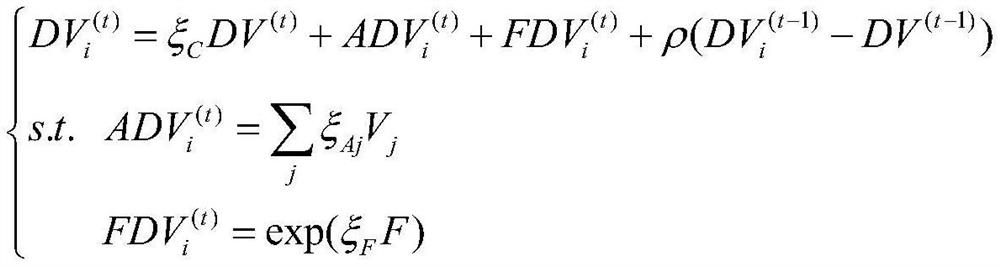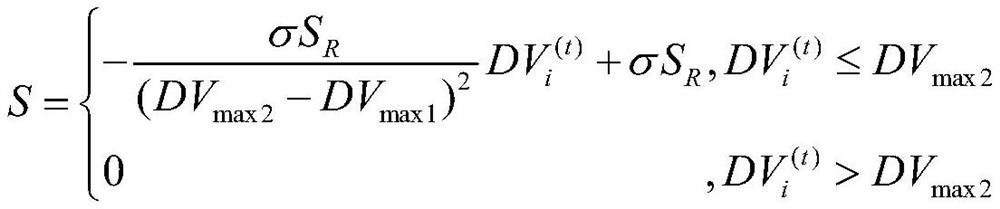Campus network security architecture and network monitoring system
A campus network and security technology, applied in transmission systems, digital transmission systems, security communication devices, etc., can solve problems such as potential safety hazards, achieve the effects of ensuring normal use, alleviating the shortage of IP address resources, and ensuring network security and stability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0052] The present invention is further outlined below in conjunction with the accompanying drawings.
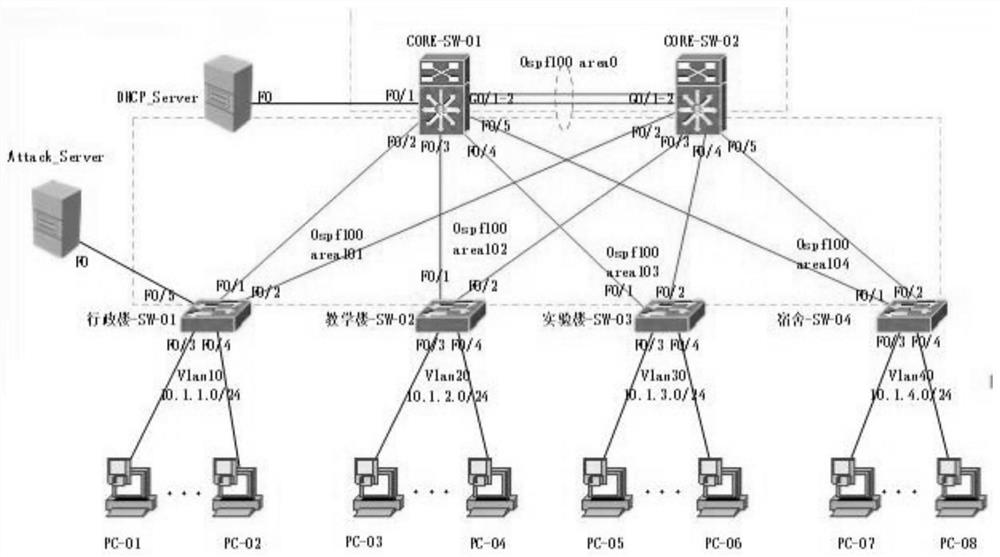
[0053] A campus network security architecture includes an access layer, an aggregation layer, a core layer and network interconnection equipment; the campus network security architecture includes a network monitoring system;
[0054] The access layer, as a direct port for users to connect to the network, is used to allow the local network to access the work site;
[0055] The convergence layer, which realizes data transmission, management and aggregation for the access layer, also selectively restricts the direct access of the access layer equipment to the core layer equipment, associates the nodes of the access layer with the nodes of the core layer, and becomes a network connection A bridge for communication between incoming equipment and the core layer;
[0056] The core layer, as the core and link of the entire network structure design, is used to realize high-quality t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com