Device, system and method for reducing attacks on DNS
A detection device and unified technology, applied in the field of network security, can solve problems such as no suitable response strategy, and achieve the effect of low cost, simple implementation, and suppression of attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
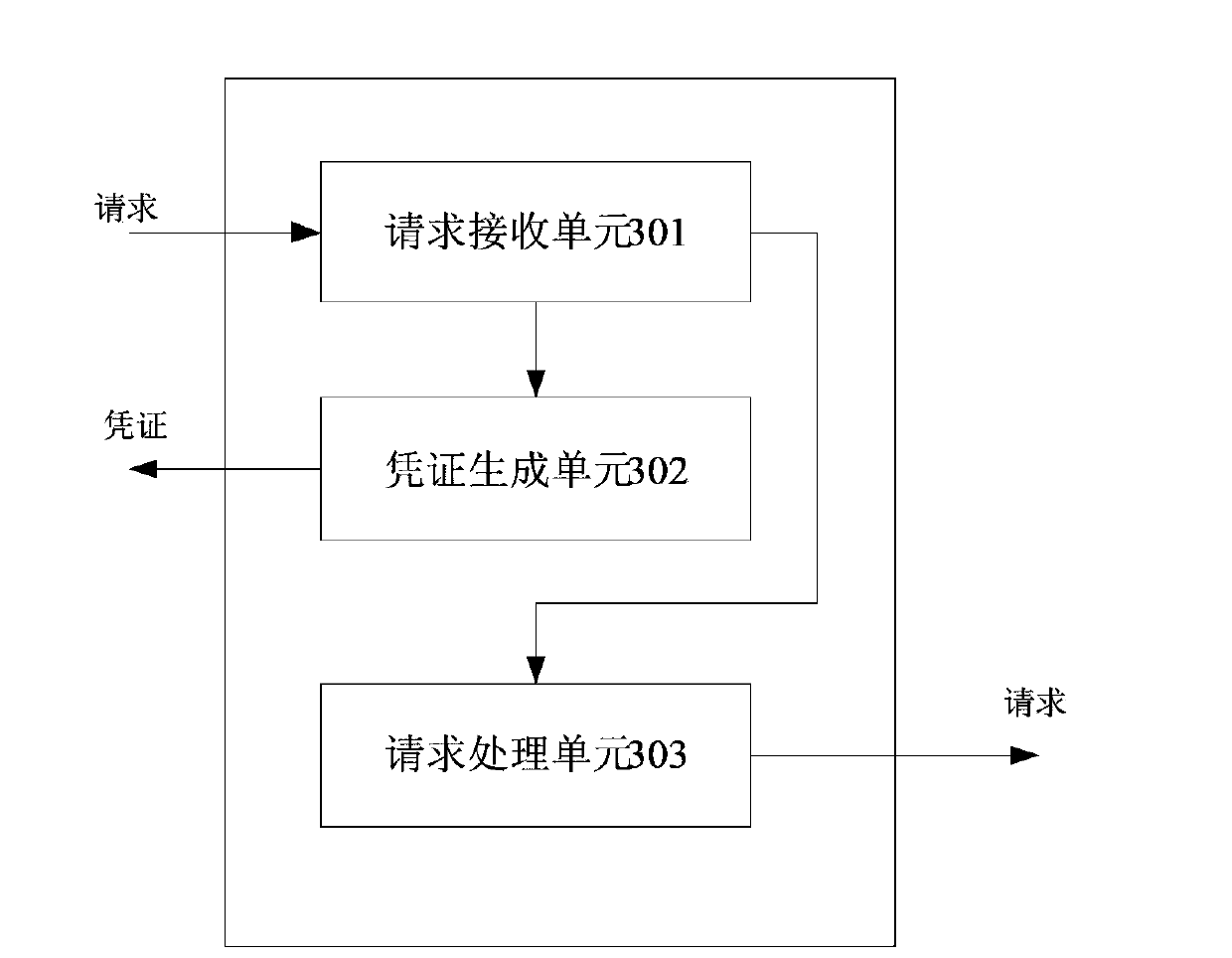
[0037] image 3 It is a structural diagram of a device for reducing attacks on DNS according to Embodiment 1 of the present invention. This means sits on the local recursive name server side of the DNS system. from image 3 It can be seen that the device includes a request receiving unit 301 , a credential generating unit 302 and a request processing unit 303 . The request receiving unit 301 receives the request sent by the parser of the client, forwards the request carrying the certificate to the request processing unit 303, and forwards the request not carrying the certificate to the certificate generating unit 302; the certificate generating unit 302 generates a request for not carrying the certificate Voucher, send the credential to the source IP address of the request, and store the generated credential; the request processing unit 303 judges whether the credential carried in the received request is correct according to the locally stored credential, and then forwards t...
Embodiment 2
[0047] Figure 4 It is a structural diagram of a device for reducing attacks on DNS according to Embodiment 2 of the present invention, and the device is located at the client side of the DNS system. from Figure 4 It can be seen that the device includes a request sending unit 401 , a credential receiving unit 402 and a request retransmitting unit 403 . Wherein, the request sending unit 401 is used to send a request to the local recursive name server side; the credential receiving unit 402 is used to receive the credential generated by the local recursive name server side; the request retransmission unit 403 is used to carry the credential in the request, and resend the request carrying the credential to the local recursive name server side.
Embodiment 3
[0049] Figure 5 It is a structural diagram of a system for reducing attacks on DNS in Embodiment 3 of the present invention. The system for reducing attacks against DNS in this embodiment includes a resolver 501 , a server-side detection device 502 and a local recursive name server 503 . The detection device 502 on the server side may adopt the device in Embodiment 1.
[0050] In the system of this embodiment, the server-side detection device 502 receives the first request sent by the parser 501, and if it is judged that the first request does not carry a certificate, it generates a certificate for the first request, stores the certificate, and sends the first request to the The resolver 501 of the source IP address of the request sends the certificate; after the resolver 501 receives the certificate, it generates the first request carrying the certificate, and resends the first request carrying the certificate to the local recursive name server 503; the server-side detectio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com