Protecting against distributed network flood attacks
A network device and network address technology, which is applied in the field of computer networks, can solve problems such as loss of income, customer dissatisfaction, and legal users cannot use it, and achieve the effect of reduced business traffic and good scalability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
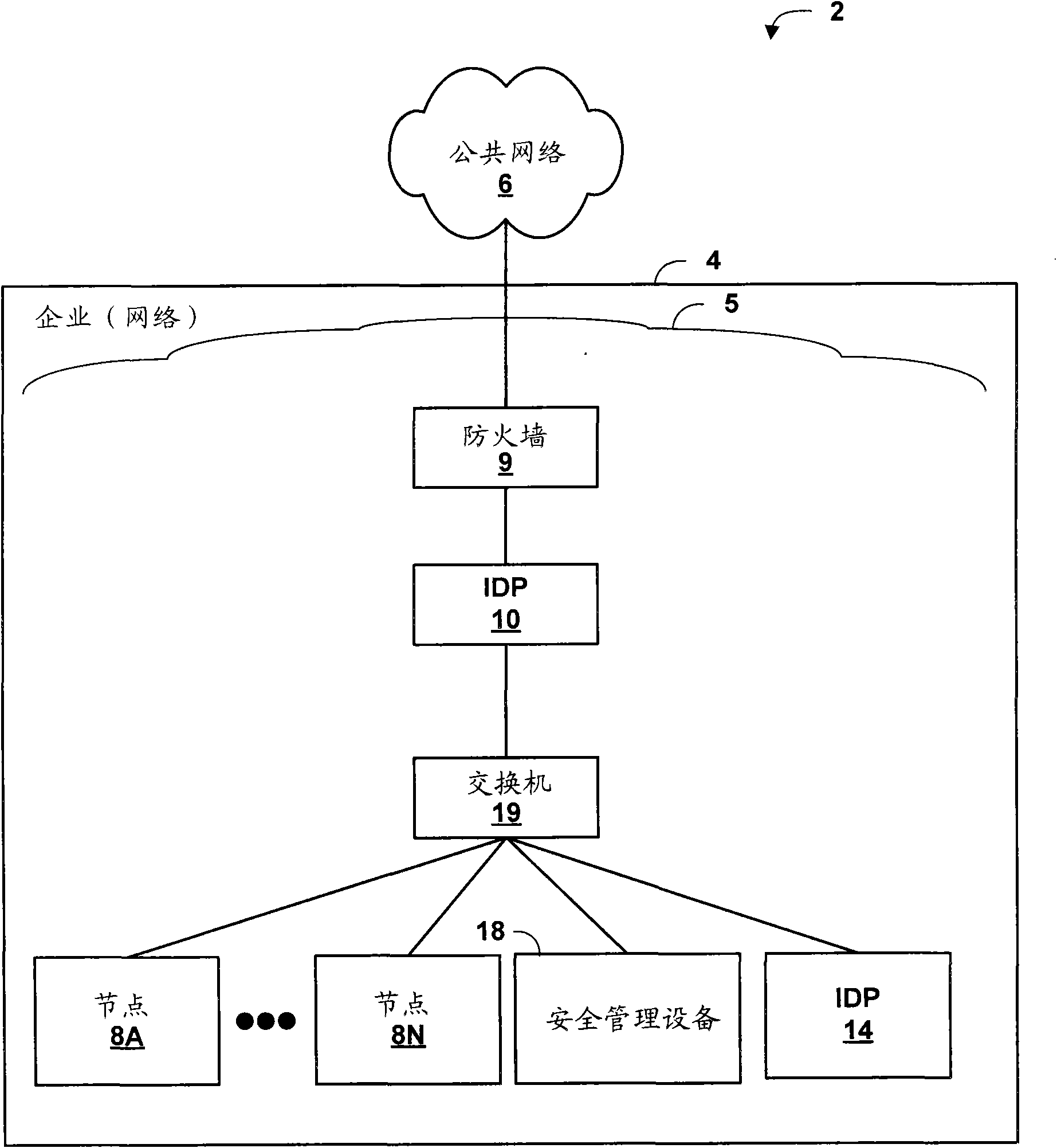
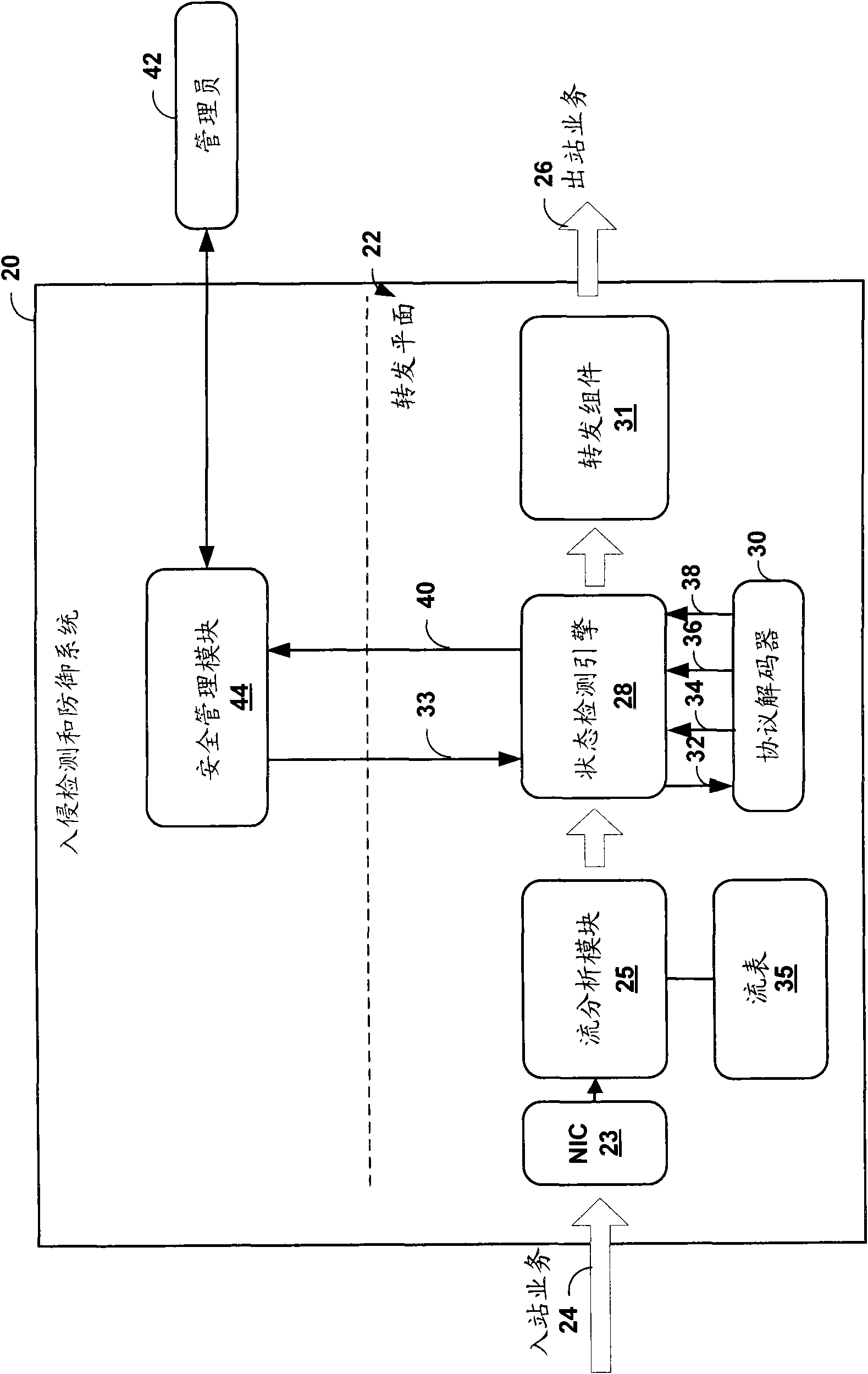
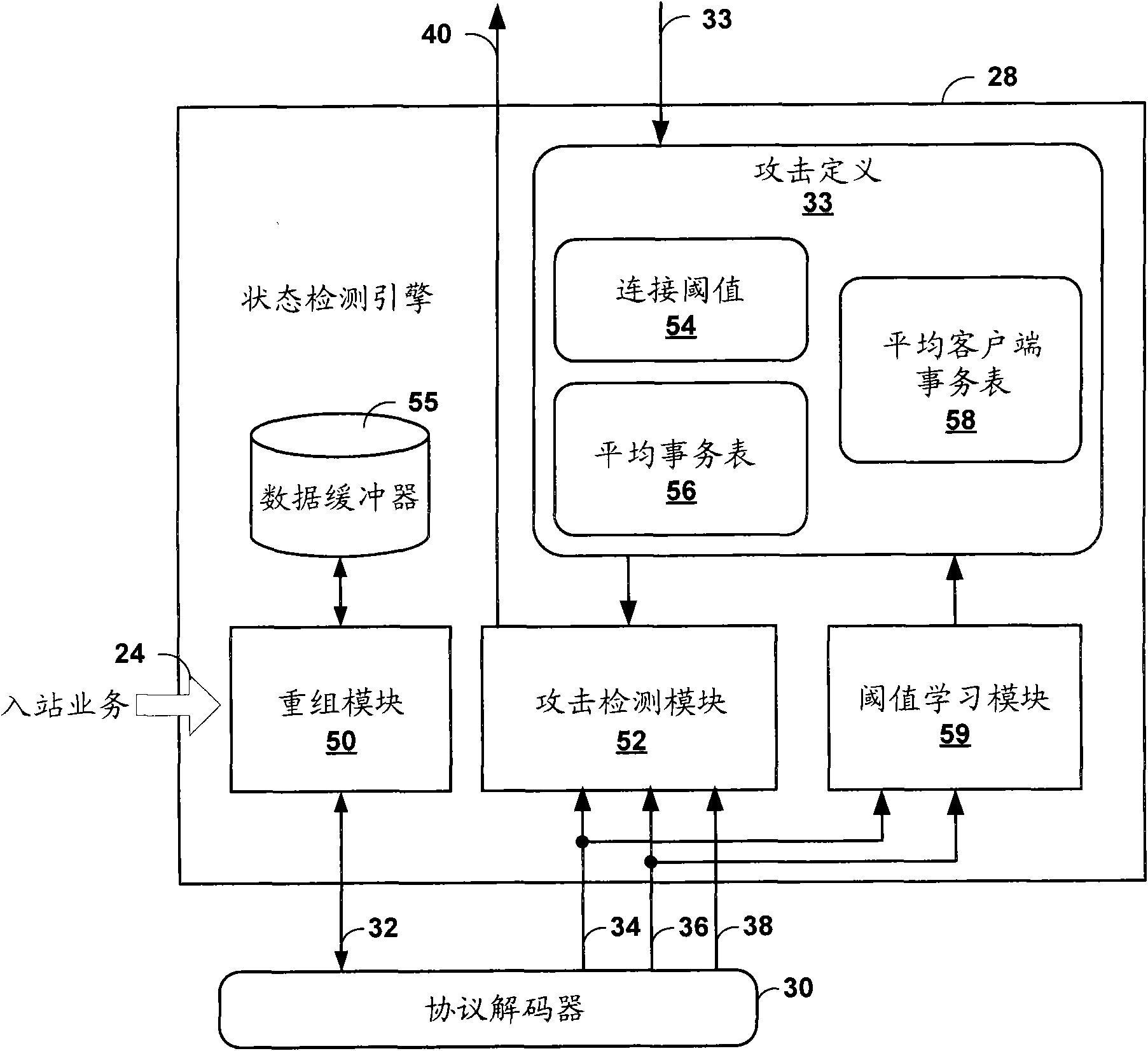
[0030] figure 1 is a block diagram illustrating an exemplary enterprise computer network 4 in which an intrusion detection and prevention (IDP) device 10 may attempt to prevent flooding initiated by malicious entities, such as malicious automated software agents, in accordance with the techniques in this disclosure attack. Although the IDP device 10 is mainly described, it should be understood that the techniques disclosed in the present invention may be implemented by any of various network devices. For example, a network device including a service plane for coupling general security service cards (including implementations of these technologies) or service cards specifically implementing these technologies may implement the techniques disclosed herein. Gateway devices, routers, hubs, firewalls, and servers are examples of network devices that may contain these service planes. Likewise, any network security device can implement the techniques disclosed in this invention. T...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com