Method for suppressing mac address attack in evi network and edge device ed
A MAC address and MAC address table technology, applied in electrical components, transmission systems, etc., can solve problems such as affecting the normal forwarding of data service traffic, affecting the normal forwarding of service traffic, occupying equipment CPU resources, etc., so as to guide normal forwarding and reduce usage. rate, and the effect of suppressing MAC address attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0036] In order to make the purpose, technical solution and advantages of the present application clearer, the present application will be described in detail below through specific embodiments and with reference to the accompanying drawings.
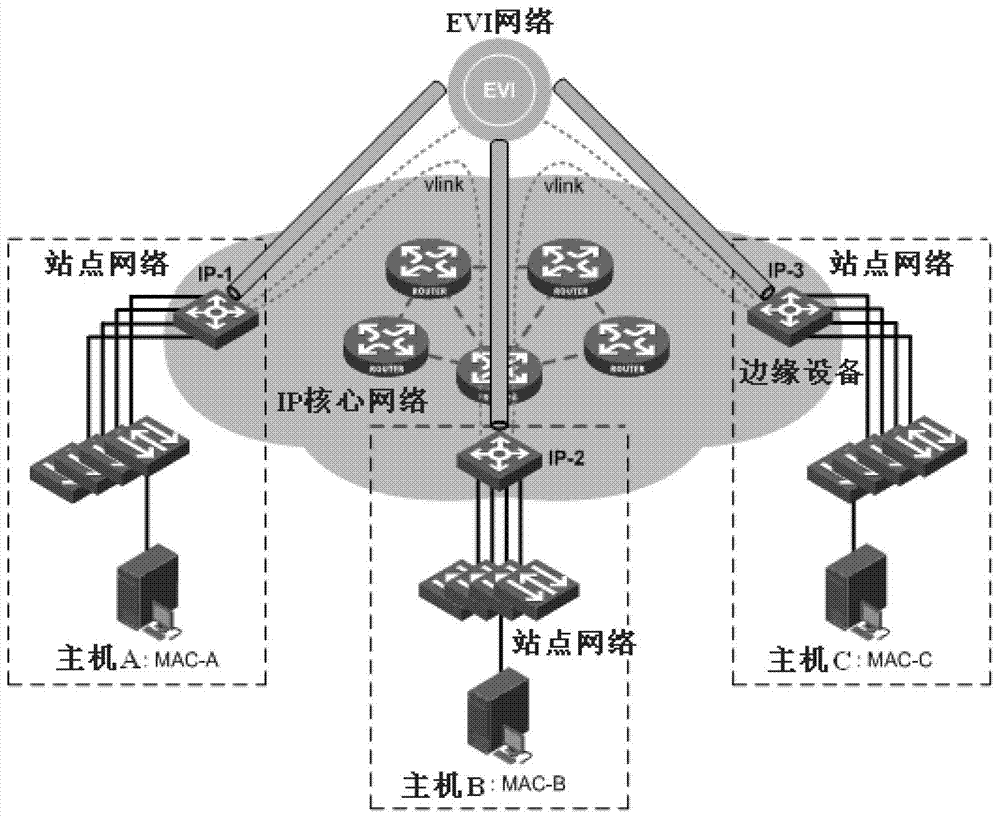
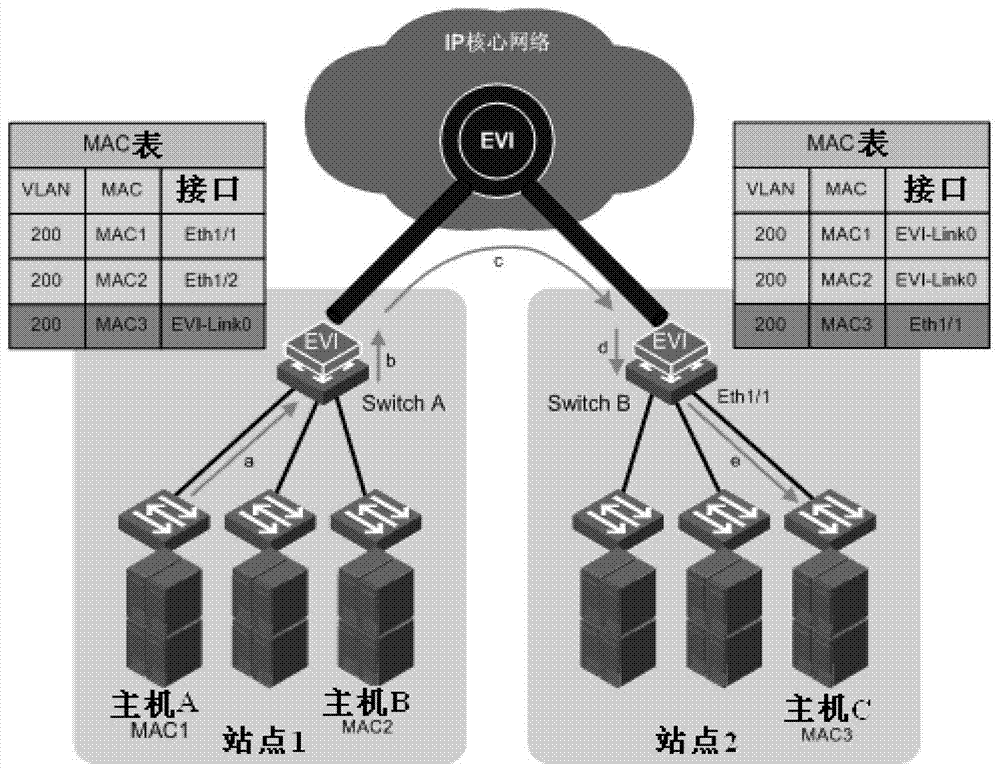
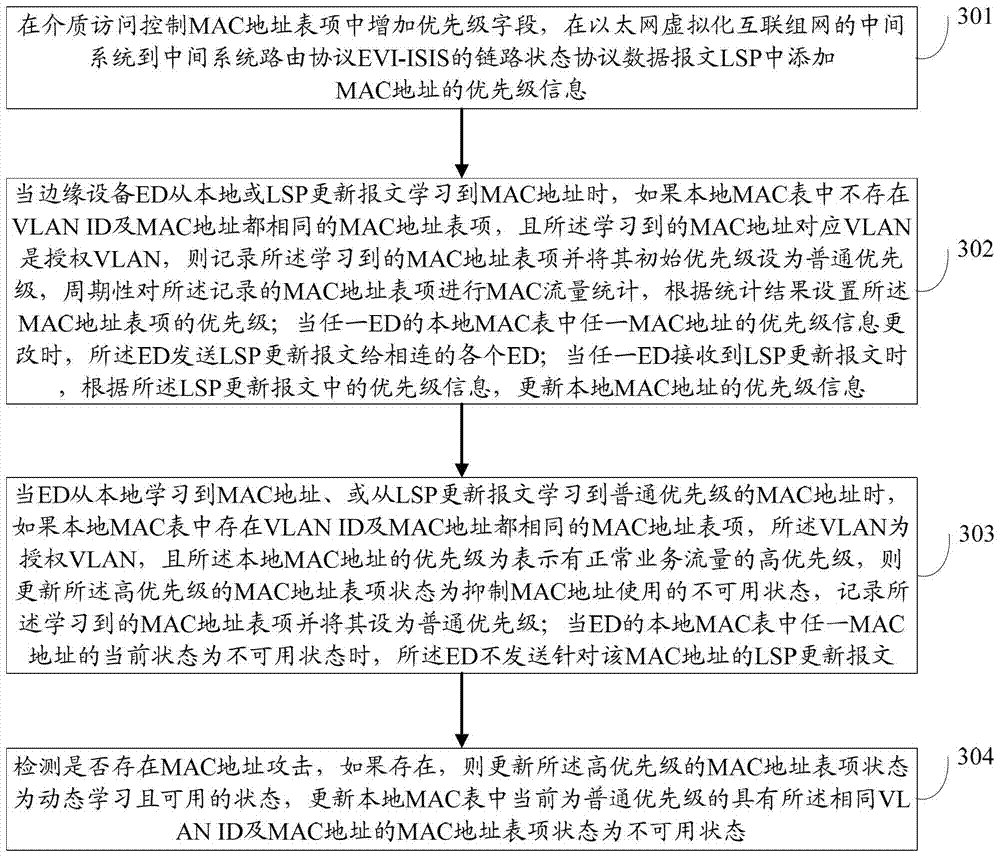
[0037] This application proposes a method for suppressing MAC address attacks in an EVI network, adding a priority field in the MAC address entry of the media access control, and connecting the intermediate system to the intermediate system EVI-ISIS routing protocol in the Ethernet virtualized interconnection network. Add the priority information of the MAC address in the data packet LSP of the road status protocol;
[0038] When the ED learns the MAC address from the local or LSP update message, if there is no MAC address entry with the same VLAN ID and MAC address in the local MAC table, and the VLAN corresponding to the learned MAC address is an authorized VLAN, then Recording the learned MAC address entry and setting its initial pri...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com