Wireless network security control method, device and wireless router
A security control and wireless network technology, applied in the fields of devices, wireless routers, and wireless network security control methods, can solve problems such as hidden dangers of local area network network security, equipment paralysis, network slowness, etc., and achieves sensitive response to flooding attacks and fast detection speed. , the effect of preventing flooding attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
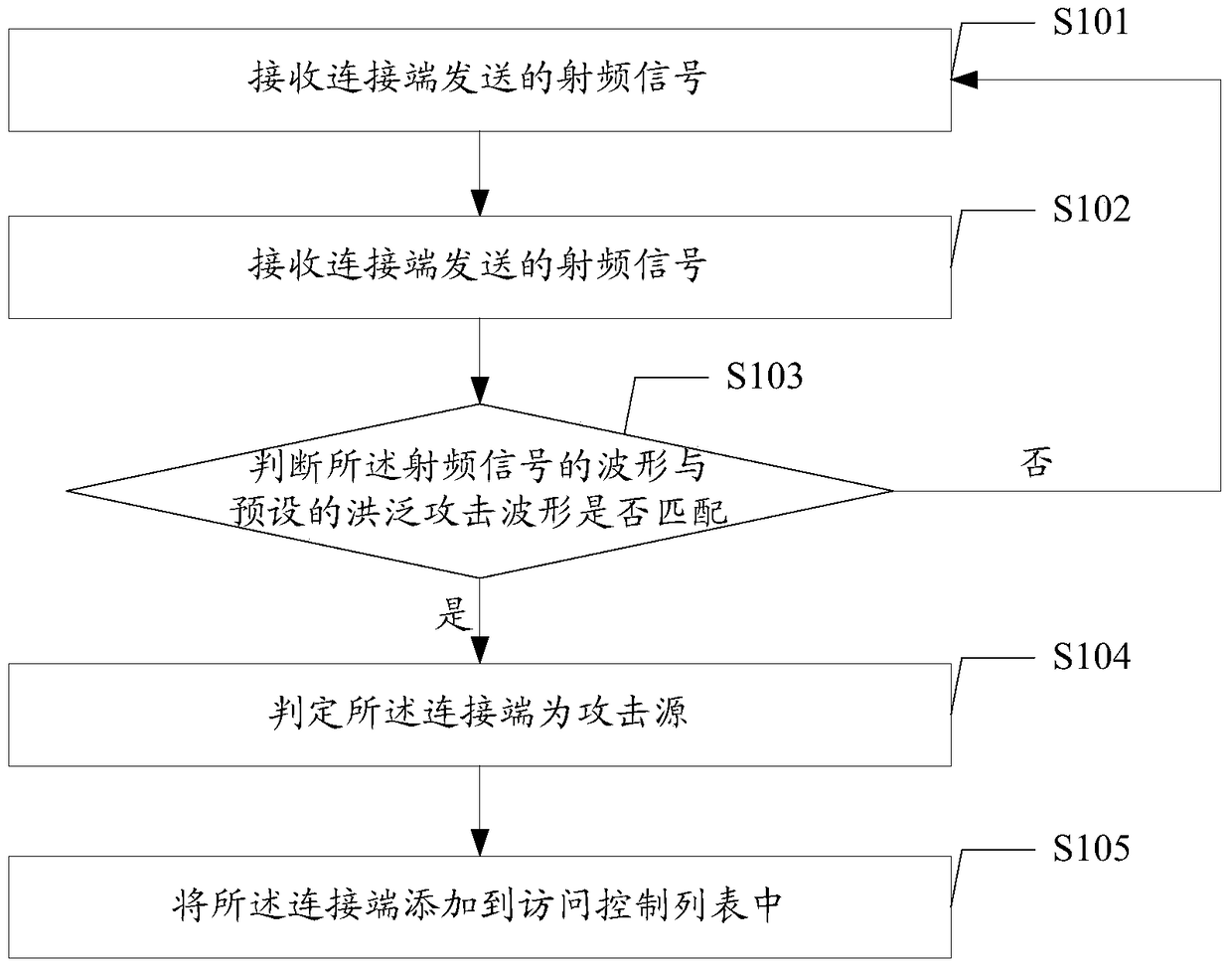
[0033] Currently, denial of service attack is a common and easy to cause serious damage among the attacks on wireless local area network. For example, in an ARP attack, attackers forge IP addresses and MAC addresses to perform ARP spoofing, and continuously send out response requests, thereby generating a large amount of ARP traffic in the network and seriously consuming network and device resources. For another example, the ICMP command can be used to check whether the network is unobstructed. By continuously sending ICMP data packets, the wireless LAN is bombarded, causing the network to be slow and even the equipment to be paralyzed. Existing wireless routers can realize the function of transmitting and receiving wireless signals and the function of data forwarding, but cannot effectively prevent the above-mentioned denial of service attacks, thereby causing hidden dangers to the network security of the local area network.
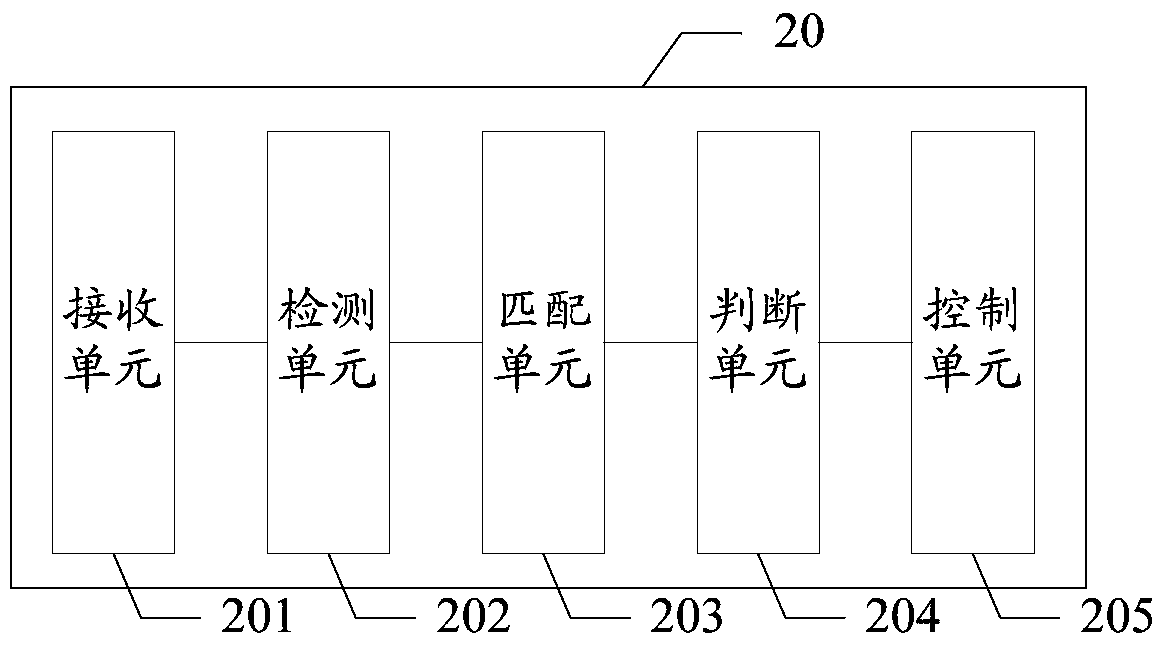
[0034] In the embodiment of the present invention...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com