Patents
Literature
36 results about "DHCP snooping" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
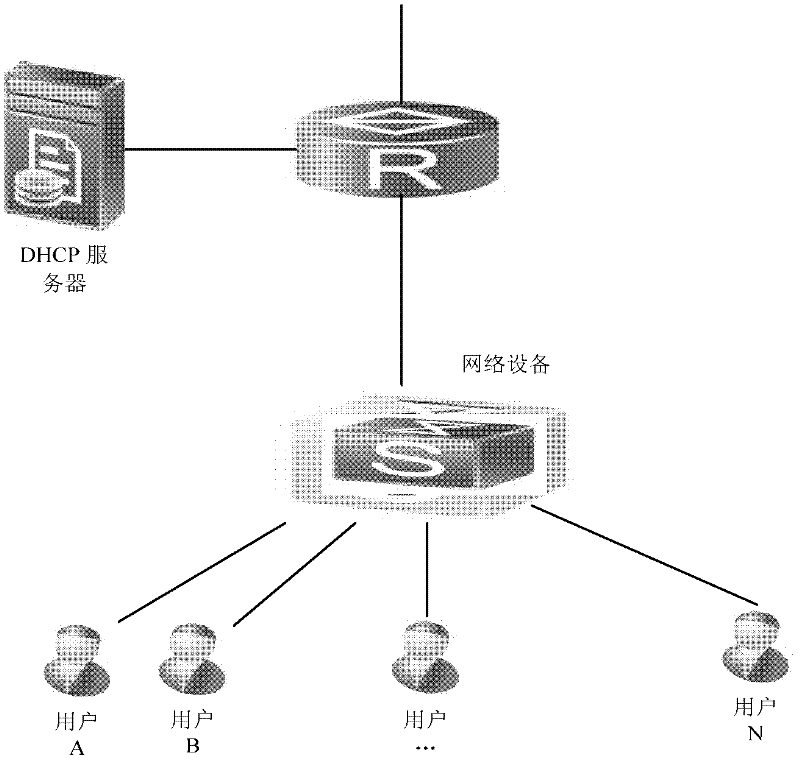
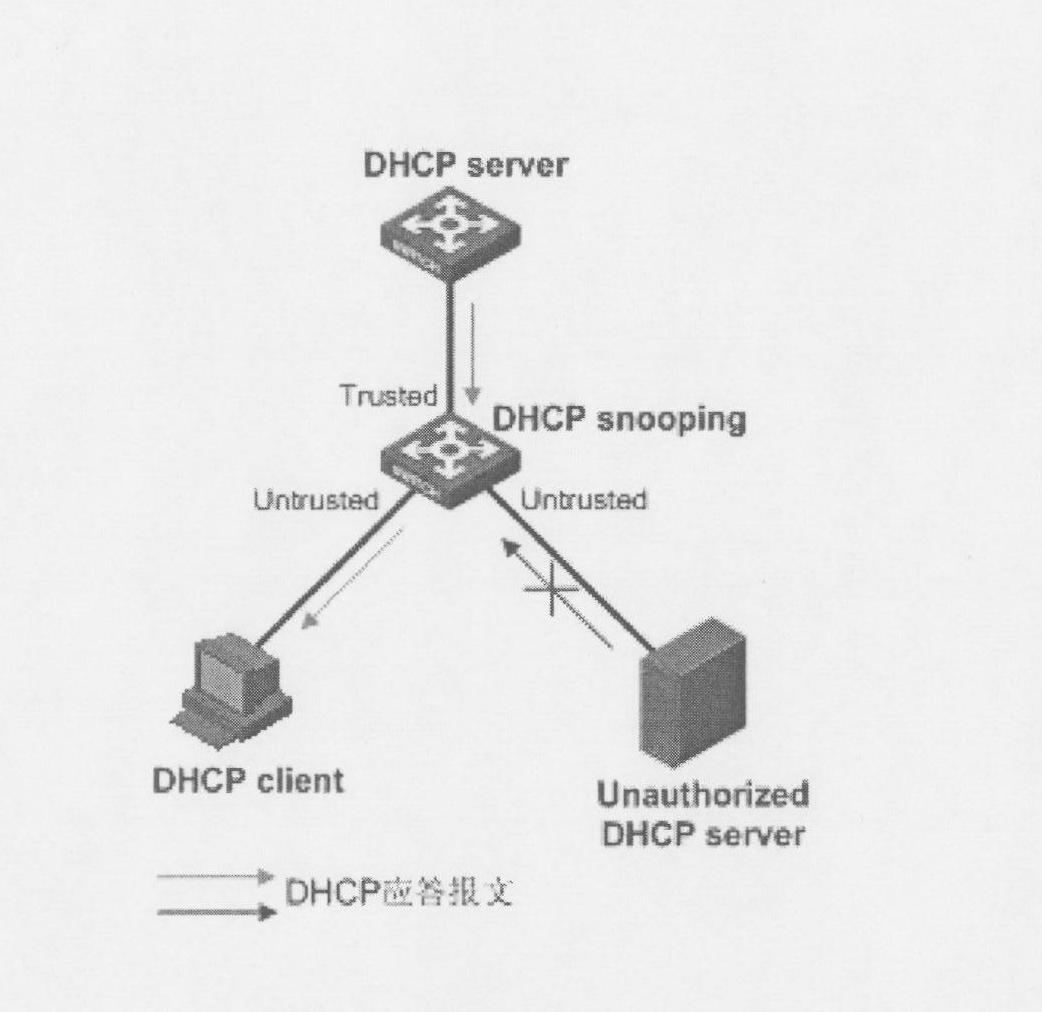
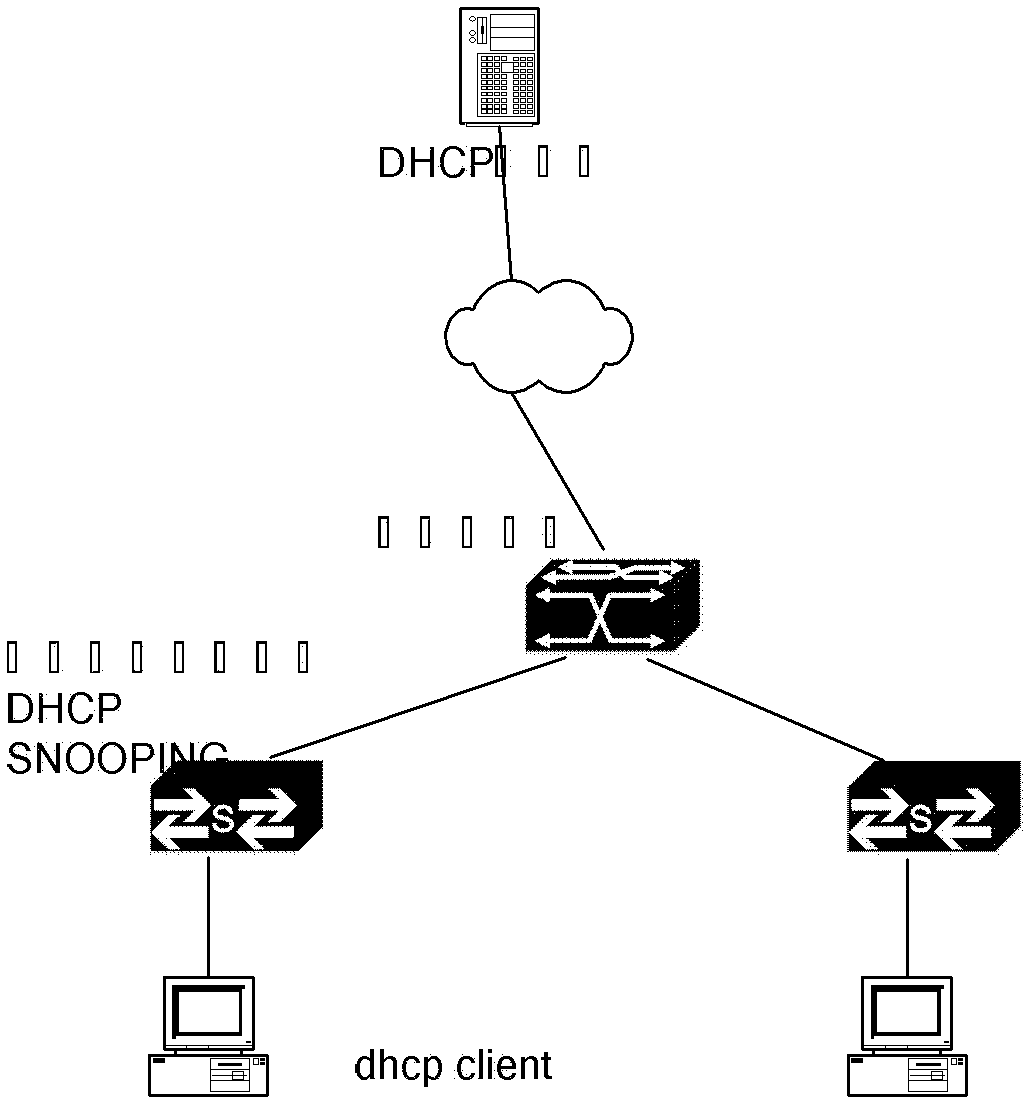
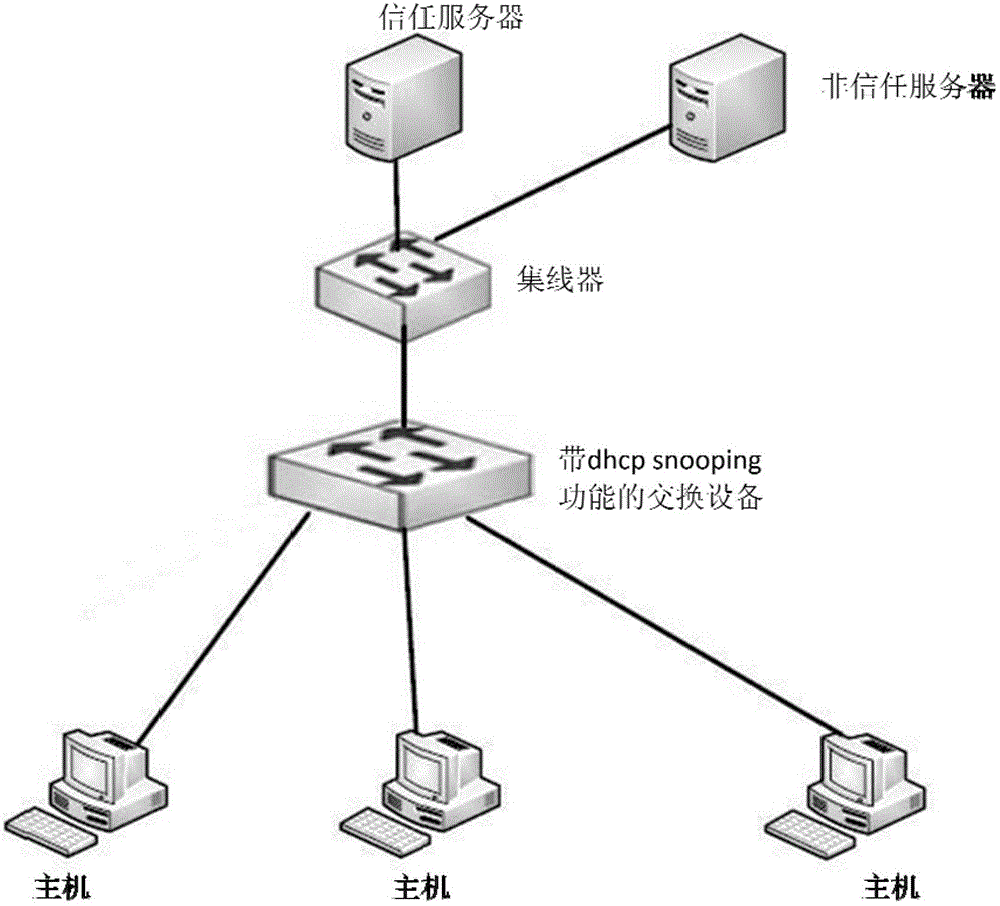
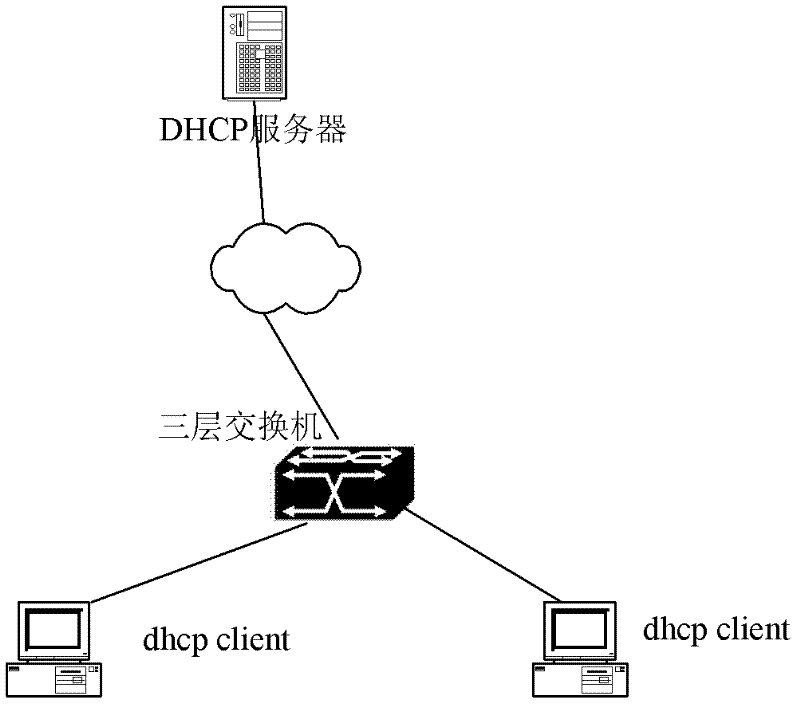
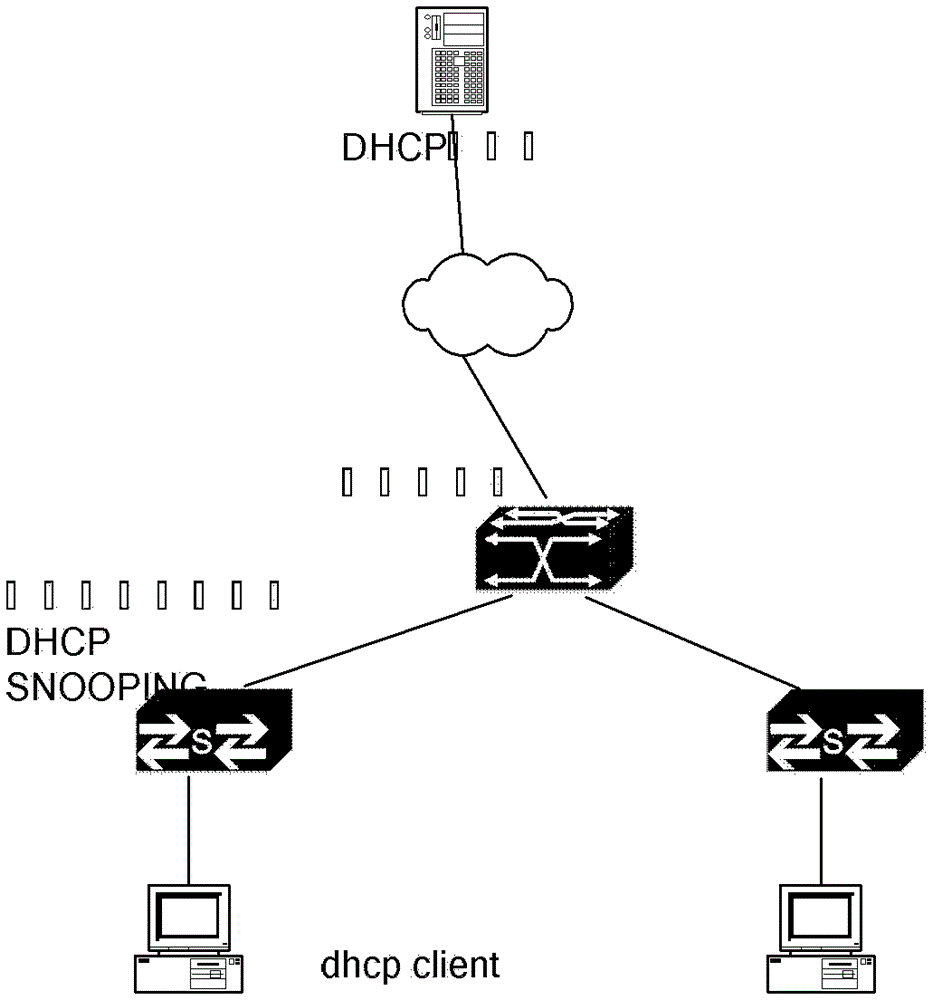
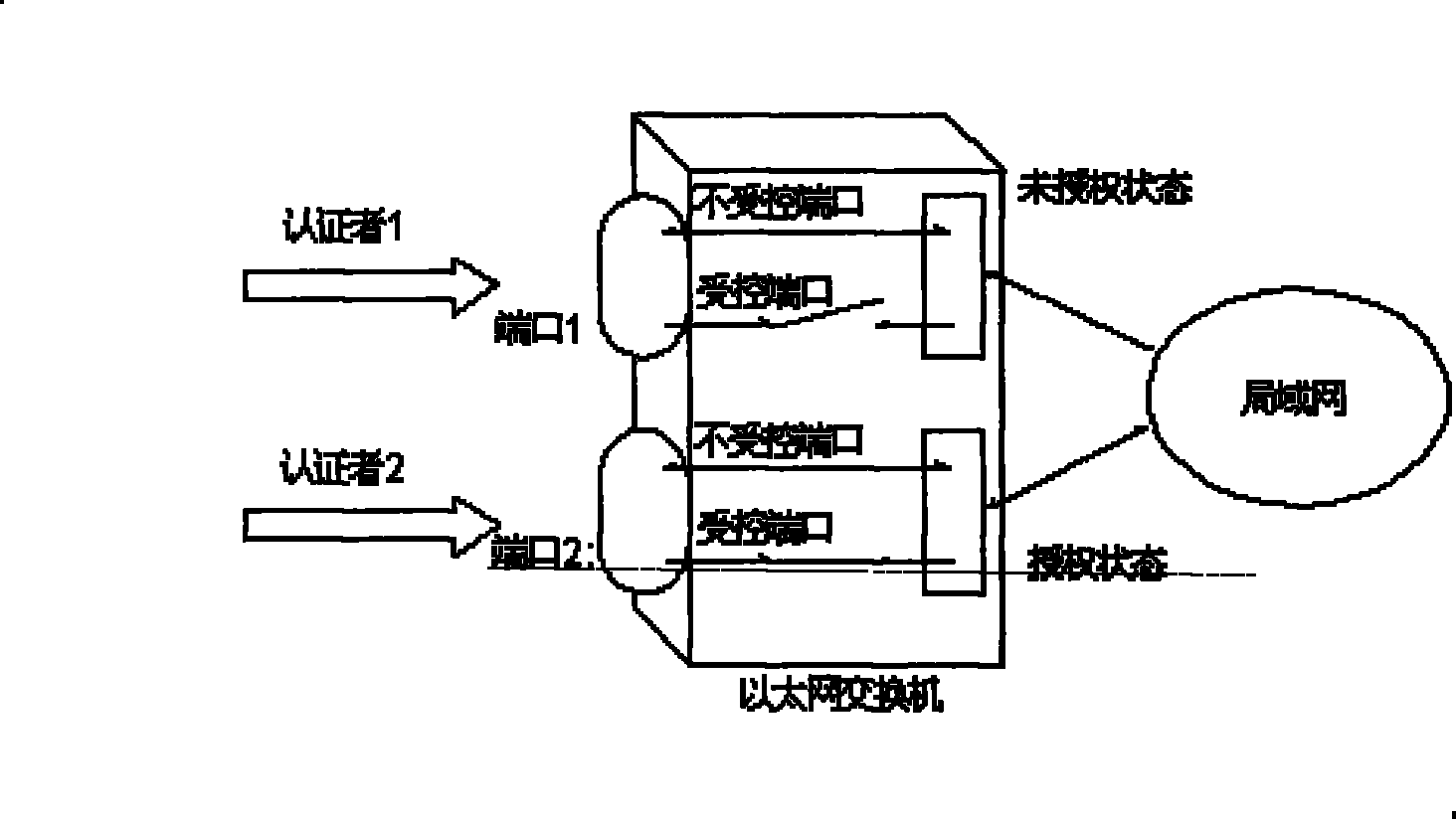
In computer networking, DHCP snooping is a series of techniques applied to improve the security of a DHCP infrastructure. When DHCP servers are allocating IP addresses to the clients on the LAN, DHCP snooping can be configured on LAN switches to prevent malicious or malformed DHCP traffic, or rogue DHCP servers. In addition, information on hosts which have successfully completed a DHCP transaction is accrued in a database of "bindings" which may then be used by other security or accounting features.
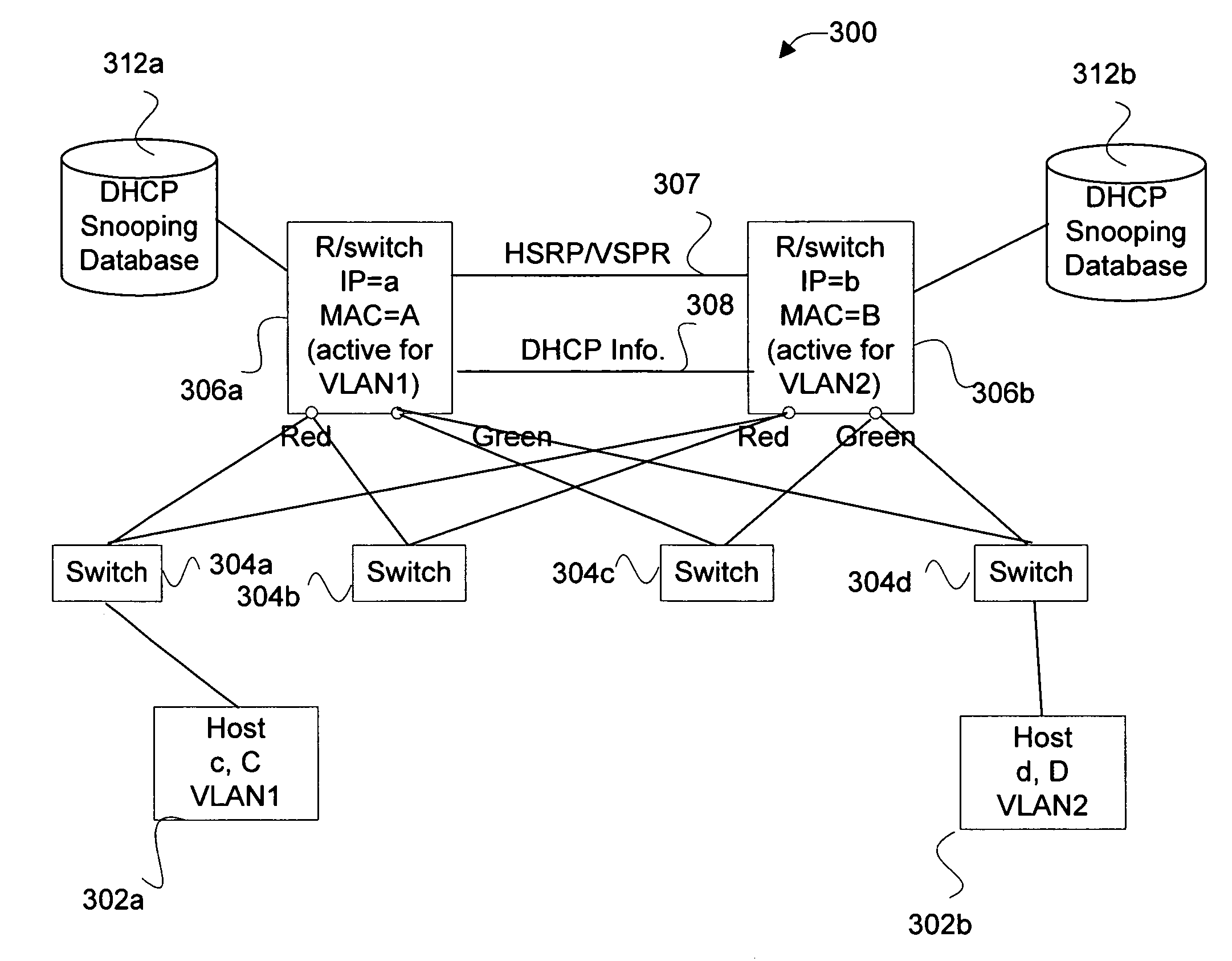
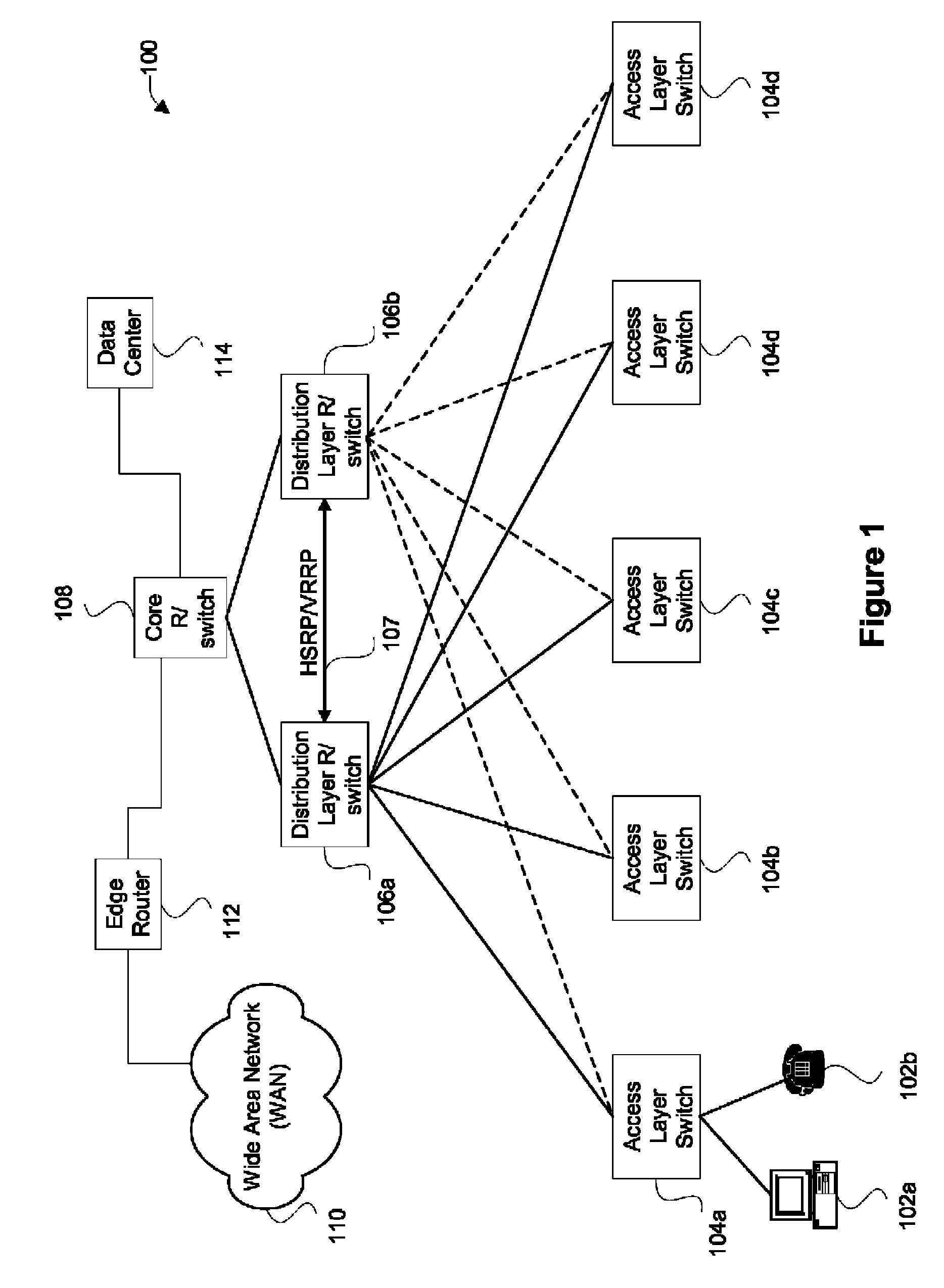
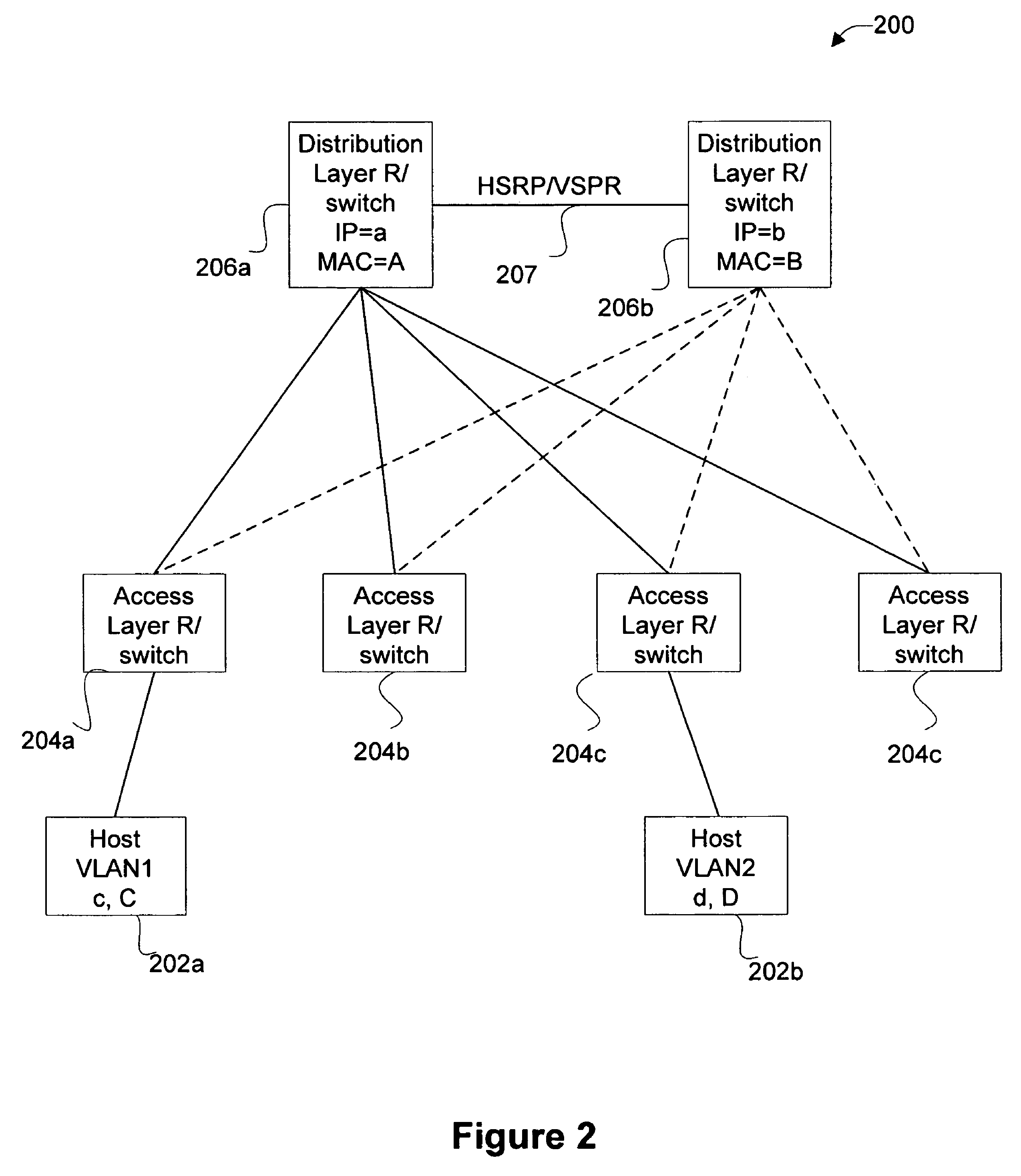
Extending sso for DHCP snooping to two box redundancy
InactiveUS20070121617A1OptimizationData switching by path configurationAddress Resolution ProtocolIp address
Disclosed are mechanisms for facilitating the use of DHCP (dynamic host configuration protocol) binding data. In general, certain applications include mechanisms for intercepting data being sent from a node and then determining whether the data corresponds to a valid IP address and MAC address binding. Embodiments of the present invention provide mechanisms for sharing such DHCP binding data between routers (or other type of network devices) in a redundancy group so that any of the routers may take over the data inspection to validate DHCP bindings. In particular aspects of the invention, the DHCP binding data is validated in procedures related to DHCP snooping, dynamic ARP (address resolution protocol) inspection, and the like.
Owner:CISCO TECH INC
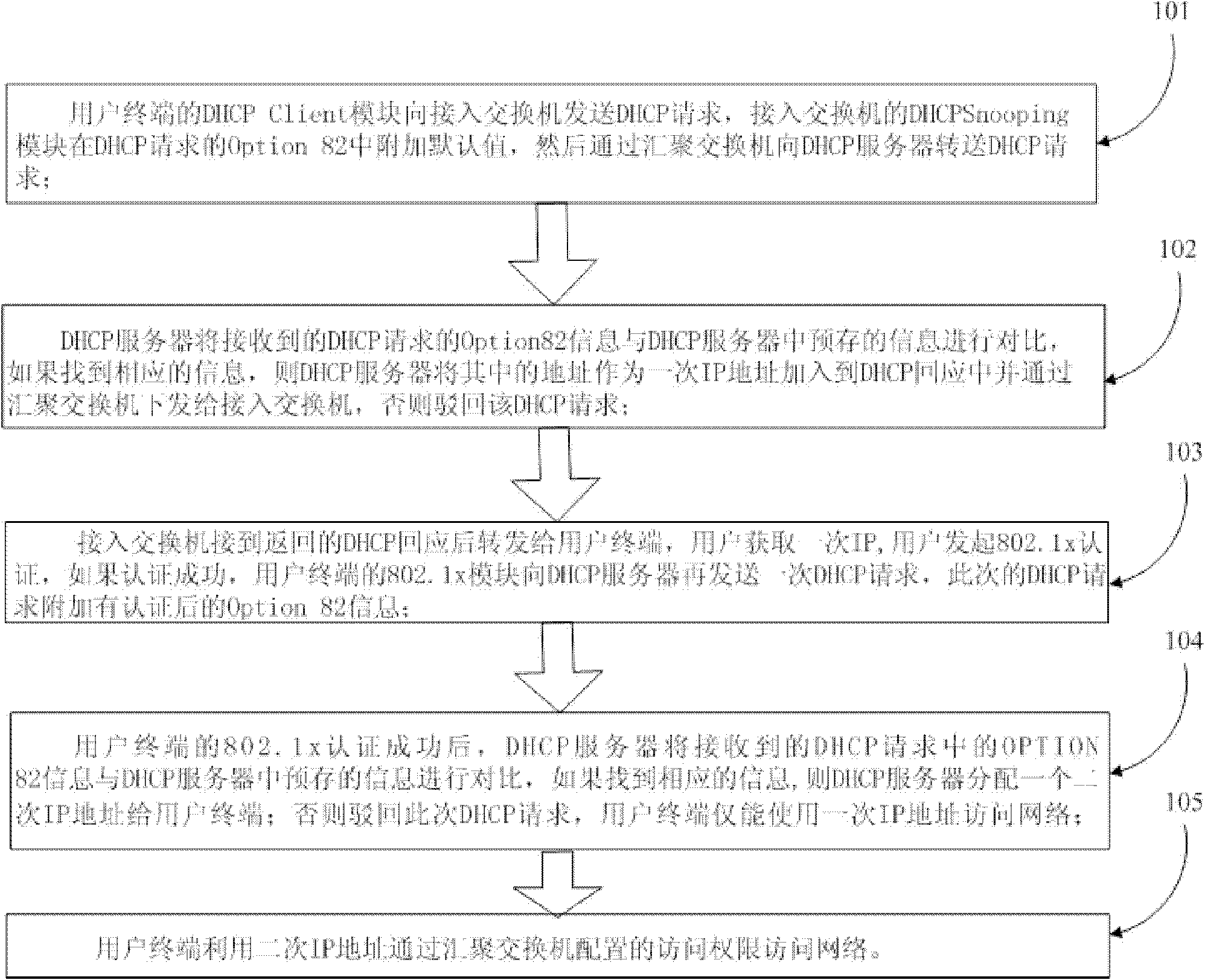
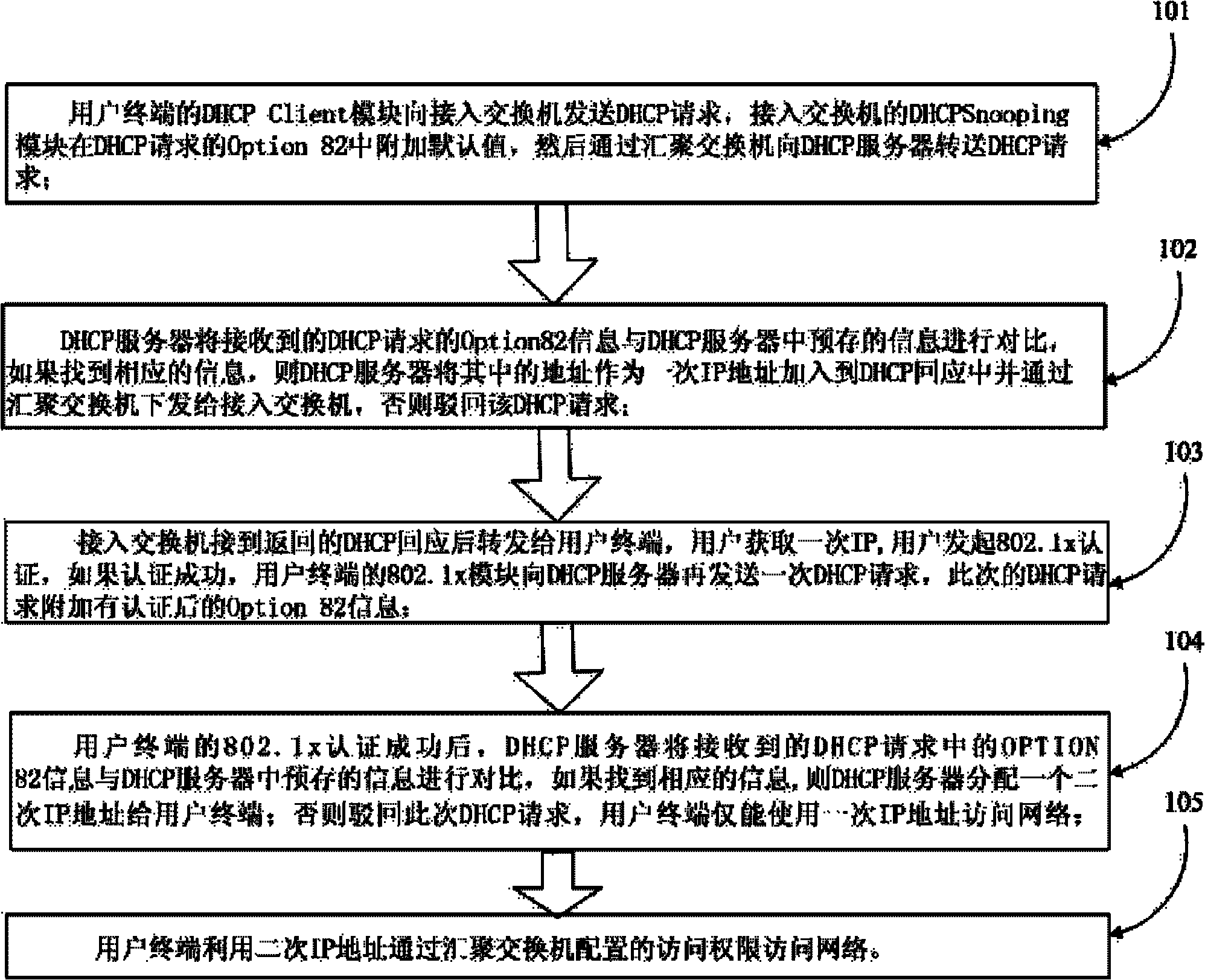
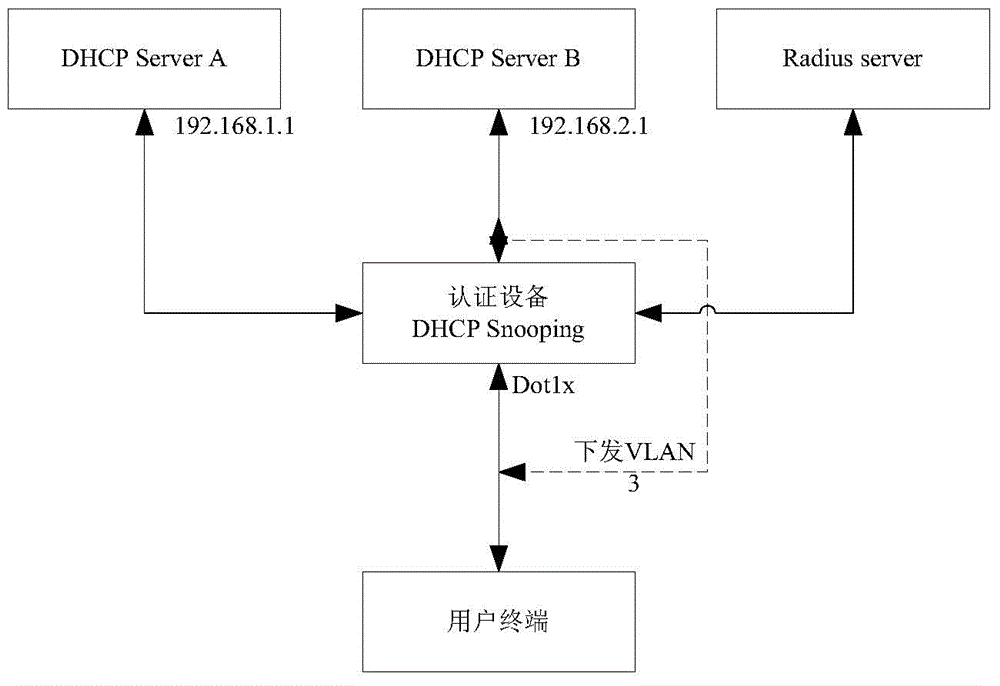
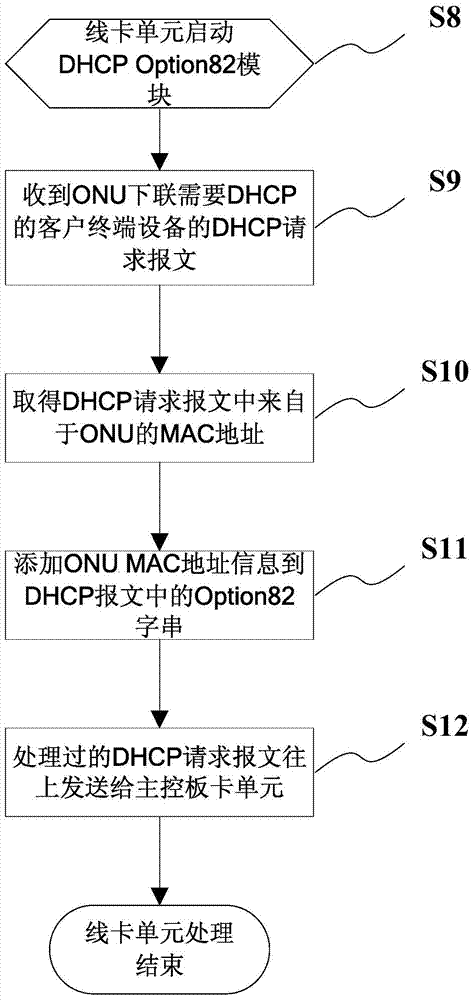
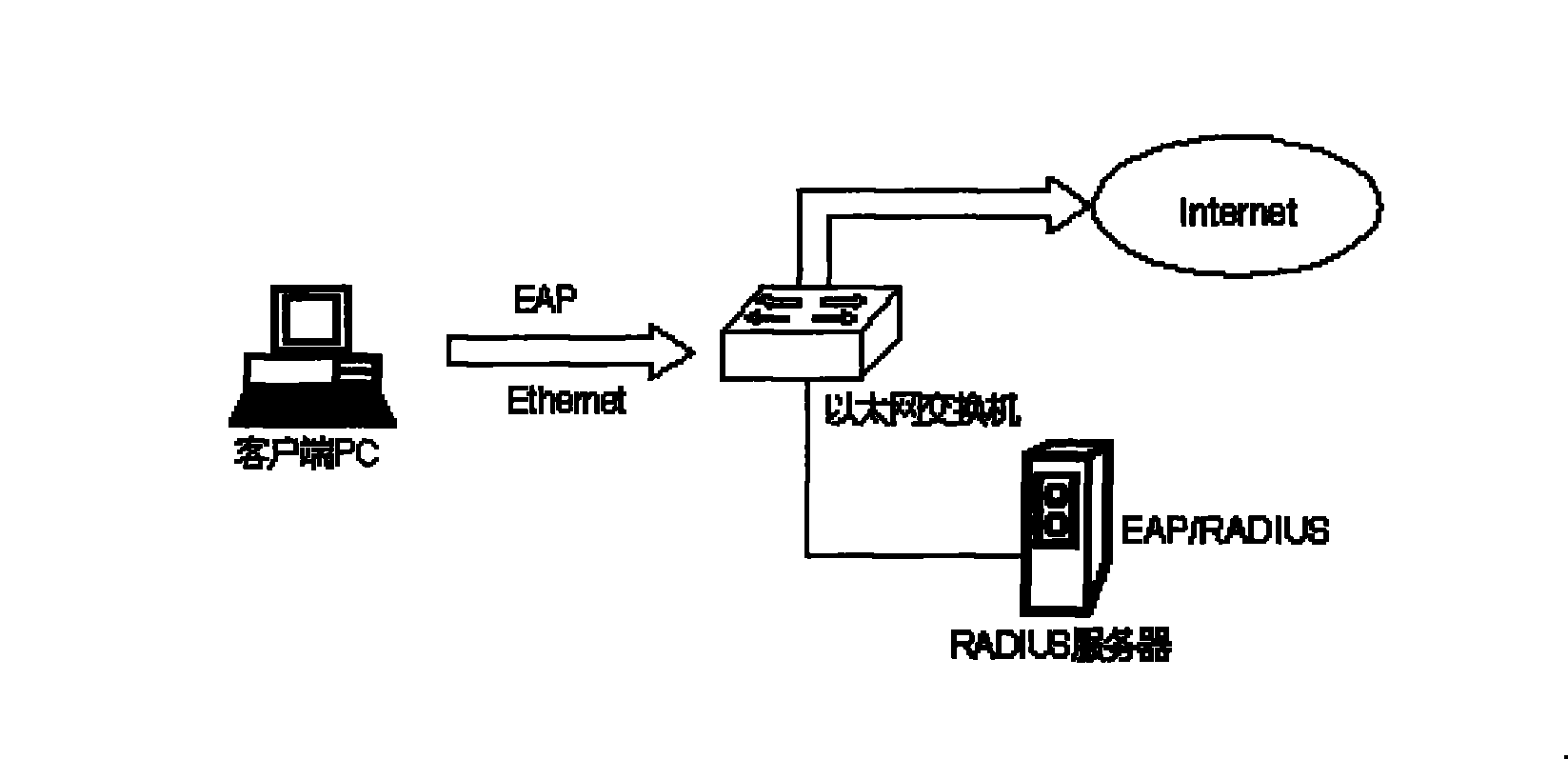
DHCP (Dynamic Host Configuration Protocol) Option 82 based user accessing authority control method
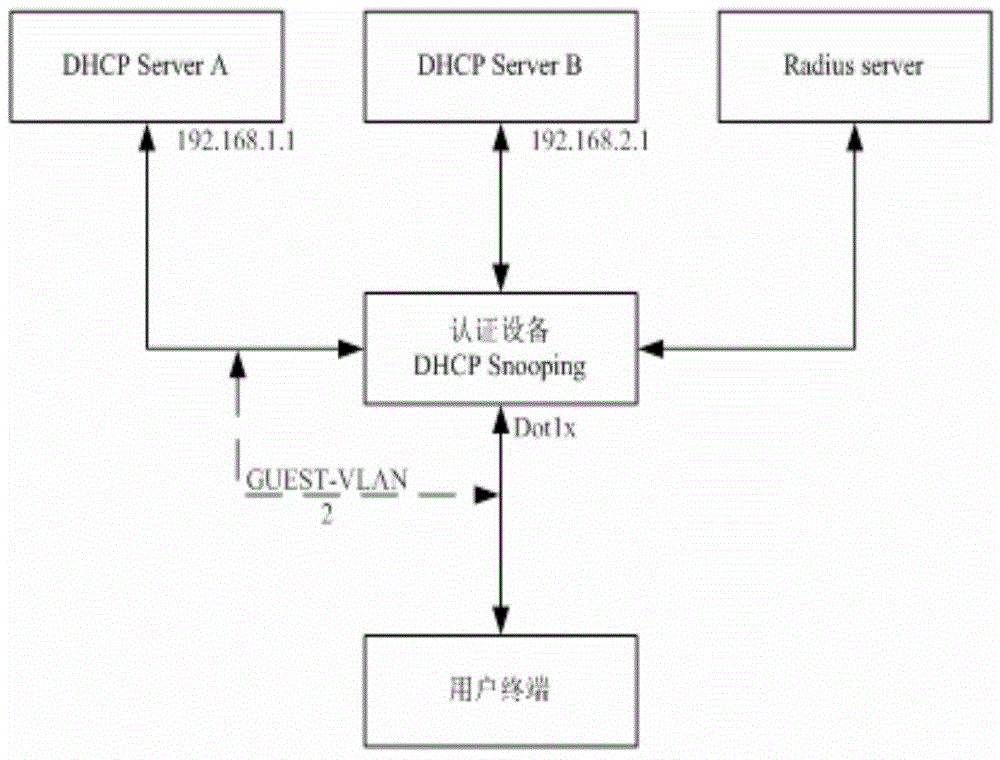
The invention discloses a DHCP (Dynamic Host Configuration Protocol) Option 82 based user accessing authority control method and belongs to the field of computer data communication. The method comprises the following steps: adding Option 82 information when a DHCP Snooping module is used for monitoring a DHCP request of a user terminal; sending Option 82 authenticating information of a user by a Radius server after the user terminal successfully acquires an address and passes the authentication; reapplying an address by 802.1x, after the user terminal successfully passes the authentication; adding the authenticated Option 82 information to the DHCP request by the DHCP Snooping module; and allocating another address to the user by a DHCP server according to the Option 82 information. A hardware ACL (Access Control List) item is configured on a converging switcher, thereby limiting the resources which can be accessed by the users with different source IP addresses and further controlling the access authority of the user terminal before and after authentication.
Owner:北京神州数码云科信息技术有限公司
Client access method, equipment and system
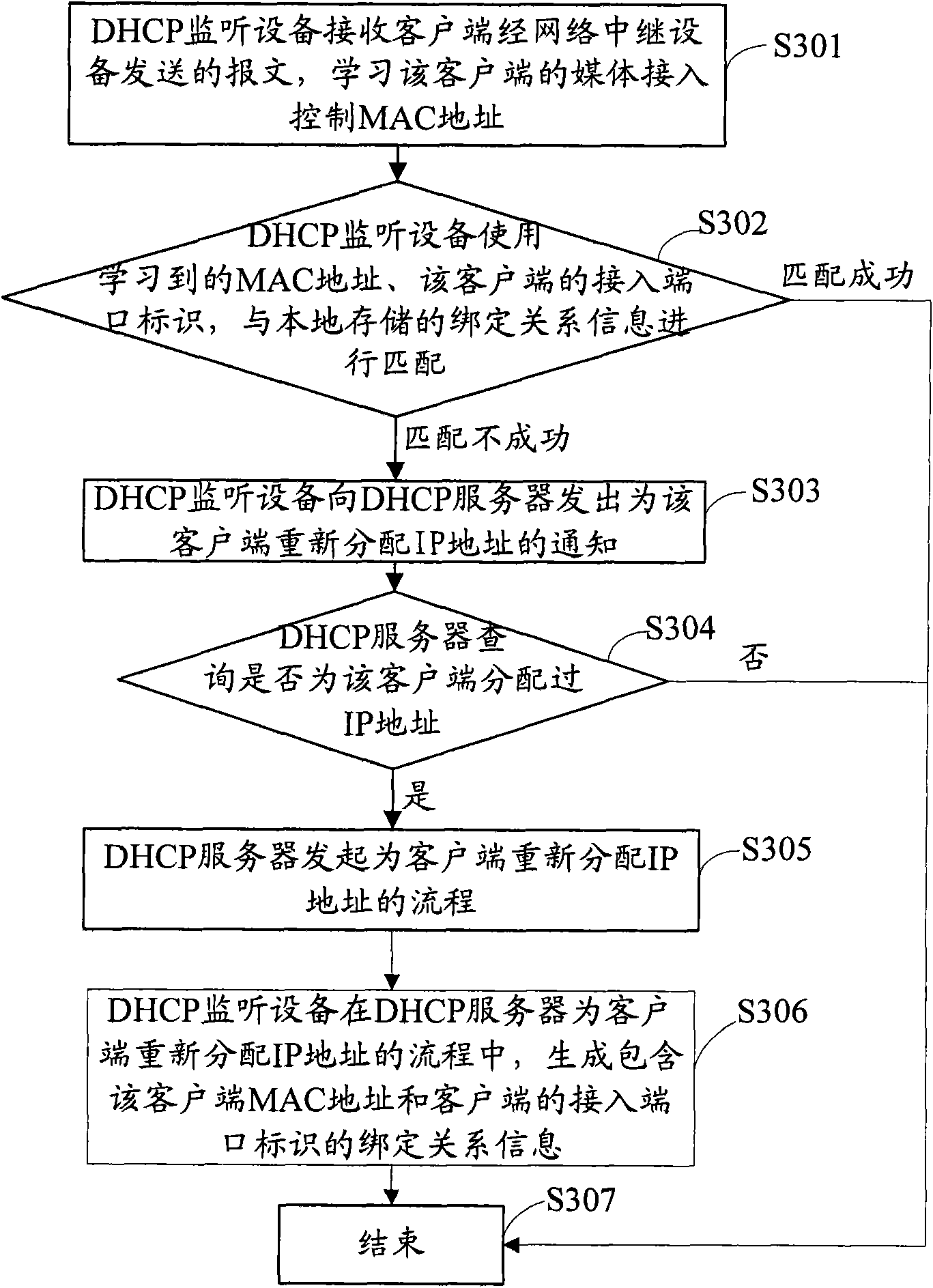
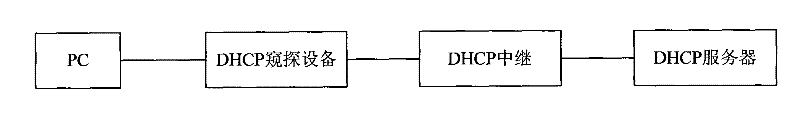
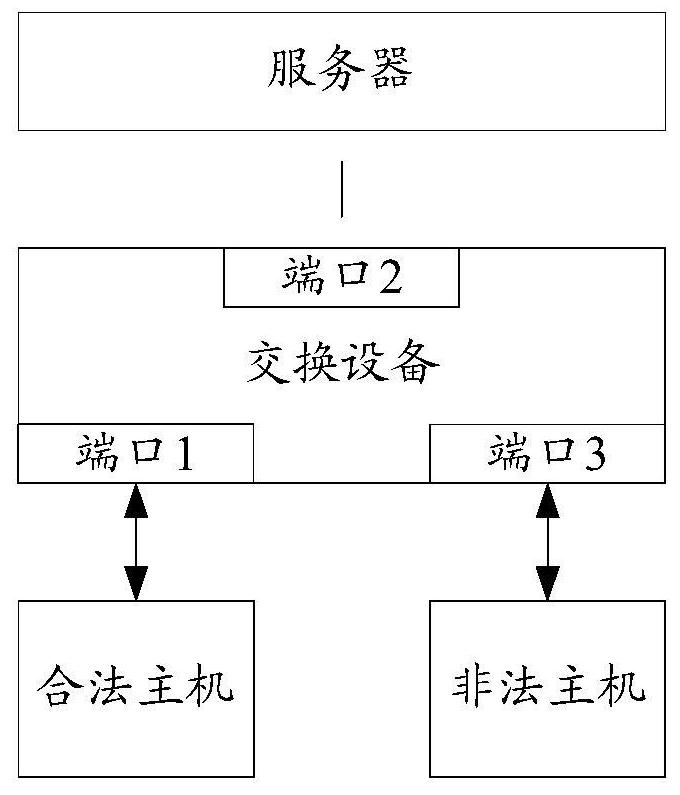
The invention discloses a client access method, equipment and a system. The method comprises the following steps that: DHCP snooping equipment receives a message transmitted by a client through network trunk equipment and learns the MAC address of the client from the message; the DHCP snooping equipment uses the learned MAC address and the access port identifier of the client to match with locally stored binding relationship information; when the learned MAC address and the access port identifier of the client are not matched with the binding relationship information, a notice for reassigning an IP address for the client is transmitted to a DHCP server; when the DHCP server inquires that the IP address is assigned to the client, a process for reassigning the IP address to the client is initiated; and in the process that the DHCP snooping equipment reassigns the IP address to the client, the binding relationship information containing the MAC address and the access port identifier of the client is generated. The invention ensures that the client can use the reassigned IP address to normally communicate with the DHCP snooping equipment through the network trunk equipment.
Owner:BEIJING XINWANG RUIJIE NETWORK TECH CO LTD
Intelligent control method for realizing city Ethernet exchanger switch-in security
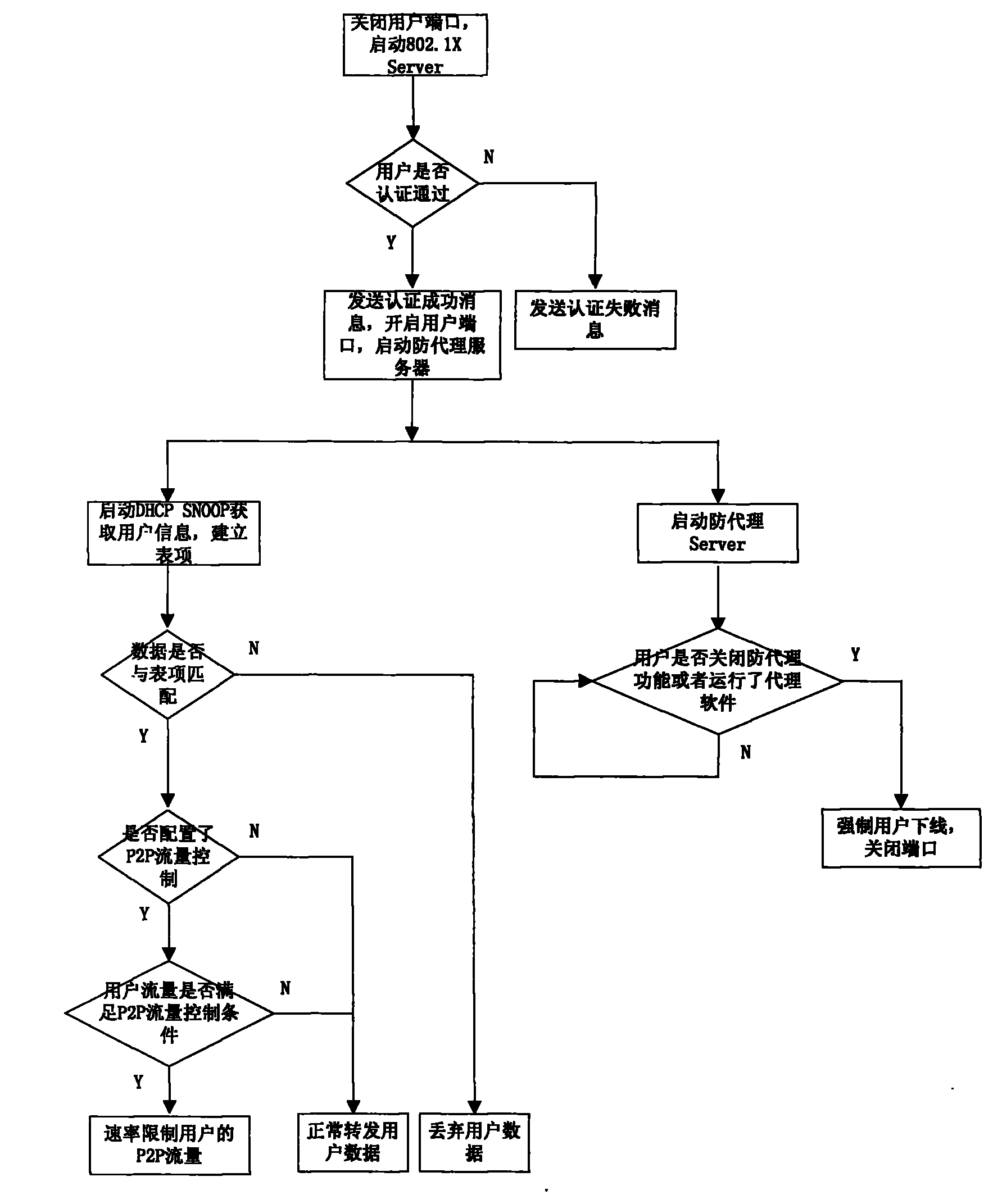
InactiveCN101022340AAchieve legality certificationComprehensive monitoringUser identity/authority verificationData switching by path configurationTraffic capacityMetro Ethernet
An intelligently controlling method for realizing city Ethernet switch-board access safety integrates functions of certificating user legality, exerting illegal agent proof of legal user, controlling P2P flow rate and DHCP SNOOP together in said method for controlling and monitoring user in order to raise safety of network.
Owner:WUHAN FIBERHOME NETWORKS
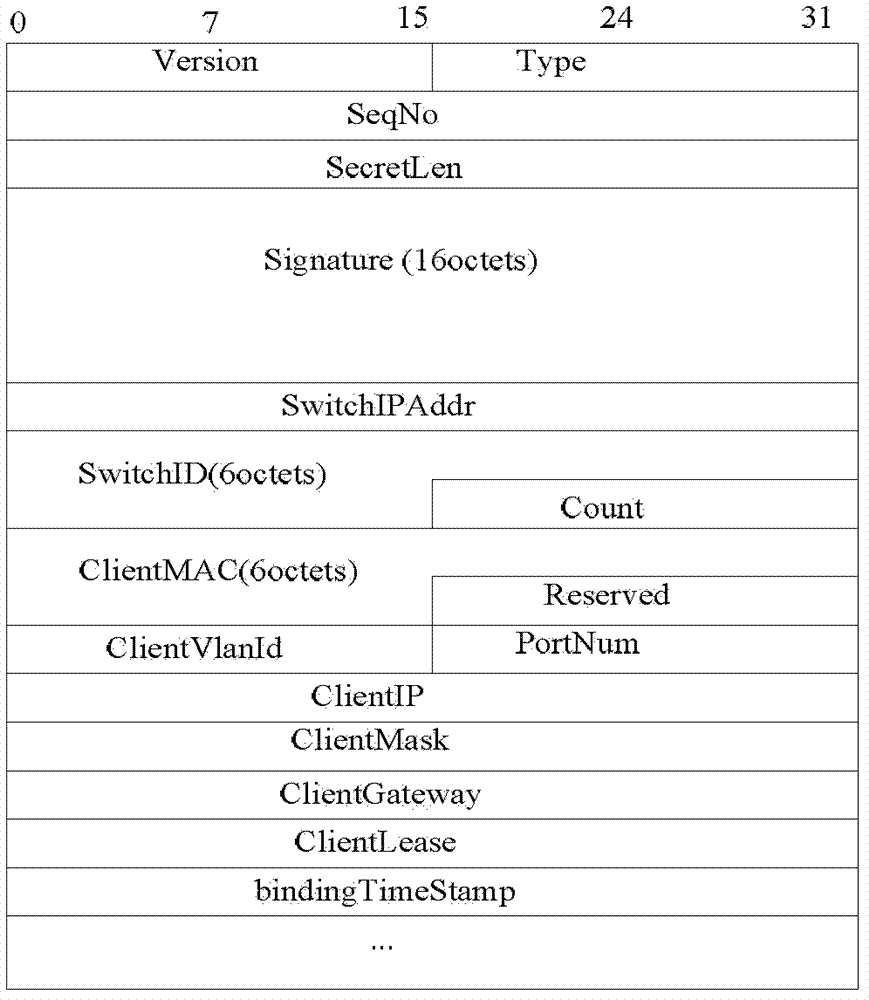
Method, device, equipment and system for generating DHCP (Dynamic Host Configuration Protocol) Snooping binding table
The embodiment of the invention provides a method, device, equipment and system for generating a dynamic host configuration protocol (DHCP) Snooping binding table. The method comprises the steps of: structuring a request message used for acquiring DHCP user information, and sending the request message to a DHCP server; receiving a response message, corresponding to the request message, of the DHCP server, and extracting the user information in the response message, wherein the user information comprises a user internet protocol (IP) address and a media access control (MAC) address; and acquiring a user virtual local area network (VLAN) number and input port number according to the MAC address to further generate the DHCP Snooping binding table. By adopting the technical scheme provided by the embodiment of the invention, the DHCP binding table can be generated for a user with established connection with the DHCP server before DHCP Snooping is started, and the problem of flow loss of a part of users due to DHCP Snooping binding table deficiency of the part of users in a DHCP Snooping starting process can be solved.
Owner:HUAWEI TECH CO LTD
Automatic updating method for IP address of terminal and Ethernet access device
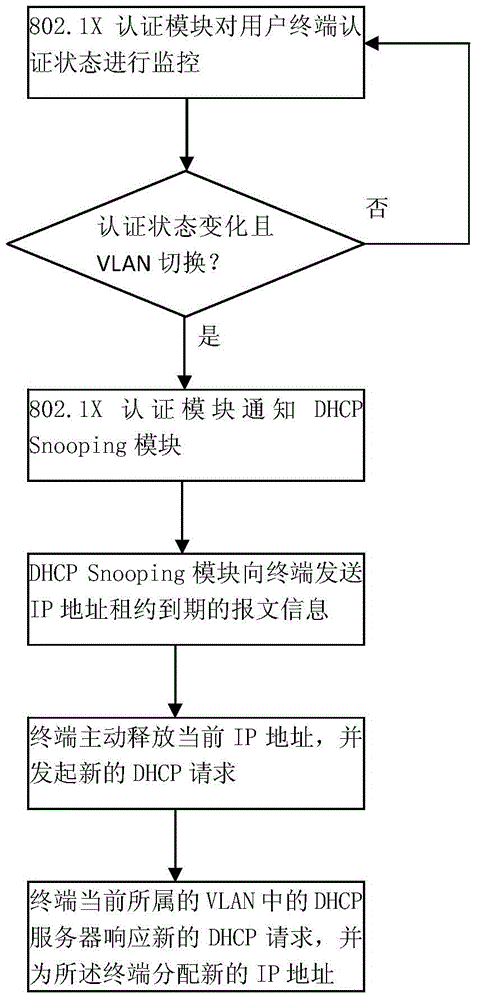
The invention belongs to the field of network communication, and aims at solving the problem that when a VLAN, to which a client belongs, changes, the client cannot update the IP address automatically and thereby cannot visit the network. According to an automatic updating method for the IP address of a terminal and an Ethernet access device provided by the invention, 802.1X is combined with DHCP Snooping, and a DHCP Snooping module is extended. The DHCP Snooping monitors the whole process of DHCP, and stores basic information of a DHCP server, a DHCP client and Translation ID and the like. When a 802.1X authentication module detects that the authentication state of the terminal changes and the VLAN to which the terminal belongs is switched, the DHCP Snooping module is informed, the DHCP Snooping simulates that the DHCP server sends a DHCP ACK message with lease of zero to the DHCP client according to the stored information, to allow the client to actively release the current IP address and initiating a new DHCP request. The automatic updating method is applicable to Ethernet switches.
Owner:MAIPU COMM TECH CO LTD
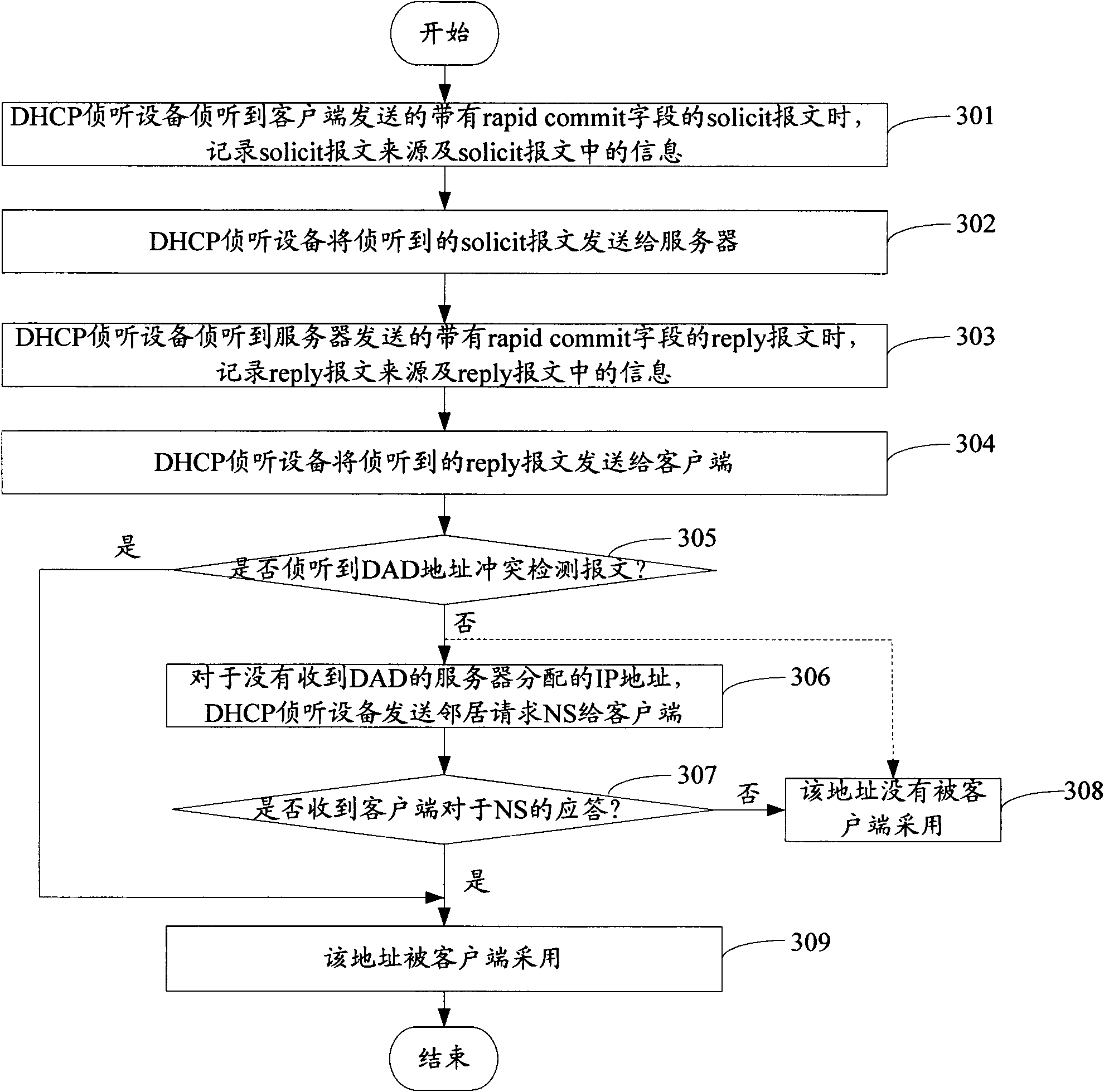
Method for rapidly acquiring IPv6 (Internet Protocol Version 6) address and DHCP (Dynamic Host Configuration Protocol) snooping equipment
The invention provides a method for rapidly acquiring an IPv6 (Internet Protocol Version 6) address. The method comprises the following steps that: DHCP (Dynamic Host Configuration Protocol) snooping equipment snoops a reply message which is with a field of rapid commit and transmitted by a server after transmitting a solicit message with a field of rapid commit to a server, and records the address of the server sending the reply message and an IP (Internet Protocol) address assigned for a client terminal; and for the IP address assigned for the client terminal, the DHCP snooping equipment determines that the IP address is not adopted by the client terminal and notifies the server to release the lease of the IP address when the DHCP equipment does not receive a DAD (Duplicate Address Detection) message transmitted by the client terminal. The invention simultaneously discloses the DHCP snooping equipment. By applying the method for rapidly acquiring the IPv6 address and the DHCP snooping equipment provided by the invention, the client terminal is ensured to rapidly acquire the address, and the address waster is also avoided.
Owner:NEW H3C TECH CO LTD
Extending sso for DHCP snooping to two box redundancy
InactiveUS7903647B2Multiplex system selection arrangementsSpecial service provision for substationAddress Resolution ProtocolIp address
Disclosed are mechanisms for facilitating the use of DHCP (dynamic host configuration protocol) binding data. In general, certain applications include mechanisms for intercepting data being sent from a node and then determining whether the data corresponds to a valid IP address and MAC address binding. Embodiments of the present invention provide mechanisms for sharing such DHCP binding data between routers (or other type of network devices) in a redundancy group so that any of the routers may take over the data inspection to validate DHCP bindings. In particular aspects of the invention, the DHCP binding data is validated in procedures related to DHCP snooping, dynamic ARP (address resolution protocol) inspection, and the like.
Owner:CISCO TECH INC
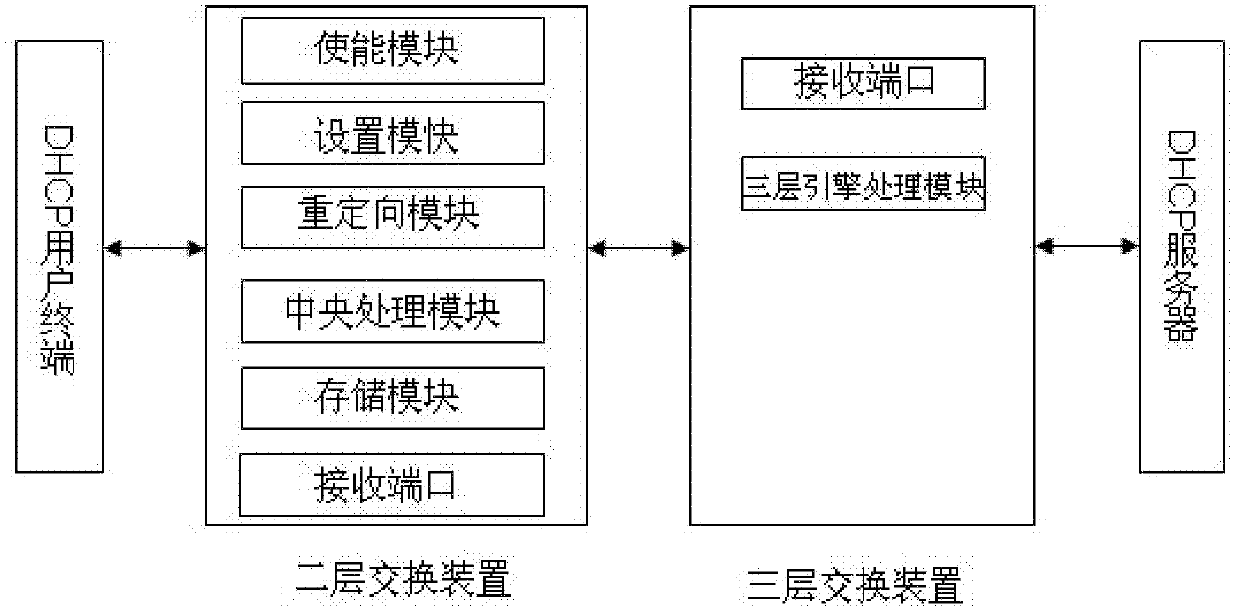
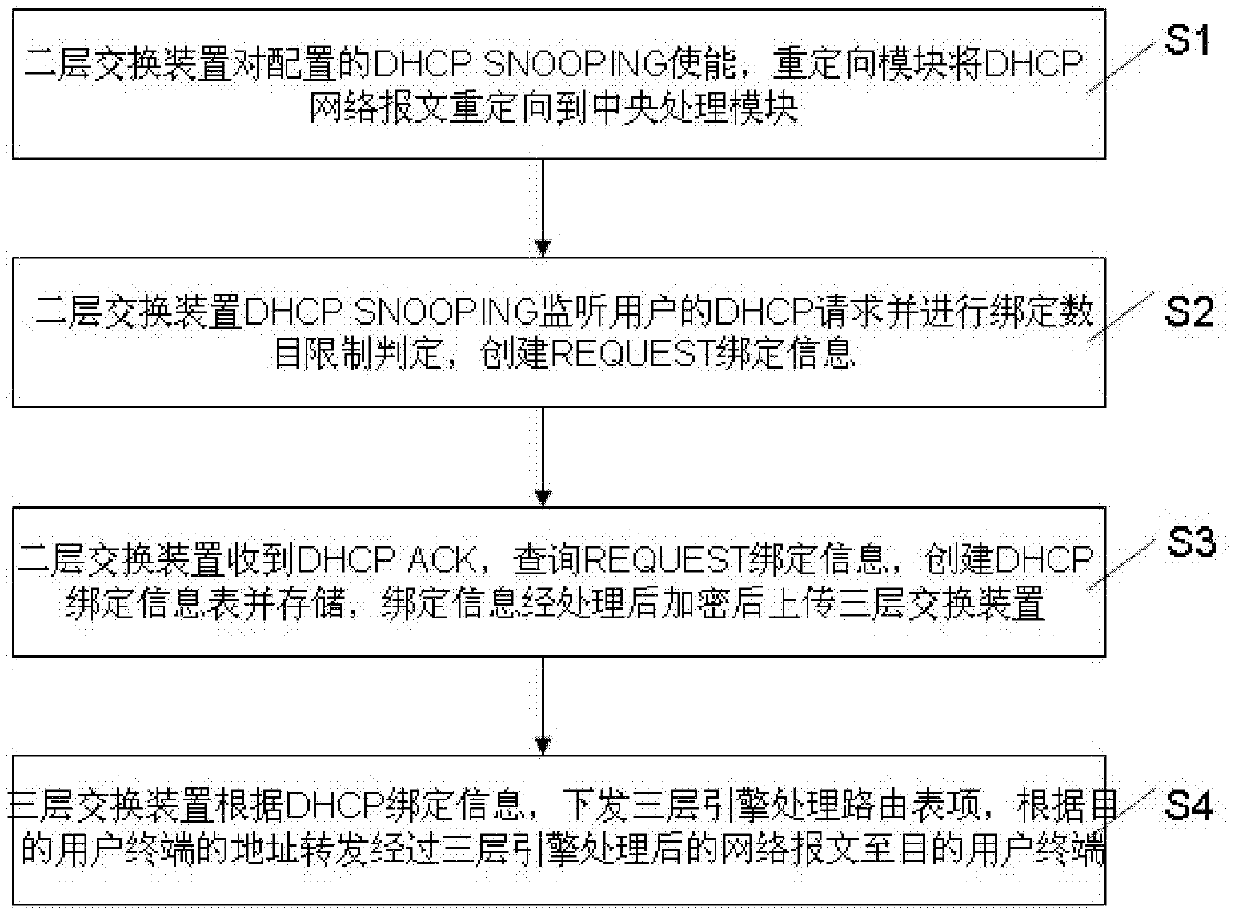
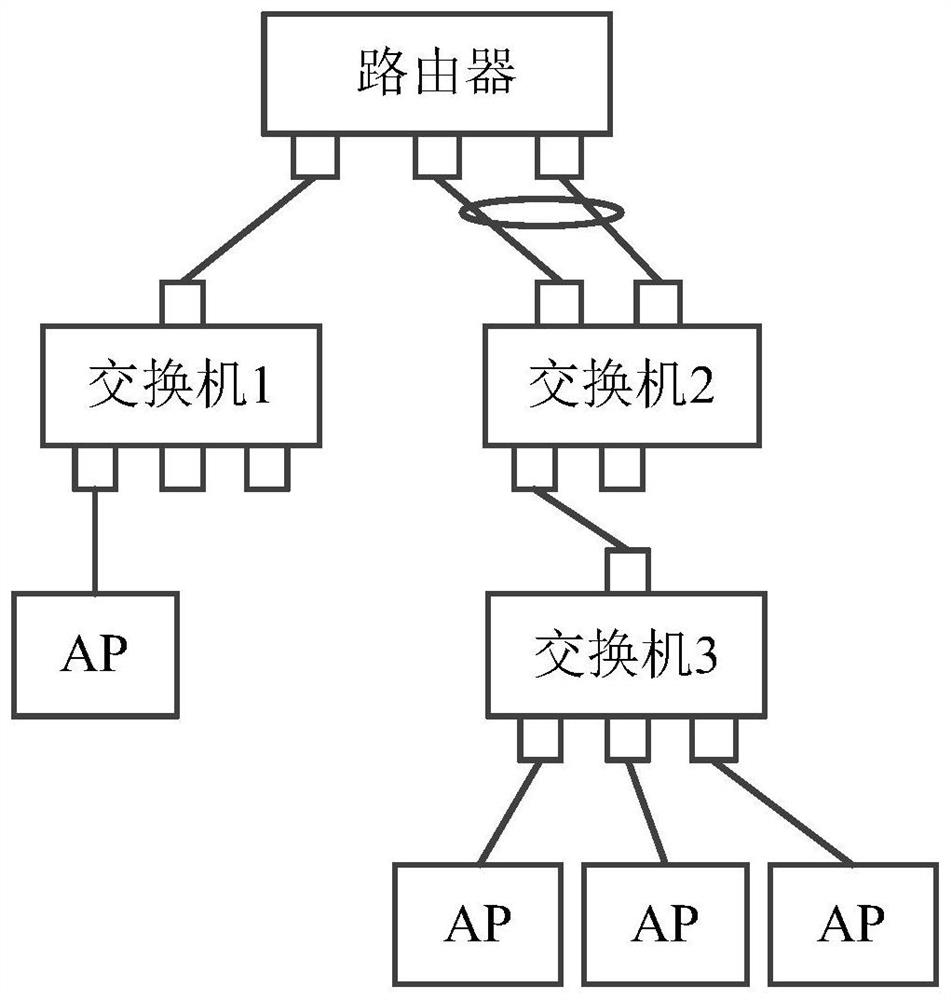
Layer-3 switching system and method based on layer-2 DHCP (Dynamic Host Configuration Protocol) SNOOPING
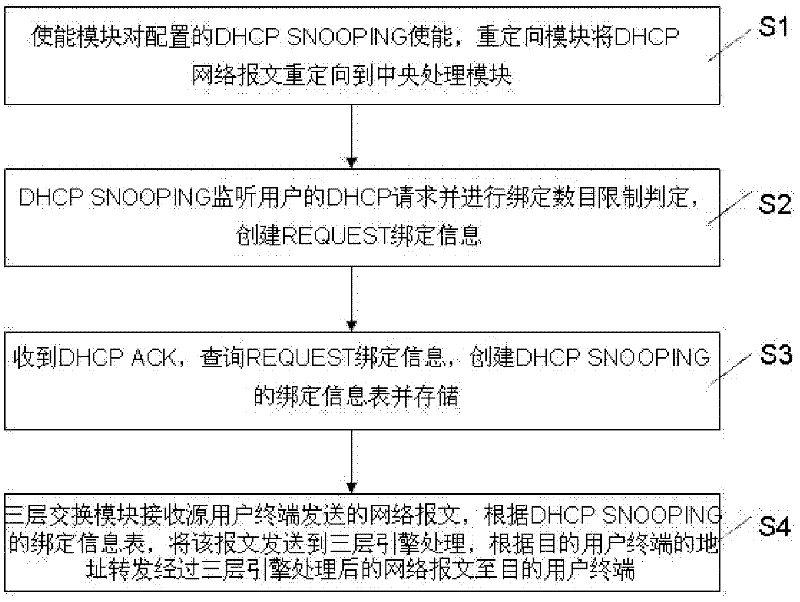
The invention discloses a layer-3 switching system and method based on layer-2 DHCP (Dynamic Host Configuration Protocol) SNOOPING. The system comprises a DHCP user terminal, a layer-2 switching device, a layer-3 switching device and a DHCP server. The system is characterized in that the layer-2 switching device comprises an enabling module for enabling the DHCP SNOOPING configured for the layer-2 switching device so as to monitor a DHCP requesting process of the user terminal, creating DHCP binding information and storing the created information; the layer-2 switching device processes and uploads the binding information to the layer-3 switching device, and the layer-3 switching device issues a layer-3 engine processing routing table entry according to the DHCP binding information and forwards a network message processed by a layer-3 engine to a target user terminal according to the address of the target user terminal. According to the technical scheme of the invention, approaches to learning for layer-3 table entries of a switch in DHCP environment are increased, and t he stability and safety of the table entries are effectively ensured.
Owner:武汉神州数码云科网络技术有限公司
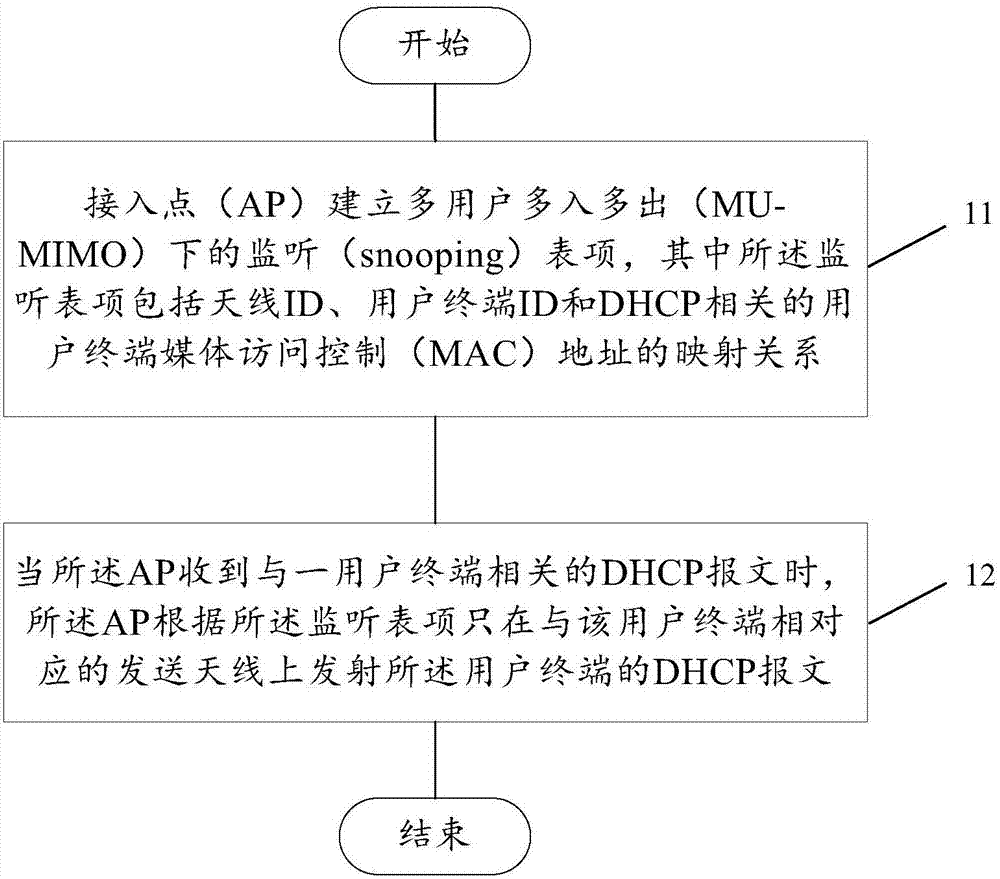
Sending method of DHCP report and device
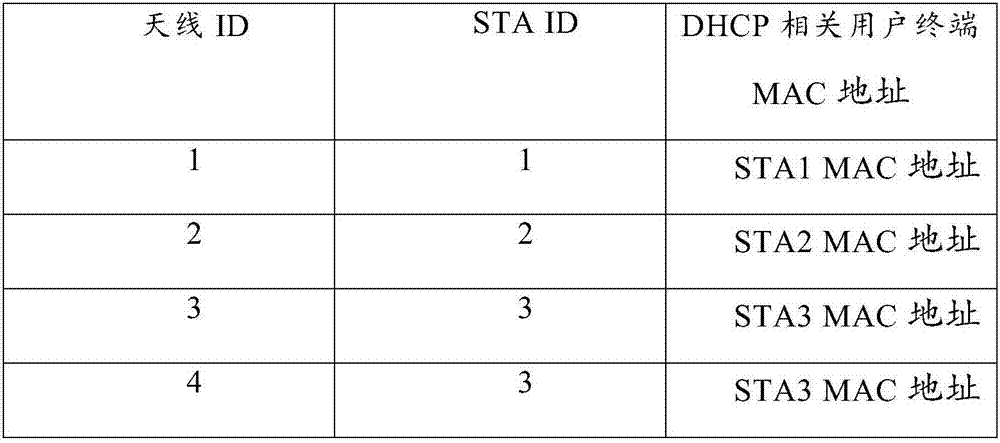
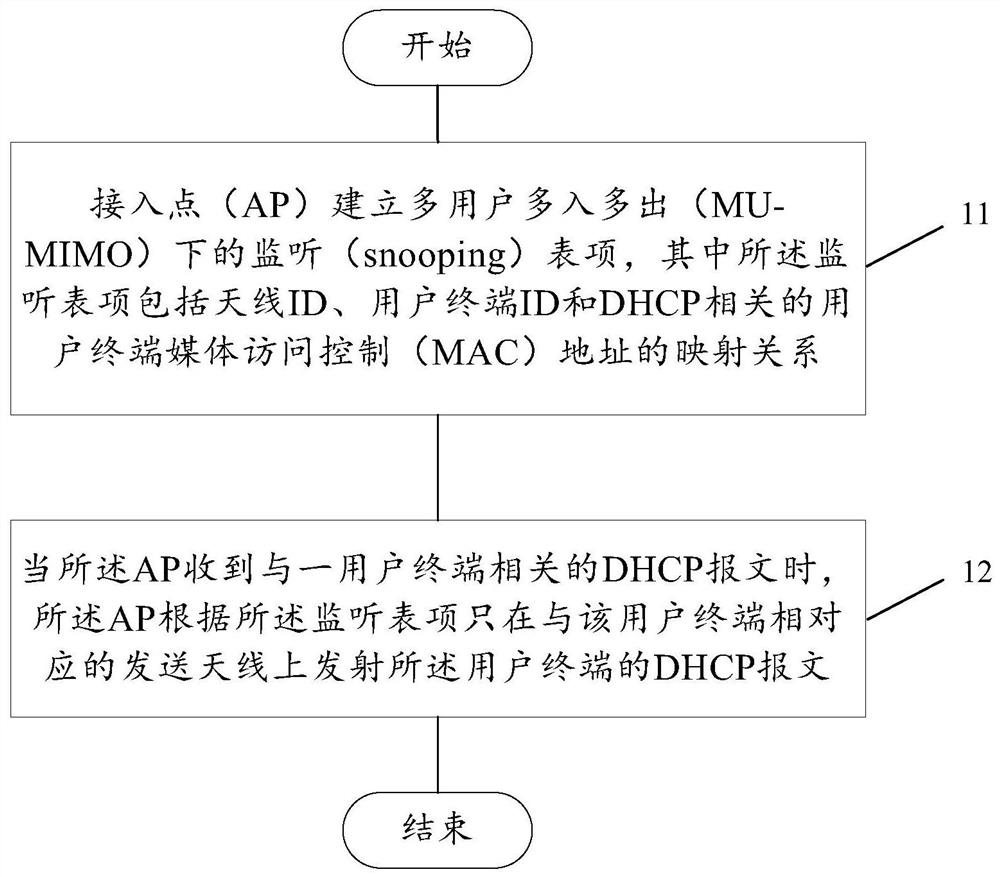
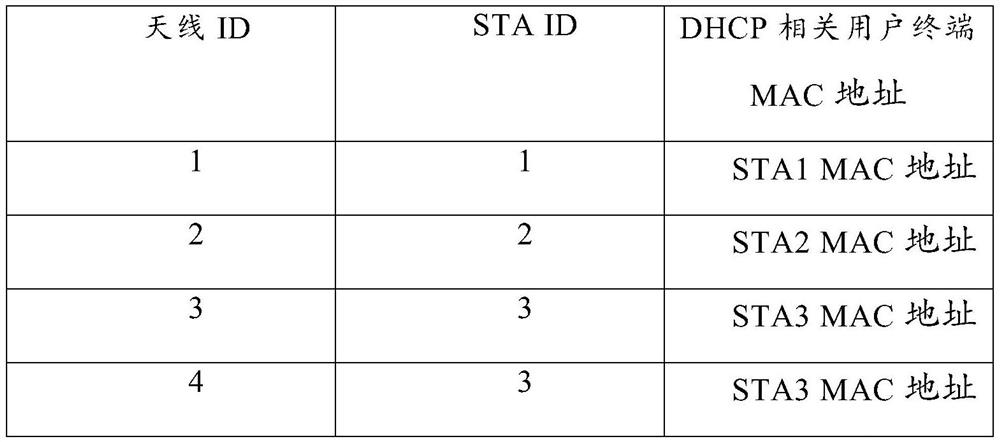
The embodiment of the invention discloses a sending method of a DHCP report and a device. An AP establishes a snooping table item under multiple users and multiple-input multiple output conditions, wherein the snooping table item comprises a mapping relation between an antenna ID, a user terminal ID and a user terminal MAC address related to the DHCP. When the AP receives a DHCP report related to a user terminal, the AP only emits the DHCP report on the antenna corresponding to the user terminal according to the snooping table item. According to the invention, 'snooping' of an access point where the DHCP snooping function is achieved to the antenna is achieved.
Owner:义乌市智享通讯设备有限公司
Method for generating dynamic host configuration protocol (DHCP) snooping binding information, and device thereof
InactiveCN101656722AInhibit migrationAvoid attackError prevention/detection by using return channelData switching networksComputer hardwareDHCP snooping
Owner:BEIJING XINWANG RUIJIE NETWORK TECH CO LTD
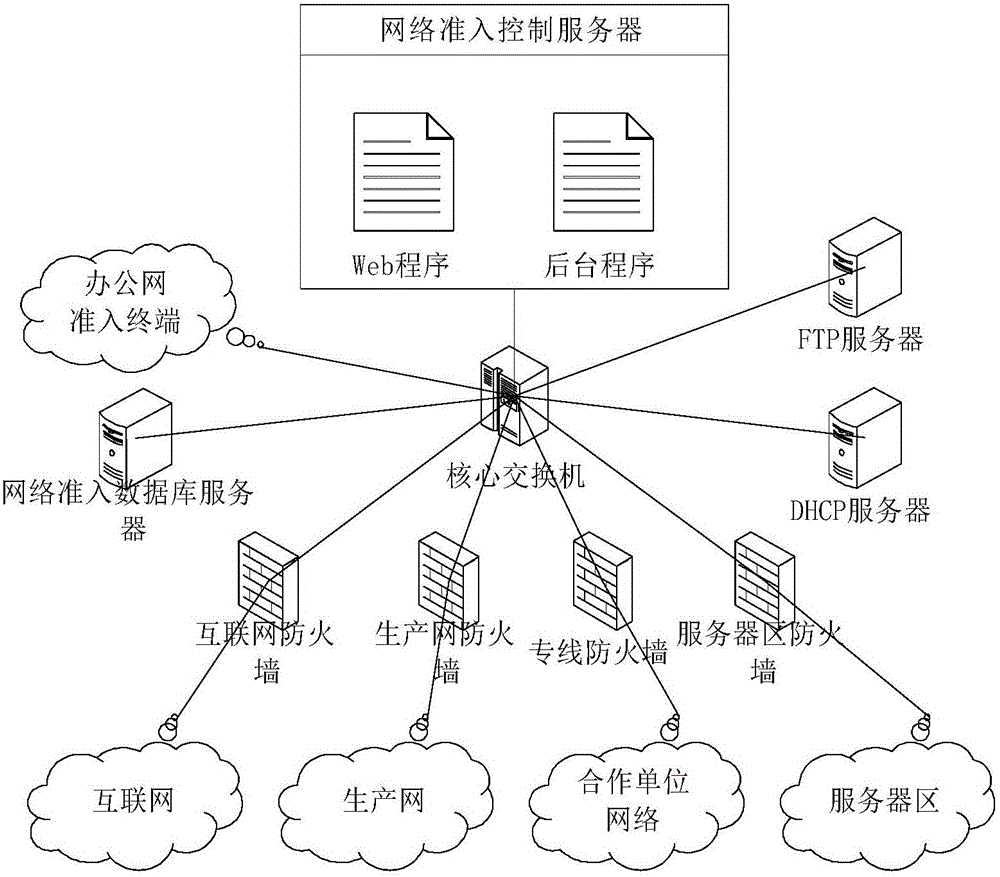
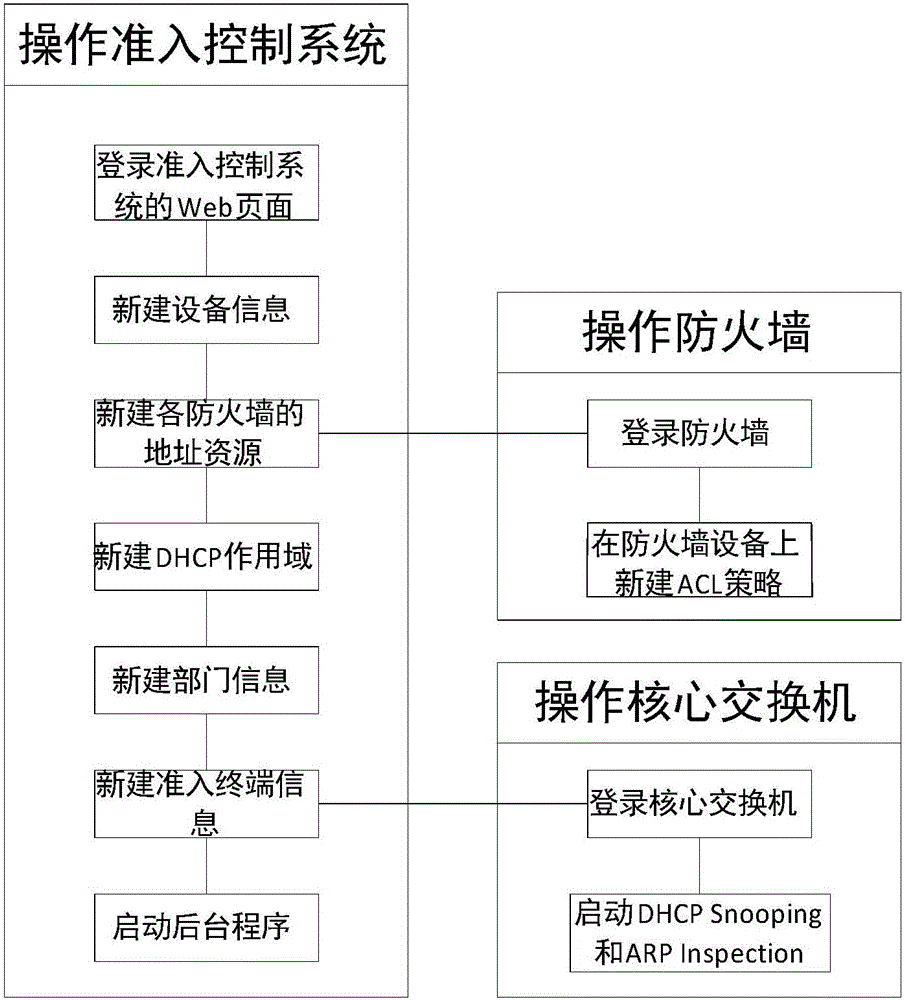
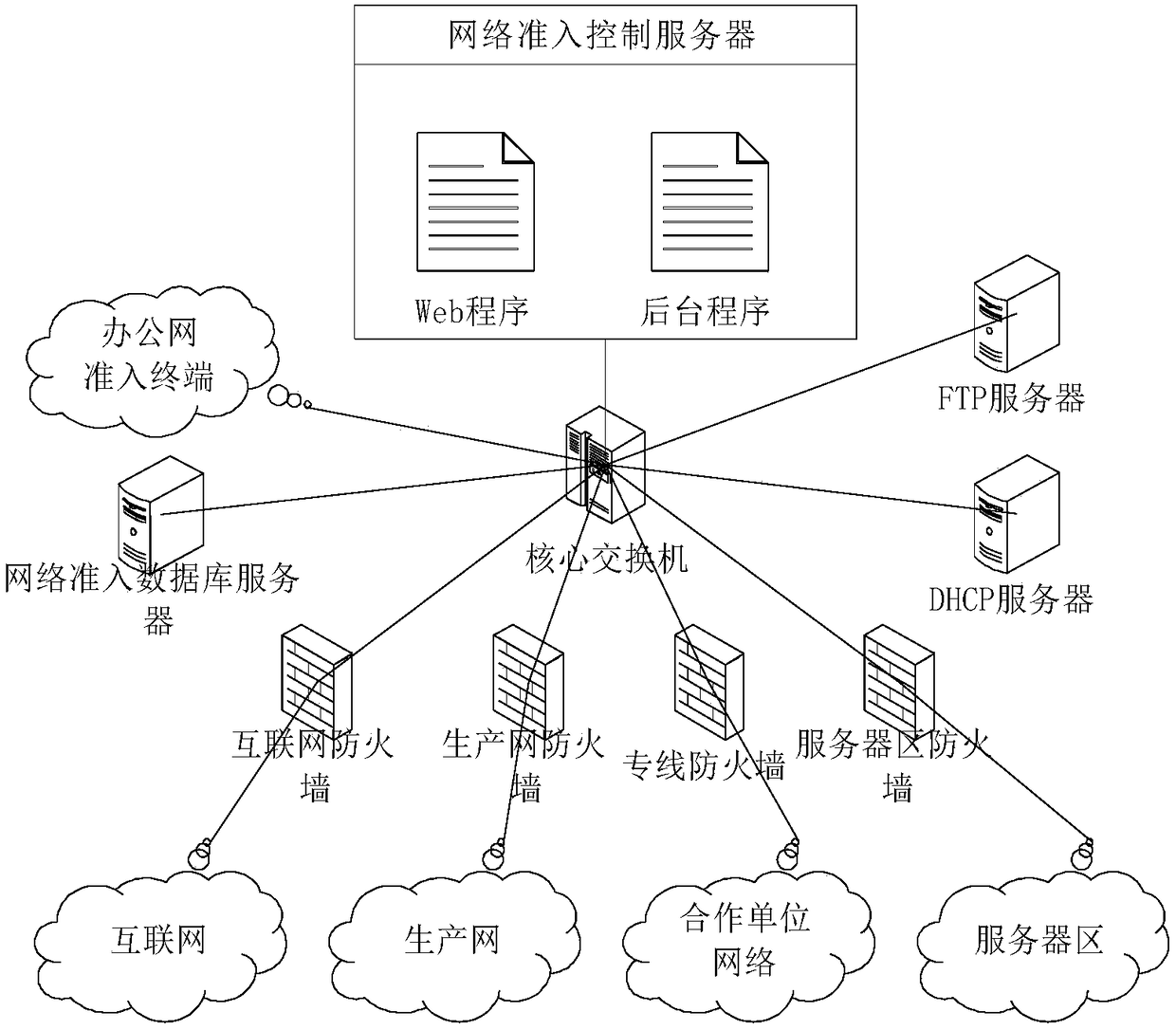
IP-MAC real-name binding based network access control system and control method
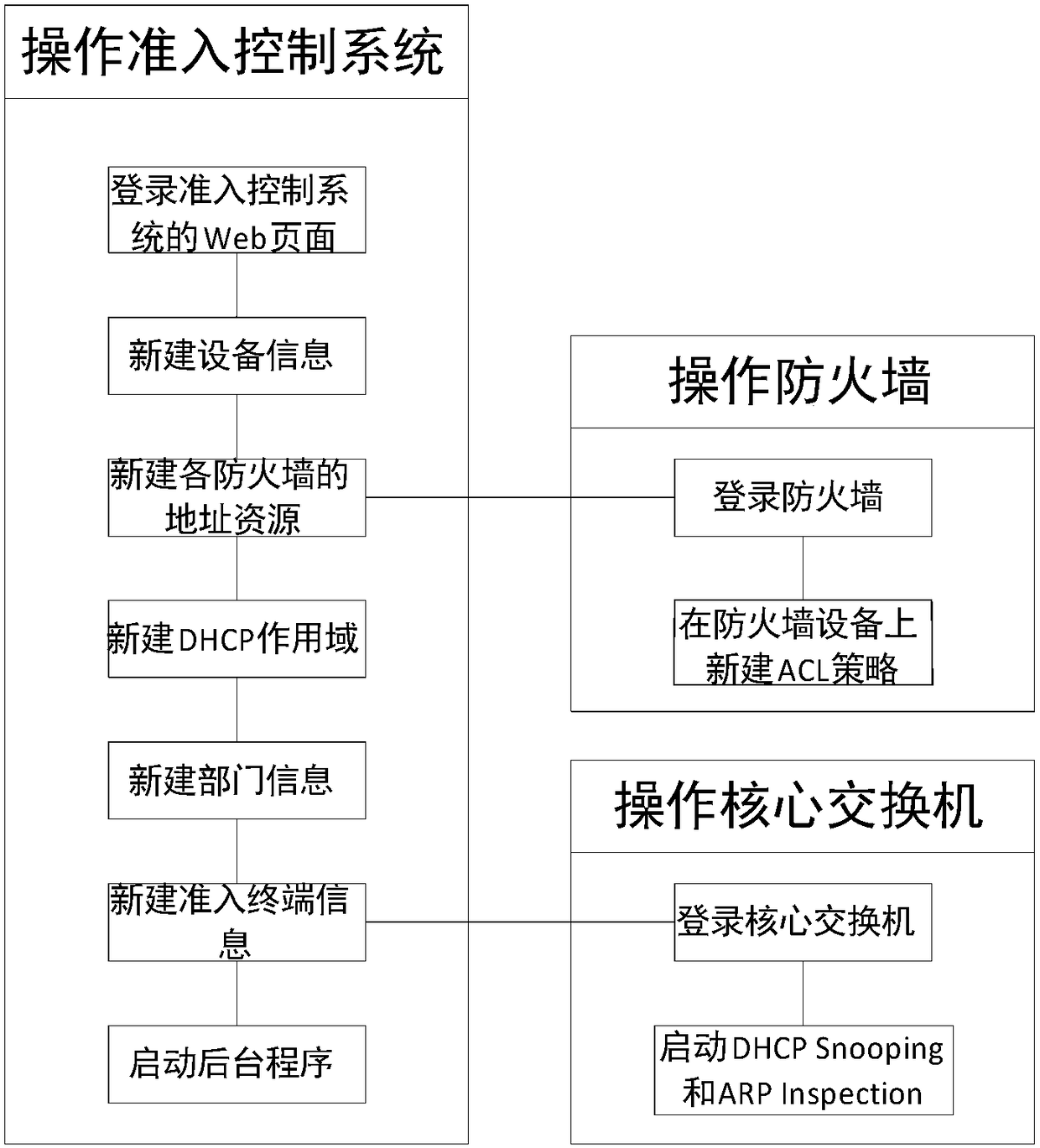
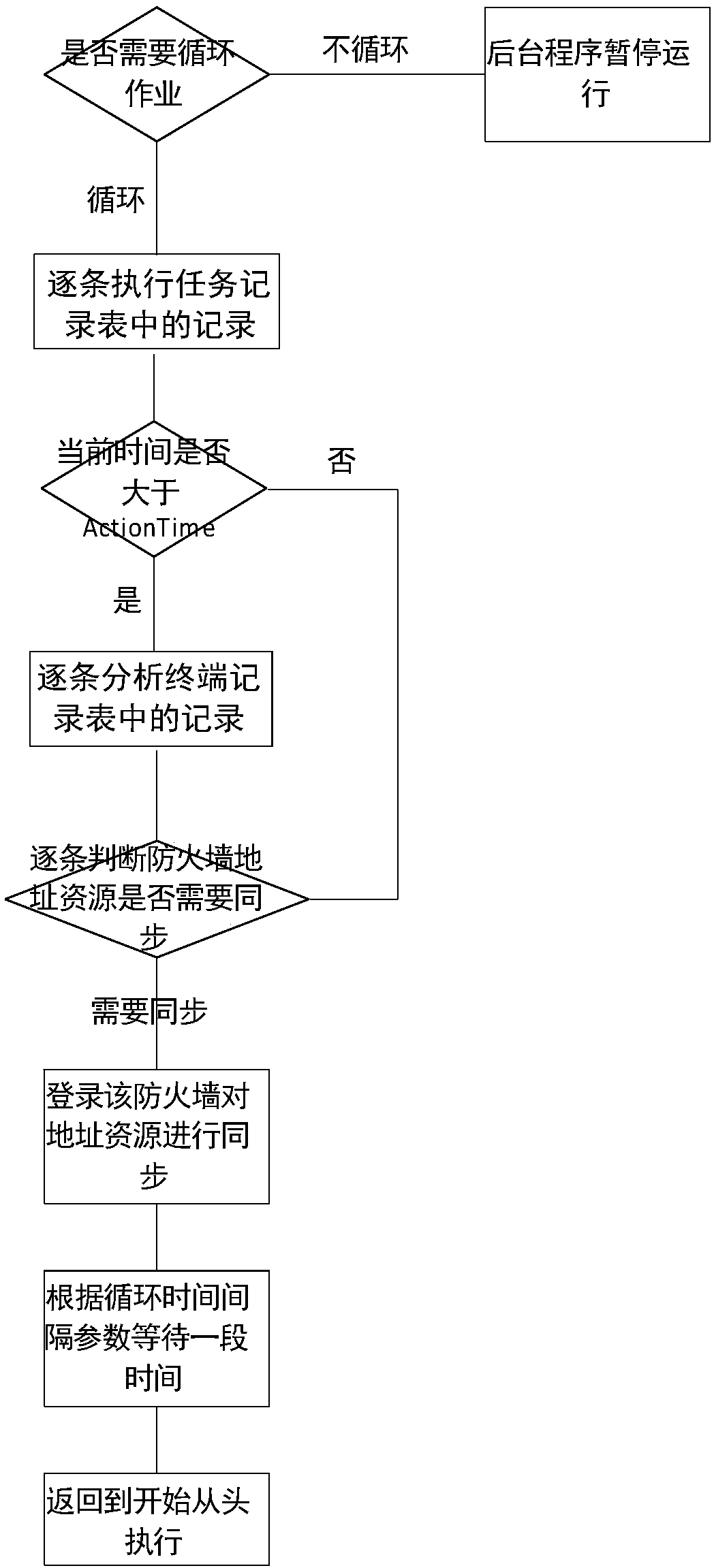
The invention relates to the technical field of local area network access technologies, in particular to an IP-MAC real-name binding based network access control system and control method. The system comprises a core switch, a DHCP server, an FTP server and an access terminal, wherein the core switch uses a DHCP Snooping function and an ARP Inspection function; and the system further comprises a network access database server, a network access control server, a production network firewall, a server area firewall, an internet firewall and a private firewall. According to the IP-MAC real-name binding based network access control system and control method, Web programs and background programs are built in the network access control server; parameter configuration can be performed on the system through the Web programs; meanwhile, parameters are performed by utilizing the background programs, IP-MAC real-name binding and access authority effective time control can be implemented. Furthermore, due to function configuration of the core switch, shielding on a counterfeit DHCP server and a manually configured IP address can be implemented, so that sequential management of an IP address is facilitated.
Owner:霍焕潇
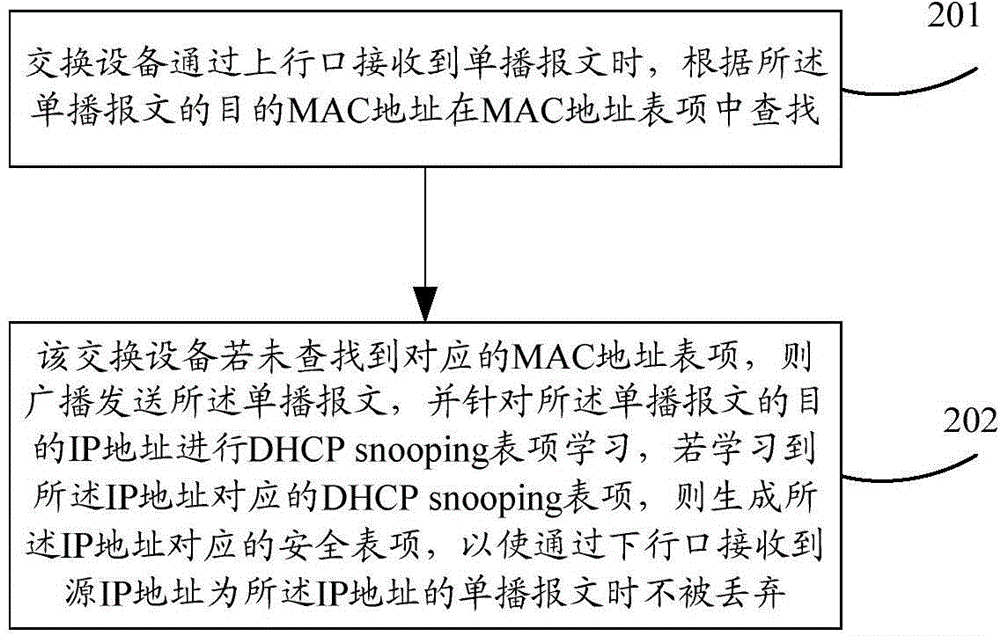
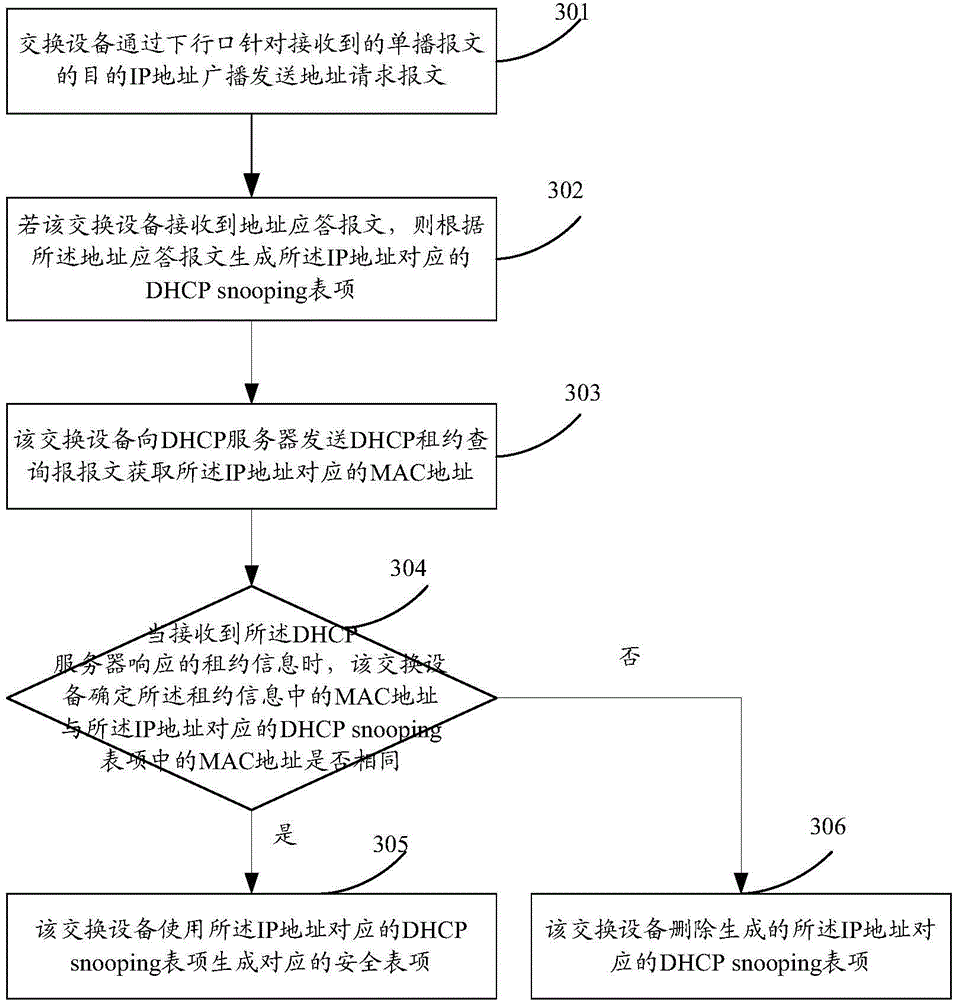
Generation method and device for security entries
The invention provides a generation method of security entries. The generation method comprises the following steps: when an unknown unicast message is received through an uplink port, switching equipment broadcasts the unicast message and learns a DHCP snooping entry specific to a destination IP address of the unicast message; if the DHCP snooping entry corresponding to the IP address is learnt, a security entry corresponding to the IP address is generated, so that the unicast message received through a downlink port is not abandoned, wherein a source IP address of the unicast message is the IP address. Based on the same inventive concept, the application further provides a generation device of security entries; the generation device can generate the security entry of a host as soon as possible according to a downstream, in order to avoid that a legal upstream is abandoned.
Owner:NEW H3C TECH CO LTD
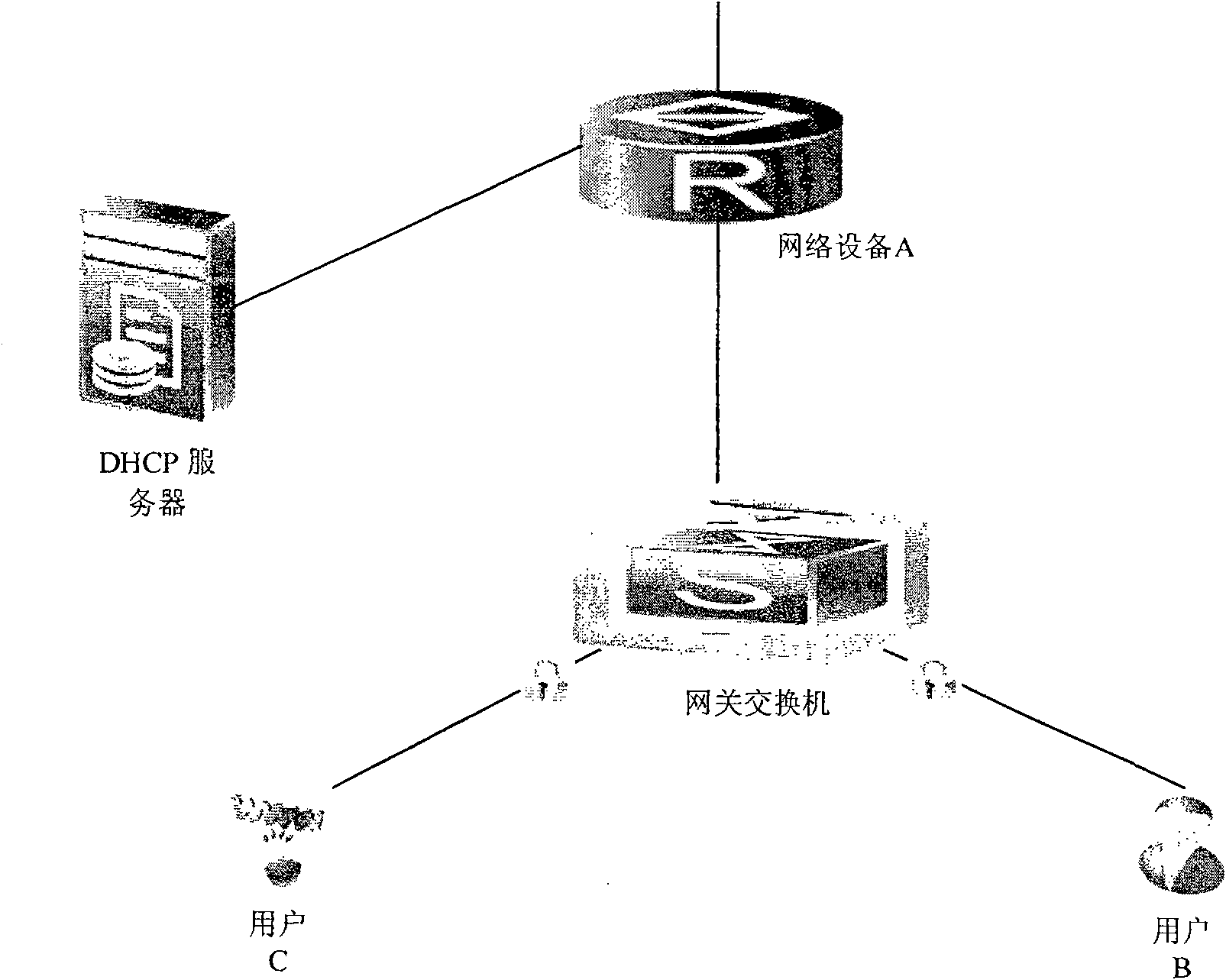
Method for preventing attack of untrusted servers
InactiveCN104009967APrevent spoofing attacksEffective forwardingTransmissionIp addressSpoofing attack
The invention provides a method for preventing attack of untrusted servers. The method comprises the following steps: a trusted server IP address list is added to switching equipment starting DHCP Snooping for a local area network performing DHCP Snooping; when the switching equipment receives a DHCP response packet, the source address of the DHCP response packet is extracted, and the source address is verified based on IP addresses in the trusted server IP address list; and through the verification, the switching equipment only forwards DHCP response packets of which the source addresses exist in the trusted server IP address list. The method of the invention can effectively prevent spoofing attack of untrusted servers. Compared with the prior art, spoofing attack from trusted ports when untrusted servers are in a non-direct connection state can be avoided. Further, when the port of a server is switched, configuration of the switching equipment does not need to be modified, and data packets of trusted servers can continue to be forwarded effectively, and spoofing attack of untrusted servers can continue to be prevented effectively.
Owner:PHICOMM (SHANGHAI) CO LTD
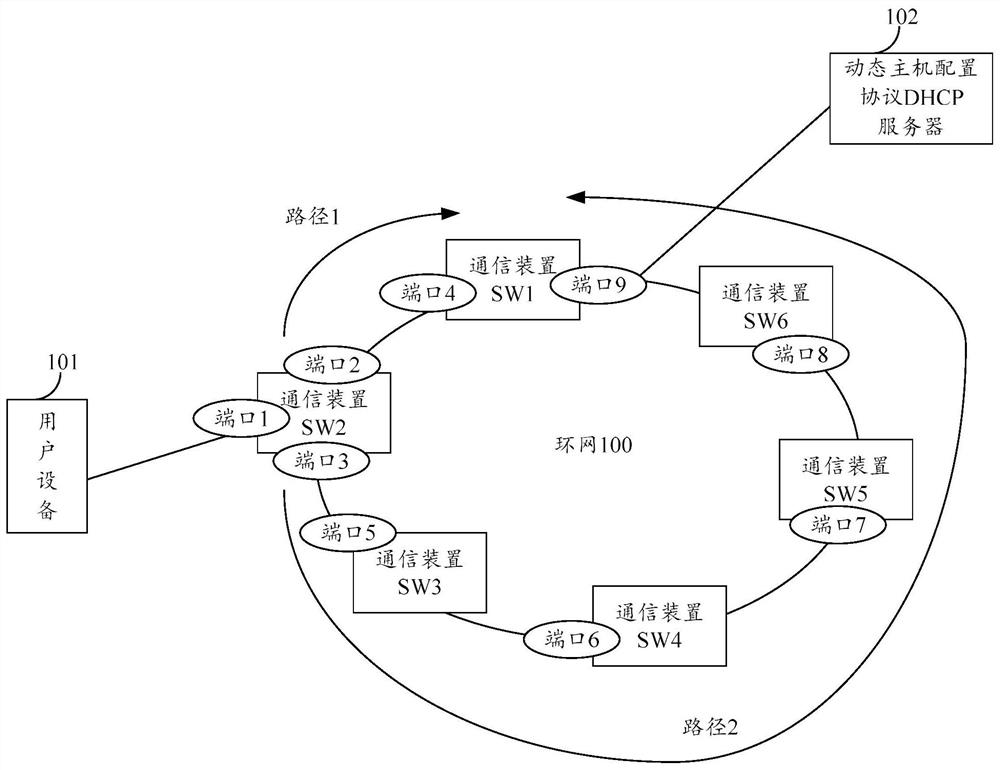
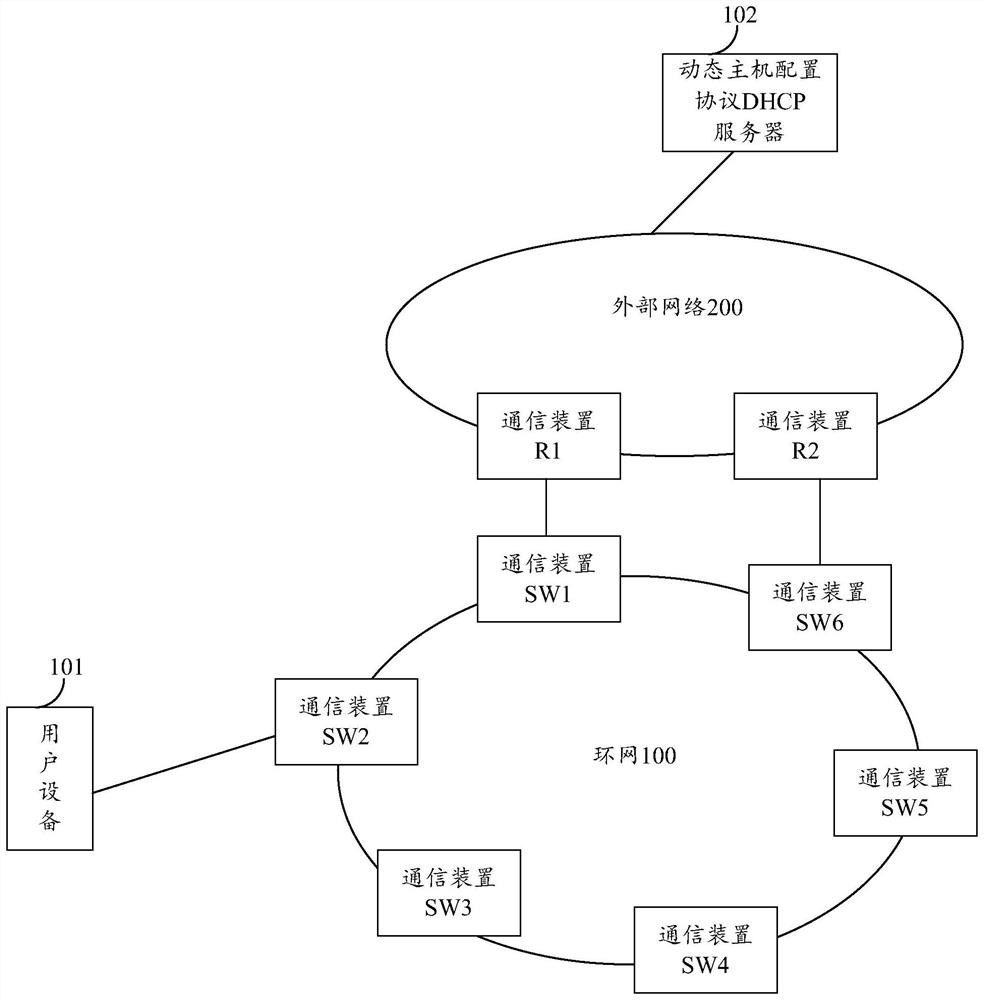
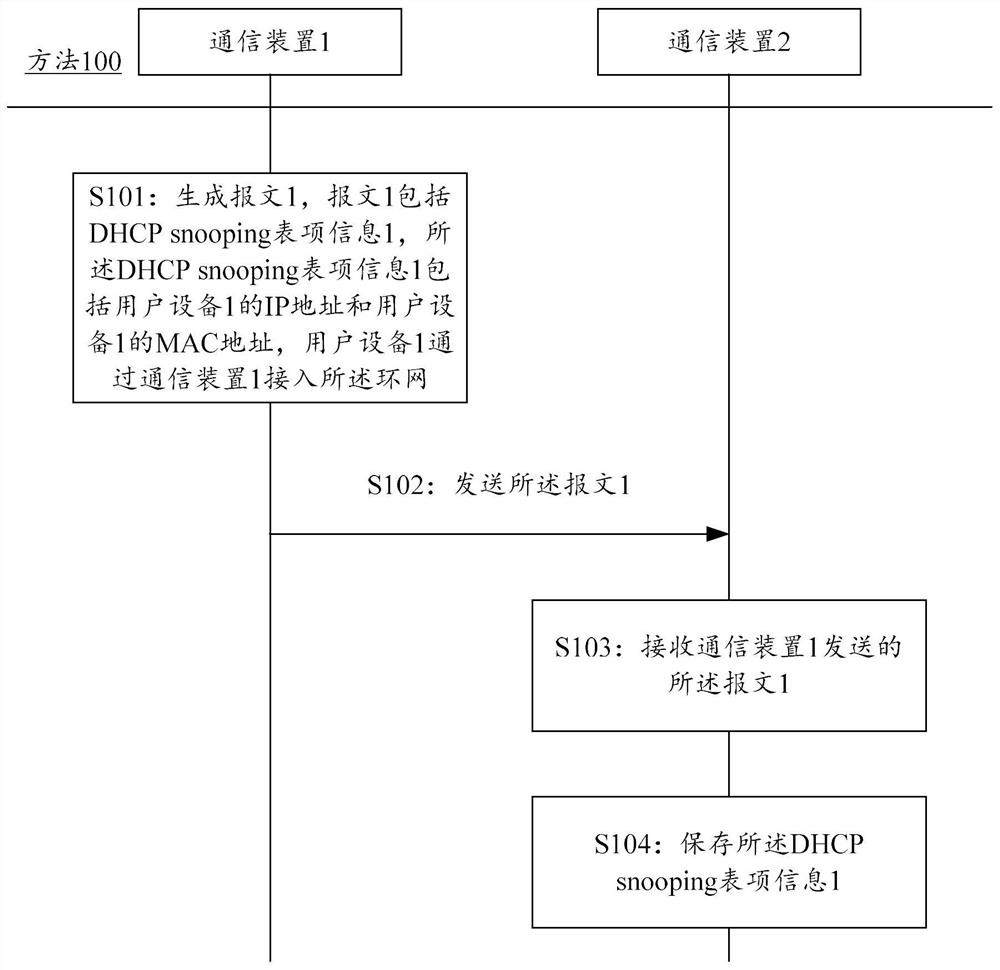
Table item information processing method and device
The invention provides a method for processing DHCP snooping table item information in a ring network. The method is executed by a first communication device on the ring network. In one example, a first communication device may acquire DHCP snooping entry information and synchronize the DHCP snooping entry information to a ring network or to other one or more nodes in communication with the ring network. The DHCP snooping table item information comprises a first internet protocol IP address of the first user equipment and a first MAC address of the first user equipment, wherein the first user equipment accesses the looped network through the first communication device. According to the scheme, after the message transmission path is changed, the node on the new path can perform DHCP snooping according to the obtained DHCP snooping table item information, so that network attacks can be effectively prevented while a legal user can access a network.
Owner:HUAWEI TECH CO LTD
Terminal connection status management with network authentication
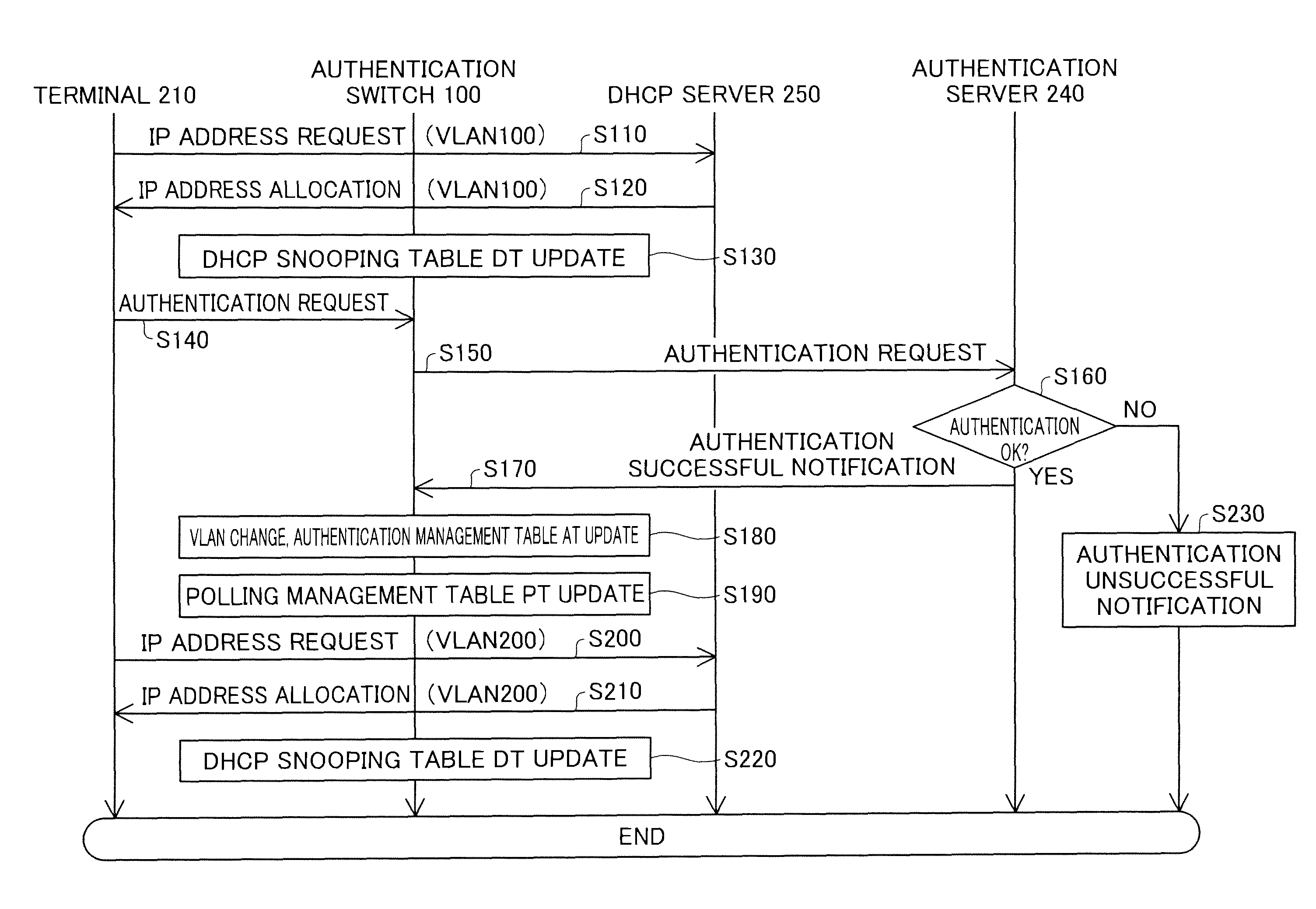
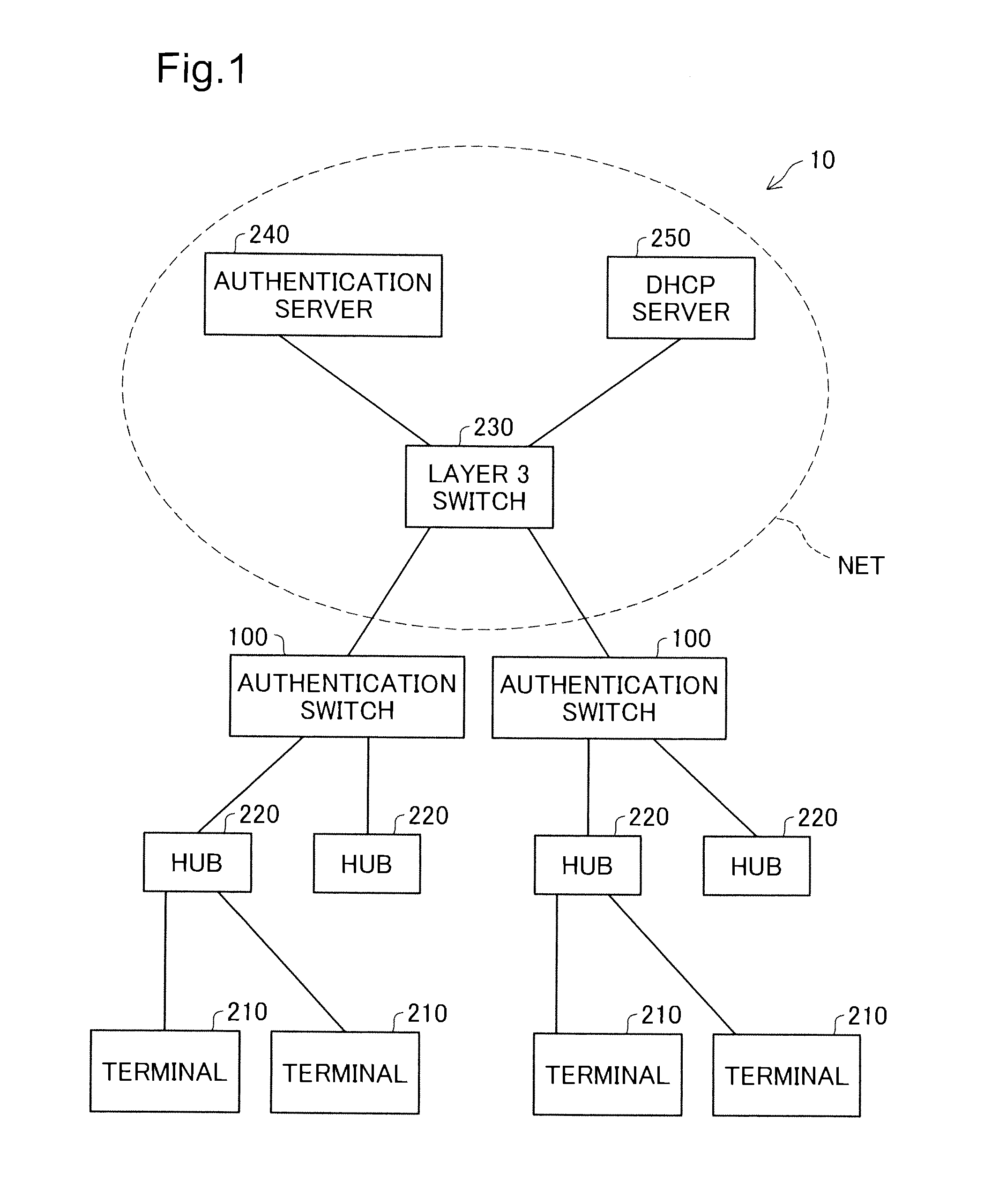
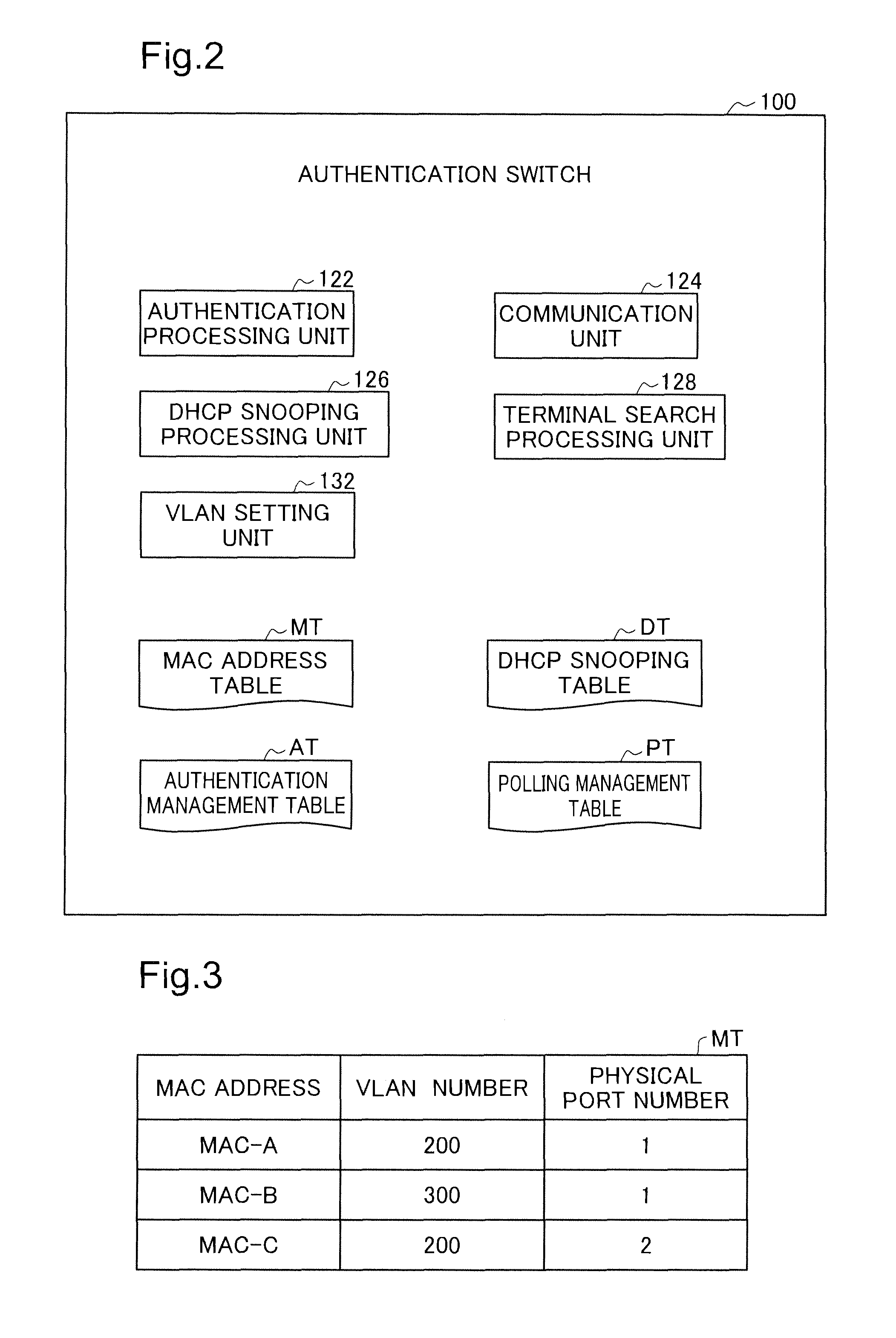
ActiveUS8910248B2Improve securityMemory loss protectionDigital data processing detailsComputer hardwareWeb authentication
A network relay device includes a communication unit, an authentication processing unit, a DHCP snooping processing unit, and a terminal search processing unit. The authentication processing unit creates first information specifying an authenticated terminal device according to web authentication, and manages whether relay of communication data between a terminal device and a node on the specified network is permissible based on the first information. The DHCP snooping processing unit executes snooping of DHCP communication data between a terminal device and a DHCP server, and creates second information specifying a layer 3 address allocated to each terminal device. The terminal search processing unit specifies an authenticated terminal device based on the first information, specifies a layer 3 address allocated to the specified authenticated terminal device based on the second information, and causes the communication unit to send, to the specified layer 3 address, confirmation communication data.
Owner:ALAXALA NETWORKS
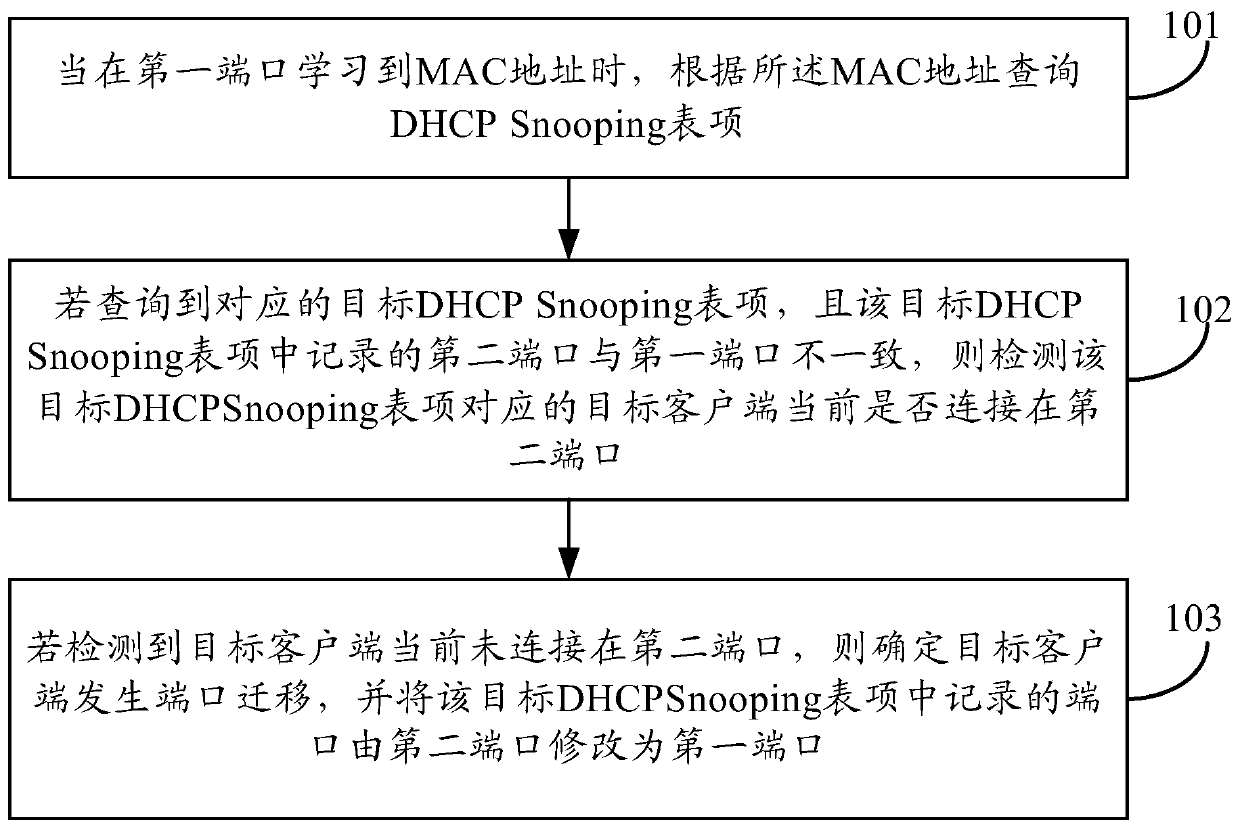
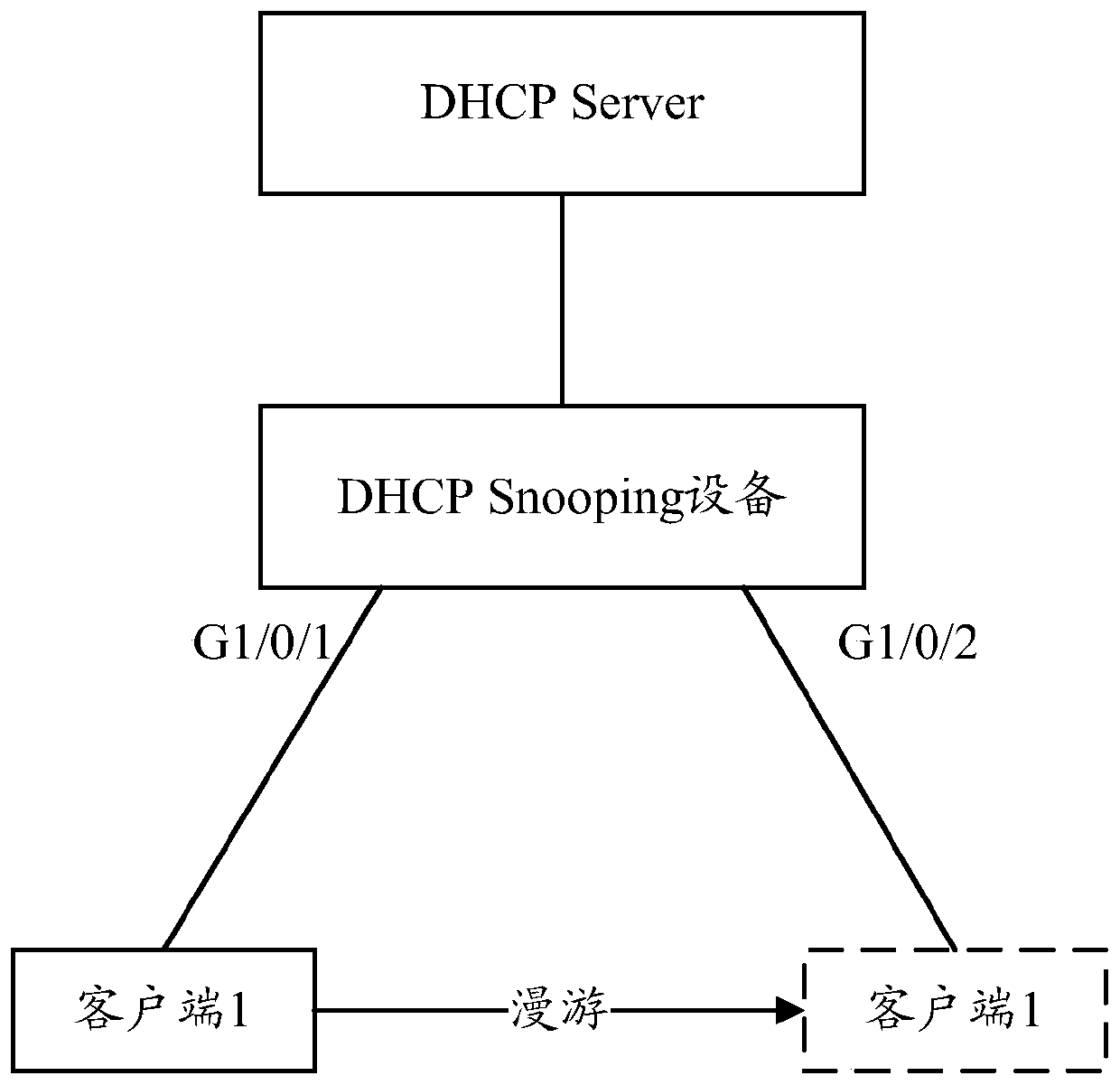
A method and device for supporting port migration detection
The present invention provides a method and device for supporting port migration detection. The method includes: when a MAC address is learned on a first port, querying a Dynamic Host Configuration Protocol (DHCP) Snooping entry according to the MAC address; If the corresponding target DHCP Snooping entry is found, and the second port recorded in the target DHCP Snooping entry is inconsistent with the first port, then detect whether the target client corresponding to the target DHCP Snooping entry is currently connected At the second port; if it is detected that the target client is not currently connected to the second port, it is determined that port migration occurs in the target client, and the port recorded in the target DHCP Snooping entry is replaced by The second port is changed to the first port. The application of the embodiment of the present invention can ensure that the port migration can be carried out normally when the DHCP Snooping security mechanism is applied.
Owner:NEW H3C TECH CO LTD
Method and device for sending dhcp message
The embodiment of the present invention discloses a method and device for sending a DHCP message. The AP establishes a multi-user multi-input multi-output monitoring table item, wherein the monitoring table item includes an antenna ID, a user terminal ID, and a DHCP-related user terminal MAC. Address mapping relationship: when the AP receives a DHCP message related to a user terminal, the AP only transmits the DHCP message on the antenna corresponding to the user terminal according to the listening entry. Through the method and device of the embodiment of the present invention, the access point realizing the DHCP snooping function can "snooping" (listen) to the antenna.
Owner:义乌市智享通讯设备有限公司
DHCP (dynamic host configuration protocol) SNOOPING based three-layer switching device and DHCP SNOOPING based three-layer switching method
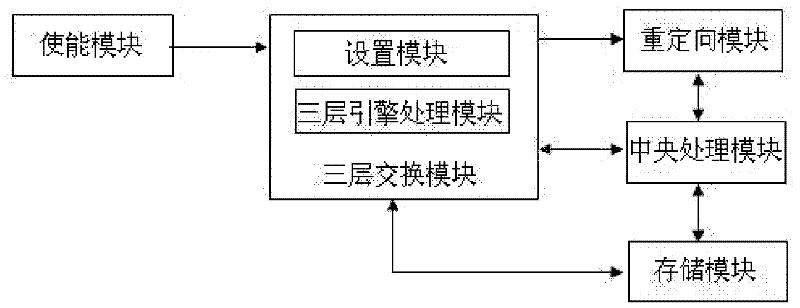
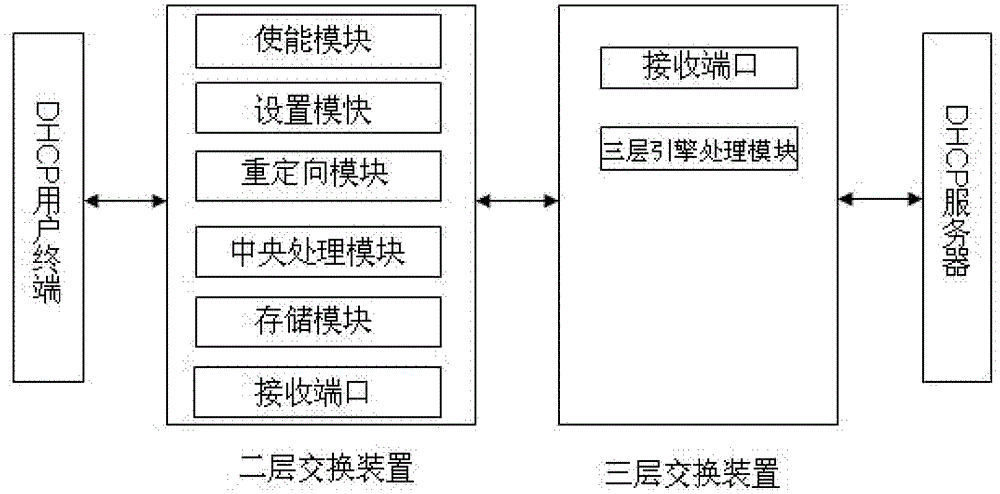
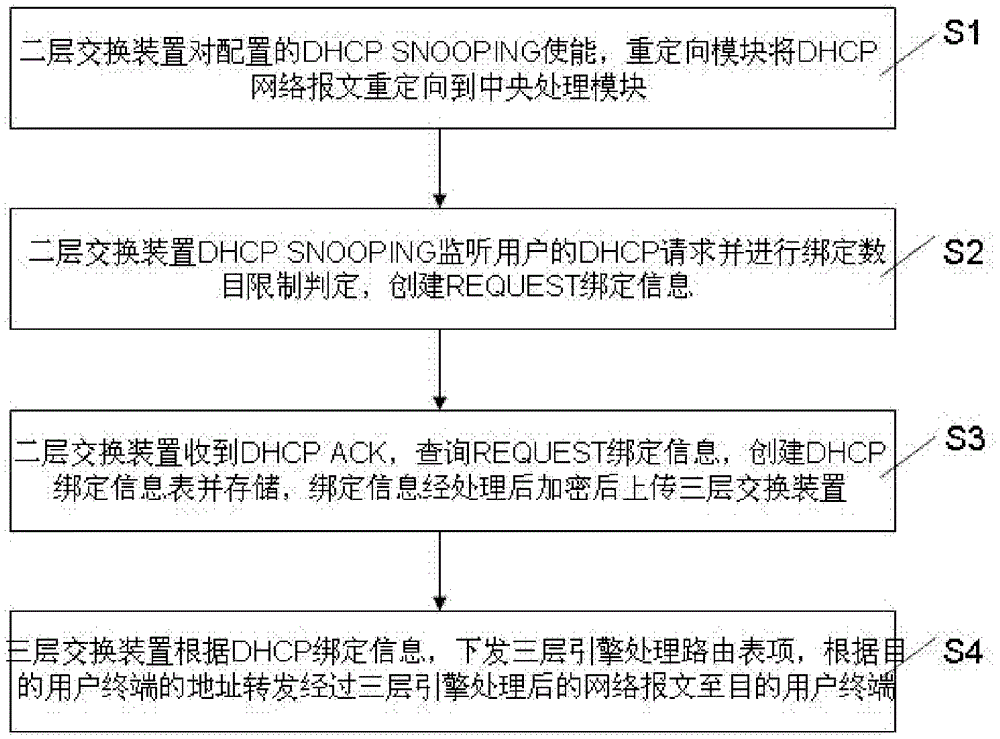
InactiveCN102638390ARealize forwardingIncrease the learning pathNetworks interconnectionVirtual LANComputer terminal
The invention discloses a DHCP (dynamic host configuration protocol) SNOOPING based three-layer switching device and a DHCP SNOOPING based three-layer switching method. The device connected with a plurality of virtual local area networks comprises an enable module, a redirecting module, a central processing module, a storage module and a three-layer switching module, wherein the enable module is used for enabling configured DHCP SNOOPING, the redirecting module is used for redirecting network message requests transmitted to a source user terminal to the central processing module, the central processing module is used for judging legality of received network messages, processing the messages and creating a DHCP binding information table, the storage module is used for storing the DHCP binding information table, and the three-layer switching module is used for receiving the network messages transmitted by the source user, transmitting the messages to three-layer engines to process according to the DHCP binding information table, and forwarding the network messages subjected to three-layer engine processing to a target user terminal according to an target user terminal address. By means of the technical scheme, learning approaches of three-layer table entries of a switchboard in the DHCP environment are added, and stability and safety of the table entries are effectively guaranteed.
Owner:北京神州数码云科信息技术有限公司
Network access control system and control method based on ip-mac real-name binding
The invention relates to the technical field of local area network access technologies, in particular to an IP-MAC real-name binding based network access control system and control method. The system comprises a core switch, a DHCP server, an FTP server and an access terminal, wherein the core switch uses a DHCP Snooping function and an ARP Inspection function; and the system further comprises a network access database server, a network access control server, a production network firewall, a server area firewall, an internet firewall and a private firewall. According to the IP-MAC real-name binding based network access control system and control method, Web programs and background programs are built in the network access control server; parameter configuration can be performed on the system through the Web programs; meanwhile, parameters are performed by utilizing the background programs, IP-MAC real-name binding and access authority effective time control can be implemented. Furthermore, due to function configuration of the core switch, shielding on a counterfeit DHCP server and a manually configured IP address can be implemented, so that sequential management of an IP address is facilitated.
Owner:霍焕潇
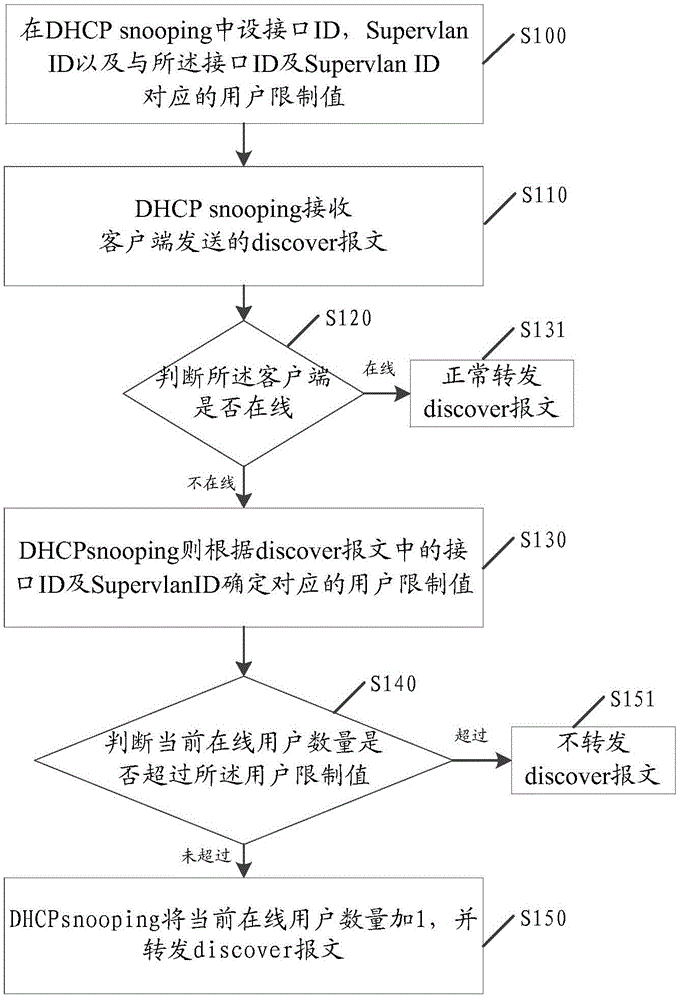
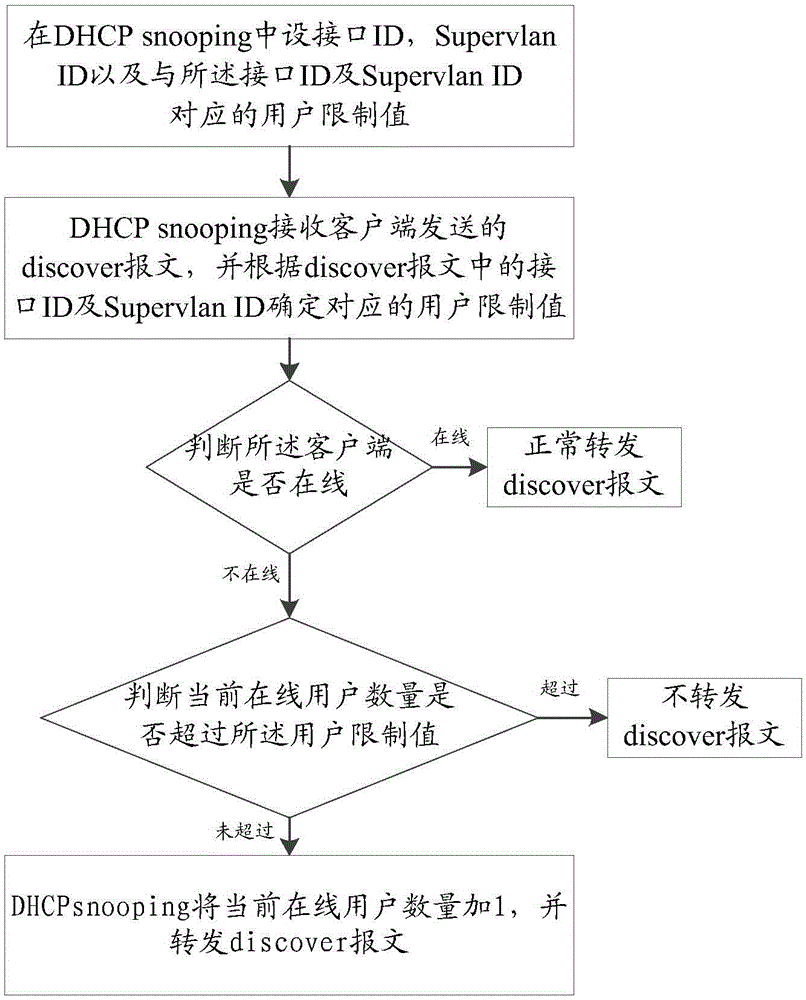
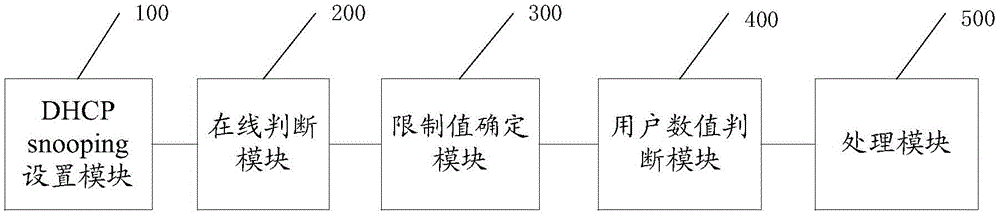
Method, device and system for preventing DHCP (Dynamic Host Configuration Protocol) attacks in flat network
The invention discloses a method, a device and a system for preventing DHCP (Dynamic Host Configuration Protocol) attacks in a flat network. The method comprises the following steps: setting an interface ID, a Supervlan ID and a corresponding user limit value in DHCP snooping; receiving a discover message sent by a client through the DHCP snooping, and judging whether the client is online or not; if the client is not online, determining the corresponding user limit value according to the interface ID and the Supervlan ID in the discover message; judging whether a quantity of current online users exceeds the user limit value or not; if so, not forwarding the discover message; and otherwise, adding the quantity of the current online users with 1, and forwarding the discover message. Through adoption of the method, the device and the system, address exhausting caused by the DHCP attacks can be prevented; the network security is enhanced; and the availability and user experience of a whole scheme are improved.
Owner:HUNAN KEAYSHARE COMM TECH CO LTD
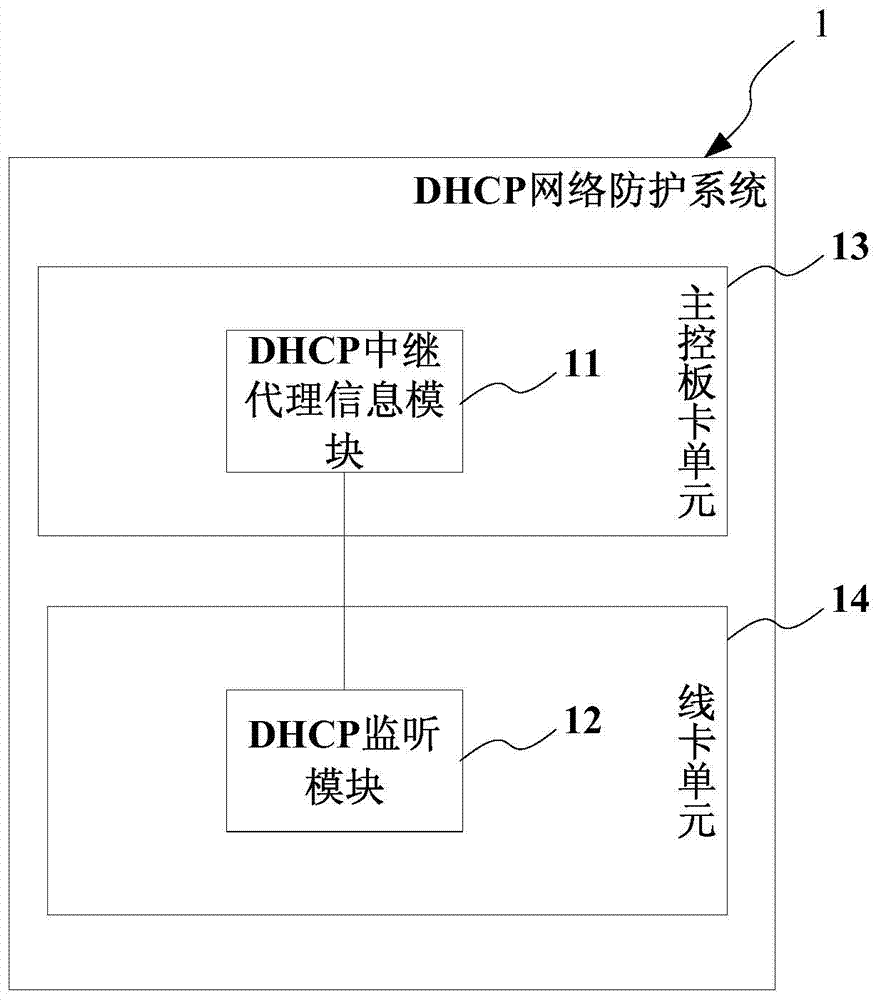
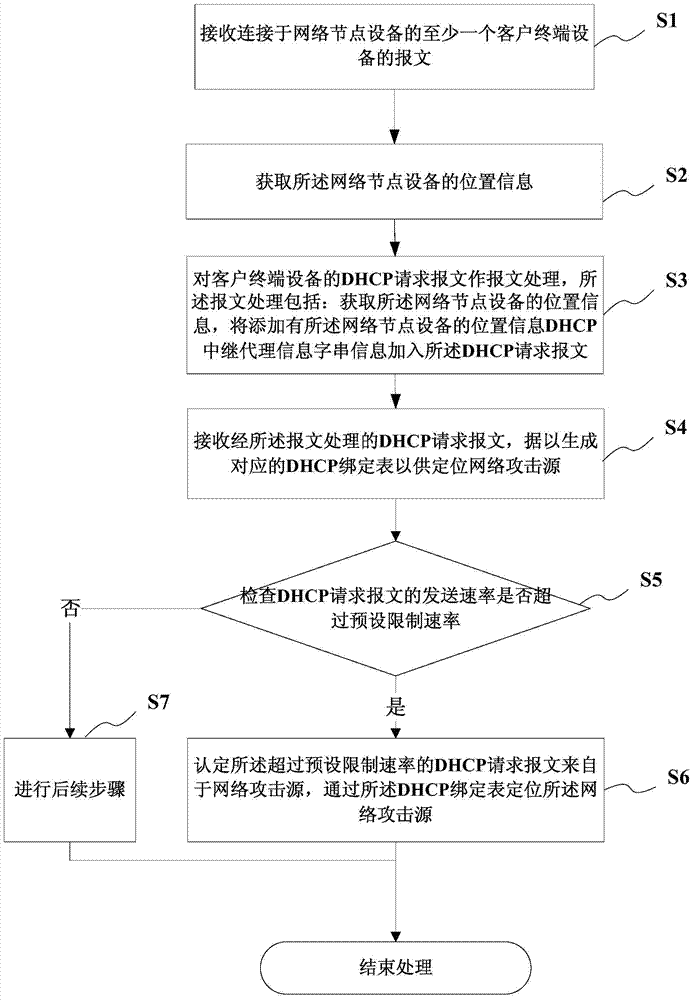
A kind of dhcp network protection system and method
The present invention provides a DHCP network protection system and method. The DHCP relay agent information module performs message processing on the DHCP request message of the client terminal equipment, so as to add the location information of the connection intermediate network node equipment to the DHCP relay agent. In the proxy information string information, the DHCP monitoring module receives the DHCP request message added with the DHCP relay agent information string information to generate a corresponding DHCP binding table for locating the network attack source, and the DHCP monitoring module also presets the rate Restriction, can accurately determine and locate the source of network attacks, improve the accuracy and efficiency of DHCP network security protection, and the DHCP relay agent information module and DHCP monitoring module are separated and run on different boards, reducing the number of modules running on the same board. This reduces the pressure of processing a large number of packets, and makes the upstream DHCP request packet carry more information to identify the source of the request packet.
Owner:广东网安科技有限公司
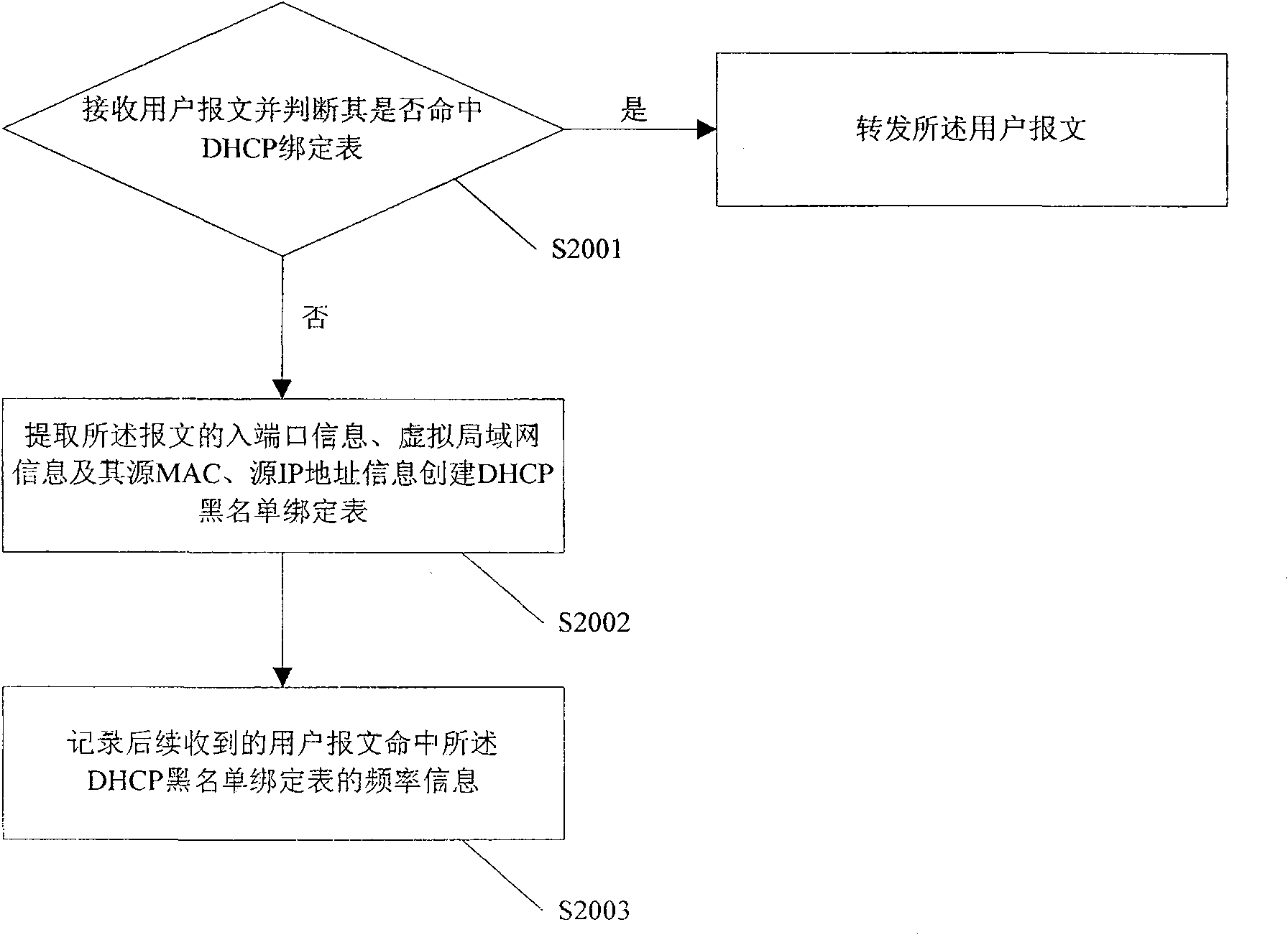
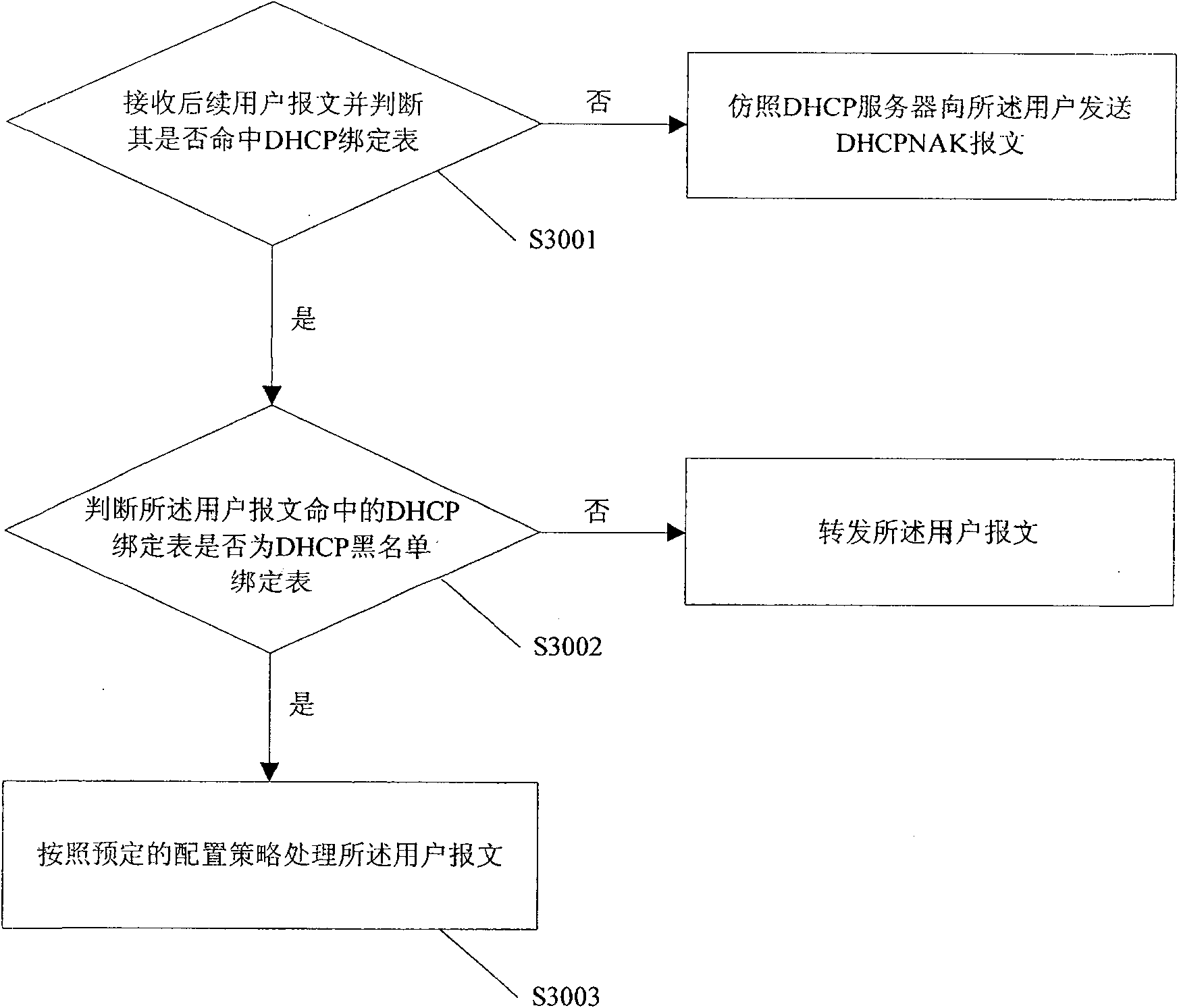
DHCP monitoring method and apparatus thereof
InactiveCN100563149CObtain attack behavior informationEasy to analyzeData switching networksSecuring communicationNetwork managementBlack list
The invention discloses a DHCP monitoring method. When the received user message fails to hit the DHCP binding table, a DHCP blacklist binding table is established, and the frequency information of the DHCP blacklist binding table being hit is recorded, so as to achieve tracking attacker's purpose. The invention also discloses a DHCP monitoring device. Through the invention, the attacker's attack behavior can be tracked and necessary information can be obtained, which is convenient for the network administrator to analyze.
Owner:HUAWEI TECH CO LTD
Method for generating dynamic host configuration protocol (DHCP) snooping binding information, and device thereof
InactiveCN101656722BAvoid attackInhibit migrationError prevention/detection by using return channelData switching networksComputer hardwareProtocol for Carrying Authentication for Network Access
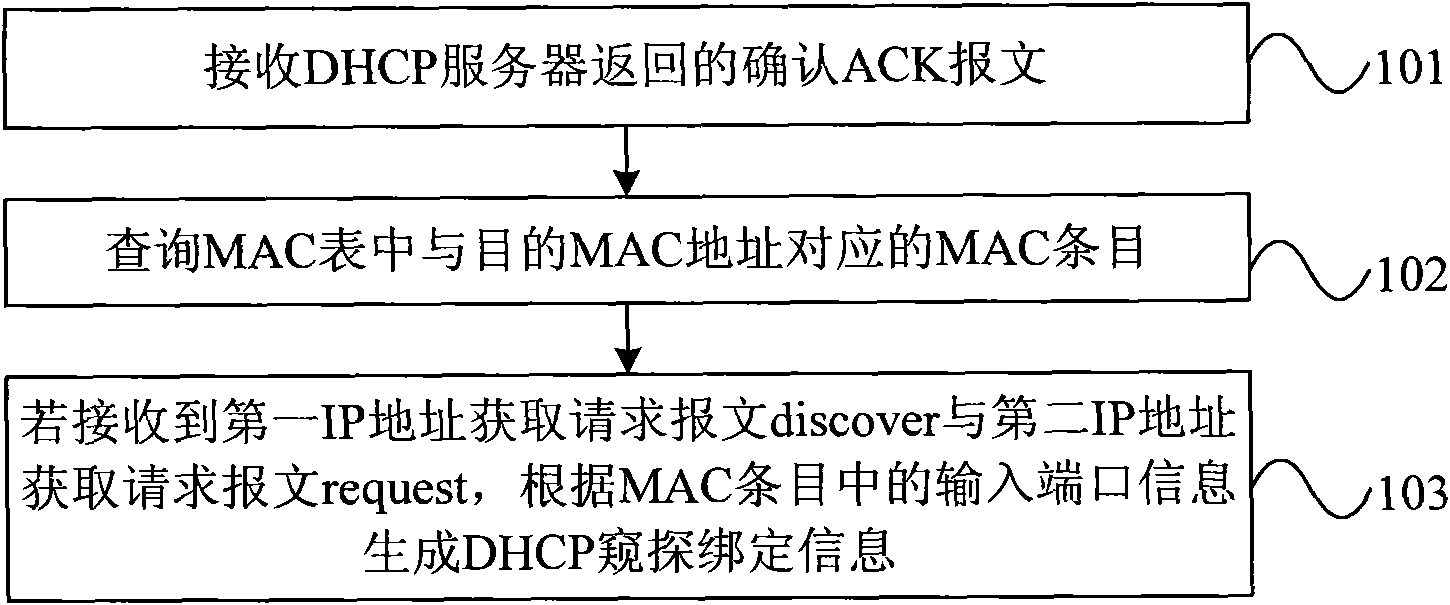
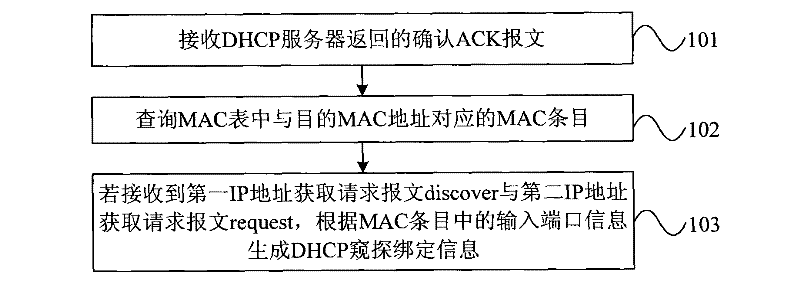
The embodiment of the invention discloses a method for generating dynamic host configuration protocol (DHCP) snooping binding information, and a device thereof, wherein the method comprises: receiving ACK message including target MAC address returned by a DHCP server; querying items corresponding to the target MAC address; according to a first identification position and a second identification position in MAC items, if receiving message discover and message request, generating the DHCP snooping binding information according to input port information in the MAC items, and ensuring source MAC address, the input port information and input VLAN ID in the message discover and the message request to be respectively and correspondingly the same as each other. The embodiment of the invention canavoid the pot corresponding to the MAC address in a MAC table not being shifted caused by MAC address spoofing, and effectively guarantees the accuracy of the DHCP snooping binding information.
Owner:BEIJING XINWANG RUIJIE NETWORK TECH CO LTD
A configuration method, device, SDN controller, and medium of a security entry
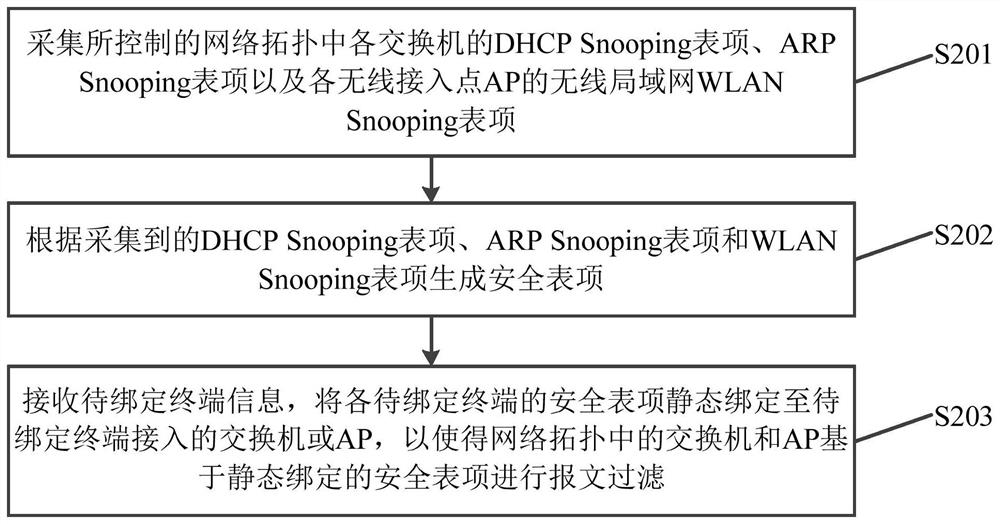
Embodiments of the present invention provide a security entry configuration method, device, SDN controller and medium, and relate to the technical field of communications. The embodiment of the present application includes: collecting the DHCP Snooping entry, the ARP Snooping entry and the WLAN Snooping entry of each AP in the controlled network topology; according to the collected DHCP Snooping entry, ARP Snooping entry and WLAN Snooping The table item generates a security table item; receives the information of the terminal to be bound, and statically binds the security table item of each terminal to be bound to the switch or AP connected by the terminal to be bound, so that the switch and AP in the network topology are based on the static The bound security entry performs packet filtering. On the premise of ensuring terminal access security, the configuration workload can be reduced and configuration efficiency can be improved.
Owner:NEW H3C BIG DATA TECH CO LTD
Layer 3 switching system and method based on Layer 2 dhcp SNOOPING
The invention discloses a three-layer switching system and method based on two-layer DHCP SNOOPING. The system includes a DHCP user terminal, a two-layer switching device, a three-layer switching device and a DHCP server, and is characterized in that the two-layer switching device includes an enabling The module, by enabling DHCP SNOOPING configured on the Layer 2 switching device, monitors the DHCP request process of the user terminal, creates and saves DHCP binding information; the Layer 2 switching device processes the binding information and uploads it to the Layer 3 switching device, and the third layer According to the DHCP binding information, the layer switching device delivers a routing table entry for processing by the Layer 3 engine, and forwards the network packet processed by the Layer 3 engine to the destination user terminal according to the address of the destination user terminal. The technical scheme of the present invention increases the learning method of the three-layer table entry of the switch in the DHCP environment, and effectively ensures the stability and security of the table entry.
Owner:武汉神州数码云科网络技术有限公司
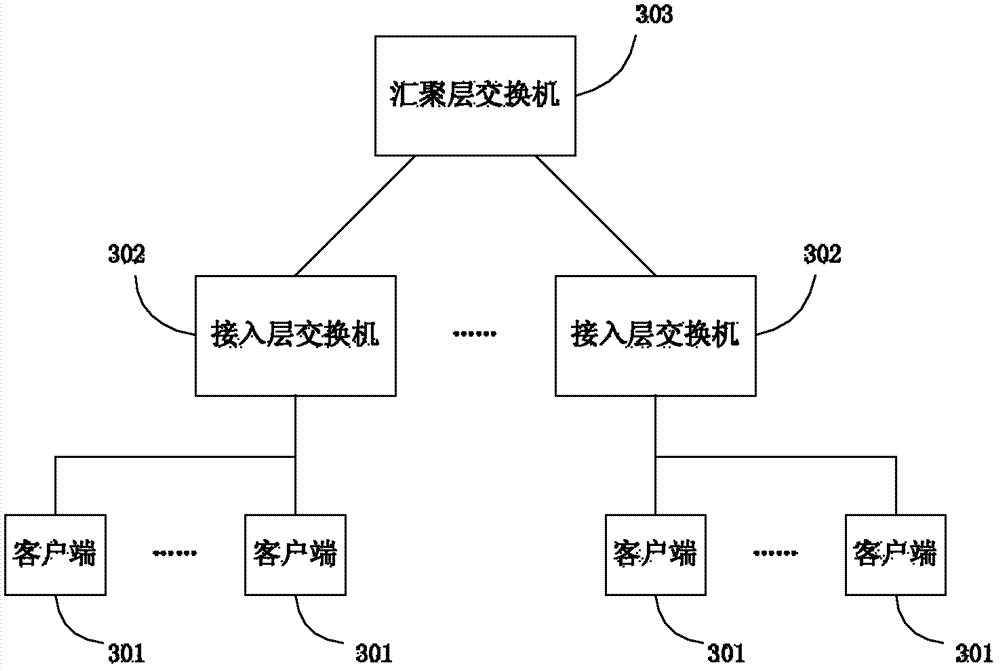
Campus network security architecture and network monitoring system
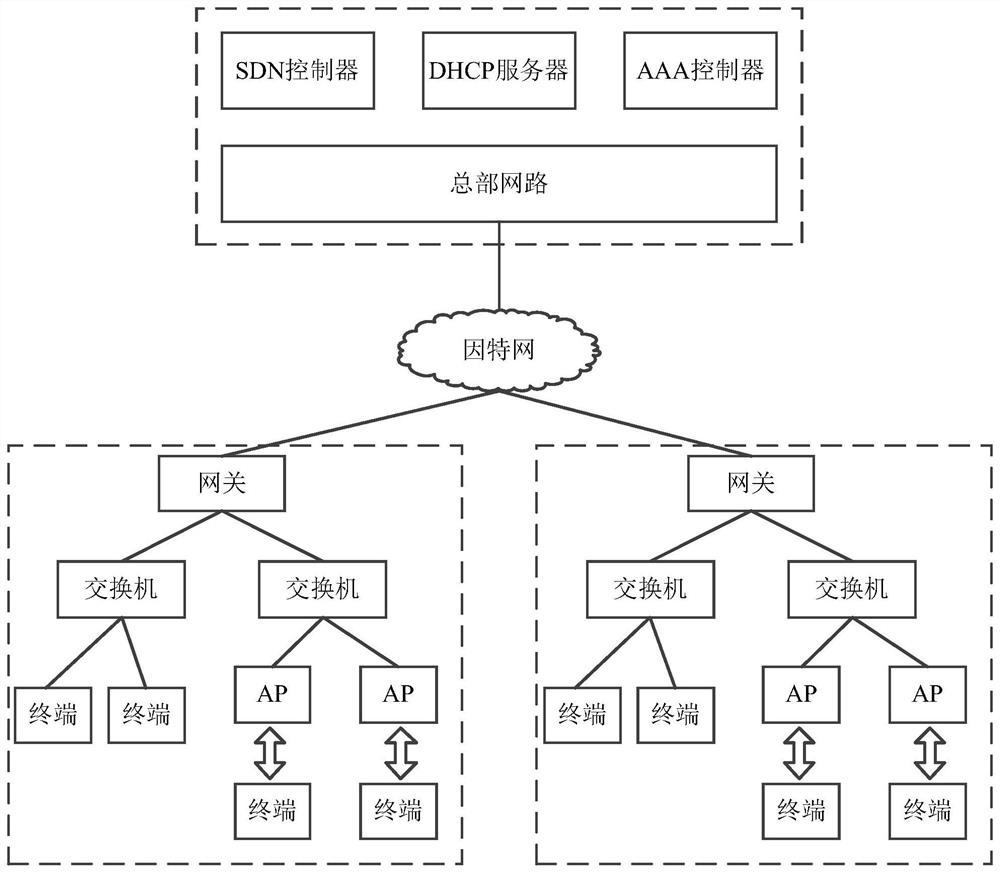
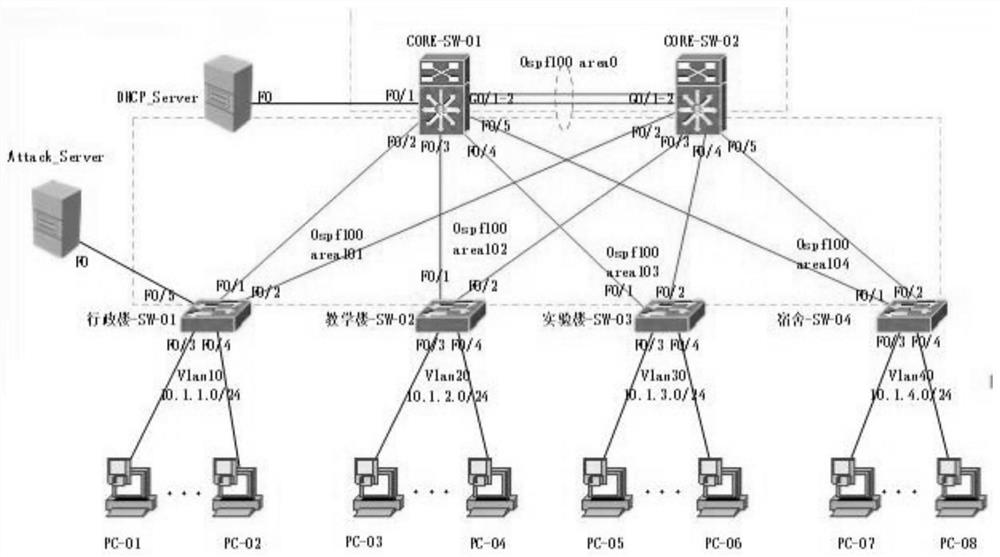
PendingCN114710388AGuarantee data securityEnsure network securitySecuring communicationEngineeringAccess stratum
The invention discloses a campus network security architecture. The campus network security architecture comprises a network monitoring system. The architecture comprises an access layer, a convergence layer, a core layer and network interconnection equipment, the network interconnection device comprises a first core switch and a second core switch, and the first core switch and the second core switch serve as core devices of the whole campus network and are connected with all areas of the campus network. The terminal equipment in each area adopts a DHCP (Dynamic Host Configuration Protocol) to acquire an address, and the DHCP comprises a DHCP client and a The DHCP server is connected to the first core switch and the second core switch, and DHCP Snooping is configured on the first core switch and the second core switch to guarantee access of the safety terminal and guarantee that the terminal can obtain the safety address. According to the invention, the DHCP Snooping technology is used on the access layer equipment in the network to protect the data security of each user in the network, so that the network security and stability of the whole campus network are better ensured.
Owner:JIANGSU UNIV OF SCI & TECH
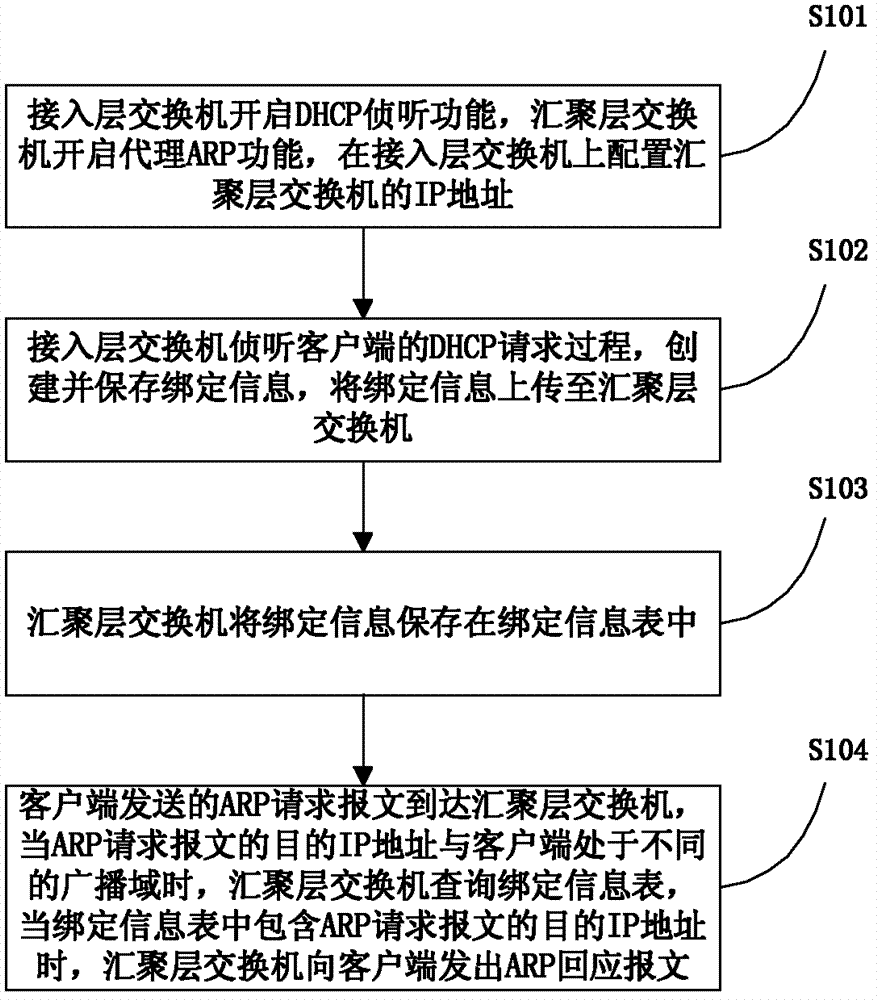
Method and system for realizing proxy arp function based on dhcp listening
ActiveCN102546307BImprove accessibilityEnsure interoperabilityData switching networksIp addressClient-side
Owner:北京神州数码云科信息技术有限公司
Intelligent control method for realizing city Ethernet exchanger switch-in security
InactiveCN101022340BComprehensive supervisionAvoid controlUser identity/authority verificationData switching by path configurationTraffic capacityMetro Ethernet
An intelligently controlling method for realizing city Ethernet switch-board access safety integrates functions of certificating user legality, exerting illegal agent proof of legal user, controlling P2P flow rate and DHCP SNOOP together in said method for controlling and monitoring user in order to raise safety of network.
Owner:WUHAN FIBERHOME NETWORKS
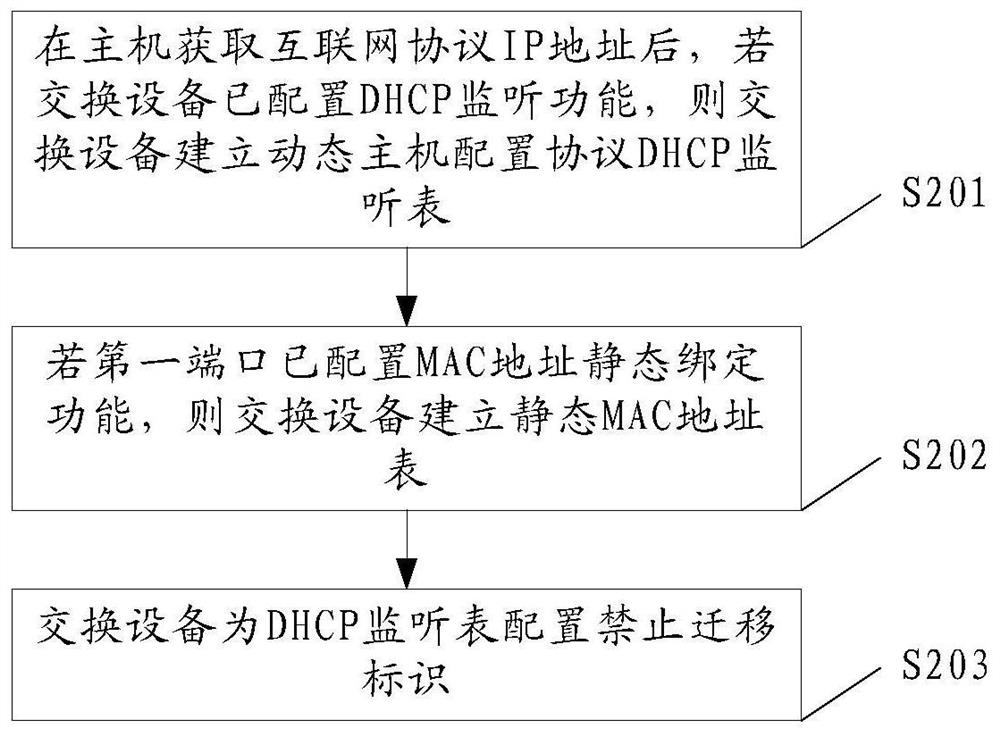
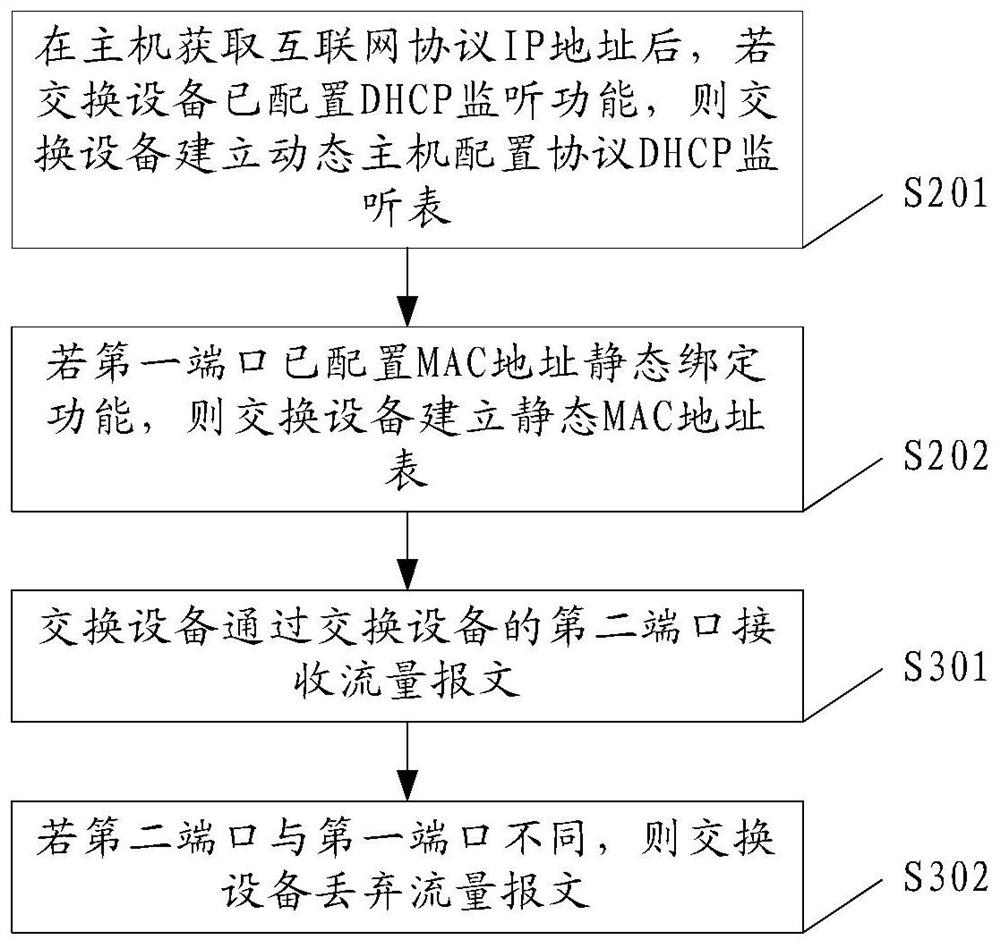
Method for preventing mac address drifting in dhcp network and switching equipment
This application provides a method and switching equipment for preventing MAC address drift in a DHCP network, which relates to the field of data communication, and can prevent the MAC address of a host bound with an assigned IP address from drifting under the premise that the IP address can be dynamically allocated. . The method includes: after the host obtains the IP address of the Internet protocol, if the switching device has configured a DHCP monitoring function, then the switching device establishes a DHCP monitoring table; if the first port has configured a MAC address static binding function, then the switching device establishes a static MAC address table; the switching device configures the prohibition migration flag for the DHCP snooping table; wherein, the DHCP snooping table includes the IP address of the host, the media access control MAC address and the first port of the host, and the static MAC address table includes the MAC address, the first port, and the static Binding flag, the first port is the port connected to the host in the switching device, the static binding flag prohibits the switching device from modifying the static MAC address table, and the migration prohibition flag prohibits the switching device from modifying the DHCP listening table.
Owner:MAIPU COMM TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com