Network device attack prevention method and device and network device
A network device and anti-attack technology, which is applied in the direction of data exchange network, digital transmission system, electrical components, etc., can solve the problems of deleting routing tables, network equipment cannot forward, cache is full, etc., and achieve the effect of ensuring normal communication
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
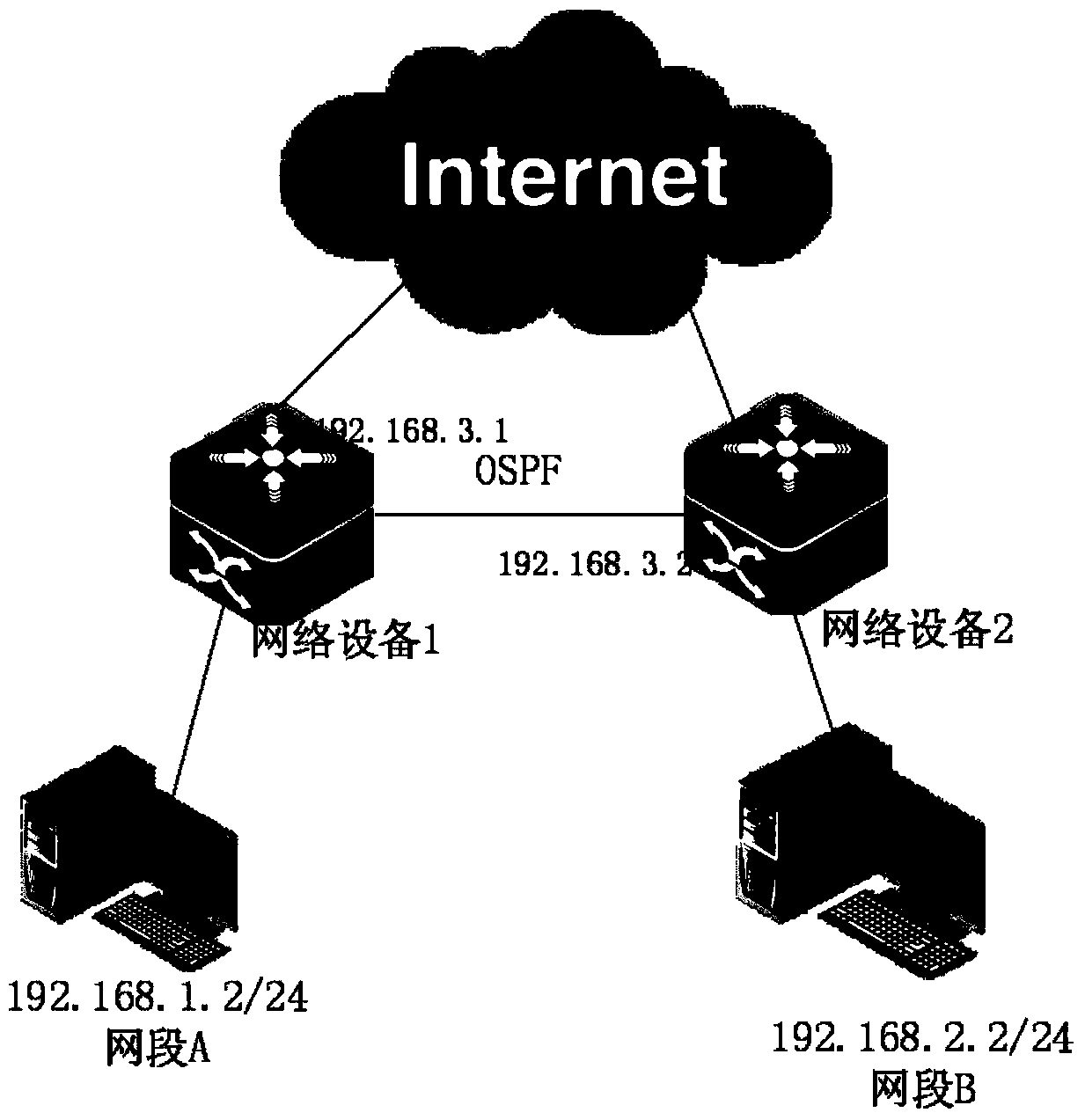
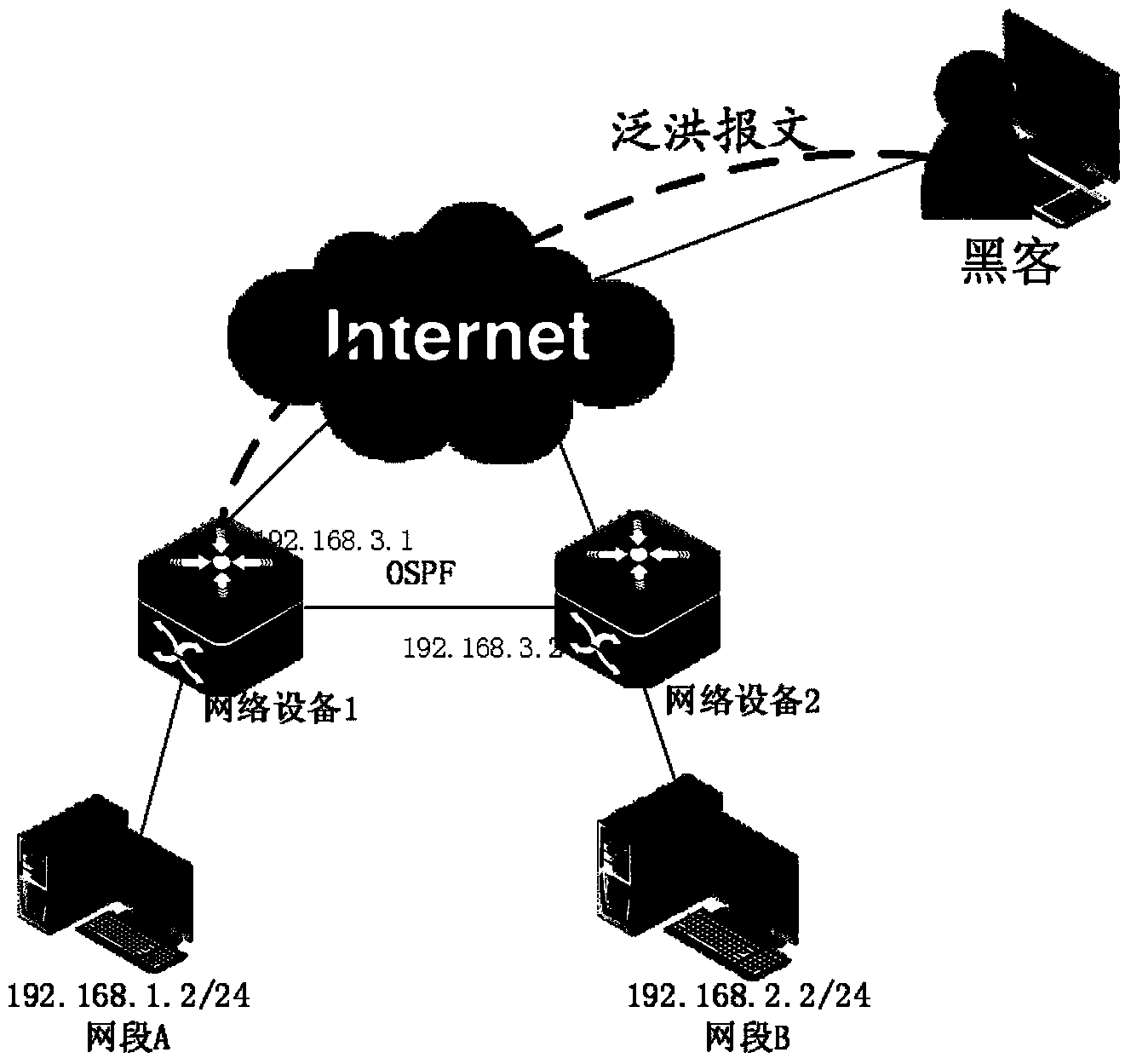
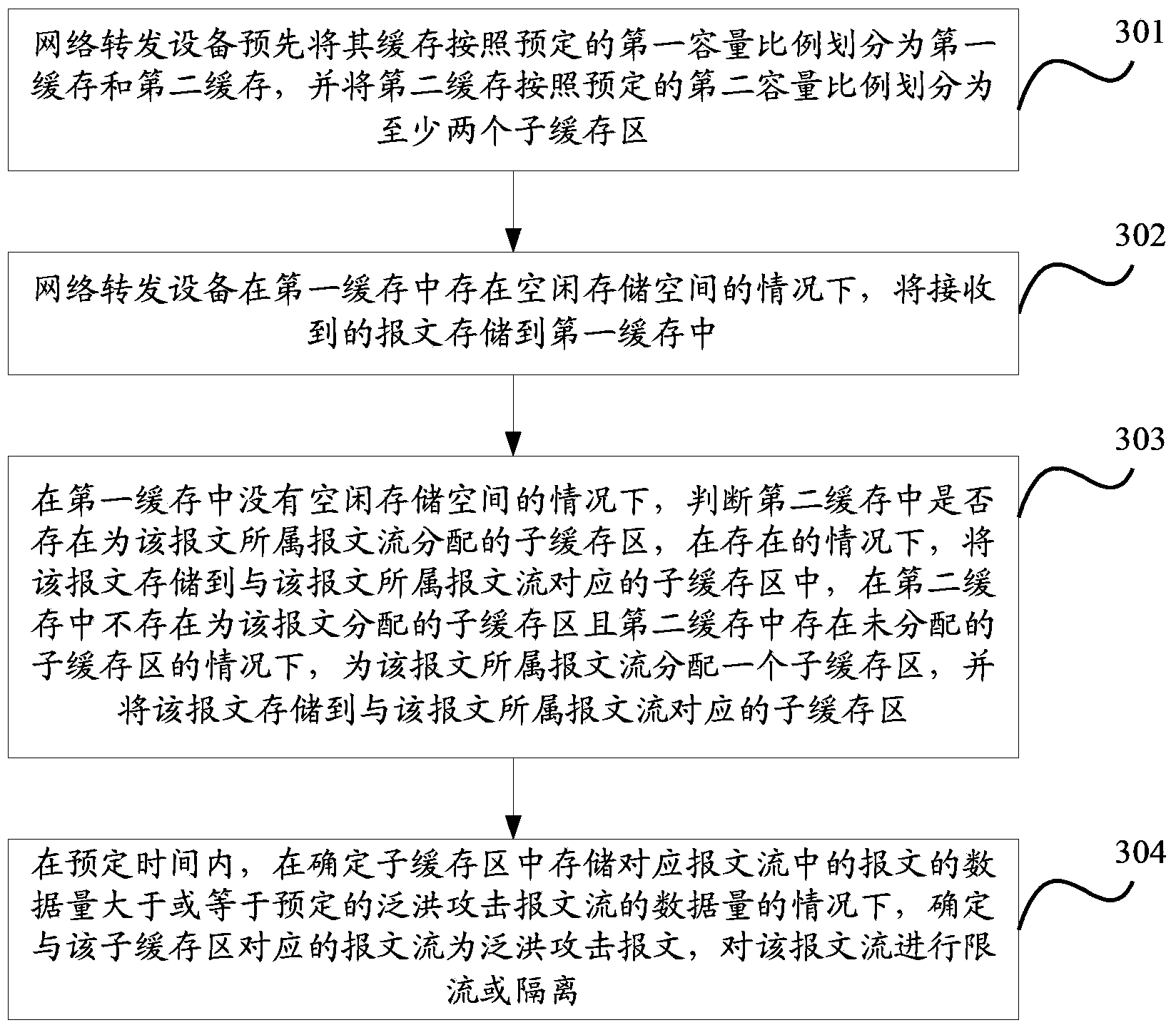
[0044] image 3 A working flowchart of a method for defending a network device against an attack provided by an embodiment of the present invention is shown, and the method includes:
[0045] Step 301, the network forwarding device pre-divides its cache into a first cache and a second cache according to a predetermined first capacity ratio, and divides the second cache into at least two sub-buffer areas according to a predetermined second capacity ratio;
[0046] Wherein, the first cache is equivalent to a public cache and is used to store various types of messages, and the second cache is equivalent to a specified cache and is used to cache messages of a specified message flow;
[0047] Among them, the first capacity ratio and the second capacity ratio can be set according to the needs of specific application scenarios. Two-capacity ratio, that is, the capacity of the first cache is greater than the capacity of the second cache. Similarly, the capacity of the sub-buffer with...
Embodiment 2
[0093] Figure 10 A working flowchart of a method for defending a network device against an attack provided by an embodiment of the present invention is shown, and the method includes:
[0094] Step 1001, the network forwarding device pre-divides the transmission bandwidth with other network forwarding devices into the first bandwidth and the second bandwidth according to the predetermined first capacity ratio, and divides the second bandwidth according to the predetermined second capacity ratio into at least Two sub-bandwidths;
[0095]Specifically, the first bandwidth is equivalent to a public bandwidth and is used to transmit various types of messages, and the second bandwidth is equivalent to a specified bandwidth and is used to transmit messages of a specified message flow;
[0096] Wherein, the setting of the first capacity ratio and the second capacity ratio can refer to the above-mentioned step 301, which will not be repeated here;
[0097] Specifically, such as Fi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com