Method of automatically detecting host-passing-off ARP spoofing
A technology of ARP spoofing and automatic detection, applied in the field of network communication, it can solve the problems of ARP firewall's self-defense, difficult centralized management, system performance degradation, etc., to avoid misjudgment and maintain good performance.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0013] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be further described in detail below in conjunction with the accompanying drawings.
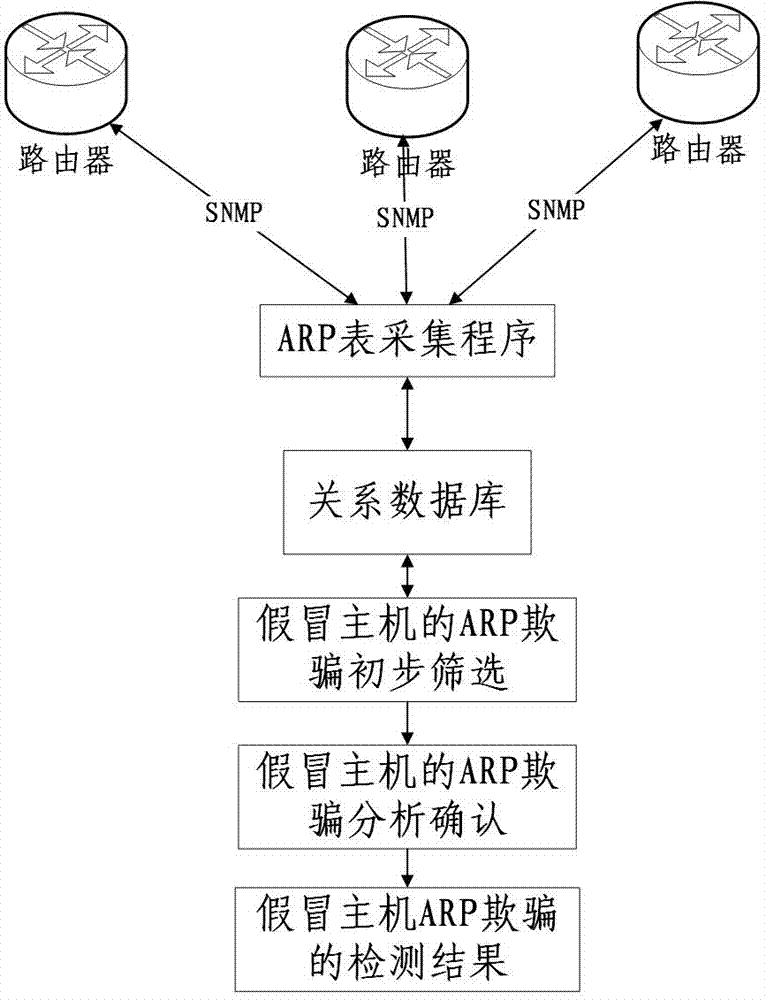
[0014] The implementation of the present invention discloses a method for automatically detecting fake host ARP spoofing, the topological structure diagram is as follows figure 1 As shown, it includes two parts: the data collection method and the ARP spoofing detection method, and the detection method includes preliminary screening and analysis and confirmation.
[0015] 1. Data Acquisition Program
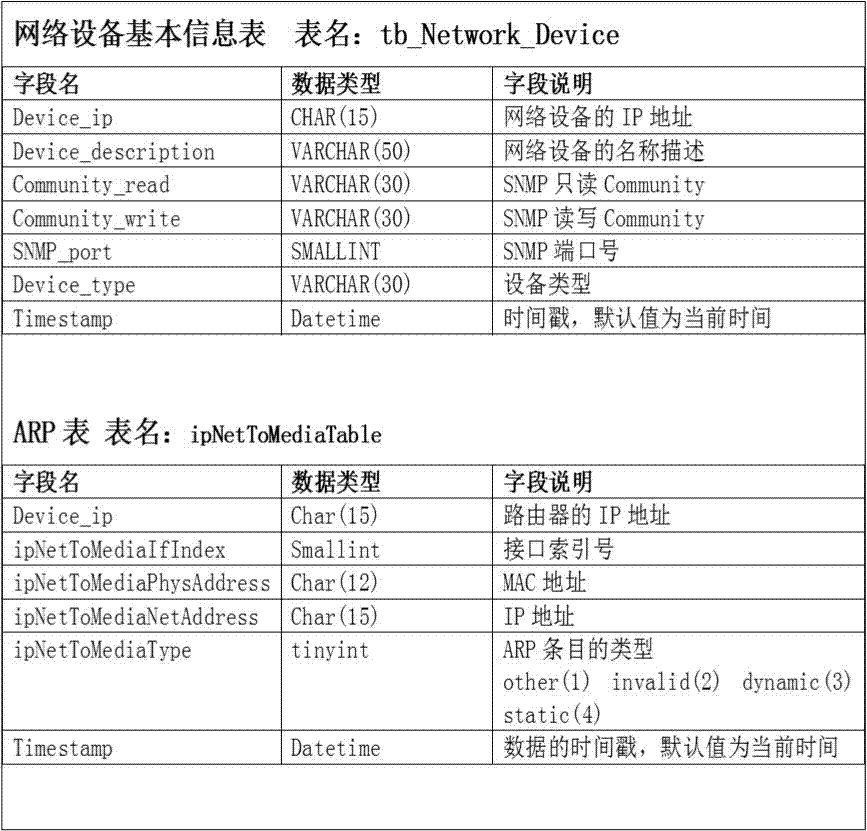
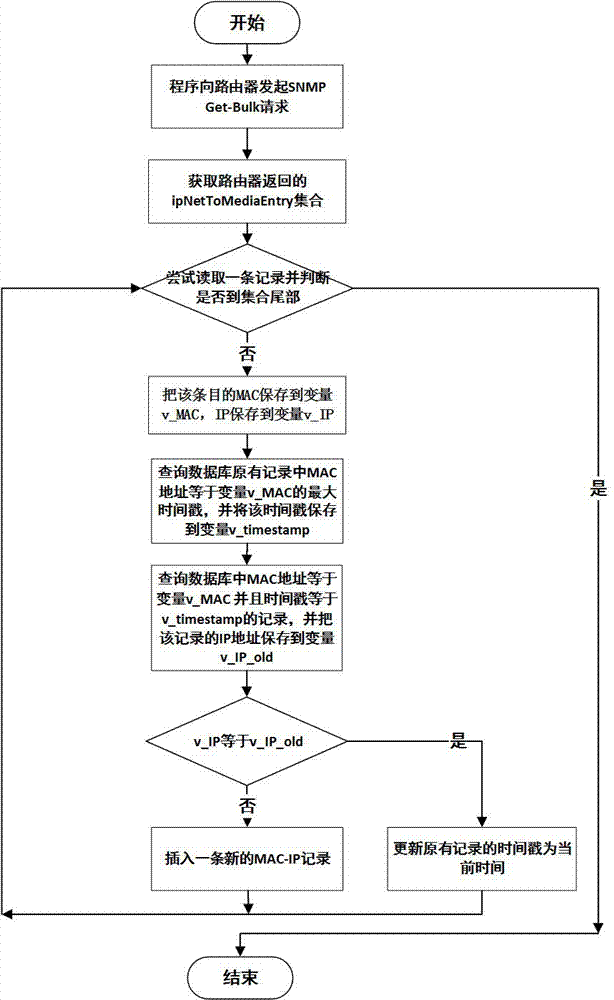
[0016] The data collection program uses the SNMP protocol to automatically and regularly obtain the ARP table of the three-layer device (router, three-layer switch, firewall and other devices that work on the third layer of the TCP / IP protocol) and save it to the database. The collection frequency should be less than the expiration of the device's ARP table Time (us...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com