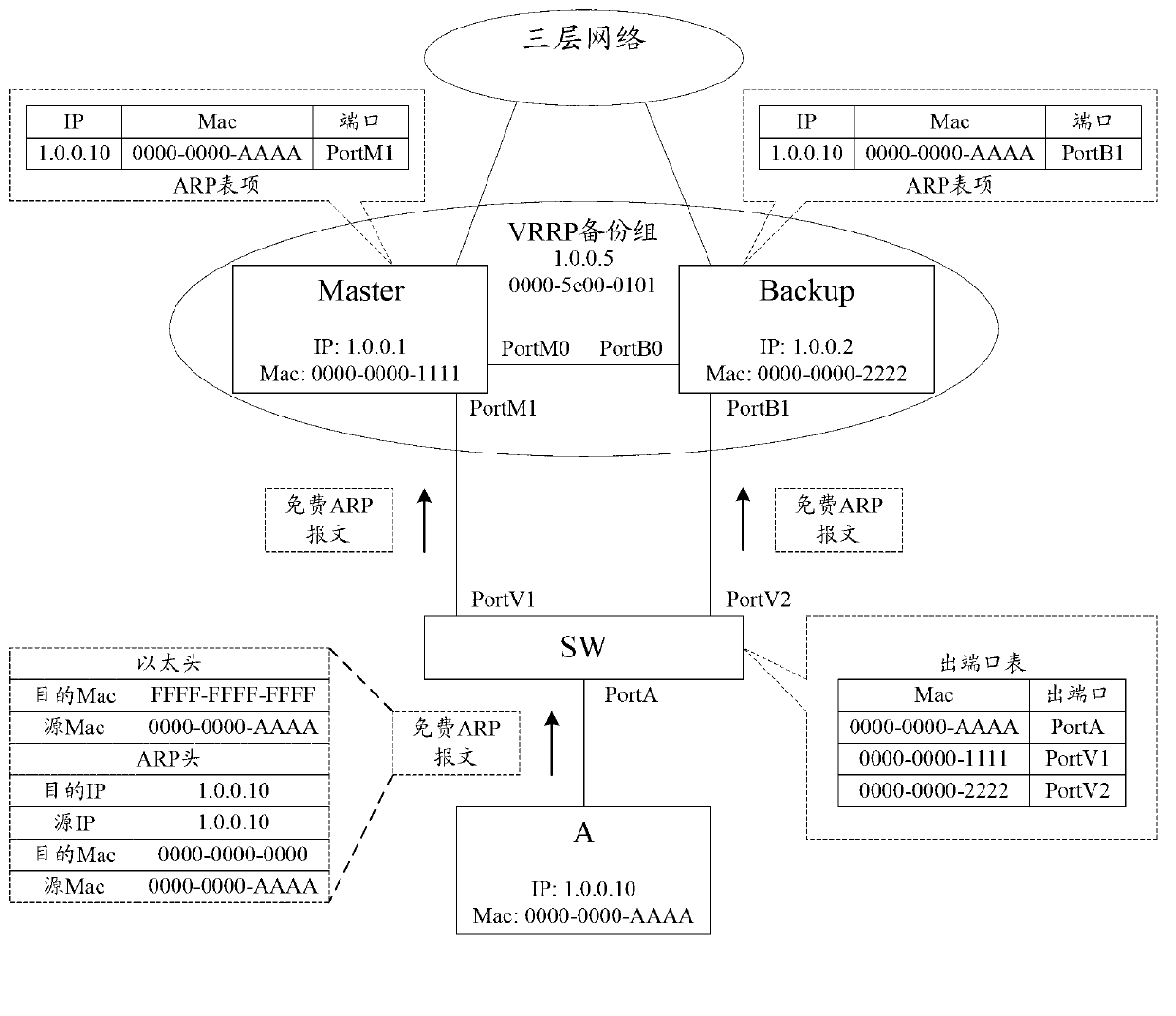
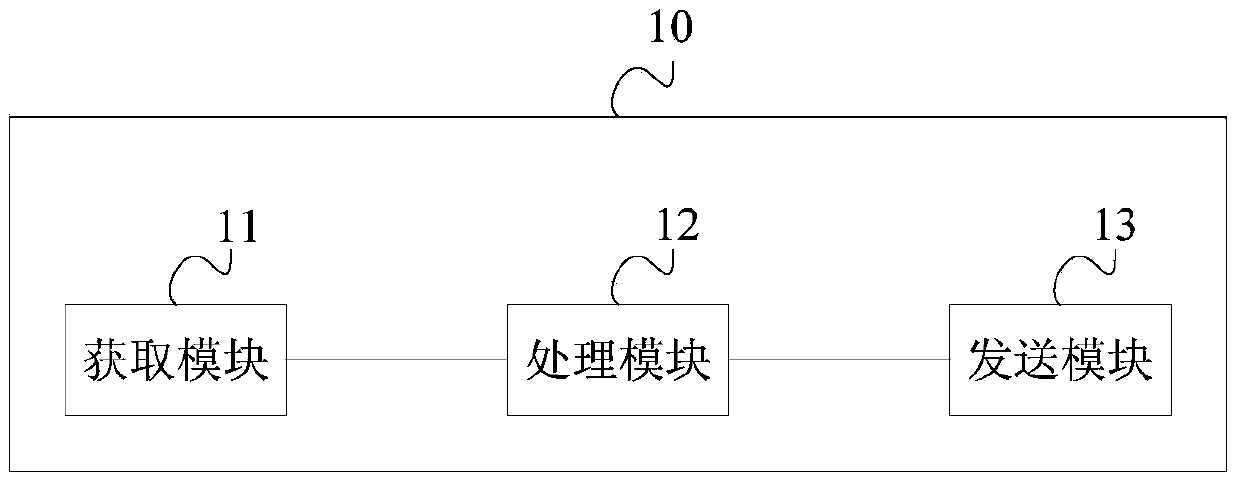
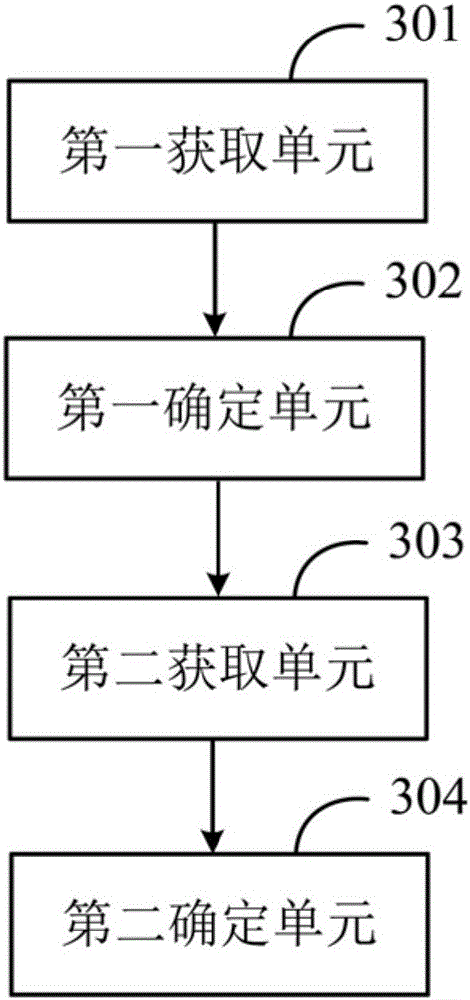
Patents
Literature
92 results about "ARP spoofing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
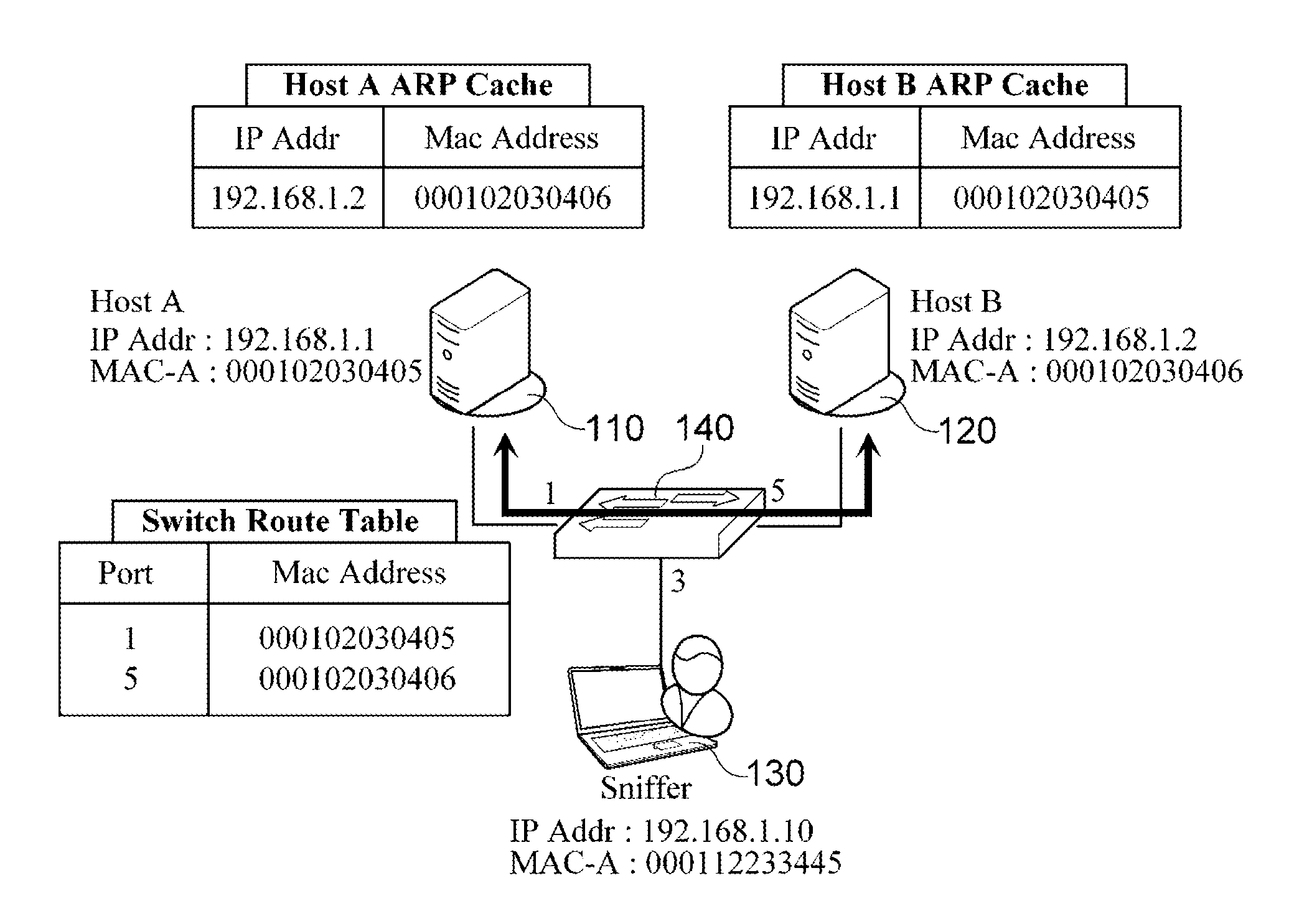
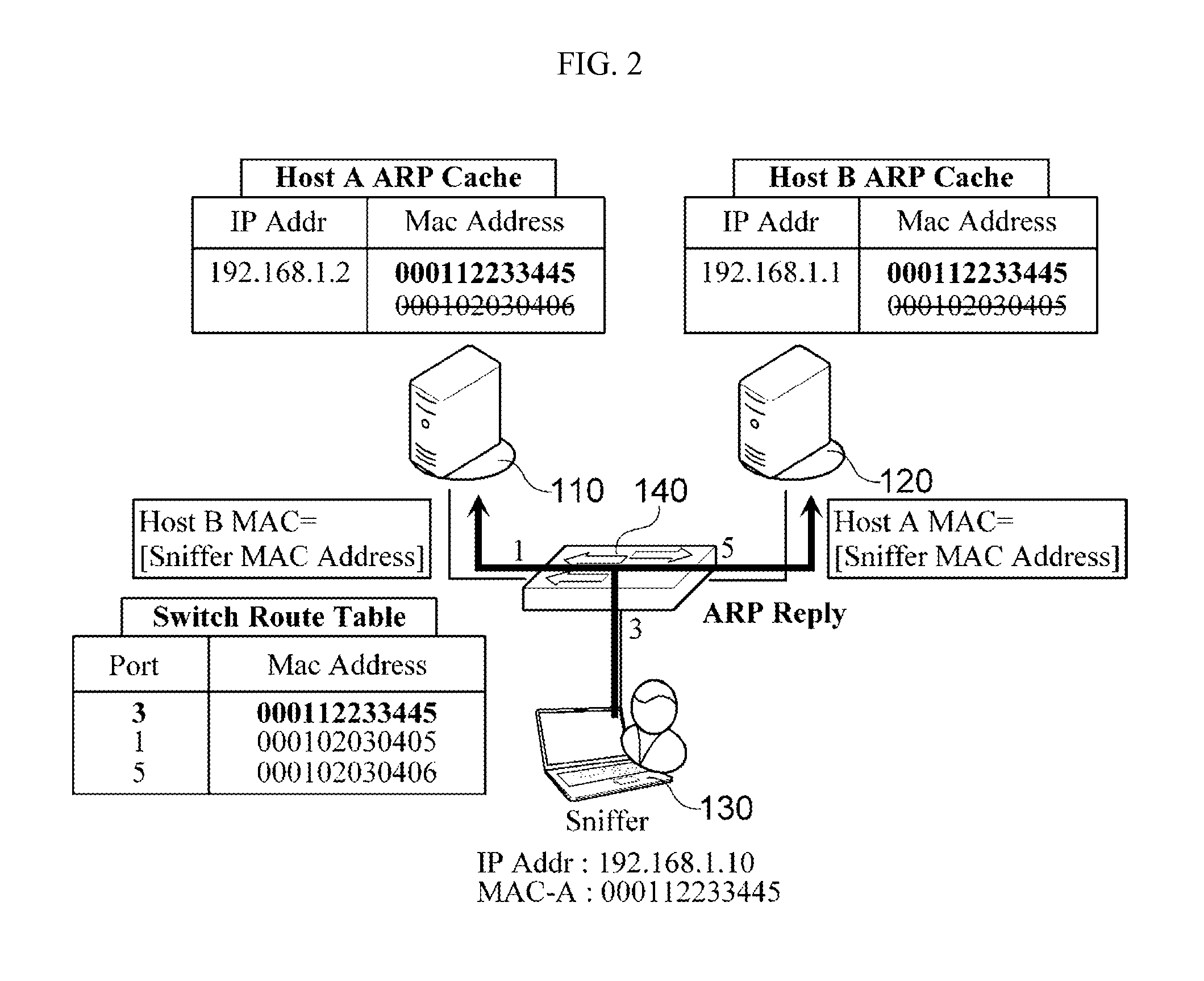
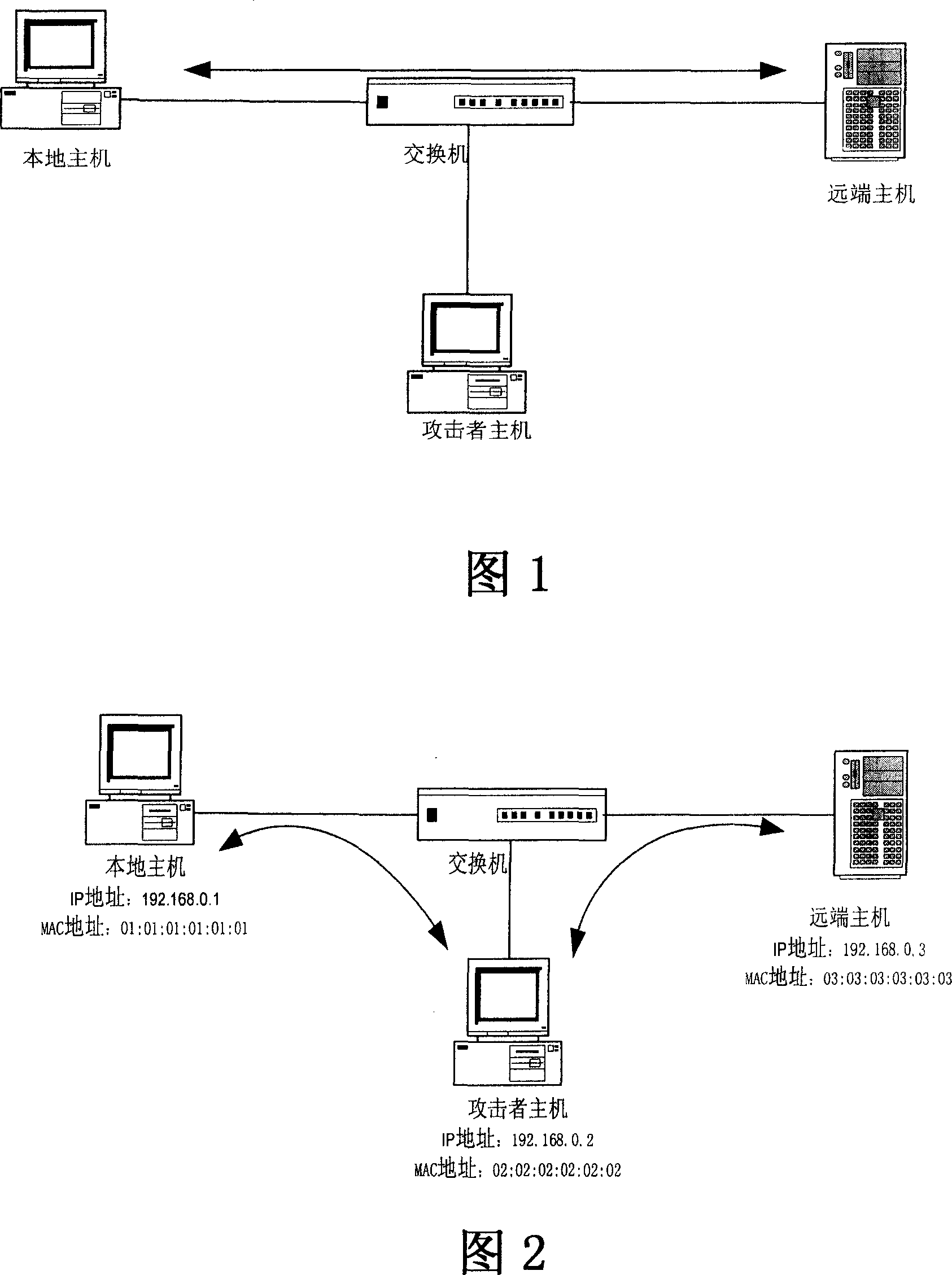
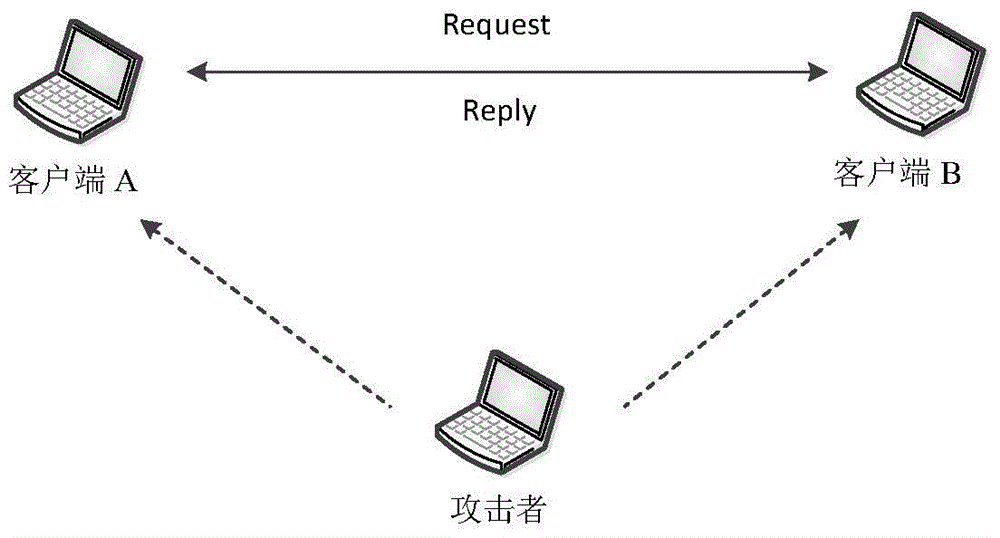
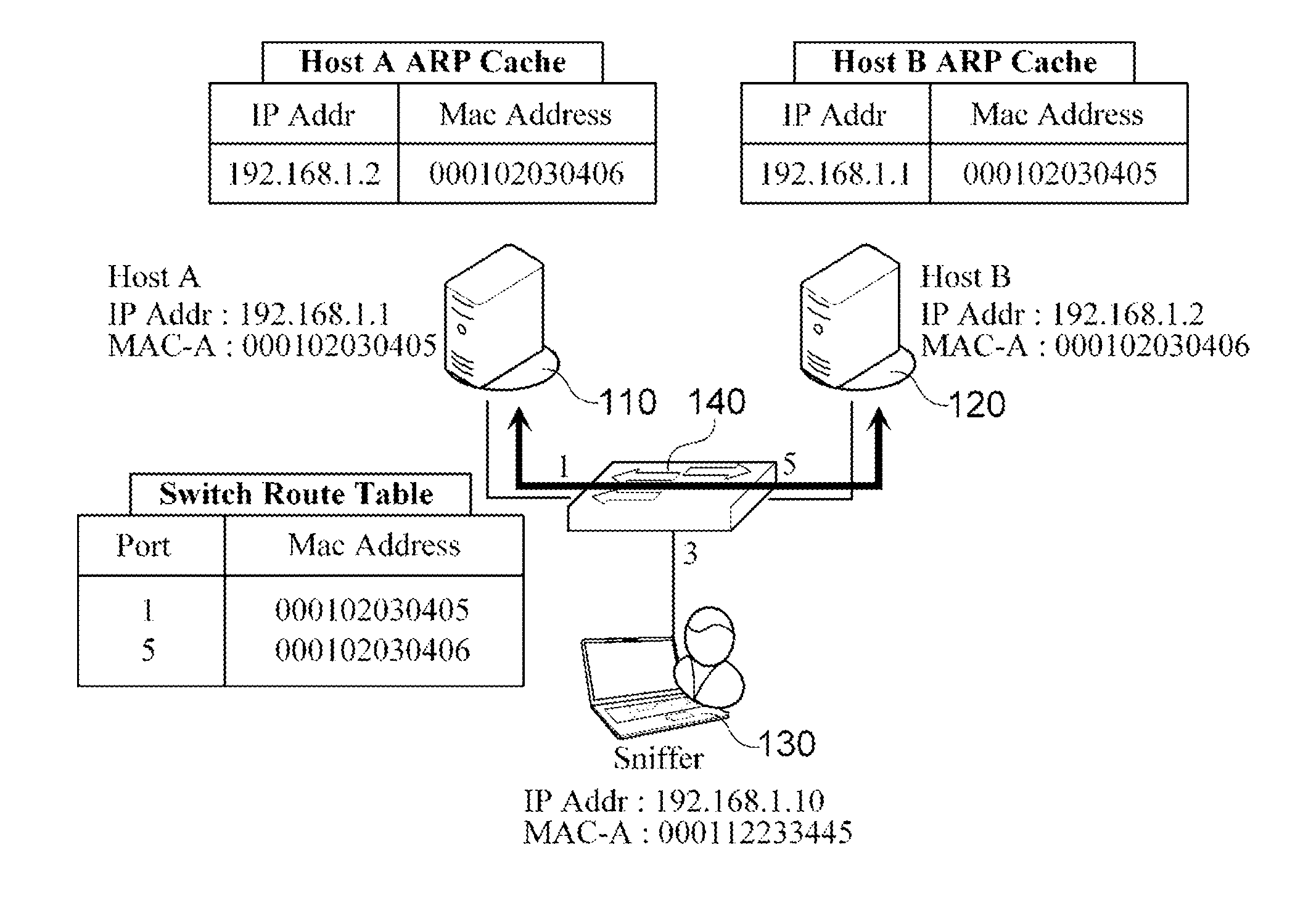
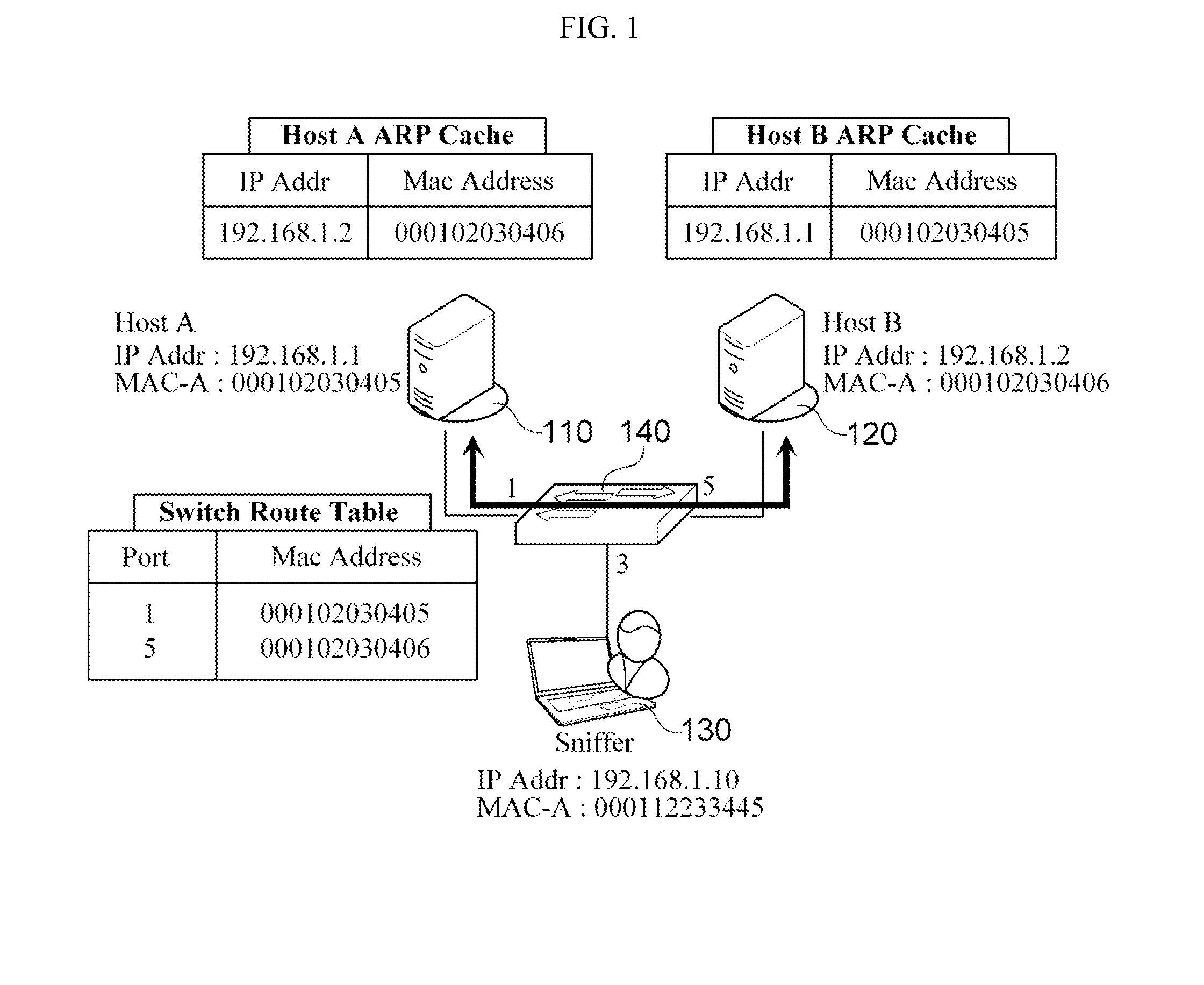
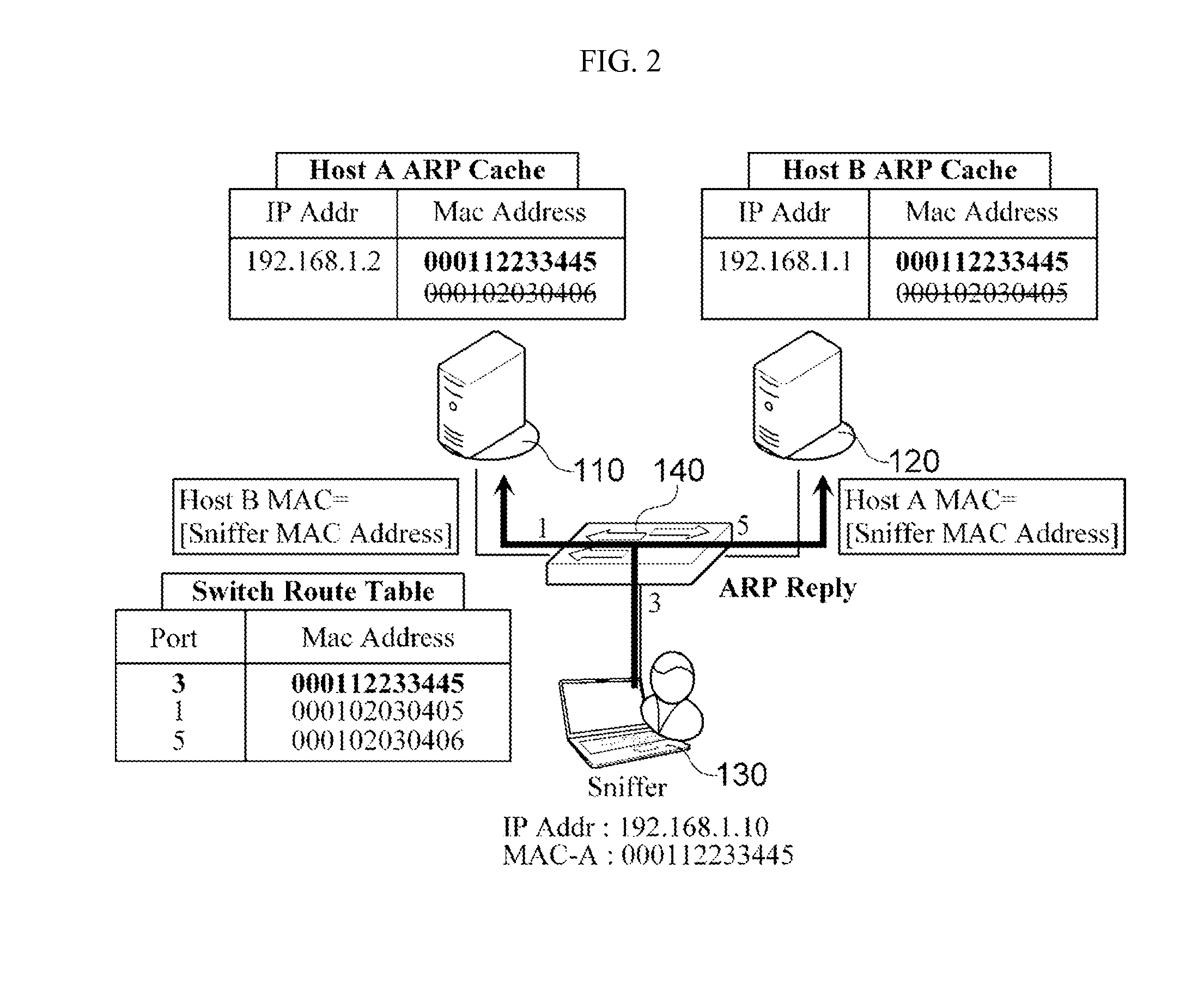
In computer networking, ARP spoofing, ARP cache poisoning, or ARP poison routing, is a technique by which an attacker sends (spoofed) Address Resolution Protocol (ARP) messages onto a local area network. Generally, the aim is to associate the attacker's MAC address with the IP address of another host, such as the default gateway, causing any traffic meant for that IP address to be sent to the attacker instead.
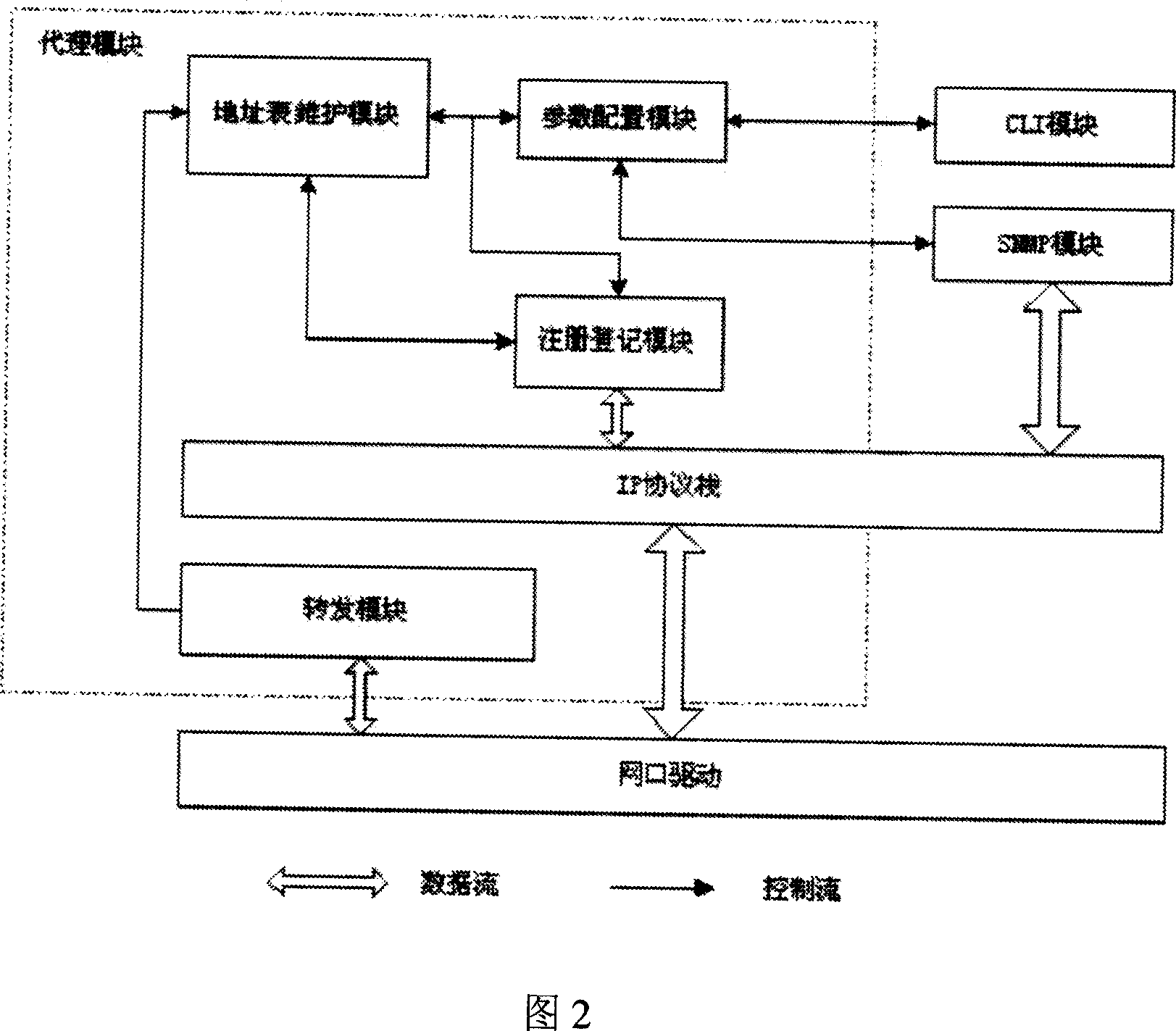
Processing method, access device and communication system for address resolution protocol
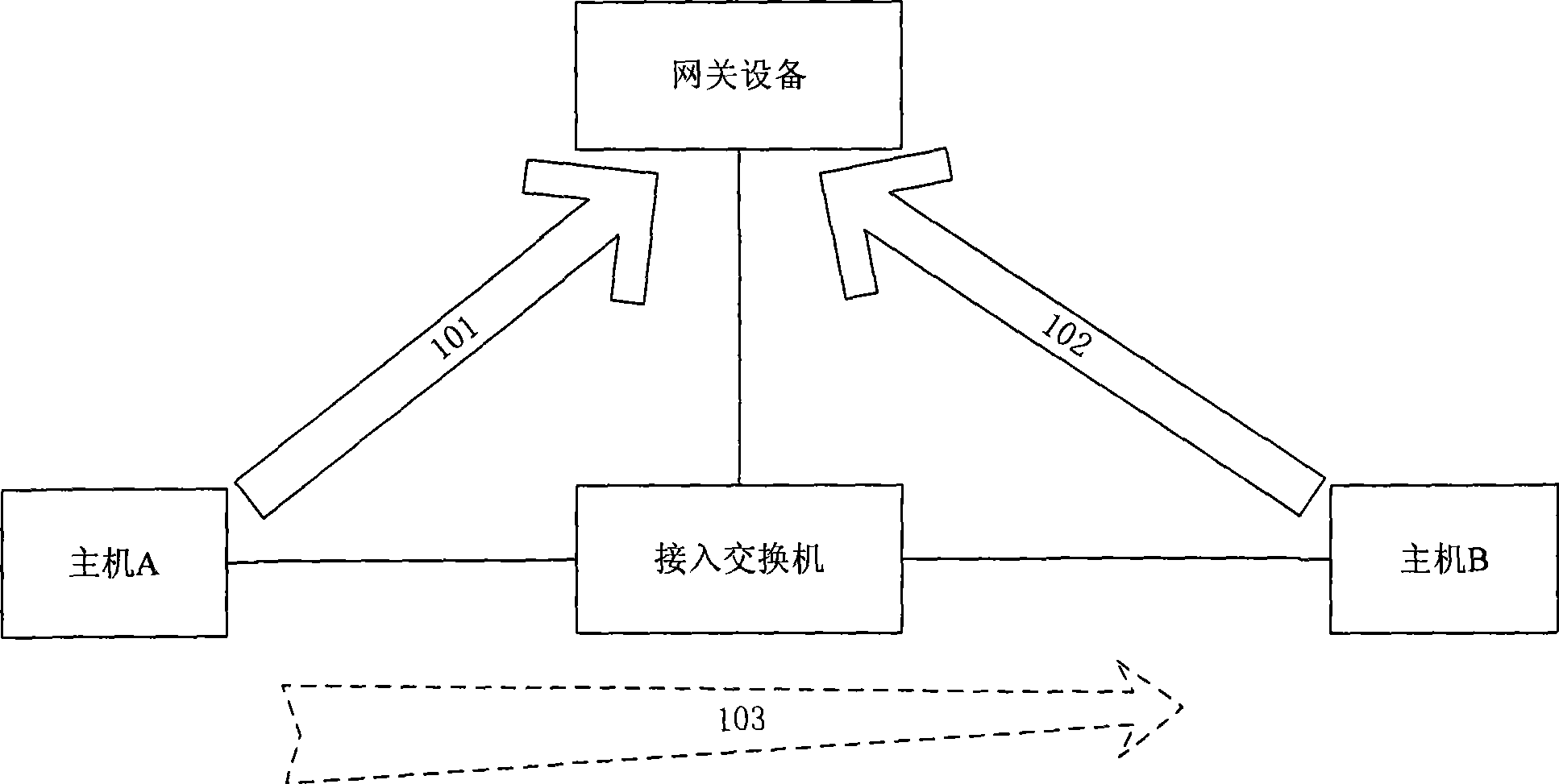
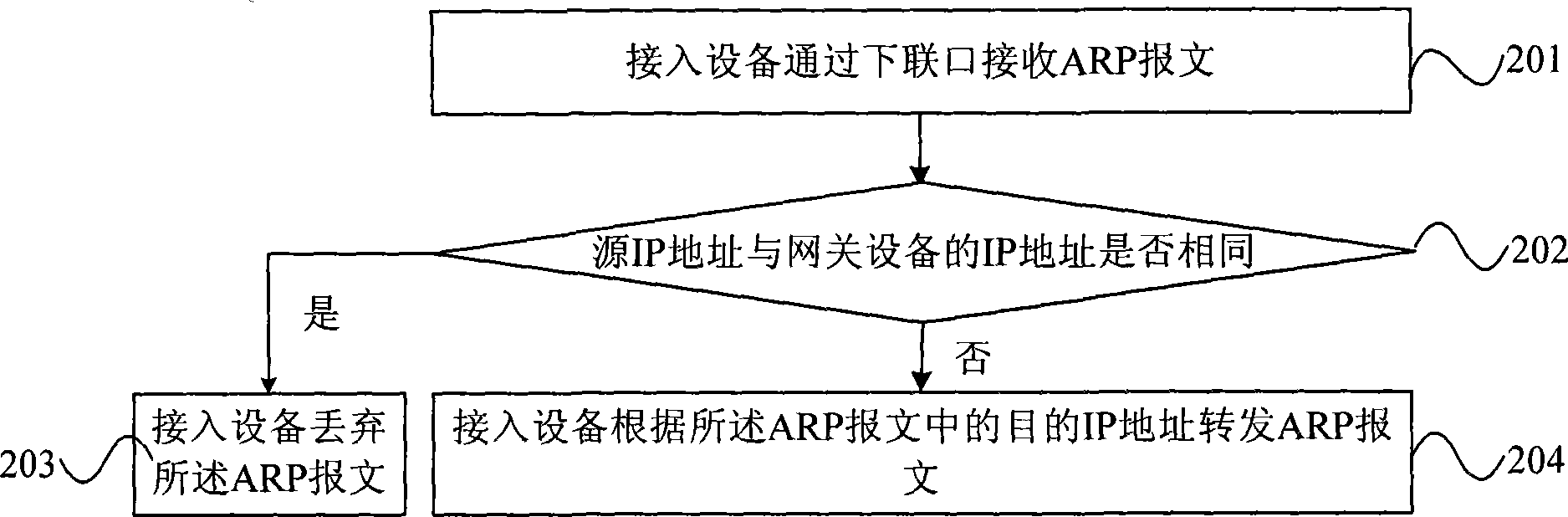
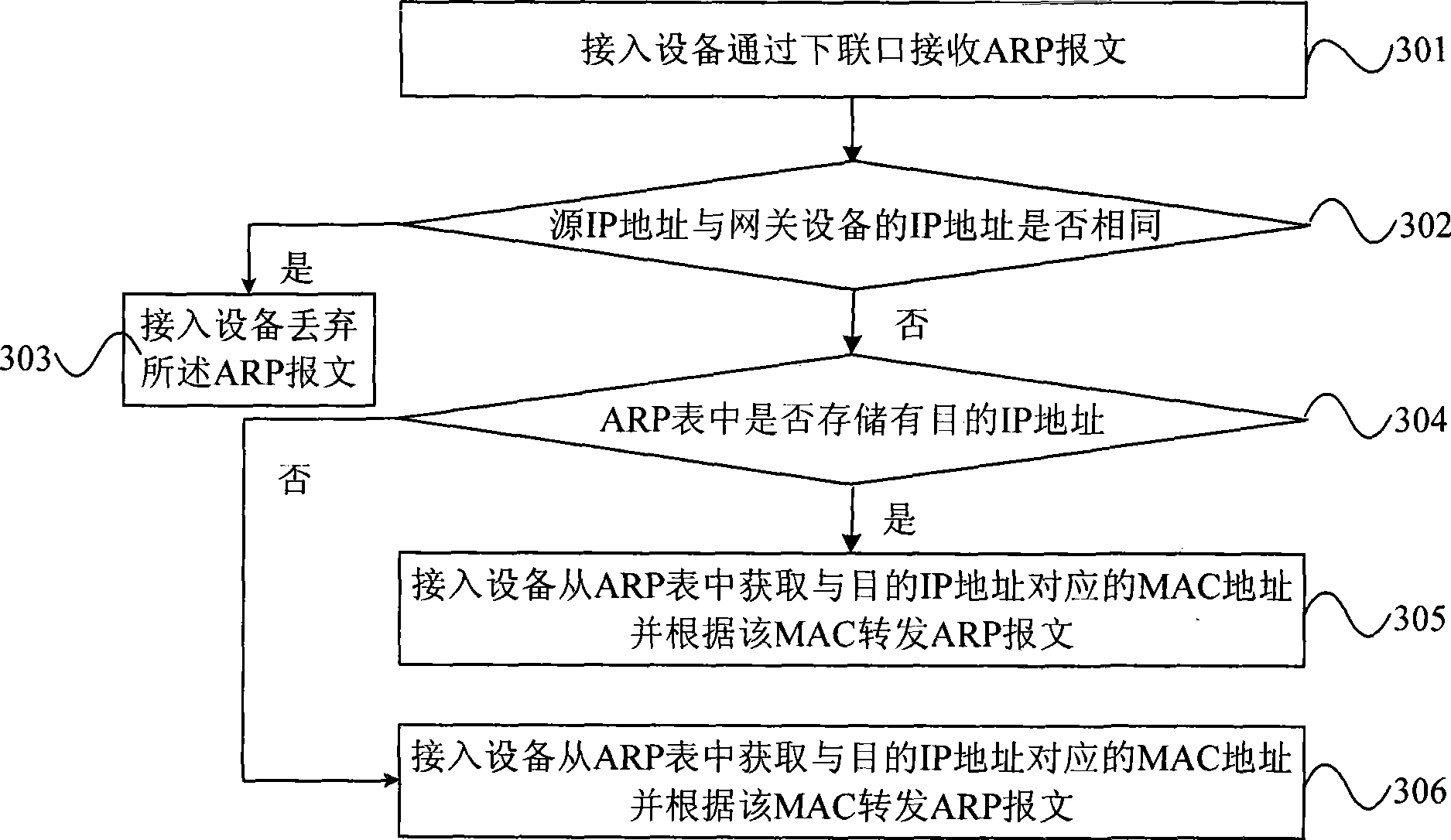
ActiveCN101394360AAvoid vibration and other failuresReduce the burden onData switching networksAddress Resolution ProtocolCommunications system
The invention discloses a method for handling an address resolution protocol (ARP) packet, and access equipment and a communication system thereof. The method comprises the following steps: access equipment receives an ARP packet through a lower interface, which carries an active Internet protocol (IP) address, a source media access control (MAC) address, a destination IP address and a destination MAC address; the access equipment judges whether the source IP address is the same as the IP address of gateway equipment configured on the lower interface, and the upper interface of the access equipment is connected with the gateway equipment; if the source IP address is the same as the IP address of gateway equipment, the access equipment discards the ARP packet; and if the source IP address is different from the IP address of gateway equipment, the access equipment forwards the ARP packet according to the destination IP address in the ARP packet. The embodiment of the invention can prevent the ARP packet which is deceived by an illegal host and passes through the gateway equipment of not performing ARP spoofing with respect to the gateway equipment, without imposing heavier load upon the gateway equipment.
Owner:BEIJING XINWANG RUIJIE NETWORK TECH CO LTD
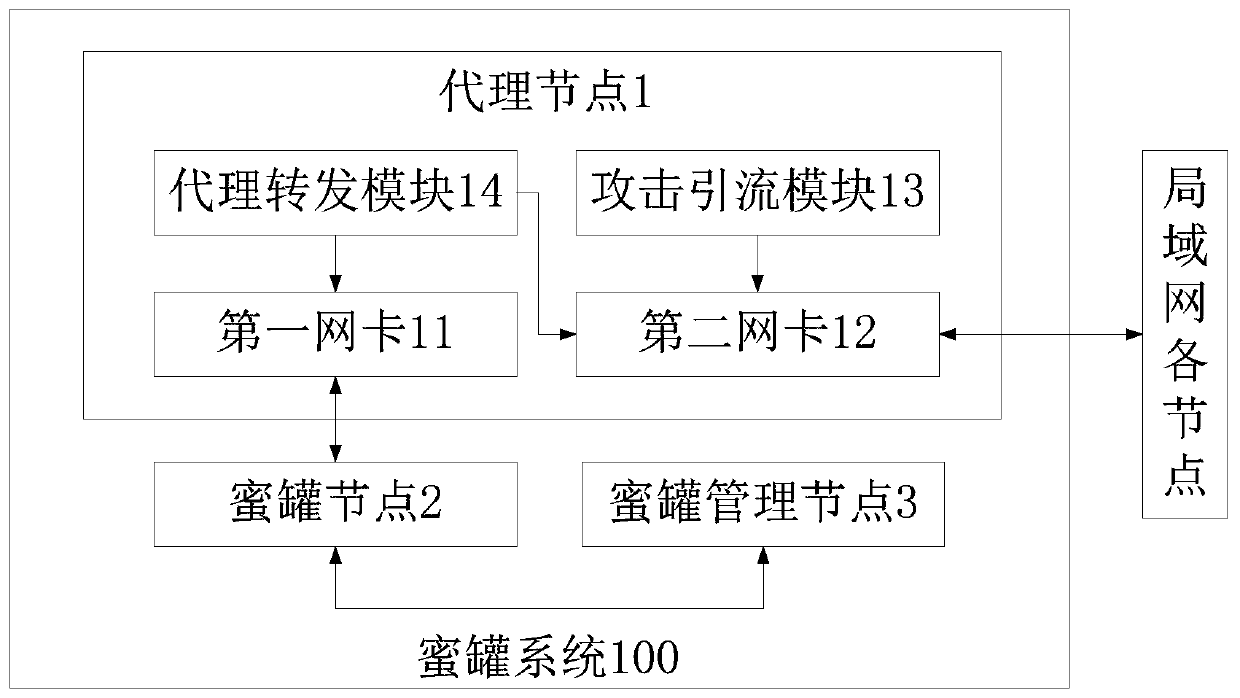
High-coverage intranet honeypot system
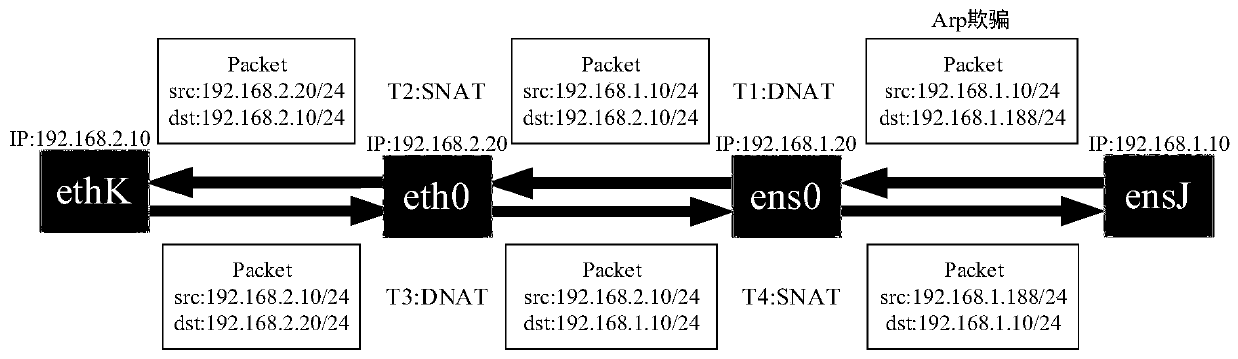
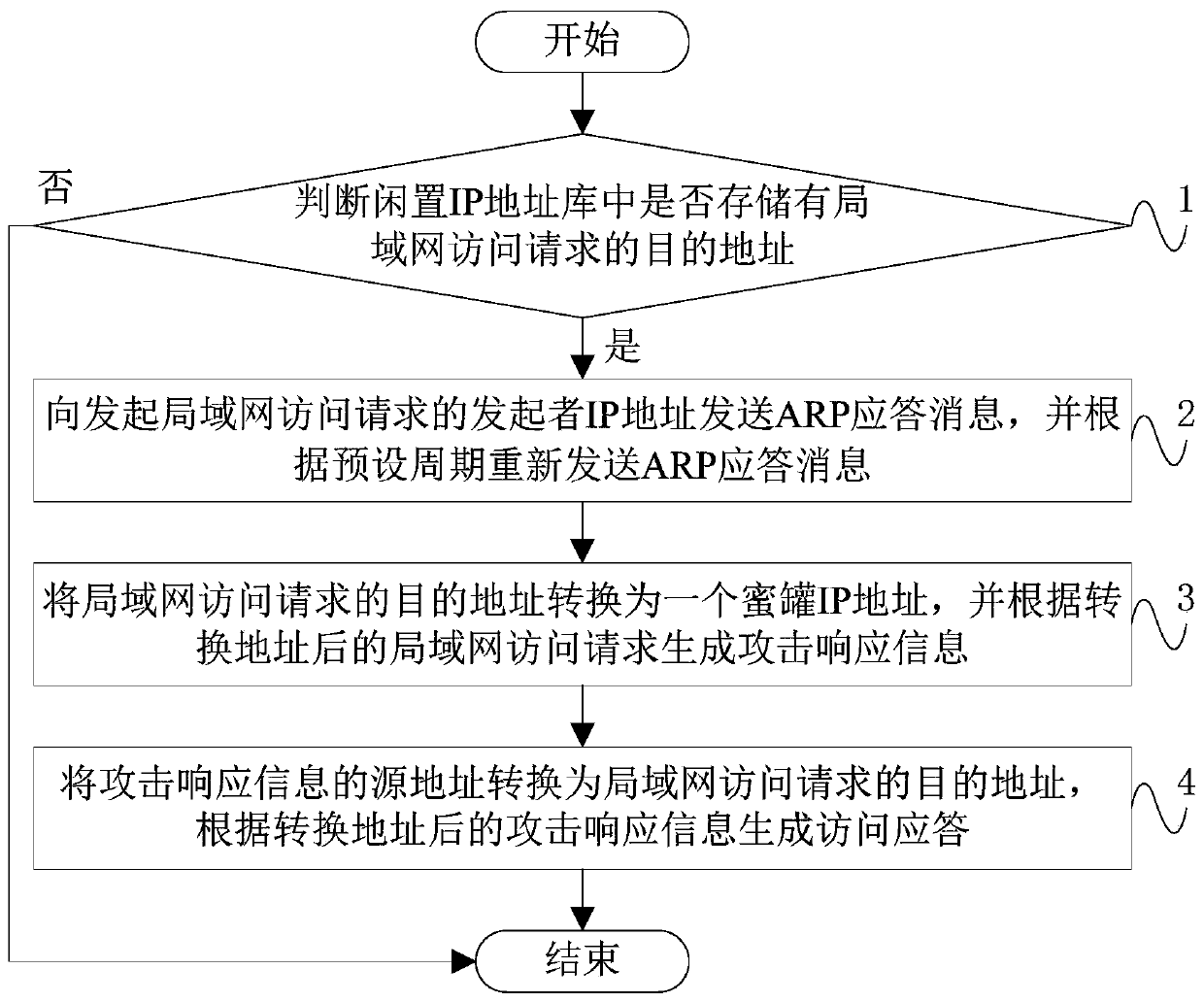
InactiveCN109768993AIncrease the chance of being attackedAvoid occupyingTransmissionIp addressARP spoofing
The invention discloses a high-coverage intranet honeypot system. The honeypot system comprises an agent node comprising an attack drainage module; a first network card, a second network card and a proxy forwarding module, the attack drainage module is used for passing ARP spoofing; guiding a local area network access request of which a destination address is an idle IP address in a network segment where the local area network is located to the agent node, the IP address of the first network card and the IP address of the honeypot are in the same network segment; the first network card is usedfor communicating with a honeypot node; the IP address of the second network card and the IP address of the protected device in the local area network are in the same network segment. The second network card is used for communicating with equipment in the local area network, and the agent forwarding module is used for sending the local area network access request guided to the agent node to the honeypot node and sending attack response information returned by the honeypot node to an initiator IP address of the local area network access request. Through the technical scheme provided by the invention, the IP address coverage rate of the honeypot in the honeypot system is improved while the IP address occupation of the honeypot is reduced.
Owner:中国人民解放军32082部队
System and method for detecting address resolution protocol (ARP) spoofing
ActiveUS20130111589A1Easy to detectMemory loss protectionData taking preventionAddress Resolution ProtocolNetwork packet
There are provided a system and method for detecting Address Resolution Protocol (ARP) attacks. The ARP spoofing attack detection system includes: a reception module which receives an ARP packet, and which determines whether the received ARP packet is an unsolicited ARP packet; a transmission module which creates, if the ARP packet is an unsolicited ARP packet, an ARP request packet corresponding to the unsolicited ARP packet, and which broadcasts the ARP request packet; and a detection module which determines, if an ARP response packet corresponding to the ARP request packet is received, whether an input port of the ARP response packet is identical to an input port of the unsolicited ARP packet, and which determines that an ARP spoofing attack has occurred if the input port of the ARP response packet is not identical to the input port of the unsolicited ARP packet.
Owner:SAMSUNG SDS CO LTD
Method and system for preventing local area network ARP defection attacks
InactiveCN101635713AAvoid sendingBlocking deceptionData switching networksOperational systemAddress resolution
The invention discloses a method for preventing local area network ARP defection attacks, which mainly comprises the following steps: disposing a defined address resolution mapping table between a network card and an operating system of a terminal host in a local area network to ensure that each terminal only has one IP and MAC mapping relation; ensuring the correctness of the mapping table by a service program; and ensuring whether the ARP is reliable or not by matching ARP packs transmitted and received by the terminal host and the mapping table. The invention also discloses a system for preventing local area network ARP defection attacks; and the terminal host can defense the ARP attacks of a local host and the outside in the local area network.
Owner:BEIJING ANTIY NETWORK SAFETY TECH CO LTD
Method and apparatus for defending against arp spoofing attacks
ActiveUS20100107250A1Reliable and effective ARP verificationReduce signaling interactionMemory loss protectionDigital data processing detailsAddress Resolution ProtocolIp address
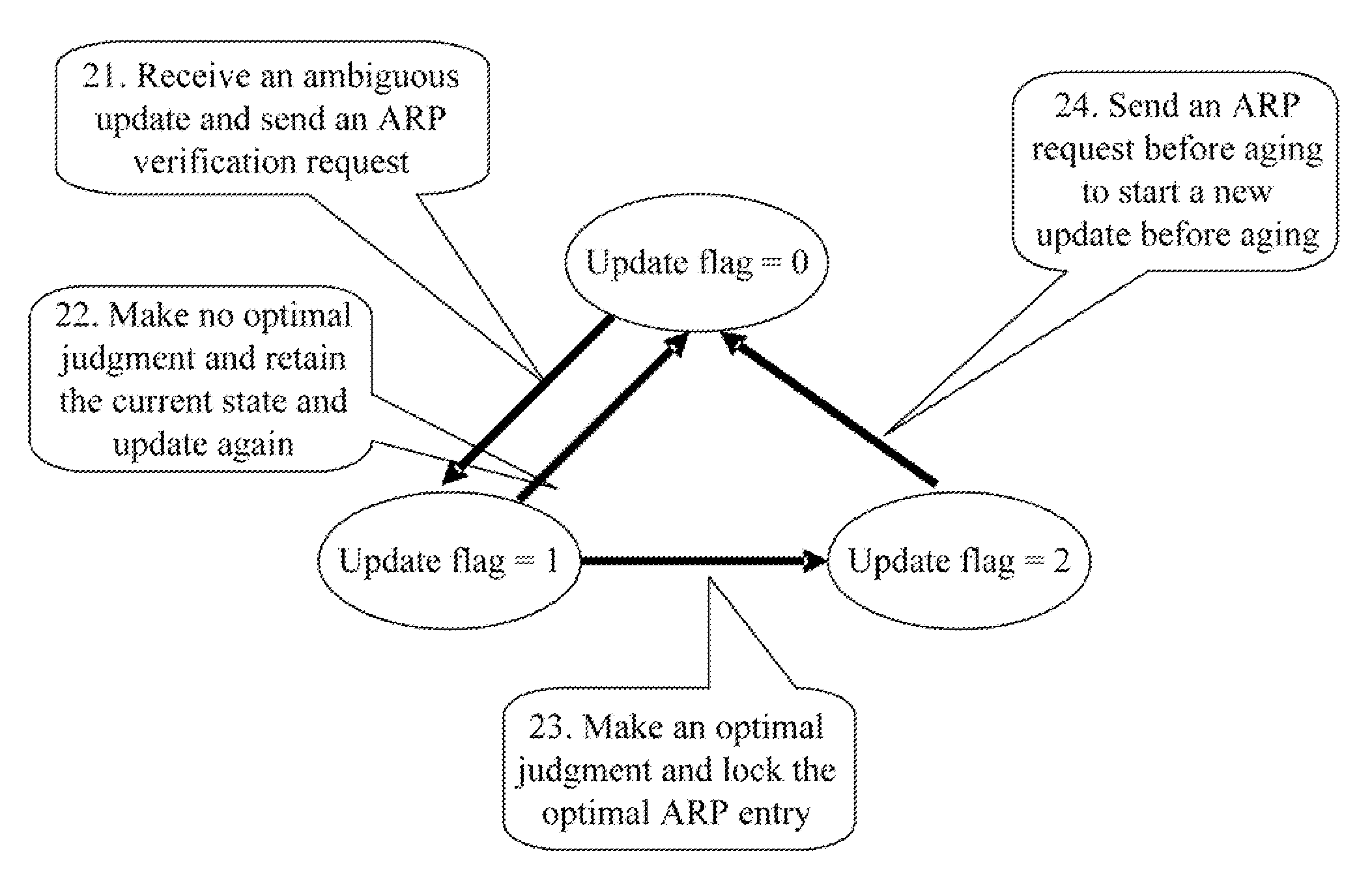
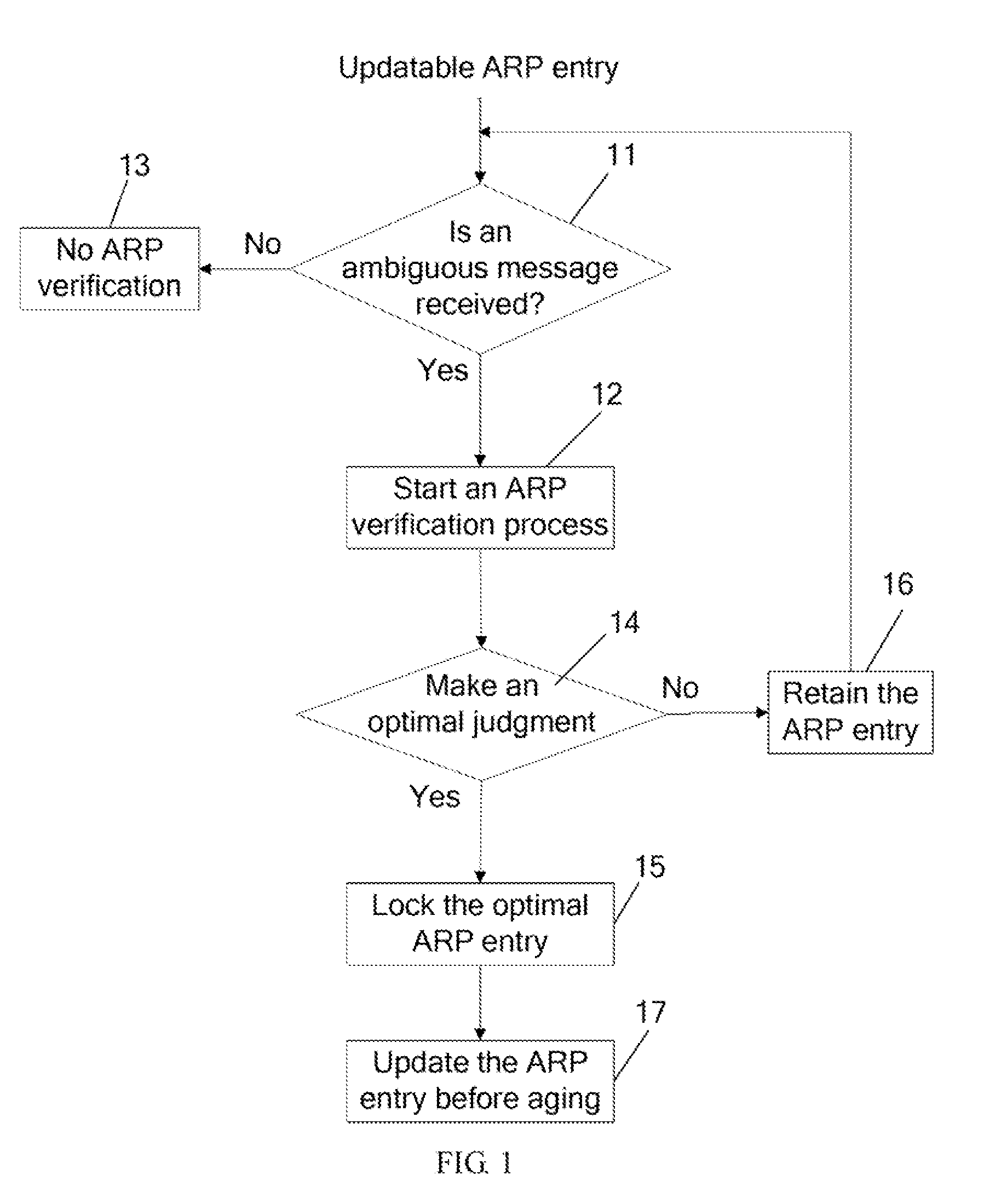
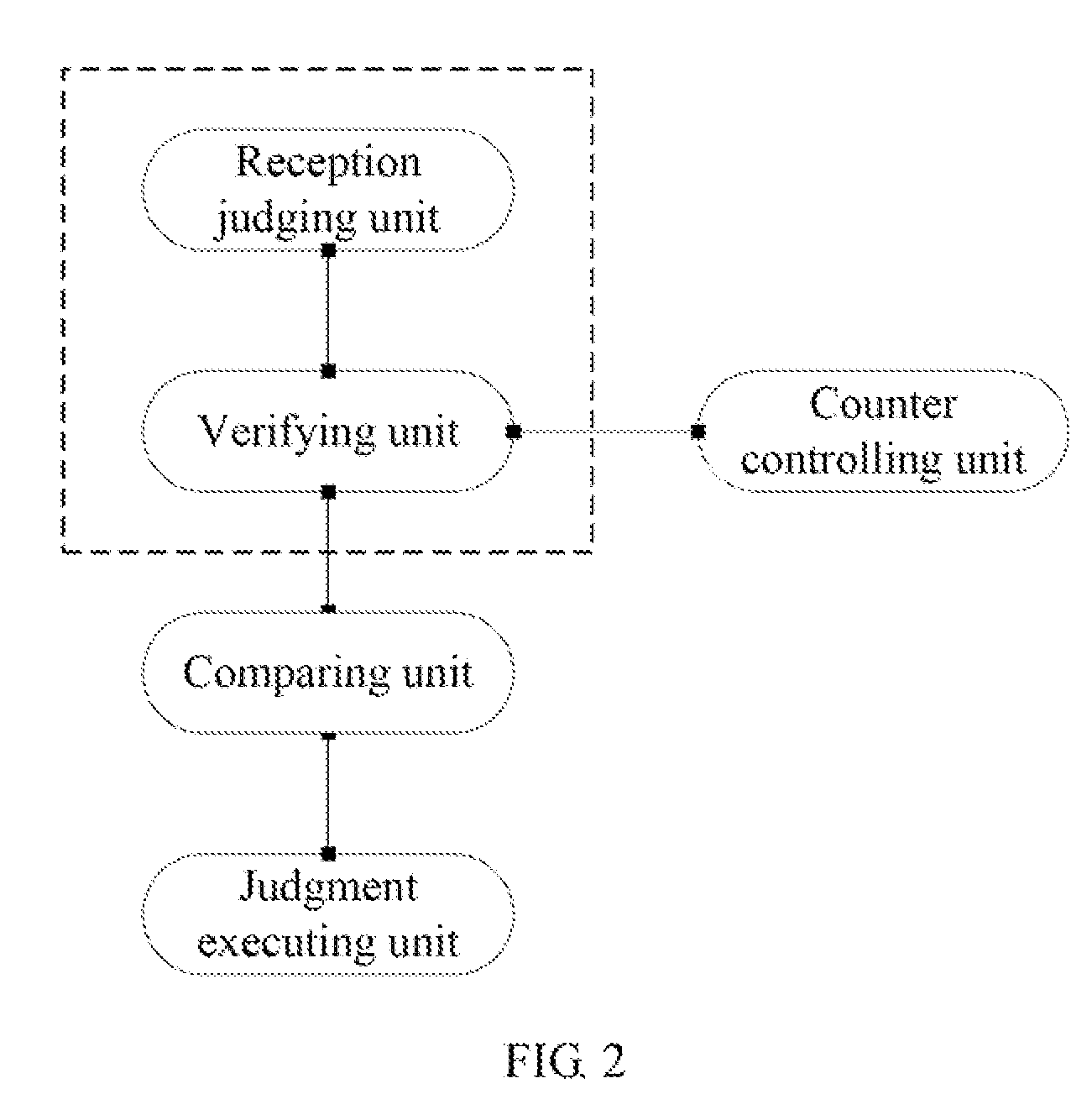
A method and an apparatus for defending against Address Resolution Protocol (ARP) spoofing attacks are disclosed. The method includes: when an ARP entry is updatable, judging whether the MAC address of a received ARP message is the same as the MAC address in the ARP entry, where the ARP message has the same Internet Protocol (IP) address as the ARP entry; if the MAC addresses are different, determining the received ARP message as an ambiguous ARP message and starting an ARP verification process, or else starting no ARP verification. In this way, when no address spoofing attacks occur, no verification messages are generated, and thus reducing signaling interactions and saving network resources; besides, spooling attacks possibly happening at any time are avoided, which effectively prevents address spoofing attacks via random scanning and protects the normal application of the real host.
Owner:HUAWEI TECH CO LTD
Software defined network (SDN) broadcast processing method based on cycle trigger agent
InactiveCN103209225ABroadcast EliminationData switching networksTraffic capacityAddress Resolution Protocol
The invention provides a software defined network (SDN) broadcast processing method based on a cycle trigger agent. The method solves the problem of address resolution protocol (ARP) broadcast in the Ethernet. Whole network host information hash tables (IP-to-MAC and MAC-MAP) are established at the initial stage of accessing a host to a network, and an update strategy for the IP-to-MAC table and the MAC-MAP table is raised, so that a control end can uniformly respond to the ARP request of any host in the network, and flooding of the whole network is avoided. The method is applied to a screen of a random centralized network architecture, and has the characteristics of eliminating the ARP broadcast in the Ethernet, reducing the network traffic and the host load pressure, effectively preventing dynamic host configuration protocol (DHCP) spoofing, avoiding ARP spoofing, supporting the motion of the host and the like.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Method and device used for synchronous ARP (Address Resolution Protocol) list item of virtual router redundancy protocol backup set
ActiveCN103001868ASave resourcesData switching networksAddress Resolution ProtocolNetwork management
The invention discloses a method and a device used for synchronous ARP (Address Resolution Protocol) list item of a virtual router redundancy protocol backup set. In the invention, a Master member device is capable of imitating a local host to realize ARP spoofing for a Backup member device, and the Backup member device is promoted to carry out ARP learning through the ARP spoofing of the Backup member device, so that the Backup member device and the Master member device can establish ARP list item synchronously. Therefore, while the ARP list item is realized synchronously, the improvement of announce message for virtual router redundancy protocol is not required, and dependence on the support of network management is not required.
Owner:NEW H3C TECH CO LTD
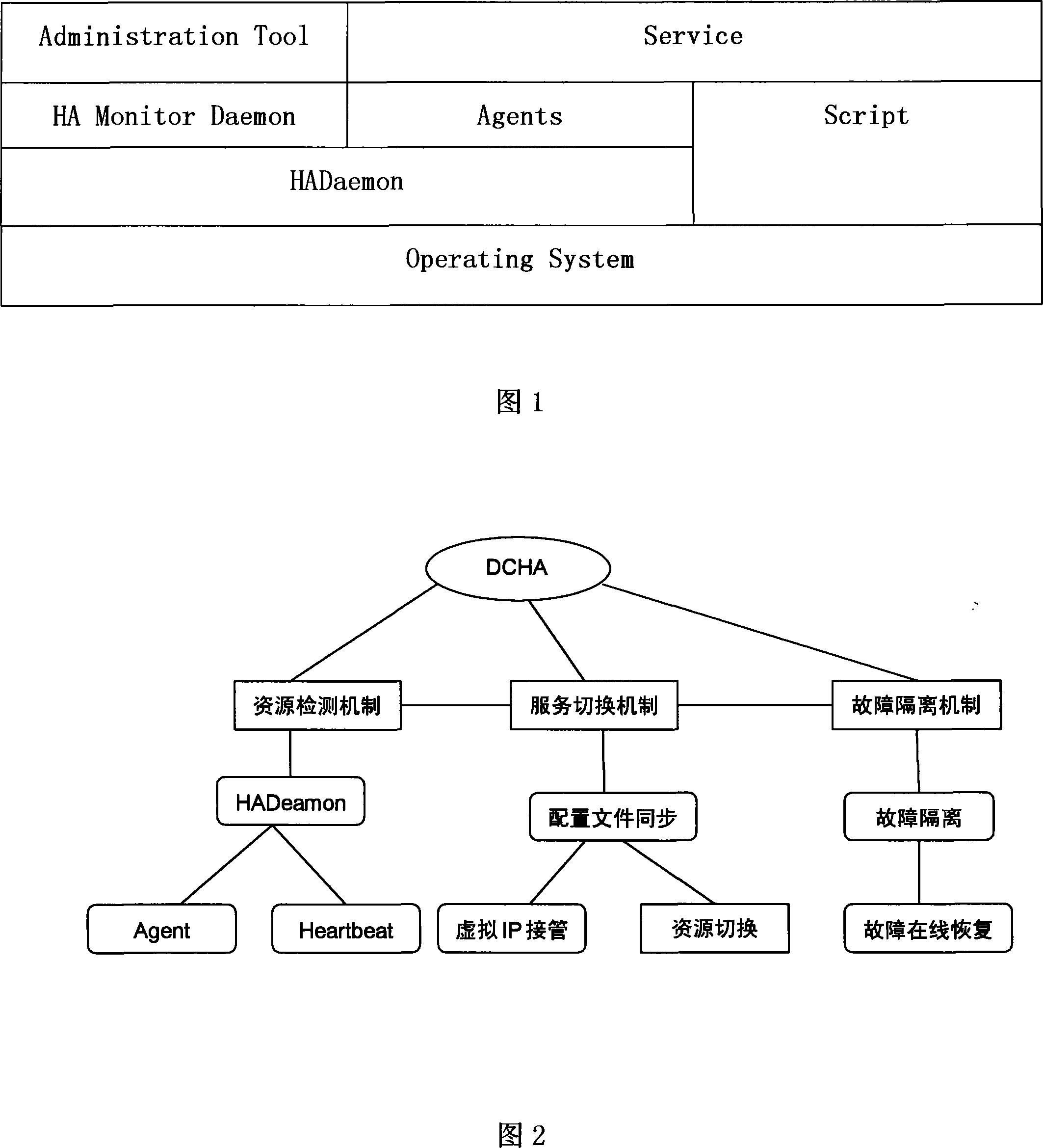
A synchronous detection and failure separation method for dual control high-availability system
InactiveCN101237315ARealize seamless switchingAvoid single point of failureError preventionData switching networksARP spoofingControl theory
The invention provides a method of synchronous detection and failure isolation for a double control highly available system. The system is provided with two controllers which use special channels integrated on a PCI mainboard, serial ports or network card cables to monitor the HADaemon process of the counterpart. When a failure appears, a primary controller and a secondary controller conduct the following control steps of: 1), the primary controller releases virtual IPs of a server and the secondary controller takes over the IPs through ARP deception; 2), the resources of the main controller are hung and send state information to the primary controller, and a related service is started to realize seamless switching; 3), during the taking over of IP and the switching of servers, an alarm is given in an email log; 4), the primary controller after restoration choose takeover service or no takeover as a backup of synchronous detection; 5), in order to improve the availability of heartbeat transmission, network cards and serial ports are used together to avoid single point failure of a link; 6), a failure occuring in a network for external services of the primary controller can also be detected by the HADaemon which then triggers the primary controller to take over the virtual IP and switch the resources.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
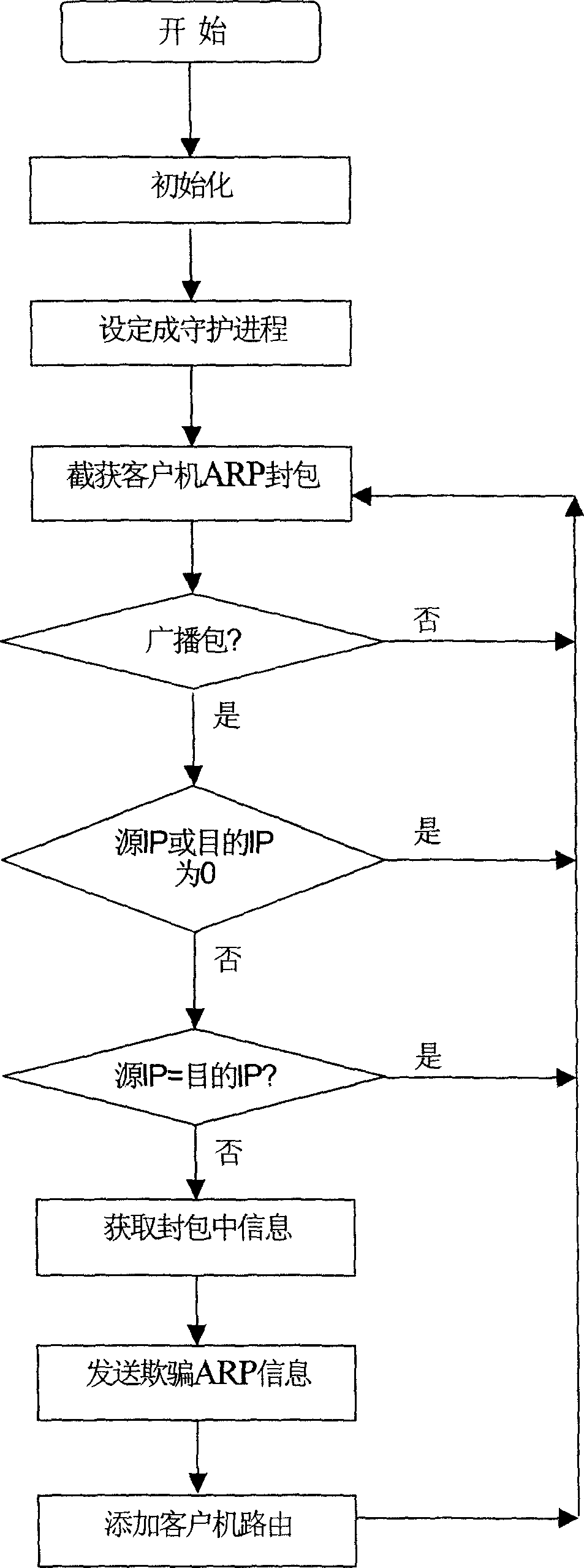
Immediate plug and instant use proxy gateway and method thereof
InactiveCN1674563ANo added costNo increase in productivityNetwork connectionsBroadcast packetThe Internet
The present invention provides a plug and play proxy gateway and its method. It can make user have no need of changing network configuration of customer machine and can access interconnected network. Said invention includes a network equipment, in said network equipment are mounted a web card and a proxy gateway execution module, said proxy gateway module includes: an ARP broadcast packet interception submodule, an ARP deception packet generation and transmitting submodule and a customer machine route list, and an ARP response packet interception submodule. Said invention also provides the concrete function and action of every above-mentioned submodule and customer machine.
Owner:MICROIT NETWORK COMM CO LTD
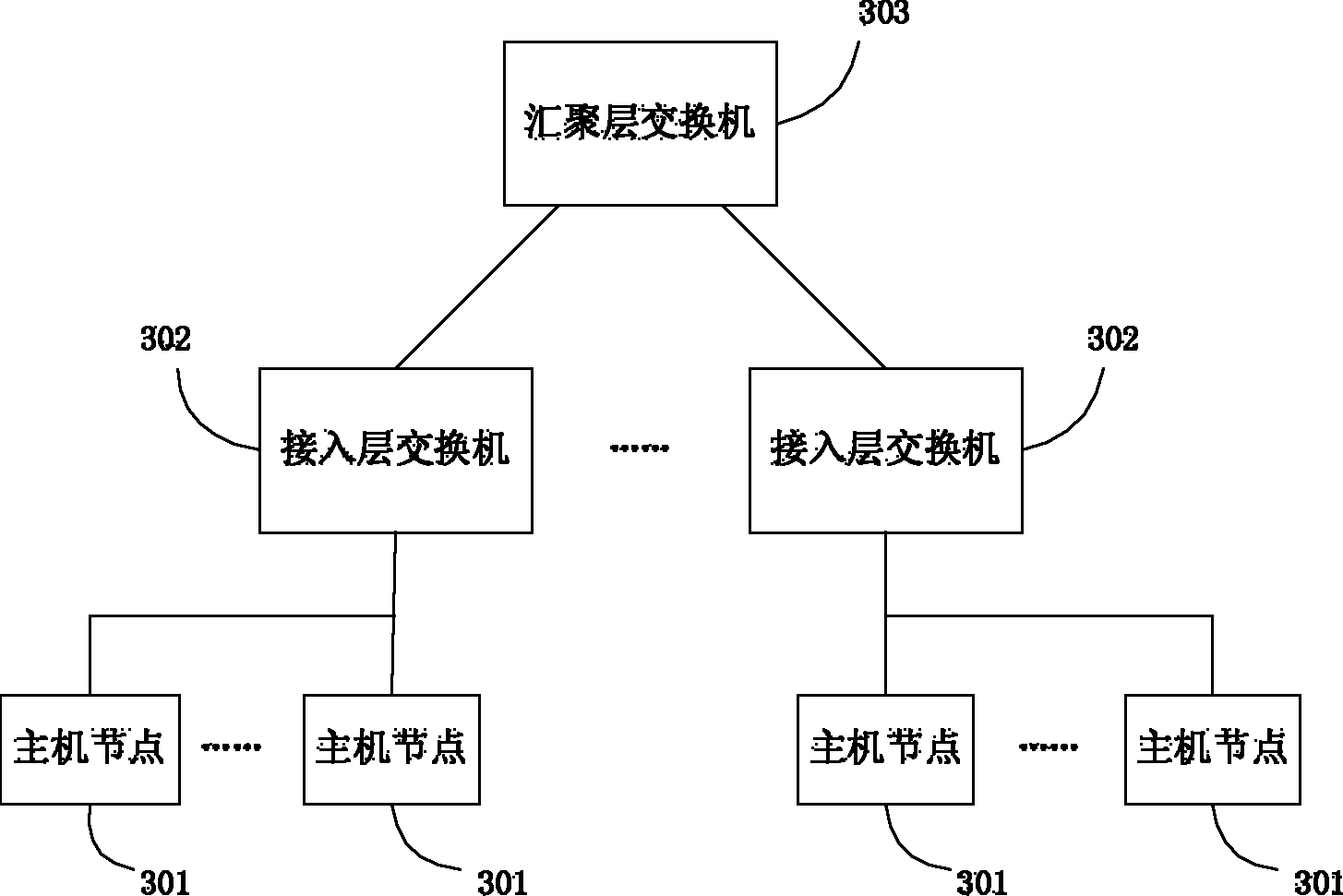
Method and system for preventing address resolution protocol (ARP) gateway spoofing
InactiveCN102546658ASolve the problem of ARP spoofingRelieve CPU pressureData switching networksAddress Resolution ProtocolAddress resolution
The invention discloses a method and a system for preventing address resolution protocol (ARP) gateway spoofing. The method comprises the following steps that: a convergence-layer switch stores a mapping relationship between the Internet protocol (IP) address and media access control (MAC) address of each layer-three interface, and transmits the mapping relationship to an access-layer switch; the access-layer switch stores the mapping relationship in a mapping table, and enables an ARP monitoring function; and the access-layer switch receives an ARP message, discards the ARP message when the IP address of an ARP message transmission or receiving party is an IP address in the mapping table and the MAC address of the ARP message transmission or receiving party is inconsistent with a corresponding MAC address in the mapping table, and forwards the ARP message when the IP address of the ARP message transmission or receiving party is not the IP address in the mapping table. By the method and the system, the problem of ARP IP gateway spoofing in a network is solved; and the ARP monitoring function is devolved to the access-layer switch, so that the pressure of a central processing unit (CPU) of the convergence-layer switch is greatly alleviated.
Owner:北京神州数码云科信息技术有限公司
A method for preventing the address parsing cheating
InactiveCN101009689APrevent cheatingImprove securityData switching networksCommunications securityComputer hardware
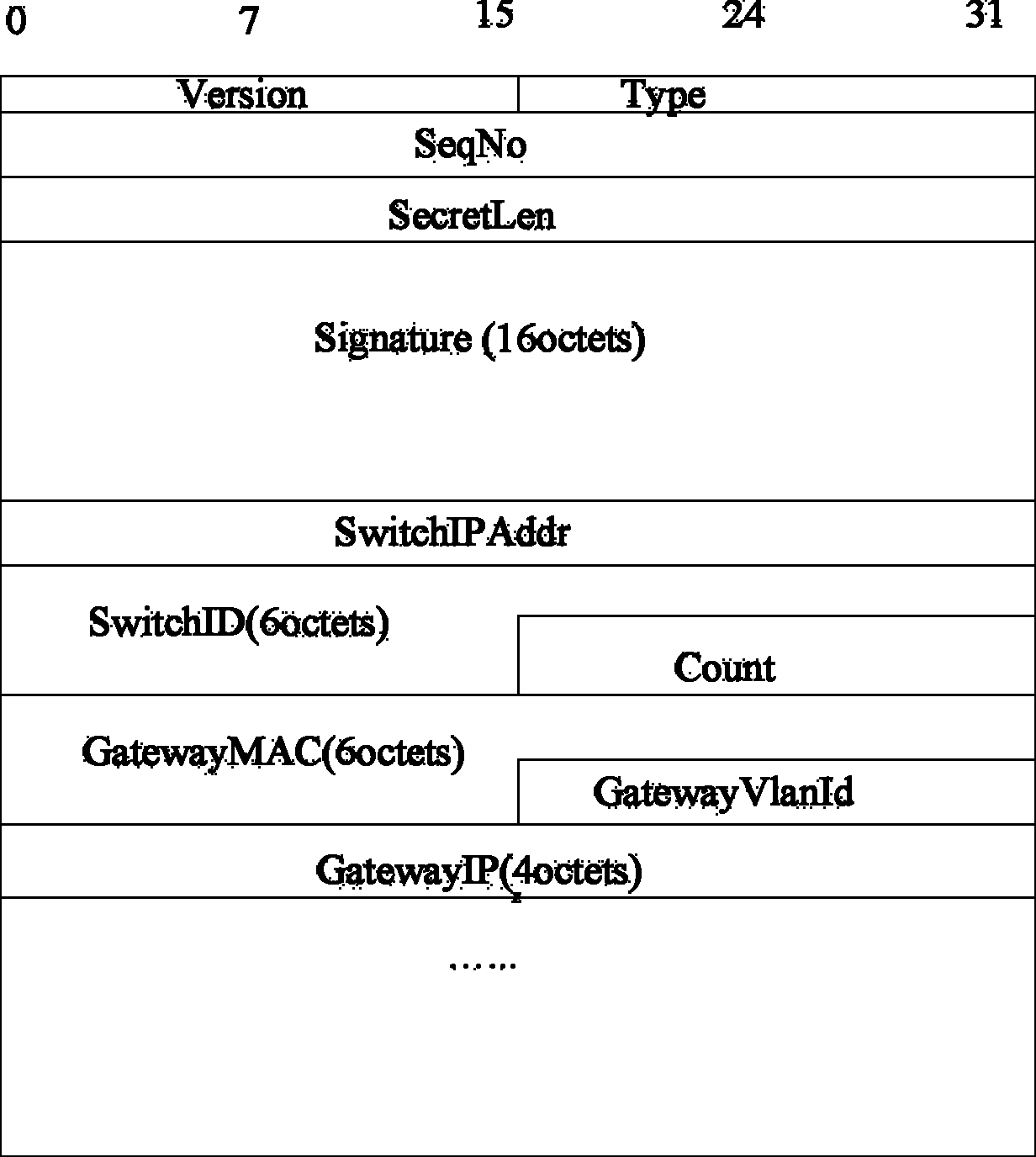
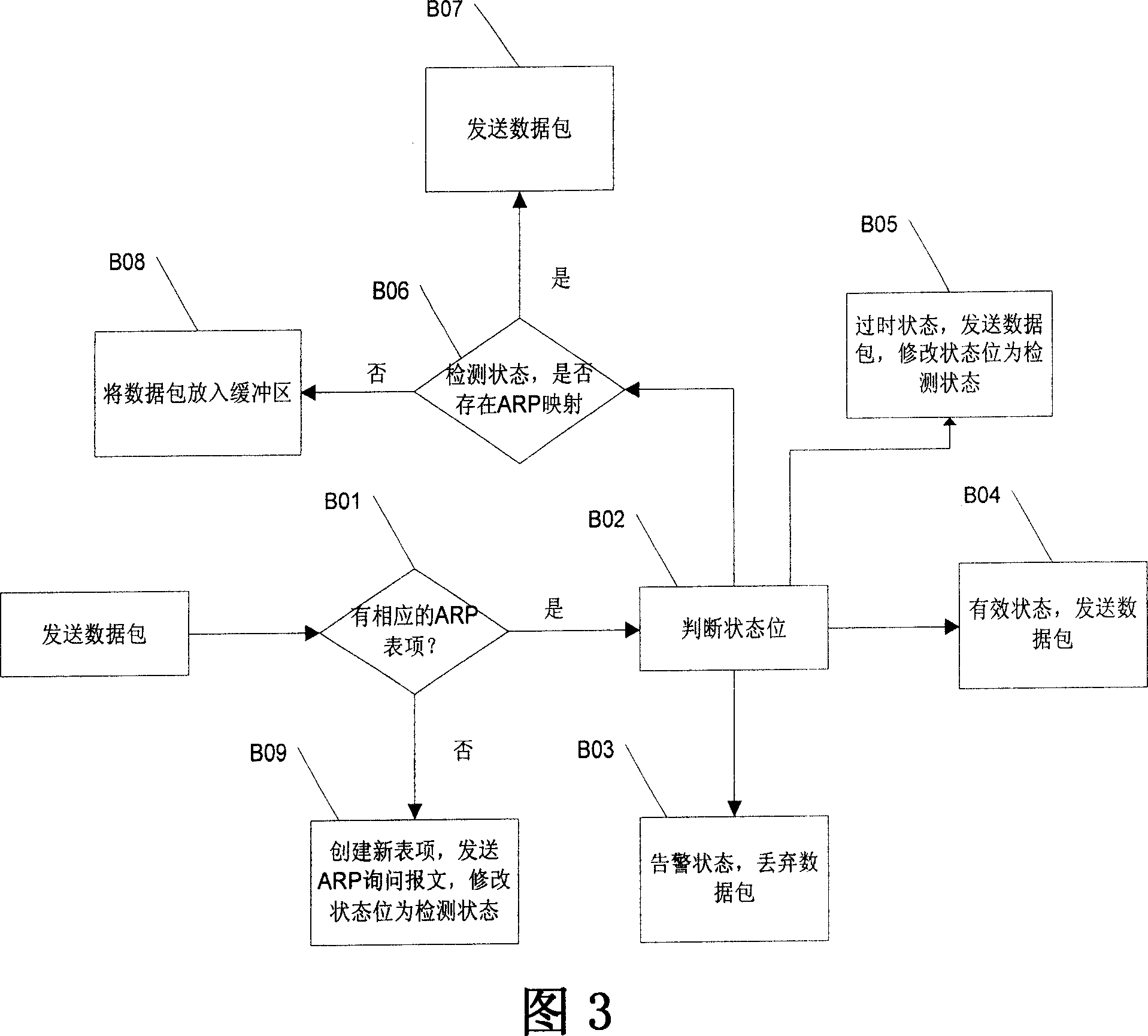
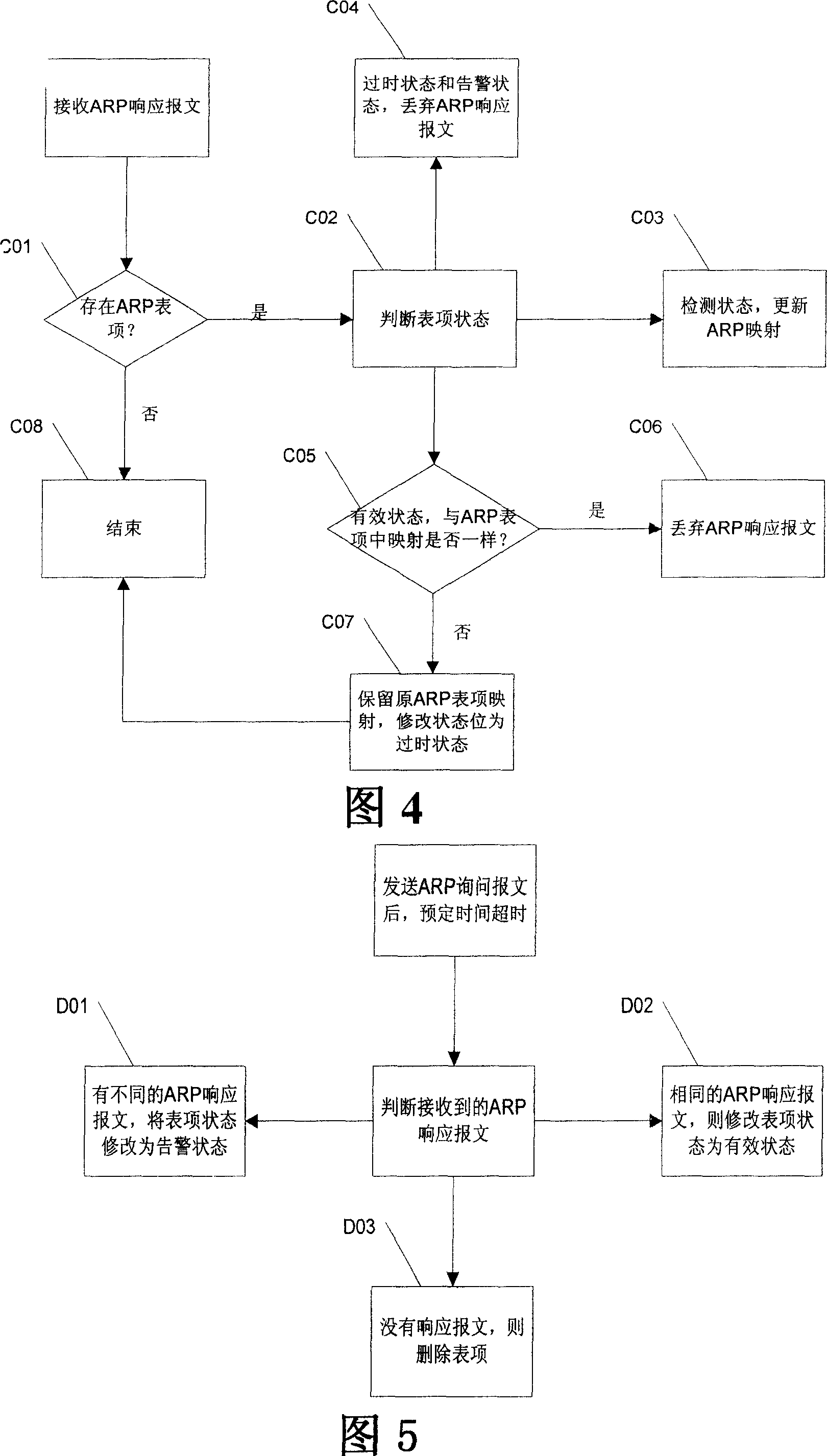
The related method resistant to address analysis cheat for network communication security comprises: adding a state bit into the item of local host ARP buffer table, receiving remote ARP message, modifying the corresponding state bit in local host ARP table, and processing the message according to said state bit. This invention just needs a little of network source to improve computer security conveniently.
Owner:SIEMENS CHINA
Address resolution protocol (ARP) message processing method, device and access equipment
ActiveCN101888329AReduce the burden onPrevent ARP SpoofingData switching networksNetwork deploymentAddress Resolution Protocol
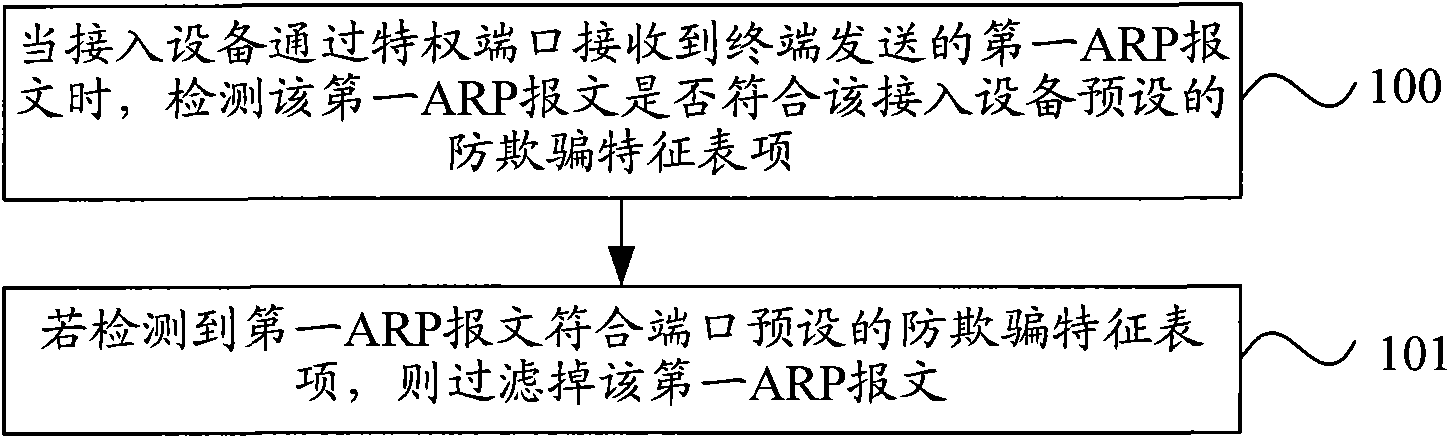
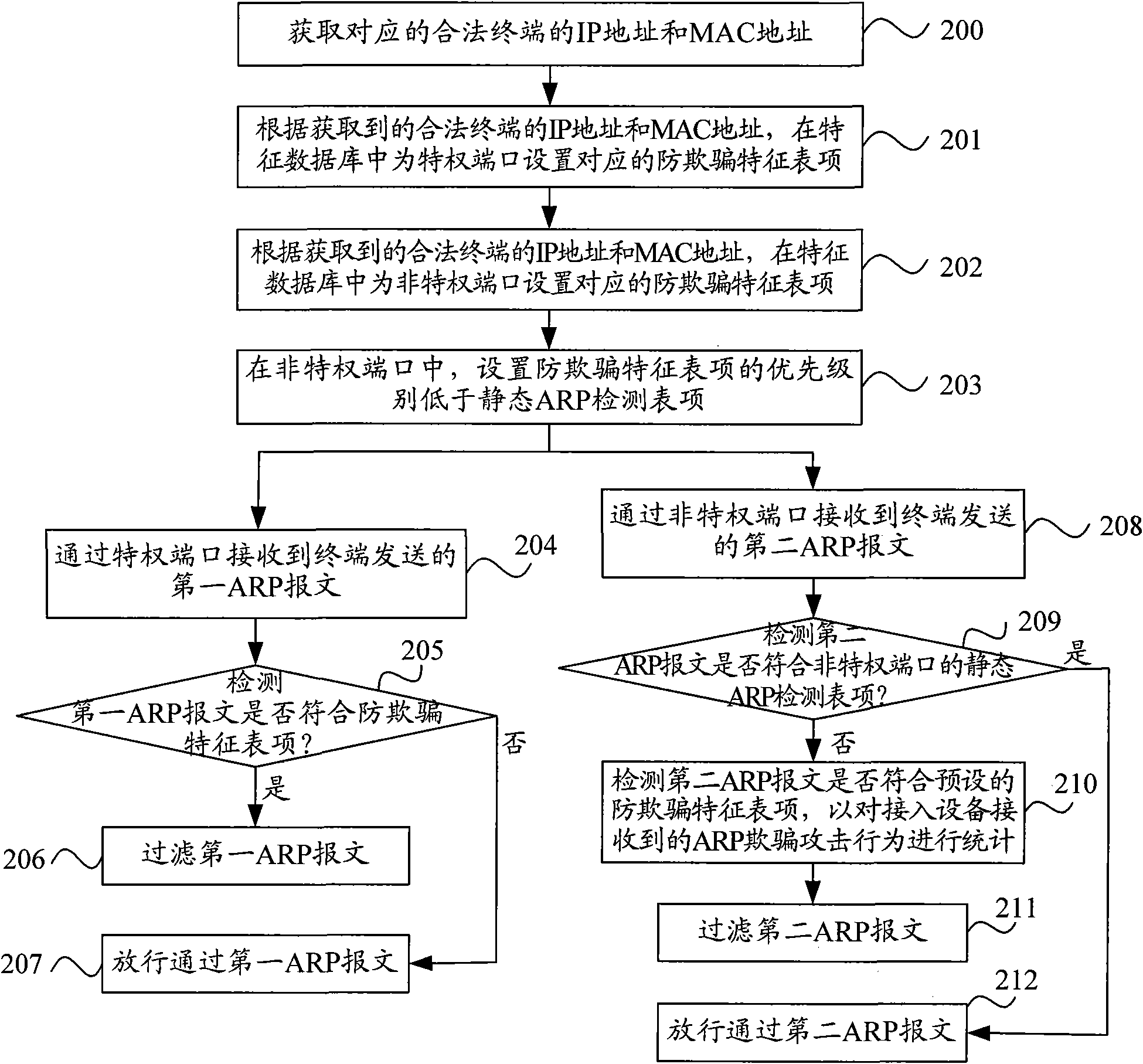
The invention provides address resolution protocol (ARP) message processing method, device and access equipment. The method comprises the following steps of: detecting whether an ARP message conforms to the preset anti-cheating feature entry of the access equipment when the access equipment receives the ARP message transmitted by a terminal through privileged ports, wherein the anti-cheating feature entry comprises the filtration of ARP messages of which the transmit leg IP address is the IP address of any legal terminal of the access equipment and ARP messages of which the transmit leg MAC address is the MAC address of any legal terminal, and the privileged ports comprise ports which do not set up static ARP detection functions; and if the ARP message conforms to the preset anti-cheatingfeature entry, filtering the ARP message. The invention effectively prevents an illegal terminal from carrying out ARP cheat by personating a legal terminal through privileged ports. Besides, the invention can be realized without the participation of gateway equipment and a user's host, thereby ensuring simple network configuration and improving the flexibility, the stability and the safety of network allocation.
Owner:BEIJING XINWANG RUIJIE NETWORK TECH CO LTD
Message processing method, device and network equipment
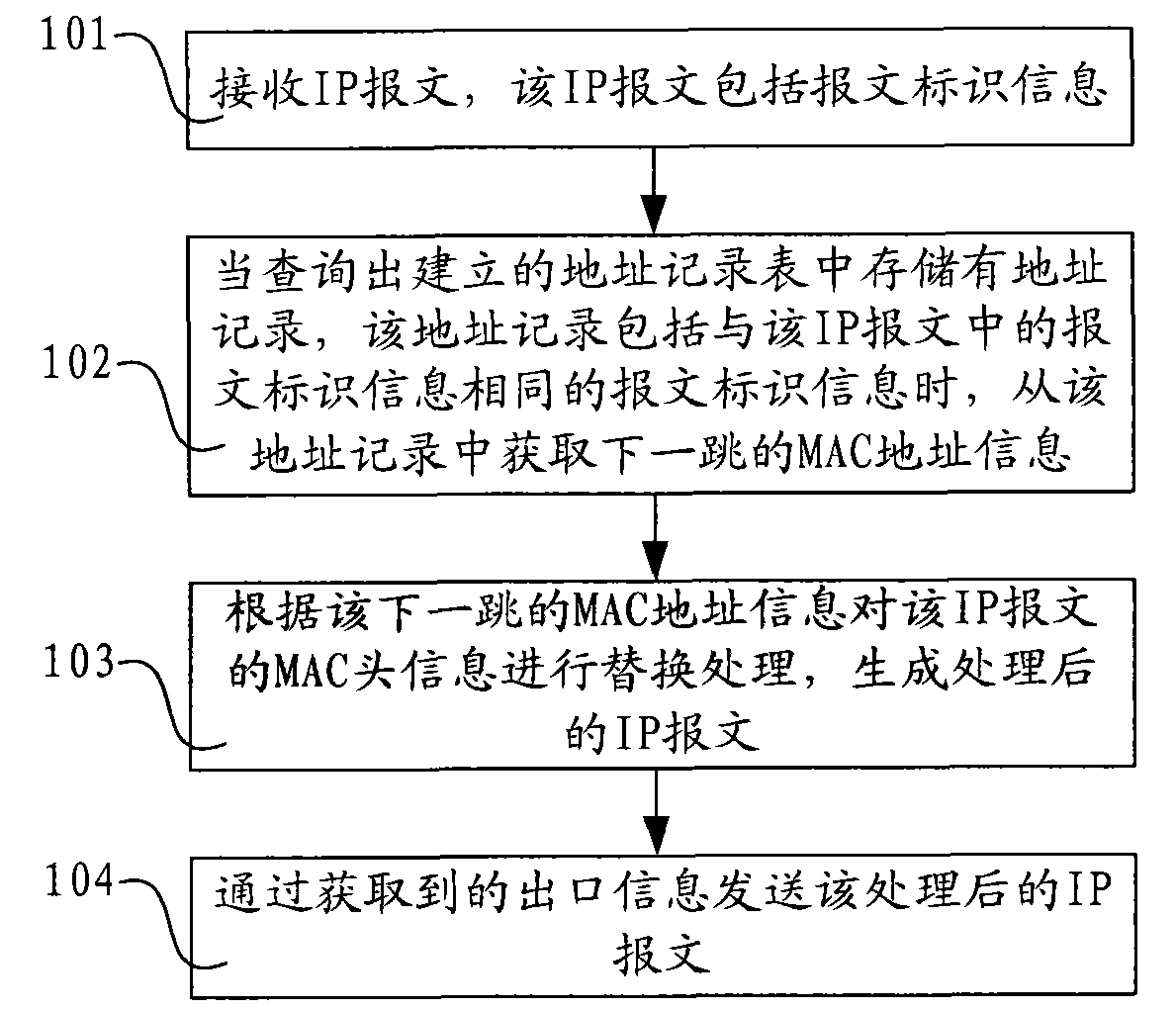
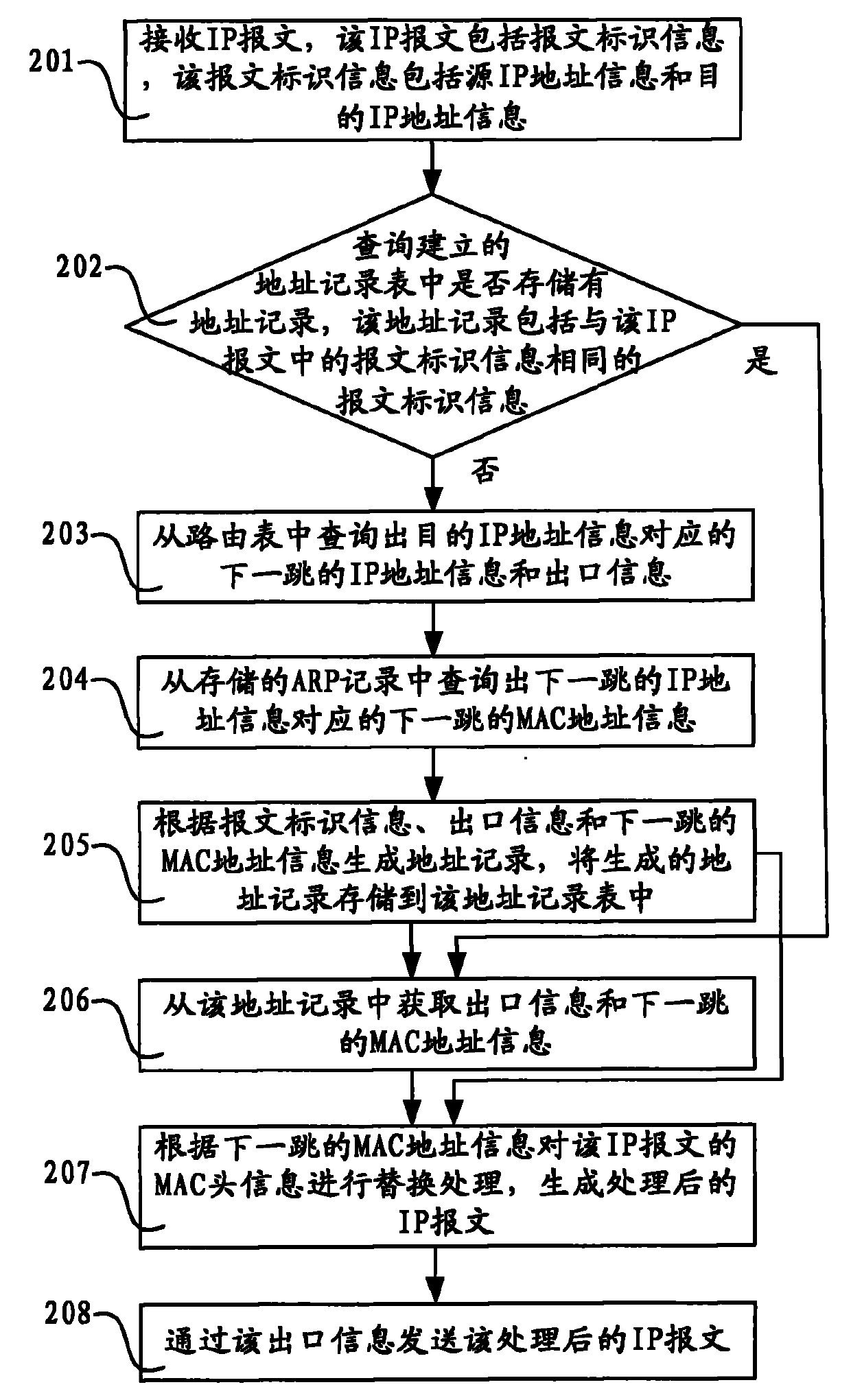
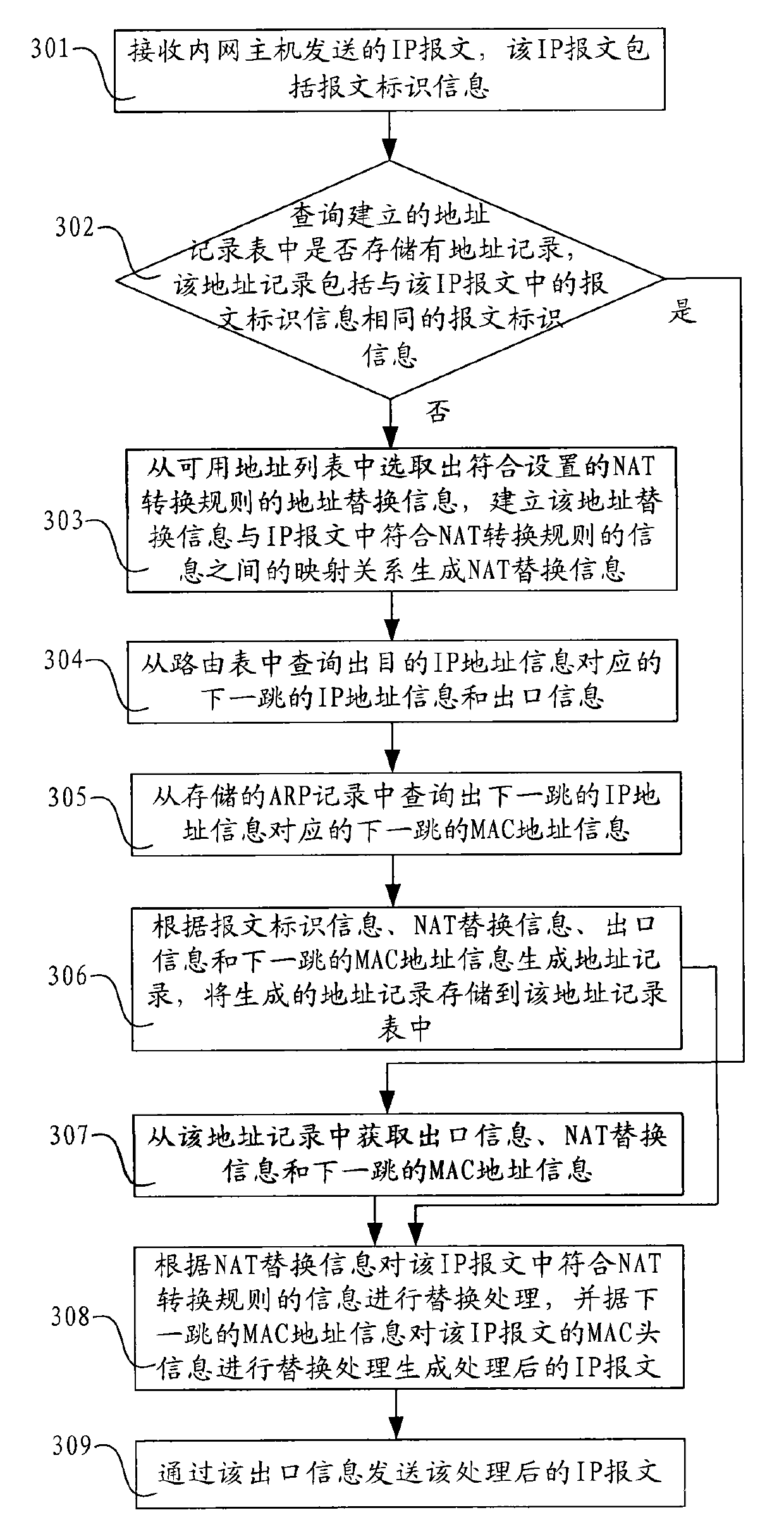
ActiveCN101771732AAvoid interruptionData switching networksComputer hardwareAddress Resolution Protocol
The invention discloses message processing method and device and network equipment. The method comprises the steps of: receiving an internet protocol (IP) message comprising message identification information; when address records stored in the established address record list are inquired, and the address records comprise message identification information same as that in the IP message, acquiring MAC address information of the next hop from the address records; replacing the MAC head information of the IP message in accordance with the MAC address information of the next hop to generate the processed IP message; and sending the processed IP message through the acquired output information. The invention does not need acquiring the MAC address information of the next hop from address resolution protocol (ARP) records so as to avoid network communication interruption caused by ARP spoofing.
Owner:RUIJIE NETWORKS CO LTD
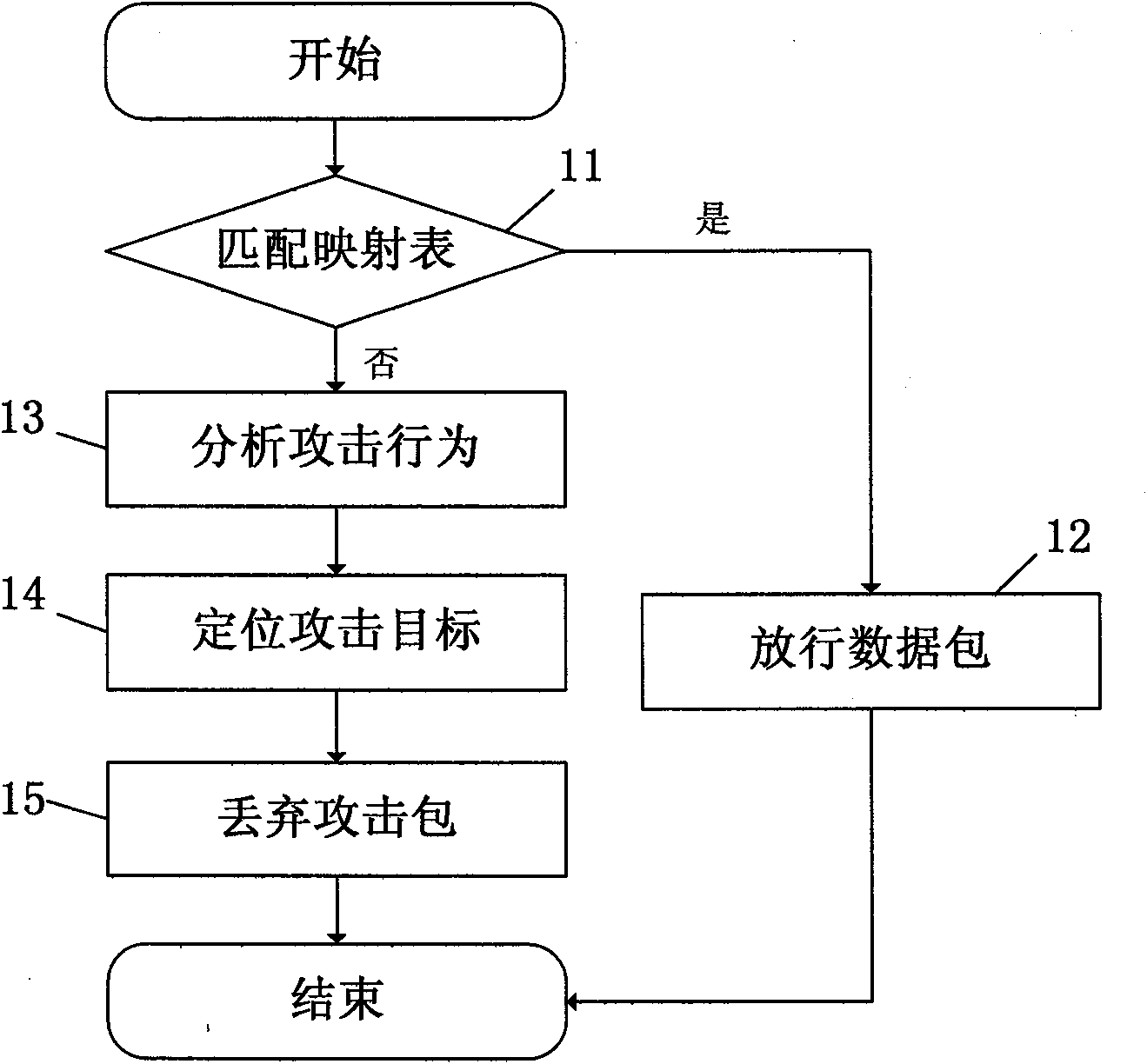
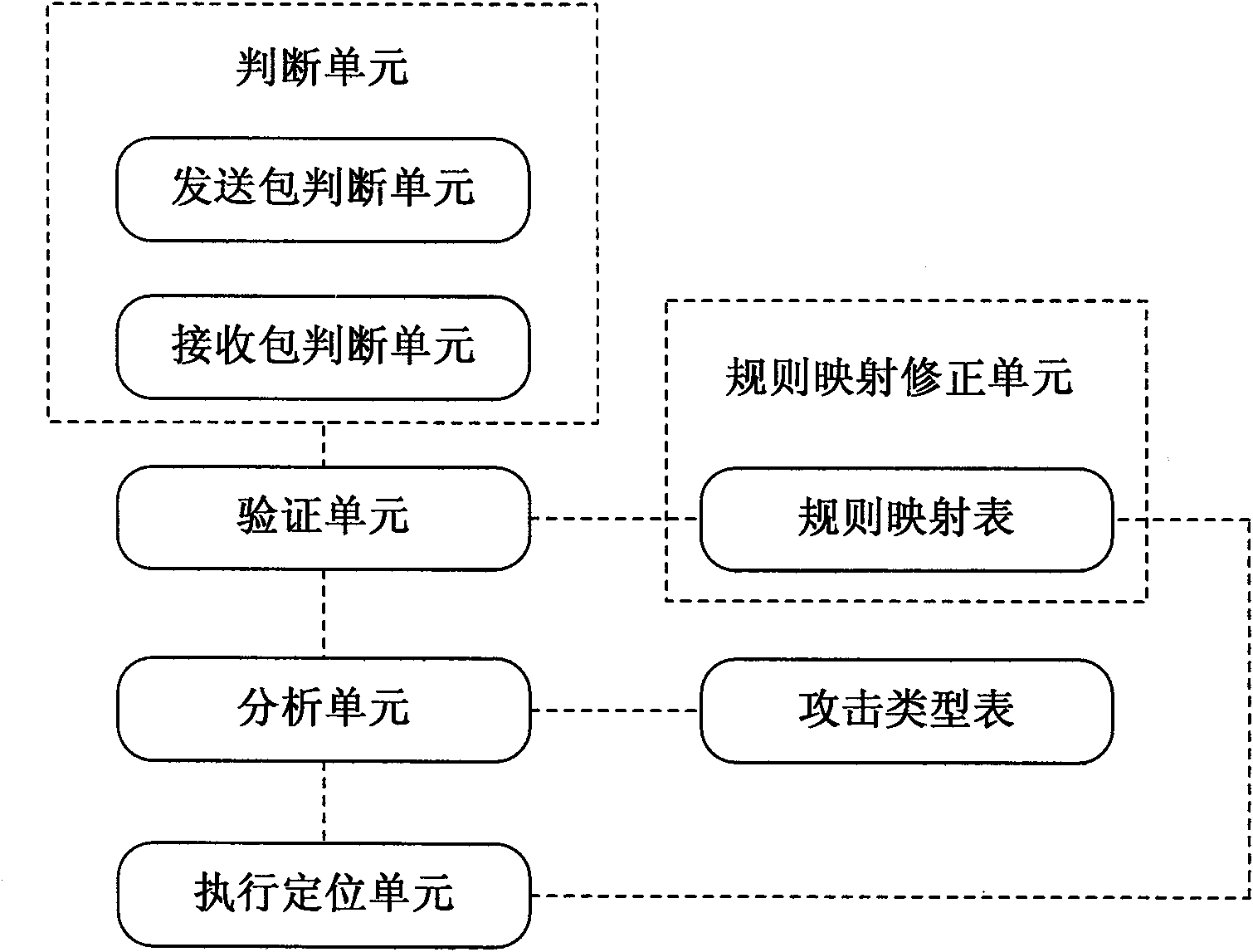
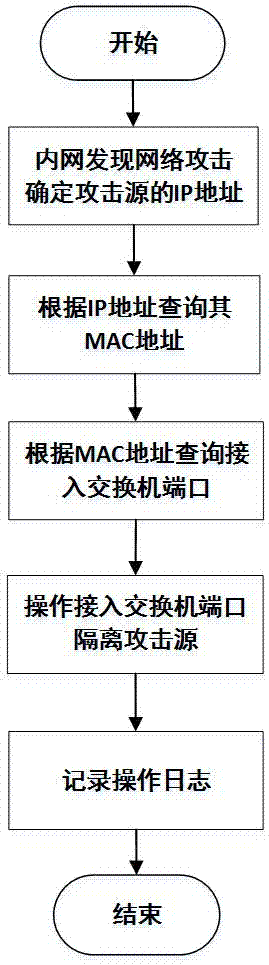
Automatic locating and isolating method of internal attack source of local area network
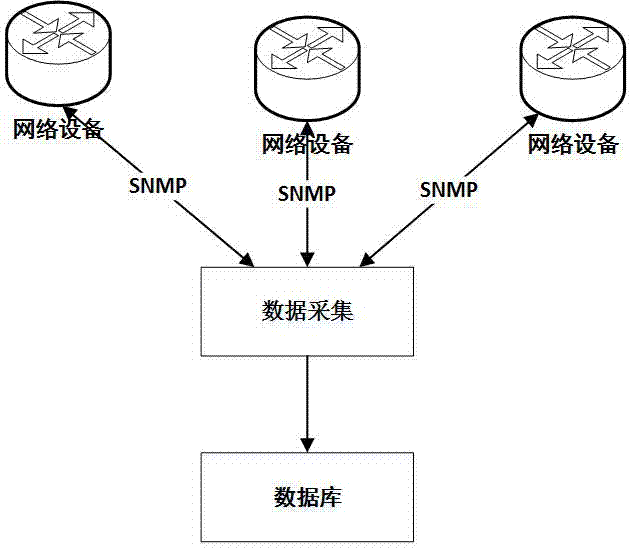
The embodiment of the invention discloses an automatic locating and isolating method of an internal attack source of a local area network. The method comprises the following steps: automatically collecting data of a network device, and storing the data in a database, inquiring an MAC address of the network device according to an IP address of the attack source, detecting ARP fraud counterfeiting the host and matching the timestamps of different IP-MAC items to automatically process the situation that one IP address corresponds to a plurality of MAC addresses, locating a switch port according to the MAC address, and filtering a cascade port of the switch and matching the timestamps of different MAC-switch port items to automatically process the situation that one MAC address corresponds to a plurality of switch ports, and operating the switch to isolate the attack source. The automatic locating and isolating method can be applicable to all kinds of network environments without any manual operation, the larger the network scale is, the more obvious the effect of the automatic locating and isolating method is, by adoption of the automatic locating and isolating method, the processing time of a network security event can be shortened, the working efficiency of a network administrator is improved, and the network security of the local area network is ensured.
Owner:SHANTOU UNIV
ARP spoofing attack detection method based on local area network
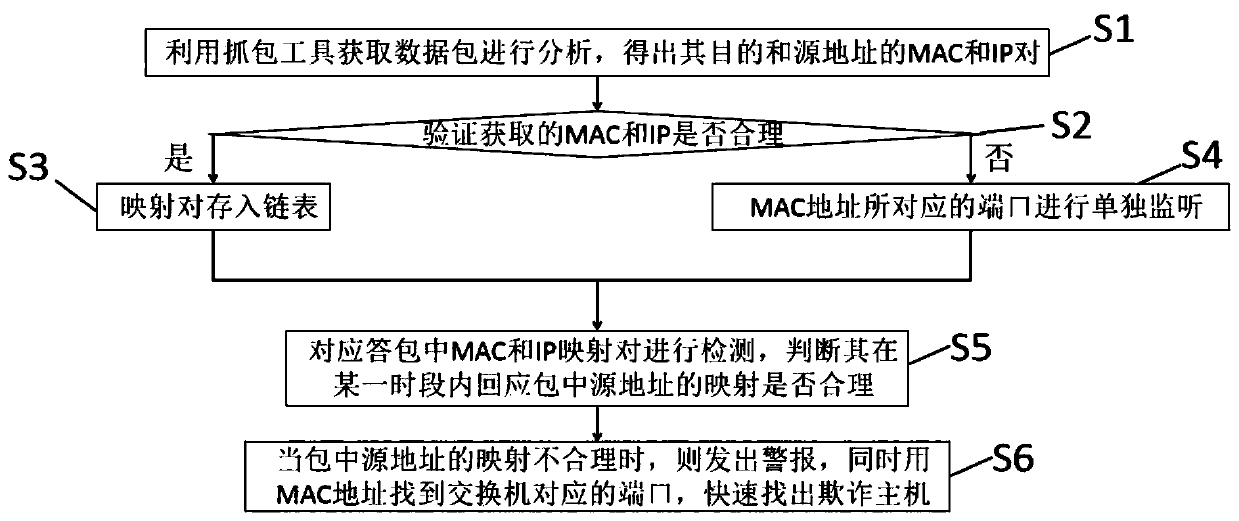
The invention discloses an ARP spoofing attack detection method based on a local area network, and relates to the technical field. The method comprises the following steps: acquiring a data packet byusing a packet capturing tool and analyzing the data packet to obtain MAC and IP pairs of a destination and a source address of the data packet; independently monitoring a port corresponding to the unreasonable MAC address; detecting MAC and IP mapping pairs in the response packet, and judging whether mapping of a source address in the response packet is reasonable or not within a certain period of time; and when the mapping of the source address in the packet is unreasonable, finding a port corresponding to the switch by using the MAC address, and quickly finding out the fraud host. Accordingto the packet capturing tool, an ARP detection system is realized. In cooperation with the port mirroring technology, the static IP is used for carrying out bidirectional binding on the MAC and the IP under the condition that the IPV4 protocol is not changed, meanwhile, the VLAN is used for reducing the local area network, the retrieval efficiency is improved, the ARP deception defense efficiencyis improved, and the burden generated to the network is avoided.
Owner:山东信天辰信息安全技术有限公司
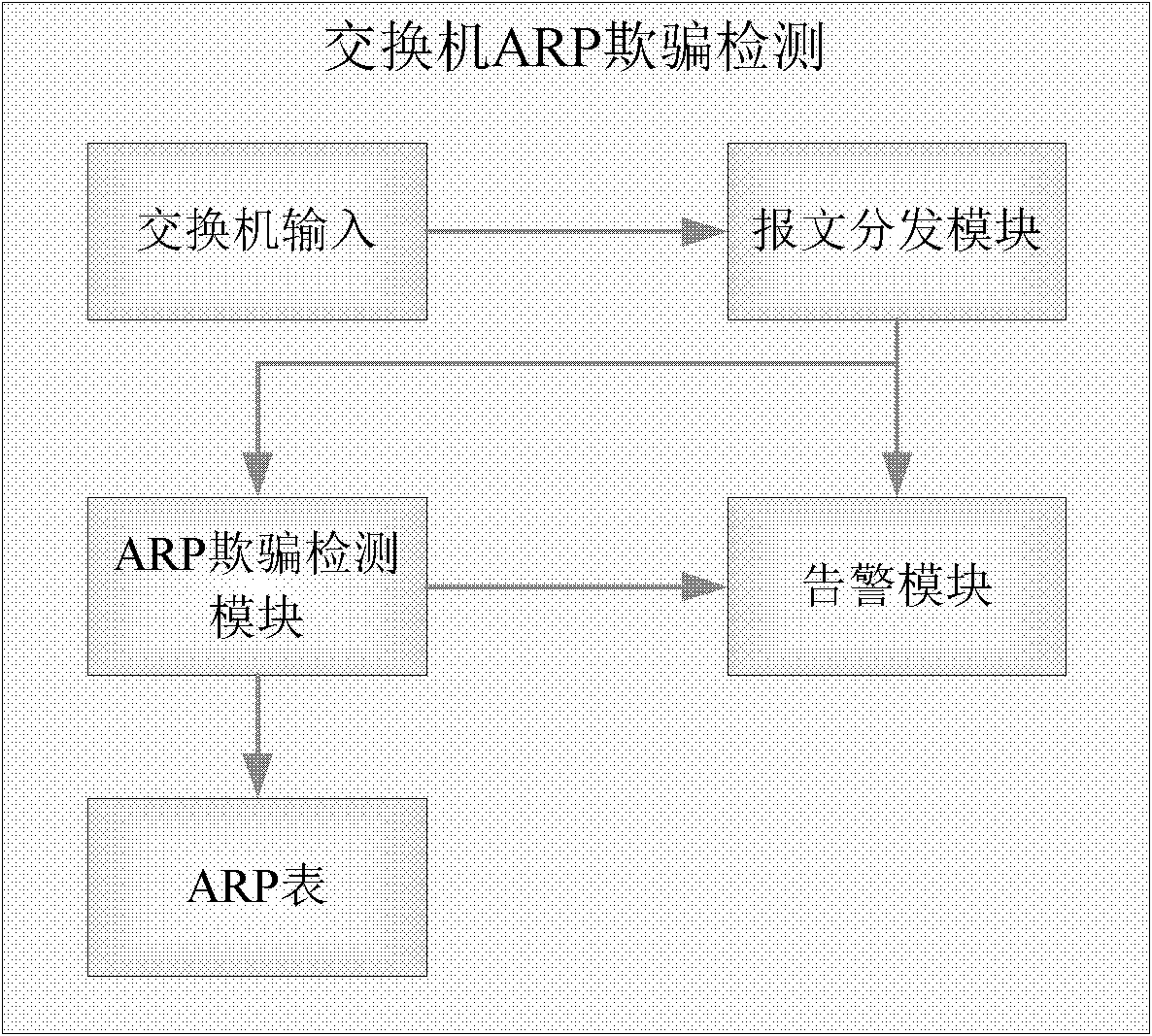
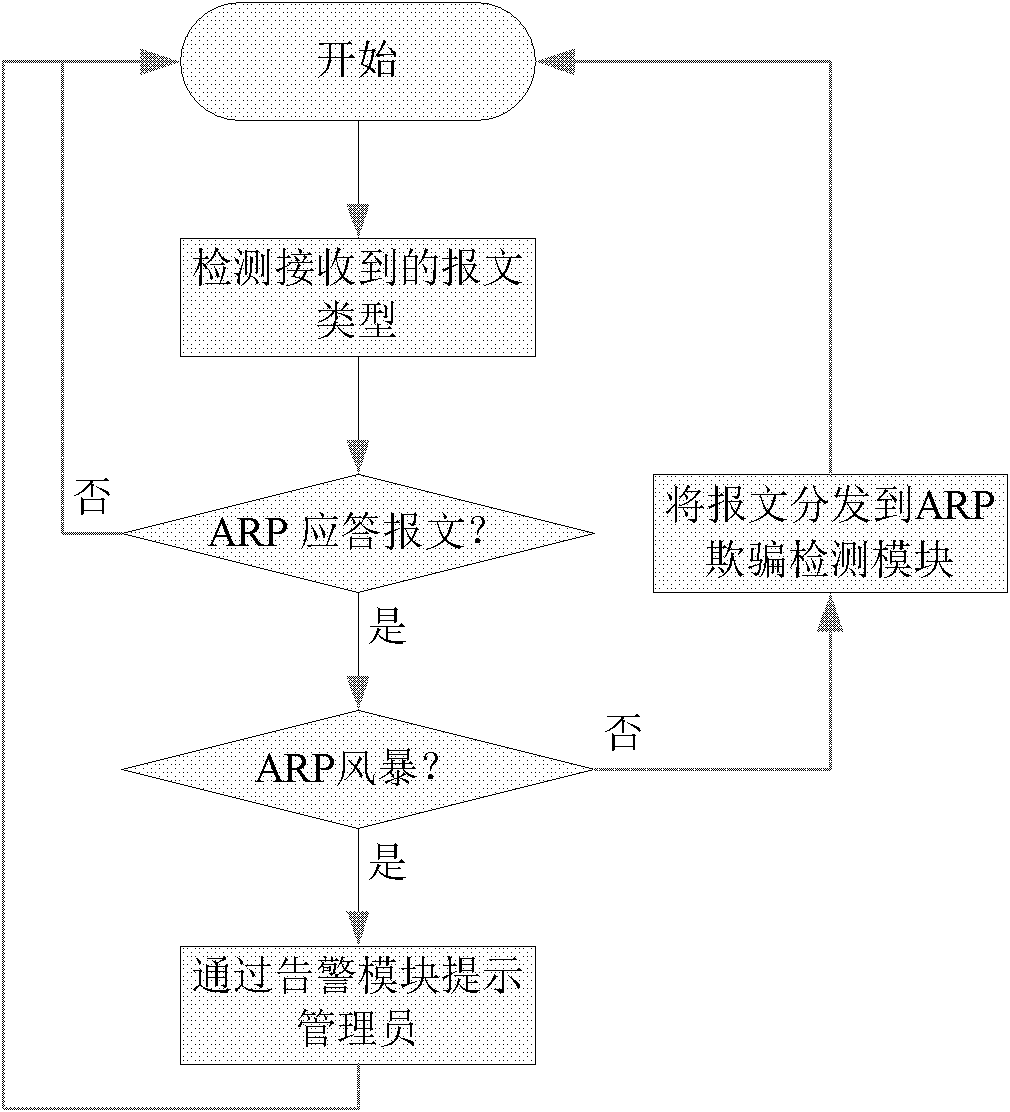
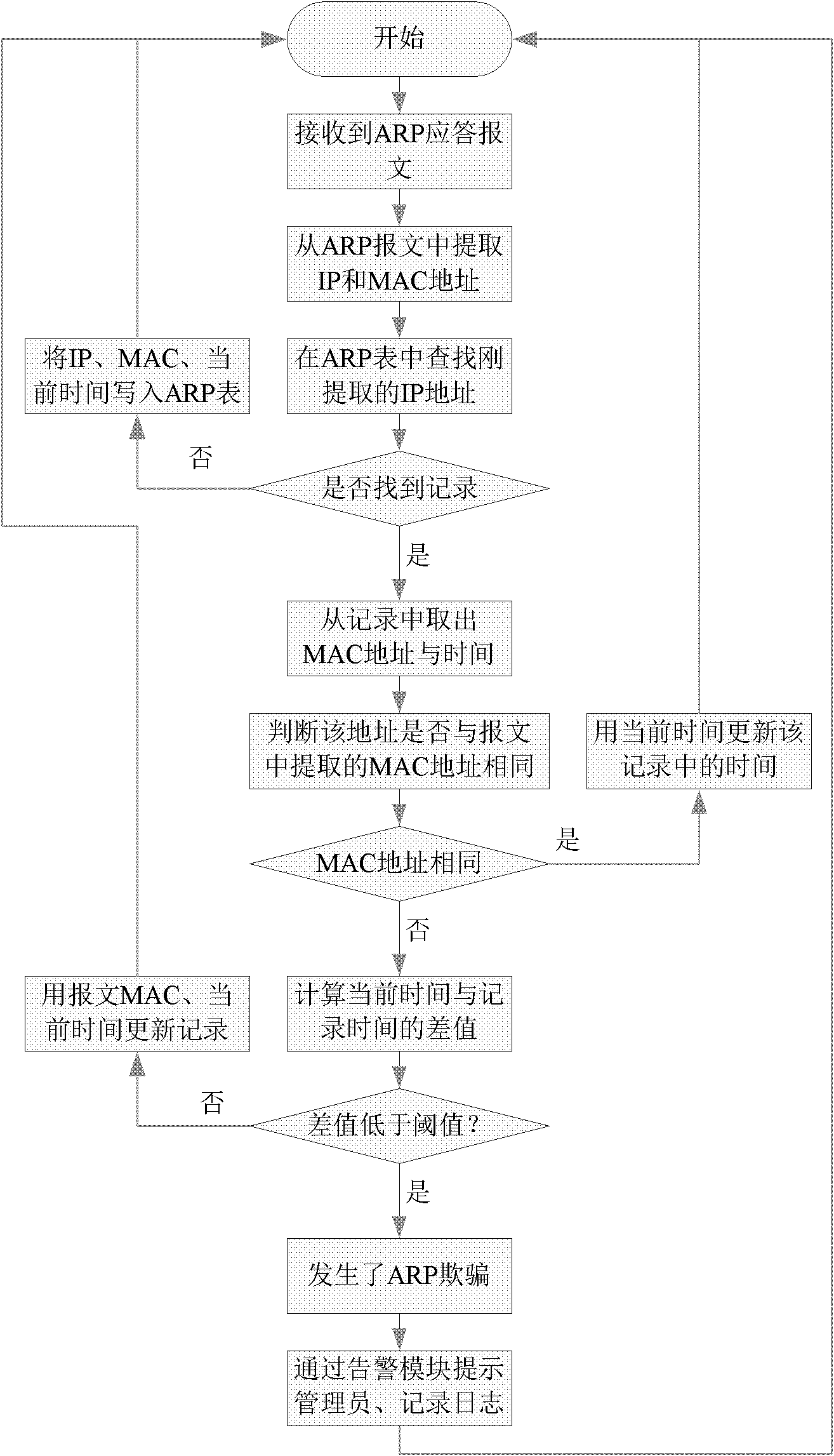
Method for realizing address resolution protocol (ARP) deception detection on switch
The invention discloses a method for realizing address resolution protocol (ARP) deception detection on a switch. The method specifically comprises the following steps of: sending switch input into a message distribution module; when the entered message is an ARP message, judging whether an ARP storm occurs by the message distribution module, if the ARP storm occurs, prompting by an alarm module, and if the ARP storm does not occur, distributing the ARP message to the ARP deception detection module; and judging whether ARP deception occurs by the ARP deception detection module through the information recorded by an ARP table, if so, recording a deception event, and prompting by the alarm module. By the adoption of the method, the disadvantages of low safety, high cost and the like in a related technology are overcome, and the problem of the ARP deception is solved in an extremely economic way.
Owner:CHINA NAT ACAD NANOTECH & ENG
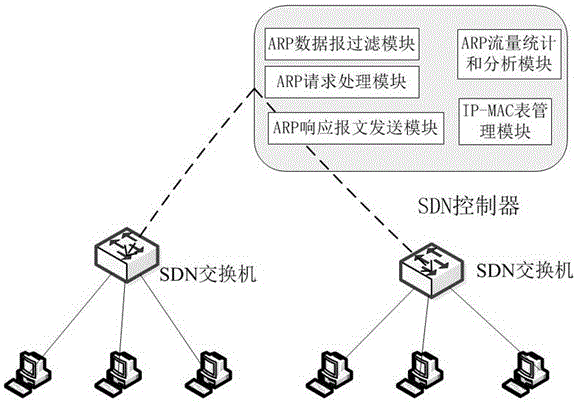
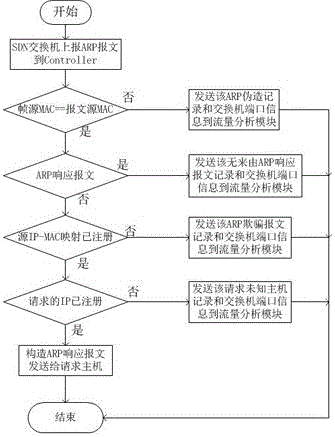
ARP (Address Resolution Protocol) auxiliary model based on SDN (Software Defined Network)
InactiveCN106506200AReduce or even eliminate broadcastingFlexible controlData switching networksAddress Resolution ProtocolTraffic capacity
The invention discloses an ARP (Address Resolution Protocol) auxiliary model based on an SDN (Software Defined Network). The ARP auxiliary model comprises an ARP datagram filtering module, an ARP request datagram processing module, an ARP response message sending module, an ARP traffic statistics and analysis module and an IP-MAC (Internet Protocol-Media Access Control) mapping table management and configuration module, wherein the ARP datagram filtering module is used for performing format correctness detection on an ARP message reported by a switch; the ARP request datagram processing module is used for answering an ARP request message; the ARP response message sending module is used for constructing and sending an ARP response datagram of a non-empty query result; the ARP traffic statistics and analysis module is used for receiving various ARP message event records and switch port information transmitted by the ARP datagram filtering module and the ARP request processing module; and the IP-MAC mapping table management and configuration module is used for providing management and configuration interfaces of an IP-MAC mapping table. When the ARP auxiliary model is applied to the SDN, ARP broadcast can be effectively isolated; ARP spoofing is prevented; an executor of the ARP spoofing is traced; and global IP-MAC information is managed and maintained.
Owner:COMP APPL RES INST CHINA ACAD OF ENG PHYSICS
ARP spoofing fine-grained detecting method and system
ActiveCN104883360ADetection Efficient DynamicsNo signaling burden addedData switching networksCountermeasureTime segment
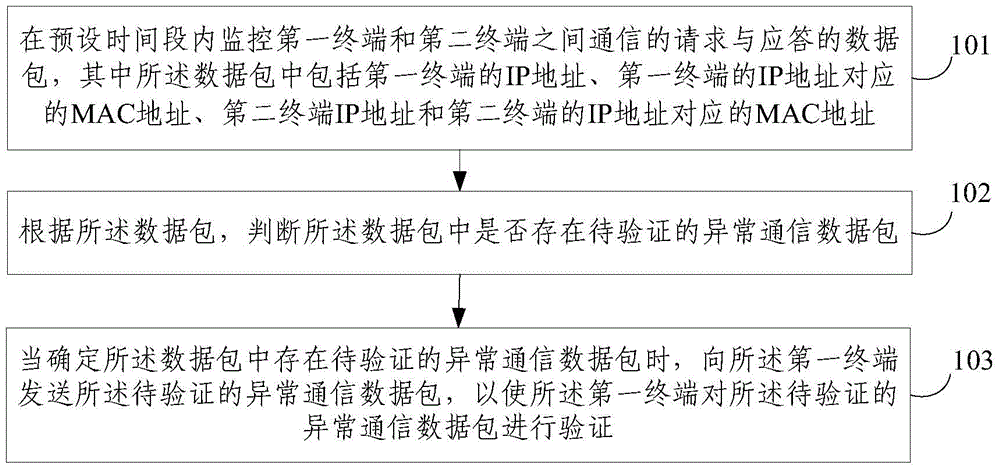
The invention discloses an ARP spoofing fine-grained detecting method and system. The method comprises: monitoring a communication request and a response data packet between a first terminal and a second terminal within a preset time segment, wherein the data packet includes the IP address of the first terminal, a MAC address corresponding to the IP address of the first terminal, the IP address of the second terminal, and a MAC address corresponding to the IP address of the second terminal; determining whether an abnormal communication data packet to be verified is included in the data packet according to the data packet; and if yes, transmitting the abnormal communication data packet to be verified to the first terminal in order that the first terminal verifies the abnormal communication data packet to be verified. The method and the system may detect and find out ARP spoofing behaviors in real time, achieve high detection efficiency, guarantee one-to-one correspondence between verified IP address and the MAC address of the terminal, and achieve high-efficient and dynamic detection of ARP attack and countermeasure.
Owner:INST OF INFORMATION ENG CAS
Distributed detection method and system for ARP (Address Resolution Protocol) cheating
ActiveCN104901953ANo signaling burden addedDetection Efficient DynamicsTransmissionAddress Resolution ProtocolNetwork packet
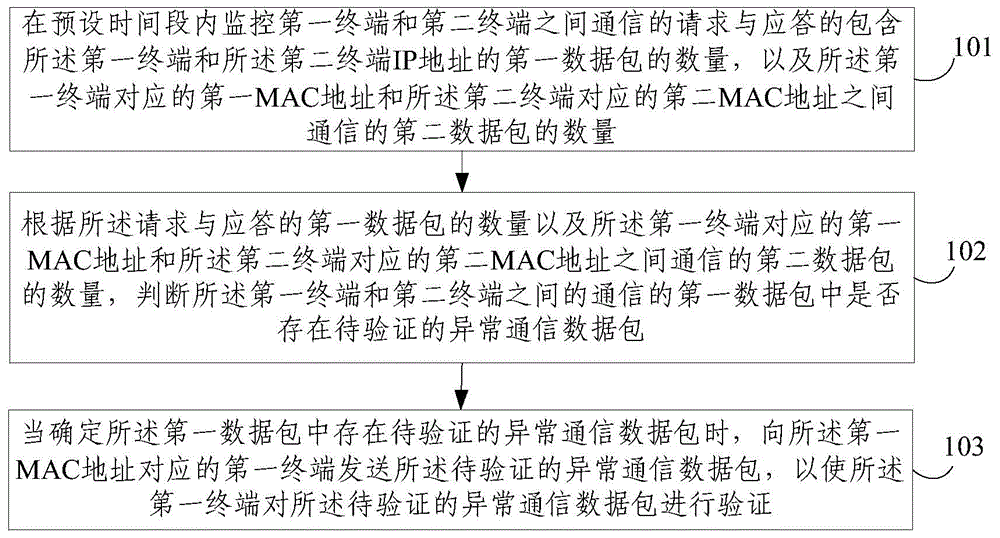
The invention discloses a distributed detection method and system for ARP (Address Resolution Protocol) cheating. The method comprises: monitoring the quantity of first data packets requested and answered for communication between a first terminal and a second terminal and including IP addresses of the first terminal and the second terminal, and the quantity of second data packets for communication between a first MAC (Multimedia Access Control) address corresponding to the first terminal and a second MAC address corresponding to the second terminal in a preset time period; judging whether the first data packets for communication between the first terminal and the second terminal have abnormal communication data packets to be verified according to the quantity of the first data packets and the quantity of the second data packets; and when the first data packets have the abnormal communication data packets to be verified, sending the abnormal communication data packets to be verified to the first terminal corresponding to the first MAC address, so that the first terminal verifies the abnormal communication data packets to be verified. The method and the system can be used for detecting ARP cheating behaviors in real time, and have high detection accuracy and high detection efficiency.
Owner:INST OF INFORMATION ENG CAS
Method and device for preventing gateway deceit
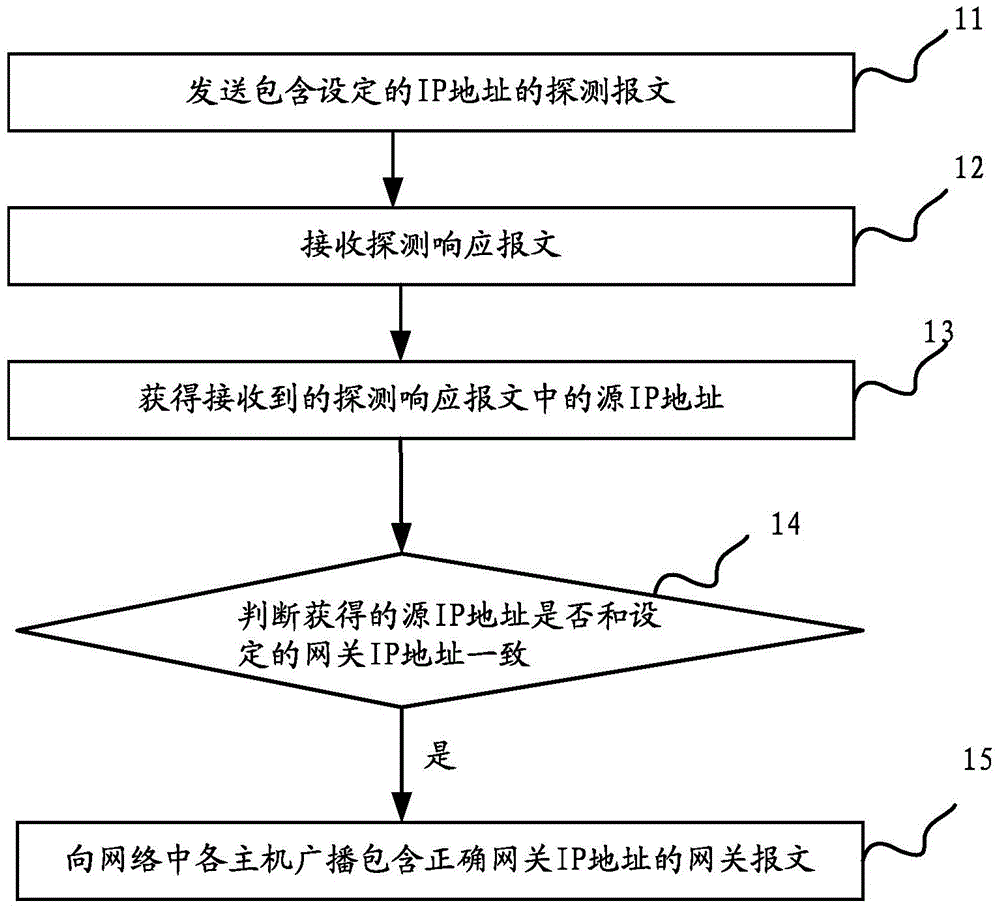
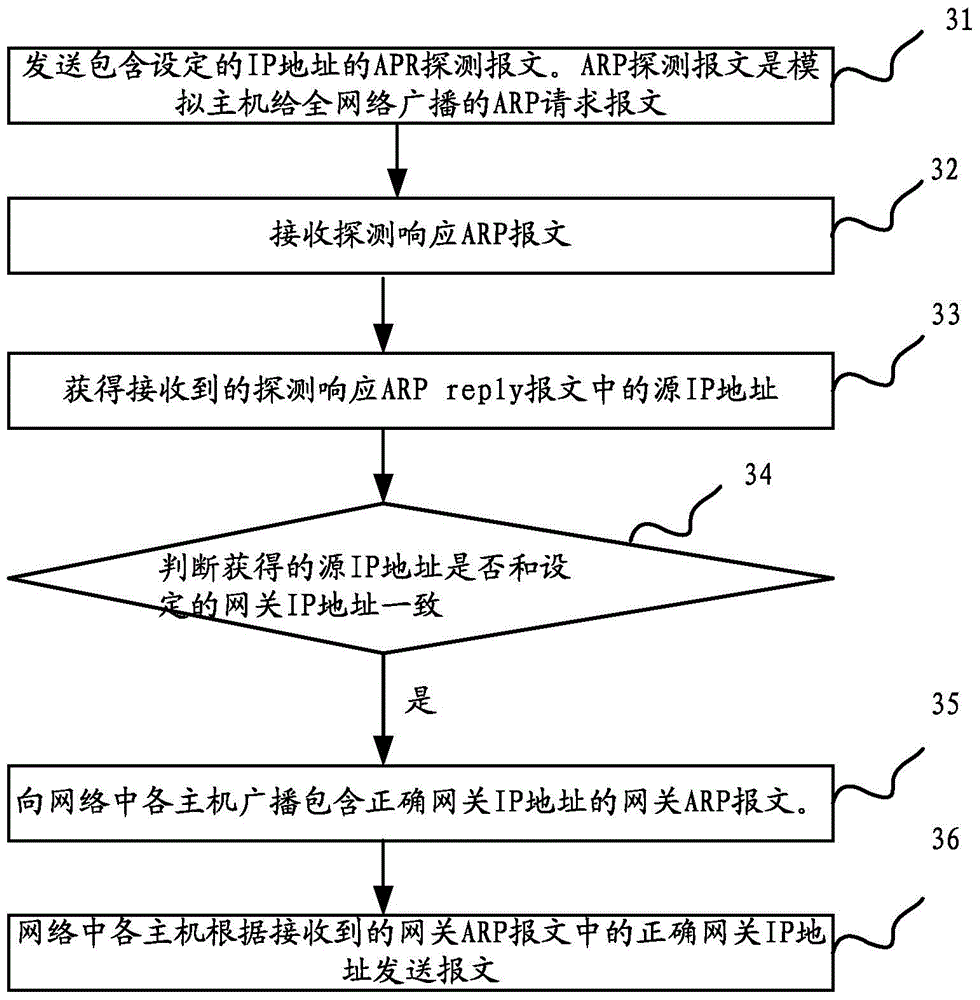
InactiveCN104363243ARestore normal communicationDeception blockingTransmissionIp addressThe Internet
The invention discloses a method and device for preventing gateway deceit. The method comprises the steps of sending a detection message which contains a set IP address and is used for detecting whether a gateway deceit virus exists or not; receiving a detection response message; obtaining the source IP address in the received detection response message; judging whether the IP address of the source IP address is identical with a set gateway IP address; broadcasting a gateway message containing correct gateway IP address to all hosts in a network when the source IP address and the set gateway IP address are identical, wherein the gateway message containing the correct gateway IP addresses enables the hosts with tampered IP addresses in the network to obtain correct IP addresses and normal communication between the hosts and the gateway to be recovered. The method and device for preventing gateway deceit are used for solving the safety problem of the network when ARP deceit viruses exist in the network.
Owner:RUIJIE NETWORKS CO LTD
System and method for detecting address resolution protocol (ARP) spoofing
ActiveUS20150188942A1Easy to detectMemory loss protectionData taking preventionAddress Resolution ProtocolNetwork packet
There are provided a system and method for detecting Address Resolution Protocol (ARP) attacks. The ARP spoofing attack detection system includes: a reception module which receives an ARP packet, and which determines whether the received ARP packet is an unsolicited ARP packet; a transmission module which creates, if the ARP packet is an unsolicited ARP packet, an ARP request packet corresponding to the unsolicited ARP packet, and which broadcasts the ARP request packet; and a detection module which determines, if an ARP response packet corresponding to the ARP request packet is received, whether an input port of the ARP response packet is identical to an input port of the unsolicited ARP packet, and which determines that an ARP spoofing attack has occurred if the input port of the ARP response packet is not identical to the input port of the unsolicited ARP packet.
Owner:SAMSUNG SDS CO LTD
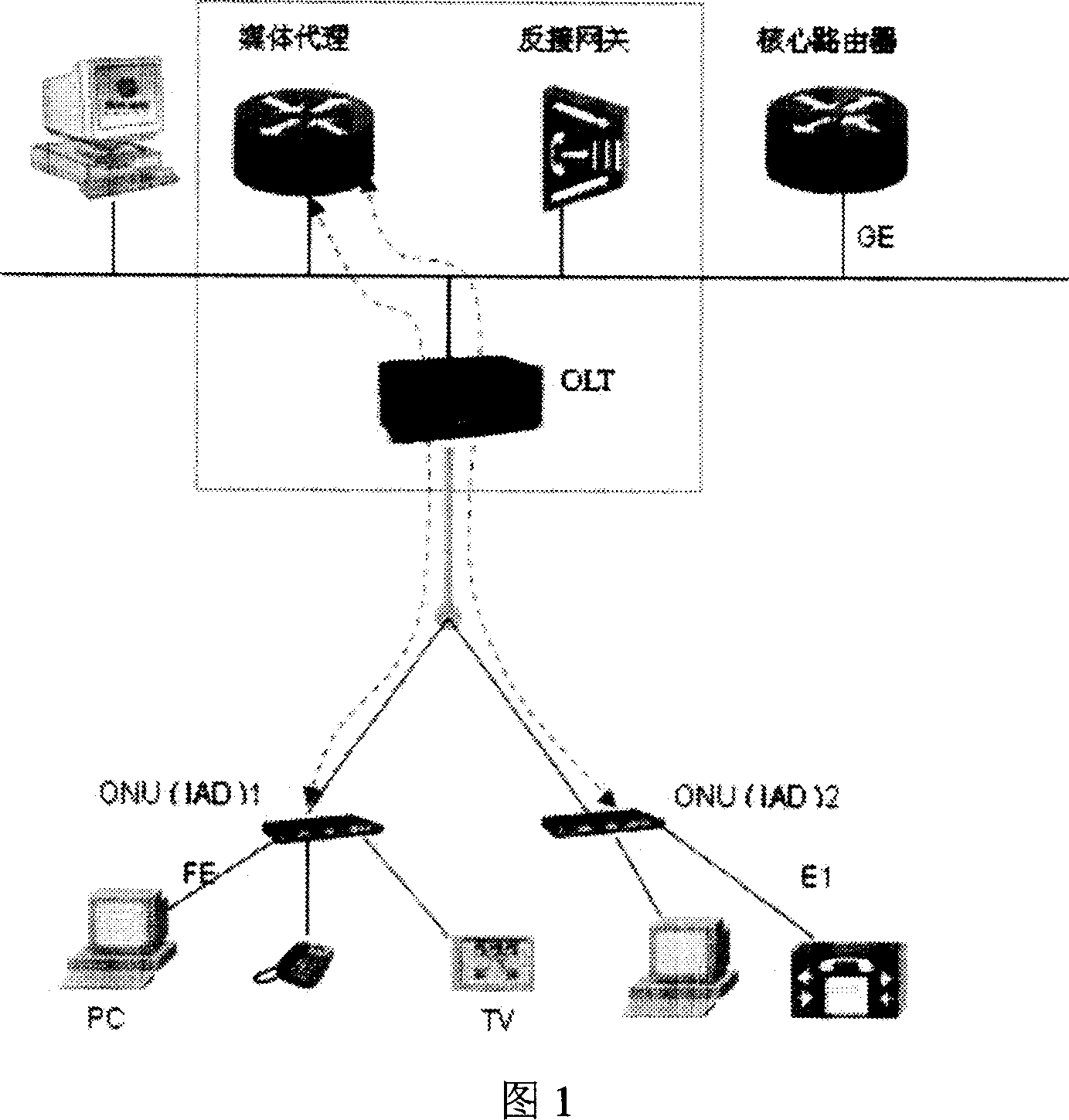
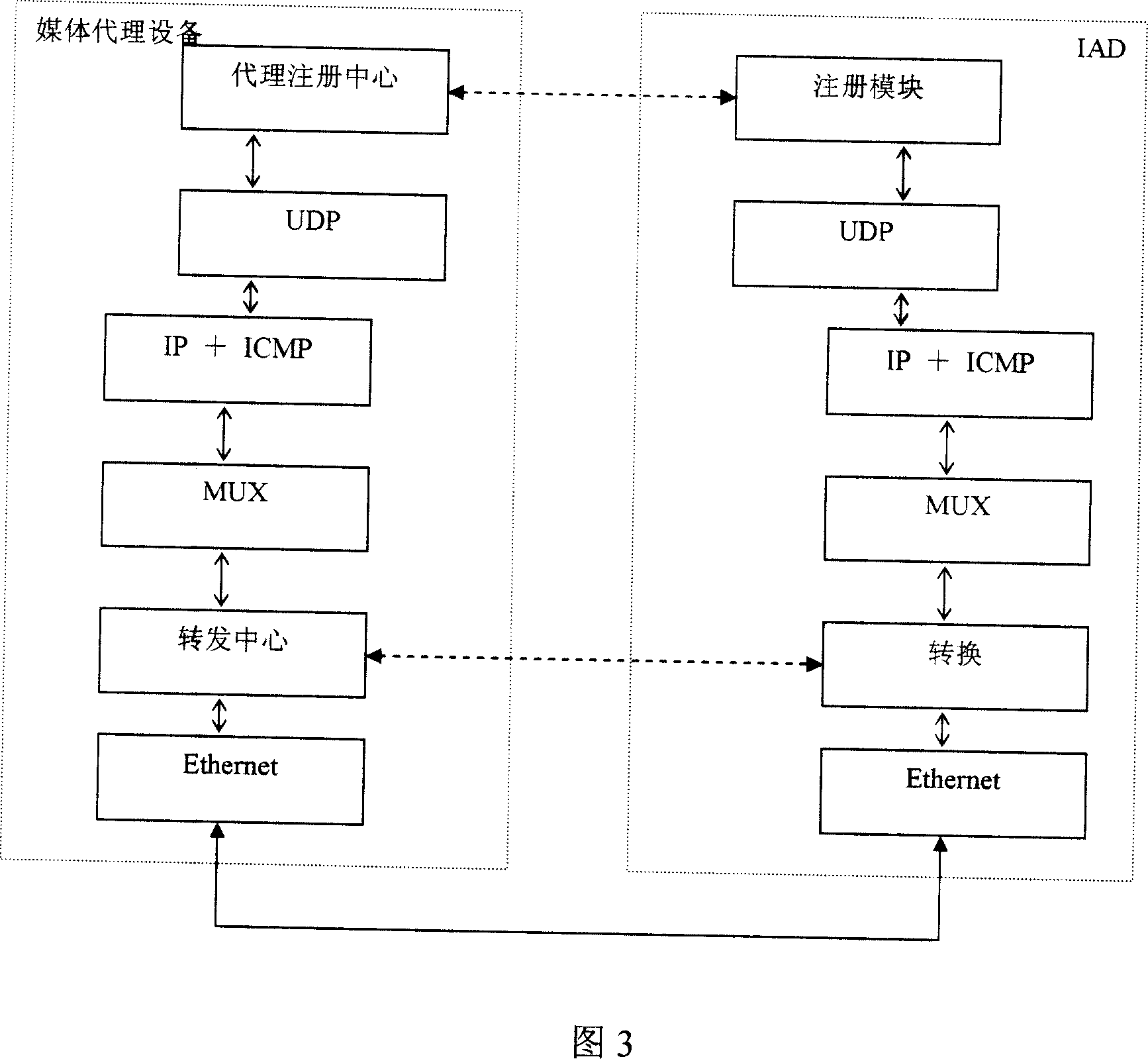
Method for realizing interworking of VoIP service in a same OLT of EPON
ActiveCN101014043AReal-time loginImplement ARP spoofing functionInterconnection arrangementsNetwork connectionsARP spoofingPacket forwarding
The invention provides one method to realize VoIP business connection in same OLT of EPON, which sets media agent device in upper device of OLT, wherein, the media agent device realizes same OLT two ONU VoIP modules data pack transfer through ARP deception and data pack transfer type to realize VoIP business connection. The invention media agent device modifies these data composed of source MAC address and aims one to transfer the real needed data VoIP module.
Owner:广州市高科通信技术股份有限公司
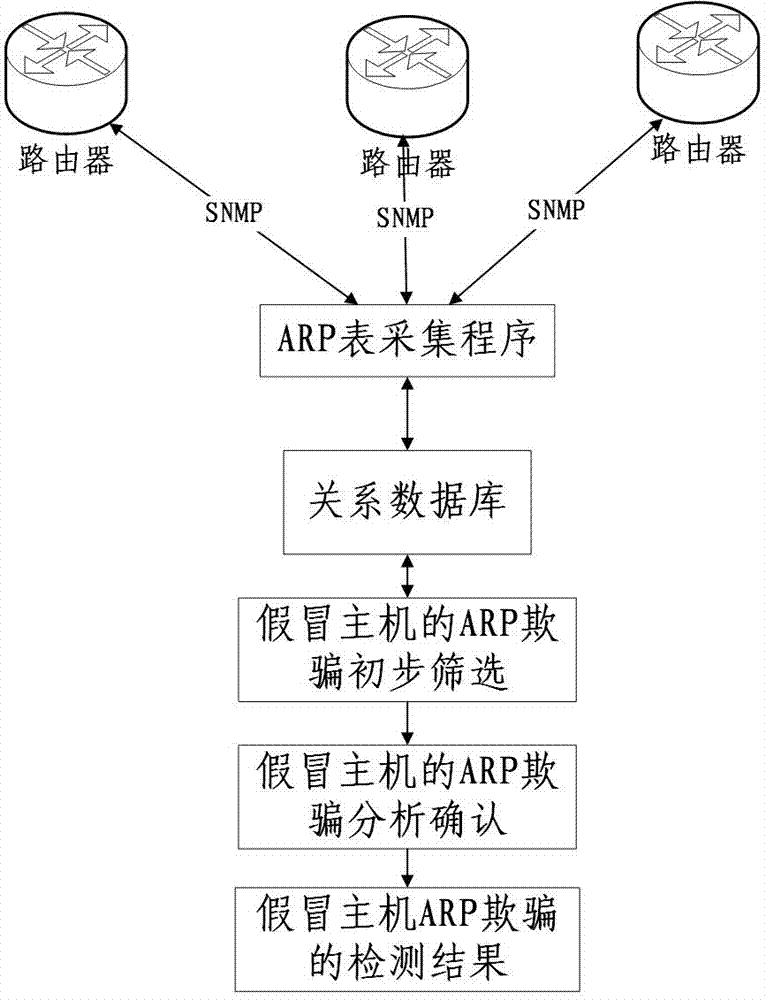
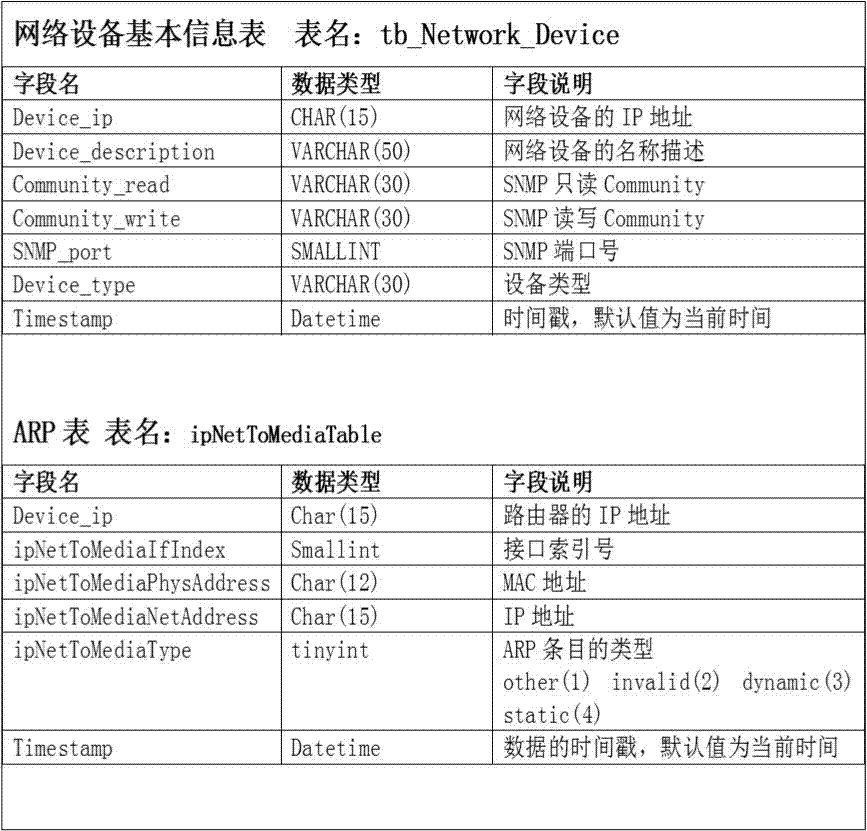
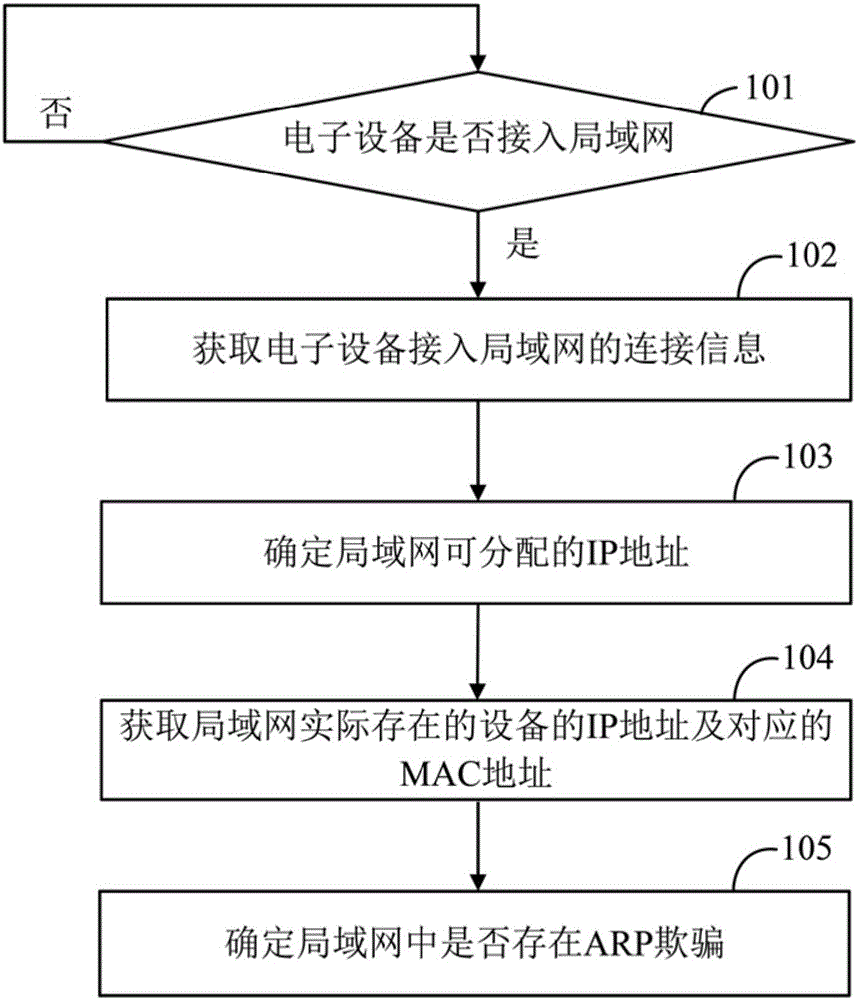
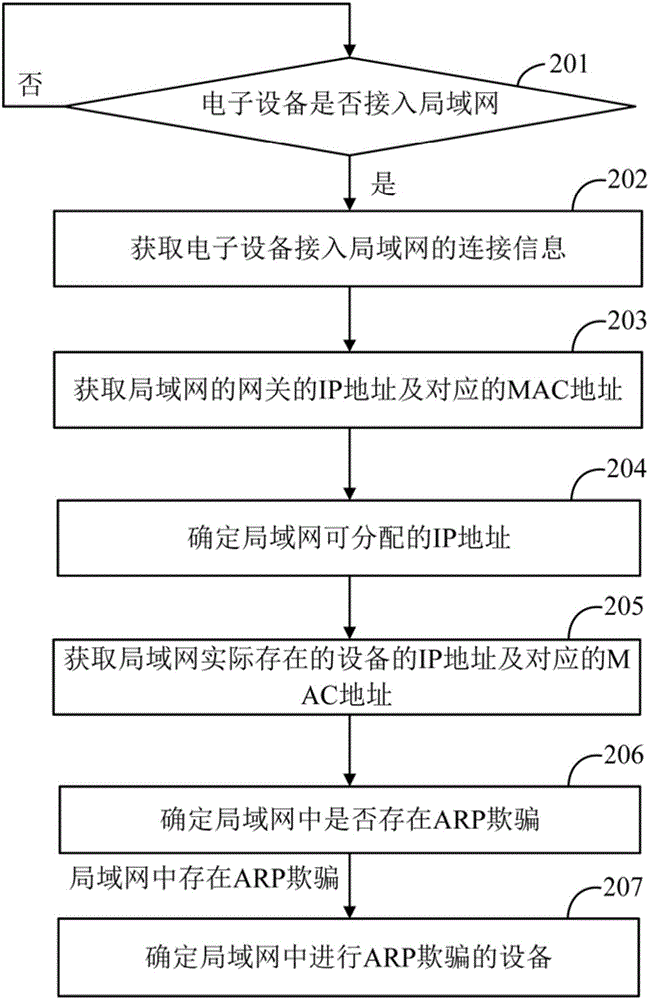
Method of automatically detecting host-passing-off ARP spoofing
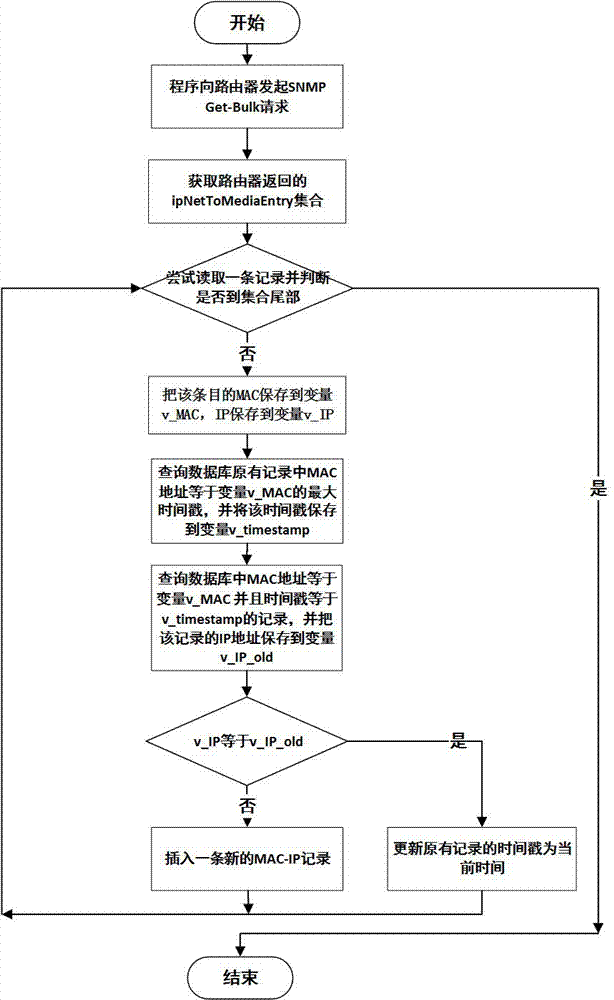
ActiveCN106899612AAvoid misjudgmentImprove performanceTransmissionAddress Resolution ProtocolIp address
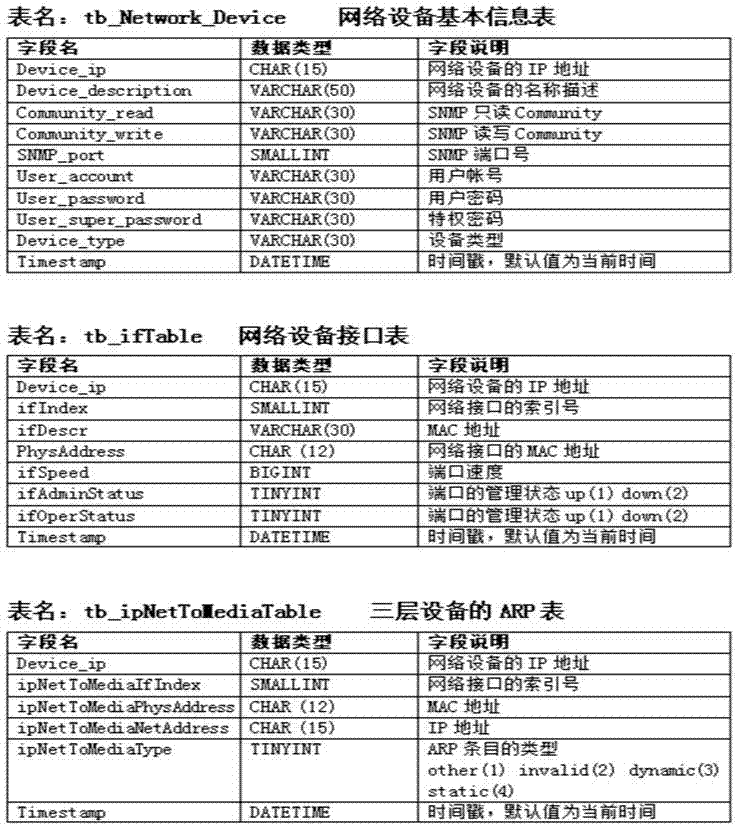
The embodiment of the invention discloses a method of automatically detecting host-passing-off ARP (Address Resolution Protocol) spoofing. The method of automatically detecting host-passing-off ARP spoofing includes a data acquisition method and an ARP spoofing detection method, wherein a data acquisition program uses an SNMP (Simple Network Management Protocol) to automatically obtain an ARP table of three-layer equipment on time and saving the ARP table in a database; the ARP spoofing detection method includes an initial screening stage and an analysis determination stage and includes the following steps: initially screening and obtaining the record that the number of different IP (Internet Protocol) addresses corresponding to one MAC (Media Access Control) address in the database is greater than one threshold; performing analysis and determination on each MAC address of the initial screening result; and through a white list, analysis of the value of ipNetToMediatype, analysis of the distribution range and the tense change rule of IP addresses, and other technical means, eliminating the special situations that the address is the own MAC address of a router and other network devices and a plurality of virtual machines are running on one computer, determining that the address is the ARP spoofing.
Owner:SHANTOU UNIV
Maintenance method for terminal list item of network equipment and network equipment
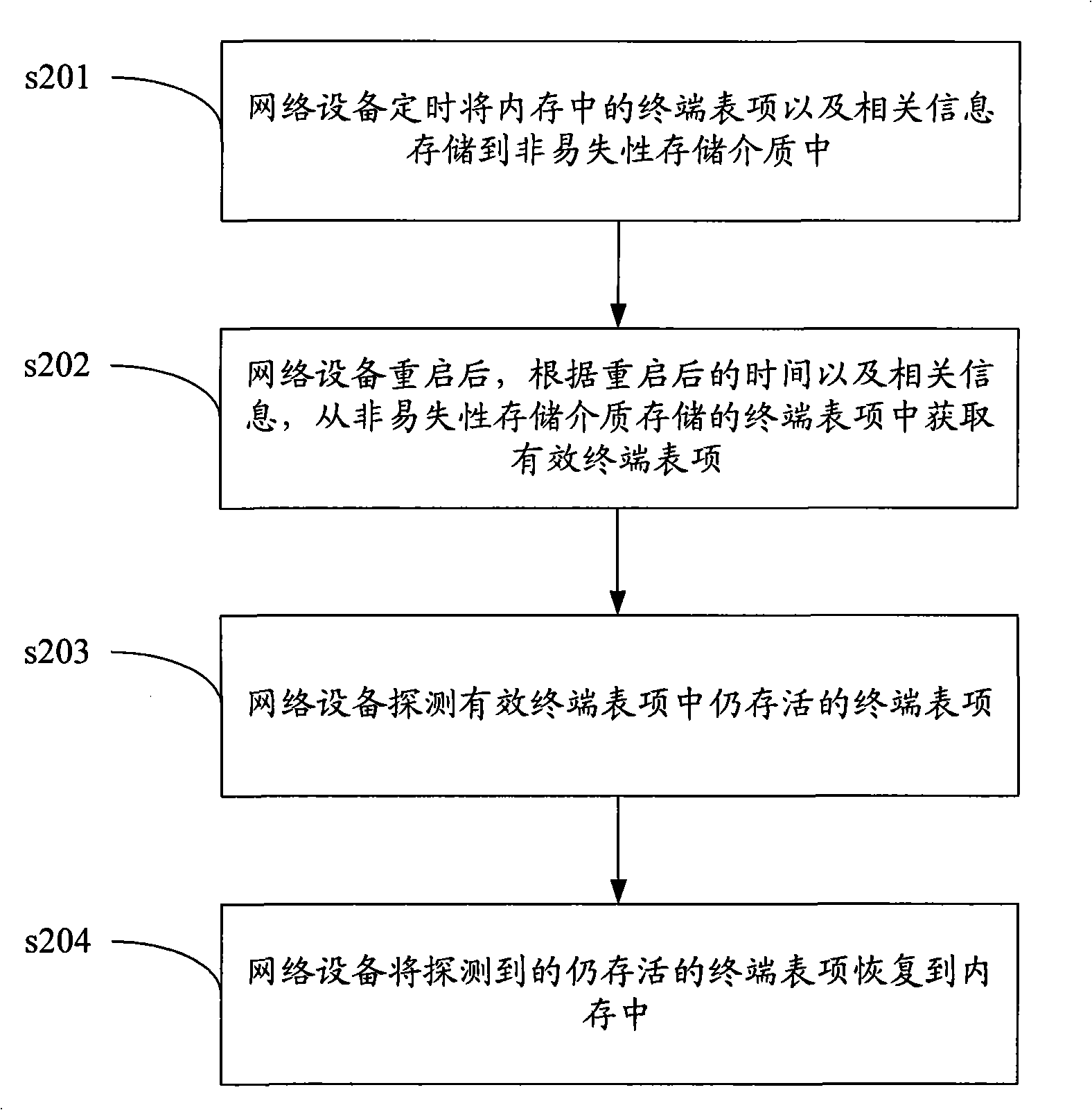
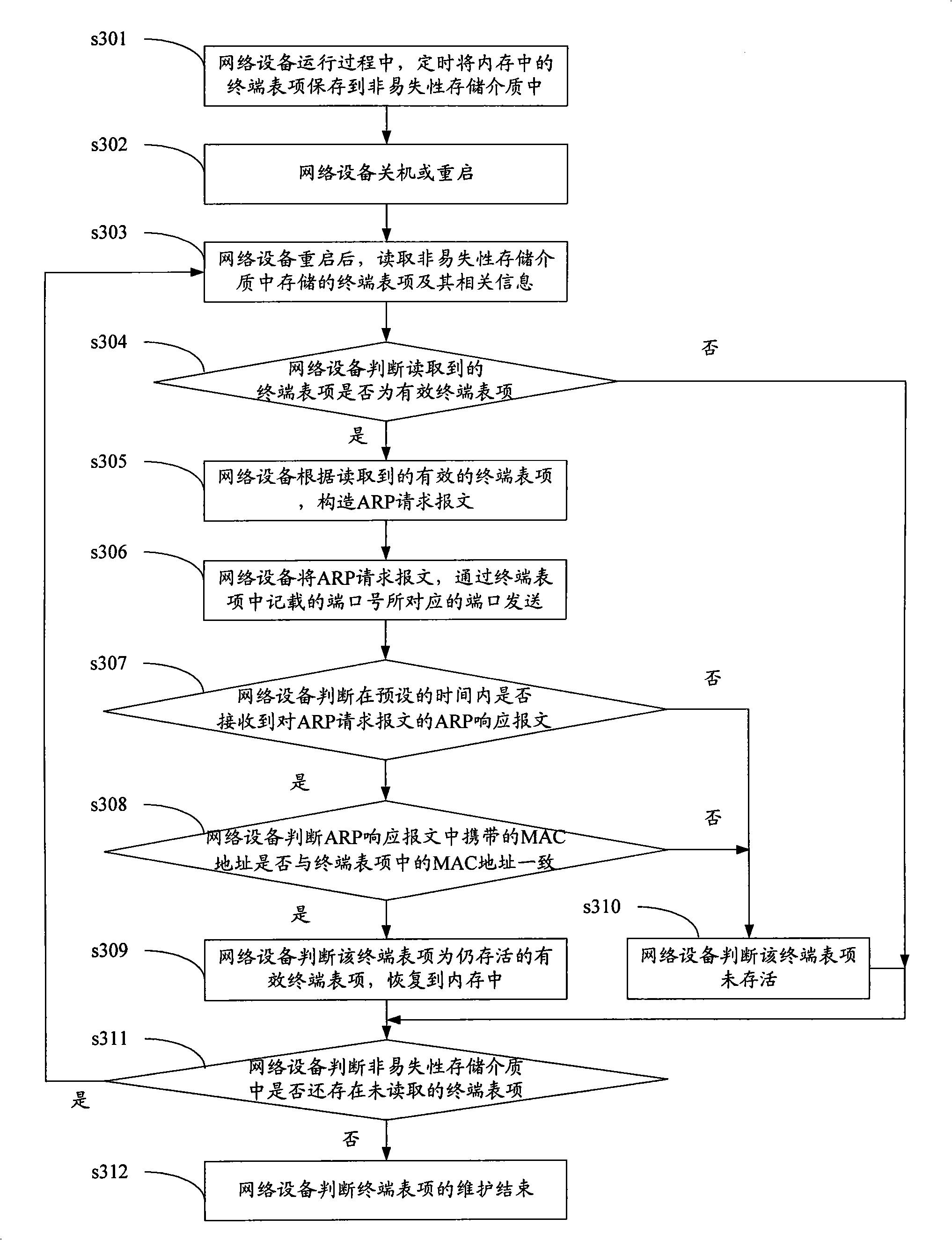
ActiveCN101494562AGuaranteed uptimeWill not affect the online experienceData switching networksRelevant informationTimestamp
The invention provides a maintaining method of terminal table entries on network equipment and network equipment applying the method. The method is applied to the network equipment starting the defense function for ARP spoofing and comprises the following steps: the network equipment stores the terminal table entries and relevant information in a memory into a non-volatile storage medium; the terminal table entries comprise an IP address and an MAC address of the terminal and binding relation of port numbers; the relevant information comprises the residual survival time of the terminal table entries and the timestamp of the current time; after the network equipment is restarted, the effective terminal table entries are obtained from the terminal table entries of the non-volatile storage medium; the network equipment detects the survival terminal table entries in the effective terminal table entries; and the network equipment restores the detected survival terminal table entries into the memory. By using the invention, the network equipment avoids the process of releasing the IP address and then obtaining again while guaranteeing the normal operation of the defense function for ARP spoofing.
Owner:NEW H3C TECH CO LTD
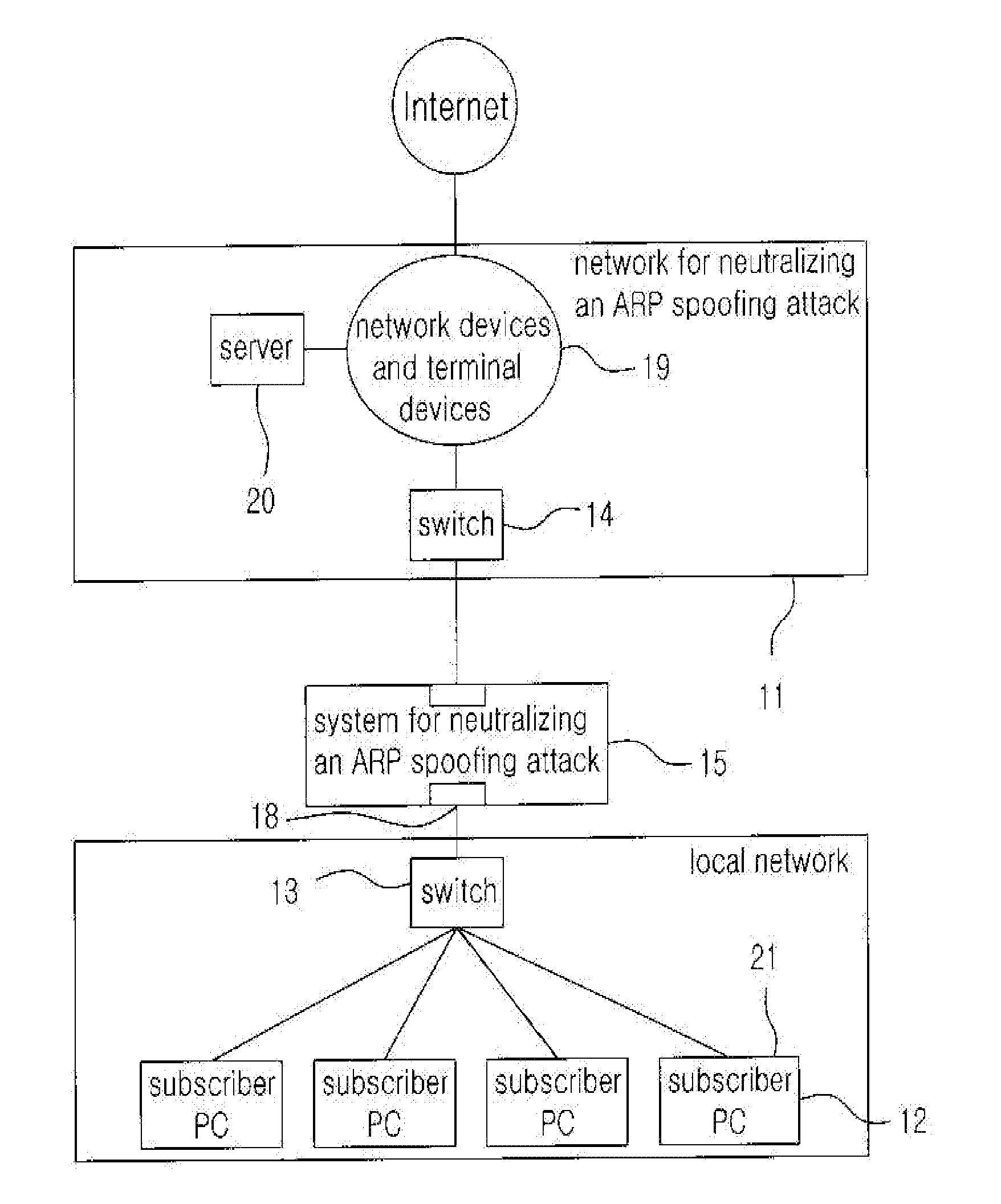
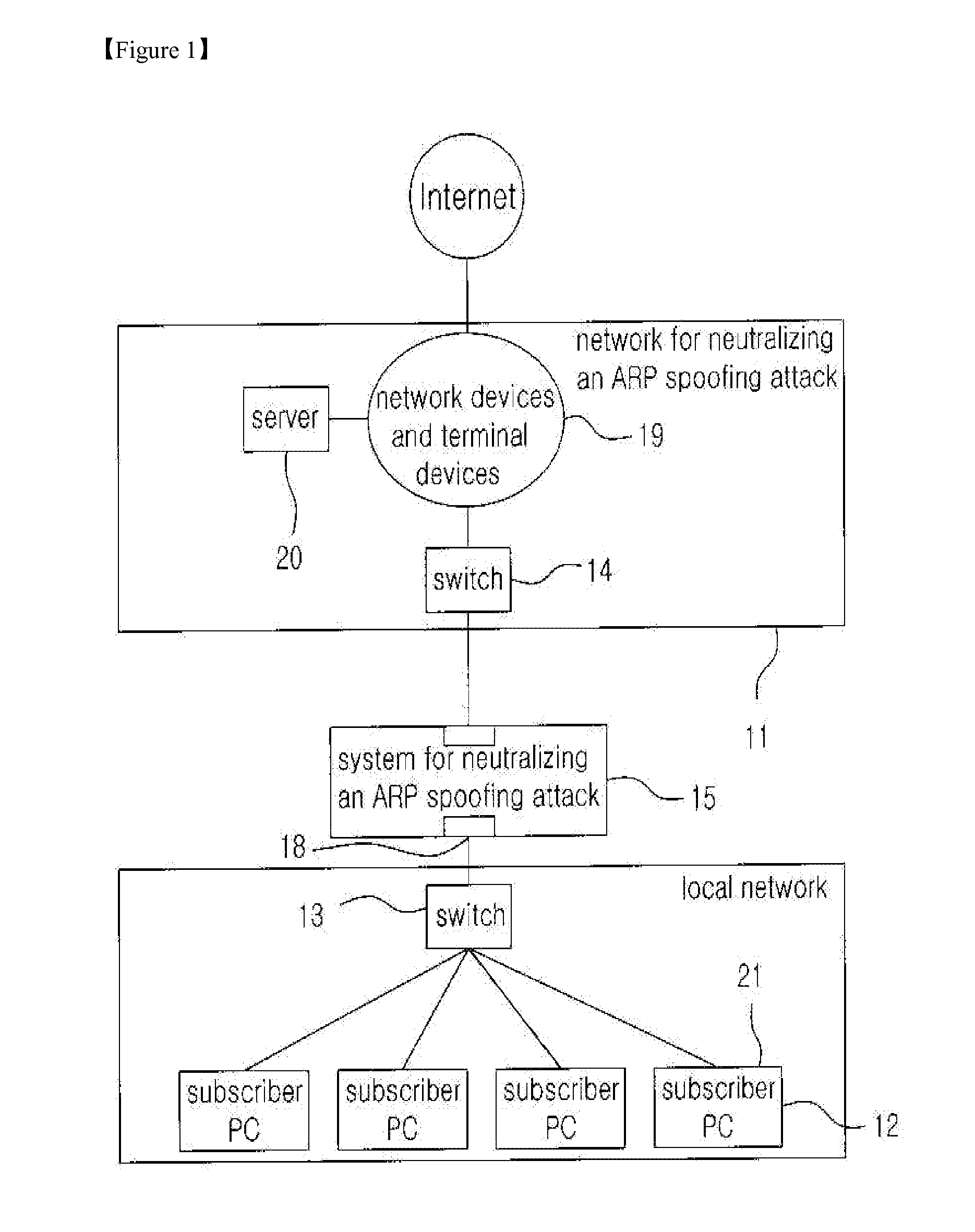
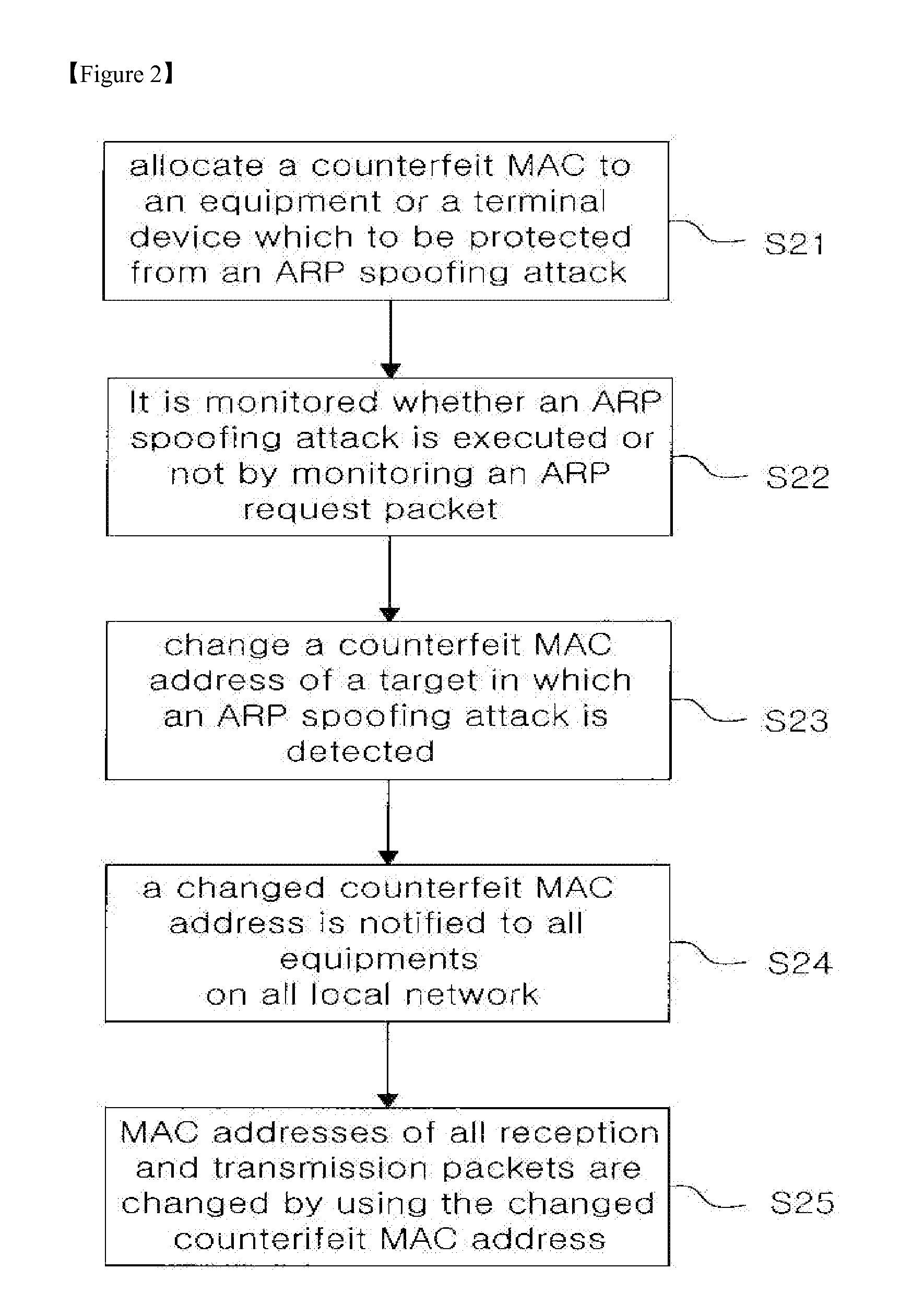
Method for neutralizing the arp spoofing attack by using counterfeit mac addresses
InactiveUS20110179486A1Effective attackEfficiently neutralizedMemory loss protectionData taking preventionARP spoofingSpoofing attack
The present invention is related to a method for neutralizing a malicious ARP spoofing attack generated in a local network and in particular, the present invention provides a method for neutralizing an ARP spoofing attack comprising a step for detecting an ARP spoofing attack based on an ARP request packet generated for an ARP spoofing attack; a step for generating a plurality of counterfeit MAC addresses and dynamically changing MAC addresses of network devices or servers which are to be protected whenever an ARP spoofing attack is generated; and a step for neutralizing an ARP spoofing attack by using a counterfeit MAC address which is capable of neutralizing an ARP spoofing attack adequately.
Owner:PLUSTECH
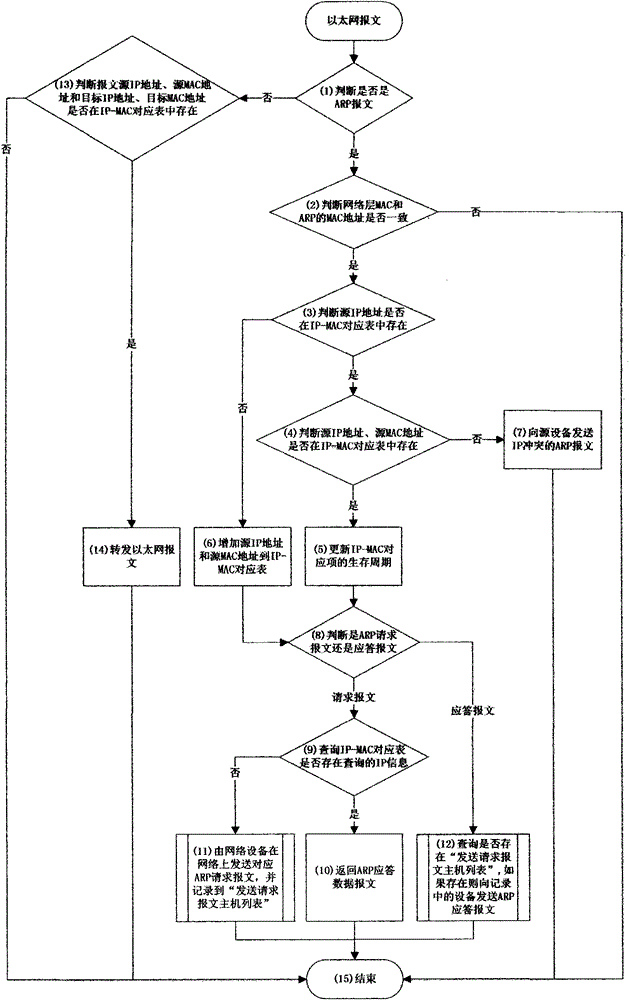
ARP message management method based on network equipment
The invention provides an ARP message management method based on network equipment, and the method is to solve the problem of network attacks of ARP spoofing and ARP storm and the like. The method comprises the following steps: 1) judging whether a message is an ARP message; 2) judging whether network layer MAC and ARP MAC addresses are consistent; 3) judging whether a source IP address exists in an IP-MAC corresponding table; 4) judging whether the source IP address and a source MAC address exist in the IP-MAC corresponding table; 5) updating life periods of corresponding items of the source IP address and the source MAC address in the IP-MAC corresponding table; 6) adding the source IP address and the source MAC address to the IP-MAC corresponding table; 7) sending an IP conflict ARP message to a source device, and skipping to a step (15); 8) judging whether the message is an ARP request message or a response message; 9) searching whether searched IP information exists in the IP-MAC corresponding table; and 10) returning the ARP response data message.
Owner:BEIJING HUAIJIAO NETWORK TECH SERVICE
Method of increasing safety of address conflict detection process
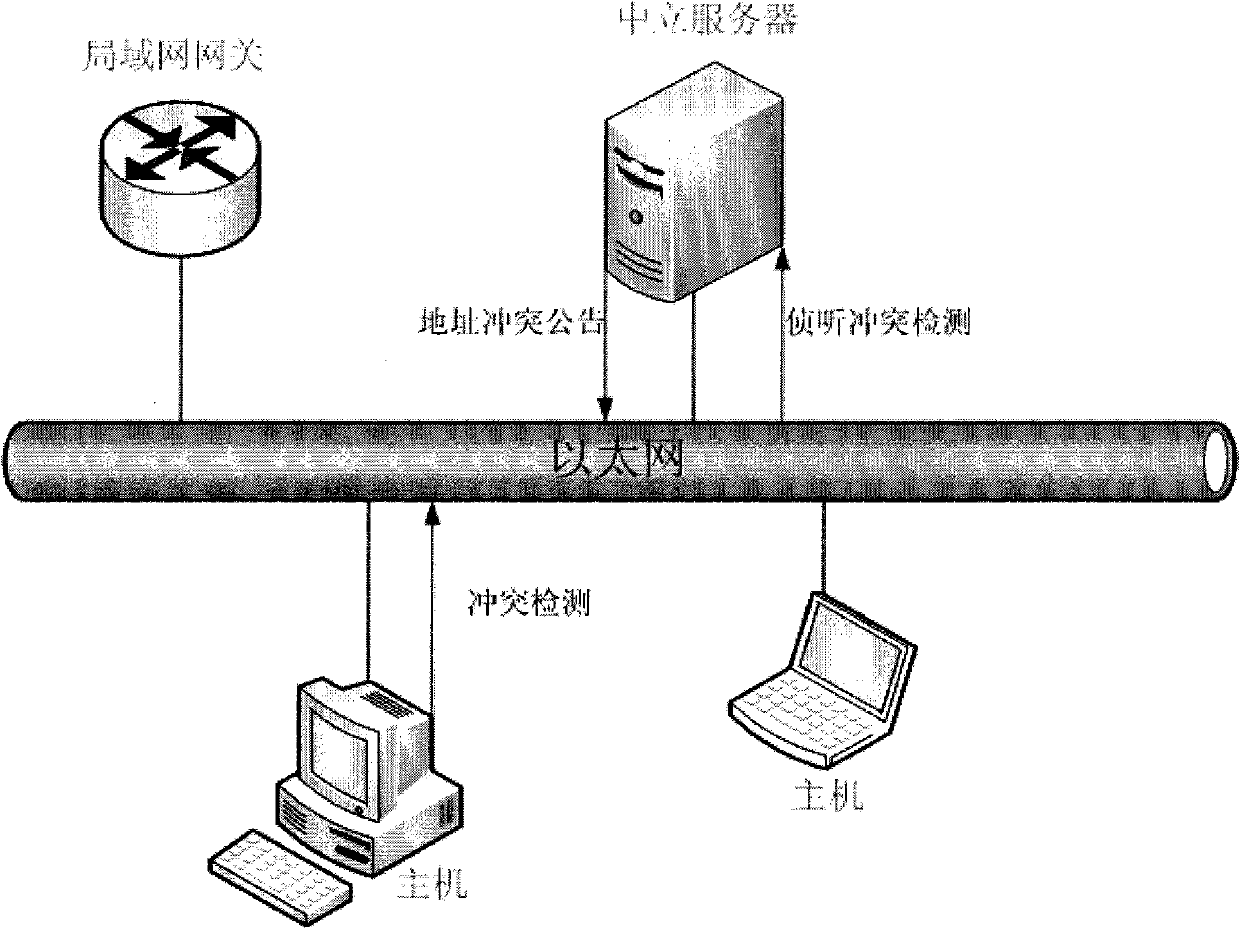
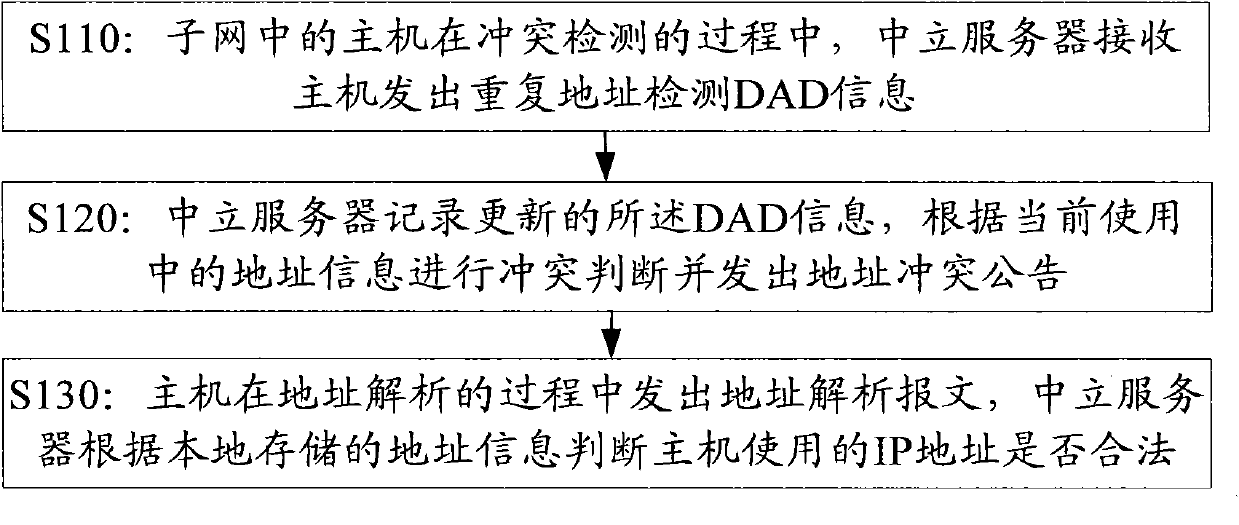
ActiveCN101951415AConvenient automatic configurationAutomatic configuration mode is fastData switching networksAddress resolutionIp address
The embodiment of the invention provides a method of increasing the safety of the address conflict detection process. The method comprises the following steps: when a host in a subnet performs a conflict detection, a neutral server receives the duplication address detection (DAD) information sent from the host; the neutral server records the updated DAD information, performs a conflict judgment according to the currently used address information and sends an address conflict notice; the host in the subnet sends an address resolution message during the address resolution process, and the neutral server judges whether the IP address of the host is legal according to the local address information. In the scheme provided by the invention, the neutral server is added in the subnet so as to solve the possible security threats of address conflict concealment, address conflict misrepresentation, ARP deception and the like during the stateless address autoconfiguration process of the Ipv6 network, and increasing the safety of the address conflict detection process.
Owner:TSINGHUA UNIV
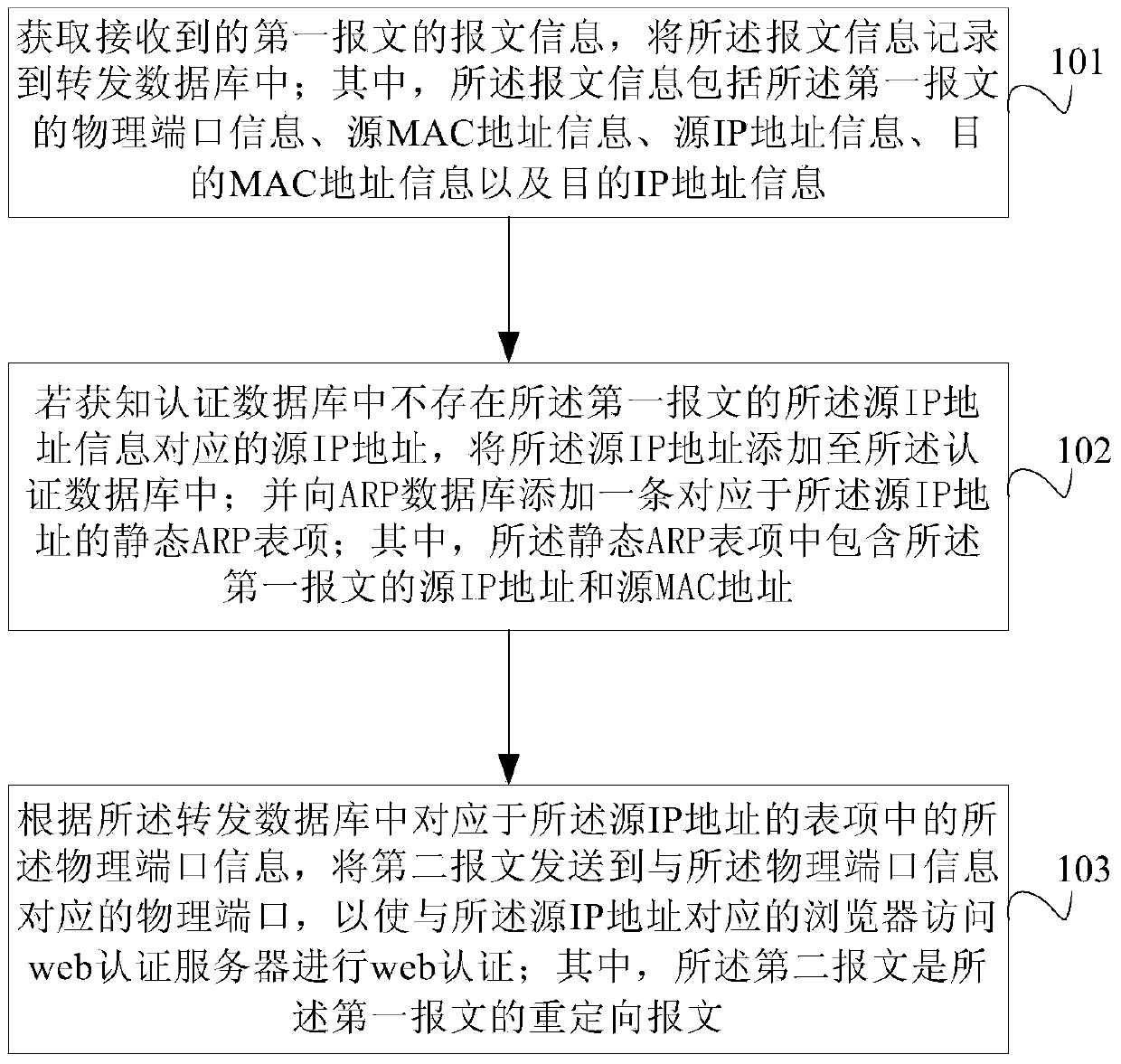
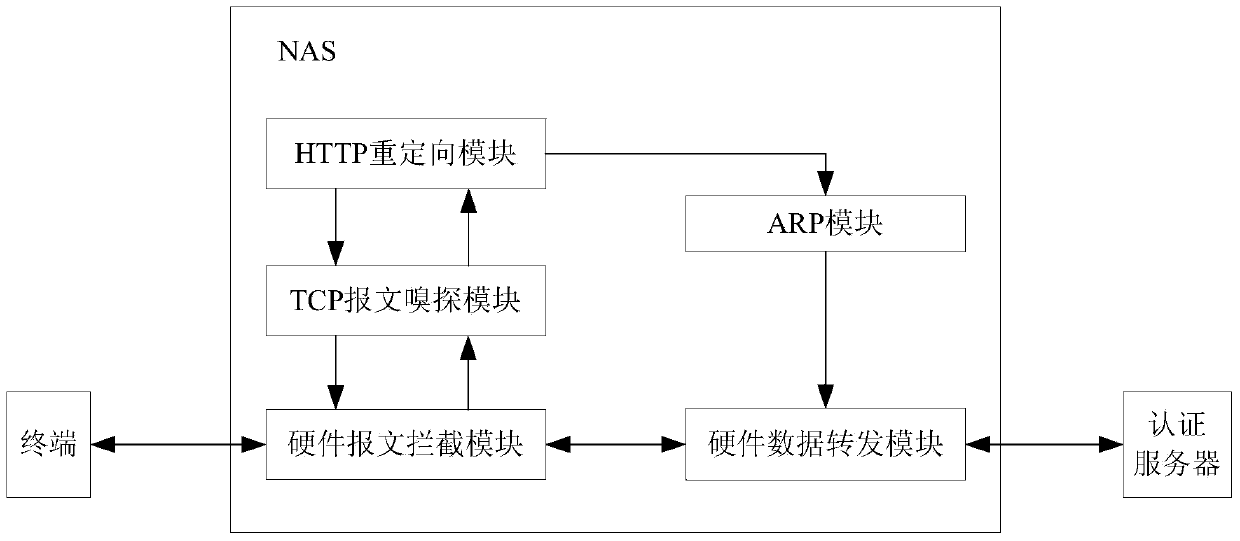
Method and device for preventing ARP cheating and network access server
The embodiment of the invention provides a method and device for preventing ARP cheating and a network access server. The method comprises the steps that message information of an obtained first message is recorded in a first forwarding database; when a user knows that a source IP address corresponding to source IP address information of the first message does not exist in an authenticated database, the source IP address is added to the authenticated database; a static ARP table item corresponding to the source IP address is added to an ARP database; a second message is sent to a physical port corresponding to physical port information according to the physical port information, corresponding to the source IP address table item, in the first forwarding database, so that a browser corresponding to the source IP address skips to have access to a web authentication server to carry out web authentication, wherein the second message is a redirect message of the first message. Therefore, the purpose that ARP cheating is prevented in the web authentication process is achieved.
Owner:BEIJING XINWANG RUIJIE NETWORK TECH CO LTD
ARP spoofing detection method and system
InactiveCN106209837ACope wellQuick detection of ARP spoofingTransmissionAddress Resolution ProtocolIp address
The invention discloses an ARP (Address Resolution Protocol) spoofing detection method applied to an electronic device. The method comprises the steps of obtaining connection information, used for accessing a local area network, of the electronic device; determining an IP (Internet Protocol) address allocable for the local area network according to the connection information, used for accessing the local area network, of the electronic device; obtaining an IP address and a corresponding MAC (Media Access Control) address of a device actually existent in the local area network according to the IP address allocable for the local area network; and determining whether ARP spoofing exists in the local area network or not according to the IP address and the corresponding MAC address of the device actually existent in the local area network. The invention furthermore provides an ARP spoofing detection system. According to the method and the system, the ARP spoofing in the local area network can be quickly detected.
Owner:MEIZU TECH CO LTD
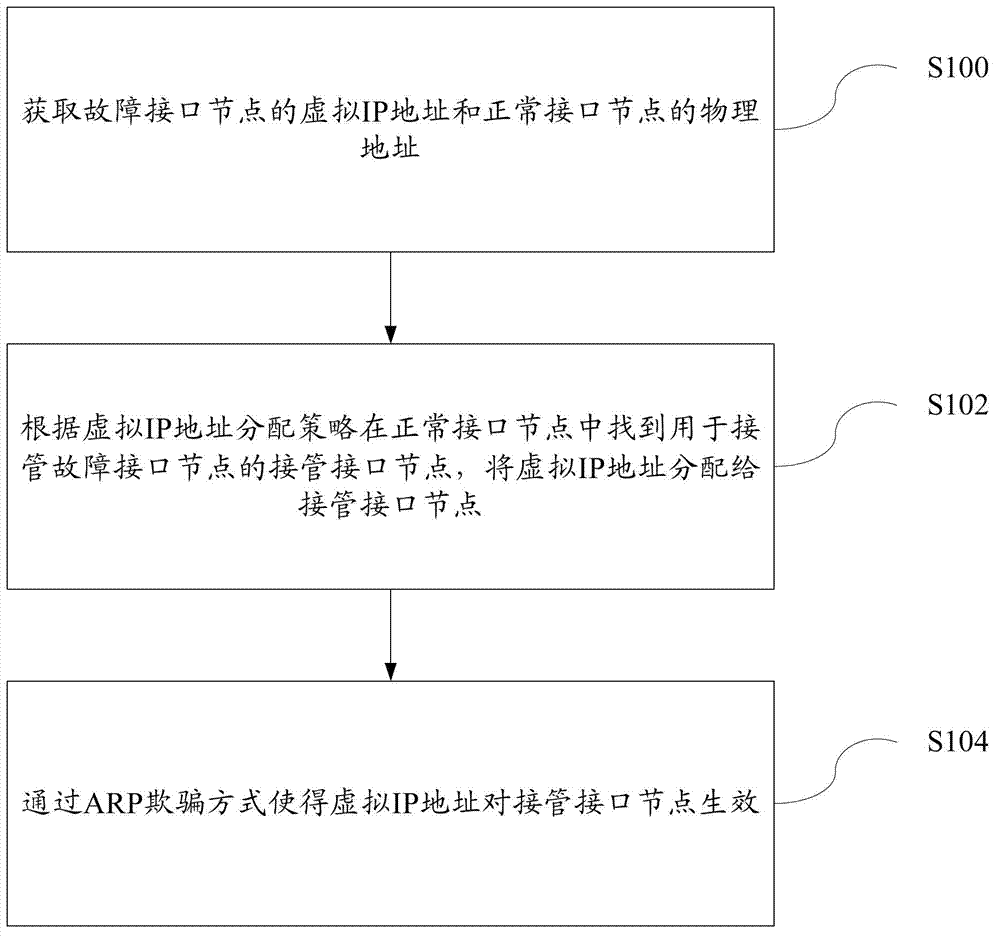
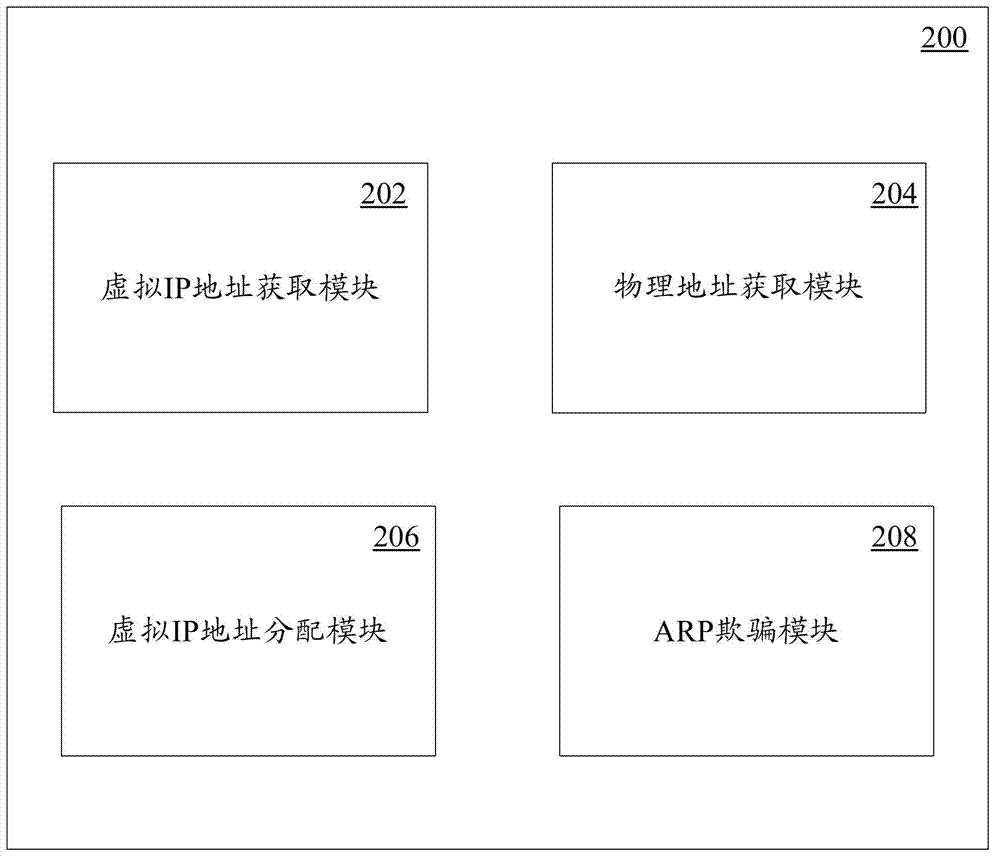
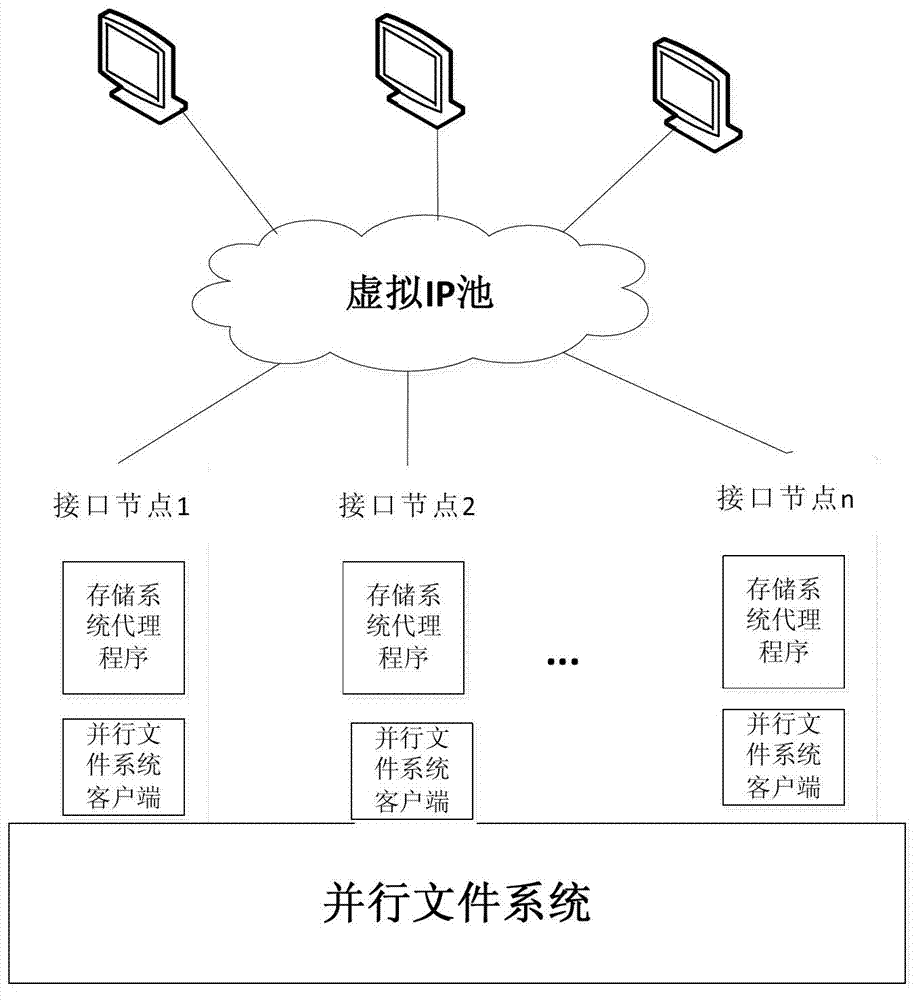
Method and system for taking over fault interface node
The invention discloses a method for taking over a fault interface node in a storage system. The method comprises the steps of S1: obtaining a virtual Internet protocol (IP) address of the fault interface node and a normal interface node; S2: finding out a taking-over interface node which takes over the fault interface node in the normal interface node according to a virtual IP address allocation strategy, and allocating the virtual IP address to the taking-over interface node; and S3: enabling the virtual IP address to take effect on the taking-over interface node according to an address resolution protocol (ARP) cheating method. Besides, the invention also discloses a system for taking over the fault interface node. The system comprises the fault interface node, the normal interface node, a fault interface node virtual IP address acquisition module, a normal interface node acquisition module, a virtual IP address allocation module and an ARP cheating module. By the aid of the method and the system for taking over the fault interface node, the fault interface node can be taken over smoothly.
Owner:SUGON INFORMATION IND
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com