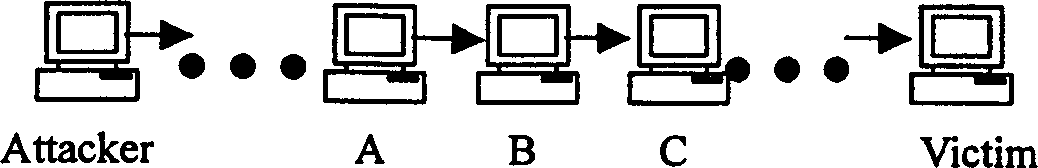
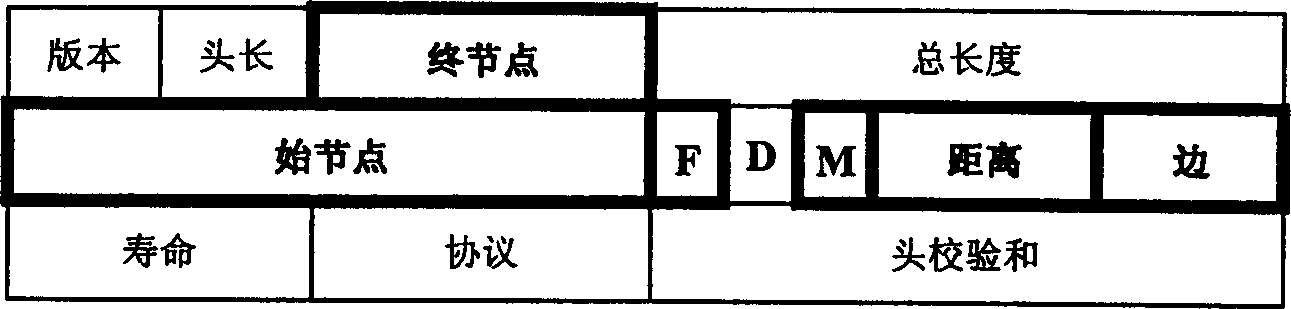
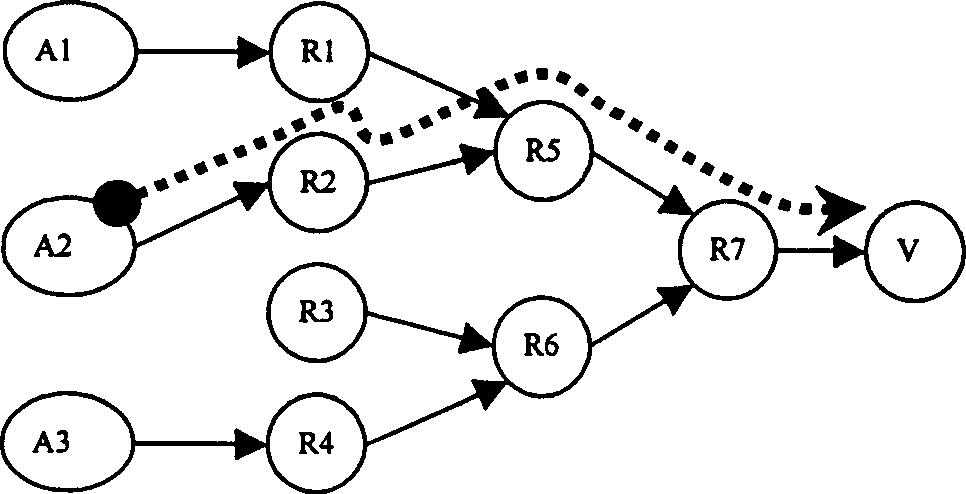
Efficient safety tracing scheme based on flooding attack
A flood attack and scheme technology, applied in the field of network security, can solve the problems of security, performance, and inability to implement algorithms
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0056] 1. Selection of marking probability:
[0057] Assuming that the length of an attack path is d, and all nodes on the path mark the data packets with probability p, the number of data packets required to reconstruct the path N 1 nd p ( 1 - p ) d - 1 . It can be seen from the formula that when reconstructing an attack path, the number of data packets required is very large. For example, when the length of the attack path is 20 and we select the marking probability as p=0.2, the upper bound of the number of packets required to reconstruct this path exceeds 1000. If the marking information fragments need to be marked in different packets, the requir...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com