Denial of 911 emergency service attacks prevention method
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
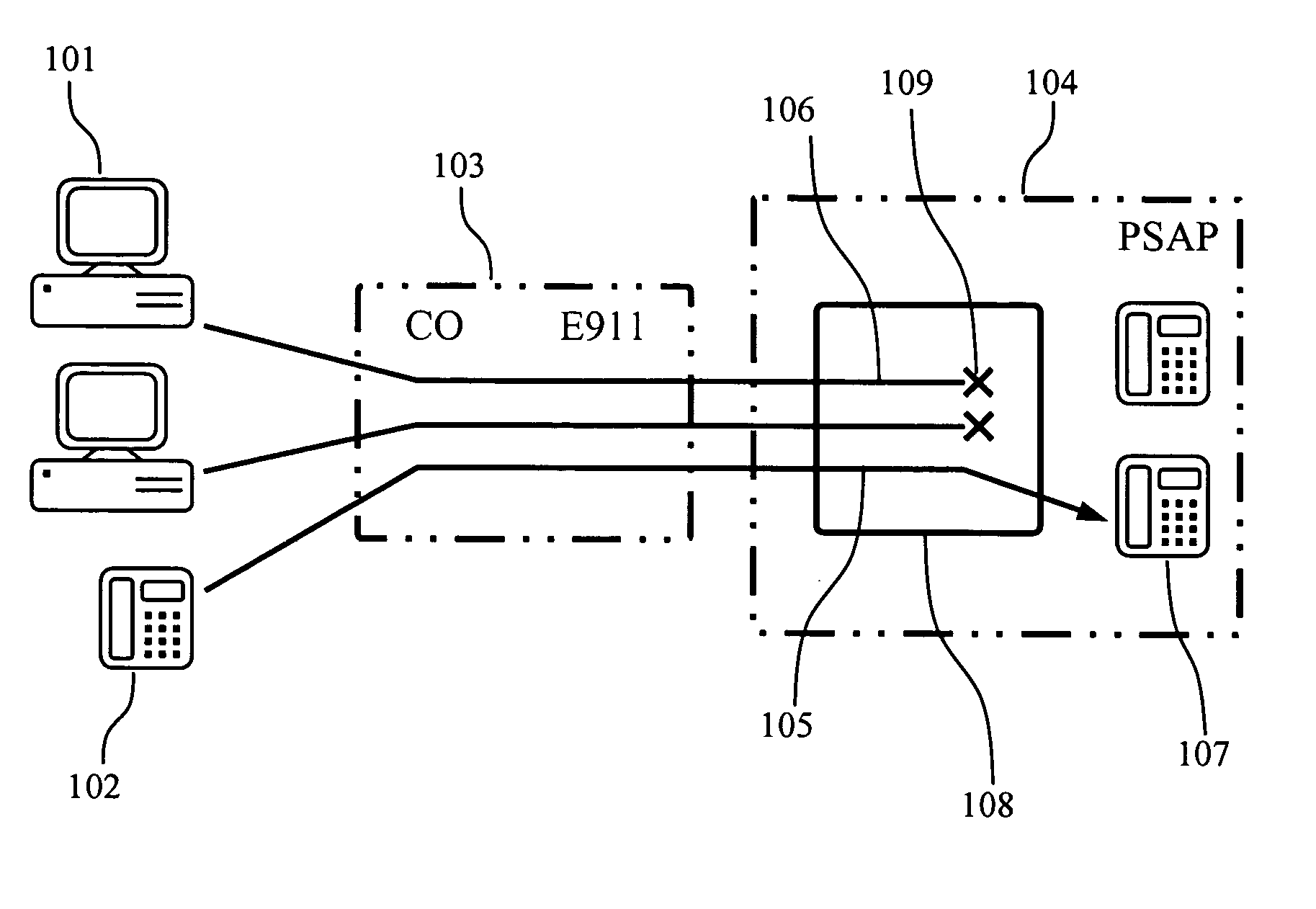
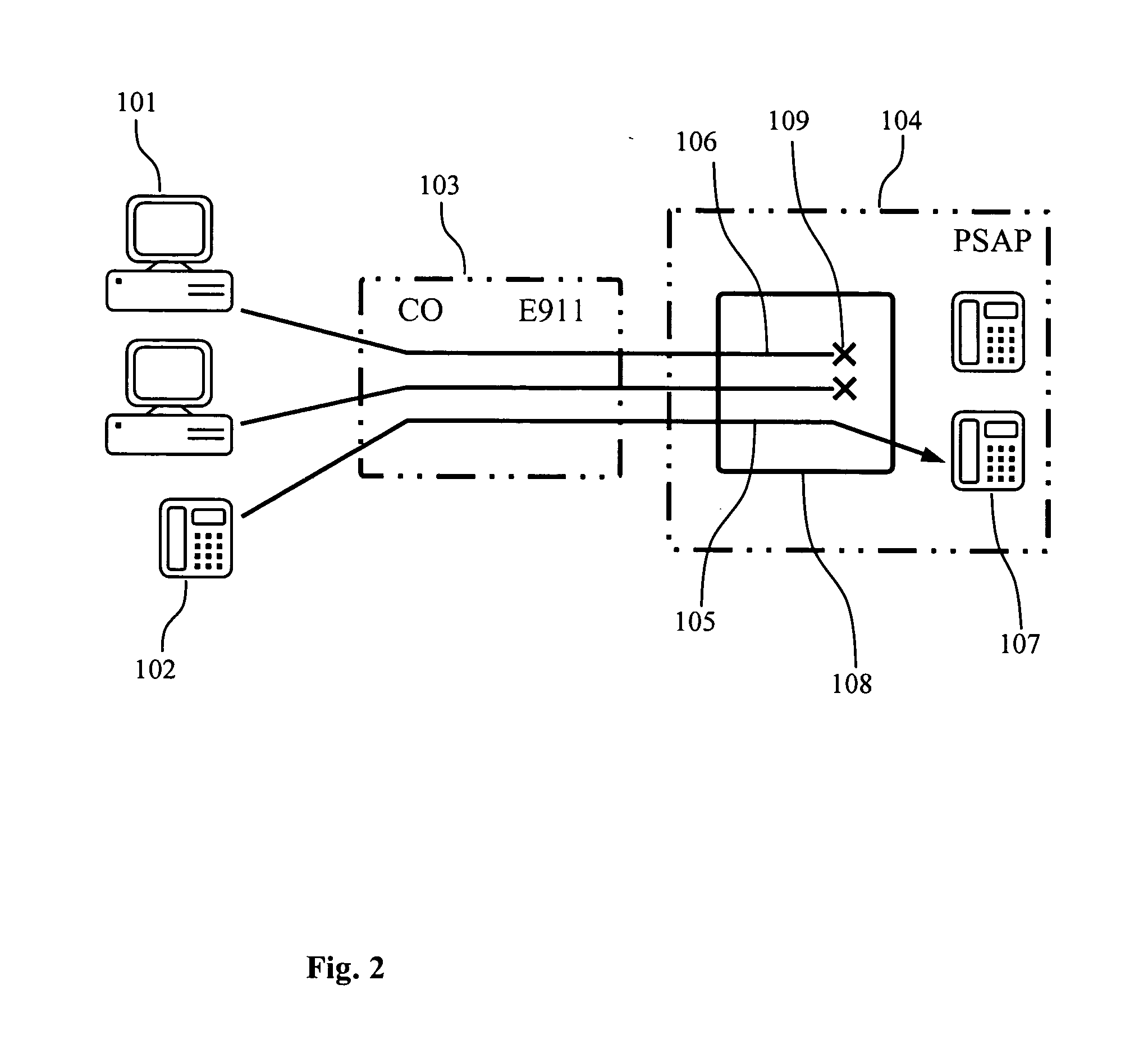
[0016]FIG. 2 is a schematic diagram illustrating the preferred embodiment of the first method of the present invention. In FIG. 2, compromised computer systems equipped with modems 101 launching DDOS attack are initiating telephone calls 106 targeting PSAP 104. The call initiator detection module 108 installed at the PSAP 104 analyses the call request, determines that the call was placed by a computer device and terminates it 109 before forwarding it to the operator 107. The legitimate calls 105 initiated by humans 102 reach operator 107.
[0017] To determine whether the call was originated by a modem or a human, one can analyze the DTMF tones pattern issued during the call placement by the subscriber. For example, when a modem dials up a number using the DTMF tone dialing mode, it provides quite accurate and constant duration of the DTMF tone followed by the fixed silent period. In contrast, when a human dials a number, the duration of the tone or a silent phase will be random and v...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com