Automatic locating and isolating method of internal attack source of local area network
An internal attack and automatic positioning technology, applied in the field of network communication, can solve problems such as heavy maintenance workload, error-prone, cumbersome judgment process, etc., and achieve the effects of improving work efficiency, ensuring network security, and shortening processing time
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0019] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be further described in detail below in conjunction with the accompanying drawings.
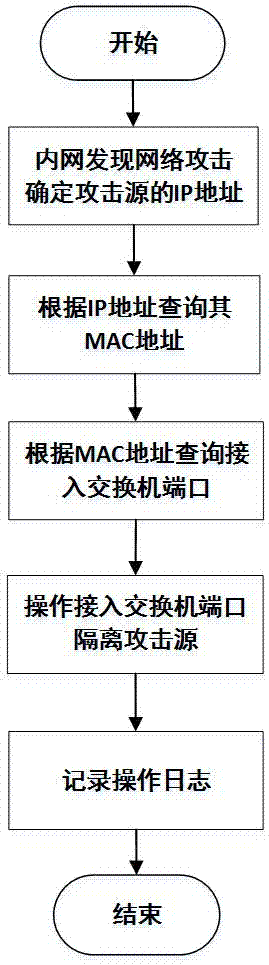
[0020] A method for automatically locating and isolating an internal attack source in a local area network according to an embodiment of the present invention includes the following steps.
[0021] combine figure 1 shown.
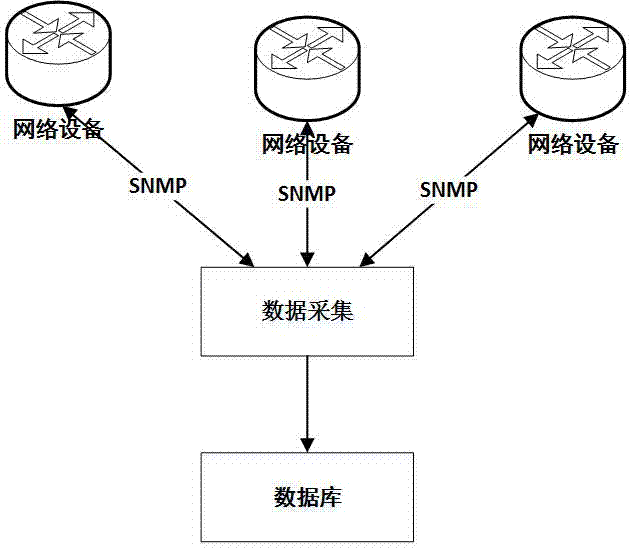
[0022] Data collection steps:
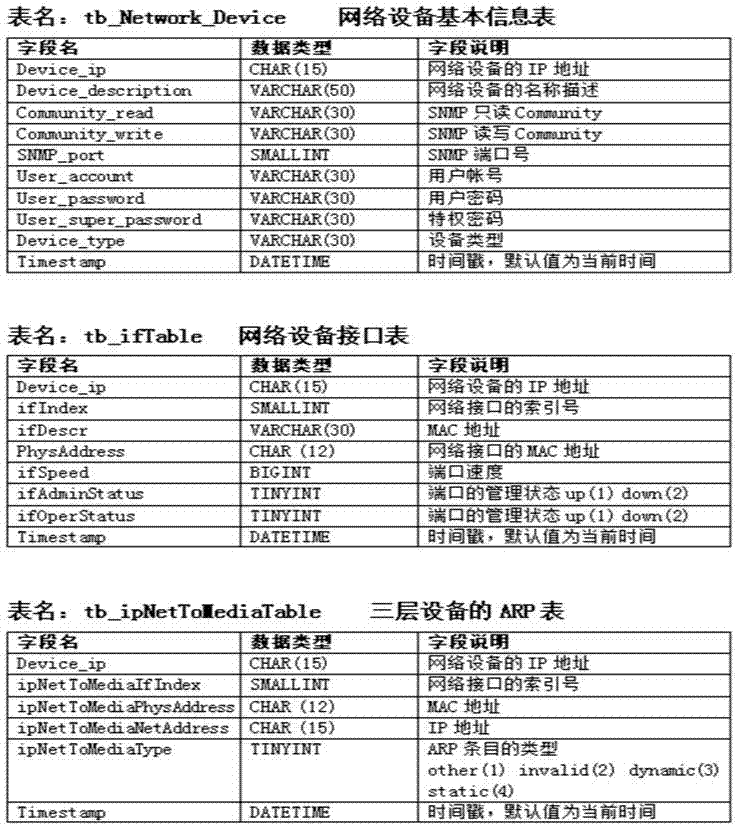
[0023] The data acquisition program automatically collects the data of the network equipment and saves it to the database. The data acquisition program uses SNMP to obtain the data of the MIB (Management Information Base) of the network equipment. The current network equipment supports the SNMP protocol. The operation of the network equipment through SNMP and the manufacturer model of the equipment (except private MIB) and software configuration have nothing to do. SNMPv2 provides With the Get-Bulk primitive (...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com