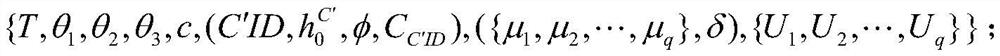Patents
Literature
30results about How to "Prevent spoofing attacks" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
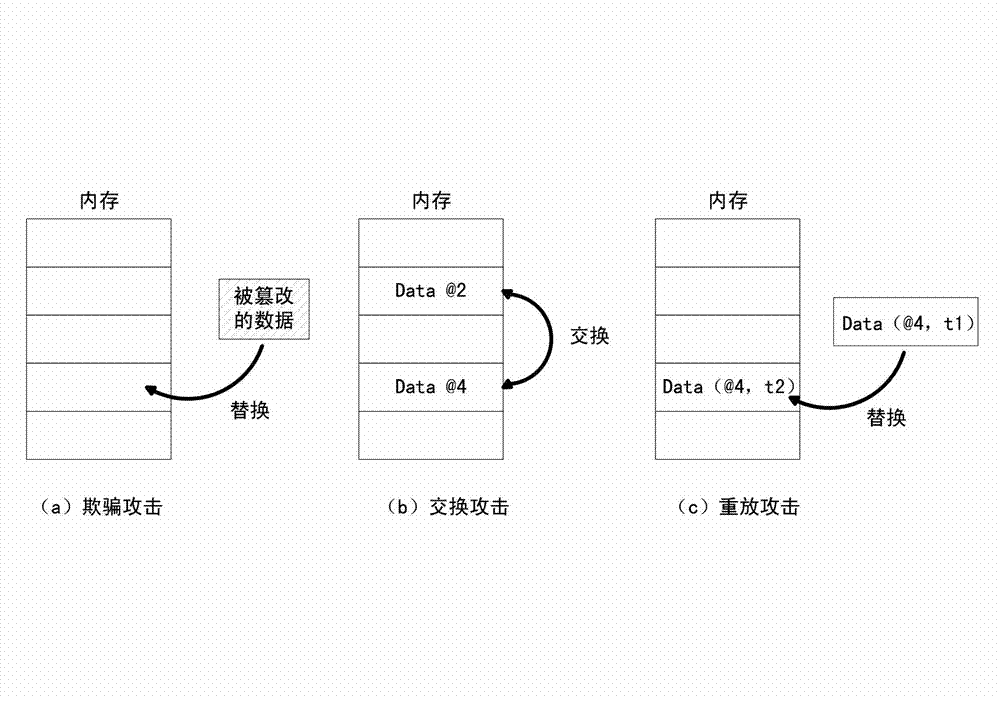
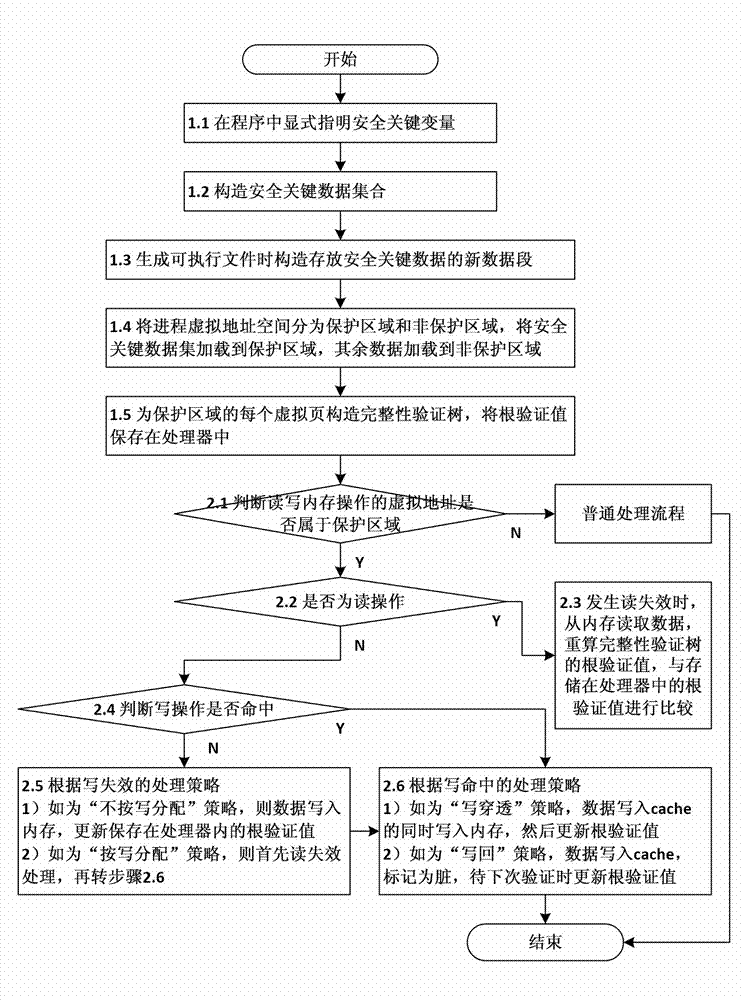
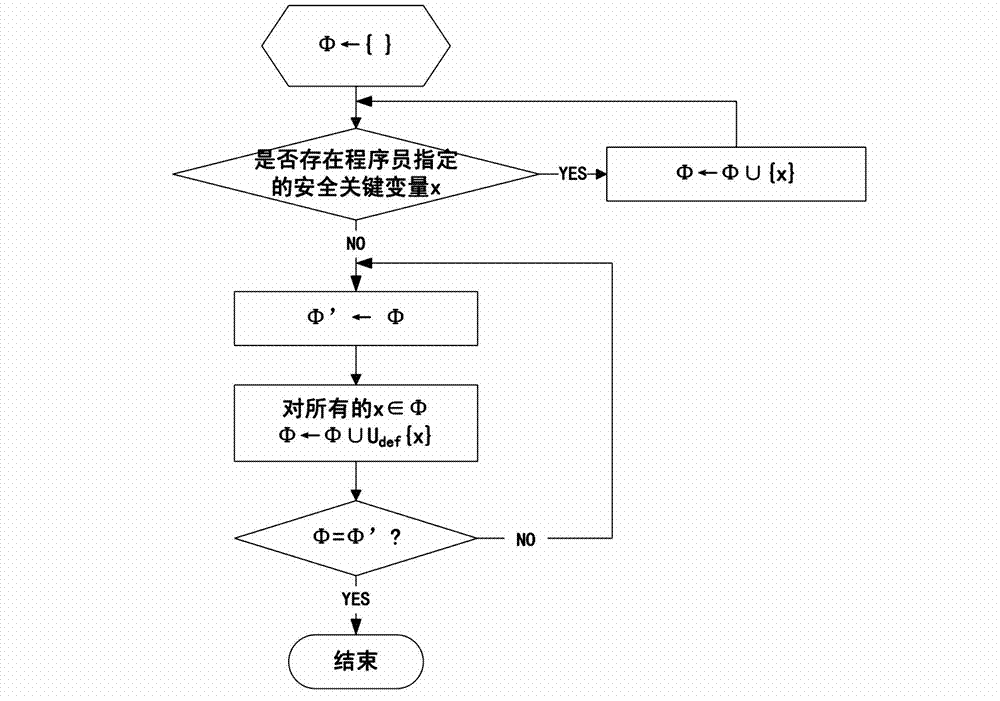
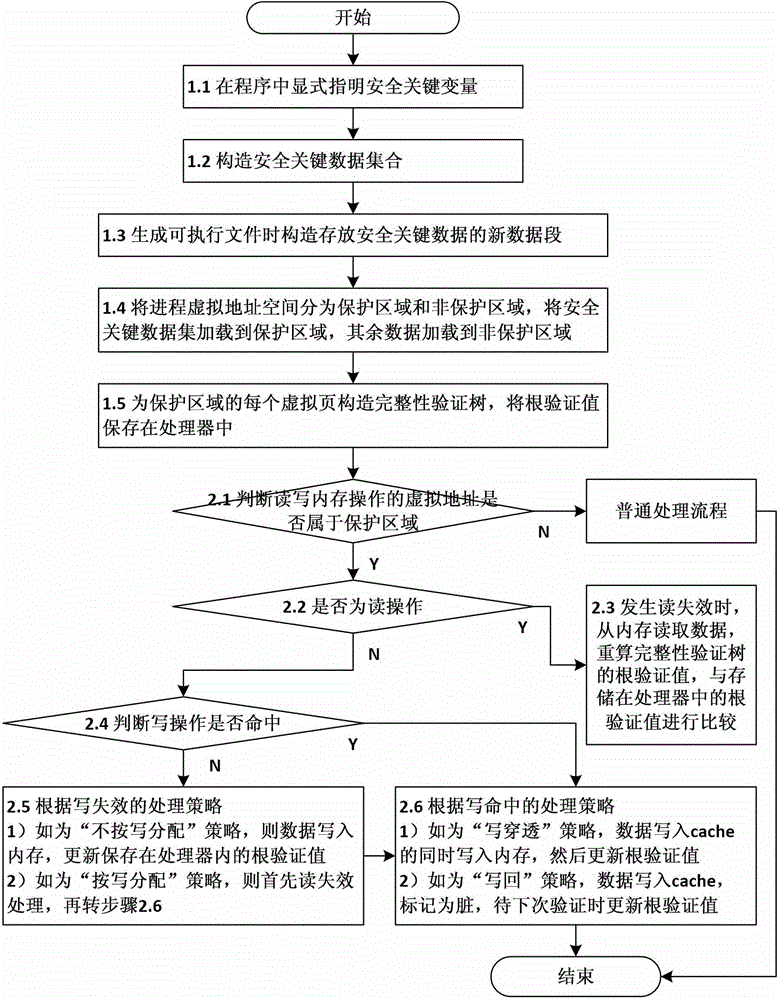
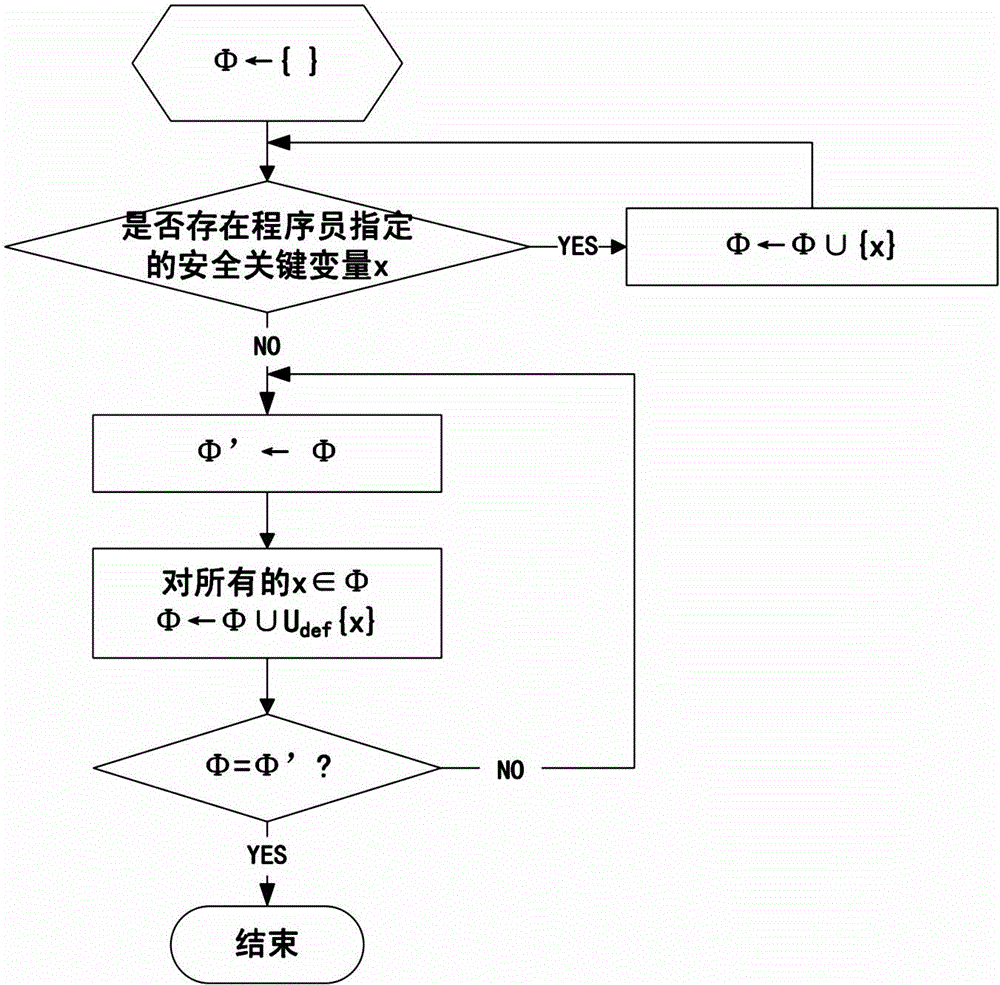
Method and device for verifying integrity of security critical data of program in process of running
ActiveCN102930185AAvoid attackIntegrity verification implementationProgram/content distribution protectionData setData integrity
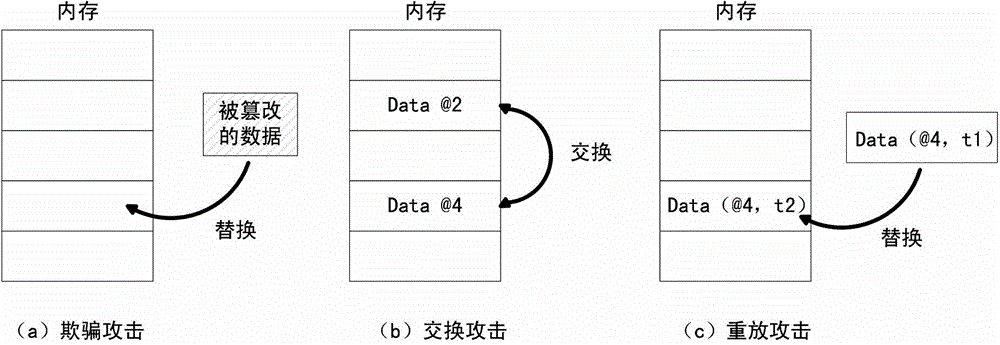
The invention discloses a method and a device for verifying the integrity of security critical data of a program in the process of running. The method comprises the following steps: 1) indicating a security critical variable in the program, generating a security critical data set in the process of compiling, dividing a virtual address space of the program into a protected area and a non-protected area in the process of loading the program, loading the security critical data set to the protected area, and constructing an integrity verification tree for a virtual page of the protected area of the program; and 2) in the process of writing program data into a memory, updating a root verification value; and in the process of reading program data from the memory, generating a new root verification value, comparing the new root verification value with the original root verification value, if the two are equal, determining that the security critical data set is not tampered, otherwise, determining that the security critical data set is tampered. The device comprises a data integrity verification circuit, a root verification value storage module and a comparator. The method and the device disclosed by the invention have the advantages of high safety performance, strong attack prevention performance, small calculated amount, and less occupied storage space.
Owner:NAT UNIV OF DEFENSE TECH
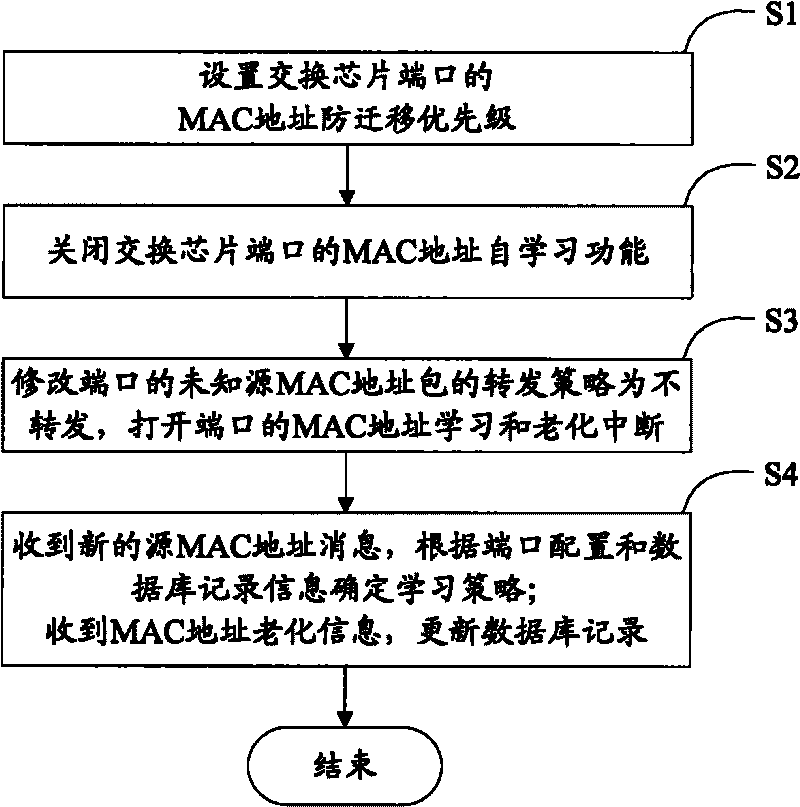
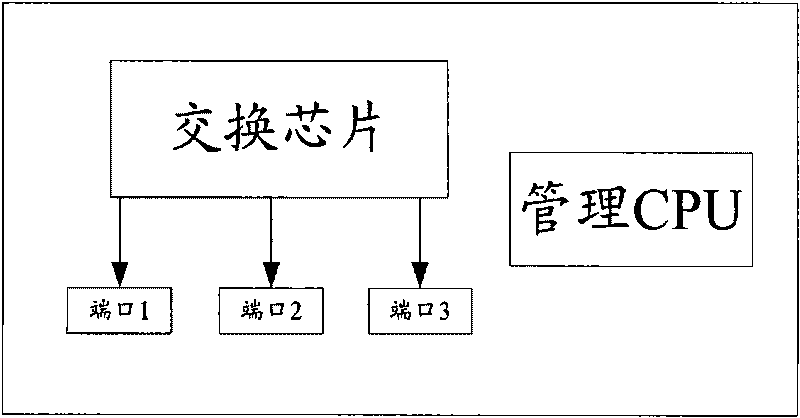
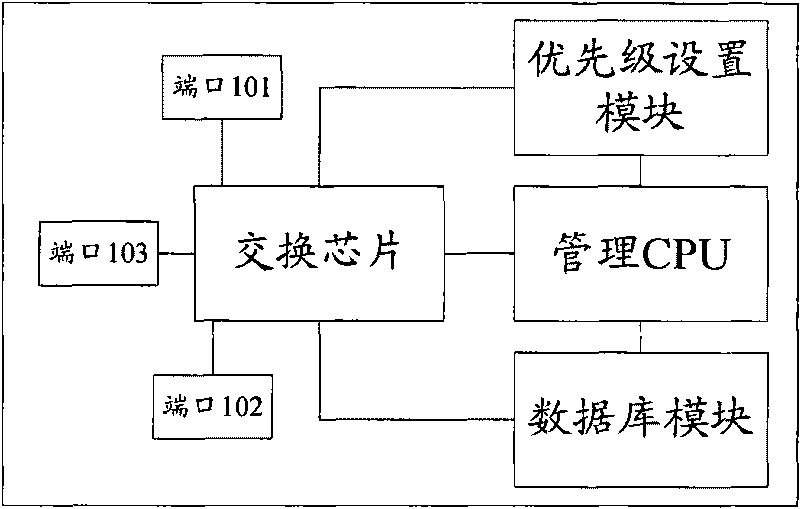
Method and device for preventing switch ports from MAC address transfer
InactiveCN101764753ARealize the function of anti-migrationThe anti-migration function reachesData switching by path configurationEmbedded systemAccess network
The invention discloses a method and a device for preventing switch ports from MAC address transfer, which relate to the access network security technology of an Ethernet switch and aim to solve the problem that MAC address transfer prevention cannot be effectively realized on an Ethernet switch chip of the switch in the prior art. The method comprises the following steps: setting the MAC address transfer prevention authority of each port of the switch chip in the switch; disenabling automatic MAC address leaning functions of all the ports; modifying a forwarding strategy of unknown source MAC address packets of the ports to indicate the unknown MAC address packets are not to be forwarded, and starting the MAC address learning and ageing interruption of the ports; when new source MAC address messages are received, determining a learning strategy according to the configuration of the ports and database record information; and if MAC address ageing information is received, updating database record. The switch comprises the switch chip, a priority setting module, a database module and a management CPU.
Owner:ZTE CORP
Transparent data integrity auditing and transparent encrypted data deduplication protocol based on block chain
ActiveCN110278076AEnsure safetyIntegrity guaranteedKey distribution for secure communicationEncryption apparatus with shift registers/memoriesData integrityInformation security
The invention belongs to the field of information security, and particularly relates to a transparent data integrity auditing and transparent encrypted data deduplication protocol based on a block chain. The scheme of the invention comprises four modules: parameter initialization, encryption key acquisition, bidirectional upheaval checking, transparent integrity auditing and transparent de-duplication. Compared with the prior art, the protocol can resist the bias audit and delay audit of the cloud server, and meanwhile, the situation that the cloud server claims an erroneous duplicate removal level to charge additional fees can be avoided. According to the protocol, single-point failure attacks and exhaustion attacks can be prevented, and bidirectional ownership proof of a user and a cloud server can be provided. The invention realizes a secure and effective protocol based on the block chain, and can simultaneously realize transparent data integrity auditing and transparent data de-duplication.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
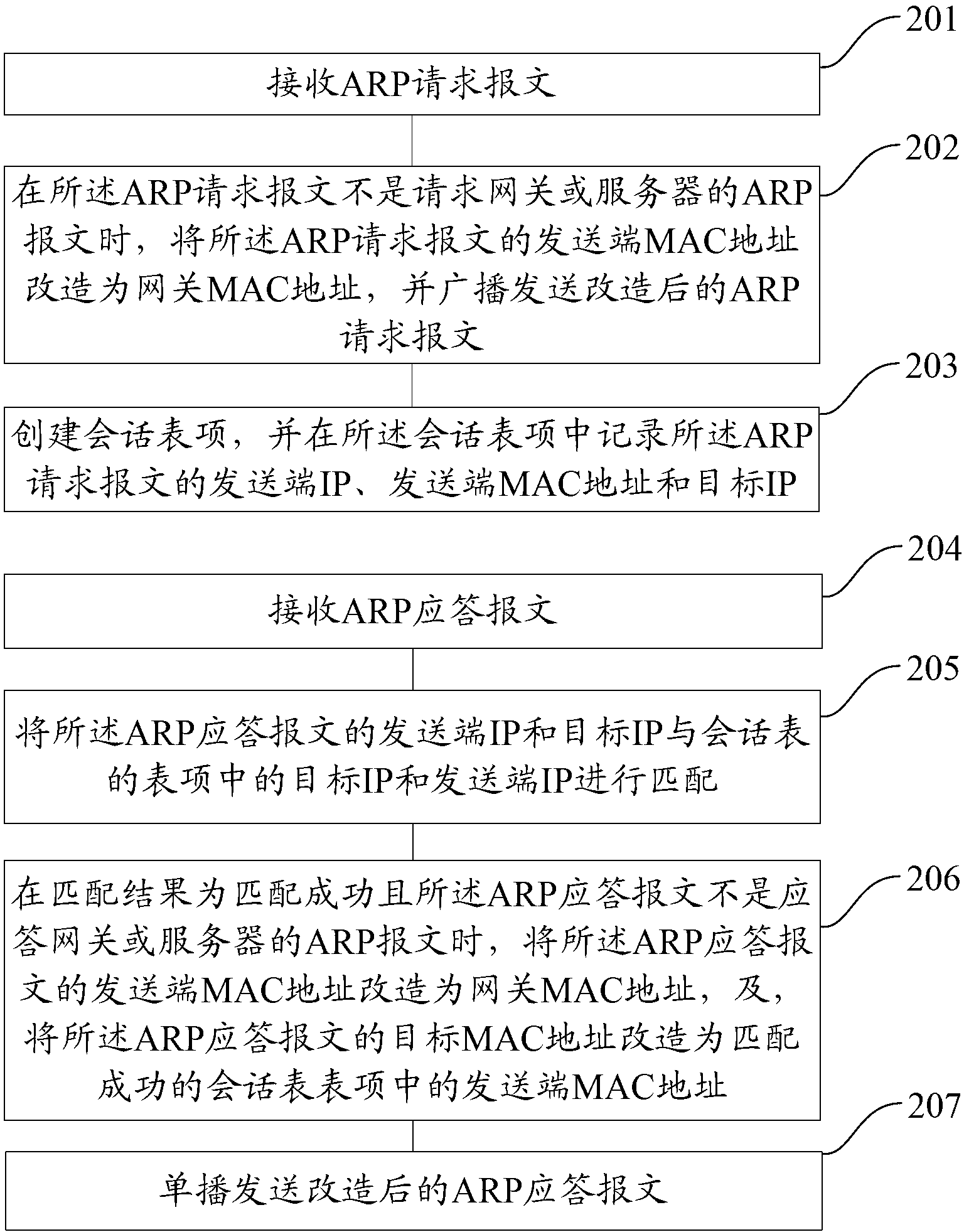
Method and device for media access control forced forwarding of address resolution protocol (ARP) message
ActiveCN103023818AAccurate detectionEfficient detectionData switching networksAddress Resolution ProtocolIp address
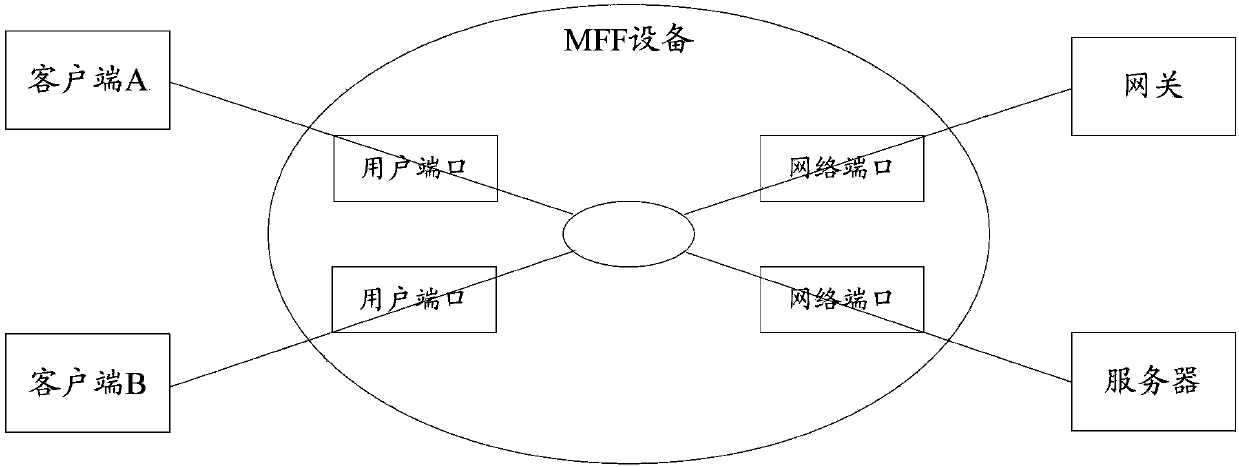
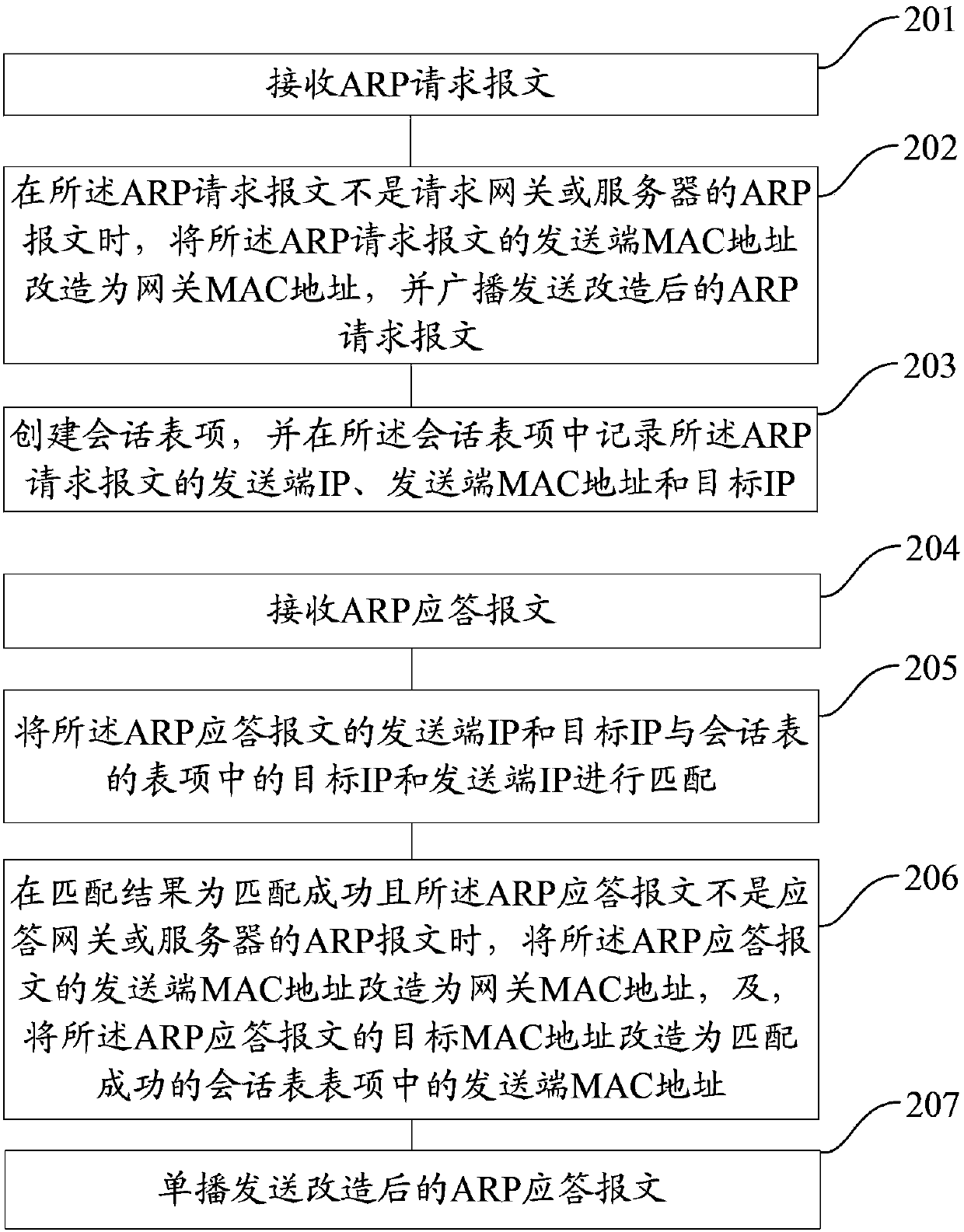
The invention provides a method and a device for media access control forced forwarding of an address resolution protocol (ARP) message. The method specifically includes that when an ARP request message is not an ARP message of a request gateway or a server, a sending end media access control (MAC) of the ARP request message is transformed to be a gateway MAC, and the ARP request message is sent in a broadcast mode; entries of a session table are established, and information of the ARP request message is recorded in the entries of the session table; and a sending end internet protocol (IP) and a target IP of an ARP response message are matched with a target IP and a sending end IP in the entries of the session table, when the matching result is successful and the ARP response message is not an ARP message of a response gateway or a server, a sending end MAC of the ARP response message is transformed to be a gateway MAC and a target MAC of the ARP response message is transformed to be a sending end MAC in the entries of the session table which is successfully matched, and the ARP response message is sent in an unicast mode. By means of the method and the device, IP address conflict in the network can be accurately and effectively detected.
Owner:XINHUASAN INFORMATION TECH CO LTD
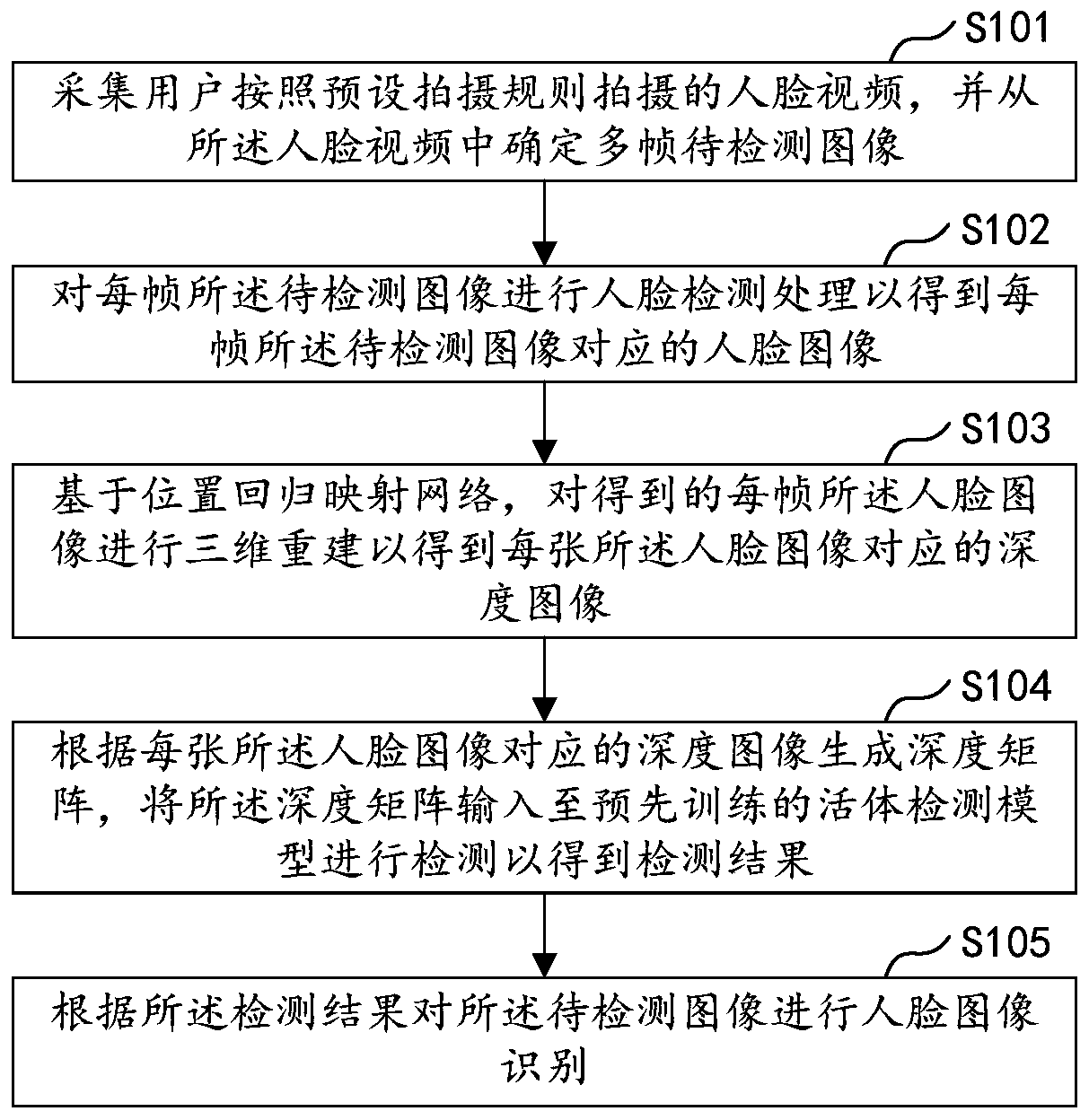
Face recognition method and device, computer equipment and storage medium
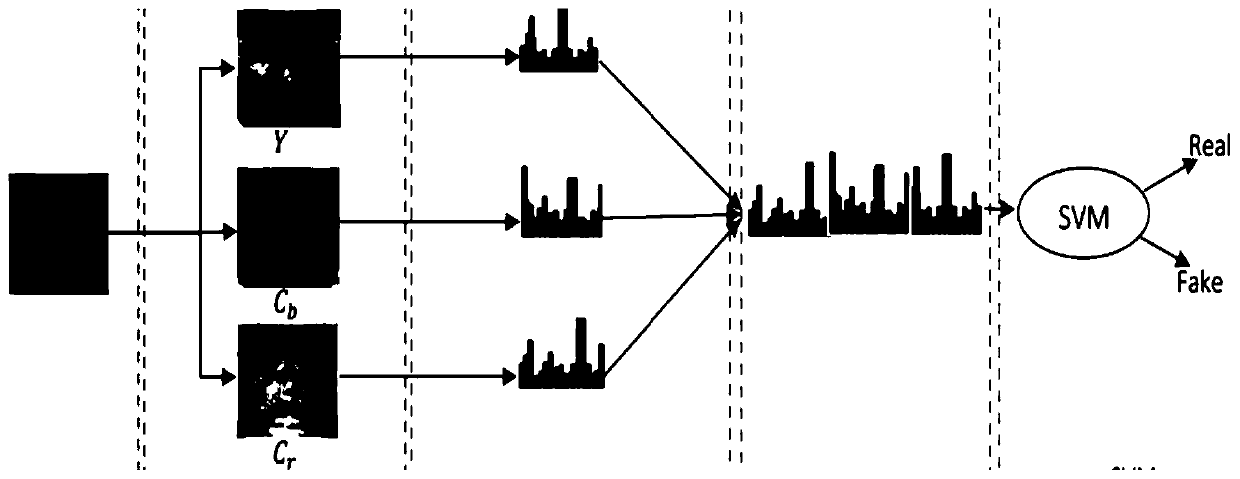
PendingCN110222573AImprove efficiencyImprove accuracySpoof detection3D modellingLocal binary pattern histogramSpoofing attack
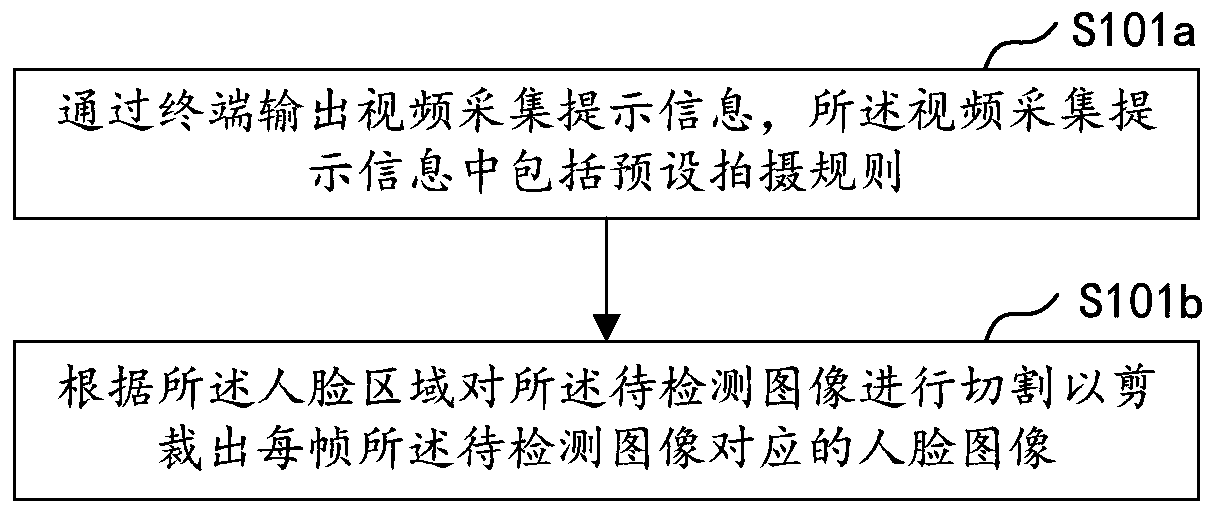
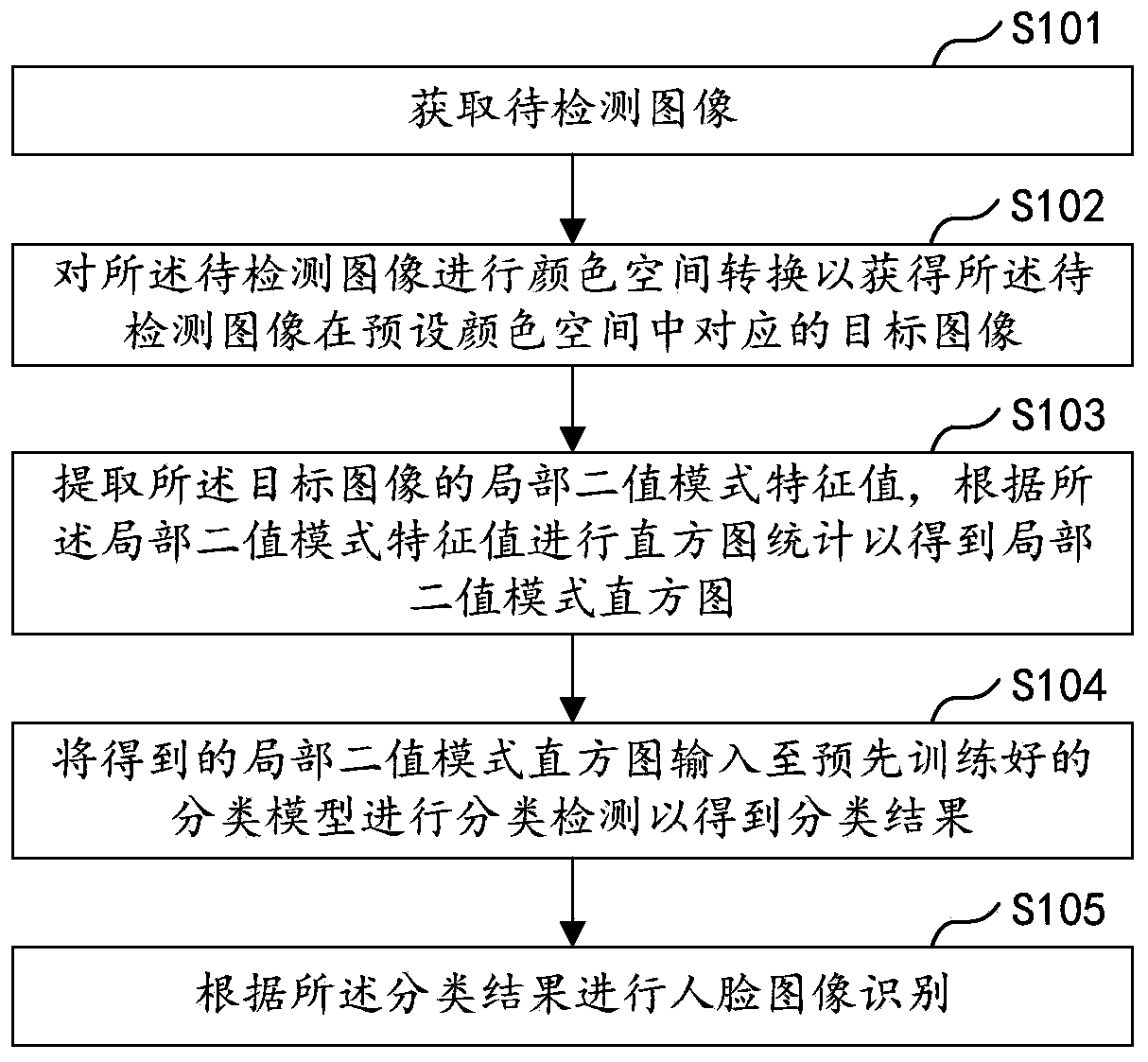
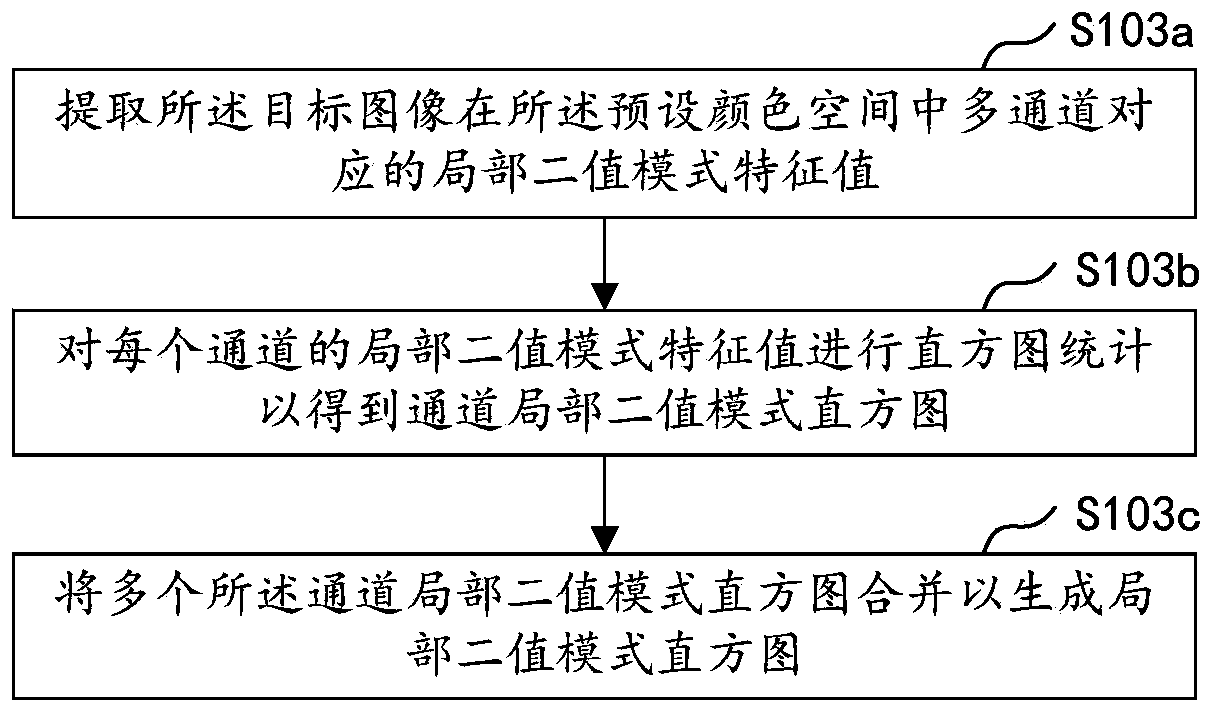
The invention relates to the technical field of biological recognition, and is used for face recognition. The invention particularly discloses a face recognition method and device, computer equipmentand a storage medium. The method comprises the steps of acquiring a to-be-detected image; performing color space conversion on the to-be-detected image to obtain a target image corresponding to the to-be-detected image in a preset color space; extracting a local binary pattern characteristic value of the target image, and performing histogram statistics according to the local binary pattern characteristic value to obtain a local binary pattern histogram; inputting the obtained local binary pattern histogram into a pre-trained classification model for classification detection to obtain a detection result; and performing face image recognition according to the detection result. According to the method, the efficiency and accuracy of face recognition can be improved, and face recognition spoofing attacks are prevented.
Owner:PING AN TECH (SHENZHEN) CO LTD
Face recognition method and device, computer equipment and storage medium
PendingCN110084135AImprove efficiencyImprove accuracyCharacter and pattern recognitionLocal binary pattern histogramSpoofing attack
The invention relates to the technical field of biological recognition, and is used for face recognition. The invention particularly discloses a face recognition method and device, computer equipmentand a storage medium. The method comprises the steps of acquiring a to-be-detected image; performing color space conversion on the to-be-detected image to obtain a target image corresponding to the to-be-detected image in a preset color space; extracting a local binary pattern characteristic value of the target image, and performing histogram statistics according to the local binary pattern characteristic value to obtain a local binary pattern histogram; inputting the obtained local binary pattern histogram into a pre-trained classification model for classification detection to obtain a classification result; and performing face image recognition according to the classification result. According to the method, the efficiency and accuracy of face recognition can be improved, and face recognition spoofing attacks are prevented.
Owner:PING AN TECH (SHENZHEN) CO LTD
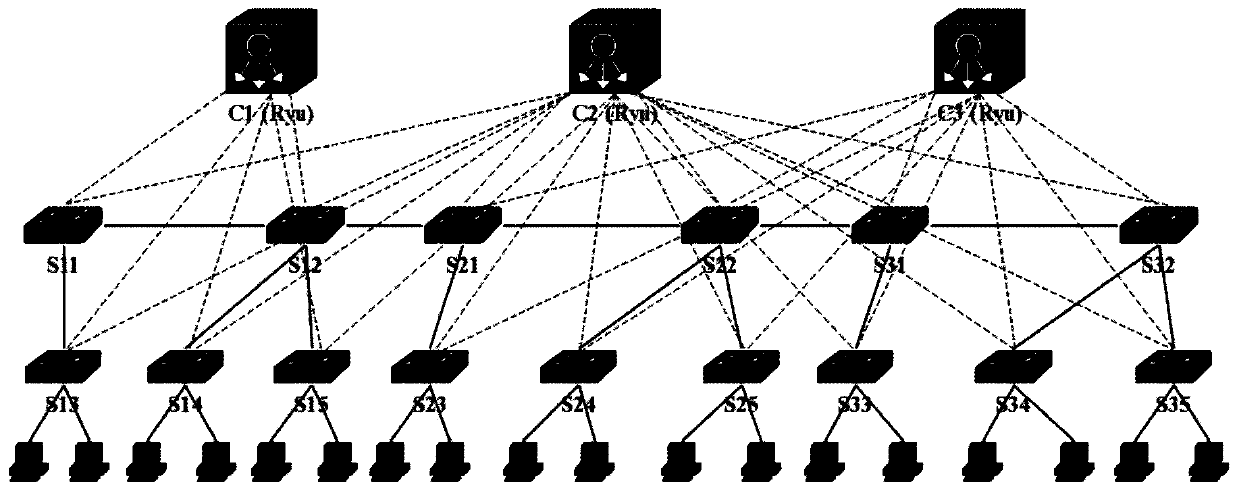
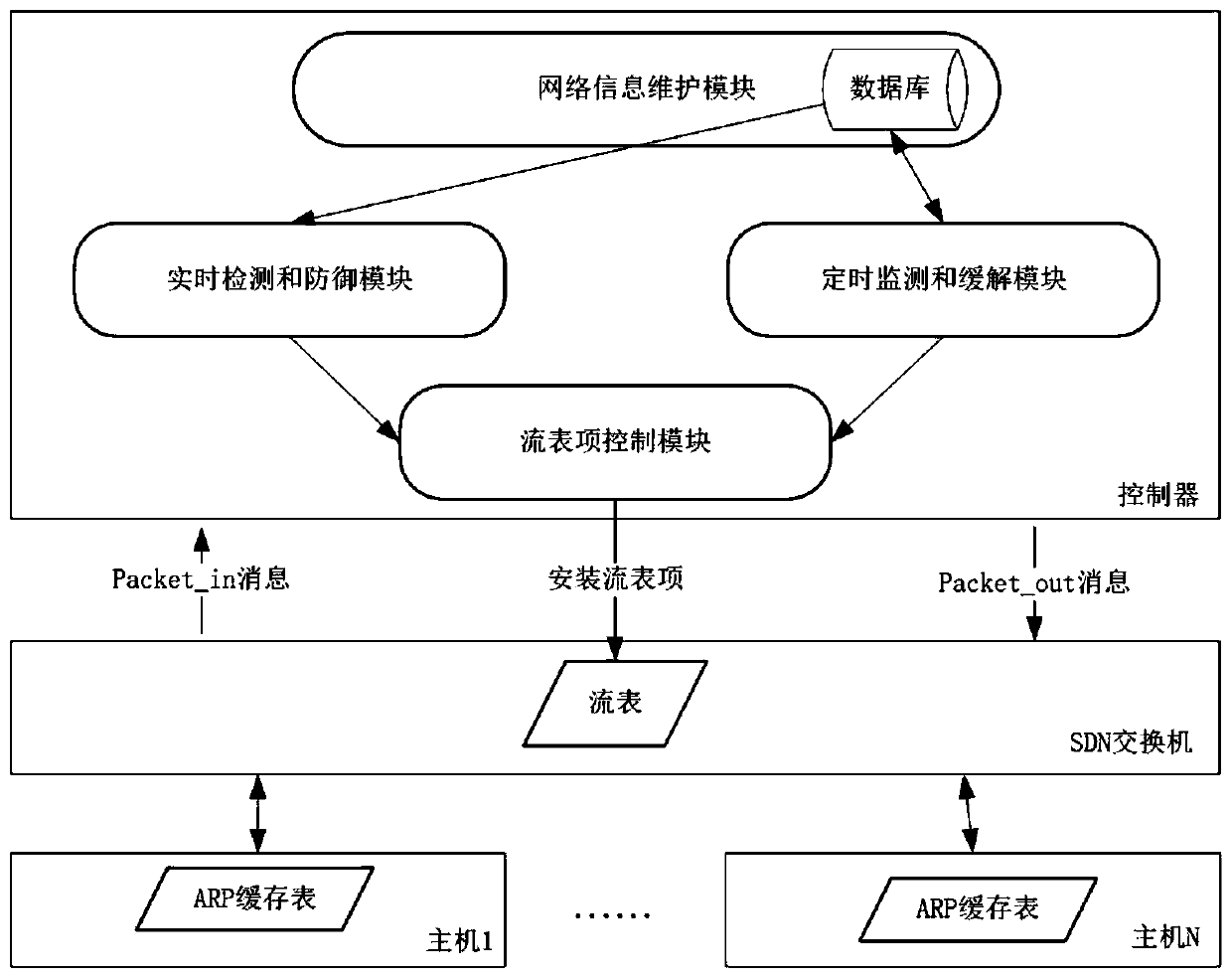
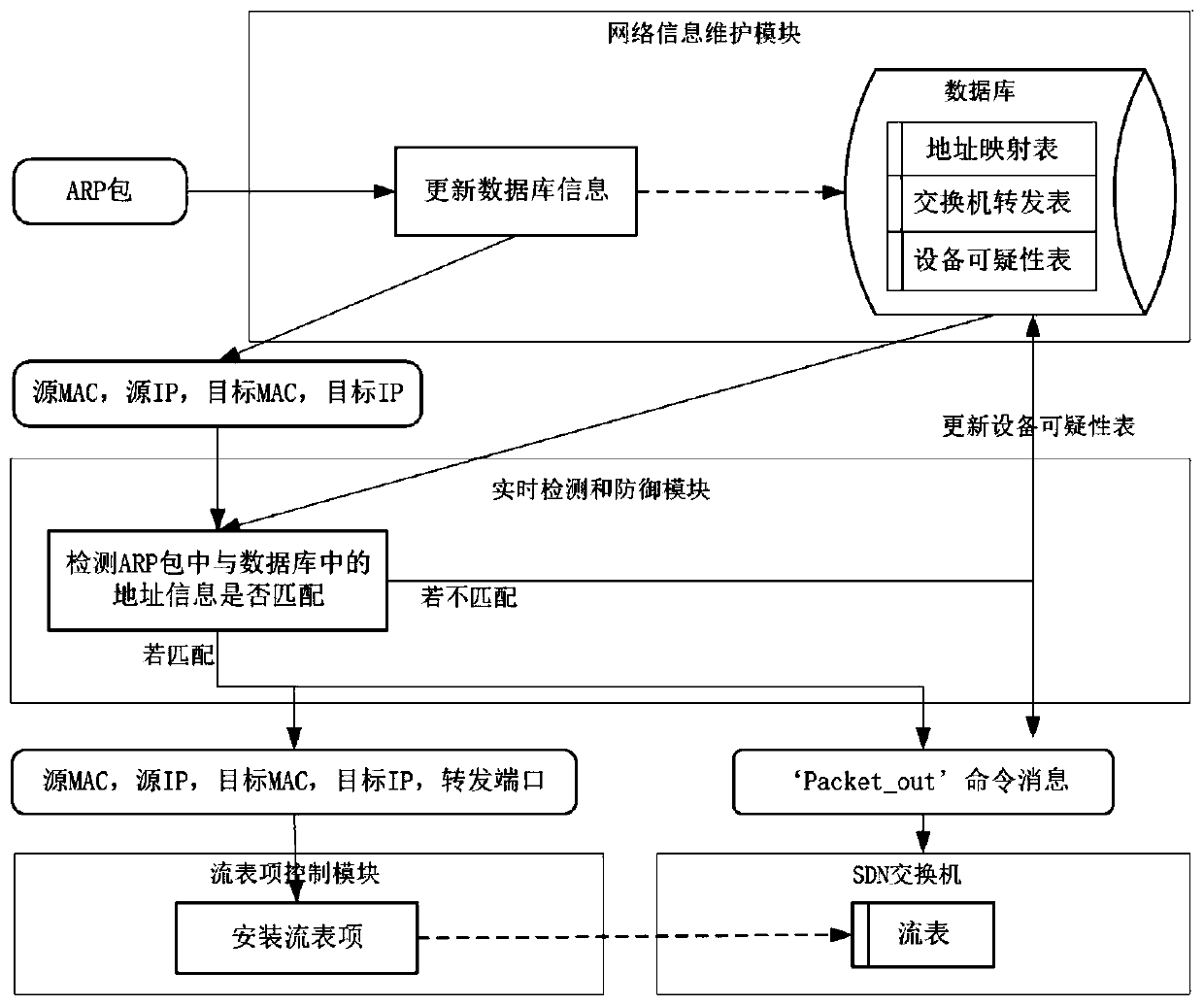
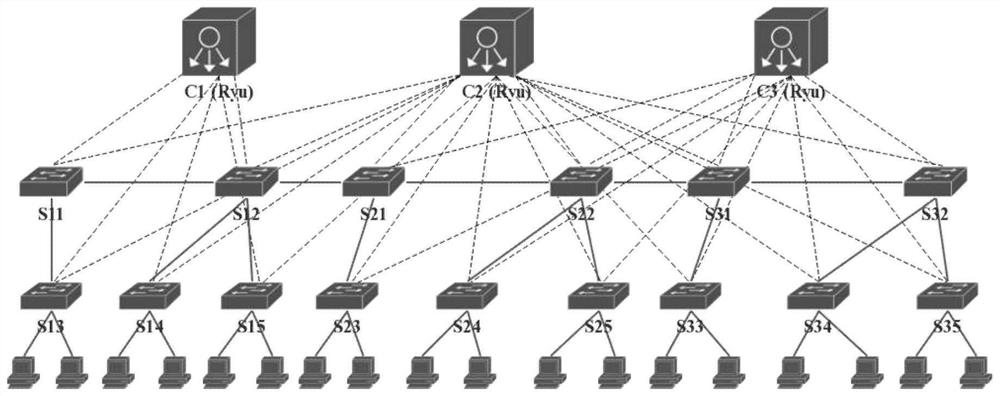
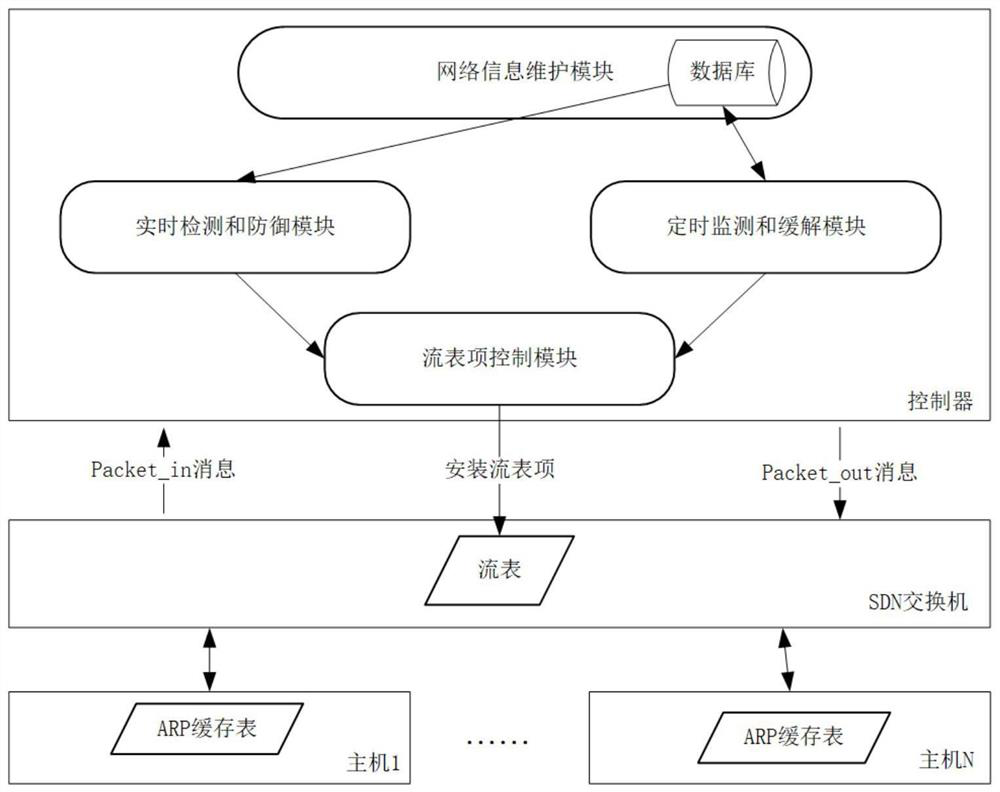
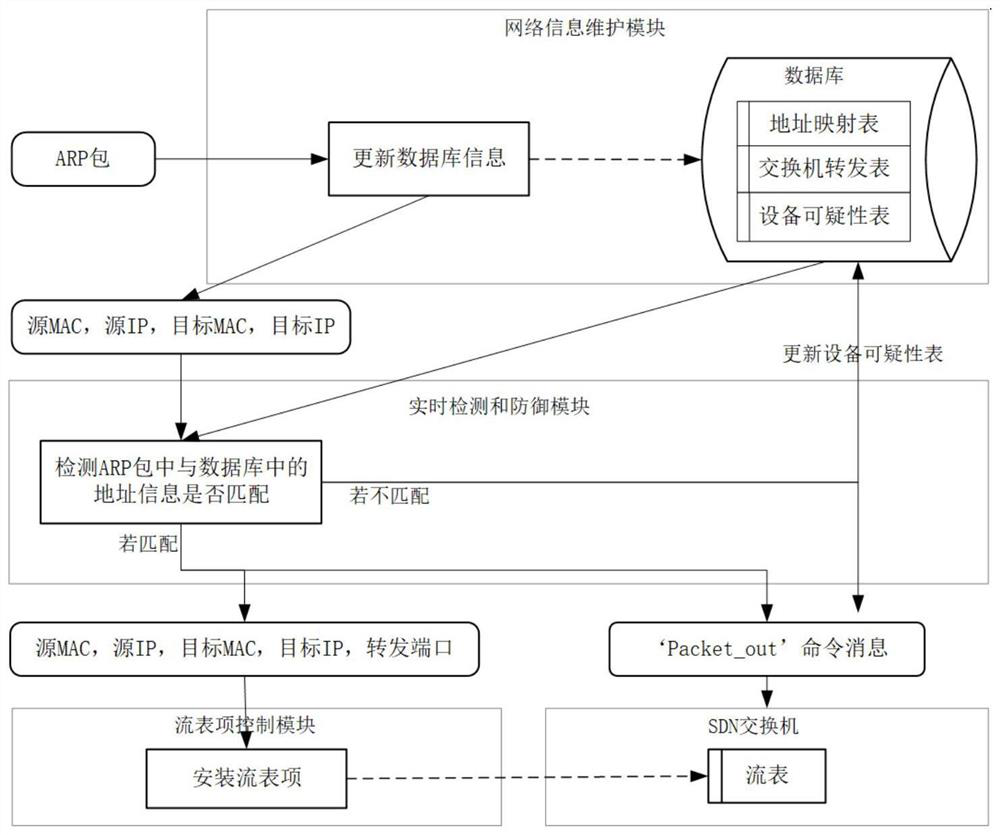
System and method for detecting and relieving ARP attacks based on SDN cloud environment
The invention provides a system and method for detecting and relieving ARP attacks based on an SDN cloud environment. The system comprises a network information maintenance module, a real-time detection and defense module, a timing monitoring and relieving module and a flow table item control module. The method comprises a starting stage; acquiring network information; detecting and defending an ARP attack stage in real time; and regularly monitoring and relieving an ARP attack stage. SDN technology is used in the invention, an ARP request packet and an ARP reply packet are detected; ARP spoofing attacks are detected in real time by analyzing ARP packets; a forged packet is discarded to prevent damage of ARP spoofing attack to the host; in addition, ARP storm attacks can be distinguished by regularly acquiring ARP flow and detecting flow statistical data of ports of the edge SDN switch, the flow of the corresponding ports can be timely blocked, the influence of the ARP storm attacks on the cloud network is relieved, and the security of the cloud computing network is comprehensively protected.
Owner:NANJING UNIV
Network security method based on wireless firewall
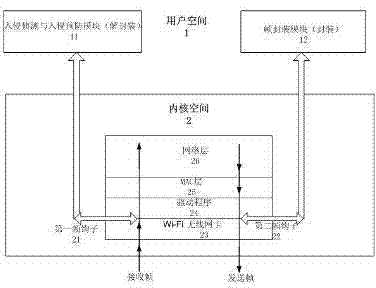
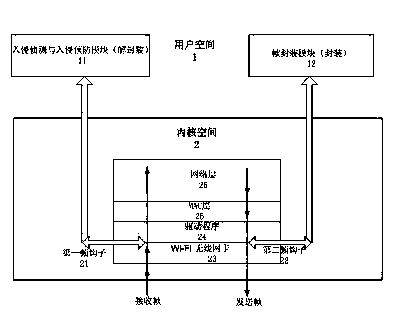
InactiveCN102378166AIncrease aggressivenessImprove usabilitySecurity arrangementOperational systemIntrusion detection and prevention
The invention relates to a network security method based on a wireless firewall. In the method, the wireless firewall acts on an MAC (Media Access Control) layer of OSI (Open System Interconnection) and comprises an intrusion detection and prevention module, a first frame hook and a second frame hook, wherein, the intrusion detection and prevention module is positioned in a user space of a system; the first frame hook is connected with a kernel space and the user space of the operating system, one end of the first frame hook is arranged in a wireless LAN (local area network) card driver in the kernel space of the operating system, the other end of the first frame hook is arranged in the user space and is connected with the intrusion detection and prevention module, the first frame hook transfers a frame received by the wireless LAN card driver to the intrusion detection and prevention module, and then the frame is sent back to the driver through the frame hook or is deleted after being processed by the module; and one end of the second frame hook is arranged in the wireless LAN card driver in the kernel space of the operating system, and the other end of the second frame hook is arranged in the user space and is connected with a frame encapsulation module. By adopting the network security method, the hacker attack resistance can be strengthened and the availability of the wireless network is improved.
Owner:周伯生
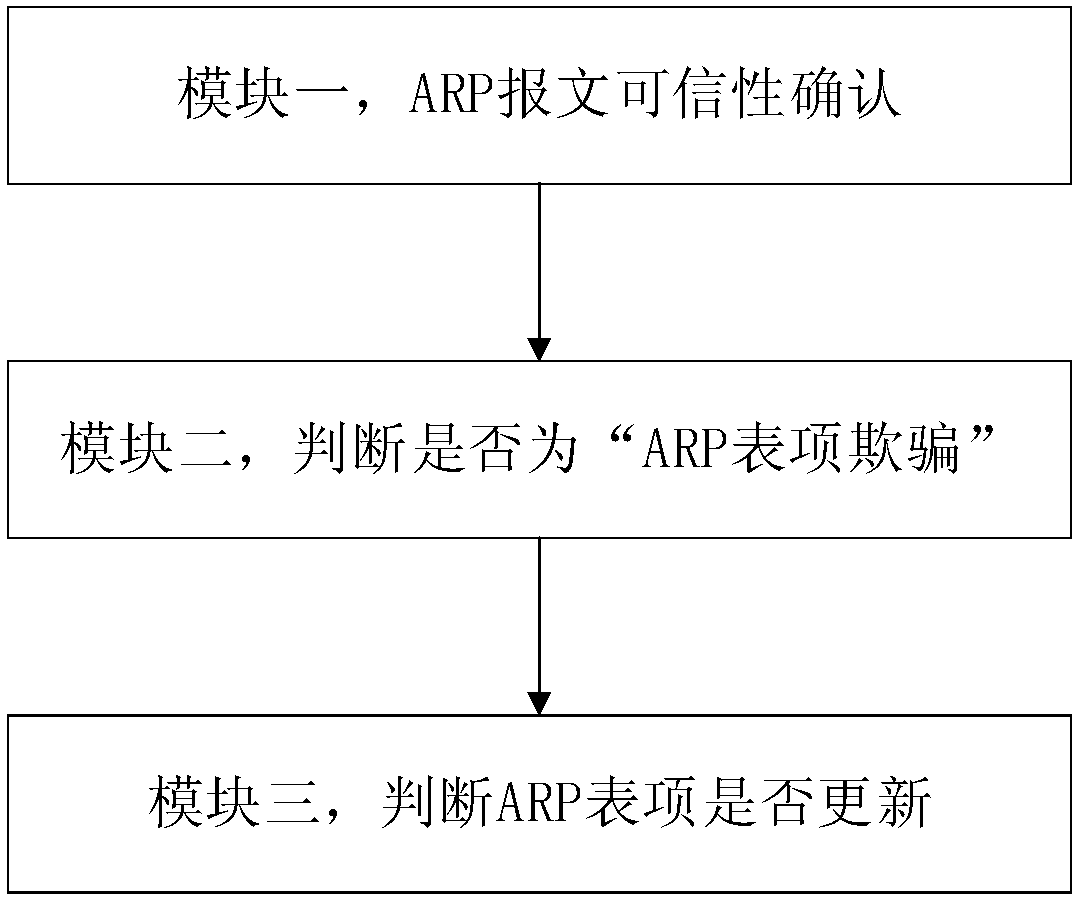
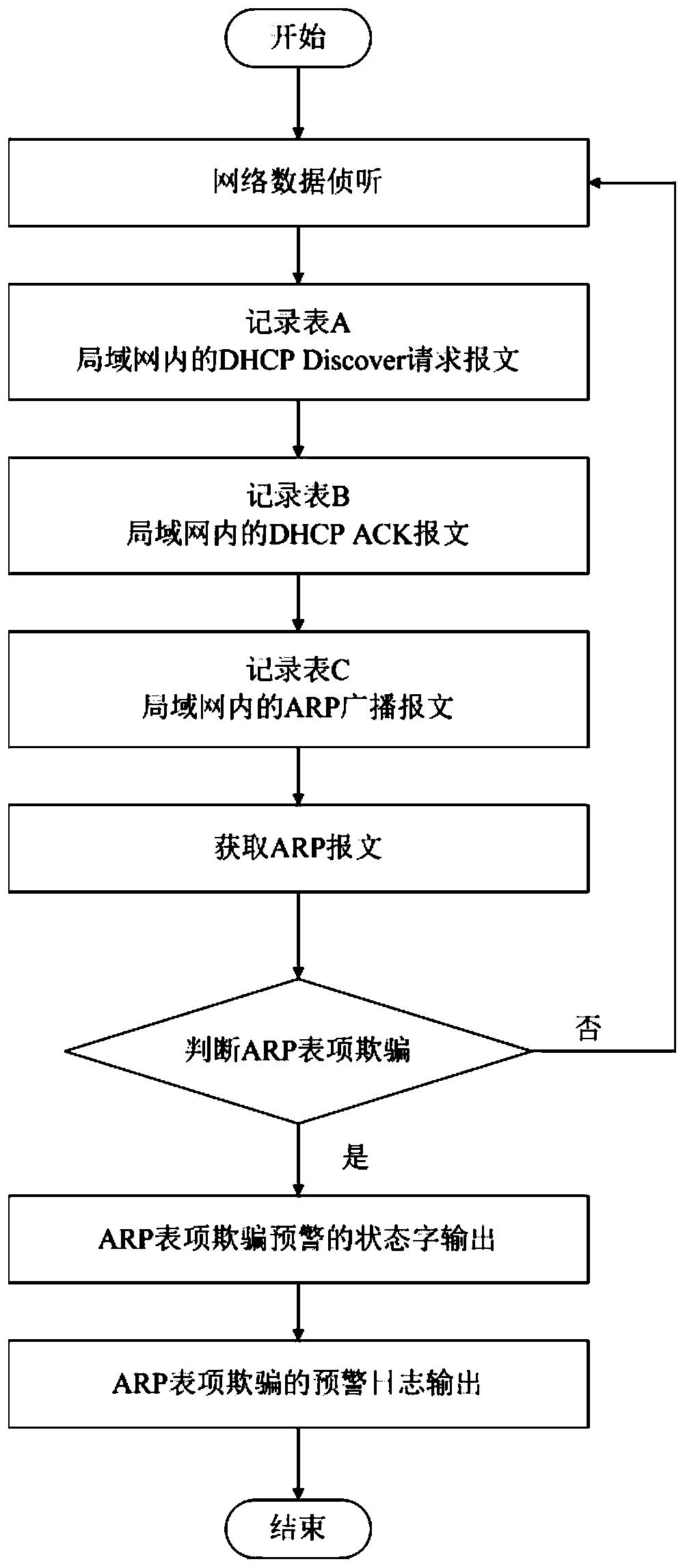
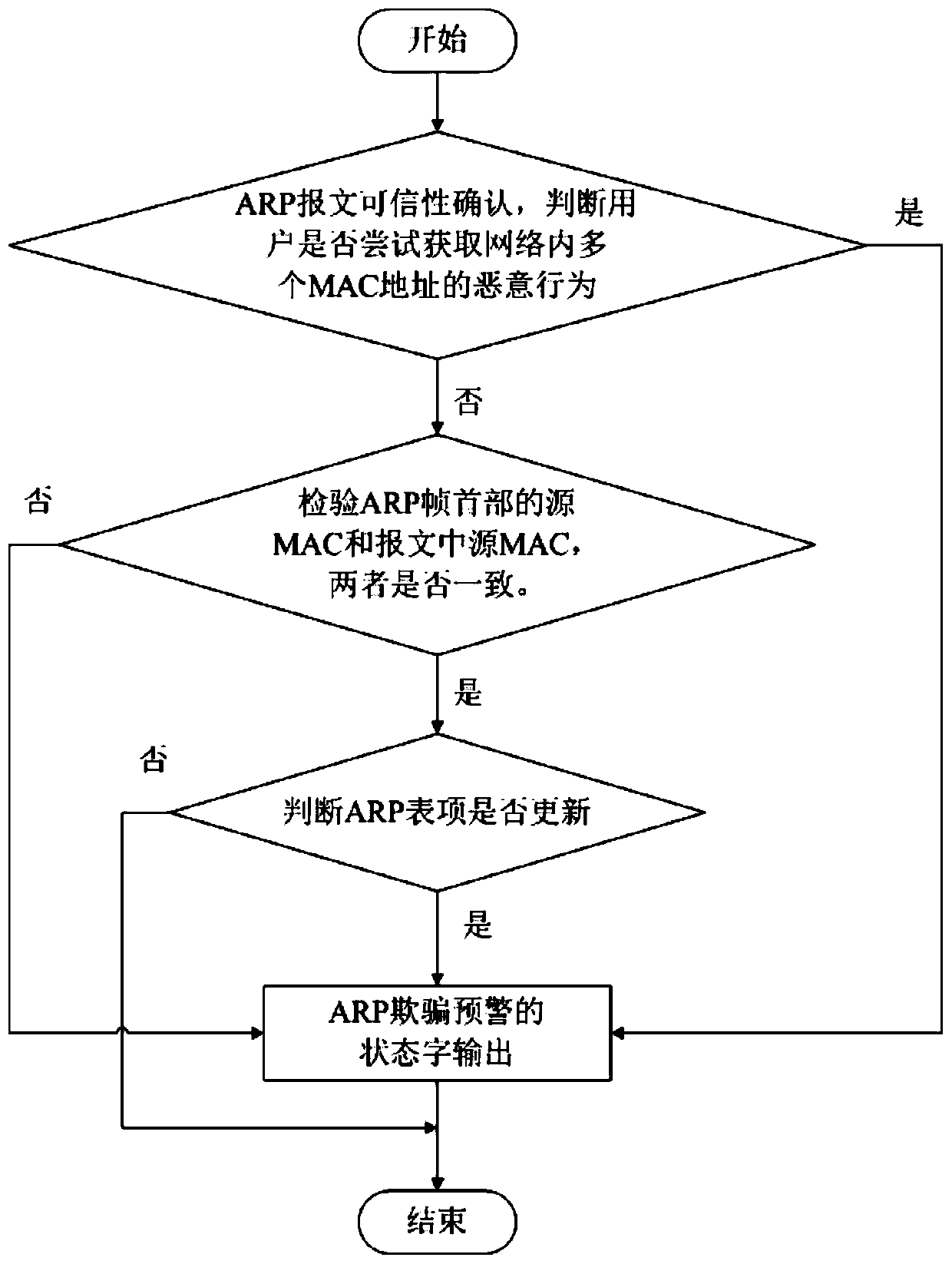
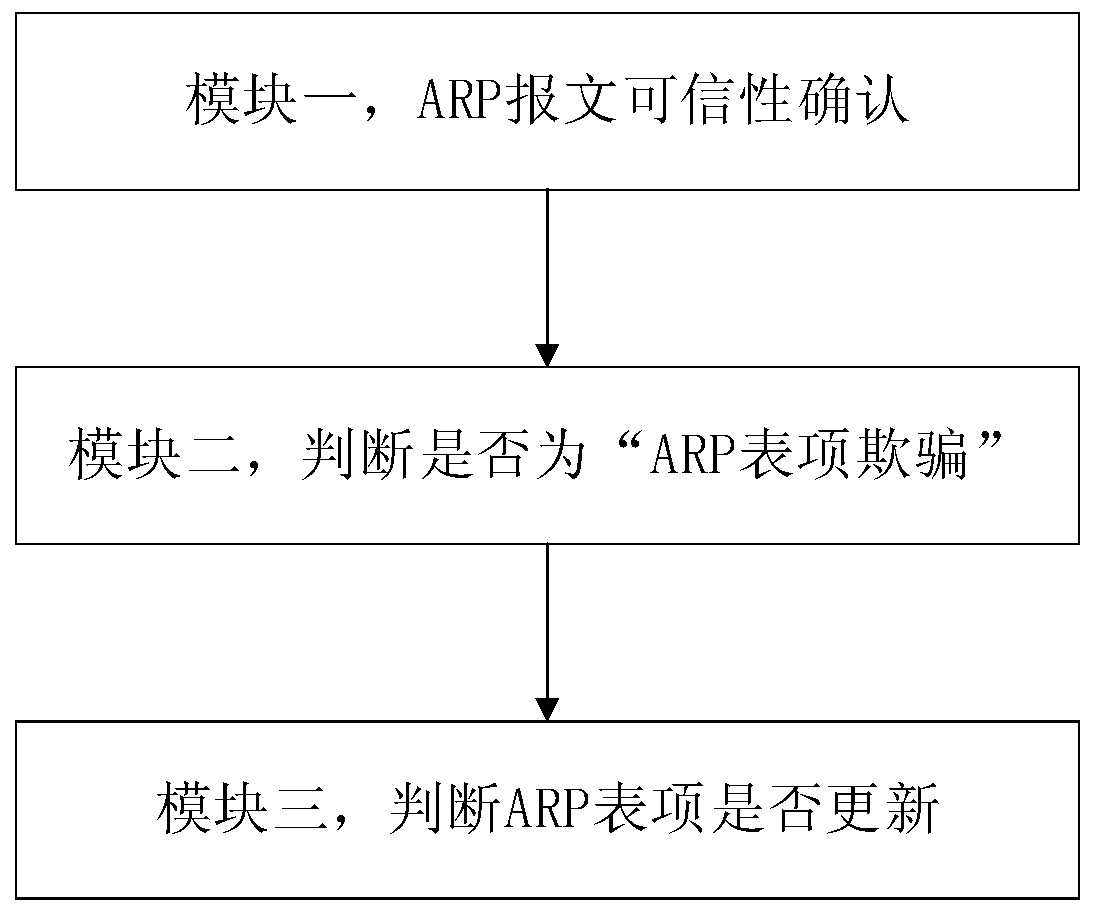
Early warning method and device for ARP table entry spoofing attack in local area network
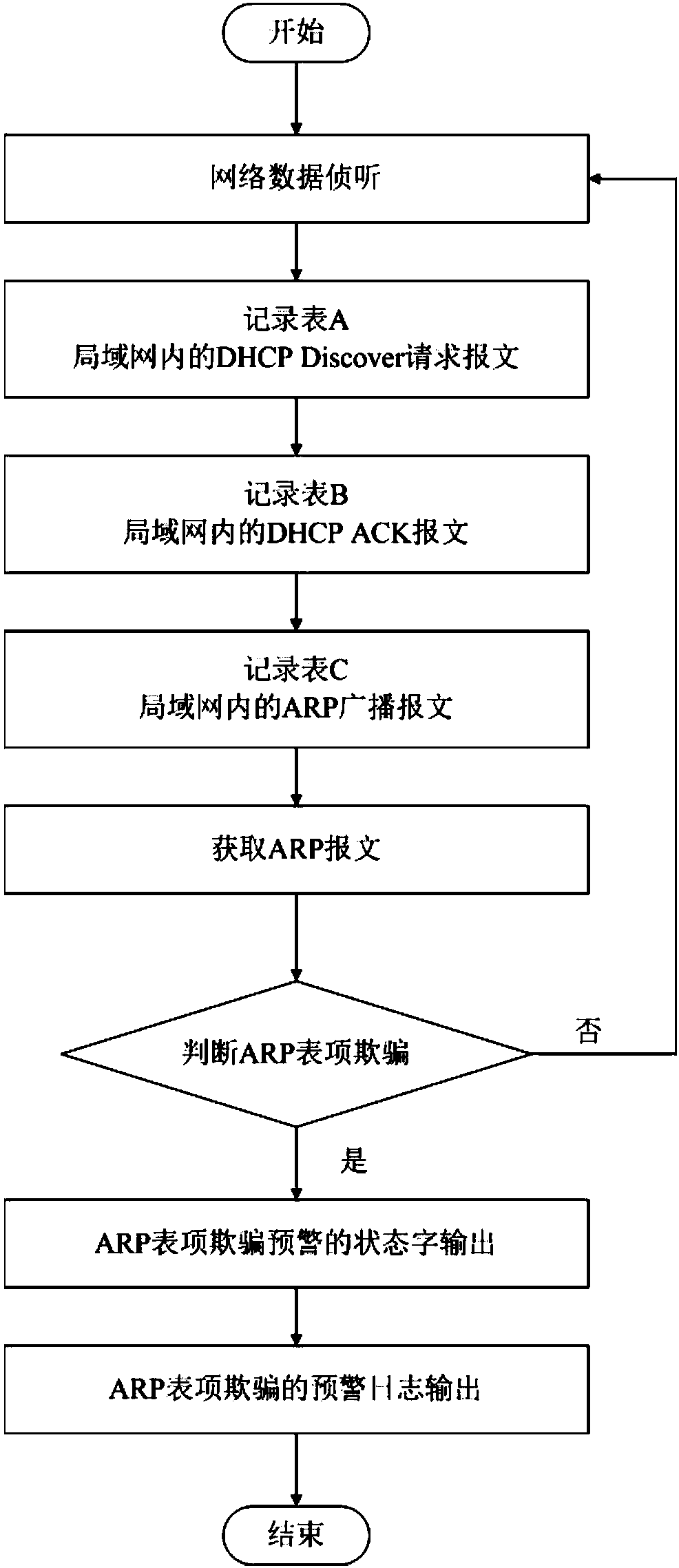
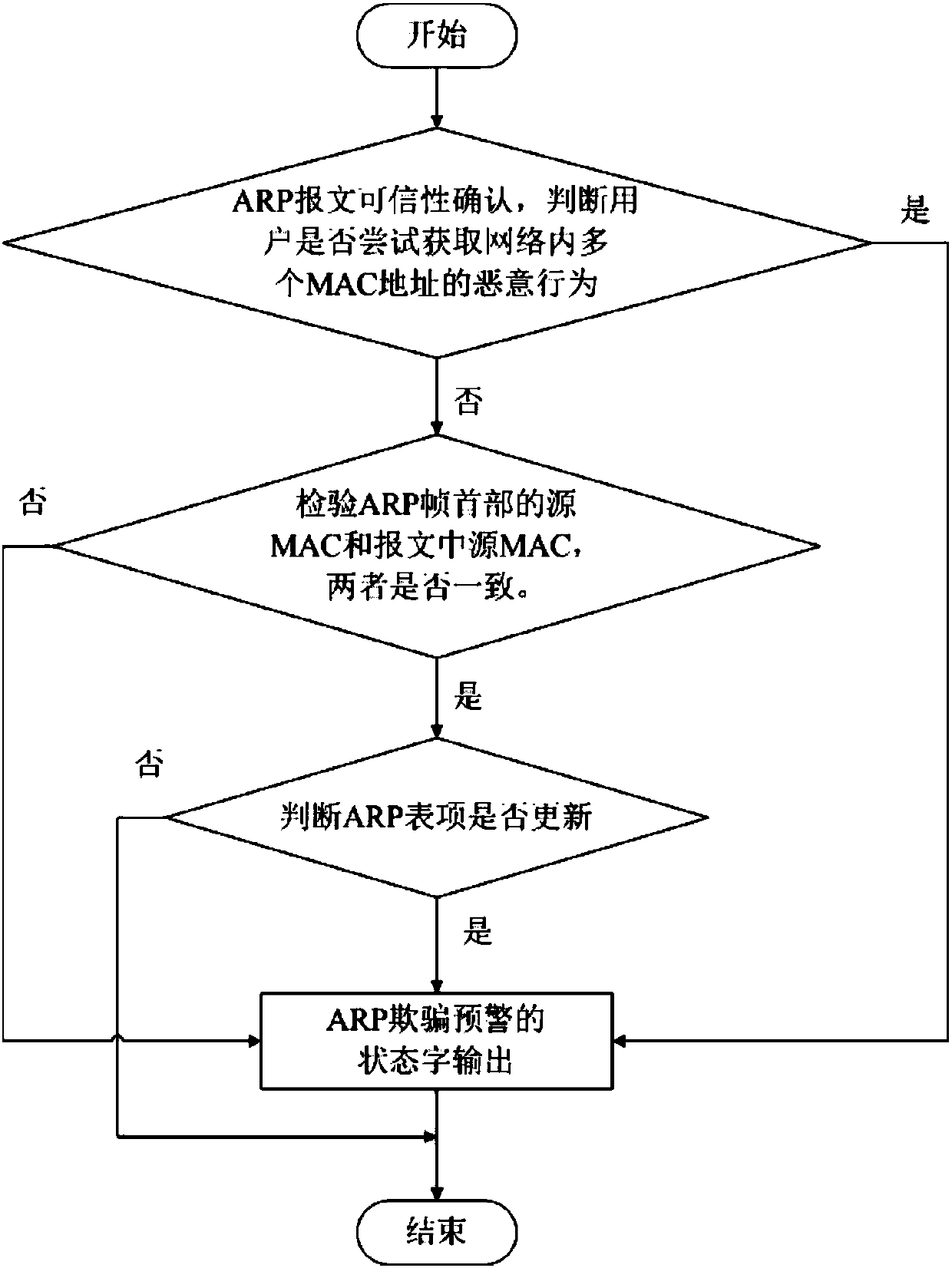
ActiveCN107786496APrevent spoofing attacksTransmissionAddress Resolution ProtocolNetwork communication
The invention provides an early warning method and device for an address resolution protocol (ARP) table entry spoofing attack in a local area network, and belongs to the technical field of network communication. The early warning problem of the ARP table entry spoofing attack in the local area network is solved. The technical points are as follows: S1. monitoring network data; S2. confirming thecredibility of an ARP message; S2.1. when the ARP message is not credible, performing early warning judgment on ARP table entry spoofing; and S2.2. when the ARP message is credible, performing analysis on an ARP message table entry to judge the ARP table entry spoofing. The early warning method and device have the beneficial effects that the ARP table entry spoofing attack can be prevented.
Owner:DALIAN ROILAND SCI & TECH CO LTD
Method for preventing LAN from cheat aggressing by address analysis protocol
The invention relates to a network security maintenance method of a local area network, in particular to a method for preventing the local area network from being attacked by address resolution protocol spoofing. The method solves and prevents the address resolution protocol spoofing by adopting bidirectional binding. The method comprises the following steps of: binding the IP of a security gateway and an MAC address on a PC; and binding the IP of a user host and the MAC address on the security gateway. The method can guarantee the smoothness and safety in using the network and the facilities in the network.
Owner:SHANGHAI MINHANG HIGH SCHOOL +1
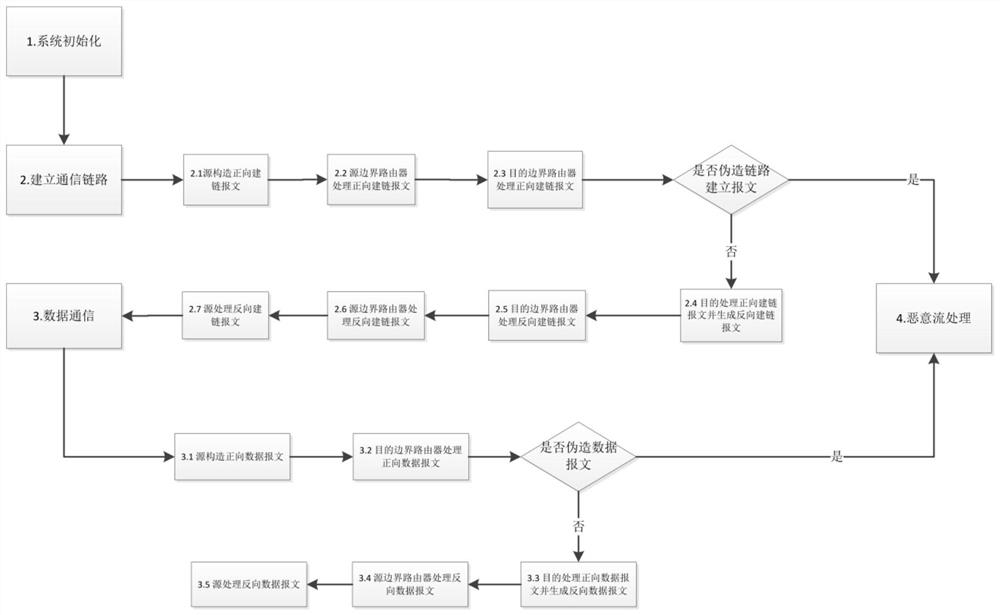
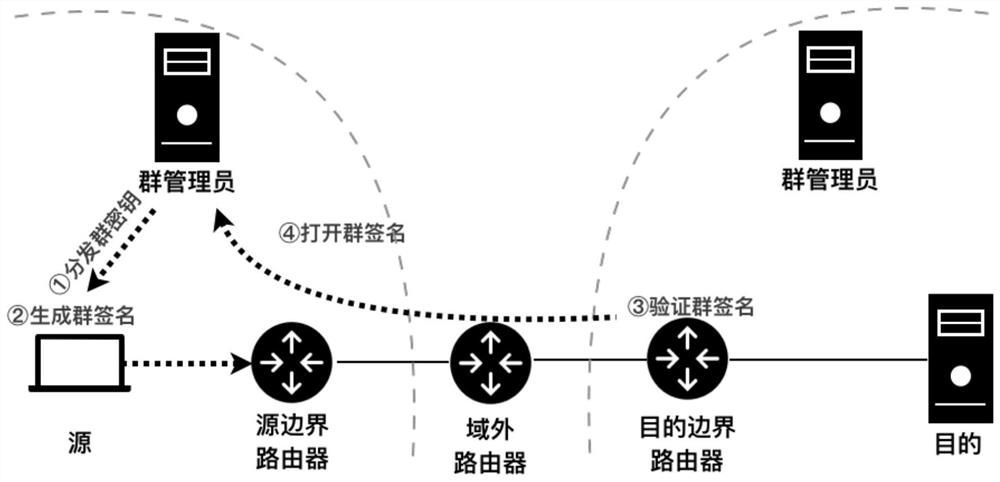
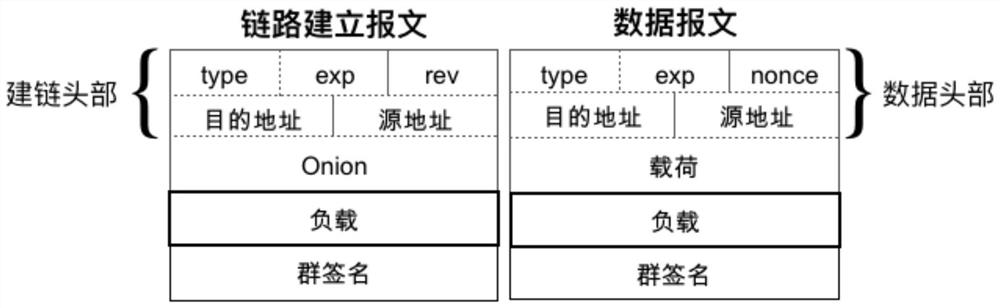
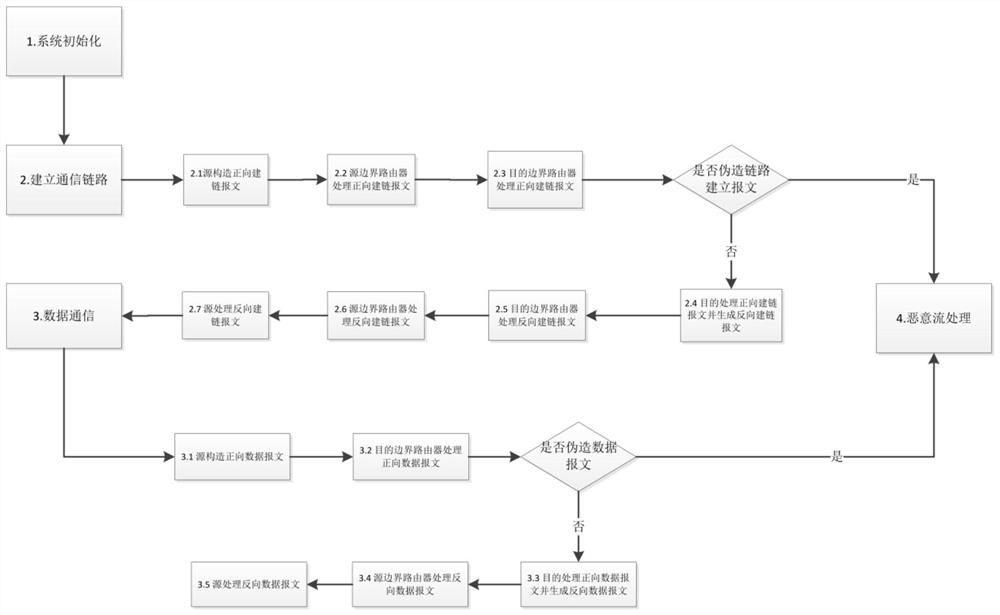
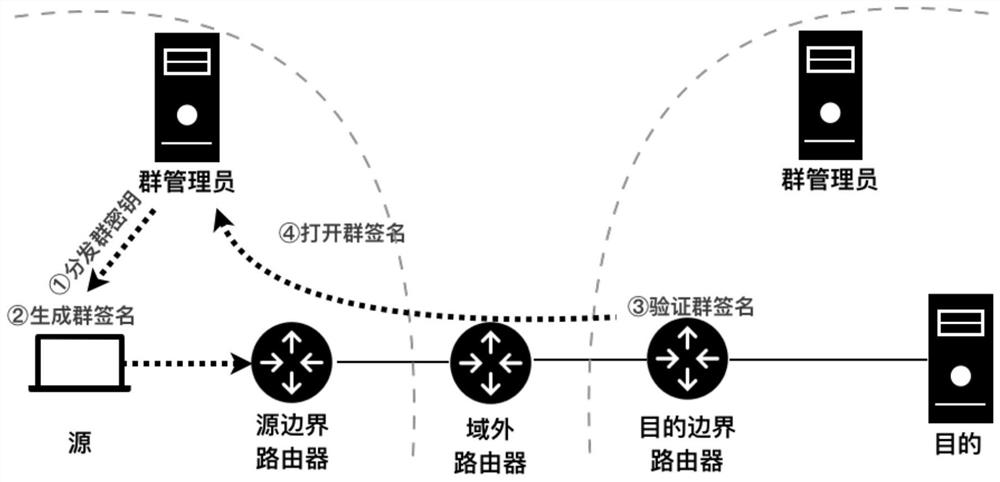
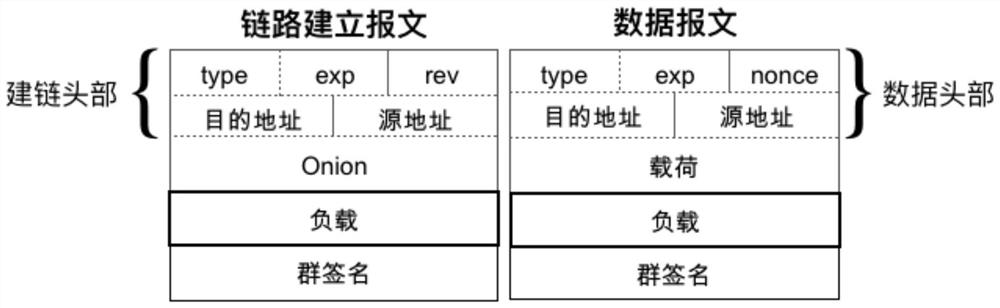
Routing method with metadata privacy protection and source responsibility investigation capabilities
ActiveCN111884816AImprove protectionPrevent spoofing attacksKey distribution for secure communicationUser identity/authority verificationPathPingPrivacy protection
The invention belongs to the technical field of computer network security, and relates to an efficient routing protocol for simultaneously providing anonymity and responsibility investigation capability in a network layer, in particular to a routing method with metadata privacy protection and source responsibility investigation capabilities. According to the method of the invention, a group signature is attached to a message network layer to realize the balance between anonymity and responsibility. The group signature in the message can provide wide and efficient responsibility investigation,and the authenticity of the message can be verified by any router on a path in a non-interaction mode, so that the communication overhead during message verification is eliminated. Meanwhile, the privacy of the sender is protected by the group signature, so that the signer in the group cannot be distinguished by entities outside the group. In addition, in order to further reduce the verification overhead of the group signature, a challenge-based separation verification mechanism is designed. Compared with pre-calculation and batch verification, the separate verification mechanism can reduce the verification load of the specified router to a greater extent, thereby improving the efficiency of the protocol.
Owner:NAT UNIV OF DEFENSE TECH
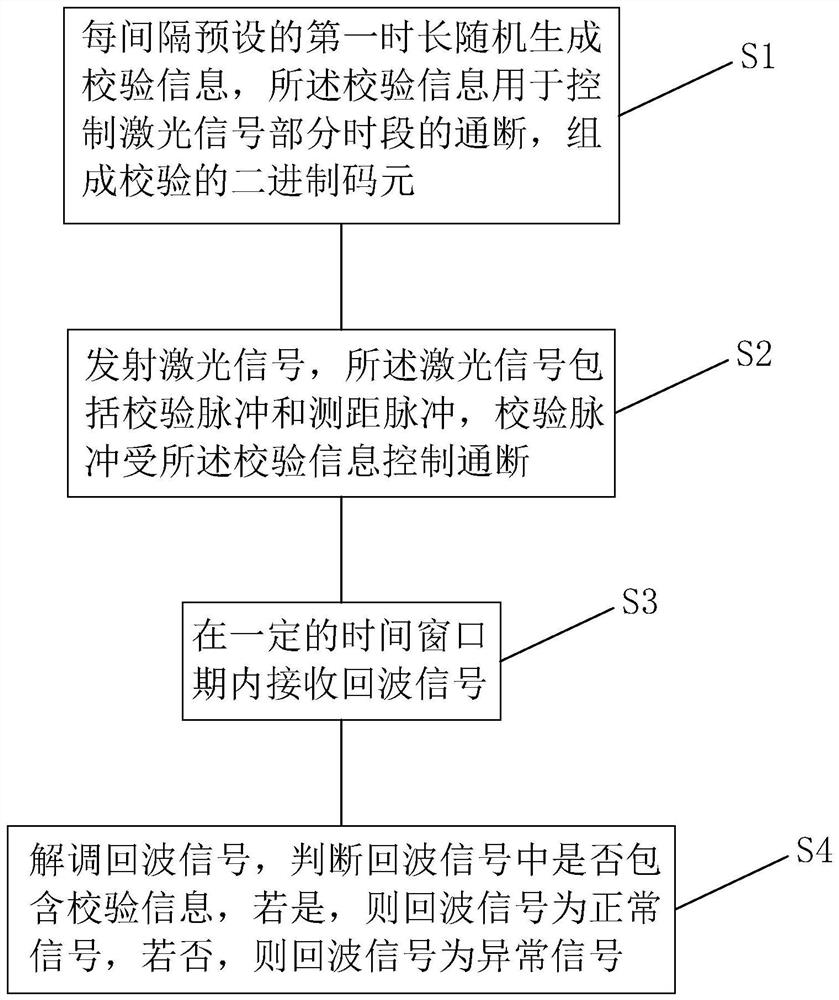
Laser radar multi-machine crosstalk prevention method and device, and storage medium
PendingCN113805191AOptimal Decision PortfolioPrevent Crosstalk ErrorsElectromagnetic wave reradiationMultiplexingInformation control
The invention relates to a laser radar multi-machine crosstalk prevention method and device, and a storage medium. The method comprises the following steps: randomly generating verification information every preset first time length, wherein the verification information is used for controlling the on-off of a laser signal in a partial time period; emitting the laser signal, wherein the laser signal comprises a verification pulse and a distance measurement pulse, and on-off of the verification pulse is controlled according to the verification information; receiving an echo signal; demodulating the echo signal, determining whether the echo signal contains verification information, if so, determining that the echo signal is a normal signal, and if not, determining that the echo signal is an abnormal signal; and according to a verification result, carrying out scanning order decision and skipping. The method is composed of a dynamic verification technology and a space-time jump multiplexing technology, and the method aims at achieving the best balance between the radar scanning rate and the detection accuracy under the multi-machine coexistence condition.
Owner:LIANG PING
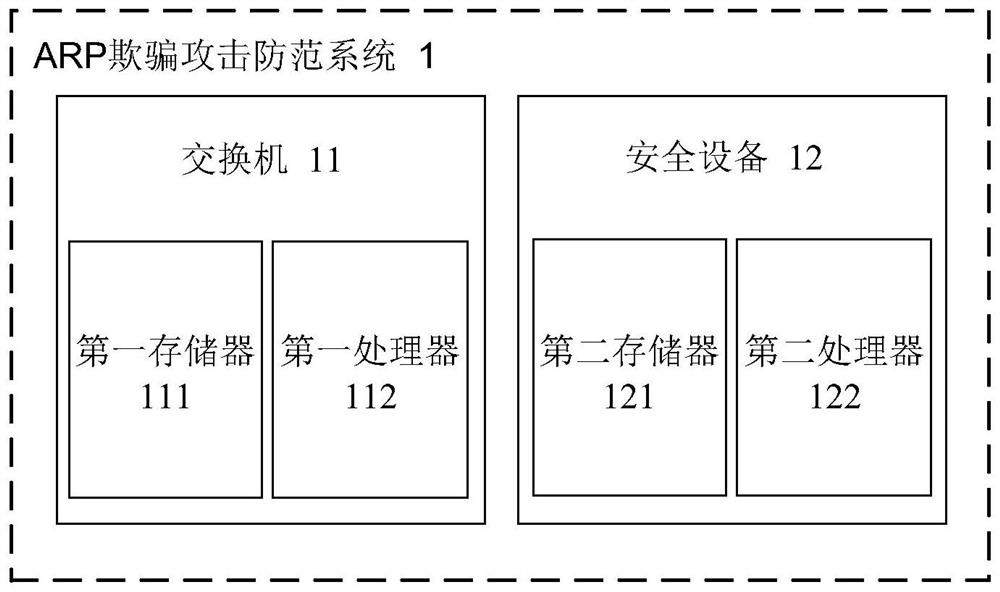
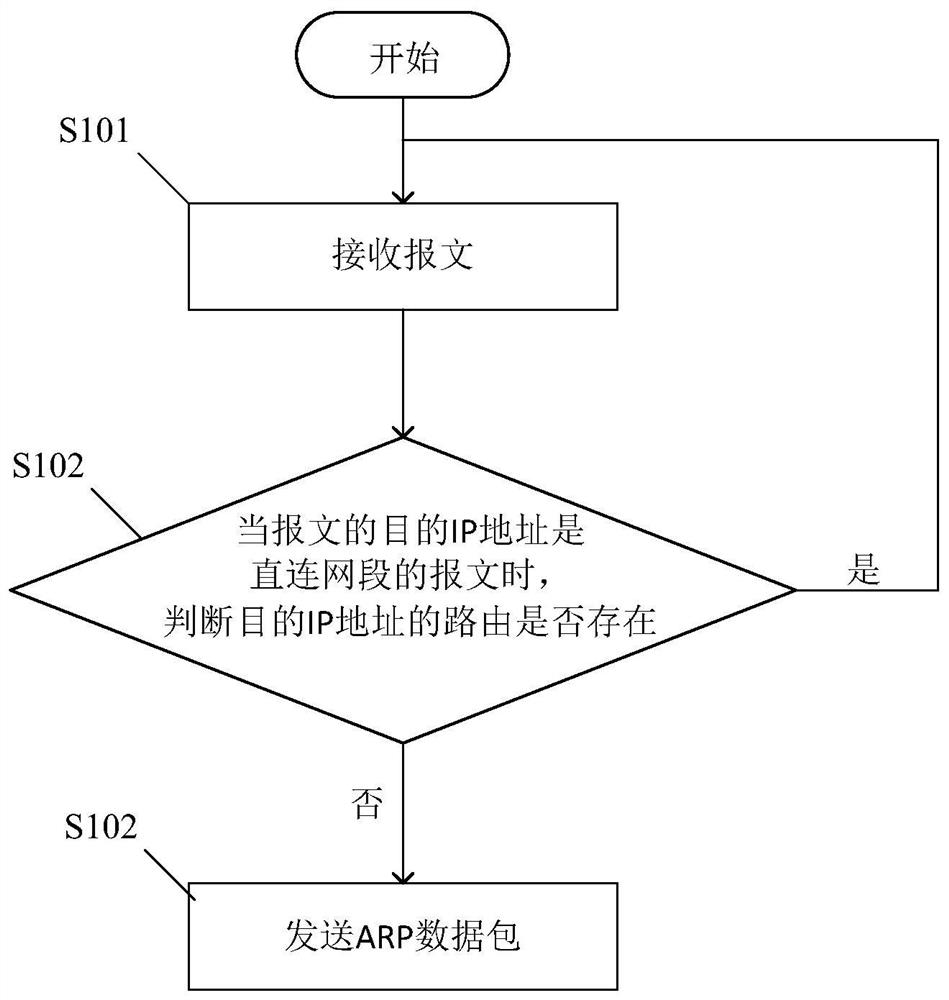
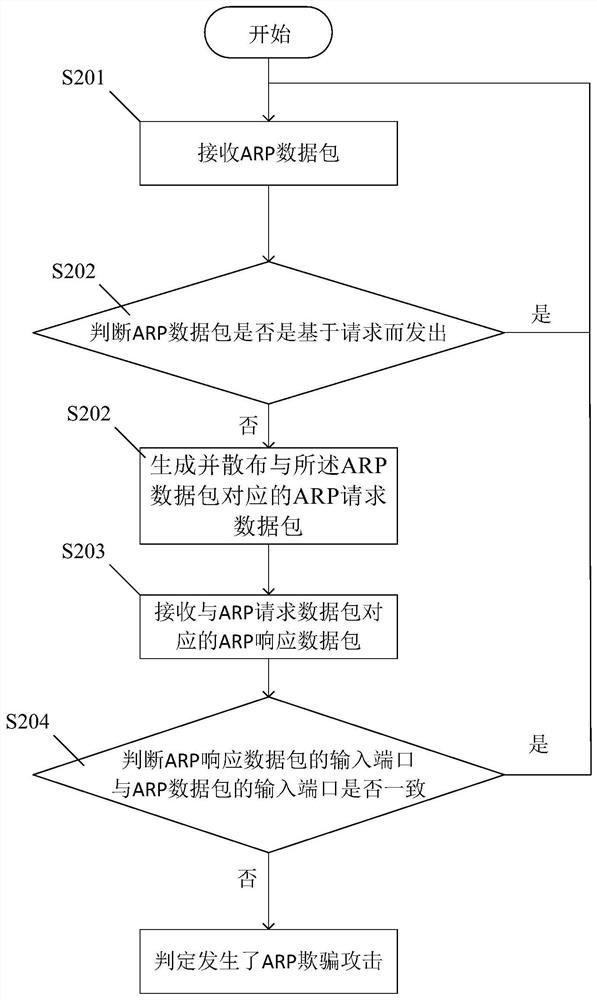
ARP spoofing attack prevention method and system
The invention provides an ARP spoofing attack prevention method. The ARP spoofing attack prevention method comprises the following steps executed on a switch: receiving a message; when the destination IP address of the message is the message of the direct network segment, judging whether a route of the destination IP address exists, and when the route does not exist, sending an ARP data packet. The security device executes the following steps: receiving the ARP data packet; judging whether the ARP data packet is sent based on a request, and if not, generating and distributing an ARP request data packet corresponding to the ARP data packet; receiving an ARP response data packet corresponding to the ARP request data packet; and judging whether the input port of the ARP response data packet is consistent with the input port of the ARP data packet: if not, judging that the ARP spoofing attack occurs.
Owner:AECC SHANGHAI COMML AIRCRAFT ENGINE MFG CO LTD
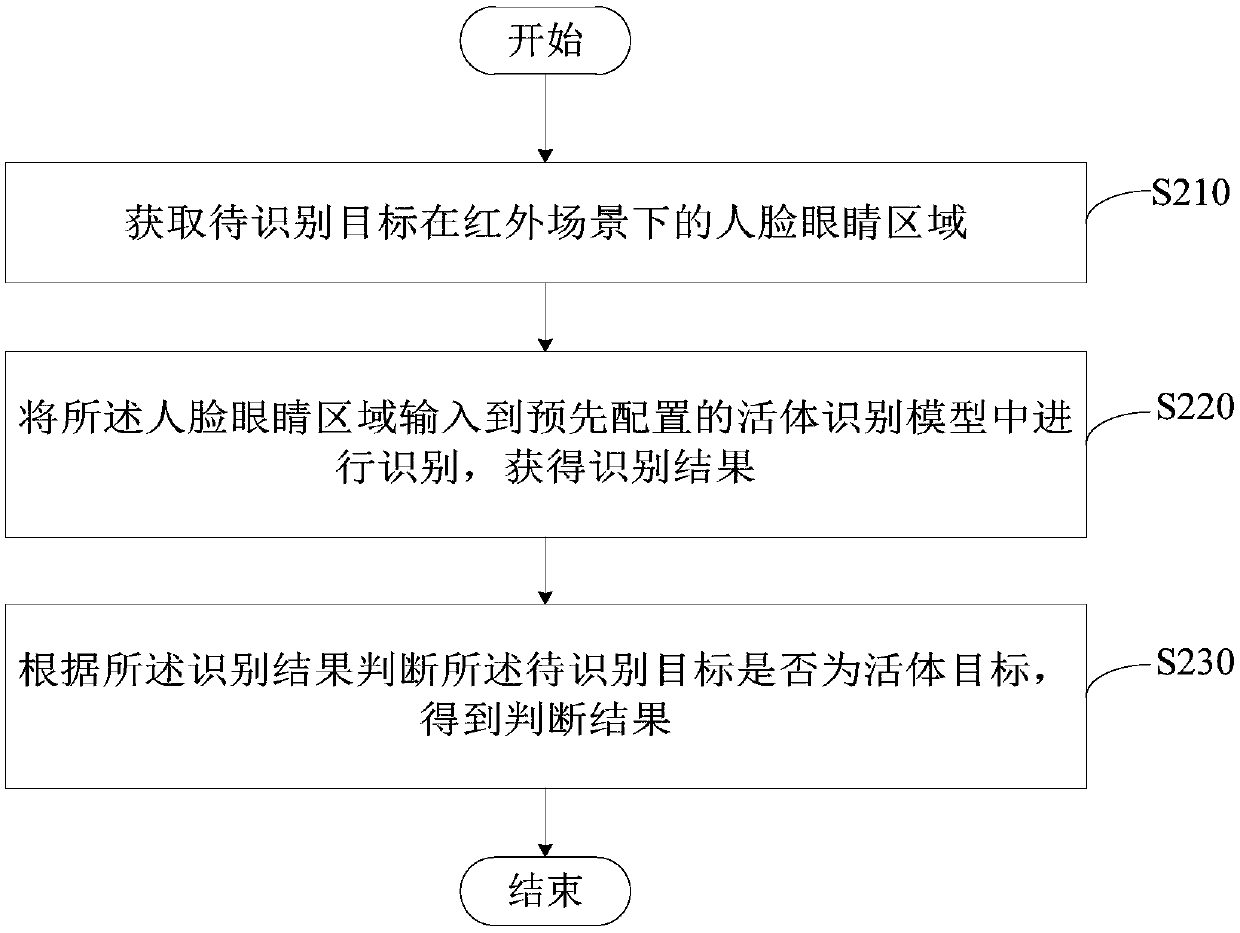
Living body judgment method and device
PendingCN110738072ASimple and efficient human face liveness judgmentAccurate identificationSpoof detectionComputer visionOphthalmology
The embodiment of the invention provides a living body judgment method and device. The method comprises the steps of obtaining a human face eye region of a to-be-recognized target in an infrared scene; inputting the human face eye area into a pre-configured living body recognition model for recognition to obtain a recognition result; and judging whether the to-be-identified target is a living bodytarget or not according to the identification result to obtain a judgment result. Therefore, the face living body judgment can be simply and efficiently carried out, so that the authenticity of the face is accurately distinguished, the security system is prevented from being attacked by lawbreakers through face duplication and spoofing, and the security in a security scene is further improved.
Owner:ZHEJIANG UNIVIEW TECH
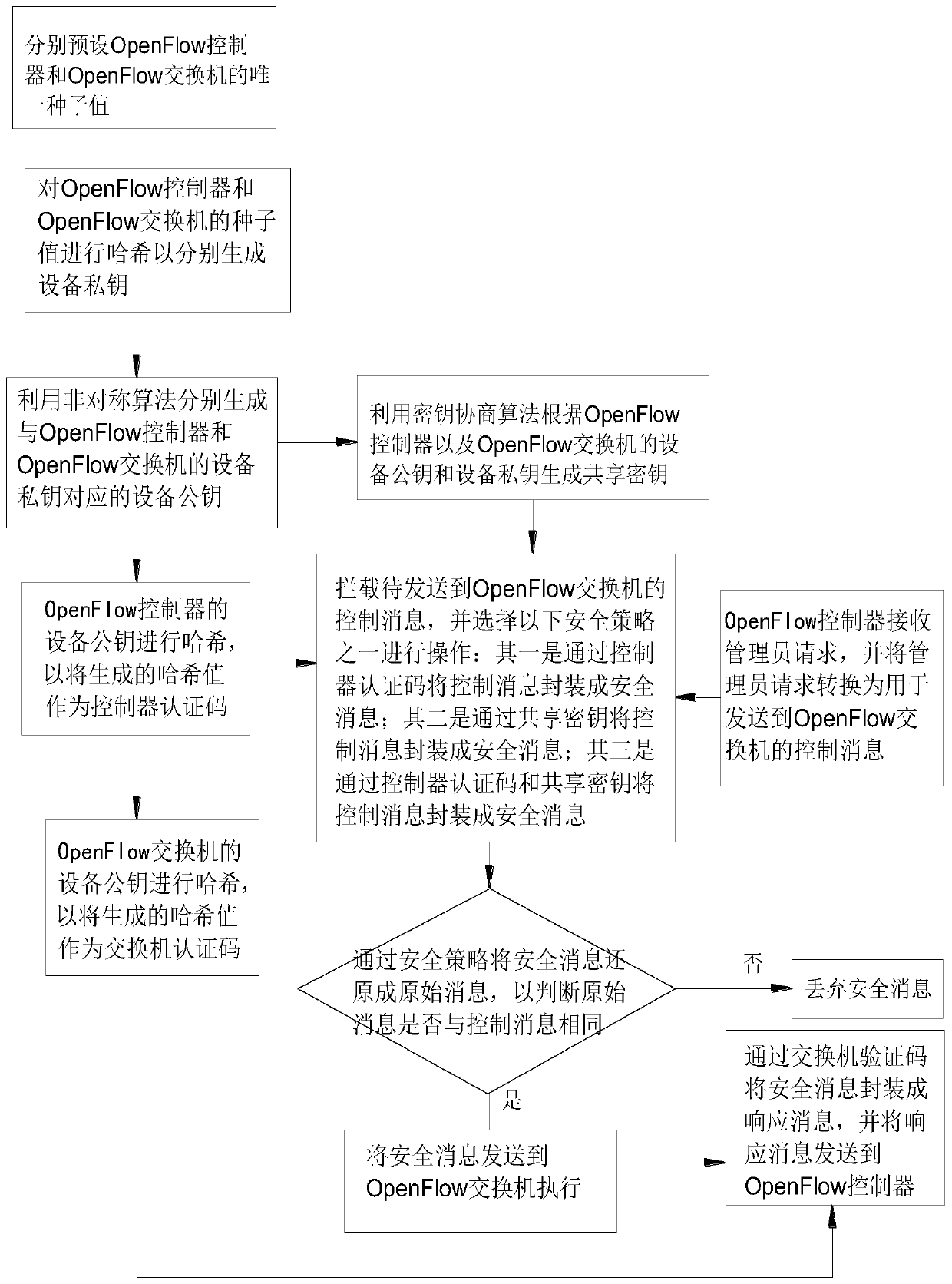
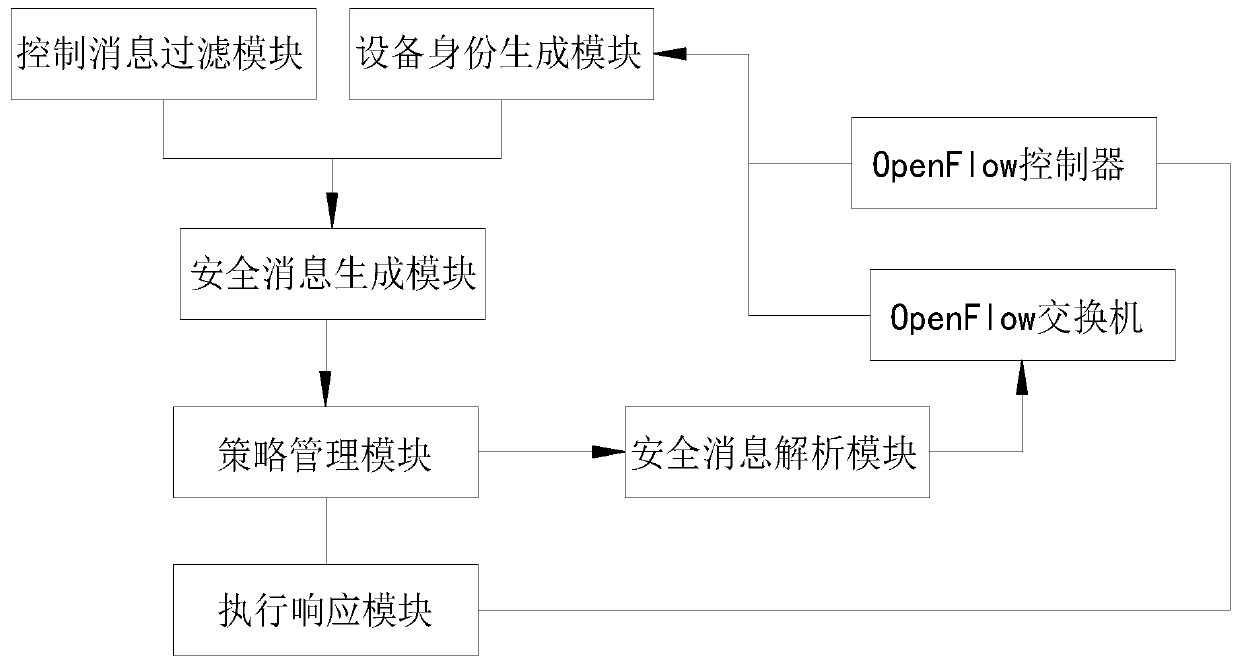
Lightweight control channel communication protection method and system in OpenFlow network
ActiveCN111404947AImprove securityEasy to useEncryption apparatus with shift registers/memoriesCommunications securityHash function
The invention provides a lightweight control channel communication protection method and system in an OpenFlow network, and relates to the field of communication. The lightweight control channel communication protection method in the OpenFlow network comprises the following steps: respectively presetting unique seed values for an OpenFlow controller and an OpenFlow switch; respectively hashing thetwo seed values to generate an equipment private key; enabling the two equipment private keys to respectively generate equipment public keys by using an asymmetric cryptographic algorithm; processingthe equipment public key of the OpenFlow controller by utilizing a hash function, and taking the generated hash value as a controller message authentication code for identifying the OpenFlow controller; and the OpenFlow controller and the equipment private key and the equipment public key of the OpenFlow switch generate a shared key through a key negotiation algorithm. According to the invention,the problems of low communication security and high energy consumption of the OpenFlow network are solved.
Owner:李子钦
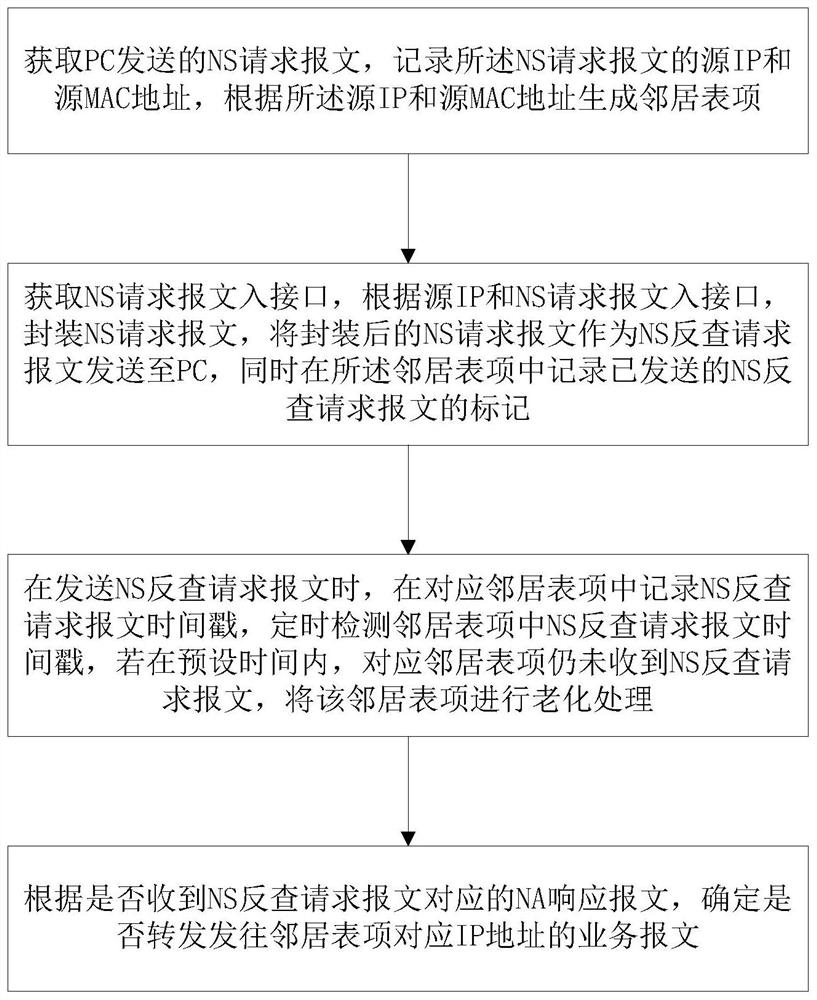
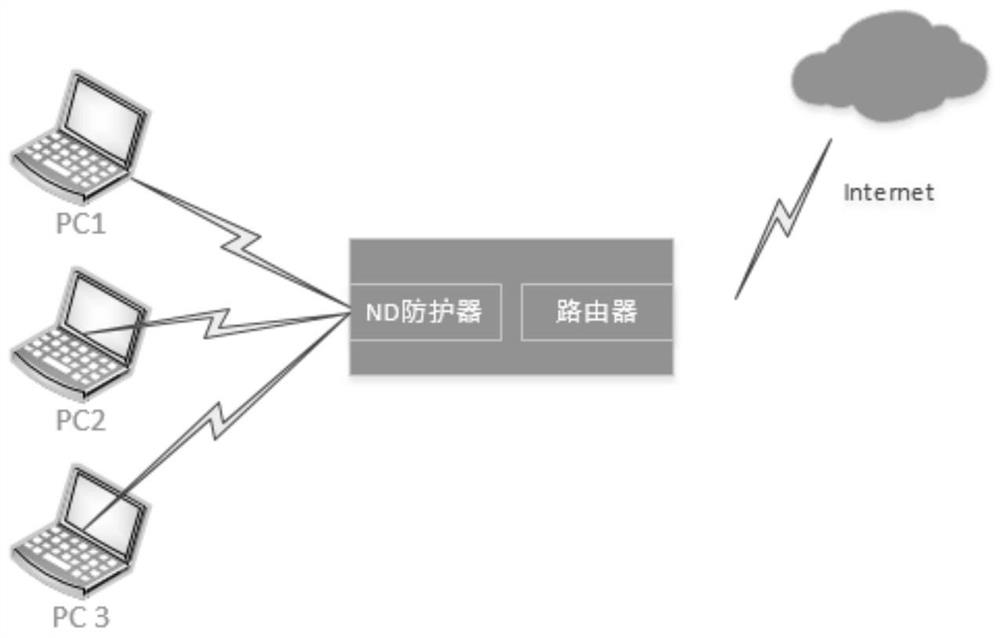
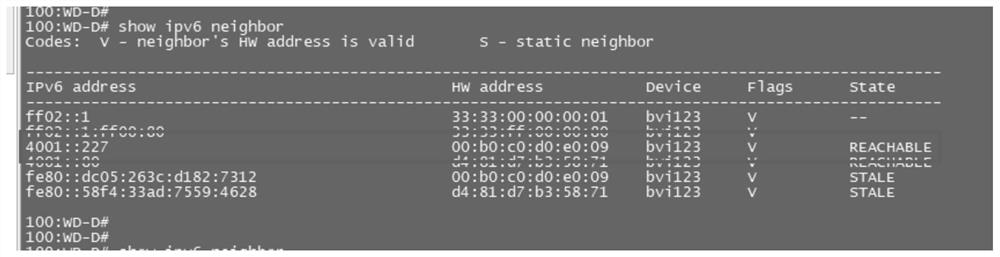
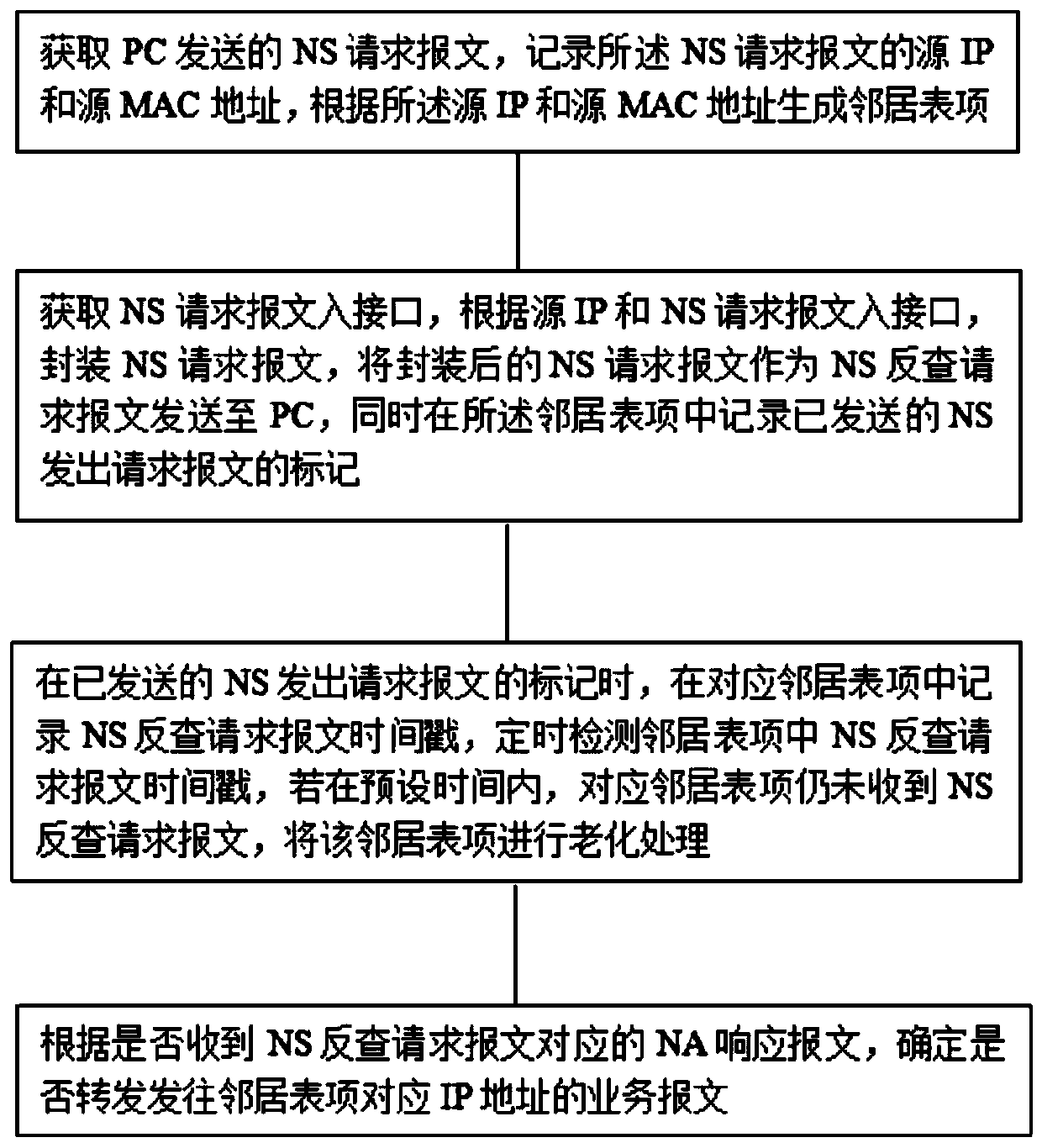
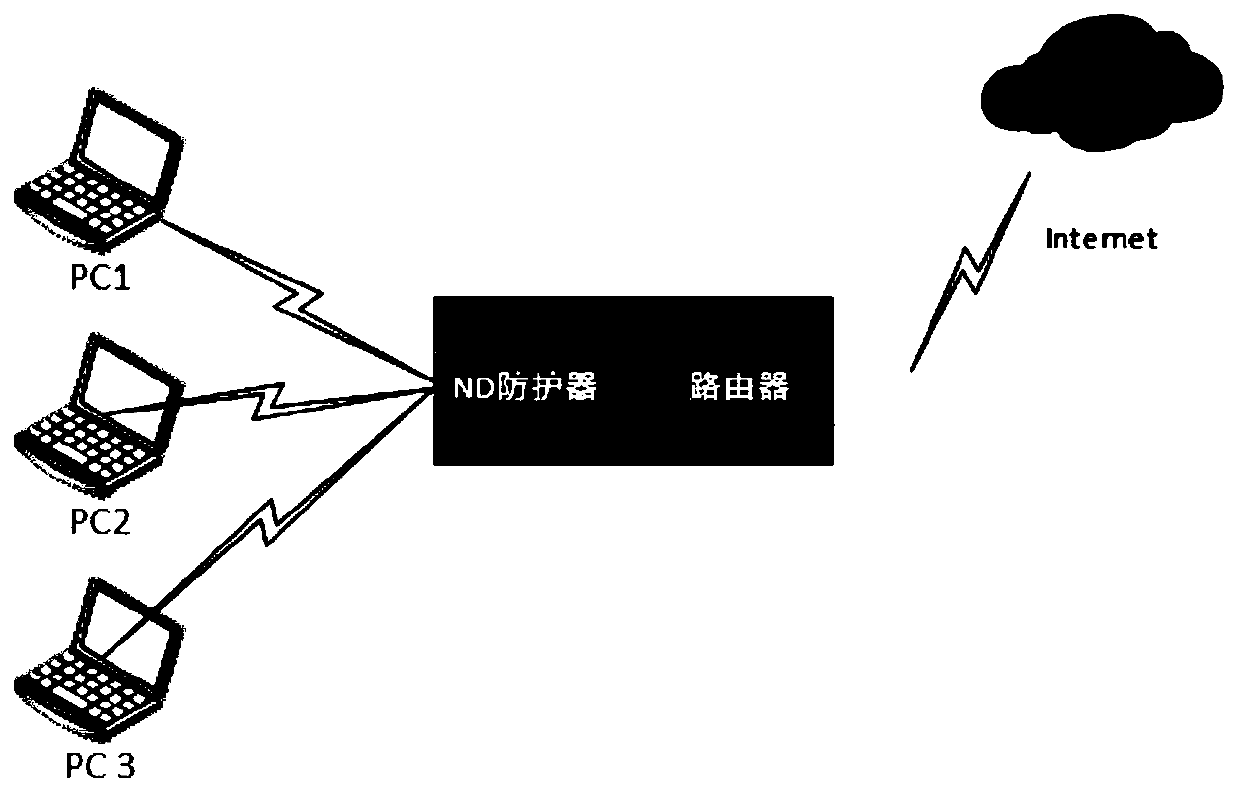
Method and system for preventing address spoofing attacks by ns reverse query
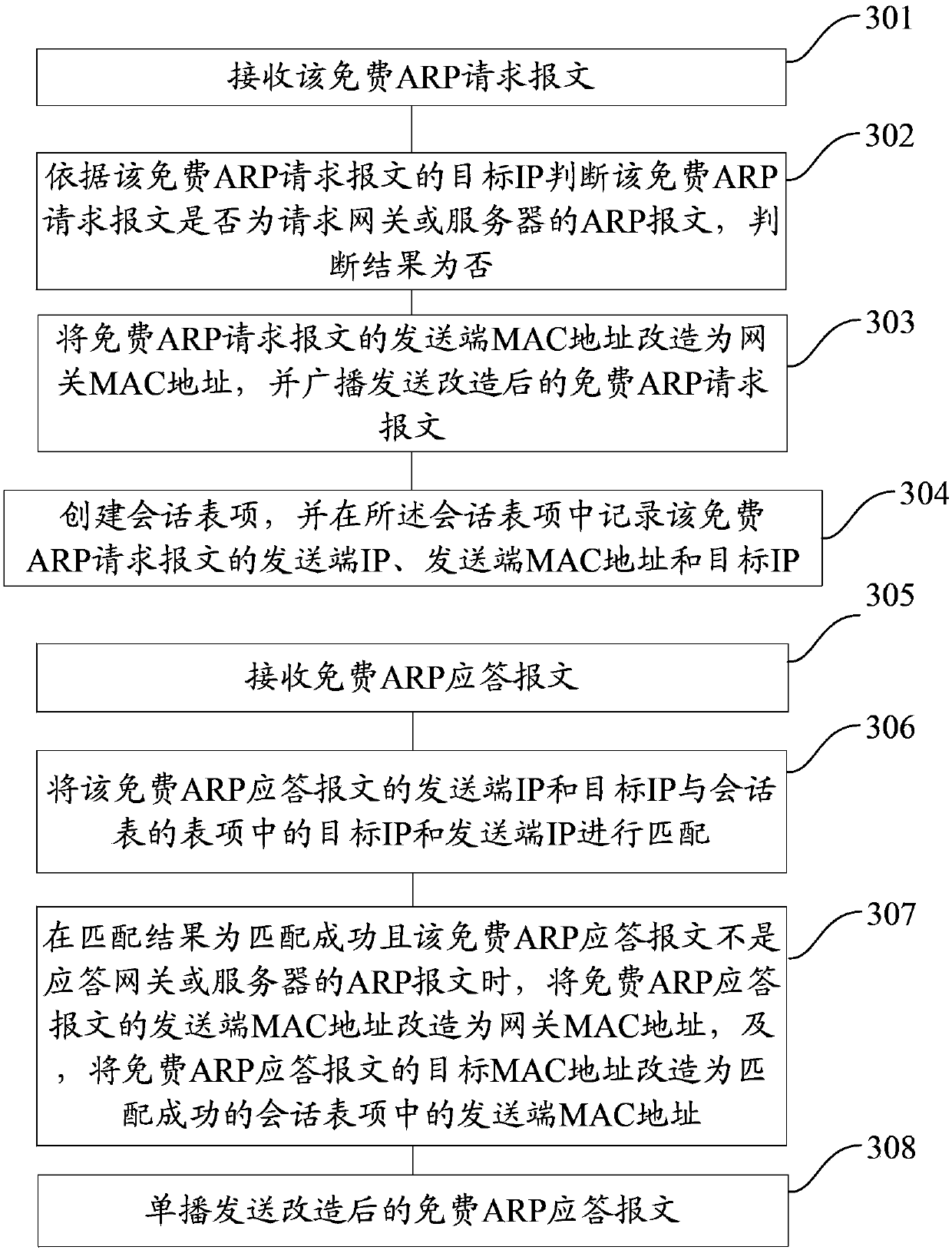
The invention discloses a method and a system for preventing an address spoofing attack by NS reverse query, belongs to the technical field of prevention of ND address spoofing, and solves the problems that the prior art is not suitable for complex networks and the number of hosts is huge. The method for preventing address spoofing attacks through NS reverse query comprises the following steps ofacquiring an NS request message sent by a PC to generate neighbor table entries; obtaining an NS request message incoming interface, packaging an NS request message, sending the packaged NS request message as an NS reverse query request message to a PC, and recording a mark of the sent NS sending request message in the neighbor table entry; and carrying out aging processing on the corresponding neighbor table entry, and determining whether to forward a service message corresponding to the IP address of the neighbor table entry according to whether an NA response message corresponding to the NSreverse query request message is received or not. Under the condition of not being limited by the network environment and the number of hosts, the ND address spoofing attack in the network environment is effectively prevented.
Owner:武汉思普崚技术有限公司
A dynamic host configuration protocol monitoring and protection method and system
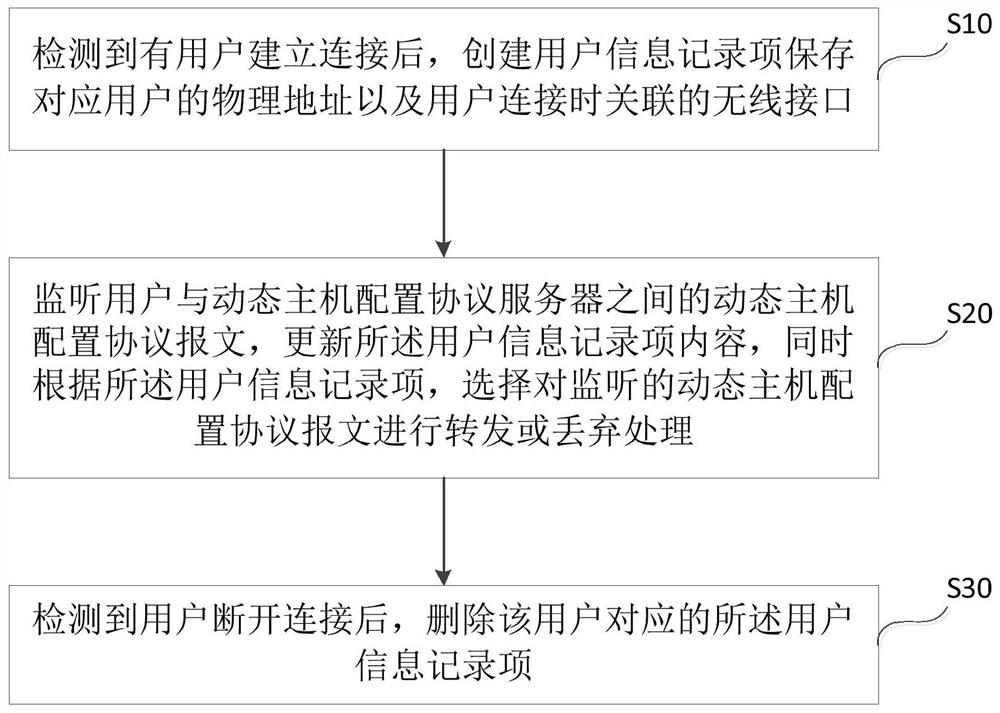
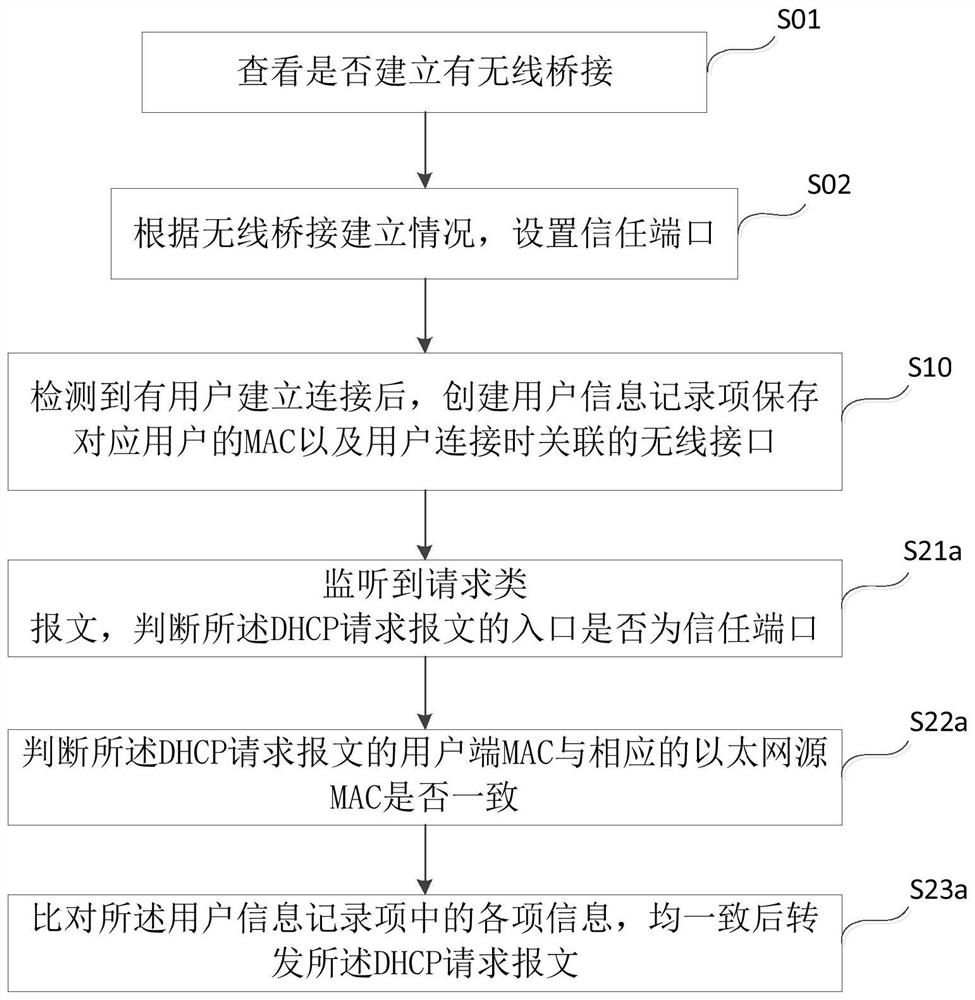
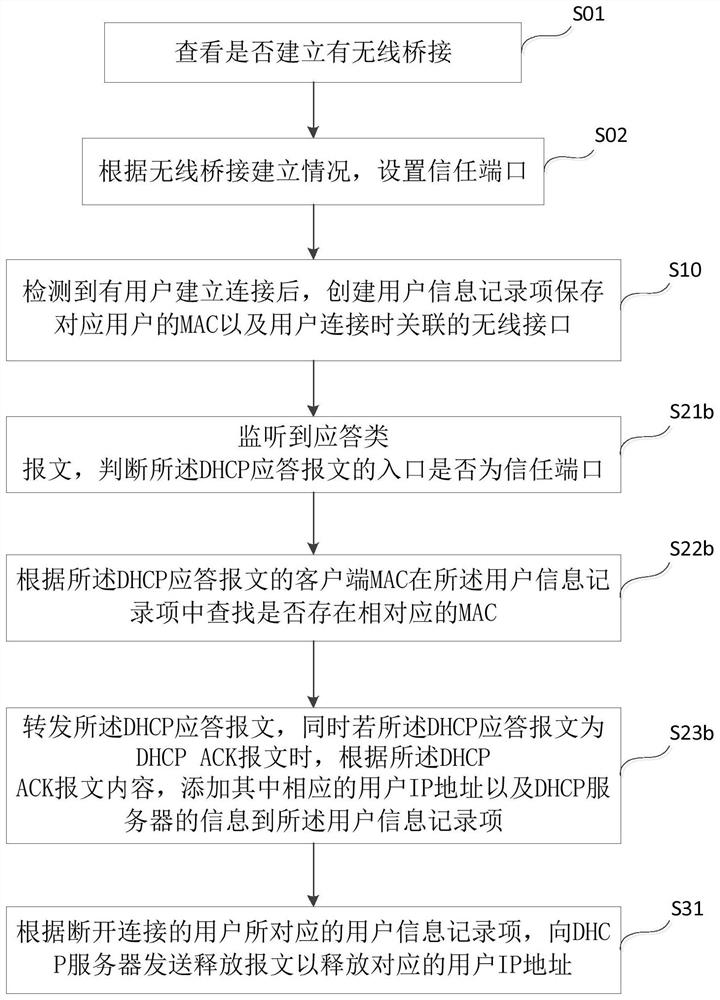
The present invention discloses a dynamic host configuration protocol monitoring and protection method and system, which are applied to wireless access points. The method includes: S10: After detecting that a user has established a connection, create a user information record item to save the physical address of the corresponding user And the wireless interface associated when the user connects; S20: Monitor the DHCP message between the user and the DHCP server, update the content of the user information record item, and select the monitor according to the user information record item Forwarding or discarding the dynamic host configuration protocol message; S30: After detecting that the user is disconnected, delete the user information record item corresponding to the user. The invention can help the wireless network access point to prevent the dynamic host configuration protocol deception and starvation attack caused by the forged message being forwarded by the attacker.
Owner:台州市吉吉知识产权运营有限公司
Network security method based on wireless firewall
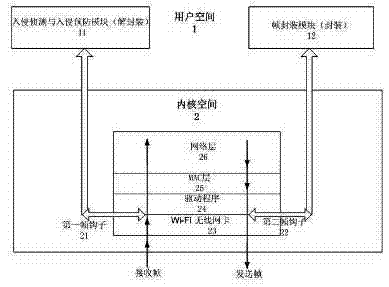
InactiveCN102378166BIncrease aggressivenessImprove usabilitySecurity arrangementIntrusion detection and preventionOpen Systems Interconnection
The invention relates to a network security method based on a wireless firewall. In the method, the wireless firewall acts on an MAC (Media Access Control) layer of OSI (Open System Interconnection) and comprises an intrusion detection and prevention module, a first frame hook and a second frame hook, wherein, the intrusion detection and prevention module is positioned in a user space of a system; the first frame hook is connected with a kernel space and the user space of the operating system, one end of the first frame hook is arranged in a wireless LAN (local area network) card driver in the kernel space of the operating system, the other end of the first frame hook is arranged in the user space and is connected with the intrusion detection and prevention module, the first frame hook transfers a frame received by the wireless LAN card driver to the intrusion detection and prevention module, and then the frame is sent back to the driver through the frame hook or is deleted after being processed by the module; and one end of the second frame hook is arranged in the wireless LAN card driver in the kernel space of the operating system, and the other end of the second frame hook is arranged in the user space and is connected with a frame encapsulation module. By adopting the network security method, the hacker attack resistance can be strengthened and the availability of the wireless network is improved.
Owner:周伯生
Method and device for forced forwarding of arp message by media access control
ActiveCN103023818BAccurate detectionEfficient detectionData switching networksAddress Resolution ProtocolIp address
The invention provides a method and a device for media access control forced forwarding of an address resolution protocol (ARP) message. The method specifically includes that when an ARP request message is not an ARP message of a request gateway or a server, a sending end media access control (MAC) of the ARP request message is transformed to be a gateway MAC, and the ARP request message is sent in a broadcast mode; entries of a session table are established, and information of the ARP request message is recorded in the entries of the session table; and a sending end internet protocol (IP) and a target IP of an ARP response message are matched with a target IP and a sending end IP in the entries of the session table, when the matching result is successful and the ARP response message is not an ARP message of a response gateway or a server, a sending end MAC of the ARP response message is transformed to be a gateway MAC and a target MAC of the ARP response message is transformed to be a sending end MAC in the entries of the session table which is successfully matched, and the ARP response message is sent in an unicast mode. By means of the method and the device, IP address conflict in the network can be accurately and effectively detected.
Owner:XINHUASAN INFORMATION TECH CO LTD
Integrity verification method and device for runtime program safety-critical data
ActiveCN102930185BAvoid attackIntegrity verification implementationProgram/content distribution protectionData setData integrity
The invention discloses a method and a device for verifying the integrity of security critical data of a program in the process of running. The method comprises the following steps: 1) indicating a security critical variable in the program, generating a security critical data set in the process of compiling, dividing a virtual address space of the program into a protected area and a non-protected area in the process of loading the program, loading the security critical data set to the protected area, and constructing an integrity verification tree for a virtual page of the protected area of the program; and 2) in the process of writing program data into a memory, updating a root verification value; and in the process of reading program data from the memory, generating a new root verification value, comparing the new root verification value with the original root verification value, if the two are equal, determining that the security critical data set is not tampered, otherwise, determining that the security critical data set is tampered. The device comprises a data integrity verification circuit, a root verification value storage module and a comparator. The method and the device disclosed by the invention have the advantages of high safety performance, strong attack prevention performance, small calculated amount, and less occupied storage space.
Owner:NAT UNIV OF DEFENSE TECH
System and method for detecting and mitigating arp attacks based on sdn cloud environment
The present invention provides a system and method for detecting and mitigating ARP attacks based on an SDN cloud environment. The system includes: a network information maintenance module, a real-time detection and defense module, a timing monitoring and mitigation module, and a flow entry control module; the method includes: The start-up stage; the stage of obtaining network information; the stage of real-time detection and defense of ARP attacks; the stage of regular monitoring and mitigation of ARP attacks. The present invention uses SDN technology to detect ARP request packets and ARP reply packets, detects ARP spoofing attacks in real time by analyzing ARP packets, and then discards forged packets to prevent ARP spoofing attacks from harming the host, and can also obtain ARP traffic at regular intervals to detect The traffic statistics data of the port of the edge SDN switch can identify the ARP storm attack, and can block the traffic of the corresponding port in time, alleviate the impact of the ARP storm attack on the cloud network, and comprehensively protect the security of the cloud computing network.
Owner:NANJING UNIV
A routing method with metadata privacy protection and source accountability capabilities
ActiveCN111884816BImprove protectionPrevent spoofing attacksKey distribution for secure communicationUser identity/authority verificationPathPingPrivacy protection
The invention belongs to the technical field of computer network security, relates to an efficient routing protocol that provides both anonymity and accountability at the network layer, and specifically relates to a routing method with metadata privacy protection and source accountability capabilities. The technical solution of the invention is to attach the group signature to the message network layer to achieve the balance of anonymity and accountability. The group signature in the message can provide extensive and efficient accountability. It can be verified by any router on the path in a non-interactive way to verify the authenticity of the message, thereby eliminating the communication overhead when verifying the message. At the same time, the group signature protects the privacy of the sender, making the signer indistinguishable from entities outside the group within the group. In addition, in order to further reduce the verification overhead of the group signature, the present invention designs a challenge-based separation verification mechanism. Compared with precomputation and batch verification, the separate verification mechanism can reduce the verification load of the designated router to a greater extent, thereby improving the efficiency of the protocol.
Owner:NAT UNIV OF DEFENSE TECH
A blockchain-based transparent data integrity audit and transparent encrypted data deduplication method
ActiveCN110278076BResistance to spoofing attacksResist cheatingKey distribution for secure communicationEncryption apparatus with shift registers/memoriesData integrityAttack
The invention belongs to the field of information security, and is specifically a blockchain-based transparent data integrity audit and transparent encrypted data deduplication method; the scheme of the invention includes four modules: initialization parameters, acquisition of encryption keys, two-way Usability inspection, transparent integrity audit and transparent deduplication. Compared with the existing scheme, the present invention can resist biased audit and delayed audit of the cloud server, and can avoid the cloud server claiming the wrong deduplication level to charge additional fees; the present invention can prevent single point failure attacks and exhaustive attacks, It can provide a two-way ownership certificate between the user and the cloud server; the present invention implements a safe and effective protocol based on the block chain, and can realize transparent data integrity audit and transparent data deduplication at the same time.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
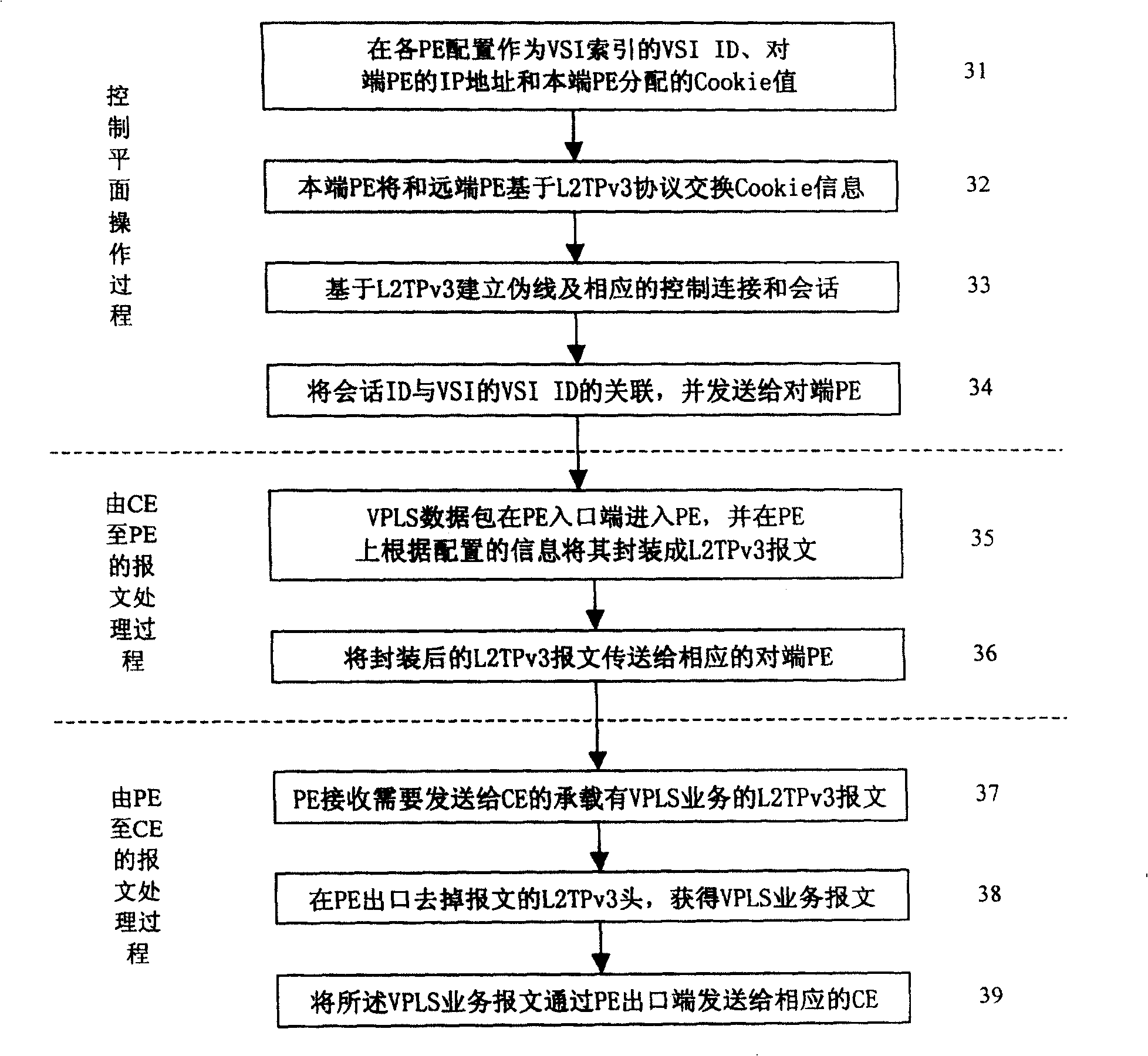
Implementing method and system for support VPLS service on IP skeletal network
This invention relates to a method for supporting VPLS services on an IP backbone network and a system including: setting up an L2TPv3 tunnel for transmitting the VPLS service based on the L2TPv3 in the IP network, then, utilizing said L2TPv3 tunnel to transmit the VPLS service, in which, this invention can use the L2TPv3 signaling protocol to support VPLS service on the IP backbone network, so that the VPLS can break away from the MPLS network and applies the IP backbone network.
Owner:HUAWEI TECH CO LTD
Early warning method and device for arp entry spoofing attack on local area network
Owner:DALIAN ROILAND SCI & TECH CO LTD
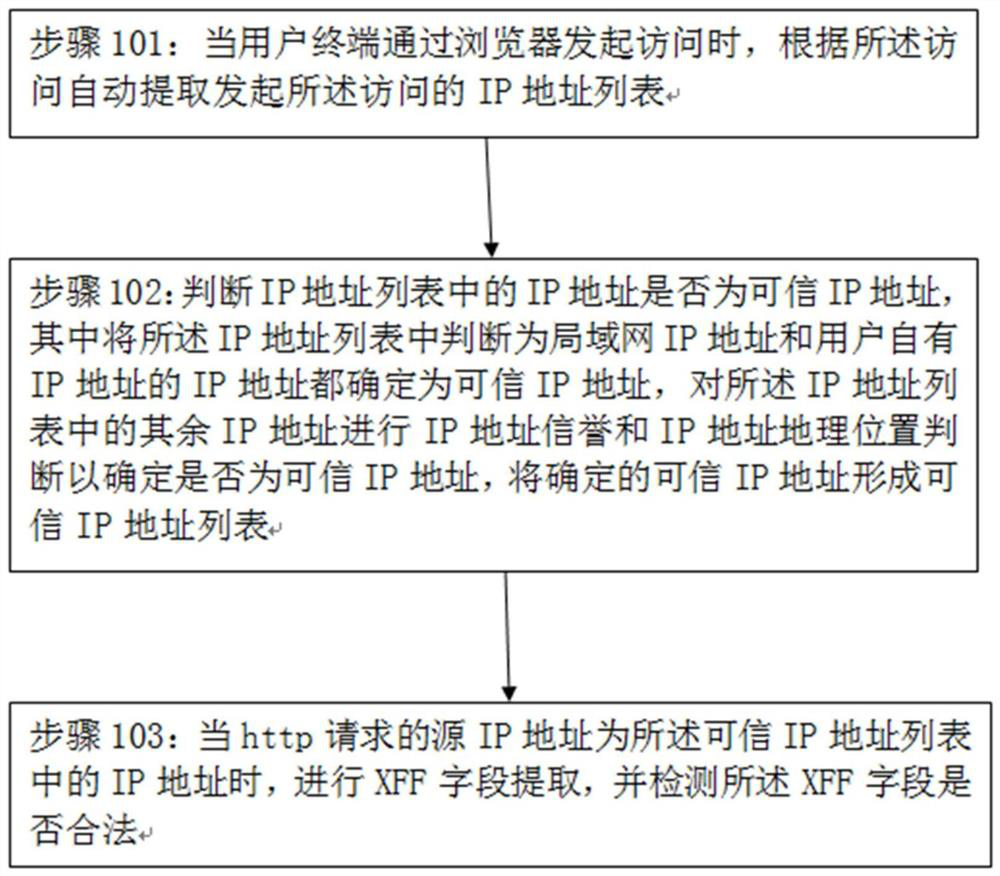
Method for preventing original address spoofing attack, device, server and storage medium
The invention discloses a method for preventing original address spoofing attacks, a device, a server and a storage medium. The method includes: when a user terminal initiates an access through a browser, automatically extracting a list of IP addresses that initiate the access according to the access ; Judging whether the IP address in the IP address list is a trusted IP address, wherein the IP addresses that are judged to be the LAN IP address and the user's own IP address in the IP address list are all determined as trusted IP addresses. The remaining IP addresses in the address list are judged by IP address reputation and IP address geographic location to determine whether they are trusted IP addresses, and the determined trusted IP addresses form a trusted IP address list; when the source IP address of the http request is the described When the IP address in the trusted IP address list is selected, the XFF field is extracted, and whether the XFF field is legal is detected. The method automatically processes the traffic, automatically identifies the trusted IP address list, and prevents original address spoofing attacks.
Owner:北京微步在线科技有限公司
Method and system for preventing address spoofing attack by NS reverse query
The invention discloses a method and a system for preventing an address spoofing attack by NS reverse query, belongs to the technical field of prevention of ND address spoofing, and solves the problems that the prior art is not suitable for complex networks and the number of hosts is huge. The method for preventing address spoofing attacks through NS reverse query comprises the following steps ofacquiring an NS request message sent by a PC to generate neighbor table entries; obtaining an NS request message incoming interface, packaging an NS request message, sending the packaged NS request message as an NS reverse query request message to a PC, and recording a mark of the sent NS sending request message in the neighbor table entry; and carrying out aging processing on the corresponding neighbor table entry, and determining whether to forward a service message corresponding to the IP address of the neighbor table entry according to whether an NA response message corresponding to the NSreverse query request message is received or not. Under the condition of not being limited by the network environment and the number of hosts, the ND address spoofing attack in the network environment is effectively prevented.
Owner:武汉思普崚技术有限公司
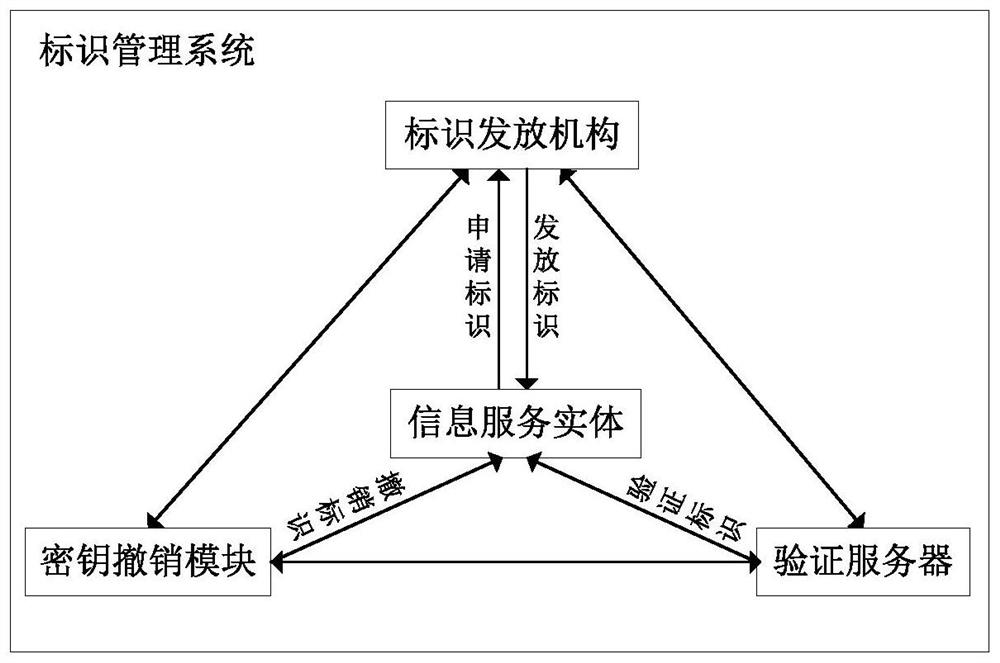
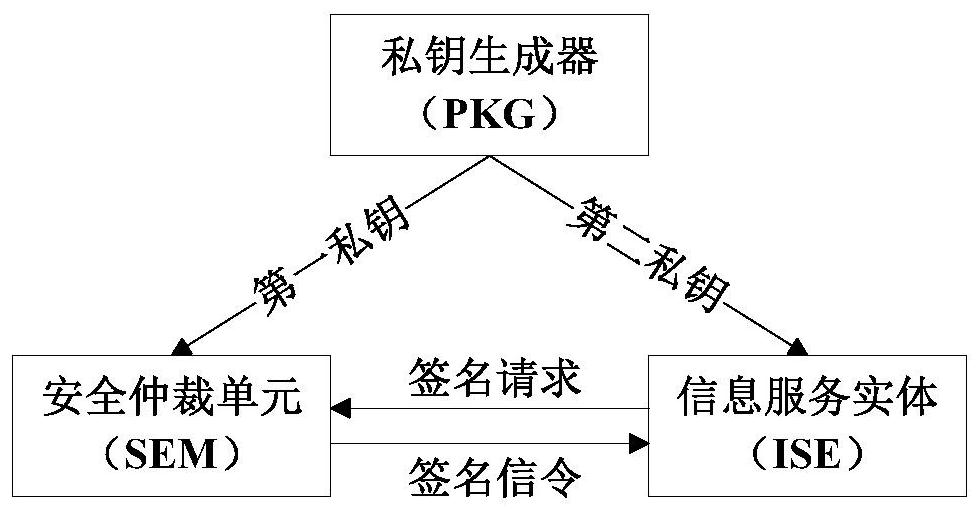
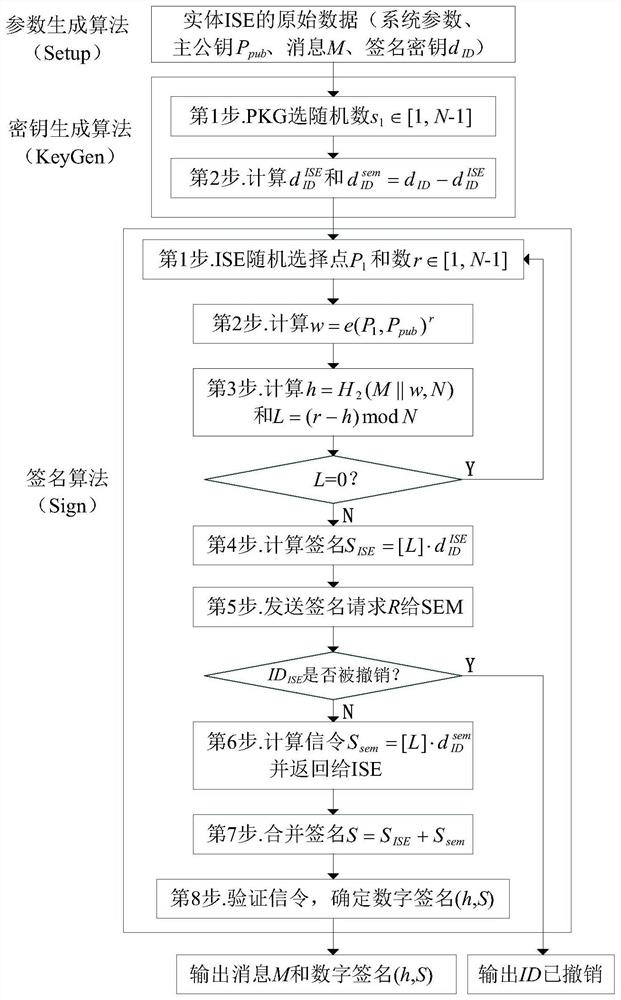
Information Service Entity Identity Quick Revocation Method
ActiveCN108737391BUndo quickPrevent spoofing attacksKey distribution for secure communicationUser identity/authority verificationComputational securityInternet privacy
The invention discloses an information service entity identity management system and a quick identity revocation method, which can solve the problem of instant revocation of an entity identity. A keyrevocation module is added in an identity management system, and the key revocation module includes a security arbitration unit, which can quickly revoke the identity of an information service entitywhen services of the information service entity are invalid or illegal. The implementation of the quick revocation method includes the following steps that: system initialization is performed, and keygeneration and segmentation of the information service entity is performed; and the information service entity and the security arbitration unit cooperate with part of private keys to implement the signature of a message, and a verification server verifies the signature of the message to achieve the unified management and authentication of a network space information service entity identity. According to the scheme of the invention, the invalid or illegal identity can be quickly revoked, the computational security is based on the difficulty of solving discrete logarithms on elliptic curves, the characteristic of quick revocation can be realized, high security can also be achieved, and the scheme is suitable for network environments with high security requirements.
Owner:XIDIAN UNIV
Method for protecting security of account
ActiveCN102164141BImprove authentication strengthImprove reliabilityTransmissionPasswordMobile phone
Owner:陈珂
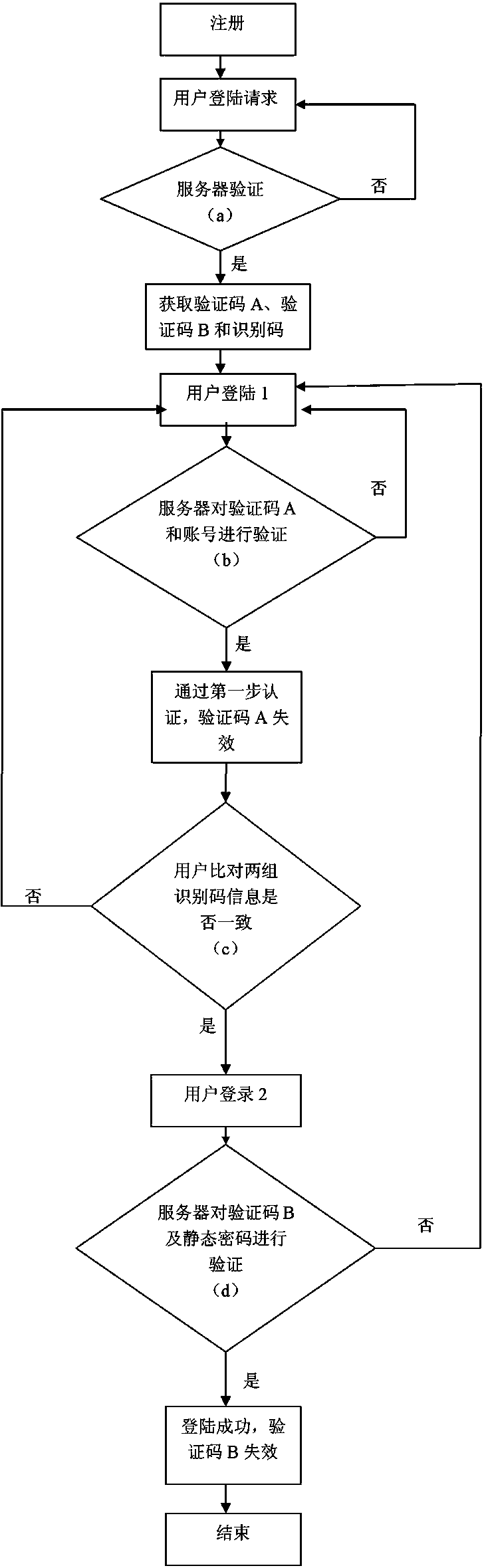
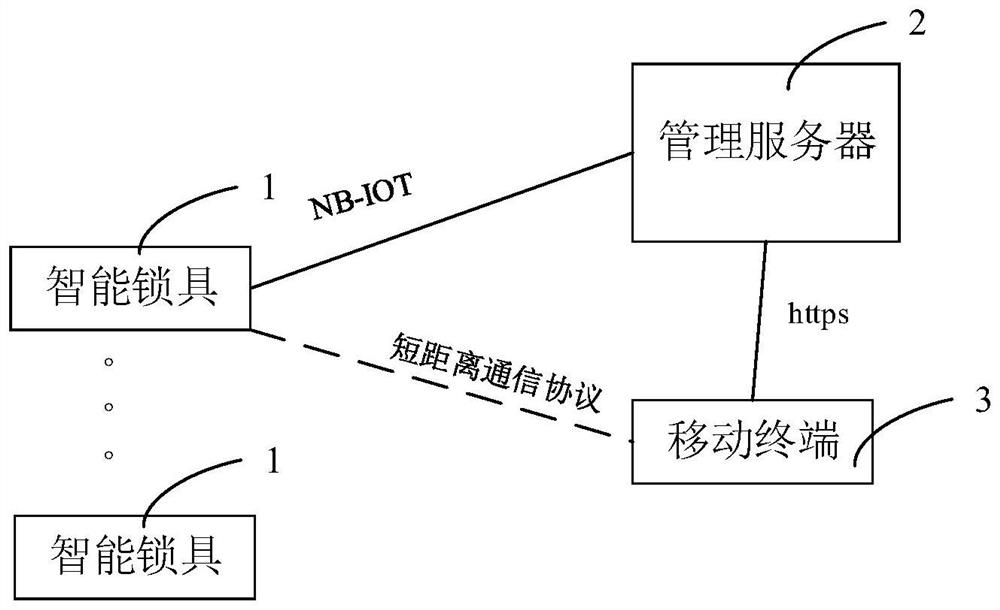
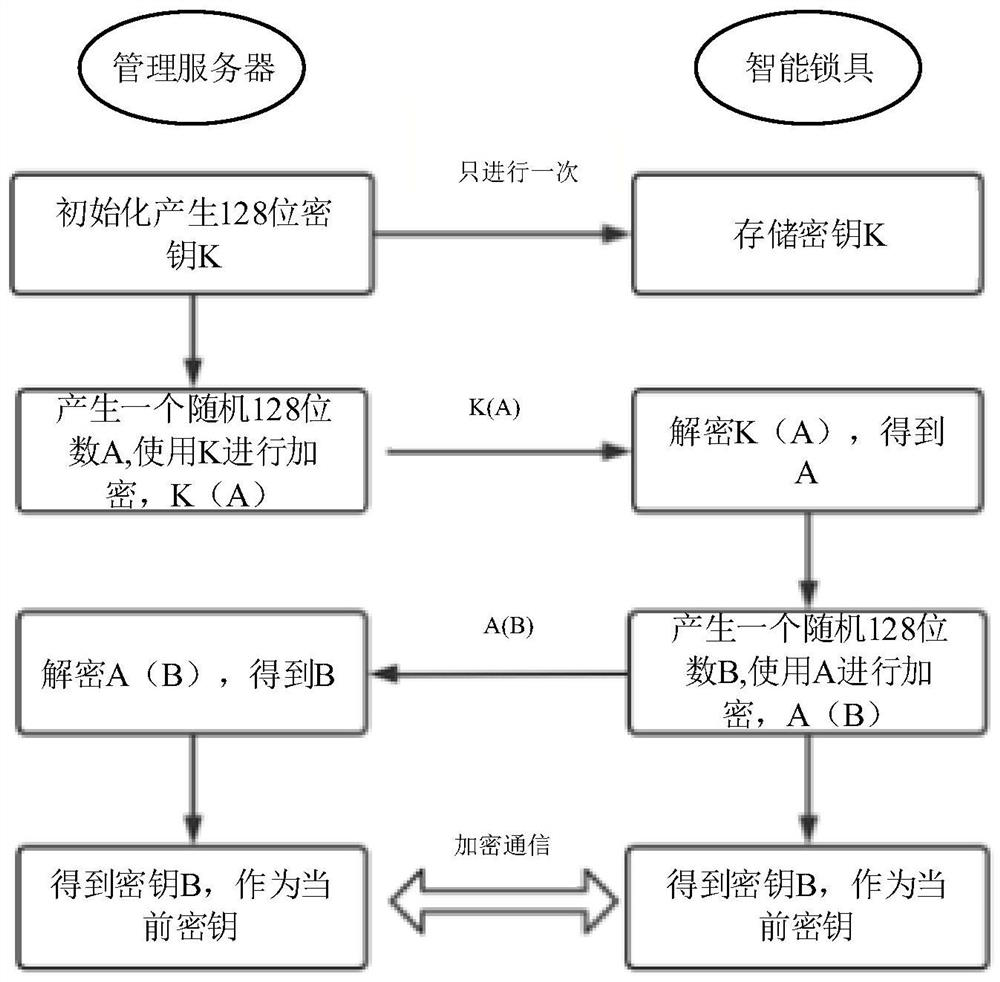
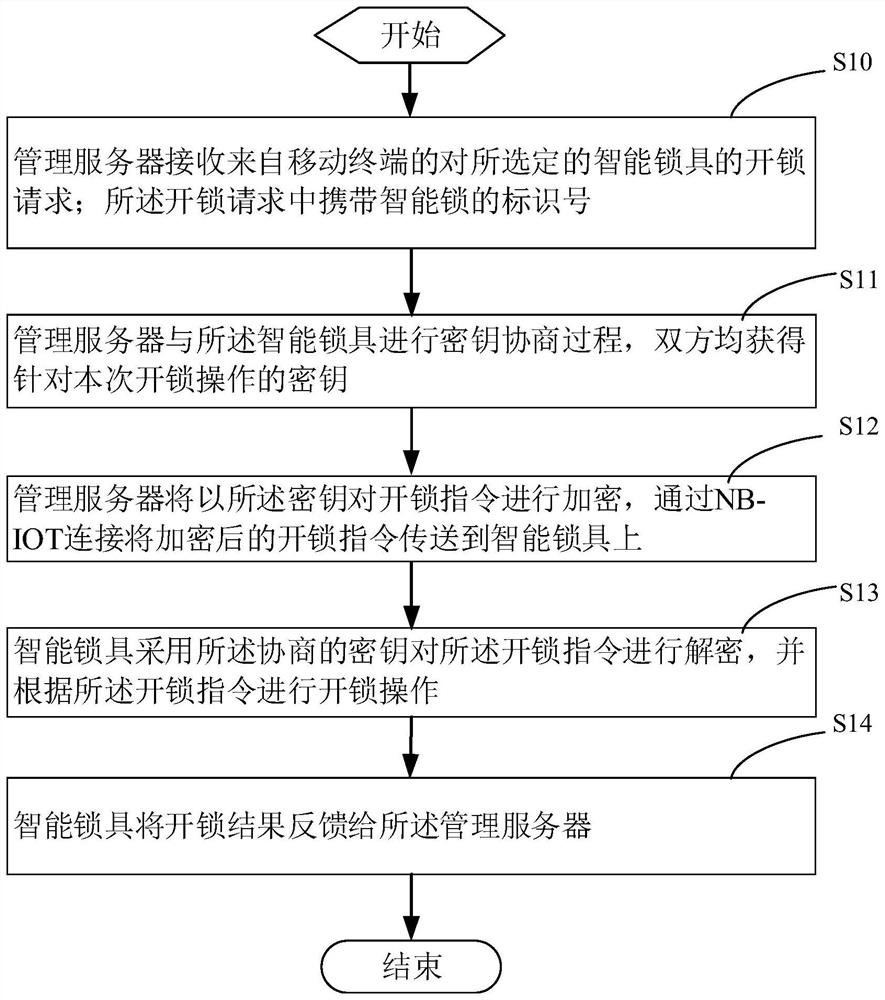
Communication safety guarantee method and system for intelligent lock of power supply equipment
PendingCN114255530APrevent replay attacksPrevent spoofing attacksIndividual entry/exit registersCommunications securityEmbedded system
The invention provides a communication security guarantee method for an intelligent lock of power supply equipment. The communication security guarantee method comprises the following steps: step S10, a management server receives an unlocking request for the selected intelligent lock from a mobile terminal; step S11, the management server and the intelligent lock perform a key negotiation process, and both the management server and the intelligent lock obtain a key for the unlocking operation; step S12, the management server encrypts the unlocking instruction by using the secret key, and transmits the encrypted unlocking instruction to the intelligent lock through the NB-IOT network; step S13, the intelligent lock decrypts the unlocking instruction by adopting the negotiated secret key, and performs unlocking operation according to the unlocking instruction; and S14, the intelligent lock feeds back an unlocking result to the management server. The invention further provides a corresponding system. According to the invention, the security of the intelligent lock in the communication process can be improved.
Owner:SHENZHEN POWER SUPPLY BUREAU
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com