Patents
Literature
197 results about "Flooding attack" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
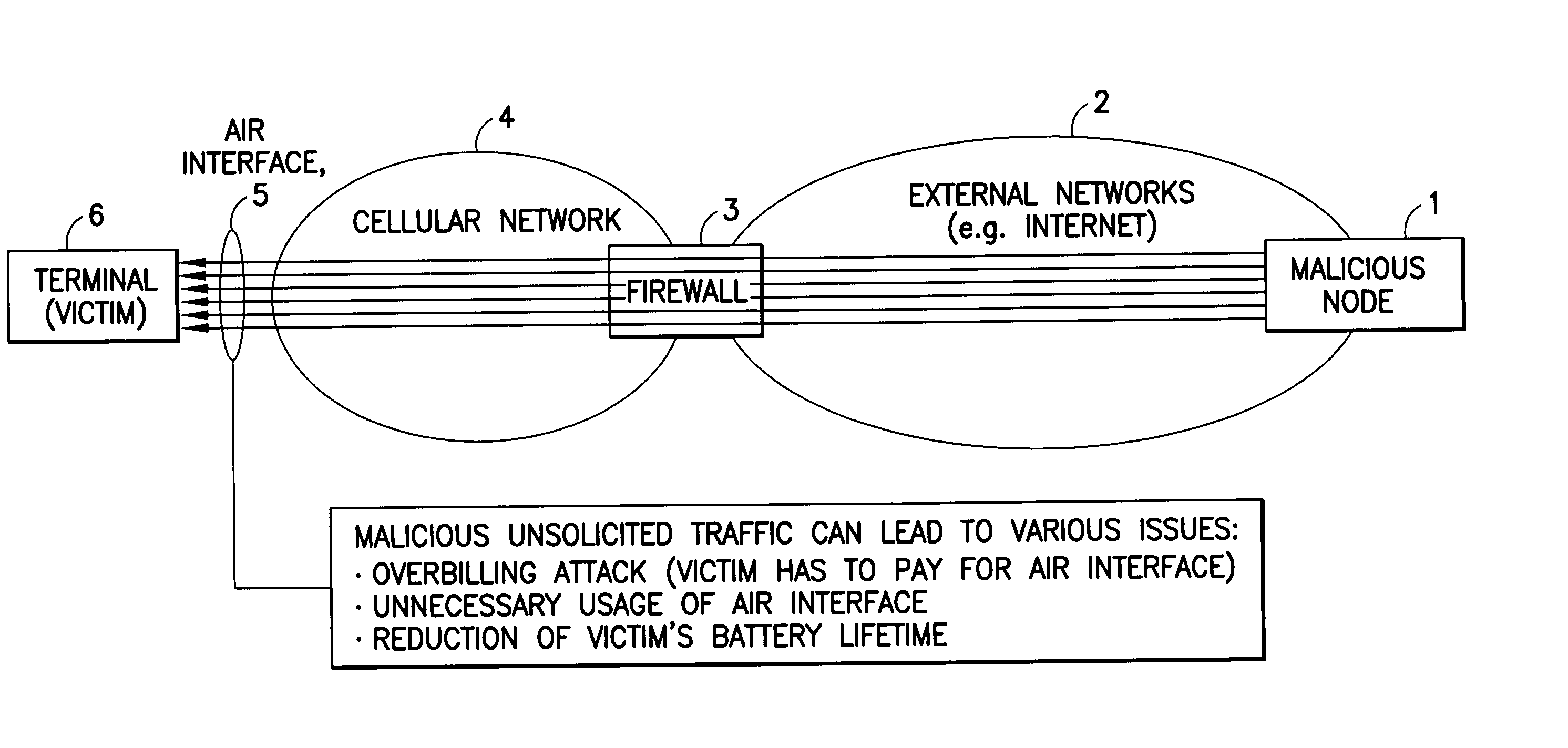
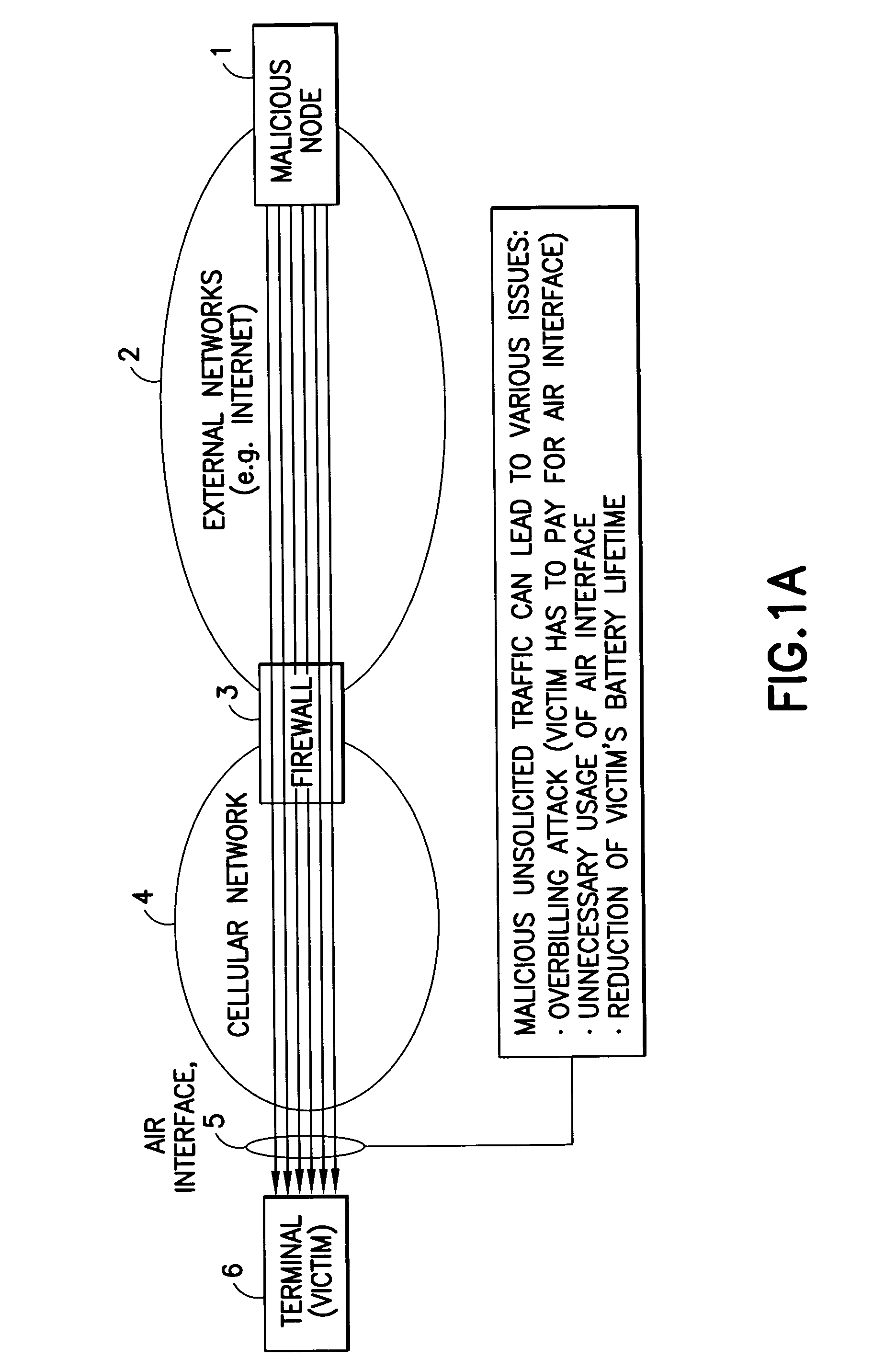
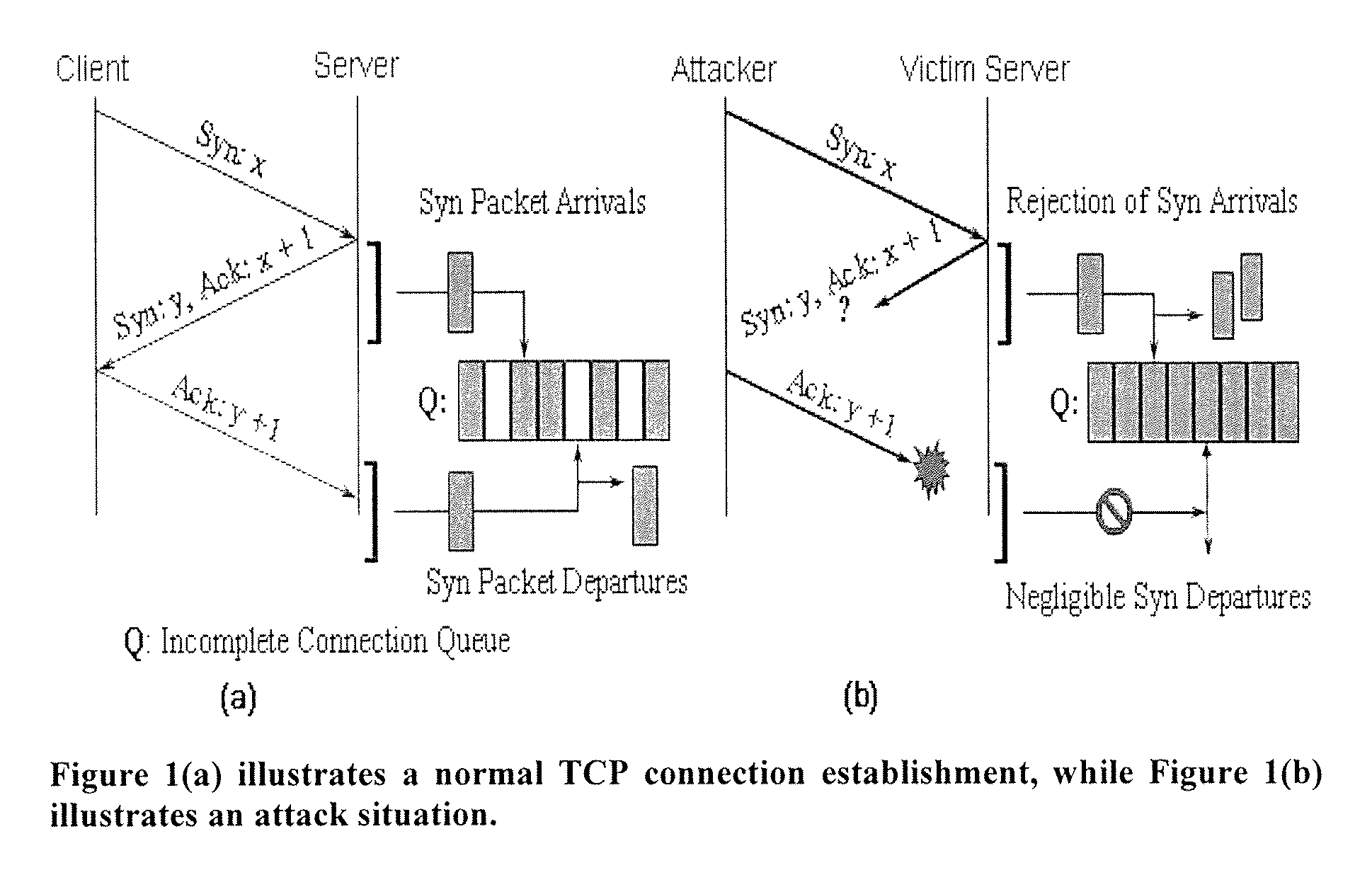
Answer Wiki. Flooding Attacks: A SYN flood is a form of denial-of-service attack in which an attacker sends a succession of SYN requests to a target's system in an attempt to consume enough server resources to make the system unresponsive to legitimate traffic.
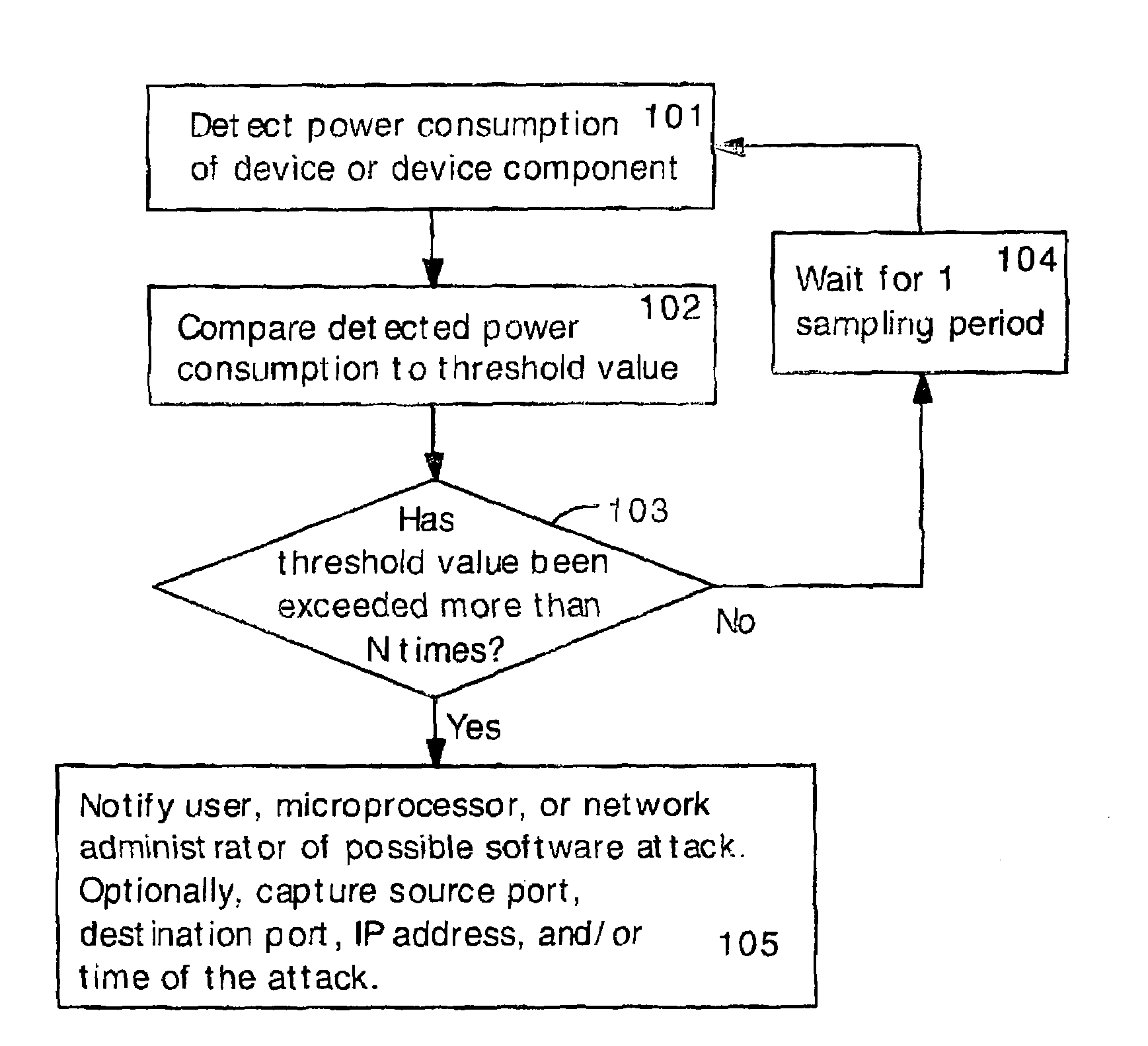
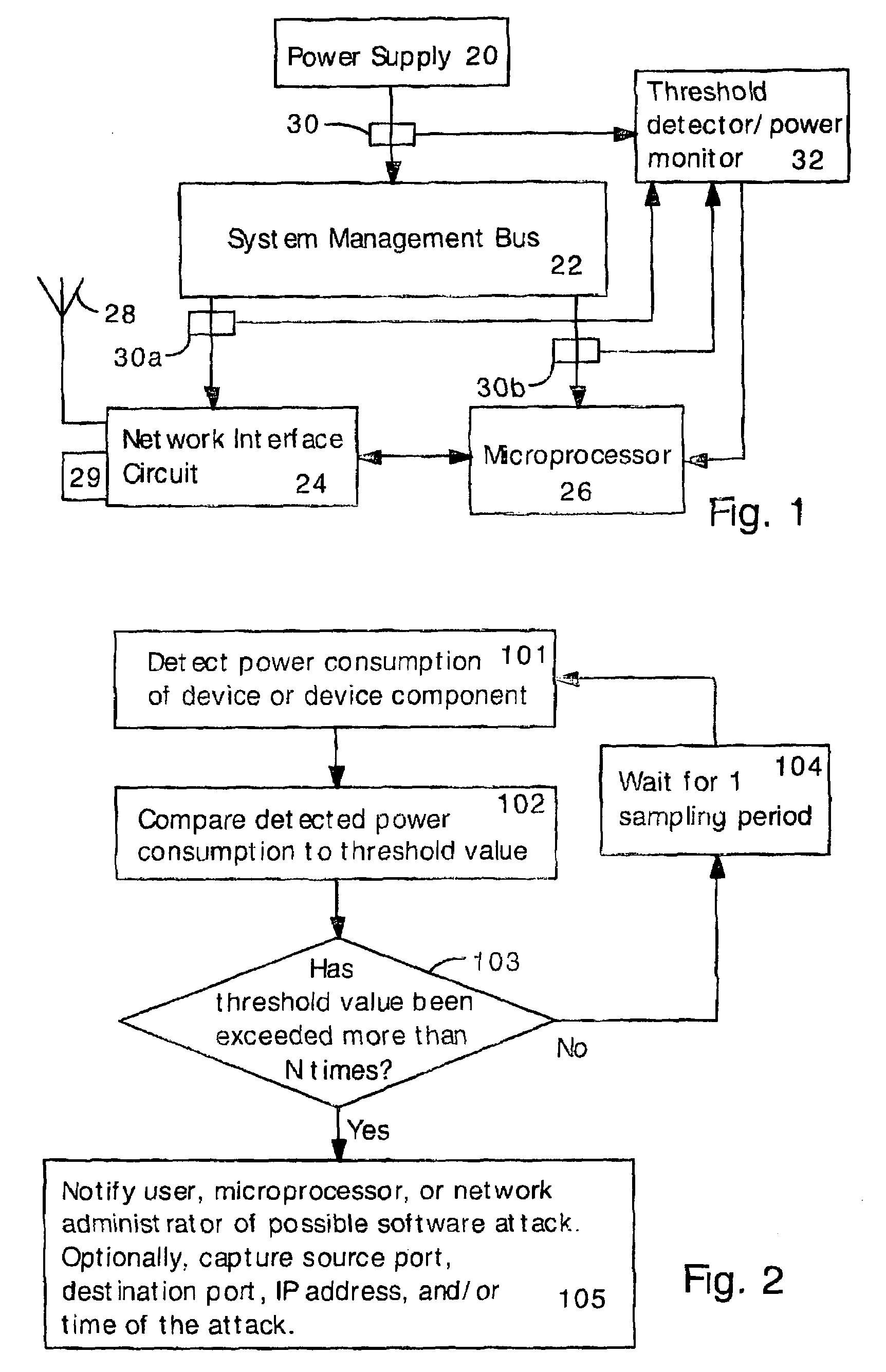
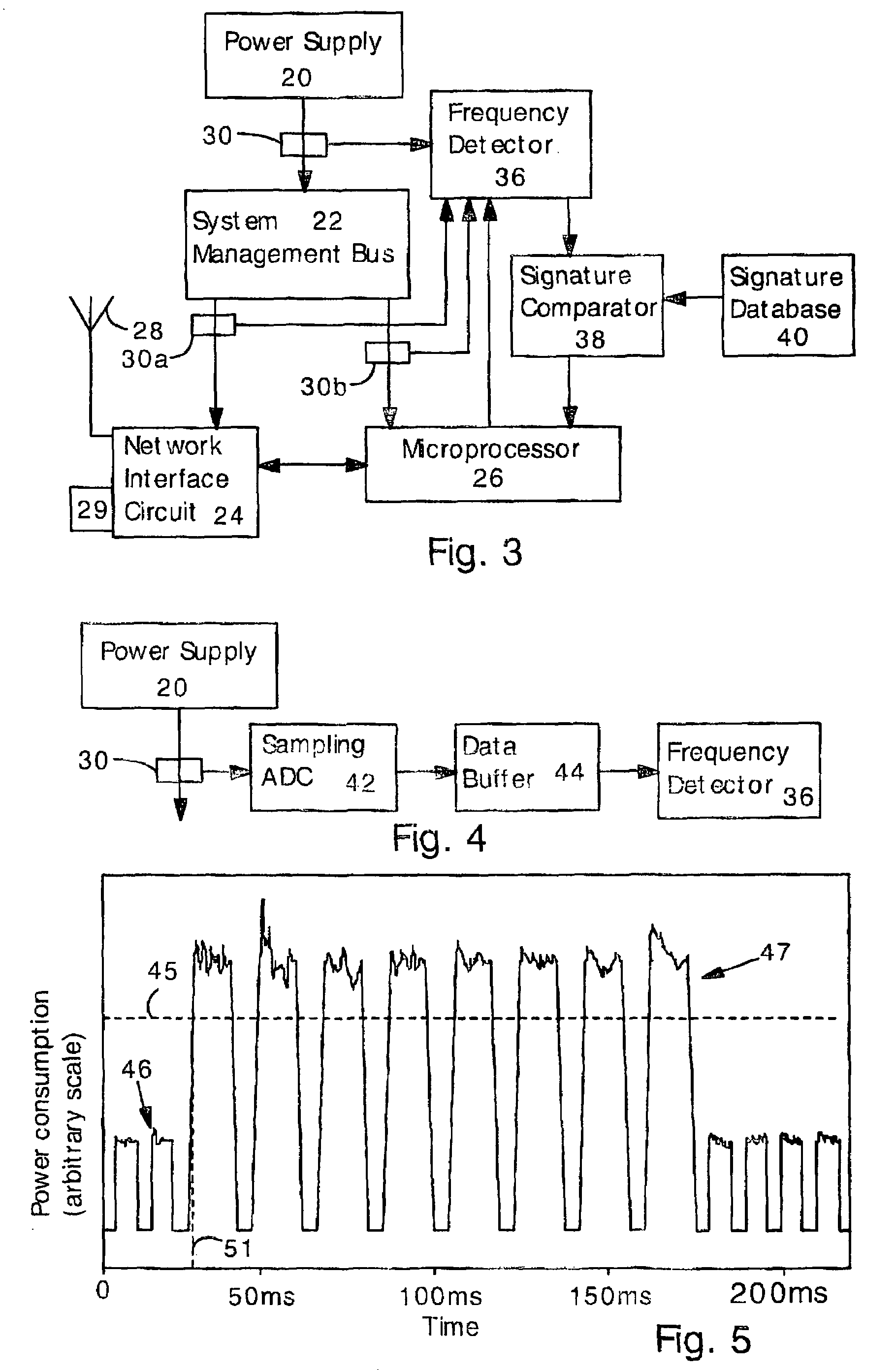
Detecting Software Attacks By Monitoring Electric Power Consumption Patterns
ActiveUS20080276111A1Reduce the valueMemory loss protectionUnauthorized memory use protectionFourier transform on finite groupsEngineering
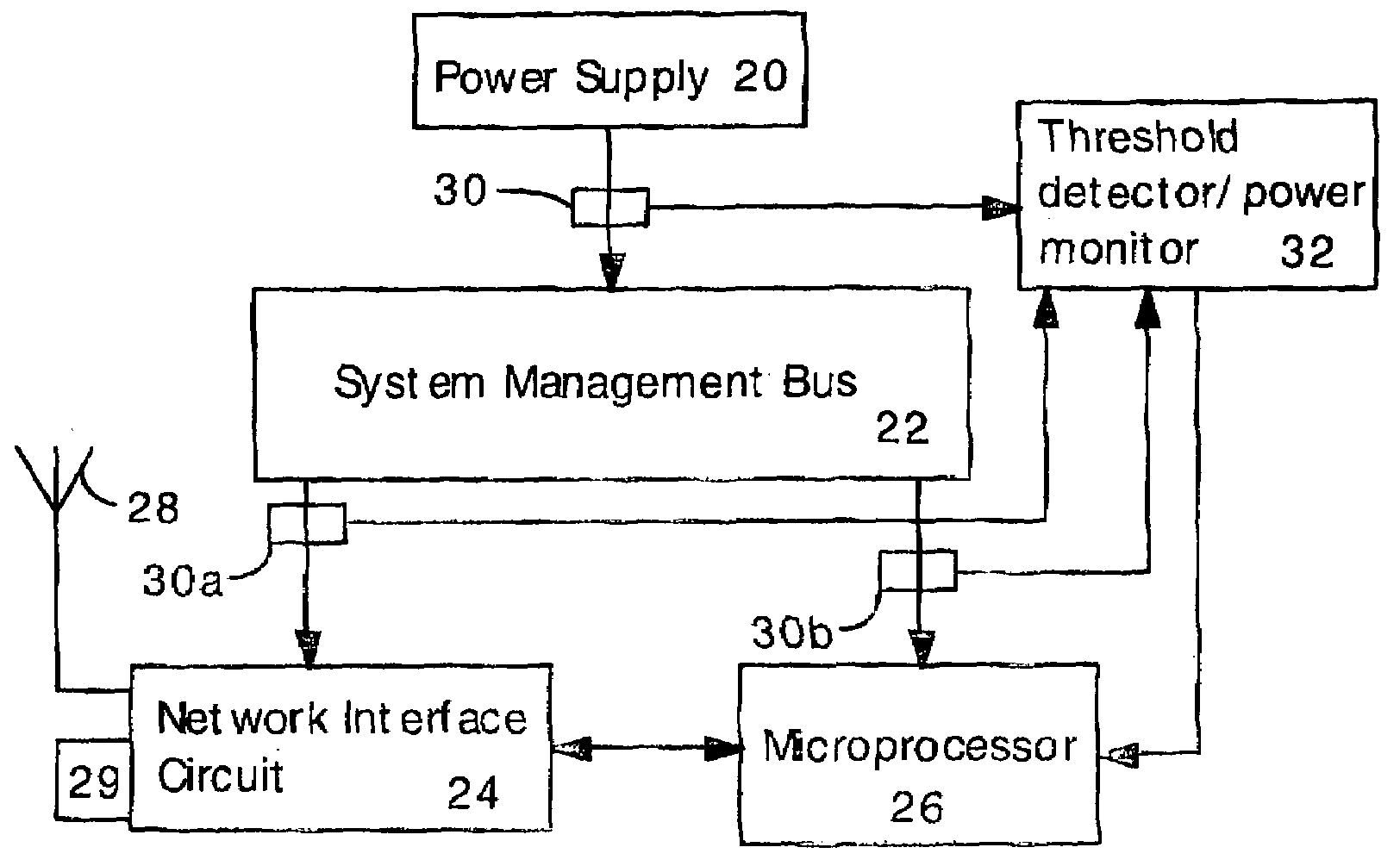
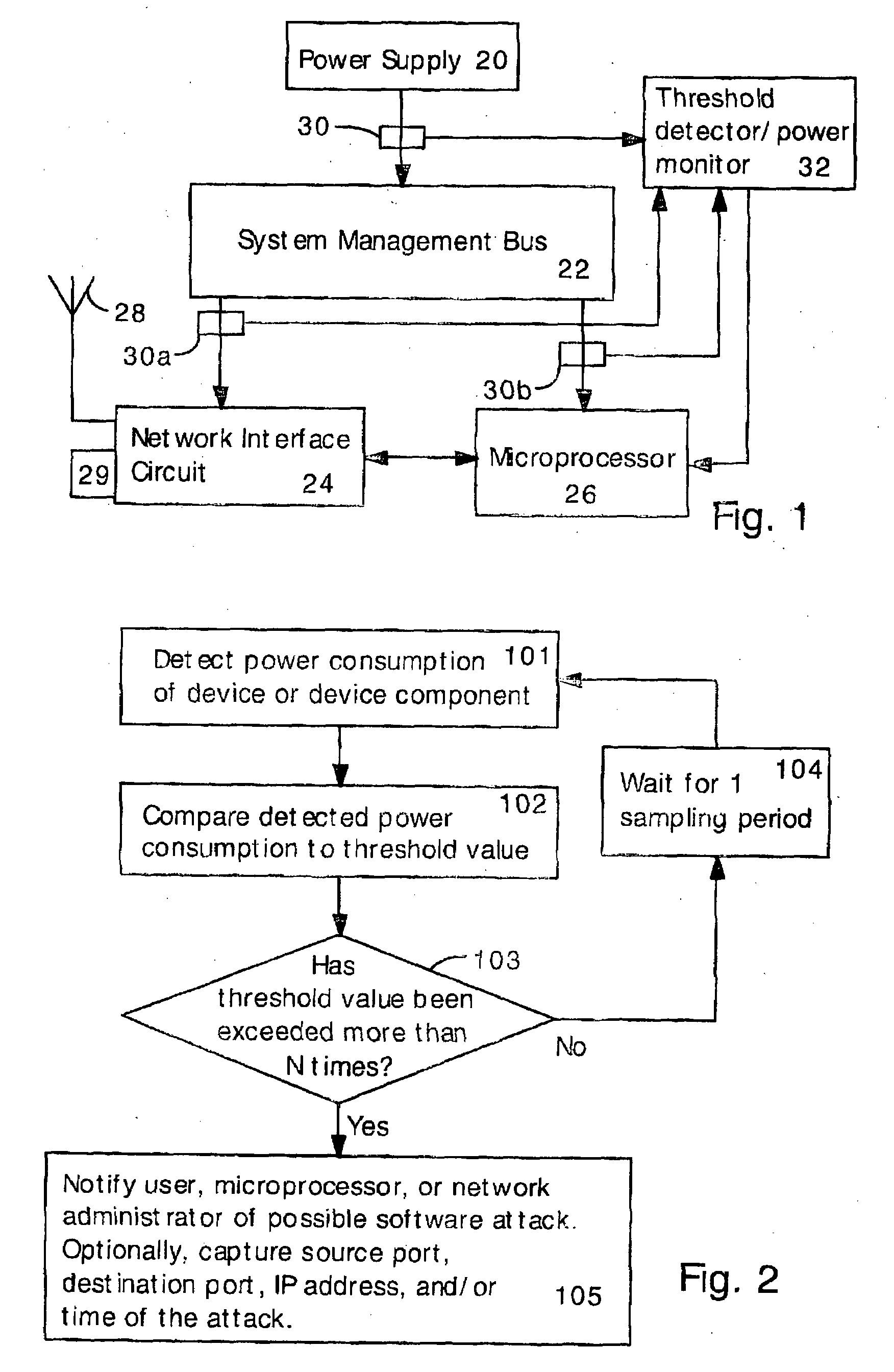
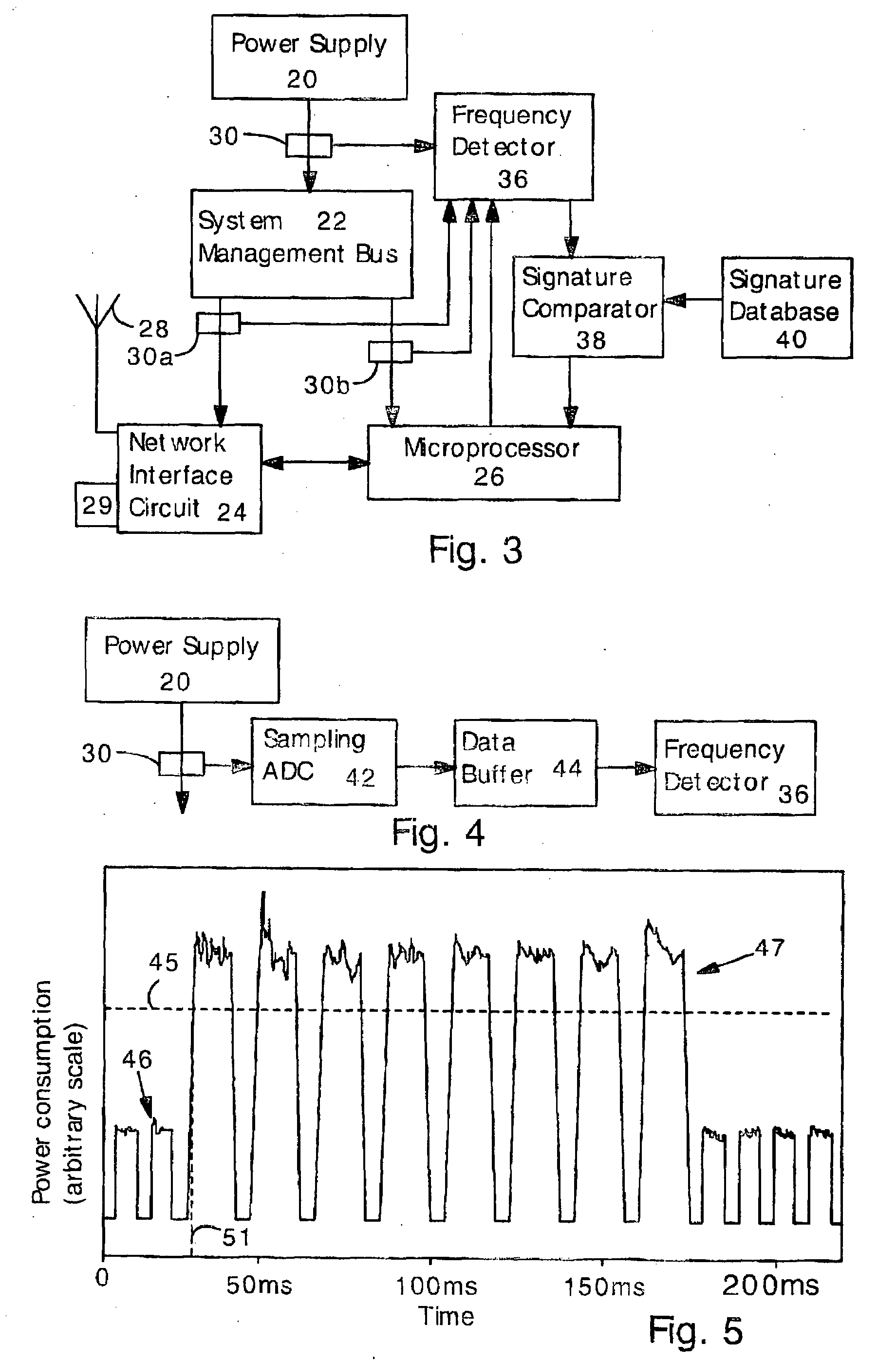
Software attacks such as worms and viruses are detected in an electronic device by monitoring power consumption patterns. In a first embodiment, software attacks are detected by an increase in power consumption. The increased power consumption can be caused by increased network traffic, or by increased activity in the microprocessor. Monitoring power consumption is particularly effective for detecting DOS / flooding attacks when the electronic device is in an idle state. In a second embodiment, a power consumption signal is converted to the frequency domain (e.g., by fast Fourier transform). The highest amplitude frequencies are identified. Specific software attacks produce characteristic frequencies in the power consumption signal. Software attacks are therefore detected by matching the highest amplitude frequencies with frequencies associated with specific worms and viruses. Identification of a particular software attack typically requires matching of 3 or more of the highest amplitude frequencies, and, optionally, amplitude information.
Owner:UNITED STATES OF AMERICA THE AS REPRESENTED BY THE SEC OF THE ARMY +1
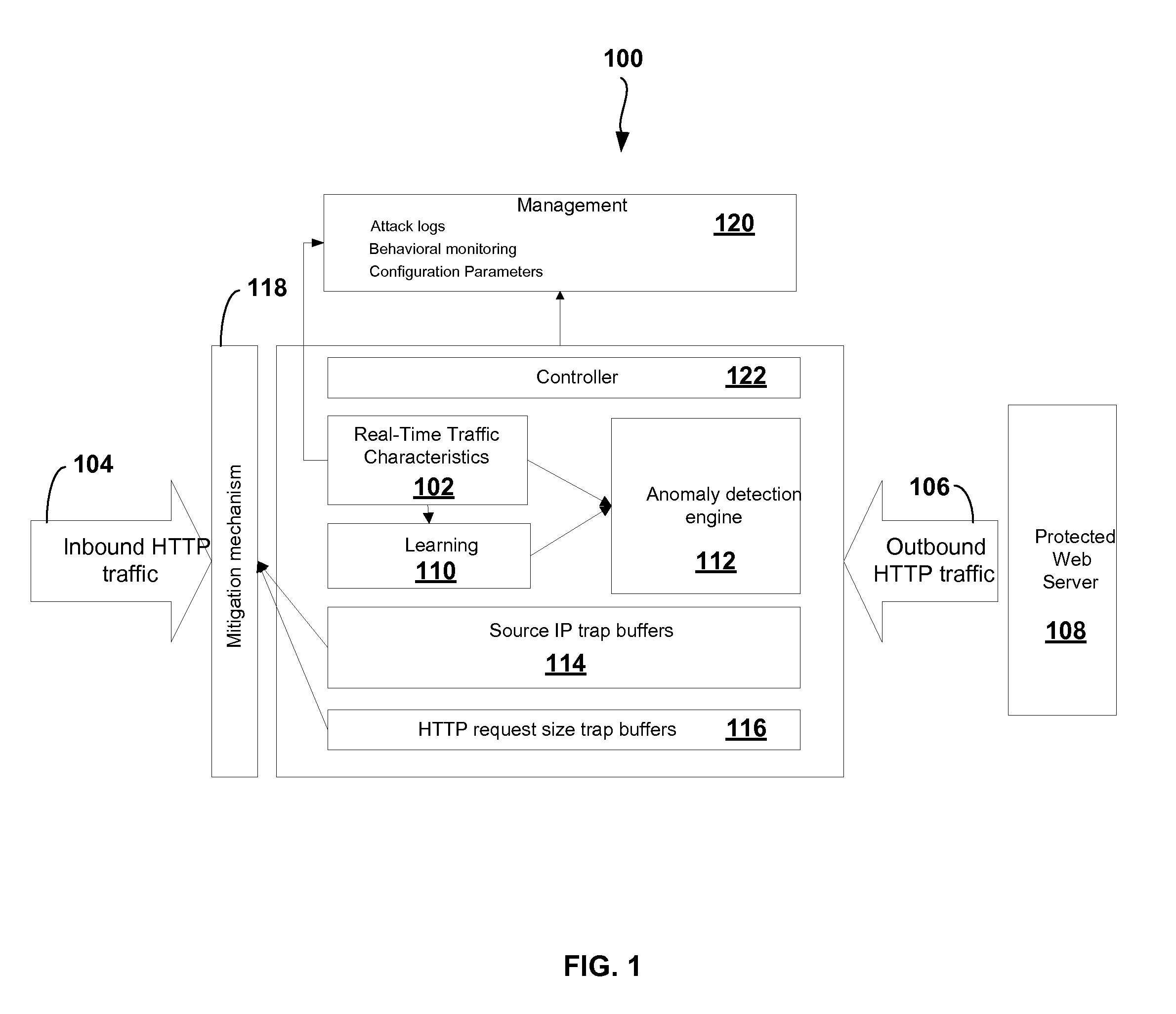
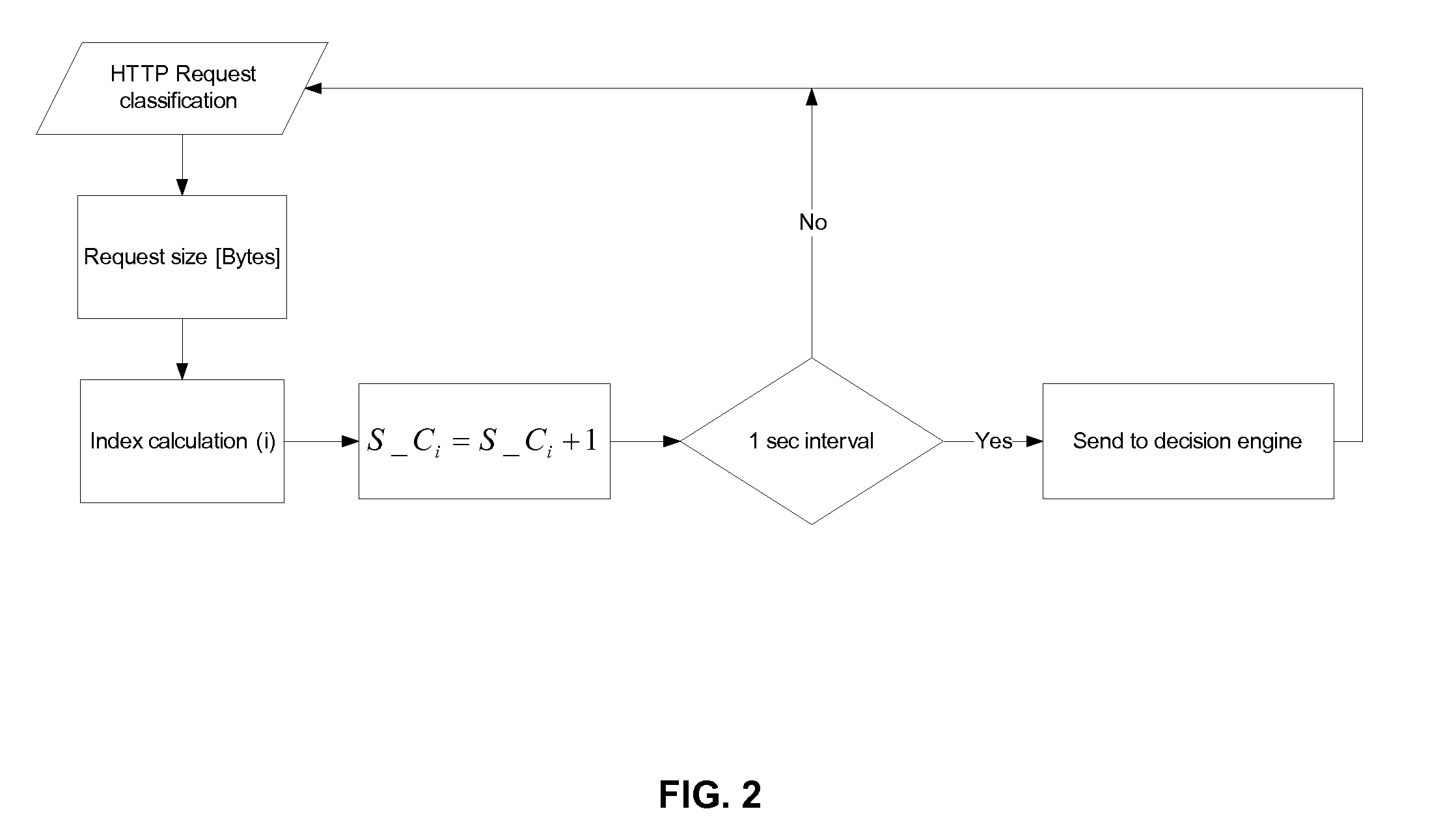
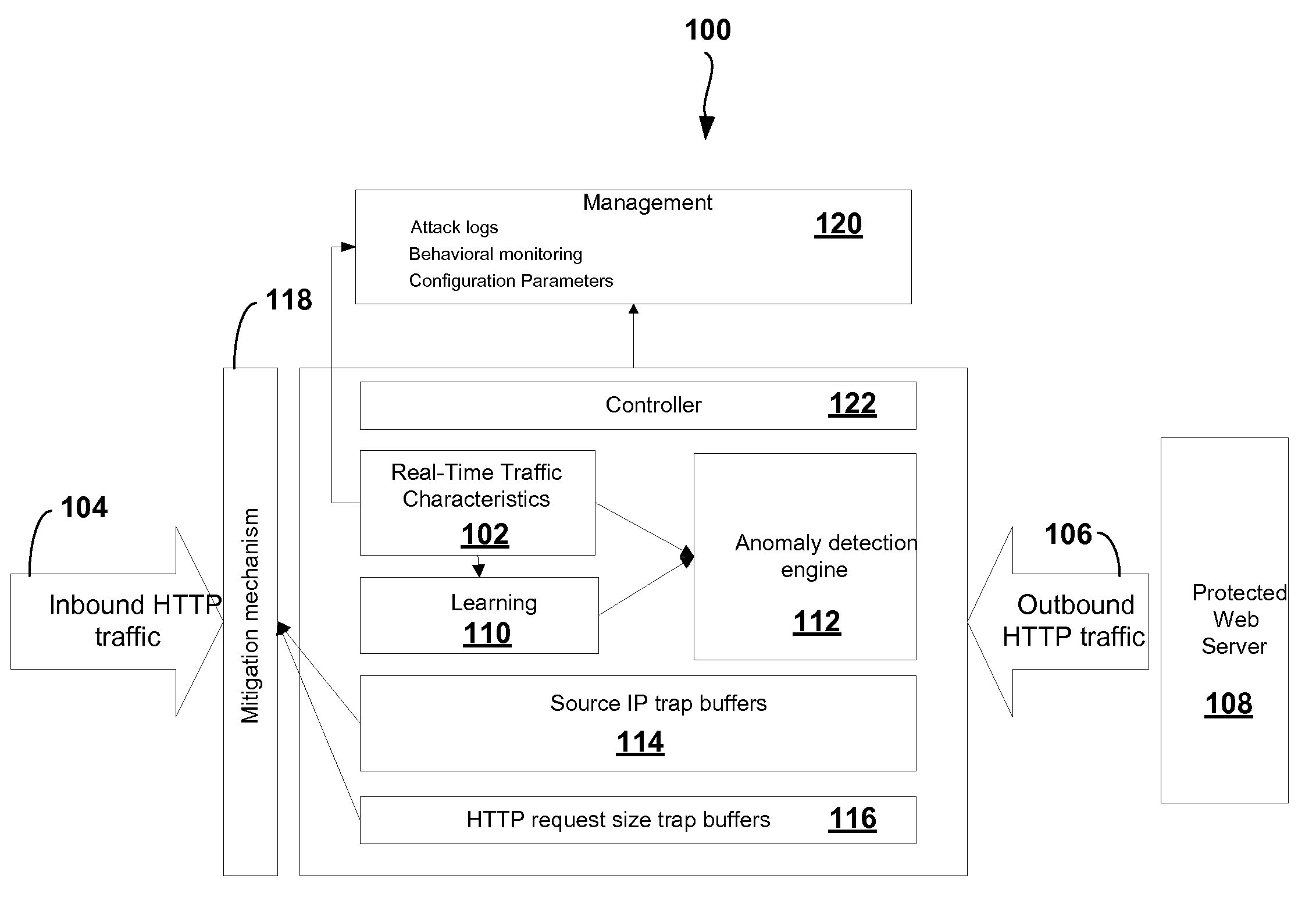
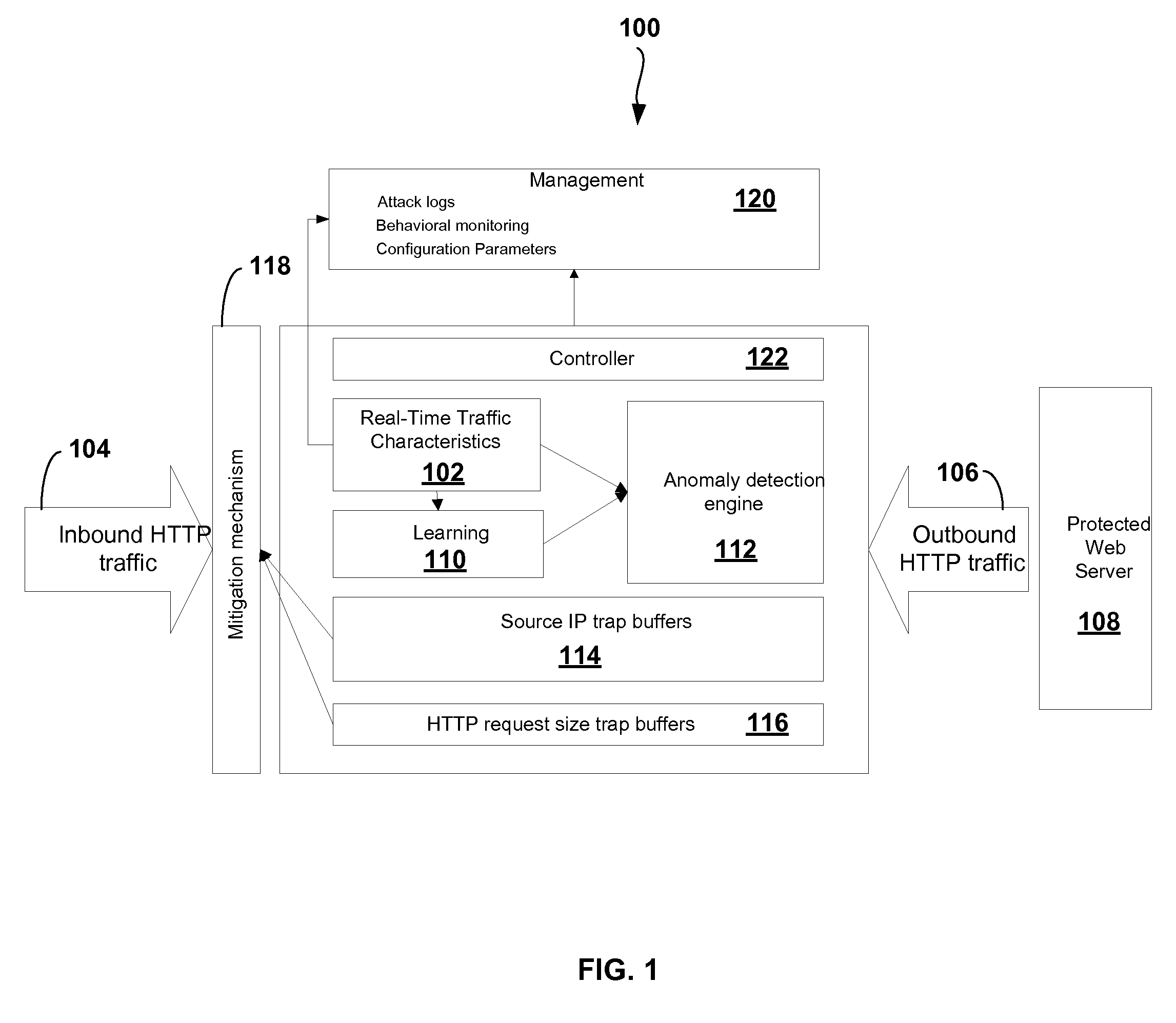
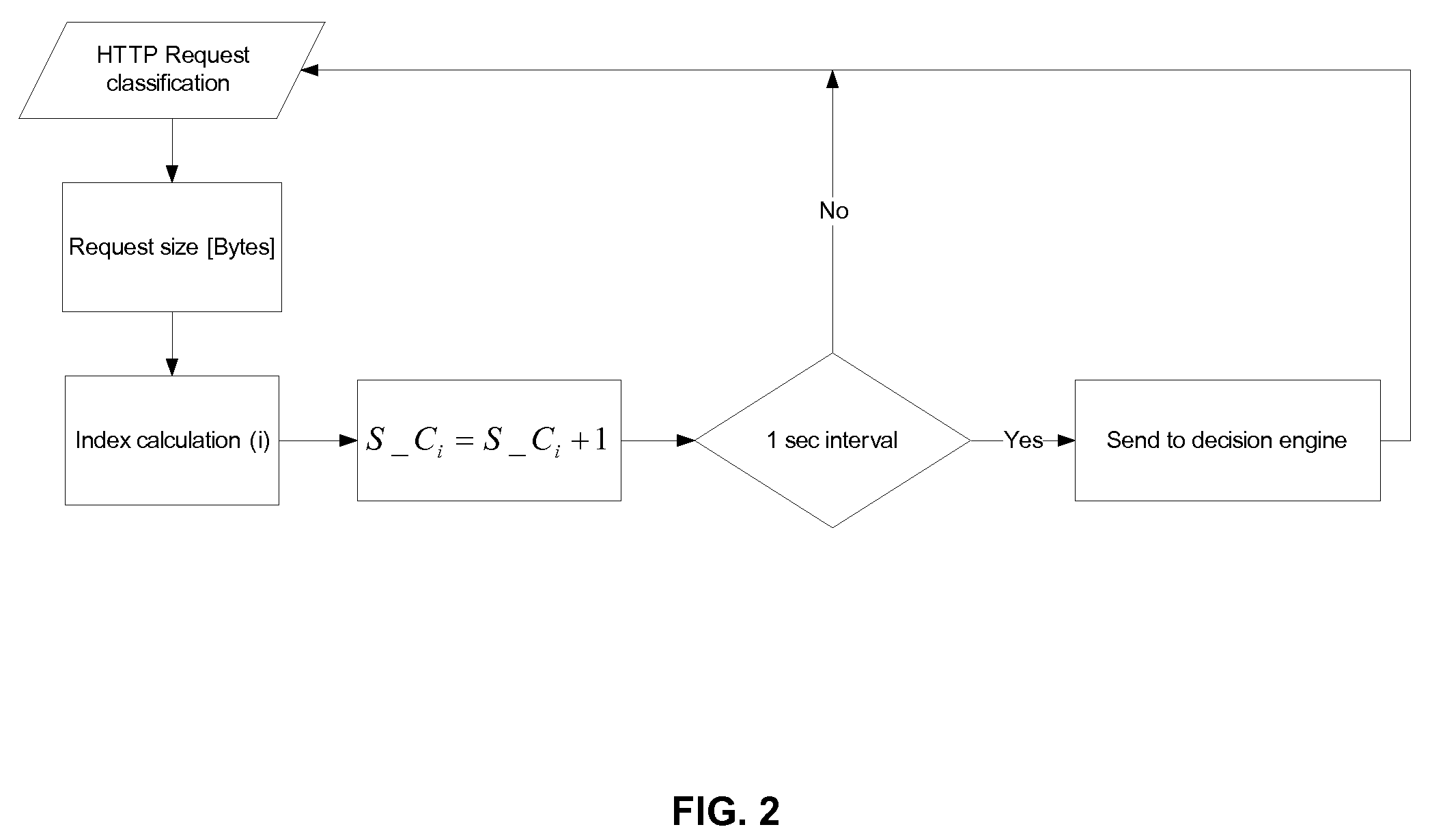
Adaptive Behavioral HTTP Flood Protection
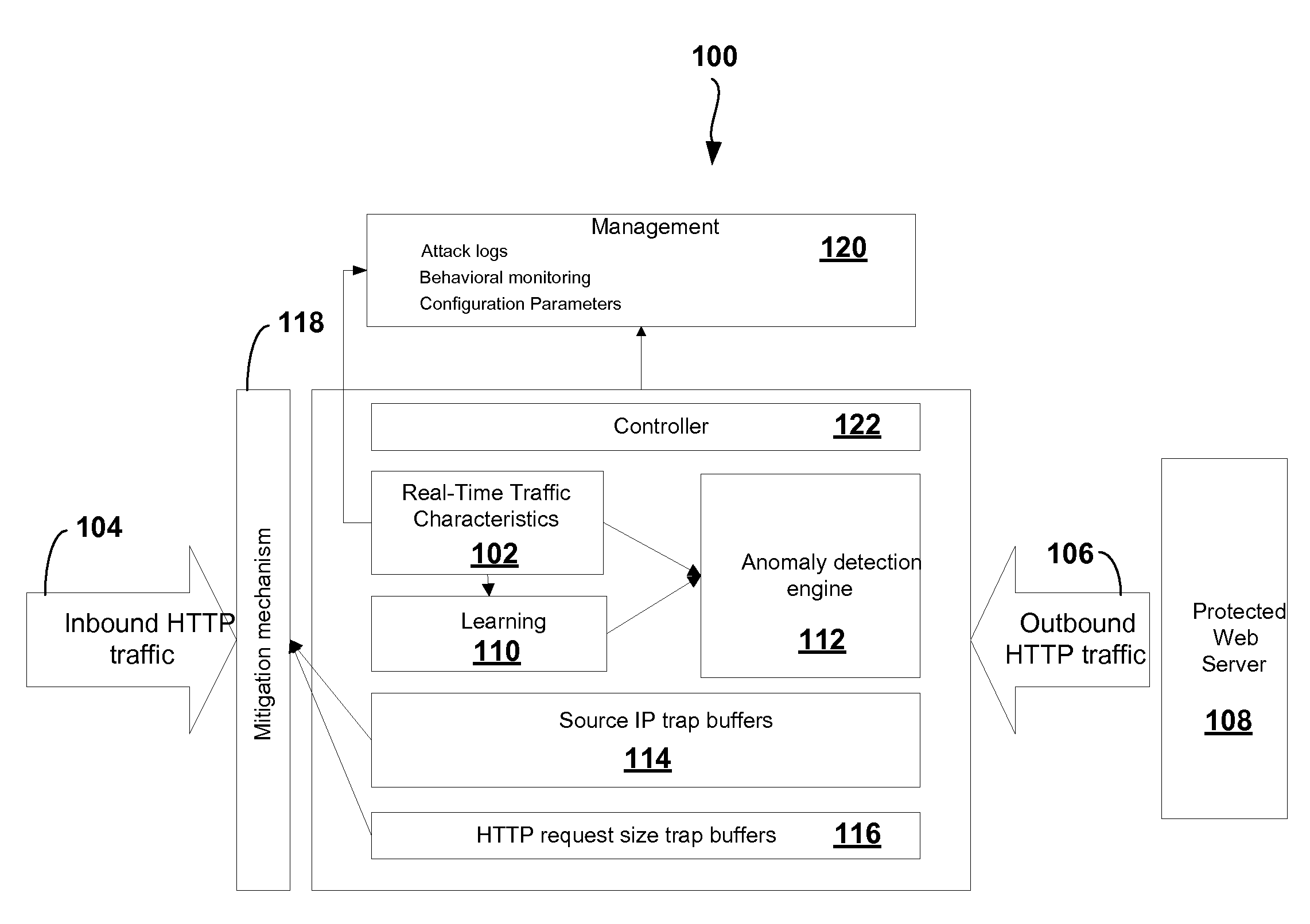
A system and method to detect and mitigate denial of service and distributed denial of service HTTP “page” flood attacks. Detection of attack / anomaly is made according to multiple traffic parameters including rate-based and rate-invariant parameters in both traffic directions. Prevention is done according to HTTP traffic parameters that are analyzed once a traffic anomaly is detected. This protection includes a differential adaptive mechanism that tunes the sensitivity of the anomaly detection engine. The decision engine is based on a combination between fuzzy logic inference systems and statistical thresholds. A “trap buffer” characterizes the attack to allow an accurate mitigation according to the source IP(s) and the HTTP request URL's that are used as part of the attack. Mitigation is controlled through a feedback mechanism that tunes the level of rate limit factors that are needed in order to mitigate the attack effectively while letting legitimate traffic to pass.
Owner:RADWARE
Apparatus, method and computer program product to reduce TCP flooding attacks while conserving wireless network bandwidth
InactiveUS20060230129A1Digital data processing detailsTime-division multiplexData packFlooding attack
Owner:NOKIA CORP
Dynamic DoS flooding protection
Detecting and protecting against denial of service flooding attacks that are initiated against an end system on a computer network. In accordance with one aspect of the invention, a filter is established at a network location. The filter prevents data packets received at a first network location and deemed responsible for the denial of service flooding condition from being forwarded to a subsequent network location. Data packets received at the first network location are then monitored to determine whether the flow of any data packets from a network source exhibit a legitimate behavior, such as where the flow of data packets exhibits a backoff behavior. The filter is then modified to permit data packets that exhibit legitimate behavior to pass through the filter.
Owner:VIRTUAL INSTR CORP
Method and apparatus for deflecting flooding attacks
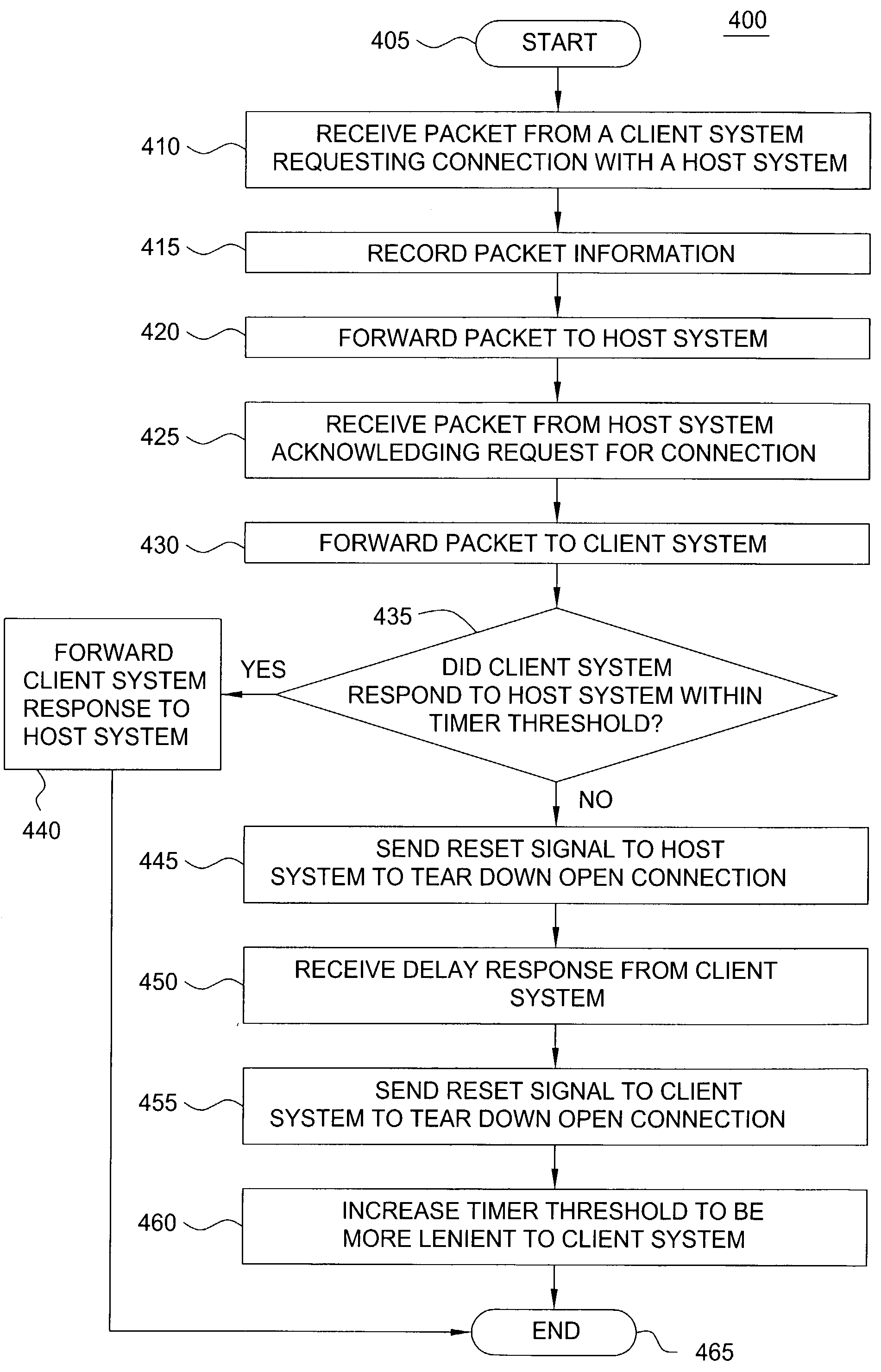
Method and apparatus for deflecting connection flooding attacks. Specifically, the stateful firewall allows all connection attempts to flow into the destination host, but monitors the connection attempts to ensure that only legitimate connections are allowed. If the firewall detects that a connection is half-open for longer than a certain timer threshold, it will instruct the destination host to tear down the half-open connection, thereby freeing up resources in the destination host for other connection attempts. The timer threshold can be dynamically adjusted if a connection flooding attack is detected.
Owner:NVIDIA CORP
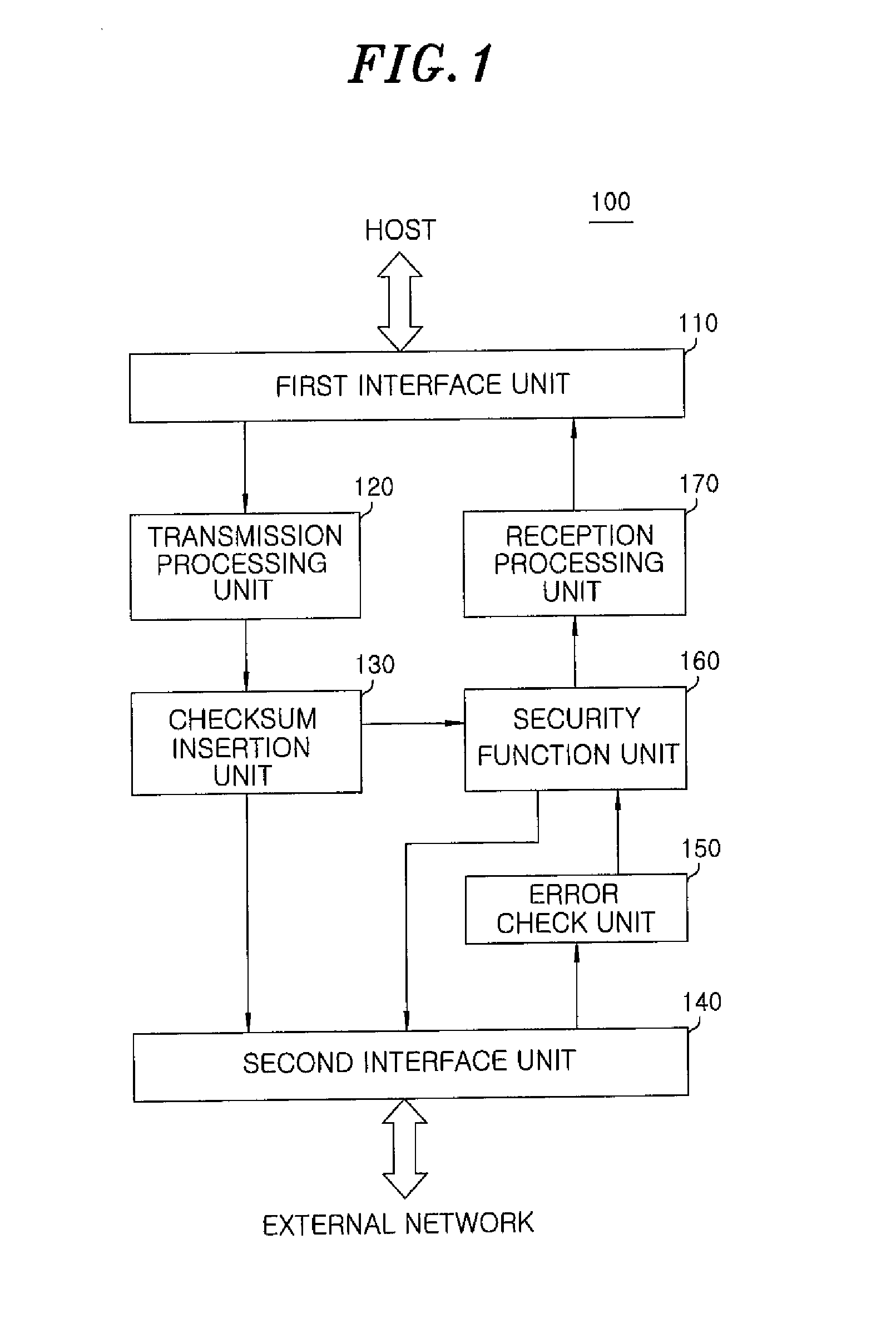
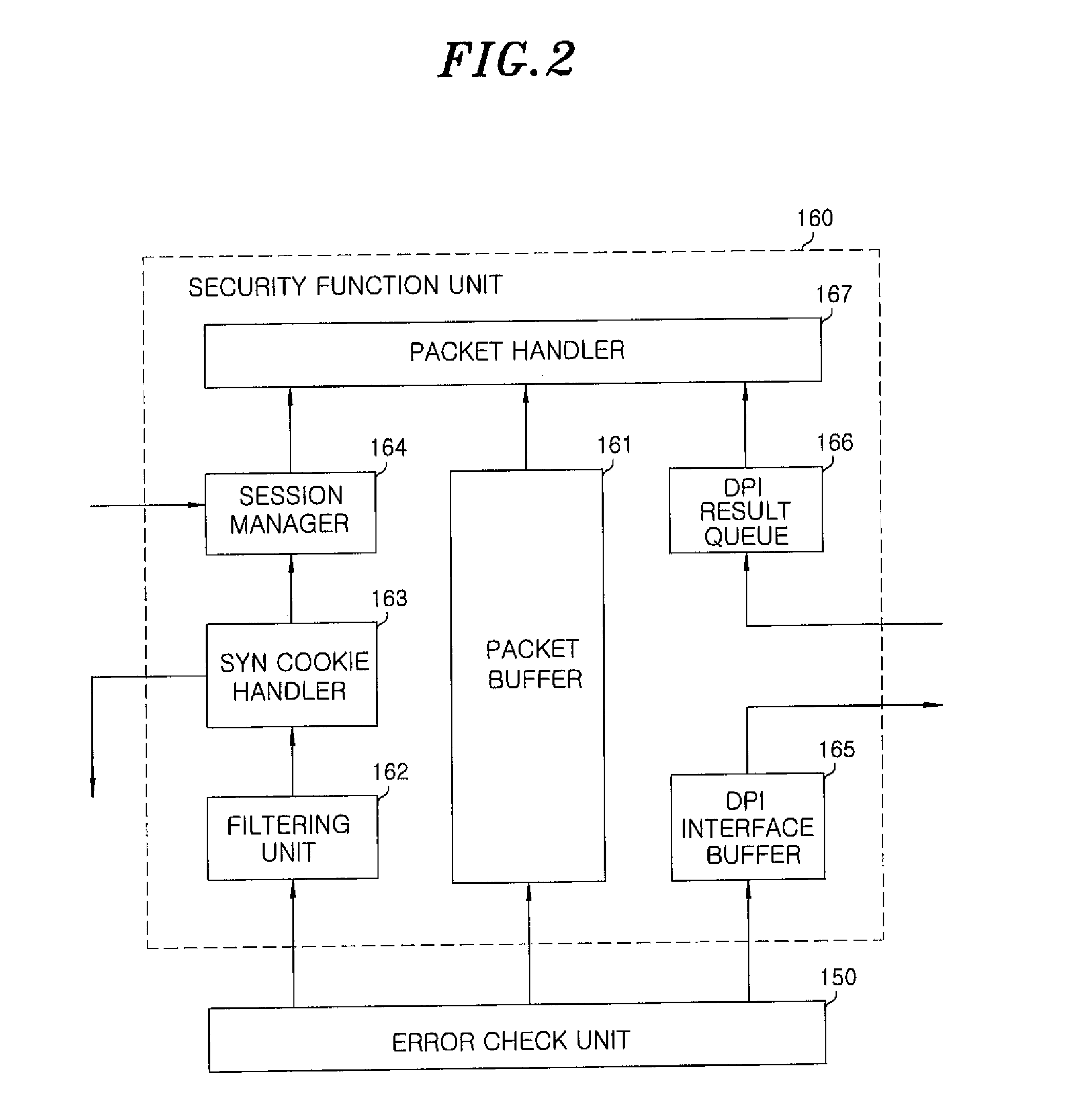
Apparatus and method for preventing network attacks, and packet transmission and reception processing apparatus and method using the same
InactiveUS20110131646A1Prevent cyber attacksData taking preventionMultiple digital computer combinationsSession managementNetwork attack
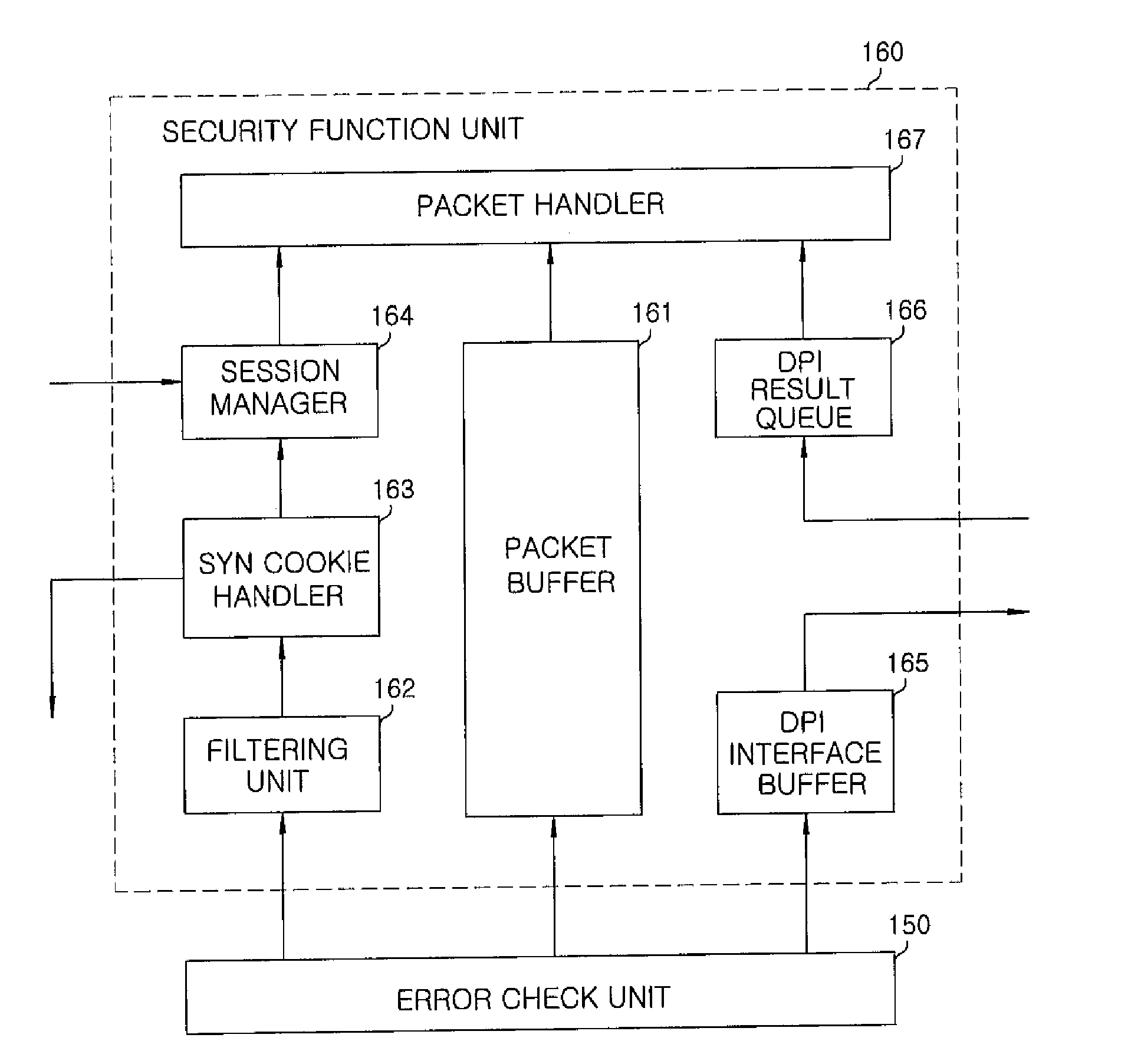
An apparatus for preventing network attacks includes: a packet buffer for storing received packets from a network; a filtering unit for filtering harmful packets based on a result of comparison between information of the received packets and preset filtering information to select a first filtering target packet; an SYN cookie handler for selecting a second filtering target packet using an SYN cookie if it is determined that there is a TCP SYN flooding attack based on the information of the received packets after said filtering; and a session manager for selecting a third filtering target packet through session management if there is a TCP flag flooding attack based on the information of the received packets after said filtering. The apparatus further includes a packet transmission and receipt processing method and apparatus using above.
Owner:ELECTRONICS & TELECOMM RES INST
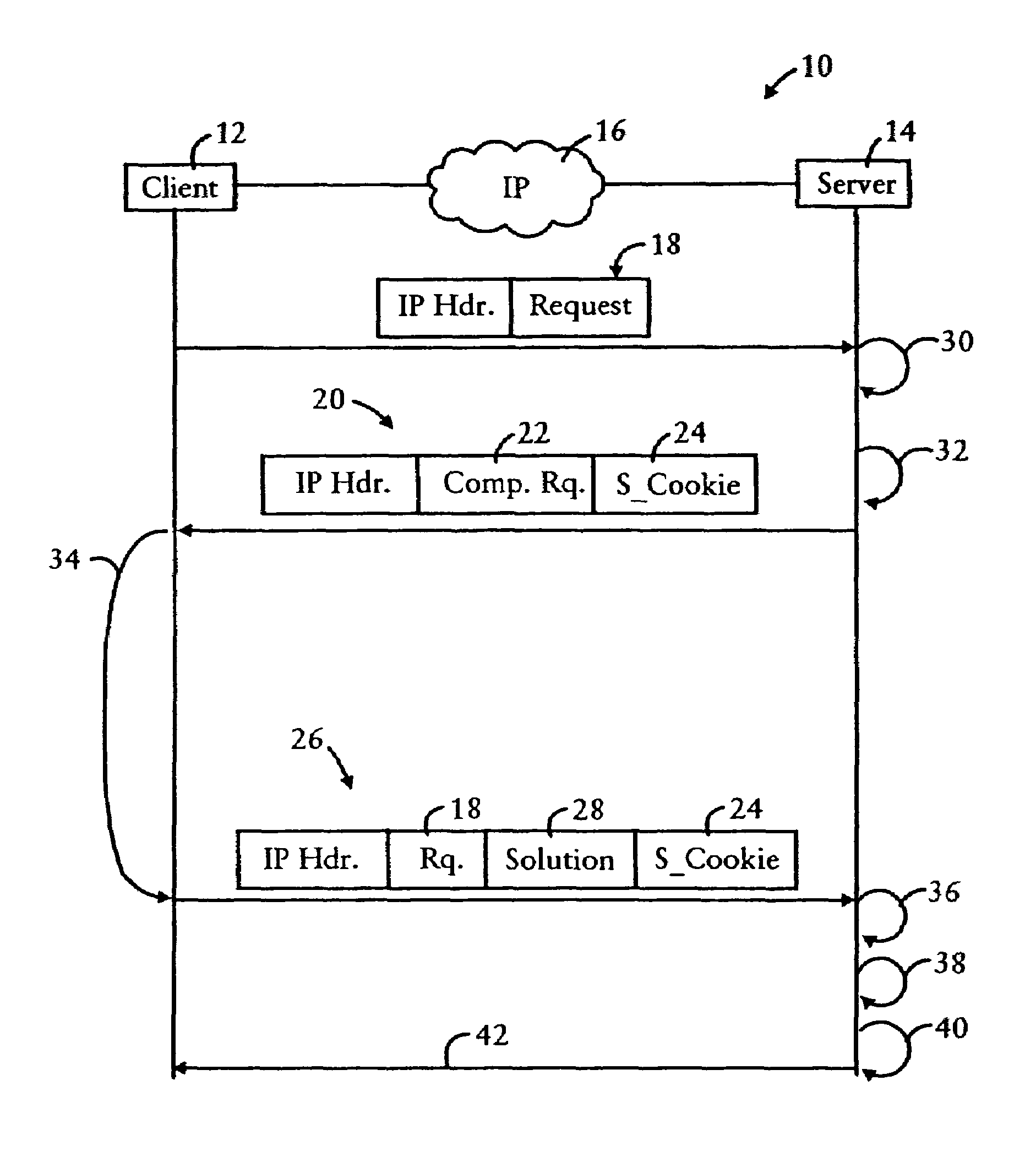
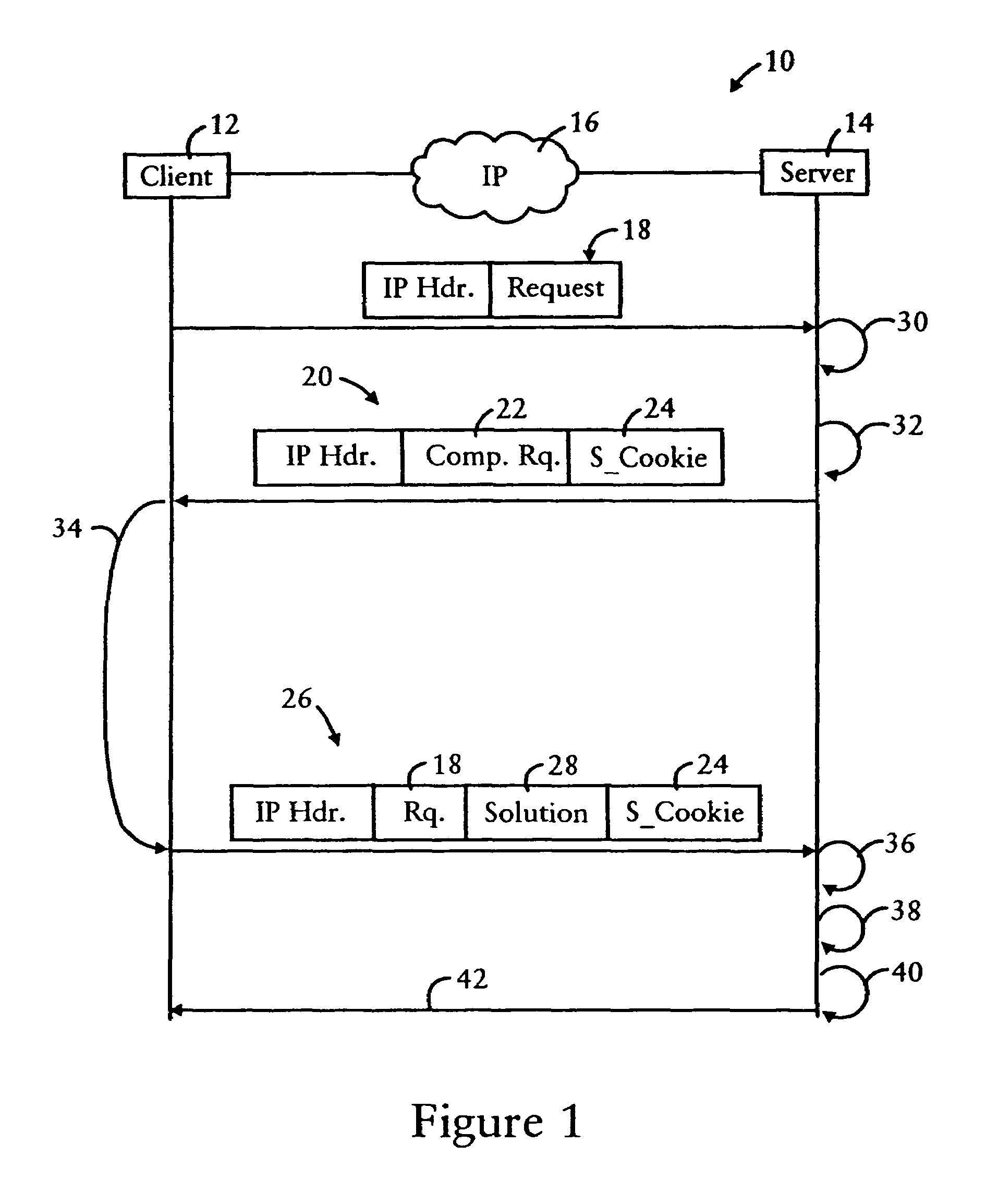
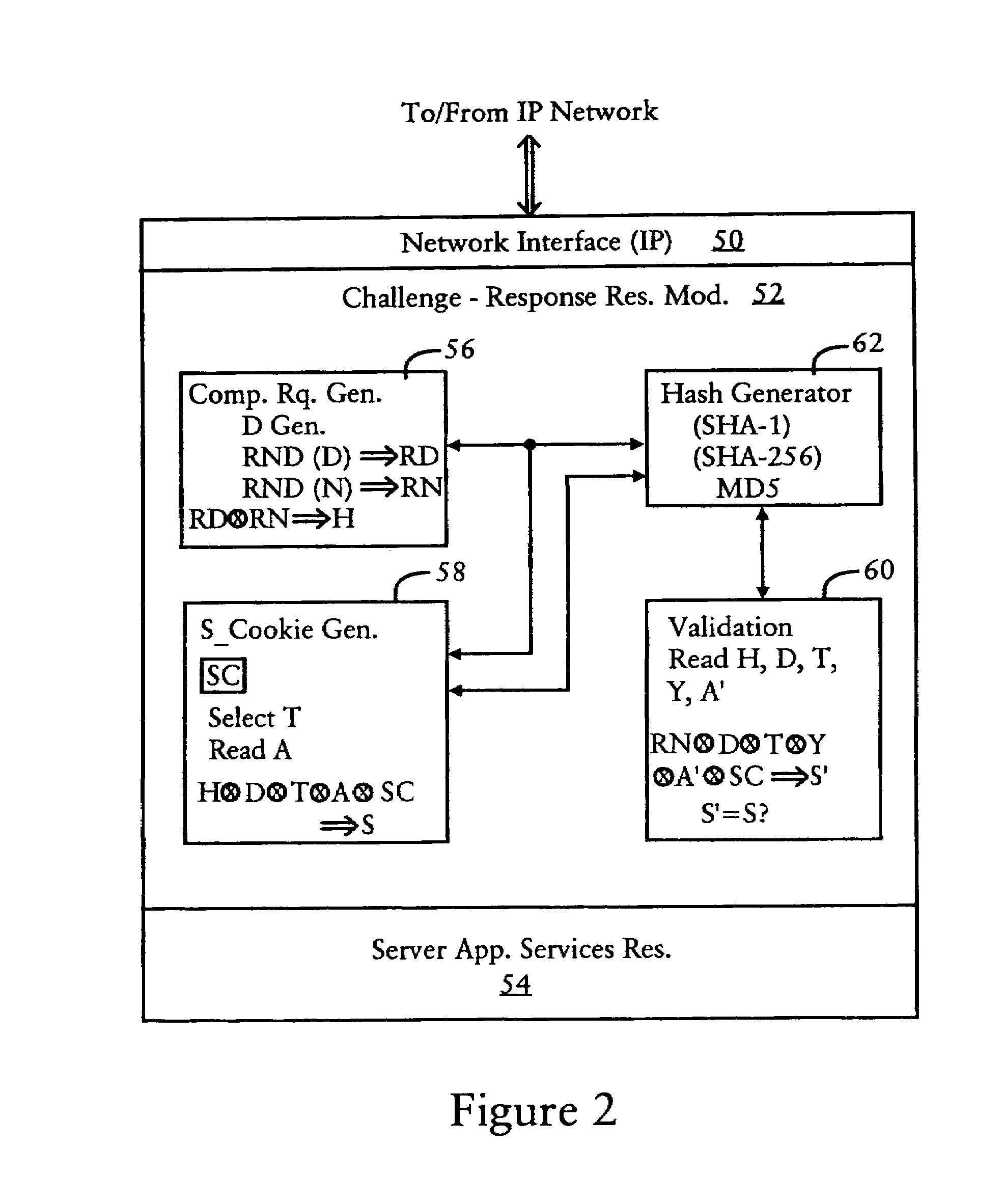
Server preventing attacks by generating a challenge having a computational request and a secure cookie for processing by a client
InactiveUS7694335B1Convenient verificationAvoid attackRandom number generatorsMemory loss protectionNetwork addressingUnique identifier
A server is configured for preventing flood attacks by a client having sent a request, by dynamically generating a challenge to be performed by the client before the server will perform any work for the client. The challenge includes a dynamically generated computational request and a dynamically generated secure cookie. The server generates a first hash result based on hashing a first random number, having a prescribed length, with a second random number having a dynamically selected length. A secure cookie is generated based on hashing the first hash result with a prescribed secure key known only by the server, and a unique identifier for the request such as the client network address with a time stamp. The challenge requires the client to determine the second random number based on the first random number and the hash result. The server validates the challenge results using the secure cookie.
Owner:CISCO TECH INC
Adaptive Behavioral HTTP Flood Protection
A system and method to detect and mitigate denial of service and distributed denial of service HTTP “page” flood attacks. Detection of attack / anomaly is made according to multiple traffic parameters including rate-based and rate-invariant parameters in both traffic directions. Prevention is done according to HTTP traffic parameters that are analyzed once a traffic anomaly is detected. This protection includes a differential adaptive mechanism that tunes the sensitivity of the anomaly detection engine. The decision engine is based on a combination between fuzzy logic inference systems and statistical thresholds. A “trap buffer” characterizes the attack to allow an accurate mitigation according to the source IP(s) and the HTTP request URL's that are used as part of the attack. Mitigation is controlled through a feedback mechanism that tunes the level of rate limit factors that are needed in order to mitigate the attack effectively while letting legitimate traffic to pass.
Owner:RADWARE
Detecting software attacks by monitoring electric power consumption patterns
ActiveUS7877621B2Reduce the valueMemory loss protectionUnauthorized memory use protectionFourier transform on finite groupsFrequency matching
Software attacks such as worms and viruses are detected in an electronic device by monitoring power consumption patterns. In a first embodiment, software attacks are detected by an increase in power consumption. The increased power consumption can be caused by increased network traffic, or by increased activity in the microprocessor. Monitoring power consumption is particularly effective for detecting DOS / flooding attacks when the electronic device is in an idle state. In a second embodiment, a power consumption signal is converted to the frequency domain (e.g., by fast Fourier transform). The highest amplitude frequencies are identified. Specific software attacks produce characteristic frequencies in the power consumption signal. Software attacks are therefore detected by matching the highest amplitude frequencies with frequencies associated with specific worms and viruses. Identification of a particular software attack typically requires matching of 3 or more of the highest amplitude frequencies, and, optionally, amplitude information.
Owner:UNITED STATES OF AMERICA THE AS REPRESENTED BY THE SEC OF THE ARMY +1
Apparatus, method and computer program product to reduce TCP flooding attacks while conserving wireless network bandwidth
InactiveUS7613193B2Digital data processing detailsTime-division multiplexFlooding attackComputer program
Owner:NOKIA CORP
Method for resisting abnegation service aggression
ActiveCN101436958AImprove access speedImprove system efficiencyData switching networksFlooding attackAuthentication
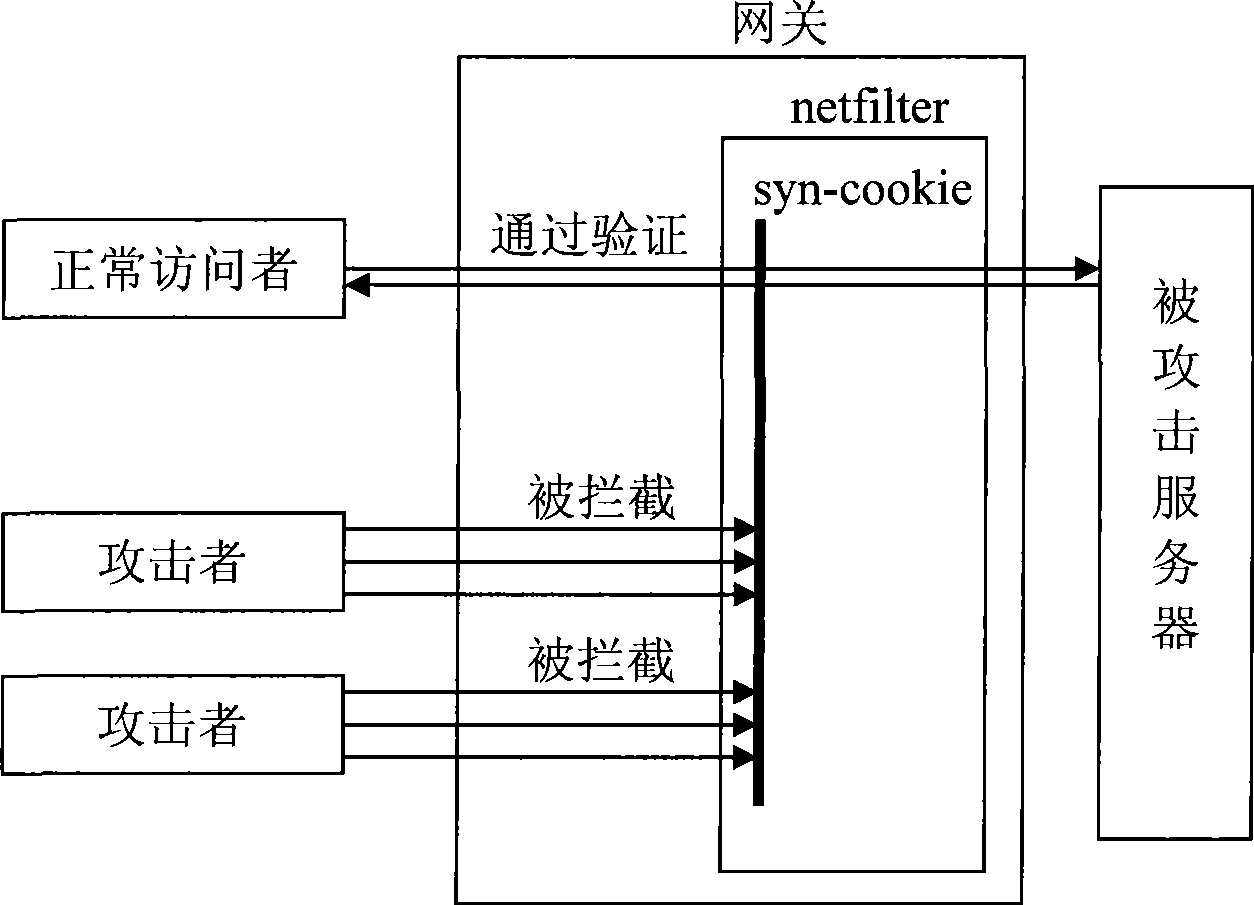
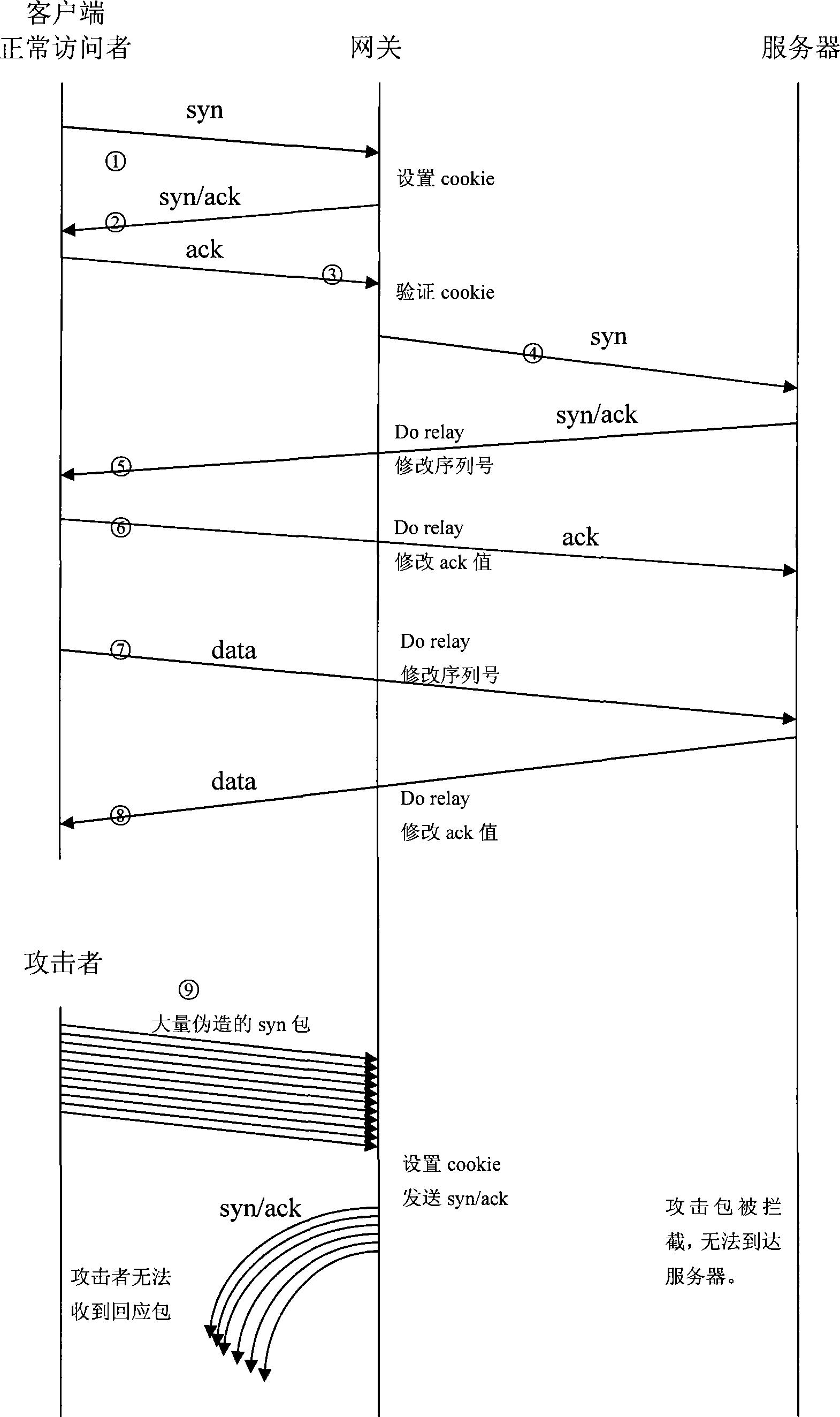
The invention relates to a method for defending a syn flooding attack, which is realized based on netfilter and syn-cookie. In the method, a netfilter is set in a gateway, and the authenticity of a syn packet can be authenticated by syn-cookie mechanism, and a syn request passing the authentication can be released, while the request which does not pass the authentication is intercepted.
Owner:TAIJI COMP
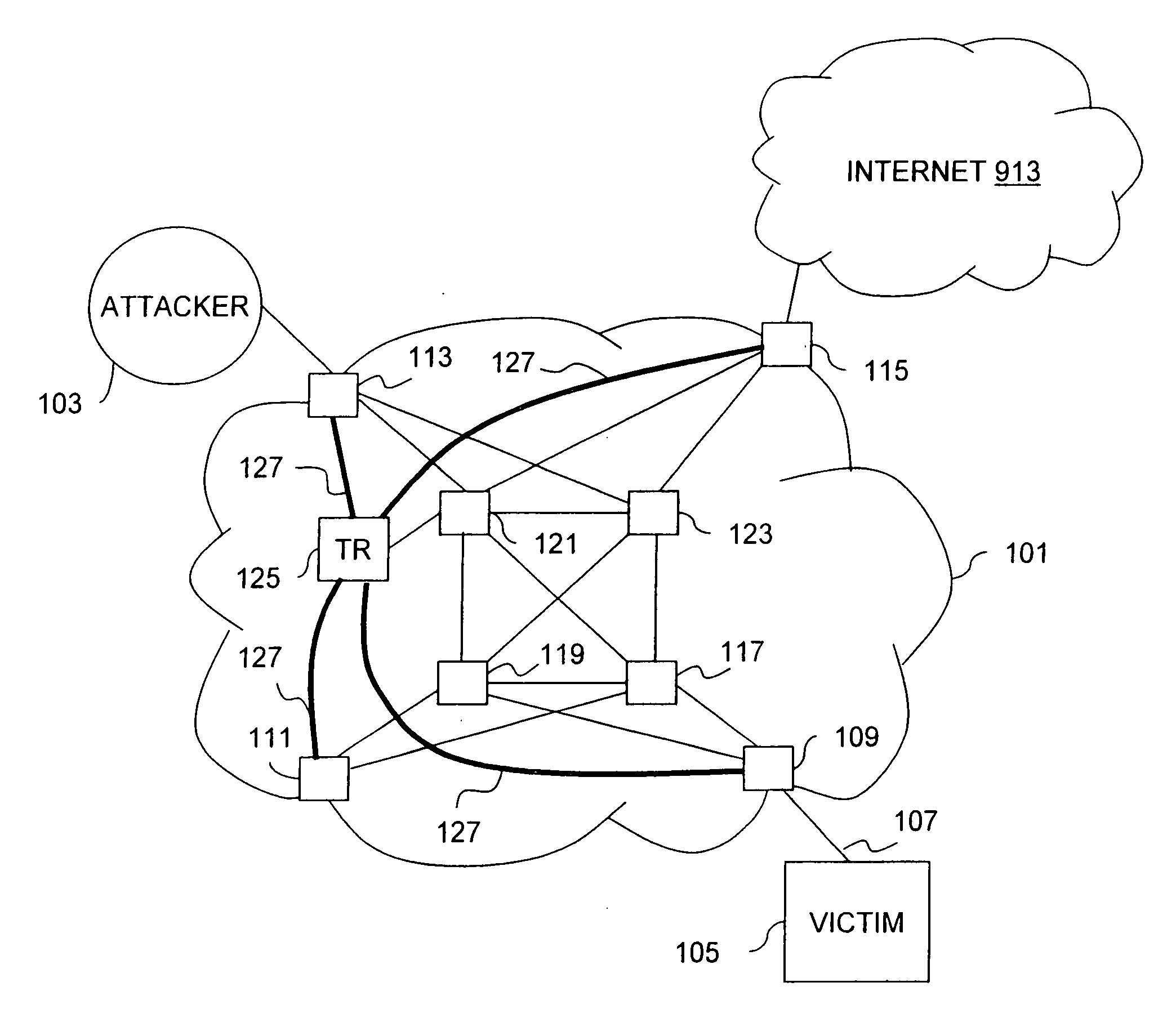
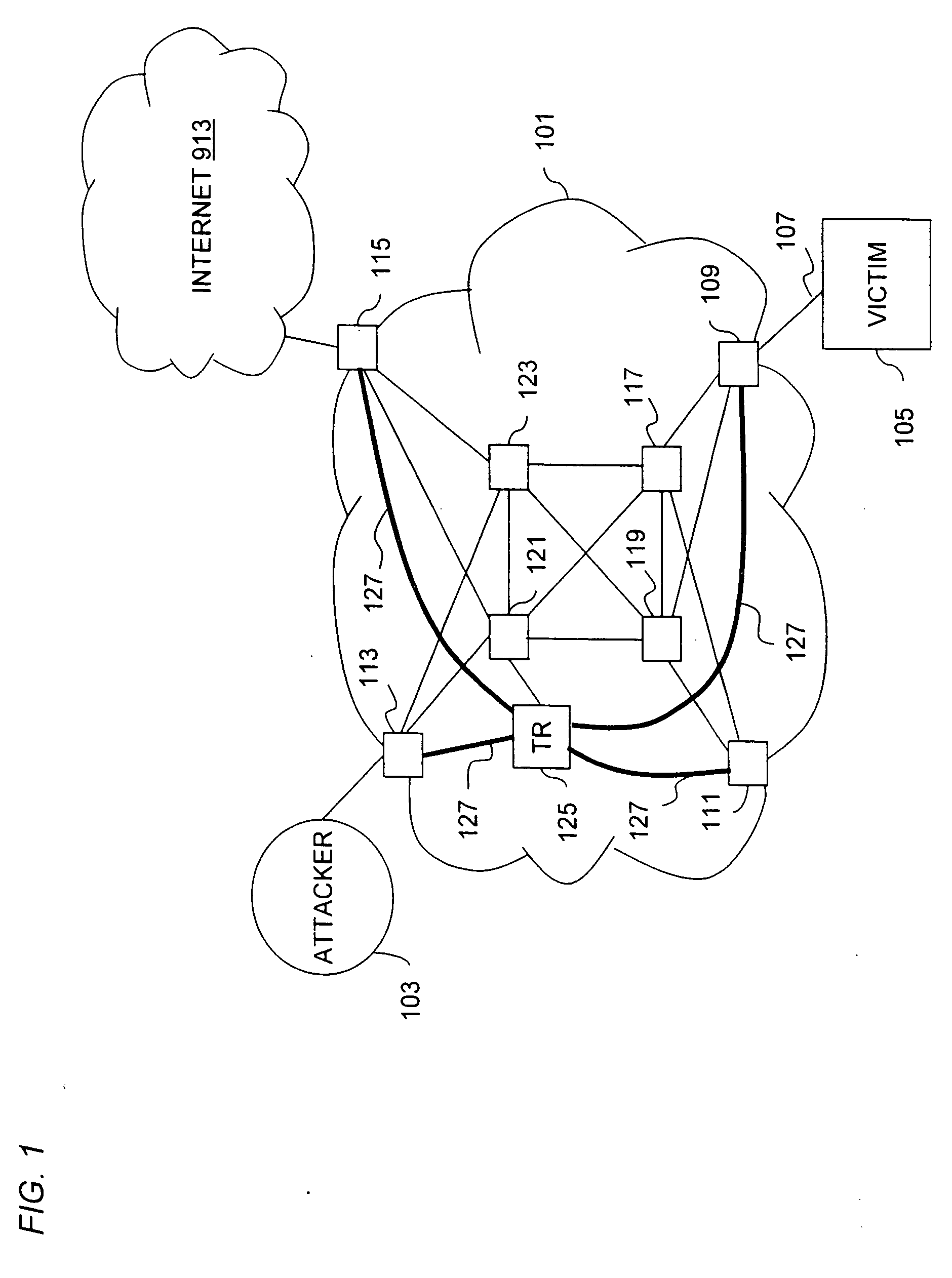
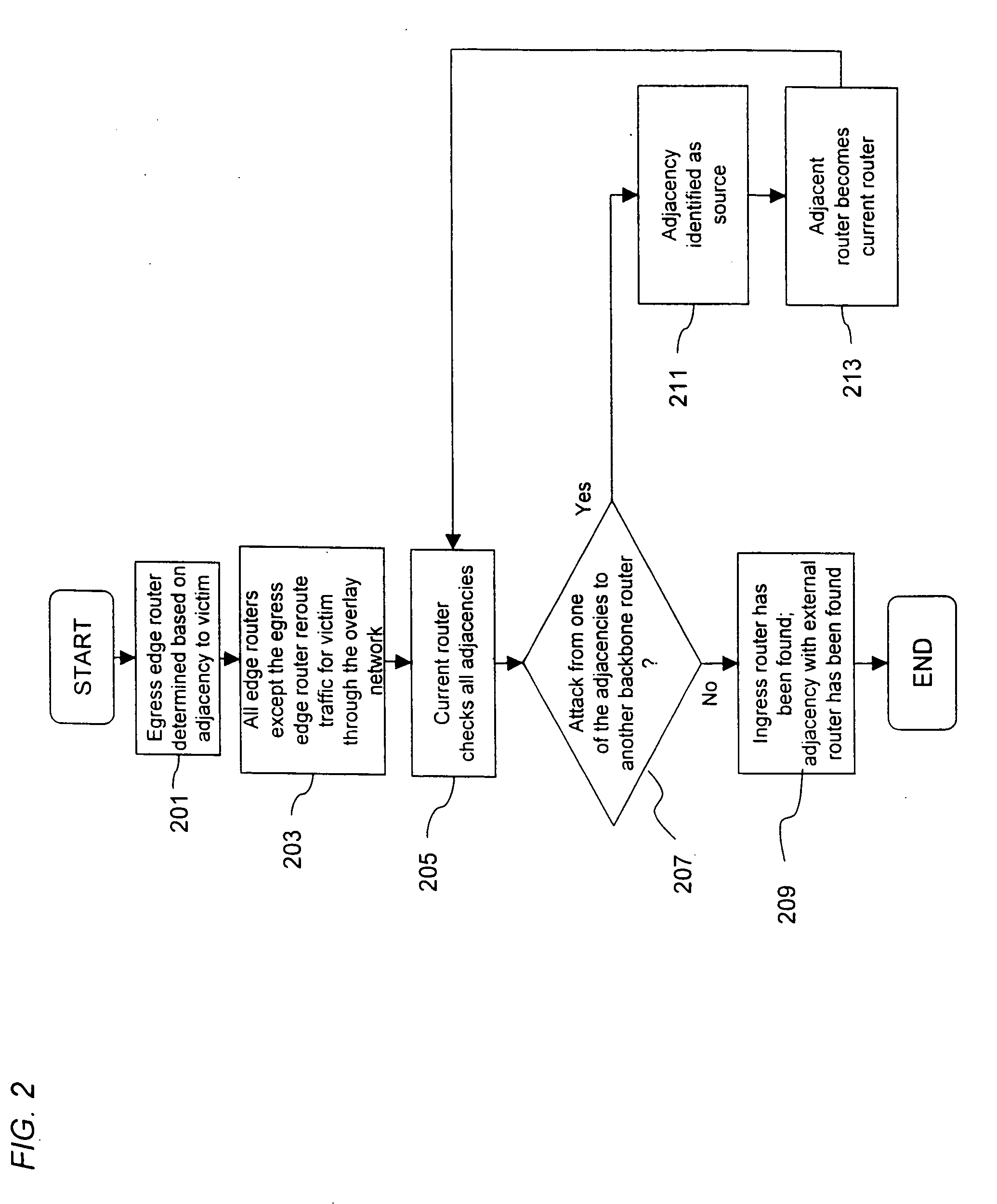
Overlay network for tracking denial-of-service floods in unreliable datagram delivery networks
ActiveUS20060156402A1Low costDeployment to minimizedMemory loss protectionUser identity/authority verificationService provisionIP tunnel
An approach for tracking denial-of-service (DoS) flood attacks using an overlay IP (Internet Protocol) network is disclosed. One or more tracking routers form an overlay tracking network over the network of an Internet Service Provider (ISP). The ISP network includes numerous transit routers and edge routers. The tracking routers communicate directly with all the edge routers using IP tunnels. The edge routers within the ISP network perform security diagnostic functions, in part, to identify a DoS flood attack that has been launched by one or more attackers. To track down an attacker, an egress edge router identifies the DoS flood attack datagrams, rerouting these datagrams to the overlay tracking network. The tracking routers perform hop-by-hop input debugging to identify the ingress edge router associated with the source of the DoS flood attack.
Owner:PALO ALTO NETWORKS INC
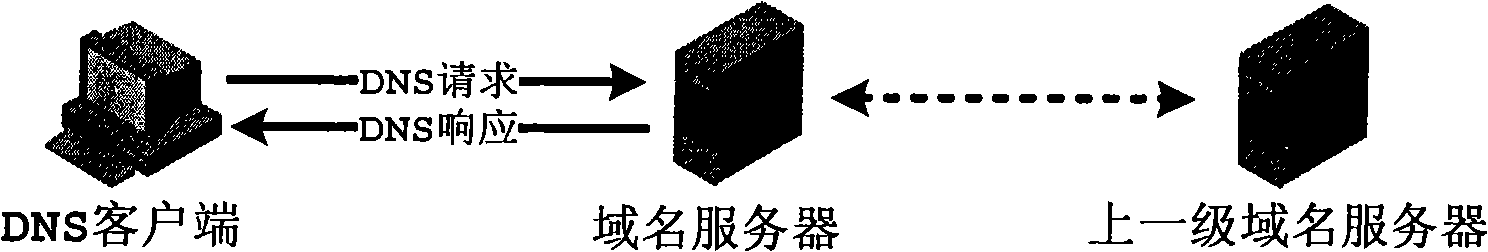
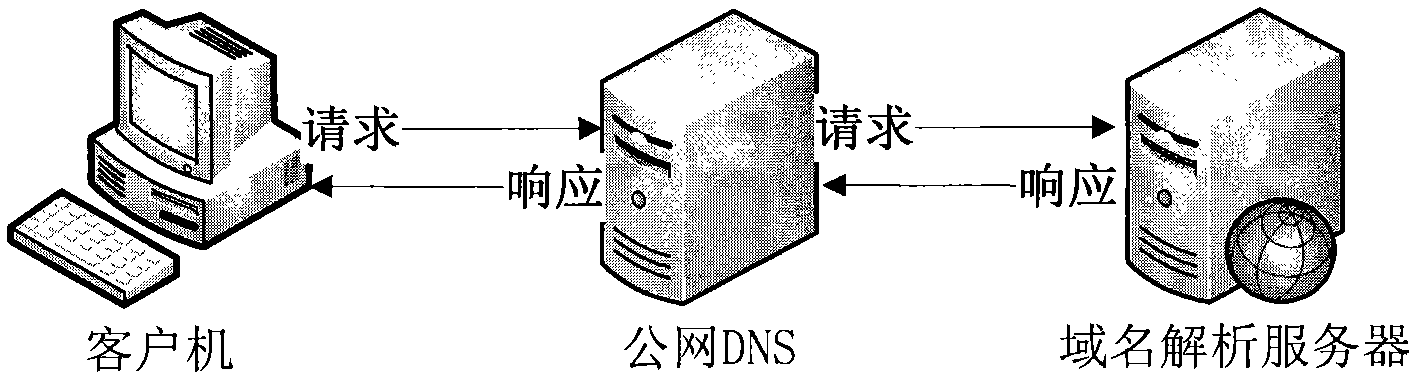
Method and apparatus for preventing DNS request message from flooding attack
InactiveCN101282209AIdentify legalityAttack reduction or avoidanceSecuring communicationClient-sideFlooding attack
The present invention provides a method for avoiding the DNS query message flood attack and a device thereof. The method comprises the following steps: receiving a DNS query message borne by UDP transmitted from a DNS client by a DNS server; transmitting a DNS response message by the DNS server to the DNS client, and marking the TC and AA in the DNS response message to a position 1; and when the DNS server receives the TCP SYN message transmitted by the DNS client in a prearranged time, detecting the validity of the DNS client through a TCP cookie mode. According to the invention, the flood attack of the DNS query message borne by the UDP can be effectively avoided.
Owner:NEW H3C TECH CO LTD
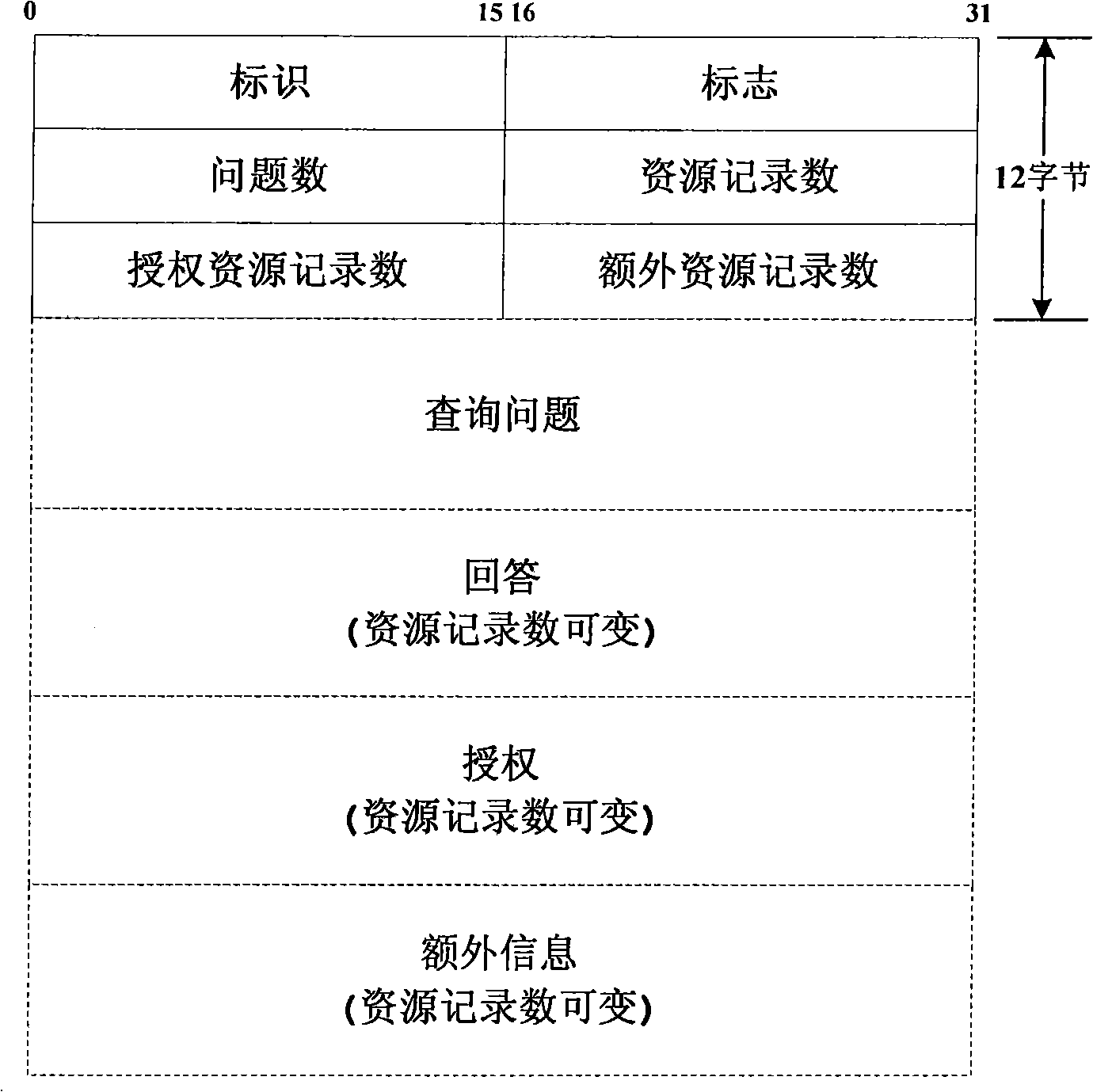
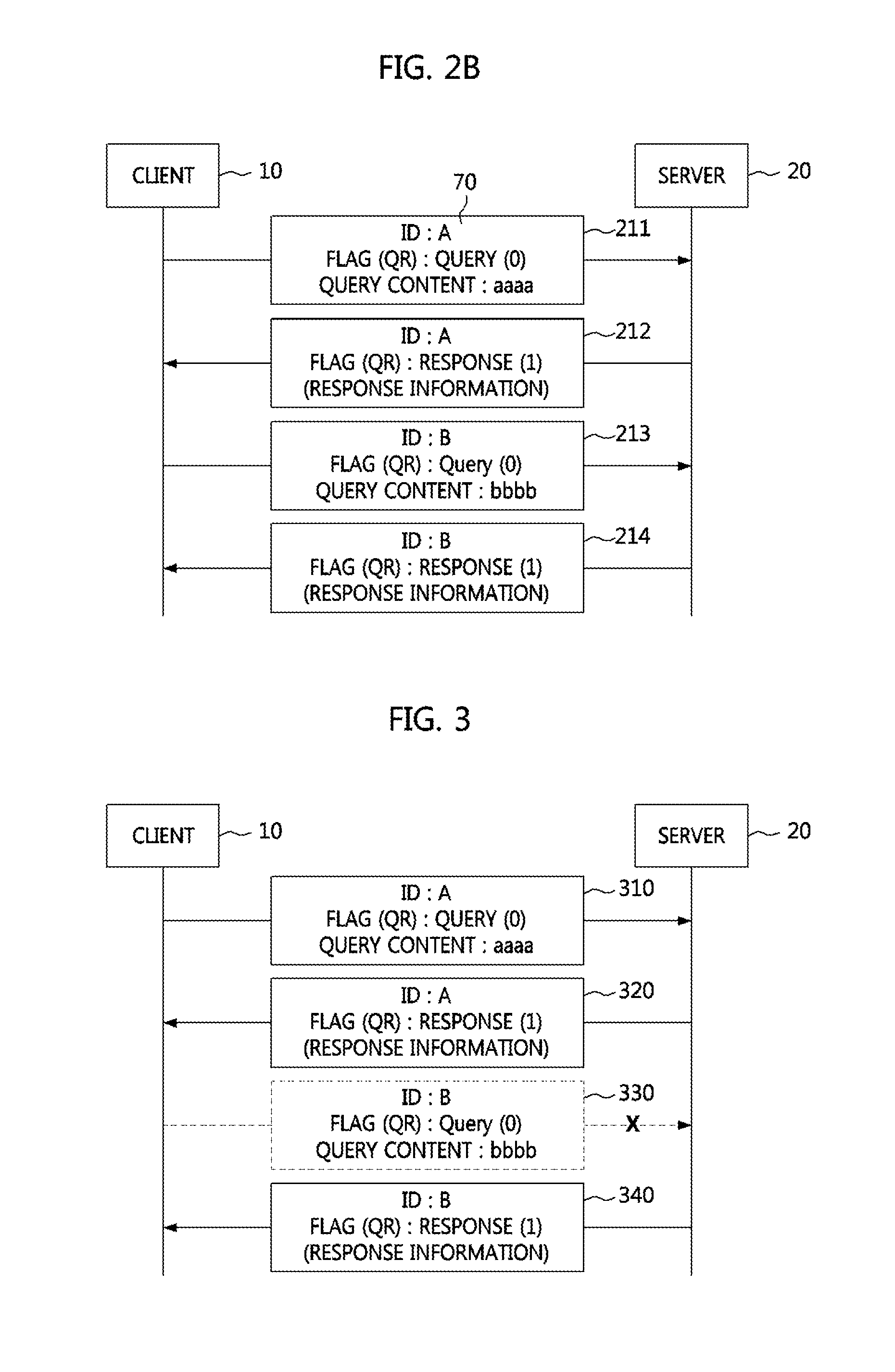
Methods of detecting DNS flooding attack according to characteristics of type of attack traffic
Disclosed are methods of detecting a domain name server (DNS) flooding attack according to characteristics of a type of attack traffic. A method of detecting an attack by checking a DNS packet transmitted over a network in a computer device connected to the network, includes determining whether the number of DNS packets previously generated within a threshold time with the same type of message, the same specific address and the same field value as in the transmitted packet is greater than or equal to a given number, and determining the transmitted DNS packet as a packet related to the attack if the number of DNS packets previously generated within the threshold time is greater than or equal to the given number.
Owner:ELECTRONICS & TELECOMM RES INST
Method and apparatus for monitoring and processing DNS query traffic
A method for monitoring and processing domain name system (DNS) query traffic includes: monitoring DNS query traffic in each time slot during a monitoring period comprised of n number of time slots; extracting traffic information during the monitoring period by using the DNS query traffic monitored in said each time slot; and analyzing the extracted traffic information to detect a DNS traffic flooding attack.
Owner:ELECTRONICS & TELECOMM RES INST
SYN flooding attack defence method based on connection request authentication
InactiveCN1630248AEfficient detectionEffective defenseData switching networksSecuring communicationClient-sideServer-side
A connection request verification based method for defending SYN-flooding attack contains sending SYNY to user end package as server end receiving user end SYNY package, when server end receiving SYNX / ACKY+1 package from user end, obtaining certification identification information from affirmation sequence number of said package to verifying, when it is effective TCP connection request, obtaining connection state information and setting TCP connection, sending back ACKX+1 package to user end, as user receiving said package the TCP connection is completed, when it is effective TCP connection request, the SYNX / ACKY+1 is dropped, which effectively defends the SYN-flooding attack using a lot of ineffective TCP connection request of pretended source address to use up system resource.
Owner:BEIHANG UNIV
Transmission control protocol flooding attack prevention method and apparatus
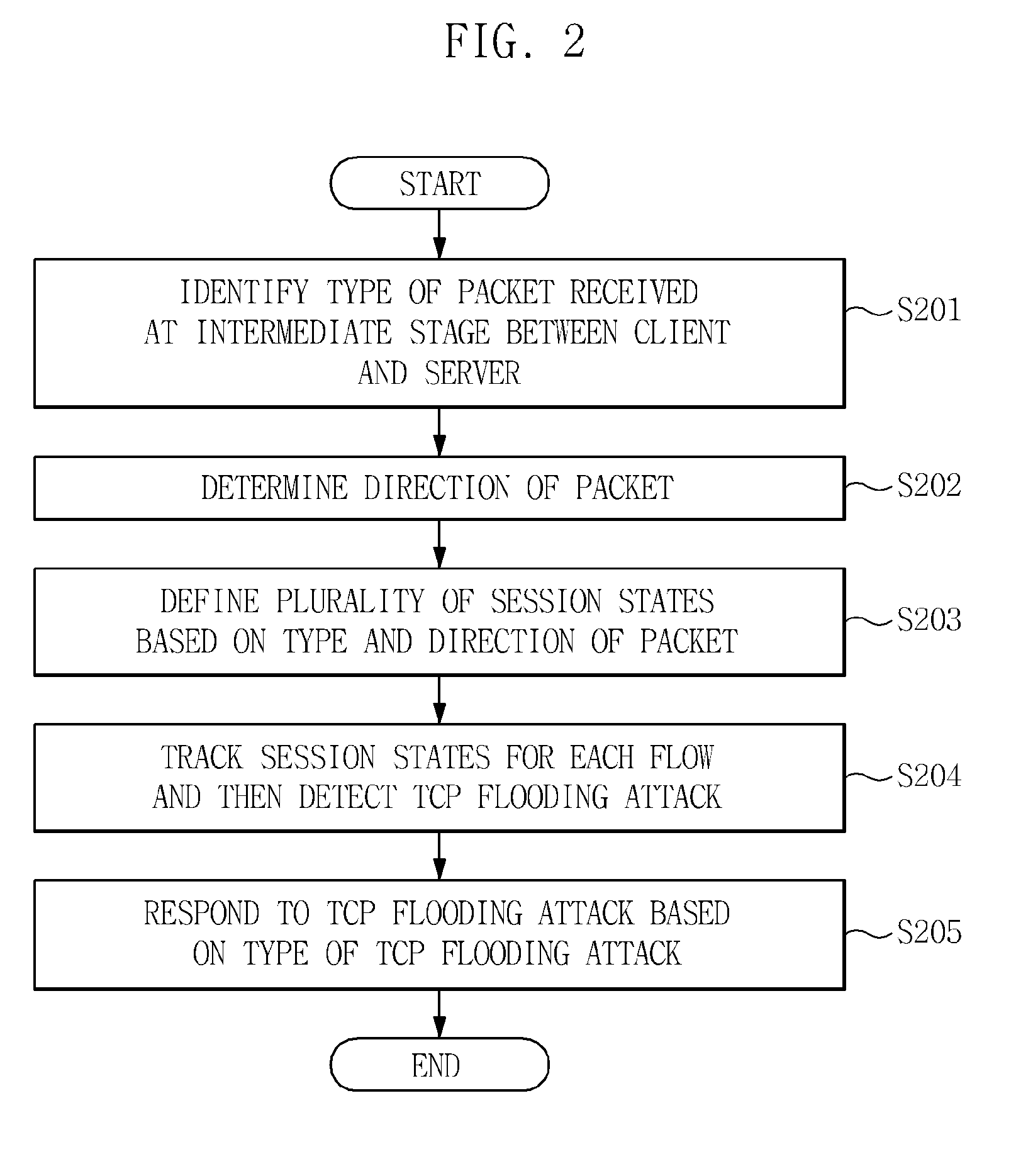
ActiveUS20120117646A1Rapidly and accurately detectingRapidly and accurately and preventingMemory loss protectionUnauthorized memory use protectionIntermediate stageClient-side
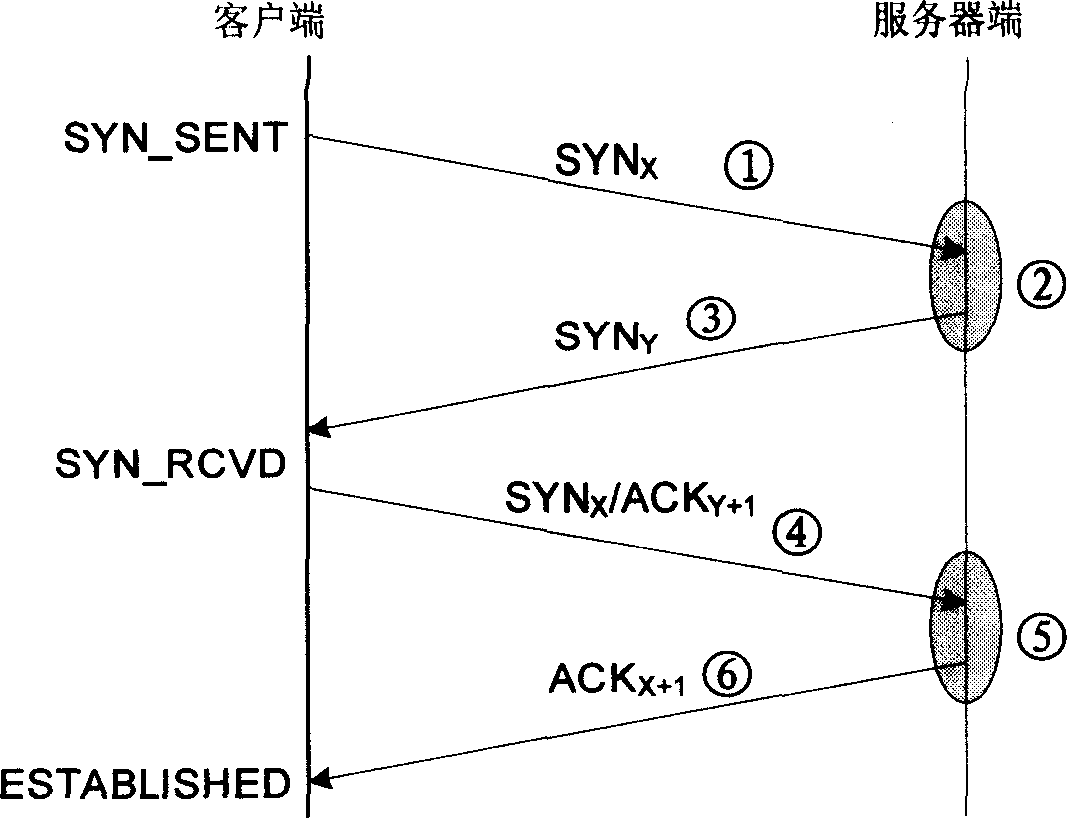
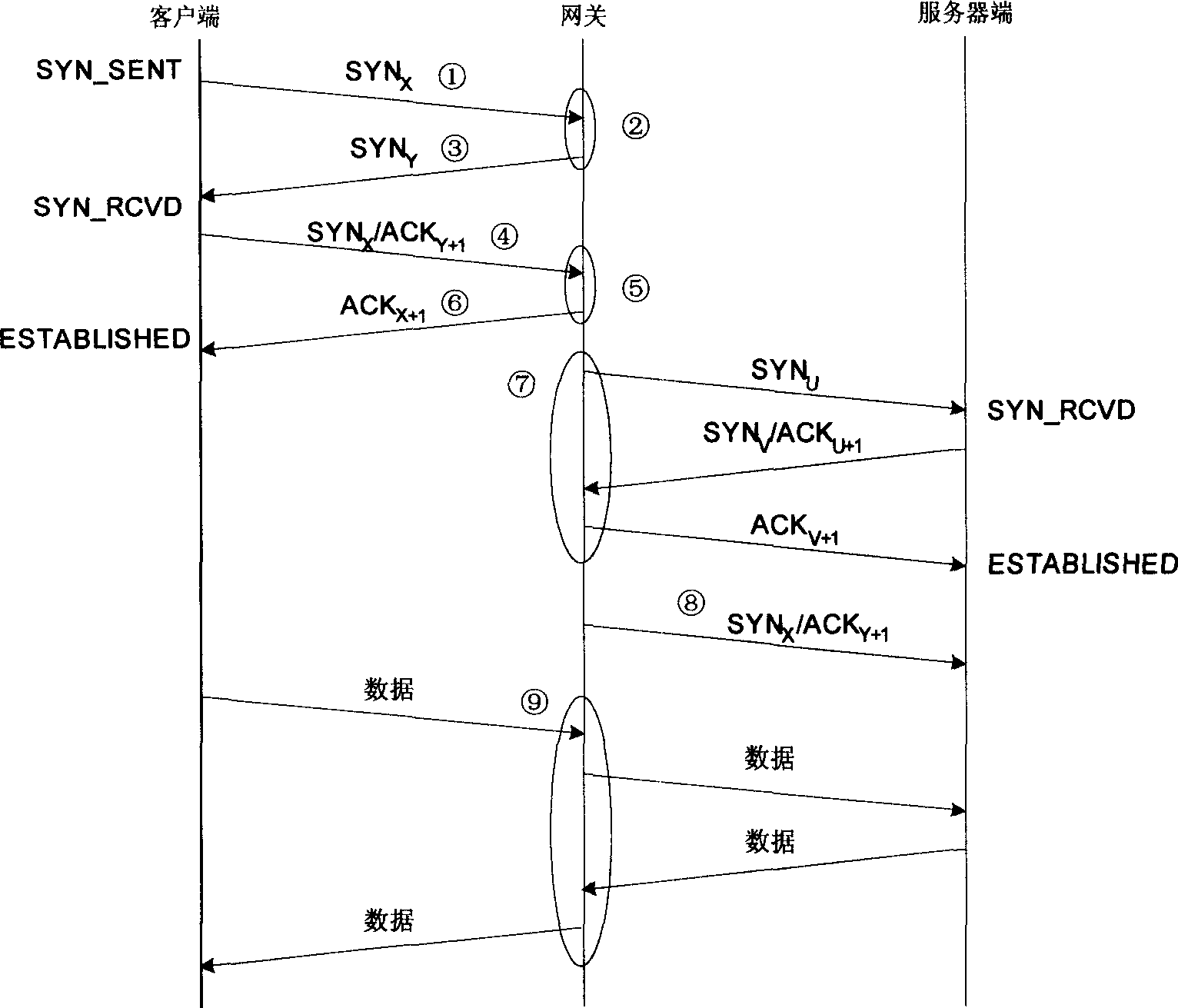
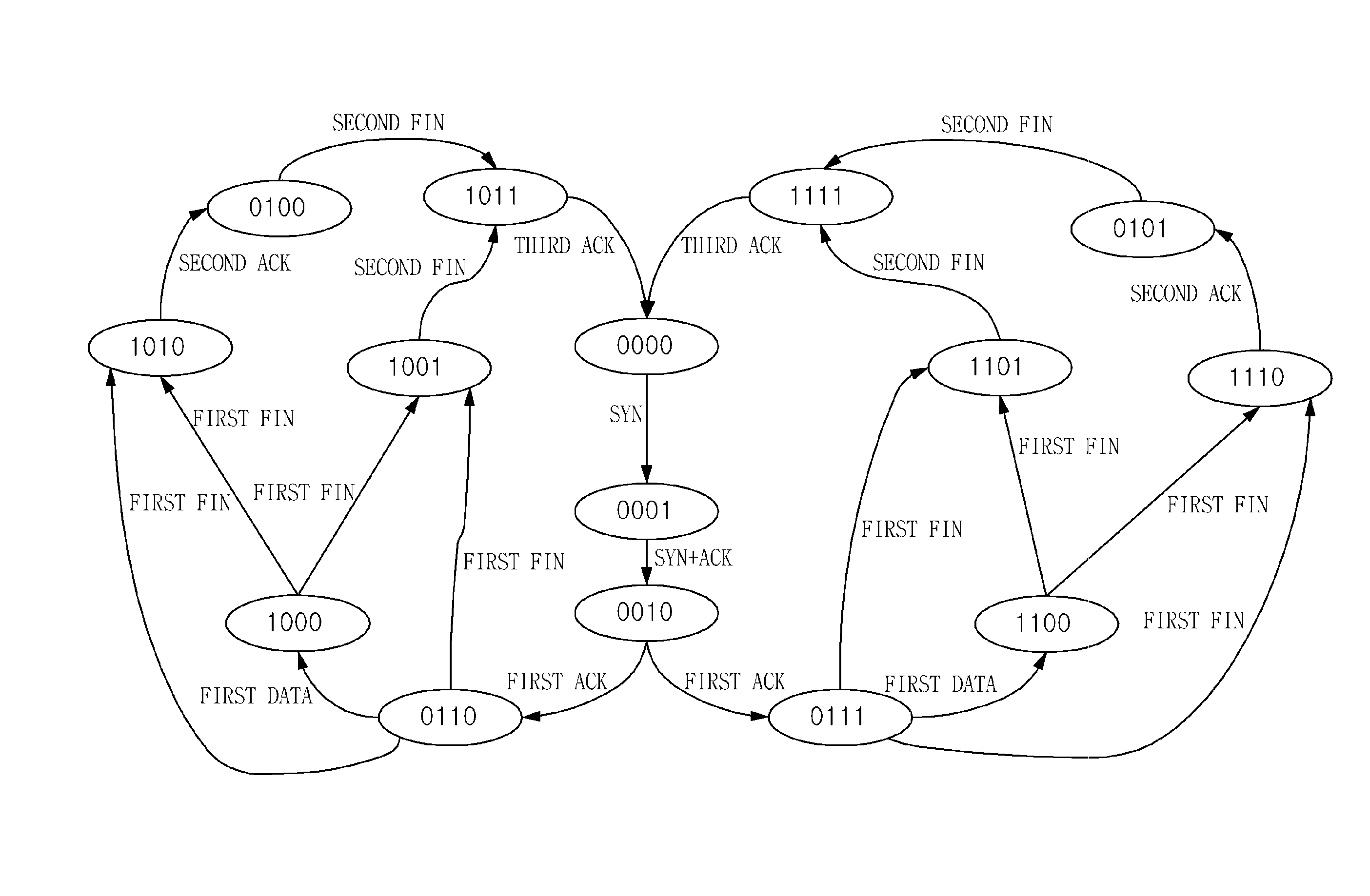
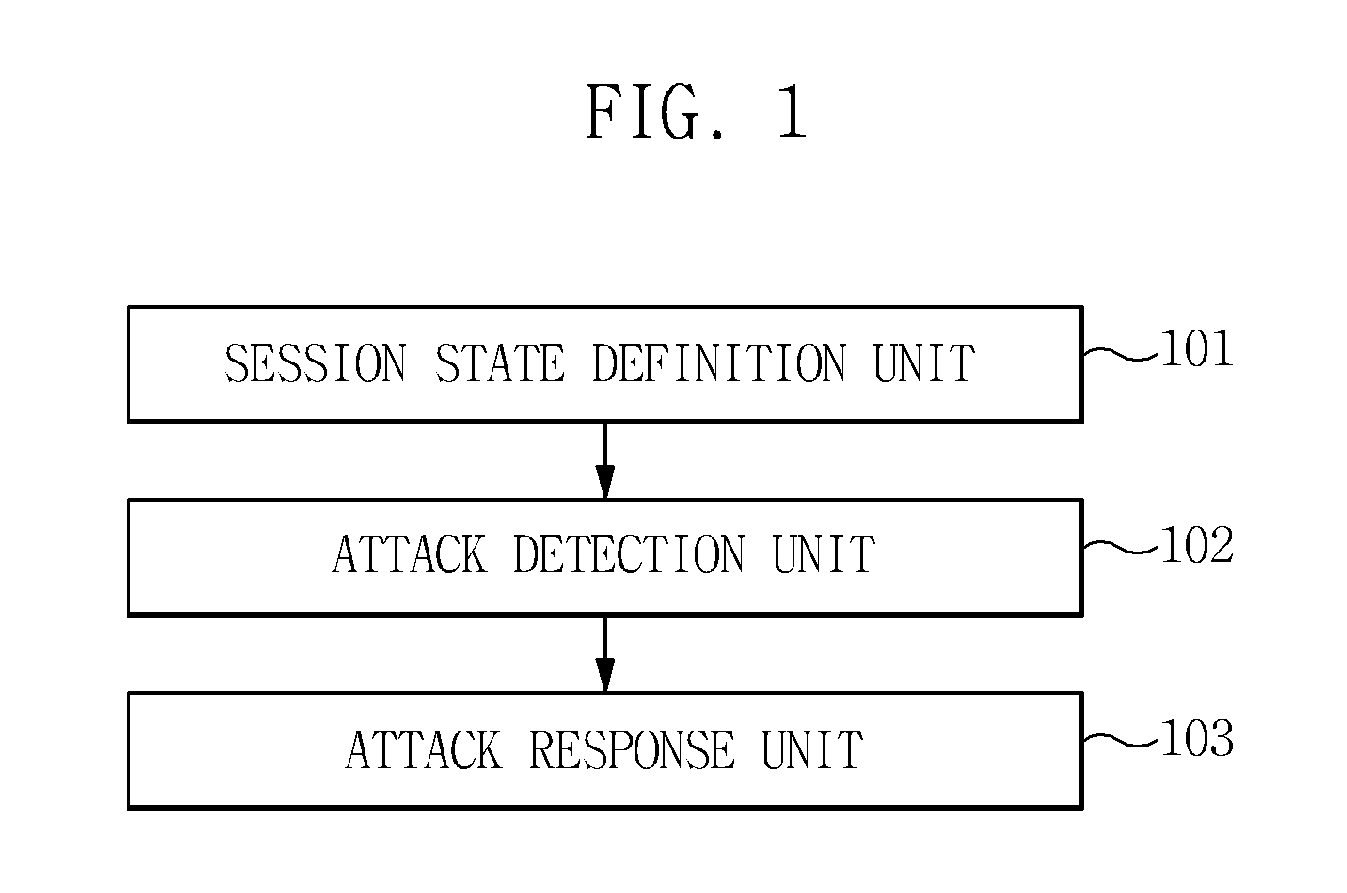
Disclosed herein is a Transmission Control Protocol (TCP) flooding attack prevention method. The TCP flooding attack prevention method includes identifying the type of a packet received at an intermediate stage between a client and a server; determining the direction of the packet; defining a plurality of session states based on the type and the direction of the packet; detecting a TCP flooding attack by tracking the session states for each flow; and responding to the TCP flooding attack based on the type of the TCP flooding attack.
Owner:GAGYOTECH
Method to detect SYN flood attack
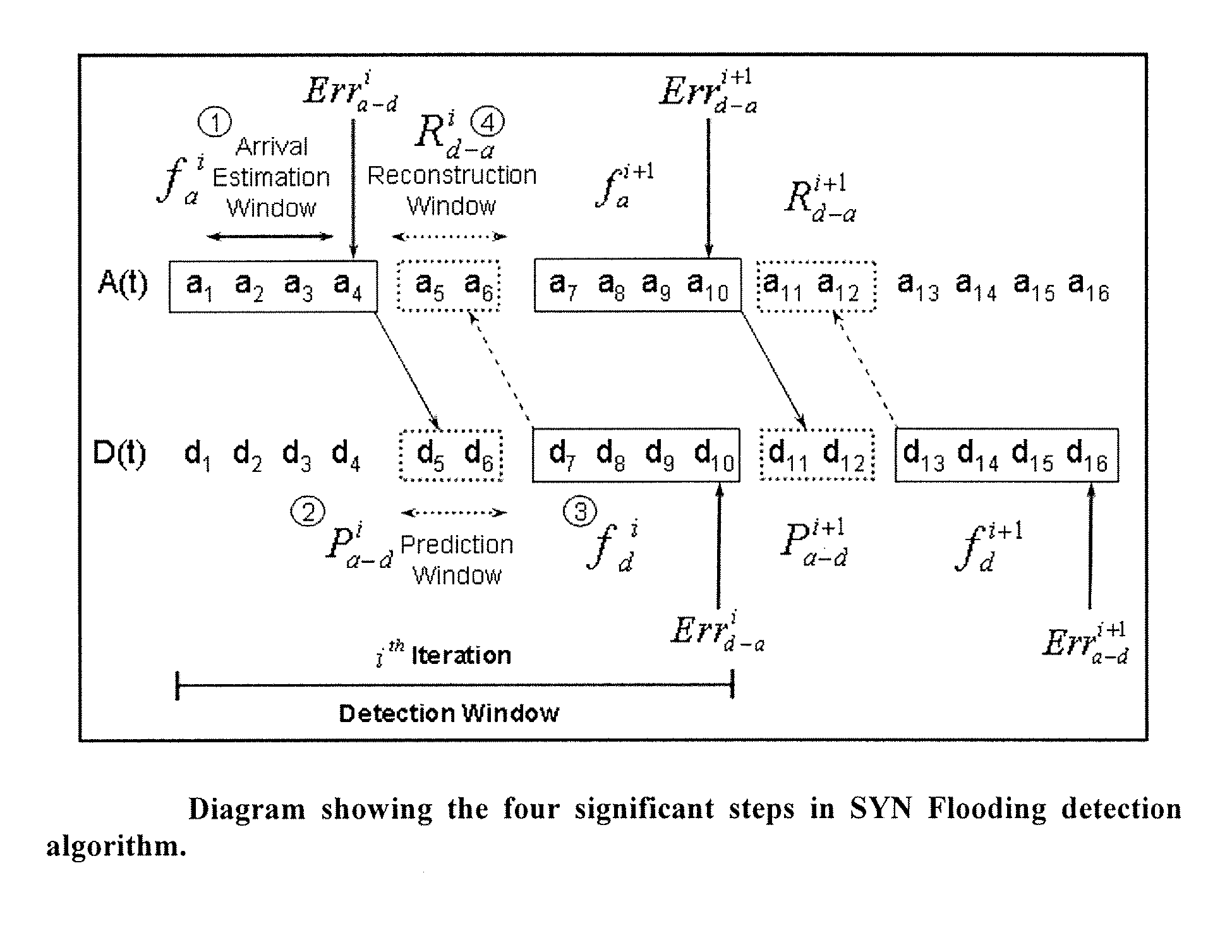
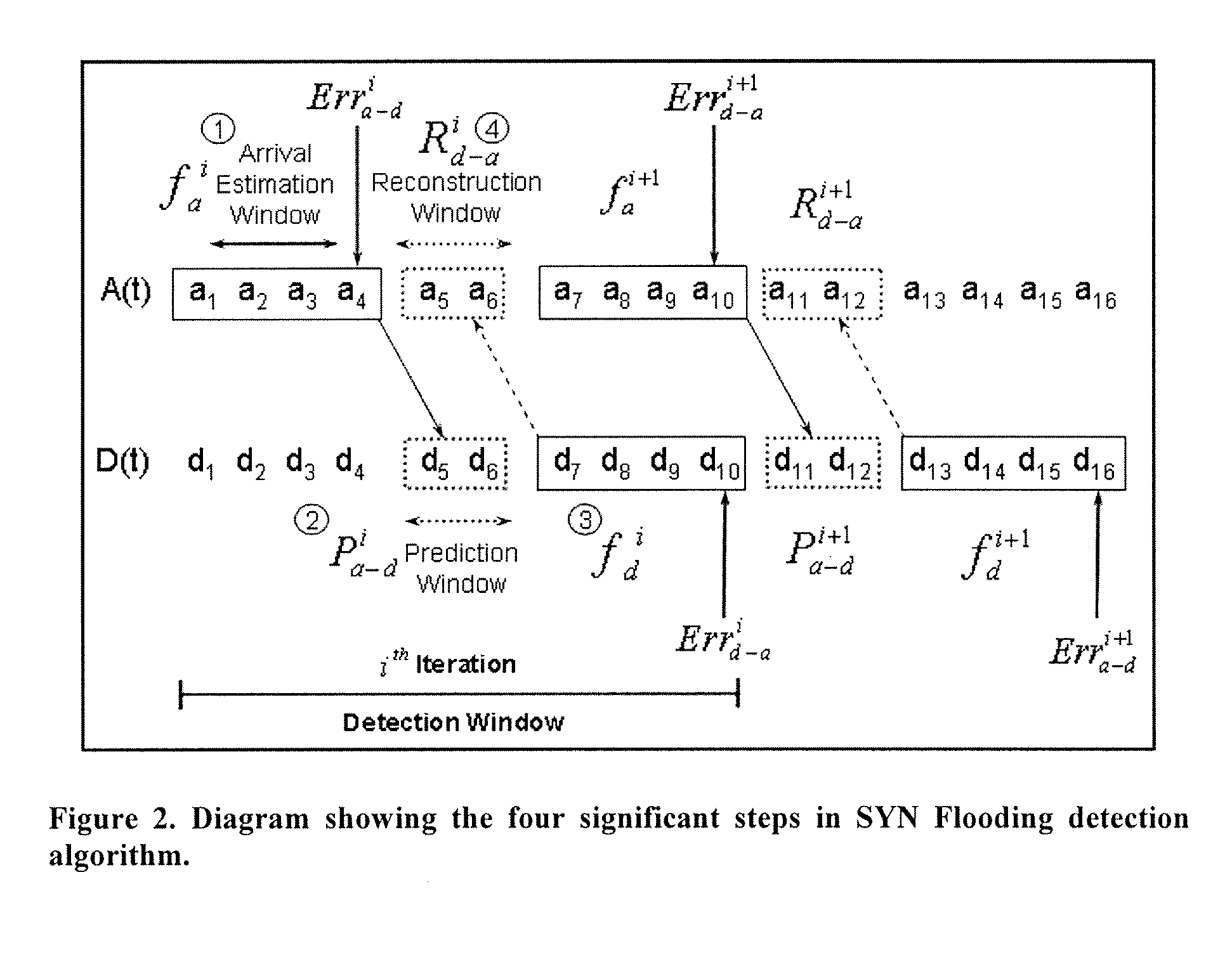
The invention is a method of predicting a SYN flooding attack on a server. The method tracks the number of SYN signals received (or SYN+ACK signals sent) over the communications port of the server in a specified time interval, the arrival estimation window. The invention then predicts the number of anticipated ACK signals to be received over the communication port within a predetermined time length prediction window. The prediction may be made at multiple points within the prediction window. The prediction window is offset in time from the arrival estimation window. The prediction of ACK signals to be received is based upon the number of SYN signals received or SYN+ACK signals sent in the arrival estimation window. In one embodiment, a polynomial is fit to the data in the Arrival estimation window and extrapolated to the prediction window. The predicted number of ACK signals is compared to the actual number received in the prediction window, and if the difference is in excess of a threshold value, and attack is indicated.
Owner:LOUISIANA TECH RES CORP
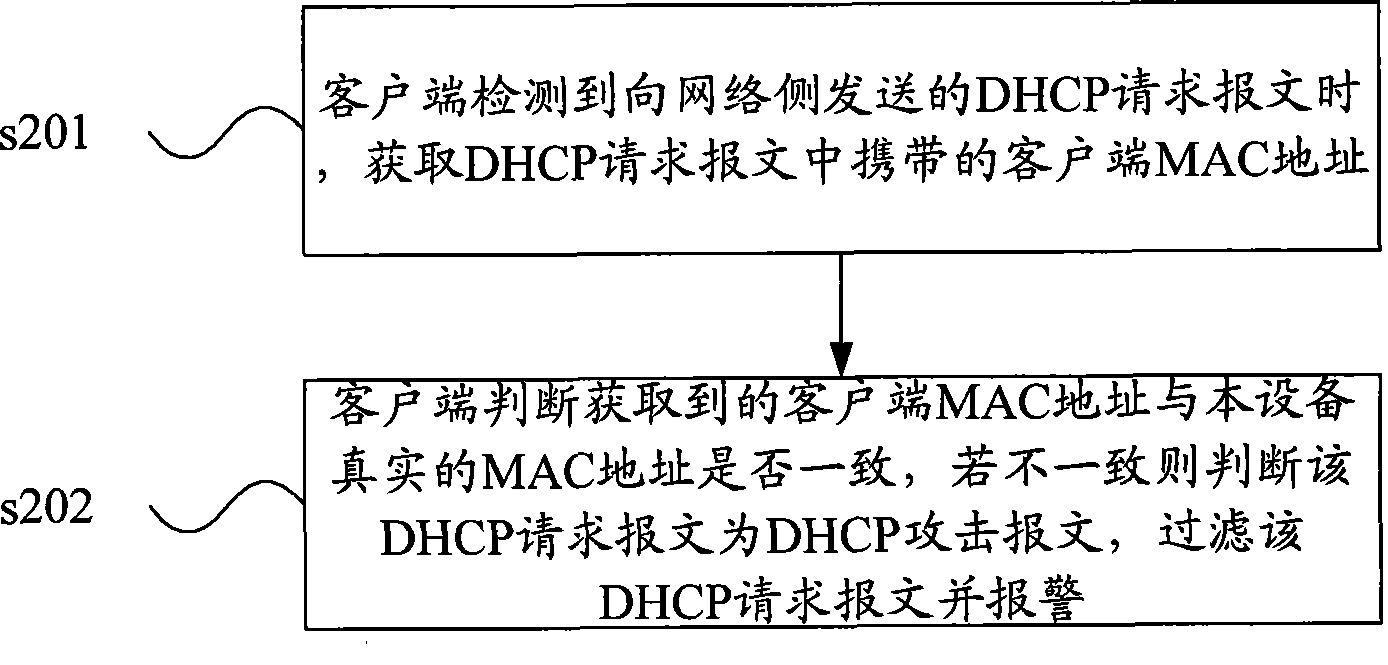
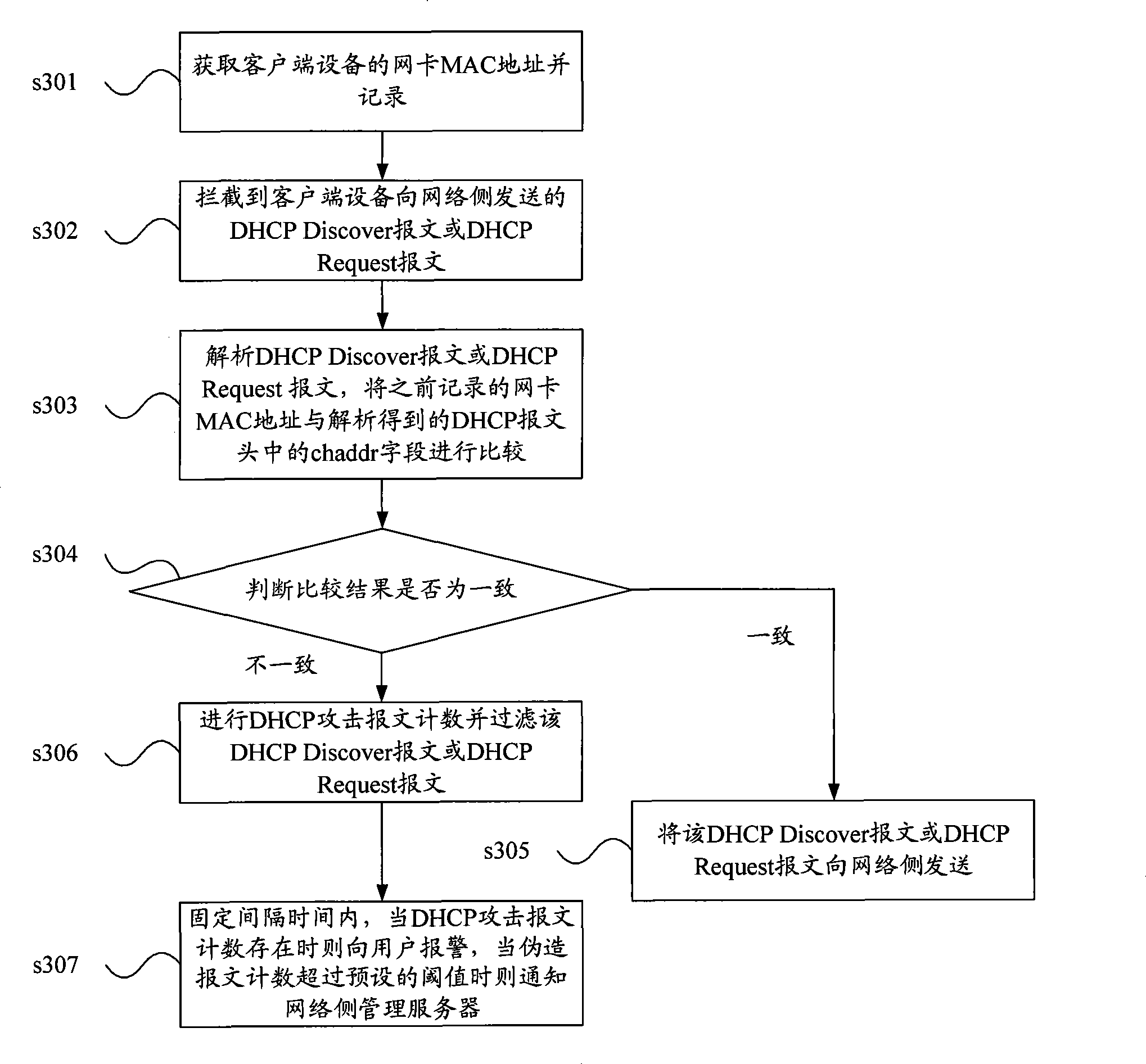
DHCP attack guarding method and customer terminal equipment
ActiveCN101483515AAvoid attackPrevent flood attacksSecuring communicationIp addressTerminal equipment
The present invention discloses a DHCP attack protecting method and a client device. In the method and client device provided by the invention, the client can prevent the DHCP attach without the matching of service end device. The method is executed from each client of internal network and ensures that each internal network client is not used as an attack source for attacking the DHCP server. Simultaneously the invention also can be matched with the management server end for inquiring the suspected attack source and processing the attach source according to a corresponding safety processing strategy. The operations of warning, reminding the user for virus killing, etc. can be provided to the user. The DHCP flooding attack is effectively prevented and the IP address attack is refused.
Owner:NEW H3C TECH CO LTD
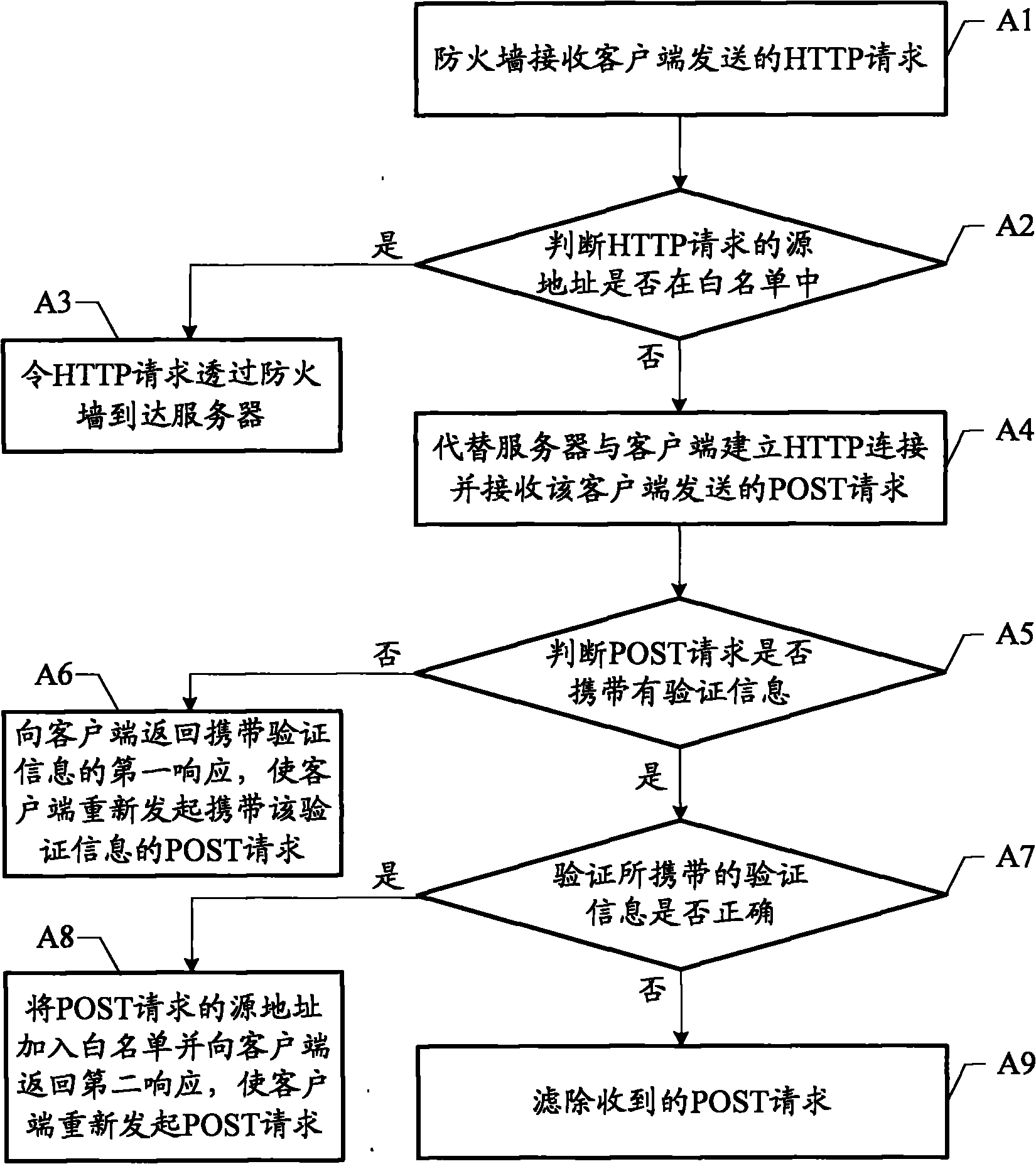
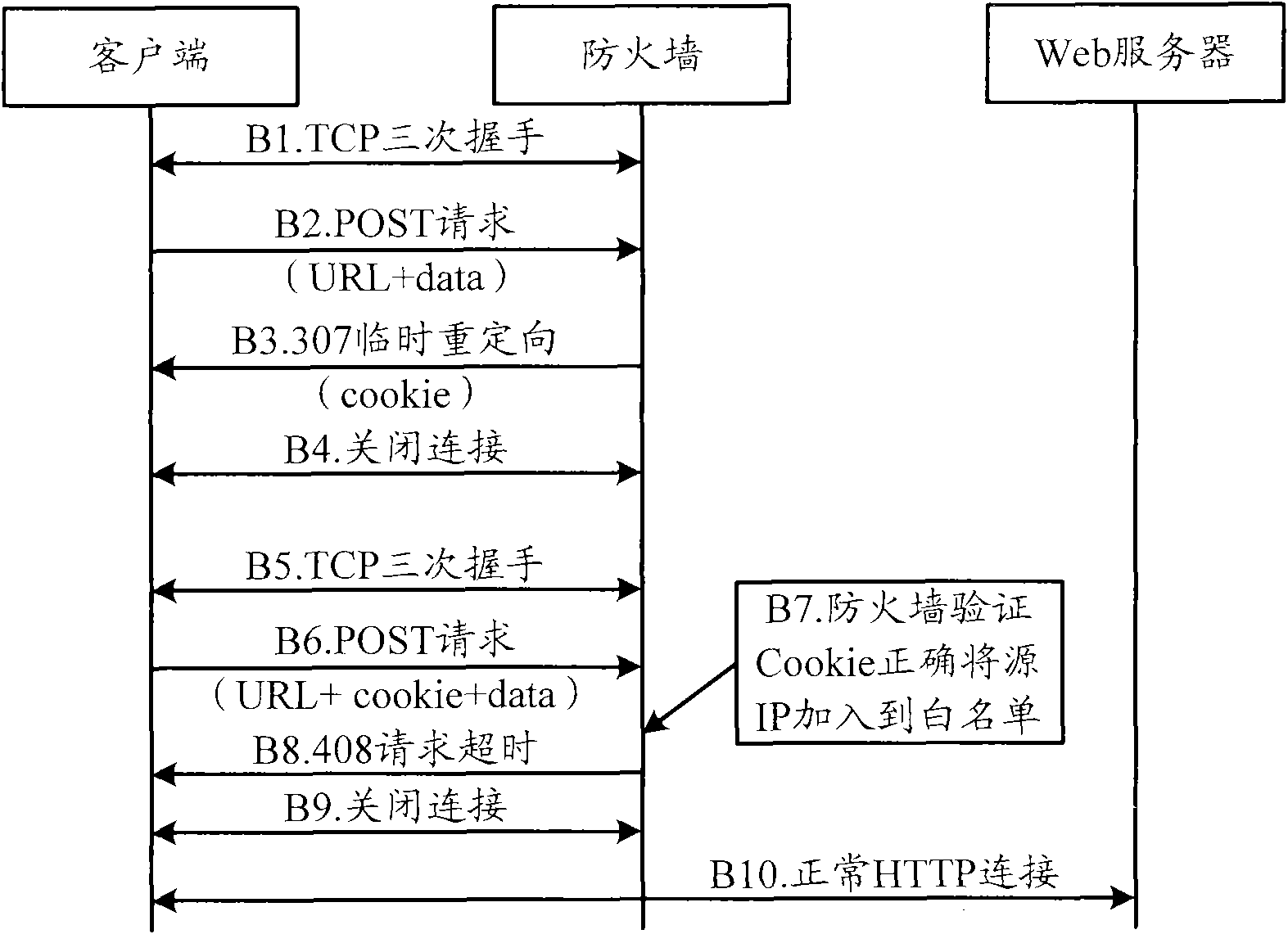
Method and firewall for preventing HTTP POST flooding attacks
The embodiment of the invention discloses method and firewall for preventing HTTP POST flooding attacks. The embodiment responses verification information to a primary hypertext transfer protocol HTTP POST request of a user client, carries the verification information when the user client requests again, effectively prevents HTTP POST flooding attacks by detecting the correctness of the verification information and effectively guides the safety of a network server.
Owner:HUAWEI DIGITAL TECH (CHENGDU) CO LTD
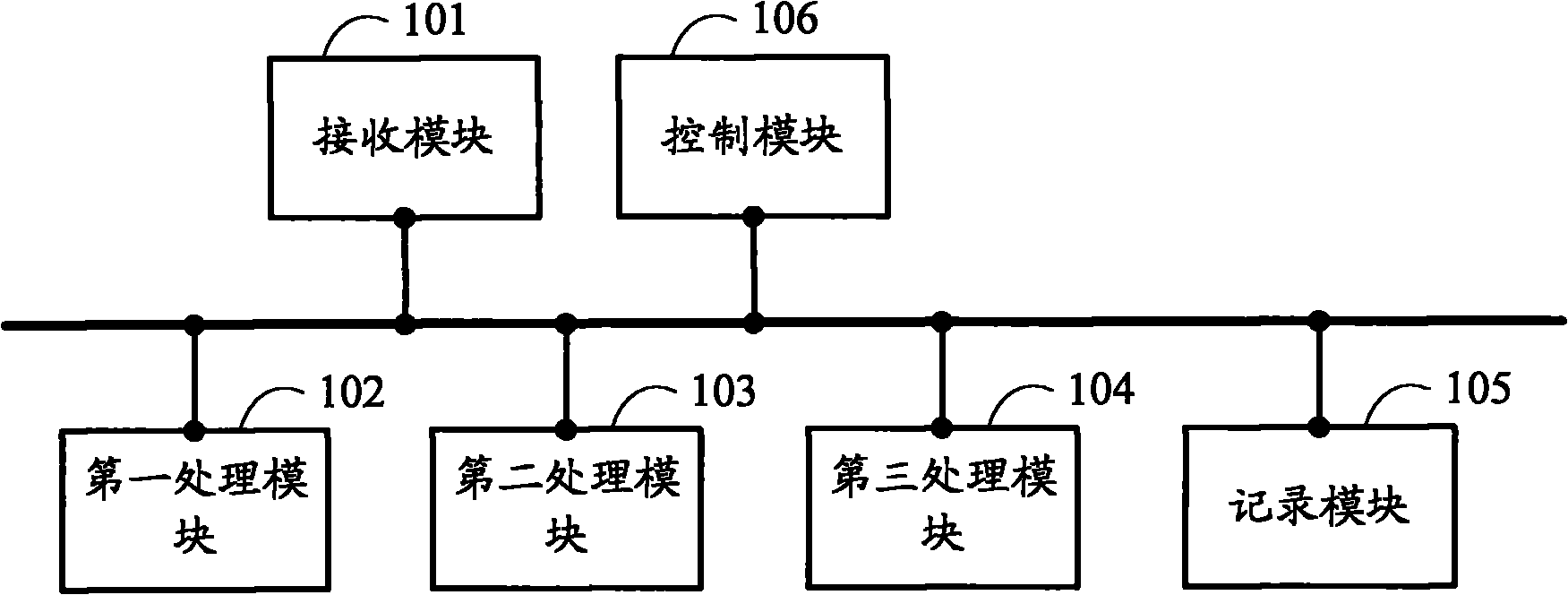
Method and system for domain name resolution server to resist flooding attacks of DNS (Domain Name System) request reports
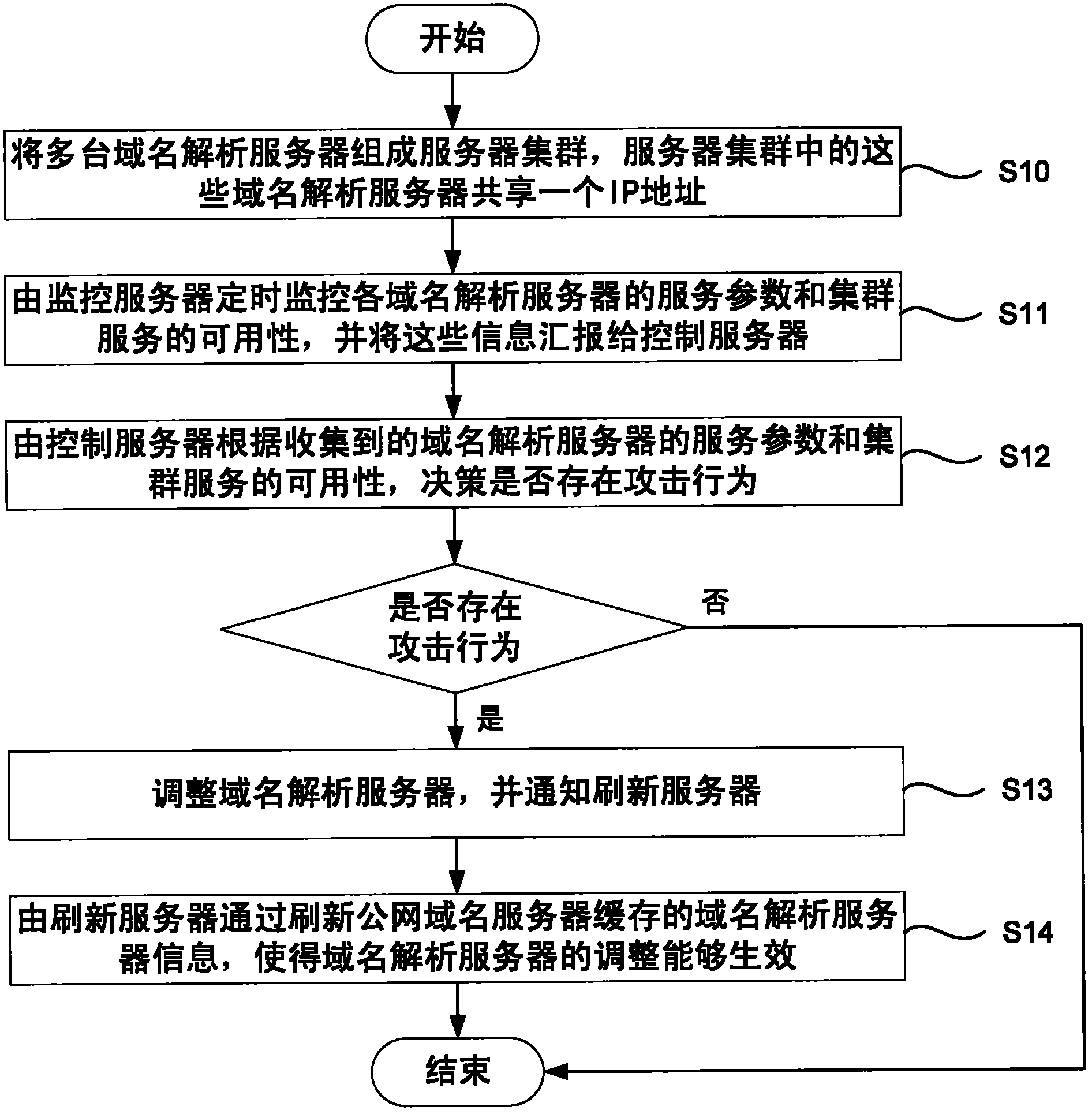
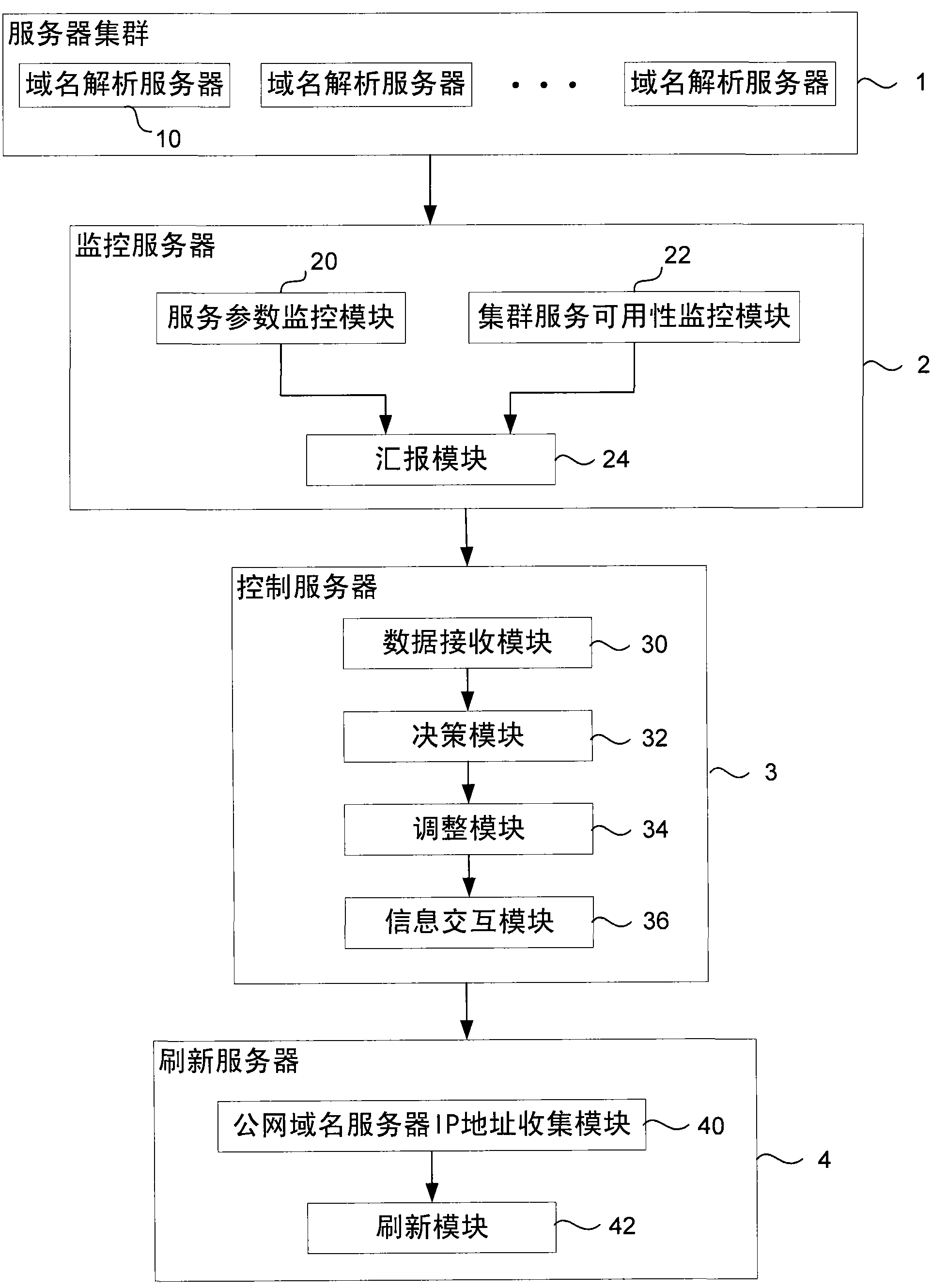
ActiveCN101924776AAttack takes effectProtect against flooding attacksData switching networksDomain nameIp address
The invention discloses a method and a system for a domain name resolution server to resist the flooding attack of DNS (Domain Name System) request messages, which can effectively resist the flooding attacks of the DNS request messages, protect the domain name resolution server, and ensure the normal operation of domain name resolution. In the technical scheme, the method comprises the steps of: combining a plurality of domain name resolution servers into a server cluster which shares one IP address; timely monitoring the service parameters and the cluster service availability of all the domain name resolution servers by a monitoring server, and reporting the service parameters and the cluster service availability to a control server; determining whether attacks exist or not by the control server according to the collected service parameters and cluster service availability of the domain name resolution server; if so, adjusting the domain name resolution server and notifying a refreshing server; and refreshing the domain name resolution server information cached by a public network domain name server by the refreshing server so as to ensure that the adjustment of the domain name resolution server takes effect.
Owner:CHINANETCENT TECH
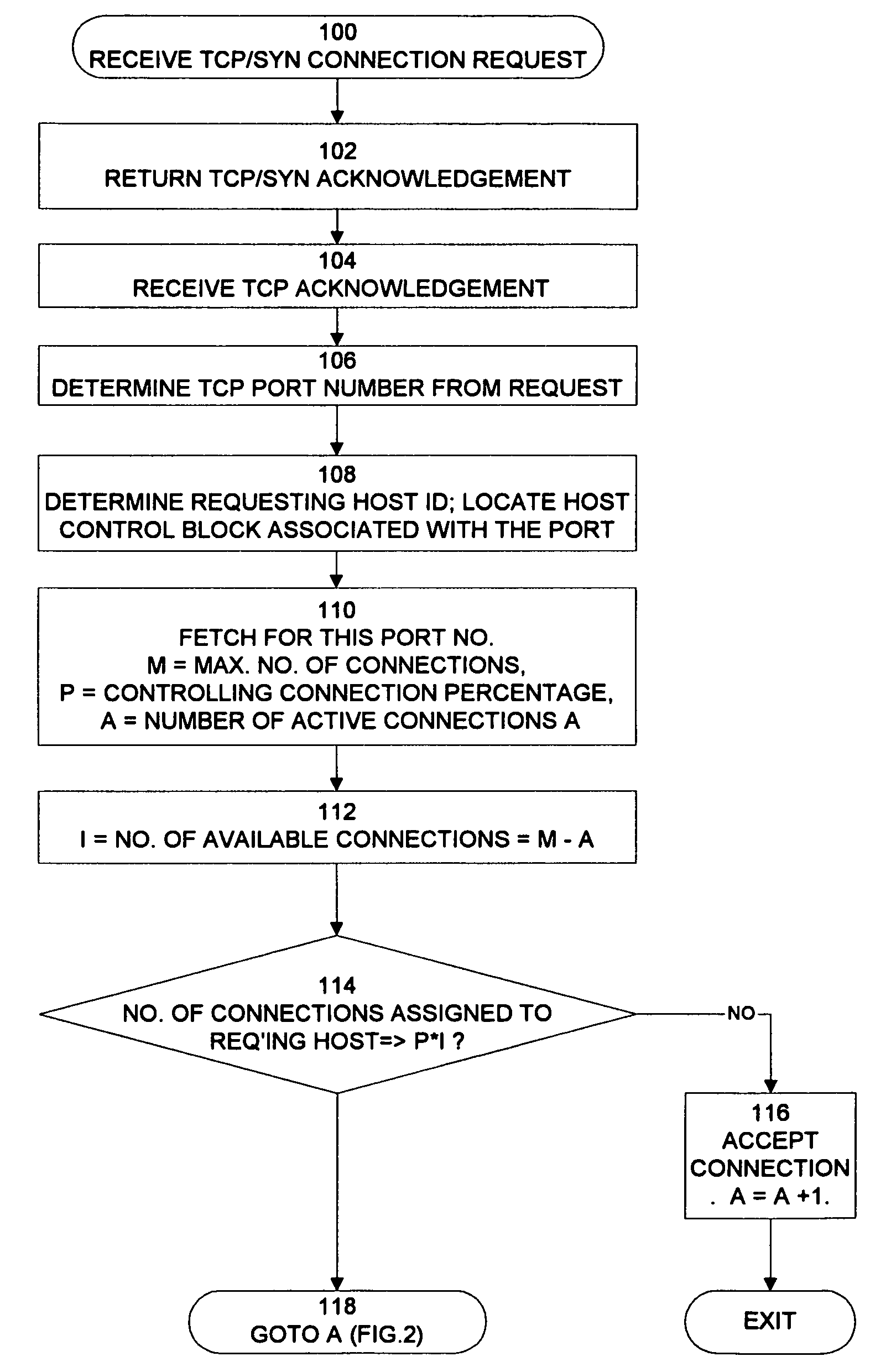
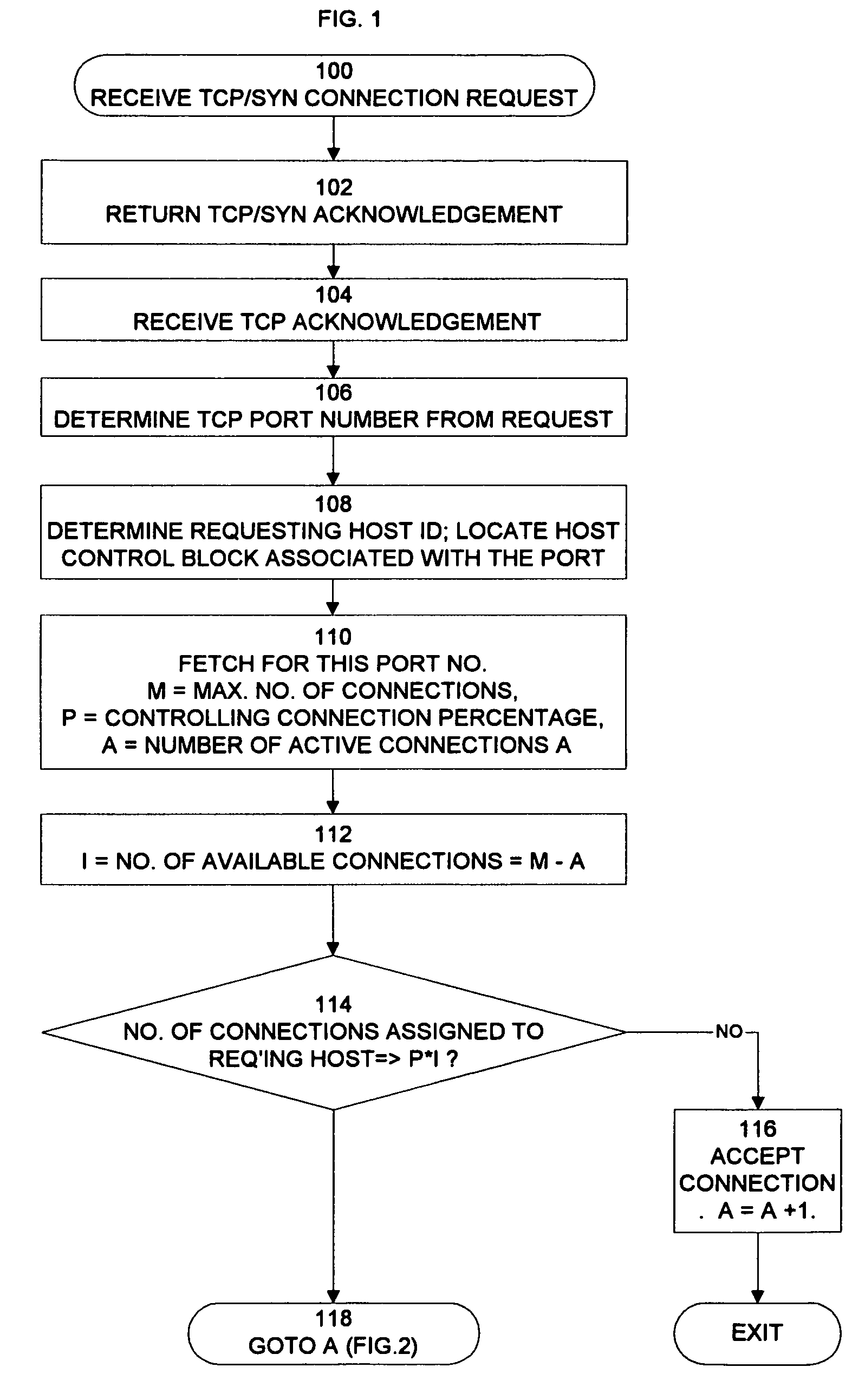
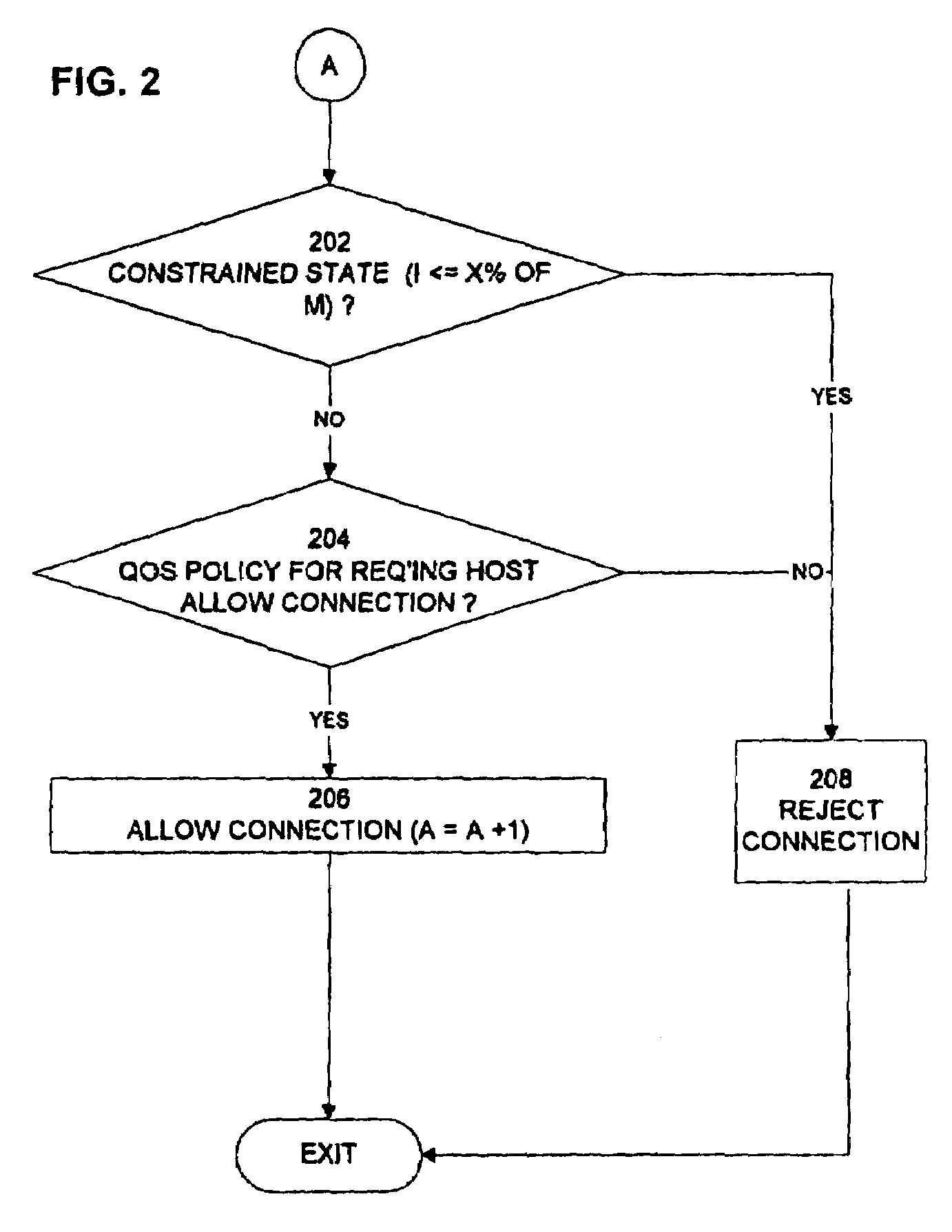
Technique of defending against network connection flooding attacks
InactiveUS7137144B1Minimize consequencesPrevents one or more attackers from consuming all server resourcesMemory loss protectionError detection/correctionQuality of serviceNetwork connection
The invention prevents server overload and possible server crippling due to a flooding of connect requests caused by intentional attack or otherwise. In response to a connection request from a host for a specified port, the number of connections to the port that are assigned to the host are determined. If this number exceeds a first threshold, the request is denied. It is possible to override this denial if a quality of service parameter pertaining to the host permits such an override. However, if the number of available connections to the port is less than a second threshold, the connection request is denied in any event.
Owner:TREND MICRO INC
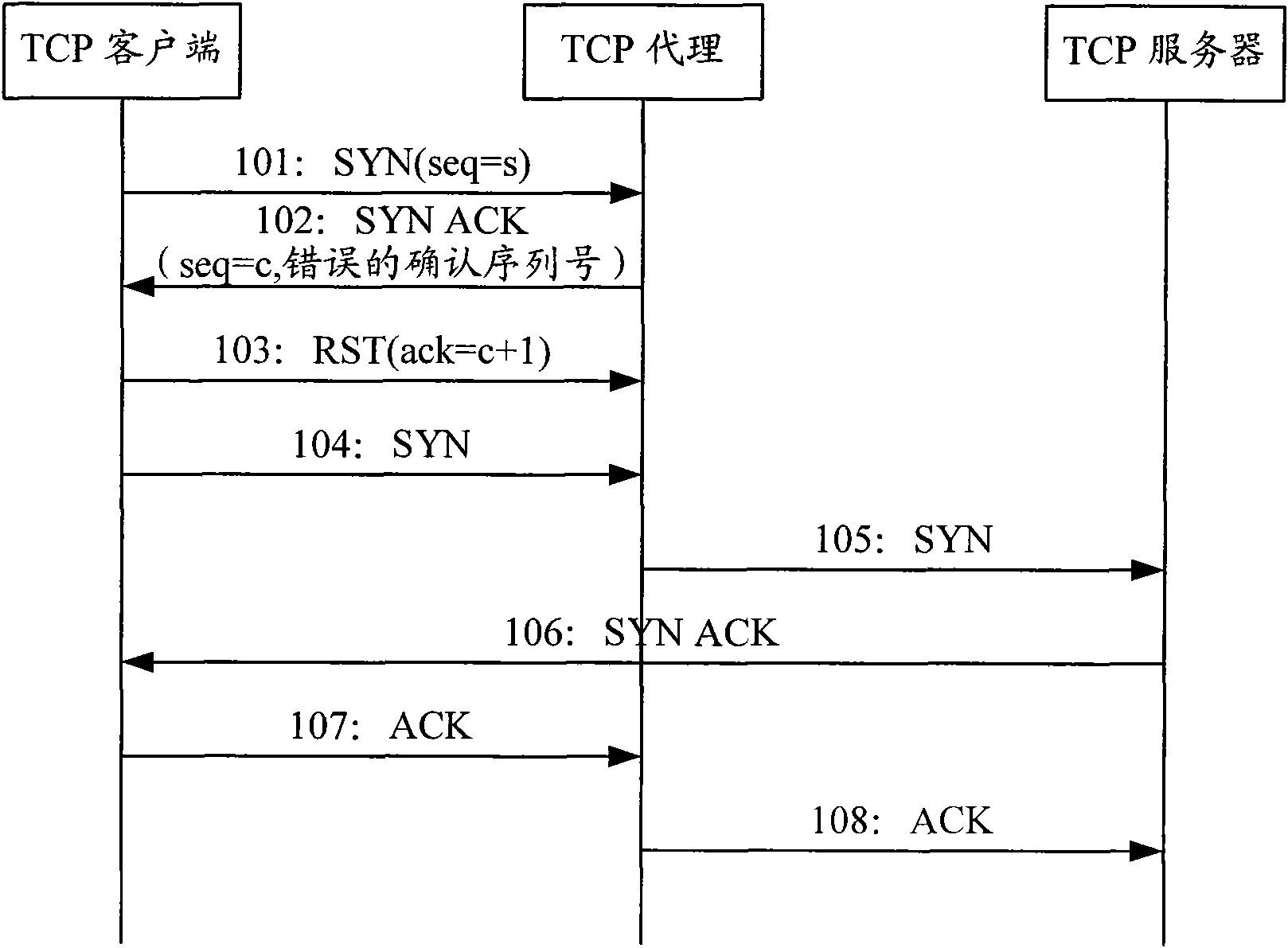
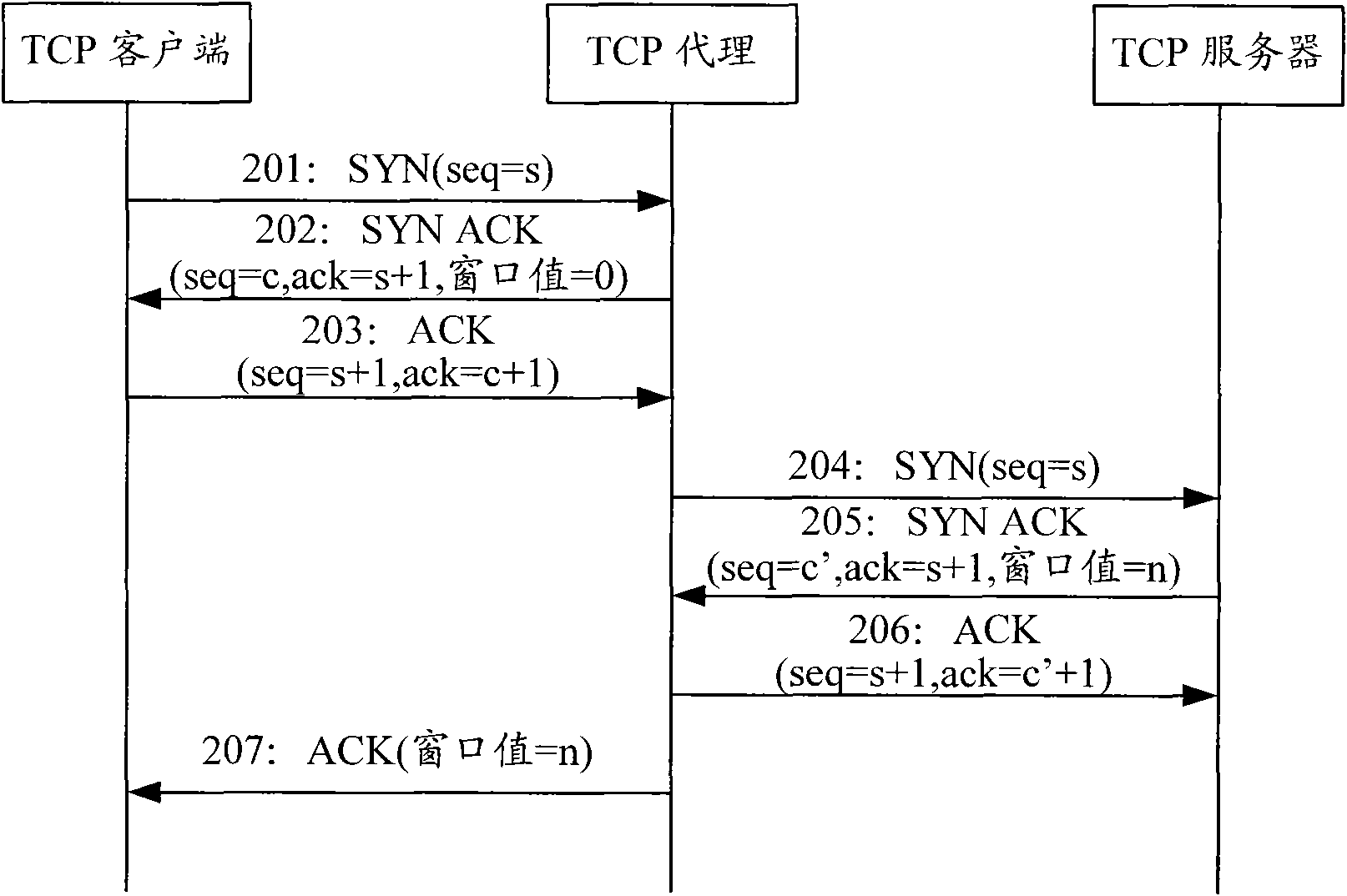
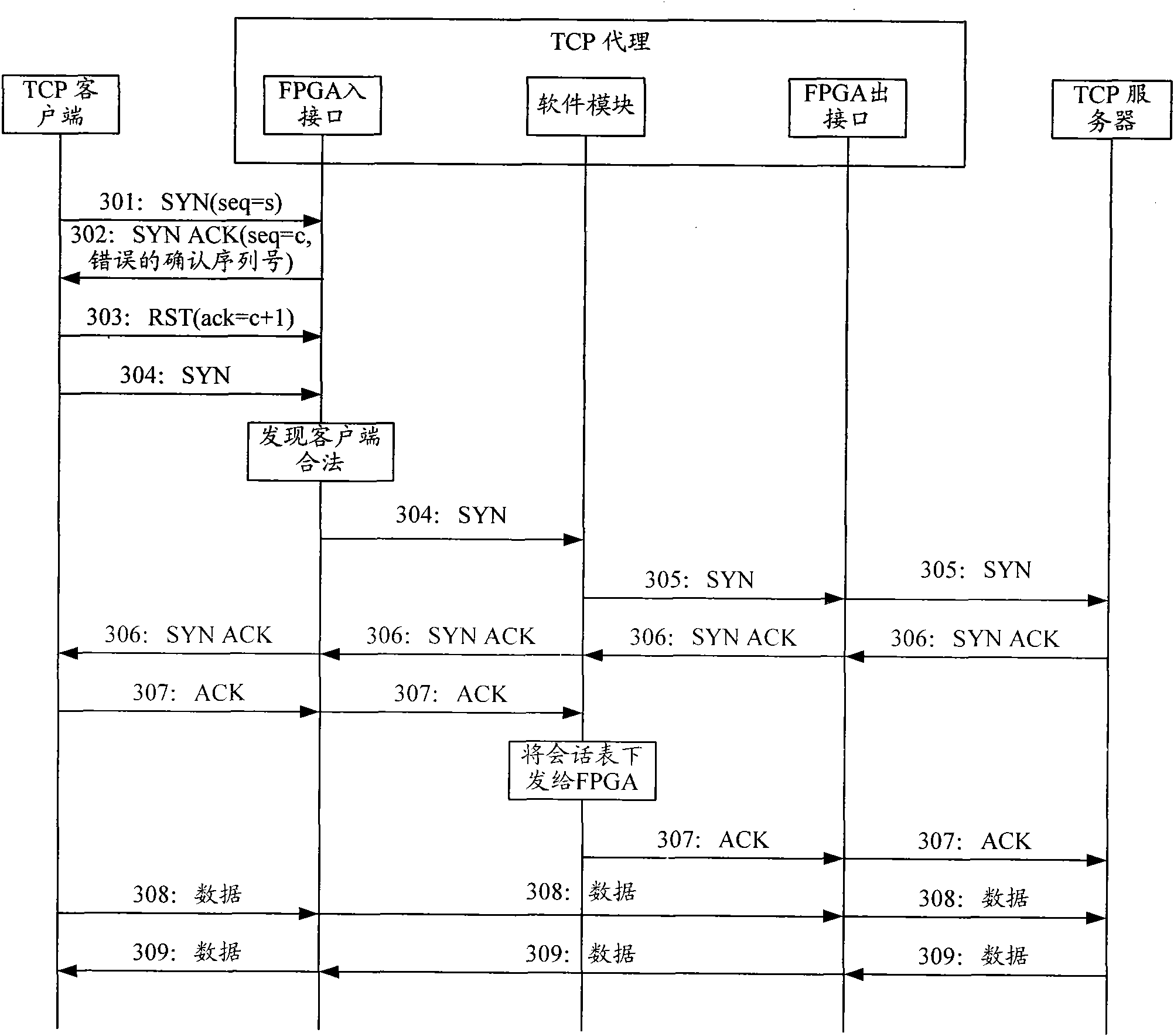
Method for defensing transmission control protocol synchronous flooding attack and transmission control protocol agent
InactiveCN101594359AHigh speedIncrease aggressivenessData switching networksClient-sideSoftware modules
The invention discloses a method for defensing a transmission control protocol synchronous flooding attack and a transmission control protocol agent. The method comprises that: FPGA on a TCP agent and a client perform TCP three-way handshake to verify the legality of the client; after the client passes the legality verification, a software module on the TCP agent begins establishing TCP connection between the client and a server, and transmits a session table to the FPGA; and the FPGA forwards data messages interacted between the client and the server according to the session table. The method improves the effect of defensing the TCP synchronous flooding attack.
Owner:NEW H3C TECH CO LTD
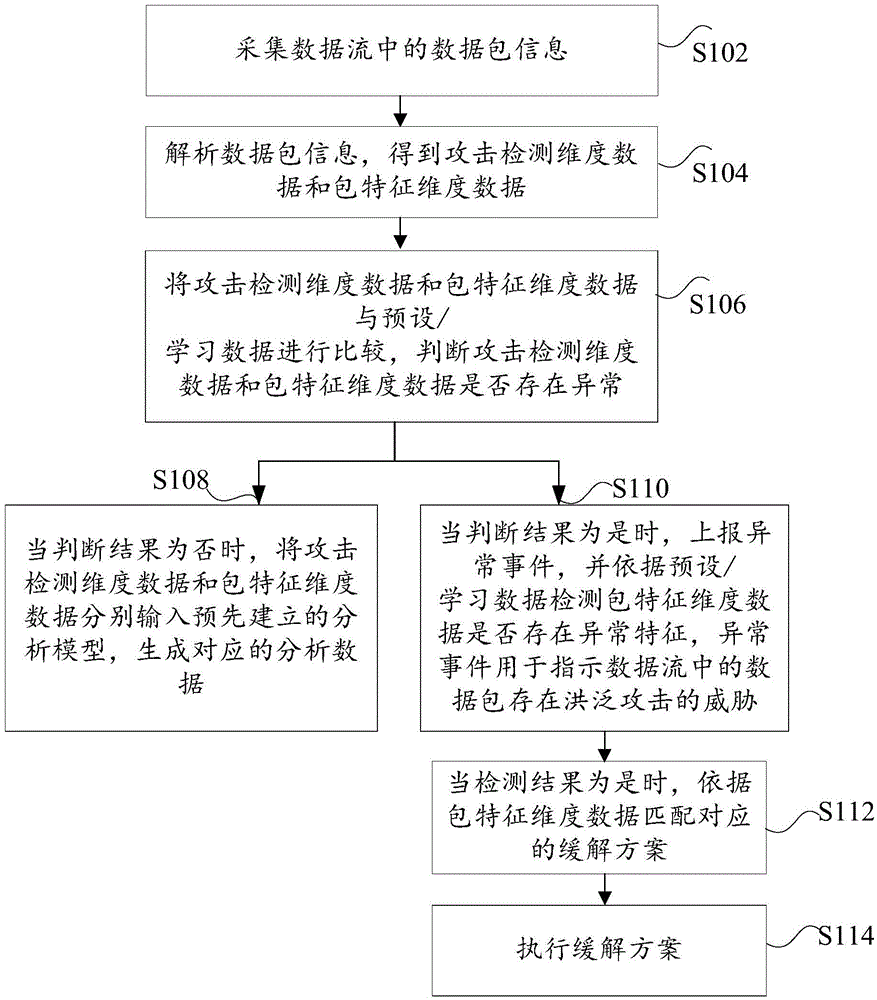
Network attack processing method and device
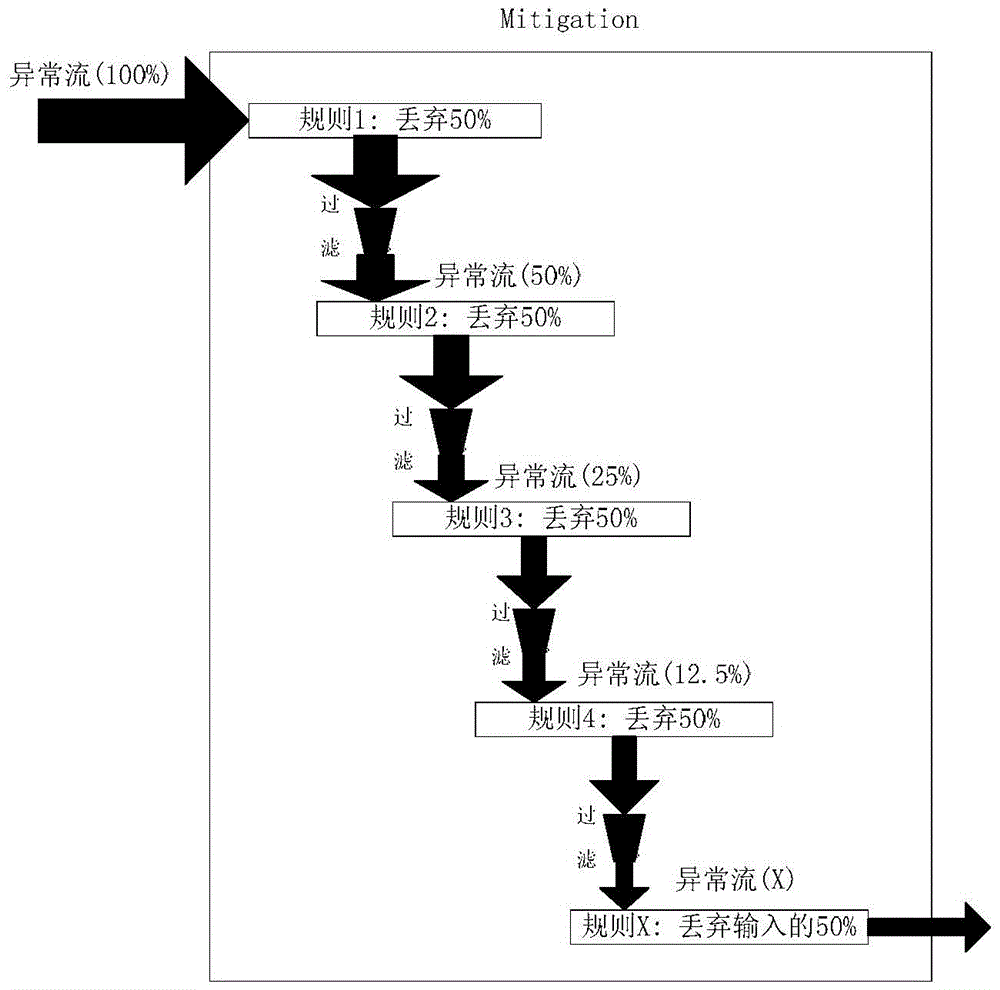
The invention discloses a network attack processing method and device. The method comprises the following steps: collecting data packet information in data stream; analyzing the data packet information to obtain attack detection dimension data and packet characteristic dimension data; comparing the attack detection dimension data and the packet characteristic dimension data with preset / learnt data to judge whether the attack detection dimension data and the packet characteristic dimension data are abnormal; when the judgment result is positive, reporting an abnormal event, and detecting whether the packet characteristic dimension data have abnormal characteristics according to the preset / learnt data; when the judgment result is negative, matching a corresponding easing scheme according to the packet characteristic dimension data; and executing the easing scheme. The network attack processing method and device disclosed by the invention are used for solving the technical problems in the prior art that the accidental damage to a data packet with normal flow in a flooding attack easing process is large, the attach confirmation precision is low and large system resources are consumed for preventing flooding attacks.
Owner:HILLSTONE NETWORKS CORP
Increment deployment SDN network-based method for defending link flooding attack
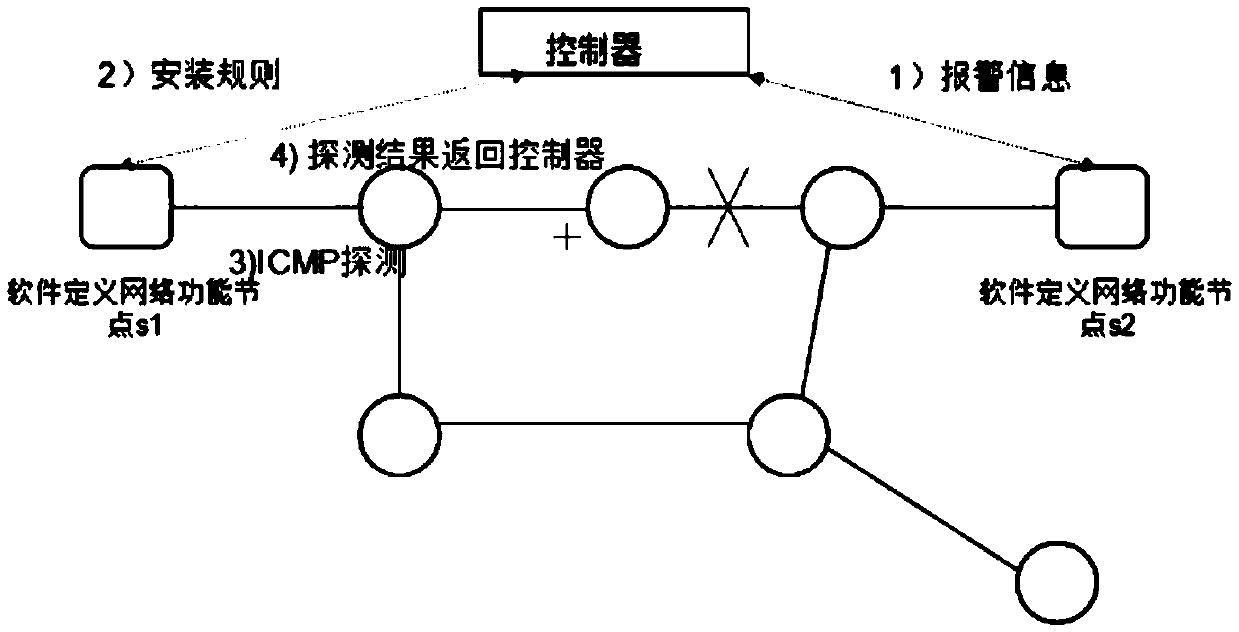
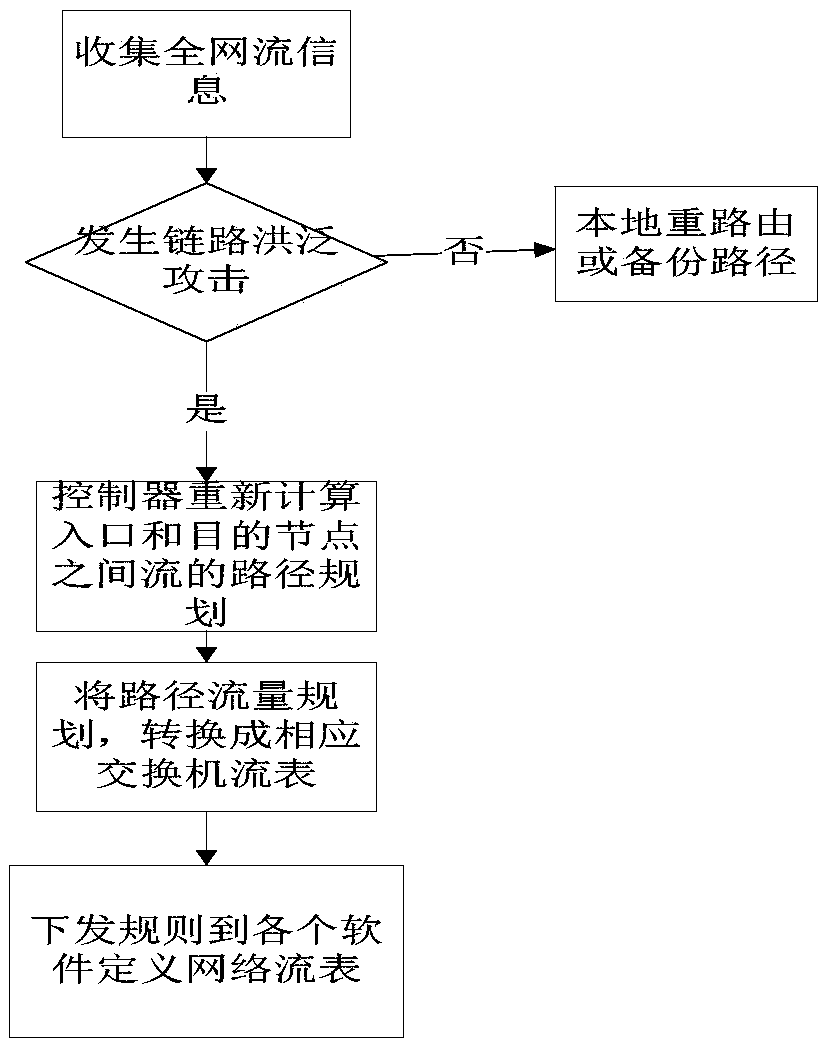
The invention relates to an increment deployment SDN network-based method for defending a link flooding attack. A node upgrade algorithm is utilized to pick out routers that need to be upgraded into software-defined network function nodes and the routers are upgraded; when congestion occurs in a network, a congestion link is positioned through the software-defined network function nodes deployed in the network; congestion link information of the whole network is collected, and on this basis, whether current network congestion forms a link flooding attack is judged; and if the link flooding attach is formed, global flow engineering is started to balance flow of the whole network, otherwise, the congestion link is relieved through backup of a path. According to the increment deployment SDN network-based method for defending a link flooding attack, in a traditional network, a small quantity of nodes are upgraded into software-defined network function nodes, the link flooding attack is detected, a link group that is attacked is positioned, and link flow of the whole network is balanced through centralized control flow engineering, so that the root of a link flooding attack is eliminated, thereby effectively defending the link flooding attack.
Owner:SHENZHEN GRADUATE SCHOOL TSINGHUA UNIV
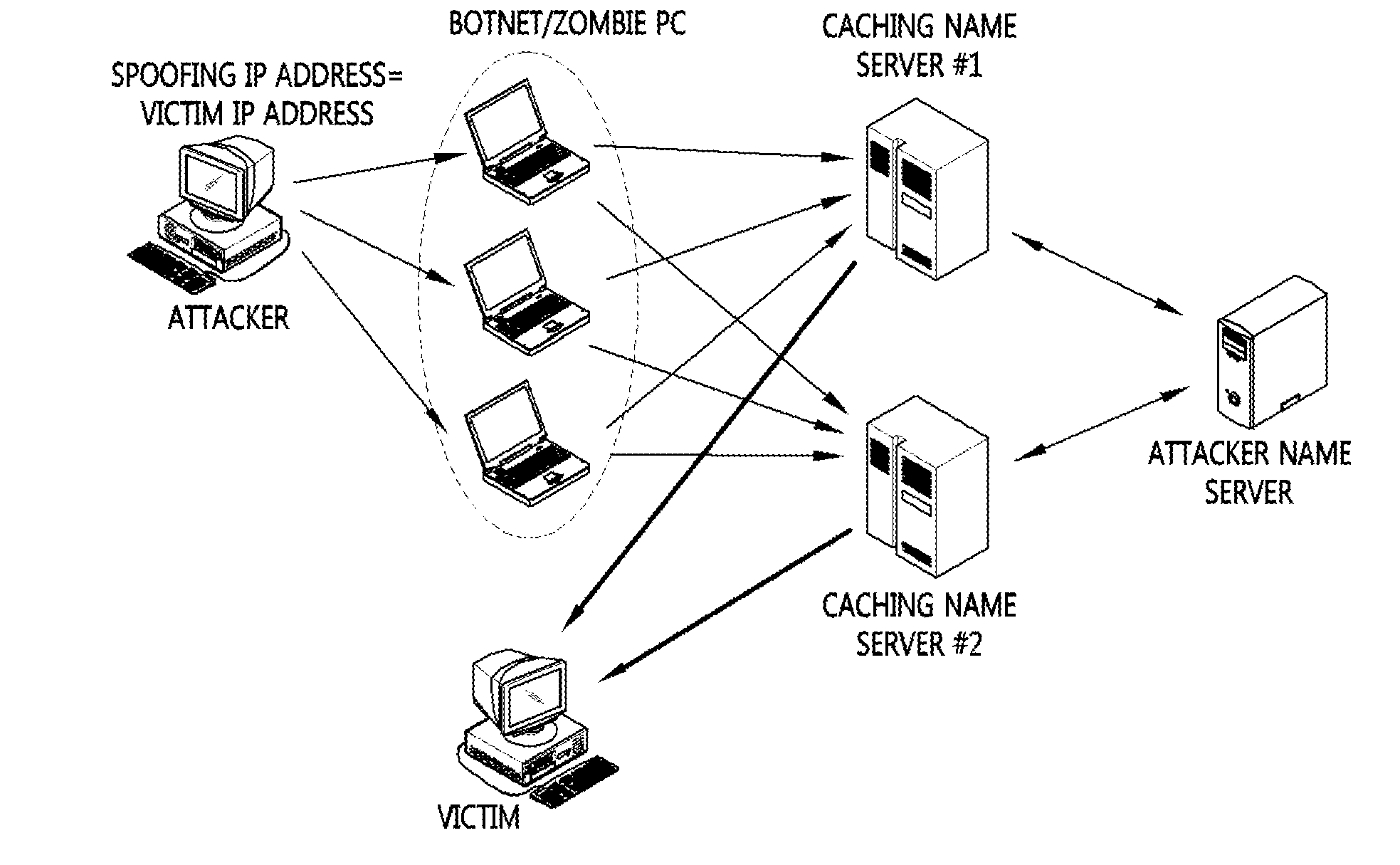
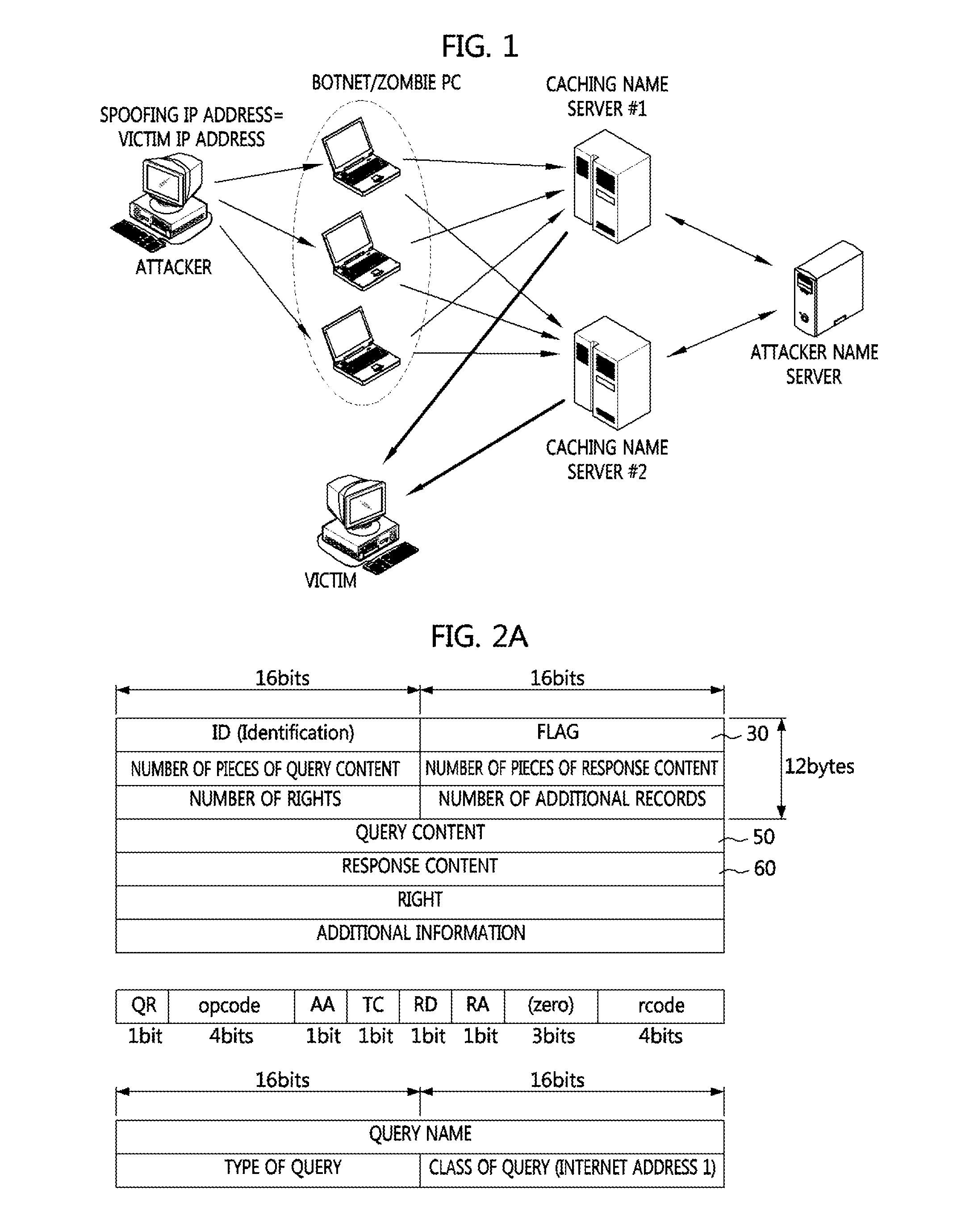
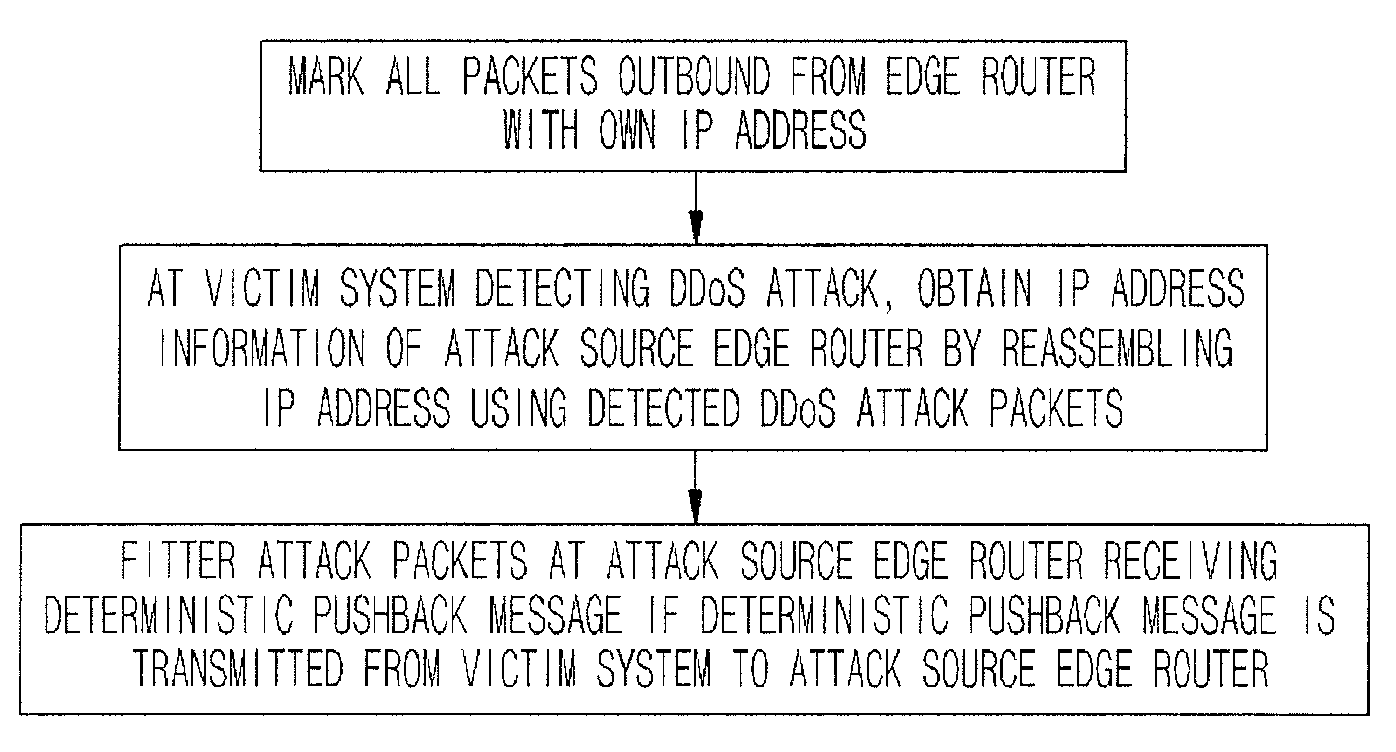
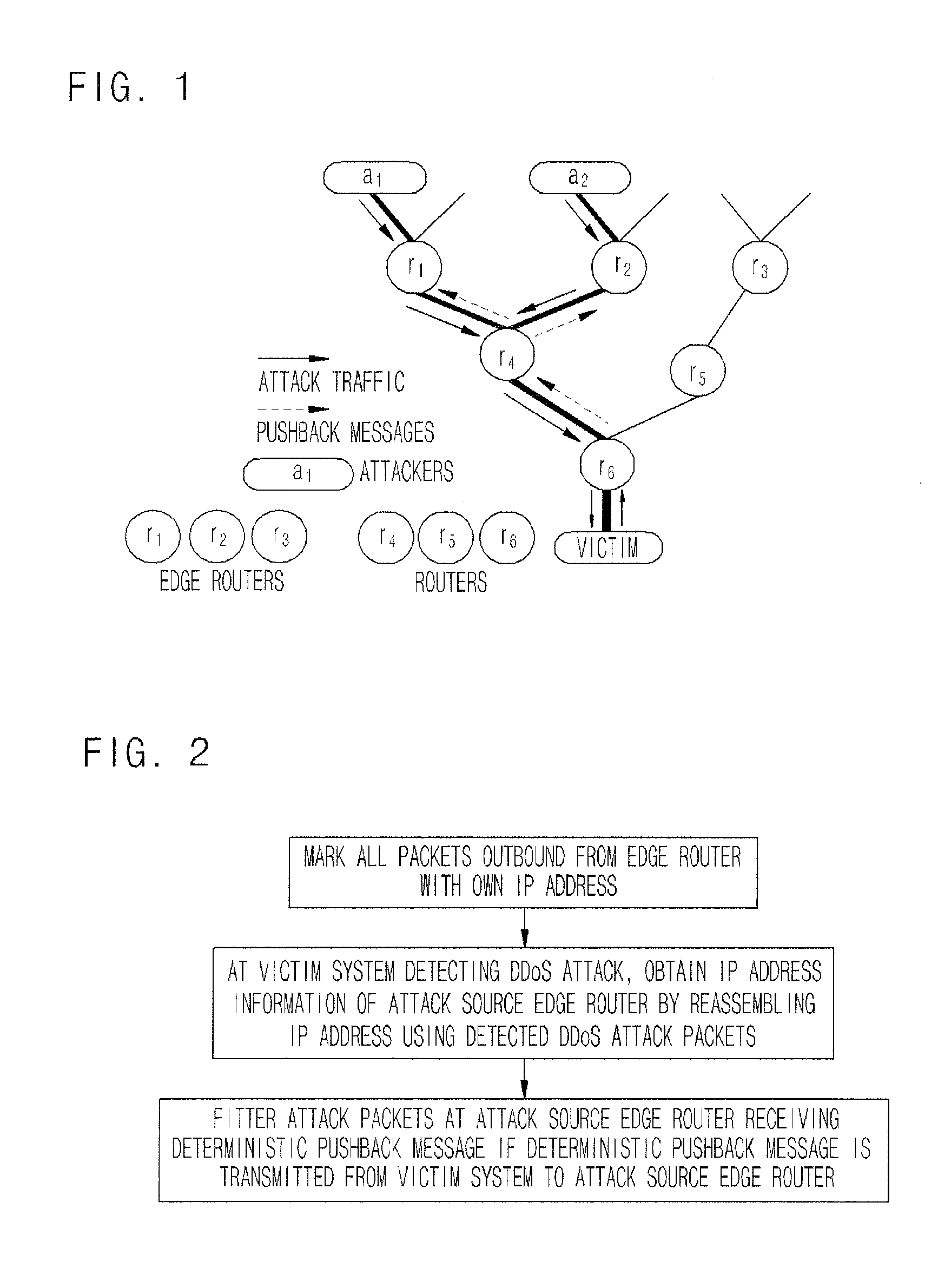
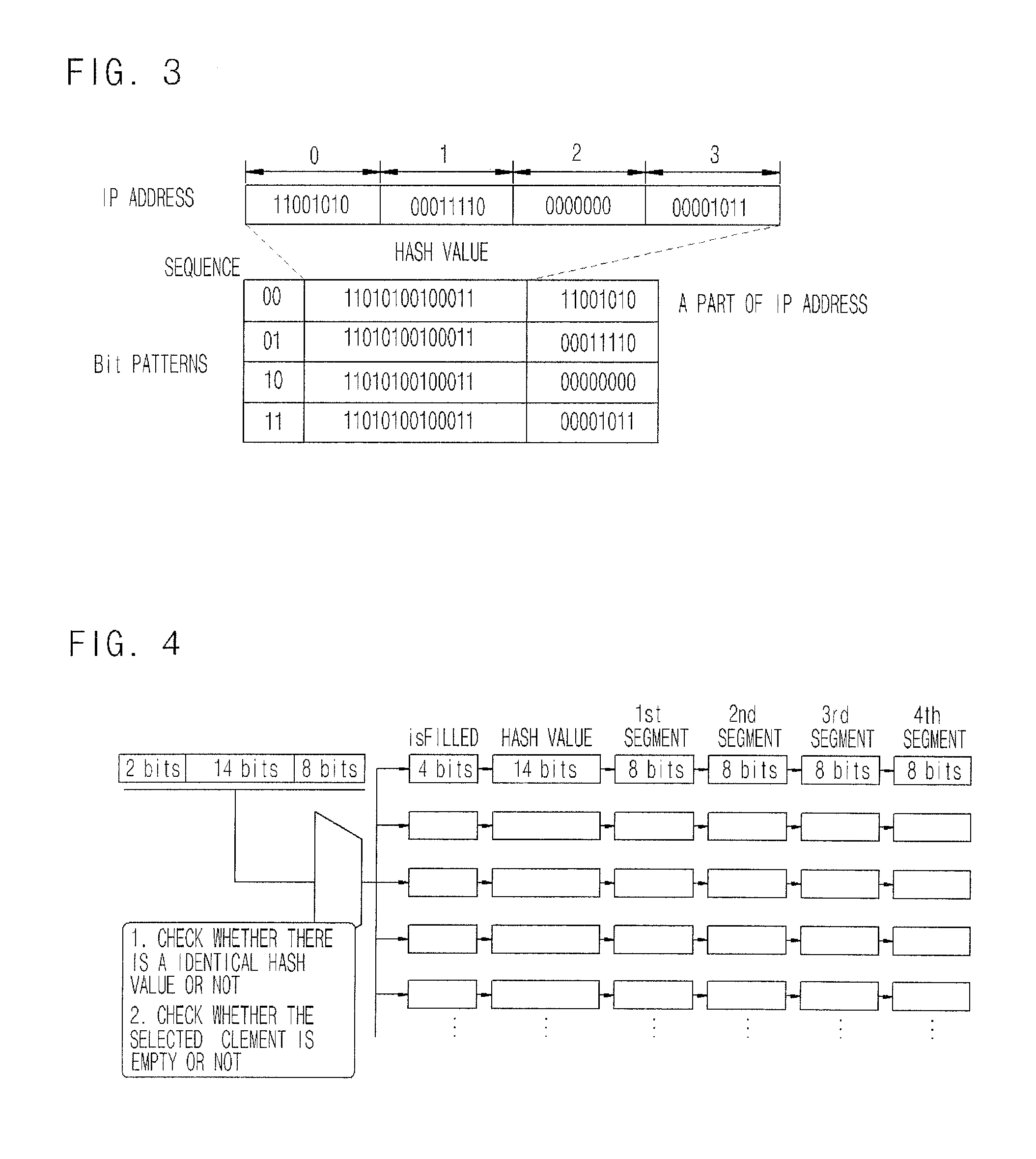
DDoS FLOODING ATTACK RESPONSE APPROACH USING DETERMINISTIC PUSH BACK METHOD
InactiveUS20080127324A1Eliminate the problemComputer security arrangementsMultiple digital computer combinationsIp addressFlooding attack
Provided is a method for responding a distributed denial of service (DDoS) attack using deterministic pushback scheme. In the method, all of packets outbound from an edge router of a predetermined network system to the other network system are marked with own IP address in order to enable a victim system to confirm an IP address of an attack source edge router for DDoS attack packets. Then, IP address information of an attack source edge router is obtained by reassembling an IP address of detected DDoS attack packets at a victim system that detects DDoS attack. A deterministic pushback message is received at an attack source edge router if a victim system transmits a deterministic pushback message to the attack source edge router, information of the attack source edge router is confirmed, and corresponding attack packets are filtered.
Owner:ELECTRONICS & TELECOMM RES INST
Efficient safety tracing scheme based on flooding attack
InactiveCN1777182ATracking is fast and efficientAttack suppressionData switching networksInterference resistanceFlooding attack
The disclosed scheme is a scheme for defending DoS / DdoS attack actively. Tracing attack source, the invention restrains attacks from source. Tracing to source of attack provides evidence for investigating liability of attacker further. Researching on algorithm, the invention strengthens own security from algorithm self, and enhances interference immunity of the algorithm. Probability method for selecting marker is adopted in the scheme instead of original fixing probability method for each route forwarding node so as to optimize capability when attack route is reconstructed.
Owner:NANJING UNIV OF POSTS & TELECOMM
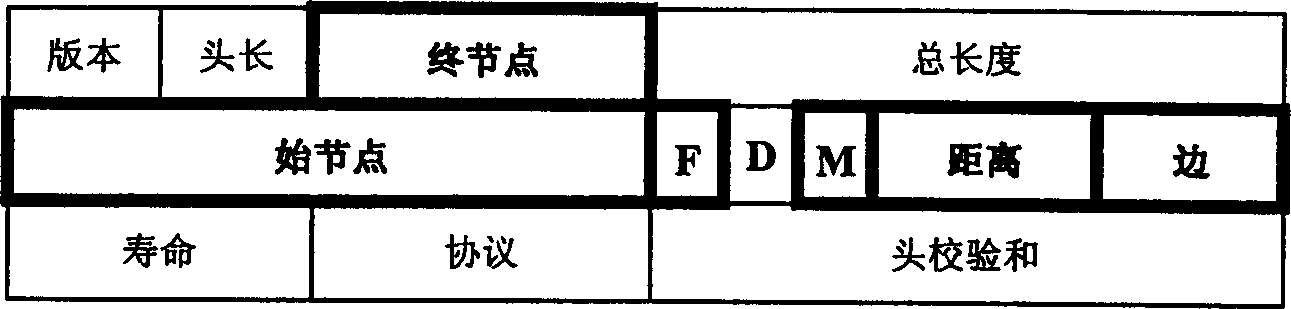
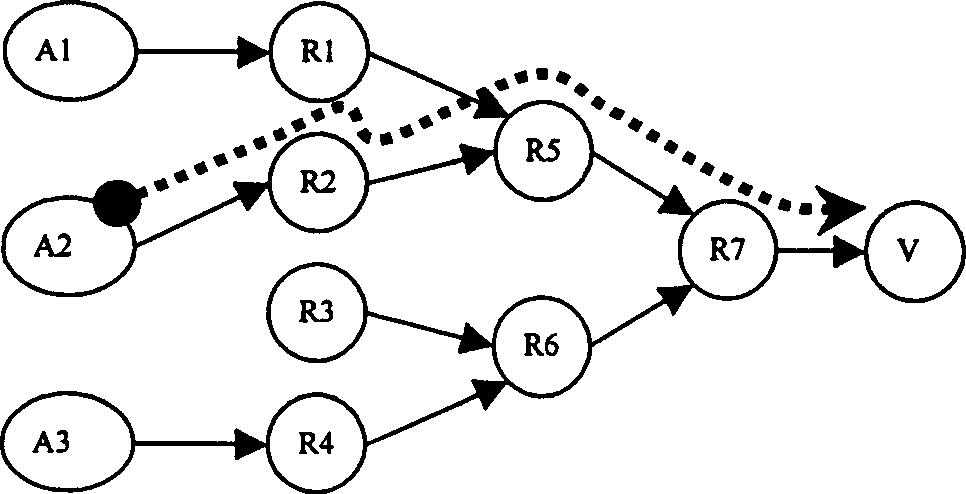
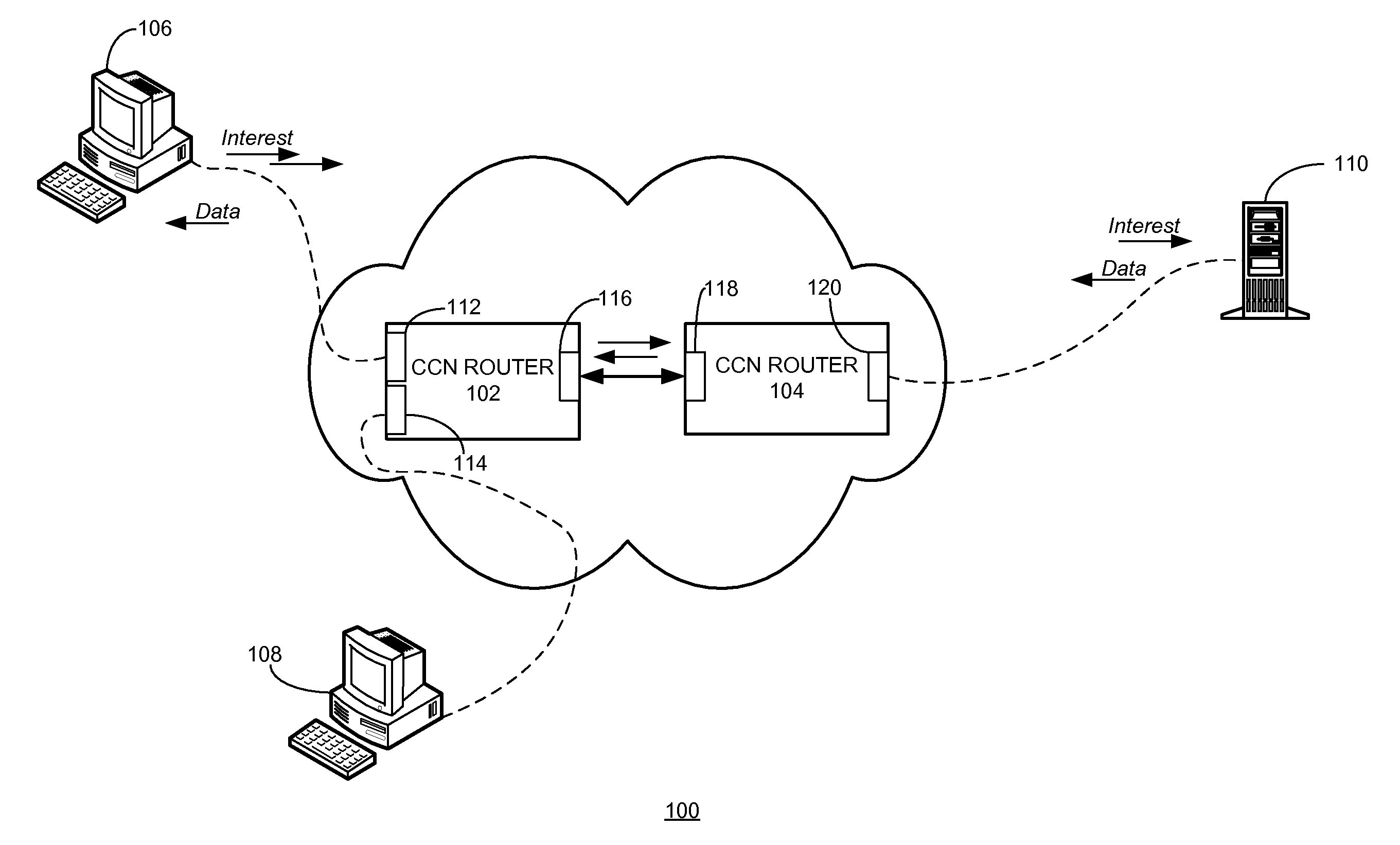
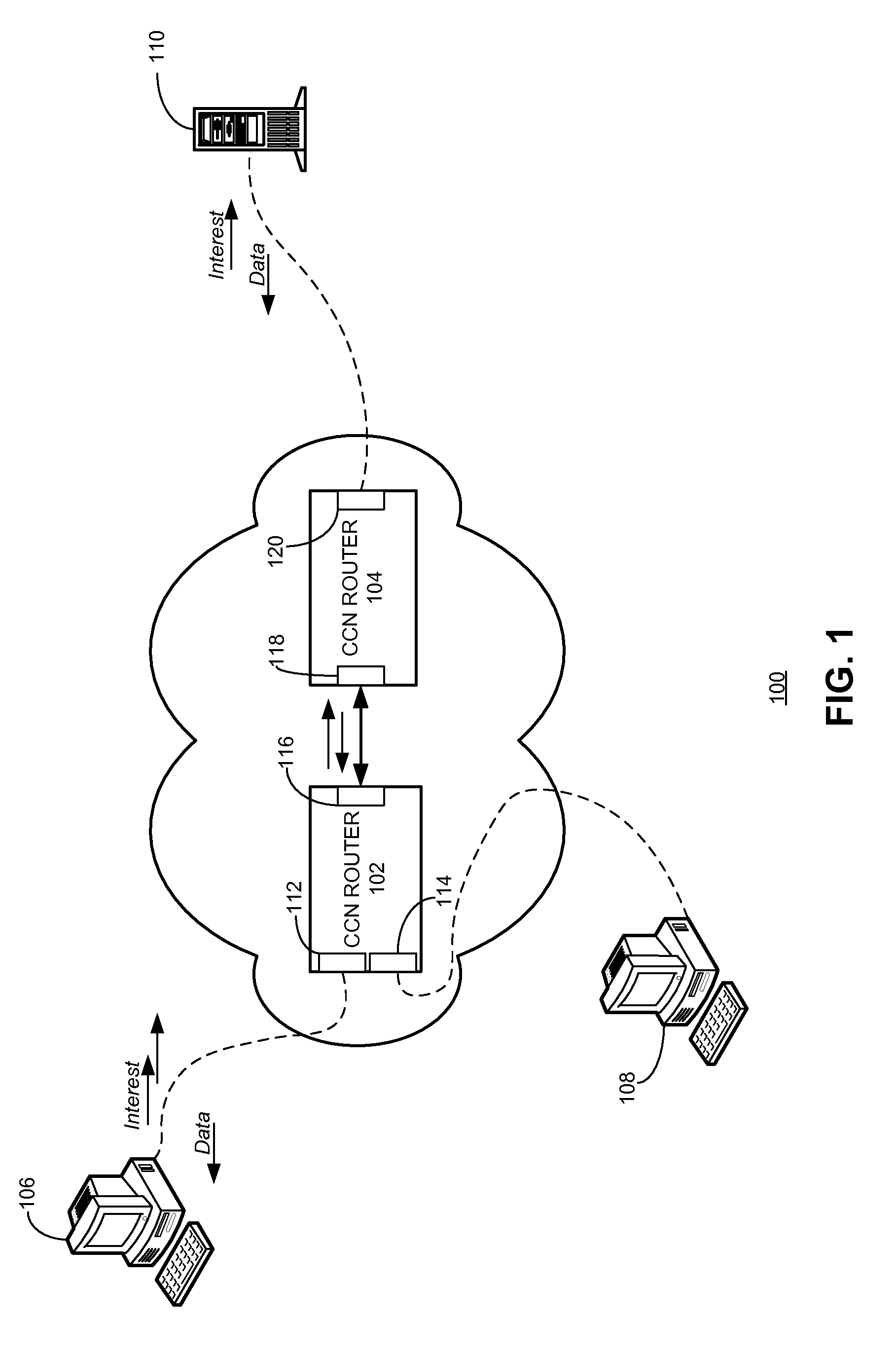
Method and system for mitigating interest flooding attacks in content-centric networks
ActiveUS20140351929A1Memory loss protectionError detection/correctionContent centricPhysical interface
One embodiment of the present invention provides a system for mitigating interest flooding attacks in content-centric networks (CCNs). During operation, the system receives, at a physical interface of a router, an interest packet; obtains current interest satisfaction statistics associated with the physical interface; and determines whether to forward or drop the interest packet based on the current interest satisfaction statistics.
Owner:CISCO TECH INC
Firewall of vehicle-mounted information system of automobile
ActiveCN105871830ABlock network communicationPrevent Hong Fan AttackTransmissionIn vehicleSecurity rule
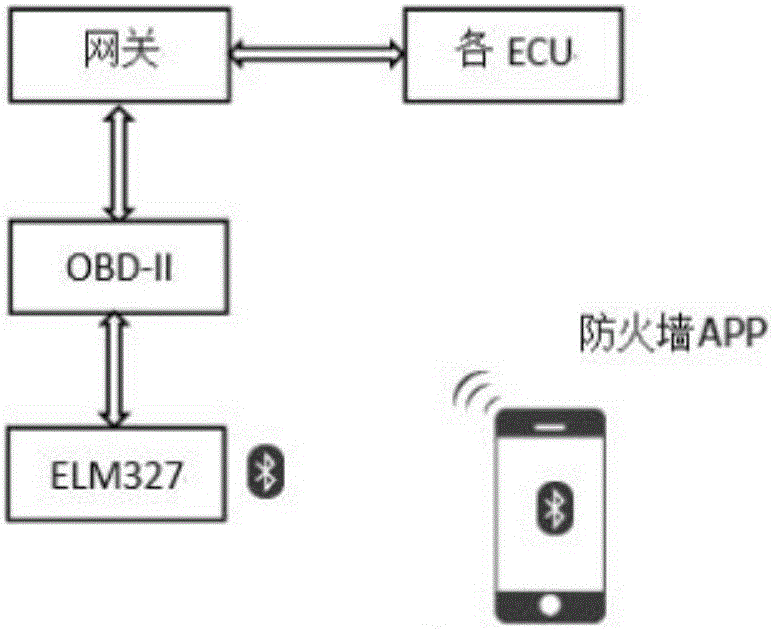
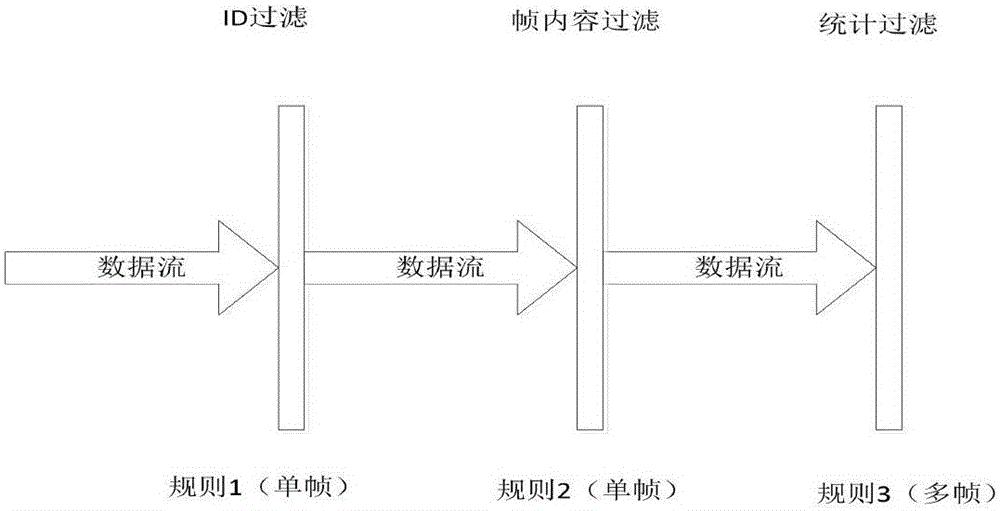
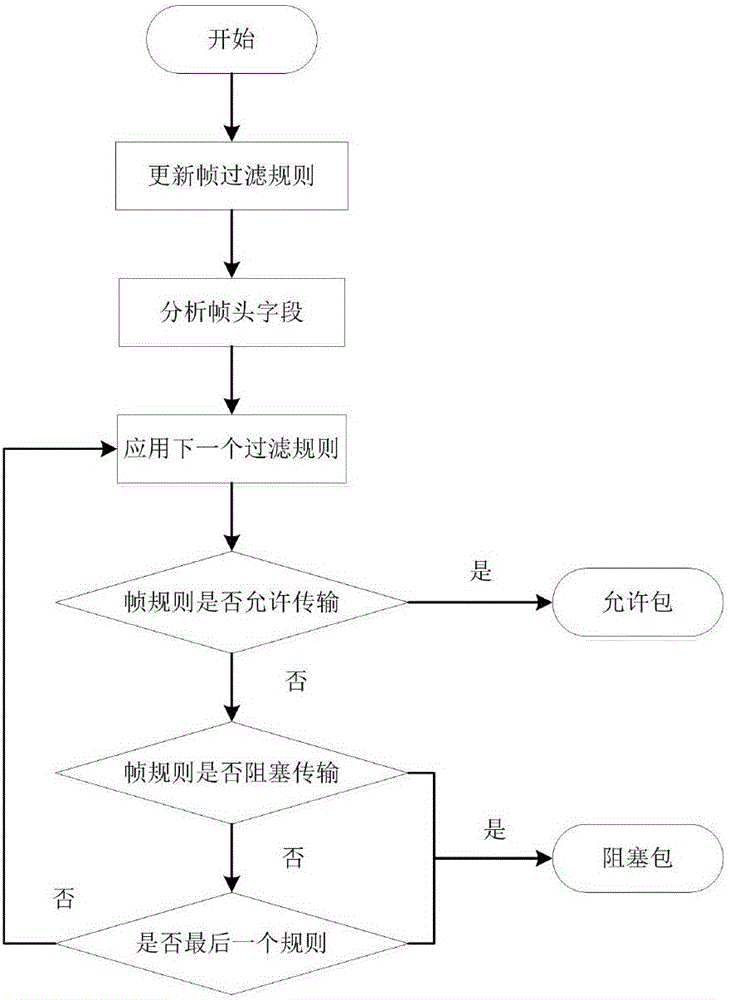
The invention discloses a firewall of a vehicle-mounted information system of an automobile. According to the firewall, a hardware platform is composed of a smart phone or a smart terminal connected with an external network. The firewall is an APP installed in the smart phone or the smart terminal. The firewall is the unique entry / exit for connecting the vehicle-mounted information system and the external network. Data enters a gateway in the automobile after passing through an ELM327 connected with the smart phone or terminal and then passing through an OBD-II connected with the ELC327. The data is forwarded to different intra-automobile buses by the gateway according to the features of the data. Finally the data enters corresponding ECUs for execution. The illegal data is filtered by security rules of the firewall and then is discarded. The firewall of the vehicle-mounted information system of the automobile comprises the ELM327, the OBD-II, the gateway, the ECUs and the firewall APP. According to the system, a flooding attack can be prevented and a service attack can be rejected through statistical rules; and a replay attack can be prevented through address filtration.
Owner:CHENGDU UNIV OF INFORMATION TECH
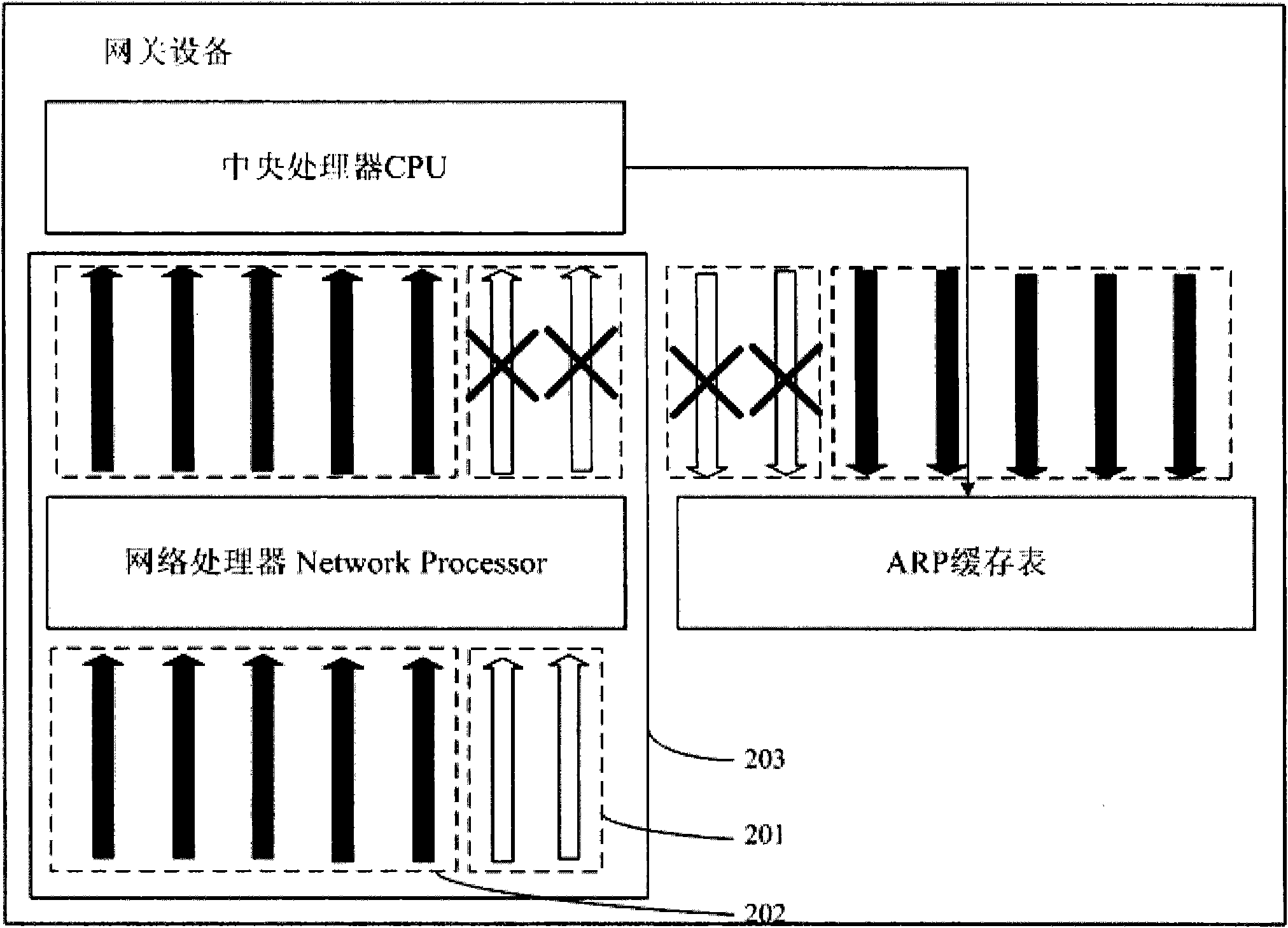
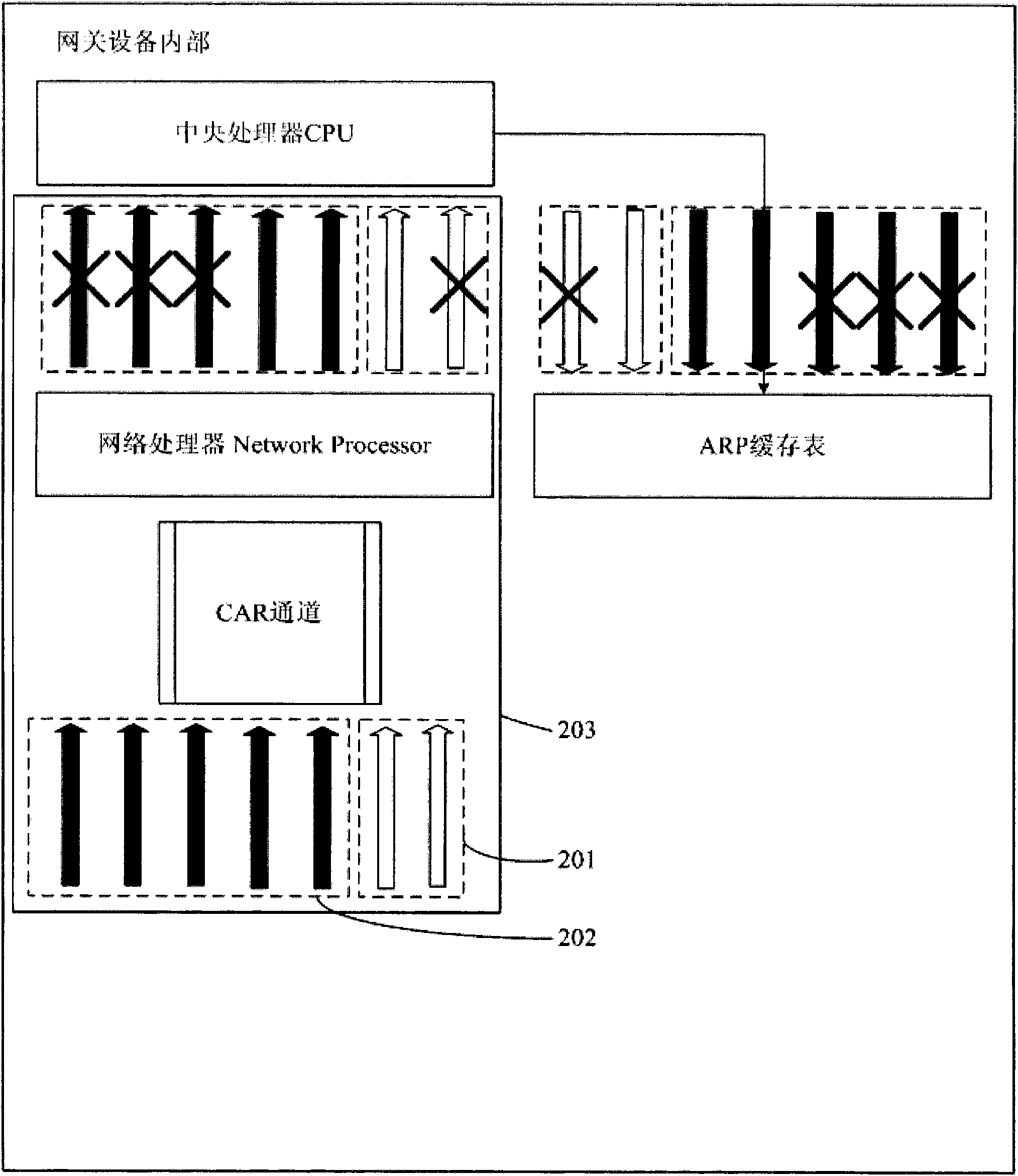
Flood attack prevention method and device
The embodiment of the invention provides a flood attack prevention method comprising the following steps of: carrying out CAR (Committed Access Rate) limitation on messages sent to different IP addresses, and respectively arranging CAR channels; and carrying out Hash processing on messages sent by all IP addresses based on IP addresses. The embodiment also provides a flood attack prevention device comprising a CAR limitation unit and a Hash processing unit based on IP addresses. According to the embodiment, normal flow messages can be separated from attach flow messages, so that the attach flow messages are filtered by the CAR channels due to large flow rate, and the normal flow messages are sent to a CPU to be processed through the CAR channels. The normal business running of attached equipment is ensured.
Owner:HUAWEI TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com