Patents
Literature
168 results about "Attack prevention" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A heart attack prevention checklist Take your medications. Be as physically active as you can be. Sign up for cardiac rehabilitation. Get a flu shot. Drink alcohol in moderation. Lose some weight.
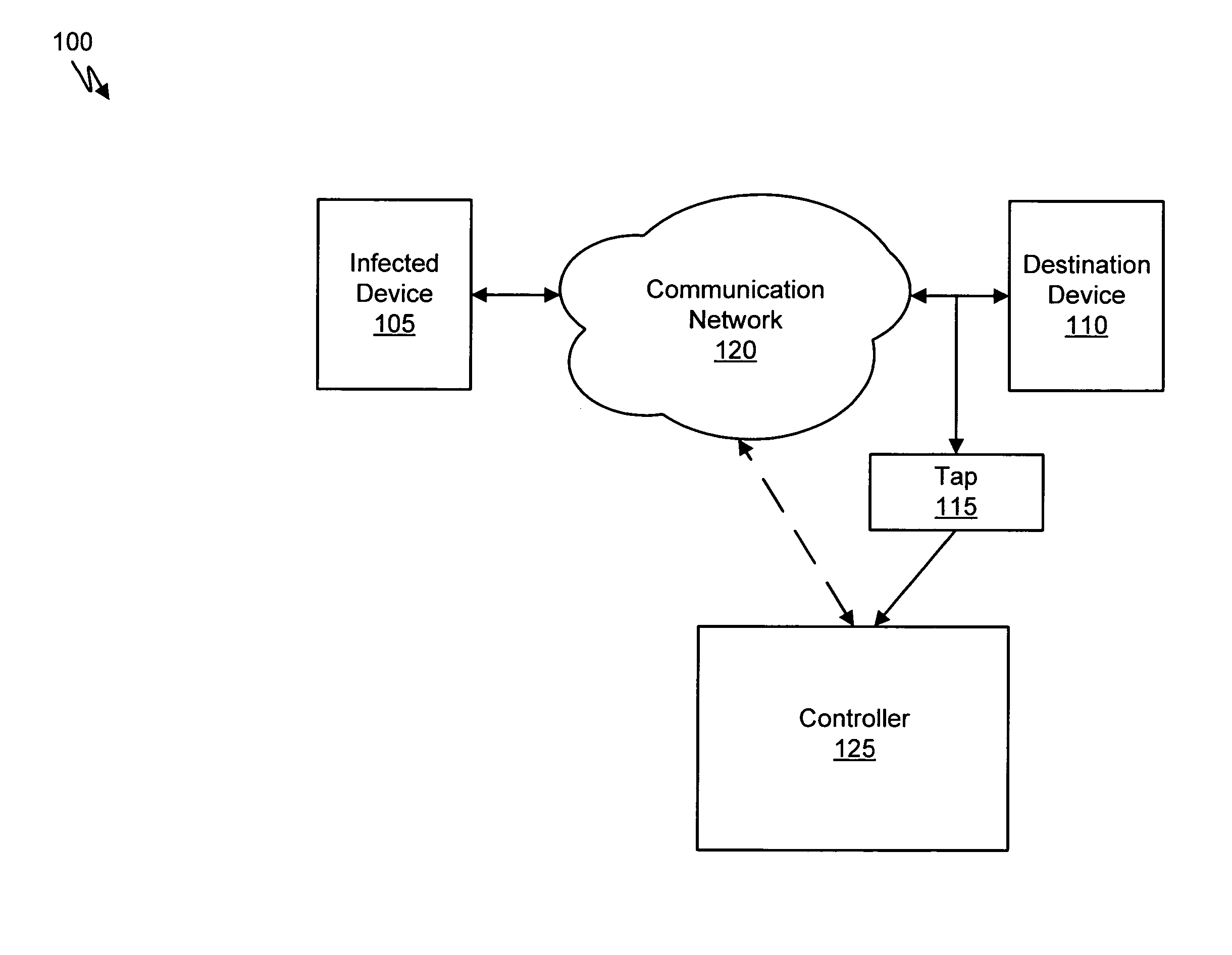
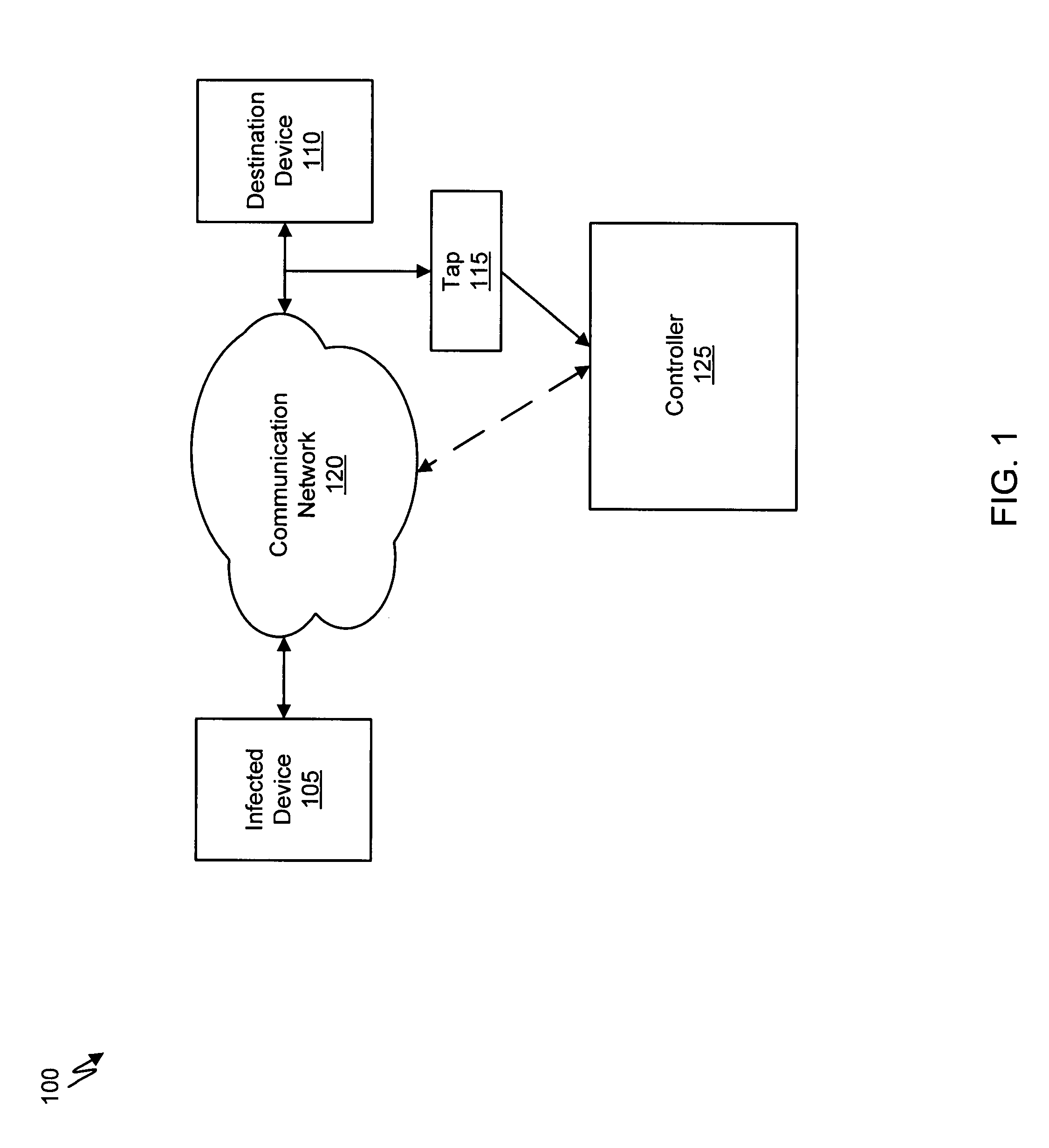
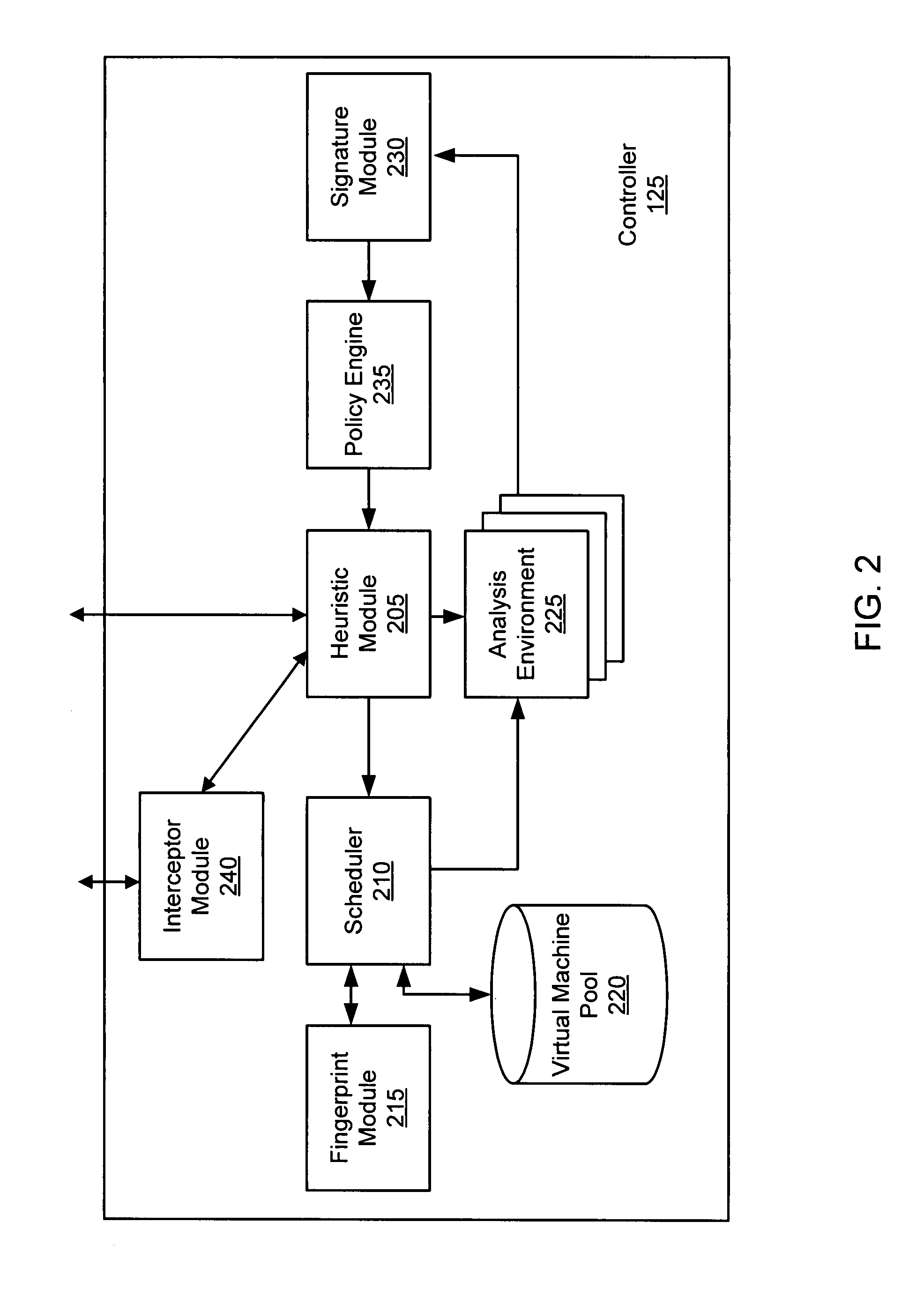
Systems and methods for malware attack prevention
Systems and methods for malware attack prevention are provided. Network data is copied from a communication network. It is then determined if a possible malware attack is within the copied network data. The network data is intercepted based on the determination. The network data is then analyzed to identify a malware attack.
Owner:FIREEYE SECURITY HLDG US LLC
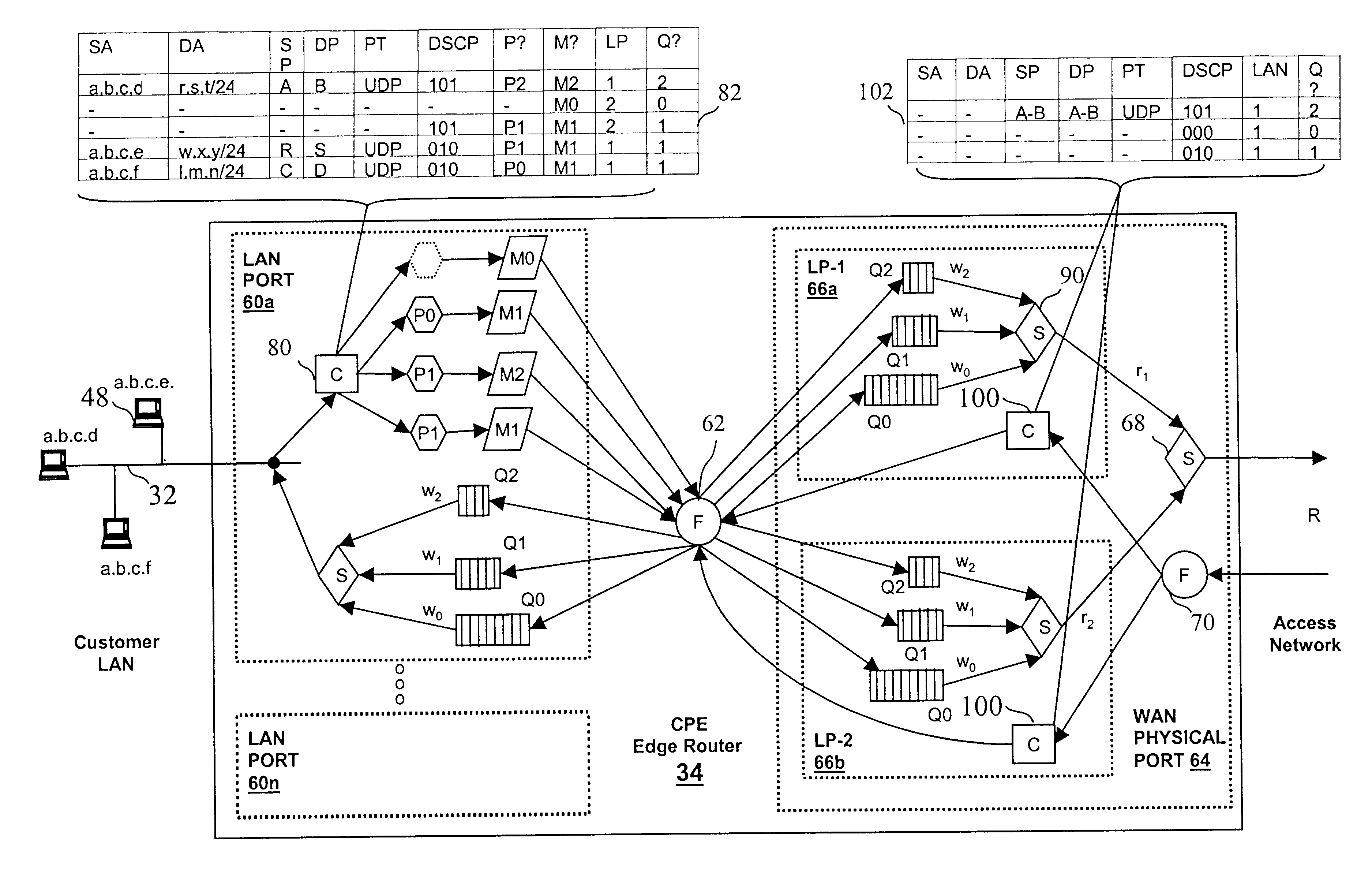
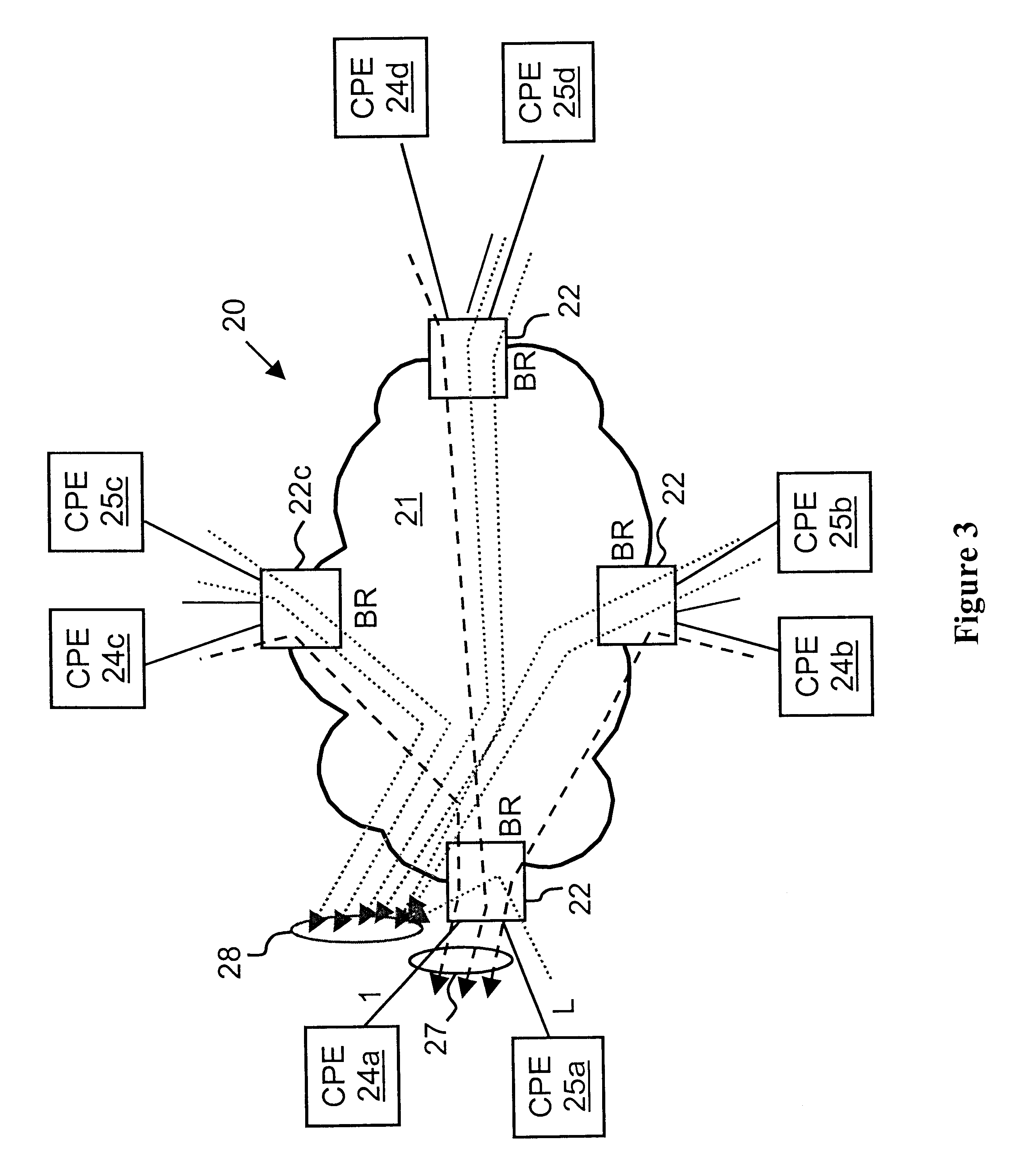
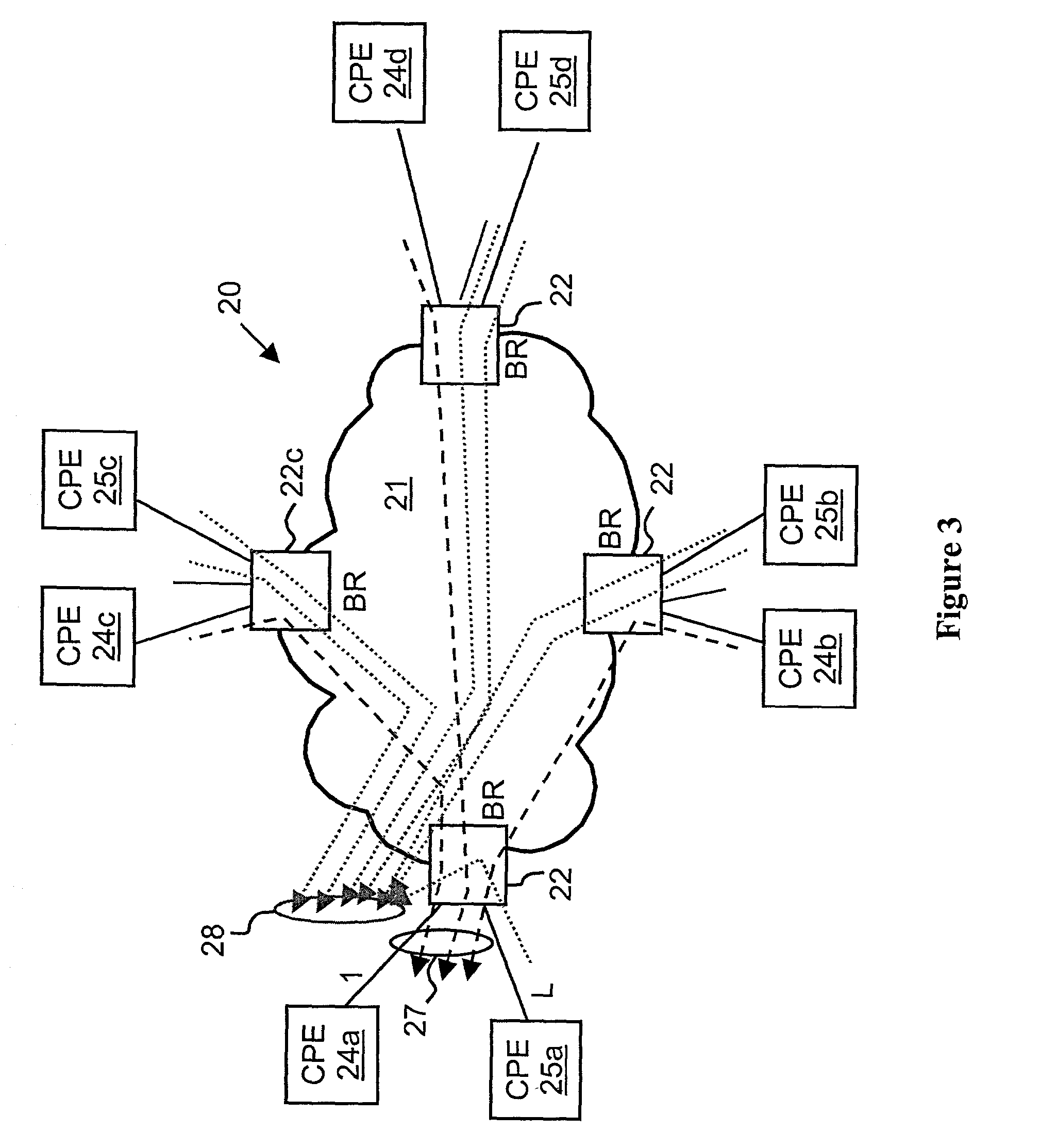
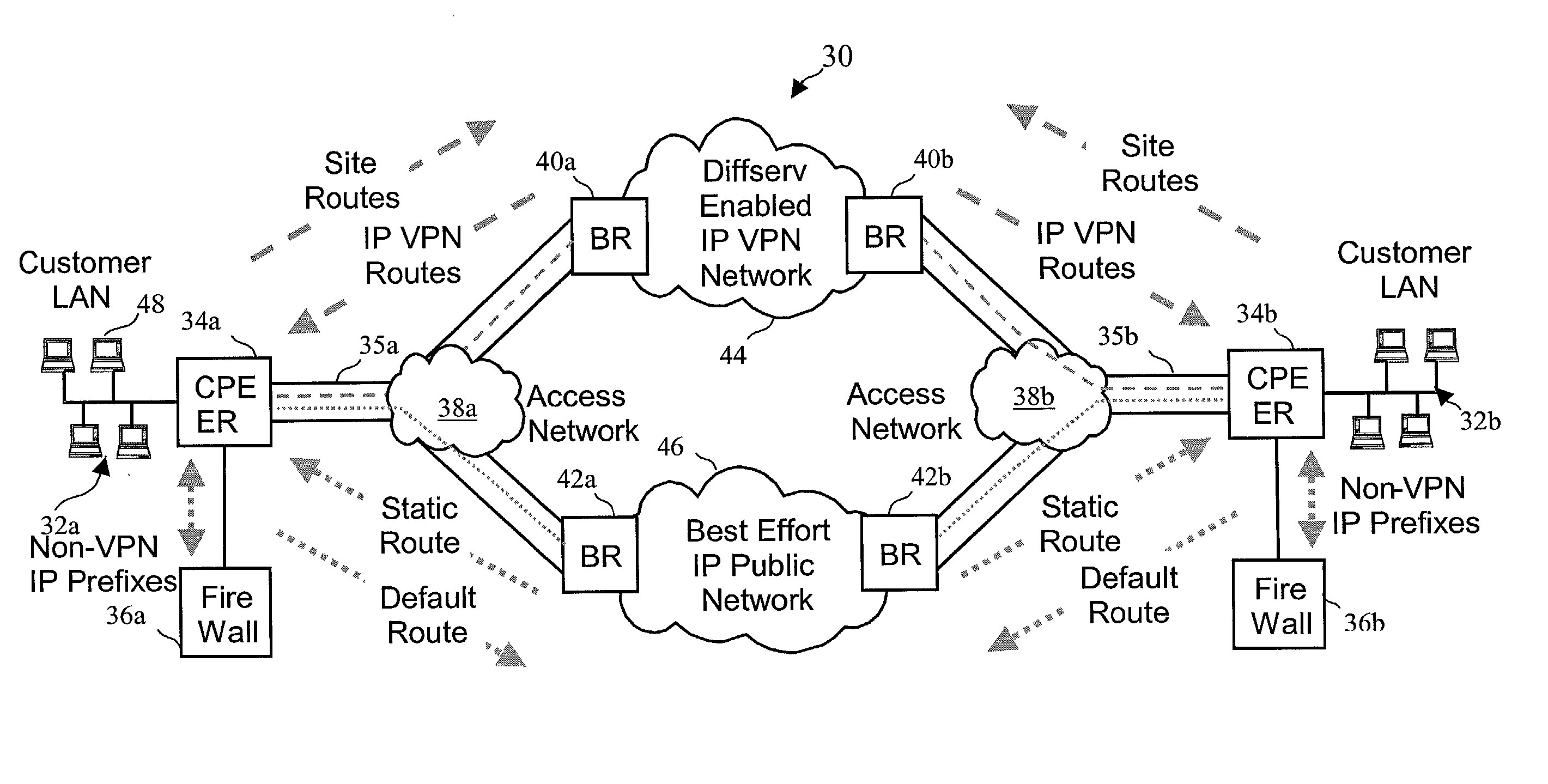
Virtual private network (VPN)-aware customer premises equipment (CPE) edge router
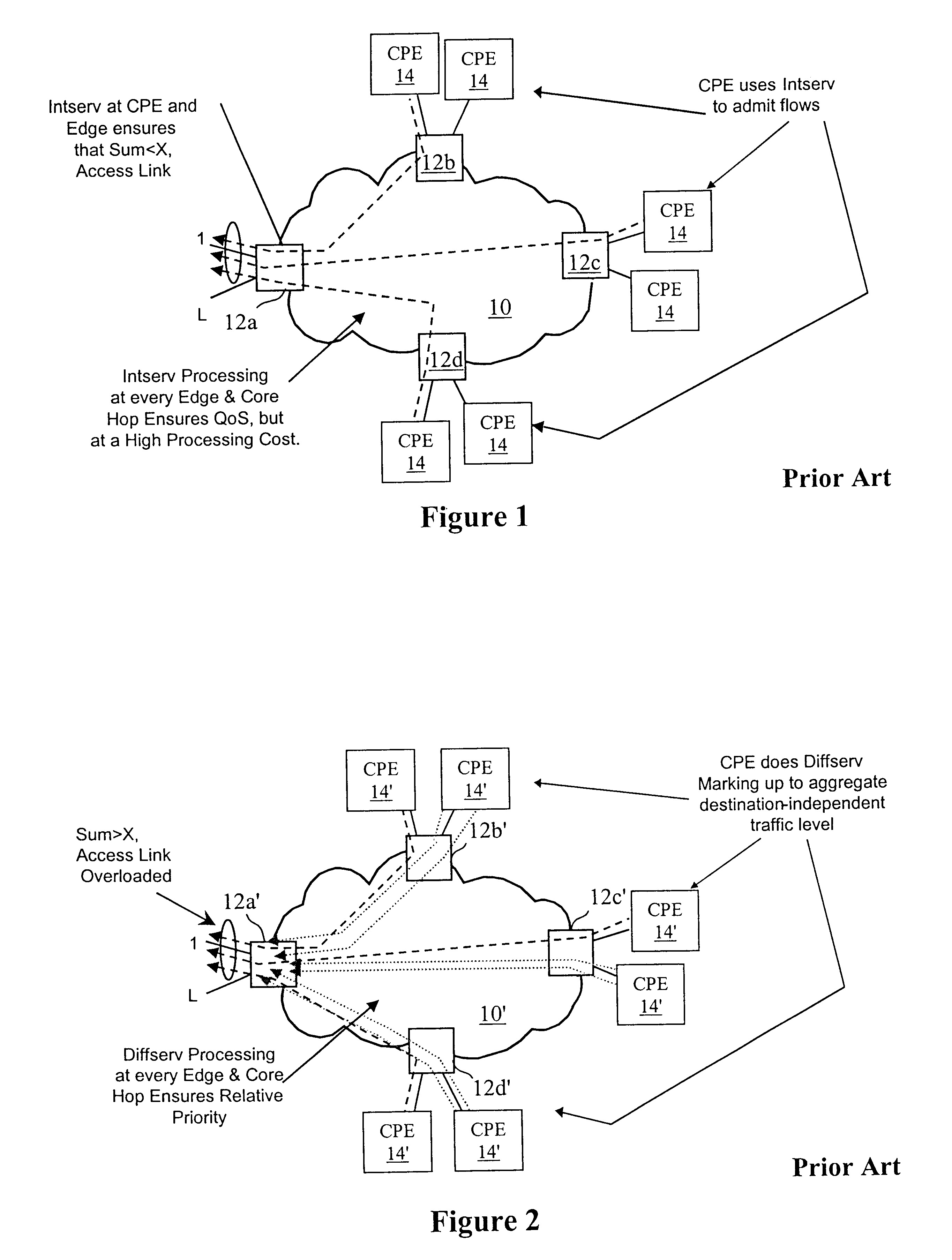
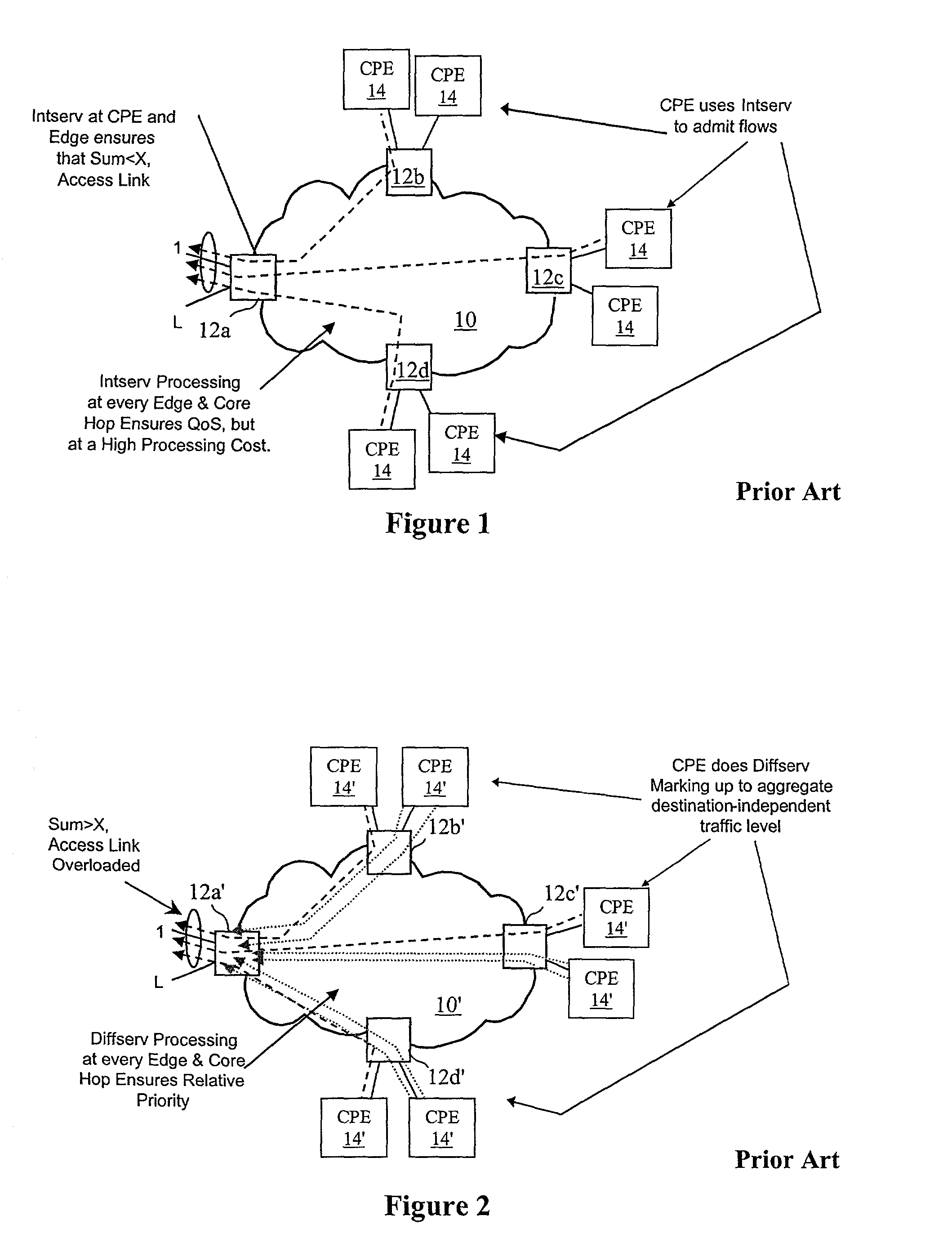
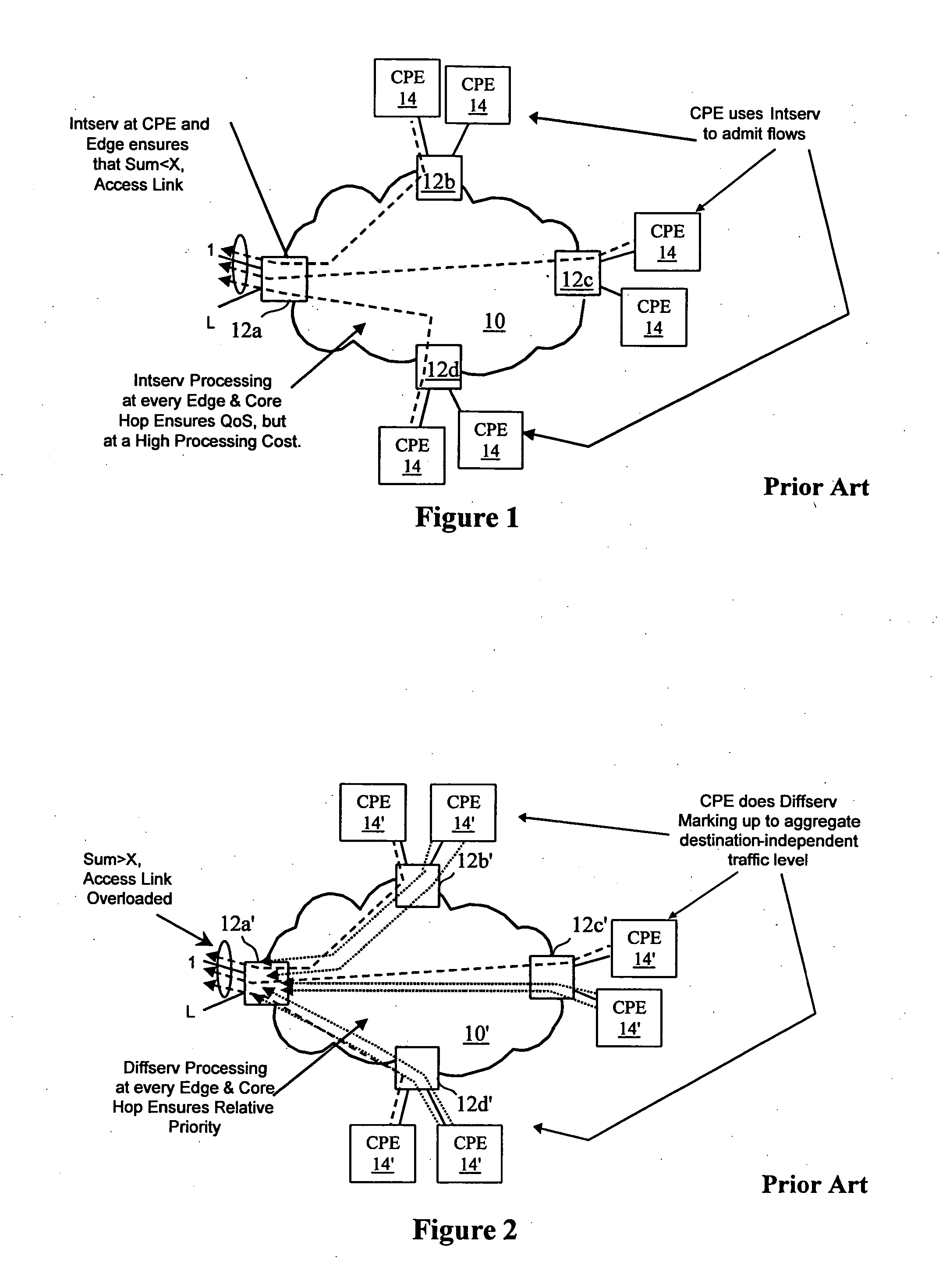
InactiveUS6778498B2Metering/charging/biilling arrangementsError preventionPrivate networkNetwork architecture
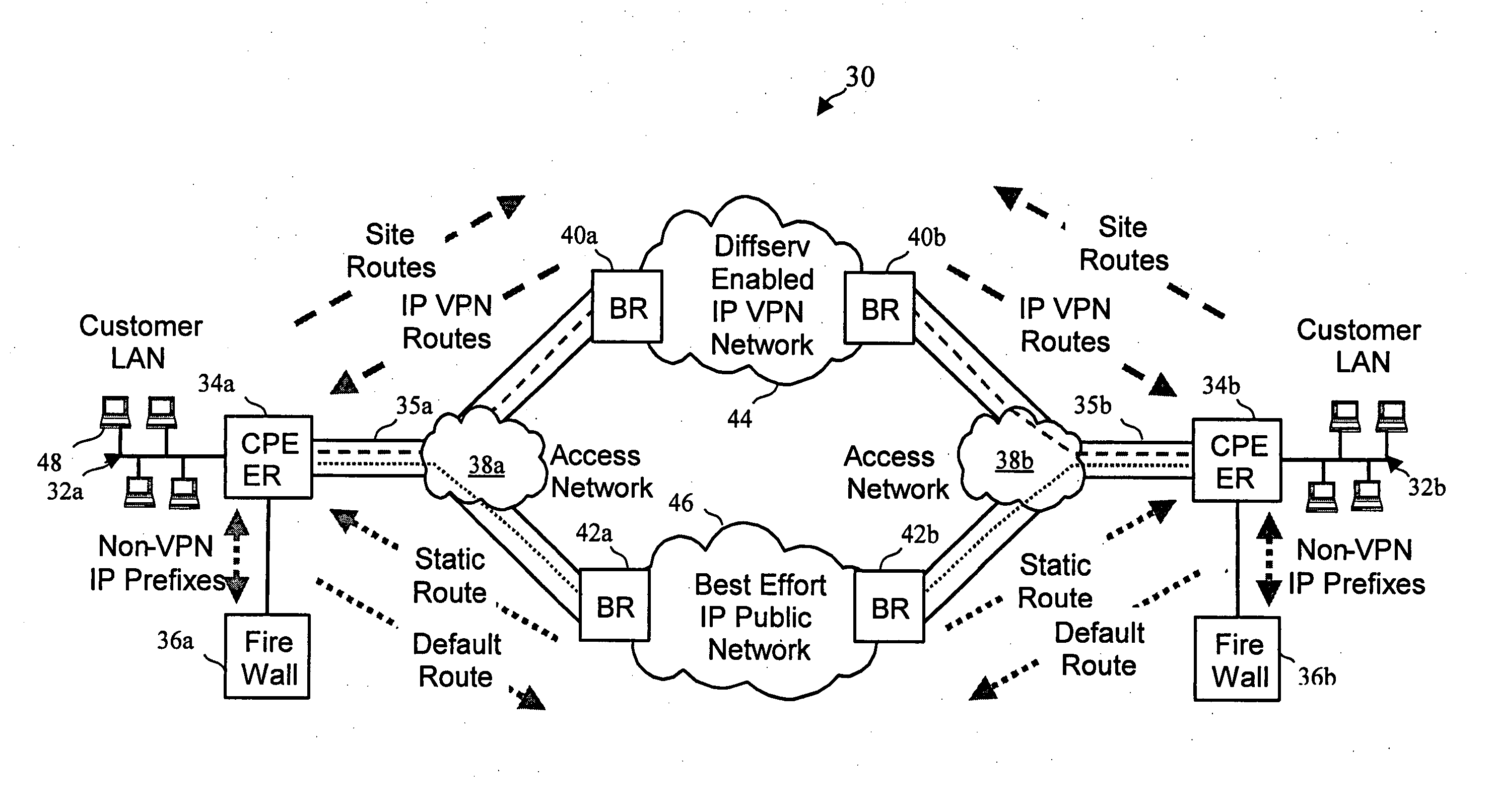
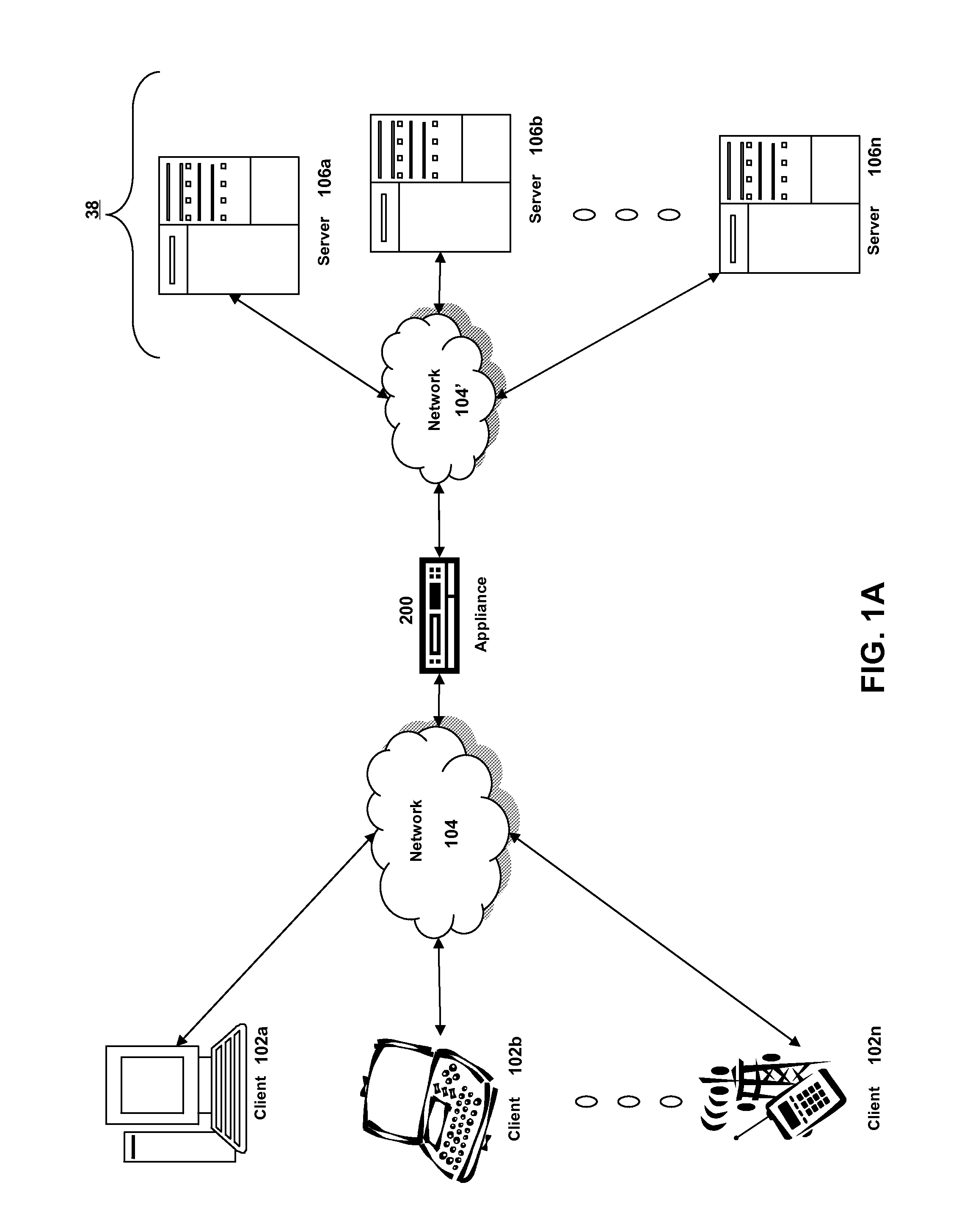
A network architecture includes a communication network that supports one or more network-based Virtual Private Networks (VPNs). The communication network includes a plurality of boundary routers that are connected by access links to CPE edge routers belonging to the one or more VPNs. To prevent traffic from outside a customer's VPN (e.g., traffic from other VPNs or the Internet at large) from degrading the QoS provided to traffic from within the customer's VPN, the present invention gives precedence to intra-VPN traffic over extra-VPN traffic on each customer's access link through access link prioritization or access link capacity allocation, such that extra-VPN traffic cannot interfere with inter-VPN traffic. Granting precedence to intra-VPN traffic over extra-VPN traffic in this manner entails partitioning between intra-VPN and extra-VPN traffic on the physical access link using layer 2 multiplexing and configuration of routing protocols to achieve logical traffic separation between intra-VPN traffic and extra-VPN traffic at the VPN boundary routers and CPE edge routers. By configuring the access networks, the VPN boundary routers and CPE edge routers, and the routing protocols of the edge and boundary routers in this manner, the high-level service of DoS attack prevention is achieved.
Owner:VERIZON PATENT & LICENSING INC
Virtual private network (VPN)-aware customer premises equipment (CPE) edge router
InactiveUS20030112755A1Metering/charging/biilling arrangementsError preventionPrivate networkNetwork architecture
A network architecture includes a communication network that supports one or more network-based Virtual Private Networks (VPNs). The communication network includes a plurality of boundary routers that are connected by access links to CPE edge routers belonging to the one or more VPNs. To prevent traffic from outside a customer's VPN (e.g., traffic from other VPNs or the Internet at large) from degrading the QoS provided to traffic from within the customer's VPN, the present invention gives precedence to intra-VPN traffic over extra-VPN traffic on each customer's access link through access link prioritization or access link capacity allocation, such that extra-VPN traffic cannot interfere with inter-VPN traffic. Granting precedence to intra-VPN traffic over extra-VPN traffic in this manner entails partitioning between intra-VPN and extra-VPN traffic on the physical access link using layer 2 multiplexing and configuration of routing protocols to achieve logical traffic separation between intra-VPN traffic and extra-VPN traffic at the VPN boundary routers and CPE edge routers. By configuring the access networks, the VPN boundary routers and CPE edge routers, and the routing protocols of the edge and boundary routers in this manner, the high-level service of DoS attack prevention is achieved.
Owner:VERIZON PATENT & LICENSING INC
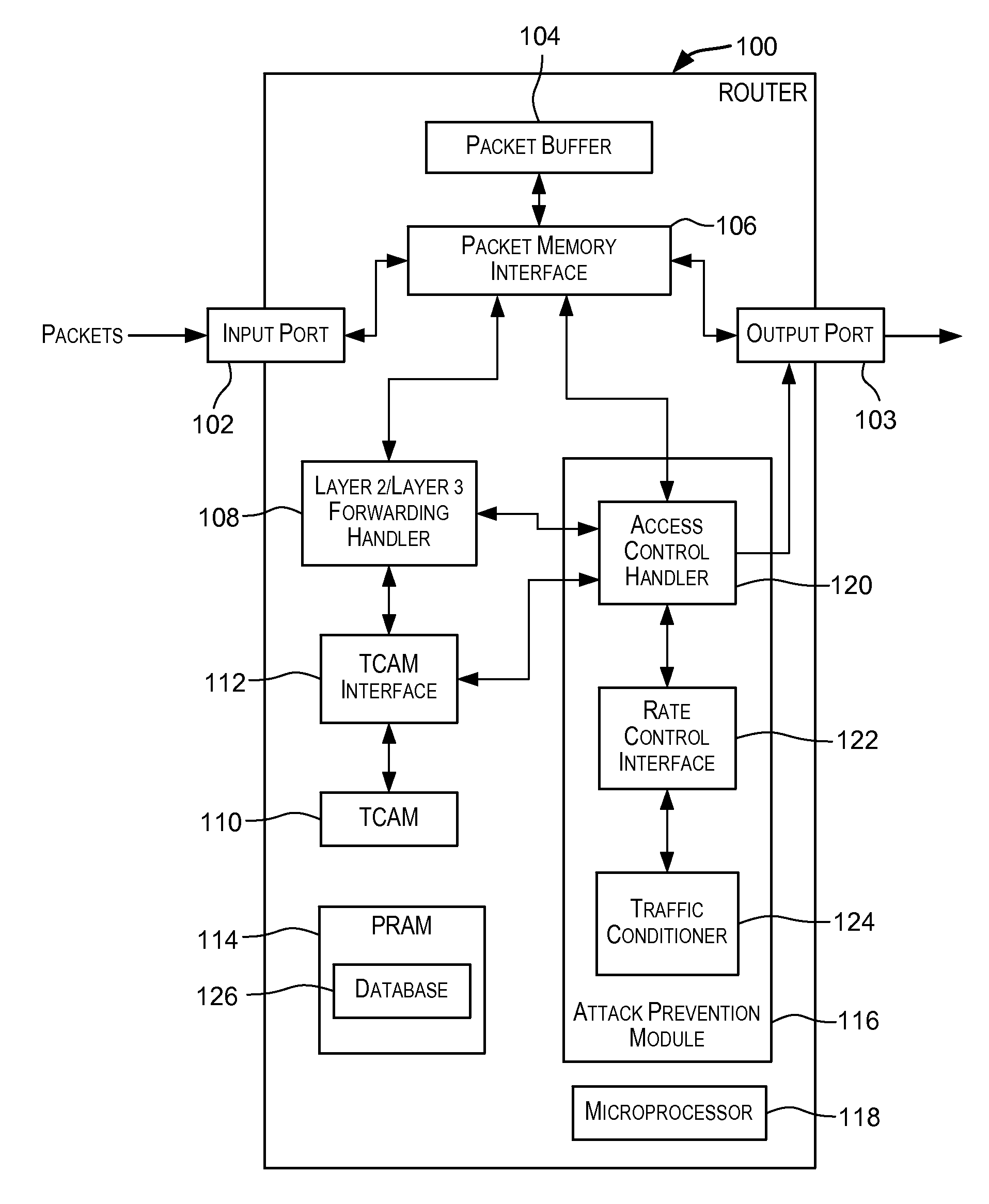
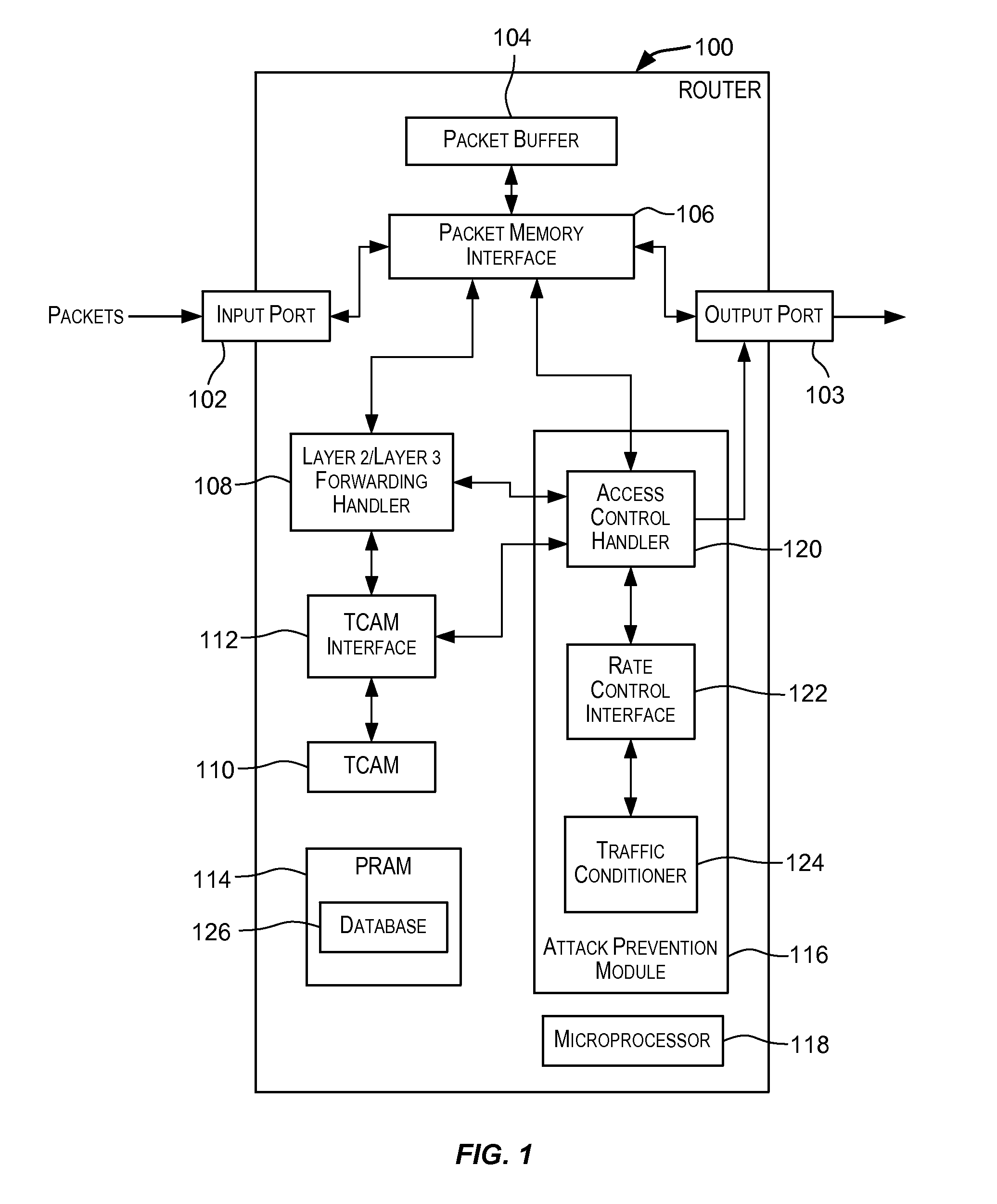
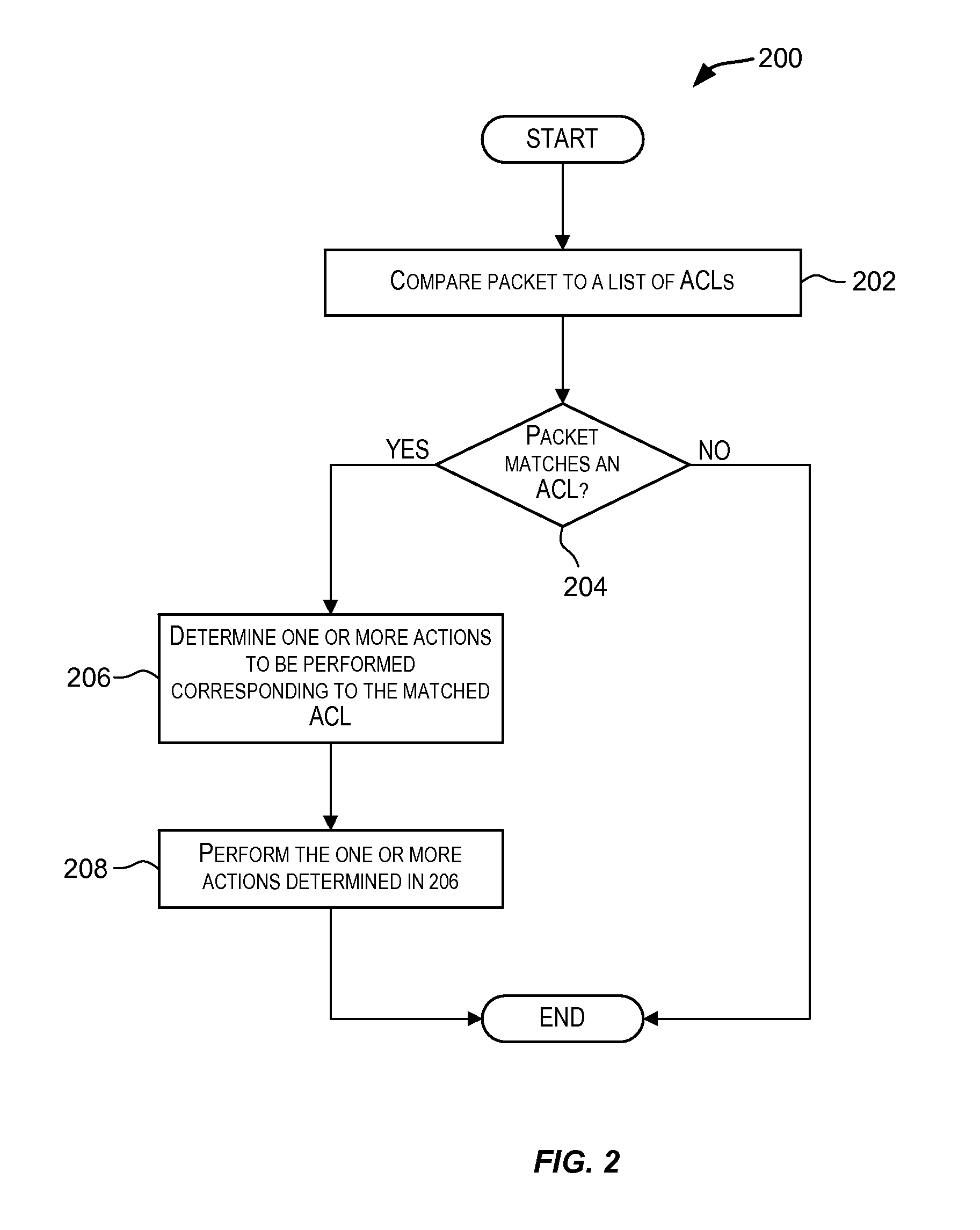
Attack prevention techniques
Techniques for detecting and responding to attacks on computer and network systems including denial-of-service (DoS) attacks. A packet is classified as potentially being an attack packet if it matches an access control list (ACL) specifying one or more conditions. One or more actions may be performed responsive to packets identified as potential attack packets. These actions may include dropping packets identified as potential attack packets for a period of time, rate limiting a port over which the potential attack packets are received for a period of time, and other actions.
Owner:AVAGO TECH INT SALES PTE LTD
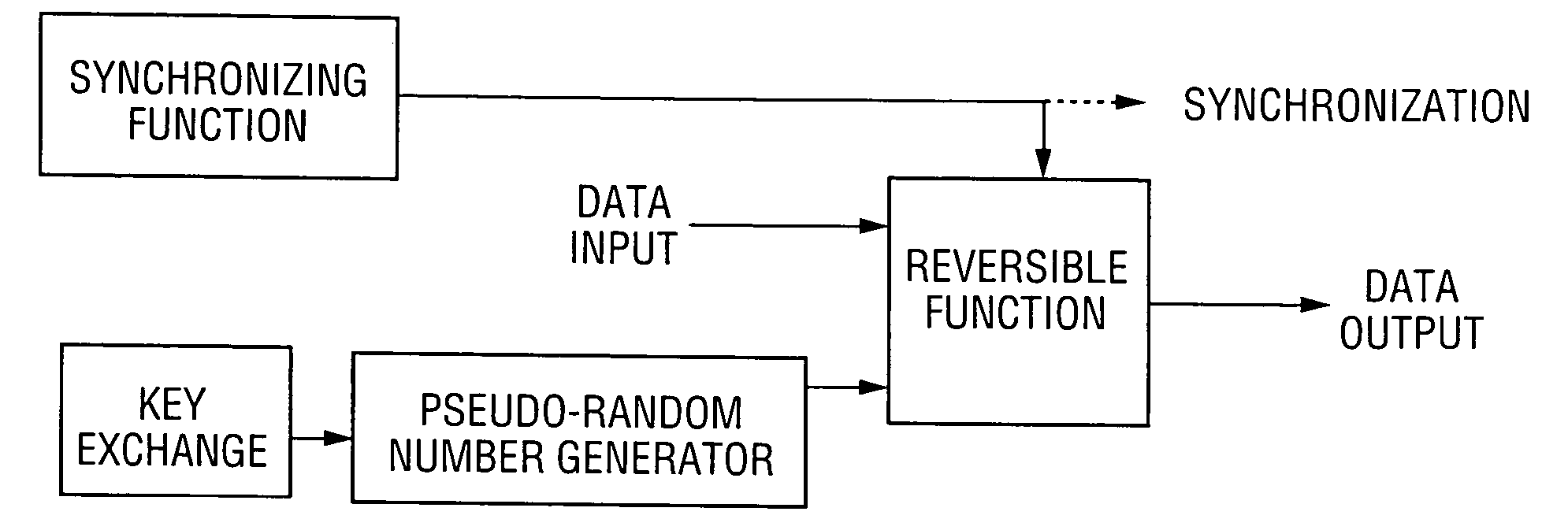
Method and apparatus for encrypting data transmitted over a serial link
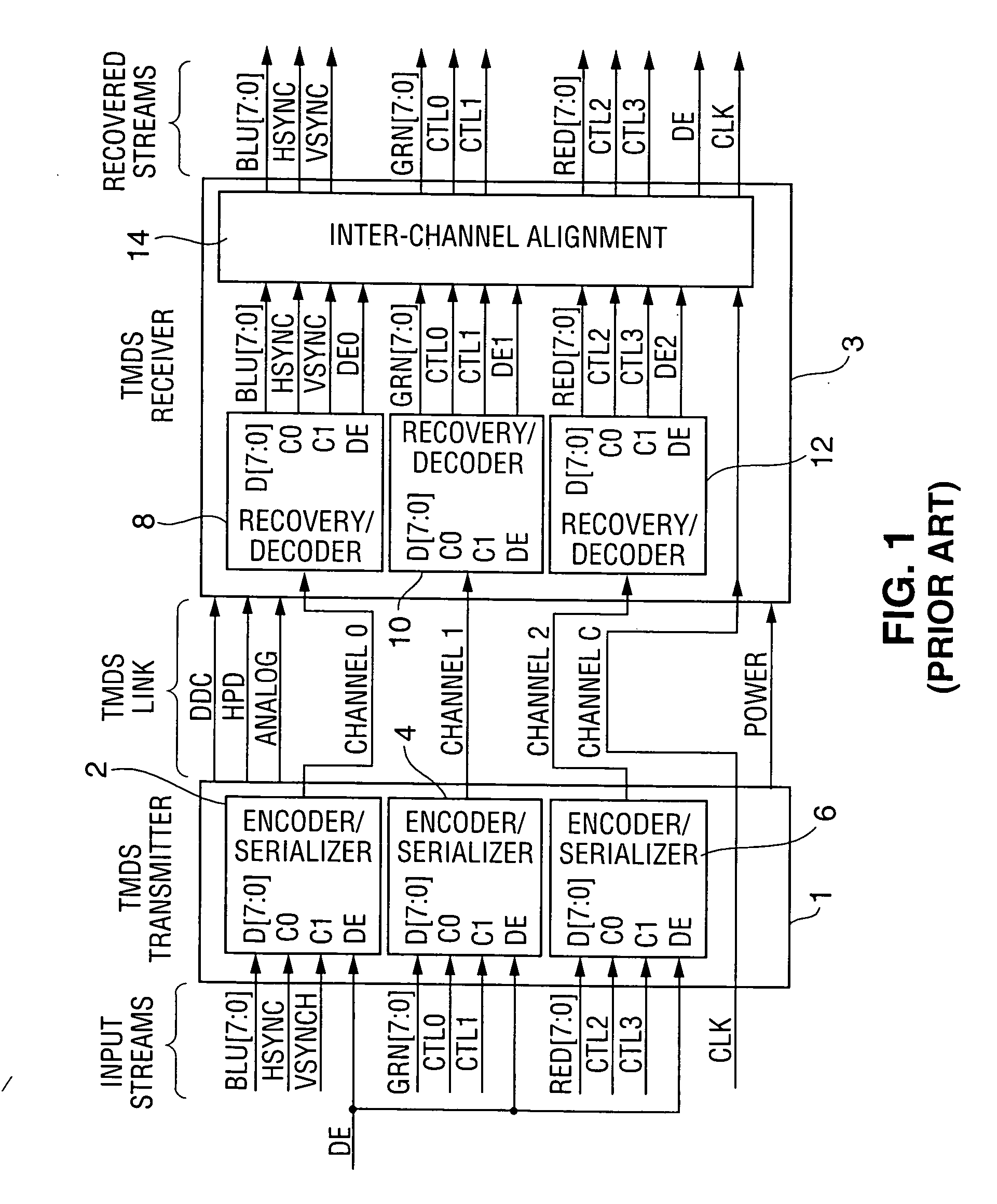
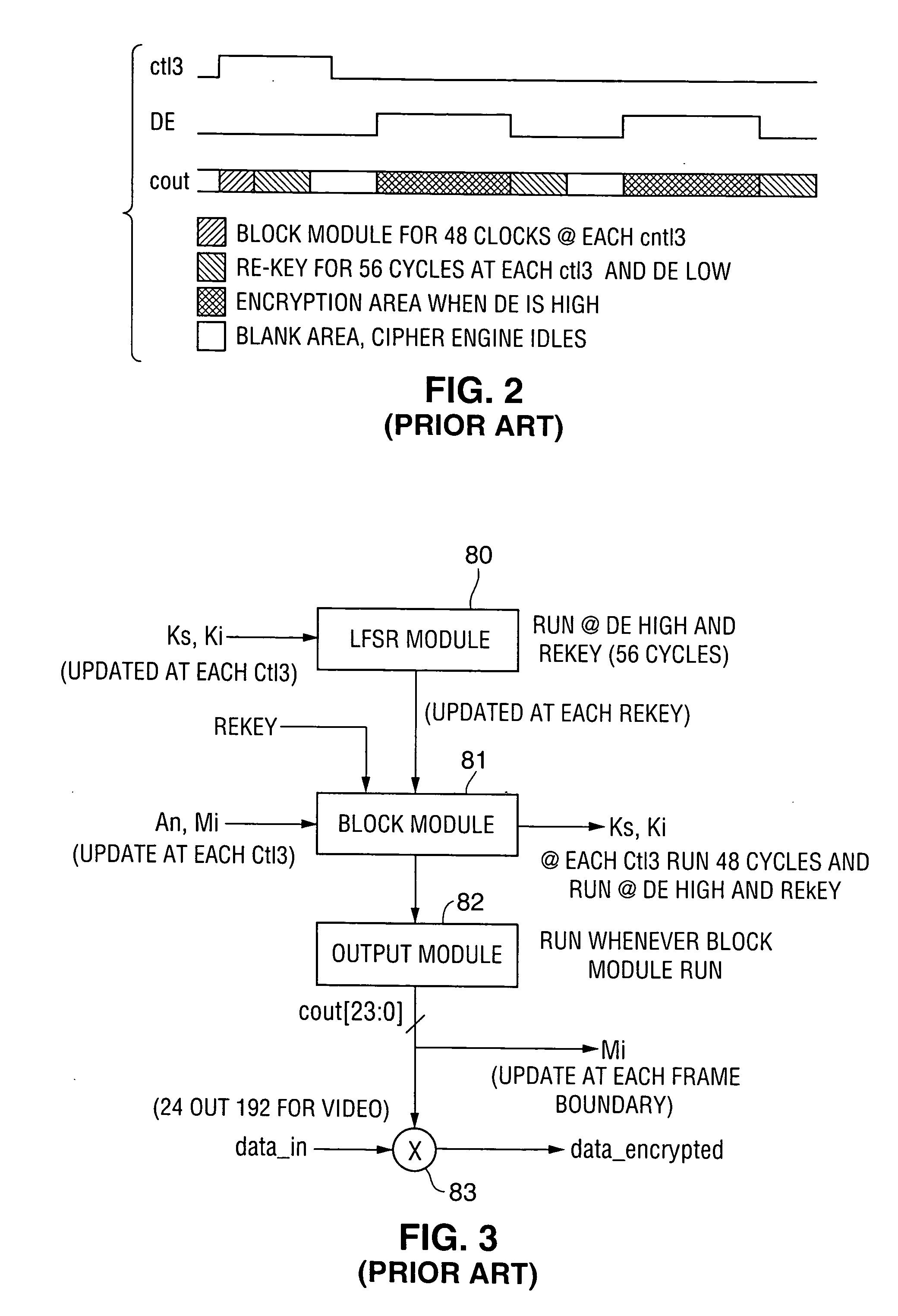
ActiveUS7131004B1Improve performanceSynchronising transmission/receiving encryption devicesData stream serial/continuous modificationComputer hardwareCommunications system
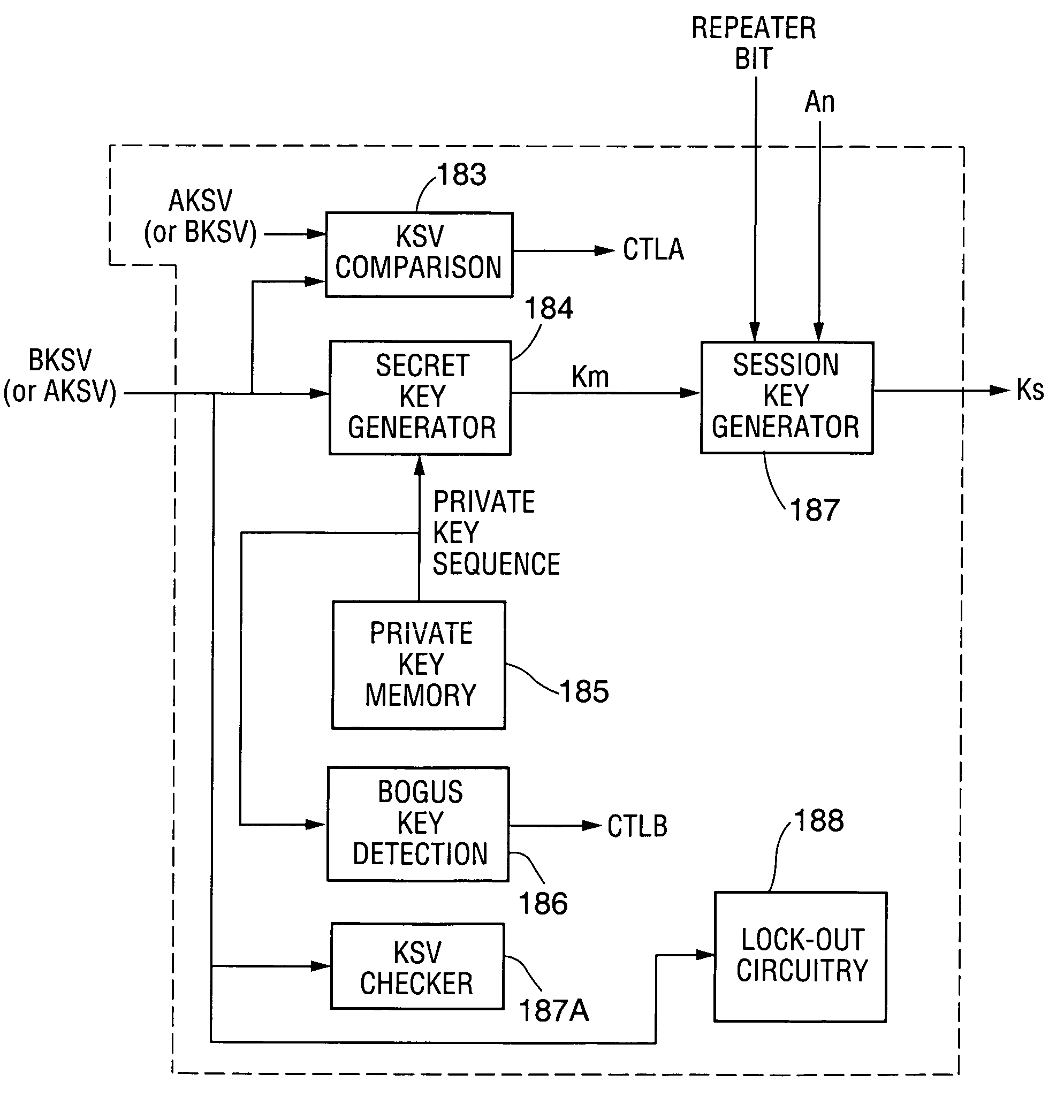
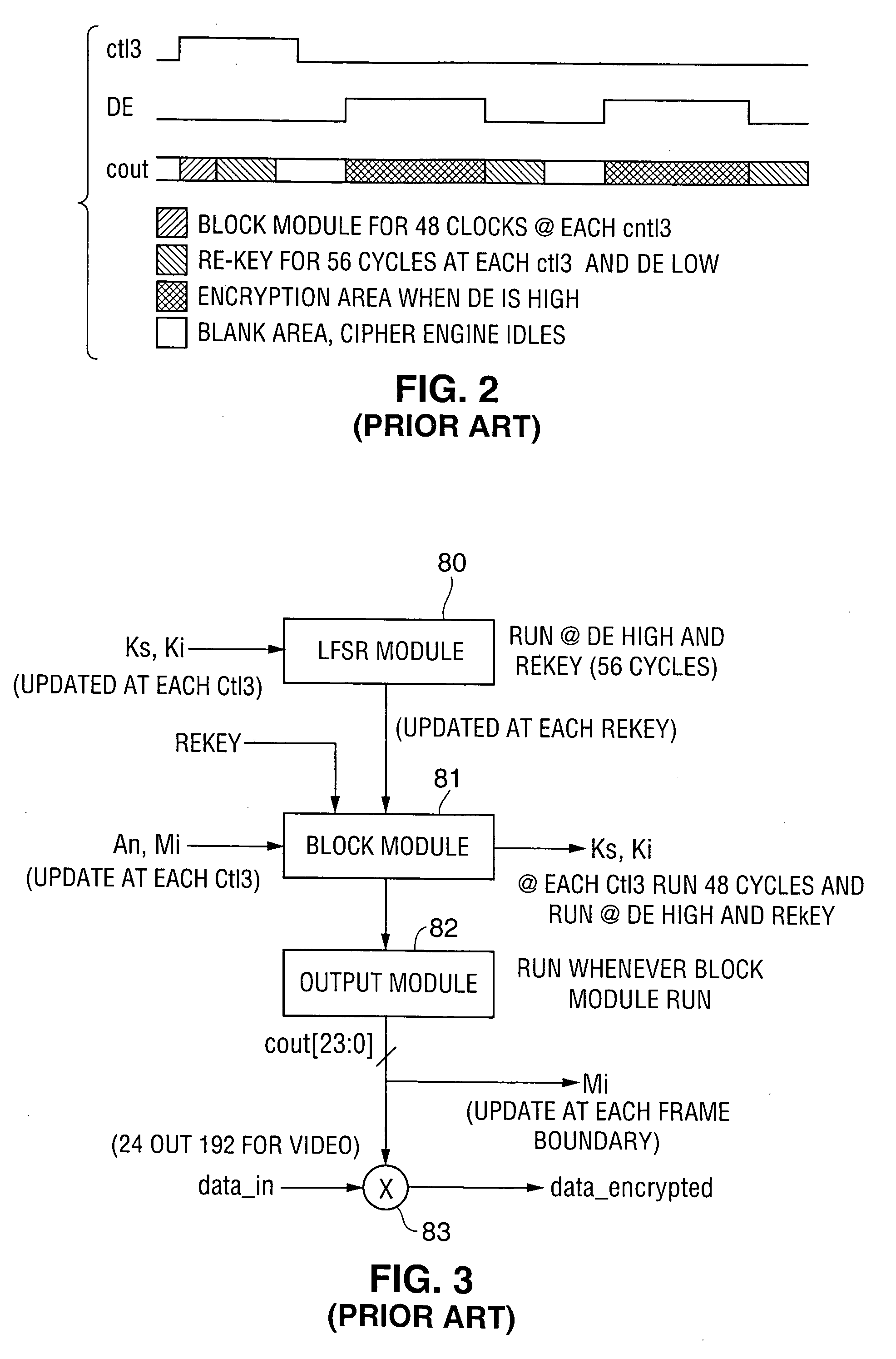
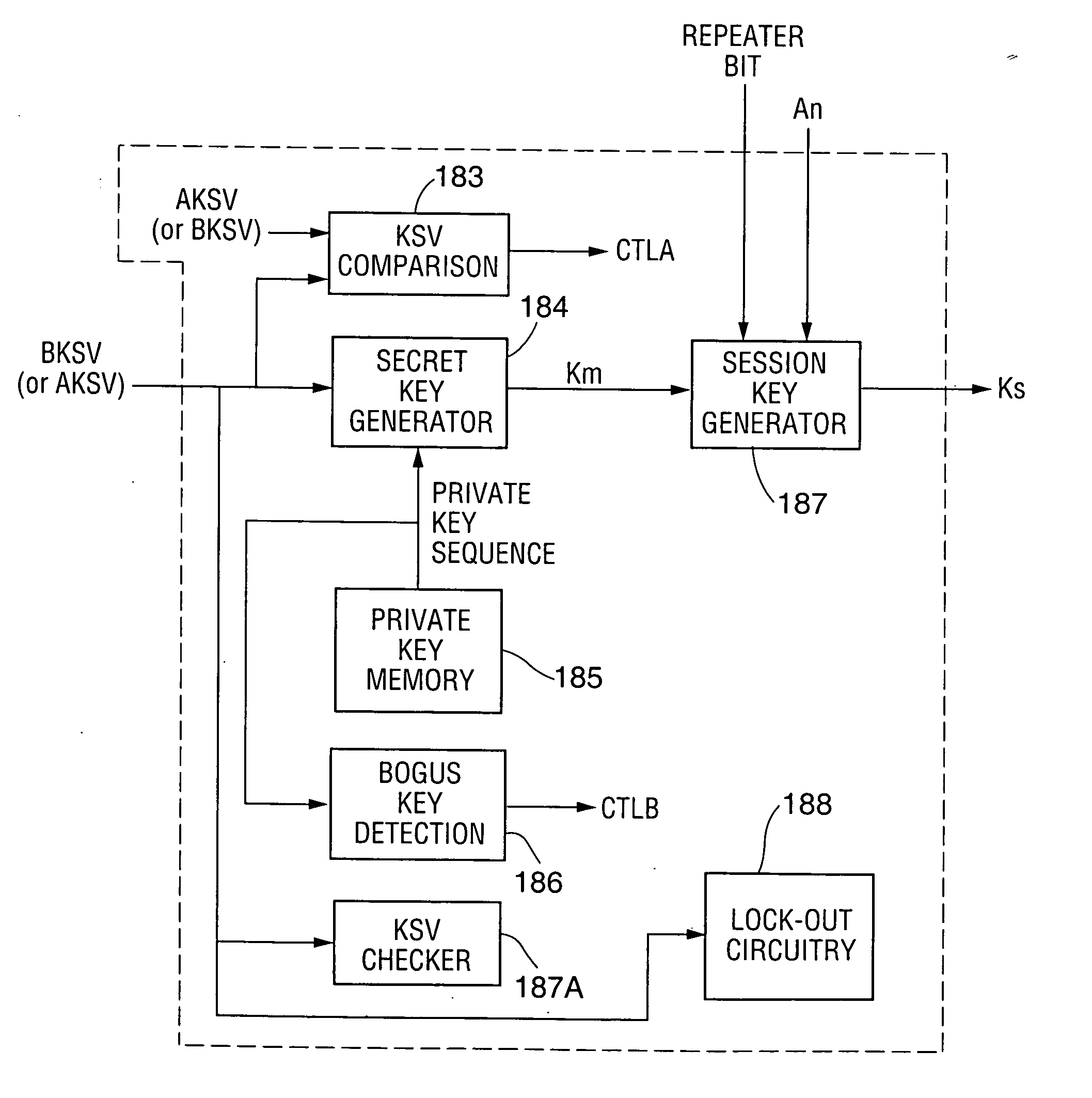
A communication system including a transmitter, a receiver, and a serial link (for example, a TMDS-like link) in which video data (or other data) are encrypted, the encrypted data are transmitted from the transmitter to the receiver, and the transmitted data are decrypted in the receiver, a transmitter and a receiver for use in such systems, a cipher engine for use in such a transmitter or receiver, a method for operating such a transmitter or receiver to encrypt or decrypt data, and a method for authenticating a receiver prior to transmission of encrypted data to the receiver over a serial link. Each transmitter, receiver, and cipher engine is configured to implement a content protection protocol in a manner that implements at least one and preferably more than one of a class of attack prevention features disclosed herein. In preferred embodiments the invention is employed to encrypt data in accordance with the High-bandwidth Digital Content Protection (“HDCP”) protocol, or a modified version of the HDCP protocol.
Owner:LATTICE SEMICON CORP
Virtual private network (VPN)-aware customer premises equipment (CPE) edge router
ActiveUS20040208122A1Metering/charging/biilling arrangementsError preventionPrivate networkNetwork architecture
A network architecture includes a communication network that supports one or more network-based Virtual Private Networks (VPNs). The communication network includes a plurality of boundary routers that are connected by access links to CPE edge routers belonging to the one or more VPNs. To prevent traffic from outside a customer's VPN (e.g., traffic from other VPNs or the Internet at large) from degrading the QoS provided to traffic from within the customer's VPN, the present invention gives precedence to intra-VPN traffic over extra-VPN traffic on each customer's access link through access link prioritization or access link capacity allocation, such that extra-VPN traffic cannot interfere with inter-VPN traffic. Granting precedence to intra-VPN traffic over extra-VPN traffic in this manner entails partitioning between intra-VPN and extra-VPN traffic on the physical access link using layer 2 multiplexing and configuration of routing protocols to achieve logical traffic separation between intra-VPN traffic and extra-VPN traffic at the VPN boundary routers and CPE edge routers. By configuring the access networks, the VPN boundary routers and CPE edge routers, and the routing protocols of the edge and boundary routers in this manner, the high-level service of DoS attack prevention is achieved.
Owner:VERIZON PATENT & LICENSING INC
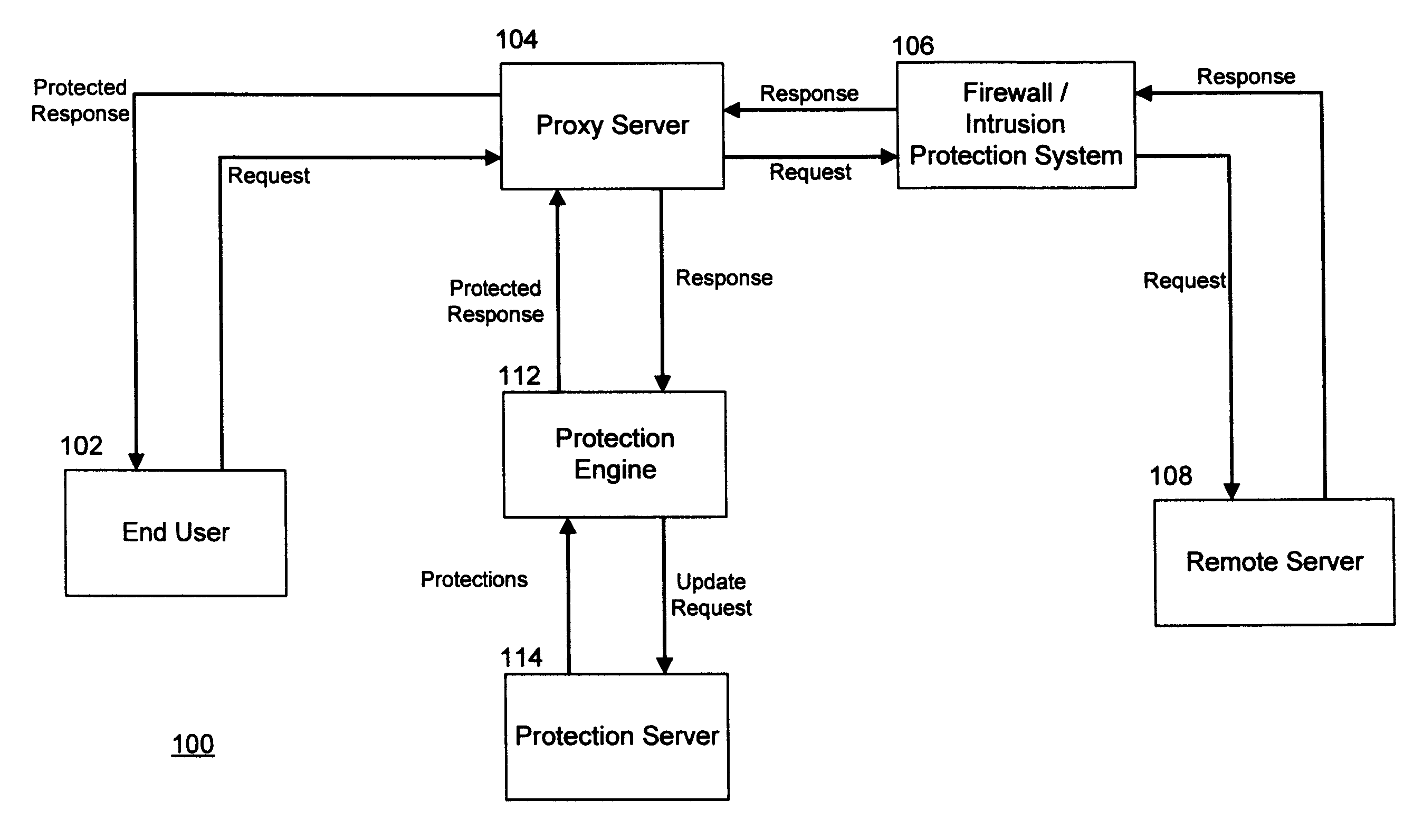
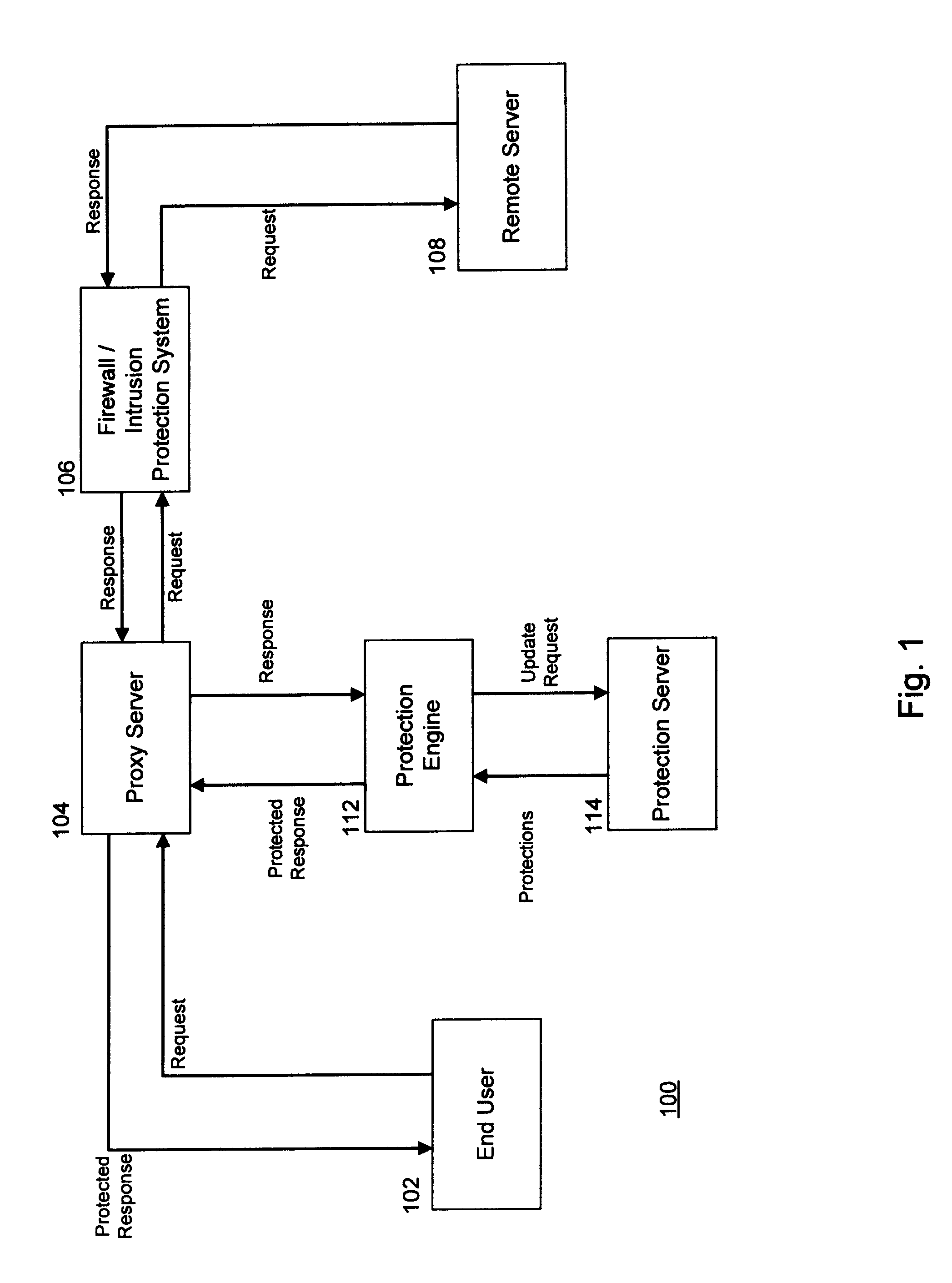
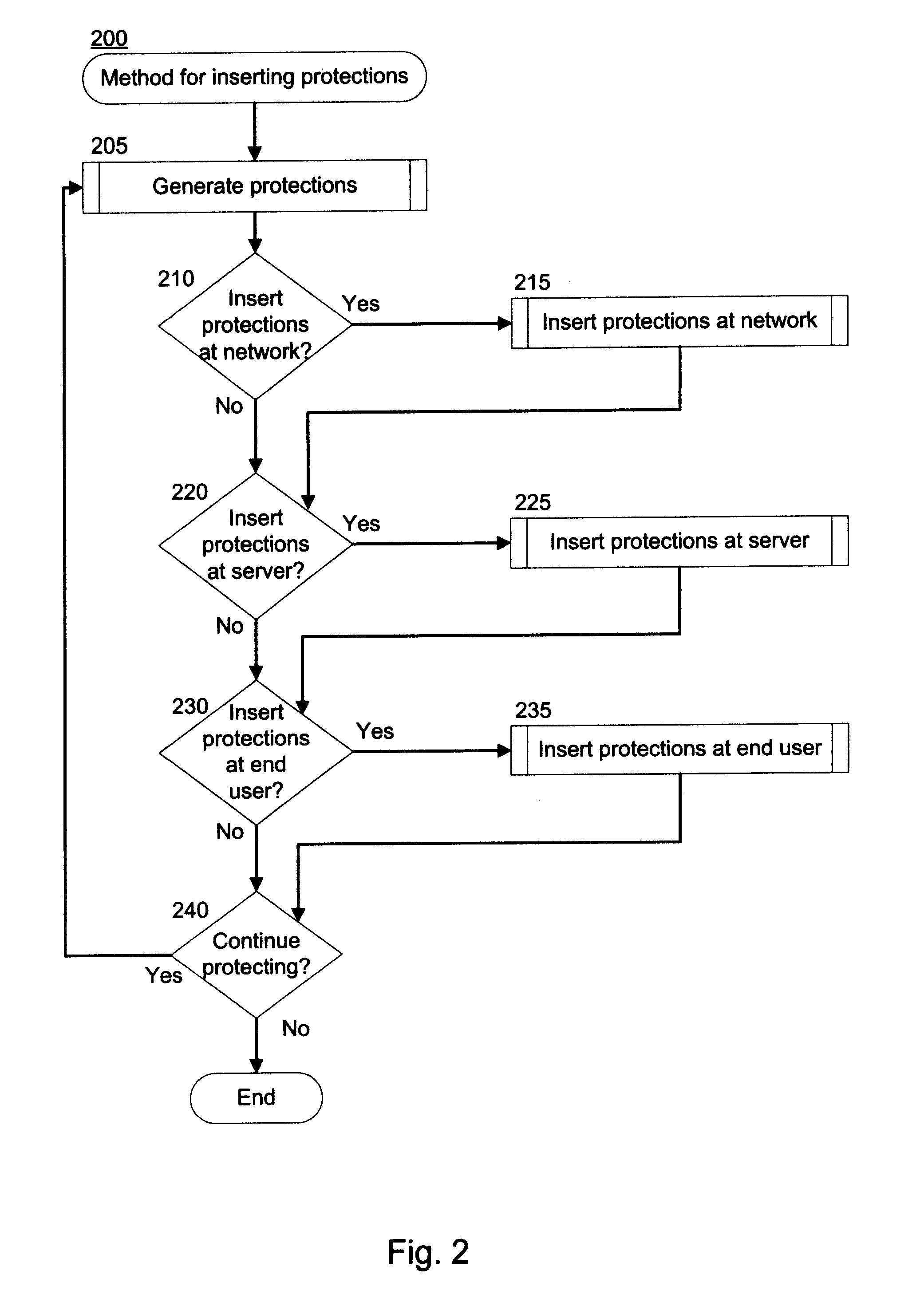
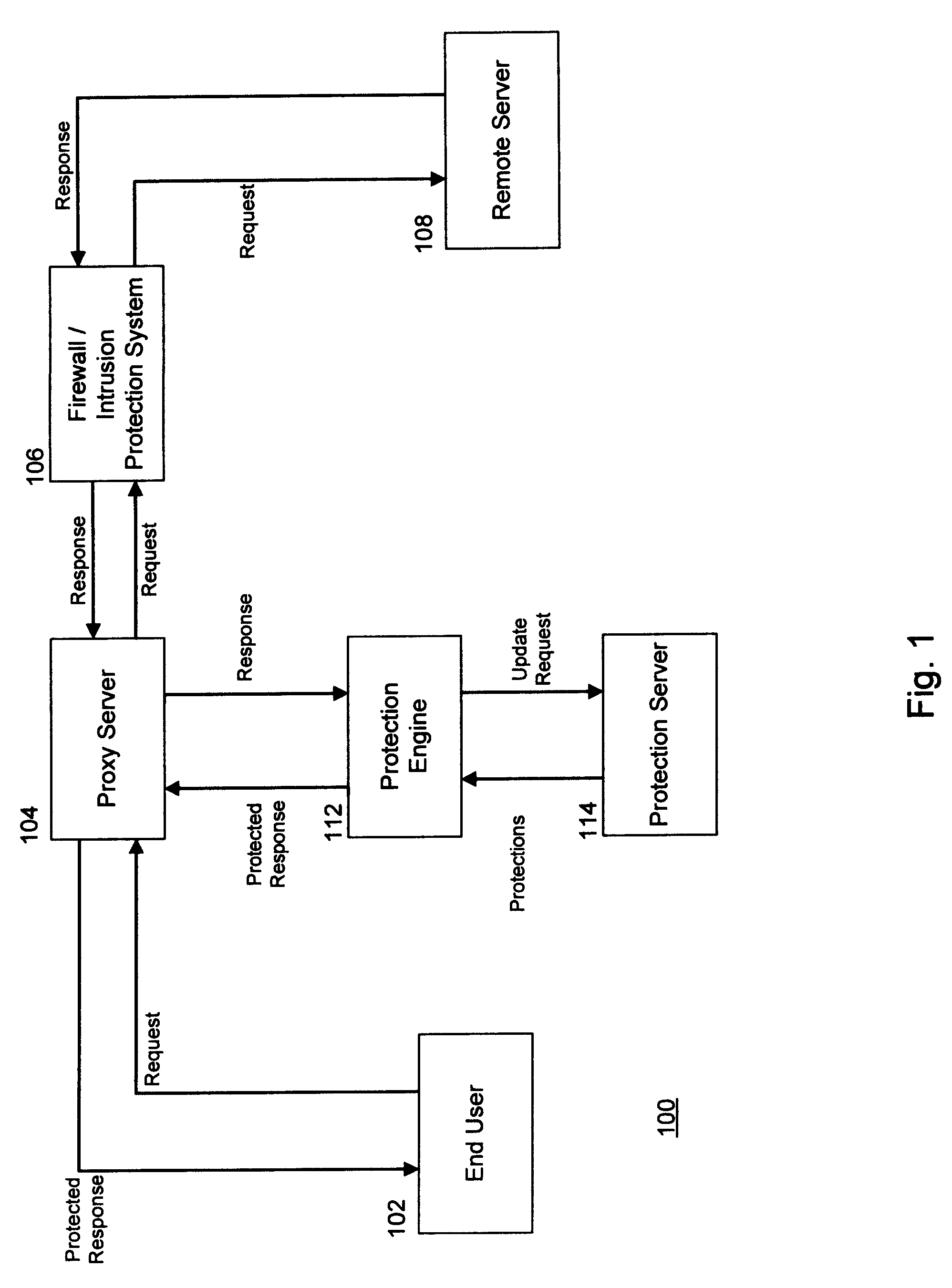
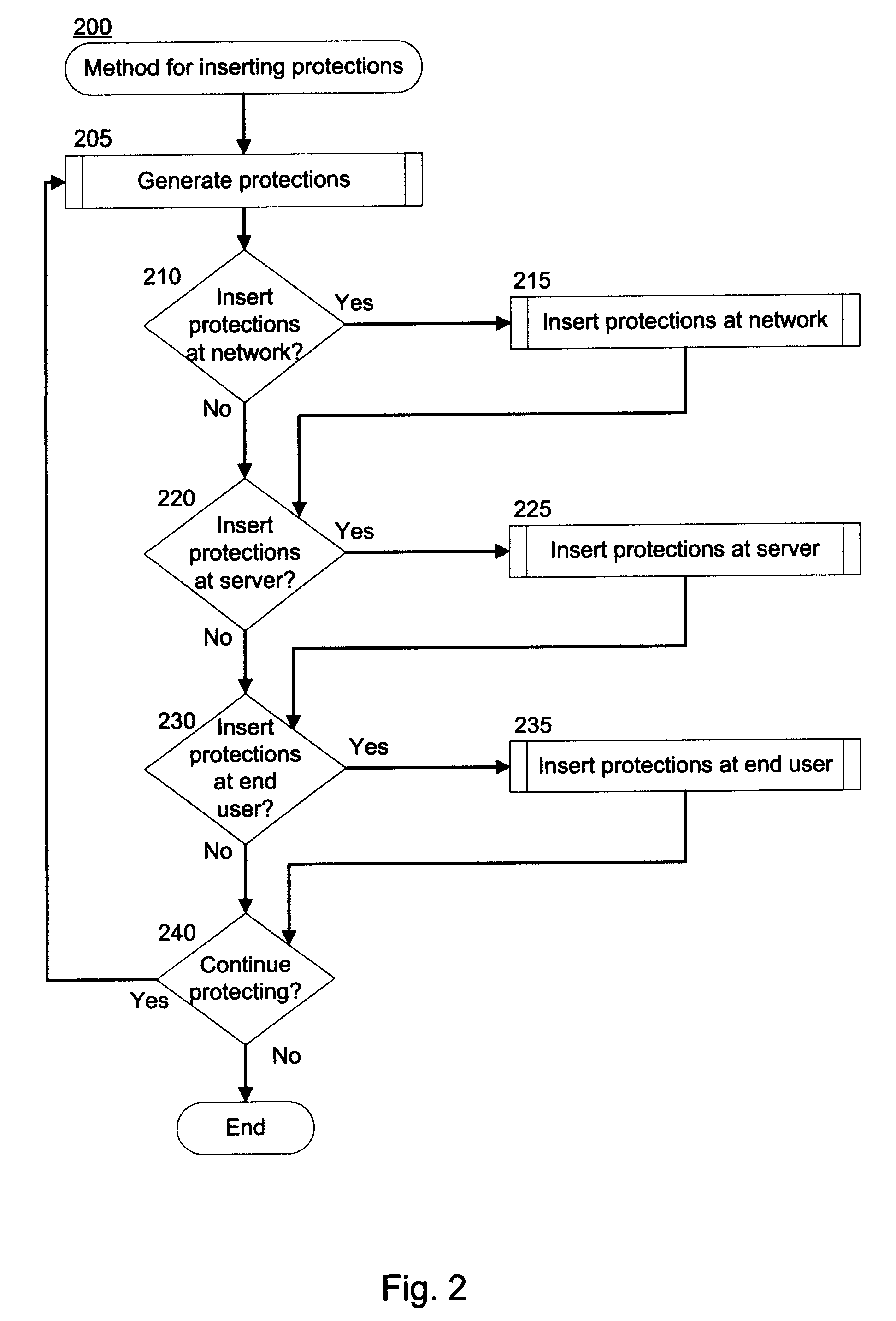
System and Method for Run-Time Attack Prevention
ActiveUS20100125913A1Avoid attackMemory loss protectionDigital data processing detailsRunning timeVulnerability
Preventing attacks on a computer at run-time. Content that is configured to access at least one function of a computer is received by the computer. Protections corresponding to the function are added to the content, wherein the protections override the function. The content and the protections are then transmitted to the computer. The function may expose a vulnerability of the computer, and arguments passed to the function may exploit that vulnerability. The protections are executed when the content is executed, and determine whether the arguments the content passed into the function represent a threat. In response to determining that the arguments represent a threat, execution of the content is terminated without executing the function.
Owner:SECUREWORKS
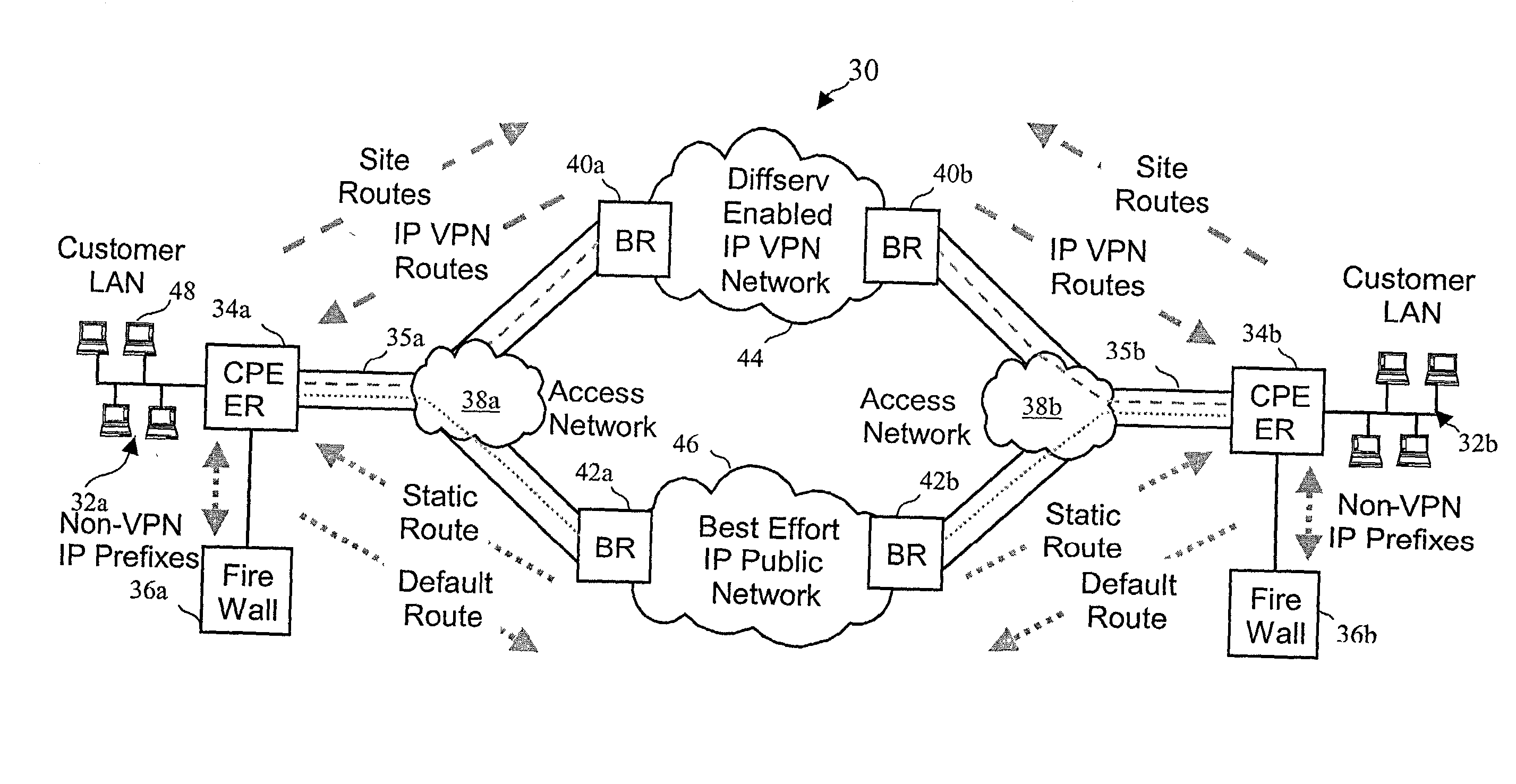
System, method and apparatus that employ virtual private networks to resist IP QoS denial of service attacks
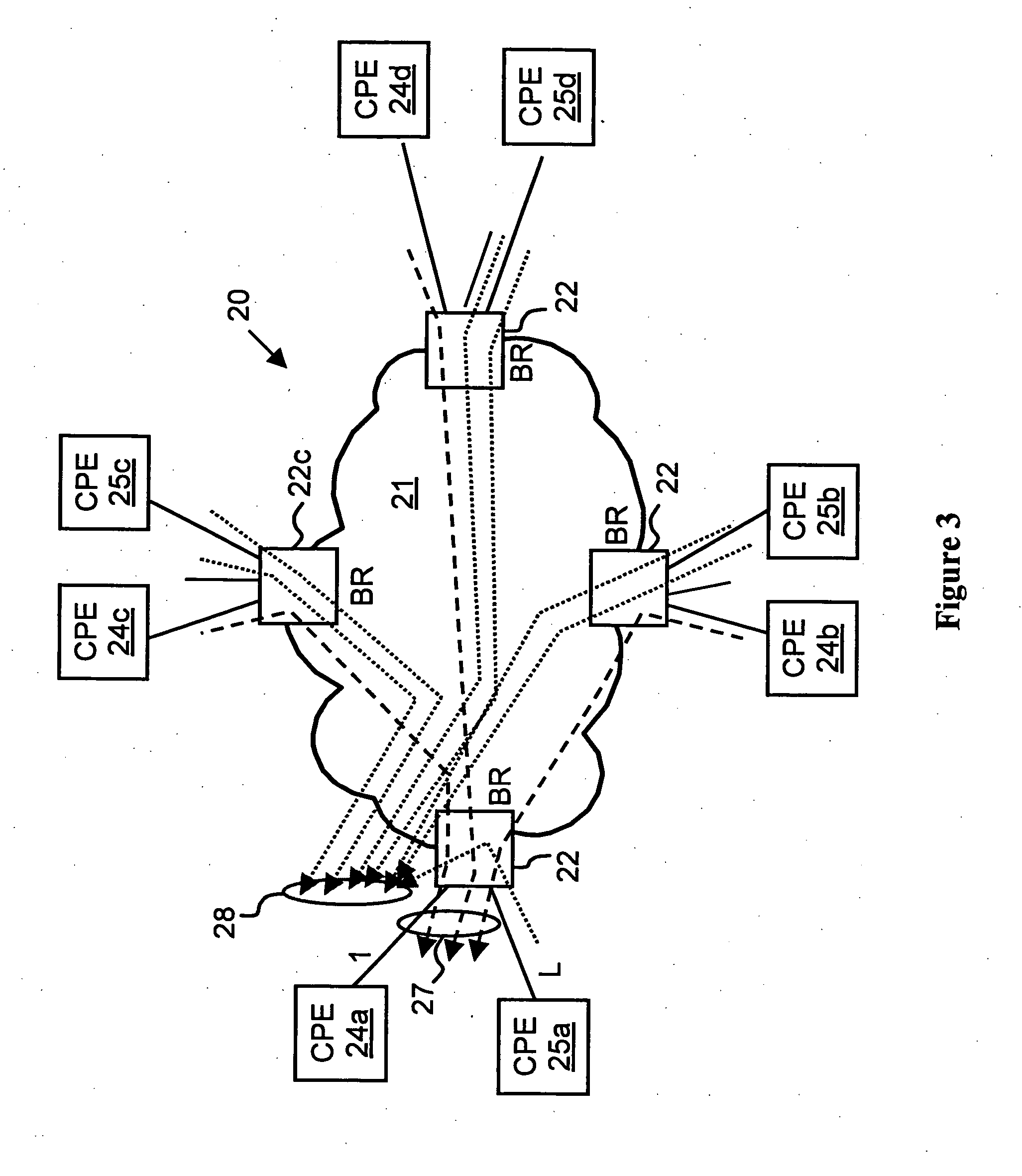
InactiveUS20030115480A1Error detection/correctionVolume/mass flow measurementPrivate networkThe Internet
A network architecture in accordance with the present invention includes a communication network that supports one or more network-based Virtual Private Networks (VPNs). The communication network includes a plurality of boundary routers that are connected by access links to CPE edge routers belonging to the one or more VPNs. To prevent traffic from outside a customer's VPN (e.g., traffic from other VPNs or the Internet at large) from degrading the QoS provided to traffic from within the customer's VPN, the present invention gives precedence to intra-VPN traffic over extra-VPN traffic on each customer's access link through access link prioritization or access link capacity allocation, such that extra-VPN traffic cannot interfere with inter-VPN traffic. Granting precedence to intra-VPN traffic over extra-VPN traffic in this manner entails special configuration of network elements and protocols, including partitioning between intra-VPN and extra-VPN traffic on the physical access link using layer 2 multiplexing and the configuration of routing protocols to achieve logical traffic separation between intra-VPN traffic and extra-VPN traffic at the VPN boundary routers and CPE edge routers. By configuring the access networks, the VPN boundary routers and CPE edge routers, and the routing protocols of the edge and boundary routers in this manner, the high-level service of DoS attack prevention is achieved.
Owner:VERIZON PATENT & LICENSING INC
Method of providing cyber security as a service
InactiveUS20140259095A1Memory loss protectionError detection/correctionChange managementNetworked system
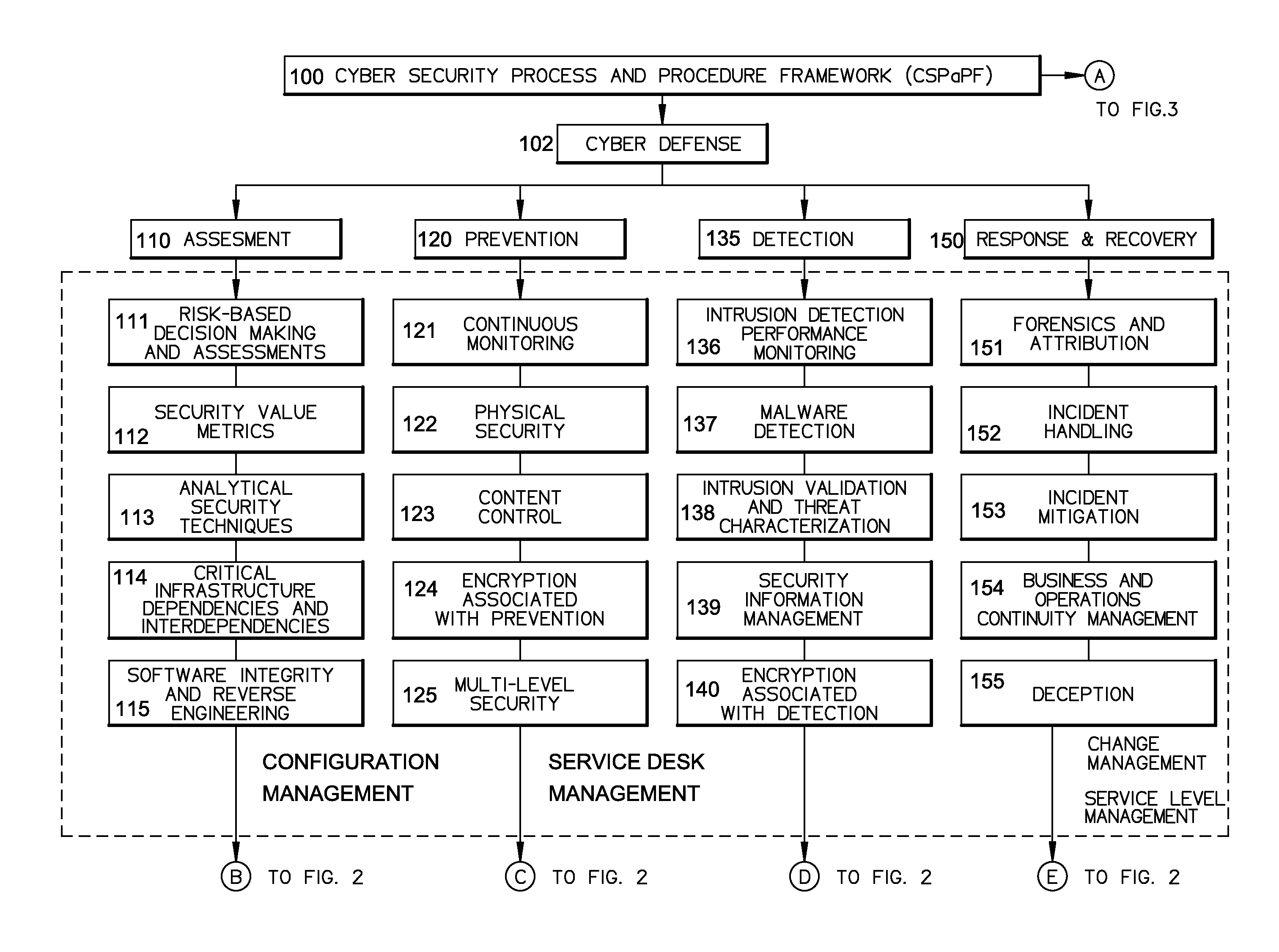
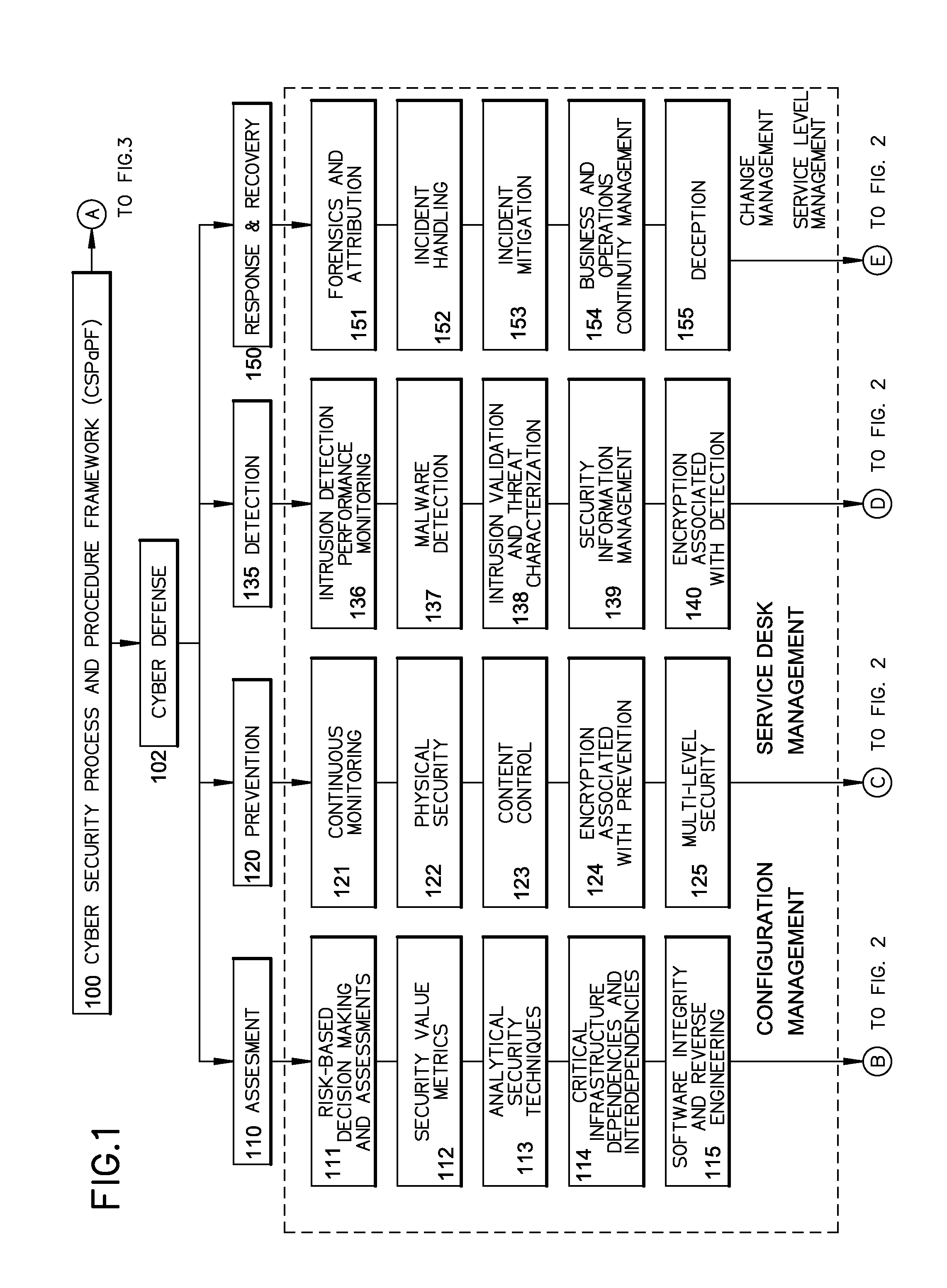
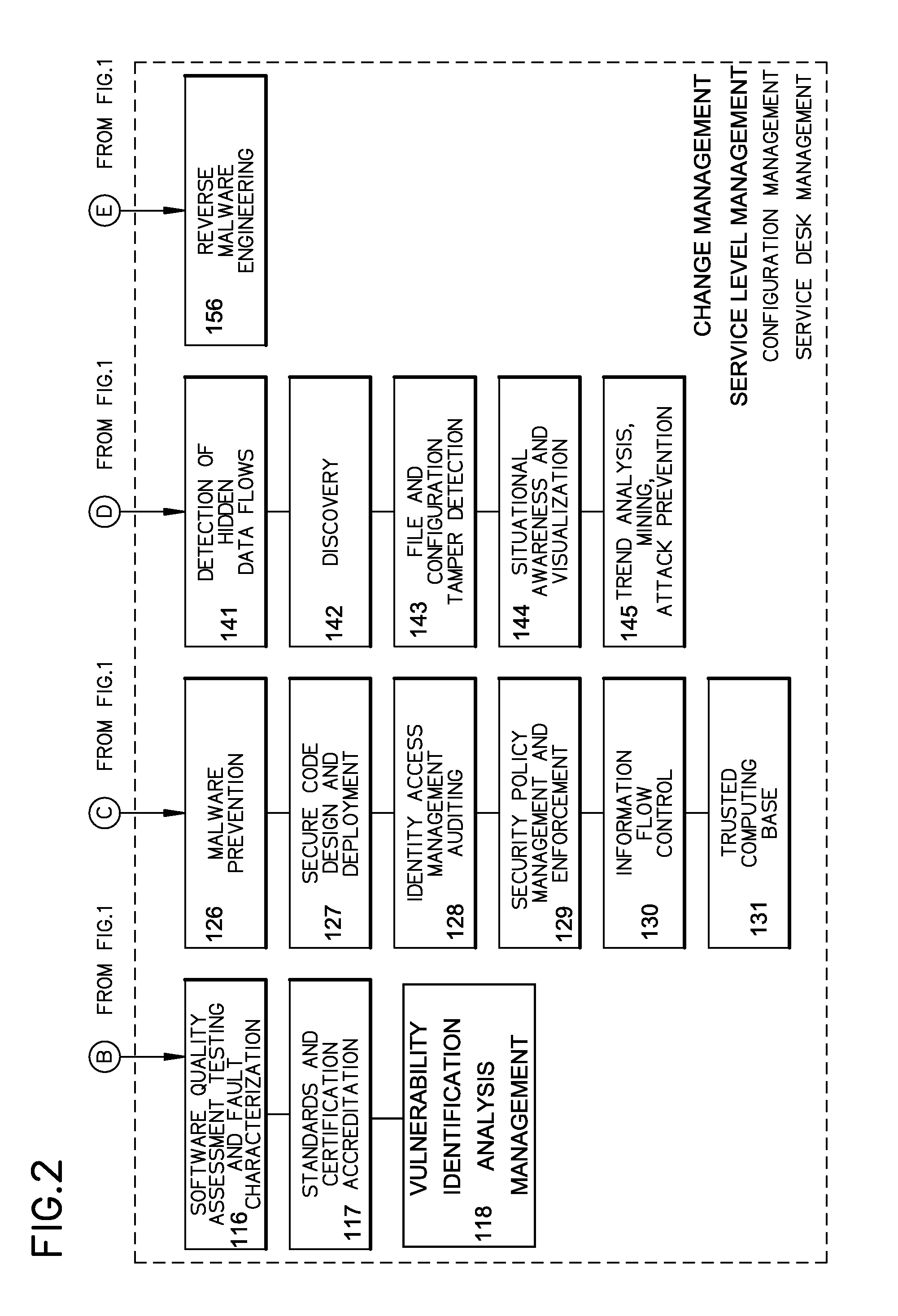
A cyber system including a method of providing cyber security as a service is provided. The cyber system may include an integrated architecture of defensive and offensive security procedures and processes that enable enterprises to practice safe, holistic security techniques. The plurality of cyber defense procedures may include a plurality of risk-based assessment procedures, a plurality of attack-prevention procedures, a plurality of detection procedures and a plurality of response and recovery procedures. The plurality of cyber offense procedures may include a plurality of cyber weapon procedures, a plurality of cyber Intelligence, surveillance and reconnaissance procedures, a plurality of information operations target exploitation procedures and a plurality of information operations attack procedures. The cyber system may also include a plurality of overlapping processes interconnecting the plurality of cyber offense procedures and plurality of cyber defense procedures. The plurality of overlapping processes may include a change management, a configuration management, a service desk and a service-level management. The change management may be structured within an enterprise for ensuring that changes in people, facilities, technology and / or processes are smoothly and successfully implemented to achieve lasting benefits. The configuration management may establish and maintain the consistency of a product's performance, functional and physical attributes with its requirements, design and operational information throughout its life. The service desk may provide the communication needs of the users, employees and customers. Service-level management may assess the impact of change on service quality and establish performance metrics and benchmarks.
Owner:BRYANT JAMES ALVIN
Systems and methods for http-body DOS attack prevention with adaptive timeout
ActiveUS20140304798A1Facilitate mitigating adverse effectKeep for a long timeMultiple digital computer combinationsProgram controlTransport layerClient-side
The present disclosure is directed generally to systems and methods for changing an application layer transaction timeout to prevent Denial of Service attacks. A device intermediary to a client and a server may receive, via a transport layer connection between the device and the client, a packet of an application layer transaction. The device may increment an attack counter for the transport layer connection by a first predetermined amount responsive to a size of the packet being less than a predetermined fraction of a maximum segment size for the transport layer connection. The device may increment the attack counter by a second predetermined amount responsive to an inter-packet-delay between the packet and a previous packet being more than a predetermined multiplier of a round trip time. The device may change a timeout for the application layer transaction responsive to comparing the attack counter to a predetermined threshold.
Owner:CITRIX SYST INC
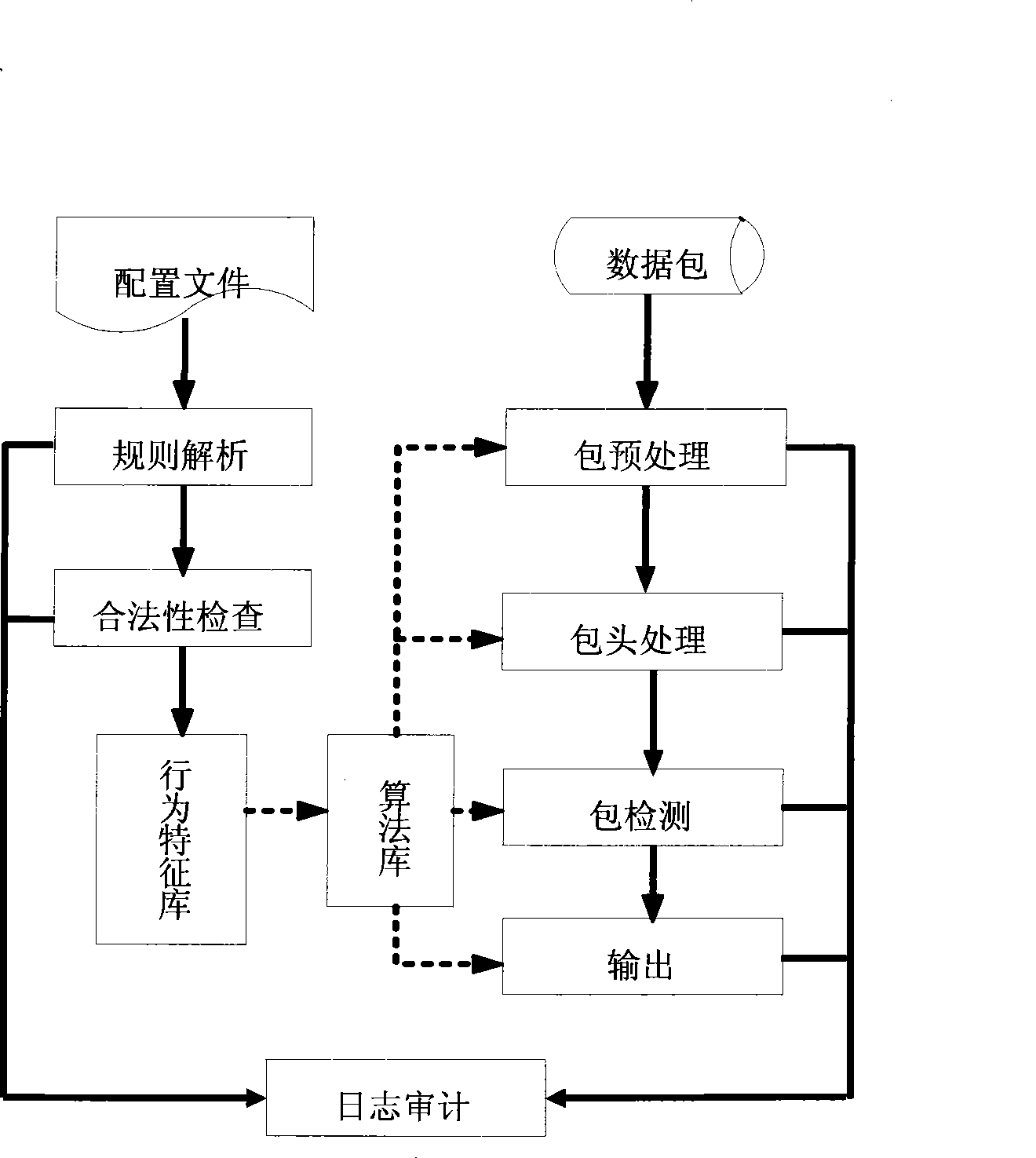
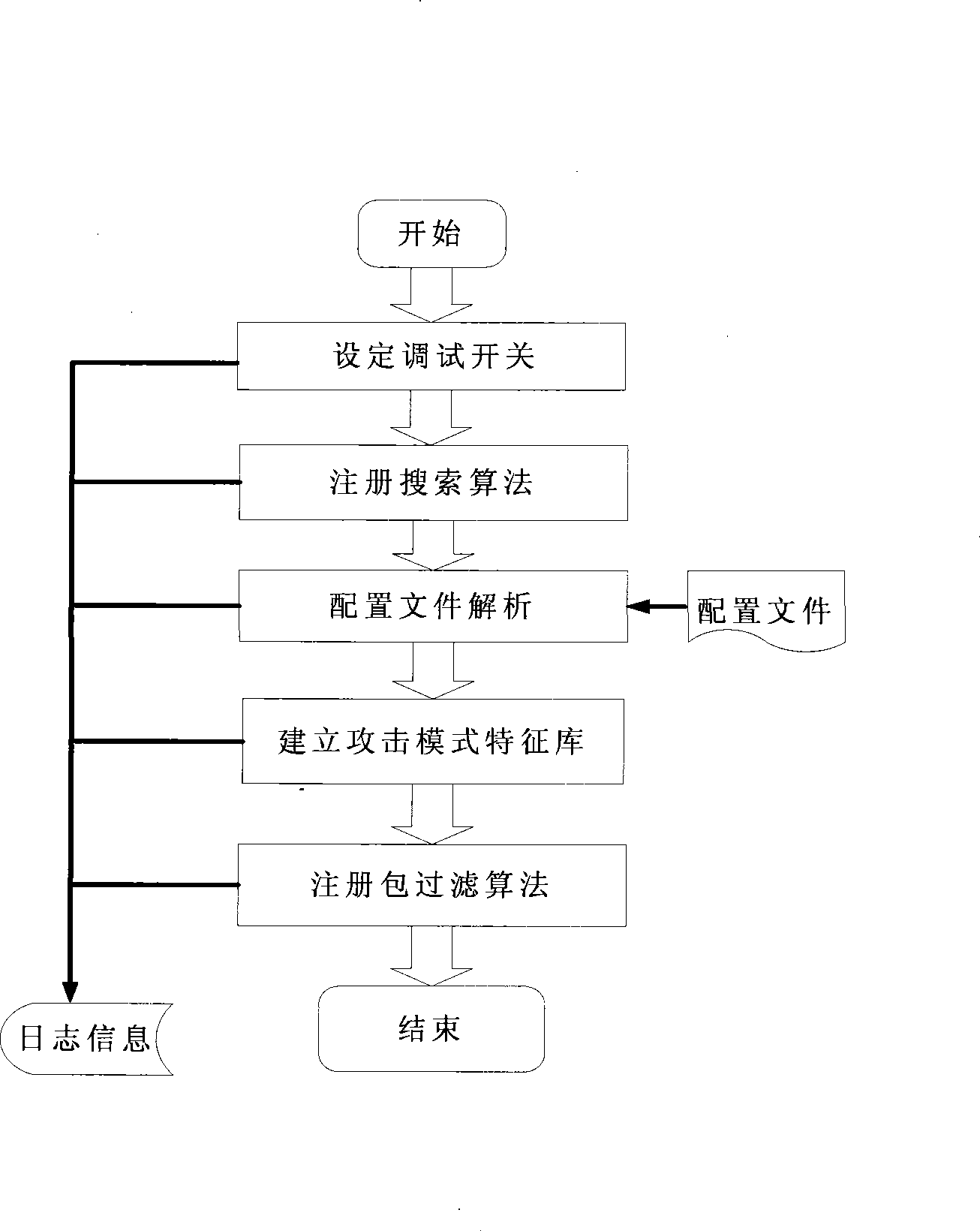
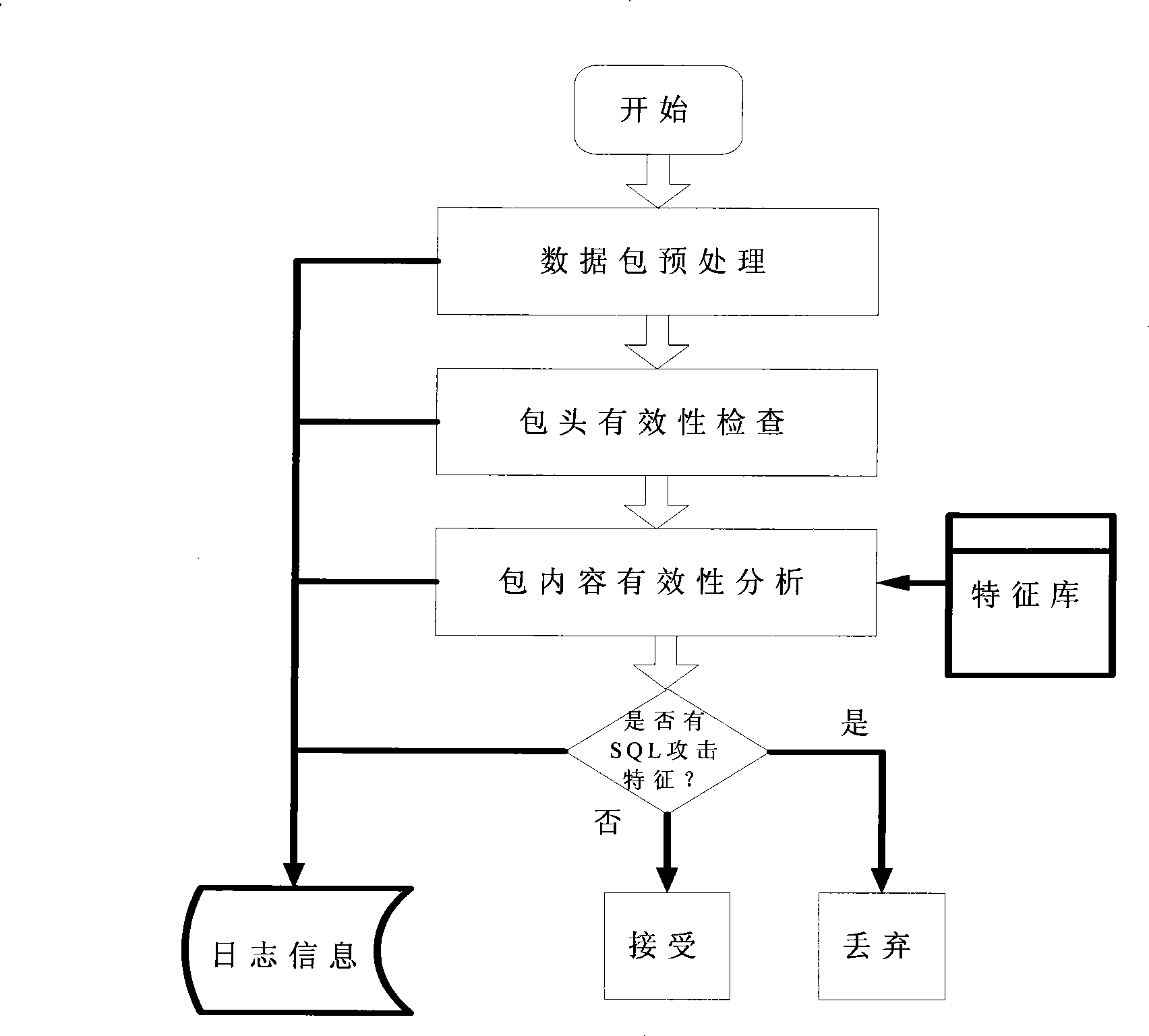
Attack prevention system based on structured query language (SQL)
ActiveCN101448007AImprove accuracyNo false positivesData switching networksSpecial data processing applicationsFeature extractionApplication server
The invention provides a modified misuse-type structured query language (hereinafter referred as to SQL) attack defense system which is based on application system services and an SQL-injected characteristic extraction malicious attack behavior characteristic library and combined with the SQL request of the characteristic library to a user to carry out strict test and block the SQL request with the attack characteristics according to test results, so as to provide the security protection for the database and the corresponding audit record. The invention can be flexibly allocated to boundary defense devices, application servers, database servers and various security audit software, and the SQL attack behavior characteristic library can be updated at any time when the application environment is changed and a new attack type or normal behavior pattern appears.
Owner:CHINA ELECTRIC POWER RES INST +2
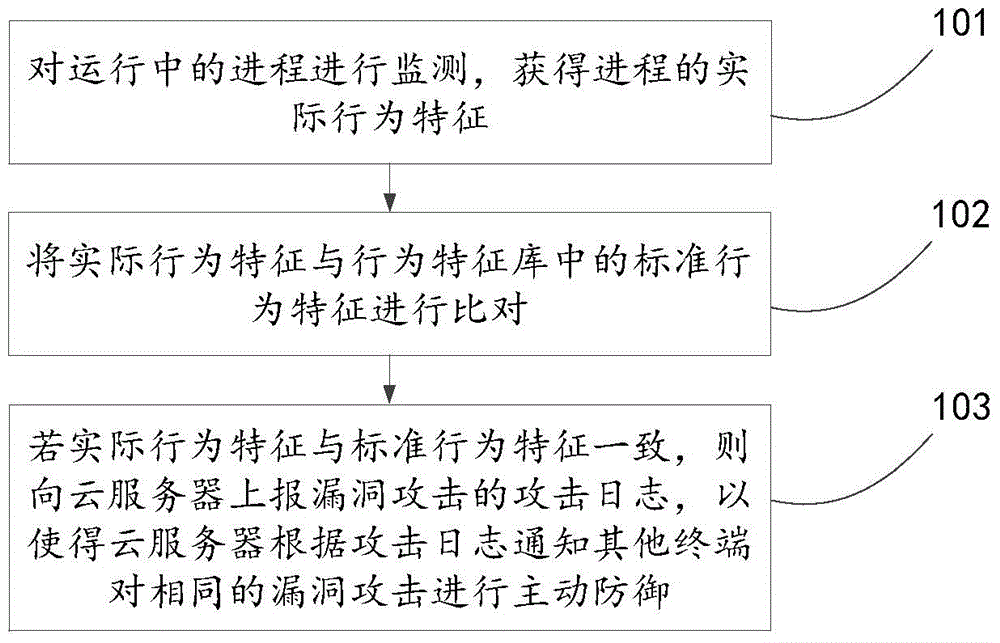
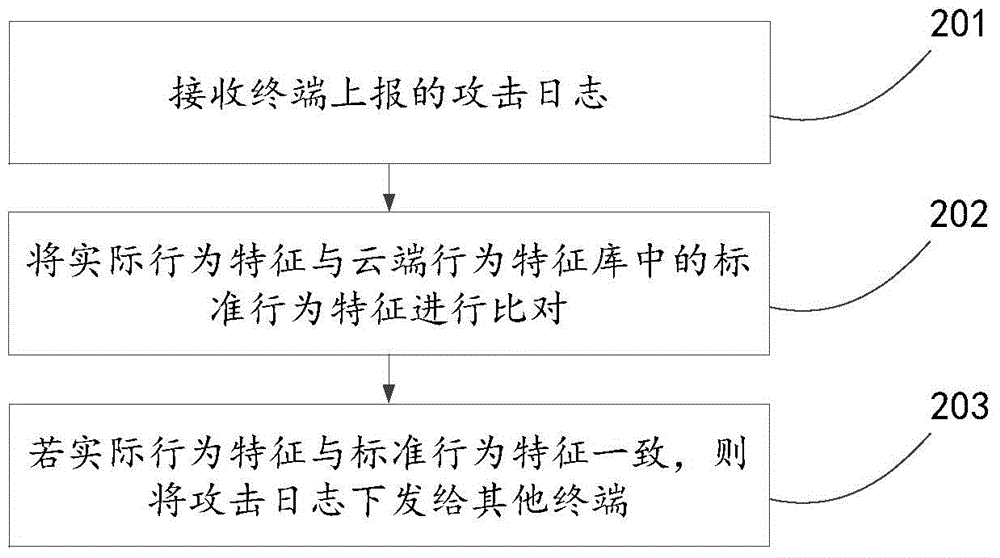
Loophole attack prevention method, device and system
The invention discloses a loophole attack prevention method, device and system, and relates to the field of network security. The loophole attack prevention method, device and system aim to actively defense a loophole attack timely and effectively under the situation that a loophole is not repaired. The method includes the steps that a running process is monitored, the actual behavior feature of the process is obtained, and the process comprises an application process and a system process; the actual behavior feature is compared with a standard behavior feature in a behavior feature library, and the standard behavior feature is used for describing behaviors related to the loophole attack; if the actual behavior feature is consistent with the standard behavior feature, an attack log of the loophole attack is reported to a cloud server so that the cloud server can inform other terminals to actively defense the same loophole attack according to the attack log. The loophole attack prevention method is mainly applied to active attack defense under a private cloud environment.
Owner:BEIJING QIHOO TECH CO LTD +1
Method and device for verifying integrity of security critical data of program in process of running
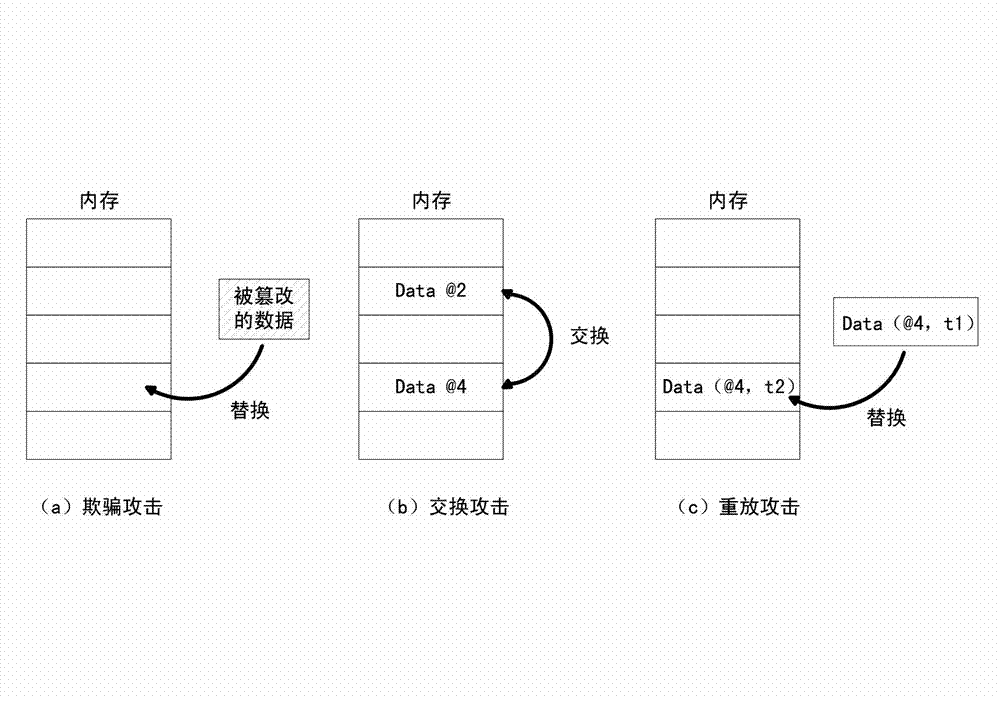
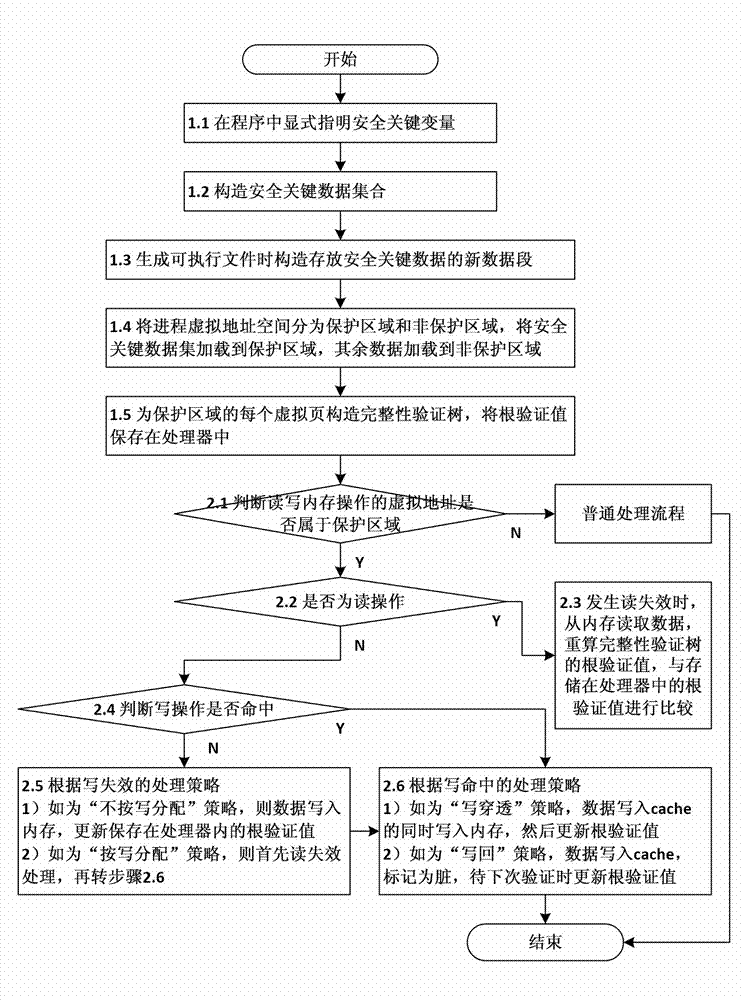
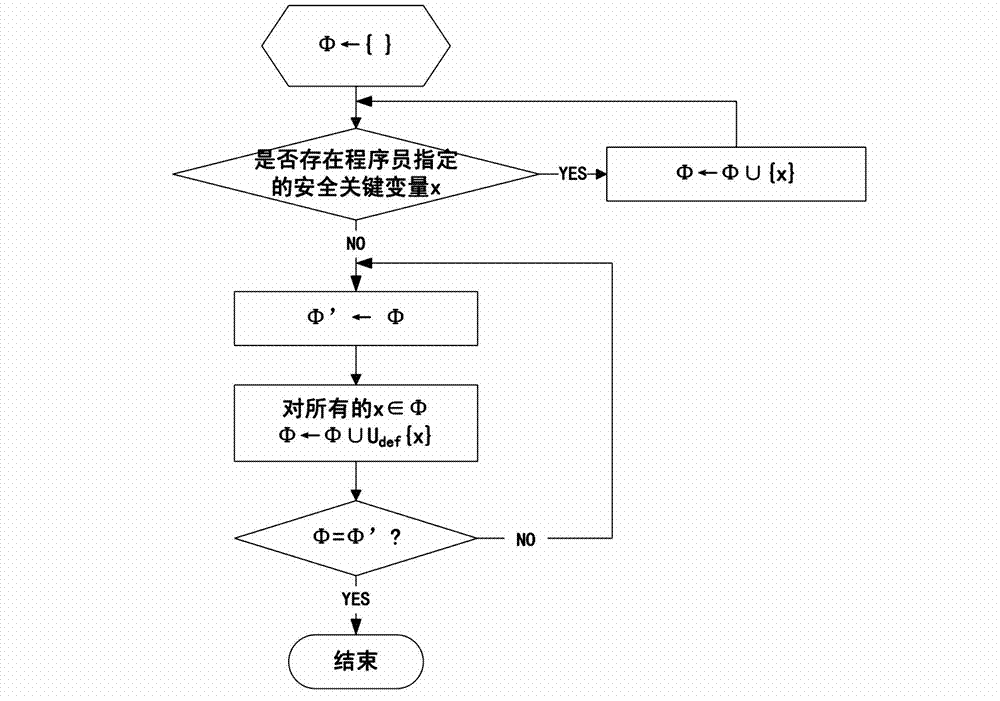
ActiveCN102930185AAvoid attackIntegrity verification implementationProgram/content distribution protectionData setData integrity
The invention discloses a method and a device for verifying the integrity of security critical data of a program in the process of running. The method comprises the following steps: 1) indicating a security critical variable in the program, generating a security critical data set in the process of compiling, dividing a virtual address space of the program into a protected area and a non-protected area in the process of loading the program, loading the security critical data set to the protected area, and constructing an integrity verification tree for a virtual page of the protected area of the program; and 2) in the process of writing program data into a memory, updating a root verification value; and in the process of reading program data from the memory, generating a new root verification value, comparing the new root verification value with the original root verification value, if the two are equal, determining that the security critical data set is not tampered, otherwise, determining that the security critical data set is tampered. The device comprises a data integrity verification circuit, a root verification value storage module and a comparator. The method and the device disclosed by the invention have the advantages of high safety performance, strong attack prevention performance, small calculated amount, and less occupied storage space.
Owner:NAT UNIV OF DEFENSE TECH
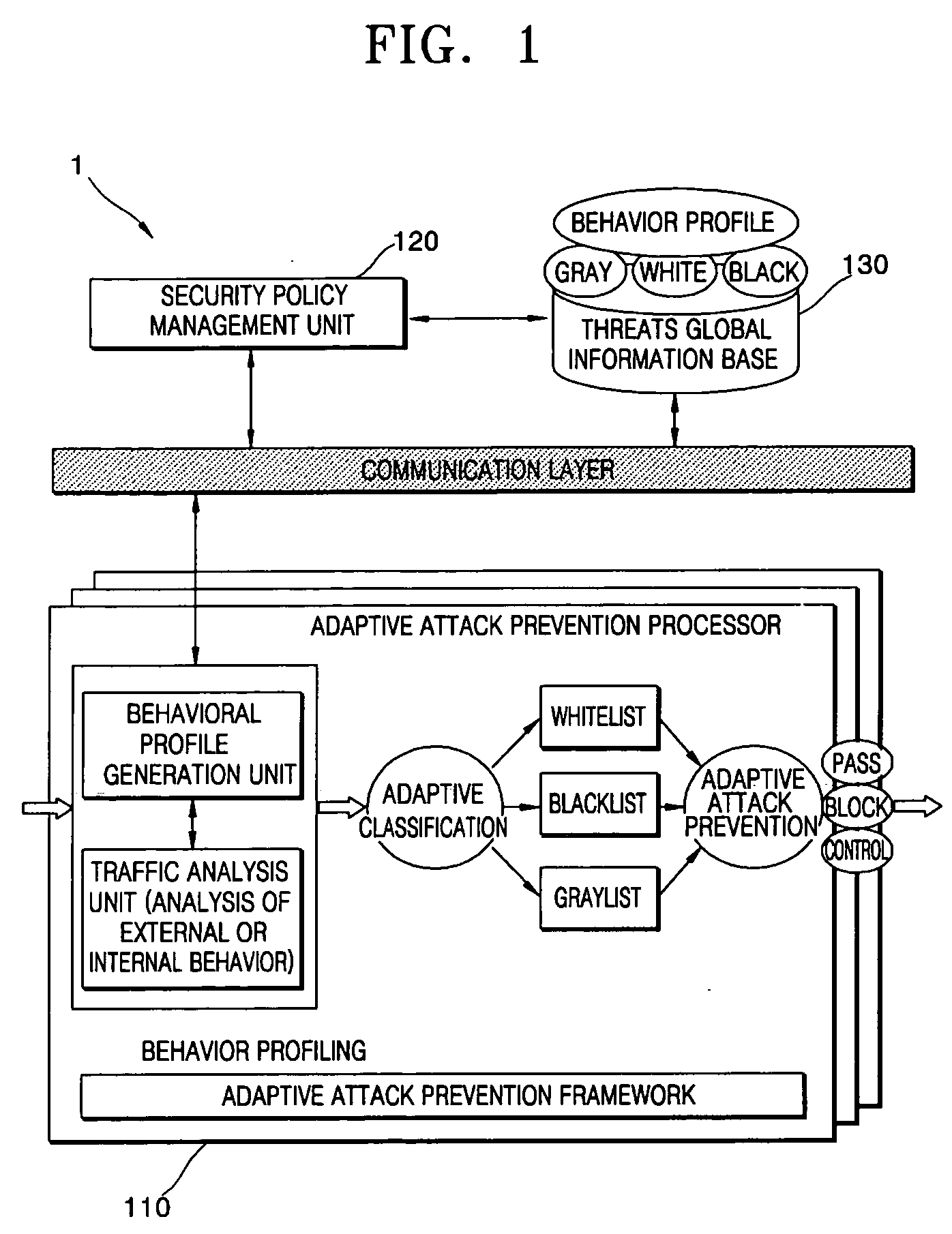
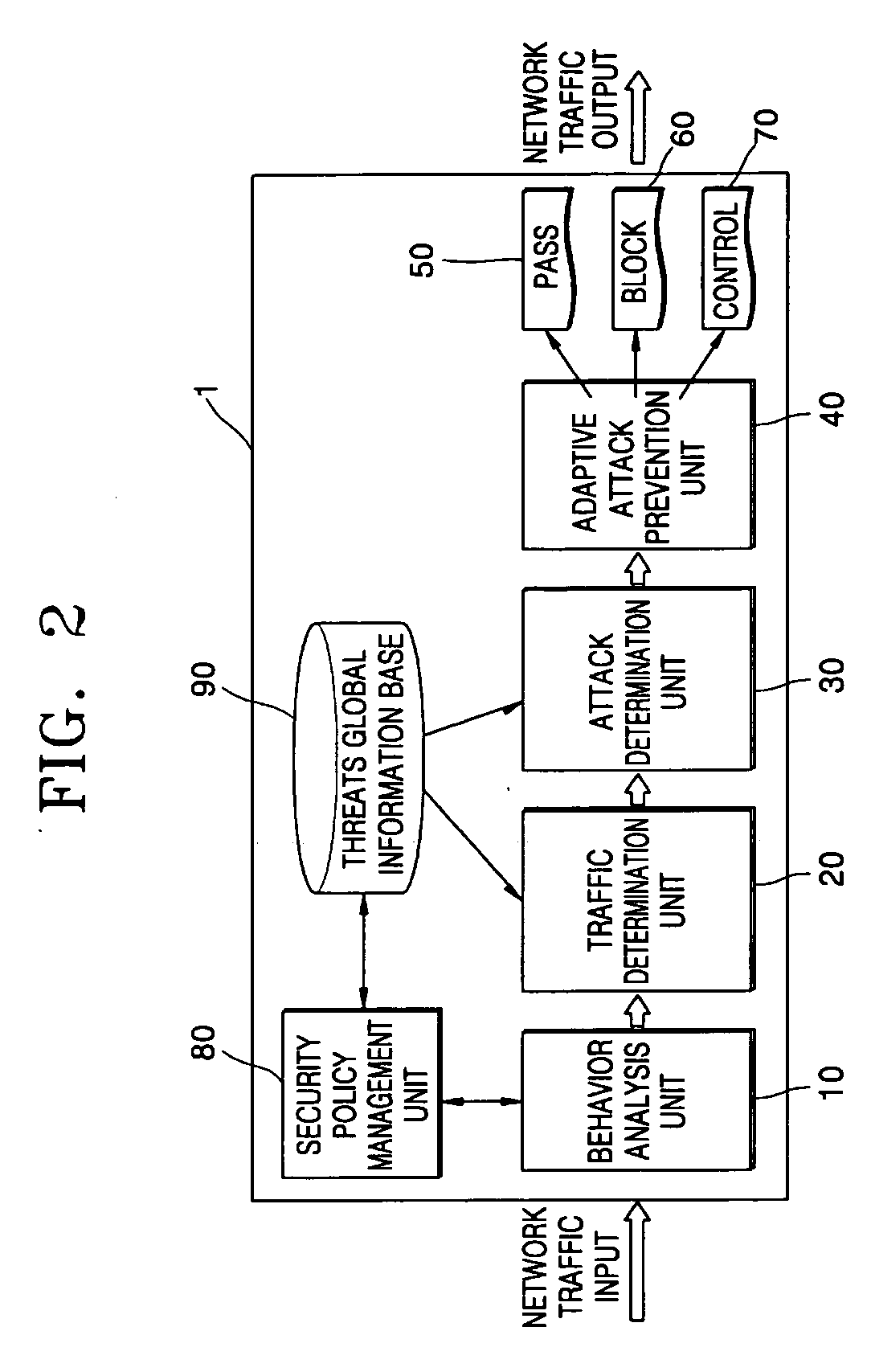
Apparatus and method for adaptively preventing attacks
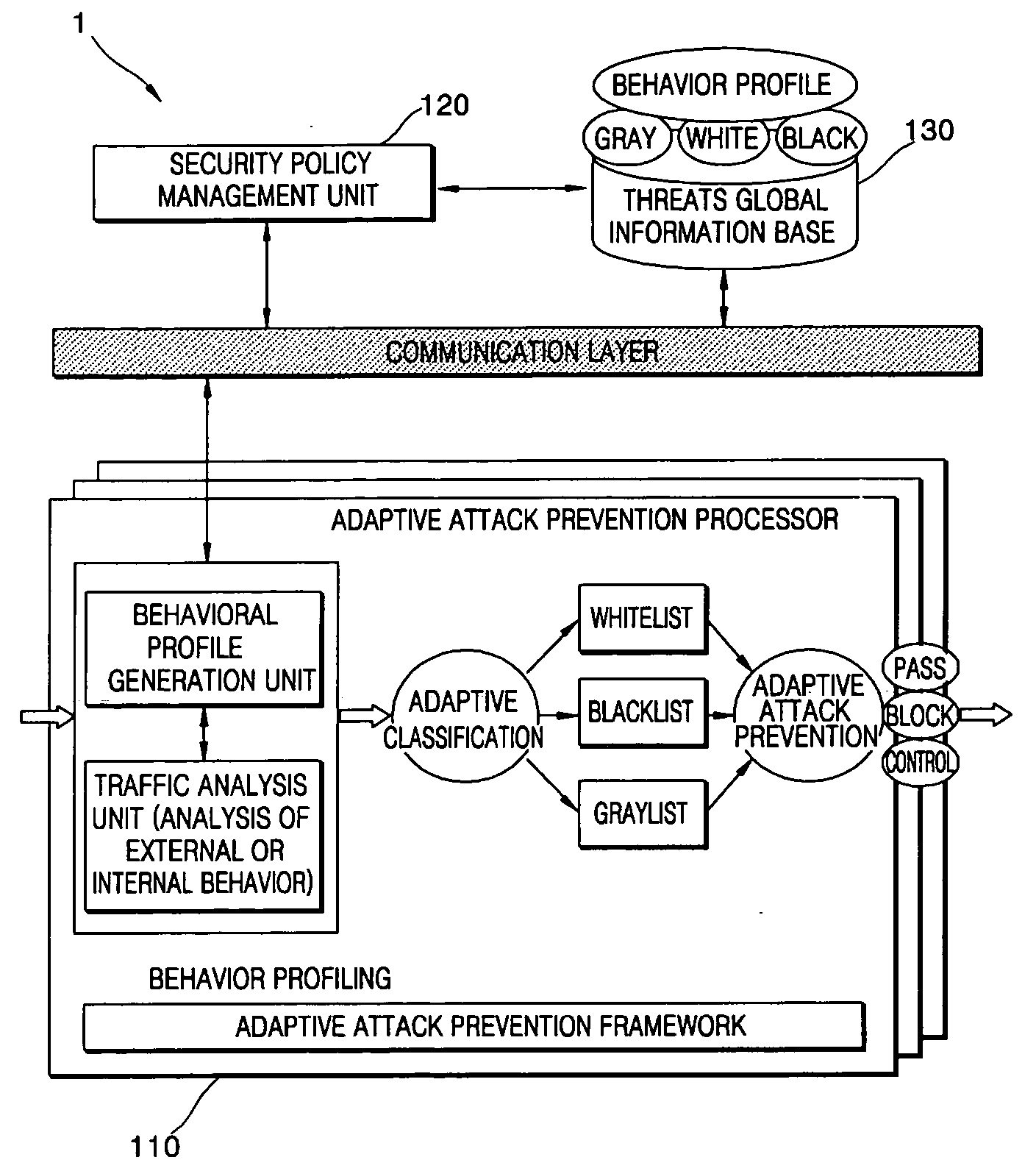
InactiveUS20060206935A1Reducing false positives and negativesMemory loss protectionData taking preventionBehavioral analyticsInternet traffic
An apparatus and method for adaptively preventing attacks which can reduce false positives and negatives for abnormal traffic and can adaptively deal with unknown attacks are provided. The apparatus includes: a behavior analysis unit which estimates an attack detection critical value by analyzing the behavior of network traffic; a traffic determination unit which determines what type of traffic the network traffic is using the estimated attack detection critical value; an attack determination unit which determines whether the network traffic is abnormal by analyzing the network traffic according to a set of determination rules; and an adaptive attack prevention unit which handles the network traffic based on the determination results provided by the attack determination unit. Accordingly, it is possible to reduce false positives and negatives for abnormal traffic or unknown attacks input to a network.
Owner:ELECTRONICS & TELECOMM RES INST
Method and apparatus for encrypting data transmitted over a serial link
InactiveUS20070016779A1Synchronising transmission/receiving encryption devicesData stream serial/continuous modificationComputer hardwareCommunications system
A communication system including a transmitter, a receiver, and a serial link (for example, a TMDS-like link) in which video data (or other data) are encrypted, the encrypted data are transmitted from the transmitter to the receiver, and the transmitted data are decrypted in the receiver, a transmitter and a receiver for use in such systems, a cipher engine for use in such a transmitter or receiver, a method for operating such a transmitter or receiver to encrypt or decrypt data, and a method for authenticating a receiver prior to transmission of encrypted data to the receiver over a serial link. Each transmitter, receiver, and cipher engine is configured to implement a content protection protocol in a manner that implements at least one and preferably more than one of a class of attack prevention features disclosed herein. In preferred embodiments the invention is employed to encrypt data in accordance with the High-bandwidth Digital Content Protection (“HDCP”) protocol, or a modified version of the HDCP protocol.
Owner:LYLE JAMES D
Firewall security policy configuration method and management unit
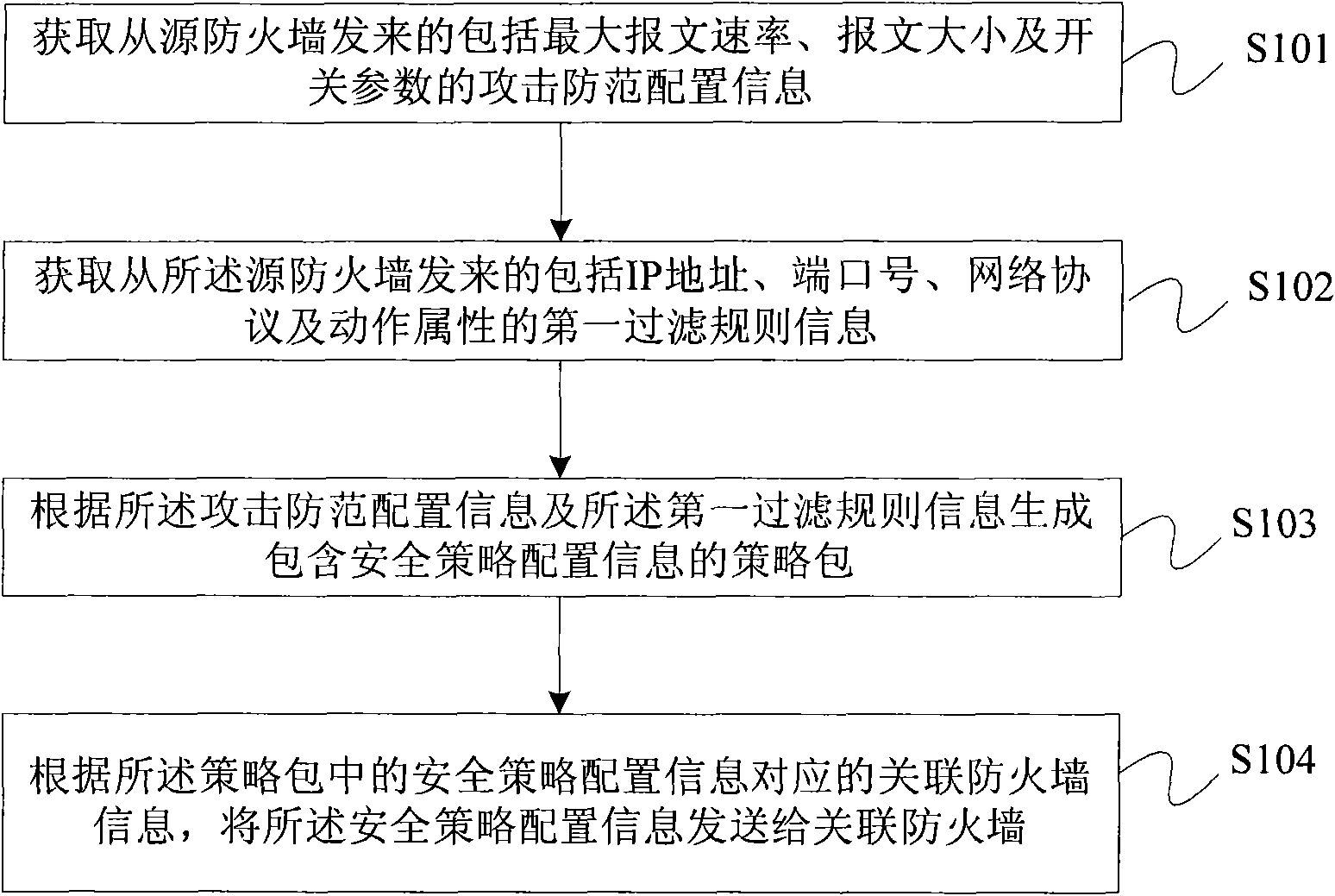
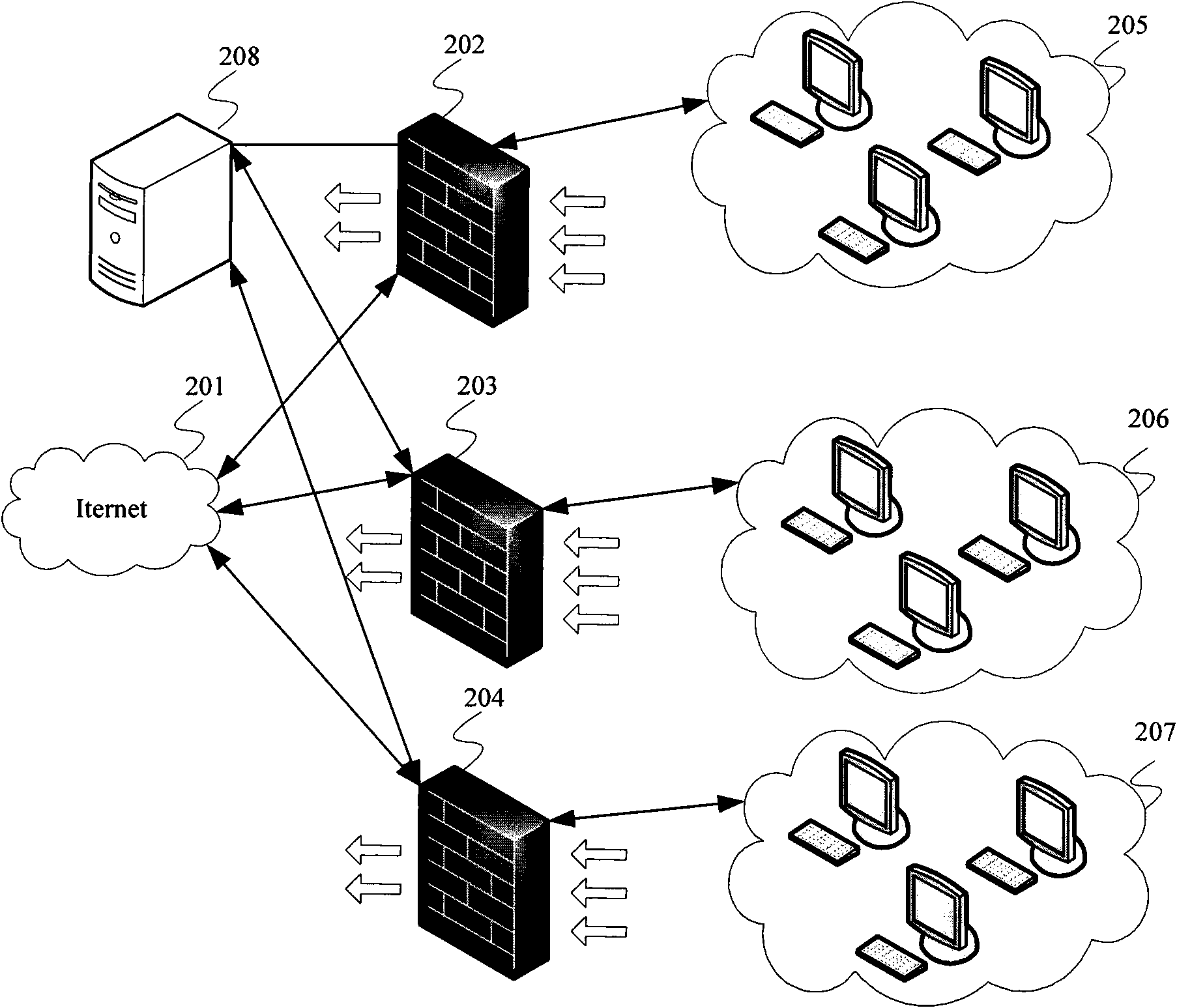
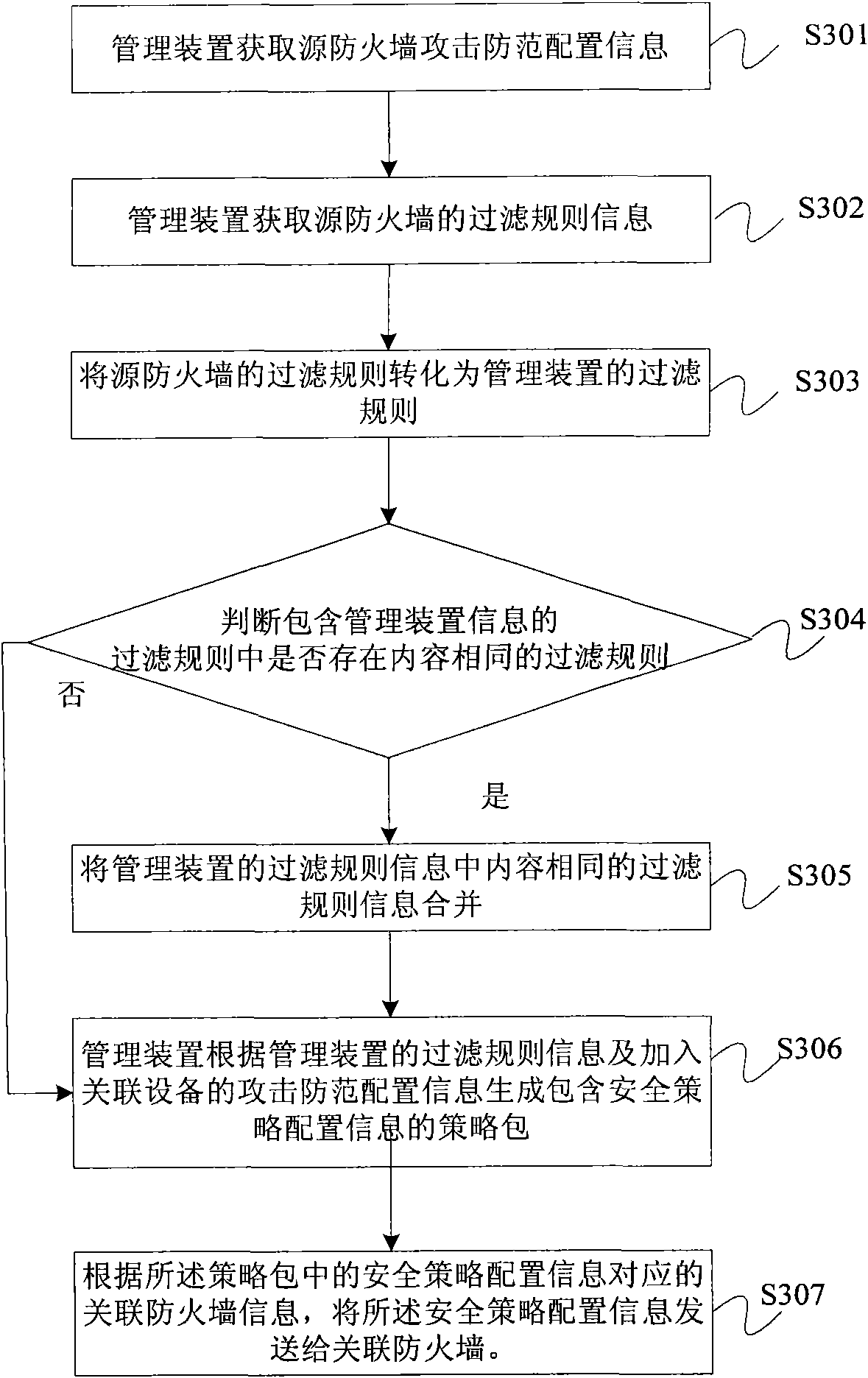
The invention provides a firewall security policy configuration method and a management unit. The method comprises the following steps of: obtaining attack prevention configuration information which includes maximum message rate, message size or an on-and-off parameter and is sent from the firewall; obtaining first filter rule information which includes an IP address, a port number, a network protocol and action attribute and is sent from the firewall; generating a policy package including security policy configuration information according to the attack prevention configuration information and the first filter rule information; and sending the security policy configuration information to the association firewall according to association firewall information corresponding to the security policy configuration information in the policy package. In the embodiment of the invention, the security policy of a single firewall is reversely reduced to the policy package, thus providing convenience for a user to conduct security policy configuration on the firewall.
Owner:CHENGDU HUAWEI TECH
Method and system for preventing cross-site attack
Efficient cross-site attack prevention, in which web pages are stored on a site, the web pages being organized into entry pages that do not accept input, and protected pages that are not entry pages. A request is received from a user application to receive a requested web page, the request including a referrer string indicative of a referring web page, and identification data. It is determined whether the requested web page is an entry page or a protected page, and it is further determined, if the requested web page is determined to be a protected page, if the user application is authorized based upon the identification data, and if the referring web page is stored on the site based upon the referrer string.; The requested web page is transmitted to the user application if the user application is determined to be authorized and if the referring web page is determined to be stored on the site, and the request is redirected to an entry page if the user application is determined to be not authorized or if the referring web page is determined to be not stored on the site.
Owner:SAP AG
Method and apparatus for encrypting data transmitted over a serial link
ActiveUS20070016778A1Synchronising transmission/receiving encryption devicesData stream serial/continuous modificationComputer hardwareCommunications system
A communication system including a transmitter, a receiver, and a serial link (for example, a TMDS-like link) in which video data (or other data) are encrypted, the encrypted data are transmitted from the transmitter to the receiver, and the transmitted data are decrypted in the receiver, a transmitter and a receiver for use in such systems, a cipher engine for use in such a transmitter or receiver, a method for operating such a transmitter or receiver to encrypt or decrypt data, and a method for authenticating a receiver prior to transmission of encrypted data to the receiver over a serial link. Each transmitter, receiver, and cipher engine is configured to implement a content protection protocol in a manner that implements at least one and preferably more than one of a class of attack prevention features disclosed herein. In preferred embodiments the invention is employed to encrypt data in accordance with the High-bandwidth Digital Content Protection (“HDCP”) protocol, or a modified version of the HDCP protocol.
Owner:LATTICE SEMICON CORP
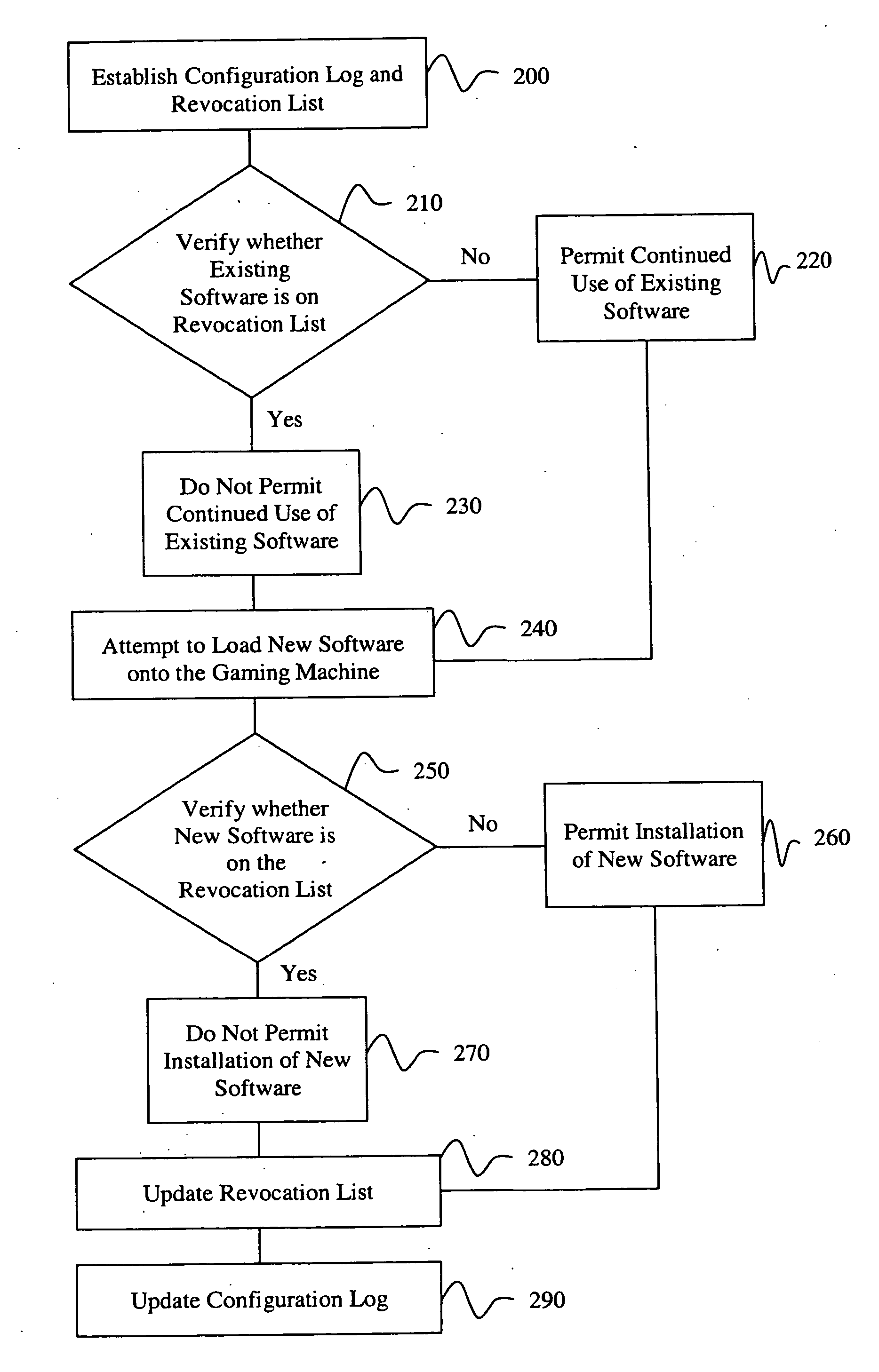
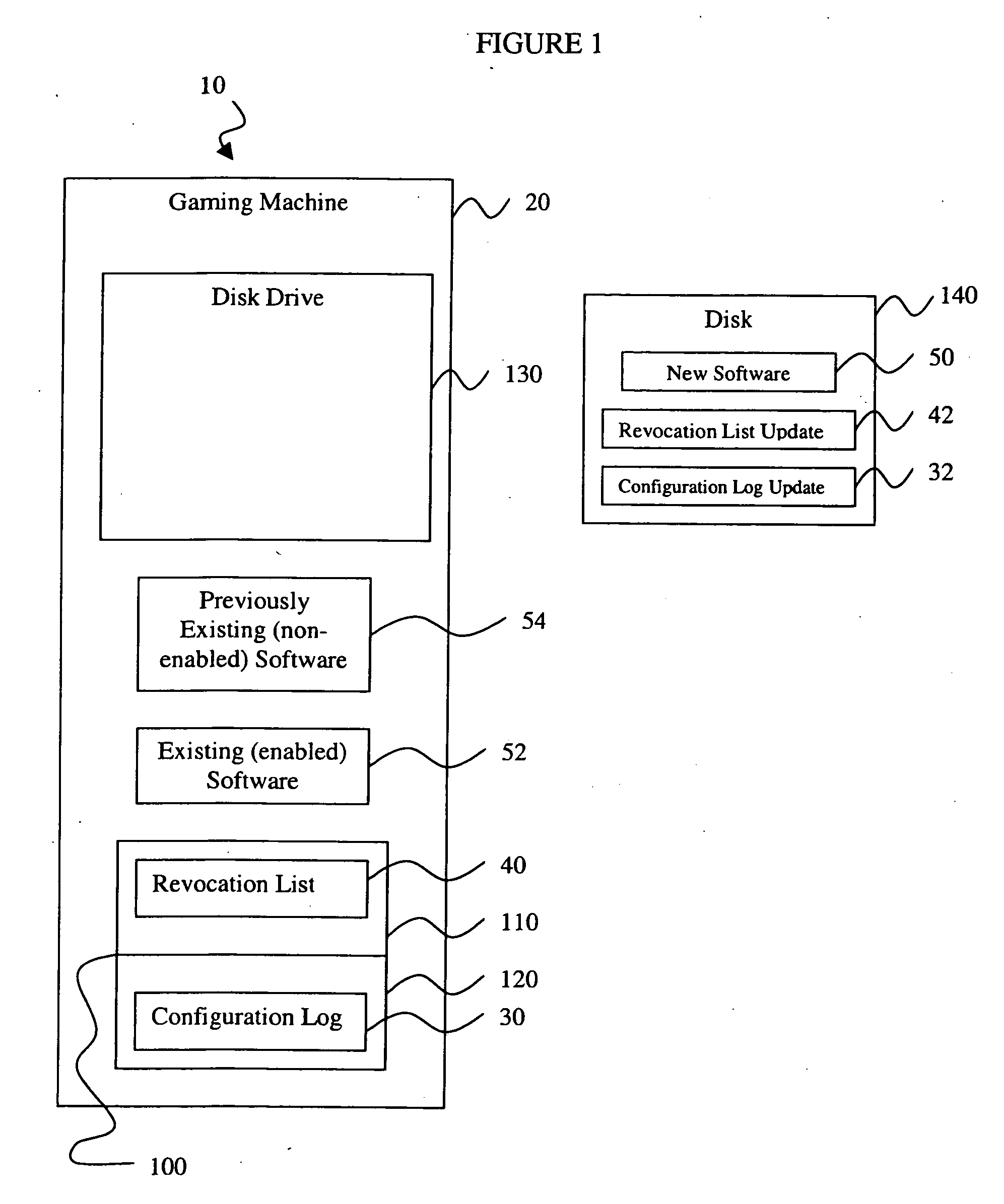
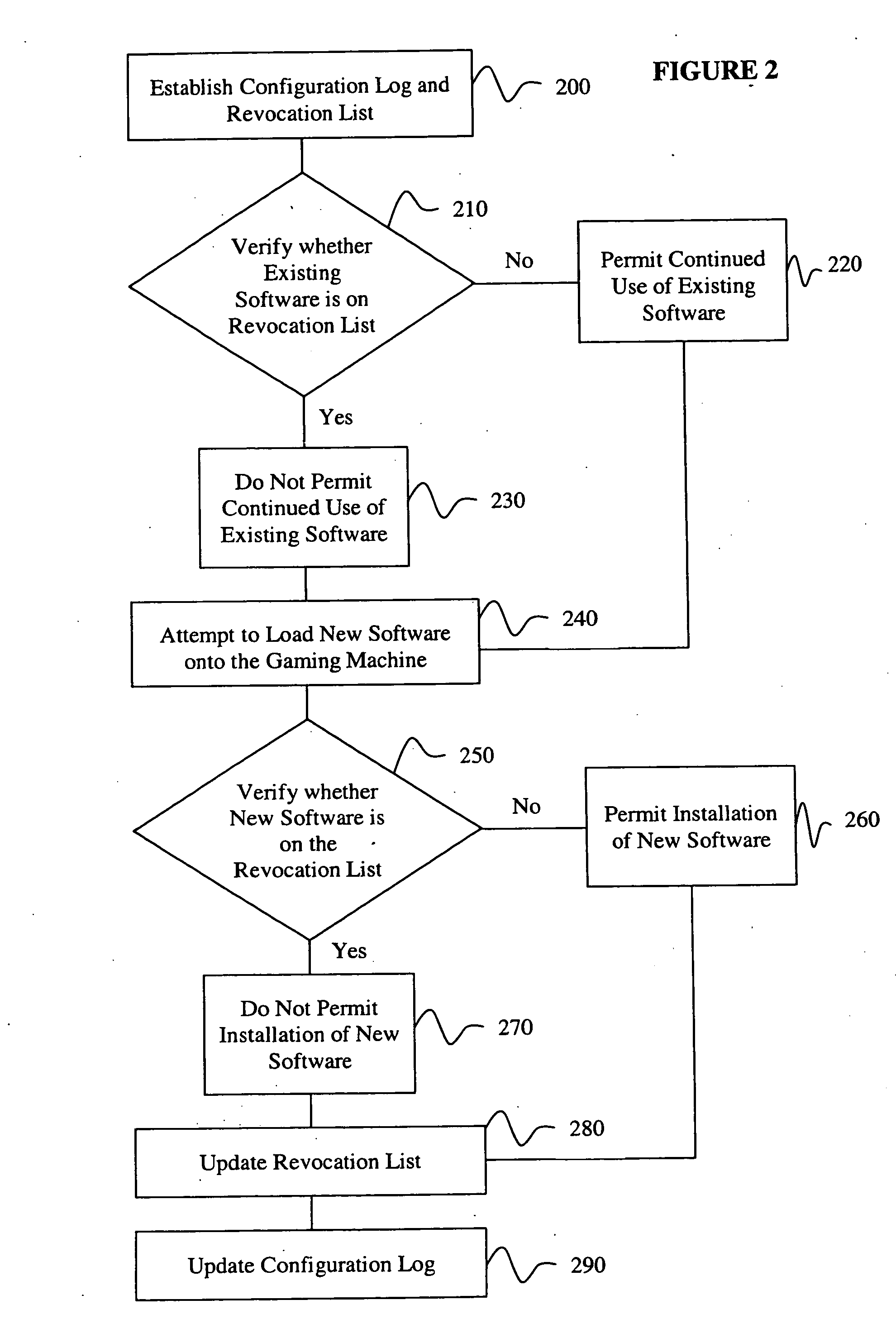
Rollback attack prevention system and method
InactiveUS20050044401A1Unauthorized installationUnauthorized useDigital data processing detailsUser identity/authority verificationComputer scienceSoftware
A rollback attack prevention system 10 for a gaming machine 20 includes a configuration log 30 and a revocation list 40. Preferably, the configuration log 30 includes a protected record of software that has been installed on the gaming machine 20. Further, the revocation list 40 includes an inventory of unauthorized software that the prevention system 10 prevents from being installed and / or used on the gaming machine 20.
Owner:BALLY GAMING INC
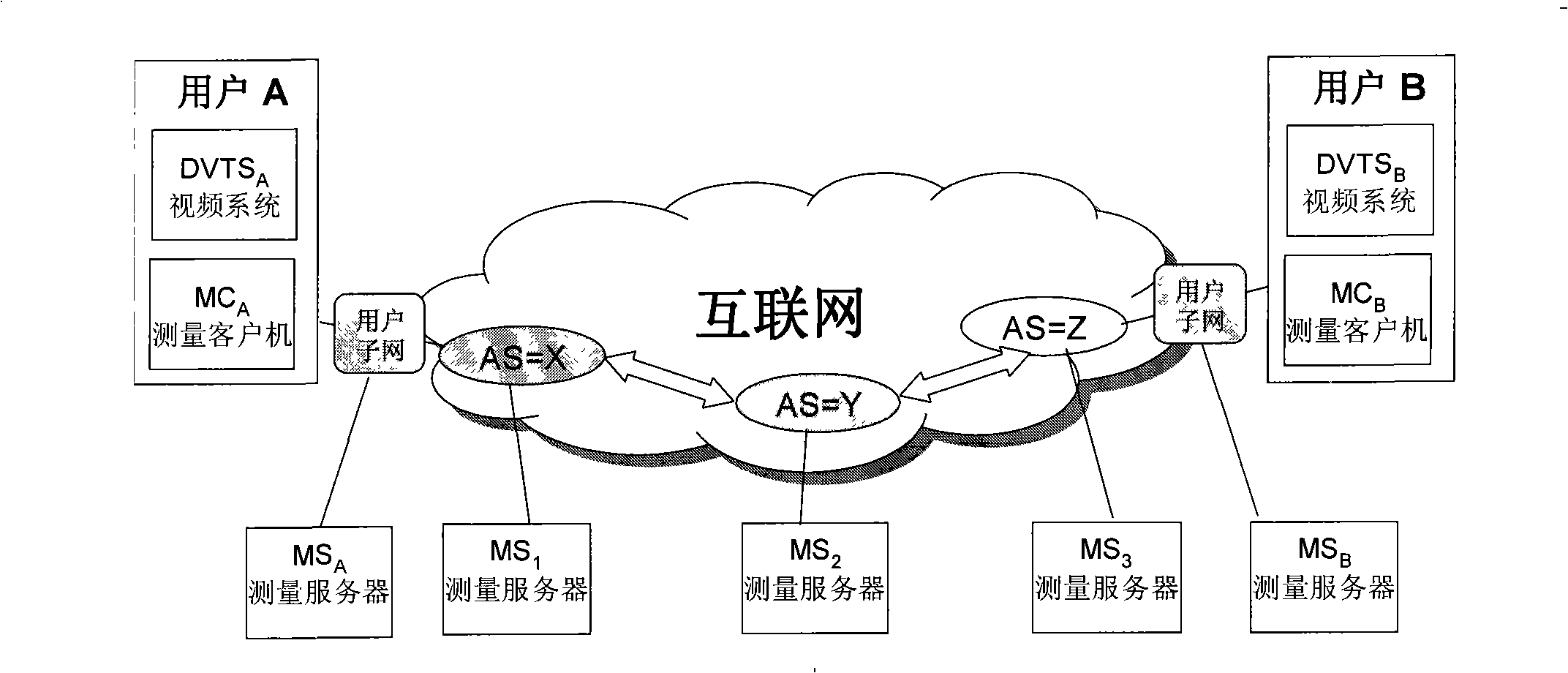
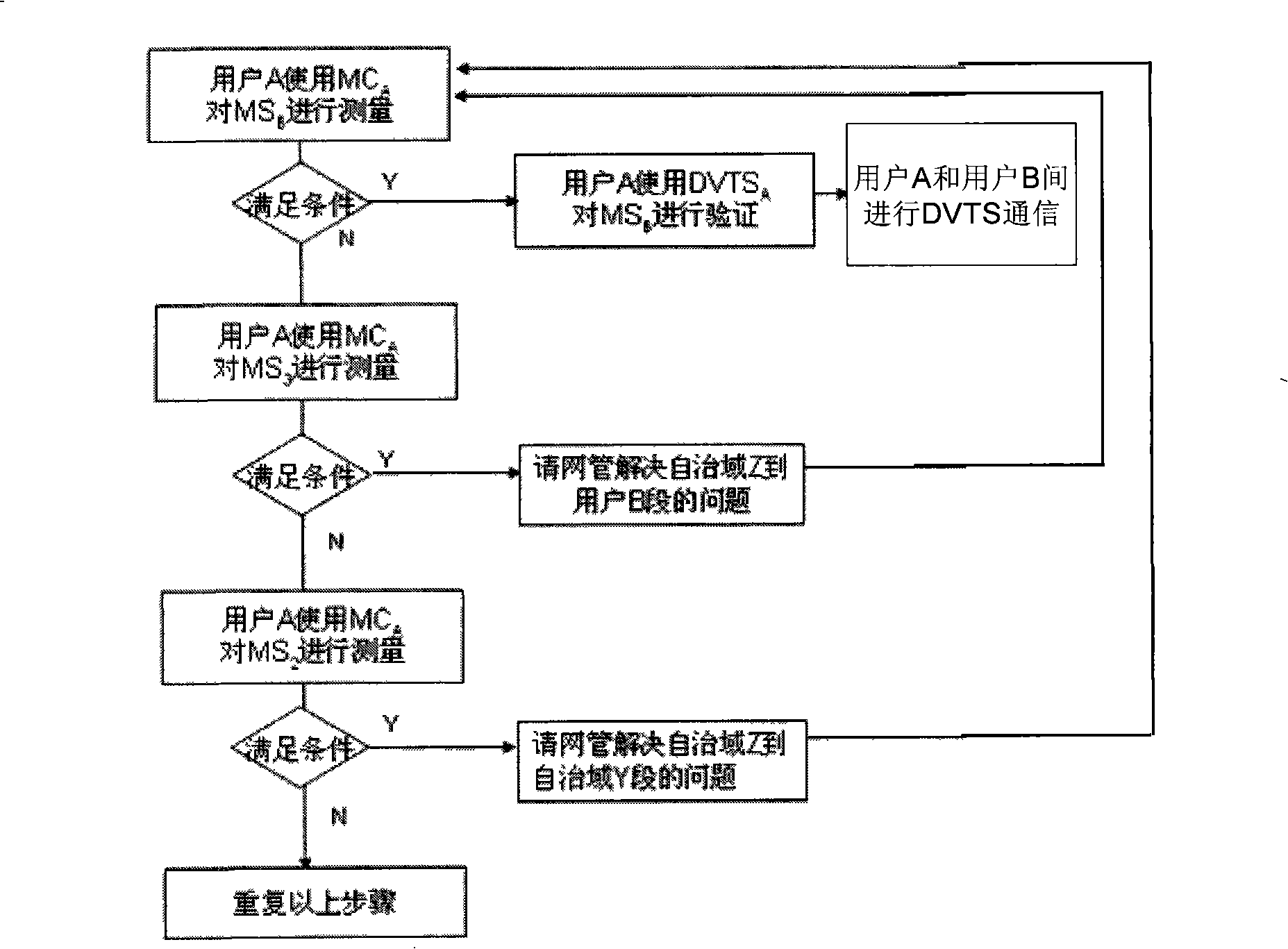
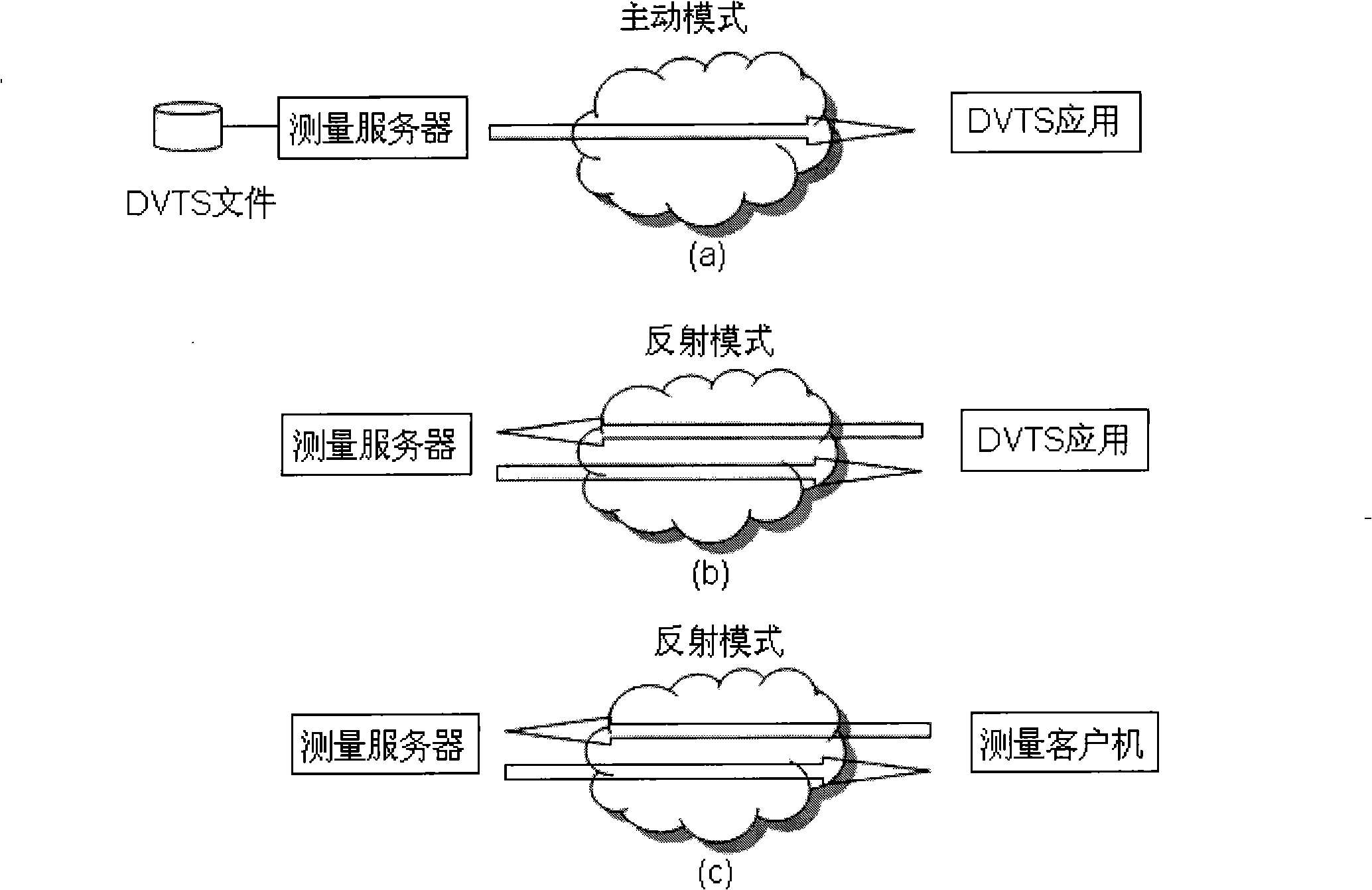
Method for measuring network application performance supporting internet high bandwidth real time video application
InactiveCN101282247ACoordinate to resolve transmission bottlenecksData switching networksData streamIndependent measure
A network application performance measuring method which supports the application of high bandwidth real-time video of internet belongs to the technical field of bidirectional transmission performance measurement of IPv4 / IPv6 internet. The invention is characterized in that a random data flow which simulates the virtual real-time video or virtual real-time video data flow is adopted as a ''probe'', a network which combines a user application system with a measuring server and is based on an active mode and a reflection mode and an application performance measuring method thereof, a network which combines the client system with the measuring server and is based on the reflection mode and the application performance measuring method thereof, and the invention has the functions of subscriber identification and DOS attack prevention. The invention effectively realizes the intercommunication of the network measuring method which supports the application of high bandwidth real-time video and the application system. The description languages of the video application subscriber, the application system engineer and the network engineer to the network problem are unified. A real-time automatic and independent measuring environment is established. The criterion is provided for quickly finding out the bandwidth bottleneck of network transmission for diagnosing the failure and settling the problem.
Owner:TSINGHUA UNIV
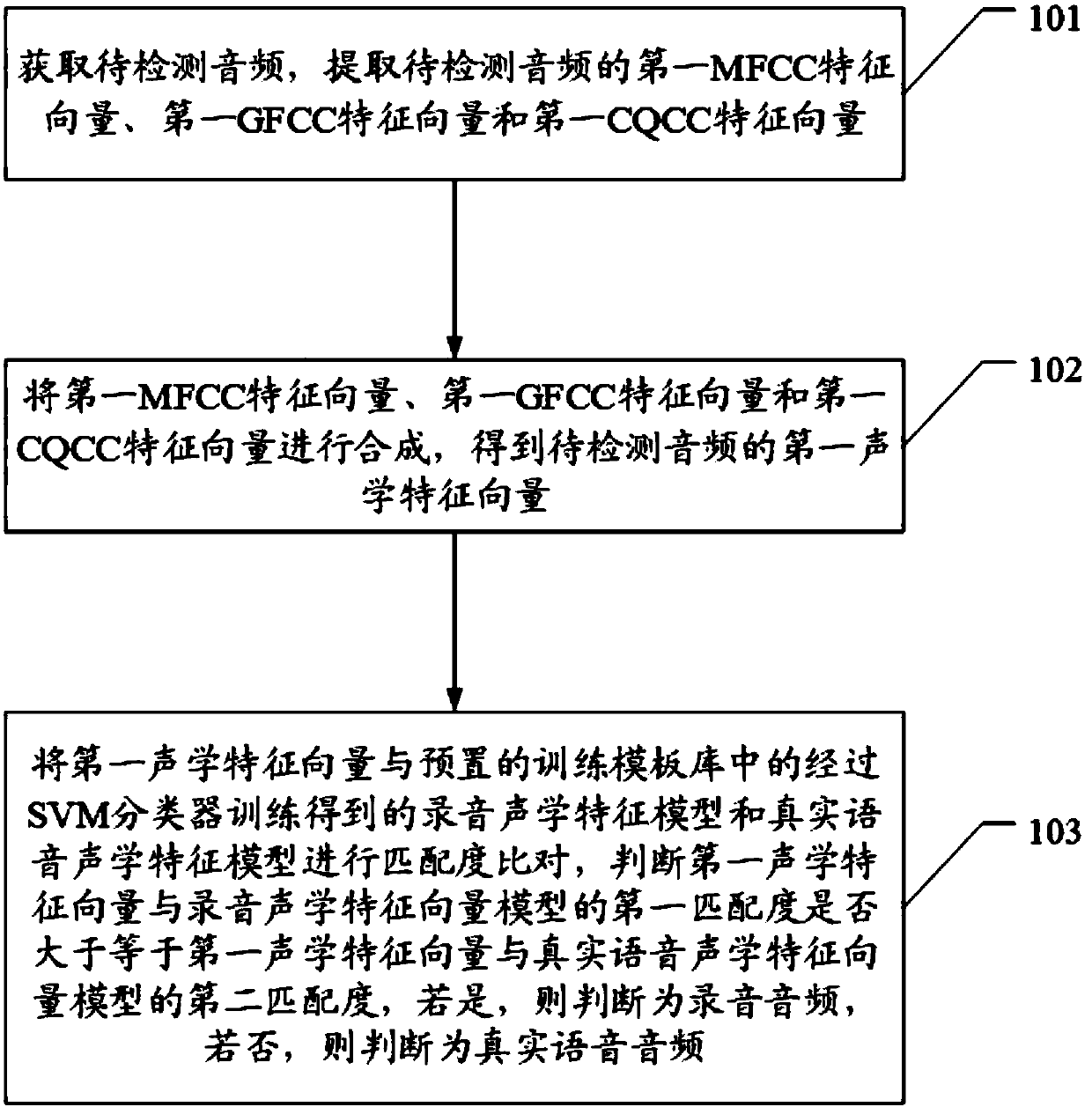
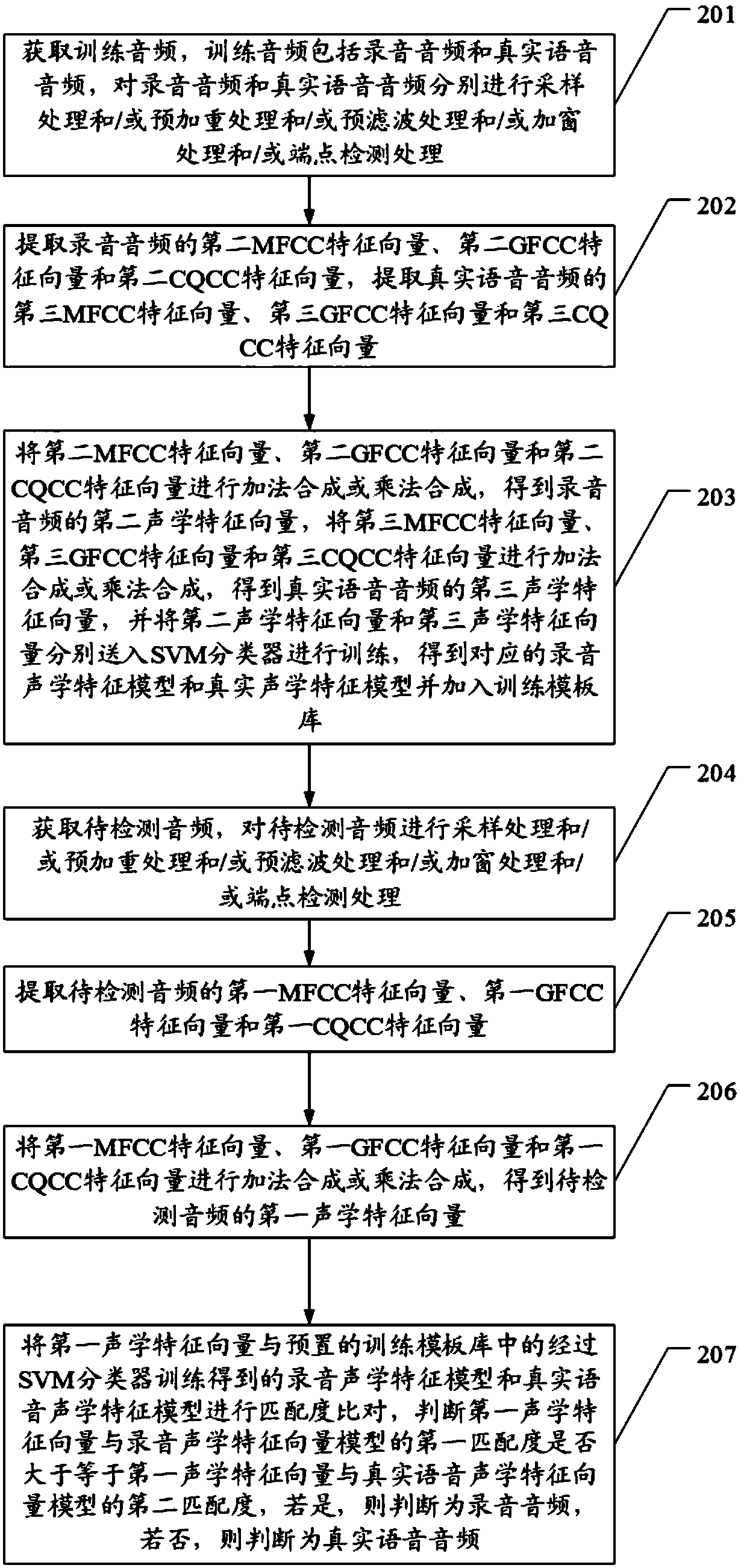
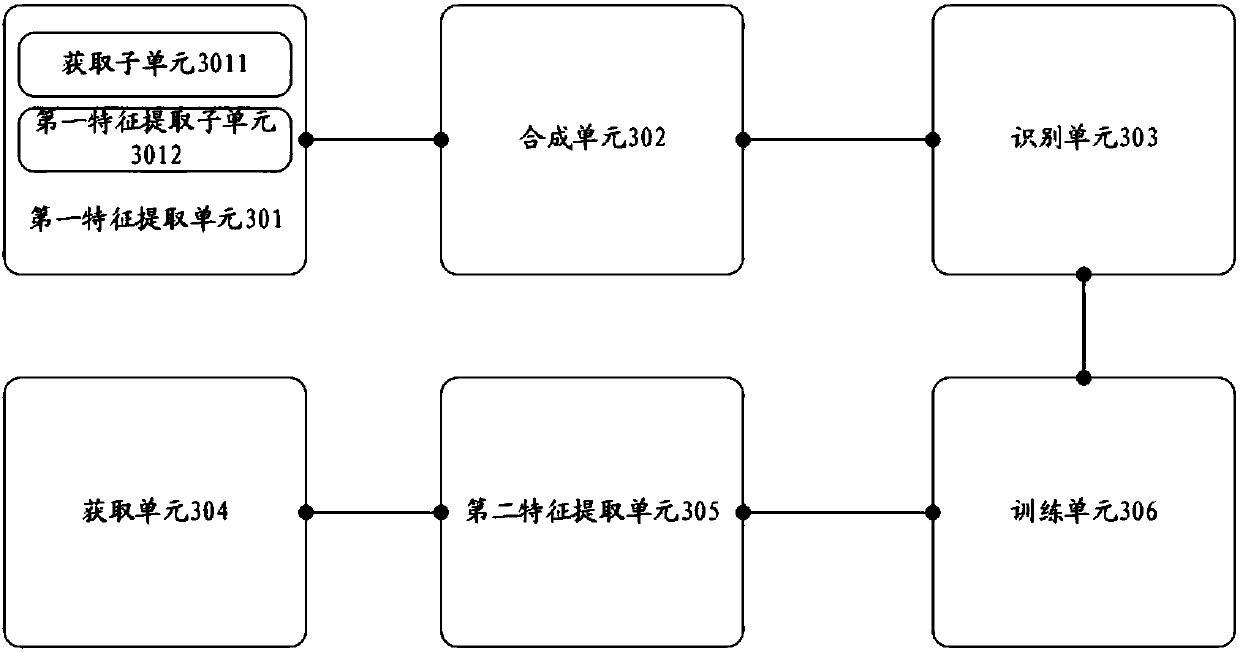
Recording attack prevention voiceprint recognition method and device and access control system
ActiveCN108039176AReal voiceRealize the judgment of the recordingSpeech analysisIndividual entry/exit registersFeature vectorSpeaker recognition system
The invention discloses a recording attack prevention voiceprint recognition method and device and an access control system. The method comprises the following steps of obtaining an audio to be detected; extracting a first MFCC feature vector, a first GFCC feature vector and a first CQCC feature vector of the audio to be detected; synthesizing the first MFCC feature vector, the first GFCC featurevector and the first CQCC feature vector; obtaining the first acoustic feature vector of the audio to be detected; performing matching degree comparison on the first acoustic feature vector, a recording acoustic feature model obtained through the training by an SVM classifier in the preset training template base and a real voice acoustic feature model; judging whether the first matching degree ofthe first acoustic feature vector and the recording acoustic feature vector model is greater than or equal to the second matching degree of the first acoustic feature and the real voice acoustic feature vector model or not; if so, judging that the audio to be detected is the recording audio; if not, judging that the audio to be detected is the real voice audio. The technical problems that the existing speaker recognition system has low voice recognition accuracy and relies on the specific text are solved.
Owner:SPEAKIN TECH CO LTD
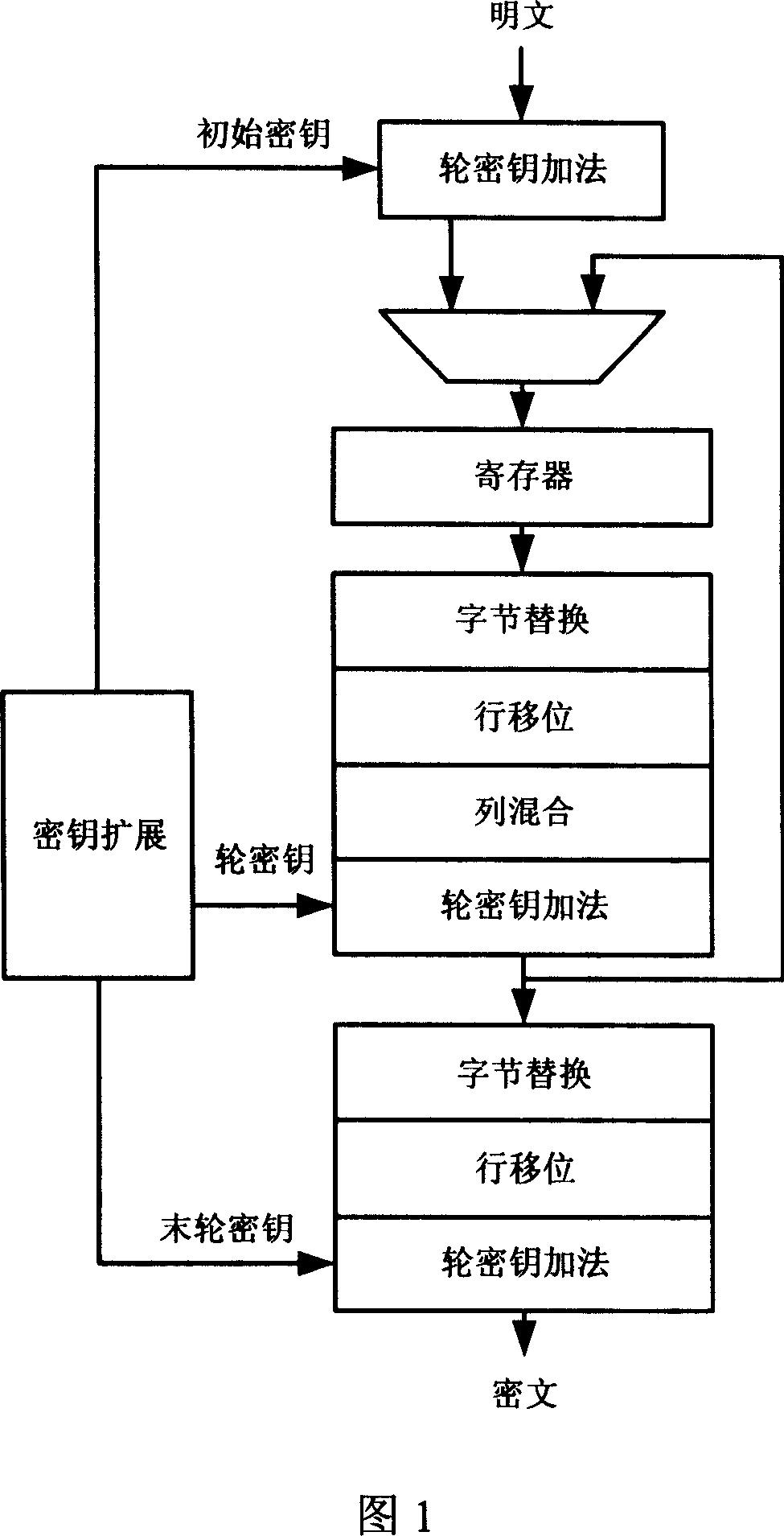
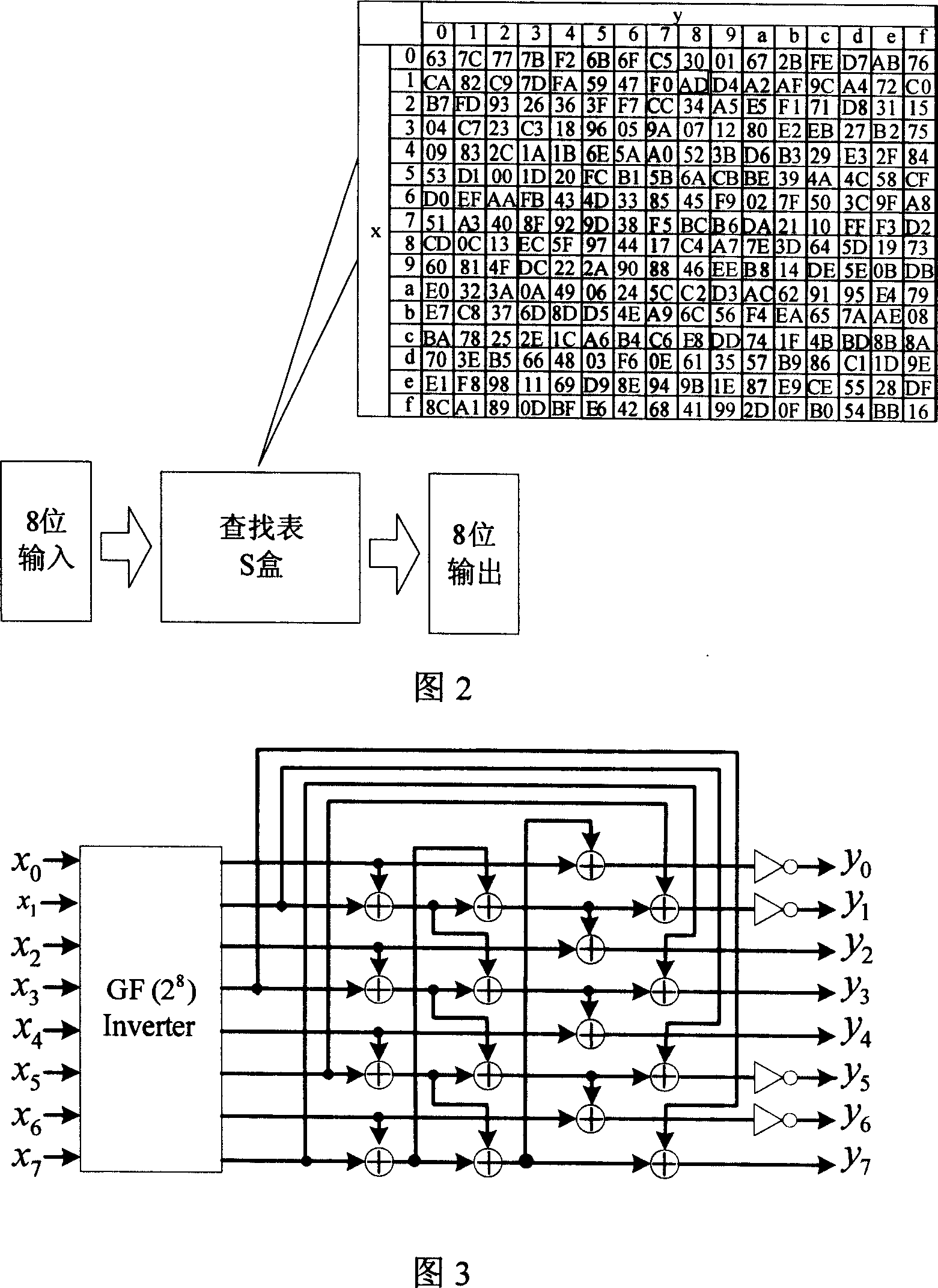
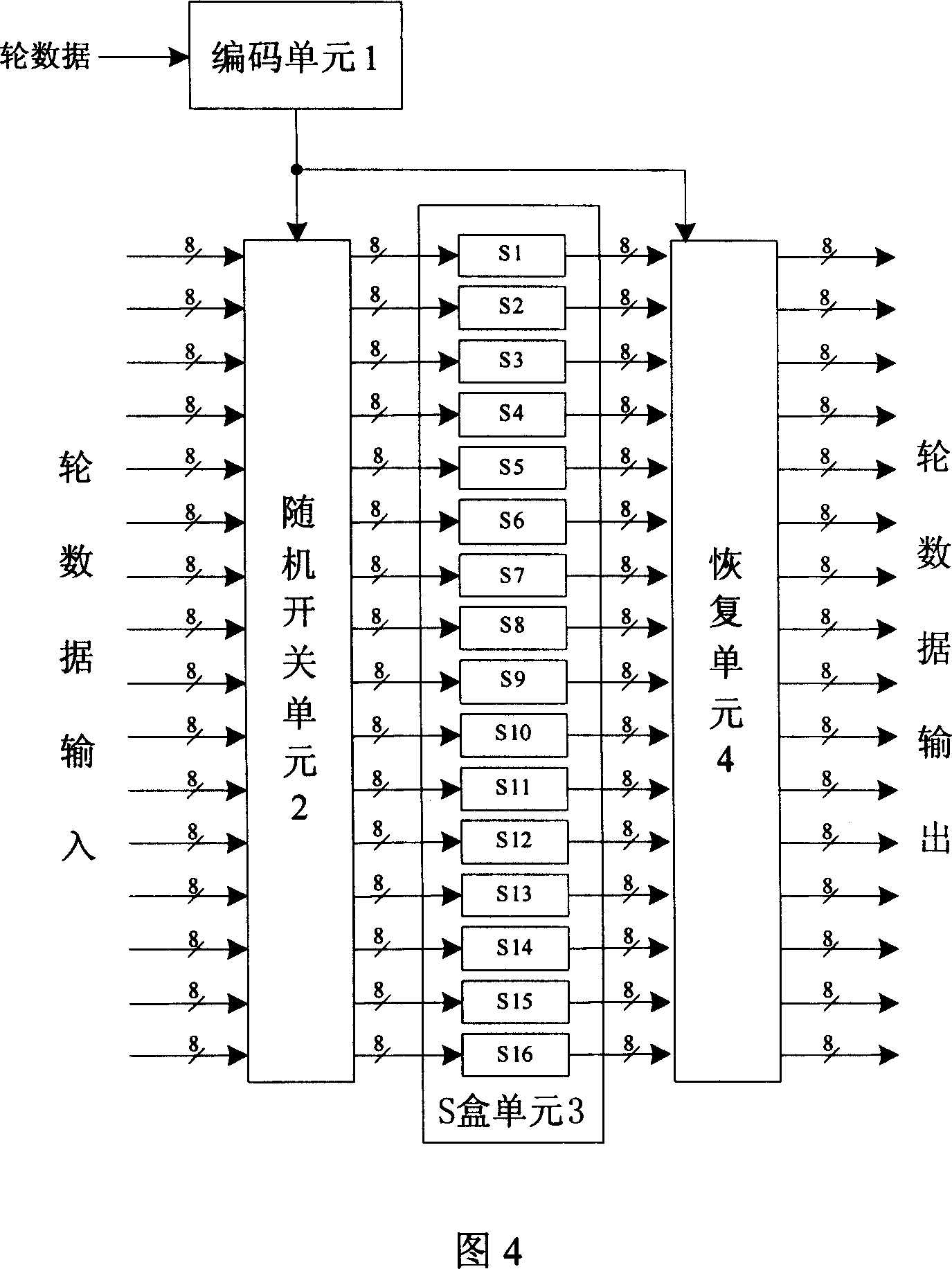
A byte replacement circuit for power consumption attack prevention
InactiveCN101009554AEnhanced anti-power attack featuresEncryption apparatus with shift registers/memoriesPlaintextS-box
The invention discloses a byte alternative circuit of anti power consumption attack that includes coding unit, random switching unit, S-box unit, and recovery unit. The S-box unit consists of 4-16 isomerous S-boxes. The invention adopts isomerous S-box unit to replace the traditional signal S-box, the switching unit is inserted in the input end of S-box unit, and the recovery unit is added behind the output end. When it is been attracting, the invention can select according to the input data of attack, and no need the additional random number generator. On the other hand, the method which adds the number of random plaintext is invalid for the circuit which is provided by the invention. The invention don't need to apply the special circuit and logical mode, and can be compatible with the presexisting AES enciphering circuit. The invention can improve the anti power consumption attack greatly with less expense, and it can cover the key when the hardware of AES is encrypting and decrypting to make the power attack not get the correct key.
Owner:HUAZHONG UNIV OF SCI & TECH
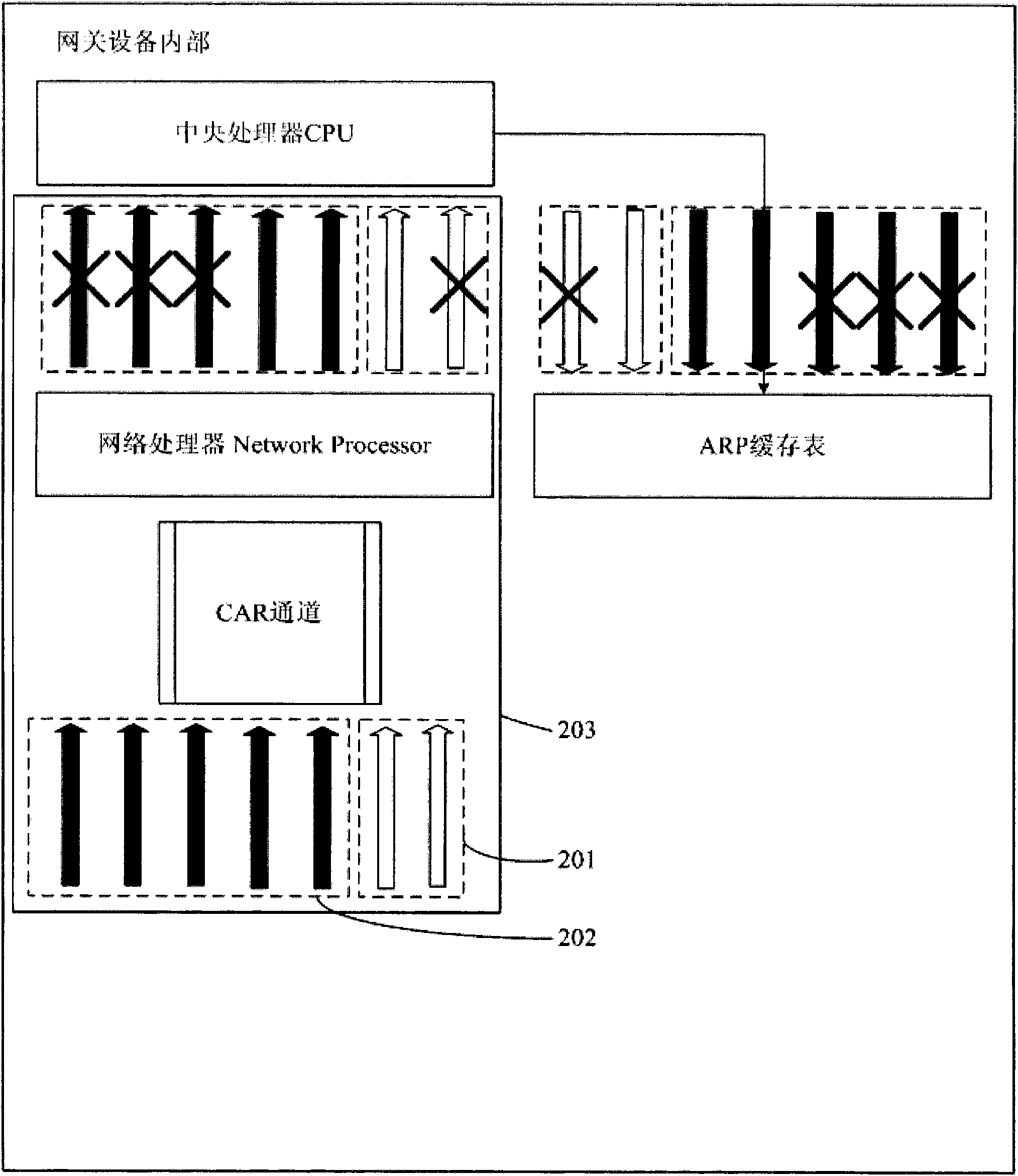
Flood attack prevention method and device
The embodiment of the invention provides a flood attack prevention method comprising the following steps of: carrying out CAR (Committed Access Rate) limitation on messages sent to different IP addresses, and respectively arranging CAR channels; and carrying out Hash processing on messages sent by all IP addresses based on IP addresses. The embodiment also provides a flood attack prevention device comprising a CAR limitation unit and a Hash processing unit based on IP addresses. According to the embodiment, normal flow messages can be separated from attach flow messages, so that the attach flow messages are filtered by the CAR channels due to large flow rate, and the normal flow messages are sent to a CPU to be processed through the CAR channels. The normal business running of attached equipment is ensured.
Owner:HUAWEI TECH CO LTD
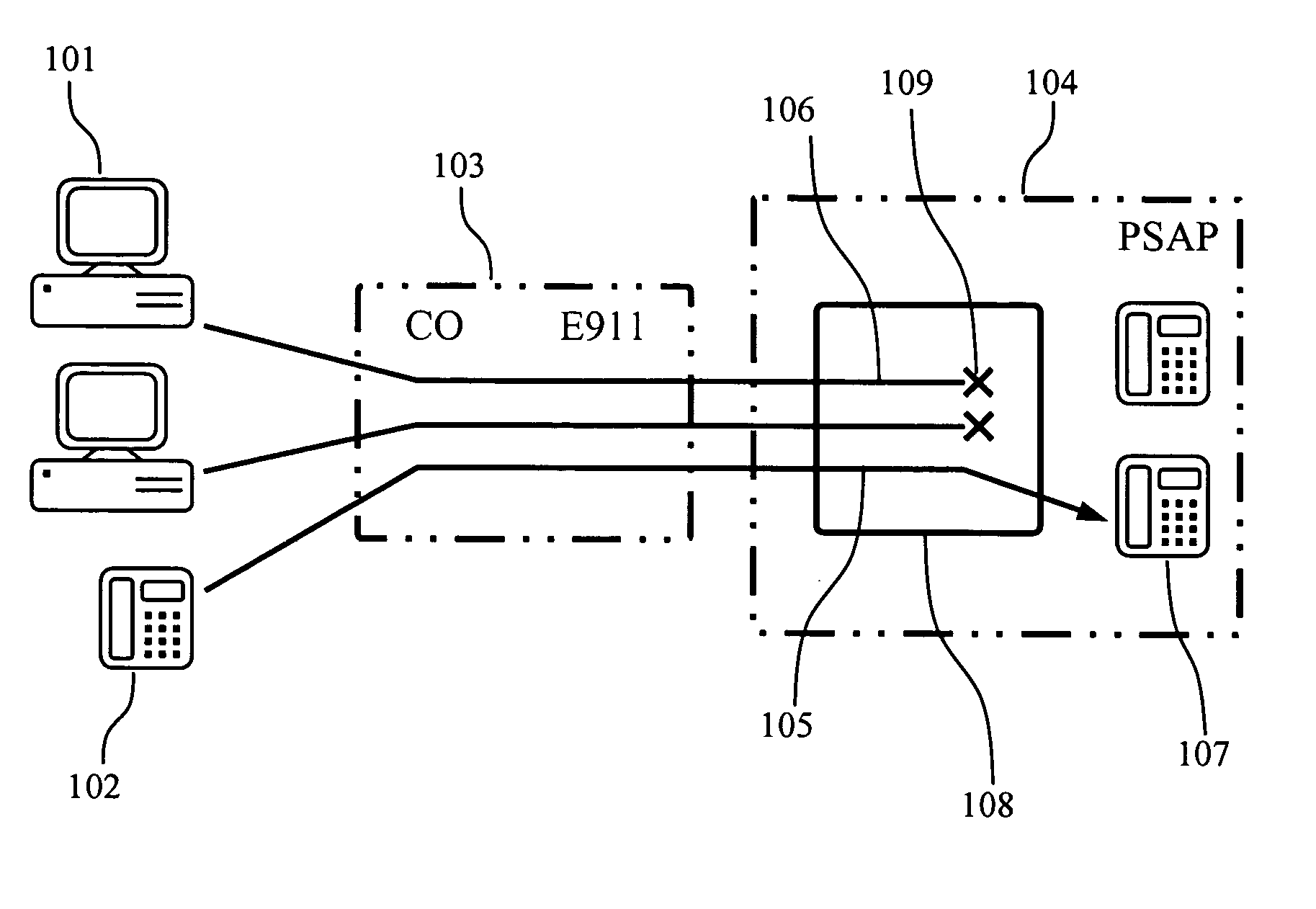
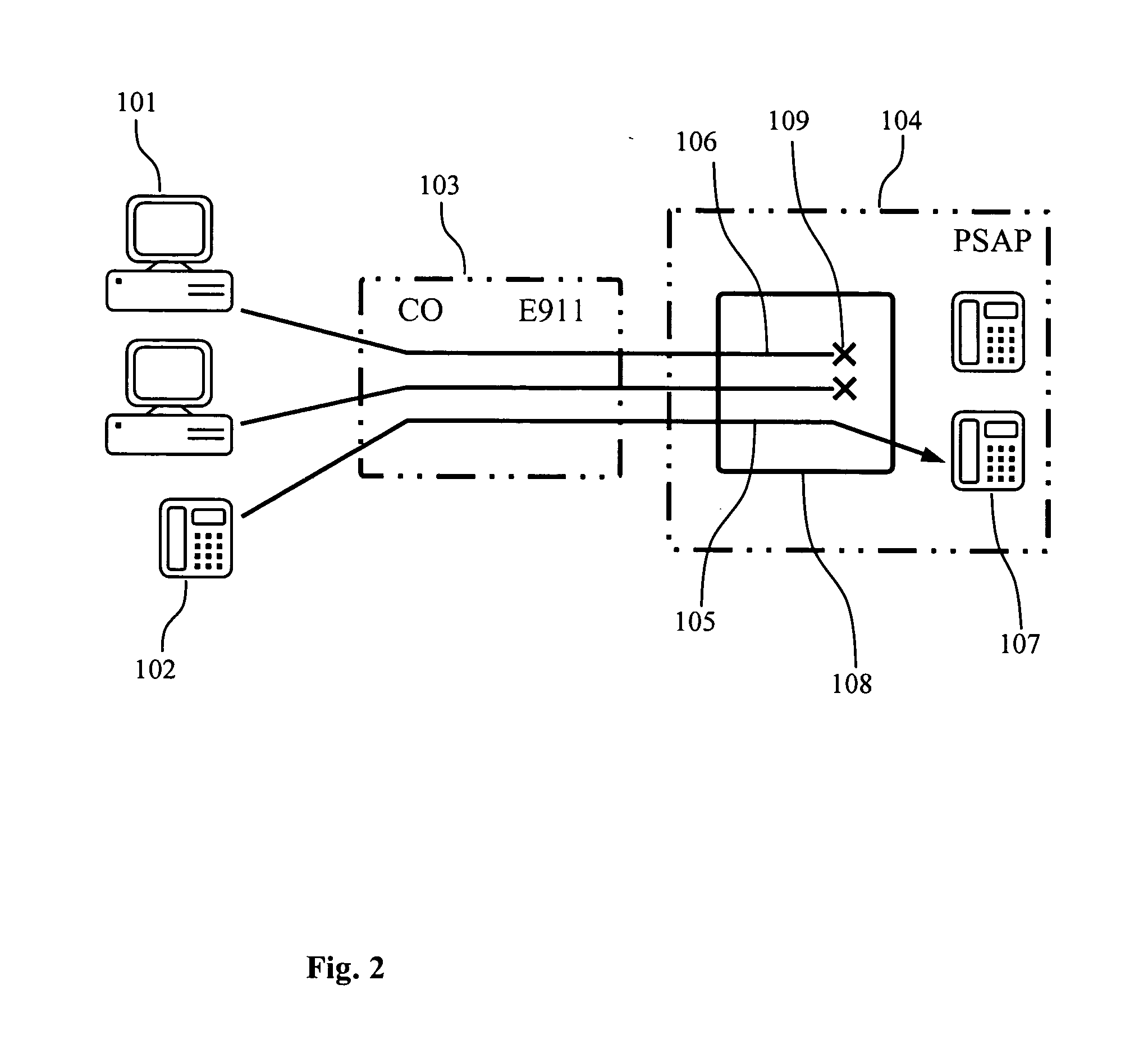
Denial of 911 emergency service attacks prevention method
InactiveUS20060039540A1Improve securityReduce vulnerabilityTelephonic communicationNetwork connectionsEmergent systemsModem device
A method for preventing Distributed Denial Of Service (DDOS) attacks on telecommunication systems handling special number calls such as 911 emergency systems launched from compromised personal computers equipped with modems connected to public telephone networks is disclosed. For each initiated call, a probability that the originator of the call is a computer device rather then a human is determined. The call is then further handled using determined probability of the call originator.
Owner:ISSINSKI ANTON
Method and system for defending ddos attack
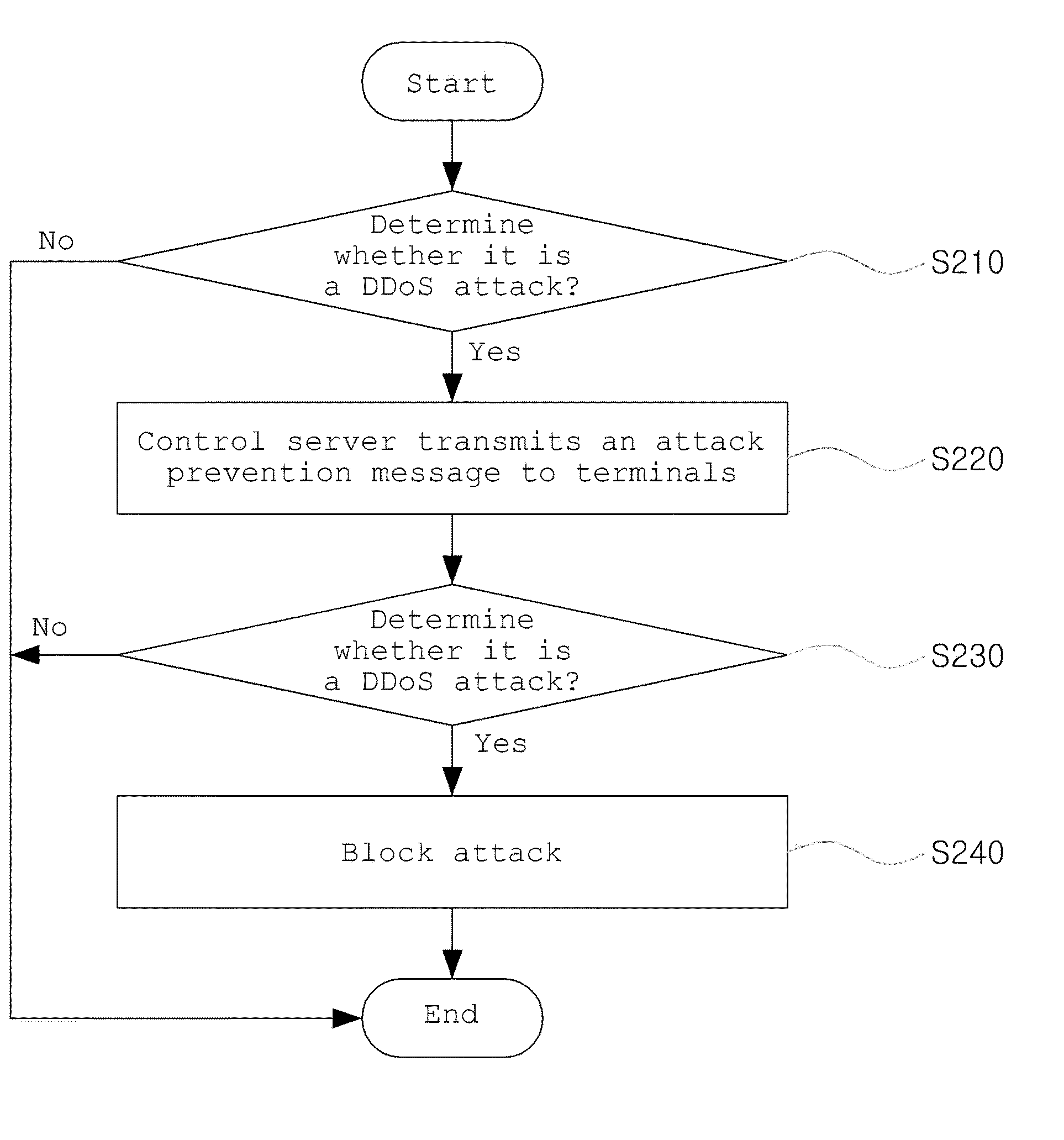
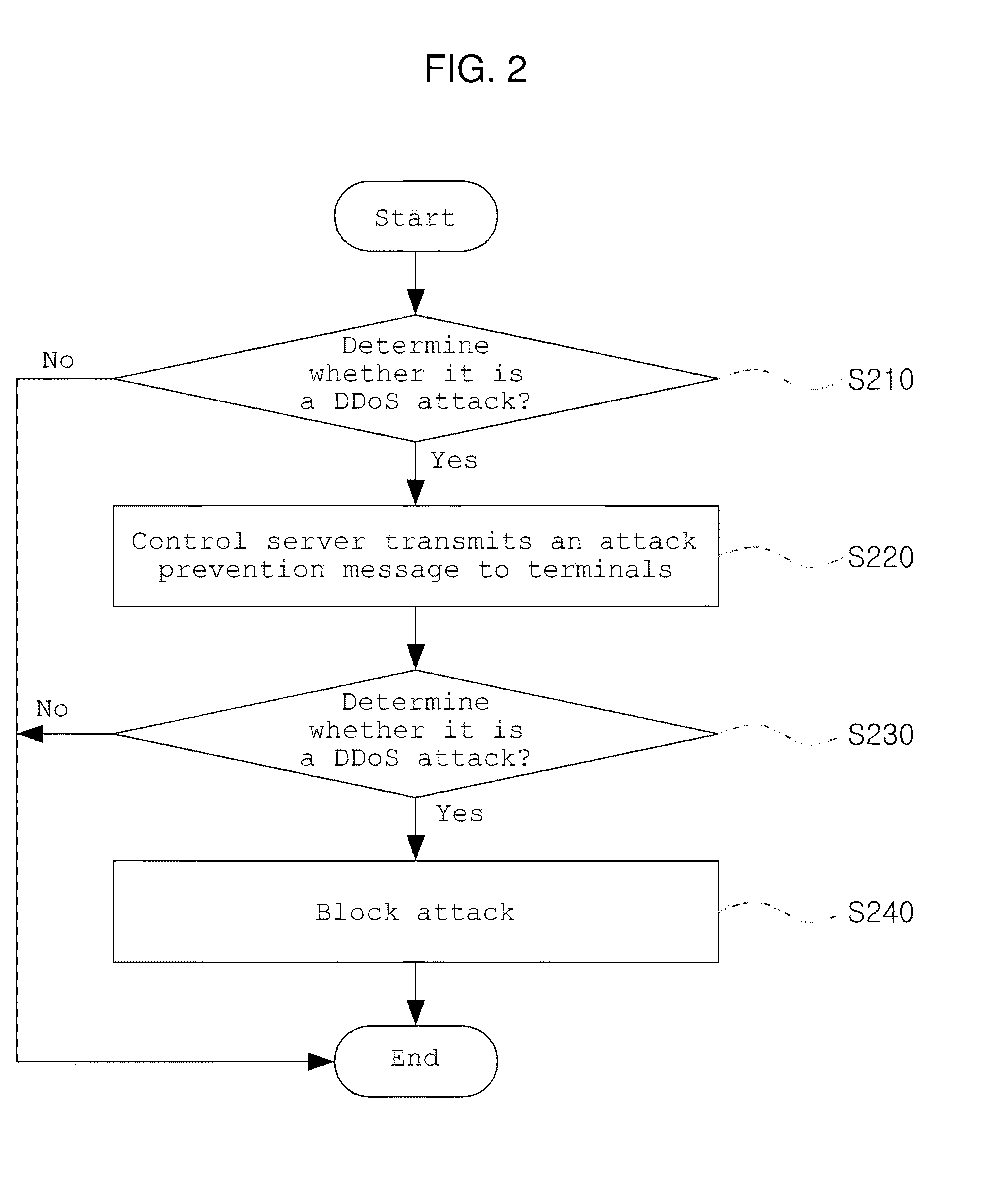
InactiveUS20100058471A1Effective attackMemory loss protectionData taking preventionAttack prevention
In a method of defending a Distributed Denial of Service (DDoS) attack, an attack target server determines whether the attack target server suffers a DDoS attack from a plurality of terminals and, according to a result of the determination, informs a control server that the attack target server suffers the DDoS attack by transmitting its own information to the control server. The control server which has received the information of the attack target server confirms the plurality of terminals which transmits data to the attack target server and transmits an attack prevention message to the plurality of confirmed terminals. Each of the plurality of terminals which has received the attack prevention message determines whether the terminal launches the DDoS attack and, according to a result of the determination, blocking the DDoS attack.
Owner:ESTSOFT CORP
System and method for run-time attack prevention
ActiveUS8522350B2Avoid attackMemory loss protectionDigital data processing detailsRunning timeVulnerability
Preventing attacks on a computer at run-time. Content that is configured to access at least one function of a computer is received by the computer. Protections corresponding to the function are added to the content, wherein the protections override the function. The content and the protections are then transmitted to the computer. The function may expose a vulnerability of the computer, and arguments passed to the function may exploit that vulnerability. The protections are executed when the content is executed, and determine whether the arguments the content passed into the function represent a threat. In response to determining that the arguments represent a threat, execution of the content is terminated without executing the function.
Owner:SECUREWORKS
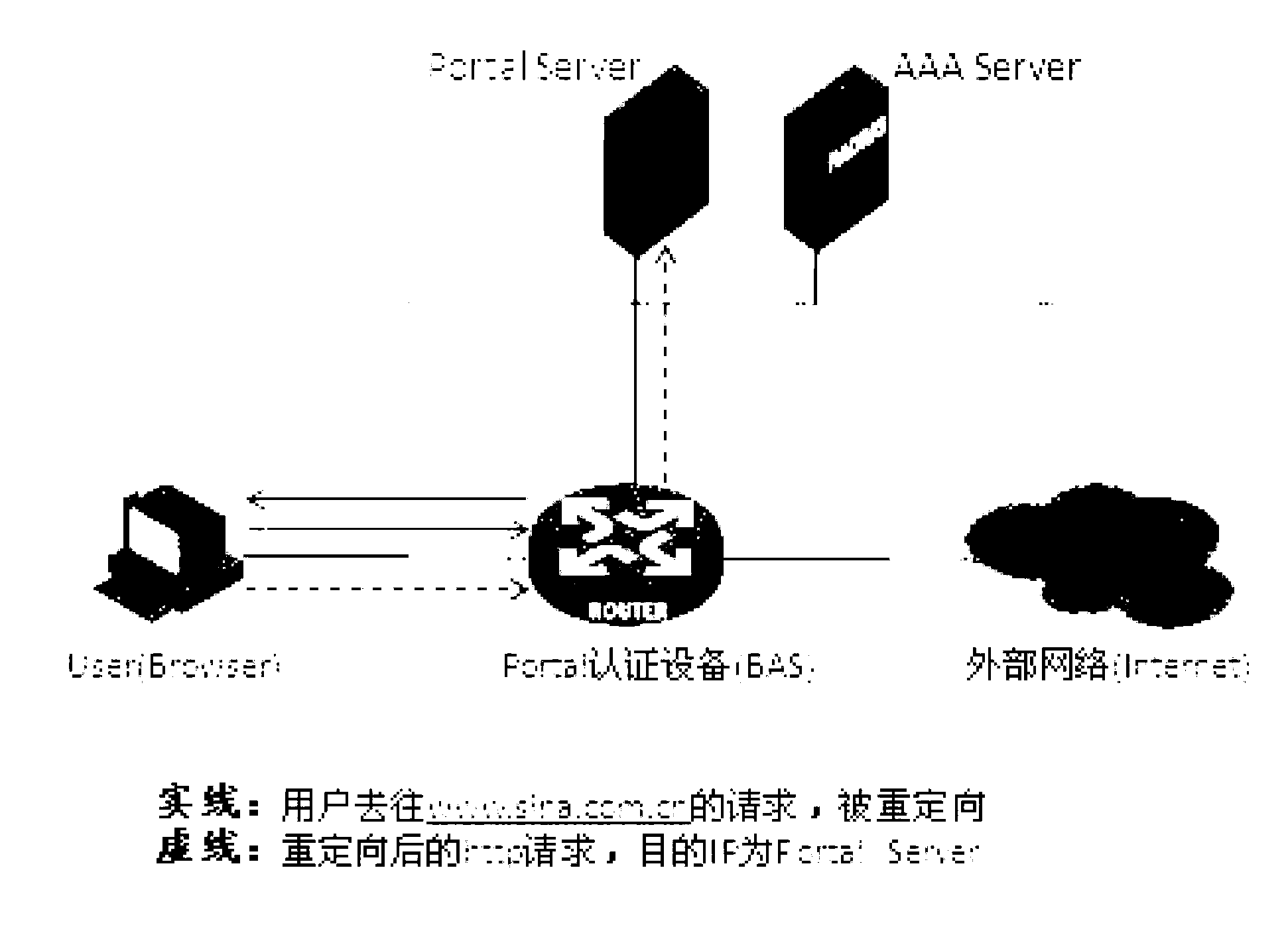
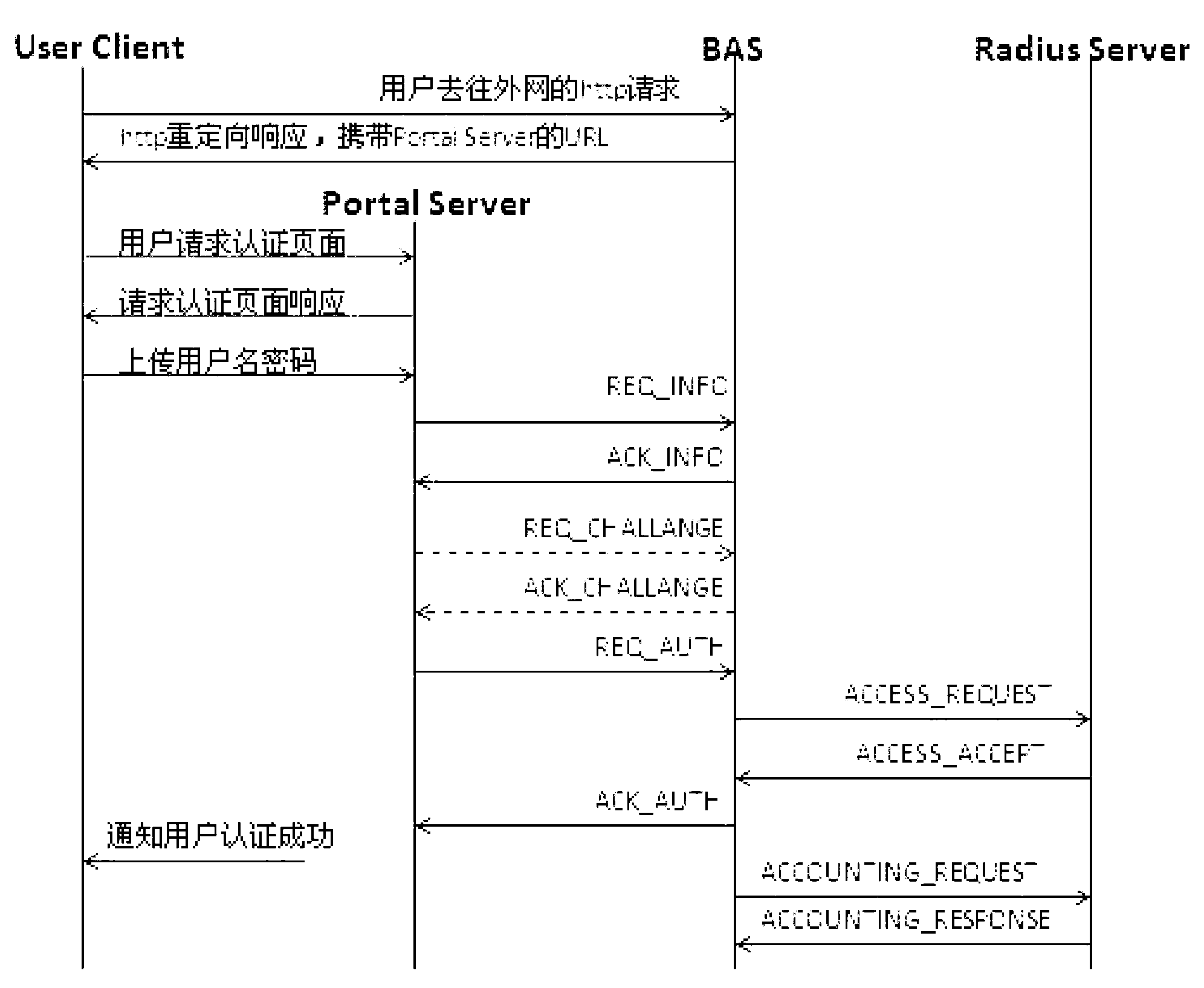
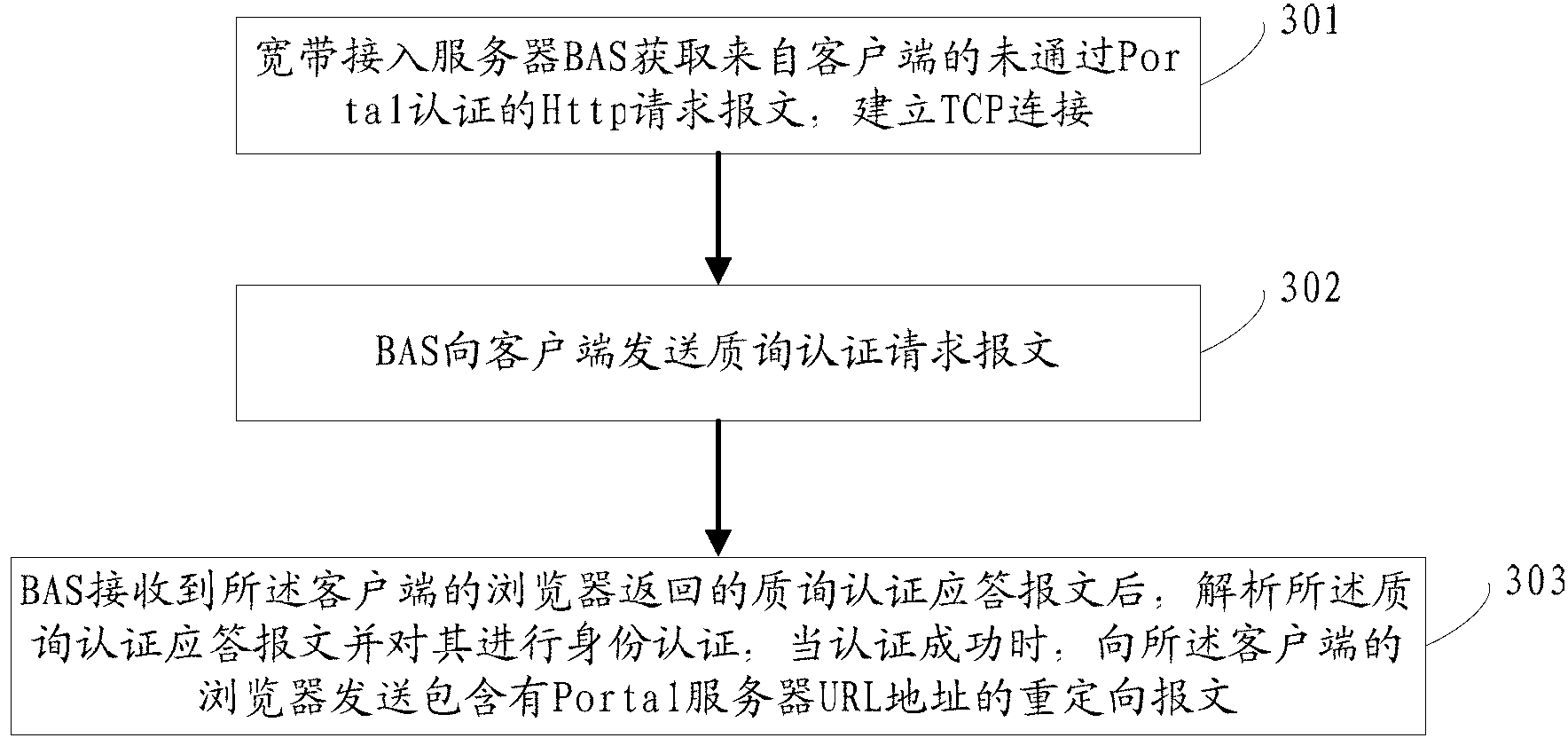
Method for realizing Portal authentication server attack prevention and broadband access server
The invention discloses a method for realizing Portal authentication server attack prevention. The method comprises the following steps of: acquiring, by a broadband access server BAS, an HTTP request message which does not pass Portal authentication from a client; establishing TCP (Transmission Control Protocol) connection; transmitting an inquiry authentication request message to the client; after receiving, by the BAS, an inquiry authentication response message returned by a browser of the client, analyzing the inquiry authentication response message and performing identity authentication on the inquiry authentication response message; and when the authentication is successful, transmitting to the browser of the client a redirect message comprising Portal server URL (Uniform Resource Locator). The invention also discloses the broadband access server BAS. According to the method and the broadband access server, before redirect message transmission, inquiry authentication is introduced to the obtained Http request by the BAS, the traffic flow produced by a non-browser application program of a client can be shielded, and the Portal server is prevented from being attacked; and meanwhile, after the inquiry authentication is introduced, the client actually needs to pass secondary authentication, and the safety of an accessed user is more strictly guaranteed.
Owner:NEW H3C TECH CO LTD
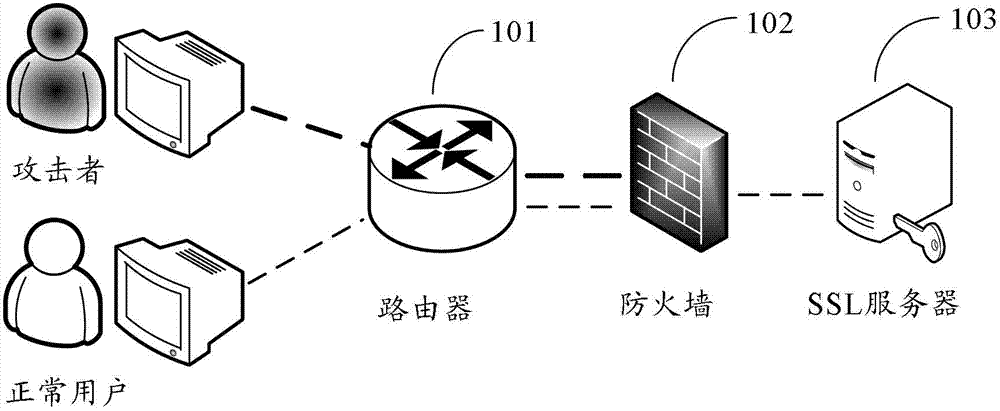
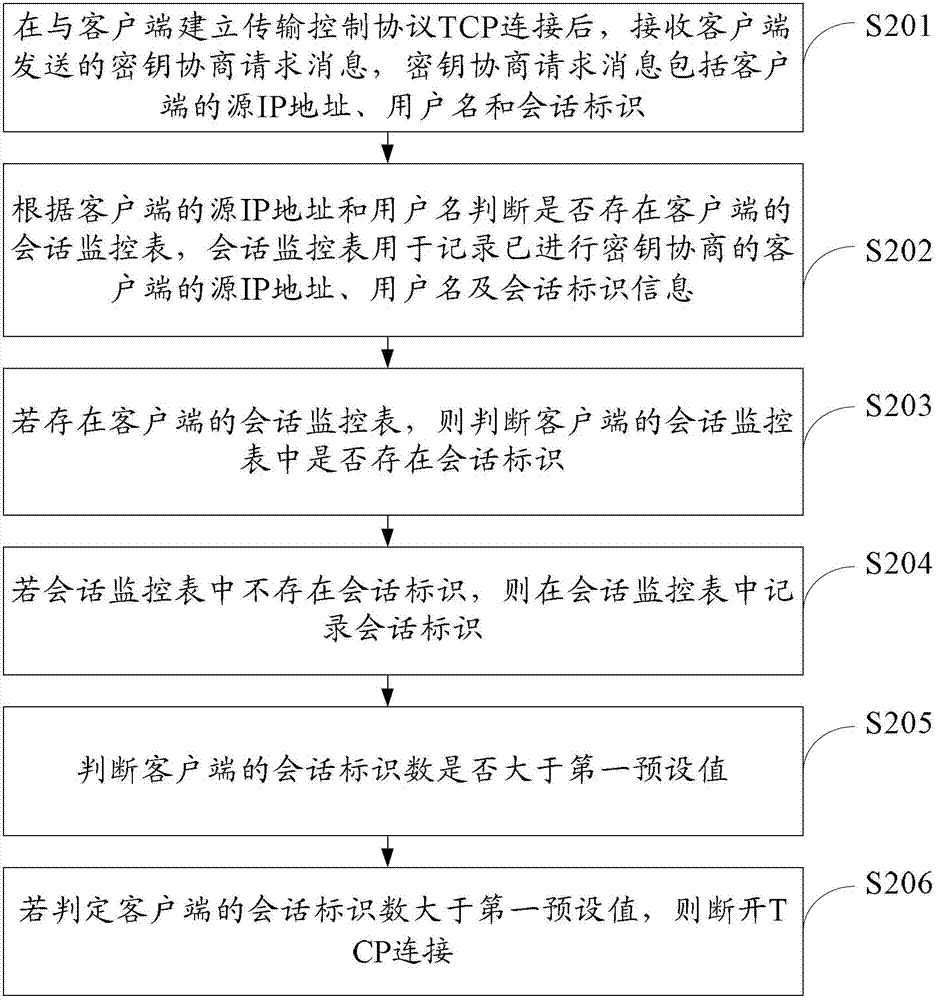
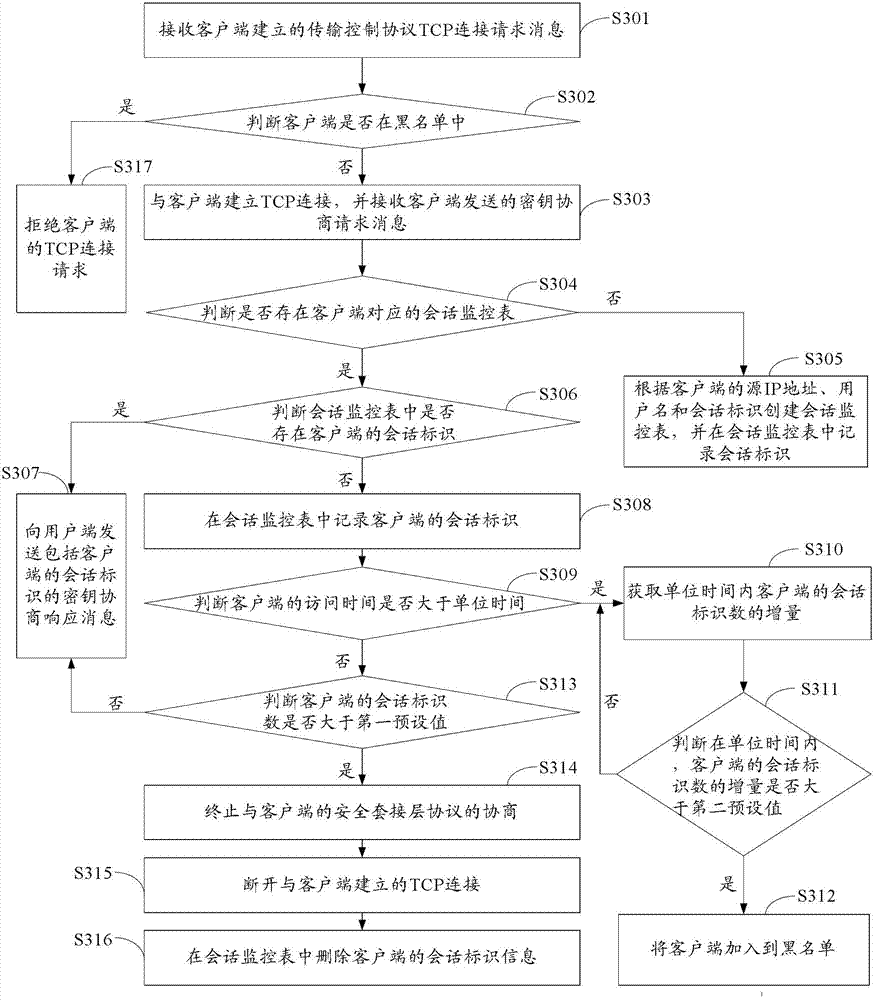
Attack prevention method and equipment
The embodiment of the invention provides an attack prevention method and equipment which relate to the field of communication and are used for effectively preventing an SSL DoS attack behavior. The method comprises the following steps that a password negotiation request message which is sent by a client terminal is received after transmission control protocol (TCP) connection with the client terminal is established; if a conversation monitoring table of the client terminal exists, the condition that whether conversation identifies exist in the conversation monitoring table of the client terminal or not is judged, and the conversion identifiers are recorded in the conversation monitoring table if a conversation identification does not exist; the condition that whether the number of the conversion identifiers of the client terminal is more than a first preset value or not is judged; and if the number of the conversation identifiers of the client terminal is more than the first preset value, the TCP connection is disconnected.
Owner:HUAWEI TECH CO LTD
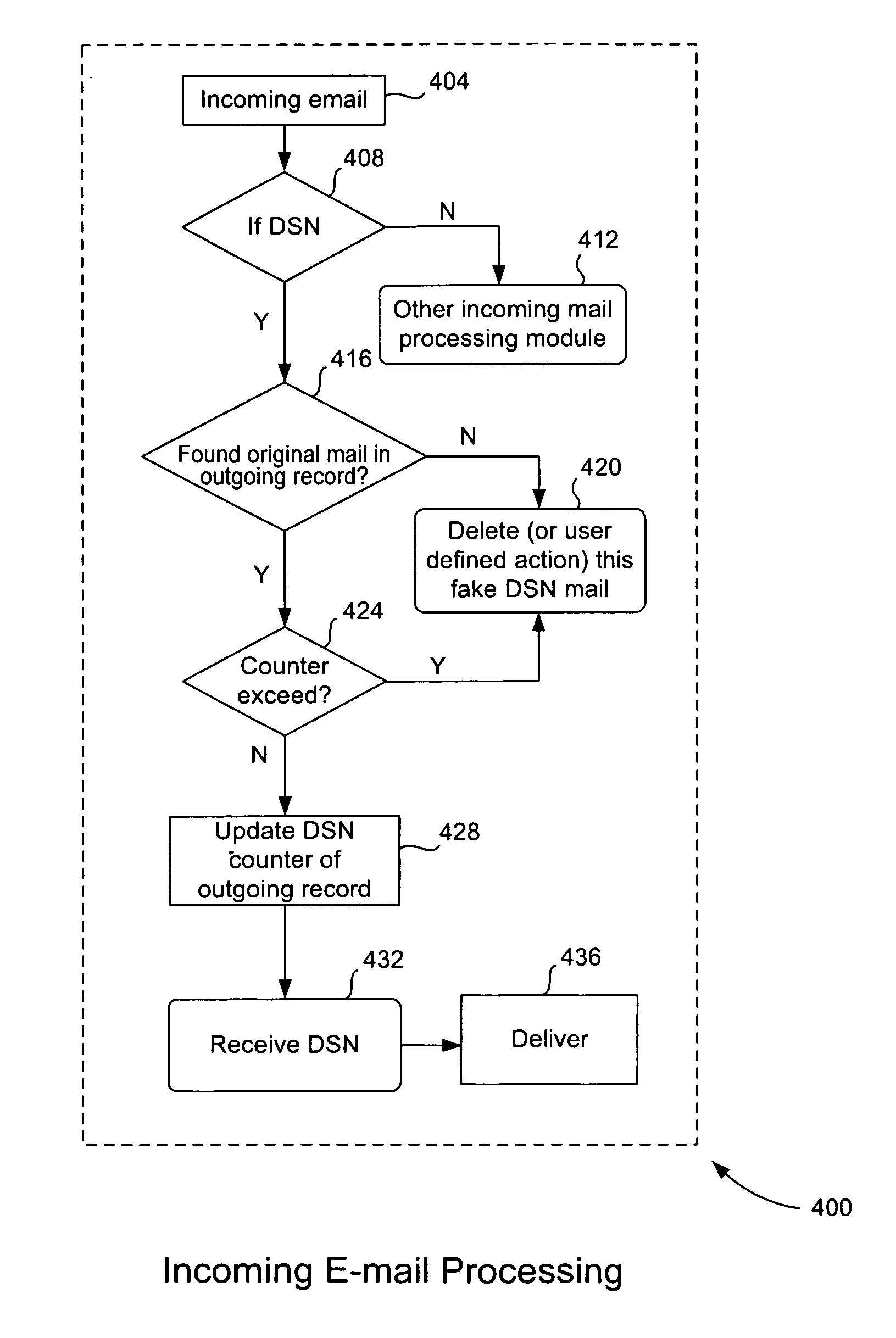
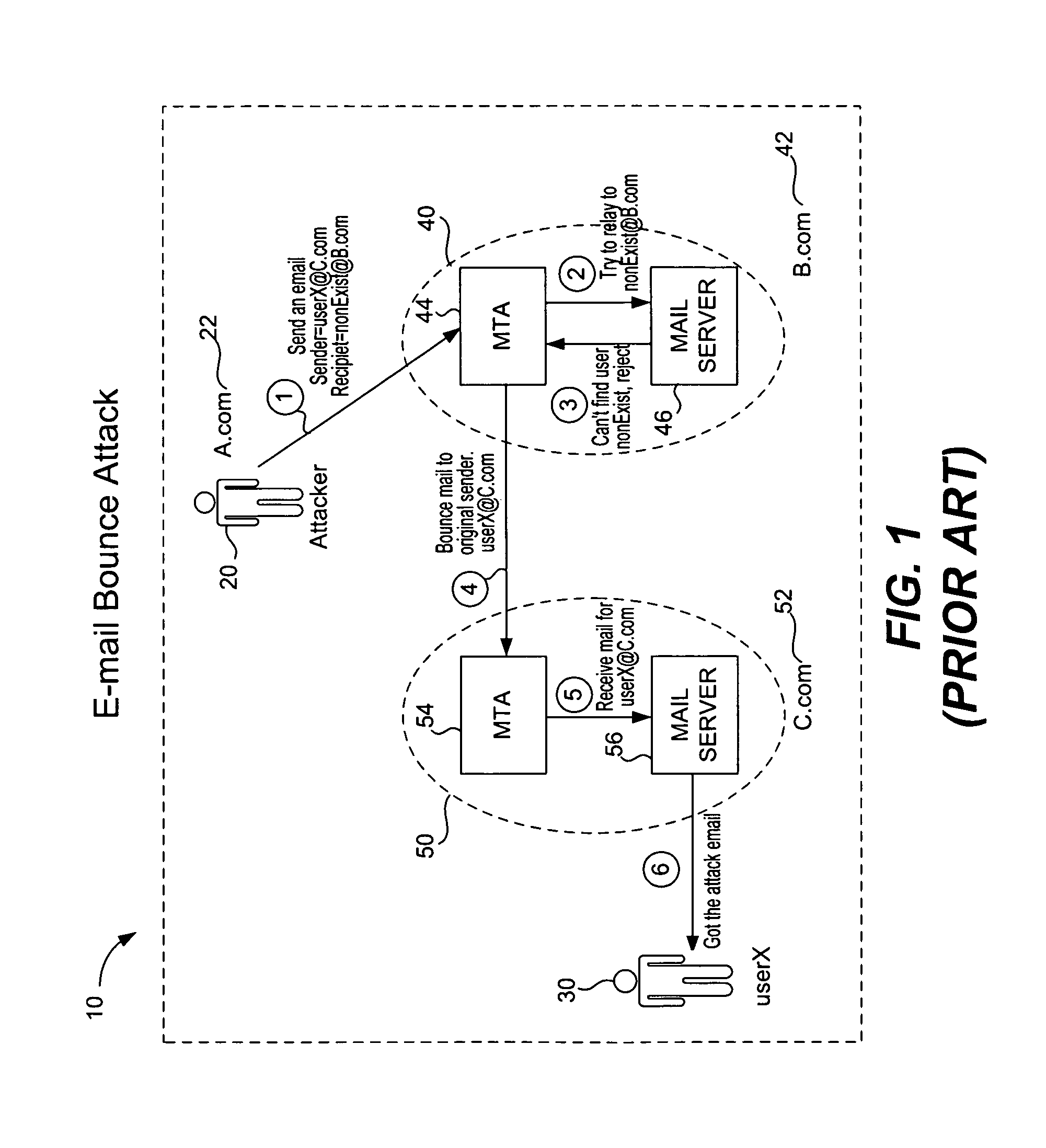
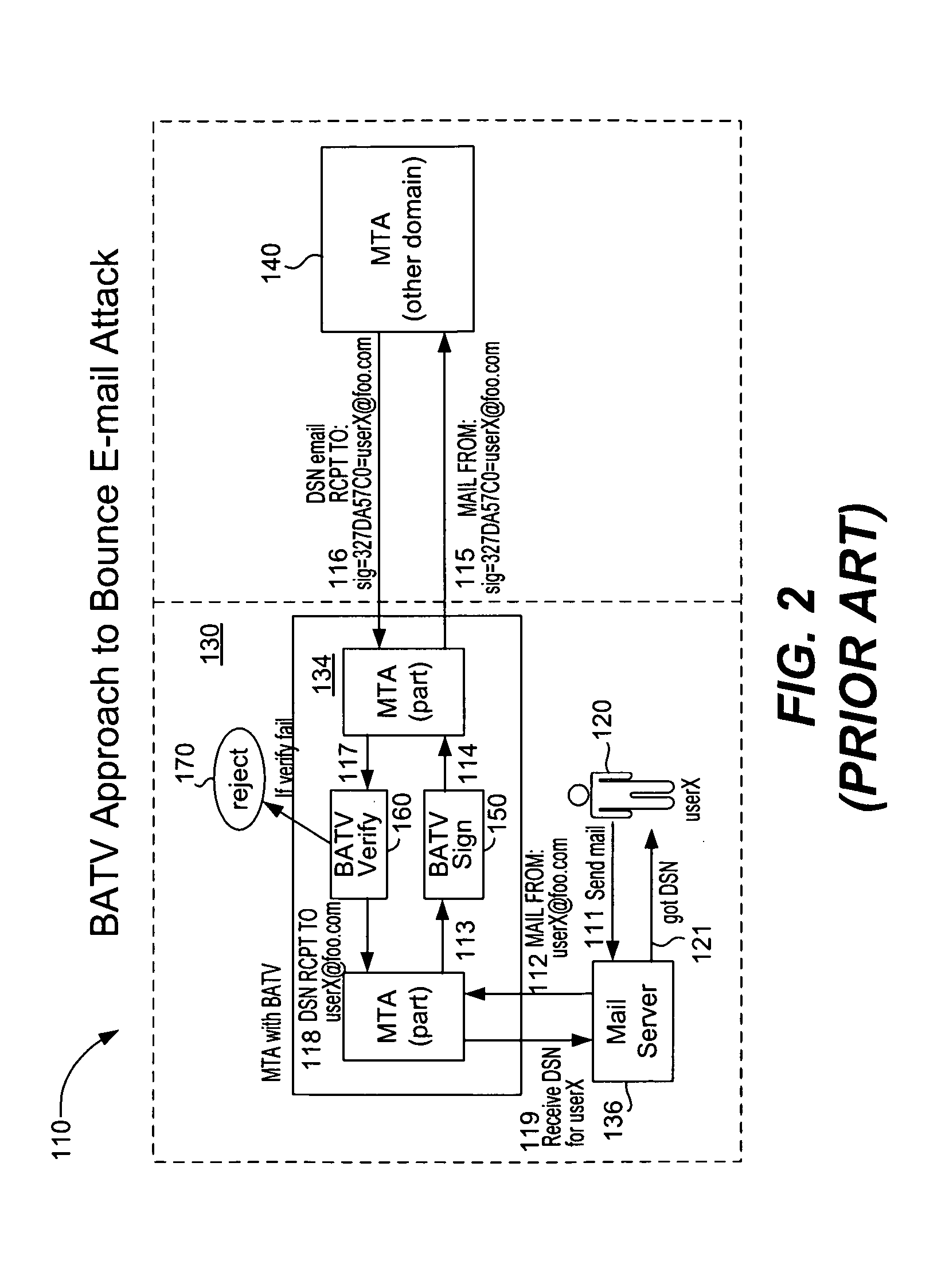
Bounce attack prevention based on e-mail message tracking
Information such as message identifier, sender, recipient, timestamp, etc., are recorded in a record in a local database as an e-mail message is sent out. A DSN counter is set equal to the total number of recipients, thus allowing returned messages to be compared against this counter to thwart a capture / replay attack. When a DSN message is received at the computer system it includes the originally sent e-mail message. The DSN message may be legitimate or it may be a faked DSN message. The system searches the local database for a record having information that matches with the returned e-mail message. If a match exists, the DSN message is legitimate and it is delivered to the original sender. If no match exists, then the DSN message has been faked and appropriate action is taken. When a match occurs, a match count value is incremented for that record and compared against the originally stored DSN count value. If the number of received DSN messages is greater than the original number of recipients, then a capture / replay attack has occurred and appropriate action is taken.
Owner:TREND MICRO INC
Network device attack prevention method and device and network device
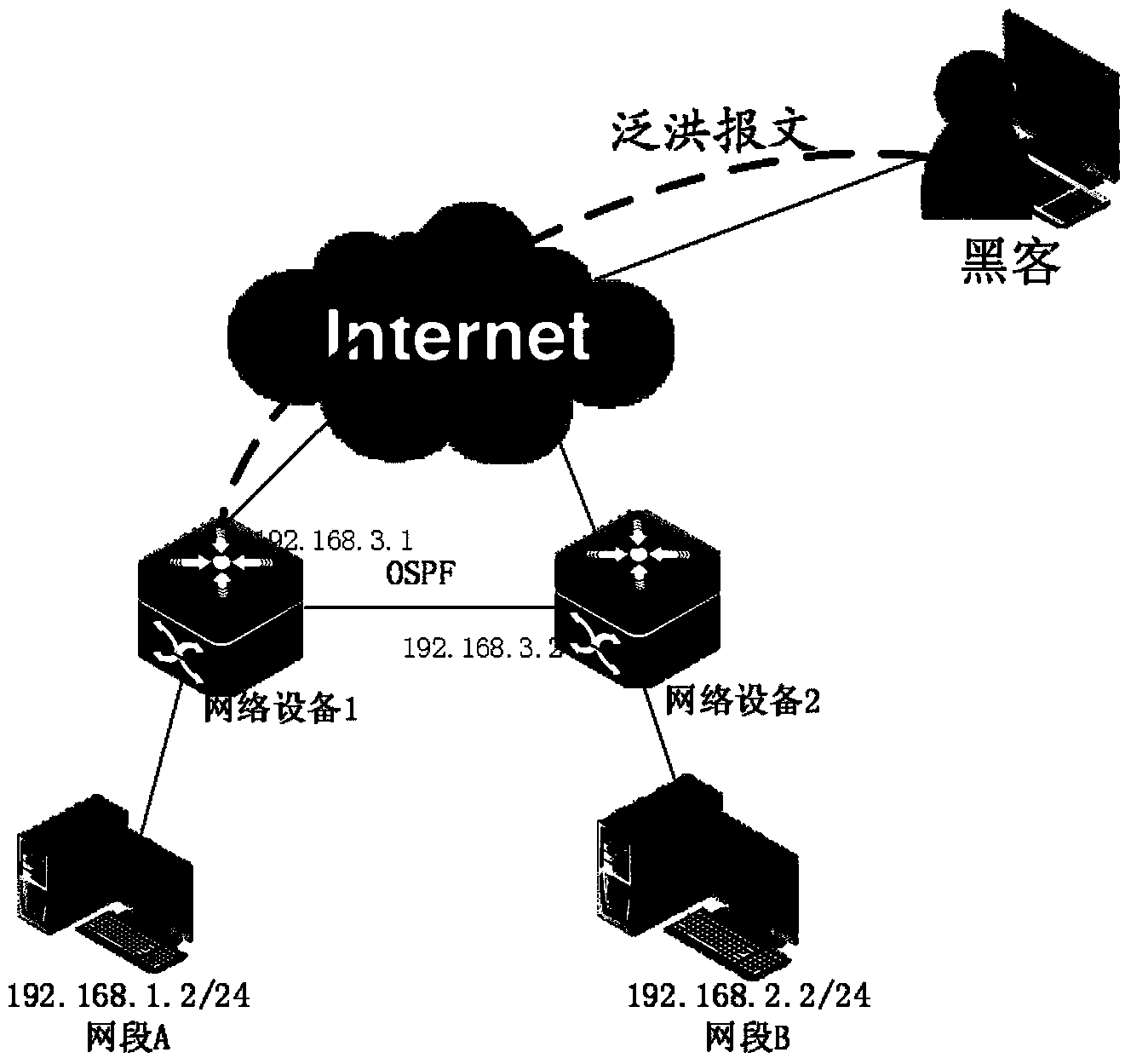
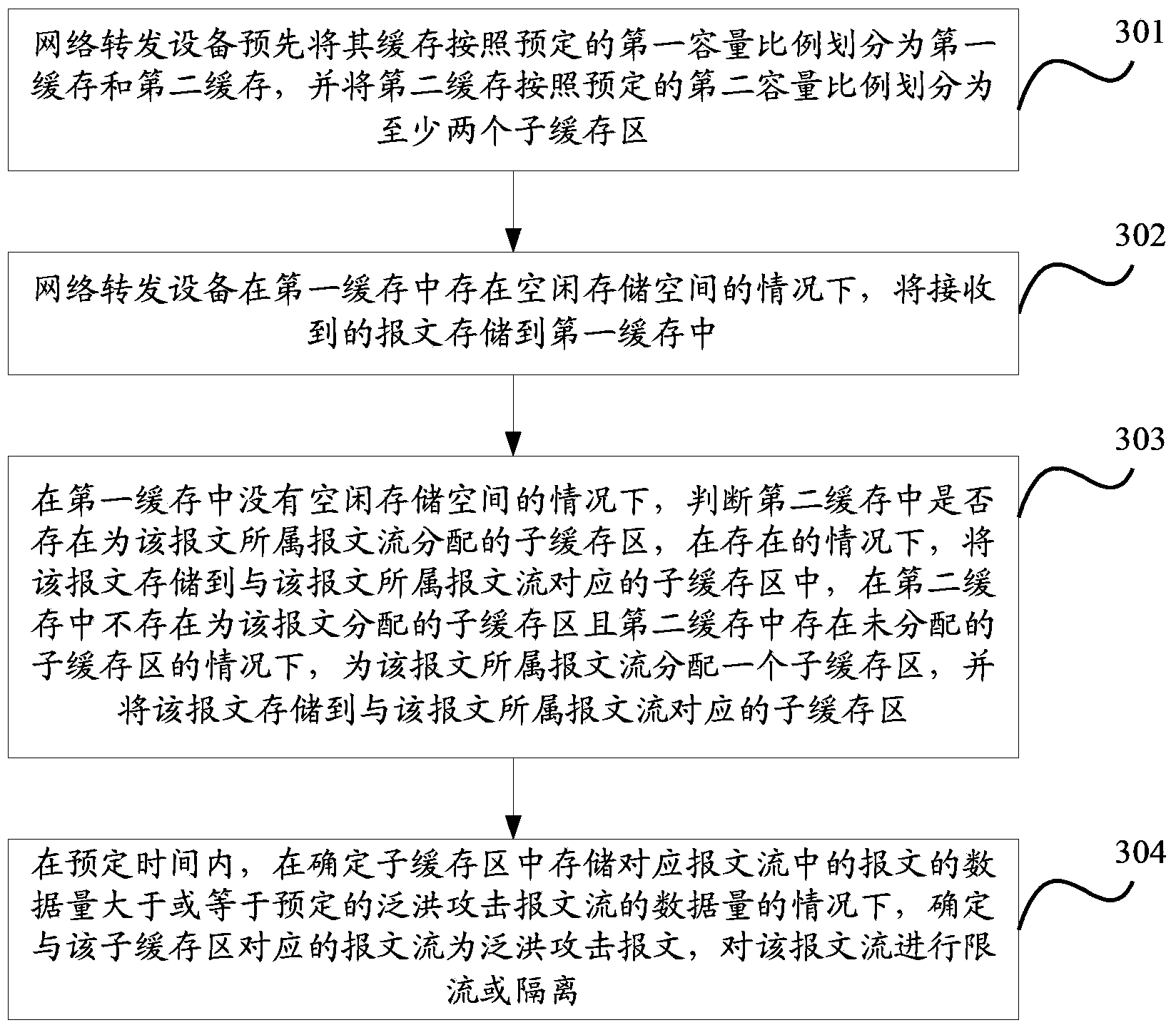
ActiveCN103384252AEnsure normal communicationEfficient identificationData switching networksRouting tableMessage flow
The invention discloses a network device attack prevention method and device and a network device. The network device attack prevention method and device and the network device are used for solving the problem that in the prior art, when the network device is attacked by network flooding messages, cache is full, so that control plane communication cannot be performed between network devices, routing tables are deleted, and forwarding between the network devices cannot be performed. Cache of a network forwarding device is divided into first cache and second cache, messages in a possible flooding attack message flow are limited to be stored in one designated sub-cache area of the first cache and the second cache, and when data volume of the messages of the corresponding message flow stored in the sub-cache area is larger than or equal to the data volume of a predetermined flooding attack message flow, the message flow corresponding to the sub-cache area is determined to be the flooding attack message. The network forwarding device can effectively recognize the network flooding attack messages and can reserve certain storage space to store other messages, and normal communication between the network forwarding devices can be ensured.
Owner:BEIJING XINWANG RUIJIE NETWORK TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com