Intelligent control method for realizing city Ethernet exchanger switch-in security
An intelligent control and switch technology, applied in the computer field, can solve problems such as complex configuration and insufficient functions, and achieve the effect of strengthening network security, simple configuration, and improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0104] The present invention will be described in detail below in conjunction with the accompanying drawings and embodiments.
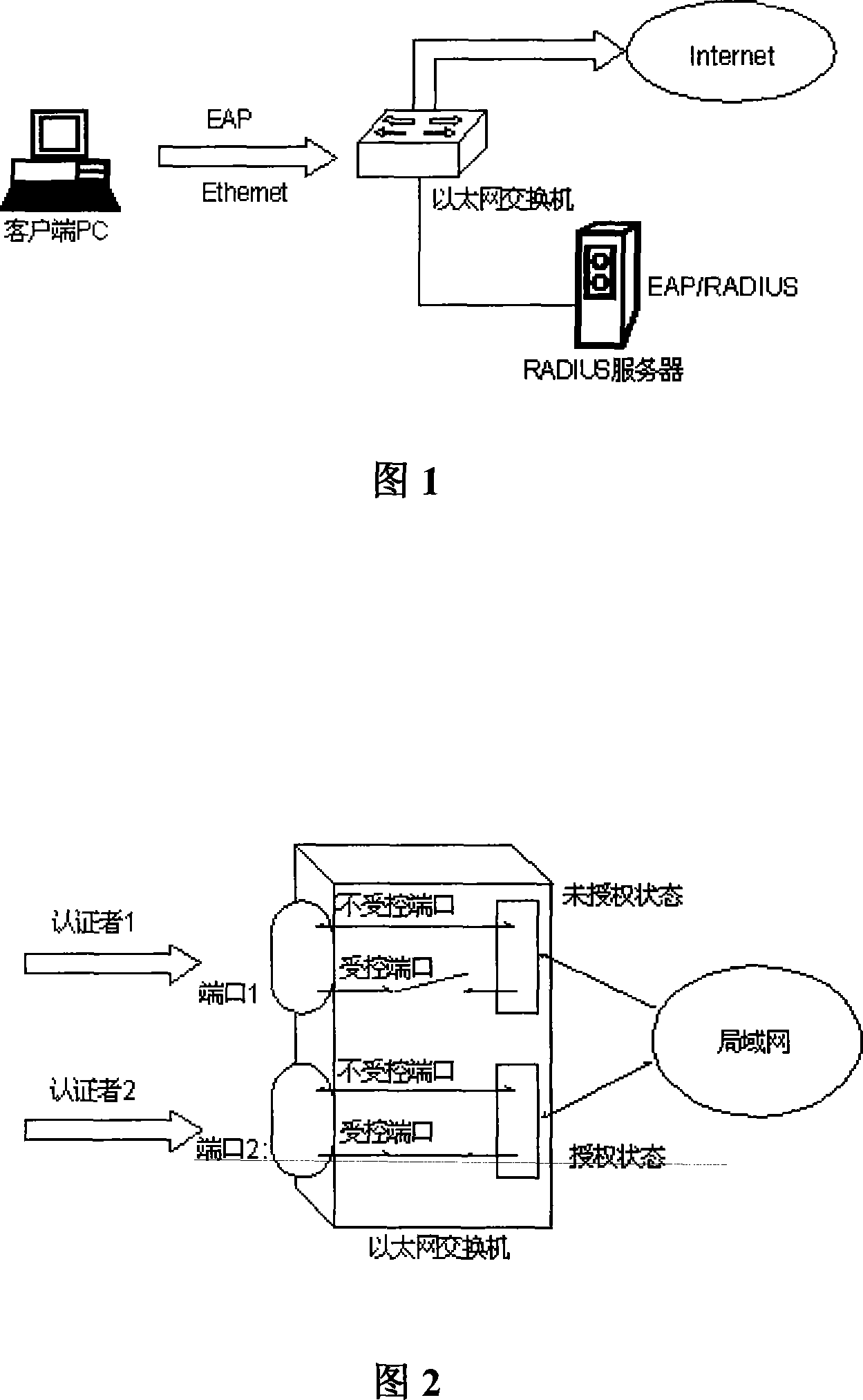
[0105] ●Adopt IEEE802.1x protocol
[0106]The protocol is based on Client / Server access control and authentication protocol. It can restrict unauthorized user equipment from accessing LAN / WAN through the access port. Before obtaining various services provided by switches or LANs, 802.1x authenticates users connected to switch ports. Before the authentication is passed, 802.1x only allows EAPoL (Extensible Authentication Protocol for LAN) data to pass through the switch port connected to the device; after the authentication is passed, normal data can pass through the switch port.
[0107] ● Anti-proxy based on switch port authentication and application binding
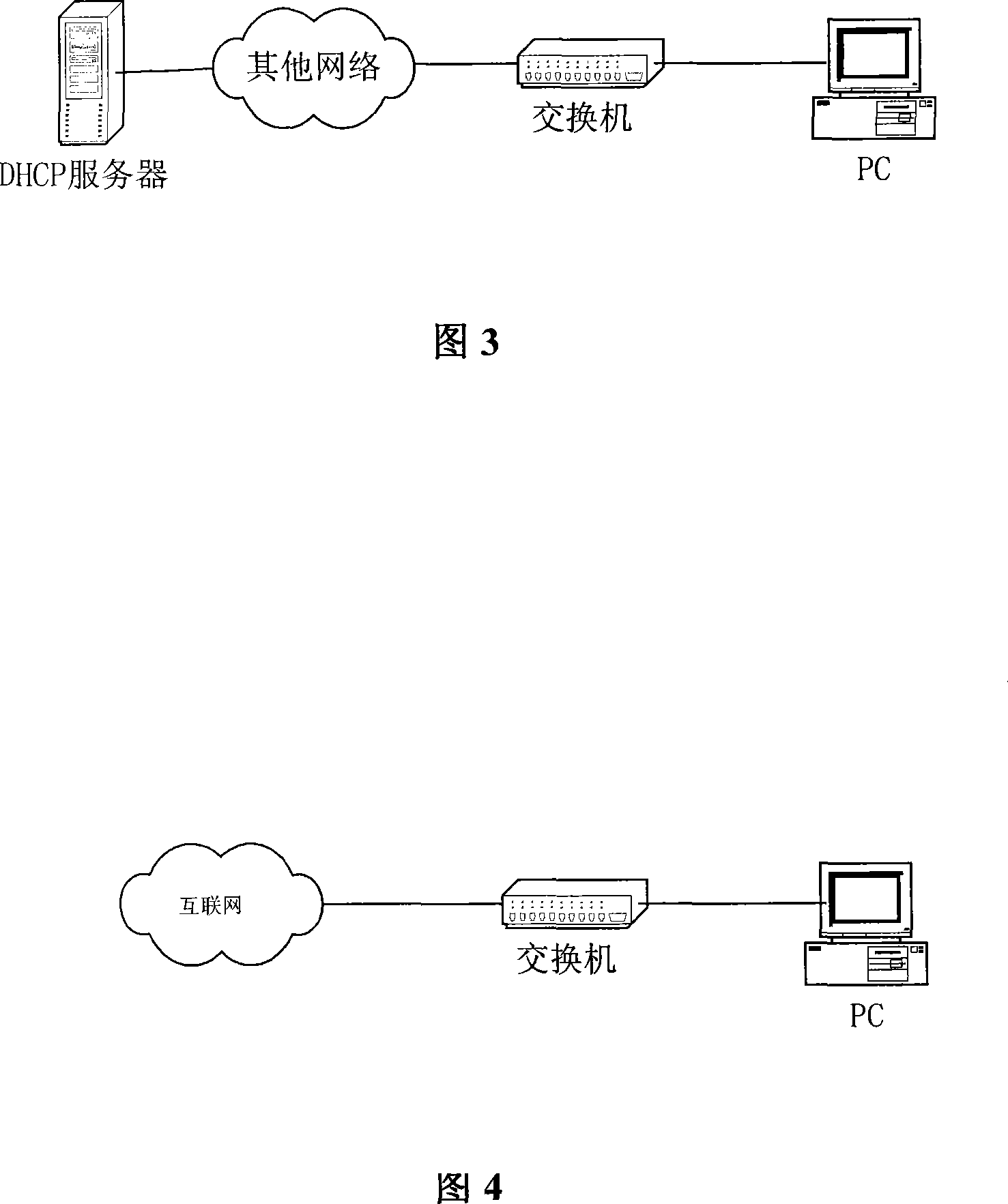
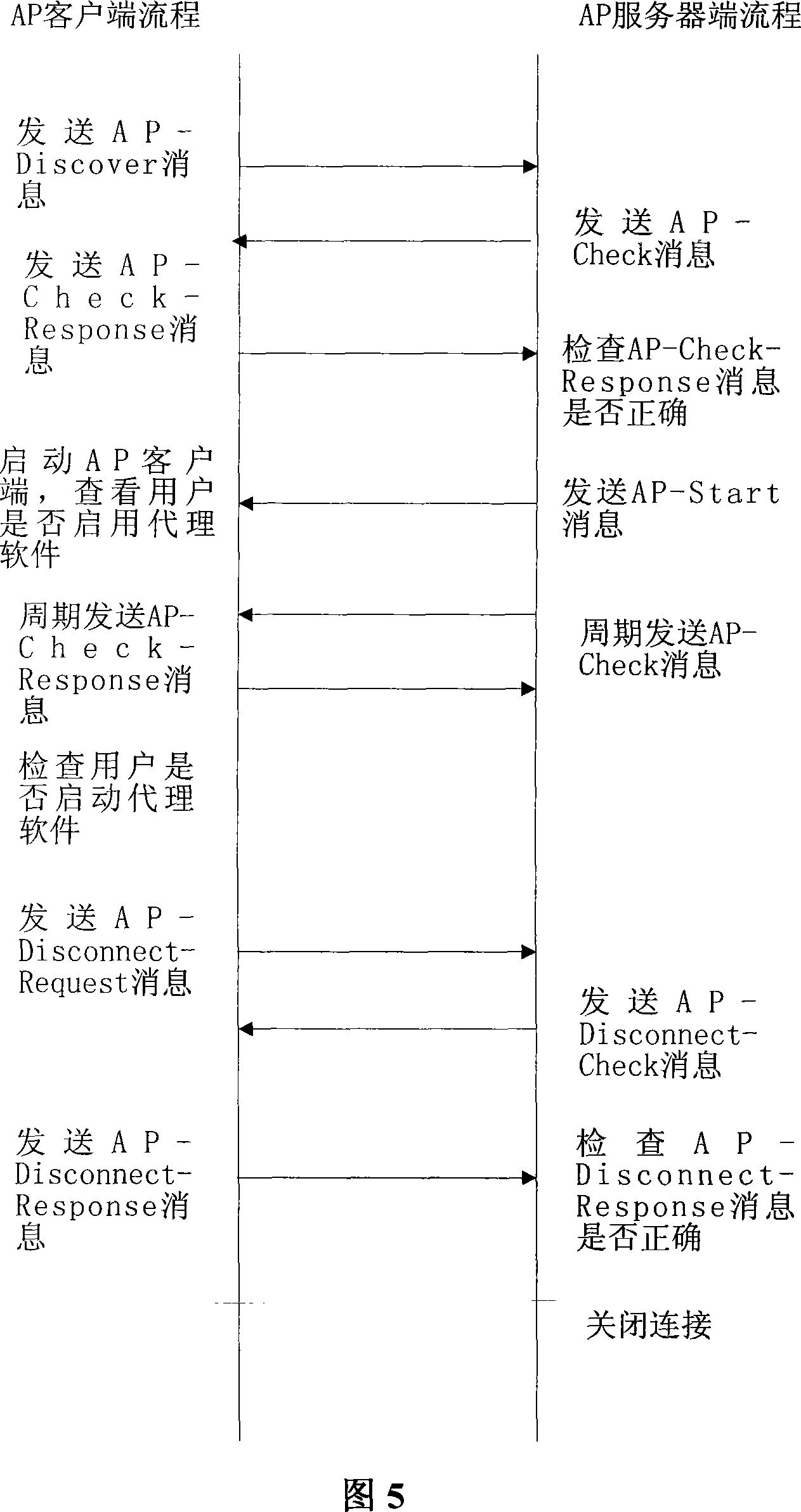
[0108] The user identity authentication technology represented by 802.1X cannot prevent illegal user PCs from accessing the Internet through proxy software on legitimate user PCs, because af...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com