Method and firewall for preventing HTTP POST flooding attacks
A flooding attack and firewall technology, applied in the field of communication, can solve problems such as attacks that cannot be used to process POST requests, and achieve the effect of protecting security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
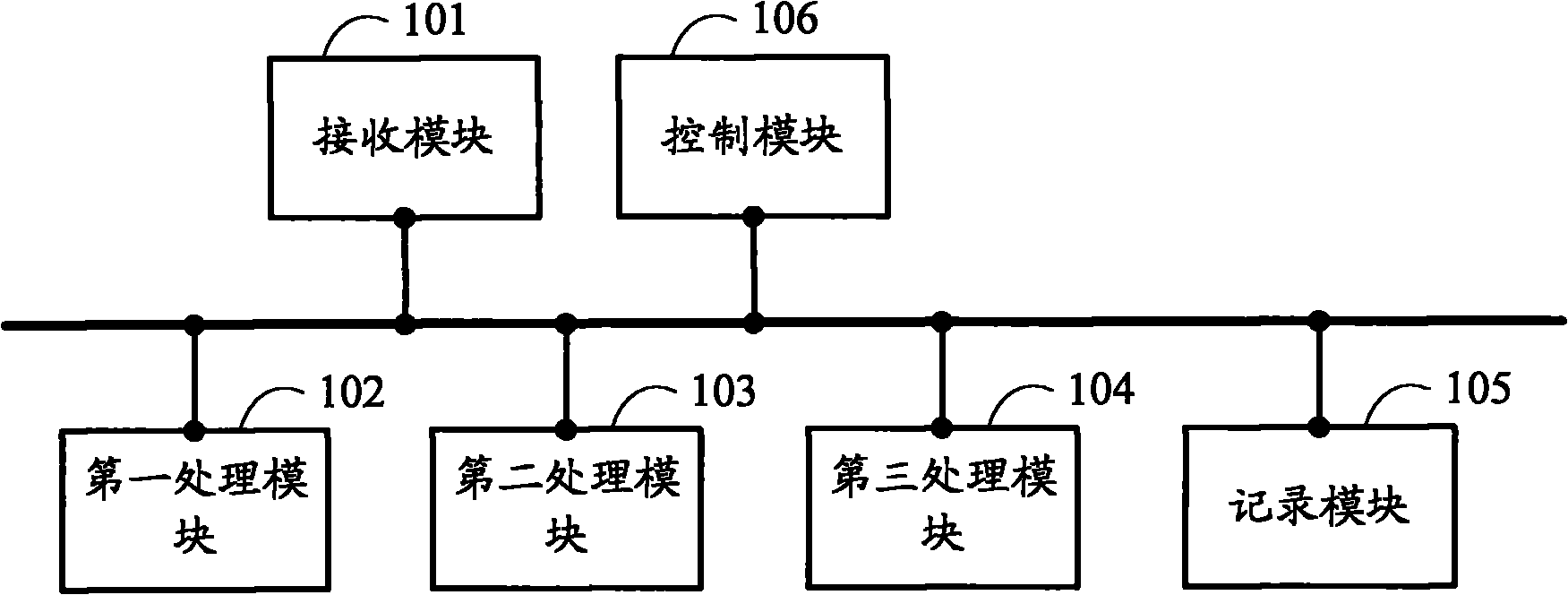
Image
Examples
Embodiment 1
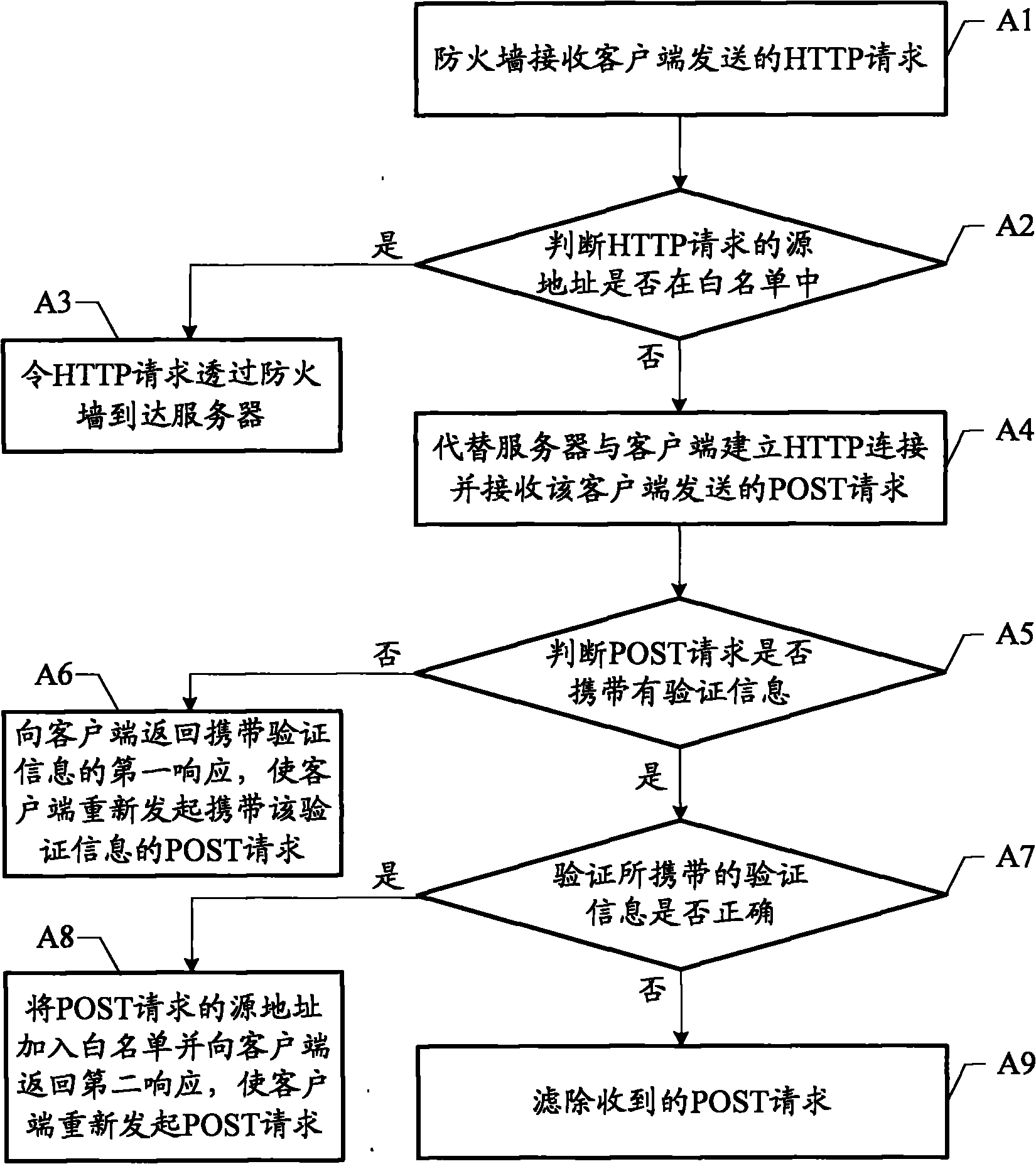
[0017] Embodiment 1. A method for preventing HTTP POST flood attacks, such as figure 1 shown, including:
[0018] A1. The firewall receives the hypertext transfer protocol HTTP request sent by the client.
[0019] In the embodiment of the present invention, the firewall can be deployed in a bypass or direct way. In the bypass deployment mode, the HTTP traffic of the upstream network is diverted to the firewall, and the firewall prevents HTTP attacks according to the method of the embodiment of the present invention. After cleaning and filtering the attack traffic, the normal HTTP access traffic is injected back to the downstream network. In the in-line deployment mode, the firewall directly defends against HTTP attack traffic from the upstream network. After filtering out the attack traffic, normal HTTP traffic enters the downstream network through the firewall.
[0020] The firewall can continue to use the method of this embodiment to defend against POST Flood attacks. Pref...
Embodiment 2
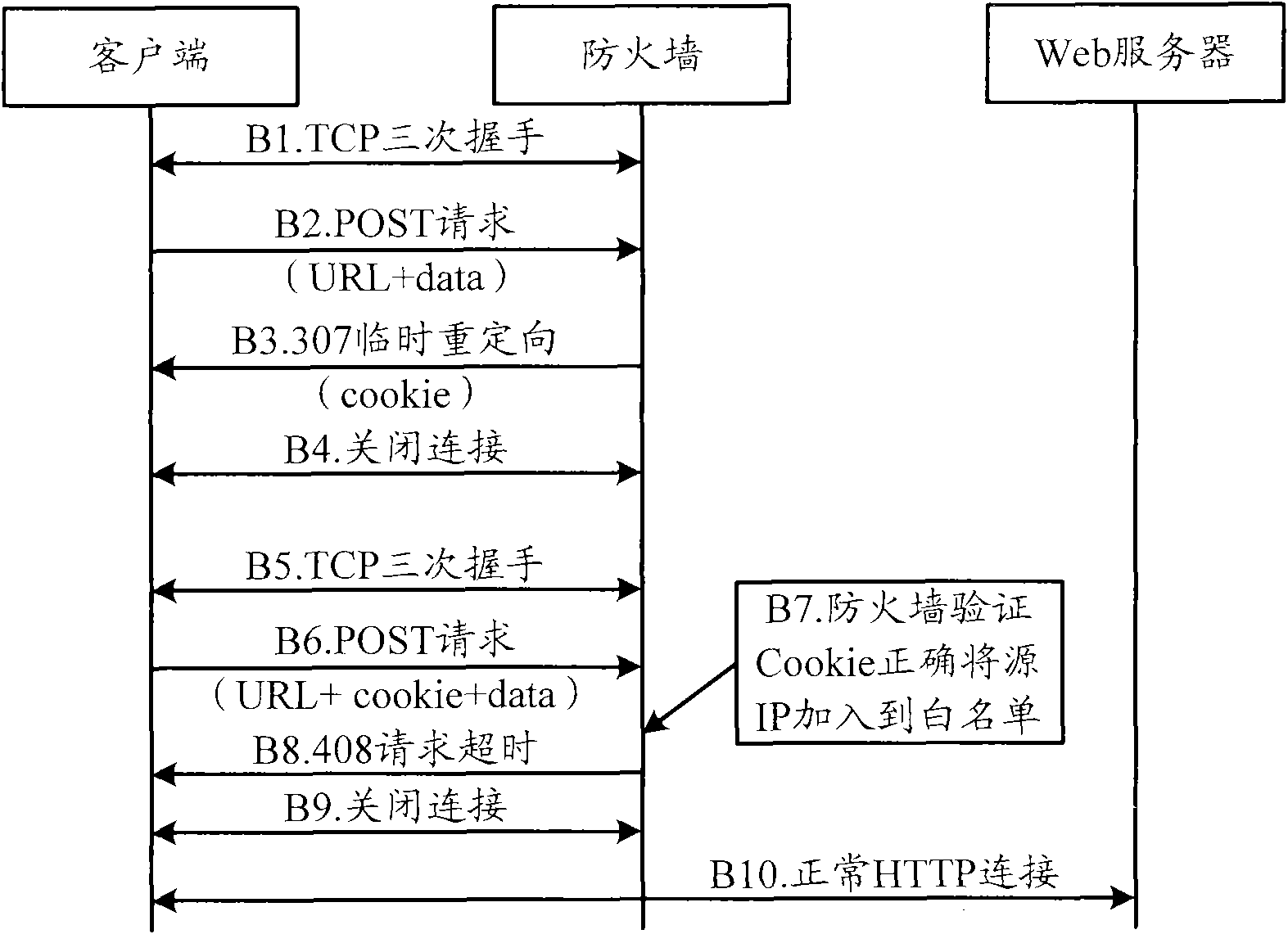
[0040] Embodiment 2. On the basis of Embodiment 1, this embodiment describes in detail the specific implementation process of using the cookie injection mechanism for prevention. In this embodiment, after the firewall detects that a POST Flood attack occurs, it starts the following defense process, wherein The signaling flow between the client and the firewall is as follows: figure 2 shown, including:
[0041] B1. The firewall receives the HTTP request sent by the client. The source IP of the client is not in the white list. The firewall replaces the web server with the client for three handshakes. After the TCP connection is successful, it is written into the source IP monitoring table, recording the number of verifications of the source IP and timestamp.
[0042] B2. The firewall receives the HTTP POST request sent by the client. The request carries the requested URL and data. Since it is the first time that the client sends the POST request, no authentication information ...
Embodiment 3
[0066] Embodiment 3. This embodiment provides an example in which the method of Embodiment 1 adopts the HTML page form (Form) automatic submission technology.
[0067] The specific execution process of this embodiment is similar to that of Embodiment 2, the difference is that:
[0068] When the firewall responds to the HTTP POST request sent by the client for the first time, it uses "200 success" as the first response (corresponding to step B3), and carries the verification information through a simple form page in the message part of the 200 response.
[0069] Specifically, the form page may include a text box and an auto-submit button, the content of the text box is a random verification code used as verification information, and the auto-submit button is used to make the client re-initiate the form that carries the text box. POST request, the automatic submission button can use the HTML onload method and Javascript scripting language to make the client browser automatically...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com