Method for preventing attack of untrusted servers
A server, non-trust technology, applied in the field of network communication, to achieve the effect of preventing spoofing attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0013] The present invention will be further described below with reference to the drawings and embodiments.
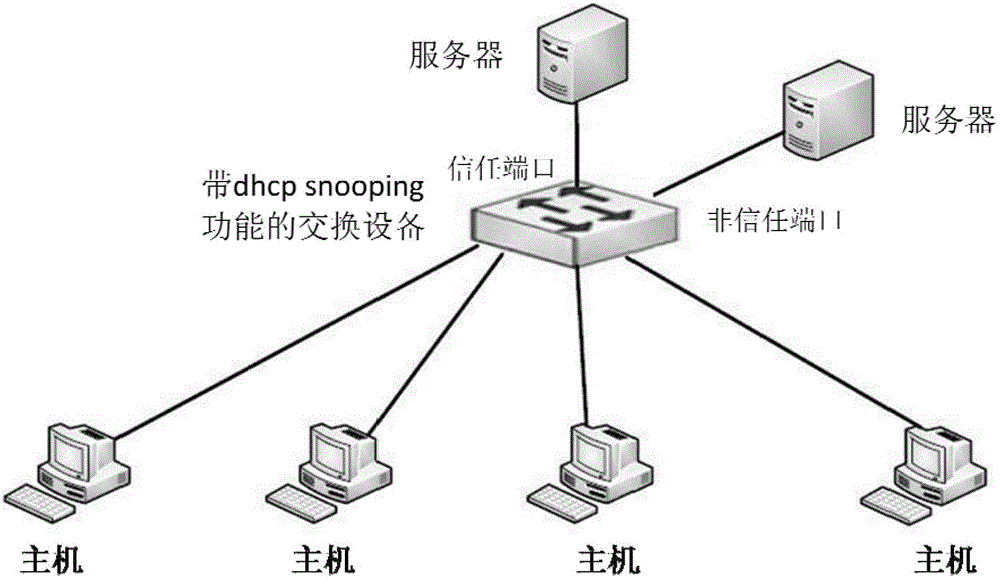
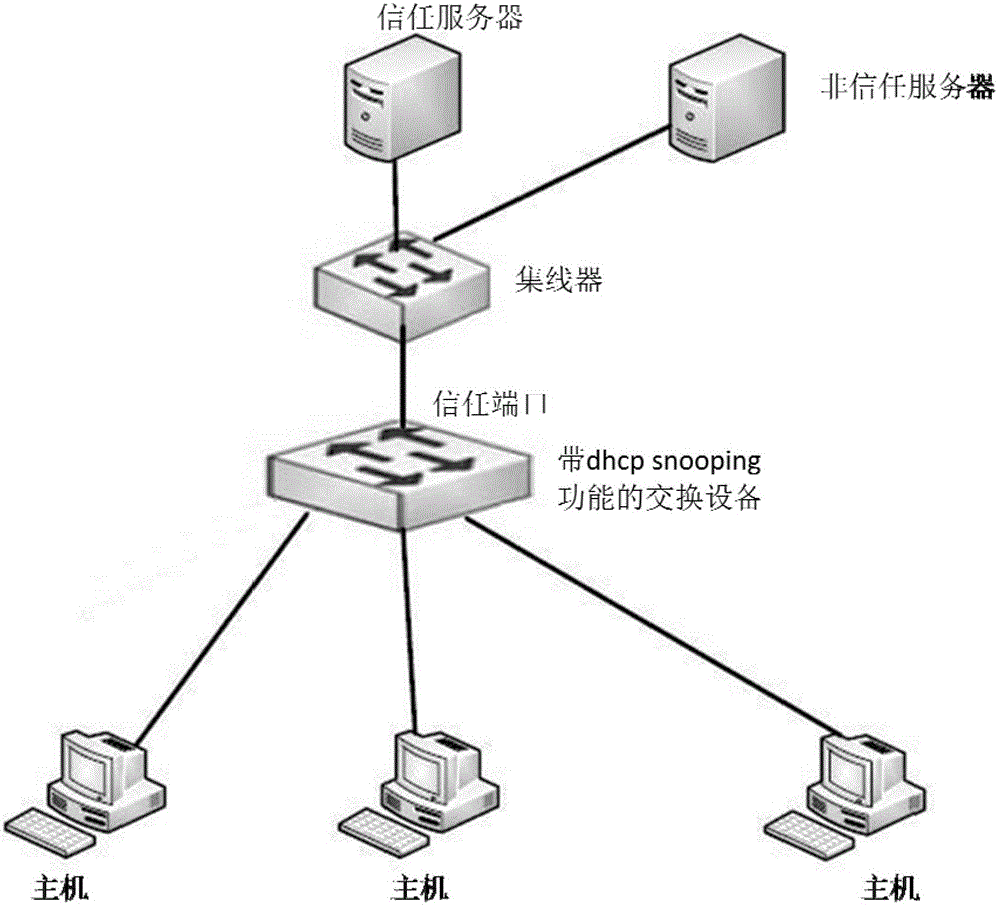
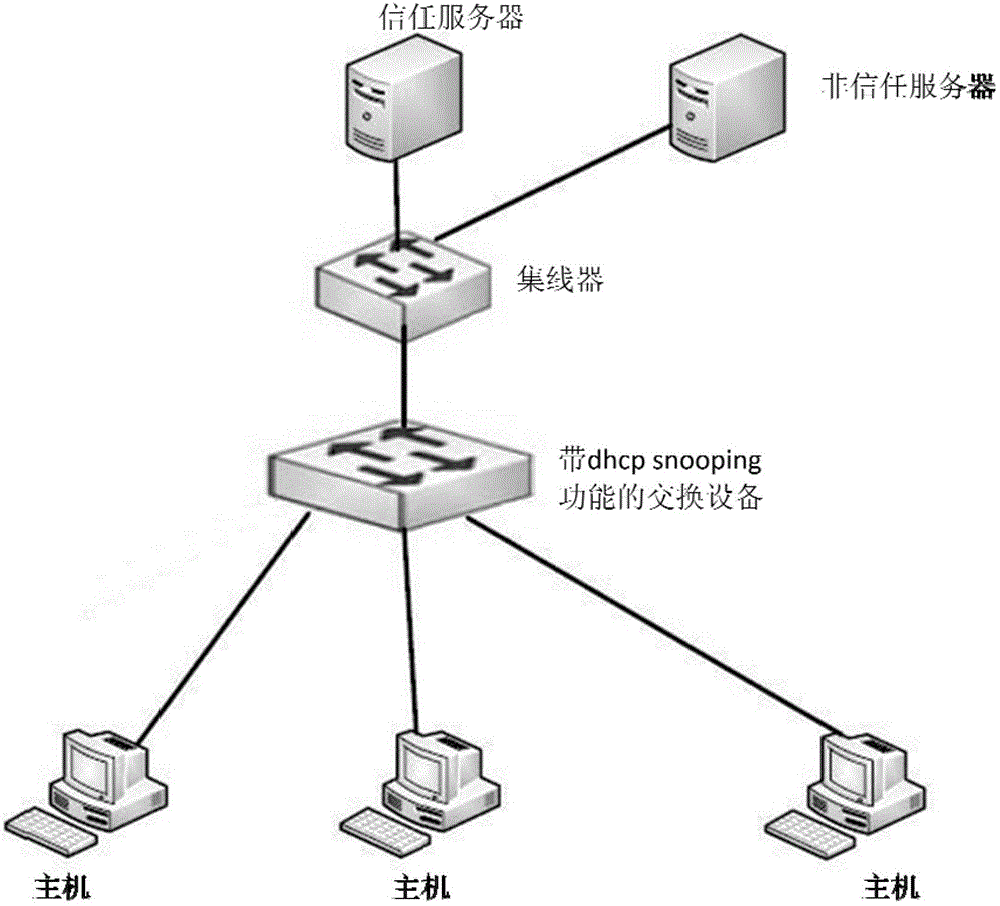
[0014] The invention provides a method for preventing untrusted server attacks, which can effectively prevent untrusted server spoofing attacks.
[0015] In an embodiment, the present invention achieves the purpose of preventing untrusted server cheating by adding a trusted server IP address list in a switching device that enables the DHCP Snooping function. When a switching device receives a DHCP Snooping response packet, it needs to verify the source address of the DHCP response packet. The source address of the DHCP response packet is the IP address of the server that sent the DHCP response packet. Only the source address is in the trusted server IP address list. In this way, the host under the switching device will not receive spoofing attacks from untrusted servers. In addition, when the server's IP address has not changed, the server's location moves, and there is n...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com