Increment deployment SDN network-based method for defending link flooding attack
A link flooding attack and network technology, which is applied in the direction of data exchange network, digital transmission system, electrical components, etc., can solve the problems that it is difficult for the server to directly detect abnormal traffic, difficult to detect, and indistinguishable, so as to eliminate Link flooding attack, the effect of defending against link flooding attack
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
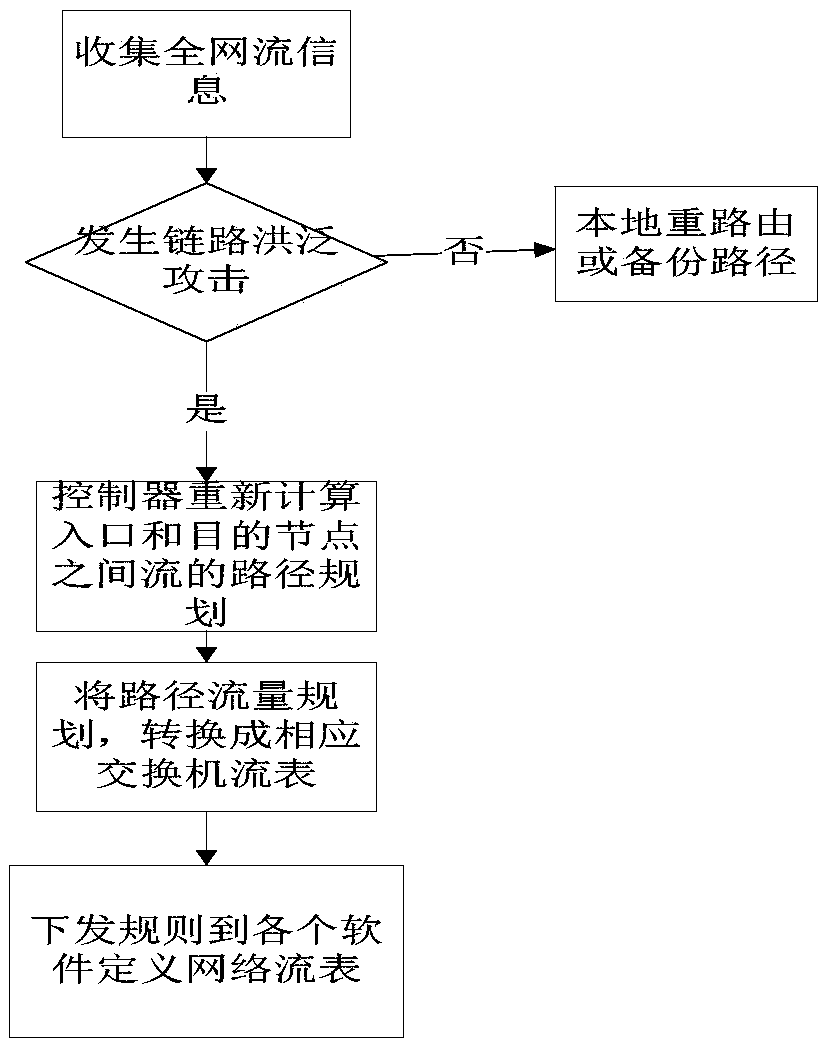
[0034] Algorithm example 1, defense mechanism algorithm framework in the present invention:
[0035]
[0036] 2. Node upgrade algorithm
[0037] 2.1 Problem description
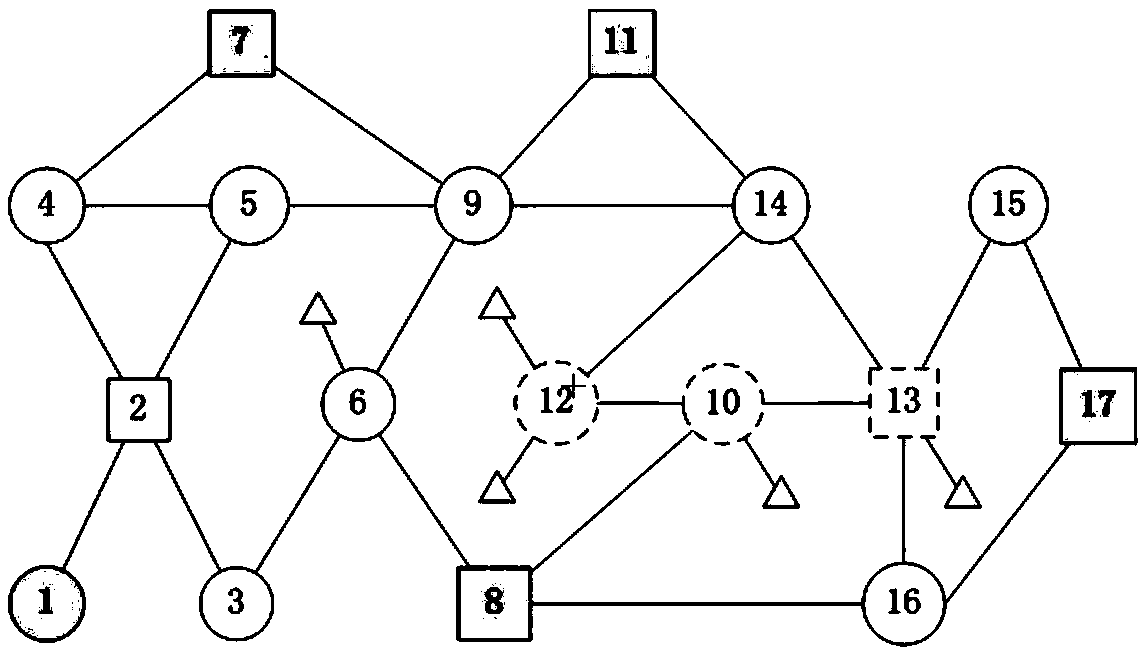
[0038] The node upgrade problem is mainly based on the network topology, as well as the distribution of entry nodes and target nodes, to select a group of nodes suitable for upgrading to software-defined network function nodes. The formal description is: For a given undirected graph G(V, E, S, D), where V is the set of all nodes in the graph, E is the set of all edges in the graph, S is the set of entry nodes, and D is A collection of destination nodes, from which m nodes are selected, which can increase the connectivity of the network to the greatest extent. The connectivity of the network here can be expressed as the communication path increased as much as possible in the entry node set and the exit node set.
[0039] 2.2 Algorithm description
[0040] Ideally, if the number of selected nodes m is la...
example 2
[0041] Algorithm example 2, upgrade node selection algorithm:
[0042]
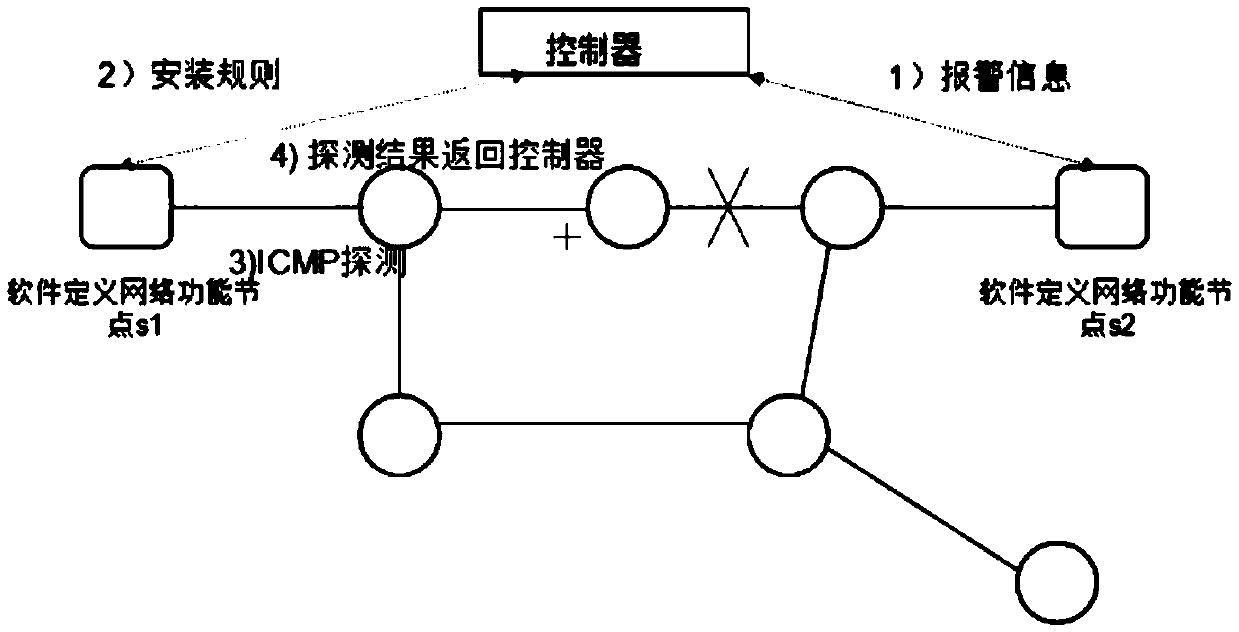
[0043] 3. Location and judgment of link flooding attack
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com