Method for preventing flooding attack in wireless local area network
A technology of wireless local area network and flooding attack, which is applied in the field of defense against flooding attack, to achieve the effect of defending against flooding attack, the method is simple and feasible, and the effect is remarkable
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] see figure 1 , figure 2 As shown, the embodiments of the present invention will be described in detail.
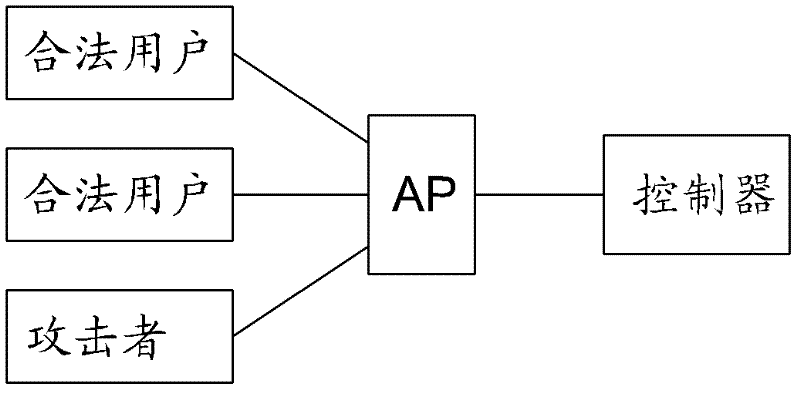
[0021] The way to launch flooding attacks now is mainly to send a large number of wireless management frames and wireless data frame messages, such as figure 1 , the attacker floods the AP by sending a large number of data frames and management frames. So many wireless data frames and wireless management frames will occupy a large amount of network bandwidth and AP device resources, and a large number of wireless management frames will also make other legitimate users frequently switch between authentication and deauthentication. The present invention solves the flooding attack aiming at this problem.
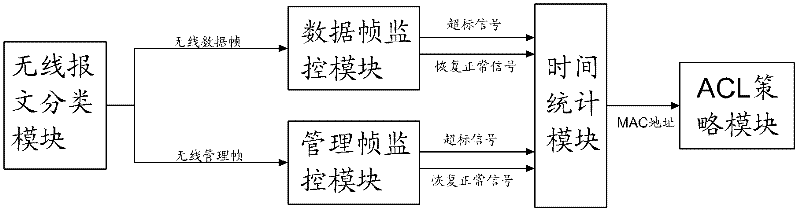
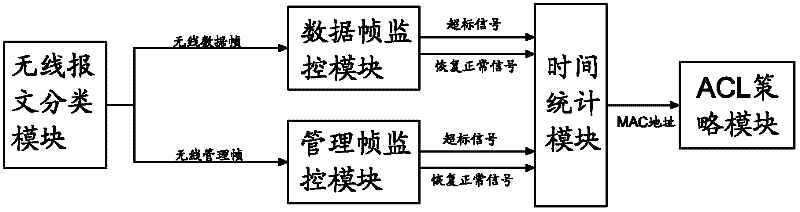
[0022] refer to figure 2 , the present invention is a method for defending against flooding attacks in a wireless local area network. The AP is provided with a wireless packet classification module, a data frame monitoring module, a management frame monitoring ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com