Method and device for verifying integrity of security critical data of program in process of running
A technology for integrity verification and key data, which is applied in the field of computer security, can solve the problems of high cost of constructing tree structures, excessive virtual address space, and difficulty in practical use, and achieves small integrity calculations, high security performance, and saving on-chip and the effect of off-chip memory space
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
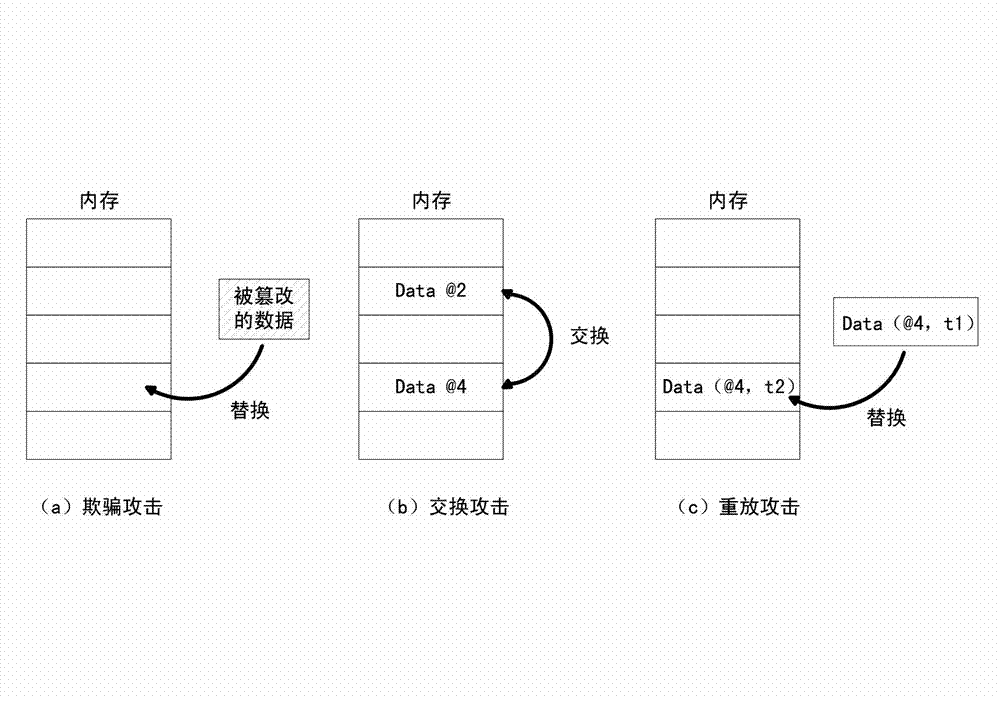
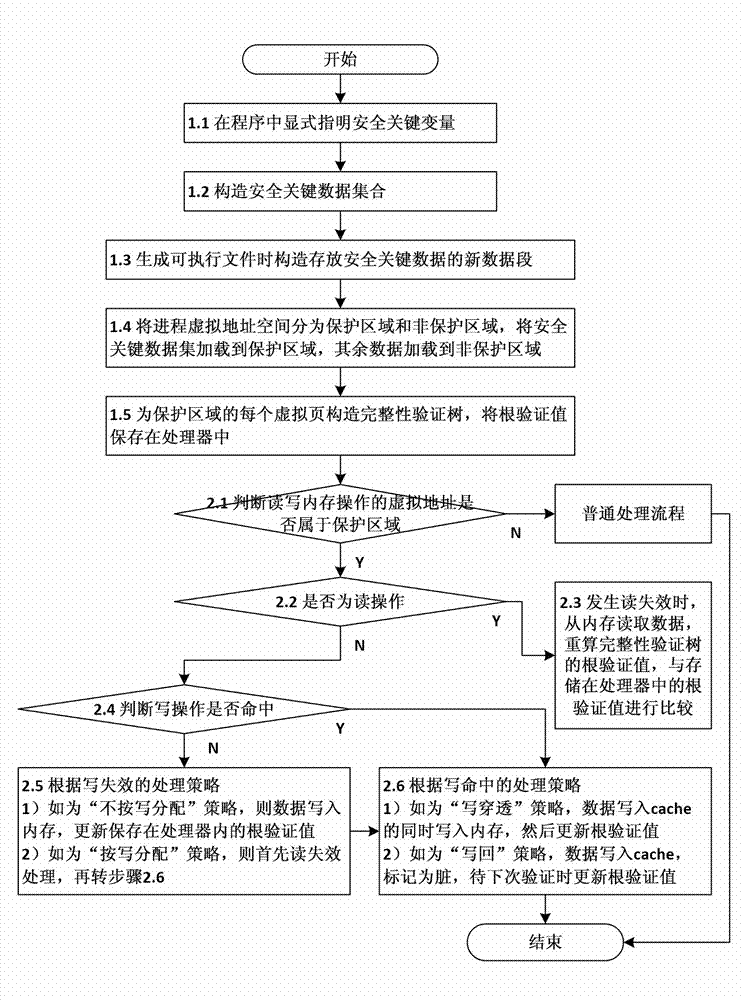
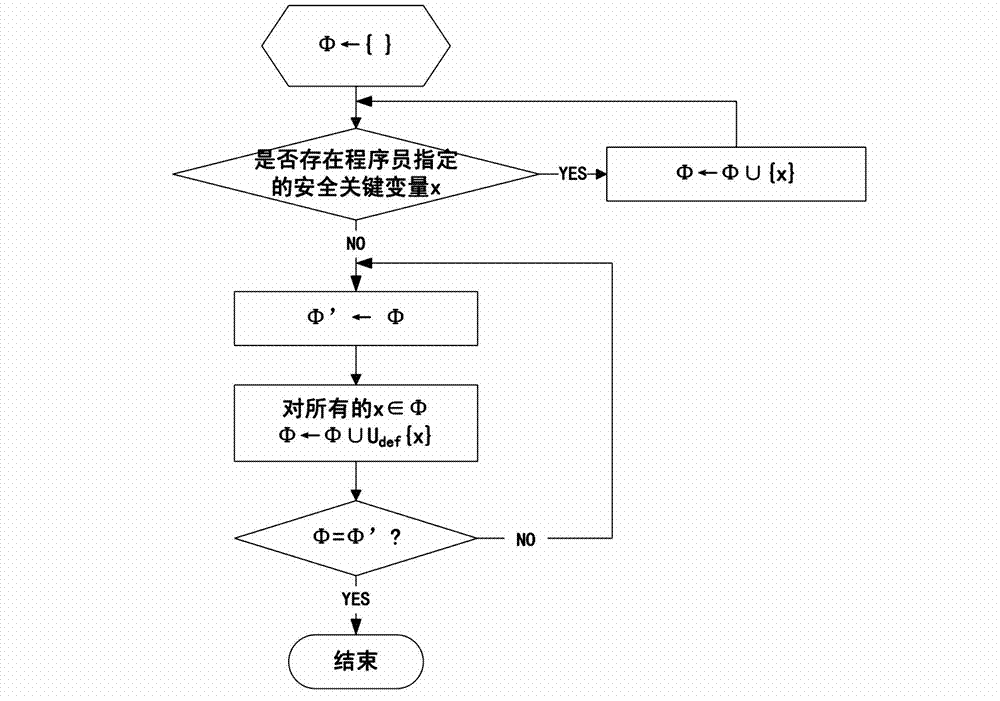
[0061] Such as figure 2 As shown, the implementation steps of the method for verifying the integrity of program safety-critical data during runtime in this embodiment are as follows:
[0062] 1) Indicate the safety-critical variables to be protected in the program, generate the corresponding safety-critical data sets for the safety-critical variables when compiling the program, divide the virtual address space of the program into protected areas and non-protected areas when loading the program, and divide the safety The key data set is loaded into the protection area, an integrity verification tree is constructed for each virtual page in the protection area of the program, and the root verification value of the integrity verification tree is saved in the processor;
[0063] 2) When the processor issues a read and write operation to write program data to the memory, update the root verification value stored in the processor; when the read and write operation of the processor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com